Application Form_Inbound V2.1_Latest
- 格式:doc
- 大小:108.00 KB
- 文档页数:2

ATTO 360™ Version 2.1 Tuning, Monitoring, and Analytics Software Installation and Operation ManualFastFrame N32210/25GbE Dual Port PCIe 3.0 Network Interface CardFastFrame N35110/25/40/50GbE Single Port PCIe 3.0 Network Interface CardFastFrame N35210/25/40/50GbE Dual Port PCIe 3.0 Network Interface CardFastFrame N31110/25/40/50/100GbE Single Port PCIe 3.0 Network Interface CardFastFrame N31210/25/40/50/100GbE Dual Port PCIe 3.0 Network Interface CardThunderlink TLN3-3102Thunderbolt 3 to 10Gb Ethernet DeviceThunderlink TLNS-3252Thunderbolt 3 to 25Gb Ethernet Device© 2021 ATTO Technology, Inc. All rights reserved. All brandor product names are trademarks of their respectiveholders. No part of this manual may be reproduced in anyform or by any means without the express writtenpermission of ATTO Technology, Inc.04/2021 PRMA-0495-000ATTO 360™ Features and Overview OverviewThe following document provides a tutorial on how to use ATTO 360™ software to tune for network performance, monitor, and identify potential network issues when using ATTO FastFrame and Thunderlink Ethernet controllers on macOS, Windows, and Linux.Getting StartedIn general, to install the ATTO 360 application, you must:1.Ensure you have the equipment andsoftware you need for the installation: •FastFrame NIC or Thunderlink controller with Ethernet interface•A computer running macOS, windows, or LinuxSoftware InstallationWindows2.Power on your system and log in as theadministrator or a user with properadministrative privileges.3.Go to https:///4.Click on downloads5.Register or log in if previously registered.6.Click on software in the left dialog.7.Navigate to ATTO Ethernet Suite forWindows in the right dialog and click on it.•A TTO Ethernet Suite includes an ATTOhardware driver for Windows 10 withoption to install ATTO 360 and 360 Viewalong with Driver installation8.Scroll down to and click the Windowsdownload.9. A download window appears. Choose SaveFile.10.Double-click the downloaded file to extractand launch the ATTO 360 Ethernet Suite. 11.Follow the on-screen instructions tocomplete the software installation.•O ptional 360 View - if you decide to opt inand install 360 View a time seriesdatabase will be stored on your localmachine•I f you are having issues with this featureplease see “Linux troubleshooting guide”in this manualLinux1.Power on your system and log in as theadministrator or a user with properadministrative privileges.2.Go to https:///3.Click on downloads4.Register or log in if previously registered.5.Click on software in the left dialog.6.Navigate to ATTO 360 Ethernet Suite in theright dialog and click on it.7.Scroll down to and click the Linux version ofATTO Ethernet Suite•A TTO Ethernet Suite is an installerpackage that includes ATTO hardwaredriver as well as ATTO 360 software andotional 360 View time series database 8. A download window appears. Choose SaveFile.9.After the download has completed, openthe ATTO 360 volume on the desktop.10.Open the Linux folder.11.Copy the .tgz file to a temporary folder.12.Open a terminal window and change thelocation of the copied tgz.13.Extract the file using the command tar -xfz<filename.tgz>.14.Change to the directory created above thenrun the installer script ./install.sh.•T o Install ATTO 360 only and not theATTO hardware driver, skip the driver bysetting this in the environment beforerunning the installer:OFED_SKIP_INSTALL=Yes•T o skip the firmware tool install, set thisin the environment before running theinstaller:MFT_SKIP_INSTALL=Yes•O ptional 360 View – if you decide to optin and install 360 View a time seriesdatabase will be stored on your localmachine•360 View uses “podman” which willneed to be installed on your machine.Please see the 360 Viewtroubleshooting section below formore infoTCP ports 3000, 9090, and 27092 are required to use this feature, please make sure these ports are open and available.•U se this command to assign portsudo env GRAFANA_PORT=3001./path/to/installer.sh•I f you are having issues with this featureplease see troubleshooting guide on Page6macOS1.Power on your system and log in as theadministrator or a user with properadministrative privileges2.Go to https:///3.Click on downloads.4.Register or log in if previously registered.5.Click on software in the left dialog.6.Navigate to your ATTO 360 in the rightdialog and click on it.7.Scroll down to and click the macOSdownload version8. A .dmg file for ATTO 360 and 360 View willappear on your desktop9.Click on ATTO 360 icon to install ATTO 360,click on 360 View icon to install the optional 360 View10.Follow the on-screen instructions.••Optional 360 View – if you decide toopt in and install 360 View a time seriesdatabase will be stored on your localmachine.DRIVER UPDATE NEEDED – ThunderLink and FastFrame 3 macOS driver version 1.07 or later is required for 360 View to work properly.•I f you are having issues with this featureplease see troubleshooting guide on Page6System InformationSystem information is the first screen that loads when you launch ATTO 360™Here you can access relevant information about your system in one convenient area. You can identify items like Operating System, CPU and see TCP/IP settings like Receive/Transmit Buffers, TCP Window Scale, firewall, IP forwarding, and hyper-threading.SMB signing – Server message block signing is an SMB protocol used to confirm the origin and authenticity of incoming packets, SMB signing can cause a drop in performance and should only be used when you have security concerns and are uncertain about the origin on incoming packets - this feature is available on macOS only IRQ Balancing – Interrupt request line blocking distributes hardware interrupts across processors on a multiprocessor system in order to increase performance - this feature is available on Linux onlyThis screen also contains two routing tables, one for IPv4 traffic and one IPv6 traffic. These tables show the topology of the networks on your machine.360°View360°View is a new feature built into ATTO 360 Version 2.0. Clicking the “launch” button from the System Information tab will open the 360°View dashboard that shows performance and other key metrics displayed over time. This feature must be enabled during installation, please see installation instructions on how to get 360 View installed.TCP ports 3000, 9090, and 27092 are required to use this feature, please make sure these ports are open and available.if you are having problems viewing data or launching 360 View’s dashboard you can find suggestions on our 360 View troubleshooting guideTroubleshooting guide for 360 ViewLinux UsersFor 360 View on the Linux platform we utilize podman container, the minimum version of podman required for 360 View to work properly is v1.8.1. Updating to the latest version of podman is encouraged. Please follow these instructions;1.Install podman from the distribution usingthis command;sudo yum install podman2.To check which version of podman you’rerunning use this command;sudo podman version3.Update to the latest podman;https://podman.io/getting-started/installation4.We have seen an issue running `yumupdate` after this where it upgrades acontainer module, which alters a config fileand causes issues for certain CENTOS users, to avoid please disable the repo afterinstalling podman using this command;sudo yum-config-manager --disable devel_kubic_libcontainers_stable CENTOS 8 users may need to follow these update instructions:sudo dnf -y module disable container-toolssudo dnf -y install 'dnf-command(copr)'sudo dnf -y copr enable rhcontainerbot/container-selinuxsudo curl -L -o/etc/yum.repos.d/devel:kubic:libcontainers:stable. repohttps:///repositories/devel:/kub ic:/libcontainers:/stable/CentOS_8/devel:kubic:libcontai ners:stable.reposudo dnf -y install podmanCENTOS 8.3 users have Podman installed already and do not need to take these stepsMac UsersmacOS users will need to update their FastFrame or Thunderlink driver to version 1.06 or later for 360 View to work properly.ALL users360 View’s dashboard run on a web browser, the latest versions of the following browsers are supported;•C hrome/Chromium•F irefox•S afari•M icrosoft EdgeInternet Explorer is NOT supported and dashboard will not load properly.5 NIC InformationNIC Information is the second option available in the left-hand menu.Select the network interface you would like to display information for in the top drop down box. You will see several interfaces, each representing a single Ethernet port. Ports connected to ATTO adapters or Thunderlink devices will be highlighted in red with [ATTO] next to their number identifier.When you select a corresponding ATTO interface you will be given access to several points of data about your NIC including, Link status/speed, Model, channel, current PCIe slot, PCI location, flags, MAC address, MTU size/selection, RSS profiles (Linux and Windows), driver version, network services(macOS only), and firmware version.You can also adjust several important settings that help in fine-tuning the performance of your NIC and can affect throughput positively or negatively.aRFS - Accelerated Receive Flow Steering is a technique where packets are forwarded based on the location of the application consuming the packet directly to a CPU that is local to the thread consuming the data. – Linux onlyGRO – Generic Receive Offload is a widely-used software based offloading technique to reduce per-packet processing overheads. – Linux onlyLRO – Large Receive Offload is a technique for increasing inbound throughput of high-bandwidth network conditions by reducing CPU overhead.TSO – TCP segmentation Offload is a technique for increasing outbound throughput of high-bandwidth TCP network communications by reducing CPU overhead.RSC – Receive Segment Coalescing enables network card miniport drivers to coalesce multiple TCP segments and indicate them as a single coalesced unit. – Windows onlyLSO – Large Send Offload is a technique for increasing outbound throughput of high-bandwidth network communications by reducing CPU overhead. – Windows onlyRSS - Receive Side Scaling is a network driver technology that enables the efficient distribution of network receive processing across multiple CPUs in multiprocessor systems. – Windows onlyFlow control – Flow control is the process of managing the rate of data transmission between two nodes to prevent a fast sender from overwhelming a slow receiver.Striding RQ – Enables a striding queue that offloads packet processing helping users deal with smaller packet traffic (not supported by FFRM-N351 and N352)6 NIC StatisticsThe NIC Statistics page allows the user to monitor Layer 2 Frame statistics and offer a view into Layer 1, for the purpose of assisting with troubleshooting issues and offering insight into performance-tuning opportunities.Term DefinitionRx Total Packets Total number of all packets received (unicast,broadcast, multicast), regardless of length,errors, or L2 filtering, but excluding flow controlpackets.Rx Broadcast Packets Number of good (non-erred) broadcast packetsreceived while the broadcast address filter isconfigured to allow reception of broadcastpackets.Rx Multicast Packets Number of good (non-erred) multicast packetsreceived that pass L2 filtering, excludingbroadcast packets and flow control packets.Rx Good Packets Number of good (non-erred) packets receivedthat pass L2 filtering and have a legal length.Counts of good packets received are alsodisplayed by packet size.Rx Good Bytes Total number of all bytes received in good (non-erred) packets from the field through the field,inclusively.Rx Errors Total number of errors in packets received. Whenerrors are displayed, check SFP, cable, MTU aswell as local or remote interfaces.CRC Errors Number of packets received with CRC errors, notincluding packets whose length is less than 64bytes (Fragments) or greater than the max packetsize (Jabbers).Illegal Bytes Number of packets received with illegal byteerrors, such as an illegal symbol in the packet. Length Errors Number of packets received whose packet lengthfield in the MAC header doesn't match the actualpacket length.Undersize Packets Receive undersize errors: Received frames thatare shorter than the minimum size (64 bytes) andhave a valid CRC.Oversize Packets Receive oversize errors: Received frames