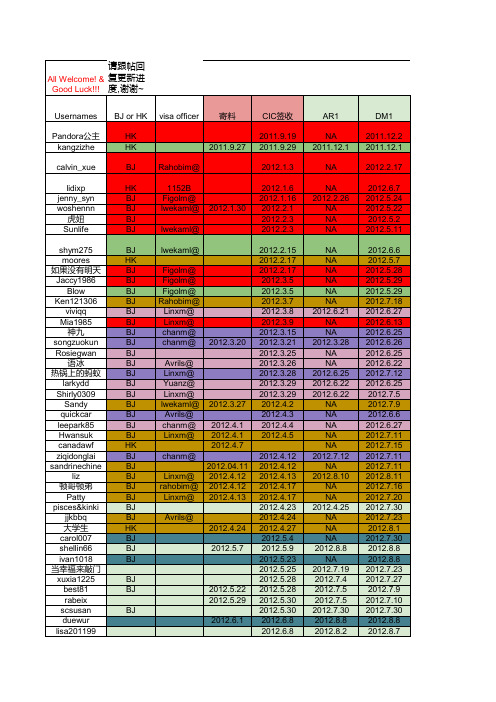
2012.8.6 cookie
- 格式:pdf
- 大小:62.00 KB
- 文档页数:3

2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
2014年水利水电工程施工技术标准有效版本目录
录
录
录
录
录
录
录
录
录
录
录
录
录
录
录
录
录
录
录
录
录
录。



HTTP State Management Specification13-DEC-2000Wireless Application ProtocolWAP-223-HTTPSM-20001213-a A list of errata and updates to this document is available from the WAP Forum™ Web site, /, in the form of SIN documents, which are subject to revision or removal without notice.© 2001, Wireless Application Forum, Ltd. All rights reserved.Terms and conditions of use are available from the WAP Forum™ Web site at/docs/copyright.htm.You may use this document or any part of the document for internal or educational purposes only, provided you do not modify, edit or take out of context the information in this document in any manner. You may not use this document in any other manner without the prior written permission of the WAP Forum™. The WAP Forum authorises you to copy this document, provided that you retain all copyright and other proprietary notices contained in the original materials on any copies of the materials and that you comply strictly with these terms. This copyright permission does not constitute an endorsement of the products or services offered by you.The WAP Forum™ assumes no responsibility for errors or omissions in this document. In no event shall the WAP Forum be liable for any special, indirect or consequential damages or any damages whatsoever arising out of or in connection with the use of this information.WAP Forum™ members have agreed to use reasonable endeavors to disclose in a timely manner to the WAP Forum the existence of all intellectual property rights (IPR's) essential to the present document. The members do not have an obligation to conduct IPR searches. This information is publicly available to members and non-members of the WAP Forum and may be found on the "WAP IPR Declarations" list at /xxxx. Essential IPR is available for license on the basis set out in the schedule to the WAP Forum Application Form.No representations or warranties (whether express or implied) are made by the WAP Forum™ or any WAP Forum member or its affiliates regarding any of the IPR's represented on this list, including but not limited to the accuracy, completeness, validity or relevance of the information or whether or not such rights are essential or non-essential.This document is available online in PDF format at /.Known problems associated with this document are published at /. Comments regarding this document can be submitted to the WAP Forum™ in the manner published at /.CONTENTS1.Scope (4)2.Document Status (5)2.1Copyright Notice (5)2.2Errata (5)2.3Comments (5)2.4Document Changes (5)2.5Document History (5)3.References (6)3.1Normative References (6)3.2Informative References (6)4.Definitions and Abbreviations (7)4.1Definitions (7)4.2Abbreviations (7)5.Overview (8)6.HTTP State Management Headers (8)6.1Cookie (8)6.2Set-Cookie (8)7.WAP Specific HTTP State Management Headers (9)7.1X-Wap-Proxy-Cookie (9)7.2X-Wap-Proxy-Set-Cookie (9)8.WAP Gateway Responsibilities (10)9.Cookie Proxy Responsibilities (10)9.1Pass Through Cookie Proxy (10)9.2Cookie Management And Storage (10)9.3Associating Cookie Storage With Clients (12)9.4Managing Proxy Cookies (12)er Agent Responsibilities (12)10.1HTTP State Management (12)10.2Cookie Proxy Management (12)11.Static Conformance Requirements (13)11.1User Agent Features (13)11.2Cookie Proxy Features (13)1. SCOPEWireless Application Protocol (WAP) is a result of continuous work by the WAP Forum to