Secure Internet Channeling Agent for Searching and Delivering Media Content
- 格式:pdf
- 大小:377.14 KB
- 文档页数:36

Kaspersky Embedded Systems Security管理员指南应用程序版本:2.2.0.605尊敬的用户:感谢您选择Kaspersky Lab 作为您的安全软件提供商。
我们希望本文档能帮助您使用我们的产品。
注意!本文档是AO Kaspersky Lab(以下简称Kaspersky Lab)的资产。
本文档的所有权利受俄罗斯联邦版权法和国际条约保护。
根据适用法律,非法复制和分发本文档或部分文档需承担民事、行政或刑事责任。
未经Kaspersky Lab 的书面许可,不得对任何材料进行任何类型的复制或分发,包括译本形式。
本文档和与之相关的图形图像只能用于信息参考、非商业和个人目的。
Kaspersky Lab 保留在没有事先通知的情况下修改本文档的权利。
对于本文档所用第三方所有的任何材料的内容、质量、相关性或准确性,或与使用此类文档相关的任何潜在损害,Kaspersky Lab 不承担任何责任。
本文档使用的注册商标和服务标志属于各自的所有者。
文档修订日期:2018.12.06© 2018 年 AO Kaspersky Lab 版权所有。
保留所有权利。
https://https://内容关于本指南 (10)本文内容 (10)文档约定 (12)有关Kaspersky Embedded Systems Security 2.2 的信息来源 (13)独立检索信息源 (13)在论坛上讨论Kaspersky Lab 应用程序 (14)Kaspersky Embedded Systems Security 2.2 (15)关于Kaspersky Embedded Systems Security 2.2 (15)新增功能 (17)分发包 (18)硬件和软件需求 (19)安装和卸载应用程序 (21)Kaspersky Embedded Systems Security 2.2 软件组件以及它们在Windows Installer 服务中对应的代码 (21)Kaspersky Embedded Systems Security 2.2 软件组件 (22)软件组件的“管理工具”集 (23)安装Kaspersky Embedded Systems Security 2.2 后系统的更改 (24)Kaspersky Embedded Systems Security 2.2 进程 (27)Windows Installer 服务的安装和卸载设置及命令行选项 (27)Kaspersky Embedded Systems Security 2.2 安装和卸载日志 (31)安装计划 (32)选择管理工具 (32)选择安装类型 (33)使用向导安装和卸载应用程序 (34)使用安装向导安装 (35)Kaspersky Embedded Systems Security 2.2 安装 (35)Kaspersky Embedded Systems Security 2.2 控制台安装 (37)在其他计算机上安装应用程序控制台以后的高级设置 (38)在安装Kaspersky Embedded Systems Security 2.2 后执行的操作 (40)修改组件集和恢复Kaspersky Embedded Systems Security 2.2 (42)使用安装向导卸载 (43)Kaspersky Embedded Systems Security 2.2 卸载 (43)Kaspersky Embedded Systems Security 2.2 控制台卸载 (44)从命令行安装和卸载应用程序 (45)关于从命令行安装和卸载Kaspersky Embedded Systems Security 2.2 (45)在安装Kaspersky Embedded Systems Security 2.2 后执行的操作 (47)添加/删除组件。
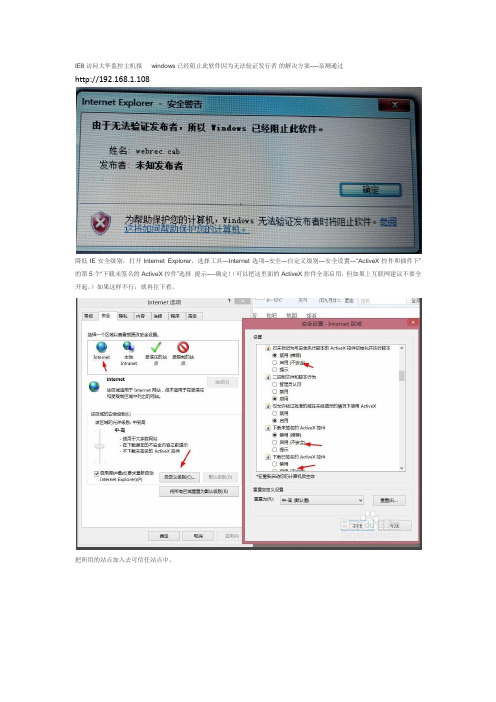
IE8访问大华监控主机报windows已经阻止此软件因为无法验证发行者的解决方案----亲测通过
http://192.168.1.108
降低IE安全级别,打开Internet Explorer,选择工具---Internet选项--安全---自定义级别---安全设置---“ActiveX控件和插件下”的第5个“下载未签名的ActiveX控件”选择提示----确定!(可以把这里面的ActiveX控件全部启用,但如果上互联网建议不要全开起。
)如果这样不行,就再往下看。
把所用的站点加入去可信任站点中。
再把可信任站点中的级别再降低,把里面的ActiveX控件和插件下的全部启动。
刷新一下如果可以就行了,如果不行再往下设置。

broadcast-probe reply disablebroadcast-probe reply disable是一种网络设置的功能,它可以禁用网络广播探测的回复。
广播探测是广播一条消息,然后等待网络上所有的设备回复,以确定网络上的设备数量和类型。
这可以帮助管理员识别网络中的设备并进行故障排查。
然而,在某些情况下,禁用广播探测的回复可能是有用的。
一种常见的情况是在网络中存在大量的设备,这样会导致广播探测的回复产生大量的网络流量。
在某些情况下,网络流量可能会造成网络拥塞,并影响正常的网络通信。
此时,禁用广播探测的回复可以有效减少网络流量,提高网络的性能和稳定性。
另一种情况是在网络中存在安全隐患的情况下,禁用广播探测的回复可以增加网络的安全性。
广播探测的回复可以泄露网络上存在的设备,包括类型、版本等信息,这可能会被黑客用来进行网络攻击和入侵。
通过禁用广播探测的回复,可以减少黑客获取有关网络设备的信息的机会,从而提高网络的安全性。
为了禁用广播探测的回复,可以按照以下步骤进行操作:1. 登录到网络设备的管理界面。
这通常需要管理员账户和密码。
2. 寻找关于广播探测的配置选项。
这在不同的设备上可能有所不同,可以参考设备的用户手册或询问设备制造商的技术支持。
3. 在广播探测的配置选项中,找到相关的设置项。
可能会有一个名为"broadcast-probe reply"的选项。
4. 将该选项的值设置为"disable"。
有些设备可能使用其他关键字或选项来实现相同的功能,可以根据设备的文档或技术支持找到正确的设置。
5. 保存更改并重新启动网络设备。
在重新启动后,网络设备将禁止回复广播探测。
需要注意的是,禁用广播探测的回复可能会影响一些网络的功能和管理任务。
例如,一些网络管理工具可能依赖广播探测来识别设备并进行管理操作。
在禁用广播探测的回复之前,应该对网络进行细致的分析和评估,以确保禁用这个功能不会对网络的正常运行造成不利影响。
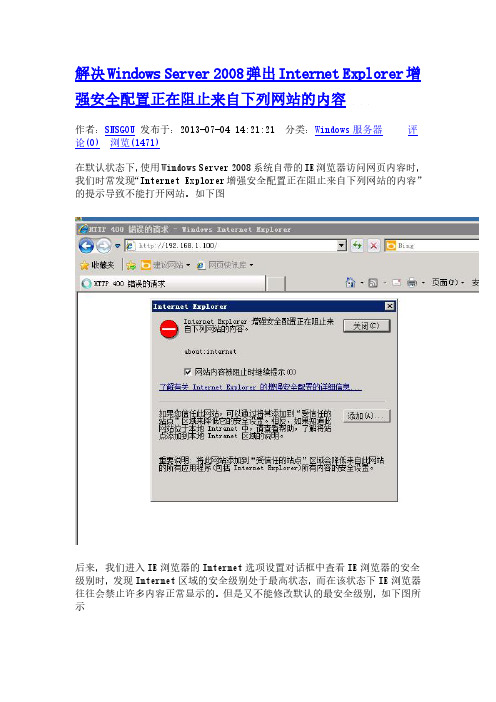
解决Windows Server 2008弹出Internet Explorer增强安全配置正在阻止来自下列网站的内容作者:SNSGOU发布于:2013-07-04 14:21:21 分类:Windows服务器评论(0)浏览(1471)在默认状态下,使用Windows Server 2008系统自带的IE浏览器访问网页内容时,我们时常发现“Internet Explorer增强安全配置正在阻止来自下列网站的内容”的提示导致不能打开网站。
如下图后来,我们进入IE浏览器的Internet选项设置对话框中查看IE浏览器的安全级别时,发现Internet区域的安全级别处于最高状态,而在该状态下IE浏览器往往会禁止许多内容正常显示的。
但是又不能修改默认的最安全级别,如下图所示解决方案如下:其实造成这种故障的最主要原因就是Windows Server 2008系统新增加了IE增强安全配置功能,在该功能在默认状态下会处于启用状态,这时我们就无法随意改变IE浏览器安全区域上的安全级别。
要想自行改变IE浏览器安全区域上的安全级别,我们只要按照如下步骤取消IE增强安全配置功能的启用状态就可以了:首先在Windows Server 2008系统环境下关闭所有已经打开的IE浏览器窗口,之后依次单击“开始”->“程序”->“管理工具”->“服务器管理器”命令(其实,在“搜索”中直接搜索“服务器管理器”即可!),在弹出的服务器管理器窗口中,找到“安全信息”设置项,单击其中的“配置IE ESC”选项,打开如下图所示的IE增强安全配置窗口在“管理员”下,选中“禁用”选项,同时在“用户”下,选中“禁用”选项,最后单击“确定”按钮,那样一来Windows Server 2008服务器系统就能将IE增强安全配置功能临时关闭了。
这样重启浏览器后再打开网页就不会出现安全提示!。
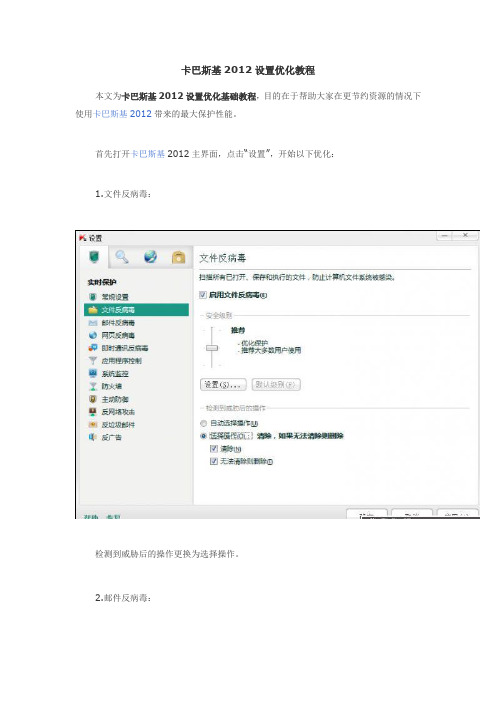
卡巴斯基2012设置优化教程
本文为卡巴斯基2012设置优化基础教程,目的在于帮助大家在更节约资源的情况下使用卡巴斯基2012带来的最大保护性能。
首先打开卡巴斯基2012主界面,点击“设置”,开始以下优化:
1.文件反病毒:
检测到威胁后的操作更换为选择操作。
2.邮件反病毒:
检测到威胁后的操作更换为选择操作。
3.网页反病毒:
检测到威胁后的操作更换为阻止下载。
点击“设置”,勾上”阻止危险网站“4.即时通讯反病毒:
保护范围更改为仅接受的信息,启发分析调为轻度扫描。
5.应用程序控制:
取消信任具有数字签名的信任程序,未知程序自动移至低限制组。
6.系统监控:
检测到恶意软件活动时,选择操作,终止恶意程序。
检测到要回滚恶意软件操作时,选择操作,恢复。
7.主动防御:
取消具有数字签名的信任程序,点击设置,隐藏对象及隐藏进程设为120或更长。
8.反网络攻击:
将攻击计算机添加到阻止计算机列表的时间更改为3分钟或更短。
9.全盘扫描,关键区域扫描,自定义扫描(三个都如此设置) 检测到威胁后的操作,选择操作,清除无法清除则删除。
点击设置,勾上仅扫描新建和已更改的文件