that arelonger than the configured maximum packet sizeand have a valid CRC.Fragments Receive fragment errors: Received frames thatare shorter than the minimum size (64 bytes) andhave an invalid CRCChecksum Errors Number of packets received that contain IPv4,TCP, UDP or SCTP checksum errors. Checksumerrors are not counted when a packet has anyMAC error (CRC, length, undersize, oversize, byteerror or symbol error).Allocation Fails Number of packets that were dropped because ofa memory allocation failure.Rx Missed Packets Number of packets received that were droppedbecause no buffer was available to receive thedata. Check MBUF structures with netstat –m.Counts the total number of packets missed on allTraffic Classes (TC).Tx Total Packets Total number of all packets transmitted, includingstandard, secure, FC, and manageability packets. Tx Broadcast Packets Number of broadcast packets transmitted.Tx Multicast Packets Number of multicast packets transmitted.Tx Good Bytes Number of successfully transmitted bytes,including bytes from the field.Tx Inlined Packets Number of Inlined packets transmitted.Tx Errors Total number of errors in packets transmitted Map Fails Number of packets that were dropped because ofan error mapping the packet memory.Other Fails Number of packets that were dropped due to ageneral failure.Tx Oversized Packets Oversize errors: Frames that are longer than theconfigured maximum packet size and have a validCRCTSO Count Number of Transmit Segmentation Offloadoperations attempted (including attempts thatmay have failed)LRO Flushed Number of Large Receive Offloads operationsflushed.Rx Flow Control XOFFs Counts of Ethernet Pause Frames (Flow Control).Flow control is a Link layer attempt to relieve thepressure on queues to avoid congestion. Whenan Ethernet device gets congested or overloaded, flow control allows it to send PAUSErequests to the transmitter until the over loadedcondition dissipates. If flow control is not enabledand an over loaded condition occurs, the devicewill drop packets. Dropping packets will impactperformance.Tx Flow Control XOFFs Counts of Ethernet Pause Frames (Flow Control).Flow control is a Link layer attempt to relieve thepressure on queues to avoid congestion. Whenan Ethernet device gets congested or overloaded, flow control allows it to send PAUSErequests to the transmitter until the over loadedcondition dissipates. If flow control is not enabledand an over loaded condition occurs, the devicewill drop packets. Dropping packets will impactperformance.7 Tuning ProfilesThe Tuning Profiles area contains 1-click settings for applying pre-designated NIC and system parameters that are designed to work with specific workflows and storage use cases. These profiles were designed by ATTO engineers to work best in certain environments.Default – The system default.High throughput – This is optimized for high throughput. This is better for systems that transmit or receive large amounts of data and favor throughput over latency.Low Latency – This is optimized for reducing latency and favors reducing packet loss over high throughput.Multi-stream Throughput – This is optimized for multi-stream packet processing. This is better for systems that transmit or receive large amounts of data over multiple queues. This profile favors throughput over latency.SMB – This profile is optimized for high throughput with SMB specific connectionsNFS – This profile is optimized for high throughput with NFS specific connectionsSMB MultiChannel – This profile is optimized for high throughput with SMB MultiChannel connections(Windows only)Partner Tuning ProfilesPartner tuning profiles can be accessed via the drop down menu in the ATTO Tuning Profiles Tab;•S everal custom Dell OneFS Tuning Profiles are available for Windows, macOS, and Linux. Select the type of network share you are using with Dell OneFS based storage (SMB, NFS, SMB-MultiChanel).•C ustom AVID Nexus profiles for Windows and macOS are available via the AVID section on the drop down menu•C ustom Autodesk profile for Linux is available via the Autodesk section on the drop down menu8 DiagnosticsThe Diagnostics menu will be highlighted red if the application recognizes settings that could be negatively impacting performance or connectivity. Selecting this option will present any built-in alerts that point to possible areas of concern or issues with performance.Appendix A GlossaryTerm DefinitionOS Indicates which Operating System is installed onthe system running ATTO 360. An operatingsystem (OS) is system software that managescomputer hardware, software resources, andprovides common services for computerprograms.CPU Indicates CPU model is installed on systemrunning ATTO 360. A central processing unit(CPU) is the electronic circuitry within a computerthat carries out the instructions of a computerprogram by performing the basic arithmetic,logic, controlling, and input/output (I/O)operations specified by the instructions. Performance Mode Indicates which CPU is running in highperformance mode rather than power saving orsleep modes that would cause performanceproblemsFirewall Indicates whether or not firewall is established. IP Forwarding Indicates whether IP forwarding isenabled/disabled.Hyper Threading Indicates whether Hyper Threading isenabled/disabled. Hyper Threading is a high-performance computing architecture thatsimulates some degree of overlap in executingtwo or more independent sets of instructions. Receive Buffer Displays size of receive buffer window. Thebuffer size of system memory that can be used bythe adapter for receiving packetsTransmit Buffer Displays size of transmit buffer window. Thebuffer size of system memory that can be used bythe adapter for sending packetsWindow Scale Displays TCP Window Scale option. The TCPwindow scale option is an option to increase thereceive window size allowed in TransmissionControl Protocol above its former maximumvalue of 65,535 bytes.Link Status Displays whether Link Status is up or down. Model Indicates model number for the ATTO adapterthat is currently installedChannel Indicates which Ethernet port the application ismonitoringThunderbolt Thunderbolt is the brand name of a hardwareinterface developed by Intel (in collaborationwith Apple) that allows the connection ofexternal peripherals to a computer.PCIe Generation Displays PCI Express generation NIC is running PCIe Width Displays PCIe width determining the number oflanes that can be used in parallel by the devicefor communication (i.e. x4, x8, x16)PCIe Speed Displays PCIe speed in gigatransfers per second PCIe Location Displays PCIe locationLink Speed Displays the maximum speed in bits per secondthat your device can communicate with thedevice that it is linked to.IPv4 Address Displays IPv4 address. The IPv4 address is a 32-bit number that uniquely identifies a networkinterface on a machine.IPv6 Address Displays IPv6 address. An IPv6 address is a 128-bit value that identifies an endpoint device in theInternet Protocol Version 6 (IPv6) addressingscheme.MAC Address Displays MAC address. A media access controladdress of a device is a unique identifier assignedto a network interface controller.MTU Here you can change MTU size. MaximumTransmission Unit (MTU) is the size of the largestprotocol data unit (PDU) that can becommunicated in a single network layertransaction.Driver Version Displays what driver version is installedFW Version Displays what Firmware version is installed forthe selected adapter。
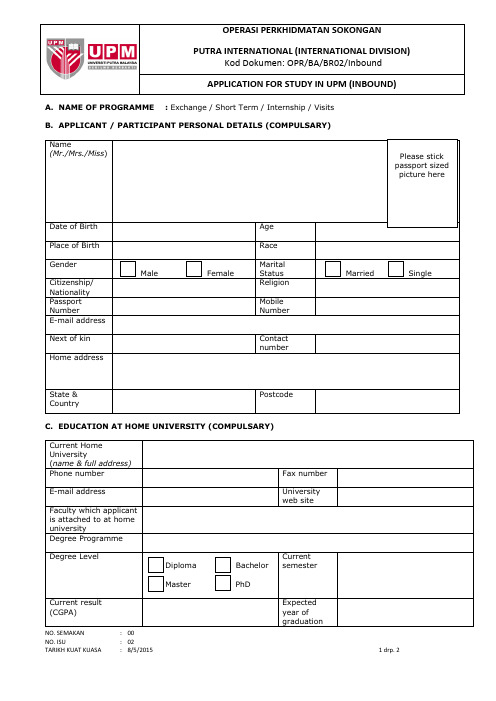
A. NAME OF PROGRAMME : Exchange / Short Term / Internship / VisitsB. APPLICANT / PARTICIPANT PERSONAL DETAILS (COMPULSARY) Name(Mr./Mrs./Miss)Date of Birth AgePlace of Birth RaceGenderMale Female MaritalStatus Married SingleCitizenship/NationalityReligionPassport Number Mobile NumberE-mail addressNext of kin ContactnumberHome addressState &CountryPostcodeC. EDUCATION AT HOME UNIVERSITY (COMPULSARY)Current HomeUniversity(name & full address)Phone number Fax numberE-mail address Universityweb site Faculty which applicantis attached to at homeuniversityDegree ProgrammeDegree LevelDiploma BachelorMaster PhD Current semesterCurrent result (CGPA)Expectedyear ofgraduationOPERASI PERKHIDMATAN SOKONGANPUTRA INTERNATIONAL (INTERNATIONAL DIVISION)Kod Dokumen: OPR/BA/BR02/InboundAPPLICATION FOR STUDY IN UPM (INBOUND)Please stickpassport sizedpicture hereNO. SEMAKAN : 00D. STUDY IN UPM (COMPULSARY)E. LANGUAGENO. SEMAKAN : 00G. INTER-OFFICE COMMUNICATION (COMPULSARY)Please include the contact person from the home university (international affairs officer/student exchange coordinator) who is responsible for correspondence.I hereby declare that the information provided in this form is true.Signature : ____________________________________ Date: ________________________ Name : ____________________________________NOTE:* Incomplete application form will not be processed** Please submit copy of Academic Transcript, 2 current blue colored photographs (passport size) and a copy of your passport (front page only)NO. SEMAKAN : 00A. NAME OF PROGRAMME : Exchange / Short Term / Internship / VisitsB. APPLICANT / PARTICIPANT PERSONAL DETAILS (COMPULSARY) Name(Mr./Mrs./Miss)Wu JiaDate of Birth 23rd,February,1996 Age 18 Place of Birth Shanghai Race ChineseGenderMale Female MaritalStatus Married SingleCitizenship/NationalityChinese ReligionPassport Number MobileNumber+86XXXXXXE-mail address XXXXXXX@Next of kin Wu Zhiyong Contactnumber+86XXXXXX Home address XXXX No.352XiangYin Road,YangPu District,Shanghai,ChinaState &CountryXingning,Guangdong Postcode 433C. EDUCATION AT HOME UNIVERSITY (COMPULSARY)Current Home University(name & full address)Guilin University of Electronic Technology1st ,Jinji Road,Qixing District,Guilin City,ChinaPhone number 0773-XXXXXX Fax number 0773-XXXXXX E-mail address XXXXXX @ Universityweb siteFaculty which applicantis attached to at homeuniversityCollege of BusinessDegree Programme Logistics ManagementDegree LevelDiploma BachelorMaster PhD Currentsemester6/9-7/7Current result (CGPA) 66.06 Expectedyear ofgraduation8/7OPERASI PERKHIDMATAN SOKONGANPUTRA INTERNATIONAL (INTERNATIONAL DIVISION)Kod Dokumen: OPR/BA/BR02/InboundAPPLICATION FOR STUDY IN UPM (INBOUND)Please stickpassport sizedpicture hereNO. SEMAKAN : 00D. STUDY IN UPM (COMPULSARY)E. LANGUAGENO. SEMAKAN : 00G. INTER-OFFICE COMMUNICATION (COMPULSARY)Please include the contact person from the home university (international affairs officer/student exchange coordinator) who is responsible for correspondence.I hereby declare that the information provided in this form is true.Signature : ____________________________________ Date: ________________________ Name : _Wu Jia______________________________NOTE:* Incomplete application form will not be processed** Please submit copy of Academic Transcript, 2 current blue colored photographs (passport size) and a copy of your passport (front page only)NO. SEMAKAN : 00Attention:1.Form must be completed.2.Please attach a copy of previous semester examination result slip.3.The completed form must be submitted to the International Division, Universiti Putra Malaysia with Mobility Program Application Form PART A: APPLICANT INFORMATION(to be completed by student)Name :Passport No. : Email Address :Home InstitutionProgram : Date of Birth :UPM Program : Place of birth :Period of Study inUPM : to Citizen :Home Country : Religion :Home Institution: :PART B: COURSE INFORMATION FOR TRANSFER OF CREDIT(to be completed by student)Fill in the course of the University Putra Malaysia to be taken in the space provided.No. CourseCodeCourse Name CreditOPERASI PERKHIDMATAN SOKONGANPUTRA INTERNATIONAL (INTERNATIONAL DIVISION)Kod Dokumen: OPR/BA/BR02/Transfer APPLICATION FORM FOR TRANSFER OF CREDIT BETWEEN INSTITUTIONS(INBOUND)NO. SEMAKAN : 00NO. SEMAKAN : 00NO. SEMAKAN : 00Attention:4. Form must be completed.5. Please attach a copy of previous semester examination result slip.6. The completed form must be submitted to the International Division, Universiti Putra Malaysia with Mobility Program Application FormPART A: APPLICANT INFORMATION(to be completed by student)Name: Wu Jia Passport No. :Email Address : XXX @ Home Institution Program : Logistics Management Date of Birth : 23rd ,February,1996 UPM Program : Logistics Management Place of birth : Shanghai Period of Study in UPM : 5/9 to6/1Citizen : Guilin,China Home Country : ChineseReligion :Home Institution: : Guilin University of Electronic TechnologyPART B: COURSE INFORMATION FOR TRANSFER OF CREDIT(to be completed by student)Fill in the course of the University Putra Malaysia to be taken in the space provided. No. Course Code Course NameCredit 2 MTH 3004 INTRODUCTION TO ECONOMICS AND BUSINESS MATHEMATICS4 4 ACT 2112 INTRODUCTORY ACCOUNTING 4 7 ECN 3005 PRINCIPLES OF MACROECONOMICS3 9 ECN 3104 MICROECONOMI 11 3 10 ECN 3105 MACROECONOMICS 1 3 14 ECN 3111 HISTORY OF ECONOMICS THOUGHT3 21 ACT 3211 FINANCIAL MANAGEMENT 3 22 ACT 4211 CORPORATE FINANCE 3 23 ECN 3003PRINCIPLES OF MICROECONOMICS3OPERASI PERKHIDMATAN SOKONGANPUTRA INTERNATIONAL (INTERNATIONAL DIVISION)Kod Dokumen: OPR/BA/BR02/TransferAPPLICATION FORM FOR TRANSFER OF CREDIT BETWEEN INSTITUTIONS(INBOUND)NO. SEMAKAN : 00Date: XX th XXXX 5Nur Maisarah Roslan (Mrs)Administrative OfficerInternational DivisionBangunan C11, Lorong Pongamia 1Universiti Putra Malaysia43400 UPM Serdang, Selangor Darul EhsanMalaysiaDear Nur Maisarah:This is to certify that Miss XX will be participating in the student exchange program at Universiti Putra Malaysia. The details are as follow:1 Name : CHEN HUI2 Country : China: From XXX 6 till XXXX 63 Date of ExchangeProgramme4 Place of Exchange at UPM : F aculty of Modern Language and CommunicationPlease don’t hesitate to contact me if you do have any inquiry.Sincerely,XXXXNO. SEMAKAN : 00NO. SEMAKAN : 00NO. SEMAKAN : 00NO. SEMAKAN : 00。

