Cisco 6509配置手册
- 格式:doc
- 大小:161.00 KB
- 文档页数:23

cisco6509 时间访问列表配置要达到的具体要求如下:周一到周五早8:00到12:00不允许上网,12:00到13:00可以上网,13:00到17:00不可以上网,17:00以后到第二天早上8:00可以,周六,周日两天都可以上网。
大师们,帮帮我吧,我感觉不用网管软件实现起来是不是太困难了阿。
#1首先配置NTP服务,让你的路由器时间和北京时间一致。
Router(config)#ntp source gigabitEthernet 0/1指定NTP服务使用哪个端口连接国家授时中心Router(config)#ntp server 210.72.145.44(国家授时中心地址)Router(config)#ntp update-calendar让国家授时中心提供的日期时间更新你的路由器电池供电的电子表时间这样你的路由器时间就很准确了。
#2配置时间序列,基于时间的访问列表。
通过它,可以根据一天中的不同时间或者根据一星期中的不同日期(当然也可以二者结合起来)控制网络数据包的转发,实现上网控制。
Router(config)#time-range time_online(能够上网时间序列)Router(config-time-range)#periodic weekdays 12:00 to 13:00(工作日12点到13点)Router(config-time-range)#periodic weekdays 17:00 to 23:59(工作日17点到00点)Router(config-time-range)#periodic weekdays 00:00 to 08:00(工作日00点到08点)Router(config-time-range)#periodic weekend 00:00 to 23:59(休息日全天)这样就实现了基于北京时间的准确上网时间序列。
#3配置基于北京时间的访问控制列表Router(config)#ip access-list extended net_control(ACL名称)Router(config-ext-nacl)#permit ip any any time-range time_online(刚配好的上网时间序列)Router(config-ext-nacl)#end#4将该ACL应用到要控制上网的内网口,收工。

Cisco6509-VSS配置VSS配置一、在核心交换机65-1上配置VSS(1)将核心交换机65-1 上与65-2 相连的接口TenGigabitEthernet5/4 和TenGigabitEthernet5/5配置为EtherChannel:switch-1(config)#interface range tenGigabitEthernet 5/4 - 5 switch-1(config-if-range)#channel-group 10 mode onswitch-1(config-if-range)#no shutdown% Range command terminated because it failed on TenGigabitEthernet5/4switch-1(config-if-range)#exit(2)配置VSS域名与VSS主机号:switch-1(config)#switch virtual domain 100Domain ID 100 config will take effect onlyafter the exec command 'switch convert mode virtual' is issuedswitch-1(config-vs-domain)#switch 1switch-1(config-vs-domain)#switch 1 priority 200switch-1(config-vs-domain)#switch 1 preemptPlease note that Preempt configuration will make the ACTIVE switch with lower priority to reload forcefully when preempt timer expiresswitch-1(config-vs-domain)#exit说明:配置VSS 的域名为100,范围为1-255,两台交换机必须相同;配置VSS的主机号码为1,必须一台为1,另一台为2;并配置VSS 优先级为200,默认为100,数字越大,优先级越高,便能成为主VSS 交换机。

目录第1章CISCO交换机概述 (6)1.1概述 (6)1.2 Cisco交换机产品介绍 (7)1.2.1低端产品 (7)1.2.2中端产品 (7)1.2.3高端产品 (7)1.2.4单板与华为S8016的对比............................................................... 错误!未定义书签。
第2章Catalyst6000系列 (8)2.1特性表与华为S8016的对比...................................................................... 错误!未定义书签。
2.2接口模块与华为S8016的对比.................................................................. 错误!未定义书签。
第3章多层交换技术 (9)3.1概述 (9)3.2 Catalyst交换机的VLAN交换技术 (11)第4章6509的进一步配置 (18)4.1准备 (18)4.1.1网桥或交换机 (18)4.1.2生成树协议 (18)4.1.3 V L A N (18)4.1.4中继 (19)4.1.5捆绑端口 (19)4.1.6配置 (19)4.2 6509配置实战 (20)4.2.1 Catalyst模式 (20)4.2.2控制台波特率 (21)4.2.3 sc0接口 (21)4.2.4 IP允许表 (21)4.2.5 Reset命令 (22)4.2.6配置文件 (22)4.2.7快速以太网和千兆快速以太网端口的配置 (25)4.2.8生成树协议的使用 (26)4.2.9配置VLAN (26)4.2.10配置动态VLAN (26)4.2.11使用外部路由器路由VLAN (26)关键词:Catalyst 6509;S8016;多层交换(MLS);VLAN;6509配置摘要:第一章CISCO交换机概览”,对于想了解cisco的Catalyst系列交换机知识的可以看看;第二章Catalyst6000系列”,着重简述了6000系列交换机的规格。

关于Cisco 6509/7609 交换机Netflow的配置Netflow 在6500和7209 交换机上配置和路由器上配置有所不同,在公司开发Netflow的应用上,发现现场工程师基本没有配置对,导致流量出不来。
下面列出配置信息;CATOS的配置也的参考该配置1、首先看看Netflow配置是否正常起来:Switch# show mls nde一般看到都是Netflow Data Export disabled 这说明Netflow都没有起来。
参看Cisco 《Configuring NetFlow Data Export》PDf文档,默认是Disabled的2、启动netflowSwitch(config)# mls netflow3、启动netflow 的双向流量Switch(config)# mls flow ip destination-source4、启动NDE发送以及发送版本Switch(config)# mls nde sender [version {5 | 7}]如果只输入mls nde sender系统默认启用的是版本7,如果需要版本5,则mls nde send er version 5,目前版本能配的是5或7,这两个版本WEB均能出现正常的数据。
对于Cisco IOS 12.17以下版本的交换机,只有版本7。
5、进入VLAN,启动接口Netflow(如果在物理接口上其3层,则直接进入物理接口)。
Switch(config)# interface vlan 5Switch(config-if)# ip flow-export ingressSwitch(config-if)# ip route-cache flow6、配置Netflow的数据源,如果没有配置Loopback的接口,可以采用物理接口,建议配置L oopback接口Switch(config)# ip flow-export source loopback 07、检测Switch# show mls nde (能看到如下的信息,而且明确Netflow Data Export enable d )Netflow Data Export enabledExporting flows to 10.110.10.254 (9991)Exporting flows from 10.16.68.72 (55425)Version: 5Include Filter not configuredExclude Filter is:Total Netflow Data Export Packets are:49 packets, 0 no packets, 247 recordsTotal Netflow Data Export Send Errors:IPWRITE_NO_FIB = 0IPWRITE_ADJ_FAILED = 0IPWRITE_PROCESS = 0Switch(config)# show mls netfow ip看到大量的流量信息,大量的滚屏信息。

CISCO 6509配置手册1.设置时间switch#config tswitch(config)# clock timezone GMT 8 ;配置时区switch(config)# clock set 13:30:21 31 JAN 2004 ;配置交换机时间2.设置主机名及密码Switch#congfig tSwitch(config)#hostname 6509a //配置交换机名称6509a(config)#enable password cisco //配置用户密码6509a (config)#enable secret cisco //配置安全密码6509a (config-line)#line vty 0 15 //配置远程访问密码6509a (config-line)#login6509a (config-line)#password cisco6509a (config-line)#login6509a (config-line)#^z6509a #show running-config //查看配置信息6509a #copy running-config startup-config6509a #show startup-config6509a #show bootvar6509a #dir bootflash:6509a #copy system:running-config nvram:startup-config6509a #show fabric status6509a #show hardware3.配置vlan6509a #config t6509a (config)#vlan 3016509a (config-vlan)# name hexinxitong6509a (config)#vlan 3026509a (config-vlan)# name callcenter6509a (config)#vlan 3036509a (config-vlan)# name kuaijicaiwu6509a (config)#vlan 3046509a (config-vlan)# name guojiyewu6509a (config)#vlan 3056509a (config-vlan)# name guanlixitong6509a (config)#vlan 3066509a (config-vlan)# name ceshihuanjing6509a (config)#vlan 3076509a (config-vlan)# name wangluoguanli6509a (config-vlan)#exit6509a (config)#exit6509a #show vlan6509a (config)#interface range giga 2/1 – 8 //配置端口信息6509a (config-if-range)#switchport //二层交换模式6509a (config-if-range)#switchport mode access6509a (config-if-range)#switchport access vlan 3016509a (config-if-range)#exit6509a (config)#interface range giga 2/9– 146509a (config-if-range)#switchport mode access6509a (config-if-range)#switchport access vlan 3026509a (config-if-range)#exit6509a (config)#interface range giga 2/15 – 176509a (config-if-range)#switchport mode access6509a (config-if-range)#switchport access vlan 3036509a (config-if-range)#exit6509a (config)#interface range giga 2/18 – 226509a (config-if-range)#switchport mode access6509a (config-if-range)#switchport access vlan 3046509a (config)#interface range giga 2/23 – 266509a (config-if-range)#switchport mode access6509a (config-if-range)#switchport access vlan 3056509a (config-if-range)#exit6509a (config)#interface range giga 2/27 – 336509a (config-if-range)#switchport mode access6509a (config-if-range)#switchport access vlan 3066509a (config-if-range)#exit6509a (config)#interface range giga 2/34 – 396509a (config-if-range)#switchport mode access6509a (config-if-range)#switchport access vlan 3076509a (config-if-range)#exit6509a (config)#interface giga 2/486509a (config-if)#ip address 12.10.254.2 255.255.255.0 6509a (config-if)#no shut6509a (config)#exit6509a #show vlan4.配置trunk6509a(config)#int giga 5/16509a(config-if)#shut down6509a(config-if)#switchport6509a(config-if)#switchport trunk enca dot1q6509a(config-if)#switchport mode trunk6509a #show int giga 2/48 trunk6509a #show vtp counters6509a #show vtp status6509a(config)#int giga 6/16509a(config-if)#shut down6509a(config-if)#switchport6509a(config-if)#switchport trunk enca dot1q6509a(config-if)#switchport mode trunk6509a(config-if)#no shut down5.