define an industry-wide specification for developing applications that operate over wireless communication networks. The scope of the WAP Forum is to define a set of specifications to be used by service applications for wireless communication devices. The wireless market is growing very quickly and reaching new customers and services. To enable operators and manufacturers to meet the challenges in advanced services, differentiation and fast/flexible service creation, WAP defines a set of protocols in transport, session and application layers. For additional information on the WAP architecture, refer to "Wireless Application Protocol Architecture Specification" [WAP].This specification defines the HTTP state management model for the WAP architecture. The WAP HTTP state management model is an implementation of the HTTP State Management Mechanism, also known as "cookie management", as defined in [RFC2109]. On the World Wide Web, the HTTP State Management mechanism stores state information in a file ("cookie") on the client, as defined in [RFC2109]. The same mechanism can also be used over the WAP protocols, as HTTP headers are used to convey all state and state manipulation information.Some WAP user agents may have motivation to store and manage cookies locally, as defined in [RFC2109]. This functionality follows precisely the current World Wide Web model, where cookies are typically stored and managed by regular web browsers.This specification defines an additional mechanism to let an intermediate proxy store and manage cookies on behalf of the WAP client, as an alternative to client-local storage and management. Storing cookies in the network has many advantages. WAP user agents may have a limited storing capacity. When cookies are stored in the proxy, they do not have to be transmitted across the air, for every request/response transaction. In case the user changes device, and cannot move the cookies from the old device to the new one, the user can still access the cookies in the proxy via the new device. On the other hand, storing and managing cookies in the client allows the user to gain the benefit of the same cookies independent of the access point used. This aspect becomes more important in the future in conjunction with WAP gateway roaming architecture. Some users may prefer storing private information in the client, instead of depending on the security of the network. Because both models are complementary, this specification defines a dual approach to WAP HTTP state management, while still maintaining full interoperability between the implementations and RFC2109.2. DOCUMENT STATUSThis document is available online in the following formats:• PDF format at /.2.1 Copyright Notice© Copyright Wireless Application Forum Ltd, 2000 all rights reserved.Terms and conditions of use are available from the Wireless Application Forum Ltd. web site at /docs/copyright.htm.2.2 ErrataKnown problems associated with this document are published at /.2.3 CommentsComments regarding this document can be submitted to the WAP Forum in the manner published at /.2.4 Document ChangesChange Request Title CommentsCR-WAP-223-HTTP-STATE-MGMT-NOKIA-20000913 Backward Compatibility toearlier releasesThese changes are as aresult of architecturalconsistency review of thedocument.CR-WAP-223-HTTP-STATE-MGMT-NOKIA-20001031 Clarifications from initial Architectural Consistency reviewCR-WAP-223-HTTP-STATE-MGMT-NOKIA-20001213 Editorial changes from closeout architectural consistency review2.5 Document HistoryDocument Name Date of ReleaseWAP-223-HTTPSM-20000530-d 30-MAY-2000 