Routing-Aware Query Optimization for Conserving Energy in Wireless Sensor Networks
- 格式:pdf
- 大小:462.82 KB
- 文档页数:9



图神经网络GNN基本知识掌握图神经网络GNN基本,看这篇文章就够了 3 图 (Graph) 3 图神经网络 3 DeepWalk:第一个无监督学习节点嵌入的算法 4 GraphSage:学习每个节点的嵌入 6 总结 7 使用图神经网络(GNN)寻找最短路径 8 引言 8 人工智能中“图神经网络GNN”如何理解?(附斯坦福综述)19 DeepMind、谷歌大脑、MIT等机构联合提出“图网络”(GNN),将端到端学习与归纳推理相结合,有望解决深度学习无法进行关系推理的问题。
19 掌握图神经网络GNN基本,看这篇文章就够了【新智元导读】图神经网络(GNN)在各个领域越来越受欢迎,本文介绍了图神经网络的基本知识,以及两种更高级的算法:DeepWalk和GraphSage。
最近,图神经网络 (GNN) 在各个领域越来越受到欢迎,包括社交网络、知识图谱、推荐系统,甚至生命科学。
GNN 在对图形中节点间的依赖关系进行建模方面能力强大,使得图分析相关的研究领域取得了突破性进展。
本文旨在介绍图神经网络的基本知识,以及两种更高级的算法:DeepWalk和 GraphSage。
图 (Graph) 在讨论 GNN 之前,让我们先了解一下什么是图 (Graph)。
在计算机科学中,图是由两个部件组成的一种数据结构:顶点 (vertices) 和边 (edges)。
一个图 G可以用它包含的顶点 V 和边 E 的集合来描述。
边可以是有向的或无向的,这取决于顶点之间是否存在方向依赖关系。
一个有向的图 (wiki) 顶点通常也被称为节点 (nodes)。
在本文中,这两个术语是可以互换的。
图神经网络图神经网络是一种直接在图结构上运行的神经网络。
GNN 的一个典型应用是节点分类。
本质上,图中的每个节点都与一个标签相关联,我们的目的是预测没有ground-truth 的节点的标签。
本节将描述 The graph neural network model (Scarselli, F., et al., 2009) [1] 这篇论文中的算法,这是第一次提出 GNN 的论文,因此通常被认为是原始 GNN。

Product OfferingsFortiADC and FortiGSLB Cloud Available in:Appliance VirtualMachine SaaS CloudApplication delivery without any limitsFortiADC is an advanced Application Delivery Controller (ADC) that ensures application availability, application security, and application optimization. FortiADC offers advanced security features (WAF, DDoS, and AV) and application connectors for easy deployment and full visibility to your networks and applications. You can deploy FortiADC as a physical or virtual machine (VM), or as a cloud solution.FortiADC provides unmatched application acceleration, load balancing, and web security, regardless of whether it is used for applications within a single data center or serves multiple applications for millions of users around the globe. FortiADC includes application acceleration, WAF, IPS, SSLi, link load balancing, and user authentication in one solution to deliver availability, performance, and security in a single, all-inclusive license.FortiADC also offers the FortiGSLB Cloud service that helps optimize end client requests fora specific domain by dynamically distributing workload across virtual servers, data centers, and locations. You can route traffic to your network resources based on geography, server performance (CPU/memory) and load, measured client and network performance, weighted distributions, consistent (sticky) routing, and more.• VM Subscription (Public/Private Cloud): virtual solution supported across public and private clouds.• Hardware appliance: on-premise FortiADC appliance providing multicore processor technology combined with hardware-based SSL offloading and server optimization to increase end-user QoE.• FortiGSLB Cloud Service: DNS-based load balancing as a service, enabling you to deploy redundant resources around the globe without having to maintain and manage your own load-balancing infrastructure. Leverage FortiGSLB Cloud to keep your businesses online in the event of localized traffic spikes or outages.ADVANCED APPLICATION DELIVERY CONTROLLER1HARDWARE ACCELERATED APPLIANCES120F220F300F400F1200F2200F4200F5000F3 GBPS 5 GBPS8 GBPS12 GBPS40 GBPS60 GBPS100 GBPS250 GBPS L4 Throughput 3 Gbps5 Gbps8 Gbps15 Gbps40 Gbps60 Gbps100 Gbps250 Gbps L7 Throughput 1.8 Gbps 4 Gbps8 Gbps12 Gbps30 Gbps35 Gbps80 Gbps220 GbpsSSL Throughput500 Mbps (NoASIC)1.2 Gbps (NoASIC)3 Gbps (NoASIC)6 Gbps (SSLASIC)20 Gbps (SSLASIC)25 Gbps (SSLASIC)50 Gbps (SSLASIC)120 Gbps (SSLASIC)Global Server Load Balancing (GSLB) Web Application Firewall SECURITY SERVICES10/100/10006xGE4xGE, 4xSFP4xGE, 4xSFP4xGE, 4xSFP8xGE, 8x SFP8x SFP10G SFP+4xSFP+8x SFP+12x SFP+8x SFP+40G QSFP4xQSFP8xQFSP 100G QSFP 284xQSFP28Dual PSSingle(optionalRedundant PS)Dual Dual Dual DualForm Factor1RU1RU1RU1RU1RU1RU2RU2RU SECURITY SERVICESIP Reputation StandardWAF Signature StandardCredential Stuffing Defense