Maryland Hand Hygiene Code Data Set Observation Tool
- 格式:doc
- 大小:56.00 KB
- 文档页数:2

Maya BlastcodeBlastcode 主控制窗口面板介绍我们通过制作墙面的爆炸来熟悉下Blastcode的窗口面板和基本操作流程先看下墙面爆炸的最终效果注意:Blastcode的运算基于一个控制平面,这个控制平面必须是一个Nurbs的物体。
在场景中创建Nurbs平面,修改通道栏属性选择刚创建的NURBS平面,打开Blast Code>Blast Window命令,可以看到这是Blast Code的主控制窗口,按New Control创建一个新的Control, 可能看到在Control Source窗口中创建一个nurbsPlane1转到Explosive模块中,点击Locator Explosive,创建一个爆炸选择Explosive1,在Source Control Surface窗口可以看到刚才创建的nurbsPlane1(注意:默认爆炸对它是不起作用的,必须点击这个名字,才起作用),点击nurbsPlane1名字,使它激活。
播放动画,发现爆炸的位置和方向不正确。
在大纲中选择(我们以后就叫它为炸弹)在场景中移动到控制平面的中心保持炸弹被选择的状态点击Ctal+A 打开其属性编辑窗口,将Use Origin Flag 勾选。
Origin 后面的三个数值框代表的是爆炸的三个轴向,分别为X、Y、Z。
数值越大爆炸的效果越倾向于该轴向。
如果爆炸的方向是X、Y、Z的正方向则输入负值,反方向则正值。
再次播放动画,方向正确。
时间轴回到第一帧,选择NURBS平面执行Blast Code > Create Slab命令在大纲中选择NurbsPlane1 打开属性编辑窗口,选择Slab1 将Mesh Thickness 修改为0.5个单位播放动画打开属性编辑窗口,选择Slab1节点,把Fracture Option 改为Fracture Map,它碎裂的方式以贴图表示。
给Fracture Map一个Leather的3D程序纹理帖图修改Leather节点属性选择Slab1节点,把Fracture Threshold的值改为大约0.6。

2020年贵阳市第七中学高三英语模拟试题及答案第一部分阅读(共两节,满分40分)第一节(共15小题;每小题2分,满分30分)阅读下列短文,从每题所给的A、B、C、D四个选项中选出最佳选项AProvincetown, Cape Cod RestaurantsAfter a day on the sands or exploring our charming town, enjoy local eats, from fresh seafood and lobster to authentic Italian. You’ll find many wonderful Provincetown, Cape Cod restaurants and cafes just steps away. Fanizzi’s RestaurantRight next door to our hotel, this award-winning local eatery is one of the finest Cape Cod restaurants. The menu highlights seafood, Italian, steaks, burgers, and fresh salads. Enjoy the Friday Fish Fry, Early Bird Specials, and Sunday Brunch, available from 10:00 a.m. to 2:00 p.m. all year long.539 Commercial Street 508-487-1964Napi’s RestaurantNapi’s serves dinner all year round and lunch from April to October. A cozy place located just off Commercial Street and overflowing with local art, this Cape Cod, Massachusetts classic specializes in everything from freshly caught seafood to Portuguese and Brazilian dishes to vegetarian items.7 Freeman Street 800-571-6274Mews RestaurantEnjoy views of Provincetown Harbor at this waterfront restaurant just steps from Surfside Hotel & Suites. Intercontinental dishes are served in the beach-level dining room, while upstairs you’ll find a casual American bistro. Summer months bring on a brunch menu, and dinner is served year-round.429 Commercial Street 508-487-1500The Red InnA favorite among our guests, The Red Inn is located on Provincetown’s picturesque waterfront which provides diners with the most gorgeous harbor views and spectacular sunsets. The Red Inn provides historic old world charm with new world pleasure. Their menu features the finest local seafood.15 Commercial Street 508-487-73341.Which restaurant offers a special breakfast for early risers?A.Fanizzi’s Restaurant.B.Napi’s Restaurant.C.Mews Restaurant.D.The Red Inn.2.What is special about The Red Inn?A.It exhibits the good local art.B.It is the finest local restaurant.C.It offers the best local seafood.D.It serves brunch all year round.3.What does the text mainly talk about?A.Accommodation.B.Life styles.C.Sightseeing.D.Dining.BThe United Nations Educational, Scientific and Cultural Organization (UNESCO) included on December 17, 2020 China's Tai Chi on the Representative List of the Intangible(无形的)Cultural Heritage of Humanity. The decision was announced during the online meeting of the UNESCO Intergovernmental Committee for the Safeguarding of the Intangible Cultural Heritage held from December 14 to19 inKingston, capital ofJamaica.“Born in the mid-17th century in a small village named Chenjiagou located in Central China's Henan province, Tai Chi is not only a kind of traditional Wushu integrated with slow movements and deep breathing, but is also deeply rooted in many areas of Chinese culture, such as medicine and philosophy,”Zhu Xianghua says, who is the son of the famous Tai Chi master Zhu Tiancai.Although it has spread to more than 150 countries and regions, attracting more than 100 million people to practice, the idea that Tai Chi is for the elderly has stopped many young people practicing the ancient Wushu. They think of it as a slow exercise, which is specially made and better suited for their grandparents. Instead, many young people are turning to the Indian practice of yoga(瑜伽)to relieve stress, which was placed on the UNESCO's List in 2019.In order to promote Tai Chi, joint efforts have been made from individuals and the Chinese government in the last decades. Xi'an Jiaotong University requires students to learn Tai Chi. Wang Yunbing, a professor in the university's sports center, stressed that Tai Chi is not only good physical exercise-researchers from the American College of Rheumatology find that it can help manage several diseases but is also conned ted to ancient Chinese eivilization. Since 2014, the World Tai Chi Championships have been held every two years by the International Wushu Federation. It provides a platform for communication and learning between the Tai Chi masters and Tai Chi lovers around the globe. In January 2020, Tai Chi became an official event in the 2026 Dakar Youth Olympic Games.4. What does Zhu Xianghua say about Tai Chi in paragraph 2?A. It originated from fast Kung Fu action.B. It was born around the 1750s in a village.C. It is related to other cultural fields ofChina.D. It integrates Chinese medicine and western philosophy.5. Why do some young people choose to practice yoga instead of Tai Chi?A. They think it easier to practice yoga to keep fit.B. The elderly stop young people practicing Tai Chi.C. They consider Tai Chi is custom-built for old people.D. Yoga was included in the world culture earlier than Tai Chi.6. What is the main purpose of the last paragraph?A. To promote contemporary Chinese civilization.B. To show many efforts made to popularize Tai Chi.C. To stress the importance of Chinese Tai Chi masters.D. To advise people to practise Tai Chi to cure diseases.7. Which of the following is the best title for the passage?A. Tai Chi Steps on the UNESCO's List.B. Tai Chi isCompeting against Yoga.C. Tai Chi Has Regained populate Globally.D. Opinions Greatly Differ on Tai Chi and Yoga.CIt’s a big change from homeless teen to Yale (耶鲁)medical school student, butperseverancepaid off for Chelesa Fearce of Clayton County, Georgia.Fearce was a fourth grader when her mom was diagnosed (诊断) with Lymphoma (淋巴瘤).That began a hard time for the family. They had to move in and out of shelters,hotels and even the family car.“I know I have been made stronger. I was homeless. My family slept on the floor and we were lucky if we got more than one full meal a day. Getting a shower, food and clean clothes was an everyday struggle,” Fearce said in a speech she gave at her high school graduation ceremony. Fearce overcame her day-to-day struggles by focusing on a better day. “I just told myself to keep working, because the future will not be like this anymore. And that helped me get through,” she told WSBTV.Fearce was determined to be a good role model for her younger sister. She found inspiration in her late grandmother, struggling with deadly diseases, who gave Fearce emotional support. In her junior and senior year,Fearce took both high school and college courses, missing out on the free meals she depended on so she could get to her college classes. Despite having to use her cellphone to study after the shelter lights were turned off at night, she not only graduated as valedictorian (毕业生代表) of her 2013 class with a 4.5 grade average, but was also given a ride scholarship—including a meal plan to Spelman College in Atlanta.After graduation, she worked full time for two years at the National Institutes for Health inBethesda,Maryland,doing research on drugs. Last fall, she entered Yale and set a course to earn both a PhD and medical degree.8. What does the underlined word “perseverance” in paragraph 1 refer to?A. instant passion.B. continuous efforts.C. great patience.D. selfless ambitions.9. How did Fearce feel facing the sufferings?A. Sad and disappointed.B. Stressed and defeated.C. Determined and confident.D. Joyous and contented.10. What can we know about Fearce’s learning experience?A. Her grandma encouraged her to study medicine.B. Her high school offered her free meals and courses.C. She failed to study late due to frequent power cut.D. She gained remarkable high school achievement.11. What can be a suitable title for the text?A. From Homeless to YaleB. Meet American’s Top GirlC. Disabled but not DefeatedD. Chelesa Fearce: A Girl of Many TalentsDWe touch our faces all the time, and it had never seemed to be a big problem—until COVID-19 arrived. Touching our faces—the "T-zone" of our eyes, nose and mouth in particular—can mean giving ourselves the deadly virus.This is why organizations like the Centers for Disease Control and Prevention (CDC) have suggested that we avoid touching our faces. "Just stop this simple behavior," William Sawyer, founder of Henry