计算机网络(第7版)
- 格式:pptx
- 大小:2.84 MB
- 文档页数:83

Computer Networking: A Top-Down Approach, 7th Edition计算机网络自顶向下第七版Solutions to Review Questions and ProblemsChapter 6 Review Questions1.The transportation mode, e.g., car, bus, train, car.2.Although each link guarantees that an IP datagram sent over the link will bereceived at the other end of the link without errors, it is not guaranteed that IP datagrams will arrive at the ultimate destination in the proper order. With IP,datagrams in the same TCP connection can take different routes in the network, and therefore arrive out of order. TCP is still needed to provide the receiving end of the application the byte stream in the correct order. Also, IP can lose packets due to routing loops or equipment failures.3.Framing: there is also framing in IP and TCP; link access; reliable delivery: thereis also reliable delivery in TCP; flow control: there is also flow control in TCP;error detection: there is also error detection in IP and TCP; error correction; full duplex: TCP is also full duplex.4.There will be a collision in the sense that while a node is transmitting it will startto receive a packet from the other node.5.Slotted Aloha: 1, 2 and 4 (slotted ALOHA is only partially decentralized, since itrequires the clocks in all nodes to be synchronized). Token ring: 1, 2, 3, 4.6.After the 5th collision, the adapter chooses from {0, 1, 2,…, 31}. The probabilitythat it chooses 4 is 1/32. It waits 204.8 microseconds.7.In polling, a discussion leader allows only one participant to talk at a time, witheach participant getting a chance to talk in a round-robin fashion. For token ring, there isn’t a discussion leader, but there is wine glass that the participants take turns holding. A participant is only allowed to talk if the participant is holding the wine glass.8.When a node transmits a frame, the node has to wait for the frame to propagatearound the entire ring before the node can release the token. Thus, if L/R is small as compared to t prop, then the protocol will be inefficient.9.248 MAC addresses; 232 IPv4 addresses; 2128 IPv6 addresses.10.C’s adapter will process the frames, but the adapter will not pass the datagrams upthe protocol stack. If the LAN broadcast address is used, then C’s adapter will both process the frames and pass the datagrams up the protocol stack.11.An ARP query is sent in a broadcast frame because the querying host does notwhich adapter address corresponds to the IP address in question. For the response, the sending node knows the adapter address to which the response should be sent, so there is no need to send a broadcast frame (which would have to be processed by all the other nodes on the LAN).12.No it is not possible. Each LAN has its own distinct set of adapters attached to it,with each adapter having a unique LAN address.13.The three Ethernet technologies have identical frame structures.14.2 (the internal subnet and the external internet)15.In 802.1Q there is a 12- bit VLAN identifier. Thus 212 = 4,096 VLANs can besupported.16.We can string the N switches together. The first and last switch would use oneport for trunking; the middle N-2 switches would use two ports. So the totalnumber of ports is 2+ 2(N-2) = 2N-2 ports.Chapter 6 ProblemsProblem 11 1 1 0 10 1 1 0 01 0 0 1 01 1 0 1 11 1 0 0 0Problem 2Suppose we begin with the initial two-dimensional parity matrix:0 0 0 01 1 1 10 1 0 11 0 1 0With a bit error in row 2, column 3, the parity of row 2 and column 3 is now wrong in the matrix below:0 0 0 01 1 0 10 1 0 11 0 1 0Now suppose there is a bit error in row 2, column 2 and column 3. The parity of row 2 is now correct! The parity of columns 2 and 3 is wrong, but we can't detect in which rows the error occurred!0 0 0 01 0 0 10 1 0 11 0 1 0The above example shows that a double bit error can be detected (if not corrected).Problem 301001100 01101001+ 01101110 01101011------------------------------10111010 11010100+ 00100000 01001100------------------------------11011011 00100000+ 01100001 01111001-----------------------------00111100 10011010 (overflow, then wrap around)+ 01100101 01110010------------------------------10100010 00001100The one's complement of the sum is 01011101 11110011Problem 4a)To compute the Internet checksum, we add up the values at 16-bit quantities:00000001 0000001000000011 0000010000000101 0000011000000111 0000100000001001 00001010-------------------------00011001 00011110The one's complement of the sum is 11100110 11100001.b)To compute the Internet checksum, we add up the values at 16-bit quantities: 01000010 0100001101000100 0100010101000110 0100011101001000 0100100101001010 01001011-------------------------10011111 10100100The one's complement of the sum is 01100000 01011011c)To compute the Internet checksum, we add up the values at 16-bit quantities: 01100010 0110001101100100 0110010101100110 0110011101101000 0110100101101010 01101011-------------------------00000000 00000101The one's complement of the sum is 11111111 11111010.Problem 5If we divide 10011 into 1010101010 0000, we get 1011011100, with a remainder of R=0100. Note that, G=10011 is CRC-4-ITU standard.Problem 6a) we get 1000110000, with a remainder of R=0000.b) we get 010*******, with a remainder of R=1111.c) we get 1011010111, with a remainder of R=1001.Problem 7a) Without loss of generality, suppose ith bit is flipped, where 0<= i <= d+r-1 and assume that the least significant bit is 0th bit.A single bit error means that the received data is K=D*2r XOR R + 2i. It is clear that if we divide K by G, then the reminder is not zero. In general, if G contains at least two 1’s, then a single bit error can always be detected.b) The key insight here is that G can be divided by 11 (binary number), but any number of odd-number of 1’s cannot be divided by 11. Thus, a sequence (not necessarily contiguous) of odd-number bit errors cannot be divided by 11, thus it cannot be divided by G.Problem 8a)1)1()(--=N p Np p E21)1)(1()1()('------=N N p N Np p N p E))1()1(()1(2----=-N