Services AdvancedAntiVirus AdvancedIPS AdvancedCloud Sandbox AdvancedWeb Filtering Add-on licenseADDITIONAL SERVICES24x7 SupportHARDWARE ACCELERATED APPLIANCESHARDWARE BUNDLES120F220F300F400F1200F2200F4200F5000FStandard Renewal Bundle FAD-120F-BDL-973-DDFAD-220F-BDL-973-DDFAD-300F-BDL-973-DDFAD-400F-BDL-973-DDFAD-1200F-BDL-973-DDFAD-2200F-BDL-973-DDFAD-4200F-BDL-973-DDFAD-5000F-BDL-973-DDAdvanced Renewal Bundle FAD-120F-BDL-619-DD FAD-220F-BDL-619-DDFAD-300F-BDL-619-DDFAD-400F-BDL-619-DDFAD-1200F-BDL-619-DDFAD-2200F-BDL-619-DDFAD-4200F-BDL-619-DDFAD-5000F-BDL-619-DDFortiADC application delivery controllers are available as hardware appliances, virtual machines, and public cloud VMs. FortiADC-HW provides multicore processor technology combined with hardware-based SSL offloading.FortiADC-VM S-series is a yearly subscription of our virtual ADC supported on all common hypervisors and public cloud providers. When choosing the virtual ADC (FortiADC-VM S series), remember this is a yearly subscription. Choose between the standard and advanced subscription bundles, which vary by the type of services included.FORTIADC PRODUCT OFFERINGSORDER INFORMATION22 ORDERING GUIDE | FORTIADCVIRTUAL MACHINE SUBSCRIPTIONSVM01VM02VM04VM08VM16VM321 GBPS2 GBPS 4 GBPS8 GBPS16 GBPS24 GBPS L4 Throughput 1 Gbps 2 Gbps 4 Gbps8 Gbps16 Gbps24 Gbps L7 Throughput500 Mbps 1 Gbps 2 Gbps 4 Gbps8 Gbps12 Gbps SSL Throughput500 Mbps 1 Gbps 2 Gbps3 Gbps 4.5 Gbps 6 Gbps Global Server Load Balancing (GSLB) Web Application Firewall SECURITY SERVICESIP Reputation StandardWAF Signature StandardCredential Stuffing Defense Services AdvancedAntiVirus AdvancedIPS AdvancedCloud Sandbox AdvancedWeb Filtering Add-on licenseADDITIONAL SERVICES24x7 Support FORTIADC PRODUCT OFFERINGSVIRTUAL MACHINE SUBSCRIPTIONSVM SUBSCRIPTIONS VM01VM02VM04VM08VM16VM32Standard Bandwidth Bundle FC1-10-ADVMS-942-02-DD FC2-10-ADVMS-942-02-DDFC3-10-ADVMS-942-02-DDFC4-10-ADVMS-942-02-DDFC5-10-ADVMS-942-02-DDFC6-10-ADVMS-942-02-DDAdvanced Bandwidth Bundle FC1-10-ADVMS-635-02-DD FC2-10-ADVMS-635-02-DDFC3-10-ADVMS-635-02-DDFC4-10-ADVMS-635-02-DDFC5-10-ADVMS-635-02-DDFC6-10-ADVMS-635-02-DDORDER INFORMATION3ORDERING GUIDE | FORTIADCORDERING GUIDE | FORTIADCFORTIGSLB CLOUD PRODUCT OFFERINGSFortiGSLB Cloud provides load balancing across multiple data centers and cloud applications based on GSLB Cloud policies, with site selection according to application/server availability (health checks) and client geolocation. FortiGSLB supports stackable licenses.FORTIGSLB CLOUDLICENSES OFFERINGDNS Query Per Second100 QPS500 QPS1,000 QPSAdvanced Health Check 2 Advanced Health Check10 Advanced Health Check100 Advanced Health Check SERVICESGlobal Application LBDNS ServicesApplication Visibility ADDITIONAL SERVICES24x7 Support Included Included Included ORDER INFORMATIONFORTIGSLB CLOUDDNS QUERY PER SECOND100 QPS500 QPS1,000 QPSDNS Subscription FC2-10-CGSLB-330-02-DD FC3-10-CGSLB-330-02-DD FC4-10-CGSLB-330-02-DD ADVANCED HEALTH CHECK 2 Advanced Health Check10 Advanced Health Check100 Advanced Health Check Health Check Subscription FC1-10-CGSLB-332-02-DD FC2-10-CGSLB-332-02-DD FC4-10-CGSLB-332-02-DD44FORTIADC CHEAT SHEETThe SpaceThe ADC market continues to evolve with application automation and software-centric use cases:• Application automation and integration with microservices (CI/CD)• Autoscaling and application security (WAF)• “Over the top” ADC services (GSLB)• Application visibility and ease-of-use focusProduct LineupFortiADC product line includes various options:• On-premise: any FortiADC can be purchased as HW, VM, and Cloud VM models. Models are from1.5 Gbps and up to 300 Gbps throughput.