the Hand, a nonprofit organization that promotes hand hygiene (卫生), told The Washington Post. "It's the one behavior that would bebetter than any vaccine (疫苗) ever created."Yet, stopping this "simple" behavior might be harder than you think because it's already hardwired (固定存在于) into our system.Some face touchingis an automatic reflex (反射) —like when there is an itch (痒) on your nose, you'll scratch (挠) it without thinking. According to CNBC, a 2014 study found that touching your face also helps to reduce stress and regulate emotions. For example, you're more likely to do it when you feel awkward or embarrassed. According to Dacher Keltner, a psychologist at the University of California Berkeley, US, this action may also come with a social function: When you are talking to someone and want to change the subject, for example, touching your face is like "the curtains on a stage, closing up one act of the social drama, ushering (引导) in the next," Keltner told the BBC.Moreover, face-touching in almost all of these occasions is subconscious, which means it's very hard to change "because you don't even know you're doing it", said Sawyer. But you're not alone. In a 2015 study, wherea group of medical students were filmed in class, it was found that they touched their faces an average of 23 times an hour—with 44 percent of the touches being in the "T-zones". That was particularly surprising since medical students were supposed to know better.Since it's so hard to shake the habit, maybe the easiest way is to wash our hands more often. This way, we can be sure that our hands are free from the novel coronavirus.12. What do the first two paragraphs talk about?A. The best way to fight COVID-19B. How organizations are fighting COVID-19.C. Typical hand hygiene problems in the fight against COVID-19.D. The necessity to avoid touching our faces to fight COVID-19.13. Why is it hard for people to stop touching their faces?A. It makes people feel more confident.B. Many are unaware of this behavior's risks.C. They usually do it automatically and subconsciouslyD. Many think the action helps them express their emotions.14. Which of the following is a social function of touching faces, according to the text?A. Using it as a sign to change the topicB. Bringing a conversation to an end.C. Showing an interest in the ongoing subject.D. Making others feel relaxed while talking.15. What is the author's purpose in mentioning a 2015 study on a group of medical students?A. To give tips on how to stop touching faces.B. To prove that it is common for people to touch their faces.C. To show it is impossible to shake the habit of touching your face.D. To show how hygiene awareness helps people avoid touching their faces.第二节(共5小题;每小题2分,满分10分)阅读下面短文,从短文后的选项中选出可以填入空白处的最佳选项。
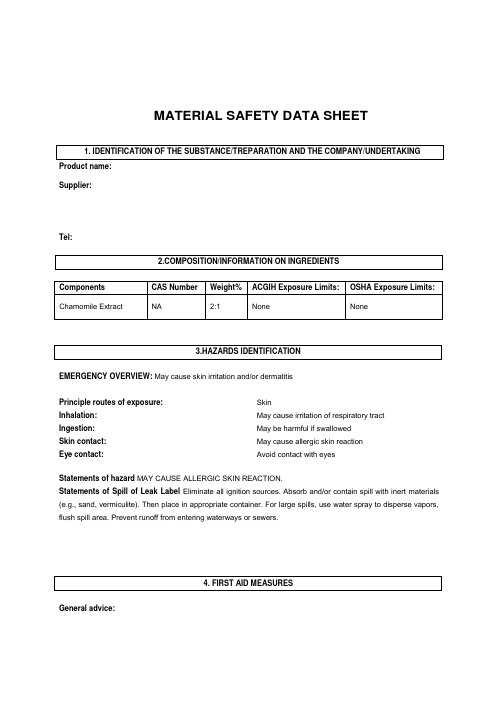
1. IDENTIFICATION OF THE SUBSTANCE/TREPARATION AND THE COMPANY/UNDERTAKING3.HAZARDS IDENTIFICATION4. FIRST AID MEASURESMATERIAL SAFETY DATA SHEETProduct name:Supplier:Tel:EMERGENCY OVERVIEW: May cause skin irritation and/or dermatitisPrinciple routes of exposure: Inhalation: Ingestion: Skin contact: Eye contact:SkinMay cause irritation of respiratory tract May be harmful if swallowed May cause allergic skin reaction Avoid contact with eyesStatements of hazard MAY CAUSE ALLERGIC SKIN REACTION.Statements of Spill of Leak Label Eliminate all ignition sources. Absorb and/or contain spill with inert materials (e.g., sand, vermiculite). Then place in appropriate container. For large spills, use water spray to disperse vapors, flush spill area. Prevent runoff from entering waterways or sewers.General advice:POSITION/INFORMATION ON INGREDIENTSInhalation:Skin contact:Ingestion:Eye contact:Protection of first – aiders:Medical conditions aggravated by exposure: In the case of accident or if you fell unwell, seek medical advice immediately (show the label where possible).Move to fresh air, call a physician immediately.Rinse immediately with plenty of water and seek medical adviceDo not induce vomiting without medical advice.In the case of contact with eyes, rinse immediately with plenty of water and seek medical advice.No information availableNone knownSuitable extinguishing media:Specific hazards:Special protective equipment for firefighters:Flash point:Autoignition temperature:NFPA rating Use dry chemical, CO2, water spray or “alcohol” foam Burning produces irritant fumes.As in any fire, wear self-contained breathing apparatus pressure-demand, MSHA/NIOSH (approved or equivalent) and full protective gearNot determinedNot determinedNFPA Health: 1 NFPA Flammability: 1 NFPA Reactivity: 0Personal precautions: Environmental precautions: Methods for cleaning up: Use personal protective equipment.Prevent product from entering drains.Sweep up and shovel into suitable containers for disposalStorage:7. HANDLING AND STORAGE5.FIRE-FIGHTING MEASURES6. ACCIDENTAL RELEASE MEASURESRoom temperature Handling:Safe handling advice: Incompatible products:Use only in area provided with appropriate exhaust ventilation.Wear personal protective equipment.Oxidising and spontaneously flammable productsEngineering measures: Respiratory protection: Skin and body protection:Eye protection: Hand protection: Hygiene measures:Ensure adequate ventilation.Breathing apparatus only if aerosol or dust is formed. Usual safety precautions while handling the product will provide adequate protection against this potential effect. Safety glasses with side-shieldsPVC or other plastic material glovesHandle in accordance with good industrial hygiene and safety practice.Melting point/range: Boiling point/range: Density: Vapor pressure: Evaporation rate: Vapor density: Solubility (in water): Flash point:Autoignition temperature:No Data available at this time. No Data available at this time. No data available No data available No data available No data available No data available Not determined Not determinedStability: Stable under recommended storage conditions. Polymerization: None under normal processing.Hazardous decomposition products: Thermal decomposition can lead to release of irritating gases and vapours such as carbon oxides.Materials to avoid: Strong oxidising agents.10. STABILITY AND REACTIVITY9. PHYSICAL AND CHEMICAL PROPERTIES8. EXPOSURE CONTROLS/PERSONAL PROTECTION11. TOXICOLOGICAL INFORMATIONConditions to avoid: Exposure to air or moisture over prolonged periods.Product information Acute toxicityChronic toxicity:Local effects: Chronic exposure may cause nausea and vomiting, higher exposure causes unconsciousness.Symptoms of overexposure may be headache, dizziness, tiredness, nausea and vomiting.Specific effects:May include moderate to severe erythema (redness) and moderate edema (raised skin), nausea, vomiting,headache.Primary irritation: Carcingenic effects: Mutagenic effects: Reproductive toxicity:No data is available on the product itself. No data is available on the product itself. No data is available on the product itself. No data is available on the product itself.Mobility:Bioaccumulation: Ecotoxicity effects: Aquatic toxicity:No data available No data available No data availableMay cause long-term adverse effects in the aquatic environment.12. ECOLOGICAL INFORMATION13. DISPOSAL CONSIDERATIONSWaste from residues/unused products:Contaminated packaging:Waste disposal must be in accordance with appropriate Federal, State and local regulations. This product, if unaltered by use, may be disposed of treatment at a permitted facility or as advised by your local hazardous waste regulatory authority. Residue from fires extinguished with this material may be hazardous.Do not re-use empty containers.UN/Id No:Not regulated14. TRANSPORT INFFORMATIONDOTProper shipping name: Not regulatedTGD(Canada)WHMIS hazard class: Non - controlledIMDG/IMOIMDG – Hazard Classifications Not ApplicableIMO – labels:15. REGULATORY INFOTMATION International Inventories16. OTHER INFORMATIONPrepared by: Health & SafetyDisclaimer: The information and recommendations contained herein are based upon tests believed to be reliable.However, XABC does not guarantee the accuracy or completeness NOR SHALL ANY OF THIS INFORMATION CONSTITUTE A WARRANTY, WHETHER EXPRESSED OR IMPLIED, AS TO THE SAFETY OF THE GOOD, THE MERCHANTABILITY OF THE GOODS, OR THE FITNESS OF THE FITNESS OF THE GOODS FOR A PARTICULAR PURPOSE. Adjustment to conform to actual conditions of usage maybe required. XABC assumes no responsibility for results obtained or for incidental or consequential damages, including lost profits arising from the use of these data. No warranty against infringement of any patent, copyright or trademark is made or implied.End of safety data sheet。