10.报告,隔离和备份设置:
存储报告不超过更改为三天,最大文件大小更改为20,存储对象不超过三天。
可根据情况自己更改!
11.卡巴斯基安全部队显示设置
勾上当执行任务是激活托盘图标,取消开启新闻通知。
12.免疫更新
取消“更新后扫描隔离区”。

一、什么是 User-Agent在网络通信中,User-Agent 是客户端软件(通常是网页浏览器)中包含的一个特殊字符串标识。
它用于向全球信息站服务器传递有关客户端身份的信息,以便服务器能够根据客户端特性返回适当的内容或进行适当的处理。
二、User-Agent 的组成User-Agent 字符串通常包含了客户端软件的名称、版本号、操作系统信息等内容。
一个典型的 User-Agent 可能是这样的:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36这个 User-Agent 描述了一个使用了 Chrome 87 浏览器的 Windows 10 操作系统客户端的信息。
通过这个信息,服务器能够对请求做出相应的处理。
三、User-Agent 的作用1. 浏览器兼容性:全球信息站服务器可以根据 User-Agent 的信息,选择性地返回兼容特定浏览器的内容,以保证最佳的浏览体验。
2. 流量统计和分析:全球信息站可以通过收集 User-Agent 信息,对访问者的使用习惯、偏好等进行统计和分析,为优化全球信息站内容和用户体验提供数据支持。
3. 安全防护:全球信息站服务器可以根据不同 User-Agent 的特征,进行黑白名单策略的制定,以防范恶意请求和攻击行为。
四、User-Agent 的变化与隐私保护随着隐私保护意识的增强,越来越多的用户开始关注自己的隐私安全。
一些浏览器和全球信息站为了保护用户隐私,采取了对 User-Agent进行匿名化处理的策略,从而减少客户端信息的泄露。
但是,同时也有一些危害用户隐私的行为,如一些恶意软件利用伪装的 User-Agent 信息,骗取服务器信任以进行恶意操作。
五、User-Agent 的定制和修改一些高级用户可能需要自己定制或修改 User-Agent 信息,来适应特定的访问需求。
netconf message framing error
“netconf message framing error”的意思是“网络配置消息帧错误”。
这种错误可能是由多种原因导致的,例如:
- 网络设备故障:设备可能存在硬件或软件问题,导致无法正确处理网络配置消息。
- 配置错误:网络配置可能存在语法错误或不符合网络设备的要求。
- 网络连接问题:网络连接可能由于网络拥塞、干扰或其他原因而不可靠,导致消息丢失或损坏。
为了解决这个问题,可以尝试以下方法:
- 检查网络设备的配置:确保配置正确且符合设备的要求。
- 检查网络连接:确保网络连接可靠,没有干扰或其他问题。
- 重启网络设备:有时重启设备可以解决临时性问题。
- 联系网络设备供应商:如果问题仍然存在,请联系设备供应商寻求技术支持。
如果你对“netconf message framing error”的解决方法还有其他疑问,可以继续向我提问。
windows 10 mmagent用法-回复Windows 10中的mmagent是一个强大的命令行工具,它可以让用户在系统上运行各种管理和监控任务。
在这篇文章中,我们将根据以下主题逐步介绍mmagent的用法和功能。
1. 什么是mmagent- mmagent是Windows 10操作系统中自带的一个命令行工具,可以用于管理和监控系统。
- mmagent通过提供一系列命令和参数,可以让用户执行各种系统管理任务,例如文件操作、进程管理、性能监控等。
2. 安装和配置mmagent- mmagent是Windows 10操作系统中默认安装的,所以不需要额外安装。
- 若要配置mmagent,可以通过编辑mmagent的配置文件或使用命令行选项来更改工具的行为。
3. mmagent的基本用法- mmagent的命令行语法通常是“mmagent [命令] [参数]”,用户可以根据自己的需求输入不同的命令和参数组合。
- 像其他命令行工具一样,mmagent也可以通过在命令后加上“/?”或“-h”来获取帮助信息和具体命令的使用方法。
4. 文件操作命令- mmagent提供了一系列文件操作命令,例如复制文件、移动文件、删除文件等。
- 用户可以使用这些文件操作命令来管理文件和文件夹,如创建、删除、修改文件的属性等。
5. 进程管理命令- mmagent还提供了一些进程管理命令,可以让用户查看系统中运行的进程、启动和停止进程等。
- 这些进程管理命令对于识别和终止恶意进程或处理占用过多系统资源的进程非常有用。
6. 系统性能监控命令- mmagent还具备一些系统性能监控命令,允许用户实时监控系统的性能指标,如CPU使用率、内存使用情况等。
- 用户可以使用这些性能监控命令来识别系统性能瓶颈,了解系统的状态并进行有效优化。
7. 远程管理命令- 除本地管理外,mmagent还支持远程管理。
用户可以使用适当的命令和参数,连接到远程计算机,执行命令并获取结果。
Secure Internet Channeling Agentfor Searching and Delivering Media ContentJohn J. Parkjpark@CONTENTS1.INTRODUCTION 41.1Motivation 41.2Problem Statement 45Statement1.3Thesis5REVIEW2.LITERATURE5DeliveryContent2.1MediaCachingProxy6Media2.1.1Distribution8Media2.1.2Content2.1.3 Peer-to-Peer Media File Sharing 10P2P 10Unstructured2.1.3.111P2P2.1.3.2Structured2.2Control and security Issues in Media Content Delivery 1214RESEARCH3.PROPOSED3.1Architecture of Secure Internet Channeling Agent (SIChA) 143.1.1Fundamental Concepts and techniques 14SIChAof163.1.2NetworkOverview3.1.3Sequential workflow under SIChA system 1821SIChA3.1.4Functionaloverviewof3.1.4.1Media searching and delivering control 223.1.4.2Network channel key control 23Evaluation23and3.2Implementation3.2.1Implementation 243.2.2Evaluation 283.3UniqueContributions 29 4.REFERENCES 311.INTRODUCTIONThis document proposes a research project in the area of searching and delivering media content over the Internet. The particular focus is on a third party trusted Internet agent service which would provide secure and controllable media content delivery. This proposal is organized as follows: section 1 presents the motivation for searching and delivering systems of media content. It presents a problem statement of media content delivery technologies, and provides a thesis statement for a secure Internet channeling agent. In section 2, I review the literature on media proxy caching, media content distribution, and peer-to-peer file sharing. In the first part of section 3, I explain the architecture for a Secure Internet Channeling Agent (SIChA). In the latter part of section 3, I propose an implementation and an evaluation of the proposed architecture. I conclude this proposal with a research schedule and an approximate dissertation outline in sections 4 and 5.1.1MotivationMore efficient media content delivery technology over the Internet has enabled Web media users around the world to transfer media content from a media server to browsers on various user devices. Today’s Internet is increasingly used to deliver media contents, namely, video, audio, and