设置vlan地址及HSRP6509a #config t6509a(config) #int vlan 3016509a(config-if) #ip address 192.1.2.2 255.255.255.0 6509a(config-if) #no ip redirects6509a(config-if) #standby 1 ip 192.1.2.16509a(config-if) #standby 1 priority 1056509a(config-if) #standby 1 preempt6509a(config-if) #standby 1 track giga 1/486509a(config-if) #no shutdown6509a(config-if) #exit6509a(config) #exit6509a#show ip interface brief6509a #config t6509a(config) #int vlan 3026509a(config-if) #ip address 192.100.4.2 255.255.255.06509a(config-if) #no ip redirects6509a(config-if) #standby 2 ip 192.100.4.16509a(config-if) #standby 2 priority 1056509a(config-if) #standby 2 preempt6509a(config-if) #standby 2 track giga 1/486509a(config-if) #no shutdown6509a(config-if) #exit6509a(config) #exit6509a#show ip interface brief6509a #config t6509a(config) #int vlan 3036509a(config-if) #ip address 192.100.5.2 255.255.255.0 6509a(config-if) #no ip redirects6509a(config-if) #standby 3 ip 192.100.5.16509a(config-if) #standby 3 priority 1056509a(config-if) #standby 3 preempt6509a(config-if) #standby 3 track giga 1/486509a(config-if) #no shutdown6509a(config-if) #exit6509a(config) #exit6509a#show ip interface brief6509a #config t6509a(config) #int vlan 3046509a(config-if) #ip address 192.100.6.2 255.255.255.0 6509a(config-if) #no ip redirects6509a(config-if) #standby 4 ip 192.100.6.16509a(config-if) #standby 4 priority 1056509a(config-if) #standby 4 preempt6509a(config-if) #standby 4 track giga 1/486509a(config-if) #no shutdown6509a(config-if) #exit6509a(config) #exit6509a#show ip interface brief6509a #config t6509a(config) #int vlan 3056509a(config-if) #ip address 192.100.7.2 255.255.255.0 6509a(config-if) #no ip redirects6509a(config-if) #standby 5 ip 192.100.7.16509a(config-if) #standby 5 preempt6509a(config-if) #no shutdown6509a(config-if) #exit6509a(config) #exit6509a#show ip interface brief6509a #config t6509a(config) #int vlan 3066509a(config-if) #ip address 192.100.8.2 255.255.255.0 6509a(config-if) #no ip redirects6509a(config-if) #standby 6 ip 192.100.8.16509a(config-if) #standby 6 preempt6509a(config-if) #no shutdown6509a(config-if) #exit6509a(config) #exit6509a#show ip interface brief6509a #config t6509a(config) #int vlan 3076509a(config-if) #ip address 192.100.9.2 255.255.255.0 6509a(config-if) #no ip redirects6509a(config-if) #standby 7 ip 192.100.9.16509a(config-if) #standby 7 preempt6509a(config-if) #no shutdown6509a(config-if) #exit6509a(config) #exit6509a#show ip interface brief6.配置EIGRP6509a #config t6509a(config) #ip routing eigrp 1006509a(config) #router eigrp 1006509a(config-router) #network 192.1.2.06509a(config-router) #network 192.100.0 .0 255.255.0.0 6509a(config-router) #network 12.0.0.06509a(config-router) #network 192.254.253.06509a(config-router) #no auto-summary6509a(config-router) #^z6509a #show ip proto6509a #show ip route。

清除vlanzhaozhou-6006 (enable) clear vlan 400This command will deactivate all ports on vlan 400in the entire management domainDo you want to continue(y/n) [n]?yVlan 400 deletedzhaozhou-6006 (enable)保存配置zhaozhou-6006 (enable) copy config 2Upload configuration to bootflash:211395136 bytes available on device bootflash, proceed (y/n) [n]? y.................................................Configuration has been copied successfully.zhaozhou-6006 (enable) sh flash-#- ED --type-- --crc--- -seek-- nlen -length- -----date/time------ name1 .. ffffffff 671e2eaa 49e1e4 25 4579681 Dec 02 1999 19:44:41 cat6000-sup.5-3-2-CSX.bin2 .. ffffffff 8bce2df9 4a1f40 6 15578 Oct 22 2001 17:54:41 zz60063 .. ffffffff bbf1e548 4a7c94 1 23762 Apr 05 2006 10:19:22 211371372 bytes available (4619412 bytes used)zhaozhou-6006 (enable) copy config flashFlash device [bootflash]?Name of copy to []? dqtvnet2006Upload configuration to bootflash:dqtvnet200611371244 bytes available on device bootflash, proceed (y/n) [n]? y.................................................Configuration has been copied successfully.zhaozhou-6006 (enable)删除带有名字的vlanzhaozhou-6006 (enable) copy config 2Upload configuration to bootflash:211395136 bytes available on device bootflash, proceed (y/n) [n]? y.................................................Configuration has been copied successfully.zhaozhou-6006 (enable) sh flash-#- ED --type-- --crc--- -seek-- nlen -length- -----date/time------ name1 .. ffffffff 671e2eaa 49e1e4 25 4579681 Dec 02 1999 19:44:41 cat6000-sup.5-3-2-CSX.bin2 .. ffffffff 8bce2df9 4a1f40 6 15578 Oct 22 2001 17:54:41 zz60063 .. ffffffff bbf1e548 4a7c94 1 23762 Apr 05 2006 10:19:22 211371372 bytes available (4619412 bytes used)zhaozhou-6006 (enable) copy config flashFlash device [bootflash]?Name of copy to []? dqtvnet2006Upload configuration to bootflash:dqtvnet200611371244 bytes available on device bootflash, proceed (y/n) [n]? y.................................................Configuration has been copied successfully.zhaozhou-6006 (enable)查看端口命令zhaozhou-6006 (enable) sh intsl0: flags=51<UP,POINTOPOINT,RUNNING>slip 0.0.0.0 dest 0.0.0.0sc0: flags=63<UP,BROADCAST,RUNNING>vlan 100 inet 221.209.150.82 netmask 255.255.255.248 broadcast 221.209.150.87 zhaozhou-6006 (enable)通过命令设置多个端口vlanzhaozhou-6006 (enable) set vlan 1 2/1-48VLAN 1 modified.VLAN 100 modified.VLAN Mod/Ports---- -----------------------1 2/1-485/1-48zhaozhou-6006 (enable)vtp清除#vtpset vtp domain zxstkset vtp mode serverset vtp v2 disableset vtp pruning disableset vtp pruneeligible 2-1000clear vtp pruneeligible 1001-1005set vlan 1 name default type ethernet mtu 1500 said 100001 state activeset vlan 1002 name fddi-default type fddi mtu 1500 said 101002 state activeset vlan 1004 name fddinet-default type fddinet mtu 1500 said 101004 state active bridge 0x0 stp ieeeset vlan 1005 name trnet-default type trbrf mtu 1500 said 101005 state active bridge 0x0 stp ibm set vlan 1003 name token-ring-default type trcrf mtu 1500 said 101003 state active parent 0 ring 0x0 mode srb aremaxhop 0 stemaxhop 0!#ipset interface sc0 100 221.209.150.82/255.255.255.248 221.209.150.87set interface sc0 upzhaozhou-6006 (enable) clear vtp domain zxstkUsage: clear vtp statisticsclear vtp pruneeligible <vlans..>(vlans: 1..1005An example of vlans is 2-10,1005)zhaozhou-6006 (enable) clear vtp pruneeligible 2-1000Vlans 1-1005 will not be pruned on this device.VTP domain zxstk modified.zhaozhou-6006 (enable)设置vtp模式透明zhaozhou-6006 (enable) set vtp mode ?Usage: set vtp [domain <name>] [mode <mode>] [passwd <passwd>][pruning <enable|disable>] [v2 <enable|disable>(mode = client|server|transparentUse passwd '0' to clear vtp password)Usage: set vtp pruneeligible <vlans>(vlans = 2..1000An example of vlans is 2-10,1000)zhaozhou-6006 (enable) set vtp mode transparentVTP domain zxstk modifiedzhaozhou-6006 (enable)设置端口汇聚zhaozhou-6006 (enable) set trunk ?Usage: set trunk <mod_num/port_num> [on|off|desirable|auto|nonegotiate] [vlans] [trunk_type] (vlans = 1..1005An example of vlans is 2-10,1005)(trunk_type = isl,dot1q,dot10,lane,negotiate)zhaozhou-6006 (enable) set trunk 2/3 on 1-400Adding vlans 1-400 to allowed list.Please use the 'clear trunk' command to remove vlans from allowed list.Port(s) 2/3 allowed vlans modified to 1-1005.Failed to set port 2/3 to trunk mode on.Trunk mode 'on' not allowed with trunk encapsulation type 'negotiate'.zhaozhou-6006 (enable) set trunk 2/3 on 1-400 dot1qAdding vlans 1-400 to allowed list.Please use the 'clear trunk' command to remove vlans from allowed list.Port(s) 2/3 allowed vlans modified to 1-1005.Port(s) 2/3 trunk mode set to on.Port(s) 2/3 trunk type set to dot1q.zhaozhou-6006 (enable)。
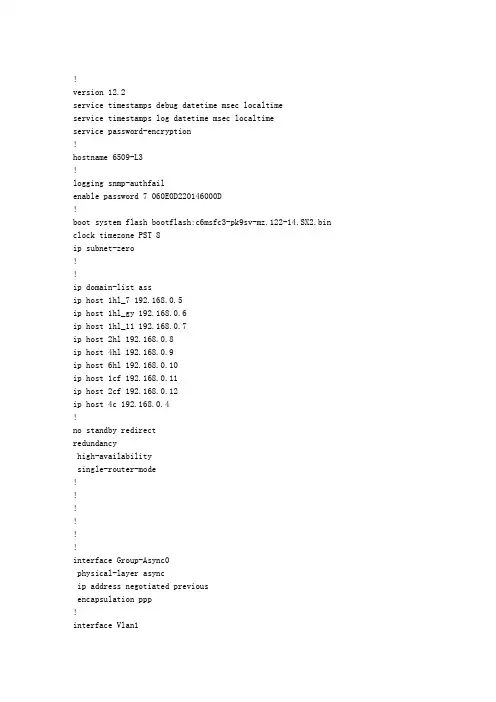