Draft accepted by WAGWAP-223-HTTPSM-20000922-d 22-SEP-2000 Draft submitted for proposedWAP-223-HTTPSM-20001213-d 13-DEC-2000 Reviewed For ArchitecturalConsistencyWAP-223-HTTPSM-20001213-p 24-JAN-2001 Proposed (No changes)WAP-223-HTTPSM-20001213-a Approved (No changes)3. REFERENCES3.1 Normative References[RFC2616] "Hypertext Transfer Protocol - HTTP/1.1", R. Fielding, et al., June 1999. URL: /rfc/rfc2616.txt[RFC2109] "HTTP State Management Mechanism", D. Kristol, et al, February 1997. URL: /rfc/rfc2109.txt[WAE] "Wireless Application Environment Specification", WAP Forum, 04-November-1999. URL: /3.2 Informative References[RFC2119] "Key words for use in RFC's to Indicate Requirement Levels", S. Bradner, March 1997. URL: /rfc/rfc2119.txt[WAP] "Wireless Application Protocol Architecture Specification", WAP Forum, 30-April-1998. URL: /[WSP] "Wireless Session Protocol", WAP Forum, 30-April-1998. URL:/4. DEFINITIONS AND ABBREVIATIONS4.1 DefinitionsThe following are terms and conventions used throughout this specification.The key words "MUST", "MUST NOT", "REQUIRED", "SHALL", "SHALL NOT", "SHOULD", "SHOULD NOT", "RECOMMENDED", "MAY" and "OPTIONAL" in this document are to be interpreted as described in [RFC2119].Client - a device (or application) that initiates a request for a connection with a server.Cookie Proxy - an intermediate program that acts as a user agent for the purpose of managing cookies and cookie storage on behalf of other user agents.Origin Server - the server, on which a given resource resides or is to be created, often referred to as a web server or an HTTP server. (also referred to as a "server" in this specification.)Proxy - an intermediate program that acts as both a server and a client for the purpose of making requests on behalf of other clients ([RFC2616]).Server - see "origin server".User - a person, who interacts with a user agent to view, hear or otherwise use a resource.User Agent - a user agent is any software or device that interprets WML, WMLScript or other content. This may include textual browsers, voice browsers and search engines.User Agent Session – a session which begins when user agent is activated and ends when it exits.4.2 AbbreviationsFor the purposes of this specification, the following abbreviations apply.HTTP Hypertext Transfer Protocol [RFC2616]RFC Request For CommentsURI Universal Resource IdentifierURL Universal Resource LocatorW3C World Wide Web ConsortiumWAE Wireless Application Environment [WAE]WAP Wireless Application Protocol [WAP]WSP Wireless Session Protocol [WSP]5. OVERVIEWThe HTTP State Management Mechanism is defined in [RFC2109]. In short, RFC2109 defines a means whereby an origin server can request that a small unit of state (a "cookie") is stored in the user agent, and included in subsequent requests to the origin server. A variety of controls are available to the origin server, allowing it to control when the "cookie" is included in subsequent requests, when the "cookie" expires as well as other state management and transport controls. As defined in [RFC2109], the user agent is responsible for cookie management. In this model, the WAP gateway conveys state information between the user agents and the origin servers. It is then the responsibility of the user agent to manage and store the cookies and to offer the user means for control over these functions.Although RFC2109 puts cookie management in the user agent, it may, in some cases be convenient to take advantage of an architecture, which enables network elements to manage and store cookies. The WAP HTTP State Management Architecture