ASVS Item #RequirementV2.1Verify all pages and resources require authentication except those specifically intended to be public (Principle of complete mediation).V2.2Verify all password fields do not echo the user’s password when it is entered.V2.4Verify all authentication controls are enforced on the server side.V2.5Verify all authentication controls (including libraries that call external authentication services) have a centralized implementation.V2.6Verify all authentication controls fail securely to ensure attackers cannot log in.V2.7Verify password entry fields allow or encourage the use of passphrases, and do not prevent long passphrases or highly complex passwords being entered, and provide a sufficient minimum strength to protect against the use of commonly chosen passwords.V2.8Verify all account identity authentication functions (such as registration, update profile, forgot username, forgot password, disabled / lost token, help desk or IVR) that might regain access to the account are at least as resistant to attack as the primary authentication mechanism.V2.9Verify users can safely change their credentials using a mechanism that is at least as resistant to attack as the primary authentication mechanism.V2.12Verify that all authentication decisions are logged. This should include requests with missing required information, needed for security investigations.V2.13salted using a salt that is unique to that account (e.g., internal user ID, account creation) and use bcrypt, scrypt or PBKDF2 before storing the password.V2.16Verify that credentials, and all other identity information handled by the application(s), do not traverse unencrypted or weakly encrypted links.V2.17Verify that the forgotten password function and other recovery paths do not reveal the current password and that the new password is not sent in clear text to the user.V2.18Verify that username enumeration is not possible via login, password reset, or forgot account functionality.V2.19Verify there are no default passwords in use for the application framework or any components used by the application (such as “admin/password”).V2.20Verify that a resource governor is in place to protect against vertical (a single account tested against all possible passwords) and horizontal brute forcing (all accounts tested with the same password e.g. “Password1”). A correct credential entry should incur no delay. Both these governor mechanisms should be active simultaneously to protect against diagonal and distributed attacks.V2.21Verify that all authentication credentials for accessing services external to the application are encrypted and stored in a protected location (not in source code).V2.22other recovery paths send a link including a time-limited activation token rather than the password itself. Additional authentication based on soft-tokens (e.g. SMS token, native mobile applications, etc.) can be required as well before the link is sent over.V2.23Verify that forgot password functionality does not lock or otherwise disable the account until after the user has successfully changed their password. This is to prevent valid users from being locked out.V2.24Verify that there are no shared knowledge questions/answers (so called "secret" questions and answers).V2.25Verify that the system can be configured to disallow the use of a configurable number of previous passwords.V2.26Verify re-authentication, step up or adaptive authentication, SMS or other two factor authentication, or transaction signing is required before any application-specific sensitive operations are permitted as per the risk profile of the application.V3.1Verify that the framework’s default session management control implementation is used by the application.V3.2Verify that sessions are invalidated when the user logs out.V3.3Verify that sessions timeout after a specified period of inactivity.V3.4Verify that sessions timeout after an administratively-configurable maximum time period regardless of activity (an absolute timeout).V3.5Verify that all pages that require authentication to access them have logout links.V3.6Verify that the session id is never disclosed other than in cookie headers; particularly in URLs, error messages, or logs. This includes verifying that the application does not support URL rewriting of session cookies.V3.7Verify that the session id is changed on login to prevent session fixation.V3.8Verify that the session id is changed upon re-authentication.V3.10Verify that only session ids generated by the application framework are recognized as valid by the application.V3.11Verify that authenticated session tokens are sufficiently long and random to withstand session guessing attacks.V3.12Verify that authenticated session tokens using cookies have their path set to an appropriately restrictive value for that site. The domain cookie attribute restriction should not be set unless for a business requirement, such as single sign on.V3.14Verify that authenticated session tokens using cookies sent via HTTP, are protected by the use of "HttpOnly".V3.15Verify that authenticated session tokens using cookies are protected with the "secure" attribute and a strict transport security header (such as Strict-Transport-Security: max-age=60000; includeSubDomains) are present.V3.16Verify that the application does not permit duplicate concurrent user sessions, originating from different machines.V4.1Verify that users can only access secured functions or services for which they possess specific authorization.V4.2Verify that users can only access secured URLs for which they possess specific authorization.V4.3Verify that users can only access secured data files for which they possess specific authorization.V4.4Verify that direct object references are protected, such that only authorized objects or data are accessible to each user (for example, protect against direct object reference tampering).V4.5Verify that directory browsing is disabled unless deliberately desired.V4.8Verify that access controls fail securely.V4.9Verify that the same access control rules implied by the presentation layer are enforced on the server side for that user role, such that controls and parameters cannot be re-enabled or re-added from higher privilege users.V4.10Verify that all user and data attributes and policy information used by access controls cannot be manipulated by end users unless specifically authorized.V4.11Verify that all access controls are enforced on the server side.V4.12Verify that there is a centralized mechanism (including libraries that call external authorization services) for protecting access to each type of protected resource.V4.14Verify that all access control decisions are be logged and all failed decisions are logged.V4.16Verify that the application or framework generates strong random anti-CSRF tokens unique to the user as part of all high value transactions or accessing sensitive data, and that the application verifies the presence of this token with the proper value for the current user when processing these requests.V4.17Aggregate access control protection – verify the system can protect against aggregate or continuous access of secured functions, resources, or data. For example, possibly by the use of a resource governor to limit the number of edits per hour or to prevent the entire database from being scraped by an individual user.V5.1Verify that the runtime environment is not susceptible to buffer overflows, or that security controls prevent buffer overflows.V5.3Verify that all input validation failures result in input rejection.V5.4Verify that a character set, such as UTF-8, is specified for all sources of input.V5.5Verify that all input validation or encoding routines are performed and enforced on the server side.V5.6Verify that a single input validation control is used by the application for each type of data that is accepted.V5.7Verify that all input validation failures are logged.V5.8Verify that all input data is canonicalized for all downstream decoders or interpreters prior to validation.V5.10Verify that the runtime environment is not susceptible to SQL Injection, or that security controls prevent SQL Injection.V5.11Verify that the runtime environment is not susceptible to LDAP Injection, or that security controls prevent LDAP Injection.V5.12Verify that the runtime environment is not susceptible to OS Command Injection, or that security controls prevent OS Command Injection.V5.13Verify that the runtime environment is not susceptible to XML External Entity attacks or that security controls prevents XML External Entity attacks.V5.14Verify that the runtime environment is not susceptible to XML Injections or that security controls prevents XML Injections.V5.16Verify that all untrusted data that are output to HTML (including HTML elements, HTML attributes, JavaScript data values, CSS blocks, and URI attributes) are properly escaped for the applicable context.V5.17If the application framework allows automatic mass parameter assignment (also called automatic variable binding) from the inbound request to a model, verify that security sensitive fields such as “accountBalance”, “role” or “password” are protected from malicious automatic binding.V5.18Verify that the application has defenses against HTTP parameter pollution attacks, particularly if the application framework makes no distinction about the source of request parameters (GET, POST, cookies, headers, environment, etc.)V5.19Verify that for each type of output encoding/escaping performed by the application, there is a single security control for that type of output for the intended destination.V7.1Verify that all cryptographic functions used to protect secrets from the application user are implemented server side.V7.2Verify that all cryptographic modules fail securely.V7.3Verify that access to any master secret(s) is protected from unauthorized access (A master secret is an application credential stored as plaintext on disk that is used to protect access to security configuration information).V7.6Verify that all random numbers, random file names, random GUIDs, and random strings are generated using the cryptographic module’s approved random number generator when these random values are intended to be unguessable by an attacker.V7.7Verify that cryptographic modules used by the application have been validated against FIPS 140-2 or an equivalent standard.V7.8Verify that cryptographic modules operate in their approved mode according to their published security policies.V7.9Verify that there is an explicit policy for how cryptographic keys are managed (e.g., generated, distributed, revoked, expired). Verify that this policy is properly enforced.V8.1Verify that the application does not output error messages or stack traces containing sensitive datathat could assist an attacker, including session id and personal information.V8.2Verify that all