• Cloud VM: FortiADC also runs on public cloud (AWS, OCI, Azure, and GCP). We support perpetual licenses (BYOL and PAYG).Ordering GuideProduct Offerings: OPEX and CAPEX options OPEX: one option available:• FortiADC-VM: S-series provides yearlysubscription for IaaS/private cloud. All-inclusivestandard/advanced bundle options.CAPEX: two options available:• HW appliances: selected by throughput (1.5 Gbps to 250 Gbps)• FortiADC-VM: preferably choose S-series though perpetual license is available.Where to Find More Info• Demo: FortiADC automation, SAP security and availability, FortiADC SSL proxy and FW LB• What’s New: FortiADC new features• Training: the most commonly use FortiADC features Application connectors and automation for autoscaling and service availability.Advanced application LB with L7 routing, advanced health checks, and application optimization.Unleash the power of the script: With FortiADC Script, you can manage and control network/application traffic.SSL visibility and inspection: SSL-based attacks are rising. With FortiADC, you can monitor and block SSL attacks.Global LB: real-time traffic LB between multiple locations/data centers for best availability and quality of experience to reduce latency.Application security: The most secure ADC in the market with WAF (OWASP Top-10), antivirus, IPS, DDoS protection, and Sandbox integration.Ease of use: FortiView provides real-time data analytics and application visibility. FortiADC has integration with Splunk, FortiAnalyzer, and FortiSIEM.Major Capabilities to Pitch5ORDERING GUIDE | FORTIADC。

Wireless Sensor Network, 2012, 4, 162-166doi:10.4236/wsn.2012.46023 Published Online June 2012 (/journal/wsn)MNMU-RA: Most Nearest Most Used Routing Algorithm for Greening the Wireless Sensor NetworksHafiz Bilal Khalil, Syed Jawad Hussain ZaidiSchool of Electrical Engineering & Computer Sciences, National University of Sciences and Technology, Islamabad, PakistanEmail: {10mseetkhalil, 10mseejzaidi}@.pkReceived February 22, 2012; revised March 22, 2012; accepted April 10, 2012ABSTRACTWireless sensors are widely deployed in military and other organizations that significantly depend upon the sensed in-formation in any emergency situation. One of the main designs issues of the wireless sensor network (WSN) is the con-servation of energy which is directly proportional to the life of the networks. We propose most nearest most used rout-ing algorithm (MNMU-RA) for ad-hoc WSNs which vitally plays an important role in energy conservation. We find the best location of MNMU node for energy harvesting by apply our algorithm. Our method involves the least number of nodes in transmission of data and set large number of nodes to sleep in idle mode. Based on simulation result we shows the significant improvement in energy saving and enhance the life of the network.Keywords: Energy Efficiency; Wireless Sensor Networks; Routing1. IntroductionThe growth in wireless sensor networks and its applica- tions dramatically increased in last decade. Wireless sen- sor nodes are widely used in military surveillance, intel- ligence and targeting in war operations. Energy available at each sensor for sensing and communications is limited because of the cost constraints and smaller size, which affects the sensor application and network lifetime. The purpose of green networking is to overcome the carbon foot print, reduce the energy consumption and energy losses. Energy efficiency is an important issue to enhance the life time of the network. To achieve the green net- working every component of the network is integrated with energy efficient protocols, e.g., energy-aware rout- ing on network layer, energy-saving mode on MAC layer, etc. One of the most important components of the sensor node is the power source. In sensor networks generally there are three modes of power consumption: sensing, data processing, and communication. Compared to sensing and data processing, much more energy is required for data communication in a typical sensor node [1]. These are also categorized as sleep (idle) and wakeup (trans-mission) mode.In