defines the concept of a Cookie Proxy. The cookie proxy is an HTTP proxy or proxy equivalent (e.g., WAP Gateway) that manages cookies on behalf of WAP user agents that do not implement the HTTP state function directly. The cookie proxy is responsible for managing and storing cookies on behalf of the user agents, and modifies HTTP requests and responses to and from the user agent to implement this function.This architecture supports clients with and without local cookie storage, and enables the user agent to control whether proxy cookie storage is enabled. In addition to this, WAP specific HTTP state management headers allow a simple synchronization scheme for user agent and proxy-based cookies. User agents can indicate if they rely on having cookies stored in the Cookie Proxy for a specific user agent session, and Cookie Proxy can notify the user agent if it has problems with their management.The cookie proxy operation has three stages:• Enabling or disabling the storage of cookies on the proxy. The user agent controls this function with an HTTP header.• Origin server request for a cookie to be stored for the duration of the user agent session or fora certain predefined period of time. This is performed via the HTTP Set-Cookie header, asspecified in [RFC2109].• Delivery of the cookie to the origin server in subsequent requests. This is performed via the HTTP Cookie header, as specified in [RFC2109].6. HTTP STATE MANAGEMENT HEADERS6.1 CookieCookie header is defined in [RFC2109].6.2 Set-CookieSet-Cookie header is defined in [RFC2109].7. WAP SPECIFIC HTTP STATE MANAGEMENT HEADERS7.1 X-Wap-Proxy-CookieThis header is sent in the request from the user agent to indicate whether the Cookie Proxy should store cookies from origin servers or not. X-Wap-Proxy-Cookie header is also used to send status information from user agent to the Cookie Proxy.x-wap-proxy-cookie = "X-Wap-Proxy-Cookie:" choicechoice = "cache" | "cache-has-state" | "delete" |"none" | "session" | "session-has-state" The choices are introduced briefly as follows:• When the value is "cache" or "cache-has-state", the Cookie Proxy caches cookies and sends them to the origin server on behalf of the user agent. Requests and responsesbetween the Cookie Proxy and the origin server include Cookie and Set-Cookieheaders, as they are defined in RFC2109. User agent appends cache-has-state value instead of cache in case it has received at least one X-Wap-Proxy-Set-Cookie header during the ongoing user agent session. This mechanism enables simple method forsynchronization between user agents and Cookie Proxy. On account of this informationCookie Proxy can e.g. detect if the user agent session based cookies from the previoususage time should be discarded.• When the value is "delete", the Cookie Proxy does not send any cookies to the origin server or store any received cookies. That is, the proxy acts as a filter ("cookie monster")and deletes all cookies before they are sent to the user agent.• If the header is not present, or has a value of "none", the proxy passes all HTTP cookie headers through between the user agent and the origin server without interception. In this document, a Cookie Proxy executing this function is known as a Pass-Through CookieProxy. This is the default condition.