p p p N NN p p E 1*0)('=⇒=b)N N N N N N p E N N N 11)11()11()11(1*)(11--=-=-=-- 1)11(lim =-∞→N N e N N N 1)11(lim =-∞→ Thuse p E N 1*)(lim =∞→Problem 9)1(2)1()(--=N p Np p E)3(2)2(2)1)(1(2)1()('------=N N p N Np p N p E))1(2)1(()1()3(2----=-N p p p N N121*0)('-=⇒=N p p E)1(2)1211(12*)(----=N N N N p E e e p E N 21121*)(lim =⋅=∞→Problem 10a) A’s average throughput is given by pA(1-pB).Total efficiency is pA(1-pB) + pB(1-pA).b) A’s throughput is pA(1-pB)=2pB(1-pB)= 2pB- 2(pB)2.B’s throughput is pB(1-pA)=pB(1-2pB)= pB- 2(pB)2.Clearly, A’s throughput is not twice as large as B’s.In order to make pA(1-pB)= 2 pB(1-pA), we need that pA= 2 – (pA / pB).c)A’s throughput is 2p(1-p)N-1, and any other node has throughput p(1-p)N-2(1-2p).Problem 11a)(1 – p(A))4 p(A)where, p(A) = probability that A succeeds in a slotp(A) = p(A transmits and B does not and C does not and D does not)= p(A transmits) p(B does not transmit) p(C does not transmit) p(D does not transmit)= p(1 – p) (1 – p)(1-p) = p(1 – p)3Hence, p(A succeeds for first time in slot 5)= (1 – p(A))4 p(A) = (1 – p(1 – p)3)4 p(1 – p)3b)p(A succeeds in slot 4) = p(1-p)3p(B succeeds in slot 4) = p(1-p)3p(C succeeds in slot 4) = p(1-p)3p(D succeeds in slot 4) = p(1-p)3p(either A or B or C or D succeeds in slot 4) = 4 p(1-p)3(because these events are mutually exclusive)c)p(some node succeeds in a slot) = 4 p(1-p)3p(no node succeeds in a slot) = 1 - 4 p(1-p)3Hence, p(first success occurs in slot 3) = p(no node succeeds in first 2 slots) p(some node succeeds in 3rd slot) = (1 - 4 p(1-p)3)2 4 p(1-p)3d)efficiency = p(success in a slot) =4 p(1-p)3Problem 12Problem 13The length of a polling round is)/(poll d R Q N +.The number of bits transmitted in a polling round is NQ . The maximum throughput therefore isQR d R d R Q N NQ poll poll +=+1)/( Problem 14a), b) See figure below.c)1. Forwarding table in E determines that the datagram should be routed to interface 192.168.3.002.2. The adapter in E creates and Ethernet packet with Ethernet destination address 88-88-88-88-88-88.3. Router 2 receives the packet and extracts the datagram. The forwarding table in this router indicates that the datagram is to be routed to 198.162.2.002.4.Router 2 then sends the Ethernet packet with the destination address of 33-33-33-33-33-33 and source address of 55-55-55-55-55-55 via its interface with IP address of 198.162.2.003.5.The process continues until the packet has reached Host B.a)ARP in E must now determine the MAC address of 198.162.3.002. Host E sendsout an ARP query packet within a broadcast Ethernet frame. Router 2 receives the query packet and sends to Host E an ARP response packet. This ARP response packet is carried by an Ethernet frame with Ethernet destination address 77-77-77-77-77-77.Problem 15a)No. E can check the subnet prefix of Host F’s IP address, and then learn that F ison the same LAN. Thus, E will not send the packet to the default router R1. Ethernet frame from E to F:Source IP = E’s IP addressDestination IP = F’s IP addressSource MAC = E’s MAC addressDestination MAC = F’s MAC addressb)No, because they are not on the same LAN. E can find this out by checking B’s IPaddress.Ethernet frame from E to R1:Source IP = E’s IP addressDestination IP = B’s IP addressSource MAC = E’s MAC addressDestination MAC = The MAC address of R1’s interface connecting to Subnet 3.c)Switch S1 will broadcast the Ethernet frame via both its interfaces as the receivedARP frame’s destination address is a broadcast address. And it learns that Aresides on Subnet 1 which is connected to S1 at the interface connecting to Subnet1. And, S1 will update its forwarding table to include an entry for Host A.Yes, router R1 also receives this ARP request message, but R1 won’t forward the message to Subnet 3.B won’t send ARP query message asking for A’s MAC address, as this address can be obtained from A’s query message.Once switch S1 receives B’s response message, it will add an entry for host B in its forwarding table, and then drop the received frame as destination host A is on the same interface as host B (i.e., A and B are on the same LAN segment).Lets call the switch between subnets 2 and 3 S2. That is, router R1 between subnets 2 and 3 is now replaced with switch S2.a) No. E can check the subnet prefix of Host F’s IP address, and then learn that F is on the same LAN segment. Thus, E will not send the packet to S2. Ethernet frame from E to F: Source IP = E’s IP address Destination IP = F’s IP address Source MAC = E’s MAC addressDestination MAC = F’s MAC addressb) Yes, because E would like to find B’s MAC address. In this case, E will send an ARP query packet with destination MAC address being the broadcast address. This query packet will be re-broadcast by switch 1, and eventually received by Host B. Ethernet frame from E to S2: Source IP = E’s IP address Destination IP = B’s IP address Source MAC = E’s MAC addressDestination MAC = broadcast MAC address: FF-FF-FF-FF-FF-FF.c) Switch S1 will broadcast the Ethernet frame via both its interfaces as the received ARP frame’s destination address is a broadcast address. And it learns that Aresides on Subnet 1 which is connected to S1 at the interface connecting to Subnet 1. And, S1 will update its forwarding table to include an entry for Host A.Yes, router S2 also receives this ARP request message, and S2 will broadcast this query packet to all its interfaces.B won’t send ARP query message asking for A’s MAC address, as this address can be obtained from A’s query message.Once switc h S1 receives B’s response message, it will add an entry for host B in its forwarding table, and then drop the received frame as destination host A is on the same interface as host B (i.e., A and B are on the same LAN segment).Problem 17Wait for 51,200 bit times. For 10 Mbps, this wait is12.51010102.5163=⨯⨯bps bitsmsecFor 100 Mbps, the wait is 512 μsec.At 0=t A transmits. At 576=t , A would finish transmitting. In the worst case, B begins transmitting at time t=324, which