ad-hoc WSNs (Wireless Sensor Networks) always the nodes are cooperative, they sense and transmit their own data and also act as router to route the sensed infor- mation of other nodes towards the data center or gateway node which is connected to the internet. Most of the nodes consumed their power resource while transmitting the data of neighboring nodes. The scope of this paper is to minimize the power consumption in transmitting or routing process and set large number of nodes into sleep mode. The remaining sections of this paper organized as follows. Section 2 explains related work and current en-ergy efficient techniques for sensor networks. Section 3 introduces some problems and research issues in current work. Section 4 describes overview of network model, our proposed algorithm and proposed solution respec-tively. In Section 5 experiment, Results and comparisons are given.2. Related WorkEnergy efficiency is already achieved by many appro- aches. These approaches include energy aware protocol development and hardware optimizations, such as sleep- ing schedules to keep electronics inactive most of the time, dynamic optimization of voltage, and clock rate. In[2] Smart Dust motes are designed that are not more thana few cubic millimeters. They can float in the air, keep sensing and transmitting for hours or days. In [3] authors described the µAMPS wireless sensor node, it is hard- ware based solution in which they simultaneously con- sider the features of the microprocessors and transceivers to reduce the power consumption of the each wireless sensor node in network. Routing algorithms also play an important role to reduce the energy consumption during the routing of data. A lot of work is done in MAC layer and Mac protocols;MAC protocol for wireless sensorH. B. KHALIL, S. J. H. ZAIDI163networks is not like the traditional wireless MACs such as IEEE 802.11. One of the most important goals is en-ergy conservation, fairness and latency is less important [4].SMAC/AL (Sensor MAC with Adaptive Listening) is a famous MAC protocol for WSNs proposed by Ye et al. [5,6]. Main purpose of SMAC/AL is to reduce energy consumption. But in SMAC/AL without considering the distance among the nodes, all nodes unnecessarily con- sume the energy by transmitting information with con- stant power level. An energy efficient MAC protocol with adaptive transmit power scheme named ATPM (Adap- tive Transmit Power MAC) is proposed in [7]. By meas- uring the received power ATPM can calculate the dis- tance between the sender and the receiver, and then adap- tively choose the suitable transmit power level according to the propagation model and distance. The ATMP can not only conserve the energy source, but also decrease the collision probability. A Novel Clustering Algorithm for Energy Efficiency in Wireless Sensor Networks (AN-CAEE) has been proposed [8]. It minimizes energy utili-zation during data transmission and energy consumptions are distributed uniformly among all nodes. Each cluster contains cluster head, each node send its data to cluster head with single hop transmission. And cluster transmits the combined data to the base station with multi hope transmission. This approach reduces energy consumption of nodes within the cluster.3. Problem StatementSensor nodes which are one hope away or closest to the gateway node always consume their power more quickly than others because they have to transmit the data of other nodes in addition to transmission of their own sensed information. In [9] a solution was proposed for such type of scenario by implementing the multiple base stations and periodically changing their positions. But the prob- lem is that if every time the most far away sensor trans- mits its data then major part of overall network energy will be consumed. Another solution for prolong the sen- sor network lifetime