From ontology to relational databases
- 格式:pdf
- 大小:114.03 KB
- 文档页数:12

数据库选择题答案1. A relational database management system (RDBMS) is a system that manages relational databases and allows users to interact with data stored in these databases. It provides a structured way to organize and manage data, making it easier to query, update, and analyze.2. Structured Query Language (SQL) is a programming language used to manage and manipulate data in a relational database. It provides a standardized way to retrieve, insert, update, and delete data from databases.3. The main components of a relational database system include:- Database: A collection of related data organized and stored in a structured format.- Tables: A database consists of one or more tables, which hold the data.- Rows: Each row in a table represents a record or instance of data.- Columns: Each column in a table represents a specific attribute or field of the data.- Primary key: A primary key is a unique identifier for each record in a table.- Foreign key: A foreign key is a reference to a primary key in another table, establishing a relationship between the two tables.4. The advantages of using a relational database management system are:- Data integrity: RDBMS ensures data integrity by enforcing constraints and rules on data manipulation.- Data consistency: RDBMS maintains a consistent view of data across the database, ensuring that changes are propagated correctly.- Data security: RDBMS provides features like access control and encryption to protect data from unauthorized access.- Scalability: RDBMS allows for the efficient management of large amounts of data and can scale to accommodate growing needs.- Query flexibility: SQL provides a powerful and flexible way to query and retrieve data from databases.- Data independence: RDBMS separates the physical and logical representation of data, allowing for easier management and modifications.5. When choosing a database system, several factors need to be considered:- Data requirements: Assess the type of data, volume, and complexity to determine the most suitable database system.- Performance: Consider the expected workload and performance requirements to select a database system that can handle the anticipated load.- Scalability: Determine if the database system can scale to accommodate future growth in data volume and user concurrency.- Availability: Evaluate the high availability features andbackup/recovery mechanisms provided by the database system.- Cost: Consider the licensing fees, hardware requirements, and maintenance costs associated with the database system.- Vendor support: Look for a reputable vendor that offers reliable technical support and regular updates for the database system.- Integration capabilities: Assess the compatibility and integration options with other systems and applications in the environment.6. The popular relational database management systems include:- Oracle Database: A widely used RDBMS known for its scalability, reliability, and advanced features.- MySQL: An open-source RDBMS suitable for small to medium-sized applications.- Microsoft SQL Server: A commercial RDBMS with excellent integration capabilities and comprehensive tooling.- PostgreSQL: An open-source RDBMS known for its robustness, extensibility, and support for advanced SQL features.7. Non-relational databases, also known as NoSQL databases, are an alternative to traditional relational databases. They are designed to handle large-scale data storage and processing requirements. Some popular types of NoSQL databases include:- Key-value stores: These databases store data in a key-value format for fast retrieval.- Document databases: These databases store and retrieve data in JSON-like documents.- Wide-column stores: These databases store data in tables with columns that can vary per row or record.- Graph databases: These databases are optimized for managing relationships between data elements.In conclusion, a relational database management system (RDBMS) is a powerful tool for organizing and managing data. When choosing a database system, it is important to consider factors such as data requirements, performance, scalability, availability, cost, vendor support, and integration capabilities. Popular RDBMS options include Oracle Database, MySQL, Microsoft SQL Server, and PostgreSQL. Additionally, NoSQL databases provide alternative solutions for specific data storage and processing needs.。

Database System PrinciplesTest One(07401 — 07405)Class____________No____________Name____________1.Fill in blanks (1 x 7 points)(1)The collection of information stored in the database at a particular moment is called an _instance____of the database.(2)The database system provides users with three levels of data abstraction, the _view__ level of abstraction describes only part of the entire database.(3)Database design involves the following phases: requirements analysis,conceptual/external schema design, logical schema design and physical schema design.(4) Data model is a collection of conceptual tools for describing data, datarelationships, data semantics, and data constraints.(5) As human-machine interfaces, the database language consists of two parts, i.e the datadefinition language (DDL) and DML (data manipulation language) . (6)In the following figure, the participation constraints of A in R is partial , themapping cardinality form A to B is many-to-many(7) An entity set that does not have a primary key is referred to as a weak entity set .2.Choice (1 x 9 points)(1)For the entity set Student(#student, sname, department, course, grade), the primaryattributes are .A. #student, courseB.{#student}C. {#student, course}D. #studentE.#student F. course(2)With respect to the following relational database, is the data model,is the relational schema.A.R={ <a1, a2, …., a n> }B.<Smith, 0441112, CS, database, 90>C. Student(sname, #student, department, course, grade)(3)relationship set “服务于” among the entity sets cell and MS, primary_key(服务于) isA. either primary_key(MS) or primary_key(cell)B. primary_key(MS)C. primary_key(cell)D. primary_key(MS) ∪ primary_key(cell)For the descriptive attribute “业务类型” of the relationship set “服务于” among MS and cell, when reducing “服务于” into the relational table, how to deal with the attribute “业务类型”A. “业务类型” can only be assigned as the attribute of the table corresponding to MSB. “业务类型” can only be assigned as the attribute of the table corresponding to cellC. “业务类型” can only be assigned as the attribute of the table corresponding to 服务于(4)For a many-to-one relationship sets R that associates entity set A and B, if R ispartially on the many-side A and the one-side B, how to deal with R ?A.R should be represented as a independent table corresponding to RB.R should not be represented as a independent table, it can be reduced to the table Acorresponding to the many and total side entity set AC.R should not be represented as a independent table, it can be reduced to the table Bcorresponding to the one and part side entity set B(5)For the extended E-R model in Fig.3, if entity-set-L1 ∩ entity-set-L2=Φ, then thegeneralization/specialization isA. overlappingB. disjoint, and if (entity-set-L1 ∪entity-set-L2) ≠H-entity-set, then thegeneralization/specialization isA. totalB. partial(6)Given the cardinalities of the entity sets A and B with respect to therelationship set R, the participation constraints of A can be decided by ;A. l AB. h AC. l BD. h BThe mapping cardinality from A to B can be decided by .A. [l A, l B]B. [h A , h B]C. [h B , h A]D. [l A, h B]答案:A A C B A A B B A CReduce the E-R diagram in Fig.3 into relational schemas.3.(10 points)Answers :BTS(BTS-id, 发射功率);天线(BTS-id, 对应扇区, 型号,增益,方向角)4. (6 points) Convert the following E-R diagram into the diagram that containsonly binary relationshipsRBCAAttr-RAnswers :E = { e i } , | E |= | R |, i.e. each (a i , b i , c i ) in Rcorresponds to one ei in E, or E = { ei }=R={(a i , b i , c i ) } R a = { (e i , a i) | e i∈E , a i∈A }, relating E and AR b = { (e i , b i) | e i ∈E , b i ∈B } , relating E and BR c = { (e i , c i) | e i ∈E , c i ∈B }, relating E and CE has an identifying attribute e ( candidate key) todistinguish each e i i n Eall attributes of R, i.e. attr-R, are assigned to E5. (10 points)Convert the entity set “学生”, of which the attribute “老乡” is amultivalued attribute, in Fig.4 into relational tablesstudent-id籍贯老乡性别年龄男 20 07494 北京 07596,0761107498 河北 07320,女 1907321Fig.4Answers:student-id籍贯性别年龄07494 北京男 2007498 河北女 19student-id老乡07494 0759607494 0761107498 0732007498 073216.(15 points) 给出下列关系代数操作对应的SQL语句(1) σp(r) (2) ∏A1, A2, .., Am ( r )(3) r∞s ,, 假设r(A, B, C), s(C, E, F)(4) r ∩ s(5) loan ←loan∪σamount ≥ 0and amount ≤ 50 (loan)假设loan(loan-number, branch, amount) Answers:(1)select * from r where P(2)select A1, A2, .., Am from r(3)select * from r natual join sselect * from rwhere r.C =s.C(4)r intersect s(5)insert into loanselect * from loanwhere amount ≥ 0and amount ≤ 507.(9 points)给出下列SQL语句对应的关系代数表达式(1) select branch-name, max (salary)from pt-worksgroup by branch-name假设pt-works(employee-name, branch-name, salary) (2) delete form rwhere P(3) update loanset amount = amount *1.2where amount > 1000Answers:(1) branch_name G max(salary) (pt-works)(2) r ← r —σp(r)(3) T1 ← пloan-number, branch_name, amount*1.2σamount > 1000 (loan)T2 ←σamount≤ 1000 (loan)loan ← T1 ∪ T28. (14 points). Here is the schema diagram for the bank-customer database.Use SQL statements to implement the following operations:(1)Define the table account, it is assumed that the null value is inappropriate for theattribute branch_name and the attribute balance ranges from 5000 to 100,000.(3 points)(2)Find out the name of each customer who has accounts in only one branch. (5points)(3)Modify the structure of the table branch, add a new attribute account_amount into it,which describes the total number of accounts in a branch. And then assign thecorrect value of account_amount for each branch in the table branch.(6 points)Answers:(1)create table account{ account-number integer primay keybranch-name varchar not nullbalance integerforeign key (branch-name) reference branchcheck (balance between 5000 and 100000)}(2)select custom-namefrom account, depositorwhere aoount.account-number= depositor.account-numbergroup by customer-namehaving count(distinct branch-name)=1(3) step1.alter table branch add account-amount integerstep2.create view sum-amount as b-name, total{ select branch-name, count(*)from accountgroup by branch-name}step3. (MS SQL Server支持的语法)update branchset account-amount = sum-amount.totalfrom branch, sum-amountwhere branch.branch-name=sum-amount.b-name或:update branchset account-amount = sum-amount.totalfrom branch JOIN sum-amounton branch.branch-name=sum-amount.b-name或:(Oralce和DB2都支持的语法):update branchset account-amount =select sum-amount.totalfrom sum-amountwhere branch.branch-name=sum-amount.b-name另一种解法:step1.create view sum-amount as b-name, total{ select branch-name, count(*)from accountgroup by branch-name}Step2.create table new-branch{ branch-name varchar primay keybranch-city varchassets integeraccount-amount integer}Step3.insert into new-branchselect branch-name, branch-city, assets, totalfrom branch, sum-amountwhere branch.branch-name = sum-amount.b-name step4. drop branchstep5. 利用DBMS相关机制,将new-branch换名为branch或者:在new-branch上定义新视图branch9. (20 points) A school is going to arrange a sports day for the students. A database to keep track of participants and activities during the sports day is to be created. Consider the following information:(1). Participating persons. Each person has a number and a name. The person is identified by the number.(2). Teams. Each team has a number and a name. The team is identified by the number.(3). A team consists of several persons, and a person can be a member of several teams. A team must have at least one person, and a person may not participate in any team. (4). Activities, such as baseball or long jump. Each activity has a number, a name, and a starting time, and is identified by the number.(5). Participation in the activities. Both teams and individual persons can participate in more than one activities. Each person and each team must participate in at least one activity. Each activity can have many teams and many persons.(1) Design the E/R diagram for the database on the basis of the information mentioned above .( 15 points)Note: mapping cardinality of each relationship and participation of each entity to the relationship should be described in the diagram.(2) Convert the E-R diagram to the proper relational schemas, and give the primary keys of each relation schemas by underlines. (15 points)Answers:team(t_number, t_name)person(p_number, p_name)activity(a_number, a_name, a_time) member(t_number, p_number) participation1(t_number, a_number) participation2(p_number, a_number)。

数据库原理(双语)习题assignment - of - module02Assignment of Module02Questions:2.1 Discuss each of the following concepts in the context of therelational data model: (a) relation (b) domain (c) attribute (d) tuple(e) degree and cardinality2.2 Discuss the properties of a relation2.3 Discuss the difference between the candidate keys and the primary key of a relation. Example what is meant by a foreign key. How do foreign keys of relations relate to primary key? Give examples to illustrate your answer. (1)Candidate Key (2)Primary Key (3) Foreign Keys2.4 Define the two principal integrity rules for the relational model. Discuss why it is desirable to enforce these rules.2.5 What is view? Discuss the difference between a view and a base relation.Exercises :The following tables form part of a database held in a relational DBMS: Hotel (hoteNo, hoteName, city) Room (roomNo, hoteNo, type, price)Booking (hoteNo, guestNo, dateFrom, dataTo, roomNo) Guest (guestNo, guestName, guestAddress)Where Hotel contains hotel details and hotelNo is the primary keys;Room contains room details for each hotel and (roomNo, hoteNo) forms the primary key;Booking contains details of bookings and (hoteNo, guestNo, dateFrom) forms the primary key; Guest contains guest details and guestNo is the primary key.2.6 Identify the foreign keys in this schema. Explain how the entity and referential integrity rules apply to these relations.2.7 describe the relations that would be produced by the following relational algebra operations: a) ∏hotelNo(? price>50(Hotel))b) ? Hotel.hotelNo=Room.hotelNo(Hotel × Room)c) ∏hotelNo(Hotel∞Hotel.hotelNo=Room.hotelNo(? price>50(Room)))d) (? dataeTo≥’1-Jan-2002’(Booking))∝Gueste) Hotel�SHotel.hotelNo=Room.hotelNo(? price>50(Room)) (‘�S’meanssemi-join operation) f) (∏guestNo,hotelNo (Booking∞(Guest)))÷∏hotelNo(? city=’London’Hotel))2.8(a) List full details of all hotels.(b) List all single rooms with a price below $20 per night. (c) List the names and cities of all guests.(d) List the price and type of all rooms at the Grosvenor Hotel. (e) List the guests currently staying at the Grosvenor Hotel.(f) List the details of all rooms at the Grosvenor Hotel, including the name of the guest staying in the room, if the room is occupied(g) List the guest details(guestNo, guestName, and guestAddress) of all guests staying at Grosvenor Hotel.2.9 Using relational algebra, create a view of all rooms in the Grosvenor Hotel, excluding price detail. What are the advantage of this view?2.10 Represent, by means of one or more relations, the information contained in a timetable of departures from a railway station. Show the number, time, final destination, category and stops of every departing train.感谢您的阅读,祝您生活愉快。