is the time right before the first bit of A’s frame arrives at B. At time t=324+325=649 B 's first bit arrives at A . Because 649> 576, A finishes transmitting before it detects that B has transmitted. So A incorrectly thinks that its frame was successfully transmitted without a collision.Problem 19Because A 's retransmission reaches B before B 's scheduled retransmission time (805+96), B refrains from transmitting while A retransmits. Thus A and B do not collide. Thus the factor 512 appearing in the exponential backoff algorithm is sufficiently large.Problem 20a) Let Y be a random variable denoting the number of slots until a success:1)1()(--==m m Y P ββ,where β is the probability of a success.This is a geometric distribution, which has mean β/1. The number of consecutive wasted slots is 1-=Y X thatββ-=-==11][][Y E X E x1)1(--=N p Np β11)1()1(1-----=N N p Np p Np xefficiency11)1()1(1-----+=+=N N p Np p Np k kxk kb)Maximizing efficiency is equivalent to minimizing x , which is equivalent tomaximizing β. We know from the text that β is maximized at Np 1=.c)efficiency 11)11()11(1-----+=N N NN k k∞→N lim efficiency 1/1/11-+=-+=e k kee k kd) Clearly, 1-+e k kapproaches 1 as ∞→k .Problem 21i) from A to left router: Source MAC address: 00-00-00-00-00-00Destination MAC address: 22-22-22-22-22-22Source IP: 111.111.111.001Destination IP: 133.333.333.003ii) from the left router to the right router: Source MAC address: 33-33-33-33-33-33Destination MAC address: 55-55-55-55-55-55Source IP: 111.111.111.001Destination IP: 133.333.333.003iii) from the right router to F: Source MAC address: 88-88-88-88-88-88Destination MAC address: 99-99-99-99-99-99Source IP: 111.111.111.001Destination IP: 133.333.333.003Problem 22i) from A to switch: Source MAC address: 00-00-00-00-00-00Destination MAC address: 55-55-55-55-55-55Source IP: 111.111.111.001Destination IP: 133.333.333.003ii) from switch to right router: Source MAC address: 00-00-00-00-00-00Destination MAC address: 55-55-55-55-55-55Source IP: 111.111.111.001Destination IP: 133.333.333.003iii) from right router to F: Source MAC address: 88-88-88-88-88-88Destination MAC address: 99-99-99-99-99-99Source IP: 111.111.111.001Destination IP: 133.333.333.003111.111.111.00311-11-11-11-11-11122.222.222.00466-66-66-66-66Problem 23If all the 11=9+2 nodes send out data at the maximum possible rate of 100 Mbps, a total aggregate throughput of 11*100 = 1100 Mbps is possible.Problem 24Each departmental hub is a single collision domain that can have a maximum throughput of 100 Mbps. The links connecting the web server and the mail server has a maximum throughput of 100 Mbps. Hence, if the three collision domains and the web server and mail server send out data at their maximum possible rates of 100 Mbps each, a maximum total aggregate throughput of 500 Mbps can be achieved among the 11 end systems.Problem 25All of the 11 end systems will lie in the same collision domain. In this case, the maximum total aggregate throughput of 100 Mbps is possible among the 11 end sytems. Problem 26Problem 27a) The time required to fill 8⋅L bits is.sec 16sec 1012883m LL =⨯⋅b) For ,500,1=L the packetization delay is.sec 75.93sec 161500m m =For ,50=L the packetization delay is.sec 125.3sec 1650m m =c) Store-and-forward delay RL 408+⋅=For 500,1=L , the delay issec 4.19sec 1062240815006μ≈⨯+⋅For ,50=L store-and-forward delay sec 1μ<.d) Store-and-forward delay is small for both cases for typical link speeds. However, packetization delay for 1500=L is too large for real-time voice applications.Problem 28The IP addresses for those three computers (from left to right) in EE department are: 111.111.1.1, 111.111.1.2, 111.111.1.3. The subnet mask is 111.111.1/24.The IP addresses for those three computers (from left to right) in CS department are: 111.111.2.1, 111.111.2.2, 111.111.2.3. The subnet mask is 111.111.2/24.The router’s interface card that connects to port 1 can be configured to contain two sub-interface IP addresses: 111.111.1.0 and 111.111.2.0. The first one is for the subnet of EE department, and the second one is for the subnet of CS department. Each IP address is associated with a VLAN ID. Suppose 111.111.1.0 is associated with VLAN 11, and 111.111.2.0 is associated with VLAN 12. This means that each frame that comes from subnet 111.111.1/24 will be added an 802.1q tag with VLAN ID 11, and each frame that comes from 111.111.2/24 will be added an 802.1q tag with VLAN ID 12. Suppose that host A in EE department with IP address 111.111.1.1 would like to send an IP datagram to host B (111.111.2.1) in CS department. Host A first encapsulates the IP datagram (destined to 111.111.2.1) into a frame with a destination MAC address equal to the MAC address of the router’s interface card that connects to port 1 of the switch. Once the router receives the frame, then it passes it up to IP layer, which decides that the IP datagram should be forwarded to subnet 111.111.2/24 via sub-interface 111.111.2.0. Then the router encapsulates the IP datagram into a frame and sends it to port 1. Note that this frame has an 802.1q tag VLAN ID 12. Once the switch receives the frame port 1, it knows that this frame is destined to VLAN with ID 12, so the switch will send the frame to Host B which is in CS department. Once Host B receives this frame, it will remove the 802.1q tag.Problem 30(The following description is short, but contains all major key steps and key protocols involved.)Your computer first uses DHCP to obtain an IP address. You computer first creates a special IP datagram destined to 255.255.255.255 in the DHCP server discovery step, and puts it in a Ethernet frame and broadcast it in the Ethernet. Then following the steps in the DHCP protocol, you computer is able to get an IP address with a given lease time.A DHCP server on the Ethernet also gives your computer a list of IP addresses of first-hop routers, the subnet mask of the subnet where your computer resides, and the addresses of local DNS servers (if they exist).Since