Proteintech Group,USA, 5400Pearl Street,Suite300, Rosemont,IL60018,USA t1-888-478-4522Proteintech Europe,4th Floor,196Deansgate,Manchester,M33WFt(+44)-161-83-93-007San Ying Biotechnology,China,D3-3,No.666Gaoxin Avenue,Wuhan East LakeHi-tech Development Zone,Wuhan,P.R.C.t86-27-87531629SAFETY DATA SHEET(SDS)1.IDENTIFICATION OF THE SUBSTANCE/PREPARATION AND OF THECOMPANY/UNDERTAKINGProduct Name:CoraLite594-Phalloidin(red)Catalog Number:PF00003REACH registration number:No registration number is given yet for this substance/substances in this mixture since the annual import quantity is less than one tonnage per annum or the transition period for its registration according to Article23of REACH has not yet expired.Company/undertaking Identification:Proteintech Group5400Pearl StreetSTE300Rosemont,IL60018312-455-8498Emergency telephone number:312-455-8498,ext8022.HAZARDOUS IDENTIFICATION:Classification according to Regulation(EC)No1272/2008[CLP]Physical hazards:Not hazardousHealth hazards:Not HazardousEnvironmental Hazards:Not HazardousAdditional information:Not applicableLabel elementsLabelling according to Regulation(EC)No1272/2008[CLP]Hazard pictograms:Signal word:DangerHazard statements:Harmful if swallowedEU Specific Hazard Statements:Not applicablePrecautionary StatementsPrevention:Not applicableResponse:Not applicableStorage:Not applicableDisposal:Not applicableOther Hazards:Not applicable3.INGREDIENT COMPOSITION/INFORMATION:Component Cas No.Weight Classification according to Regulation ECNo1272/2008(CLP)Phalloidin None100%Acute tox2–H300,H310,H3304.FIRST AID MEASURES:Skin Contact Wash off skin thoroughly with soap and water.Remove contaminated clothing and wash before reuse.Eye Contact Ensure adequate flushing of eye contamination for at least 15minutes.Inhalation Remove from exposure,rest and keep warm.Ingestion Wash mouth out thoroughly with water and drink plenty of water.Most important symptoms and effects:both acute and delayed Symptoms of allergic reaction may include rash,itching,swelling,trouble breathing,tingling of the hands and feet,dizziness,lightheadedness,chest pain,muscle pain,or flushing.Indication of any immediate medical attention and special treatment needed: Treat symptomatically.Advice for emergency responders:For further assistance,contact your local Poison Control Center.Protection of first-aid responders:Ensure that medical personnel are aware of the material(s)involved,and take precautions to protect themselves.5.FIRE FIGHTING MEASURES:Suitable extinguishing media:Water Spray,Carbon Dioxide,DryChemical Powder,or appropriate foam.Unsuitable extinguishing media:No information availableSpecial hazards arising from the substance or mixture:Not known.Advice for fire-fighters:Standard procedure for chemical fires6.ACCIDENTAL RELEASE MEASURES:Wear appropriate personal protective clothing(Section8).Mop up with an absorbent cloth and arrange removal by a disposal company.Wash site of spillage thoroughly with water and detergent and prevent further leakage or spillage if safe to do so.No special environmental precautions required.7.HANDLING AND STORAGE:Use only in area provided with exhaust ventilation.Avoid contact with skin,eyes and clothing.Wear appropriate protective clothing(Section8).Keep container tightly closed,and in a dark,well-ventilated area.Store at-20℃.8.EXPOSURE CONTROLS/PPE:Follow good laboratory practice when handling this product.Hygiene measures:Handle in accordance with good industrial hygiene and safety practiceRecommended personal protection equipmentEye protection:Laboratory safety goggles.Hands:Chemical resistant gloves.Skin:Laboratory protective clothing.Respiratory:Fume hood or in areas with adequate ventilation.Control Parameters:Not applicable9.PHYSICAL AND CHEMICAL PROPERTIES: Appearance:SolidOdor:NoneMelting point/melting range:UntestedBoiling point/boiling range:UntestedProteintech Group,USA, 5400Pearl Street,Suite300, Rosemont,IL60018,USA t1-888-478-4522Proteintech Europe,4th Floor,196Deansgate,Manchester,M33WFt(+44)-161-83-93-007San Ying Biotechnology,China,D3-3,No.666Gaoxin Avenue,Wuhan East LakeHi-tech Development Zone,Wuhan,P.R.C.t86-27-87531629Flash point:UntestedAutoignition temperature:UntestedDecomposition temperature:UntestedEvaporation rate:UntestedFlammability:UntestedUpper explosion limit:UntestedLower explosion limit:UntestedVapor pressure:UntestedRelative density:UntestedSpecific gravity:UntestedSolubility:UntestedPartition coefficient:UntestedExplosive properties:Untested10.CHEMICAL STABILITY AND REACTIVITY:Reactivity:None knownChemical stability:Stable under normal conditionsPossibility of hazardous reactions:None reportedConditions to avoid:No information availableIncompatible materials:No dangerous reaction knownHazardous decomposition products:None11.TOXICOLOGICAL INFORMATION:Inhalation:May be irritating to mucous membranes and upper respiratory tract.Eye contact:May cause irritationSkin contact:May cause irritationIngestion:May be harmful if swallowedCarcinogenic effects:Not availableMutagenic effects:Not availableReproductive toxicity:Not availableSTOT–Single exposure:Not availableSTOT–Repeated exposure:Not availableTeratogenic effects:Not available12.ECOLOGICAL INFORMATION:Data not yet available.13.DISPOSAL CONSIDERATIONS:Waste disposal methods:Should not be released into the environment.Disposal considerations:Do not empty into drains;dispose of material and container in safe way.14.TRANSPORT INFORMATION:DOTUN number UN2811UN proper shipping name Toxic solid,organic,n.o.s.(phalloidin)Transport hazard class(es)6.1Packing group II Special provisions IB8,IP2,IP4,T3,TP33Emergency response guide154numberIATAUN number UN2811UN proper shipping name Toxic solid,organic,n.o.s.(phalloidin)Transport hazard class(es)6.1Packing group IISpecial provisions A3,A5.15.REGULATORY INFORMATION:Substances of Very High Concern:None.Restricted substances under EC1907/2006,Annex XVII:None. Substances listed under Annex I of Regulation(EC)No689/2008:None. Restricted substances under Annex V of Regulation(EC)No689/2008:None. Substances under Regulation(EC)No850/2004of the European Parliament and of the Council of29April2004on persistent organic pollutants and amending Directive79/117/EEC:None.German Water hazard classes(Wassergefährdungsklassen):Not classified. Other International Inventories:No information available16.OTHER INFORMATION:Reason for revision:New productRevision number:1Revision:2/4/2021The above information is believed to be correct but should only be used as a guide for experienced personnel.Proteintech Group Inc.will not be liable for any damage resulting from the handling of or from contact with the above product.For lab use only,not for diagnostic or therapeutic work.。

Data Replication with Code Ocean–A How-To Guidefor PA AuthorsSimon HeubergerOctober2,2019Contact•Code Ocean support:Online browser chat or*********************•PA replication team:**************************************Workflow for Authors•Create a capsule for your material on the Code Ocean website.If you don’t have a free account yet,you need to sign up for one•Add the member of the PA replication team as a collaborator(use the PA contact email provided above)•Add your material.If you have any questions or problems during the setup,contact the PA replication team with questions.If needed,refer to the Code Ocean help documentation and/or contact the Code Ocean support team(use the email provided above)as well•When you think your material is ready to work in the capsule,email the PA replication team.PA then checks:–The Readme–That allfigures and tables are saved to the/results folder and named correctly –Whether all libraries and dependencies are installed via the environment screen,not during runtime•After a successful check,replicate your material by clicking on“Reproducible Run”.This will run your material in the capsule remotely,i.e.you can close your browser andfiles will continue to be run.If there are any issues/errors during the run and you need helpfixing them,email the PA replication team/Code Ocean support•After a successful reproducible run,fill out the publication metadata section of the cap-sule,and submit your material for publication by clicking on“Submit for publication”.Successful submission requires one complete run of the material without errors•PA gets a notification that the material has been submitted,compares the produced output to the manuscript,and checks the metadata•If aspects are missing or there are discrepancies between the code output and the manuscript,make the required changes to the material and resubmit.This process is repeated until the material is ready for publication•Upon successful comparison/check,Code Ocean publishes your material as a repro-ducible capsule and publishes a copy to Dataverse for long-term preservationLanguages offered by Code Ocean•Code Ocean offers the three data analysis software programs that are most often used in political science:R,Stata,and Python•Code Ocean also offers selected other pieces of more advanced programming software, such as Jupyter(Programming languages on Code Ocean).However,PA’s focus lies on the three standard programs above.If your material uses a language other than R, Stata,or Python,please contact PA before setting up a capsuleHow to set up a Code Ocean capsule and install packages in R,Stata,and Python •Create a new blank capsule on your dashboard(What is a capsule?;What is the dashboard?)