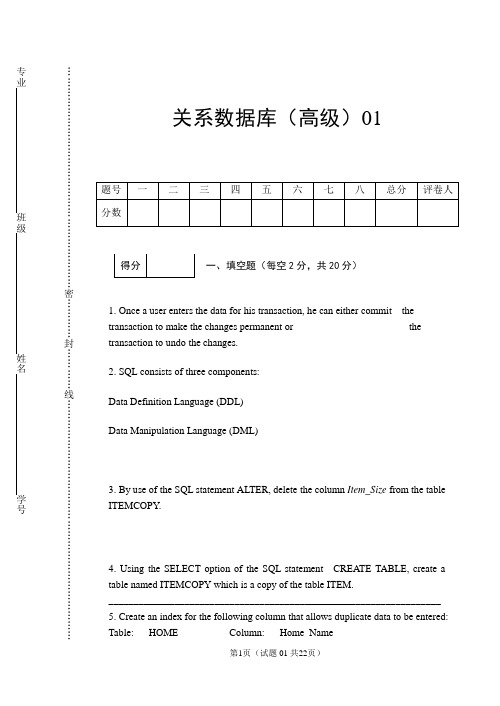
关系数据库(高级)01一、填空题(每空2分,共20分)1. Once a user enters the data for his transaction, he can either commit the transaction to make the changes permanent or ______________________ the transaction to undo the changes.2. SQL consists of three components:Data Definition Language (DDL)Data Manipulation Language (DML)___________________________3. By use of the SQL statement ALTER, delete the column Item_Size from the table ITEMCOPY.__________________________________________________________________4. Using the SELECT option of the SQL statement CREATE TABLE, create a table named ITEMCOPY which is a copy of the table ITEM.__________________________________________________________________ 5. Create an index for the following column that allows duplicate data to be entered:Table: HOME Column: Home_Name__________________________________________________________________6. Create a view named ITEM_PRICELIST, on the table ITEM, which only includes the columns:Item_No, Item_Description, Item_Wholesale_Price, Item_Retail_Priceand sorts the result by the Item_Description.__________________________________________________________________ 7. Assign the appropriate privileges on the table ITEMCOPY to the last one of the users detailed below(HN92):__________________________________________________________________8. Create a synonym named ANOTHER_ITEM on the table ITEMCOPY.__________________________________________________________________ 9. Insert the following record into the Franchise table:Franchise No MF999Franchise Name Mature Fashions (Shetlands)Franchise Address 1, Lonely Spot, LerwickFranchise Postcode 2E1 1AAFranchise Tel 01595 1245Franchise Fax 01595 2356Franchise Start Date 22nd January 2002__________________________________________________________________ 10.Update the above record and change the address to 1, Main Street, Lerwick and the Start Date 15th February 2002.__________________________________________________________________二、判断以下的说法是否正确,如果正确,将在括号中,填入T(TRUE),否则,填入F(FALSE)。

it面试题库及答案IntroductionWith the rapid development of information technology, the demand for IT professionals has been increasing. As a result, IT interviews have become a crucial step in the hiring process. To succeed in an IT interview, it is essential to have a comprehensive understanding of commonly asked questions and well-prepared answers. This article aims to provide a detailed IT interview question bank along with sample answers.1. Technical Questions1.1 Programming Languages1.1.1 What is the difference between Java and Python?Java and Python are both popular programming languages but differ in various aspects. Java is a compiled language that runs on the Java Virtual Machine (JVM), while Python is an interpreted language. Java is mainly used for enterprise-level applications, while Python is known for its simplicity and readability. Additionally, Java requires explicit declaration of data types, while Python uses dynamic typing.1.1.2 What is object-oriented programming?Object-oriented programming (OOP) is a programming paradigm that organizes software design around objects that represent real-world entities. It emphasizes the concepts of encapsulation, inheritance, and polymorphism. OOP allows for modular and reusable code, making it easier to maintain and expand software systems.1.2 Database Management1.2.1 What is the difference between SQL and NoSQL databases?SQL (Structured Query Language) databases are relational databases that store and manage structured data in tables with predefined schemas. They are suitable for complex queries and transactions. NoSQL (Not only SQL) databases, on the other hand, are non-relational databases designed for handling large amounts of unstructured or semi-structured data. They provide flexible schemas and horizontal scalability.1.2.2 What is ACID in database management?ACID (Atomicity, Consistency, Isolation, Durability) is a set of properties that ensure reliability and consistency in database transactions. Atomicity guarantees that a transaction is treated as a single unit of work, either fully completed or fully rolled back if any part fails. Consistency ensures that the database remains in a valid state before and after a transaction. Isolation prevents interference from concurrent transactions, and Durability guarantees that once a transaction is committed, its changes are permanent.2. Behavioral Questions2.1 Problem-Solving2.1.1 Describe a challenging technical problem you encountered and how you resolved it.2.1.2 Give an example of a time when you had to work under pressure to meet a tight deadline. How did you handle it?2.2 Communication Skills2.2.1 Explain a complex technical concept to someone without a technical background.2.2.2 Describe a situation where you had to communicate and collaborate with a team to solve a problem.3. Sample Answers1.1.1 Java and Python differ in their execution models and use cases. Java is a compiled language that runs on the JVM, allowing for high performance and platform independence. It is commonly used for building enterprise-level applications. In contrast, Python is an interpreted language known for its simplicity and readability. It is widely adopted in web development, scientific computing, and data analysis due to its ease of use and extensive library support.1.1.2 Object-oriented programming (OOP) is a software development paradigm that focuses on modular and reusable code. It organizes software design around objects, which are instances of classes representing real-world entities. OOP emphasizes encapsulation, where data and methods are bundled together within objects. It also enables inheritance, allowing classes to inherit attributes and behaviors from parent classes. Polymorphism, another key concept in OOP, allows objects to take on many forms and exhibit different behaviors based on the context. OOP enhances code reusability, maintainability, and scalability.2.1.1 In my previous role, I encountered a challenging technical problem where a critical database server went down, causing a major disruption inour production environment. I promptly identified the root cause, which was a disk failure. To resolve the issue, I replaced the faulty disk and restored the database from the latest backup. However, to minimize the downtime, I implemented a backup server configuration and utilized a replication mechanism to keep the data synchronized. This solution ensured both data integrity and high availability.2.1.2 Working under pressure to meet tight deadlines is a common occurrence in the IT industry. In one instance, I received a project with an unexpectedly shortened timeline due to unexpected client requirements. To handle the situation, I immediately prioritized the tasks, focusing on critical components and breaking down the project into manageable subtasks. I communicated with the team, delegating responsibilities and ensuring everyone was aware of the new timeline. By working overtime, maintaining constant communication, and efficiently managing resources, we successfully met the deadline without compromising the quality of the deliverables.2.2.1 Complex technical concepts can be challenging to explain to non-technical individuals. To overcome this, I often use analogies and relatable examples to help them grasp the idea. For instance, when explaining encryption, I compare it to sending secret messages using a lock and key. I describe how encryption algorithms scramble data (message) using a key (like a lock), making it unreadable to unauthorized parties. Only someone with the correct key can decrypt (unlock) and access the original message. This simplifies the concept and allows non-technical individuals to understand the fundamentals of encryption.2.2.2 Collaboration and effective communication are vital in solving complex technical problems. In a recent project, our team encountered a challenging software bug that affected the system's stability. To overcome this, we organized regular meetings to discuss and share ideas. Each team member had a specialized area of expertise, so we collaborated closely, actively listening to each other's suggestions and insights. By pooling our knowledge and skills, we successfully identified the root cause and implemented a comprehensive solution. This experience highlighted the importance of teamwork and effective communication in problem-solving.ConclusionThe field of information technology is vast and evolving, and IT interviews are designed to evaluate candidates' technical knowledge, problem-solving abilities, and communication skills. By familiarizing yourself with common IT interview questions and crafting thoughtful answers, you can increase your chances of success. Remember to adapt your answers based on your own experience and expertise. Good luck with your upcoming IT interviews!。
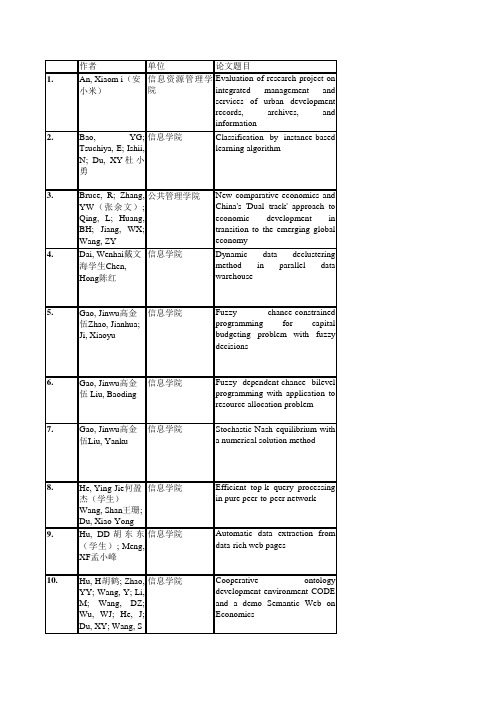
作者单位论文题目1.An, Xiaom i(安小米)信息资源管理学院Evaluation of research project onintegrated management andservices of urban developmentrecords, archives, and information2.Bao,YG;Tsuchiya,E;Ishii,N; Du, XY杜小勇信息学院Classification by instance-basedlearning algorithm3.Bruce,R;Zhang,YW(张余文);Qing,L;Huang,BH;Jiang,WX;Wang, ZY 公共管理学院New comparative economics andChina's'Dual track'approach toeconomic development intransition to the emerging globaleconomy4.Dai, Wenhai戴文海学生Chen,Hong陈红信息学院Dynamic data declustering methodin parallel data warehouse5.Gao, Jinwu高金伍Zhao, Jianhua;Ji, Xiaoyu 信息学院Fuzzy chance-constrainedprogramming for capitalbudgeting problem with fuzzydecisions6.Gao, Jinwu高金伍 Liu, Baoding 信息学院Fuzzy dependent-chance bilevelprogramming with application toresource allocation problem7.Gao, Jinwu高金伍Liu, Yanku 信息学院Stochastic Nash equilibrium witha numerical solution method8.He, Ying-Jie何盈杰(学生)Wang, Shan王珊;Du, Xiao-Yong 信息学院Efficient top-k query processing inpure peer-to-peer network9.Hu,DD胡东东(学生);Meng,XF孟小峰信息学院Automatic data extraction fromdata-rich web pages10.Hu,H胡鹤;Zhao,YY;Wang,Y;Li,M;Wang,DZ;Wu,WJ;He,J;Du, XY; Wang, S 信息学院Cooperative ontologydevelopment environment CODEand a demo Semantic Web onEconomics11.Hu, He胡鹤Du,Xiaoyong 信息学院Description logics based oninterval fuzzy theory12.Hu, He胡鹤Liu,Dayou; Zhan, Kai 信息学院Ontology middleware in the ESplatform13.Hu, He胡鹤Liu,Dayou; Hu,Zhiyong 信息学院Spatio-temporal ontologyconstruction based on logicmapping14.Hu, He胡鹤Liu,Dayou; Hu,Zhiyong 信息学院Web ontology server and its queryinterface15.Huang,YF(黄燕芬)公共管理学院Poverty and the minimum livingguarantee in China16.Huang, Zhiyong黄志勇Jiang,Yunping; Wang,Yuefei 信息学院On conformal measures forinfinitely renormalizablequadratic polynomials17.Li,C林灿学生;Qian,Z;Meng,XF孟小峰;Liu,WY 信息学院Postal address detection from webdocuments18.Li,M;李曼(学生) Du, XY杜小勇; Wang, S 信息学院A semi-automatic ontologyacquisition method for theSemantic Web19.Li,M李曼(学生);Wang,DZ;Du,XY杜小勇;Wang, S 信息学院Ontology construction forsemantic web:A role-basedcollaborative development method20.Li, Man李曼(学生)Wang, Da-Zhi; Du, Xiao-Yong杜小勇;Wang, Shan 信息学院Dynamic composition of webservices based on domainontology21.Li, Man李曼(学生)Du, Xiao-Yong杜小勇;Wang, Shan 信息学院Learning ontology from relationaldatabase22.Li,Man李曼(学生)Wang,Yan;Zhao,Yiyu;Du,Xiaoyong;Wang,Shan 信息学院Study on storage schema of largescale ontology based on relationaldatabase23.Li, Q李青公共管理学院Case study of institutionaleconomics-China's reform in thenatural monopoly of publicutilities24.Li, Sheng-En李盛恩(学生)Wang, Shan王珊信息学院Multidimensional data model ER([script H] )25. Liang, K Margarita as symbol of eternalfemininity: A religiousinterpretation of 'The Master andMargarita'26.Liu, Qing刘青Zhou, Peng 信息学院Data analysis of cosmicallymicroarray gene expression basedon neural networks with enhancedgeneralization27.Lu, Yanmin卢燕敏学生Chen,Hong陈红信息学院Markov model prediction basedcache management policy28.Luo, Dao-Feng罗道锋(学生)Meng, Xiao-Feng;孟小峰 Jiang, Yu 信息学院Updating of extended preordernumbering scheme on XML29.Ma,YW;Yan,F;Zhu, J; Kou, W Timing asteroid occultations by photometry30.Mao,JY毛基业;Vredenburg,K;Smith,PW;Carey, T 商学院The state of user-centered designpractice-UCD is gaining industryacceptance-but its currentpractice needs fine-tuning.31.Mao,W(毛薇);Zheng,FT(郑风田);Mao, J 农业与农村发展学院The researches on food safetysystem from the perspective ofpublic administration32.Song, YF宋雅范图书馆Continuing education in Chineseuniversity libraries:Issues andapproaches33.Tang, YJ A study on durability andpreservation of imaging discs34.Wang,CY汪昌云?财政金融学院Ownership and operatingperformance of Chinese IPOs35.Wang,HC;Yin,MQ Stock return and systematic risk: An empirical study on Shanghai stock market36.Wang, Jing王静(学生)Meng,Xiao-Feng; Wang,Yu; Wang, Shan 信息学院Target node aimed pathexpression processing for XMLdata37.Wang, Shan王珊Zhang, Kun-Long 信息学院Searching databases withkeywords38.Wei, Y(袁卫)统计学院The statistical profession in China39.Wen, Ji-Jun文继军(学生)Wang, Shan 信息学院SEEKER:Keyword-basedinformation retrieval overrelational databases40.Yang, Nan杨楠Gong, Danzhi; Li,Xian; Meng,Xiaofeng 信息学院Survey of Web communitiesidentification41.Ye,XM;Fan,SR;Liang, J Domestic e-shop comprehensive evaluation research42.Yong,L林勇;Kai, W 信息学院ARFIMA model and the nonlinearanalysis of the Chinese securitiesmarkets43.Yu, Li余力Liu,Lu; Li, Xuefeng 信息学院A hybrid collaborative filteringmethod for multiple-interests andmultiple-content recommendationin E-Commerce44.Yu, Li余力 Di,Yan; Wang, Jun;Cao, Shujuan 信息学院Exploration of budgeting for landconsolidation project45.Yu,SY(于澍燕);Li,SH;Huang,HP;Zhang,ZX;Jiao,Q;Shen,H;Hu,XX; Huang, H 化学系Molecular self-assembly withmodularization and directionality:Vector-manipulation at metalcenters46.Zha,DJ(查道炯)国际关系学院Comment: can China rise?47.Zhan, Jiang占江学生 Feng, Yueli;Wang, Shan王珊信息学院Research and implementation offull text index on Chinese inPostgreSQL48.Zhang,H(张晗);Xu,EM(徐二明);Xu,W 商学院The research of strategiccorporate governance based on thecorrelativity analysis49.Zhang,KL张坤龙(学生);Wang,S王珊信息学院LinkNet:A new approach forsearching in a large peer-to-peersystem50.Zhang,Y;Yang,B; Chen, PF Flowstep:A web-based distributed workflow management system51.Zhang, Zhanlu张占录Yang,Qingyuan 公共管理学院Driving force analysis of theconsolidation of countryresidential areas in Shunyi district52.Zhang, Zhengfeng张正峰 Chen,Baiming 公共管理学院Land consolidation sub-zoning:Acase study of Daxing district ofBeijing53.Xu, GQ许光清环境学院The system dynamics-an effectiveway to address sustainability54.Zhao,XJ(赵锡军);Chen,QQ;Wei, GY 财政金融学院Monetary and financialcooperation in Asia:Retrospectand future proposal55.Liyue Study on the financial function onindustrial technical progress:Theory and the practice of China56.Zhao,XJ(赵锡军); Chen, QQ 财政金融学院Research on Asian stock marketintegration57.Yang,QJ;Chen,C; Qi, ZQ Rough approximations in complete Boolean lattice58.Zhang,YS张越松; Li, GJ 公共管理学院Diagnosis and optimization ofDEA ineffectiveness of theconstruction projects59.Tao, CG Research on the growth of estateconstruction enterprises in China60.Xie,ZJ;Hong,C;Wang, L Subnets based distributed data-centric hierarchical ant routing for sensor networks61.Sun,CH;Shiu,SCK; Wang, XZ Organizing large case library by linear programming62.Yang,B;Fu,HJ;Zuo, MY 经济学院?