your computer’s ARP cache is initially empty, your computer will use ARP protocol to get the MAC addresses of the first-hop router and the local DNS server.Your computer first will get the IP address of the Web page you would like to download. If the local DNS server does not have the IP address, then your computer will use DNS protocol to find the IP address of the Web page.Once your computer has the IP address of the Web page, then it will send out the HTTP request via the first-hop router if the Web page does not reside in a local Web server. The HTTP request message will be segmented and encapsulated into TCP packets, and then further encapsulated into IP packets, and finally encapsulated into Ethernet frames. Your computer sends the Ethernet frames destined to the first-hop router. Once the router receives the frames, it passes them up into IP layer, checks its routing table, and then sends the packets to the right interface out of all of its interfaces.Then your IP packets will be routed through the Internet until they reach the Web server. The server hosting the Web page will send back the Web page to your computer via HTTP response messages. Those messages will be encapsulated into TCP packets and then further into IP packets. Those IP packets follow IP routes and finally reach yourfirst-hop router, and then the router will forward those IP packets to your computer by encapsulating them into Ethernet frames.Problem 32a) Each flow evenly shares a link’s capacity with other flows traversing that link, then the 80 flows crossing the B to access-router 10 Gbps links (as well as the access router to border router links) will each only receive 10 Gbps / 80 = 125 Mbpsb) In Topology of Figure 5.31, there are four distinct paths between the first and third tier-2 switches, together providing 40 Gbps for the traffic from racks 1-4 to racks 9-12. Similarly, there are four links between second and fourth tier-2 switches, together providing 40 Gbps for the traffic from racks 5-8 to 13-16. Thus the total aggregate bandwidth is 80 Gbps, and the value per flow rate is 1 Gbps.c) Now 20 flows will need to share each 1 Gbps bandwidth between pairs of TOR switches. So the host-to-host bit rate will be 0.5 Gbps.Problem 33a)Both email and video application uses the fourth rack for 0.1 percent of the time.b)Probability that both applications need fourth rack is 0.001*0.001 = 10-6.c)Suppose the first three racks are for video, the next rack is a shared rack for bothvideo and email, and the next three racks are for email. Let's assume that thefourth rack has all the data and software needed for both the email and video applications. With the topology of Figure 5.31, both applications will have enough intra-bandwidth as long as both are not simultaneously using the fourth rack.From part b, both are using the fourth rack for no more than .00001 % of time, which is within the .0001% requirement.。

计算机网络课程教学大纲一、课程概述本课程旨在介绍计算机网络的基本概念、原理和技术,帮助学生了解和掌握计算机网络的基本知识和应用。
通过理论教学与实践操作相结合的方式,培养学生的计算机网络分析、设计和管理能力。
二、教学目标1. 理解计算机网络的基本概念和发展历程;2. 掌握计算机网络的体系结构和各层次的功能;3. 理解计算机网络的传输媒介、拓扑结构和网络设备;4. 学习网络编程和网络安全的基本原理和技术;5. 掌握局域网和广域网的组建和管理方法;6. 培养解决计算机网络故障和网络优化的能力。
三、教学内容和进度安排本课程包括以下内容:1. 计算机网络概述- 计算机网络的定义和分类- 计算机网络的发展历程和应用领域- 计算机网络的优缺点2. 网络体系结构- OSI参考模型和TCP/IP协议栈- 各层次的功能和协议- 网络接口和传输介质3. 网络传输和互联- 数据传输的基本原理和方法- 数据传输方式的选择- 局域网和广域网的连接和互联4. 网络设备和拓扑结构- 路由器、交换机和集线器的功能和配置- 网络拓扑结构和布线方案- 网络设备的性能指标和选型5. 网络编程和安全- 网络通信协议和编程接口- 网络编程的基本原理和技术- 网络安全的威胁和防范措施6. 局域网建设和管理- 局域网的组网方案和拓扑结构- 局域网的管理和维护方法- 局域网的性能优化和故障排除7. 广域网的组建和管理- 广域网的连接方式和传输介质- 广域网的路由选择和优化方法- 广域网的带宽管理和故障恢复四、教学方法和评价方式1. 教学方法- 理论授课与案例分析相结合,加强学生对知识的理解和应用;- 实验操作和实际项目实践,巩固学生的动手能力和解决问题的能力;- 虚拟仿真实验和网络模拟软件的使用,提高学生的实践操作能力。
2. 评价方式- 平时表现与实验报告考核;- 课堂测试和小组讨论;- 期末考试或项目实践评估;- 学术论文或研究报告撰写。
五、参考教材1. 《计算机网络(第7版)》- 谢希仁2. 《计算机网络教程》- 毛翔宇3. 《TCP/IP详解卷1:协议》- W. Richard Stevens六、其他说明1. 本大纲仅作为教学参考,请根据教学实际情况进行调整和完善;2. 建议学生配备计算机实验环境,进行网络配置和实验操作;3. 鼓励学生参与网络项目实践和竞赛,提升实践能力和创新思维。

3.《计算机网络技术》课程标准《计算机网络技术》课程标准计算机网络技术是现代社会重要的基础学科之一,它涉及很多领域,如计算机网络的基础知识、网络协议、网络安全等。
为了规范计算机网络技术的教学,制定《计算机网络技术》课程标准是必要的。
本文将对《计算机网络技术》课程标准进行详细论述。
1. 课程目标计算机网络技术的课程目标旨在培养学生具备以下几个方面的能力:(1) 掌握计算机网络的基础知识,了解网络体系结构、传输介质和网络设备等。
(2) 理解网络协议的原理和应用,掌握TCP/IP协议族的工作原理。
(3) 掌握网络安全的基本概念和常见攻击方式,了解安全防护措施。
(4) 掌握网络管理和维护技术,能够进行网络故障排除和性能优化。
2. 课程内容(1) 计算机网络基础知识- 网络体系结构:分层模型、自顶向下设计思想。
- 传输介质:有线和无线传输介质的特点及应用。
- 网络设备:路由器、交换机、集线器等的功能和作用。
(2) 网络协议- TCP/IP协议族:IP地址、子网划分、路由选择和网络地址转换等。
- 网络层协议:IPv4和IPv6的特点及应用。
- 传输层协议:TCP和UDP的特点及应用。
(3) 网络安全- 安全概念:机密性、完整性、可用性等基本概念。
- 防火墙:类型、配置和工作原理。
- 加密与解密:对称加密和非对称加密的原理和应用。
(4) 网络管理与维护- 故障排除:网络故障的类型、定位和解决方法。
- 性能优化:带宽管理、QoS、负载均衡等技术。
3. 教学方法(1) 理论授课:通过讲授理论知识,使学生掌握计算机网络的基本概念和原理。
(2) 实验实践:通过实验操作,使学生巩固理论知识,培养动手能力。
(3) 项目实践:组织学生参与网络设计和部署项目,提高解决实际问题的能力。
(4) 案例分析:通过分析实际网络案例,使学生了解网络故障排除和性能优化的方法。
4. 考核方式(1) 平时成绩:包括课堂表现、实验报告和作业情况等。

一、《计算机网络》第7版,作者:谢希仁1. 本书是深圳大学计算机专业重点推荐教材,全面系统地介绍了计算机网络的基本概念、技术和应用,包括网络体系结构、传输介质、网络协议、网络管理等内容,适合深入学习计算机网络方面的同学参考。
2. 书中内容详实、权威性强,作者谢希仁是我国计算机网络领域的资深专家,他的研究成果被广泛应用在国内外的网络技术领域,该书拥有很高的参考价值。
二、《计算机组成与设计:硬件/软件接口》第5版,作者:DavidA.Patterson, John L.Hennessy1. 该书是计算机体系结构领域的经典教材,主要介绍了计算机系统的各个方面,包括指令级并行、处理器设计、存储系统、I/O系统、并行系统、网络互连等内容,适合对计算机硬件感兴趣的同学参考。
2. 书中涉及的内容丰富多样,涵盖了从传统的计算机系统结构、性能评价到现代的并行计算机体系、多核处理器等前沿技术,对于深入理解计算机组成与设计具有重要的指导意义。
三、《C++ Primer》第5版,作者:Stanley B.Lippman, Josée Lajoie, Barbara E.Moo1. 作为一本权威的C++编程语言教材,该书从基本概念到高级应用都进行了全面覆盖,包括语法、面向对象编程、模板、异常处理、STL 库等内容,适合对C++编程语言感兴趣的同学参考。
2. 本书在国际上获得广泛的赞誉,被誉为C++语言领域的经典之作,对于学习和掌握C++语言的同学来说,是不可多得的宝藏教材。
四、《算法导论(原书第3版)》,作者:Thomas H.Cormen, Charles E.Leiserson, Ronald L.Rivest, Clifford Stein1. 该书是计算机算法领域的经典教材,系统地介绍了算法分析与设计的基本原理,包括递归、排序与顺序统计量、数据结构、图算法、算法问题复杂性等内容,适合对算法与数据结构感兴趣同学参考。

计算机网络课程设计报告书Company Document number:WUUT-WUUY-WBBGB-BWYTT-1982GT《计算机网络》课程设计报告书专业:计嵌班级:计嵌151学号:姓名:张耀目录一、设计题目二、设备选型三、IP地址规划四、拓扑图设计五、主要技术六、配置清单七、总结一、设计题目1、课设目的巩固《计算机网络》和《网络通信》两门课程的知识,在本次课程设计中充分利用前面所学的知识,熟练应用所有技术,系统掌握一个较为复杂的网络配置过程。
在课设中有少量需要的技术教学过程中没有涉及,请自己查阅CCNA资料。
2、课设内容项目背景:某中小型企业有两个部门,销售部(vlan 10)与行政部(vlan 20)。
要求同部门之间采用二层交换网络相连;不同部门之间采用单臂路由方式互访。