!version 12.2service timestamps debug datetime msec localtimeservice timestamps log datetime msec localtimeservice password-encryption!hostname 6509-L3!logging snmp-authfailenable password 7 060E0D220146000D!boot system flash bootflash:c6msfc3-pk9sv-mz.122-14.SX2.bin clock timezone PST 8ip subnet-zero!!ip domain-list assip host 1hl_7 192.168.0.5ip host 1hl_gy 192.168.0.6ip host 1hl_11 192.168.0.7ip host 2hl 192.168.0.8ip host 4hl 192.168.0.9ip host 6hl 192.168.0.10ip host 1cf 192.168.0.11ip host 2cf 192.168.0.12ip host 4c 192.168.0.4!no standby redirectredundancyhigh-availabilitysingle-router-mode!!!!!!interface Group-Async0physical-layer asyncip address negotiated previousencapsulation ppp!interface Vlan1ip address 192.168.0.1 255.255.255.0ip access-group tofirewall out!interface Vlan10ip address 192.168.41.1 255.255.255.0!interface Vlan20ip address 192.168.42.1 255.255.255.0!interface Vlan30ip address 172.16.9.1 255.255.255.0!interface Vlan40ip address 172.16.10.1 255.255.255.0ip access-group invlan40 inip access-group outvlan40 out!interface Vlan50ip address 172.16.11.1 255.255.255.0ip access-group invlan50 inip access-group outvlan50 out!interface Vlan60ip address 172.16.0.1 255.255.255.0!interface Vlan70ip address 172.16.1.1 255.255.255.0!interface Vlan80ip address 172.16.2.1 255.255.255.0!interface Vlan90ip address 172.16.3.1 255.255.255.0!interface Vlan100ip address 172.16.4.1 255.255.255.0!interface Vlan110ip address 172.16.5.1 255.255.255.0!interface Vlan120ip address 172.16.7.1 255.255.254.0 secondary ip address 172.16.6.1 255.255.254.0no ip redirects!interface Vlan130ip address 172.16.12.1 255.255.254.0ip access-group inbound inip access-group outbound out!interface Vlan140ip address 172.16.8.1 255.255.255.0!interface Vlan150ip address 172.16.16.1 255.255.255.252!router ripversion 2network 172.16.0.0network 192.168.0.0!ip classlessip route 0.0.0.0 0.0.0.0 192.168.0.236ip route 10.0.0.0 255.0.0.0 192.168.0.100ip route 172.16.17.0 255.255.255.0 172.16.16.2ip route 192.168.1.0 255.255.255.0 172.16.1.65ip route 220.201.208.112 255.255.255.252 172.16.16.2ip http server!!ip access-list extended inboundpermit ip any any reflect iptrafficip access-list extended invlan40permit ip host 172.16.10.168 any reflect iptrafficpermit ip any host 192.168.0.244 reflect iptrafficpermit ip any host 192.168.0.53 reflect iptrafficpermit ip any host 192.168.0.254 reflect iptrafficpermit ip any host 172.16.8.110 reflect iptrafficpermit ip host 172.16.10.82 any reflect iptrafficpermit ip host 172.16.10.117 any reflect iptrafficpermit ip any host 172.16.8.52 reflect iptrafficpermit tcp host 172.16.10.70 any eq domain reflect iptraffic permit tcp host 172.16.10.70 any eq pop3 reflect iptraffic permit tcp host 172.16.10.70 any eq smtp reflect iptraffic permit udp host 172.16.10.70 any eq domain reflect iptraffic permit ip any host 172.16.8.50 reflect iptrafficpermit ip any host 192.168.0.110 reflect iptrafficpermit ip any host 172.16.8.94 reflect iptrafficevaluate iptrafficip access-list extended invlan50permit ip any any reflect iptrafficip access-list extended outboundpermit ip host 192.168.0.3 anypermit ip host 172.16.1.65 anypermit ip any host 172.16.13.253permit ip any host 172.16.13.252permit ip any host 172.16.12.9permit ip host 172.16.8.52 anypermit ip host 192.168.0.247 host 172.16.12.52 permit ip host 172.16.8.50 anypermit ip host 192.168.0.110 anypermit ip host 172.16.8.94 anyevaluate iptrafficip access-list extended outvlan40permit ip any host 172.16.10.168permit ip host 192.168.0.237 anypermit ip any host 172.16.10.117permit ip host 172.16.8.52 anypermit tcp any host 172.16.10.70 eq domainpermit tcp any host 172.16.10.70 eq pop3permit tcp any host 172.16.10.70 eq smtppermit udp any host 172.16.10.70 eq domainpermit ip host 172.16.8.50 anypermit ip host 192.168.0.110 anypermit ip host 172.16.4.105 host 172.16.10.82 permit ip host 172.16.11.160 host 172.16.10.82 permit ip host 172.16.8.94 anyevaluate iptrafficip access-list extended outvlan50permit ip host 192.168.0.108 anypermit ip host 172.16.1.60 host 172.16.11.52 permit ip host 172.16.1.60 host 172.16.11.53 permit ip host 172.16.1.61 host 172.16.11.52 permit ip host 172.16.1.61 host 172.16.11.53 permit ip host 172.16.6.230 anypermit ip host 172.16.6.231 anypermit ip host 192.168.0.237 anypermit ip host 10.0.1.147 host 172.16.11.52permit ip host 10.0.1.147 host 172.16.11.53permit ip host 10.0.1.147 host 172.16.11.72permit ip host 172.16.6.171 host 172.16.11.52 permit ip host 172.16.6.171 host 172.16.11.53permit ip host 172.16.6.183 host 172.16.11.52 permit ip host 172.16.6.183 host 172.16.11.53 permit ip host 172.16.6.183 host 172.16.11.72 permit ip host 172.16.4.190 host 172.16.11.52 permit ip host 172.16.4.190 host 172.16.11.53 permit ip host 172.16.3.57 host 172.16.11.52 permit ip host 172.16.3.57 host 172.16.11.53 permit ip host 172.16.3.57 host 172.16.11.72 permit ip host 172.16.3.64 host 172.16.11.52 permit ip host 172.16.3.64 host 172.16.11.53 permit ip host 172.16.3.64 host 172.16.11.72 permit ip host 172.16.3.101 host 172.16.11.52 permit ip host 172.16.3.101 host 172.16.11.53 permit ip host 172.16.3.101 host 172.16.11.72 permit ip host 172.16.2.185 host 172.16.11.52 permit ip host 172.16.2.185 host 172.16.11.53 permit ip host 172.16.2.185 host 172.16.11.72 permit ip host 172.16.2.196 host 172.16.11.53 permit ip host 172.16.2.196 host 172.16.11.52 permit ip host 172.16.2.196 host 172.16.11.72 permit ip host 172.16.2.245 host 172.16.11.52 permit ip host 172.16.2.245 host 172.16.11.53 permit ip host 172.16.2.245 host 172.16.11.72 permit ip host 172.16.2.81 host 172.16.11.52 permit ip host 172.16.2.81 host 172.16.11.53 permit ip host 172.16.2.81 host 172.16.11.72 permit ip host 172.16.2.96 host 172.16.11.52 permit ip host 172.16.2.96 host 172.16.11.53 permit ip host 172.16.2.96 host 172.16.11.72 permit ip host 172.16.2.94 host 172.16.11.52 permit ip host 172.16.2.94 host 172.16.11.53 permit ip host 172.16.2.94 host 172.16.11.72 permit ip host 172.16.2.151 host 172.16.11.52 permit ip host 172.16.2.151 host 172.16.11.53 permit ip host 172.16.2.151 host 172.16.11.72 permit ip host 10.0.1.27 host 172.16.11.72permit ip host 10.0.1.27 host 172.16.11.53permit ip host 10.0.1.27 host 172.16.11.52permit ip host 172.16.4.55 host 172.16.11.52 permit ip host 172.16.4.55 host 172.16.11.53 permit ip host 172.16.4.55 host 172.16.11.72 permit ip host 172.16.4.190 host 172.16.11.121 permit ip host 172.16.4.190 host 172.16.11.250permit ip host 172.16.3.101 host 172.16.11.250 permit ip host 172.16.3.57 host 172.16.11.250 permit ip host 172.16.3.101 host 172.16.11.121 permit ip host 172.16.3.57 host 172.16.11.121 permit ip host 172.16.1.61 host 172.16.11.250 permit ip host 172.16.8.75 host 172.16.11.52 permit ip host 172.16.8.77 host 172.16.11.52 permit ip host 172.16.8.73 host 172.16.11.52 permit ip host 172.16.8.80 host 172.16.11.52 permit ip host 172.16.8.75 host 172.16.11.53 permit ip host 172.16.8.77 host 172.16.11.53 permit ip host 172.16.8.73 host 172.16.11.53 permit ip host 172.16.8.80 host 172.16.11.53 permit ip host 172.16.8.75 host 172.16.11.72 permit ip host 172.16.8.77 host 172.16.11.72 permit ip host 172.16.8.80 host 172.16.11.72 permit ip host 172.16.8.73 host 172.16.11.72 permit ip host 172.16.8.75 host 172.16.11.121 permit ip host 172.16.8.77 host 172.16.11.121 permit ip host 172.16.8.73 host 172.16.11.121 permit ip host 172.16.8.80 host 172.16.11.121 permit ip host 172.16.8.75 host 172.16.11.250 permit ip host 172.16.8.77 host 172.16.11.250 permit ip host 172.16.8.73 host 172.16.11.250 permit ip host 172.16.8.80 host 172.16.11.250 permit ip host 172.16.1.61 host 172.16.11.121 permit ip host 172.16.7.108 host 172.16.11.250 permit ip host 172.16.7.108 host 172.16.11.52 permit ip host 172.16.7.108 host 172.16.11.53 permit ip host 172.16.7.108 host 172.16.11.72 permit ip host 172.16.7.114 host 172.16.11.121 permit ip host 172.16.7.114 host 172.16.11.52 permit ip host 172.16.7.114 host 172.16.11.53 permit ip host 172.16.7.114 host 