• When the value is "session", or "session-has-state", Cookie Proxy and user agent functionalities are combined. If Cookie Proxy receives a response containing a Set-Cookie header from the origin server, it decides the place for cookie storage according to the presence of the Max-Age attribute in the Set-Cooki e header. This method can beused to separate session-based cookies from long-lived ones. The difference betweensession and session-has-state values is similar to the difference between cacheand cache-has-state values, which is described above.Note that status of the session is bound to the user agent session, which begins when the user agent starts and ends when it exits. Status is not related to a certain cookie-derived session, but it simply tells if the user agent has cookies managed by the Cookie Proxy during a particular user agent session. The user agent session is not related to the concept of session defined in [WSP].7.2 X-Wap-Proxy-Set-CookieThis header is sent in the response to the user agent from the Cookie Proxy to indicate that one or more cookies were received in a response from an origin server and stored in the cookie proxyand/or at least one cookie was sent in the corresponding request. In addition to this, Cookie Proxy uses X-Wap-Proxy-Set-Cookie header to report an erroneous status to the user agents.x-wap-proxy-set-cookie = "X-Wap-Proxy-Set-Cookie: choice"choice = "state" | "error"The choices are introduced briefly as follows:• When value is "state", the user-agent is able to detect that a stateful session is in progress. Cookie Proxy sends this value in the response to the user agent when it receivesa Set-Cookie header from the origin server and chooses to manage the cookie. Thisheader is also sent when the Cookie Proxy has added a Cookie header in the relatedHTTP request.• When the value is "error", Cookie Proxy has detected a mismatch between the status of the user agent and the Cookie Proxy (i.e. Cookie Proxy has lost the cookies during aparticular user agent session).8. WAP GATEWAY RESPONSIBILITIESThe WAP gateway is responsible for delivering state management information between the user agent and the origin server. Header encoding for HTTP state management headers and WAP specific state management headers are defined in [WSP].9. COOKIE PROXY RESPONSIBILITIES9.1 Pass Through Cookie ProxyThe Cookie Proxy MUST implement Pass Through Cookie Proxy functionality, i.e. passing the HTTP headers between the user agent and the origin server without interference. If HTTP state management is not implemented in the client user agent, then the actions taken by the Cookie Proxy are undefined in this specification.9.2 Cookie Management And StorageThe Cookie Proxy MAY be responsible for managing and storing cookies on behalf of user agents. If this functionality is implemented, the X-Wap-Proxy-Cookie and X-Wap-Proxy-Set-Cookie headers MUST be used for communication between the client and the proxy. The proxy emulates user agent functionality when communicating with origin servers. User agent role in HTTP state management mechanism is defined in RFC2109.The user agent MAY control the cookie management in the Cookie Proxy with X-Wap-Proxy-Cookie header. The Cookie Proxy MUST enforce the following rules when receiving WAP specific HTTP headers from the client (precondition: Cookie Proxy has identified and authenticated the client and chosen to manage cookies on behalf of the user agents)1. If the choice in X-Wap-Proxy-Cookie header equals cache or cache-has-state,Cookie Proxy MUST cache cookies and send them to the origin server on behalf of the user agent. In addition to this, when Cookie Proxy receives X-Wap-Proxy-Cookie: cacheheader, it MUST discard all the current user agent session -based cookies (i.e. cookies which were sent from the origin server without Max-Age –attribute).2. If the choice in X-Wap-Proxy-Cookie header equals