graphics.1.2Problem StatementDespite impressive efforts to implement media content delivery technology in all its aspects, there is still a lack of optimized network connections and trustworthy security formedia content. Since media content delivery technologies connect both unknown users and media providers, each having different systems and locations, it is difficult to build reliable and trusted connections.1.3 Thesis StatementA third party trusted Internet agent service, with specialized protocols to optimize and secure the network media connections, can support media content delivery in a way that is effective, efficient, reliable, secure, and trustworthy.2.LITERATURE REVIEWMedia content delivery strategies have been developed using several approaches. In this literature review, I will introduce a concept of media content delivery strategy and describe the existing research papers on three separate methods: media proxy caching, media content distribution and peer-to-peer media file sharing. Also, I will discuss some implementation problems with these approaches.2.1Media Content DeliveryDigital content data on the Web are scattered all over network servers, and can be accessed by users from around the world. Although users can easily retrieve digital content from the Internet, there are troubles with the access time and process. These troubles are mainly because of congested network links, queuing delays, network packet loss, network latency, and heavy server loads. In order to reduce the network problems,most content delivery architectures replicate the content in separate servers in the network, and direct user requests to a server that is determined to be optimal. This architecture allows content to be positioned in appropriate locations for the end users while minimizing network bandwidth, the original server load, and user latency.Recently, many researchers have shown interests in the field of delivery architecture for streaming video and audio. Streaming video and audio are classified as continuous media contents that transfer meaningful data only when presented in an appropriate period of time. Systems that deliver continuous media content through the Internet should provide sufficient quality of service, secure encoding, and efficient streaming video and audio across distributed computing networks from source servers to media users. Transmission of continuous media content typically increases bandwidth consumption, imposes heavy server load, and creates network latency. The current research for content delivery architectures addresses the field of streaming multimedia over the Internet and media content delivery. The media content delivery method consists of three primary technologies: media proxy caching, media content distribution network, and peer-to-peer media file sharing. The following sections address the particular issues and review major approaches and mechanisms.2.1.1 Media Proxy CachingThe first architecture, proxy cache, tries to locate media content close to the users. This has become a popular approach to reduce bandwidth consumption on the network links and the load on the servers [1], [3]. A cache retrieves files from the original server, storescopies locally and then passes them on to the users who request them. Whenever the cache has the files in the local storage, it forwards the local files directly to the users rather than going all the way to the original server. If the Web cache does not have the files, it receives the files from the original server and then provides them to the users. The web cache stores copies of the new files in its storage for the next time they are requested. Thereafter, the cache serves both the role of a server and of a client. The main benefits from web caching is the reducing of the response time for a user request, the decreasing traffic on a main server’s access link, and its rapid distribution of the content.In order to provide good quality of multimedia service thorough the Internet, an adequate network system for continuous media delivery is crucial [7]. This is because network support for the multimedia streaming can reduce the transport delay and the packet loss ratio. Cache sharing and cache hierarchies were designed to serve web requests for generic non-continuous