error handling is performed on trusted devicesV8.3Verify that all logging controls are implemented on the server.V8.4Verify that error handling logic in security controls denies access by default.V8.5Verify security logging controls provide the ability to log both success and failure events that are identified as security-relevant.V8.6Verify that each log event includes: a timestamp from a reliablesource,severity level of the event, an indication that this is asecurity relevant event (if mixed with other logs), the identity of the user that caused the event (if there is a user associated with the event), the source IP address of the request associated with the event, whether the event succeeded or failed, and a description of the event.V8.7Verify that all events that include untrusted data will not execute as code in the intended log viewing software.V8.8Verify that security logs are protected from unauthorized access and modification.V8.9Verify that there is a single application-level logging implementation that isused by the software.V8.10Verify that the application does not log application-specific sensitive data that could assist an attacker, including user’s sessionidentifiers and personal orsensitive information. The length and existence of sensitive data can be logged.V8.11Verify that a log analysis tool is available which allows the analyst to search for log events based on combinations of search criteria across all fields in the log record format supported by this system.V8.13Verify that all non-printable symbols and field separators are properly encoded in log entries, to prevent log injection.V8.14Verify that log fields from trusted and untrusted sources are distinguishable in log entries.V8.15Verify that logging is performed before executing the transaction. If logging was unsuccessful (e.g. disk full, insufficient permissions) the application fails safe. This is for when integrity and non-repudiation are a must.V9.1Verify that all forms containing sensitive information have disabled client side caching, including autocomplete features.V9.2Verify that the list of sensitive data processed by this application is identified, and that there is an explicit policy for how access to this data must be controlled, and when this data must be encrypted (both at rest and in transit). Verify that this policy is properly enforced.V9.3Verify that all sensitive data is sent to the server in the HTTP message body (i.e., URL parameters are never used to send sensitive data).V9.4Verify that all cached or temporary copies of sensitive data sent to the client are protected from unauthorized access orpurged/invalidated after the authorized user accesses the sensitive data (e.g., the proper no-cache and no-store Cache-Control headers are set).V9.5Verify that all cached or temporary copies of sensitive data stored on the server are protected from unauthorized access orpurged/invalidated after the authorized user accesses the sensitive data.V9.6Verify that there is a method to remove each type of sensitive data from the application at the end of its required retention period.V9.7Verify the application minimizes the number of parameters sent to untrusted systems, such as hidden fields, Ajax variables, cookies and header values.V9.8Verify the application has theability to detect and alert on abnormal numbers of requests for information or processing high value transactions for that user role, such as screen scraping, automated use of web service extraction, or data loss prevention. For example, the average user should not be able to access more than 5 records per hour or 30 records per day, or add 10 friends to a social network per minute.V10.1Verify that a path can be built from a trusted CA to each Transport Layer Security (TLS) server certificate, and that each server certificate is valid.V10.2Verify that failed TLS connections do not fall back to an insecure HTTP connection.V10.3Verify that TLS is used for all connections (including both external and backend connections) that are authenticated or that involve sensitive data or functions.V10.4Verify that backend TLS connection failures are logged.V10.5Verify that certificate paths are built and verified for all client certificates using configured trust anchors and revocation information.V10.6Verify that all connections to external systems that involve sensitive information or functions are authenticated.V10.7Verify that all connections to external systems that involve sensitive information or functions use an account that has been set up to have the minimum privileges necessary for the application to function properly.V10.8Verify that there is a single standard TLS implementation that is used by the application that is configured to operate in an approved mode of operation (See/groups/STM/cmvp /documents/fips140-2/FIPS1402IG.pdf ).V10.9Verify that specific character encodings are defined for all connections (e.g., UTF-8).V11.2Verify that the application accepts only a defined set of HTTP request methods, such as GET and POST and unused methods are explicitly blocked.V11.3Verify that every HTTP response contains a content type header specifying a safe character set (e.g., UTF-8).V11.6Verify that HTTP headers in both requests and responses contain only printable ASCII characters.V11.8Verify that HTTP headers and / or other mechanisms for older browsers have been included to protect against clickjacking attacks.V11.9Verify that HTTP headers added by a frontend (such as X-Real-IP), and used by the application, cannot be spoofed by the end user.V11.10Verify that the HTTP header, X-Frame-Options is in use for sites where content should not be viewed in a 3rd-party X-Frame. A common middle ground is to send SAMEORIGIN, meaning only websites of the same origin may frame it.V11.12Verify that the HTTP headers do not expose detailed version information of system components.V13.1Verify that no malicious code is in any code that was either developed or modified in order to create the application.V13.2Verify that the integrity of interpreted code, libraries, executables, and configuration files is verified using checksums or hashes.V13.3Verify that all code implementing or using authentication controls is not affected by any malicious code.V13.4Verify that all code implementing or using session management controls is not affected by any malicious code.V13.5Verify that all code implementing or using access controls is not affected by any malicious code.V13.6Verify that all input validation controls are not affected by any malicious code.V13.7Verify that all code implementing or using output validation controls is not affected by any malicious code.V13.8Verify that all code supporting or using a cryptographic module is not affected by any malicious code.V13.9Verify that all code implementing or using error handling and logging controls is not affected by any malicious code.V13.10Verify all malicious activity is adequately sandboxed.V13.11Verify that sensitive data is rapidly sanitized from memory as soon as it is no longer needed and handled in accordance to functions and techniques supported by the framework/library/operating system.V15.1Verify the application processes or verifies all high value business logic flows in a trusted environment, such as on a protected and monitored server.V15.2allow spoofed high value transactions, such as allowing Attacker User A to process a transaction as Victim User B by tampering with or replaying session, transaction state, transaction or user IDs.V15.3Verify the application does not allow high value business logic parameters to be tampered with, such as (but not limited to): price, interest, discounts, PII, balances, stock IDs, etc.V15.4Verify the application has defensive measures to protect against repudiation attacks, such as verifiable and protected transaction logs, audit trails or system logs, and in highest value systems real time monitoring of user activities and transactions for anomalies.V15.5Verify the application protects against information disclosure attacks, such as direct object reference, tampering, session brute force or other attacks.V15.6Verify the application hassufficient detection and governor controls to protect against brute force (such as continuously using a particular function) or denial of service attacks.V15.7Verify the application hassufficient access controls to prevent elevation of privilege attacks, such as allowing anonymous users from accessing secured data or secured functions, or allowing users to access each other’s details or using privileged functions.V15.8process business logic flows in sequential step order, with all steps being processed in realistic human time, and not process out of order, skipped steps, process steps from another user, or too quickly submitted transactions.V15.9Verify the application hasadditional authorization (such as step up or adaptive authentication) for lower value systems, and / or segregation of duties for high value applications to enforce anti-fraud controls as per the risk of application and past fraud.V15.10Verify the application has business limits and enforces them in atrusted location (as on a protected server) on a per user, per day or daily basis, with configurable alerting and automated reactions to automated or unusual attack. Examples include (but not limited to): ensuring new SIM users don’t exceed $10 per day for a new phone account, a forum allowing more than 100 new users per day or preventing posts or private messages until the account has been verified, a health system should not allow a single doctor to access more patient records than they can reasonably treat in a day, or a small business finance system allowing more than 20 invoice payments or $1000 per day across all users. In all cases, the business limits and totals should be reasonable for the business concerned. The only unreasonable outcome is if there are no business limits, alerting or enforcement.V16.1Verify that URL redirects and forwards do not include unvalidated data.V16.2Verify that file names and path data obtained from untrusted sources is canonicalized to eliminate path traversal attacks.V16.3Verify that files obtained from untrusted sources are scanned by antivirus scanners to prevent upload of known malicious content.V16.4Verify that parameters obtained from untrusted sources are not used in manipulating filenames, pathnames or any file system object without first being canonicalized and input validated to prevent local file inclusion attacks.V16.5Verify that parameters obtained from untrusted sources are canonicalized, input validated, and output encoded to prevent remote file inclusion attacks, particularly where input could be executed, such as header, source, or template inclusionV16.6Verify remote IFRAMEs and HTML5 cross-domain resource sharing does not allow inclusion of arbitrary remote content.V16.7Verify that files obtained from untrusted sources are stored outside the webroot.V16.8Verify that web or application server is configured by default to deny access to remote resources or systems outside the web or application server.V16.9Verify the application code does not execute uploaded data obtained from untrusted sources.V16.10Verify if Flash, Silverlight or other rich internet application (RIA) cross domain resource sharing configuration is configured to prevent unauthenticated or unauthorized remote access.V17.1Verify that the client validates SSL certificatesV17.2Verify that unique device ID (UDID) values are not used as security controls.V17.3Verify that the mobile app does not store sensitive data onto shared resources on the device (e.g. SD card or shared folders)V17.4Verify that sensitive data is not stored in SQLite database on the device.V17.5Verify that secret keys or passwords are not hard-coded in the executable.V17.6Verify that the mobile app prevents leaking of sensitive data via auto-snapshot feature of iOS.V17.7Verify that the app cannot be run on a jailbroken or rooted device.V17.8Verify that the session timeout is of a reasonable value.V17.9Verify the permissions being requested as well as the resources that it is authorized to access (i.e. AndroidManifest.xml, iOS Entitlements) .V17.10Verify that crash logs do not contain sensitive data.V17.11Verify that the application binary has been obfuscated.V17.12Verify that all test