172.16.11.72 permit ip host 172.16.7.117 host 172.16.11.72 permit ip host 172.16.7.117 host 172.16.11.52 permit ip host 172.16.7.117 host 172.16.11.53 permit ip host 172.16.7.114 host 172.16.11.250 permit ip host 172.16.7.117 host 172.16.11.250 permit ip host 172.16.8.50 anypermit ip host 10.0.1.147 host 172.16.11.250 permit ip host 10.0.1.27 host 172.16.11.250permit ip host 10.0.1.147 host 172.16.11.121permit ip host 10.0.1.27 host 172.16.11.121permit ip host 192.168.0.110 anypermit tcp host 192.168.0.254 any eq ftppermit ip host 172.16.7.121 host 172.16.11.250 permit ip host 172.16.7.121 host 172.16.11.121 permit ip host 172.16.7.121 host 172.16.11.52 permit ip host 172.16.7.121 host 172.16.11.53 evaluate iptrafficip access-list extended tofirewallpermit tcp any host 192.168.0.110deny tcp any any eq echodeny tcp any any eq 139deny tcp any any eq 445deny tcp any any eq 135permit ip any any!logging 192.168.0.2access-list 11 permit 192.168.0.108access-list 11 permit 192.168.0.110access-list 11 permit 192.168.0.2access-list 11 permit 192.168.0.3access-list 11 permit 192.168.0.235access-list 11 permit 192.168.0.237access-list 11 permit 172.16.8.50arp 192.168.42.67 0014.224a.ea63 ARPAarp 172.16.7.185 000a.ebd9.7f33 ARPAarp 192.168.42.65 0010.dcd4.e74b ARPAarp 192.168.0.108 000d.61e8.a430 ARPAarp 192.168.42.71 0010.dcd4.dc0c ARPAarp 192.168.42.69 0010.dcce.e735 ARPAarp 192.168.42.75 0010.dcd4.7d3e ARPAarp 192.168.42.73 0005.5dd4.059b ARPAarp 192.168.0.101 000b.dbb7.9da4 ARPAarp 192.168.42.79 0010.dcd4.76d6 ARPAarp 192.168.0.102 000b.dbb8.4e25 ARPAarp 192.168.0.103 0016.7626.3c29 ARPAarp 192.168.42.77 000b.dbb8.cea5 ARPAarp 172.16.1.168 000d.6193.9c92 ARPAarp 172.16.7.172 0011.11a8.ab15 ARPAarp 172.16.2.164 000b.dbbb.00fa ARPAarp 172.16.2.162 0013.20d9.d0cb ARPAarp 192.168.42.95 0050.ba4f.9d8d ARPAarp 172.16.10.168 000d.61e8.3b66 ARPAarp 192.168.42.93 0011.110d.4cca ARPAarp 172.16.4.149 00e0.4cea.fab7 ARPA arp 172.16.2.254 0050.fc3a.8977 ARPA arp 172.16.5.254 0006.1bd0.b94c ARPA arp 171.16.2.254 0050.fc3a.8977 ARPA arp 172.16.8.253 0014.2246.4c96 ARPA arp 172.16.11.253 000b.dbb9.6520 ARPA arp 172.16.10.253 000d.61e8.a3ce ARPA arp 172.16.6.237 0011.110d.4de2 ARPA arp 172.16.11.208 1111.1111.1111 ARPA arp 172.16.7.209 0010.b54d.7b6c ARPA arp 172.16.7.208 000b.dbbb.00de ARPA arp 192.168.42.50 0005.5dd4.0704 ARPA arp 192.168.42.51 000a.e423.e9dd ARPA arp 172.16.7.200 0013.d303.28b1 ARPA arp 192.168.42.54 000b.dbbb.0e3b ARPA arp 192.168.42.52 000a.e43c.003a ARPA arp 192.168.42.53 000a.e423.ed2c ARPA arp 192.168.42.59 0010.dcd4.e951 ARPA arp 192.168.42.56 000b.dbb8.c8fb ARPA arp 172.16.7.199 0013.d324.c03a ARPA arp 172.16.4.56 0015.f240.edb7 ARPA arp 172.16.5.56 000c.f1ea.a554 ARPA arp 172.16.0.62 0010.dcd4.6eed ARPA arp 172.16.5.58 0011.11b7.1153 ARPA arp 172.16.0.56 000d.8740.7abf ARPA arp 172.16.2.58 0005.5dd4.0674 ARPA arp 172.16.11.50 0005.5d26.3229 ARPA arp 192.168.0.237 000b.dbb9.1131 ARPA arp 172.16.4.62 0014.2246.4bd2 ARPA arp 172.16.1.58 000f.1f5d.8b43 ARPA arp 172.16.3.56 0005.5d26.3461 ARPA arp 172.16.9.50 5254.ab14.6e7a ARPA arp 172.16.5.51 0060.6702.f70d ARPA arp 172.16.7.55 0010.c6cf.4a25 ARPA arp 172.16.4.52 0060.6706.a32c ARPA arp 172.16.3.51 0011.110d.4d16 ARPA arp 192.168.0.253 0010.5ce3.baab ARPA arp 192.168.0.254 000c.766e.ff8a ARPA arp 192.168.42.231 0013.20ac.53ed ARPA arp 192.168.42.228 0013.20d3.f9ad ARPA arp 172.16.6.23 0020.ed83.0c04 ARPA arp 172.16.6.10 0010.5cc5.811d ARPA arp 172.16.2.11 de ARPAarp 172.16.9.126 00e0.4c61.14d7 ARPAarp 172.16.2.110 0013.20d3.7d21 ARPAarp 172.16.4.107 0015.5809.c9ee ARPAarp 172.16.2.104 0011.110d.a157 ARPAarp 172.16.3.104 0010.5ce3.b37c ARPAarp 172.16.3.103 0013.20d9.cee8 ARPAarp 172.16.0.97 0013.20d9.ced5 ARPAarp 172.16.0.93 0010.b500.0657 ARPAarp 172.16.2.95 0020.ed3b.c492 ARPAarp 172.16.4.91 0015.f240.edb0 ARPAarp 172.16.10.82 0010.b54d.73e4 ARPAarp 172.16.4.93 000f.1f9e.aba3 ARPAarp 172.16.7.87 0014.2a31.7b60 ARPAarp 172.16.2.82 0010.b54d.7b6a ARPAarp 172.16.7.86 0014.2a35.ba95 ARPAarp 172.16.0.77 0010.dcd4.7d10 ARPAarp 172.16.5.75 000c.7680.fb56 ARPAarp 172.16.0.79 5254.ab14.769d ARPAarp 172.16.8.64 000b.dbb9.15c2 ARPAarp 172.16.5.77 0011.0911.bffd ARPAarp 172.16.8.65 000d.61e8.b0c1 ARPAarp 172.16.0.73 00d0.b76c.9893 ARPAarp 172.16.5.79 0010.dc48.ff46 ARPAarp 172.16.5.65 0013.20d9.cd7c ARPAarp 172.16.1.70 0020.ed15.91aa ARPAarp 172.16.7.70 000a.eb6a.0403 ARPAarp 172.16.0.66 0010.dcd4.76e3 ARPA!snmp-server community public ROsnmp-server community private RWsnmp-server chassis-idsnmp-server enable traps snmp authentication linkdown linkup coldstart warmstart snmp-server enable traps ttysnmp-server enable traps flash insertion removalsnmp-server enable traps hsrpsnmp-server enable traps configsnmp-server enable traps entitysnmp-server enable traps fru-ctrlsnmp-server enable traps bgpsnmp-server enable traps pim neighbor-change rp-mapping-change invalid-pim-message snmp-server enable traps ipmulticastsnmp-server enable traps msdpsnmp-server enable traps rsvpsnmp-server enable traps frame-relaysnmp-server enable traps rtrsnmp-server enable traps isakmp policy add snmp-server enable traps isakmp policy delete snmp-server enable traps isakmp tunnel start snmp-server enable traps isakmp tunnel stop snmp-server enable traps ipsec cryptomap add snmp-server enable traps ipsec cryptomap delete snmp-server enable traps ipsec cryptomap attach snmp-server enable traps ipsec cryptomap detach snmp-server enable traps ipsec tunnel start snmp-server enable traps ipsec tunnel stop snmp-server enable traps ipsec too-many-sas snmp-server enable traps isdn call-information snmp-server enable traps isdn layer2snmp-server enable traps isdn chan-not-avail snmp-server enable traps isdn ietfsnmp-server enable traps dlswsnmp-server host 192.168.0.2 privatesnmp-server host 192.168.0.2 public!tftp-server 192.168.0.3!line con 0exec-timeout 5 30password 7 141F1008410C233Flogging synchronousloginline vty 0 4access-class 11 inpassword 7 011B040716030F1Blogin!exception dump 192.168.0.3end。


Catalyst 6509 交换机安装手册version 1.0.0金中信息产业有限公司系统工程部2001.2.5目录1产品概述 (3)2系统描述 (4)2.1 系统特征 (4)2.1.1冗余 (4)2.1.2组件热插拔 (5)2.2 交换组件 (5)2.2.1配置选项 (5)2.2.2风扇 (5)2.2.3电源 (6)3安装 (7)1 产品概述●支持带有两个上行链路千兆端口的监控引擎;●支持MSFC及PFC;●支持可选的冗余监控引擎(带两个千兆上行链路接口);●最多支持八个附加的模块(以太网、快速以太网、千兆以太网及ATM);●支持多层交换模块(MSM);●所有的模块都可以热插拔;●支持冗余的、热插拔的AC(交流)电源或DC(直流)电源;●风扇可热插拔;●数据在背板总线上进行转发。
6509的底盘有9个插槽,插槽1保留给监控引擎使用,监控引擎提供交换、本地及远程管理、多个千兆上行链路端口功能。
插槽2可以插入一个附加的冗余监控引擎,如果第一个监控引擎失效,则这个监控引擎可以扮演备份的角色。
如果不需要冗余监控引擎,这个插槽就可以插入其它的模块。
其外形图如下:2 系统描述注:下面的描述适合所有的6000系列,除非有特殊的说明。
2.1 系统特征这个章节描述了6000系列交换机的硬件特征。
对于软件的描述,请参考the Catalyst 6000 Family Software Configuration Guide。
对于模块的描述及安装过程,请参考the Catalyst 6000 Family Module Installation Guide。
2.1.1 冗余6000系列交换机有下列特征:●底盘可放入两个热插拔的监控引擎;●底盘可放入两个冗余的、热插拔的交流或直流并进行负载共享的电源;●风扇是可热插拔的;●底板上的时钟模块是冗余的。
2.1.2 组件热插拔所有的模块(包括监控引擎,如果系统有冗余的监控引擎的话),风扇,电源,都支持热插拔,因此可以在不中断系统或使软件或接口shutdown的情况下对模块进行增加、替换、移动。
3.4.2.2. 远程telnet连接5.当完成交换机配置,并起给交换机配置了管理地址,就可以直接采用远程telnet 登陆进入交换机了,但是必须先配置line vty的密码和enable密码才能允许远程登陆。
6.配置telnet登陆命令如下:7.#conf t8.#line vty 0 49.#login ;控制vty接口是否能够telnet10.#password switch11.3. 基本信息配置12.3.1. 交换机软件版本13.Cisco的65xx交换机支持两种版本的系统软件,分别称为Natvie IOS版本和Cat OS版本的系统软件,CatOS版本的软件是为了兼容之前的65xx系列交换机的命令而沿袭下来的。
Native IOS版本软件是Cisco公司为了统一其交换机及路由器的软件风格而研发出来的新一代IOS系统软件,Cisco所有的交换机版本都在整体向Native IOS版本过渡,目前来说,Native IOS版本的软件功能和CatOS 版本的软件功能相差不多,但是今后都会向Native IOS版本软件。
14.本项目中所使用的6509交换机采用的是Native IOS版本。