杨斌The integration mechanism of IToutsourcing partnership63.Yu,MX(俞明轩);Yang,JY;Zhang, L 商学院Study on distribution ofconversion income of collectivebuilding land64.Yu,MX(俞明轩); Yang, QY 商学院A study on position evaluationsystem in real estate appraisalfirm发表刊物地址Reprint Address:Tsinghua Science and Technology,v10,n SUPPL., December, 2005, p 852-858School of Information Resources Management, Renmin University of ChinaINTELLIGENT DATA ENGINEERING AND AUTOMATED LEARNING IDEAL 2005, PROCEEDINGS, 3578: 133-140 2005Renmin Univ China,SchInformat,Beijing,PeoplesR Chinabaoyg@;eisuke@hm.aitai.ne.jp;ishii@in.aitech.ac.jp;duyong@PROCEEDINGS OF2005 INTERNATIONAL CONFERENCE ON PUBLIC ADMINISTRATION 50-68, 2005Renmin Univ China,Sch Publ Adm,Beijing, 100000 Peoples R ChinaHuazhong Keji Daxue Xuebao(Ziran Kexue Ban)/Journal of Huazhong University of Science and Technology(Natural Science Edition),v33,n SUPPL.,December,2005,p 239-242 Language: Chinese School of Information, Renmin University of ChinaLecture Notes in Artificial Intelligence (Subseries of Lecture Notes in Computer Science),v3613,n PART I,Fuzzy Systems and Knowledge Discovery:Second International Conference,FSKD2005. Proceedings, 2005, p 304-311School of Information, Renmin University of ChinaIEEE International Conference on Fuzzy Systems,Proceedings of the IEEE International Conference on Fuzzy Systems, FUZZ-IEEE 2005, 2005, p 541-545Uncertain Systems Laboratory,Department of Mathematics,Renmin University of ChinaLecture Notes in Computer Science,v3496, n I,Advances in Neural Networks-ISSN 2005:Second International Symposium on Neural Networks.Proceedings,2005,p811-816Uncertain Systems Laboratory,School of Information,Renmin University of ChinaRuan Jian Xue Bao/Journal of Software,v 16,n4,April,2005,p540-552Language: Chinese Info.Sch.,Renmin Univ. of ChinaDATABASE SYSTEMS FOR ADVANCED APPLICATIONS,PROCEEDINGS828-839, 2005Renmin Univ China,SchInformat,Beijing,PeoplesR ChinaHu,DD,Renmin UnivChina,Sch Informat,Beijing,Peoples RChina.WEB TECHNOLOGIES RESEARCH AND DEVELOPMENT-APWEB20051049-1052, 2005Renmin Univ China,SchInformat,Beijing,100872Peoples R ChinaHu,H,Renmin UnivChina,Sch Informat,Beijing,100872PeoplesR ChinaHuazhong Keji Daxue Xuebao(Ziran Kexue Ban)/Journal of Huazhong University of Science and Technology(Natural Science Edition),v33,n SUPPL.,December,2005,p 275-277 Language: Chinese Information School, Renmin Univ. of ChinaJisuanji Gongcheng/Computer Engineering,v 31,n5,Mar5,2005,p51-52+108 Language: Chinese Coll.of Info.,Renmin Univ. of ChinaJisuanji Gongcheng/Computer Engineering,v 31,n10,May20,2005,p139-141 Language: Chinese Information College, Renmin University of ChinaJisuanji Gongcheng/Computer Engineering,v 31, n 9, May 5, 2005, p 43-45Information College, Renmin University of ChinaPROCEEDINGS OF2005 INTERNATIONAL CONFERENCE ON PUBLIC ADMINISTRATION966-981, 2005Renmin Univ China,Sch Publ Adm,Beijing, Peoples R China.Science in China,Series A:Mathematics,v 48, n 10, October, 2005, p 1411-1420School of Information, Renmin University of ChinaINTERNATIONAL WORKSHOP ON CHALLENGES IN WEB INFORMATION RETRIEVAL AND INTEGRATION, PROCEEDINGS 40-45, 2005Renmin Univ,SchInformat,Beijing,100872Peoples R China.Li,C,Renmin Univ,SchInformat,Beijing,100872Peoples RChina.ADVANCES IN WEB-AGE INFORMATION MANAGEMENT, PROCEEDINGS 209-220, 2005Renmin Univ China,SchInformat,Beijing,100872Peoples R China.Li,M,Renmin UnivChina,Sch Informat,Beijing,100872PeoplesR ChinaWEB TECHNOLOGIES RESEARCH AND DEVELOPMENT-APWEB2005,3399: 609-619 2005Renmin Univ,SchInformat,Beijing100872,Peoples R China;ChineseAcad Sci,Chengdu InstComp Applicat,Chengdu610041, Peoples R ChinaLi,M,Renmin Univ,SchInformat,Beijing100872,Peoples RChina.Jisuanji Xuebao/Chinese Journal of Computers,v28,n4,April,2005,p643-650 Language: Chinese Sch.of Info.,Renmin Univ. of China2005International Conference on Machine Learning and Cybernetics,ICMLC2005, 2005International Conference on Machine Learning and Cybernetics,ICMLC2005, 2005, p 3410-3415School of Information, Renmin University of ChinaSchool of Information,Renmin University of China Language: Chinese Huazhong Keji Daxue Xuebao(Ziran Kexue Ban)/Journal of Huazhong University of Science and Technology(Natural Science Edition),v33,n SUPPL., December, 2005, p217-220Language: ChinesePROCEEDINGS OF2005 INTERNATIONAL CONFERENCE ON PUBLIC ADMINISTRATION 69-77, 2005Renmin Univ China,Sch Publ Adm,Beijing, 100872 Peoples R China.Jisuanji Xuebao/Chinese Journal of Computers,v28,n12,December,2005,p 2059-2067 Language: Chinese School of Information, Renmin University of ChinaFOREIGN LITERATURE STUDIES,(6): 118-+ DEC 2005Renmin Univ,CollLiberal Arts China,Beijing, Peoples R ChinaLiang,K,Renmin Univ,Coll Liberal Arts China,Beijing,Peoples RChina.Jisuanji Gongcheng/Computer Engineering,v 31,n3,Feb5,2005,p189-191Language: Chinese Sch.of Info.,Renmin Univ. of ChinaHuazhong Keji Daxue Xuebao(Ziran Kexue Ban)/Journal of Huazhong University of Science and Technology(Natural Science Edition),v33,n SUPPL.,December,2005,p 261-264 Language: Chinese School of Information, Renmin University of ChinaRuan Jian Xue Bao/Journal of Software,v 16,n5,May,2005,p810-818Language: Chinese Information School, Renmin UniversityICARUS, 178 (1): 284-288 NOV 1 2005Renmin Univ China,HighSch,Beijing100080,Peoples R China;BeijingPlannetarium,Beijing100044,Peoples R ChinaReprint Address:Yan,F,Renmin Univ China,HighSch,37ZhongguancunRd,Beijing100080,Peoples R China.frankyanfeng@COMMUNICATIONS OF THE ACM,48 (3): 105-109 MAR 2005Renmin Univ China,Beijing,Peoples R China;Univ Waterloo,Waterloo,ON N2L3G1,Canada;IBM Corp User CtrDesign&User Engn,Toronto,ON,Canada;IBM Ctr Adv Studies,Toronto, ON, CanadaMao,JY,Renmin UnivChina,Beijing,PeoplesR China.E-mailAddress:jymao@;PROCEEDINGS OF2005 INTERNATIONAL CONFERENCE ON PUBLIC ADMINISTRATION219-222, 2005Renmin Univ,Sch Agr Econ&Rural Dev, Beijing,100872Peoples R China.LIBRI, 55 (1): 21-30 MAR 2005Renmin Univ China,Lib,Beijing100872,PeoplesR China Song, YF, Renmin Univ China, Lib, 59 Zhongguancun St, Beijing 100872, Peoples R China. E-mail Address:songyafan1@2005BEIJING INTERNATIONAL CONFERENCE ON IMAGING: TECHNOLOGY AND APPLICATIONS FOR THE 21ST CENTURY 206-207, 2005Renmin Univ China,SchInformat ResourceManagement,Beijing,Peoples R China.Tang,YJ,Renmin UnivChina,Sch InformatResource Management,Beijing,Peoples RChina.JOURNAL OF BANKING&FINANCE,29 (7): 1835-1856 JUL 2005Renmin Univ China,SchFinance,Beijing100872,Peoples R China;NatlUniv Singapore,SchBusiness,Dept Finance&Accounting,Singapore119260, SingaporeWang,CY,RenminUniv China,SchFinance, Beijing 100872,Peoples R China.E-mailAddress:bizwcy@.sgPROCEEDINGS OF THE2005 INTERNATIONAL CONFERENCE ON MANAGEMENT SCIENCE& ENGINEERING(12TH),VOLS1-31727-1731, 2005Renmin Univ China,Sch Business,Beijing,100872 Peoples R ChinaRuan Jian Xue Bao/Journal of Software,v 16,n5,May,2005,p827-837Language: Chinese Information School, Renmin University of ChinaJournal of Computer Science and Technology,v20,n1,January,2005,p55-62School of Information, Renmin University of ChinaINTERNATIONAL STATISTICAL REVIEW 73 (2): 277-278 AUG 2005Renmin Univ China,Beijing, Peoples R ChinaWei,Y,Renmin UnivChina,Beijing,PeoplesR China.Ruan Jian Xue Bao/Journal of Software,v 16,n7,July,2005,p1270-1281Language: Chinese Information School, Renmin University of ChinaJisuanji Yanjiu yu Fazhan/Computer Research and Development,v42,n3,March, 2005, p 439-447 Language: Chinese Sch.of Information, Renmin Univ. of China2005INTERNATIONAL CONFERENCE ON SERVICES SYSTEMS AND SERVICES MANAGEMENT,VOLS1 AND2,PROCEEDINGS1446-1450,2004(请核对论文集是哪年发表?)RenMin Univ,Beijing,100872 Peoples R ChinaYe,XM,RenMin Univ,Beijing,100872PeoplesR ChinaWAVELET ANALYSIS AND ACTIVE MEDIA TECHNOLOGY VOLS1-31451-1456, 2005Renmin Univ China,Informat Sch,Beijing,100872 Peoples R China.Yong,L,Renmin UnivChina,Informat Sch,Beijing,100872PeoplesR ChinaExpert Systems with Applications,v28,n1, January, 2005, p 67-77School of Information, Renmin University of ChinaNongye Gongcheng Xuebao/Transactions of the Chinese Society of Agricultural Engineering,v21,n SUPPL.,February, 2005, p 119-122 Language: Chinese Department of Agricultural Economy, Renmin University of ChinaCURRENT ORGANIC CHEMISTRY,9 (6): 555-563 APR 2005Renmin Univ China,DeptChem,Beijing100872,Peoples R China;ChineseAcad Sci,State Key LabPolymer Phys&Chem,Inst Chem,Beijing100080,Peoples R China;Chinese Acad Sci,GradSch,Beijing100080,Peoples R China;ChineseAcad Sci,Fujian Inst ResStruct Matter,State KeyLab Struct Chem,Fuzhou350002,Peoples R China;Lanzhou Univ,State KeyLab Appl Organ Chem,Lanzhou100080,PeoplesR ChinaYu,SY,Renmin UnivChina,Dept Chem,Beijing100872,PeoplesR China.REVIEW OF INTERNATIONAL STUDIES, 31 (4): 775-785 OCT 2005Renmin Univ China,SchInt Studies,Beijing,Peoples R ChinaZha,DJ,Renmin UnivChina,Sch Int Studies,Beijing, Peoples R ChinaHuazhong Keji Daxue Xuebao(Ziran Kexue Ban)/Journal of Huazhong University of Science and Technology(Natural Science Edition),v33,n SUPPL.,December,2005,p 213-216 Language: Chinese School of Information, Renmin University of ChinaPROCEEDINGS OF THE2005 INTERNATIONAL CONFERENCE ON MANAGEMENT SCIENCE& ENGINEERING(12TH),VOLS1-3949-953, 2005Renmin Univ China,Sch Business,Beijing,100872 Peoples R China.WEB TECHNOLOGIES RESEARCH AND DEVELOPMENT-APWEB2005,3399: 241-246 2005Renmin Univ China,SchInformat,Beijing100872,Peoples R ChinaZhang,KL,RenminUniv China,SchInformat,Beijing100872,Peoples RChinaFOURTH WUHAN INTERNATIONAL CONFERENCE ON E-BUSINESS:THE INTERNET ERA&THE GLOBAL ENTERPRISE,VOLS1AND2599-609, 2005Renmin Univ China, Informat Sch,Beijing, Peoples R China.Nongye Gongcheng Xuebao/Transactions of the Chinese Society of Agricultural Engineering,v21,n11,November,2005,p 49-53 Language: Chinese College of Public Administration,Renmin University of ChinaNongye Gongcheng Xuebao/Transactions of the Chinese Society of Agricultural Engineering,v21,n SUPPL.,February, 2005, p 123-126 Language: Chinese Land Management Department,Renmin University of ChinaPROCEEDINGS OF THE2005 CONFERENCE OF SYSTEM DYNAMICS AND MANAGEMENT SCIENCE,VOL1-SUSTAINABLE DEVELOPMENT OF ASIA PACIFIC 166-173, 2005Renmin Univ China,Sch Environm&Nat Resources,Beijing, Peoples R China.PROCEEDINGS OF THE2005 INTERNATIONAL CONFERENCE ON MANAGEMENT SCIENCE AND ENGINEERING-PROCEEDINGS OF 2005INTERNATIONAL CONFERENCE ON MANAGEMENT SCIENCE AND ENGINEERING 899-904, 2005Renmin Univ China,Sch Finance,Beijing,100872 Peoples R ChinaPROCEEDINGS OF THE2005 INTERNATIONAL CONFERENCE ON MANAGEMENT SCIENCE AND ENGINEERING-PROCEEDINGS OF 2005INTERNATIONAL CONFERENCE ON MANAGEMENT SCIENCE AND ENGINEERING 905-910, 2005Renmin Univ China, Finance&Secur Inst, Beijing,100872Peoples R ChinaINTERNATIONAL CONFERENCE ON MANAGEMENT SCIENCE AND ENGINEERING-PROCEEDINGS OF 2005INTERNATIONAL CONFERENCE ON MANAGEMENT SCIENCE AND ENGINEERING 927-932, 2005Finance,Beijing,100872 Peoples R China.PROCEEDINGS OF THE2005IEEE INTERNATIONAL CONFERENCE ON NATURAL LANGUAGE PROCESSING AND KNOWLEDGE ENGINEERING (IEEE NLP-KE'05) 791-795, 2005Renmin Univ China,SchInformat,Beijing,100872Peoples R China.Yang,QJ,Renmin UnivChina,Sch Informat,Beijing,100872PeoplesR China.PROCEEDINGS OF2005 INTERNATIONAL CONFERENCE ON CONSTRUCTION&REAL ESTATE MANAGEMENT,VOLS1AND2-CHALLENGE OF INNOVATION IN CONSTRUCTION AND REAL ESTATE 243-245, 2005Renmin Univ China, Beijing,100872Peoples R China.PROCEEDINGS OF2005 INTERNATIONAL CONFERENCE ON CONSTRUCTION&REAL ESTATE MANAGEMENT,VOLS1AND2-CHALLENGE OF INNOVATION IN CONSTRUCTION AND REAL ESTATE 1024-1027, 2005Renmin Univ China,Sch Finance,Beijing,Peoples R China2005INTERNATIONAL CONFERENCE ON WIRELESS COMMUNICATIONS, NETWORKING AND MOBILE COMPUTING P ROCEEDINGS,VOLS1 AND 2 895-900, 2005RenMin Univ,SchInformat,Beijing,100872Peoples R China.Xie,ZJ,RenMin Univ,Sch Informat,Beijing,100872 Peoples R ChinaMICAI2005:ADVANCES IN ARTIFICIAL INTELLIGENCE 554-564, 2005Renmin Univ China,Informat Sch,Beijing,100872 Peoples R China.Sun,CH,Renmin UnivChina,Informat Sch,Beijing,100872PeoplesR China.SEVENTH INTERNATIONAL CONFERENCE ON ELECTRONIC COMMERCE,VOLS1AND2, SELECTED PROCEEDINGS801-803, 2004(会议时间是05?)Renmin Univ China,Informat Sch,Beijing,100872 Peoples R China.Renmin Univ China,Informat Sch,Beijing,100872Peoples RChina.PROCEEDINGS OF CRIOCM2005 INTERNATIONAL RESEARCH SYMPOSIUM ON ADVANCEMENT OF CONSTRUCTION MANAGEMENT AND REAL ESTATE 325-329, 2005Renmin Univ China,Sch Business,Beijing,100872 Peoples R China.INTERNATIONAL RESEARCH SYMPOSIUM ON ADVANCEMENT OF CONSTRUCTION MANAGEMENT AND REAL ESTATE 448-454, 2005Business,Beijing,100872 Peoples R China.EISCI、ISTP ISSHPEIEI 、ISTP、SCI EI、ISTPEI、ISTP、SCI EIISTP、SCI ISTP、EI、SCIEIEIEIISSHPEIISTPISTP、SCI ISTP、SCI、EIEIEI、ISTPISSHP EIA&HCI EIEIEI SCIEI 、SCIISSHPSSCIISTPSSCIISTP 、ISSHP EIEI 、SCI ISTP 、SCIEIISTP、 ISSHP ISTPEIEISCISSCIISTP、ISSHP SCI、ISTP、EIISTP、ISSHPEIEIISTP、ISSHP ISTP、ISSHP ISTP、ISSHPISTP、ISSHP ISTPISTP、ISSHP ISTP、ISSHP ISTPISTP、SCI ISSHP ISSHP。