•Select your base environment(What is a base environment?;Selecting a base environ-mment)–For R,Code Ocean offers versions3.4.4,3.5.3,and3.6–For Stata,Code Ocean offers Stata15with R and Stata15with Matlab–For Python,Code Ocean offers versions3.7.3,3.7.0,3.6.3,and TensorFlow2.7•Install needed packages on the next screen.It is not possible to install packages insidea script–they need to be installed here.Click on+Add,type in the package nameand version(the latter is optional),and click on the tick(Adding packages on Code Ocean)–For R,use CRAN and GitHub–For Stata,use ssc(Using Stata on Code Ocean)–For Python,use conda and pipHow to use two data analysis software programs together•R and Stata–CodeOcean has a pre-provided environment(see the subsection on Stata baseenvironments above)•R and Python–With R as the basis∗Add python3-pip(Python3)or python-pip(for Python2)via apt-get(What is apt-get?)–With Python as the basis∗Add R as a conda package,then add the package you want(e.g.r-ggplot2)∗The conda list of R packages is quite limited:Some packages are in a differentconda channel(e.g.randomizr which is in channel conda-forge,not r),others are not in conda at all(e.g.blockTools)–General rule:If a material is mainly in R,use R as the base.Likewise for Python Folders in a capsule•The key folders on Code Ocean are/code,/data,and/results•/code–Contains all your scriptfiles•/data–Contains all your datafiles–To ensure complete reproducibility,/data is reset to its original form after eachrun.This means everything your code saves in/data would be lost at the endof a run.To avoid this,save all code output in/results instead(see subsection/results below)•/results–Everything that your code saves needs to be saved in/results(Savingfiles onCode Ocean).This includesfigures,tables,and any created.csv,.Rdata etc.files that other scriptfiles read in after creation.For instance,if a.csvfile iscreated in first.R and then needs to be read in by second.R,save and load the.csv to/from/results.Everything saved in/results is available after each run run•run is a shell run script that is central to the working of Code Ocean.In order to run any scriptfile in any programming language,it needs to be listed in run(What is a run script?)•run is not present when you create a new blank capsule.To create it,select an uploaded scriptfile and select“Set as File to Run”with right-point-and-click.run will appear in the Files tab and list the selected script•It is currently not possible to select several scriptfiles and select“Set as File to Run”.If your material includes more than one scriptfile to run(which is very likely),create a master scriptfile that reads in the others(then only this masterfile needs to be listed in run).Alternatively,select“Set as File to Run”for thefirstfile and manually enter the otherfiles into run,e.g.(for all three languages):Rscript"first.R"Rscript"second.R"python-u"first.py"python-u"second.py"stata"first.do"stata"second.do"•If you want a full log of any run scriptfiles(i.e.including all executed commands) enter scriptfiles in the following way into run:Rscript-e"source(‘first.R’,echo=T)"python-m trace--trace"first.py"For Stata,set up a logfile within the.dofileYour material in the capsule•Creating subfolders–Hover the cursor over any folder.A downward arrow will appear on the right.Click it and select“New Folder”to create a new subfolder in this folder •Uploadingfiles/folders–Hover the cursor over any folder.A downward arrow will appear on the right.Click it and select“Upload File(s)”to uploadfiles or folders to this folder.Ifuploading folders doesn’t work,switch to Chrome as your browser(some browserslike Safari don’t work with this feature)(Uploadingfiles/folders to Code Ocean)–Upload your scriptfiles to/code and your datafiles to/data•Readme–Provide a Readme that briefly describes your material and the related manuscript –The Readme can be uploaded to/code in any format•Saving code output–Your code needs to replicate and create saved output for all code-createdfigures and tables in the main text as well as in the supplementary material–Everything that your code saves needs to be saved in/results(see section“Fold-ers in a capsule”above)–If you want to save anyfigures,tables,or datafiles in subfolders within/results, these subfolders have to be set up in run.For instance,to set up the subfolder /sims in/results,enter the following into run:mkdir-p/results/sims–Figures need to be saved in.pdf format.Tables can be saved in the format you deem most appropriate(e.g..csv,.txt,.tex etc.)–Allfigures and tables need to be saved according to their respective numbers in the manuscript,e.g.figure1.pdf,table2.tex etc.•Reading infiles–Files that are present when you set up the capsule need to be read in from/data –Files that are created by a script and needed in subsequent scripts need to be saved to and read in from/results(see section“Folders in a capsule”above)•File paths–Always use relative paths,e.g.../data and../results,when reading in and savingfiles(File paths on Code Ocean)–If you have code in a subfolder,don’t forget to add..as necessary,e.g.load(‘../../data/simulations.csv’).This code would go up two parent di-rectories and then look for./data/simulations.csv–The working directory is/code.If you source any scriptfiles,you thus don’t need relative paths,e.g.source("calculations.R")will work•Runningfiles–After a successful PA check of your setup(see section“Workflow for Authors”above),click on“Commit Changes”,then on“Reproducible Run”–This will run all scriptfiles listed in run remotely–You can close your browser once reproduction has started.Files will continue to be run(Runningfiles on Code Ocean)–If there is an error in your code,execution will be halted.Execution will also be halted if your code requires interactive user input•Computing power–Your material will be run on at least a16-core machine with120GB of memory.If your material requires more computing power please contact PA(Computing power on Code Ocean)•Looking at resulting plots–Click on any saved plot and it will open in a new tab.If you see an empty tab, switch to Chrome as your browser(some browsers like Safari don’t work with this feature)•Submitting your material for publication–After a successful reproducible run,click on“Submit for publication”–Successful submission requires one complete run of your material without errors(Publishing on Code Ocean)–If you can’t see the“Submit for publication”button,make sure to commit allchanges(Where is the‘Submit for Publication’button?)–After submitting your material for publication,add the metadata(see section“Publication metadata”below).PA will then check your material.Upon success-ful check,Code Ocean makes your material publicly available(What’s involvedwith a published capsule?)Publication metadata(must be completed for publication)•Description•Basic info–Capsule name–Researchfield(“Social Sciences”)–Tags(optional)•License info–Software license(“MIT”is recommended)–Data license(“No Rights Reserved”is recommended)•Associated Publication–Select whether the publication associated with this capsule is:∗Published∗Yet to be published∗There is no associated article–If you have a DOI,select“Published”.Otherwise choose“Yet to be published”•Authors and affiliations。

ARIZONA PHX3PHX5PHX6PHX7TFC1CALIFORNIA ONT2ONT6ONT8ONT9OAK3OAK4XUSD CONNECTICUT BDL1DELAWARE PHL1PHL3PHL7PHL8Florida LAL1TPA1Indiana XUSE IND1IND2IND3IND4IND5IND6Kansas TUL1MCI1Kentucky SDF1SDF2CVG1CVG2CVG3LEX1LEX2Maryland BWI2Massachusetts BOS5Nevada RNO1RNO2LAS2New Hampshire BOS1New Jersey EWR4EWR5Pennsylvania AVP1ABE2ABE3ABE5PHL4PHL5PHL6South Carolina CAE1GSP1Tennessee BNA1BNA2BNA3BNA4CHA1CHA2Texas DFW1DFW6DFW7SAT1XUSBWashington BFI1BFI3BFI4SEA6SEA8Wisconsin MKE1Canada YVR2YYZ1YYZ2YYZ3PRTOArizona#PHX3 – 6835 W. Buckeye Rd. Phoenix, AZ, 85043 – Maricopa County#PHX5 – 16920 W. Commerce Dr. Goodyear, AZ, 85338 – Maricopa County#PHX6 – 4750 W. Mohave St. Phoenix, AZ, 85043 – Maricopa County#PHX7 – 800 N. 75th Ave Phoenix, AZ, 85043 – Maricopa County#TFC1 – 5050 W. Mohave St. Phoenix, AZ 85043 – Maricopa CountyCalifornia#ONT2 – 1910 E Central Ave. San Bernadino, CA, 92408 – San Bernardino County#OAK3 – 255 Park Center Drive Patterson, CA, 95363 – Stanislaus County#XUSD– 1909 Zephyr St Stockton, CA 95206 – San Joaquin County#OAK4 – 1555 N. Chrisman Rd. Tracy, CA, 95304 – San Joaquin County#ONT6 – 24208 San Michele Rd. Moreno Valley, CA, 92551 – Riverside County#ONT8 - Golden State FC LLC24300 Nandina AveMoreno Valley, CA 92551#ONT9 – 2125 W. San Bernandino Ave. Redlands, CA, 92374 – San Bernardino CouConnecticut#BDL1 – 801 Day Hill Rd. Windsor, CT, 06095 – Hartford CountyDelaware#PHL1 – 1 Centerpoint Blvd. New