15.3.2. 查看交换机基本配置16.show version ;查看系统版本,内存配置,寄存器等基本信息17.show module all ;查看交换机配置模块18.show catalyst6000 chassis-mac-address ;查看交换机MAC地址19.#show version输出信息如下:20.Cisco Internetwork Operating System Software21.IOS (tm) s72033_rp Software (s72033_rp-PK9S-M), Version 12.2(17a)SX1, EARLY22.DEPLOYMENT RELEASE SOFTWARE (fc1)23.TAC Support: /tac24.Copyright (c) 1986-2003 by cisco Systems, Inc.piled Wed 29-Oct-03 08:16 by cmong26.Image text-base: 0x40008FBC, data-base: 0x41E5000027.28.ROM: System Bootstrap, Version 12.2(14r)S9, RELEASE SOFTWARE (fc1)29.BOOTLDR: s72033_rp Software (s72033_rp-PK9S-M), Version 12.2(17a)SX1, EARLY30.DEPLOYMENT RELEASE SOFTWARE (fc1)31.32.Router uptime is 29 minutes33.Time since Router switched to active is 29 minutes34.System returned to ROM by power-on (SP by power-on)35.System restarted at 12:57:08 PST Sat Jan 31 200436.System image file is "sup-bootflash:s72033-pk9s-mz.122-17a.SX1.bin"37.38.39.This product contains cryptographic features and is subject to United40.States and local country laws governing import, export, transfer ande. Delivery of Cisco cryptographic products does not imply42.third-party authority to import, export, distribute or use encryption.43.Importers, exporters, distributors and users are responsible forpliance with U.S. and local country laws. By using this product you45.agree to comply with applicable laws and regulations. If you are unable46.to comply with U.S. and local laws, return this product immediately.47.48.A summary of U.S. laws governing Cisco cryptographic products may be found49.at:50./wwl/export/crypto/tool/stqrg.html51.52.If you require further assistance please contact us by sending email to53.export@.54.55.cisco WS-C6509 (R7000) processor (revision 3.0) with 458752K/65536K bytes of56.memory.57.Processor board ID SAL0743NKW858.SR71000 CPU at 600Mhz, Implementation 0x504, Rev 1.2, 512KB L2 Cachest reset from power-on60.X.25 software, Version 3.0.0.61.Bridging software.62.1 Virtual Ethernet/IEEE 802.3 interface(s)63.48 FastEthernet/IEEE 802.3 interface(s)64.36 Gigabit Ethernet/IEEE 802.3 interface(s)65.1917K bytes of non-volatile configuration memory.66.8192K bytes of packet buffer memory.67.65536K bytes of Flash internal SIMM (Sector size 512K).68.Standby is up69.Standby has 458752K/65536K bytes of memory.70.71.Configuration register is 0x210272.73.Router#sho module all74.Mod Ports Card Type Model Serial75.No.76.--- ----- -------------------------------------- ------------------ -----------77.2 16 16 port 1000mb GBIC78.ethernet WS-X6416-GBIC SAL0750QNJP79.3 16 16 port 1000mb GBIC80.ethernet WS-X6416-GBIC SAL0750QNFV81.5 2 Supervisor Engine 72082.(Active) WS-SUP720-BASE SAD075000YF83.6 2 Supervisor Engine 72084.(Warm) WS-SUP720-BASE SAD075109SZ85.7 48 48 port 10/100 mb86.RJ45 WS-X6348-RJ-45 SAL0752R3E687.88.Mod MAC89.addresses Hw Fw Sw Status90.--- ---------------------------------- ------ ------------ ------------ -------91.2 000e.8442.4850 to 000e.8442.485f 2.5 5.4(2) 8.2(0.56)TET Ok92.3 000e.8442.48f0 to 000e.8442.48ff 2.5 5.4(2) 8.2(0.56)TET Ok93.5 000d.290f.fd08 to 000d.290f.fd0b 3.0 7.7(1) 12.2(17a)SX1 Ok94.6 000e.3838.1a8c to 000e.3838.1a8f 3.0 7.7(1) 12.2(17a)SX1 Ok95.7 000e.84c8.54f0 to 000e.84c8.551f 6.8 5.4(2) 8.2(0.56)TET Ok96.97.Mod98.Sub-Module Model Serial Hw Statu99.s100.--- --------------------------- ------------------ ------------ ------- ------- 101.5 Policy Feature Card 3 WS-F6K-PFC3A SAD0752009D 2.0 Ok 102.5 MSFC3 Daughterboard WS-SUP720 SAD075109HX 2.0 Ok 103.6 Policy Feature Card 3 WS-F6K-PFC3A SAD0751085J 2.0 Ok104.6 MSFC3 Daughterboard WS-SUP720 SAD0751077C 2.0 Ok105.7 Inline Power Module WS-F6K-PWR 0.0 Ok106.107.Mod Online Diag Status108.--- -------------------109.2 Pass110.3 Pass111.5 Pass112.6 Pass113.7 Pass114.3.3. 配置机器名、telnet、密码115.在全局模式下,用conf t,进入配置模式,进行以下配置:116.#conf t117.#clock timezone GMT 8 ;配置时区118.#clock set 13:30:21 31 JAN 2004 ;配置交换机时间119.#clock calendar-valid ;使能硬件时钟同步120.#service timestamps debug datetime localtime ;配置系统debug记录时间格式121.#service timestamps log datetime localtime ;配置系统日志记录时间格式122.#service password-encryption ;配置使用加密服务,主要针对口令加密123.#hostname xxxx ;配置交换机名称124.#enable secret 0 xxxxx ;配置enable口令125.#copy run start ;将配置信息保存到NVRAM中,重启动不会丢失126.#line vty 0 4 ;配置telnet127.#exec-timeout 30 0128.#password 0 xxxx129.#login130.3.4. 配置snmp131.#conf t132.#snmp-server community cisco ro(只读);配置只读通信字符串133.#snmp-server community secret rw(读写);配置读写通信字符串134.#snmp-server enable traps ;配置网关SNMP TRAP135.#snmp-server host 10.254.190.1 rw ;配置网关工作站地址136.137.3.5. 启动三层功能138.#ip routing ;启动路由功能139.3.6. 查看和配置系统环境变量140.使用show bootvar命令查看系统启动环境变量,包括BOOT, BOOTLDR, and 141.CONFIG_FILE参数:142.Router# show bootvar143.BOOT variable = slot0:c6sup22-jsv-mz.121-5c.EX.bin,1;144.CONFIG_FILE variable does not exist145.BOOTLDR variable = bootflash:c6msfc2-boot-mz.121-3a.E4146.Configuration register is 0x2147.Router#148.改变BOOT,、BOOTLDR、CONFIG_FILE 这三个环境变量使用命令:149.BOOT #boot system150.BOOTLDR #boot bootldr151.CONFIG_FILE #boot config152.153.共5页: 上一页[1] 2 [3] [4] [5] 下一页154.155.156.157.65xx系列交换机配置(Native IOS)(3)158.发布时间:2004-06-17 浏览次数:159.160.161.162.4. 端口设置163.4.1. 端口基本设置164.Cisco 65xx系列交换机的端口缺省都是路由模式,一般都会配置为交换端口使用,进入端口配置模式:165.对于单一端口,在配置模式下输入:interface Ethernet,Fast Ethernet,Gigabit 166.Ethernet x/y, x为槽位号,y为端口号。

一、拓扑二、IOS升级(由于新6509两块引擎ios版本不一致)1.升级的目的由于6509两块引擎版本不一致,无法配置引擎冗余,需升级另一块引擎ios,两块引擎ios版本一致,才可做sso2.升级前确认首先查看两块引擎板卡ios版本分别为:s72033-ipbase-mz.122-33.SXI7;s72033-ipservices_wan-vz.122-33.SXI7然后分别备份两块板卡引擎ios。
两块板卡引擎升级后同为s72033-ipservices_wan-vz.122-33.SXI7版本。
3.升级步骤上传s72033-ipservices_wan-vz.122-33.SXI7至主引擎,指定交换机从新的ios文件引导启动(boot system flash sup-bootdisk: s72033-ipservices_wan-vz.122-33.SXI7)no boot system flash sup-bootdisk:s72033-ipbase-mz.122-33.SXI(取消旧的ios启动项)boot system flash sup-bootdisk:s72033-ipservices_wan-vz.122-33.SXI7(设置新的ios为启动项)show run | begin boot 会显示启动项如若show boot 显示ios 启动参数为empty,此时reload4.升级后检验配置冗余强制切换Redundancy force-switcher5. 设备状态检查Show module ;show switch virtual等三、基础配置1.port-channel配置:6509-720(config)#interface range gigabitEthernet 7/1 – 26509-720(config-if)#switchport6509-720(config-if)switchport trunk encapsulation dot1q6509-720(config-if)switchport mode trunk6509-720(config-if)channel-group 3 mode on6509-720(config)#interface port-channel 36509-720(config-if)#switchport trunk encapsulation dot1q6509-720(config-if)#switchport mode trunk另一台6509port-channel配置如上一样。
cisco 6509交换机配置手册一个经典配置包括Catalyst6509 4006交换机配置方案拓扑图如下:一、 Catalyst 6509交换机配置方案1.1 、配置 6509 二层交换Console> (enable) set system name bg-sw-01 /设备名称Bg-sw-01> (enable) set passwordEnter old password:Enter new password: test/ 设备口令Retype new password: testBg-sw-01> (enable) set enablepassEnter old password:Enter new password: test/ 设备口令Retype new password: testBg-sw-01> (enable) set banner motd % Welcome to the c6509 in the office %/提示文本Bg-sw-01> (enable) set interface sc0 10.234.180.21 255.255.255.0/ 设置管理接口#sh intBg-sw-01> (enable) set ip route default 10.234.180.234/ 设置默认网关#sh iprouteBg-sw-01> (enable) set vtp mode server/ 设置 VTP模式 #sh vtpdomainBg-sw-01> (enable) set vtp domain Core_Net/ 设置 VTP域名Bg-sw-01> (enable) set vlan 31 name ZhongSanLu/ 创建 VLAN #sh vlanBg-sw-01> (enable) set vlan 32 name YiYangBg-sw-01> (enable) set vlan 33 name JianXiuBg-sw-01> (enable) set vlan 34 name RaoDianBg-sw-01> (enable) set vlan 35 name JinSanLouBg-sw-01> (enable) set vlan 36 name WuZiBg-sw-01> (enable) set port channel 1/1-2 on/ 设置 Channel #shport channelBg-sw-01> (enable) set trunk 1/1 on dot1q 1-1005Bg-sw-01> (enable) set trunk 2/2 on dot1q 1-1005 /设置trunk口#sh trunk #Bg-sw-01> (enable) set trunk 2/3 on dot1q 1-1005Bg-sw-01> (enable) set trunk 2/4 on dot1q 1-1005Bg-sw-01> (enable) set trunk 2/5 on dot1q 1-1005Bg-sw-01> (enable) set trunk 2/6 on dot1q 1-1005Bg-sw-01> (enable) set trunk 2/7 