media files [5], [22]. Recently, the fast growth of multimedia services and the limited capacity of the Internet have increased network congestion for Internet applications [14]. In order to avoid the high latency and loss rate of streaming media in the Internet with scalable and reliable operations, prefix caching allows the storage of a prefix, a partial dataset of frames from the beginning of the streaming media, on the proxy of the Internet close to users rather than storing the entire contents [4], [29], [34], [35]. The proxy immediately transmits the prefix while it simultaneously requests the suffix, the remainder of the stream, from the media server.Moreover, considering the heterogeneous network systems of continuous and non-continuous multiple media types, the proxy cache has been developed for different cache resource usages. The Resource-Based Caching (RBC) algorithm [32] characterizes and caches each data object by its resource requirement and usage. The Quality-of-Service (QoS)-Adaptive proxy-caching scheme [37] proposes a media characteristic-weighted replacement policy to improve the cache hit ratio of mixed media, and a resource-management mechanism to dynamically re-allocate cache resources. The dynamic proxy caching method [11] applies back-end caching approaches, so it provides both reverse proxy and forward proxy configuration to get fine-grained caching. Also, because of the un-cached segments from the proxy delay on the client side, there is proxy jitter in the multimedia streaming caching. Proxy jitter is proxy delay in fetching the uncached segments. The Hyper Proxy streaming system [6] minimizes proxy jitter by lowering delayed startup ratio and network traffic, and by managing network resources by giving a high priority to clients.2.1.2 Media Content DistributionContent Distribution Networks (CDNs) adapt a different network model than media proxy caching. In this model, a content provider uses an independent CDN to deliver its content to the requested users without a long delay. CDN companies, such as Akamai and Digital Island, install CDN servers which duplicate the content of a provider’s original files in the main server throughout the Internet [15]. Whenever the provider updates its content, the CDN duplicates and distributes the new content to the CDN servers. In this way, a media user can retrieve data from the nearest duplicate CDNserver which allows users to get the best network performance [19]. The users can be redirected to the optimal server with DNS redirection [16], [24].CDNs also extensively support the distribution of continuous audio and video data. The researchers of streaming media CDN architecture [10] has focused on the distributing, storage, and delivery of continuous audio and video content over IP networks. Streaming media traffic is usually much heavier than normal web file traffic in a network and causes a severe burden on regular caches. Therefore, the streaming media CDNs help prevent server overload, provide a shorter network path for media delivery, and are very effective in storing and playing live multimedia streaming content [36]. CDN servers often apply streaming control protocols such as RTSP [28], SCTP [21], and DCCP [18]. To solve the additional network problem of a CDN, the ASM-FastReplica algorithm [8] optimizes replication of large streaming media files by partitioning the files in sub-files. Each node starts a file transfer to the next node, right after receiving the first packet of the corresponding sub-file. Then, cross-nodes from the different multicast trees connect with each other to exchange their sub-files to receive an entire file.Network security is an important concern for media CDNs. A server owned by a media provider and a user node need mutual authentication and authorization mechanisms to support business transactions and network security. This will ensure that only media requests from authorized users can access to the media contents. The primary network security threat in media CDNs is a man-in-the-middle attack, which is caused by IP spoofing, eavesdropping, and Denial of Service (DoS).2.1.3 Peer-to-Peer Media File SharingThe third architecture is Peer-to-peer (P2P) file sharing systems such as Napster [20], Gnutella [12], and KaZaA [17]. The P2P file sharing