What are the entities used to model data in the Relational Model?^^^^A. A collection of instances of entities.^^^^B. Relations, attributes and tuples^^^^C. A collection of instances of record types.^^^^D. Table, rows and columns}Which of the following is true about Relational Databases?^^^^A. A column can store values of different data types.^^^^B. A table consists of columns and rows.^^^^C. Rows in the same table can have a different set of columns.^^^^D. Rows are also known as fields of the table.}A company has a large amount of data to store and wants to be able to do the following with the data:Have a standard interface for accessing the data.Have multiple users with the ability to insert, update and delete data.Make changes to the data without risk of losing data and its consistency.Have the capability to handle huge volumes of data and users.Have tools for data backup, restore and recovery.What data storage method is the most optimal solution for the company?^^^^A. Text files^^^^B. Comma delimited data files^^^^C. Spreadsheets^^^^D. Database}When using a Relational Database, which of the following does not apply?^^^^A. Accesses data using Data Manipulation Language (DML) such as SQL.^^^^B. Define your database schema using a Data Definition Language (DDL).^^^^C. Data is stored in a hierarchical model.^^^^D. You can use normalization to avoid redundant data in your tables.}Which of the following is not true about the Information Model?^^^^A. Abstract management of objects at a conceptual level.^^^^B. Defines relationships between managed objects.^^^^C. It is a group of descriptions explaining objects of a data model.^^^^D. Data models can be used to map an Information Model to a software implementation.}Which Data Model was created with the focus of providing better data independence ? ^^^^A. Relational^^^^B. Hierarchical^^^^C. Semantic^^^^D. Network}Which of the following is NOT true about columns?^^^^A. Each column consists of one or more fields^^^^B. Each column contains a specific type of information^^^^C. Columns must be designated a specific data type^^^^D. Columns are also known as fields}Which of the following is true about columns?^^^^A. Each column consists of one or more records^^^^B. Columns are where the individual pieces of information are stored for each record^^^^C. Columns must be designated a specific data type^^^^D. Columns are also known as records}You are tasked with designing a model that can be used by the software developer to implement a given application. Which of the following is NOT true about your model?^^^^A. The model is a low level of abstraction with concrete and detailed design.^^^^B. The model includes specific implementation and protocol details.^^^^C. The model should define relationships between the managed objects.^^^^D. The model being designed is an Information Model.}Using DB2’s CLP , to access a remote database for the first time, it is necessary to:^^^^A. First catalog the remote system or node, and then catalog the database within the remote node^^^^B. First register the remote system user in the system catalog, and then setup a SSH communication to the remote node^^^^C. DB2 cannot use databases in remote systems unless SYSADM authority is granted to the local user^^^^D. First list all the remote databases with the db2 list database directory command, and then select the remote database from the list}Which of the following statements is not true regarding Table Spaces on DB2?^^^^A. A Table Space is a logical object in between logical table and physical containers^^^^B. All tables, indexes, and other data are stored in a table space^^^^C. A Table Space is a logical object required to store data, indexes and tables in temporary memory^^^^D. A Table Space is always associated to a Buffer Pool}Assuming that you are currently connected to TESTDB, which of the following will allow the view of the database settings with details?^^^^A. db2 get db cfg with detail^^^^B. db2 get db cfg show detail^^^^C. db2 get dbm cfg with detail^^^^D. db2 get dbm cfg show detail}(实例级)Which of the following commands would delete the SAMPLE database?^^^^A. db2 drop sample^^^^B. db2 delete database sample^^^^C. db2 drop sample db^^^^D.db2 drop database sample}What is the purpose of a DB2 Access Plan?^^^^A. SQL developers can define Access Plans to tell DB2 the best way to retrieve the data from a SQL query^^^^B. Describes the order of operations to access data necessary to execute a SQL or XQuery statement^^^^C. To replicate data between a DB2 database and relational databases from other vendors^^^^D. To visually construct complex DML statements and examine the results of their execution}How does automatic storage work in DB2?^^^^A. Automatic storage simplifies storage management by allowing you to specify storage paths where the database manager can place table space data, and where the database manager allocates space for various uses.^^^^B. Automatic storage is an option which is set when you create a DB2 database. It allows transactions that are written to the database to be automatically committed.^^^^C. Automatic storage is a function of DB2 that allows tables to be backed up automatically on a set schedule.^^^^D. Automatic Storage can be used to automatically reorganize the data on the physical media in order to improve performance.}Which of the following is the lowest cost DB2 product that can be legally installed on a Linux server that has 2 CPUs?^^^^A. DB2 Express Edition^^^^B. DB2 Enterprise Server Edition^^^^C. DB2 Everyplace^^^^D. DB2 Workgroup Server Edition}You were assigned the task of importing a large amount of data into a DB2 database. Considering you must have logged information about the rows imported and that you want to perform the load as fast as possible, which of the tools would you be the best choice for the job?^^^^A. DB2 INSERT^^^^B. DB2 IMPORT^^^^C. DB2 LOAD^^^^D. DB2 CLP}Which of the following is the lowest cost DB2 product that can be legally installed on a windows server that has 4 CPUs capable of performing row compression?^^^^A. DB2 Express Edition^^^^B. DB2 Workgroup Edition^^^^C. DB2 Express-C Edition^^^^D. DB2 Enterprise Edition }Which of the following is true about a well-formed XML document?^^^^A. Has one or more root nodes^^^^B. Tags can have at most one attribute^^^^C. Always has a single document node^^^^D. End tags are optional}Which of the following is a well-formed XML document?^^^^A. <Name xmlns="htpp://" Gender="MALE"> <FirstName>Amitabh</FirstName><LastName>Patel</LastName></Name>^^^^B. <Name xmlns="" MALE="Gender"> <FirstName>Amitabh</FirstName><LastName>Patel</LastName></name>^^^^C. <Name Gender="MALE"><FirstName>Amitabh <LastName>Patel</FirstName> </LastName></Name>^^^^D. <Name Gender=FEMALE><FirstName>Jaya</FirstName><LastName>Patel</LastName></Name>}What is SQL/XML?^^^^A. SQL/XML is a communication protocol for DB2 databases^^^^B. A.SQL/XML is part of the XQuery standard and provides various publishing functions to transform XML data into relational form and vice versa^^^^C. SQL/XML is a language that provides various publishing functions to transform XML data into relational form and vice versa^^^^D. SQL/XML is an extension to SQL standard and provides various publishing functions to transform XML data into relational form and vice versa}Which of the following is not part of the XQuery FLWOR expression:^^^^A. FOR clause^^^^B. LET clause^^^^C. ORDER BY clause^^^^D. WITH clause}Consider the following XML document:<customerinfo><name>John Smith</name><addr country="Canada"><street>Fourth</street><city>Calgary</city><prov-state>Alberta</prov-state><pcode-zip>M1T 2A9</pcode-zip></addr><phone type="work">963-289-4136</phone></customerinfo>Consider the following UPDATE expression:update xmlcustomerset info = xmlquery( 'transformcopy $new := $imodify (do insert <phone type="cell">777-555-3333</phone> after $new/customerinfo/addr,for $j in $new/customerinfo/addr/phonereturn do rename $j as "telephone")return $new' passing info as "i")where cid = 1000;Which of the following represents the XML document after the TRANSFORM expression has been executed:^^^^A. <customerinfo><name>John Smith</name><addr country=“Canada"><street>Fourth</street><city>Calgary</city><prov-state>Alberta</prov-state><pcode-zip>M1T 2A9</pcode-zip></addr><phone type=“cell">777-555-3333</phone><phone type="work">963-289-4136</phone> </customerinfo>^^^^B . <customerinfo><name>John Smith</name><addr country=“Canada"><street>Fourth</street><city>Calgary</city><prov-state>Alberta</prov-state><pcode-zip>M1T 2A9</pcode-zip></addr><phone type=“cell">777-555-3333</phone><telephone type="work">963-289-4136</telephone> </customerinfo>^^^^C. <customerinfo><name>John Smith</name><addr country=“Canada"><street>Fourth</street><city>Calgary</city><prov-state>Alberta</prov-state><pcode-zip>M1T 2A9</pcode-zip></addr><phone type=“cell">777-555-3333</phone><telephone type="work">963-289-4136</telephone> </customerinfo>^^^^D. <customerinfo><name>John Smith</name><addr country=“Canada"><street>Fourth</street><city>Calgary</city><prov-state>Alberta</prov-state><pcode-zip>M1T 2A9</pcode-zip><phone type=“cell">777-555-3333</phone></addr><telephone type="work">963-289-4136</telephone></customerinfo>Which of the following is an XML-based language for transforming XML documents?^^^^A. XHTML^^^^B. XSLT^^^^C. HTML^^^^D. Java}Which of the following properties is related to the fact that a committed transaction guarantees that all of the operations are completed and in a roll backed transaction the effect of all operations are reverted?^^^^A. Consistency^^^^B. Atomicity^^^^C. Isolation^^^^D. Durability}Which of the following best define what a transaction is?^^^^A. A sequence of one or more SQL operations grouped together, also known as a single unit of work^^^^B. A set of independent operations that can be executed in parallel^^^^C. A data isolation level that can help prevent deadlocks by allowing reads on previously committed data.^^^^D. An object of a DB2 database}Which of the following statements is FALSE about transactions?^^^^A. Operations inside a transaction are executed in parallel.^^^^B. Only 1 COMMIT statement can be executed inside the same transaction. --- ?^^^^C. Transactions guarantee atomicity of a group of operations.^^^^D. A ROLLBACK or COMMIT statement finalizes a transaction. }Application B wants to read a subset of rows from table EMPLOYEE multiple times inside the same transaction. Which isolation level should be used in order to guarantee that every time the same set of rows is returned?^^^^A. Currently Committed^^^^B. Read Stability^^^^C. Repeatable Read^^^^D. Uncommitted Read}A Dirty Read occurs when?^^^^A. A transaction read the same row of data twice and returns different data values with each read^^^^B. A search based on some criterion returns additional rows after consecutive searches during a transaction^^^^C. Uncommitted data is returned, but the transaction that originated them was rolled back^^^^D. Two transactions read and then attempt to update the same data, the secondupdate will overwrite the first update before it is committed}How can an application modify the isolation level of operations running against a DB2 database?^^^^A. Isolation level can be changed for a particular SQL statement.^^^^B. Isolation level can only be changed for the whole user session and all operations in that session will be affected.^^^^C. Isolation level to be used can be specified when executing the COMMIT operation.^^^^D. Isolation level is determined at the moment an application connects to the database. To change the isolation level, an application is required to create a new connection specifying the desired level.}Consider the following scenario. You have 3 tables with the same name (TABLE_1) under 3 different schemas (SYSIBM, DEFAULT and DB2INST1). You are connected to a DB2 database in your Linux server as db2inst1 and issue the following statement:SELECT * FROM table_1Which table will you be selecting data from:^^^^A. You get an error because your query is ambiguous, as the table schema is not specified^^^^B. SYSIBM.table_1^^^^C. DEFAULT.table_1^^^^D. DB2INST1.table_1}Which of the following is NOT a supported type of trigger?^^^^A. AFTER^^^^B. BEFORE^^^^C. DURING^^^^D. INSTEAD OF}When attempting to establish a connection to a database residing on your local machine, which command can help you determine why the following message was displayed:SQL1013N The database alias name or database name "SAMPLE" could not be found. SQLSTATE=42705^^^^A. list database directory^^^^B. list admin node directory^^^^C. list node directory^^^^D. list dcs directory}Which of the following is FALSE about views?^^^^A. Do not contain real data^^^^B. Any view can be updated, independent of its definition^^^^C. When changes are made to data through a view, the data is changed in the underlying table^^^^D. Can be used interchangeably with tables when retrieving data}Given the options below, which of the following statements can add records to a table?^^^^A. ADDREC^^^^B. ADDRECORD^^^^C. INSERT^^^^D. ADD}Consider the following command:CREATE TABLESPACE MYTBSP1 MANAGED BY AUTOMATICWhat will the command result in?^^^^A. Creation of a normal table space called mytbsp1 that is managed automatically ^^^^B. Creation of a user table space called mytbsp1 that is managed automatically.^^^^C. Creation of a temporary table space called mytbsp1 that is managed automatically.^^^^D. This command will return an error to the user.}What is authorization?^^^^A. Authorization is a process that checks whether you have sufficient privileges to perform the desired database operation^^^^B. Authorization is the process where the DBA gathers information to see who will have access to the database^^^^C. Authorization is the process where the DB2 database checks with Windows security to see if you have access to the DB2 database^^^^D. Authorization is a process that validates that you are who you claim to be by verifying your user ID and password}Which of the following statements grants user John the ability to insert data to table tab1?^^^^A. GRANT ADD ON TABLE tab1 TO John^^^^B. GRANT INSERT ON TABLE tab1 TO John^^^^C. GRANT ADD ON TABLE tab1 TO USER John^^^^D. GRANT INSERT ON TABLE tab1 TO USER John}Assume a table which contains the following columns:EMP_IDEMP_NAMEPHONEEMAILSALARYWhich of the following is the simplest way to restrict users from viewing SALARY information, while still allowing them to see the other values?^^^^A. Encrypt the table's data^^^^B. Create a view that does not contain the SALARY column. Grant access to the view and revoke access from the original table^^^^C. Revoke SELECT access for the SALARY column from users who should not see SALARY data^^^^D. Store SALARY data in a separate table and grant SELECT privilege for that table to the appropriate users}What is a Trusted Context?^^^^A. It is a special area in a buffer pool that can be written only by a selectedset of users.^^^^B. It is a DB2 capability that allows applications to change users without breaking the connection to the database.^^^^C. It is a DB2 capability that allows users to establish a connection to the database without providing user name or password.^^^^D. It is a type of container in a table space that allows faster I/O operations.}After the following SQL statement is executed:GRANT ALL PRIVILEGES ON TABLE student TO USER user1Assuming user USER1 has no other authorities or privileges, which of the following actions is USER1 allowed to perform?^^^^A. Grant all privileges on table STUDENT to other users^^^^B. Drop a view associated to the table STUDENT^^^^C. Drop the table STUDENT^^^^D. None of the above}When a user is connected to a database, which of the following privileges is required for the user to use a package?^^^^A. BIND^^^^B. BINDADD^^^^C. EXECUTE^^^^D. USE}Which of the following best describes what an incremental cumulative backup is? ^^^^A. Backup all of the data that has changed since the last successful full ordelta backup^^^^B. Backup of a single table space^^^^C. Backup of the entire database^^^^D. Backup all of the data that has changed since the last full backup}Which of the following is a tool to configure automatic database backup?