data has been removed from the app container (.ipa, .apk, .bar).V17.13Verify that the application does not log sensitive data to the system log or filesystem.V17.14Verify that the application does not enable autocomplete for sensitive text input fields, such as passwords, personal information or credit cards.V17.15Verify that the mobile app implements certificate pinning to prevent the proxying of app traffic.V17.16Verify no misconfigurations are present in the configuration files (Debugging flags set, world readable/writable permissions) and that, by default, configuration settings are set to theirsafest/most secure value.V17.17Verify any 3rd-party libraries in use are up to date, contain no known vulnerabilities.V17.18Verify that web data, such as HTTPS traffic, is not cached.V17.19Verify that the query string is not used for sensitive data. Instead, a POST request via SSL should be used with a CSRF token.V17.20Verify that, if applicable, any personal account numbers are truncated prior to storing on the device.V17.21Verify that the application makes use of Address Space Layout Randomization (ASLR).V17.22Verify that data logged via the keyboard (iOS) does not contain credentials, financial information or other sensitive data.V17.23If an Android app, verify that the app does not create files with permissions of MODE_WORLD_READABLE or MODE_WORLD_WRITABLEV17.24Verify that sensitive data is stored in a cryptographically secure manner (even when stored in the iOS keychain).V17.25Verify that anti-debugging and reverse engineering mechanisms are implemented in the app.V17.26Verify that the app does not export sensitive activities, intents, content providers etc. on Android.V17.27Verify that mutable structures have been used for sensitive strings such as account numbers and are overwritten when not used. (Mitigate damage from memory analysis attacks).V17.28Verify that any exposed intents, content providers and broadcast receivers perform full data validation on input (Android).需求Level 1Level 2验证所有页面和资源要求除了那些专门旨在成为公共的Y Y(完整的调解原则)认证。

CommcommanderProduct Update Bulletin version 2.1.2revised 10/12/09CommcommanderVersion 2.1.2October 2009Copyright © 2009, Oracle. All rights reserved.The Programs (which include both the software and documentation) contain proprietary information; they are provided under a license agreement containing restrictions on use and disclosure and are also protected by copyright, patent, and other intellectual and industrial property laws. Reverse engineering, disassembly, or decompilation of the Programs, except to the extent required to obtain interoperability with other independently created software or as specified by law, is prohibited.The information contained in this document is subject to change without notice. If you find any problems in the documentation, please report them to us in writing. This document is not warranted to be error-free. Except as may be expressly permitted in your license agreement for these Programs, no part of these Programs may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose.If the Programs are delivered to the United States Government or anyone licensing or using the Programs on behalf of the United States Government, the following notice is applicable:U.S. GOVERNMENT RIGHTSPrograms, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the Programs, including documentation and technical data, shall be subject to the licensing restrictions set forth in the applicable Oracle license agreement, and, to the extent applicable, the additional rights set forth in FAR 52.227-19, Commercial Computer Software--Restricted Rights (June 1987). Oracle USA, Inc., 500 Oracle Parkway, Redwood City, CA 94065.The Programs are not intended for use in any nuclear, aviation, mass transit, medical, or other inherently dangerous applications. It shall be the licensee's responsibility to take all appropriate fail-safe, backup, redundancy and other measures to ensure the safe use of such applications if the Programs are used for such purposes, and we disclaim liability for any damages caused by such use of the Programs.The Programs may provide links to Web sites and access to content, products, and services from third parties. Oracle is not responsible for the availability of, or any content provided on, third-party Web sites. You bear all risks associated with the use of such content. If you choose to purchase any products or services from a third party, the relationship is directly between you and the third party. Oracle is not responsible for: (a) the quality of third-party products or services; or (b) fulfilling any of the terms of the agreement with the third party, including delivery of products or services and warranty obligations related to purchased products or services. Oracle is not responsible for any loss or damage of any sort that you may incur from dealing with any third party.Oracle, JD Edwards, and PeopleSoft are registered trademarks of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners.THIRD PARTY SOFTWARE NOTICESThis product includes software developed by the Apache Software Foundation (/).THIS SOFTWARE IS PROVIDED "AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE APACHE SOFTWARE FOUNDATION OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.Contents of this Product BulletinOracle is pleased to announce the general availability of Commcommander version 2.1.2 asof October 12, 2009. Commcommander is a general-purpose communications program foryour IBM MVS host and Microsoft Windows or IBM AIX servers.Please use these links to navigate the document:“Overview” on page 1“Features & Enhancements” on page 2“Fixed Trouble Tickets” on page 3“Product Documentation” on page 4“Product Ordering Instructions” on page 4OverviewCommcommander uploads data from the PC to the mainframe and downloads data from themainframe to the PC using its own inbound and outbound message handlers.Commcommander comprises the following three components:Commcommander Servers—provide Docucorp products with client/servercommunications across multiple platforms, using either TCP/IP or Advanced Program toProgram Communication (APPC). You must install one Server for the mainframe host(IBM OS/390 or z/OS) and one for the PC (Windows NT/ 2000 or IBM AIX).Commcommander Drivers—provide specific program interfaces, giving you access to specific program capabilities. The Commcommander Drivers require CommcommanderServers, and the following three Drivers are available:Commcommander VLAM™ Driver—lets you manipulate VLAM (Virtual Library Access Method™) Library members between platforms. The Commcommander VLAMDriver is required if you're using the VLAMcommander GUI interface component.Commcommander JES Driver—uploads Metacode and AFP print data streams from the PC to mainframe-attached printers.Commcommander VRF Driver—downloads and uploads mainframe VRFs (Variable Replacement Files) to and from Documerge, Documaker fp, and DocumakerWorkstation fp.Other drivers will be added as the Commcommander architecture is expanded for futureproduct functionality.VLAMcommander for Windows—is the GUI interface for transferring files to and from the mainframe VLAM libraries to the PC. If you use the VLAMcommander component, theCommcommander Servers and the Commcommander VLAM Driver are required.Features & EnhancementsCommcommander 2.1 Level 2Distribution and PackagingCommcommander, including its Servers and Drivers, has been repackaged and isdistributed on a single installation media for each operating system platform (excluding themainframe.) The IBM MVS platform has three installation media components:1.) All the Commcommander Servers and Drivers2.) Associated JCL3.) SOURCE installation datasets.N OTEThe IBM MVS installation media are in TRANSMIT/RECEIVE format. Use TSORECEIVE to install the components onto your system. Refer to the Commcommander2.1 users guide for setup and usage instructions.Compatibility Considerations (required or supported versions)Commcommander 2.1 Level 2 is at the same level as Commcommander 2.1 Level 1, with theaddition of a much simpler delivery package and installation procedure.Fixed Trouble TicketsCommcommander 2.1 Level 2The following Trouble Tickets were upgraded or corrected for this version ofCommcommander:APAR ExplanationTT15619CCSNDPRT/CCRCVPRT - Modified to gracefully handle records greater than 8205.TT11265DFCVLAM - Modified to release dynamic VLAM resources when they are no longer in use.TT11374CCRCVPRT - Modified to capture the application log in correct directory folder.TT12700DFCVLAM - Modified to correct erroneous ‘LIBLIST’ error.TT11877ISIJESO/ISIVRFO – Modified code to respect the Prompt command before executing the DELETE queue entry command.TT11886VLMCMDR – Modified to correctly process Metacode and AFP print streams while processing the ‘DUMP’ command.n/a DFCVLAM - Modified to improve the execution of the DELMEM, DELCHAIN, and CHAINSIZ commands.n/a DFCVLAM – Performance enhancement - Modified to allow only oneconnection per mainframe task.Note: Each mainframe task can open and process multiple VLAM Librariesduring a conversation. After the conversation ends, all of the VLAM Librariesopen to that conversation will be closed.Product DocumentationThe following documentation has been updated for this version of Docuflex:Commcommander, Version 2.1.2Product Ordering InstructionsTo receive Commcommander 2.1.2, your organization mustBe a licensed user of Commcommander or VLAMcommanderBe current on Commcommander or VLAMcommander software maintenance feesIf you need assistance with OII, please log a Service Request using My Oracle Support atAddress any additional inquiries to:Oracle CorporationWorld Headquarters500 Oracle ParkwayRedwood Shores, CA 94065U.S.A.Worldwide Inquiries:Phone: +1.650.506.7000Fax: +1.650.506.7200。

[disclaimer: work in progress still]APF (Advanced Policy Firewall) - 0.9.6 [apf@]Copyright (C) 1999-2007, R-fx Networks <proj@>Copyright (C) 2007, Ryan MacDonald <ryan@>This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License as published bythe Free Software Foundation; either version 2 of the License, or(at your option) any later version.This program is distributed in the hope that it will be useful,but WITHOUT ANY WARRANTY; without even the implied warranty ofMERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See theGNU General Public License for more details.You should have received a copy of the GNU General Public Licensealong with this program; if not, write to the Free SoftwareFoundation, Inc., 59 Temple Place, Suite 330, Boston, MA 02111-1307 USA Contents:1 ............. Introduction1.1 ........... Introduction: Supported Systems & Requirements2 ............. Installation2.1 ........... Installation: Boot Loading3 ............. Configuration3.1 ........... Configuration: Basic Options3.2 ........... Configuration: Advanced Options3.3 ........... Configuration: Reactive Address Blocking3.4 ........... Configuration: Virtual Network Files3.5 ........... Configuration: Global Variables & Custom Rules4 ............. General Usage4.1 ........... General Usage: Trust System4.2 ........... General Usage: Global Trust System4.3 ........... General Usage: Advanced Trust Syntax4.4 ........... General Usage: Dynamic Trust Files5 ............. License6 ............. Support Information1) Introduction:Advanced Policy Firewall (APF) is an iptables(netfilter) based firewall system designed around the essential needs of today's Internet deployed servers and the unique needs of custom deployed Linux installations. The configuration of APFis designed to be very informative and present the user with an easy to followprocess, from top to bottom of the configuration file. The management of APF on a day-to-day basis is conducted from the command line with the 'apf' command, which includes detailed usage information and all the features one would expect from a current and forward thinking firewall solution.The technical side of APF is such that it embraces the latest stable featuresput forward by the iptables(netfilter) project to provide a very robust and powerful firewall. The filtering performed by APF is three fold:1) Static rule based policies (not to be confused with a "static firewall")2) Connection based stateful policies3) Sanity based policiesThe first, static rule based policies, is the most traditional