systems have developed very popular ways to access huge volumes of media files. While a client-server network model relies on a centralized server, the P2P network model sets up symmetric communication between peers, which are computer units at the edge of the network [27]. For the P2P network, each node works as either the client or the server. This allows a P2P network system to be very scalable because peers can retrieve and transfer data content directly between the other participating peers without relying on third party servers. Generally, the researchers of the P2P network model has focused two main categories for locating content: unstructured P2P and structured P2P.2.1.3.1 Unstructured P2PUnstructured P2P does not have precise control over the network topology or its content placement. In unstructured P2P, random distribution of nodes and content may cause content to be hard to locate. Thus, the position of this content can only be found by flooding the request to the peer. Most of the popular networks such as Napster, Gnutella, and KaZaA are unstructured.Napster [20] is a centralized model among unstructured P2Ps because a central database maintains an index of all files that are shared by the peers currently logged in the P2P network. The database can be queried by all peers, and provides the IP addresses andports of all peers who share the requested file. Napster is categorized as an unstructured P2P network since its overlay network and content distribution is not managed by a network topology. The main disadvantage of a centralized unstructured P2P is poor scalability, and an inability to located file with a single point of failure.Gnutella [12] does not have a central database server since it is a decentralized and unstructured P2P. Each peer floods search queries to all other neighboring peers without any knowledge about the other peers. The main disadvantage of Gnutella is that peers of the overlay network generate a large amount of messages per query which cause heavy network load when the number of peers grows. Also, there is no guarantee that you will find requested files in the unstructured P2P network system.KaZaA [17] is a hierarchical and unstructured P2P, where super-nodes are placed among the ordinary peers to track the requested file effectively. Each super-node replicates an index of other’s child-nodes file content. When a peer asks to search a file, a super-node initially tracks the file in all its child-nodes. The super-node floods queries to other super-nodes when it cannot find the file in its child-nodes.2.1.3.2Structured P2PThe main focus of structured architecture is how to control and deliver data file directories. A structured architecture with a P2P network topology and with a set of connections between P2P nodes is tightly controlled. Data files are placed at specified locations in the structured system. The CoopNet model [23] has a centralized algorithmthat works with a source server, which has all the information about the nodes, to develop and manage a tree system. Chord [30], a distributed lookup algorithm, addresses each node with a key associated with a particular data item. It then stores a pair key and data item at the node, and adapts the answer query system when nodes join and leave the system. Pastry [26] develops application-level routing and data file location in an overlay network of participating nodes through the Internet. CAN [25] applies a hash table-like network to make the P2P system scalable and fault-tolerant. The CAN system also provides a self-organizing architecture. Other models of structured architecture are Narada, NICE, ZIGZAG, and virtual multicast. While the Narada model [9] applies a mesh to interconnect only small scale peers, NICE [2] and ZIGZAG [33] employ hierarchical clustering when fits in large scale peers. The P2P systems in the structured architecture are very dynamic, but its tree structure is complicated and hard to build and maintain. Virtual multicast introduced the subnet broadcast approach by using network-layer multicasting for the P2P system [31].2.2 Control and Security Issues in Media Content Delivery Improvements in media content delivery architectures have the potential to allow media users of an Internet media searching and delivery method to