delete, Cookie Proxy MUST NOTsend cookies to the origin server or store any received cookies. In addition to this, CookieProxy MUST NOT send any received cookies to the client. Cookie Proxy MUST NOT delete any cookies stored prior to receiving the delete header.3. If the choice in X-Wap-Proxy-Cookie header equals none or the header is missing from therequest, Cookie Proxy MUST act as a Pass Through Cookie Proxy.4. If the choice in X-Wap-Proxy-Cookie header equals session or session-has-state,Cookie Proxy MUST include cookies in the requests to the origin servers. If the Cookie Proxy receives a response containing the Set-Cookie header from the origin server, it MUSTdecide the place for cookie storage according to the presence of the Max-Age attribute in the Set-Cooki e header. If Max-Age attribute is present, cookie MUST be transmitted to the user agent without interception. Otherwise it MUST be stored by the Cookie Proxy until it receivesa subsequent X-Wap-Proxy-Cookie: session (or X-Wap-Proxy-Cookie: cache)header from the user agent. Similarly to X-Wap-Proxy-Cookie: cache header, X-Wap-Proxy-Cookie: session effectively indicates that user agent does not have any cookies bound to the current user agent session and thus all stored cookies without Max-Age attribute MUST be discarded.The Cookie Proxy MUST NOT perform any cookie management, including storage or filtering, without the receipt of an X-Wap-Proxy-Cookie: cache, X-Wap-Proxy-Cookie: cache-has-state,X-Wap-Proxy-Cookie: session or X-Wap-Proxy-Cookie: session-has-state header from the user agent, indicating that cookie management is desired.The Cookie Proxy MUST be prepared to receive Cookie headers from the user agent, regardless of the presence of an X-Wap-Proxy-Cookie header. If this situation occurs, the Cookie Proxy MUST transmit the state present in the Cookie header to the origin server, with the following criteria:1. If a cookie proxy receives both Cookie and X-Wap-Proxy-Cookie: cache/cache-has-state or X-Wap-Proxy-Cookie: session/session-has-state headers, the Cookie Proxy may append other cookies to the Cookie header prior to performing the subsequent HTTP request. In the case where a user agent and a Cookie Proxy have an identical cookie to send, i.e. both cookies have identical values for path, domain and N AME attributes, the cookie MUST be delivered to the origin server as it is specified by the user agent. Cookies MUST be ordered in the Cookie header as specified in [RFC2109].2. If cookie proxy receives both Cookie and X-Wap-Proxy-Cookie: delete or X-Wap-Proxy-Cookie: none headers, it MUST deliver the cookie header to the origin server without interception.Cookie Proxy MUST include X-Wap-Proxy-Set-Cookie: state header in the response to the client, if it has received a cookie in the response from the origin server and chosen to manage it or it has sent a Cookie header in the associated HTTP request. . This header MUST NOT be sent if neither of the Cookie and Set-Cookie headers was present in the HTTP request and response, or if the cookie proxy has not cached any cookie information.Cookie Proxy MUST include X-Wap-Proxy-Set-Cookie: error header in the response if user agent sends status information which is conflicting with the status recorded by the Cookie Proxy. This will happen when a user agent sends a request with X-Wap-Proxy-Cookie:cache-has-state or X-Wap-Proxy-Cookie: session-has-state header, but the Cookie Proxy does not have any cookies in storage for this particular user agent.Cookie Proxy MUST NOT store the received cookie, if Set-Cookie header includes secure