method of firewalling. This is when the firewall has an unchanging set of instructions (rules) on how traffic should be handled in certain conditions. An example ofa static rule based policy would be when you allow/deny an address access to the server with the trust system or open a new port with conf.apf. So the short ofit is rules that infrequently or never change while the firewall is running.The second, connection based stateful policies, is a means to distinguish legitimate packets for different types of connections. Only packets matching a known connection will be allowed by the firewall; others will be rejected. An example of this would be FTP data transfers, in an older era of firewallingyou would have to define a complex set of static policies to allow FTA data transfers to flow without a problem. That is not so with stateful policies,the firewall can see that an address has established a connection to port 21then "relate" that address to the data transfer portion of the connection and dynamically alter the firewall to allow the traffic.The third, sanity based policies, is the ability of the firewall to matchvarious traffic patterns to known attack methods or scrutinize traffic to conform to Internet standards. An example of this would be when a would-be attacker attempts to forge the source IP address of data they are sending to you, APF can simply discard this traffic or optionally log it then discard it.To the same extent another example would be when a broken router on the Internet begins to relay malformed packets to you, APF can simply discard them or in other situations reply to the router and have it stop sending you new packets (TCP Reset).These three key filtering methods employed by APF are simply a generalization of how the firewall is constructed on a technical design level, there are agreat many more features in APF that can be put to use. For a detailed description of all APF features you should review the configuration file/etc/apf/conf.apf which has well outlined captions above all options. Below isa point form summary of most APF features for reference and review:- detailed and well commented configuration file- granular inbound and outbound network filtering- user id based outbound network filtering- application based network filtering- trust based rule files with an optional advanced syntax- global trust system where rules can be downloaded from a central management server- reactive address blocking (RAB), next generation in-line intrusion prevention - debug mode provided for testing new features and configuration setups- fast load feature that allows for 1000+ rules to load in under 1 second- inbound and outbound network interfaces can be independently configured- global tcp/udp port & icmp type filtering with multiple methods of executing filters (drop, reject, prohibit)- configurable policies for each ip on the system with convenience variables to import settings- packet flow rate limiting that prevents abuse on the most widely abusedprotocol, icmp- prerouting and postrouting rules for optimal network performance- block list support to ban networks exhibiting suspicious activity- spamhaus Don't Route Or Peer List support to ban known "hijacked zombie" IP blocks- any number of additional interfaces may be configured as firewalled(untrusted) or trusted (not firewalled)- additional firewalled interfaces can have there own unique firewall policiesapplied- intelligent route verification to prevent embarrassing configuration errors- advanced packet sanity checks to make sure traffic coming and going meets the strictest of standards- filter attacks such as fragmented UDP, port zero floods, stuffed routing,arp poisoning and more- configurable type of service options to dictate the priority of different typesof network traffic- intelligent default settings to meet every day server setups- dynamic configuration of your servers local DNS revolvers into the firewall- optional filtering of common p2p applications- optional filtering of private & reserved IP address space- optional implicit blocks of the ident service- configurable connection tracking settings to scale the firewall to the size ofyour network- configurable kernel hooks (ties) to harden the system further to syn-floodattacks & routing abuses- advanced network control such as explicit congestion notification and overflow- special chains that are aware of the state of FTP DATA and SSH connections to prevent client side issues- control over the rate of logged events, want only 30 filter events a minute? 300 a minute? - you are the boss- logging subsystem that allows for logging data to user space programs orstandard syslog files- logging that details every rule added and a comprehensive set of error checks to prevent config errors- if you are familiar with netfilter you can create your own rules in any ofthe policy files- pluggable and ready advanced use of QoS algorithms provided by the Linux - 3rd party add-on projects that compliment APF featuresStill on the feature todo list is:- full support for NAT/MASQ including port forwarding- cluster oriented round-robin packet or port forwarding- in-line firewall reactive address blocking of connction floods- and much more...1.1) Introduction: Supported Systems & RequirementsThe APF package is designed to run on Linux based operating systems that have an operational version of the iptables (netfilter) package installed. The iptables (netfilter) package is supported on Linux kernels 2.4 and above,you can find out more details on the netfilter project at:/If the version of Linux you are using already has an included copy ofiptables then chances are very high it has all the iptables modules that APFwill need. If you are configuring iptables in your own custom kernel then you should be sure that the following modules are compiled with the kernel for modular support:ip_tablesiptable_filteriptable_mangleip_conntrackip_conntrack_ircip_conntrack_ftpipt_stateipt_multiportipt_limitipt_recentipt_REJECTipt_ecnipt_lengthipt_macipt_multiportipt_owneript_stateipt_ttlipt_TOSipt_TCPMSSipt_ULOGIf you would like to make sure you support these modules then you can take a look inside of /lib/modules/kernelver/kernel/net/ipv4/netfilter/ directory.# ls /lib/modules/$(uname -r)/kernel/net/ipv4/netfilter/The known Linux platforms that APF will run on are very diverse and it is hard to keep track but here is a short summary:Redhat Enterprise AS/ES 2+CentOS AnyFedora Core AnySlackware 8.0+Debian GNU/Linux 3.0+Suse Linux 8.1+Unbuntu AnyTurboLinux Server 9+TurboLinux Fuji (Desktop)RedHat Linux 7.3,8,9The base system specs for APF operating as intended are not set in stone and you can easily scale the package into almost any situation that has a Linux2.4+ kernel, iptables and bash shell with standard set of gnu-utils (grep, awk, sed and the like). Below is a short table of what is recommended: DEVICE MIN RECOMMENDEDCPU: 300Mhz 600MhzMEM: 64MB 96MBDISK: OS OSNETWORK: Any Any2) InstallationThe installation setup of APF is very straight forward, there is an includedinstall.sh script that will perform all the tasks of installing APF for you.Begin Install:# sh install.shIf one so desires they may customize the setup of APF by editing the variables inside the install.sh script followed by also editing the path variables inthe conf.apf and internals.conf files. This is however not recommends and the default paths should meet all user needs, they are:Install Path: /etc/apfBin Path: /usr/local/sbin/apfThe package includes two convenience scripts, the first is importconf which will import all the variable settings from your previous version of APF into thenew installation. The second is get_ports, a script which will output thesystems currently in use 'server' ports for the user during the installationprocess in an effort to aid in configuring port settings.All previous versions of APF are saved upon the installation of newerversions and stored in /etc/apf.bkDDMMYY-UTIME format. In addition, there is a /etc/st sym-link created to the last version of APF you had installed.After installation is completed the documentation and convenience scripts are copied to /etc/apf/docs and /etc/apf/extras respective.2.1) Installation: Boot LoadingOn installation APF will install an init script to /etc/init.d/apfand configure it to load on boot. If you are setting up APF in a morecustom situation then you may follow the below instructions.There is really 3 modes of operation for having APF firewall our systemand each has no real benifit except tailoring itself to your needs.The first is to setup APF in the init system with chkconfig (done bydefault during install), as detailed below:chkconfig --add apfchkconfig --level 345 apf onSecondly, you can add the following string too the bottom of the/etc/rc.local file:sh -c "/etc/apf/apf -s" &It is NOT recommended that you use both of these startup methods together,for most systems the init script via chkconfig should be fine.The third and final approuch is to simply run APF in an on-demand fashion. That is, enable it with the 'apf -s' command when desired and disable it with the'apf -f' when desired.3) Configuration:On your first installation of APF it will come pretty bare in the way of preconfigured options, this is intentional. The most common issue with many firewalls is that they come configured with so many options that a user may never use or disable, that it leaves systems riddled with firewall holes.Now with that said, APF comes configured with only a single incoming port enabled by default and that is port 22 SSH. Along with a set of common practice filtering options preset in the most compatible fashion for all users. All thereal advanced options APF has to offer are by default disabled including outbound (egress) port filtering, reactive address blocking (rab) and thevirtual network subsystem to name a few.The main APF configuration file is located at /etc/apf/conf.apf and has detailed usage information above all configuration variables. The file uses integer based values for setting configuration options and they are0 = disabled1 = enabledAll configuration options use this integer value system unless otherwise indicated in the description of that option.You should put aside 5 minutes and review the configuration file from top to bottom taking the time to read all the captions for the options that are provided. This may seem like a daunting task but a firewall is only as goodas it is configured and that requires you, the administrator, to take a few minutes to understand what it is you are setting up.APF is a very powerful firewall that when setup to make use of all the advanced features, will provide a sophisticated and robust level of protection. Please continue reading further along this file for more information or see thesupport options at the bottom of this file for further assistance if you find yourself lost in the configuration process.3.1) Configuration: Basic OptionsThis section will cover some of the basic configuration options found insideof the conf.apf configuration file. These options, despite how basic, are the most vital in the proper operation of your firewall.Option: DEVEL_MODEDescription: This tells APF to run in a development mode which in short means that the firewall will shut itself off every 5 minutes from a cronjob. Whenyou install any version of APF, upgrade or new install, this feature is bydefault enabled to make sure the user does not lock themself out of thesystem with configuration errors. Once you are satisfied that you have the firewall configured and operating as intended then you must disable it. Option: INSTALL_PATHDescription: As it implies, this is the installation path for APF and unlessyou have become a brave surgeon it is unlikely you will ever need to reconfigure this option - on we go.Option: IFACE_IN & IFACE_OUTDescription: These variables instruct the firewall as to what interfaces youuse for main network communication, such as to the Internet. In most cases these variables are configured to the same values such as eth0 or ppp0. In a more technical capacity these variables control what the firewall considers as the untrusted network interfaces, those which are far beyond the reasonable realmof control of an administrator.Option: IFACE_TRUSTEDDescription: It is common that you may want to set a