^^^^A. Configure Automatic Maintenance wizard^^^^B. Design Advisor^^^^C. Explain tool^^^^D. EXPORT utility}Which of the following options will perform an offline table space recovery? ^^^^A. RESTORE DATABASE SAMPLE TABLESPACE (MYTBSP) OFFLINE FROM /tbspbkp^^^^B. RESTORE DATABASE SAMPLE TABLESPACE (MYTBSP) FROM /tbspbkp^^^^C. RESTORE DATABASE SAMPLE TABLESPACE (MYTBSP) ONLINE FROM /tbspbkp^^^^D. There is no option to restore a table space in DB2}In embedded SQL code, which of the following is true about delimiters ?^^^^A. Used by the OS to delimit system variable declaration^^^^B. Used by the database to indicate the end of a column^^^^C. Used by compiler to indicate the end of the program^^^^D. Used by PRECOMPILER to identify SQL statements to be translated}Which of the following programming languages can be used to develop UDFs ?^^^^A. Java, Javascript, SQL^^^^B. C/C++, Java, .Net languages^^^^C. SQL, C# .Net, Perl^^^^D. Perl, C/C++, SQL}Which of the following is true about Dynamic SQL?^^^^A. It is precompiled and binded in dynamic databases^^^^B. The structured of an SQL statement must be completely specified at precompile time.^^^^C. It is compiled and executed by an application at run-time.^^^^D. Dynamic SQL does not exist}Which of the following DB2 client/driver packages is NOT suitable for developing ODBC applications?^^^^A. IBM Data Server Client^^^^B. IBM Data Server Driver for ODBC and CLI^^^^C. IBM Data Server Runtime Client^^^^D. IBM Data Server Driver Package}Considering the SQL statement below, which option best describes what APP.TAX is: SELECT APP.TAX(SALARY) FROM EMPLOYEE^^^^A. User Defined Function^^^^B. Stored Procedure^^^^C. Trigger^^^^D. User Defined Type}Which of the following objects you would need to create in order to execute a block of code every time table TB1 is updated.^^^^A. An AFTER trigger^^^^B. A UDF^^^^C. A Stored Procedure^^^^D. An User Defined Type}Given the following two tables:NAMES---------------------------NAME NUMBER---------- -------Wayne Gretzky 99Jaromir Jagr 68Bobby Orr 4Bobby Hull 23Mario Lemieux 66POINTS----------------------------NAME POINTS---------- -------Wayne Gretzky 244Bobby Orr 129Brett Hull 121Mario Lemieux 189Joe Sakic 94How many rows would be returned using the following statement? SELECT * FROM names, points^^^^A. 0^^^^B. 5^^^^C. 10^^^^D. 25}Given the following two tables:TAB1------------------COL_1 COL_2----- -----A 10B 12C 14TAB2-------------------COL_A COL_B----- -----A 21C 23D 25Assuming the following results are desired:COL_1 COL_2 COL_A COL_BA 10 A 21B 12 - -C 14 C 23- - D 25Which of the following joins will produce the desired results?^^^^A. SELECT * FROM tab1 INNER JOIN tab2 ON col_1 = col_a^^^^B. SELECT * FROM tab1 LEFT OUTER JOIN tab2 ON col_1 = col_a ^^^^C. SELECT * FROM tab1 RIGHT OUTER JOIN tab2 ON col_1 = col_a ^^^^D. SELECT * FROM tab1 FULL OUTER JOIN tab2 ON col_1 = col_a}Given the following table:TAB1-------------------COL1 COL2----- -----A 10B 20C 30A 10D 40C 30Assuming the following results are desired:TAB1-------------------COL1 COL2----- -----A 10B 20C 30D 40Which of the following statements will produce the desired results?^^^^A. SELECT UNIQUE * FROM tab1^^^^B. SELECT DISTINCT * FROM tab1^^^^C. SELECT UNIQUE(*) FROM tab1^^^^D. SELECT DISTINCT(*) FROM tab1}Given the following table:CURRENT_EMPLOYEES-----------------------------EMPID INTEGER NOT NULLNAME CHAR(20)SALARY DECIMAL(10,2)PAST_EMPLOYEES-----------------------------EMPID INTEGER NOT NULLNAME CHAR(20)SALARY DECIMAL(10,2)Assuming both tables contain data, which of the following statements will NOT successfully add data to table CURRENT_EMPLOYEES?^^^^A. INSERT INTO current_employees (empid) VALUES (10)^^^^B. INSERT INTO current_employees VALUES (10, 'JAGGER', 85000.00)^^^^C. INSERT INTO current_employees SELECT empid, name, salary FROM past_employees WHERE empid = 20^^^^D. INSERT INTO current_employees (name, salary) VALUES (SELECT name, salary FROM past_employees WHERE empid = 20)}Given the following UPDATE statement:UPDATE employees SET workdept =(SELECT deptno FROM department WHERE deptno = 'A01')WHERE workdept IS NULLWhich of the following describes the result if this statement is executed?^^^^A. The statement will fail because an UPDATE statement cannot contain a subquery^^^^B. The statement will only succeed if the data retrieved by the subquery does not contain multiple records --- why^^^^C. The statement will succeed; if the data retrieved by the subquery contains multiple records, only the first record will be used to perform the update^^^^D. The statement will only succeed if every record in the EMPLOYEES table has a null value in the WORKDEPT column}Given the following table definition:SALES--------------------------SALES_DATE DATESALES_PERSON CHAR(20)REGION CHAR(20)SALES INTEGERWhich of the following SQL statements will remove all rows that had a SALES_DATE in the year 1995?^^^^A. DELETE * FROM sales WHERE YEAR(sales_date) = 1995^^^^B. DELETE FROM sales WHERE YEAR(sales_date) = 1995^^^^C. DROP * FROM sales WHERE YEAR(sales_date) = 1995^^^^D. DROP FROM sales WHERE YEAR(sales_date) = 1995}Which of the following SQL statements can be used to remove data from table "users": ^^^^A. REMOVE TABLE users^^^^B. DROP TABLE users^^^^C. DELETE TABLE users^^^^D. ALTER TABLE users}If TAB1 is created using the following statementCREATE TABLE tab1 (col1 INTEGER NOT NULL,col2 CHAR(3),CONSTRAINT cst1 CHECK (col1 in (1, 2, 3, 4)))Which of the following statements will successfully insert a record into table TAB1? ^^^^A. INSERT INTO tab1 VALUES (0, 'a')^^^^B. INSERT INTO tab1 VALUES (NULL, 'abc')^^^^C. INSERT INTO tab1 VALUES (4, 'a')^^^^D INSERT INTO tab1 VALUES (4, 'abcdefhijklmnopq')}Given the following two tablesNAMES--------------------------------STUDENT_NAME STUDENT_NUMBER------------ ----------------Wayne Gretzky 99Jaromir Jagr 68Bobby Orr 4Bobby Hull 23Mario Lemieux 66MARKS--------------------------------NAME Marks-------- -------Wayne Gretzky 80Bobby Orr 94Brett Hull 77Mario Lemieux 83How many rows would be returned using the following statement? SELECT distinct name FROM student_names, marks^^^^A. 9^^^^B. 20^^^^C. 5^^^^D 6}这个题有点问题答案应该是 4==========================================Which of the following is not a definition of a relation?^^^^A. A relation may be thought of as a set of columns.^^^^B. Each row represents a fact that corresponds to a real-world entity or relationship^^^^C. Each row has a value of an item or set of items that uniquely identifies that row in the table^^^^D. Each column typically is called by its column name or column header or attribute name}The type of data structure that is used in a relational model is?^^^^A. Table^^^^B. Tree^^^^C. Node^^^^D. None of the above}In relational terminology, an attribute is?^^^^A. A record^^^^B. An entity^^^^C. A field^^^^D. A table}The link between a column or set of columns in one table that refers to the set of column in another table is?^^^^A. Pointer^^^^B. Cursor^^^^C. Primary key^^^^D. Foreign key}A foreign key must?^^^^A. Be defined in all tables in the database^^^^B. Match the field value of a primary key in a related table or be NULL.^^^^C. Be unique^^^^D. Be numeric}Which of the following is NOT true about data?^^^^A. Data is useful and has meaning associated to it.^^^^B. Data can be quantitative or qualitative.^^^^C. Data describes a variable or set of variables.^^^^D. Essentially data can be thought of as the result of observations based on things like measurements and statistics.}Which of the following is NOT true about Database Management Systems?^^^^A. Relational Database Management Systems use Structured Query Language to interact with databases.^^^^B. Database Management Systems act as an interface used to communicate with databases.^^^^C. Applications can choose to bypass the Database Management System when accessing databases for performance reasons.^^^^D. DB2 is a Database Management System.}A database can be used to do which of the following?^^^^A. Create a repository of data.^^^^B. Provide an organized mechanism for manipulating data.^^^^C. Provide support for data processing.^^^^D. All of the above.}Which of the following is true about the table below?CREATE TABLE EMPLOYEE (ID INTEGER NOT NULL,NAME VARCHAR(30) NOT NULL,EXTENSION INTEGER NOT NULL,MANAGER VARCHAR(30) NOT NULLPRIMARY KEY (ID));TERMINATE;ID NAME EXTENSION MANAGER1 John S 53412 Y2 Susan P 54123 N3 Jennifer L 51234 N^^^^A. ID is a value found in the EMPLOYEE table^^^^B. ID, 1, 2, 3 makes up a row in the EMPLOYEE table^^^^C. The MANAGER domain consists only of the value Y^^^^D. NAME, John S, Susan P, Jennifer L makes up a column in the EMPLOYEE table} Which of the following is NOT displayed by DB2 Access Plan?。
双语基础部分选择题- 选择题1.____________ can provide over two hours of high quality video and sound comparable to that found in theaters. (2.00分)A、CD-RWB、CD-ROMC、DVD-RD、DVD-ROM正确答案:D、DVD-ROM您未选择该题.2.____________holds data and program instructions for processing data. (2.00分)A、MemoryB、Primary storageC、RAMD、a, b and c正确答案:D、a, b and c您未选择该题.3.The file an object is linked from is called the ____________. (2.00分)A、origin fileB、layout fileC、support fileD、source file正确答案:D、source file您未选择该题.4.Files that are broken into small parts and stored wherever space is available are said to be ______________. (2.00分)A、compressedB、fragmentedC、lostD、uninstalled正确答案:B、fragmented您未选择该题.5.Type of RAM that is NOT temporary is ____________. (2.00分)A、virtual memoryB、Flash RAMC、cache memoryD、virtual and cache memory正确答案:B、Flash RAM您未选择该题.6.____________ uses the Internet rather than traditional communication lines to connect two or more people via telephone. (2.00分)A、A multifunctional deviceB、a fax machineC、a dumb terminalD、Telephony正确答案:D、Telephony您未选择该题.7.Norton SystemWorks is a _____________. (2.00分)A、Web serviceB、trouble shooting programC、utilityD、utility suite正确答案:D、utility suite您未选择该题.8.A(n) ________________ is a single program that provides the functionality of a word processor, spreadsheet, database manager, and more. (2.00分)A、general-purpose applicationB、software suiteC、integrated packageD、program manager正确答案:C、integrated package您未选择该题.9. ______________ are prewritten formulas that perform calculations automatically. (2.00分)A、FunctionsB、MacrosC、TemplatesD、Caculators正确答案:A、Functions您未选择该题.10.A production department might use a _____________ to monitor manufacturing processes and assembly line operations. (2.00分)A、mainframeB、microcomputerC、midrange computerD、supercomputer正确答案:C、midrange computer您未选择该题.11.The term _______________ refers to the widespread use of mobile communication devices.(2.00分)A、ITB、Wireless RevolutionC、PDAD、RAM正确答案:B、Wireless Revolution您未选择该题.12.Multimedia, Web authoring, graphics, and virtual reality programs are examples of ___________. (2.00分)A、special-purpose applicationsB、general-purpose applicationsC、basic applicationsD、occupational applications正确答案:A、special-purpose applications您未选择该题.13.In a relational database, data is organized into ____________. (2.00分)A、fieldsB、columnsC、recordsD、tables正确答案:D、tables您未选择该题.14.The _______________consists of the equipment:keyboard, mouse, monitor, system unit, and other devices. (2.00分)A、proceduresB、hardwareC、system unitD、information正确答案:C、system unit您未选择该题.15.A(n) __________ mouse emits and senses light to detect movement. (2.00分)A、cordlessB、wirelessC、pointerD、optical正确答案:D、optical您未选择该题.16.Database management systems are comprised of tables that are made up of rows called ____________ and columns called _____________. (2.00分)A、fields, recordsB、records, fieldsC、addresses, fieldsD、ranges, sheets正确答案:B、records, fields您未选择该题.17.The _____________ operating system is designed to run on Intel and Intel-compatible microprocessors. (2.00分)A、WindowsB、Mac OSC、LinuxD、Sherlock正确答案:A、Windows您未选择该题.18.Groups of inexpensive hard-disk drives grouped together and treated as a single large-capacity hard disk are called _________. (2.00分)A、disk cachesB、versatile disksC、RAIDsD、DVDs正确答案:C、RAIDs您未选择该题.19.A(n) _____________ file might contain audience handouts, speaker notes, and electronic slides.(2.00分)A、documentB、databaseC、worksheetD、presentation正确答案:D、presentation您未选择该题.20.Another name for floppy disk is __________. (2.00分)A、disksB、flexible disksC、floppiesD、all of the above正确答案:D、all of the above您未选择该题.21.ROM is a type of ______________. (2.00分)A、slotB、adapterC、networkD、firmare正确答案:D、firmare您未选择该题.22.____________ perform an operation when held down with another key. (2.00分)A、Toggle keysB、Combination keysC、Wand readersD、Monitors正确答案:B、Combination keys您未选择该题.23.A special-purpose output device for producing bar charts, maps, architectural drawings, and three-dimensional illustrations is a _____________. (2.00分)A、chain printerB、portable scannerC、ink-jet printerD、plotter正确答案:D、plotter您未选择该题.24.Desktop operating systems are also called _____________. (2.00分)A、network operating systemsB、client operating systemsC、Mac operating systemsD、stand-alone operating systems正确答案:D、stand-alone operating systems您未选择该题.25.Random-access memory(RAM) is a kind of _____________ storage. (2.00分)A、permanentB、temporaryC、flashD、smart正确答案:B、temporary您未选择该题.26.___________ is permanent storage used to preserve data and programs. (2.00分)A、Internal storageB、volatile storageC、Nonvolatile storageD、File compression正确答案:C、Nonvolatile storage您未选择该题.27.A(n) ______________, also called a data bus, connects the parts of the CPU together. (2.00分)A、adapter cardB、parallel portC、serial portD、bus line正确答案:D、bus line您未选择该题.28.____________ is exclusively a sequential-access storage media. (2.00分)A、A floppy diskB、A hard diskC、Magnetic tapeD、CD-ROM正确答案:C、Magnetic tape您未选择该题.29.Most presentation graphics programs provide ____________ that include sample text for many different types of presentations. (2.00分)A、layout filesB、templatesC、samplesD、records正确答案:A、layout files您未选择该题.30.To remove unneeded programs and related files from a hard disk you would use a __________.(2.00分)A、trouble-shooting programB、file compression programC、antivirus programD、uninstall program正确答案:D、uninstall program您未选择该题.31.The largest network in the world is called the ____________. (2.00分)A、InternetB、WWWC、World Wide WebD、all of the above正确答案:D、all of the above您未选择该题.32.General-purpose applications are also known as ___________. (2.00分)A、software suitesB、special-purpose applicationsC、advanced applicationsD、basic applications正确答案:D、basic applications您未选择该题.33.