企业有一台内部web 服务器,承载内部网站,方便员工了解公司的即时信息.局域网路由器启用多种路由协议(静态路由、动态路由协议),并实施路由控制、负载均衡、链路认证、访问限制等功能.企业有一条专线接到运营商用以连接互联网,采用HDLC封装,由于从运营商只获取到一个公网IP地址,所以企业员工上网需要做NAT网络地址转换,具体拓扑结构如上图所示。
二、设备选型三、IP地址规划四、拓扑图设计五、主要技术Trunk:在路由/交换领域,VLAN的中继端口叫做trunk。
trunk技术用在交换机之间互连,使不同VLAN通过共享链路与其它交换机中的相同VLAN通信。
交换机之间互连的端口就称为trunk端口。
trunk是基于OSI第二层数据链路层(DataLinkLayer)的技术。
Vlan:在计算机网络中,一个二层网络可以被划分为多个不同的广播域,一个广播域对应了一个特定的用户组,默认情况下这些不同的广播域是相互隔离的。
不同的广播域之间想要通信,需要通过一个或多个路由器。
这样的一个广播域就称为VLAN。
单臂路由:在计算机网络中,一个二层网络可以被划分为多个不同的广播域,一个广播域对应了一个特定的用户组,默认情况下这些不同的广播域是相互隔离的。

计算机考研专业课推荐教材 对于准备计算机考研的同学来说,选择合适的专业课教材至关重要。好的教材能够帮助我们系统地掌握知识,提高复习效率,为取得好成绩打下坚实的基础。以下是为大家推荐的一些计算机考研专业课常用教材。
一、数据结构 1、 《数据结构(C 语言版)》严蔚敏、吴伟民 这本书是数据结构领域的经典教材,被众多高校选用。书中详细介绍了线性表、栈和队列、树和二叉树、图等常见数据结构的基本概念、存储结构和操作算法。通过大量的示例和代码实现,帮助读者深入理解数据结构的原理和应用。
2、 《数据结构与算法分析:C++描述(第三版)》Mark Allen Weiss
该书以 C++语言为描述语言,对数据结构和算法进行了全面而深入的分析。不仅涵盖了常见的数据结构,还对算法的时间和空间复杂度进行了详细的讨论,有助于培养读者的算法分析和设计能力。
二、计算机组成原理 1、 《计算机组成原理(第 2 版)》唐朔飞 这本教材内容丰富,条理清晰,从计算机的基本组成、运算方法、存储系统、指令系统到中央处理器和总线系统等方面进行了系统的阐述。书中配有大量的图表和实例,便于读者理解和掌握。
2、 《计算机组成与设计:硬件/软件接口(原书第 5 版)》David A Patterson、John L Hennessy
该书是计算机组成原理领域的权威教材之一,以全新的视角和方法介绍了计算机硬件系统的设计与实现。书中强调了硬件与软件的接口,使读者能够更好地理解计算机系统的整体工作原理。
三、操作系统 1、 《操作系统—内核与设计原理(第 7 版)》William Stallings 这本书详细介绍了操作系统的基本概念、进程管理、内存管理、文件系统和输入输出系统等核心内容。书中的示例丰富,讲解透彻,有助于读者建立起对操作系统的全面认识。
2、 《操作系统概念(第 9 版)》Abraham Silberschatz、Peter B Galvin、Greg Gagne

第一章1、(09-33)在OSI参考模型中,自下而上第一个提供端到端服务的层次是()A.数据链路层??B.传输层??C.会话层??D.应用层??2、(10-33)下列选项中,不属于网络体系结构中所描述的内容是()A.网络的层次B.每一层使用的协议C.协议的内部实现细节D.每一层必须完成的功能3、(10-34)在下图所示的采用“存储-转发”方式分组的交换网络中,所有链路的数据传输速度为100Mbps,分组大小为1000B,其中分组头大小20B,若主机H1向主机H2发送一个大小为980000B的文件,则在不考虑分组拆装时间和传播延迟的情况下,从H1发送到H2接收完为止,需要的时间至少是()A:80ms B: C: D:4、(11-33)TCP/IP参考模型的网络层提供的是()A.无连接不可靠的数据报服务 B.无连接可靠的数据报服务C.有连接不可靠的虚电路服务 D.有连接可靠的虚电路服务5、(12-33)在TCP/IP体系结构中,直接为ICMP提供服务协议的是:()A. PPPB. IPC. UDPD. TCP6、(13-33)在OSI参考模型中,下列功能需由应用层的相邻层实现的是()A.对话管理B.数据格式转换C.路由选择D.可靠数据传输7.(13-35)主机甲通过1个路由器(存储转发方式)与主机乙互联,两段链路的数据传输速率均为10Mbps,主机甲分别采用报文交换和分组大小为10kb的分组交换向主机乙发送1个大小为8Mb(1M=106)的报文。
若忽略链路传播延迟、分组头开销和分组拆装时间,则两种交换方式完成该报文传输所需的总时间分别为()、1600ms 、1600ms、800ms、 D、1600ms、801ms8.(14-33)在OSI参考模型中,直接为会话层提供服务的是()A.应用层 B表示层 C传输层 D网络层参考答案:第二章1.(09-34)在无噪声情况下,若某通信链路的带宽为3kHz,采用4个相位,每个相位具有4种振幅的QAM调制技术,则该通信链路的最大数据传输速率是()A.12kbps注:1924年奈奎斯特(Nyquist)就推导出在理想低通信道的最高大码元传输速率的公式:理想低通信道的最高大码元传输速率C= (其中W是想低通信道的带宽,N是电平强度)。

计算机网络教学大纲一、课程概述计算机网络是现代信息技术的核心基础,它实现了各种设备之间的互联互通,促进了信息的传递和共享。
本课程旨在介绍计算机网络的基本原理、协议和应用,使学生全面了解计算机网络的基本概念和技术。
二、教学目标1. 掌握计算机网络的基本概念,包括网络拓扑、协议、传输介质等。
2. 理解计算机网络的分层结构,并能够深入了解每个网络层次的功能和作用。
3. 熟悉网络通信协议的原理和应用,包括TCP/IP协议族、以太网等。
4. 掌握网络安全与管理的基本知识,包括网络攻击与防护、网络性能优化等。
5. 能够运用所学知识,设计和实施简单的计算机网络。
三、教学内容与安排1. 计算机网络基础知识- 计算机网络概述- 网络拓扑结构- 子网划分与路由选择2. 网络通信协议- OSI参考模型- TCP/IP协议族- 以太网及其扩展3. 网络传输介质- 有线传输介质- 无线传输介质4. 网络安全与管理- 网络攻击与防护- 网络性能优化- 网络管理与监控5. 计算机网络设计与实施 - 网络设计原则与方法 - 网络实施与部署- 网络故障排除与维护四、教学方法与要求1. 授课方式:理论讲解、案例分析、实验演示等相结合。
2. 学生参与:通过小组讨论、课堂互动等方式促进学生主动参与和思考。
3. 实践环节:设计实验和项目,让学生在实践中巩固所学知识。
4. 教学资源:提供相应的教材、教学课件和实验设备。
5. 学习评估:通过作业、考试和项目评估学生的学习效果。
五、考核方式1. 平时成绩:包括作业、实验报告、课堂表现等。
2. 期中考试:对学生对课堂理论知识的掌握程度进行评估。
3. 期末考试:综合考察学生对整个课程内容的理解和应用能力。
六、参考教材1. 《计算机网络》第7版,谢希仁,高教出版社2. 《TCP/IP网络配置与管理》第4版,Beale与Sidnie Feit,机械工业出版社七、备注本教学大纲仅供参考,具体教学内容和安排可能根据实际情况进行调整。

全国计算机等级考试一级b计算机是当今社会的重要组成部分,计算机等级考试是评估一个人计算机技能程度的考试。
全国计算机等级考试分为一级、二级、三级和四级,分别对应着不同的技能水平。
本文将重点介绍全国计算机等级考试一级B考试,涵盖考试内容、考试要求、参考书籍等方面的内容。
一、考试内容全国计算机等级考试一级B考试的主要内容包括以下四个方面:(一)计算机软件基础包括计算机软件基本概念、常用软件的使用和安装、操作系统基础、应用软件基础等内容。
(二)计算机硬件基础包括计算机硬件基本概念、计算机组成原理、计算机外设及其使用等内容。
(三)计算机网络基础包括计算机网络基本概念、网络应用及其安装、网络协议及其应用等内容。
(四)信息安全基础包括信息安全基本概念、计算机病毒、防火墙、网络攻击及其防范、用户密码安全等内容。
二、考试要求参加全国计算机等级考试一级B考试需要符合以下几个方面的要求:(一)考试对象:计算机使用者。
(二)考试时间:2小时。
(三)考试形式:闭卷笔试。
(四)考试分数:满分为100分,及格分数为60分。
(五)考试方式:机考或手工考试,考生可根据自身需求选择应考方式。
三、参考书籍参加全国计算机等级考试一级B考试需要认真备考,以下是一些备考参考书籍,供考生参考:(一)计算机软件基础1、《Office 2010操作指南》2、《Windows 7实用技巧》3、《计算机操作系统原理与实践》(二)计算机硬件基础1、《计算机组成实验教程》2、《数字电路与系统设计教程》3、《计算机外设管理与维护》(三)计算机网络基础1、《计算机网络(第7版)》2、《TCP/IP详解卷1:协议》3、《计算机网络与通信:基础篇》(四)信息安全基础1、《信息安全概论》2、《计算机病毒防治技术》3、《网络安全技术与实践》四、考试经验参加全国计算机等级考试一级B考试需要有一定的考试经验,以下是一些考试经验,供考生参考:(一)充分掌握考试内容,理清考试思路。
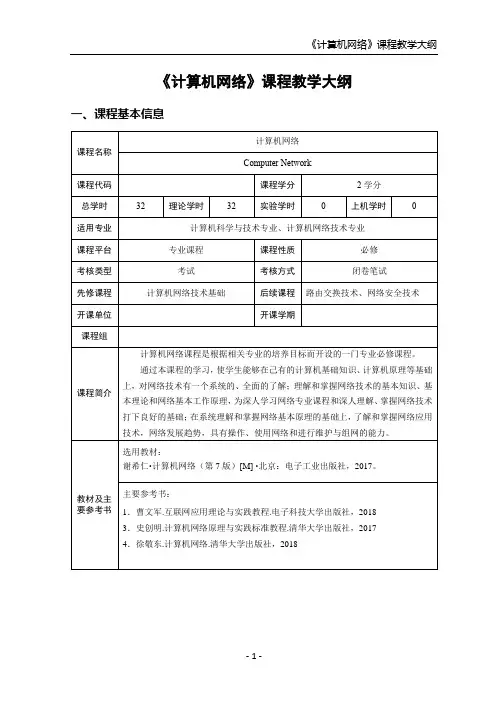
《计算机网络》课程教学大纲一、课程基本信息二、总体教学目标1.知识目标本课程的主要教学环节为理论教学,课程教学的主要目标是使学生掌握有关计算机网络的基础知识、基本理论和基本方法,培养学生对计算机网络协议体系结构的掌握和应用,为将来从事网络工程类工作奠定基础。
具体的知识目标如下:1.1了解计算机网络的产生和发展,掌握计算机网络的工作原理、协议和体系结构,并对OSI 参考模型和TCP/IP体系结构有较深的理解;1.2掌握局域网的体系结构、工作原理和组网要求,能够规划、组建、调试和维护局域网,并能够划分VLAN;1.3理解广域网的基本概念和工作原理,掌握网络层相关的协议,尤其是路由协议,会规划和配置广域网;1.4理解传输层的功能和端口的作用,掌握传输层协议的工作原理,尤其是TCP的建立管理、传输策略、拥塞控制及定时器管理;1.5理解应用层常用协议的工作原理,并能在理解的基础上配置WWW、DNS、FTP、Telnet、E-mail等常用的服务。
2.能力目标基于本课程的专业核心地位,在课程教学过程中要注重学生能力的培养,为将来从事本专业工作及跨学科和专业工作奠定基础。
具体的能力目标如下:2.1 培养学生设计思维和创新能力;2.2 培养学生的自学(终身学习)能力;2.3 培养学生分析问题解决问题的能力;2.4 培养学生具有设计网络拓扑的能力;2.5 培养学生达到运用所学知识解决网络工程实际问题的能力;2.6 培养学生运用网络工程相关技术手段进行网络组网设计的能力。
3.思政目标在教学过程中恰当融入思政育人元素,加强大学生的科学精神、工匠精神的培养,通过思政案例讲解指引大学生的人生观、价值观及世界观,将知识传播、价值塑造和能力培养有机融合,将立德树人的根本任务落实到课程教学过程之中。
具体的思政目标如下:3.1 培养和增强学生的爱国主义情怀;3.2 培养大学生职业道德素养和职业操守意识;3.3 培养和增强学生科技强国、报国的自豪感和自信心;3.4 培养和增强学生精益求精的专业精神和严谨规范的工匠精神;3.5 培养学生的环境保护意识、树立可持续发展观和职业使命感;3.6 引入哲学思维,培养学生形成正确的世界观、人生观和价值观。
计算机基础近五年的参考文献
以下是近五年内计算机基础方面的一些参考文献:
1. 《计算机组成原理》(第2版),唐朔飞,机械工业出版社,2017年。
2. 《计算机网络:自顶向下方法》(第7版),詹姆斯·F·库鲁姆,基思·W·罗斯,机械工业出版社,2017年。
3. 《计算机操作系统》(第4版),安德鲁·S·坦尼鲍姆,机械工业出版社,2015年。
4. 《计算机算法设计与分析》(第5版),David M. Mount,机械工业出版社,2017年。
5. 《计算机体系结构:量化研究方法》(第6版),John L. Hennessy,David A. Patterson,机械工业出版社,2018年。
6. 《计算机图形学:原理与实践》(第3版),Peter Shirley,Steve Marschner,机械工业出版社,2016年。
7. 《计算机科学导论》(第11版),J. Glenn Brookshear,机械工业出版社,2017年。
8. 《计算机体系结构与组成原理》(第2版),陈向群,高等教育出版社,2016年。
9. 《计算机程序设计艺术》(卷1-3),Donald E. Knuth,机械工业出版社,2017年。
10. 《计算机视觉:模型、学习和推理》(第2版),Simon J. D. Prince,机械工业出版社,2018年。
以上是一些比较经典的计算机基础方面的参考文献,供您参考。
信息工程专业参考文献
1. 《计算机网络,自顶向下方法》(原书第7版)作者,James F. Kurose, Keith W. Ross.
这本书是计算机网络领域的经典教材,涵盖了计算机网络的
基本原理、协议和应用,适合信息工程专业的学生和研究人员参考。
2. 《数据通信和计算机网络》(第7版)作者,Behrouz A. Forouzan.
该书介绍了数据通信和计算机网络的基本概念、协议和技术,包括数据链路层、网络层、传输层和应用层的内容,适合信息工程
专业的学生学习和参考。
3. 《数字通信》(第5版)作者,John G. Proakis, Masoud Salehi.
该书详细介绍了数字通信系统的原理、技术和应用,包括调
制解调、信道编码、多址接入等内容,是信息工程专业数字通信课
程的重要参考书籍。
4. 《信号与系统》(第2版)作者,Alan V. Oppenheim,
Alan S. Willsky, S. Hamid Nawab.
该书系统地介绍了信号与系统的基本理论、分析方法和应用,对于信息工程专业的学生来说是一本重要的参考书。
5. 《数字图像处理》(第4版)作者,Rafael C. Gonzalez, Richard E. Woods.