access, gather, and collect various media contents. On-line users can access various types of streaming media content such as audio and video by using an Internet media searching and delivery method. However, Internet media searching and delivery methods create the heavy transmission of increasingly various media data in networks and servers to a growingmedia user population. Also, the scalability issue of media searching and delivery methods has led to the development of multimedia content delivering architectures.The multimedia content delivering architecture review can be categorized by three application prototypes: a media hosting model, a media directory model, and a decentralized searching model. The media hosting model adopts a media proxy caching architecture and a media content distribution architecture. The media directory model applies a structured architecture of a P2P file sharing system. Finally, the decentralized searching model includes an unstructured architecture of P2P file sharing system. The current research of three application prototypes for the multimedia content delivery architectures focuses on efficient network solutions for bandwidth consumption, heavy server load, and network latency, while multimedia network control and trusted security aspects are not taken into consideration.The major issues of multimedia network control and trusted security in the multimedia content delivery are as follows. First, it is necessary that a third party trusted agent sets up and controls direct media channeling connection between a user and a media provider. In that way, the system of media content delivery is reliable and trustworthy. Second, the existing media content delivery architectures need authentication security methods to identify the media users. Using an authentication security method, media content providers could prove authenticity and adopt on-line payment methods to media users. Third, the existing media content deliveries are provided by media content based architecture so that the relationship between media users and content providers existtemporarily. Therefore, they need a media channel based control approach that allows users to reliably connect to media content providers through secure UDP channels. Fourth, there are some potential network security issues, including IP spoofing attacks, man-in-the-middle attacks, and DoS attacks. Without controll by a third party trusted agent, those security threats will allow attacks to the media delivery systems.3.PROPOSED RESEARCHI propose a new architecture called Secure Internet Channeling Agent (SIChA), which uses a third party trusted agent to obtain maximum network control and to fulfill security requirements for the media content delivery networks. For my proposed approach, I will initially explain the detailed architecture of SIChA, and then present an implementation and an evaluation method to validate the approach. I will also explain my research contribution for the area of media content delivery network.3.1Architecture of Secure Internet Channeling Agent (SIChA)The proposed research uses SIChA as a third party trusted agent to create a multimedia content connection control and a trusted secure media delivery method to enable reliable media content exchange on the Internet. In this section, I will explain fundamental concepts and techniques, the network overview, sequential workflow, and the architecture design of SIChA system.3.1.1Fundamental Concepts and techniquesThe primary goal of the SIChA architecture is to create a multimedia connection control and a trusted secure media delivery method to enable reliable exchange of media content. The SIChA, a third party trusted channeling agent, makes direct, secure, and fast Internet media connections between a user device and a media content server. The SIChA’s database reserves channeling socket information consisting of the user’s IP address and a UDP port for an initial stage. When the user requests media content, the SIChA does not return media searching information directly, but relays the user’s media request to the media content server as a channel. For fast media channeling, the SIChA relays the user’s media request with the user’s reserved channeling socket information to the media content server. At the