____________ is a Windows program that locates and eliminates unnecessary fragments and rearranges files and unused disk space to optimize operations. (2.00分)A、Disk CleanupB、Active DesktopC、SherlockD、Disk Defragmenter正确答案:D、Disk Defragmenter您未选择该题.34.Microcomputers process data and instructions in ______________. (2.00分)A、millisecondsB、microsecondsC、nonsecondsD、all of the above正确答案:B、microseconds您未选择该题.35.An internal hard disk is also known as a __________ because it is located inside the system unit. (2.00分)A、hard-disk packB、PC Card hard diskC、fixed diskD、hard disk cartridge正确答案:C、fixed disk您未选择该题.36.A network computer is also known as a(n)____________. (2.00分)A、thin clientB、intelligent terminalC、dumb terminalD、Net PC正确答案:A、thin client您未选择该题.37.Service programs are another name for ______________. (2.00分)A、operating systemsB、utilitesC、device driversD、language translators正确答案:B、utilites您未选择该题.38.The most important system software program is the ____________. (2.00分)A、word processorB、database management systemC、application softwareD、operating system正确答案:D、operating system您未选择该题.39.Speakers and headphones are the most widely used __________ devices. (2.00分)A、audio-inputB、audioC、audio-outputD、multifunctional正确答案:C、audio-output您未选择该题.40.A(n) ___________ typically combines the capabilities of a scanner, printer, fax, and copying machine. (2.00分)A、multifunctional deviceB、output deviceC、inputdeviceD、MICR正确答案:A、multifunctional device您未选择该题.41._____________ are specialized programs designed to allow input and output devices to communicate with a computer system. (2.00分)A、UtilitiesB、ResourcesC、Device driversD、GUIs正确答案:C、Device drivers您未选择该题.42.The _____________ operating system was originally designed to run on minicomputers in network envirnments. (2.00分)A、WindowsB、Mac OSC、UNIXD、Sherlock正确答案:C、UNIX您未选择该题.43.The most common input devices are the _____________ and the ____________. (2.00分)A、keyboard, printerB、mouse, monitorC、keyboard, microphoneD、mouse, keyboard正确答案:D、mouse, keyboard您未选择该题.44.____________ is a type of optical disk widely used to distribute large software application packages. (2.00分)A、CD-ROMB、CD-RC、CD-RWD、DVD-RW正确答案:A、CD-ROM您未选择该题.45.______________ is understanding the rules and the power of microcomputers. (2.00分)A、Computer competencyB、Wireless RevolutionC、ConnectivityD、Reactivity正确答案:A、Computer competency您未选择该题.46.ASCII, EBCDIC, and Unicode are examples of ______________. (2.00分)A、two-state systemsB、integrated circuitsC、binary coding schemesD、adapter cards正确答案:C、binary coding schemes您未选择该题.47.A wand reader is a type of ____________ recognition device. (2.00分)A、MICRB、OCRC、OMRD、touch surface正确答案:B、OCR您未选择该题.48.A handheld, book-sized device used to read downloaded content is a _____________. (2.00分)A、wand readerB、e-bookC、light penD、graphic tablet正确答案:B、e-book您未选择该题.nguage translators convert human language into ____________. (2.00分)A、machine languageB、UNIXC、service programsD、operating systems正确答案:A、machine language您未选择该题.50.A(n) ____________ is an input device similar to a copy machine. (2.00分)A、flatbed scannerB、printerC、digital cameraD、graphic tablet正确答案:A、flatbed scanner双语网络部分选择题- 选择题1.Modulation and demodulation are the processes of a(n) _________. (2.00分)A、connection deviceB、nodeC、modulatorD、modem正确答案:D、modem您未选择该题.2.Standard telephone lines and conventional modems provide what is called __________. (2.00分)A、network architectureB、broadbandC、dial-up serviceD、data transmission正确答案:C、dial-up service您未选择该题.3.V oiceband is also called __________. (2.00分)A、low bandwidthB、medium bandC、analog signalD、broadband正确答案:A、low bandwidth您未选择该题.4.Microcomputers with DSL, cable, and satellite connections use _________. (2.00分)A、analog signalsB、broadbandC、medium bandD、voiceband正确答案:B、broadband您未选择该题.5.In ___________, bits flow in a series or continuous stream. (2.00分)A、parallel data transmissionB、simplex communicationC、half-duplex communicationD、serial data transmission正确答案:D、serial data transmission您未选择该题.6.Every computer on the Internet has a unique numeric address called a(n) _________. (2.00分)A、packetB、RS-232 connectorC、IP addressD、bandwidth正确答案:C、IP address您未选择该题.7.The standard protocol for the Internet is _________. (2.00分)A、TCP/IPB、OSIC、RS-232CD、DSL正确答案:A、TCP/IP您未选择该题.8.__________ describes how the network is arranged and how the resources are coordinated and shared. (2.00分)A、TopologyB、Communication channelC、Sharing systemD、Network architecture正确答案:D、Network architecture您未选择该题.9.____________ controls and coordinates the activities of all computers and devices on a network.(2.00分)A、TCP/IPB、NOSC、DNSD、OSI正确答案:B、NOS您未选择该题.10.In a(n) ___________ network, each device in the network handles its own communications control. (2.00分)A、hostB、clientC、busD、sharing正确答案:C、bus您未选择该题.11.The Internet was launched in 1969 when the U.S. funded a project to develop a national computer network called _________. (2.00分)A、ARPANETB、CERNC、WWWD、the Web正确答案:A、ARPANET您未选择该题.12._____________ use telephone lines and service an area consisting of several states. (2.00分)A、Wireless service providersB、National service providersC、Local service providersD、Regional service providers正确答案:D、Regional service providers您未选择该题.13.____________ present focused content to appeal to special-interest groups. (2.00分)A、AgentsB、Horizontal portalsC、Vertical portalsD、Web portals正确答案:C、Vertical portals您未选择该题.14.To participate in a chat group, select a _________ and communicate live with others. (2.00分)A、indexB、engineC、listD、channel正确答案:D、channel您未选择该题.15.Bots are also known as _________ and __________. (2.00分)A、indexes, hitsB、agents, spidersC、providers, hitsD、agents, providers正确答案:B、agents, spiders您未选择该题.16.In a directory or _________ search, you select a category that fits the information you want.(2.00分)A、packetB、keywordC、indexD、specialized正确答案:C、index您未选择该题.17.In __________ commerce, individuals sell to other individuals without ever meeting face to face. (2.00分)A、C2CB、B2CC、B2BD、C2I正确答案:A、C2C您未选择该题.18.__________ are programs that are automatically loaded and operate as a part of your browser.(2.00分)A、Add-insB、Plug-insC、HelpersD、Utilities正确答案:B、Plug-ins您未选择该题.19.____________ are independent programs that can be executed or launched from your browser.(2.00分)A、Plug-insB、ProvidersC、AgentsD、Applets正确答案:D、Applets您未选择该题.20.___________ are programs that automatically connect to Web sites, download HTML documents, and save them to your hard disk. (2.00分)A、Off-line browsersB、Web-downloading utilitiesC、Pull productsD、all of the above正确答案:A、Off-line browsers概念复习- 选择题1.The layout of the computers and devices in a communications network is called a(n) ____. (1.00分)network architecturenetwork topologycommunications satelliteintelligent network正确答案:network topology您未选择该题.2.______________ are prewritten formulas that perform calculations automatically. (1.00分)CaculatorsTemplatesMacrosFunctions正确答案:Functions您未选择该题.3.______________ is understanding the rules and the power of microcomputers. (1.00分)ReactivityConnectivityWireless RevolutionComputer competency正确答案:Computer competency您未选择该题.4.The _______________consists of the equipment:keyboard, mouse, monitor, system unit, and other devices.(1.00分)informationsystem unithardwarepeople正确答案:system unit您未选择该题.5.____________ are independent programs that can be executed or launched from your browser. (1.00分) AppletsAgentsProvidersPlug-ins正确答案:Applets您未选择该题.6.Type of RAM that is NOT temporary is ____________. (1.00分)virtual and cache memorycache memoryFlash RAMvirtual memory正确答案:Flash RAM您未选择该题.7.The following formula is considered to be a relative reference: (1.00分)B17$B17B$17$B$17正确答案:B17您未选择该题.8.A network on which a cable forms a closed loop with all computers and devices arranged along the loop is known as a _________. (1.00分)ring networktoken ringstar networkbus network正确答案:ring network您未选择该题.9.In a(n) ___________ network, each device in the network handles its own communications control. (1.00分) sharingbusclienthost正确答案:bus您未选择该题.10.Before data can be entered to a database, a user must plan its ____________. (1.00分)modeloperatorlogicstructure正确答案:structure您未选择该题.11.The Internet was launched in 1969 when the U.S. funded a project to develop a national computer network called _________. (1.00分)the WebWWWCERNARPANET正确答案:ARPANET您未选择该题.12.Desktop operating systems are also called _____________. (1.00分)stand-alone operating systemsclient operating systemsembedded operating systemsnetwork operating systems正确答案:stand-alone operating systems您未选择该题.13.___________ are programs that automatically connect to Web sites, download HTML documents, and save them to your hard disk. (1.00分)a and bPull productsWeb-downloading utilitiesOff-line browsers正确答案:Off-line browsers您未选择该题.14.Random-access memory(RAM) is a kind of _____________ storage. (1.00分)smartflashtemporarypermanent正确答案:temporary您未选择该题.15.__________ describes how the network is arranged and how the resources are coordinated and shared. (1.00分)Network architectureSharing systemCommunication channelTopology正确答案:Network architecture您未选择该题.16.______________ is a set of hardware and software standards that allows expansion boards and other devices to install themselves. (1.00分)Industry Standard ArchitectureSystem UnitUnicodePlug and Play正确答案:Plug and Play您未选择该题.17.A handheld, book-sized device used to read downloaded content is a _____________. (1.00分)digital notebookgraphic tabletlight pene-book正确答案:e-book您未选择该题.18.Speakers and headphones are the most widely used __________ devices. (1.00分)personalaudio-outputmultifunctionalaudio-input正确答案:audio-output您未选择该题.19.Conventional computers with complete instruction sets are referred to as ____________. (1.00分) SRAMCISCASCIIRISC正确答案:CISC您未选择该题.20.__________ has to regularly make changes to a particular field. (1.00分)Data redundancyData sharingData integrityData maintenance正确答案:Data maintenance您未选择该题.21.Modulation and demodulation are the processes of a _________. (1.00分)connection devicenodemodulatormodem正确答案:modem您未选择该题.22.A(n) ______________, also called a data bus, connects the parts of the CPU together. (1.00分) bus lineserial portparallel portadapter card正确答案:bus line您未选择该题.23.Documents on the Web are called ____________. (1.00分)Web pagesWeb sitesWeb communitiesWeb tags正确答案:Web pages您未选择该题.24.Another name for asynchronous data transmission is ____________. (1.00分)go/no goupload/downloadyes/nostart/stop正确答案:start/stop您未选择该题.25.A(n) ____________ is an input device similar to a copy machine. (1.00分)portable scannerprinterdigital cameraflatbed scanner正确答案:flatbed scanner您未选择该题.26.Most presentation graphics programs provide ____________ that include sample text for many different types of presentations. (1.00分)recordssamplestemplateslayout files正确答案:layout files您未选择该题.27.The CRT technology that hits the phosphorus coated screen with an electron beam is called ____________.(1.00分)monitoringraster scanningimagingcopying正确答案:raster scanning您未选择该题.28.How much memory is required for the following display? An IBM PC with a display of 512 colors and 1024 768 pixels. (1.00分)1,769,472 bytes786,432 bytes720,000 bytes884,736 bytes正确答案:884,736 bytes您未选择该题.29._____________ are specialized programs designed to allow input and output devices to communicate with a computer system. (1.00分)GUIsDevice driversResourcesUtilities正确答案:Device drivers您未选择该题.30.In a MS Access query, what would be the criteria for displaying all employees who earn not more than $30,000?(1.00分)<30000<=30000>30000>=30000正确答案:<=30000您未选择该题.31.A cylinder is a term used to describe how data is stored on a _________. (1.00分)CD ROMDVDhard diskfloppy disk正确答案:hard disk您未选择该题.32.Which is not true of a ‘primary key’in MS Access? (1.00分)it restricts access to the tableit maintains the integrity of the databasethere cannot b e 2 records with the same primary keyit is good practice to set up a primary key in each tale of a database正确答案:it restricts access to the table您未选择该题.33.The largest network in the world is called the ____________. (1.00分)all of the aboveWebWorld Wide WebWWW正确答案:all of the above您未选择该题.34.The most important system software program is the ____________. (1.00分)operating systemapplication softwaredatabase management systemword processor正确答案:operating system您未选择该题.35.A cookie is a small file that is stored on _________. (1.00分)the serverthe E-Commerce sitethe user’s computera CDROM正确答案:the user’s computer您未选择该题.36.In which kind of network do all computers have equal status and share files and peripheral devices? (1.00分) buspeer-to-peerringstar正确答案:peer-to-peer您未选择该题.37.Bots are also known as _________ and __________. (1.00分)agents, providersproviders, hitsagents, spidersindexes, hits正确答案:agents, spiders您未选择该题.38.The two types of system software are operating systems and ____________. (1.00分)compression programsutility servicesvirus checkersfile viewers正确答案:utility services您未选择该题.39.Database management systems are comprised of tables that are made up of rows called ____________ and columns called _____________. (1.00分)ranges, sheetsaddresses, fieldsrecords, fieldsfields, records正确答案:records, fields您未选择该题.40.To have an object automatically updated in a destination file when a change is made to the source file, the object must be _______________. (1.00分)resolvedreplacedlinkedembedded正确答案:linked您未选择该题.41.A(n) ____ port can connect up to 127 different peripherals together with a single connector type. (1.00分) IrDAUSBBluetoothserial正确答案:USB您未选择该题.42.Service programs are another name for ______________. (1.00分)language translatorsdevice driversutilitesoperating systems正确答案:utilites您未选择该题.43.ROM is a type of ______________. (1.00分)firmareadapterslotsemiconductor正确答案:firmare您未选择该题.44.Groups of inexpensive hard-disk drives grouped together and treated as a single large-capacity hard disk areDVDsRAIDsversatile disksdisk caches正确答案:RAIDs您未选择该题.45.A 3 1/2 inch floppy disk contains 80 tracks and is divided into 18 sectors. Each sector in each track holds 512 characters. The disk is double sided. What is the capacity of the disk? (1.00分)1,474,560 bytes737,280 bytes512,000 bytes368,640 bytes正确答案:1,474,560 bytes您未选择该题.46.__________ are programs that are automatically loaded and operate as a part of your browser. (1.00分) UtilitiesHelpersPlug-insAdd-ins正确答案:Plug-ins您未选择该题.47.A fast computer with a limited instruction set is called ____________. (1.00分)CISCALUASCIIRISC正确答案:RISC您未选择该题.48.To participate in a chat group, select a _________ and communicate live with others. (1.00分)channellistenginesignal正确答案:channel您未选择该题.49.The _____________ operating system is designed to run on Intel and Intel-compatible microprocessors. (1.00分)NortonLinuxMac OSWindows正确答案:Windows您未选择该题.50.____________holds data and program instructions for processing data. (1.00分)all of the abovePrimary storageMemory正确答案:all of the above您未选择该题.51.Microcomputers process data and instructions in ______________. (1.00分)picosecondsnonsecondsmicrosecondsmilliseconds正确答案:microseconds您未选择该题.52.The card inserted in a slot in a personal computer to allow it to send and receive messages from the LAN is the ____________. (1.00分)CSMA/CDNICTCP/IPEFT正确答案:NIC您未选择该题.53.A special computer that directs communications traffic among several linked networks is a ____. (1.00分) nodehostclientrouter正确答案:router您未选择该题.54.A company wishes to store records on its 1500 customers and 200 stock items. Each customer requires 25 KB, each stock item 20 KB and each sales order 30 KB. Each customer has on average 20 sale orders per year. Estimate the size of the files over a one ye (1.00分)9GB0.9GB1.8GB0.8GB正确答案:0.9GB您未选择该题.55.A production department might use a _____________ to monitor manufacturing processes and assembly line operations. (1.00分)supercomputermidrange computermicrocomputermainframe正确答案:midrange computer您未选择该题.56.A(n) __________ mouse emits and senses light to detect movement. (1.00分)opticalpointer正确答案:optical您未选择该题.57.Which of the following pieces of code will show the entire text on your web page in large font? (1.00分)<HEAD><BASEFONT SIZE=7></HEAD><HEAD><BASEFONT SIZE=3></HEAD><BODY ><BASEFONT SIZE=7></BODY><TITLE><BASEFONT SIZE=7></TITLE>正确答案:<HEAD><BASEFONT SIZE=7></HEAD>您未选择该题.58.The term _______________ refers to the widespread use of mobile communication devices. (1.00分)RAMPDAWireless RevolutionIT正确答案:Wireless Revolution您未选择该题.59.Electronic Commerce is best described as: ____________. (1.00分)Business transactions across the World Wide WebBusiness transactions across the InternetBusiness transactions using any electronic mediaBuying and selling over the network正确答案:Business transactions using any electronic media您未选择该题.60.The system unit is also called the _____________. (1.00分)system cabinet and chassissystem boardchassissystem cabinet正确答案:system cabinet and chassis您未选择该题.61._____________ use telephone lines and service an area consisting of several states. (1.00分)Regional service providersLocal service providersNational service providersWireless service providers正确答案:Regional service providers您未选择该题.62.