该书介绍了数字图像处理的基本原理、算法和应用,对于信
息工程专业的学生和研究人员来说是一本权威的参考书籍。
以上这些参考文献涵盖了信息工程专业的多个领域,包括计算
机网络、数据通信、数字信号处理、图像处理等,对于信息工程专
业的学习和研究都具有重要的参考价值。
希望这些参考文献能够对
你有所帮助。
Computer Networking: A Top-Down Approach,7th EditionSolutions to Review Questions and Problems Version Date: December 2016This document contains the solutions to review questions and problems for the 7th edition of Computer Networking: A Top-Down Approach by Jim Kurose and Keith Ross. These solutions are being made available to instructors ONLY. Please do NOT copy or distribute this document to others (even other instructors). Please do not post any solutions on a publicly-available Web site. We’ll be happy to provide a copy (up-to-date) of this solution manual ourselves to anyone who asks.Acknowledgments:Over the years, several students and colleagues have helped us prepare this solutions manual. Special thanks goes to Honggang Zhang, Rakesh Kumar, Prithula Dhungel, and Vijay Annapureddy. Also thanks to all the readers who have made suggestions and corrected errors.All material © copyright 1996-2016 by J.F. Kurose and K.W. Ross. All rights reserved Chapter 1 Review Questions1.There is no difference. Throughout this text, the words “host” and “end system” areused interchangeably. End systems include PCs, workstations, Web servers, mail servers, PDAs, Internet-connected game consoles, etc.2.From Wikipedia: Diplomatic protocol is commonly described as a set of internationalcourtesy rules. These well-established and time-honored rules have made it easier for nations and people to live and work together. Part of protocol has always been the acknowledgment of the hierarchical standing of all present. Protocol rules are based on the principles of civility.3.Standards are important for protocols so that people can create networking systemsand products that interoperate.4. 1. Dial-up modem over telephone line: home; 2. DSL over telephone line: home orsmall office; 3. Cable to HFC: home; 4. 100 Mbps switched Ethernet: enterprise; 5.Wifi (802.11): home and enterprise: 6. 3G and 4G: wide-area wireless.5.HFC bandwidth is shared among the users. On the downstream channel, all packetsemanate from a single source, namely, the head end. Thus, there are no collisions in the downstream channel.6.In most American cities, the current possibilities include: dial-up; DSL; cable modem;fiber-to-the-home.7. Ethernet LANs have transmission rates of 10 Mbps, 100 Mbps, 1 Gbps and 10 Gbps.8. Today, Ethernet most commonly runs over twisted-pair copper wire. It also can runover fibers optic links.9. Dial up modems: up to 56 Kbps, bandwidth is dedicated; ADSL: up to 24 Mbpsdownstream and 2.5 Mbps upstream, bandwidth is dedicated; HFC, rates up to 42.8 Mbps and upstream rates of up to 30.7 Mbps, bandwidth is shared. FTTH: 2-10Mbps upload; 10-20 Mbps download; bandwidth is not shared.10. There are two popular wireless Internet access technologies today:a)Wifi (802.11) In a wireless LAN, wireless users transmit/receive packets to/from anbase station (i.e., wireless access point) within a radius of few tens of meters. The base station is typically connected to the wired Internet and thus serves to connect wireless users to the wired network.b)3G and 4G wide-area wireless access networks. In these systems, packets aretransmitted over the same wireless infrastructure used for cellular telephony, with the base station thus being managed by a telecommunications provider. This provides wireless access to users within a radius of tens of kilometers of the base station.11. At time t0the sending host begins to transmit. At time t1 = L/R1, the sending hostcompletes transmission and the entire packet is received at the router (no propagationdelay). Because the router has the entire packet at time t 1, it can begin to transmit the packet to the receiving host at time t 1. At time t 2 = t 1 + L/R 2, the router completes transmission and the entire packet is received at the receiving host (again, no propagation delay). Thus, the end-to-end delay is L/R 1 + L/R 2.12. A circuit-switched network can guarantee a certain amount of end-to-end bandwidth for the duration of a call. Most packet-switched networks today (including the Internet) cannot make any end-to-end guarantees for bandwidth. FDM requires sophisticated analog hardware to shift signal into appropriate frequency bands .13. a) 2 users can be supported because each user requires half of the link bandwidth.b) Since each user requires 1Mbps when transmitting, if two or fewer users transmit simultaneously, a maximum of 2Mbps will be required. Since the available bandwidth of the shared link is 2Mbps, there will be no queuing delay before the link. Whereas, if three users transmit simultaneously, the bandwidth required will be 3Mbps which is more than the available bandwidth of the shared link. In this case, there will be queuing delay before the link.c) Probability that a given user is transmitting = 0.2d) Probability that all three users are transmitting simultaneously = ()333133--⎪⎪⎭⎫ ⎝⎛p p = (0.2)3 = 0.008. Since the queue grows when all the users are transmitting, thefraction of time during which the queue grows (which is equal to the probability that all three users are transmitting simultaneously) is 0.008.14. If the two ISPs do not peer with each other, then when they send traffic to each other they have to send the traffic through a provider ISP (intermediary), to which they have to pay for carrying the traffic. By peering with each other directly, the two ISPs can reduce their payments to their provider ISPs. An Internet Exchange Points (IXP) (typically in a standalone building with its own switches) is a meeting point where multiple ISPs can connect and/or peer together. An ISP earns its money by charging each of the the ISPs that connect to the IXP a relatively small fee, which may depend on the amount of traffic sent to or received from the IXP.15. Google's private network connects together all its data centers, big and small. Traffic between the Google data centers passes over its private network rather than over the public Internet. Many of these data centers are located in, or close to, lower tier ISPs. Therefore, when Google delivers content to a user, it often can bypass higher tier ISPs. What motivates content providers to create these networks? First, the content provider has more control over the user experience, since it has to use few intermediary ISPs. Second, it can save money by sending less traffic into provider networks. Third, if ISPs decide to charge more money to highly profitable content providers (in countries where net neutrality doesn't apply), the content providers can avoid these extra payments.16. The delay components are processing delays, transmission delays, propagation delays,and queuing delays. All of these delays are fixed, except for the queuing delays, which are variable.17. a) 1000 km, 1 Mbps, 100 bytesb) 100 km, 1 Mbps, 100 bytes18. 10msec; d/s; no; no19. a) 500 kbpsb) 64 secondsc) 100kbps; 320 seconds20. End system A breaks the large file into chunks. It adds header to each chunk, therebygenerating multiple packets from the file. The header in each packet includes the IP address of the destination (end system B). The packet switch uses the destination IP address in the packet to determine the outgoing link. Asking which road to take is analogous to a packet asking which outgoing link it should be forwarded on, given the packet’s destination address.21. The maximum emission rate is 500 packets/sec and the maximum transmission rate is350 packets/sec. The corresponding traffic intensity is 500/350 =1.43 > 1.Loss will eventually occur for each experiment;but the time when loss first occurs will be different from one experiment to the next due to the randomness in the emission process.22. Five generic tasks are error control, flow control, segmentation and reassembly,multiplexing, and connection setup. Yes, these tasks can be duplicated at different layers. For example, error control is often provided at more than one layer.23. The five layers in the Internet protocol stack are –from top to bottom –theapplication layer, the transport layer, the network layer, the link layer, and the physical layer. The principal responsibilities are outlined in Section 1.5.1.24. Application-layer message: data which an application wants to send and passed ontothe transport layer; transport-layer segment: generated by the transport layer and encapsulates application-layer message with transport layer header; network-layer datagram: encapsulates transport-layer segment with a network-layer header; link-layer frame: encapsulates network-layer datagram with a link-layer header.25. Routers process network, link and physical layers (layers 1 through 3). (This is a littlebit of a white lie, as modern routers sometimes act as firewalls or caching components, and process Transport layer as well.) Link layer switches process link and physical layers (layers 1 through2). Hosts process all five layers.26. a) VirusRequires some form of human interaction to spread. Classic example: E-mail viruses.b) WormsNo user replication needed. Worm in infected host scans IP addresses and portnumbers, looking for vulnerable processes to infect.27. Creation of a botnet requires an attacker to find vulnerability in some application orsystem (e.g. exploiting the buffer overflow vulnerability that might exist in an application). After finding the vulnerability, the attacker needs to scan for hosts that are vulnerable. The