attribute. If secure attribute is present, Cookie Proxy MUST deliver the cookie to the client without interception. This attribute MAY be used by content authors to indicate that a specific cookie contains private or confidential information, and that the preferred storage is in the client.If a cookie proxy receives an X-Wap-Proxy-Cookie header from a client and chooses to manage and store cookies on its behalf, it MUST remove the X-Wap-Proxy-Cookie header from the request and thus prevent it from going further to the network. If Cookie Proxy chooses not to manage cookies on behalf of the client, it MUST let the headers pass without interception.9.3 Associating Cookie Storage With ClientsThe Cookie Proxy MUST associate cookies with a single client and prevent another client from gaining access to the cookies. This may be achieved by associating the cookies with an authenticated client identifier. Content authors should be advised that different user agents located in the same client may use the same Cookie Proxy facilities and the same cookie storage.The Cookie Proxy MUST NOT provide cookie proxy facilities to anonymous clients.9.4 Managing Proxy CookiesThe Cookie Proxy SHOULD provide a Web application to let the user browse and control the stored cookies.10. USER AGENT RESPONSIBILITIES10.1 HTTP State ManagementThe user agent MUST implement HTTP State Management, as specified in [RFC2109]. User agents with non-conforming implementations (i.e. no support) have undefined semantics. WAP user agents MUST be able to save and manage at least four cookies, with a maximum size of 125 bytes each (size includes fully-qualified host name, expiration date, and cookie data).10.2 Cookie Proxy ManagementSupport for use of Cookie Proxy functionality in the user agent is optional. User agent MAY include WAP Specific HTTP State Management Headers in requests to utilize Cookie Proxy facilities.If Cookie Proxy functionality is supported, end-user MUST have an opportunity to elect to use either cookie proxy facilities or their own local cookie management or both.User agent MUST send X-Wap-Proxy-Cookie: cache-has-state header instead of X-Wap-Proxy-Cookie: cache and X-Wap-Proxy-Cookie: session-has-state header instead of X-Wap-Proxy-Cookie: session in case it has received at least one X-Wap-Proxy-Set-Cookie header during the ongoing user agent session. When user agent receivesX-Wap-Proxy-Set-Cookie: error header, it MAY notify the user that inconsistent service behavior might occur. WAP user agents MUST be prepared to receive Set-Cookie HTTP headers even when they have requested Cookie Proxy functionality alone, and must act in accordance with [RFC2109] in this situation (e.g., the user agent should make a best effort attempt to manage the cookie (See section 10.2)).11. STATIC CONFORMANCE REQUIREMENTSThese static conformance requirements define a minimum set of features that must be implemented to support the WAP HTTP State Management mechanism. A feature can be optional (O), mandatory (M) or conditional (C (<condition>)). If optional/conditional features have labels (O.<n> or C.