is to divide sensors nodes into dis- joint sets, such that all the targets completely covered by every set [3]. Authors consider that within an active sen- sor’s operational range a target is covered. These disjoint sets are activated in round robin fashion, such that at a time only one set is active. Sensors are into the active state in an active set and all other sensors are in a low- energy sleep state. According to this method almost half of the sensor remains active and remaining half goes to sleep mode which reduce energy down to 50%. To make it more efficient and conserve the larger amount of en- ergy we proposed an algorithm named as MNMU-RA (Most nearest most used routing algorithm). That algo- rithm finds the efficient placement of active sensor nodes and set other nodes into sleep mode. An issue is also re- solved by our algorithm, reducing the number of multiple base stations by finding out the best location for the base station without changing its location periodically.4. Synopsis of Our Network ModelIn this paper we deal with the issue of energy efficiency in wireless sensor networks for surveillance of a set of targets with known locality. Scenario of the network is chosen for armed forces purposes like surveillance of the boarder, battle fields and no go areas to acquire the in- formation about enemies and their locations without tak- ing the risk for human personal. We consider that a large number of sensors are distributed randomly in close prox- imity for monitoring and send the monitored information to a gateway node. All nodes are static and makes ad-hoc wireless sensor network. Every sensor nodes must moni-tor the area all the time in its operational range and each sensor has fixed transmission range. In network model we assume that each sensor has unique pre configured Id and Global/proactive routing algorithms are used. Main advantage of proactive algorithm is not route latency but drawback is the high maintenance overhead when many of the routes are never used.Proactive routing is appro-priate for networks with: Small size, low mobility and high communication rates. We proposed an algorithm called as most nearest most used routing algorithm for this purpose. By using MNMU-RA we can find the per-fect location of node for energy harvesting which also reduce the overall energy consumption and cost.4.1. Most Nearest Most Used Routing Algorithm Run shortest path routing algorithm or link state routing to find the shortest path for each node in the wireless sensor network. Calculate all the possible shortest paths for each node. Then find the MNMU node (Figure 1).∙ A node which is most nearest to the gateway node.∙Select a node which is used in maximum number of shortest paths.Figure 1. Location of selected MNMU node.H. B. KHALIL, S. J. H. ZAIDI 164In above network model we assumed that sensed in- formation is equally probable for all the nodes. Then we calculate the shortest path for the nodes A, B and C. Then we find out the nodes which are most nearest to the gate way node. In above network model there are only two nodes X and Y which are closer to the gateway node. Then for selection we give the preference to the node which is most used in shortest paths. In above model Y is node which is most used in all shortest paths. If nodes A, B and C transmit their data the entire time node Y will be included in their path. Then every node keeps its routes information towards the node Y for future communica- tions. Flow chart of our algorithm is given in Figure 2. 