____________ can provide over two hours of high quality video and sound comparable to that found in theaters.(1.00分)DVD-ROMDVD-RCD-ROMCD-RW正确答案:DVD-ROM63.Databases integrity refers to ____________. (1.00分)a relational databasethe integrity of the useran accurate databasea redundant database正确答案:an accurate database您未选择该题.64.Modulation converts a signal form _________. (1.00分)synchronous to digitaldigital to analogdigital to synchronousanalog to digital正确答案:digital to analog您未选择该题.65.To create a link to your email address on your Web Page, the following code should be used: (1.00分)<A HREF=mail to:bobby@>My email</A><A HREF=mailto:bobby@>My email</A><A MAIL TO=bobby@>My email</A><A HREF=bobby@>My email</A>正确答案:<A HREF=mailto:bobby@>My email</A>您未选择该题.66.The tag used to enclose the content of the page is the ____________. (1.00分)body taganchor tagimage tagcontent tag正确答案:body tag您未选择该题.67.The technology that lets businesses send business forms electronically is called __________. (1.00分) Electronic Data InterchangeV oice MailFile Transfer SoftwareEFT POS正确答案:Electronic Data Interchange您未选择该题.68.An internal hard disk is also known as a __________ because it is located inside the system unit. (1.00分) hard disk cartridgeremovable diskfixed diskPC Card hard disk正确答案:fixed disk您未选择该题.69.V oiceband is also called __________. (1.00分)。
数据库考试题及答案Introduction:A database is an organized collection of data that can be stored, accessed, and managed. It plays a crucial role in various industries, including finance, healthcare, and e-commerce. In this article, we will explore a set of database exam questions and provide their corresponding answers.1. Define a relational database and explain its components.A relational database is a type of database that organizes data into tables, which consist of rows and columns. Its components include:- Tables: They represent entities or concepts in the real world and consist of rows (tuples) and columns (attributes).- Rows (tuples): Each row represents a single record or instance of an entity, and it contains values for each attribute.- Columns (attributes): They define the characteristics or properties of an entity, such as name, age, or address.- Keys: They are used to uniquely identify each row in a table. Primary keys are unique identifiers for the table, while foreign keys establish relationships between tables.- Relationships: They define associations between tables, such as one-to-one, one-to-many, or many-to-many relationships.2. What is the purpose of SQL and explain its main components.SQL (Structured Query Language) is a programming language used for managing and manipulating relational databases. Its main components include:- Data Definition Language (DDL): It is used to define and manage the structure of the database objects, such as creating tables, altering table structures, and deleting tables.- Data Manipulation Language (DML): It is used to manipulate the data within the tables, including inserting, retrieving, updating, and deleting records.- Data Control Language (DCL): It deals with user access and security, including granting and revoking permissions, and managing user roles and privileges.- Transaction Control Language (TCL): It is used to manage the database transactions, including committing or rolling back changes.3. Describe the ACID properties in the context of database transactions.ACID stands for Atomicity, Consistency, Isolation, and Durability, which are the four properties that ensure reliability and integrity in database transactions.- Atomicity: It guarantees that a transaction is treated as a single unit of work, where all its operations are completed successfully, or none of them are executed at all. If any operation fails, the transaction is rolled back, and the database is left unchanged.- Consistency: It ensures that a transaction brings the database from one consistent state to another. The integrity constraints, such as primary key or foreign key constraints, are maintained during the transaction.- Isolation: It ensures that each transaction is executed independently and in isolation from other concurrent transactions. Each transaction should not be affected by other transactions until it is completed.- Durability: It ensures that once a transaction is committed, its changes are permanent and will survive any subsequent system failures. The changes are recorded in a transaction log and can be recovered in case of a crash or restart.4. Differentiate between a primary key and a foreign key.A primary key is a unique identifier for a table that enforces the entity's integrity and ensures data uniqueness. It uniquely identifies each record in the table and is used to establish relationships between tables. Only one primary key can be defined per table.A foreign key, on the other hand, establishes a relationship between two tables. It refers to the primary key of another table and helps maintain referential integrity. A foreign key can have duplicate values and allows for multiple occurrences in a table, unlike a primary key.5. Explain the difference between SQL's JOIN and UNION operators.JOIN and UNION are two different SQL operators used for combining data from multiple tables or queries.- JOIN: It is used to retrieve data by combining rows from two or more tables based on related columns. There are different types of JOIN operations, such as INNER JOIN, LEFT JOIN, RIGHT JOIN, and FULL JOIN, each specifying a different way to combine the tables based on matching or non-matching rows.- UNION: It is used to combine the result sets of two or more SELECT statements into a single result set. The columns and data types of the SELECT statements being combined must match. UNION removes duplicate rows from the final result set, while UNION ALL retains all rows, including duplicates.Conclusion:Understanding the fundamental concepts of databases and their components is crucial for successful data management and manipulation. This article covered a range of exam questions related to databases, providing clear explanations and answers. By grasping these concepts, individuals can enhance their knowledge and skills in utilizing databases effectively.。
From Ontology to Relational DatabasesAnuradha Gali1,Cindy X.Chen1,Kajal T.Claypool1and Rosario Uceda-Sosa2 1Department of Computer Science,University of Massachusetts,Lowell,MA01854,U.S.A.{agali|cchen|kajal}@2IBM T.J.Watson Research Center,Hawthorne,NY10532,U.S.A.rosariou@Abstract.The semantic web envisions a World Wide Web in whichdata is described with rich semantics and applications can pose com-plex queries.Ontologies,a cornerstone of the semantic web,have gainedwide popularity as a model of information in a given domain that canbe used for many purposes,including enterprise integration,databasedesign,information retrieval and information interchange on the WorldWide Web.Much of the current focus on ontologies has been on thedevelopment of languages such as DAML+OIL and OWL that enablethe creation of ontologies and provide extensive semantics for Web data,and on answering intensional queries,that is,queries about the struc-ture of an ontology.However,it is almost certain that the many of thesemantic web queries will be extensional and toflourish,the semanticweb will need to accommodate the huge amounts of existing data that isdescribed by the ontologies and the applications that operate on them.Given the established record of relational databases to store and querylarge amounts of data,in this paper we present a set of techniques toprovide a lossless mapping of an OWL ontology to a relational schemaand the corresponding instances to data.We present preliminary exper-iments that compare the efficiency of the mapping techniques in termsof query performance.1IntroductionThe Semantic Web brings closer to realization the possibility of semantically organized data repositories,or ontologies,throughout the Internet that can be used for intelligent information searching both by humans and computational agents.Ontologies are human readable,comprehensive,sharable and formal which means that they are expressed in a language that has well-defined se-mantics.Ontologies are important to application integration solutions because they provide a shared and common understanding of data that exist within an application integration problem domain.Ontologies also facilitate communica-tion between people and information systems.However,while today there is an un-precedented wealth of information available on the Web,to fully realize the power of ontologies and to enable efficient andflexible information gather-ing,persistent storage of ontologies and its subsequent retrieval is of paramount importance.2There are three possible approaches to store the ontology data and execute queries on that data.One is to build a special purpose database system which will be tailored to store and retrieve ontology specific data.The second is to use an object oriented database system exploiting the rich data modeling capabili-ties of OODBMS.Given the popularity of SQL and the efficiency of executing these queries,a complimentary approach is to use relational database systems. In this approach the OWL data is mapped into tables of a relational schema and the queries posed in an ontology language are translated into SQL queries. Relational database systems are very mature and scale very well,and they have the additional advantage that in a relational database,ontology data and the traditional structured data can co-exist making it possible to build applications that involve both kinds of data.While there are approaches that focus on trans-lating XML documents into corresponding relational tables and data[9,3],to the best of our knowledge ours is thefirst to focus on the persistent relational storage of OWL ontologies.The rest of the paper is organized as follows:Section2gives an overview of OWL.Section3describes briefly the related work in terms of the different map-ping schemes available for storing the XML documents in the relational database. The algorithm for translating the given OWLfile into relational schema is ex-plained in Section4.Section5describes the preliminary performance comparison of the different approaches.We conclude in Section6.2Background:Ontologies and OWLOntology is the key enabling technology for the semantic web.The main purpose of an ontology is to enable communication between computer systems in a way that is independent of the individual system technologies,information architec-tures and application domain.The key ingredients that make up an ontology are a vocabulary of basic terms,semantic interconnections,simple rules of inference and some logic for a particular topic.Ontologies may vary not only in their content,but also in their structure, implementation,level of description,conceptual scope,instantiation and lan-guage specification.Ontologies are not all built the same way.A number of possible languages can be used,including general logic programming languages such as Prolog.More common,however,are languages that have evolved specif-ically to support ontology construction.The Open Knowledge Base Connectiv-ity(OKBC)model and languages like KIF(and its emerging successor CL–Common Logic)are examples that have become the bases of other ontology lan-guages.There are also several languages based on a form of logic thought to be especially computable,known as description logics.These include Loom and DAML+OIL,which are currently being evolved into the Web Ontology Lan-guage(OWL)standard.When comparing ontology languages,what is given up for computability and simplicity is usually language expressiveness,which many developers disagree since they feel that a good language should have a sound3 underlying semantics.[1]gives a good overview of all the relevant technologies in Ontology.OWL.OWL[6]is a language for defining and instantiating Web ontologies. An OWL ontology may include descriptions of classes,properties and their in-stances.Given an ontology,the OWL formal semantics specify how to derive its logical consequences,i.e.facts not literally present in the ontology,but entailed by the semantics.These entailments may be based on a single document or mul-tiple distributed documents that have been combined using defined OWL mech-anisms.The OWL language provides three increasingly expressive sub-languages designed for use by specific communities of implementers and users.OWL Lite supports those users primarily needing a classification hierarchy and simple constraint features.For example,while OWL Lite supports cardinal-ity constraints,it only permits cardinality values of0or1.It is typically simpler to provide tool support for OWL Lite than its more expressive relatives,and provide a quick migration path for thesauri and other taxonomies.OWL DL supports those users who want the maximum expressiveness with-out losing computational completeness(all entailments are guaranteed to be computed)and decidability(all computations willfinish infinite time)of rea-soning systems.OWL DL includes all OWL language constructs with restrictions such as type separation(a class can not also be an individual or property,a prop-erty can not also be an individual or class).OWL DL was designed to support the existing Description Logic business segment and has desirable computational properties for reasoning systems.OWL Full is meant for users who want maximum expressiveness and the syntactic freedom of RDF with no computational guarantees.For example,in OWL Full a class can be treated simultaneously as a collection of individuals and as an individual in its own right.Another significant difference from OWL DL is that a owl:DatatypeProperty can be marked as an owl:InverseFunctionalProperty. OWL Full allows an ontology to augment the meaning of the pre-defined(RDF or OWL)vocabulary.It is unlikely that any reasoning software will be able to support every feature of OWL Full.3Related Work-XML Mapping ApproachesGiven the similarities between XML and OWL,in this section we give a brief overview of the mapping approaches that have been proposed in literature for XML documents.Edge Approach.The simplest scheme proposed by Florescu et al.