on dot1q 1-1005Bg-sw-01> (enable) set spantree root 1-40 dia 4 /设为spantree的根#sh spantree Bg-sw-01> (enable) set spantree portfast 1/1-2 enable /设spantree端口快速启用Bg-sw-01> (enable) set spantree portfast 2/1-8 enableBg-sw-01> (enable) set spantree uplinkfast enable /设spantree端口快速切换Bg-sw-01> (enable) set spantree backbonefast enable /设spantree端口快速定位根1.2 、配置路由Console> (enable) session 15/ 进入路由子卡Router(config)# hostname c6509-msfc /设备名c6509-msfc (config)# enable password testc6509-msfc (config)# enable secret testC6509-msfc(config)# banner motd % Welcome to the c6509-msfc in the Office %/ 设口令/设提示文本c6509-msfc (config)# line vty 0 4 /进入VTY模式c6509-msfc (config-line)#login/登入提示c6509-msfc (config-line)#password test/设用户级口令c6509-msfc (config-line)# endC6509-msfc#configure terminal /进入全局模式Enter configuration commands, one per line. End with CNTL/Z.C6509-msfc(config)# interface vlan 1C6509-msfc(config-if)# ip address 10.234.180.232 255.255.255.0 / C6509-msfc(config-if)# no shutdownC6509-msfc(config-if)#standby 1 ip 10.234.180.234虚IP地址/ 进入虚子接口加 ip 地址/ 开启端口/ 建 HSRP组并设C6509-msfc(config-if)# standby 1 priority 110/ 设优先级C6509-msfc(config-if)# standby 1 preempt/ 设切换许可C6509-msfc(config-if)# interface vlan 31C6509-msfc(config-if)# ip address 10.234.181.60 255.255.255.192C6509-msfc(config-if)# no shutdownC6509-msfc(config-if)# standby 31 ip 10.234.181.62C6509-msfc(config-if)# standby 31 priority 110C6509-msfc(config-if)# standby 31 preemptC6509-msfc(config-if)# interfacevlan 32C6509-msfc(config-if)# ip address 10.234.181.124 255.255.255.192C6509-msfc(config-if)# no shutdownC6509-msfc(config-if)# standby 32 ip 10.234.181.126C6509-msfc(config-if)# standby 32 priority 110C6509-msfc(config-if)# standby 32 preemptC6509-msfc(config-if)# interface vlan 33C6509-msfc(config-if)# ip address 10.234.181.188 255.255.255.192C6509-msfc(config-if)# no shutdownC6509-msfc(config-if)# standby 33 ip 10.234.181.190C6509-msfc(config-if)# standby 33 priority 110C6509-msfc(config-if)# standby 33 preemptC6509-msfc(config-if)# interface vlan 34C6509-msfc(config-if)# ip address 10.234.181.220 255.255.255.224C6509-msfc(config-if)# no shutdownC6509-msfc(config-if)# standby 34 ip 10.234.181.222C6509-msfc(config-if)# standby 34 priority 110C6509-msfc(config-if)# standby 34 preemptC6509-msfc(config-if)# interface vlan 35C6509-msfc(config-if)# ip address 10.234.181.254 252.255.255.224C6509-msfc(config-if)# no shutdownC6509-msfc(config-if)# standby 35 ip 10.234.181.254C6509-msfc(config-if)# standby 35 priority 110C6509-msfc(config-if)# standby 35 preemptC6509-msfc(config-if)# interface vlan 36C6509-msfc(config-if)# ip address 10.234.182.28 255.255.255.224C6509-msfc(config-if)# no shutdownC6509-msfc(config-if)# standby 36 ip 10.234.182.30C6509-msfc(config-if)# standby 36 priority 110C6509-msfc(config-if)# standby 36 preemptC6509-msfc(config-if)# exitC6509-msfc #copy running config[page]二、 Catalyst 4006交换机配置方案2.1 、配置 4006 二层交换(三层交换模块安置在第二个槽)Console> (enable) set system name bg-sw-02 /设备名称Bg-sw-02> (enable) set passwordEnter old password:Enter new password: test/ 设备口令Retype new password: testBg-sw-02> (enable) set enablepassEnter old password:Enter new password: test/ 设备口令Retype new password: testBg-sw-02> (enable) set banner motd % Welcome to the c4006 in the office % /提示文本Bg-sw-02> (enable) set interface sc0 10.234.180.22intBg-sw-02> (enable) set ip route default 10.234.180.234 /255.255.255.0 / 设置管理接口#sh 设置默认网关#sh ip routeBg-sw-02> (enable) set vtp mode server /设置VTP模式#sh vtp domain Bg-sw-02> (enable) set vtp domain Core_Net /设置VTP域名Bg-sw-02> (enable) set vlan 31 name ZhongSanLu /创建VLAN #sh vlanBg-sw-02> (enable) set vlan 32 name YiYangBg-sw-02> (enable) set vlan 33 name JianXiuBg-sw-02> (enable) set vlan 34 name RaoDianBg-sw-02> (enable) set vlan 35 name JinSanLouBg-sw-02> (enable) set vlan 36 name WuZiBg-sw-02> (enable) set port channel 1/1-2 on /设置Channel #sh port channel Bg-sw-02> (enable) set trunk 1/1 on dot1q 1-1005Bg-sw-02> (enable) set port channel 2/1-2 on /设置Channel #sh port channelBg-sw-02> (enable) set trunk 2/1 on dot1q 1-1005Bg-sw-02> (enable) set trunk 4/1 on dot1q 1-1005 /设置trunk口#sh trunk # Bg-sw-02> (enable) set trunk 4/3 on dot1q 1-1005Bg-sw-02> (enable) set trunk 4/4 on dot1q 1-1005Bg-sw-02> (enable) set spantree root secondary 1-40 dia 4Bg-sw-02> (enable) set spantree portfast 1/1-2 enable /设spantree端口快速启用Bg-sw-02> (enable) set spantree portfast 2/1-34 enableBg-sw-02> (enable) set spantree portfast 3/1-32 enableBg-sw-02> (enable) set spantree portfast 4/1-6 enableBg-sw-02> (enable) set spantree uplinkfast enable /设spantree端口快速切换Bg-sw-02> (enable) set spantree backbonefast enable /设spantree端口快速定位根2.1 、配置三层交换模块(三层交换模块安置在第二)Console> (enable) session 2 /进入路由子卡Router(config)# hostname c4006-L3 /设备名c4006-L3 (config)# enable password testc4006-L3 (config)# enable secret testc4006-L3(config)# banner motd % Welcome to the c4006-l3 in the Office % // 设口令设提示文本c4006-L3 (config)# line vty 0 4 /进入VTY模式c4006-L3 (config-line)#login/登入提示c4006-L3 (config-line)#password test/设用户级口令c4006-L3 (config-line)# endC4006-L3#configure terminalEnter configuration commands, one per line. End with CNTL/Z.C4006-L3(config)# interface port-channel 1 /建内部虚端口C4006-L3(config)# interface g3/ 进入接口模式C4006-L3(config-if)# channel-group 1/加入到channelC4006-L3(config-if)# exitC4006-L3(config)# interface g4/ 进入接口模式C4006-L3(config-if)# channel-group 1 /加入到channel组中组中C4006-L3(config-if)# exitC4006-L3(config)# interface port-channel 1.1 /进入子接口模式C4006-L3(config-if)# encapsulation dot1q 1 native/封装trunkC4006-L3(config-if)# ip address 10.234.180.233 255.255.255.0/ 加 ip 地址C4006-L3(config-if)# no shutdown/ 开启端口C4006-L3(config-if)# standby 1 ip 10.234.180.234 /建HSRP组并设虚IP 地址C4006-L3(config-if)# standby 1 priority 100 /设优先级C4006-L3(config-if)# standby 1 preempt /设切换许可C4006-L3(config-if)# interface port-channel 1.31C4006-L3(config-if)# encapsulation dot1q 31C4006-L3(config-if)# ip address 10.234.181.61 255.255.255.192C4006-L3(config-if)# no shutdownC4006-L3(config-if)# standby 31 ip 10.234.181.62C4006-L3(config-if)# standby 31 priority 100C4006-L3(config-if)# standby 31 preemptC4006-L3(config-if)# interface port-channel 1.32C4006-L3(config-if)# encapsulation dot1q 32C4006-L3(config-if)# ip address 10.234.181.125 255.255.255.192C4006-L3(config-if)# no shutdownC4006-L3(config-if)# standby 32 ip 10.234.181.126C4006-L3(config-if)# standby 32 priority 100C4006-L3(config-if)# standby 32 preemptC4006-L3(config-if)# interface port-channel 1.33C4006-L3(config-if)# encapsulation dot1q 33C4006-L3(config-if)# ip address 10.234.181.189 255.255.255.192C4006-L3(config-if)# no shutdownC4006-L3(config-if)# standby 33 ip 10.234.181.190C4006-L3(config-if)# standby 33 priority 100C4006-L3(config-if)# standby 33 preemptC4006-L3(config-if)# interface port-channel 1.34C4006-L3(config-if)# encapsulation dot1q 34C4006-L3(config-if)# ip address 10.234.181.221 255.255.255.224C4006-L3(config-if)# no shutdownC4006-L3(config-if)# standby 34 ip 10.234.181.222C4006-L3(config-if)# standby 34 priority 100C4006-L3(config-if)# standby 34 preemptC4006-L3(config-if)# interface port-channel 1.35C4006-L3(config-if)# encapsulation dot1q 35C4006-L3(config-if)# ip address 10.234.181.253 255.255.255.224C4006-L3(config-if)# no shutdownC4006-L3(config-if)# standby 35 ip 10.234.181.254C4006-L3(config-if)# standby 35 priority 100C4006-L3(config-if)# standby 35 preemptC4006-L3(config-if)# interface port-channel 1.36C4006-L3(config-if)# encapsulation dot1q 36C4006-L3(config-if)# ip address 10.234.182.29 255.255.255.224C4006-L3(config-if)# no shutdownC4006-L3(config-if)# standby 36 ip 