same time, the SIChA generates and sends one-time symmetric channel keys to both the media content server and the user’s device. Since the media content server knows a user’s reserved channeling socket information from the SIChA, the media content server is able to start transmitting the media content stream encrypted by the channel key to the user through a virtually dedicated UDP channel. A user’s device starts to decrypt the encrypted UDP content stream by using the symmetric channel key received by the SIChA.Another functionality of SIChA is to provide the private Channel Name System (CNS) for a media community or a region on the basis of the public Domain Name System (DNS). Using the CNS protocol, a media provider can create multiple private channel names without disrupting its public domain name. While the existing public DNS has a limited domain name for the system, the private CNS allows the media providers toemploy as many media domain names as they want without conflicting with other domain names.With the SIChA, the user can directly access various Internet media providers containing diverse media content, since the system includes the media domain name translation service for media content groups and media content servers. The SIChA protects media content with two symmetric channel keys to encrypt and decrypt the content from a media provider to a user. Also the system establishes a virtually dedicated UDP channel with a reserved socket, including a user’s IP and a reserved UDP port, so the transmission time of media streams is shorter than the other models.3.1.2Network Overview of SIChAAs illustrated in figure 1, SIChA works with the user device and the media content server to transmit media content through the Internet. As an initial step, the user should have previously reserved an account in SIChA and installed the plug-in program, which the user’s device uses to request media content from the media content server using the channeling protocol. The media content could be several types such as TV, radio, video, music etc. As soon as the user requests the media content, SIChA directly relays the request to the media content server with the user’s reserved channeling socket information.tric mmeGenerally, the existing media directory system provides the IP address of the media content server to a user while the existing media content delivery system stores media content and relays the media content from the server to the user. However, the SIChA directly relays the media content request to the media content server, and lets the server provide the media content stream to the user device. The media content server transmits UDP media streams into the user’s device using the reserved socket. After setting up the link between the user and the server, the media stream is transmitted through a virtually dedicated UDP channel. In this process, the media content server uses UDP packets instead of TCP packets because the transmission speed of UDP is faster.The other function of the SIChA is generating one-time symmetric channel keys and encrypting/decrypting the media content stream. In figure 1, the SIChA, as the trusted third party authorized channeling agent, generates a pair of symmetric channel keys, anddistributes it to both the user and the media content server. The server uses it to encrypt the UDP media stream, and the user uses it to decrypt the transmitted media stream. Since the symmetric channel key is a one-time temporary secure code, it is disposed after the channel ends. The SIChA regenerates another pair of symmetric keys for a new channel to both user device and media content server. The media content server encrypts the UDP media stream with the channel key and transmits it to the user’s reserved channeling socket. The user waits for an encrypted media stream from the media content server after it receives and sets up the symmetric channel key in the plug-in program. When the encrypted UDP media stream arrives at the user’s UDP port, the user decrypts it with the symmetric channel key. Since the symmetric channel key is used to decrypt the media content stream, the media stream can be transmitted very securely through a virtually dedicated UDP channel between the user and the media content server.To terminate the channel, the