specific interface as trusted to be excluded from the firewall, these may be administrative private links, virtualized VPN interfaces or a local area network that is contains trusted resources. This feature is similar to what some term as demilitarized zone or DMZ for short, any interfaces set in this option will be excempt fromall firewall rules with an implicit trust rule set early in the firewall load. Option: SET_VERBOSEDescription: This option tells the apf script to print very detailed event logsto the screen as you are conducting firewall operations from the command line. This will allow for easier trouble shooting of firewall issues or to assist theuser in better understanding what the firewall is doing rule-by-rule. Although the SET_VERBOSE option is new to APF, this level of logging has long been provided in the /var/log/apf_log file and still remains as such.Option: SET_FASTLOADDescription: This tells APF to use a special feature to take saved snap shotsof the running firewall. Instead of regenerating every single firewall rulewhen we stop/start the firewall, APF will use these snap shots to "fast load"the rules in bulk. There are internal features in APF that will detect when configuration has changed and then expire the snap shot forcing a full reloadof the firewall.Option: SET_VNETDescription: The ever curious option called SET_VNET, to put it brief thisoption controls the virtual network subsystem of APF also known as VNET. Thisis a subsystem that generates policy files for all aliased addresses on theIFACE_IN/OUT interfaces. In general this option is not needed for the normal operation of APF but is provided should you want to easily configured unique policies for the aliased addresses on an Interface. Please see topic 3.4 ofthis document for more advanced details related to this option.Option: SET_ADDIFACEDescription: This allows you to have additional untrusted interfaces firewalledby APF and this is done through the VNET system. So for example let assume you have a datacenter provided eth2 interface for local network backups but youknow hundreds of other Internet facing servers are also on this network. Insuch a situation it would be the best course to enable this option (along withSET_VNET) so that the interface is firewalled. Please see topic 3.4 of this document for more advanced details related to this option.Option: IG_TCP_CPORTSDescription: This controls what TCP ports are allowed for incoming traffic, thisis also known as the "server" or "listening services" ports. You would forexample configure here the ports 21,25,80,110,443 if you were operating the FTP, SMTP, HTTP, POP3 & HTTPS services from this host. This is a global context rule and will apply to all addresses on this host unless virtual net rules areset to operate in another fashion.Option: IG_UDP_CPORTSDescription: This controls what UDP ports are allowed for incoming traffic, thisis also known as the "server" or "listening services" ports. You would forexample configure here the ports 20,53 if you were operating the FTP & DNS services from this host. This is a global context rule and will apply to all addresses on this host unless virtual net rules are set to operate in another fashion.Option: IG_ICMP_TYPESDescription: This controls what ICMP types are allowed for incoming traffic, these are control messages that the Internet uses to communicate any number of error messages during communication between hosts and networks. The default options should meet most needs however if you wish to filter a specific setof ICMP types you should review the 'internals/icmp.types' file. This is aglobal context rule and will apply to all addresses on this host unless virtualnet rules are set to operate in another fashion.Option: EGFDescription: This is a top level control feature for enabling or disabling allthe outbound (egress) filtering features of the firewall. In the most basicsetup of the firewall from install, this will be set to disabled and we will be operating in a mostly inbound (ingress) only filtering fashion. It is however recommended that you enable the outbound (egress) filtering as it provides a very robust level of protection and is a common practice to filtering outbound traffic.Option: EG_TCP_CPORTSDescription: This controls what TCP ports are allowed for outgoing traffic, thisis also known as the "client side" communication on a host. Here we would set any ports we wish to communicate with on the Internet, for example if you use many remote RSS feeds on websites then you will want to make sure port 80,443 is defined here so you can access the HTTP/HTTPS service on Internet servers. This is a global context rule and will apply to all addresses on this hostunless virtual net rules are set to operate in another fashion.Option: EG_UDP_CPORTSDescription: This controls what UDP ports are allowed for outgoing traffic, this is also known as the "client side" communication on a host. Here we would set any ports we wish to communicate with on the Internet, for example if you use many remote RSYNC servers then you will want to make sure port 873 is defined here so you can properly access the RSYNC service on Internet servers. This is a global context rule and will apply to all addresses on this host unlessvirtual net rules are set to operate in another fashion.Option: EG_ICMP_TYPESDescription: This controls what ICMP types are allowed for outgoing traffic, these are control messages that the Internet uses to communicate any number of error messages during communication between hosts and networks. The default options should meet most needs however if you wish to filter a specific setof ICMP types you should review the 'internals/icmp.types' file. This is aglobal context rule and will apply to all addresses on this host unless virtualnet rules are set to operate in another fashion.Option: LOG_DROPDescription: The use of this option allows to firewall to perform very detailed firewall logging of packets as they are filtered by the firewall. This can help identify issues with the firewall or provide insightful information on who is taking pokes at the host. Typically however this option is left disabled onproduction systems as it can get very noisy in the log files which also can increase i/o wait loads to the disk from the heavy logging.3.2) Configuration: Advanced OptionsThe advanced options, although not required, are those which afford the firewall the ability to be a more robust and encompassing solution in protecting a host. These options should be reviewed on a case-by-case basis and enabled only asyou determine there merit to meet a particular need on a host or network. Option: SET_MONOKERNDescription: This option tells the system that instead of looking for iptables modules, that we should expect them to be compiled directly into the kernel. So unless you have a custom compiled kernel on your system where modular support is disabled or iptables (netfilter) is compiled in directly, you should notenable this option. There are also exceptions here if you have a unique system setup and APF is unable to find certain iptables modules but you know for afact they are there, then enable this option.Option: VF_ROUTEDescription: This option will make sure that the IP addressess associated tothe IFACE_* variables do actually have route entries. If a route entry can notbe found then APF will not load as it is likely a configuration error has beenmade with possible results being a locked-up server.Option: VF_CRONDDescription: This option will make sure that the cron service is running whenthe DEVEL_MODE option is enabled. If the cron service is not found to be running then APF will not load as if there is a configuration error it is likely thatthe server will lock-up.Option: VF_LGATEDescription: This option will make sure that all traffic coming into this hostis going through this defined MAC address. This is not something you will want enabled in most situations but it is something certain people will desire with servers residing behind a NAT/MASQ gateway for example.Option: RABDescription: This is a top level toggle for the reactive address blocking inAPF and does nothing more than either enable or disable it.Option: RAB_SANITYDescription: This enables RAB for sanity violations, which is when an address breaks a strict conformity standard such as trying to spoof an address or modifypacket flags. When addresses are found to have made such violations they are temporarily banned for the duration of RAB_TIMER value in seconds. Option: RAB_PSCAN_LEVELDescription: This enables RAB for port scan violations, which is when an address attempts to connect to a port that has been classifed as malicious. These types of are those which are not commonly used in today's Internet but are the subject of scrutiny by attackers, such as ports 1,7,9,11. The values forthis option are broken into 4 intergers and they are 0 for disabled, 1 forlow security, 2 for medium security and 3 for high security.Option: RAB_HITCOUNTDescription: This controls the amount of violation hits an address must have before it is blocked. It is a good idea to keep this very low to preventevasive measures. The default is 0 or 1, meaning instant block on first hit. Option: RAB_TIMERDescription: This is the amount of time (in seconds) that an address gets blocked for if a violation is triggered, the default is 300s (5 minutes). This option has a max accepted value of 43200 seconds or 12 hours.Option: RAB_TRIPDescription: This allows RAB to 'trip' the block timer back to 0 seconds if an address attempts ANY subsiquent communication while still on the inital block period. This option really is one of the more exciting features of the RAB system as it can cut off an attack at the legs before it ever mounts into something tangible against the system.Option: RAB_LOG_HITDescription: This controls if the firewall should log all violation hits froman address. It is recommended that this be enabled to provide insightful log data on addresses which are attempting to probe or conduct questionable actions against this host. The use of LOG_DROP variable set to 1 will override this to force logging.Option: RAB_LOG_TRIPDescription: This controls if the firewall should log all subsiquent trafficfrom an address that is already blocked for a violation hit, this can generate allot of logs. However, the use of this option despite the depth of log data it may generate could provide valuble information as to the intents of an attacker. The use of LOG_DROP variable set to 1 will override this to force logging. Option: TCP_STOP, UDP_STOP, ALL_STOPDescription: These options tell the firewall in which way to go about filteringtraffic, the supported values are DROP, RESET, REJECT and PROHIBIT. We will review these options below in short and provide the pro/con's of their uses.- The default is DROP which tells the firewall silently discard packetsand not reply to them at all, which some consider to be "stealth" firewallbehavoir. The direct benifit is that it saves system resources, especially during a DoS attack in not having to reply to every discarded packet. However the problem is experienced attackers know the way TCP/IP works and it is such that when you try to connect to a service that is unavailable, your server orlocal router replies with an "icmp-port/host-unreachable" message. So when an attacker probing your IP address receives no reply from the server or localrouter to the scans, they will instantly know you are running a firewall,possibly peaking curiosity more.- Then we have RESET which allows the firewall to reply to discarded packetsin such a way that it trys to make the remote host "reset/terminate" theconnection attempts to you. This option is more in-line with TCP/IP standards however in most situations will provide no real benifits ordrawbacks. In some really isolated situations you may find that using RESET during DoS attacks will help terminate connections more promptly but ingeneral this does not serve to counter the system resources expended tosend back replies to every single packet filtered.- Then we have the REJECT value which is a more common alternative to DROP as it allows the firewall to reply to packets with an error message. Thisacomplishes the goal of filtering a packet while at the same time notallowing the remote host to know that we are running a firewall, they justthink the port/service is closed/unavailable.- Finally we have the PROHIBIT value which is specific for UDP_STOP but can be used as other *_STOP values with similar effect. When we set PROHIBIT we are telling the firewall to reply to the sender of packets with only ICMPerror messages instead of like the case with RESET, TCP packets. This is agood alternative to reply to packets with as it does not load the systemas "much" during aggressive attacks. This is also the default expectedreply for UDP packets that are not accepted by a host, however APF will bydefault use a DROP value on UDP packets.Option: PKT_SANITYDescription: This option controls the way packets are scrutinized as they flow through the firewall. The main PKT_SANITY option is a top level toggle for all SANITY options and provides general packet flag sanity as a pre-scrub for the other sanity options. In short, this makes sure that all packets coming andgoing conform to strict TCP/IP standards. In doing so we make it very difficult。