[3]is to store all attributes in a single table called the Edge table.The Edge table records the object identities(oids)of the source and target objects of the attribute,the name of the attribute,aflag that indicates whether the attribute is an inter-object reference or points to a value,and an ordinal number used to recover all attributes of an object in the right order and to carry out updates if the object4has several attributes with the same name.The Edge table,therefore,has the following structure:Edge(source,ordinal,name,flag,target)The key of the Edge table is source,ordinal.Figure2shows how the Edge table would be populated for the example XML graph.Attribute Approach.Attribute mapping scheme groups all attributes with the same name into one table.Conceptually,this approach corresponds to a horizontal partitioning of the Edge table used in thefirst approach,using name as the partitioning attribute.Thus,as many Attribute tables are created as for different attribute names in the XML document,and each Attribute table has the following structure:Aname(source,ordinal,flag,target)The key of the Attribute table is source,ordinal,and all thefields have the same meaning as in the Edge approach.Universal Approach.Universal table approach stores all the attributes of an XML document.This corresponds to a Universal table with separate columns for all the attribute names that occur in the XML document.Conception ally, this Universal table corresponds to the result of an outer join of all Attribute tables.The structure of the Universal table is as follows,if n1,n2,...,nk are the attribute names in the XML document,thenUniversal(source,ordinaln1,flagn1,targetn1,ordinaln2,flagn2,targetn2,...,ordinalnk,flagnk,targetnk) The Universal table has manyfields which are set to null,and it also has a great deal of redundancy.Normalized Universal Approach.The UnivNorm approach,is a variant of the Universal table approach.The difference between the UnivNorm and Uni-versal approach is that multi-valued attributes are stored in separate Over-flow tables in the UnivNorm approach.For each attribute name that occurs in the XML document a separate Overflow table is established,following the principle of the Attribute approach.This way,there is only one row per XML object in the UnivNorm table and that table is normalized.The structure of the UnivNorm table and the Overflow tables is as follows,if n1;:::;nk are all the attribute names in the XML document,thenUnivNorm(source,ordinaln1,flagn1,targetn1,ordinaln2,flagn2, targetn2,...,targetnk)OverflowOwn1(source,ordinal,flag,target)OverflowOwnk(source,ordinal,flag,target)The key of the UnivNorm table is source.The key of the Overflow table is fsource,ordinalg.5 Basic Inlining Approach.Basic Inlining Approach converts the XML DTD into relations.Basic inlines as many descendants of an element as possible into a single relation.Basic creates relations for every element because an XML document can be rooted at any element in a DTD.Basic approach is highly inefficient since it creates a large number of relations.Shared Inlining Approach.Shared Inlining tries to avoid the drawbacks of basic by ensuring that an element node is represented in exactly one relation. Shared identifies the element nodes that are represented in multiple relations in Basic and shares them by creating separate relation for these elements.In shared,relations are created for all elements in the DTD graph whose nodes have an in-degree greater than one.Nodes with an in-degree of one are inlined. Element nodes having an in-degree of zero are also made into separate relations, because they are not reachable from any other node.Elements below a“*”node are made into separate relations.Hybrid Inlining Approach.The hybrid inlining technique is the same as shared except that it inlines some elements that are not inlined in shared.Hy-brid additionally inlines elements with in-degree greater than one that are not recursive or reached through a“*”node.4Mapping OWL to Relational SchemaSemantic web is increasingly gaining popularity and importance with an in-creasing number of people using ontologies to represent their information.To augment the growth of ontology,efficient persistent storage of ontology concepts and data is essential.We now examine relational databases as an effective per-sistent store for ontologies.While there is research on storing XML documents in relational databases,there has not been much work done on the persistent storage of ontologies,in particular of ontologies described by OWL.In this section,we present an approach to map OWL to relational schema. The goal of our work is to devise an approach that will result in fewer joins when a user issues a query since join is an expensive operation.Since OWL is based on XML Syntax,but defines a lot of constraints on classes and provides inference,the approaches to store XML documents in relational databases are not fully applicable.We need to preserve all the constraint information while mapping OWL into relational schemas.4.1System ArchitectureOur OWL to relational schema mapping system contains three parts—Ontology Modeler,Document Manager and Ontology Resource Manager.Ontology Modeler takes OWL documents as input and creates an ontology model that is similar to DOM[2]for XML documents.While parsing the OWL documents,all the constraints will also be detected and recorded.An appropriate6OWL reasoner,depending upon the input document if its OWL Lite,OWL full or OWL DL,is selected.Currently,all the OWL documents are stored in main memory for parsing.Document Manager helps in processing and handling of OWL documents.It uses Jena[4]to assist importing of OWL documents.This is important because if we do not do this,once the imports have been processed,it would be impossible to know where a statement came from.Document Manager helps in processing and handling multiple OWL documents.It builds the union of the imported documents and creates new models for the imported OWL documents.Ontology Reasoner provides methods for listing,getting and setting the RDF[8]types of a resource.The rdf:type property defines many entailment rules in the semantic models of the various ontology languages.4.2OWL2DB AlgorithmThe algorithm we developed to map an OWL document into relational table is given in Algorithm1.1:The given OWLfile isfirst parsed for Root classes that returns an iterator over all the root classes.2:Iterate through the root classes to determine the depth of the descendants.3:The showclass method is called that keeps track of the depth of the subclasses from the root and when the depth of the graph is3then a relation table is created for all the subclasses above it with attribute names/instances as column names.4:The above step is repeated starting from the last subclass and traversing the graph and collecting the list of all the table names and column names of subclasses that are a the depth of three from the starting node.5:The depth of the Union/complement/disjoint subclasses on the same level are the same.6:Separate relations are created for classes that are disjoint from each other.7:Once the information on tablenames and corresponding attributes are collected, we need to collect the values of the instances to populate the database.The graph is parsed again to collect the values that are stored in a data structure.8:Finally,a database connection is established and all the tables are created and then the values are inserted.Inlining the root is handled the same way as a parent node.7<rdfs:comment>An example of OWL Ontology</rdfs:comment><owl:priorVersion rdf:resource="C:\usr\Repository\iris1.0\data\schema\IRISData.xsd"/><owl:imports rdf:resource="/2001/XMLSchema-instance"/> <rdfs:label>Furnite Ontology</rdfs:label><!----Main Classes-----><owl:Class rdf:ID="OntologyDependency"/><rdfs:label xml:lang="en">ShoppingCatalogOntology</rdfs:label></owl:Class><owl:Class rdf:ID="Relation"/><rdfs:label>Relation/rdfs:label></owl:Class><owl:Class rdf:ID="ProtoNode"/><rdfs:label>ProtoNode</rdfs:label></owl:Class><owl:Class rdf:ID="AtomicNode"/><rdfs:label>Atomic Node</rdfs:label></owl:Class><!----Sub Classes-----><owl:Class rdf:ID="Name"/><rdfs:subClassOf rdf:resource="#Relation"/><rdfs:label xml:lang="en">Name</rdfs:label></owl:Class><owl:Class rdf:ID="Arity"/><rdfs:subClassOf rdf:resource="#Relation"/><rdfs:label xml:lang="en">Arity</rdfs:label></owl:Class><owl:Class rdf:ID="Reflexive"/><rdfs:subClassOf rdf:resource="#Relation"/><rdfs:label xml:lang="en">Reflexive</rdfs:label></owl:Class><owl:Class rdf:ID="Name"/><rdfs:label>Name</rdfs:label><rdfs:subClassOf><owl:Restriction><owl:onProperty rdf:resource="#ProtoNode"/><owl:DatatypeProperty rdf:ID="string"></owl:Restriction></rdfs:subClassOf></owl:Class><owl:Class rdf:ID="IsAbstract"/><rdfs:label>IsAbstract</rdfs:label>8<rdfs:subClassOf><owl:Restriction><owl:onProperty rdf:resource="#ProtoNode"/><owl:DatatypeProperty rdf:ID="string"></owl:Restriction></rdfs:subClassOf></owl:Class>-<owl:Class rdf:ID="ProtoNode"/><rdfs:subClassOf><owl:Restriction><owl:onProperty rdf:resource="#ProtoNode"/></owl:Restriction></rdfs:subClassOf></owl:Class>-<owl:Class rdf:ID="Name"/><rdfs:label>Name</rdfs:label><rdfs:subClassOf rdf:resource="#ProtoNode"/><owl:Restriction><owl:DatatypeProperty rdf:ID="string"></owl:Restriction></owl:Class>-<owl:Class rdf:ID="constraintNexus"/><rdfs:label>Constraint Nexus</rdfs:label><rdfs:subClassOf><owl:Restriction><owl:onProperty rdf:resource="#ProtoNode"/></owl:Restriction></rdfs:subClassOf></owl:Class>-<owl:Class rdf:ID="Relation"/><rdfs:label>Relation</rdfs:label><rdfs:subClassOf rdf:resource="#constraintNexus"/><owl:Restriction><owl:DatatypeProperty rdf:ID="string"><rdfs:domain rdf:resource="#ProtoNode"/></owl:Restriction></owl:Class>Fig.1.Sample OWL document.9OntologyDependencyShopping CartName ReflexiveSPATIAL RELATION true2falseTable2.Relation Table5PerformanceTo test the performance of our system,we generated two OWLfiles which are wide and deeply nested based on wine.owl and food.owl[7].The OWLfile was parsed and separate relations were created for all children nodes at a depth of 2.The nodes with an in-degree less than2were inlined.The experiment was repeated,creating relations for child nodes that were at depth3,4,5, (10)etc.After each mapping,queries were executed to determine the depth-level at which the inlining should occur for optimal performance.Based on the result, we have decided that the optimal performance is obtained when the nodes with an in-degree of3to5are inlined based on the depth of the OWL document. When the inlining increases more than that then the performance is close to the performance of Universal Table approach.Experimental evaluations were conducted on all the different mapping schemes discussed in Section3and also for the OWL to relations mapping.The database used for the performance evaluation is IBM DB2[5].The parameters considered were time taken and number of joins needed to perform a simple select or update query.Separate databases were created for each mapping schemes.The same set of Queries were issued on all the databases.and the results are shown in Figure2, 3,4,and 5.The queries that were used are as follows.Query1A simple select query to display all the information in the table.S elect hasColor,hasLocation,hasBody,hasSugar from WineIsAbstractShopping Catalog Base Physical ObjectTable3.Proto Table10IsAbstract ConstraintRelationPhysical Object false ShoppingCatalogBaseTable4.Child Proto TableQuery2A delete query.D elete hasSugar from all the Wines that have hasColor=RedQuery3An update query.U pdate the hasBody for all the Wines located in Sauterine RegionQuery4A select query with joins.L ist all the Wines made in Bordeaux(several location)The performance evaluation showed in Figures2,3,4,53clearly indicate that Basic Inlining,Universal and Normalized Universal approach perform worst among the other methods.It also proves that OWL2DB performs pretty close to shared and attribute mapping approaches that are known to be the optimal mapping approaches from XML to Relations.OWL2DB is therefore a clearly an optimal mapping from OWL to Relations.6ConclusionOntology has more expressive power than XML but XML is richer in defining structures and grammar.Ontology and XML can be used to describe semi-structured natural language texts.Ontology is about sharing and consensual terminology and XML is used to accomplish that.Ontology provides a domain theory while XML provides the structure of data container.Ontology is a power-ful new tool for building enterprise and web-based information systems that hold the promise of drastically reducing system construction and maintenance costs. It helps businesses develop information systems that are reusable,maintainable, and able to talk with other systems sharing similar kinds of information.XML can be used as the underlying technology for Ontology since it is pretty mature. Both XML and Ontology together can pave the way for the dynamic knowledge management systems.This paper describes an efficient approach to mapping OWL documents into relational tables.There has not been much work in this area and we have tried to make the process autonomous,that is there is no human intervention once the input document is given.As the semantic web is gaining importance lately, we need an efficient approach to store all the ontology documents for the ease of querying and this paper introduces afirst attempt in this direction.1110 20 30 40 50 60 700 1 2 3 4 5 6 7 8 9’datafile1.dat’Fig.2.Simple Select Query Q1 0102030405060700 1 2 3 4 5 6 7 8 9’datafile1.dat’Fig.3.Update Query Q210 20 30 40 50 60 700 1 2 3 4 5 6 7 8 9’datafile1.dat’Fig.4.Delete Query Q3 0102030405060700 1 2 3 4 5 6 7 8 9’datafile1.dat’Fig.5.Join Query Q412References1.John Davies,Dieter Feasel,and Frank Van Harmelen.Towards the Semantic Web:Ontology Driven Knowledge Management.John Wiley snd Sons Inc,2003.2.Document Object Model(DOM)Level3Core Specification./TR/2004/REC-DOM-Level-3-Core-20040407/.3.Daniela Florescu and Donald Kossman.Performance evaluation of alternate map-ping schemes for stoing xml data in a relational database.Technique Report,1999.4.Jena Documentation./ontology/index.html.5.David Martineau.DB2Universal Database for Application Development.JohnWiley snd Sons Inc,1998.6.OWL Web Ontology Language./TR/owl-guide/.7.OWL Web Ontology Language Reference./TR/owl-ref/.8.RDF Primer./TR/2004/REC-rdf-primer-20040210/.9.Jayavel Shanmugasundaram,Kristin Tufte,Gang He,Chun Zhang,David DeWitt,and Jeffrey Naughton.Relational databases for querying xml documents:Limita-tions and opportunities.Proceedings of25VLDB Conference,1999.。