Castle, DE 19720 – New Castle County#PHL3 – 1600 Johnson Way New Castle, DE 19720 – New Castle County#PHL7 – 560 Merrimac Ave Middletown, DE 19709 – New Castle County #PHL8 – 727 N. Broad Street Middletown, DE 19709 – New Castle County Florida#LAL1 – 1760 County Line Rd. Lakeland, FL, 33811 – Polk County#TPA1 – 351 30th Street NE, Ruskin, FL 33570 – Hillsborough CountyIndiana XUSE IND1IND2IND3IND4IND5#XUSE – 5100 S Indianapolis Rd Whitestown, IN 46075 – Boone County#IND1 – 4255 Anson Blvd. Whitestown, IN 46075 Boone County#IND2 – 715 Airtech Pkwy. Plainfield, IN 46168 Hendricks County#IND3 – 717 Airtech Pkwy. Plainfield, IN 46168 – Hendricks County#IND4 – 710 South Girls School Rd Indianapolis, IN 46214 – Marion County#IND5 – 800 S Perry Rd Plainfield, IN 46168 – Hendricks County#IND6 – 1453 10th Street Jeffersonville, IN 47130 – Clark County#SDF8 – 900 Patrol Rd. Jeffersonville, IN 47130 – Clark CountyKansas TUL1MCI1#TUL1 – 2654 N US Highway 169 Coffeyville, KS 67337 – Montgomery Cou#MCI1 – 113th St & Renner Blvd. Lenexa, KS 66219 – Johnson County(在建)Kentucky SDF1SDF2CVG1CVG2CVG3LEX1#SDF1 – 1105 S Columbia Ave Campbellsville, KY 42718 – Taylor County#SDF2 – 4360 Robards Ln Louisville, KY 40218 – Jefferson County#CVG1 – 1155 Worldwide Blvd. Hebron, KY 41048 – Boone County#CVG2 – 1600 Worldwide Blvd. Hebron, KY 41048 – Boone County#CVG3 – 3680 Langley Dr. Hebron, KY 41048 – Boone County#LEX1 – 1850 Mercer Rd Lexington, KY 40511 – Fayette County#LEX2 – 172 Trade St. Lexington, Kentucky, 40511 – Fayette County#SDF4 – 376 Blvd Shepherdesville, KY 40165 – Bullitt County#SDF6 – 271 Omega Pkwy Shepherdsville, KY 40165 – Bullitt County#SDF7 – 300 Omicron Court Shepherdsville, KY 40165 – Bullitt County#SDF9 – 100 W. Thomas P. Echols Lane Shepherdsville, KY 40165 – Bullitt County Maryland BWI2BWI2#BWI2 – 2010 Broening Hwy. Baltimore, MD 21224 – Baltimore County Massachuse BOS5#BOS5 – 1000 Tech Center Dr Stoughton, MA 02072Nevada RNO1RNO2LAS2#RNO1 – 1600 East Newlands Dr. Fernley, NV 89408 – Lyon County,Clos#RNO2 – 8000 N Virginia St. Reno, NV 85906 – Washoe County#LAS2 – 3837 Bay Lake Trail Suite 115, North Las Vegas, NV 89030-4434 – Clark Co New Hamps BOS1#BOS1 – 10 State St Nashua, NH 03063 – Hillsborough CountyNew Jersey E WR4EWR5#EWR4 – 50 New Canton Way Robbinsville, NJ 08691 – Mercer County#EWR5 – 301 Blair Rd. Avenel, NJ 07001 – Middlesex CountyComing soon! 8001 Industrial Ave, Carteret, NJ 07008 – Middlesex County Pennsylvania AVP1ABE2ABE3ABE5PHL4PHL5#AVP1 – 550 Oak Ridge Road Hazleton, PA 18202 – Luzerne County#ABE2 – 705 Boulder Dr Breinigsville, PA 18031 – Lehigh County#ABE3 – 650 Boulder Drive Breinigsville, PA 18031 – Lehigh County#ABE5 – 6455 Allentown Boulevard Harrisburg, PA 17112 – Dauphin County#PHL4 – 21 Roadway Drive Carlisle, PA 17015 – Cumberland County#PHL5 – 500 McCarthy Dr Lewisberry, PA 17339 – York County#PHL6 – 675 Allen Rd. Carlisle, PA 17015 – Cumberland County#XUSC – 40 Logistics Drive Carlisle, PA 17013 – Cumberland County#VUBA – 1000 Keystone Industrial Park Scranton, PA 18512#VUGA – 508 Delaware Avenue West Pittston, PA 18643#PIT1– 2250 Roswell Drive, Roswell, PA 15205South Caroli CAE1GSP1#CAE1 – 4400 12th Street Extension, West Columbia, SC 29172 – Lexingto#GSP1 – 402 John Dodd Rd. Spartanburg, SC 29303 – Spartanburg County Tennessee BNA1BNA2BNA3BNA4CHA1CHA2#BNA1 – 14840 Central Pike Lebanon, TN 37090 – Wilson County#BNA2 – 500 Duke Drive Lebanon, TN 37090 – Wilson County#BNA3 – 2020 Joe B Jackson Pkwy Murfreesboro, TN 37127 – Rutherford County #BNA4 – 50 Airways Blvd Nashville, TN 37217#CHA1 – 7200 Discovery Dr Chattanooga, TN 37421 – Hamilton County#CHA2 – 225 Infinity Dr NW, Charleston, TN 37310 – Bradley CountyTexas DFW1DFW6DFW7SAT1XUSB#DFW1 – 2700 Regent Blvd DFW Airport, TX 75261#DFW6 – 940 W Bethel Road Coppell, TX 75019 – Denton County#DFW7 – 700 Westport Parkway Fort Worth, TX 76177 – Denton County or Tarrant #SAT1 – 6000 Enterprise Avenue Schertz, TX 78154 – Guadalupe, Bexar or Comal C #XUSB – 14900 Frye Rd Fort Worth, TX 76155 – Tarrant County or Dallas County Virginia RIC1RIC2#RIC1 – 5000 Commerce Way, Petersburg, VA 23803 – Dinwiddie County#RIC2/#RIC3 – 1901 Meadowville Technology Parkway Chester, VA 23836 – Cheste Washington BFI1BFI3BFI4SEA6SEA8#BFI1 – 1800 140th Ave. E, Sumner, WA – Pierce County#BFI3 – 2700 Center Drive, Dupont, WA 98327 – Pierce County#BFI4 – Kent, WA#SEA6 - 2646 Rainier Avenue, South Seattle, WA 98144#SEA8 - 1227 124th Avenue Northeast, Bellevue, WA, 98005Wisconsin MKE1#MKE1 – 38th St. Kenosha, WI, 53144 – Kenosha CountyCanada YVR2YYZ1YYZ2YYZ3PRTO#YVR2 – 450 Derwent PL Delta, British Columbia V3M 5Y9#YYZ1 – 6363 Millcreek Drive Mississauga, Ontario L5N 1L8#YYZ2 – 2750 Peddie Rd. Milton, Ontario L9T 6Y9#YYZ3 – 7995 Winston Churchill Blvd. Brampton, Ontario L6Y 0B2#PRTO – 6110 Cantay Rd. Mississauga, Ontario L5R 4JWSDF8SDF4SDF6SDF7SDF9XUSC VUBA VUGA PIT1 ricopa Countyn Bernardino Countylaus CountyRiverside Countyley, CA 92551– San Bernardino Countystle Countyastle Countystle CountyCastle CountyIND6SDF8ne CountyMarion Countyntgomery County,Closing by February 12, 2015n County(在建)LEX2SDF4SDF6SDF7SDF9 ylor Countyullitt County165 – Bullitt CountyClosing in February 12, 201589030-4434 – Clark Countydlesex CountyPHL6XUSC VUBA VUGA PIT1 Dauphin County72 – Lexington Countynburg County– Rutherford Countyton Countynty or Tarrant County upe, Bexar or Comal Countyty or Dallas Countyddie Countyer, VA 23836 – Chesterfield County。
Package‘rdnb’October14,2022Type PackageTitle R Interface to the'Deutsche Nationalbibliothek(German NationalLibrary)API'Version0.1-5Date2022-05-12Author Christian Graul[aut,cre]Maintainer Christian Graul<*************************>Description A wrapper for the'Deutsche Nationalbibliothek(German NationalLibrary)API',available at<https://www.dnb.de/EN/Home/home_node.html>.The German National Library is the German central archival library,collecting,archiving,bibliographically classifying all German andGerman-language publications,foreign publications about Germany,translations of German works,and the works of German-speaking emigrantspublished abroad between1933and1945.URL https:///chgrl/rdnbBugReports https:///chgrl/rdnb/issuesLicense MIT+file LICENSEVignetteBuilder knitrNeedsCompilation noImports brew,grDevices,httr,methods,utils,stats,stringr,xml2Suggests knitr,markdownRoxygenNote7.1.2Repository CRANDate/Publication2022-05-1221:00:02UTCR topics documented:changes (2)dnb_advanced (2)dnb_search (4)1n_rec (6)print_query (6)rdnb (7)Index8 changes View changes notes.Descriptionchanges brings up the NEWSfile of the package.Usagechanges(pkg="rdnb")Argumentspkg Set to the default"rdnb".Other packages make no sense.Examples##Not run:changes()##End(Not run)dnb_advanced Search the DNB catalogue-advanced searchDescriptiondnb_search exposes a search in the DNB catalogue,expressed in the DNB query language. Usagednb_advanced(query,limit=10,clean=TRUE,print=FALSE)Argumentsquery the search query,expressed in the DNB query language;single string value.limit number and(optional)starting point of results returned;single integer value (number of results),vector of two integer values(number of results andfirstresult,>=1)or"all"for a complete list of results.clean if TRUE(the default),the results are cleaned(see below for details).print if TRUE the search results are printed(default is FALSE).DetailsCleaning of resultsTo harmonise the results,some clutter is deleted and abbreviations frequently used in the dnb cata-logue are replaced by full words.Here is a list of all replacements:Variable Searched Replaced bycomplete dataset\u0098[deleted]complete dataset\u009c[deleted]complete dataset…,complete dataset...complete dataset;;;year[string][numeric]pages S.