10.234.182.30C4006-L3(config-if)# standby 36 priority 100C4006-L3(config-if)# standby 36 preemptC4006-L3(config-if)# exitC4006-L3#copy running config[page]三、 Catalyst 3500XL交换机配置方案3.1 、办公楼Catalyst 3500XL交换机配置方案第一台 Catalyst 3548switch#configure terminalEnter configuration commands, one per line. End with CNTL/Z.switch(config)#hostname bg-sw-03 /设备名bg-sw-03(config)#enable password test /设口令bg-sw-03(config)#enable secret testbg-sw-03(config)#banner motd % Welcome to the C3548 in the Office % /提示文本bg-sw-03(config)#line vty 0 4/进入VTY模式bg-sw-03(config.line)#login/登入提示bg-sw-03(config.line)#password test /设用户级口令bg-sw-03(config.line)#exitbg-sw-03 (config)#int vlan 1 /进入内部管理接口bg-sw-03 (config-if)#ip address 10.234.180.23 255.255.255.0bg-sw-03(config-if)#exit bg-sw-03(config)#ip default.gateway 10.234.180.234bg-sw-03(config)#end /加入 IP 地址/ 设网关bg-sw-03#vlan database/进入vtp数据库bg-sw-03(vlan)#vtp domain Corp_Net/ 设vtp域bg-sw-03(vlan)#vtp client /设定vtp模式bg-sw-03(vlan)#exitbg-sw-03(config)#spantree uplinkfast/ 设定端口快速上连bg-sw-03(config)#int g0/1/ 进入接口模式bg-sw-03(config-if)#switchport mode trunk/ 设为trunk模式bg-sw-03(config-if)#switchport trunk encapsulation dot1q/ 设定封装模式bg-sw-03(config-if)#switchport trunk allowed vlan all许可 vlanbg-sw-03(config-if)#spanning-tree portfast /设定端口快速启用/ 设定trunkbg-sw-03(config-if)#int g0/2/ 进入接口模式bg-sw-03(config-if)#switchport mode trunk/ 设为trunk模式bg-sw-03(config-if)#switchport trunk encapsulation dot1q/ 设定封装模式bg-sw-03(config-if)#switchport trunk allowed vlan all/ 设定 trunk许可 vlanbg-sw-03(config-if)#spanning-tree portfast /设定端口快速启用bg-sw-03(config-if)#exitbg-sw-03#write memory第二台 Catalyst 3548switch#configure terminalEnter configuration commands, one per line. End with CNTL/Z.switch(config)#hostname bg-sw-04 /设备名bg-sw-04(config)#enable password test /设口令bg-sw-04(config)#enable secret testbg-sw-04(config)#banner motd % Welcome to the C3548 in the Office % /提示文本bg-sw-04(config)#line vty 0 4 /进入VTY模式bg-sw-04(config.line)#login /登入提示bg-sw-04(config.line)#password test /设用户级口令bg-sw-04(config.line)#exit /进入内部管理接口bg-sw-04(config)#int vlan 1bg-sw-04(config-if)#ip address 10.234.180.24 255.255.255.0bg-sw-04(config-if)#exitbg-sw-04(config)#ip default.gateway 10.234.180.234bg-sw-04(config)#endbg-sw-04#vlan databasebg-sw-04(vlan)#vtp domain Corp_Netbg-sw-04(vlan)#vtp clientbg-sw-04(vlan)#exitbg-sw-04(config)#spantree uplinkfastbg-sw-04(config)#int g0/1bg-sw-04(config-if)#switchport mode trunkbg-sw-04(config-if)#switchport trunk encapsulation dot1qbg-sw-04(config-if)#switchport trunk allowed vlan allbd-sw-03 (config-if)# spanning-tree portfastbg-sw-04(config-if)#exitbg-sw-04(config)#int g0/2bg-sw-04(config-if)#switchport mode trunkbg-sw-04(config-if)#switchport trunk encapsulation dot1qbg-sw-04(config-if)#switchport trunk allowed vlan allbg-sw-04(config-if)#spanning-tree portfastbg-sw-04(config-if)#exitbg-sw-04#write memory3.2办公楼Catalyst 3548XL交换机配置方案switch#configure terminalEnter configuration commands, one per line. End with CNTL/Z.switch(config)#hostname zsr-sw-01zsr-sw-01(config)#enable password testzsr-sw-01(config)#enable secret testzsr-sw-01(config)#banner motd % Welcome to the C3548 in the Zhong San Lu banGong Lou %zsr-sw-01(config)#line vty 0 4zsr-sw-01(config.line)#loginzsr-sw-01(config.line)#password testzsr-sw-01(config.line)#exitzsr-sw-01(config)#int vlan 1zsr-sw-01(config-if)#ip address 10.234.180.25 255.255.255.0zsr-sw-01(config-if)#exitzsr-sw-01(config)#ip default.gateway 10.234.180.234zsr-sw-01(config)#endzsr-sw-01#vlan databasezsr-sw-01(vlan)#vtp domain Corp_Netzsr-sw-01(vlan)#vtp clientzsr-sw-01(vlan)#exitzsr-sw-1#configure terminalzsr-sw-1(config)#int f0/1zsr-sw-1(config-if)#switchport mode accesszsr-sw-1(config-if)#switchport access vlan 31zsr-sw-1(config-if)#exitzsr-sw-1(config)#int f0/2。
cisco交换机设置时间思科路由器是世界闻名的通讯设备之一了,有不少用户不知道cisco交换机设置时间?店铺为大家分享了具体操作方法,供大家参考!cisco交换机设置时间参考以下步骤:将CISCO6509配置为标准时间服务器ntp server 192.168.0.101查询当前的时间Cisco6509#show clock00:09:13.643 PDT Tue Jun 30 2009配置一个北京时区,随意取名clock timezone Beijing 8再查询一下,已经同步过来了CISCO6509#show clock15:10:00.239 Beijing Tue Jun 30 2009设定硬件时钟为权威NTPserver(config)#clock calendar-valid调整时间#clock set 15:00:00 30 jun 2009当前时钟为#show clock15:15:10.705 Beijing Tue Jun 30 2009当前硬件时钟为#show calendar14:37:59 Beijing Tue Jun 30 2009NTP源为vlan2(config)#ntp source vlan 2将同步其他时间去除no ntp server 10.20.0.103将硬件时钟与当前clock同步#clock update-calendar查看当前clock时间#show clock.15:47:57.558 Beijing Tue Jun 30 2009查看当前硬件时钟#show calendar15:48:00 Beijing Tue Jun 30 2009配置系统debug记录的时间格式(config)#service timestamps debug datetime localtime配置系统日志记录时间格式(config)#service timestamps log datetime localtime设置与其他时间服务器同步(config)#ntp server 192.168.0.102设置为第一级ntp服务器(config)#ntp master 1允许更新硬件时钟(不必须)(config)#ntp update-calendar查看的ntp设置的命令sh clock detailsh ntp stash ntp asssh ntp ass detail----配置命令ntp authentication-key 1 md5 xxntp source Loopback0ntp server 10.10.10.1 key 1配置方法:// router 7206conf tntp source FastEthernet0/1 //指定更新源地址,覆盖ntpserver中的配置ntp update-calendar //设备如带有硬件时钟,同时更新硬件时钟ntp server 202.155.248.218 source FastEthernet0/1 //指定更新目的地址,香港,并指定更新源接口为f0/1.int f0/1ntp enable这时你应该已经获得了时间,但是注意,时区是否正确,默认为格林威治时间,如想改为北京时间,下面这步是必不可少的。
Catalyst 6509 交换机配置手册version 1。
0。
0中望商业机器有限公司© 1995, 2001 Chinaweal Business Machinery CO。
LTDAll Rights Reserve目录1基础配置11.1建立到控制台的连接11。
2配置交换机的地址11。
3配置Ethernet 口31。
4配置交换机的全局参数31.5测试网络的连通性42其它参数的配置52.1配置Login Banner52。
2配置DNS62.3配置CDP协议73VLAN的配置83.1配置VTP协议(VLAN Trunk Protocol)83.2配置VLAN93.2。
1创建VLAN93.3将交换端口配置到VLAN中103。
4配置VLAN Trunks113.5在MSFC上配置IP InterVLAN路由123。
5。
1从Console口进入MSFC123。
5。
2通过Telnet Session 进入MSFC 模块133。
5.3在MSFC上配置IP InterVLAN路由133.6配置HSRP协议143.7配置以太通道161 基础配置1.1 建立到控制台的连接在进行配置和将交换机接入网络前必须通过控制台来进入交换机的CLI,对交换机进行配置。
在进入CLI后,通过命令enable进入到privileged 模式。
通过以下步骤将终端连接到交换机的控制口例如:〈... output truncated ..。
〉Cisco Systems ConsoleEnter password:Console〉enableEnter password:Console> (enable)1.2 配置交换机的地址在远程登录交换机前你必须为交换机配置地址,掩码和网关等信息- 1 -在你第一次配置交换机时,将sc0口配置到default VLAN,即VLAN 1中,在你配置了其他VLAN以后,你可以将sc0口配置到其他VLAN中,但是sc0口的地址和网关必须与所在的VLAN的网段对应.配置IP地址和网关的步骤如下例如:Console〉 (enable) set interface sc0 10.1。
6509双引擎热备router-15#sh runBuilding configuration...Current configuration:!version 12.1service timestamps debug uptimeservice timestamps log uptimeservice password-encryption!hostname router-15!boot system flash bootflash:c6msfc2-isv-mz.121-3a.E4 enable secret 5 $1$3QV6$q6vJvcpLFS3Ayzz.cAUWl. enable password 7 032C7E2C392C087F6D26!ip subnet-zeroip cef distributed!redundancyhigh-availabilityconfig-sync!!!interface ATM7/0/0no ip addressatm sonet stm-1no atm ilmi-keepalive!interface ATM7/0/0.10 point-to-pointdescription connect to xxx centermtu 1514ip address 10.x.x.x 255.255.255.252ip access-group 150 inip access-group 150 outatm pvc 2 0 119 aal5snap!interface ATM7/0/0.100 point-to-pointdescription connect to xxxmtu 1514ip address 10.x.x.x 255.255.255.252ip access-group 150 inip ospf cost 65atm pvc 10 0 109 aal5snap!interface Vlan1ip address 10.166.192.10 255.255.255.0 alt ip address 10.166.192.9 255.255.255.0 no ip redirectsstandby 1 timers 5 15standby 1 priority 120 preempt alt standby 1 priority 120 preemptstandby 1 authentication ciscostandby 1 ip 10.166.192.8 alt standby 1 ip 10.166.192.8!interface Vlan2ip address 10.166.193.10 255.255.255.0 alt ip address 10.166.193.9 255.255.255.0 no ip redirectsstandby 2 timers 5 15standby 2 priority 120 preempt alt standby 2 priority 120 preemptstandby 2 authentication ciscostandby 2 ip 10.166.193.8 alt standby 2 ip 10.166.193.8!interface Vlan3no ip addressshutdown!interface Vlan4ip address 10.166.196.10 255.255.255.0 alt ip address 10.166.196.9 255.255.255.0 no ip