Synway CTI SeriesSHN-480C-CT/PCIeVoIP Media Processing & SignalingVersion 1.0Synway Information Engineering Co., LtdContentsContents (i)Copyright Declaration (ii)Revision History (iii)Chapter 1Overview (1)1.1Functions (1)1.2Features (2)1.3Operation Principle (3)Chapter 2Installation (4)2.1Hardware Structure (4)2.2System Requirements (4)2.3Installation Procedure (5)Appendix A Technical Specifications (8)Appendix B Technical/sales Support (9)Copyright DeclarationAll rights reserved; no part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, without prior written permission from Synway Information Engineering Co., Ltd (hereinafter referred to as ‘Synway’).Synway reserves all rights to modify this document without prior notice. Please contact Synway for the latest version of this document before placing an order.Synway has made every effort to ensure the accuracy of this document but does not guarantee the absence of errors. Moreover, Synway assumes no responsibility in obtaining permission and authorization of any third party patent, copyright or product involved in relation to the use of this document.Revision HistoryVersion Date CommentsInitial publicationVersion 1.0 2014-06Note: Please visit our website to obtain the latest version of this document.Chapter 1 OverviewThe Synway CTI Series SHN-480C-CT/PCIe is a large-capacity board for VoIP media processing and signaling, integrated with LAN interfaces. It uses a high-density integrated media gateway processor which can efficiently handle VoIP CODECs for up to 480 channels. This series board provides such services as encoding, transmitting, parsing and receiving SIP messages, managing on-board channels and IP conversations, sending and receiving voice data over IP links, putting encoded or decoded voice data onto CT-BUS, etc. It supports the following applications: IP gateway, media server/conference server, Softswitch, IP PBX, IP call center, IP application server, IVR, large-capacity IAD (Integrated Access Device), VoIP solutions, and NGN networking equipment.1.1 Functionsz A single board provides up to 480 channels for IP processing.z Supports the following functions during the call: voice recording and playing, volume adjustment, dynamic CODEC change, etc.z All channels are allowed to play and record voices simultaneously. Automatic Gain Control (AGC) support in recording operation.z Supports call transfer and call hold during IP calls.z Allows DTMF signal transmission and detection by any of the three methods: in-band, out-of-band (RFC2833), signaling (SIP-INFO).z Integrated with two independent 10/100/1000M compatible Ethernet interfaces, the board can work without costing or relying on the network card resource of the computer.z Includes H.100 bus, compatible with MVIP, SC and ST bus, facilitating smooth connectivity to third-party boards with H.100 bus for the transfer of voice data from/to other devices.z The flexible distributed conferencing system sets no limit on the number of simultaneous conferences and participants in each conference, allows monitoringand recording of the whole conference and each individual speaker.z Each board has a unique hardware serial number written in the firmware to distinguish itself from other boards and prevent piracy.z The on-board authorization code identification circuit is designed for software safety.Users can apply to our company for the authorization code.1.2 Featuresz PCIe Bus SupportDeveloped with the design of PCIe X1, this board supports PCIe X1, X2, X4, X8 andX16 slots.z DMA Read and WriteThe use of PCIe-based DMA technique for data reading and writing helps minimizethe cost of the host CPU.z Integrated LANThe board is integrated with two independent 10/100/1000M BASE-TX compatibleEthernet interfaces.z Network Protocol Processing in HardwareThanks to the powerful media gateway processor on the board, such networkprotocols as TCP/UDP, HTTP, ARP/RARP, DNS, NTP, TFTP, TELNET, STUN, etc.can be processed high efficiently without costing any host CPU.z Easy Firmware UpgradeUsers may upgrade the on-board firmware simply using a software tool to the latestversion published by Synway.z Multiple Programming Modes SupportOur driver supports three programming modes: polling mode, event callback modeand Windows message mode.z Various VoIP CODECs SupportThe supported VoIP CODECs include G.711 A-Law, G.711 µ-Law, G.729A/B, G.722,G.723.1, AMR, iLBC.z Barge inSupports the Barge-in feature.z Highly Efficient and Real-time Call Control and Voice ProcessingThis board enables highly efficient call control, call management and voice processing; the multiple on-board DSPs used for voice processing give a nearlyreal-time voice effect.z Synway’s Unified SynCTI Driver Development PlatformSynway owns the intellectual property rights for the unified high-intelligence SynCTIdriver development platform. By simple API function calls on this platform, users cancustomize such features as call connection and call control, and perform variousapplications based on IP+IP or IP+TDM. Our API interfaces are highly encapsulatedand exported in ANSI C style, which eliminates the need for users to consider thebottom layer IP communication details.1.3 Operation PrincipleFigure 1-1 Operation Principle of SHN-480C-CT/PCIeNote: As the firmware chips are loaded through Ethernet1 at the board startup, you shall make sure Ethernet1 is connected properly to the network cable; otherwise the board will fail to start.∑ ∑AGC TDM Bus SwitchSwitch and ConferenceInbound Voice ∑∑AGC Playback to BusAGCDecoderDTMF/ToneGenerator Encoder Echo Canceler Outbound VoiceRecording Buffer Playback BufferK1K3K4K5ToneDet DTMF Detector Host Computer Interface (PCIe) V1 V2VoIP Barge inDetector V3K6 K2ECEnhanceEthernet1 Ethernet2Chapter 2 Installation2.1 Hardware Structurez SHN-480C-CT/PCIe BoardFigure 2-1 Left & Front ViewsFigure 2-2 Rear View2.2 System RequirementsHost System RequirementsCPU: 1600MHz Intel® Pentium® DualCore or aboveMemory: 2G or moreHD: Depends on individual requirementsSupported Operating SystemsRefer to Section 1.4 SynCTI Supported OS in SynCTI Programmer’s Manual.pdf. 2.3 Installation ProcedureNote: Always turn off the power before installation!Step 1: Properly fit the required VoIP board into the PCIe slot on the PC chassis.Notes:① For the installation of other voice boards from Synway which are used with these VoIPboards, refer to corresponding hardware manuals.② Other necessary hardware devices (such as network card, IP phones and PBX) usedto set up a whole VoIP application environment should be installed by usersthemselves.Step 2: Connect H.100 bus interfaces on all boards by bus cable.Through CT-BUS, the VoIP board can easily exchange voice data with other voice boards used with it.Notes:①See Figure 2-3 for correct insertion. Do not twist or insert in the opposite direction.Figure 2-3 Connection of H.100 Bus②T he bus cable houses stiff conducting material. Therefore, when it has beenshaped, do not bend it repeatedly or violently lest it is broken.Step 3: Boot your computer and install the driver.Regarding driver installation, refer to SynCTI_InstManual.pdf.Step 4: Connect the network cableSHN-480C-CT/PCIe has two Kilomega Ethernet ports and provides many connection mehtods.Method 1 (recommended):Note: This method uses the two Ethernet ports on the board, Ethernet 1 connecting to the PC while Ethernet 2 connecting to the Router. Meanwhile, it requires more than one network interface on the PC.Method 2:Note: This method only uses Ethernet1 on the board. As the firmware chips are loaded through Ethernet1 at the board startup, the board will fail to start without connecting Ethernet1 with the network cable. That is, you shall ensure a proper connection of both Ethernet1 and a network interface on the PC to the PBX. Here we suggest you to use a PBX instead of a router. as the router may allocate incorrect IP addresses and cause the start failure of the board.Step 5: Configure the operating parameters for the VoIP boardRefer to SynCTI Programmer’s Manual for details.Key Tips:z In a normal situation, the board can start to work just after you insert it to the PCIe slot of the PC and boot up the PC. Only when the PCIe slot is in power shortageshould you connect the board to an external power or the HD power cable. If youcome across the board failure at startup, please contact our technicians for help. Donot connect the board with an external power supply or the HD power cable untilyou find the exact cause.z Since a single board will gradually heat up while being used, if two or more boards need to be inserted to a PC whose ventilation is not good, we suggest you spacethem by at least a PCI Express slot.z As the system is expected to run for long hours unmannedly, ‘energy-saving’ mode should be turned off for both the CPU and the HD in CMOS or WINDOWS operatingsystem. This is to ensure full-speed operation of the computer, or it may lead to adrop in performance or unexpected errors after running for some time.z A chassis installed with voice boards must be grounded for safety reasons, according to standard industry requirements. A simple way is earthing with the thirdpin on the plug. No or improper grounding may cause instability in operation as wellas decrease in lightning resistance.Appendix A Technical Specifications Dimensions Automatic reversal: Support(excluding L-bracket)312×111mm2 Recording/Playing FormatWeight A-Law, µ-Law, ADPCMMaximum System Capacity ≈ 215gEnvironment Theoretically up to 2 VoIP boards concurrentlyper systemOperating temperature: 0℃—55℃Audio CODECStorage temperature: -20℃—85℃G.711A, G.711U, G.729A/B, G.722, G.723.1,Humidity: 8%— 90% non-condensingAMR, iLBCStorage temperature: 8%— 90%Sampling Ratenon-condensing8kHzOn-board LANPower RequirementsInterfaces: 2 (10/100/1000M BASE-TX(RJ-45)) Maximum power consumption: ≤30WSelf-adaptive bandwidth: SupportAppendix B Technical/sales Support Thank you for choosing Synway. Please contact us should you have any inquiry regarding our products. We shall do our best to help you.HeadquartersSynway Information Engineering Co., Ltd/9F, Synway D&R Center, No.3756, Nanhuan Road, Binjiang District,Hangzhou, P.R.China, 310053Tel: +86-571-88860561Fax: +86-571-88850923Technical SupportTel: +86-571-88864579Mobile: +86-189********Email:techsupport@Email: techsupport@MSN: synway.support@Sales DepartmentTel: +86-571-88860561Tel: +86-571-88864579Fax: +86-571-88850923Email: sales@。
下面,咱们以SAP与SAP自概念数据传输的方式为例,向大伙儿说明如何利用IDOC。
本例中,咱们从一个系统(BI5CLNT202)将SFLIGHT的数据传输到另一个系统(BT3CLNT800)。
第一,从网上贴了下大体步骤,下面咱们依照那个步骤来操作:创建IDOC:第一步:WE31 创建IDOC所包含的字段.第二步:WE30 创建IDOC 把Segment分配给IDOC第三步:WE81 创建信息类型第四步:WE82 把IDOC类型与信息类型对应.第五步:WE57 Assign Message & Idoc Type to a Function Module for Process 第六步:SM59 Define a RFC connection for Idoc transfer第七步:WE21 Define a Port ( Assign a RFC destination which created in SM59 ) 第八步:WE41/42 Creat Process Code第九步:WE20 Define a Partner Profiles( Also creat a Outbound parameters with Port, or Inbound parameters with Process code )管理IDOC:WE02 显示IDOC,可以根据时间,IDOC类型查找IDOC,查看成功,出错信息。
WE46 IDOC管理(出\入)WE60 IDOC类型文档(可以查看IDOC结构,和每个字段的描述.WE19 根据IDOC号进行IDOC处理,可以修改IDOC值进行补发动作,处理分为内向和外向。
消息配置:WE20 配置伙伴消息进和出IDOC类型WE21 配置伙伴。
以下操作在发送方:1.创建IDOC类型的段(WE31)IDOC类型的字段,是组成MESSAGE的大体单位,咱们那个地址按关键值和非关键值分为2部份:ZSEG_FLY01ZSEG_FLY02:创建完成后,能够通过菜单:EDIT->Set Release来发布SEGMENT。