<n>), support of at least one of the group of options labeled by the same number is required.11.1 User Agent FeaturesItem Functionality Reference Status Requirement10.1 MHSM_C001 User agent support for HTTP StateManagement Mechanism10.1 MHSM_C002 User agent support for at least fourcookies of at least 125 bytes totalstorage space.10.1 OHSM_C003 User agent support for more than500 bytes of cookie storage space10.2 OHSM_C004 User agent support for use ofCookie Proxy functionalityHSM_C005 User agent support for WAP10.2 C:HSM_C004specific HTTP State managementheadersItem Functionality Reference Status Requirement9.1 MHSM_S001 Cookie Proxy support for passingof HTTP headers between the useragent and the origin server withoutinterference.HSM_S002 Cookie Proxy support for Cookie9.2 OManagement and Storagefunctionality.9.2 C:HSM_S002HSM_S003 Cookie Proxy support for useragent role in HTTP StateManagement Mechanism.HSM_S004 Cookie Proxy support for WAP9.2 C:HSM_S002specific HTTP State Managementheaders and mechanisms.9.2 C:HSM_S002HSM_S005 Cookie Proxy does not store thecookie if origin server includessecure attribute in Set-Cookieheader.HSM_S006 Cookie Proxy associates HTTP9.3 C:HSM_S002state with a particular client, anddoes not provide cookiemanagement or storage foranonymous clients.HSM_S007 Cookie Proxy support for WAP9.4 OHTTP State Management userinterface。
高中数学思想方法之“分类讨论思想”(2012.8.6)一、知识整合:1.分类讨论是解决问题的一种逻辑方法,也是一种数学思想,有关分类讨论的数学命题在高考试题中占有重要位置。
2.所谓分类讨论,就是当问题所给的对象不能进行统一研究时,就需要对研究对象按某个标准分类,然后对每一类分别研究得出每一类的结论,最后综合各类结果得到整个问题的解答。
实质上,分类讨论是“化整为零,各个击破,再积零为整”的数学策略。
3.分类原则:分类对象确定,标准统一,不重复,不遗漏,分层次,不越级讨论。
4.分类方法:明确讨论对象,确定对象的全体,确定分类标准,正确进行分类;逐类进行讨论,获取阶段性成果;归纳小结,综合出结论。
5.含参数问题的分类讨论是常见题型。
解含有参数的题目时,必须根据参数的不同取值范围进行讨论。
如解不等式2ax >时分0a >、0a =和0a <三种情况讨论。
这称为含参型。
6.中学数学教材中分类讨论的知识点,大致有:①绝对值概念的定义;②一元二次方程根的判别式与根的情况;③二次函数二次项系数的正负与抛物线的开口方向;④反比例函数y =k x(x ≠0)的反比例系数k ,正比例函数y =kx 的比例系数k ,一次函数y =kx +b 的斜率k 与图象位置及函数单调性的关系;⑤幂函数y =x a 的幂指数a 的正、负与定义域、单调性、奇偶性的关系;⑥指数函数y =a x 及其反函数y =log a x 中底数a >1及a <1对函数单调性的影响;⑦等比数列前n 项和公式中q =1与q ≠1的区别;⑧不等式性质中两边同乘(除)以正数或负数时对不等号方向的影响;⑨直线与圆锥曲线位置关系的讨论;⑩运用点斜式、斜截式直线方程时斜率k 是否存在.二、典型例题:例1.已知圆x y 224+=,求经过点P ()24,,且与圆相切的直线方程。
例2.1log (1)1a x x->解关于的不等式:例3.设,问方程表示什么曲线?k R k x k y k k ∈-+-=--()()()()848422例4、(2012广东高考文科数学21题)设0<a <1,集合{|0}A x R x =∈>,2{|23(1)60}B x R x a x a =∈-++>,D AB =.(1)求集合D (用区间表示)三、巩固练习1. 若3201log (1)log (1)a a a a p a a q a a >≠=++=++,且,,,则,p q 的大小关系为( ) A. p q= B. p q < C. p q > D. a p q >>1时,;01<<<a pq 时, 2. 若{}A x x p x x R =+++=∈|()2210,,且A R +=∅,则实数中的取值范围是( ) A. p ≥-2 B. p ≤-2 C. 40p -<< D. p >-43.已知集合{}{}10,1,1A x ax B x =--==-,若A B B =,则实数a 的取值的集合是( ) A. {}1- B. {}1 C. {}1,1- D. {}0,1,1-4. 一条直线过点(5,2),且在x 轴,y 轴上截距相等,则这直线方程为( )A. x y +-=70B. 250x y -=C. 70250x y x y +-=-=或D. 70250x y y x ++=-=或5. 若sin cos 1sin cos ()n n x x x x n N +=+∈则的值为,( )A. 1B. -1C. 11-或D. 不能确定 6. 函数fx m x mx ()()=+-+231的图象与x 轴的交点至少有一个在原点的右侧,则实数m 的取值范围为( )A. [)0,+∞B. (]-∞,1C. (]01,D.7.集合A ={x ||x |≤4,x ∈R },B ={x ||x -3|<a ,x ∈R },若A ∩B=B ,那么a 的取值范围是( )A .0≤a ≤1B .a ≤1C .a <1D .0<a <18.若方程x 2k -4-y 2k +4=1表示双曲线,则它的焦点坐标为 ( ) A .(2k,0),(-2k,0) B .(0,2k ),(0,-2k )C .(2|k |,0),(-2|k |,0)D .由k 的取值确定9.若定义在区间(-1,0)内的函数f (x )=log 2a (x +1)满足f (x )>0,则a 的取值范围是 ( )A.⎝⎛⎭⎫0,12B.⎝⎛⎦⎤0,12C.⎝⎛⎭⎫12,+∞ D .(0,+∞) 10.已知双曲线的渐近线方程为y =±34x ,则双曲线的离心率为 ( ) A.53 B.52 C.52或153 D.53或5411.函数f (x )=mx 2+mx +1的定义域为一切实数,则实数m 的取值范围是____________.12.正三棱柱的侧面展开图是边长分别为6和4的矩形,则它的体积为___________13. 若lo g a 231<,则a 的取值范围为________________ 14. 与圆x y 2221+-=()相切,且在两坐标轴上截距相等的直线方程为______________ 15.函数y =a x (a >0且a ≠1)在[1,2]上的最大值比最小值大a 2,则a 的值是________. 16.若函数f (x )=a |x -b |+2在[0,+∞)上为增函数,则实数a ,b 的取值范围为________.17、(1)求曲线y =13x 3+43经过点P (2,4)的切线方程. (2)已知f (x )=12x 2-a ln x (a ∈R),求函数f (x )的单调区间;18、解关于x 的不等式2(1)10ax a x -++<。
评:我可以说这是产品经理的功劳么?
8.Facebook出现虚假账户数目可达8300万
9.“愤怒的小鸟”国内纵容盗版开店遭冷遇
评:有假的,谁买真的!!!
10.百度内部邮件曝光:多名员工违规删帖3人刑拘
评:这不是一个产业链么?是要断了么?
11.当当网多省大面积商品缺货疑陷资金短缺危机
评:好像半年前就说资金短缺了
12.在线教育平台传课网获贝塔斯曼A轮融资
评:让我想起了读者上面的“贝塔斯曼书友会”,后来都变成了“卓越”
13.创新工场新基金已募1.5亿美元
评:有梦想,什么时候都不晚!!!
14.晚报总编—曲琦.cookie(产品经理)于今日离职
评:没敢占用新闻的地方,在这小推荐下
中国目前金牌数量:金30、银17、铜14
人人都是产品经理()中国最大最活跃的产品经理学习、交流、分享平台。