redirectsstandby 4 timers 5 15standby 4 priority 120 preempt alt standby 4 priority 120 preemptstandby 4 authentication ciscostandby 4 ip 10.166.196.8 alt standby 4 ip 10.166.196.8!interface Vlan7ip address 10.166.194.10 255.255.255.0 alt ip address 10.166.194.9 255.255.255.0 no ip redirectsstandby 7 timers 5 15standby 7 priority 120 preempt alt standby 7 priority 120 preemptstandby 7 authentication ciscostandby 7 ip 10.166.194.8 alt standby 7 ip 10.166.194.8!interface Vlan11ip address 10.166.198.10 255.255.255.0 alt ip address 10.166.198.9 255.255.255.0 no ip redirectsstandby 11 timers 5 15standby 11 priority 120 preempt alt standby 11 priority 120 preemptstandby 11 au thentication ciscostandby 11 ip 10.166.198.8 alt standby 11 ip 10.166.198.8!interface Vlan14no ip addressshutdown!interface Vlan21ip address 10.166.201.10 255.255.255.0 alt ip address 10.166.201.9 255.255.255.0 no ip redirectsstandby 21 timers 5 15standby 21 priority 120 preempt alt standby 21 priority 120 preemptstandby 21 authentication ciscostandby 21 ip 10.166.201.8 alt standby 21 ip 10.166.201.8!interface Vlan31ip address 10.166.202.10 255.255.255.0 alt ip address 10.166.202.9 255.255.255.0 no ip redirectsstandby 31 timers 5 15standby 31 priority 120 preempt alt standby 31 priority 120 preempt standby 31 authentication ciscostandby 31 ip 10.166.202.8 alt standby 31 ip 10.166.202.8!interface Vlan78no ip addressshutdown!router ospf 100log-adjacency-changesarea 19 range 10.166.192.0 255.255.240.0network 10.166.192.0 0.0.15.255 area 19network 10.166.254.0 0.0.0.127 area 0network 10.166.255.0 0.0.0.127 area 0!no ip classlessip route 0.0.0.0 0.0.0.0 10.166.255.33ip route 10.0.0.0 255.0.0.0 10.166.192.50 220ip route 10.166.206.0 255.255.255.0 10.166.192.40ip route 193.1.1.0 255.255.255.0 10.166.192.39no ip http server!!map-list atmip 10.166.254.1 atm-vc 1access-list 1 permit anyaccess-list 150 permit ospf any anyaccess-list 150 permit tcp any any eq wwwaccess-list 150 permit tcp any any eq 81access-list 150 permit tcp any any eq 8080access-list 150 permit tcp any any eq 8888access-list 150 permit udp any any eq 8888access-list 150 permit tcp any any eq ftp-dataaccess-list 150 permit tcp any any eq ftpaccess-list 150 permit tcp any any eq telnetaccess-list 150 permit tcp any any eq domainaccess-list 150 permit tcp any any eq pop3access-list 150 permit tcp any any eq smtpaccess-list 150 permit tcp any any eq 1521access-list 150 permit tcp any any eq 5000access-list 150 permit tcp any any eq 5678access-list 150 permit tcp any any eq 143access-list 150 permit udp any any eq 38293access-list 150 permit udp any any eq 2967access-list 150 permit udp any any eq domainaccess-list 150 permit tcp any any eq 1503access-list 150 permit tcp any any eq 1720access-list 150 permit tcp any any gt 1023 establishedaccess-list 150 permit icmp any 10.166.254.0 0.0.0.255 echo-reply access-list 150 permit tcp any any eq 60000access-list 150 permit tcp any host 10.166.1.56access-list 150 permit tcp any host 10.166.1.55!line con 0password 7 070C285F4D06logintransport input nonelinevty 0 4password 7 030752180500login!。
Catalyst 6509 交换机配置手册version 1.0.0中望商业机器有限公司© 1995, 2001 Chinaweal Business Machinery CO. LTDAll Rights Reserve目录1基础配置11.1建立到控制台的连接11.2配置交换机的地址21.3配置Ethernet 口31.4配置交换机的全局参数41.5测试网络的连通性52其它参数的配置62.1配置Login Banner62.2配置DNS72.3配置CDP协议83VLAN的配置93.1配置VTP协议(VLAN Trunk Protocol)93.2配置VLAN103.2.1创建VLAN103.3将交换端口配置到VLAN中113.4配置VLAN Trunks123.5在MSFC上配置IP InterVLAN路由133.5.1从Console口进入MSFC133.5.2通过Telnet Session 进入MSFC 模块143.5.3在MSFC上配置IP InterVLAN路由143.6配置HSRP协议153.7配置以太通道161基础配置1.1建立到控制台的连接在进行配置和将交换机接入网络前必须通过控制台来进入交换机的CLI,对交换机进行配置。
在进入CLI后,通过命令enable进入到 privileged 模式。
通过以下步骤将终端连接到交换机的控制口例如:<... output truncated ...>Cisco Systems ConsoleEnter password:Console> enableEnter password:Console> (enable)页脚内容11.2配置交换机的地址在远程登录交换机前你必须为交换机配置地址,掩码和网关等信息在你第一次配置交换机时,将sc0口配置到default VLAN,即VLAN 1中,在你配置了其他VLAN以后,你可以将sc0口配置到其他VLAN中,但是sc0口的地址和网关必须与所在的VLAN的网段对应.配置IP地址和网关的步骤如下例如:Console> (enable) set interface sc0 10.1.1.50/255.0.0.0Interface sc0 IP address and netmask set.Console> (enable) set interface sc0 100Interface sc0 vlan set.Console> (enable) set ip route default 10.1.1.1Route added.Console> (enable) show interfacesl0: flags=51<UP,POINTOPOINT,RUNNING>slip 0.0.0.0 dest 0.0.0.0sc0: flags=63<UP,BROADCAST,RUNNING>vlan 100 inet 10.1.1.50 netmask 255.0.0.0 broadcast 10.255.255.255Console> (enable) show ip routeFragmentation Redirect Unreachable------------- -------- -----------enabled enabled enabledDestination Gateway Flags Use Interface页脚内容2----------------------- ----------------------- ------ ---------- ---------default 10.1.1.1 UG 0 sc010.0.0.0 10.1.1.50 U 0 sc0default default UH 0 sl0Console> (enable) ping 10.1.1.10010.1.1.100 is aliveConsole> (enable)1.3配置 Ethernet 口在一条连路两端的Ethernet, Fast Ethernet和 Gigabit Ethernet 口的端口速率了工作方式必须相同。
Ethernet 和Fast Ethernet 会自动配置工作方式,10/100-Mbps Fast Ethernet 口可以自动检测连路速率。
. Gigabit Ethernet总是在 full duplex方式下工作。
配置步骤如下注:对10/100-Mbps Fast Ethernet 口,当端口的速率是AUTO时,你不能手动改变工作方式。
例如:Console> (enable) set port speed 2/12 autoPort 2/12 speed set to auto detect.页脚内容3Console> (enable) set port name 2/12 NT Server 12Port 2/12 name set.Console> (enable) show port 2/12Port Name Status Vlan Level Duplex Speed Type----- ------------------ ---------- ---------- ------ ------ ----- ------------ 2/12 NT Server 12 connect 1 normal a-half a-100 10/100BaseTX <... output truncated ...>Console> (enable)1.4配置交换机的全局参数配置步骤和命令如下:例如:Console> (enable) set system name Catalyst 6000System name set.Catalyst 6000> (enable) set time 08/18/98 10:08:00Sat Apr 18 1998, 10:08:00Catalyst 6000> (enable) set passwordEnter old password:Enter new password:Retype new password:Password changed.Catalyst 6000> (enable) set enablepassEnter old password:Enter new password:Retype new password:Password changed.Catalyst 6000> (enable)页脚内容41.5测试网络的连通性在你配置了交换机的地址和网关以后,你就可以与网络上的其它节点连通了。
测试方法如下:Ping和traceroute的例子如下Console> (enable) ping -s 172.20.52.20 1200 4PING 172.20.52.20: 1200 data bytes1208 bytes from 172.20.52.20: icmp_seq=0. time=6 ms1208 bytes from 172.20.52.20: icmp_seq=1. time=6 ms1208 bytes from 172.20.52.20: icmp_seq=2. time=6 ms1208 bytes from 172.20.52.20: icmp_seq=3. time=5 ms----172.20.52.20 PING Statistics----4 packets transmitted, 4 packets received, 0% packet lossround-trip (ms) min/avg/max = 5/5/6Console> (enable) traceroute 172.20.52.20 1400traceroute to 172.20.52.20 (172.20.52.20), 30 hops max, 1440 byte packets1 172.20.52.33 (172.20.52.33)2 ms3 ms 1 ms2 172.20.52.20 (172.20.52.20) 4 ms * 4 msConsole> (enable)页脚内容52其它参数的配置2.1配置 Login Bannerlogin banner或 message of the day是在你登陆到交换机时出现在屏幕上的提示信息,最多可以配置255 个字符。
配置步骤:例如: (通过控制口):Console> (enable) set banner motd *Catalyst 6000Software Release 5.4(1)IP address 10.1.1.20*MOTD banner setConsole> (enable) exitCisco Systems ConsoleCatalyst 6000Software Release 5.4(1)IP address 10.1.1.20页脚内容6Enter password:2.2配置 DNS域名系统(Domain Name System,DNS) 可以让你使用主机名来代替交换机的IP地址。
在使用DNS前,你必须有一个或一个以上的域名服务器(DNS server) .步骤:例如:Console> (enable) set ip dns server 10.1.1.100 primary10.1.1.100 added to DNS server table as primary server.Console> (enable) set ip dns server 10.1.1.12210.1.1.122 added to DNS server table as backup server.Console> (enable) set ip dns domain Default DNS domain name set to Console> (enable) set ip dns enableDNS is enabledConsole> (enable) show ip dnsDNS is currently enabled.The default DNS domain name is: DNS name server status---------------------------------------- -------10.1.1.100 primary10.1.1.122Console> (enable)页脚内容72.3配置 CDP协议Cisco Discovery Protocol (CDP) 是一种协议和介质无关的协议。