target is basically to compromise a series of systems by exploiting that particular vulnerability. Any system that is part of the botnet can automatically scan its environment and propagate by exploiting the vulnerability. An important property of such botnets is that the originator of the botnet can remotely control and issue commands to all the nodes in the botnet. Hence, it becomes possible for the attacker to issue a command to all the nodes, that target a single node (for example, all nodes in the botnet might be commanded by the attacker to send a TCP SYN message to the target, which might result in a TCP SYN flood attack at the target).28. Trudy can pretend to be Bob to Alice (and vice-versa) and partially or completelymodify the message(s) being sent from Bob to Alice. For example, she can easily change the phrase “Alice, I owe you $1000” to “Alice, I owe you $10,000”.Furthermore, Trudy can even drop the packets that are being sent by Bob to Alice (and vise-versa), even if the packets from Bob to Alice are encrypted.Chapter 1 ProblemsProblem 1There is no single right answer to this question. Many protocols would do the trick. Here's a simple answer below:Messages from ATM machine to ServerMsg name purpose-------- -------HELO <userid> Let server know that there is a card in theATM machineATM card transmits user ID to ServerPASSWD <passwd> User enters PIN, which is sent to server BALANCE User requests balanceWITHDRAWL <amount> User asks to withdraw moneyBYE user all doneMessages from Server to ATM machine (display)Msg name purpose-------- -------PASSWD Ask user for PIN (password)OK last requested operation (PASSWD, WITHDRAWL)OKERR last requested operation (PASSWD, WITHDRAWL)in ERRORAMOUNT <amt> sent in response to BALANCE requestBYE user done, display welcome screen at ATM Correct operation:client serverHELO (userid) --------------> (check if valid userid)<------------- PASSWDPASSWD <passwd> --------------> (check password)<------------- OK (password is OK)BALANCE --------------><------------- AMOUNT <amt>WITHDRAWL <amt> --------------> check if enough $ to coverwithdrawl<------------- OKATM dispenses $BYE --------------><------------- BYEIn situation when there's not enough money:HELO (userid) --------------> (check if valid userid)<------------- PASSWDPASSWD <passwd> --------------> (check password)<------------- OK (password is OK)BALANCE --------------><------------- AMOUNT <amt>WITHDRAWL <amt> --------------> check if enough $ to cover withdrawl<------------- ERR (not enough funds)error msg displayedno $ given outBYE --------------><------------- BYEProblem 2At time N*(L/R) the first packet has reached the destination, the second packet is stored in the last router, the third packet is stored in the next-to-last router, etc. At time N*(L/R) + L/R, the second packet has reached the destination, the third packet is stored in the last router, etc. Continuing with this logic, we see that at time N*(L/R) + (P-1)*(L/R) = (N+P-1)*(L/R) all packets have reached the destination.Problem 3a) A circuit-switched network would be well suited to the application, because theapplication involves long sessions with predictable smooth bandwidth requirements.Since the transmission rate is known and not bursty, bandwidth can be reserved for each application session without significant waste. In addition, the overhead costs of setting up and tearing down connections are amortized over the lengthy duration of a typical application session.b) In the worst case, all the applications simultaneously transmit over one or morenetwork links. However, since each link has sufficient bandwidth to handle the sum of all of the applications' data rates, no congestion (very little queuing) will occur.Given such generous link capacities, the network does not need congestion control mechanisms.Problem 4a)Between the switch in the upper left and the switch in the upper right we can have 4connections. Similarly we can have four connections between each of the 3 other pairs of adjacent switches. Thus, this network can support up to 16 connections.b)We can 4 connections passing through the switch in the upper-right-hand corner andanother 4connections passing through the switch in the lower-left-hand corner, giving a total of 8 connections.c) Yes. For the connections between A and C, we route two connections through B and two connections through D. For the connections between B and D, we route two connections through A and two connections through C. In this manner, there are at most 4 connections passing through any link.Problem 5Tollbooths are 75 km apart, and the cars propagate at 100km/hr. A tollbooth services a car at a rate of one car every 12 seconds.a) There are ten cars. It takes 120 seconds, or 2 minutes, for the first tollbooth to service the 10 cars. Each of these cars has a propagation delay of 45 minutes (travel 75 km) before arriving at the second tollbooth. Thus, all the cars are lined up before the second tollbooth after 47 minutes. The whole process repeats itself for traveling between the second and third tollbooths. It also takes 2 minutes for the third tollbooth to service the 10 cars. Thus the total delay is 96 minutes.b) Delay between tollbooths is 8*12 seconds plus 45 minutes, i.e., 46 minutes and 36 seconds. The total delay is twice this amount plus 8*12 seconds, i.e., 94 minutes and 48 seconds.Problem 6a) s m d prop /= seconds.b) R L d trans /= seconds.c) )//(R L s m d end to end +=-- seconds.d) The bit is just leaving Host A.e) The first bit is in the link and has not reached Host B.f) The first bit has reached Host B. g) Want()536105.2105612083=⨯⨯==s R L m km.Problem 7Consider the first bit in a packet. Before this bit can be transmitted, all of the bits in the packet must be generated. This requires31064856⨯⋅sec=7msec.The time required to transmit the packet is6102856⨯⋅sec=μ224sec.Propagation delay = 10 msec.The delay until decoding is7msec +μ224sec + 10msec = 17.224msecA similar analysis shows that all bits experience a delay of 17.224 msec.Problem 8a) 20 users can be supported.b) 1.0=p .c) ()n n p p n --⎪⎪⎭⎫ ⎝⎛1201120. d) ()∑=--⎪⎪⎭⎫ ⎝⎛-20012011201n n n p p n . We use the central limit theorem to approximate this probability. Let j X be independentrandom variables such that ()p X P j ==1.(P “21 or more users”)⎪⎪⎭⎫ ⎝⎛≤-=∑=2111201j j X P⎪⎪⎪⎭⎫ ⎝⎛⋅⋅≤⋅⋅-=⎪⎪⎭⎫ ⎝⎛≤∑∑==9.01.012099.01.0120122112011201j j j j X P X P ()74.2286.39≤=⎪⎭⎫ ⎝⎛≤≈Z P Z P 997.0=when Z is a standard normal r.v. Thus (P “21 or more users”)003.0≈.Problem 9a) 10,000b) ()∑+=--⎪⎪⎭⎫ ⎝⎛M N n n M n p p n M 11Problem 10The first end system requires L/R1 to transmit the packet onto the first link; the packet propagates over the first link in d1/s1; the packet switch adds a processing delay of d proc; after receiving the entire packet, the packet switch connecting the first and the second link requires L/R2 to transmit the packet onto the second link; the packet propagates over the second link in d2/s2. Similarly, we can find the delay caused by the second switch and the third link: L/R3, d proc, and d3/s3.Adding these five delays givesd end-end = L/R1 + L/R2 + L/R3 + d1/s1 + d2/s2 + d3/s3+ d proc+ d procTo answer the second question, we simply plug the values into the equation to get 6 + 6 + 6 + 20+16 + 4 + 3 + 3 = 64 msec.Problem 11Because bits are immediately transmitted, the packet switch does not introduce any delay; in particular, it does not introduce a transmission delay. Thus,d end-end = L/R + d1/s1 + d2/s2+ d3/s3For the values in Problem 10, we get 6 + 20 + 16 + 4 = 46 msec.Problem 12The arriving packet must first wait for the link to transmit 4.5 *1,500 bytes = 6,750 bytes or 54,000 bits. Since these bits are transmitted at 2 Mbps, the queuing delay is 27 msec. Generally, the queuing delay is (nL + (L - x))/R.Problem 13a)The queuing delay is 0 for the first transmitted packet, L/R for the second transmittedpacket, and generally, (n-1)L/R for the n th transmitted packet. Thus, the average delay for the N packets is:(L/R + 2L/R + ....... + (N-1)L/R)/N= L/(RN) * (1 + 2 + ..... + (N-1))= L/(RN) * N(N-1)/2= LN(N-1)/(2RN)= (N-1)L/(2R)Note that here we used the well-known fact:1 +2 + ....... + N = N(N+1)/2b) It takes R LN / seconds to transmit the N packets. Thus, the buffer is empty when a each batch of N packets arrive. Thus, the average delay of a packet across all batches is the average delay within one batch, i.e., (N-1)L /2R .Problem 14a) The transmission delay is R L /. The total delay isI RL R L I R IL -=+-1/)1(b) Let R L x /=.Total delay = axx-1For x=0, the total delay =0; as we increase x, total delay increases, approaching infinity as x approaches 1/a.Problem 15Total delay aa R aL R L I R L -=-=-=-=μμμ1/1/1/1/1/.Problem 16The total number of packets in the system includes those in the buffer and the packet that is being transmitted. So, N=10+1.Because d a N ⋅=, so (10+1)=a*(queuing delay + transmission delay). That is, 11=a*(0.01+1/100)=a*(0.01+0.01). Thus, a=550 packets/sec.Problem 17a) There are Q nodes (the source host and the 1-Q routers). Let qproc d denote the processing delay at the q th node. Let q R be the transmission rate of the q th link and letq qtrans R L d /=. Let q prop d be the propagation delay across the q th link. Then[]∑=--++=Qq qprop q trans q proc end to end d d d d 1.b) Let qqueue d denote the average queuing delay at node q . Then[]∑=--+++=Qq qqueue q prop q trans q proc end to end d d d d d 1.Problem 18On linux you can use the commandtraceroute and in the Windows command prompt