user requests a channel-ending message from the SIChA. As soon as the SIChA receives the channel-ending request message, it relays the message to the media content server. The server ceases delivering the UDP media content stream through the reserved socket of the user device when the server receives the channel-ending message.3.1.3Sequential workflow under the SIChA systemFigure 2 is a sequence chart that depicts the work-flow of the SIChA. It works as a mediator to provide direct and secure Internet channeling between a user device and a media content server. The user device can be a desktop computer, a laptop computer, ahandheld device, or similar devices connected to the Internet. Media content may include pictures, audio, video, and other media data. As shown in figure 2, the SIChA performs many functions between a user device and a media content server.For the initial stage, the SIChA collects or receives reservation information of the sourceaddress or the group of media content of the media content server. The group of mediacontent includes TV, radio, movie and music files. Next, a user registers an account for his or her device in the SIChA’s database. When the SIChA receives the user’s registration, it requests the reserved socket information of the user’s device to the user. The user socket information consists of an IP address and a virtually dedicated UDP port number. When the user device sends a reserved socket information message to the SIChA, the SIChA accepts the reserved socket for transmitting media stream from a media content server to the user’s device. Using the reserved socket, a media content server can transmit the media stream through a virtually dedicated UDP channel. As soon as the SIChA receives the user’s channeling socket information, it stores theinformation in its database and transmits a secure channeling plug-in program for the user’s device to install. After the user installs the secure channeling plug-in program into the user’s device, the user can use the channeling protocol to access media content. At this point, the SIChA system ends the initial stage and is ready to start the “normal stage.”In the normal stage, the user’s device requests media content or a media content group from a media server to the SIChA through the secure channeling plug-in program. The SIChA, as a channeling request relay agent, relays the media content request to the media content server with the requested user’s reserved UDP socket information. For the secure media content protection method, the SIChA generates a pair of one-time symmetric channel keys, and provides each key to both the media content server and the user’s device. When the user’s device receives the secure UDP media stream, the user’s device decrypts the encrypted media content stream using the one-time symmetric channel key, which was sent by the SIChA.For the channel end stage, the requesting process is the same as the previous channeling request method. The user’s device requests a channel end from the SIChA, and the SIChA relays the channel-end message to the media content server. Then, the media content server stops transmitting the secure UDP media stream to the user’s device.3.1.4Functional Overview of SIChAFigure 3 describes a block diagram of a detailed functional overview of a SIChA including a database relational diagram when it communicates with either a user device or a media content server. In the SIChA, there are three main functional databases; a user account database, a media content server database, and a channel key control database. In this section, I will explain how the databases work in two function areas; media searching and delivering control, and network channel key control.er es RVirtually Dedicated UDP Media ChannelIn st al lin g a a ch M an ed ne ia lk Pl ey ug fo -In rd ec od in gng vit es qu re g ia in d ed m nco ’s er for e Us y ng ke rri nel e sf an h an Tr a c3.1.4.1 Media searching and delivering control First, the user account database manages users’ account information, users’ reserved channeling socket information, and a channeling plug-in program. The SIChA gives media content access rights to trusted customers only. In that way, the SIChA securelyn io at rm t fo en in nt et co ck ia so ed m r’s g se in U st ue eqR21。