[deleted]pages Seiten[deleted]pages[[deleted]pages][deleted]publisher Verl.Verlagpublisher verl.verlagpublisher[[deleted]publisher][deleted]edition Aufl.Auflageedition aufl.auflageedition Orig.Originaledition Ed.Editionedition ed.editionedition Ausg.Ausgabeedition ausg.ausgabeedition Nachdr.Nachdruckedition Bibliogr.Bibliografieedition[[deleted]edition][deleted]edition[x].,[x].price kart.Kartoniertprice Gb.Gebundenprice Spiralb.Spiralbindungprice Pb.PaperbackValueA data.frame of results with metadata.Examples##Not run:#german books titled with cat (male or female),#excluding titles containing dogs,since the year2001cats<-dnb_advanced("(tit=katze OR tit=kater NOT tit=hund)AND jhr>2000AND mat=books AND spr=ger") ##End(Not run)dnb_search Search the DNB catalogue-simple searchDescriptiondnb_search exposes a search in the DNB catalogue.Usagednb_search(title,author,year,publisher,keyword,type,language,limit=10,clean=TRUE,print=FALSE)Argumentstitle the title(including subtitle,short title,volume title,etc.);optional single stringvalue or vector of strings.author the author(s);optional single string value or vector of strings.year the year of publishing;optional single integer value or vector of integers.publisher the publisher(publisher name and/or location);optional single string value orvector of strings.keyword one or a set of keywords describing the work(subjects,persons,locations,or-ganisations,etc.);optional single string value or vector of strings.type the type of publication(optional),one or a vector of articles,manuscript,biographicaldoc,letters,bequest,collections,books,brailles,maps,discs,dissertations,online,films,microfiches,multimedia,music,scores,serials,persons,subjects,corperations,works,events,geographics.language the language of the work by ISO639-2/B code(https:///wiki/List_of_ISO_639-2_codes);single string value or vector of strings.limit number and(optional)starting point of results returned;single integer value(number of results),vector of two integer values(number of results andfirstresult,>=1)or"all"for a complete list of results.clean if TRUE(the default),the results are cleaned(see dnb_advanced for details).print if TRUE the search results are printed(default is FALSE).Detailsto doValueA list of results with metadata.Examples##Not run:#title searchsingle.title<-dnb_search(title="katze")multi.title<-dnb_search(title=c("katze","kater","+maus","-hund"))#author searchsingle.author<-dnb_search(author="kern")author.or.author<-dnb_search(author=c("kern","locke"))author.and.author<-dnb_search(author=c("kern","+locke"))author.not.author<-dnb_search(author=c("kern","-locke"))#publication yearsingle.year<-dnb_search(title="katze",year=2015)sequence.of.years<-dnb_search(title="katze",year=2010:2015)set.of.years<-dnb_search(title="katze",year=c(2010:2013,2015))#publisher searchsingle.publisher<-dnb_search(title="katze",publisher="kiepenheuer")set.of.publishers<-dnb_search(title="katze",publisher=c("kiepenheuer","piper"))#keyword searchsingle.keyword<-dnb_search(author="kern")keyword.or.keyword<-dnb_search(keyword=c("katze","hund"))keyword.and.keyword<-dnb_search(keyword=c("katze","+hund"))keyword.not.keyword<-dnb_search(keyword=c("katze","-hund"))#type searchsingle.type<-dnb_search(title="katze",type="books")set.of.types<-dnb_search(title="katze",type=c("books","articles","online"))#language searchnguage<-dnb_search(title="cat",language="eng")nguages<-dnb_search(title=c("cat","katze"),language=c("eng","ger")) #change limit of resultsfirst.result<-dnb_search(title="katze",limit=1)5.results.starting.with.the.21st<-dnb_search(title="katze",limit=c(5,21))all.results<-dnb_search(title="katze",limit="all")##End(Not run)6print_query n_rec Number of recordsDescriptionn_rec returns the number of items in a list of records returned by a DNB-search.Usagen_rec(dnb_obj)Argumentsdnb_obj the DNB-search object returned dnb_search or dnb_advanced.ValueNumber of records found.Examples##Not run:dnb.srch<-dnb_search(title="katze")n_rec(dnb.srch)##End(Not run)print_query Print search queryDescriptionprint_query prints out the query used for a DNB-search request.Usageprint_query(dnb_obj)Argumentsdnb_obj the DNB-serch object returned by dnb_search or dnb_advanced.ValueQuery string.rdnb7Examples##Not run:dnb.srch<-dnb_search(title="katze")print_query(dnb.srch)##End(Not run)rdnb R Interface to the Deutsche Nationalbibliothek(German National Li-brary)APIDescriptionA wrapper for the Deutsche Nationalbibliothek(German National Library)API,available at https://www.dnb.de/EN/Home/home_node.html.The German National Library is the German cen-tral archival library,collecting,archiving,bibliographically classifying all German and German-language publications,foreign publications about Germany,translations of German works,and the works of German-speaking emigrants published abroad between1933and1945.DetailsAll bibliographic data of the German National Library are provided free of charge and can be freely re-used under"Creative Commons Zero"(CC01.0)terms.The metadata and online interfaces are provided with no guarantee of their being continuous,punctual,error-free or complete,or of their not infringing the rights of third parties(e.g.personal rights and copyright).ReferencesAbout the DNB:https://www.dnb.de/EN/Ueber-uns/ueberUns_node.html;about the inter-face:https://www.dnb.de/EN/Professionell/Metadatendienste/Datenbezug/SRU/sru_node.htmlIndexchanges,2dnb_advanced,2,4,6dnb_search,4,6n_rec,6print_query,6rdnb,7rdnb-package(rdnb),78。
Hamming codeFrom Wikipedia, the free encyclopediaJump to: navigation, searchIn telecommunication, a Hamming code is a linear error-correcting code named after its inventor, Richard Hamming. Hamming codes can detect up to two contiguous bit errors, and correct single-bit errors; thus, reliable communication is possible when the Hamming distance between the transmitted and received bit patterns is less than or equal to one. By contrast, the simple parity code cannot correct errors, and can detect only an odd number of errors.In mathematical terms, Hamming codes are a class of binary linear codes. For each integer there is a code with m parity bits and 2m− m − 1 data bits. The parity-check matrix of a Hamming code is constructed by listing all columns of length m that are pairwise independent. Hammingcodes are an example of perfect codes, codes that exactly match the theoretical upper bound on the number of distinct code words for a given number of bits and ability to correct errors.Because of the simplicity of Hamming codes, they are widely used in computer memory (RAM). In particular, a single-error-correcting and double-error-detecting variant commonly referred to as SECDED.Contents[hide]∙ 1 Historyo 1.1 Codes predating Hamming▪ 1.1.1 Parity▪ 1.1.2 Two-out-of-five code▪ 1.1.3 Repetition∙ 2 Hamming codeso 2.1 General algorithm∙ 3 Hamming codes with additional parity (SECDED)∙ 4 Hamming(7,4) codeo 4.1 Construction of G and Ho 4.2 Encodingo 4.3 Hamming(7,4) code with an additional parity bit∙ 5 See also∙ 6 References∙7 External links[edit] HistoryHamming worked at Bell Labs in the 1940s on the Bell Model V computer, an electromechanical relay-based machine with cycle times in seconds. Input was fed in on punched cards, which would invariably have read errors. During weekdays, special code would find errors and flash lights so the operators could correct the problem. During after-hours periods and on weekends, when there were no operators, the machine simply moved on to the next job.Hamming worked on weekends, and grew increasingly frustrated with having to restart his programs from scratch due to the unreliability of the card reader. Over the next few years he worked on the problem oferror-correction, developing an increasingly powerful array of algorithms. In 1950 he published what is now known as Hamming Code, which remains in use today in applications such as ECC memory.[edit] Codes predating HammingA number of simple error-detecting codes were used before Hamming codes, but none were as effective as Hamming codes in the same overhead of space.[edit] ParityMain article: Parity bitParity adds a single bit that indicates whether the number of 1 bits in the preceding data was even or odd. If an odd number of bits is changed in transmission, the message will change parity and the error can be detected at this point. (Note that the bit that changed may have been the parity bit itself!) The most common convention is that a parity value of 1indicates that there is an odd number of ones in the data, and a parity value of 0 indicates that there is an even number of ones in the data. In other words: the data and the parity bit together should contain an even number of 1s.Parity checking is not very robust, since if the number of bits changed is even, the check bit will be valid and the error will not be detected. Moreover, parity does not indicate which bit contained the error, even when it can detect it. The data must be discarded entirely andre-transmitted from scratch. On a noisy transmission medium, a successful transmission could take a long time or may never occur. However, while the quality of parity checking is poor, since it uses only a single bit, this method results in the least overhead. Furthermore, parity checking does allow for the restoration of an erroneous bit when its position is known.[edit] Two-out-of-five codeMain article: Two-out-of-five codeA two-out-of-five code is an encoding scheme which uses five digits consisting of exactly three 0s and two 1s. This provides ten possible combinations, enough to represent the digits 0 - 9. This scheme can detect all single bit-errors and all odd numbered bit-errors. However it still cannot correct for these errors.