you can usetracert In either case, you will get three delay measurements. For those three measurements you can calculate the mean and standard deviation. Repeat the experiment at different times of the day and comment on any changes .Here is an example solution:Traceroutes between San Diego Super Computer Center and a)The average (mean) of the round-trip delays at each of the three hours is 71.18 ms,71.38 ms and 71.55 ms, respectively. The standard deviations are 0.075 ms, 0.21 ms,0.05 ms, respectively.b)In this example, the traceroutes have 12 routers in the path at each of the three hours.No, the paths didn’t change during any of the hours.c)Traceroute packets passed through four ISP networks from source to destination. Yes,in this experiment the largest delays occurred at peering interfaces between adjacent ISPs.Traceroutes from (France) to (USA).d)The average round-trip delays at each of the three hours are 87.09 ms, 86.35 ms and86.48 ms, respectively. The standard deviations are 0.53 ms, 0.18 ms, 0.23 ms,respectively. In this example, there are 11 routers in the path at each of the three hours. No, the paths didn’t change during any of the hours. Traceroute packets passed three ISP networks from source to destination. Yes, in this experiment the largest delays occurred at peering interfaces between adjacent ISPs.Problem 19An example solution:Traceroutes from two different cities in France to New York City in United States a)In these traceroutes from two different cities in France to the same destination host inUnited States, seven links are in common including the transatlantic link.b)In this example of traceroutes from one city in France and from another city inGermany to the same host in United States, three links are in common including the transatlantic link.Traceroutes to two different cities in China from same host in United Statesc) Five links are common in the two traceroutes. The two traceroutes diverge before reaching ChinaProblem 20Throughput = min{R s , R c , R/M}Problem 21If only use one path, the max throughput is given by:}},,,m in{,},,,,min{},,,,m ax {m in{212222111211MN M M N N R R R R R R R R R .If use all paths, the max throughput is given by ∑=Mk kN k k R R R 121},,,min{ .Problem 22Probability of successfully receiving a packet is: p s = (1-p)N .The number of transmissions needed to be performed until the packet is successfully received by the client is a geometric random variable with success probability p s . Thus, the average number of transmissions needed is given by: 1/p s . Then, the average number of re-transmissions needed is given by: 1/p s -1.Problem 23Let’s call the first packet A and call the second packet B.a) If the bottleneck link is the first link, then packet B is queued at the first link waiting for the transmission of packet A. So the packet inter-arrival time at the destination is simply L/R s .b) If the second link is the bottleneck link and both packets are sent back to back, it must be true that the second packet arrives at the input queue of the second link before the second link finishes the transmission of the first packet. That is,L/R s + L/R s + d prop < L/R s + d prop + L/R cThe left hand side of the above inequality represents the time needed by the second packet to arrive at the input queue of the second link (the second link has not startedtransmitting the second packet yet). The right hand side represents the time needed by the first packet to finish its transmission onto the second link.If we send the second packet T seconds later, we will ensure that there is no queuing delay for the second packet at the second link if we have:L/R s + L/R s + d prop + T >= L/R s + d prop + L/R cThus, the minimum value of T is L/R c L/R s .Problem 2440 terabytes = 40 * 1012 * 8 bits. So, if using the dedicated link, it will take 40 * 1012 * 8 / (100 *106 ) =3200000 seconds = 37 days. But with FedEx overnight delivery, you can guarantee the data arrives in one day, and it should cost less than $100.Problem 25a)160,000 bitsb)160,000 bitsc)The bandwidth-delay product of a link is the maximum number of bits that can be inthe link.d)the width of a bit = length of link / bandwidth-delay product, so 1 bit is 125 meterslong, which is longer than a football fielde) s/RProblem 26s/R=20000km, then R=s/20000km= 2.5*108/(2*107)= 12.5 bpsProblem 27a)80,000,000 bitsb)800,000 bits, this is because that the maximum number of bits that will be in the linkat any given time = min(bandwidth delay product, packet size) = 800,000 bits.c).25 metersProblem 28a)t trans + t prop = 400 msec + 80 msec = 480 msec.b)20 * (t trans + 2 t prop) = 20*(20 msec + 80 msec) = 2 sec.c) Breaking up a file takes longer to transmit because each data packet and its corresponding acknowledgement packet add their own propagation delays.Problem 29Recall geostationary satellite is 36,000 kilometers away from earth surface. a) 150 msec b) 1,500,000 bits c) 600,000,000 bitsProblem 30Let’s suppose the passenger and his/her bags correspond to the data unit arriving to the top of the protocol stack. When the passenger checks in, his/her bags are checked, and a tag is attached to the bags and ticket. This is additional information added in the Baggage layer if Figure 1.20 that allows the Baggage layer to implement the service or separating the passengers and baggage on the sending side, and then reuniting them (hopefully!) on the destination side. When a passenger then passes through security and additional stamp is often added to his/her ticket, indicating that the passenger has passed through a security check. This information is used to ensure (e.g., by later checks for the security information) secure transfer of people.Problem 31a)Time to send message from source host to first packet switch = sec 4sec 10210866=⨯⨯With store-and-forward switching, the total time to move message from source host to destination host = sec 123sec 4=⨯hopsb)Time to send 1st packet from source host to first packet switch = . sec 5sec 10210164m =⨯⨯. Time at which 2nd packet is received at the first switch = time at which 1st packet is received at the second switch = sec 10sec 52m m =⨯c)Time at which 1st packet is received at the destination host = sec 153sec 5m hops m =⨯. After this, every 5msec one packet will be received; thus time at which last (800th ) packet is received = sec 01.4sec 5*799sec 15=+m m . It can be seen that delay in using message segmentation is significantly less (almost 1/3rd ). d)i. Without message segmentation, if bit errors are not tolerated, if there is asingle bit error, the whole message has to be retransmitted (rather than a single packet).ii. Without message segmentation, huge packets (containing HD videos, forexample) are sent into the network. Routers have to accommodate these hugepackets. Smaller packets have to queue behind enormous packets and suffer unfair delays.e)i. Packets have to be put in sequence at the destination.ii. Message segmentation results in many smaller packets. Since header size is usually the same for all packets regardless of their size, with message segmentation the total amount of header bytes is more.Problem 32Yes, the delays in the applet correspond to the delays in the Problem 31.The propagation delays affect the overall end-to-end delays both for packet switching and message switching equally.Problem 33There are F /S packets. Each packet is S=80 bits. Time at which the last packet is receivedat the first router is SFR S ⨯+80sec. At this time, the first F/S-2 packets are at thedestination, and the F/S-1 packet is at the second router. The last packet must then be transmitted by the first router and the second router, with each transmission taking R S 80+sec. Thus delay in sending the whole file is )2(80+⨯+=S FR S delay To calculate the value of S which leads to the minimum delay, F S delay dS d400=⇒=Problem 34The circuit-switched telephone networks and the Internet are connected together at "gateways". When a Skype user (connected to the Internet) calls an ordinary telephone, a circuit is established between a gateway and the telephone user over the circuit switched network. The skype user's voice is sent in packets over the Internet to the gateway. At the gateway, the voice signal is reconstructed and then sent over the circuit. In the other direction, the voice signal is sent over the circuit switched network to the gateway. The gateway packetizes the voice signal and sends the voice packets to the Skype user.。
第一章1、(09-33)在OSI参考模型中,自下而上第一个提供端到端服务的层次是()A.数据链路层 B.传输层 C.会话层 D.应用层2、(10-33)下列选项中,不属于网络体系结构中所描述的内容是()A.网络的层次B.每一层使用的协议C.协议的内部实现细节D.每一层必须完成的功能3、(10-34)在下图所示的采用“存储-转发”方式分组的交换网络中,所有链路的数据传输速度为100Mbps,分组大小为1000B,其中分组头大小20B,若主机H1向主机H2发送一个大小为980000B的文件,则在不考虑分组拆装时间和传播延迟的情况下,从H1发送到H2接收完为止,需要的时间至少是()A:80ms B:80.08ms C:80.16ms D:80.24ms4、(11-33)TCP/IP参考模型的网络层提供的是()A.无连接不可靠的数据报服务 B.无连接可靠的数据报服务C.有连接不可靠的虚电路服务 D.有连接可靠的虚电路服务5、(12-33)在TCP/IP体系结构中,直接为ICMP提供服务协议的是:()A. PPPB. IPC. UDPD. TCP6、(13-33)在OSI参考模型中,下列功能需由应用层的相邻层实现的是()A.对话管理B.数据格式转换C.路由选择D.可靠数据传输7.(13-35)主机甲通过1个路由器(存储转发方式)与主机乙互联,两段链路的数据传输速率均为10Mbps,主机甲分别采用报文交换和分组大小为10kb的分组交换向主机乙发送1个大小为8Mb(1M=106)的报文。
若忽略链路传播延迟、分组头开销和分组拆装时间,则两种交换方式完成该报文传输所需的总时间分别为()A.800ms、1600msB.801ms、1600msC.1600ms、800ms、 D、1600ms、801ms8.(14-33)在OSI参考模型中,直接为会话层提供服务的是()A.应用层 B表示层 C传输层 D网络层参考答案:1 2 3 4 5 6 7 8B C C A B B D C第二章1.(09-34)在无噪声情况下,若某通信链路的带宽为3kHz,采用4个相位,每个相位具有4种振幅的QAM调制技术,则该通信链路的最大数据传输速率是() A.12kbps B.24kbps C.48kbps D.96kbps注:1924年奈奎斯特(Nyquist)就推导出在理想低通信道的最高大码元传输速率N (其中W是想低通信道的公式:理想低通信道的最高大码元传输速率C=2W.log2的带宽,N是电平强度)。