[edit] RepetitionMain article: triple modular redundancyAnother code in use at the time repeated every data bit several times in order to ensure that it got through. For instance, if the data bit to be sent was a 1, an n=3 repetition code would send "111". If the three bits received were not identical, an error occurred. If the channel is clean enough, most of the time only one bit will change in each triple. Therefore, 001, 010, and 100 each correspond to a 0 bit, while 110, 101, and 011 correspond to a 1 bit, as though the bits counted as "votes" towards what the original bit was. A code with this ability to reconstruct the original message in the presence of errors is known as an error-correcting code. This triple repetition code is actually the simplest Hamming code withm = 2, since there are 2 parity bits, and 22− 2 − 1 = 1 data bit.Such codes cannot correctly repair all errors, however. In our example, if the channel flipped two bits and the receiver got "001", the system would detect the error, but conclude that the original bit was 0, which is incorrect. If we increase the number of times we duplicate each bit to four, we can detect all two-bit errors but can't correct them (the votes "tie"); at five, we can correct all two-bit errors, but not all three-bit errors.Moreover, the repetition code is extremely inefficient, reducing throughput by three times in our original case, and the efficiency drops drastically as we increase the number of times each bit is duplicated in order to detect and correct more errors.[edit] Hamming codesIf more error-correcting bits are included with a message, and if those bits can be arranged such that different incorrect bits produce different error results, then bad bits could be identified. In a 7-bit message, there are seven possible single bit errors, so three error control bits could potentially specify not only that an error occurred but also which bit caused the error.Hamming studied the existing coding schemes, including two-of-five, and generalized their concepts. To start with, he developed a nomenclature to describe the system, including the number of data bits anderror-correction bits in a block. For instance, parity includes a single bit for any data word, so assuming ASCII words with 7-bits, Hamming described this as an (8,7)code, with eight bits in total, of which 7 are data. The repetition example would be (3,1), following the same logic. The code rate is the second number divided by the first, for our repetition example, 1/3.Hamming also noticed the problems with flipping two or more bits, and described this as the "distance" (it is now called the Hamming distance, after him). Parity has a distance of 2, as any two bit flips will be invisible. The (3,1) repetition has a distance of 3, as three bits need to be flipped in the same triple to obtain another code word with no visible errors. A (4,1) repetition (each bit is repeated four times) has a distance of 4, so flipping two bits can be detected, but not corrected. When three bits flip in the same group there can be situations where the code corrects towards the wrong code word.Hamming was interested in two problems at once; increasing the distance as much as possible, while at the same time increasing the code rate as much as possible. During the 1940s he developed several encoding schemes that were dramatic improvements on existing codes. The key to all of his systems was to have the parity bits overlap, such that they managed to check each other as well as the data.[edit] General algorithmThe following general algorithm generates a single-error correcting (SEC) code for any number of bits.1.Number the bits starting from 1: bit 1, 2, 3, 4, 5, etc.2.Write the bit numbers in binary. 1, 10, 11, 100, 101, etc.3.All bit positions that are powers of two (have only one 1 bit inthe binary form of their position) are parity bits.4.All other bit positions, with two or more 1 bits in the binary formof their position, are data bits.5.Each data bit is included in a unique set of 2 or more parity bits,as determined by the binary form of its bit position.1.Parity bit 1 covers all bit positions which have the leastsignificant bit set: bit 1 (the parity bit itself), 3, 5, 7,9, etc.2.Parity bit 2 covers all bit positions which have the secondleast significant bit set: bit 2 (the parity bit itself), 3,6, 7, 10, 11, etc.3.Parity bit 4 covers all bit positions which have the thirdleast significant bit set: bits 4–7, 12–15, 20–23, etc.4.Parity bit 8 covers all bit positions which have the fourthleast significant bit set: bits 8–15, 24–31, 40–47, etc.5.In general each parity bit covers all bits where the binaryAND of the parity position and the bit position is non-zero.The form of the parity is irrelevant. Even parity is simpler from the perspective of theoretical mathematics, but there is no difference in practice.This general rule can be shown visually:Bit position 1 2 3 4 5 6 7 8 9111121314 15 16 17 18 19 20...d d2 d3d d5d6d7d8d9d1d1d12d13d14d15bit coverage X X X X X X X X XX X X X X X X X X X X X X X X X X X X X X X X X X XX X X X XShown are only 20 encoded bits (5 parity, 15 data) but the pattern continues indefinitely. The key thing about Hamming Codes that can beseen from visual inspection is that any given bit is included in a unique set of parity bits. To check for errors, check all of the parity bits. The pattern of errors, called the error syndrome, identifies the bit in error. If all parity bits are correct, there is no error. Otherwise, the sum of the positions of the erroneous parity bits identifies the erroneous bit. For example, if the parity bits in positions 1, 2 and 8 indicate an error, then bit 1+2+8=11 is in error. If only one parity bit indicates an error, the parity bit itself is in error.As you can see, if you have m parity bits, it can cover bits from 1 up to 2m− 1. If we subtract out the parity bits, we are left with 2m− m− 1bits we can use for the data. As m varies, we get all the possible Hamming codes:Parity bits TotalbitsData bits Name2 3 1 Hamming(3,1) (Triple repetition code)3 74 Hamming(7,4)4 15 11 Hamming(15,11)5 31 26 Hamming(31,26)...m2m− 12m− m−1Hamming(2m− 1,2m− m− 1)If, in addition, an overall parity bit (bit 0) is included, the code can detect (but not correct) any two-bit error, making a SECDED code. The overall parity indicates whether the total number of errors is even or odd. If the basic Hamming code detects an error, but the overall parity says that there are an even number of errors, an uncorrectable 2-bit error has occurred.[edit] Hamming codes with additional parity (SECDED)These codes have a minimum distance of 3, which means that the code can detect and correct a single error, but a double bit error is indistinguishable from a different code with a single bit error. Thus, they can detect double-bit errors only if correction is not attempted.By including an extra parity bit, it is possible to increase the minimum distance of the Hamming code to 4. This gives the code the ability to detect and correct a single error and at the same time detect (but not correct) a double error. (It could also be used to detect up to 3 errors but not correct any.)This code system is popular in computer memory systems, where it is known as SECDED ("single error correction, double error detection"). Particularly popular is the (72,64) code, a truncated (127,120) Hamming code plus an additional parity bit, which has the same space overhead as a (9,8) parity code.[edit] Hamming(7,4) codeGraphical depiction of the 4 data bits and 3 parity bits and which parity bits apply to which data bitsMain article: Hamming(7,4)In 1950, Hamming introduced the (7,4) code. It encodes 4 data bits into 7 bits by adding three parity bits. Hamming(7,4) can detect and correct single-bit errors. With the addition of an overall parity bit, it can also detect (but not correct) double-bit errors.[edit] Construction of G and HThe matrix is called a (Canonical) generator matrix of a linear (n,k) code,and is called a parity-check matrix.This is the construction of G and H in standard (or systematic) form. Regardless of form, G and H for linear block codes must satisfy, an all-zeros matrix [Moon, p. 89].Since (7,4,3)=(n,k,d)=[2m− 1, 2m−1-m, m]. The parity-check matrix H of a Hamming code is constructed by listing all columns of length m that are pair-wise independent.Thus H is a matrix whose left side is all of the nonzero n-tuples where order of the n-tuples in the columns of matrix does not matter. The right hand side is just the (n-k)-identity matrix.So G can be obtained from H by taking the transpose of the left hand side of H with the identity k-identity matrix on the left hand side of G.The code generator matrix and the parity-check matrixare:andFinally, these matrices can be mutated into equivalent non-systematic codes by the following operations [Moon, p. 85]:∙Column permutations (swapping columns)∙Elementary row operations (replacing a row with a linear combination of rows)[edit] EncodingExampleFrom the above matrix we have 2k=24=16 codewords. The codewordsof this binary code can be obtained from . With with a i exist in F2 ( A field with two elements namely 0 and 1).Thus the codewords are all the 4-tuples (k-tuples).Therefore,(1,0,1,1) gets encoded as (1,0,1,1,0,1,0).[edit] Hamming(7,4) code with an additional parity bitThe same (7,4) example from above with an extra parity bitThe Hamming(7,4) can easily be extended to an (8,4) code by adding an extra parity bit on top of the (7,4) encoded word (see Hamming(7,4)). This can be summed up with the revised matrices:andNote that H is not in standard form. To obtain G, elementary row operations can be used to obtain an equivalent matrix toH in systematic form:For example, the first row in this matrix is the sum of thesecond and third rows of H in non-systematic form. Using thesystematic construction for Hamming codes from above, thematrix A is apparent and the systematic form of G is writtenasThe non-systematic form of G can be row reduced (usingelementary row operations) to match this matrix.The addition of the fourth row effectively computes thesum of all the codeword bits (data and parity) as thefourth parity bit.For example, 1011 is encoded into 01100110 where bluedigits are data; red digits are parity from theHamming(7,4) code; and the green digit is the parityadded by Hamming(8,4). The green digit makes the parityof the (7,4) code even.Finally, it can be shown that the minimum distance has increased from 3, as with the (7,4) code, to 4 with the (8,4) code. Therefore, the code can be defined as Hamming(8,4,4).[edit] See also∙Golay code∙Reed–Muller code∙Reed–Solomon error correction∙Turbo code∙Low-density parity-check code∙Hamming bound[edit] References∙Moon, Todd K. (2005). Error Correction Coding. New Jersey: John Wiley & Sons. ISBN978-0-471-64800-0./ece/faculty/tmoon/eccbook/ book.html.∙MacKay, David J.C. (September 2003). Information Theory, Inference and Learning Algorithms. Cambridge: Cambridge University Press. ISBN0-521-64298-1./mackay/itila/bo ok.html.∙ D.K. Bhattacharryya, S. Nandi. "An efficient class of SEC-DED-AUED codes". 1997 International Symposium on Parallel Architectures, Algorithms and Networks(ISPAN '97). pp. 410–415.doi:10.1109/ISPAN.1997.645128.[edit] External links∙CGI script for calculating Hamming distances (from R.Tervo, UNB, Canada)Retrieved from检错码的构造:检错码=信息字段+校验字段信息字段和校验字段之间的对应关系:校验字段越长,编码的检错能力越强,编码/解码越复杂;附加的冗余信息在整个编码中所占的比例越大,传输的有效成分越低,传输的效率下降。
TK 55526-2-PC-EN (Rev. 0, 02-18)©Thermo King CorporationSIMPLE TO DETERMINECause of Alarm1321. Press the CLEAR Key to clear analarm.2. The display screen will return to theStandard Display when the alarmsare cleared.3. Press the HELP key for additionalinformationwn on the display. Alsosee the complete Alarm Code list inthe next column.There are several options for viewing the Alarm Codes pertaining to your particular unit:1 B y visiting our /tools for a link to the Thermo King AlarmCodes App.2 B y downloading our Truck, Trailer, CyroTech and DAS Alarm Codes Booklet for all AlarmCodes This can be downloaded from the following link: www.emea-user-manuals./ or at the QR code below.3 A printed copy can also be obtained from your Thermo King Dealer Representative.SIMPLE TO VIEWClearing Alarm CodesNOTE: For more detailed information on each action, see the Operation chapter in theappropriate unit operating manual.For more information or tutorialsessions, please contact yourThermo King Service Manager22115734213141. Press the ON Key.2. A series of start-up screens willappear.3. When the unit is ready to runthe Standard Display of Box Temperature and Setpoint will appear.4. The Standard Display defaults tothe “Temperature Watch” screen after 2 1/2 minutes. This screen displays same setpoint and box temperature in larger font.1. Return to the Standard Display.2. Press the SETPOINT Key on theStandard Display.3. Press the + or - Keys to change thesetpoint reading.4. Press the YES Key when the desiredsetpoint is shown.5. The Standard Display appearswith setpoint changed to the new setpoint.1. Return to the Standard Display.2. Press the MODE SELECTION Key.IMPORTANT: As of several years ago, the display no longer shows test at the top of the display to indicate “Cycle Sentry” or “Continuous”.3. If the unit is in Cycle Sentry, the“Cycle Sentry Icon” will appear in the upper right corner of the display as shown.4. If the unit is in Continuous theCycle Sentry Icon will not be present.5. Pressing the MODE SELECTIONKey again will change the unit back to the previous mode.SIMPLE TO SETSIMPLE TO CHECK GaugesSIMPLE TO ACCESS SensorsSIMPLE TO CHECK Hourmeters1345345211. Return to the Standard Display.2. Press the DEFROST Key.3. A series of defrost screens willappear.4. The Defrost Display appears. Thebar indicator will fill in showing the time remaining to complete the Defrost cycle. When the Defrost cycle is complete the display returns to Standard Display.1223NOTE: For more detailed information on each action, see the Operation chapter in the appropriate unit operating manual.1. Return to the Standard Display.2. Press the GAUGES Key.3. Press BACK or NEXT Keys to scrollthrough following gauges: Coolant Temperature, Coolant Level,Engine Oil, Pressure, Amps, Battery Voltage, Engine RPM, Discharge Pressure, Suction Pressure, ETV Position, I/O. If no keys are pressed within 30 seconds, the screen will return to the Standard Display.4. Press the LOCK Key to display anygauge screen for 15 minutes. Press the key again to unlock the screen.1. Clear all alarm codes.2. Return to the Standard Display.3. Press the MENU key.4.Press the NEXT Key as required to show the Pretrip Menu.5. Press the SELECT Key to start aPretrip Test.6. If the unit is not running, a FullPretrip will be initiated. If the unit is running in either diesel or electric mode, a Running Pretrip will be performed.7. When all tests are complete, theresults are reported as PASS, CHECK or FAIL. If the results are CHECK or FAIL, the accompanying alarm codes will direct the technician to the cause of the problem.1. Return to the Standard Displayscreen.2. Press the MENU Key.3. Scroll through Main Menu byrepeatedly pressing the NEXT and BACK Keys until the hourmeters Main Menu Screen appears.4. Press the SELECT Key to enter theHourmeters Menu.5. Press the NEXT and BACK Keys toview the Hourmeter Displays.1. Return to the Standard Display.2. Press the SENSORS Key.3. Press the BACK or NEXT Keysto scroll through the following sensor screens: Control Return Air Temperature, Display Return Air Temperature, Control Discharge Air Temperature, Display Discharge Air Temperature, Temperature Differential, Evaporator Coil Temperature, Ambient AirTemperature, Spare 1 Temperature, Datalogger Temperature Sensors 1-6 and the Board TemperatureSensor. If no keys are pressed within 30 seconds, the screen will return to the Standard Display.4. Press the LOCK Key to display any sensor screen for for 15 minutes. Press thekey again to unlock the screen.5. Press the EXIT Key to return to the Standard Display.5. Press the EXIT Key to return to the Standard Display.NOTE: You must select the YES key within 10 seconds of selecting the new Setpoint, otherwise the change will be cancelled.。
INSTRUCTIONS FOR USE: SEE BACK
Unit: ____________________________________ Date: ___/___/___ Day of the Week:_____________ Time:______ to_______ Observer Name:_______________________________
Use of the Observation Tool: This tool is to be used by Hand Hygiene Observers who have completed the statewide Hand Hygiene Observer Training. Use one Observer per Observation Tool.
Complete 30 observations per month for all Inpatient Units and Intensive Care Units including Medical-Surgical, Pediatrics, Medical and Surgical Intensive Care Units, and Neonatal Intensive/Special Care Units. If your facility is participating in the MPSC Neonatal Collaborative and collecting hand hygiene compliance data for that unit, you may elect to continue with that measurement approach or include your Neonatal Intensive/Special Care Units in the observation measure for the Maryland Hospital Hand Hygiene Collaborative. Units excluded from the first phase of the collaborative include: Obstetric Service; Newborn Nursery; Psychiatric Service; Emergency Department; PACU; and, Operating Rooms.
Observe for hand hygiene outside of the patient room
•Identify the role of the person you are observing and record by a √ or X in the appropriate box
•Observe hand hygiene compliance and record by a √ or X in the appropriate box
•Do not exceed 5 observations per provider in one session
•Comments may include type of student observed, information about product availability, etc.
Observe for hand hygiene upon exit from PATIENT ENVIRONMENT
•Private or semi-private rooms =crossing the door
•Between patients and multi-patient room setting = crossing the “curtain line”
• A provider may use the hand rub dispenser just outside the room door, the dispenser inside the room, or the sink.
DO NOT GUESS. If your view is blocked & you cannot confirm if provider performed hand hygiene simply check “Blocked View/Unsure”Comments:
_________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________ _________________________________________________________________________________________________。