4.2. Proposed SolutionWe used our algorithm to find most nearest most used node in a network, that node should be active all the time while other sensors remain in sleep mode and keep sens- ing. As we use proactive routing so each sensor knows its path towards the MNMU node. If a node has to send its information before sending it will wake up the nodes along his route. When MNMU nodes receive the infor- mation it will forward the data to the gateway and sets all the nodes into sleep mode. The critical issue in this solu- tion is that if a node (MNMU node) remains active all the time then its energy source will be empty soon. We re- solve this issue by using the energy harvesting concept at MNMU node [1]. We can also use secondary batteryFigure 2. MNMU routing algorithm flow chart. which is rechargeable and coupled with photovoltaic cell[10]. If all the nodes can generate energy from light, vi-bration, heat etc [11,12] it will increase the system cost.We don’t need to replace all the nodes with secondary sources. By replacing only one node (MNMU node) re-solves the issue and slightly increases the cost of theoverall system. But effectively prolong the life time ofsensor network. A solution given by Gandham et al. [9]can be more energy efficient if we implement our pro-posed algorithm with every new location of mobile basestation. Split the network in equal parts and periodicallychange the position of base station in each part. Basestation can be easily implemented at the place of MNMUnode in each part of the network instead of replacing itoutside the network. MNMU node will reduce the multihop and number of transmission which directly reducethe energy consumption.5. ExperimentWe done the experiment by implementing our proposedalgorithm in a network and calculate the amount of en-ergy utilization using MATLAB. Then implement theconcept of disjoint set and analyze the values at same network. For simulation 20 nodes containing one gate-way node are distributed randomly in 30 meter squarearea. We consider the features of MICA2 mote platform.It is third generation mote specifically built for WSNs [4].MICA2 have selectable transmission power range whichoffers adjustable communication ranges, selected trans-mission range for each node is 10 meters. The packetlength is fixed at 200 bits. MICA2 usually operated with3 V battery and other features mentioned in Table 1.We divided our analysis in three parts; first we calcu-late the power consumption using disjoint sets methods[3], then we apply our algorithm and calculate & com-pare power consumption. Same network and topologytaken in which each node remains active all the time andno energy saving protocol and technique is implemented.Energy calculated during the 20 rounds, all nodes areactive in first five rounds in which they sense and trans-mit the data. After ten rounds there is no activity andnodes go to sleeping mode according to implemented Table 1. Features of MICA2 motes platform [12,13].Operation/Features UnitListening 8mA Receiving 10mA Transmission 17mA Sleep 19µA Radio Frequency 900 MHzCPU 8 bit Atmel at 8 MHzBandwidth 40KbpsH. B. KHALIL, S. J. H. ZAIDI165methodology. Calculated results are given in Figures3 and 4.Simulation ResultsFigure 3 shows the result comparison of energy con- sumption in different modes; sensing, Transmission and sleeping of network. In Figure 3(a) set of all the active nodes shown by blue line are transmitting the data with- out applying any energy saving protocol. During the transmission if all nodes are active they will keep trans- mitting the information to each other and maximum amount of energy is consumed. In disjoint system only active set take part in transmission and inactive nodesFigure 3. Power consumptions in different modes. (a) Trans- mission mode; (b) Power consume by sleeping nodes; (c)Power consume by active nodes in sleep mode. Figure 4. Result and comparison of energy consumption in different modes.remain inactive during the transmission of active set. Our proposed algorithm gives lowest amount of energy con- sumption because only the MNMU node and less number of nodes take part in transmission. Energy consumed by inactive nodes in sleeping modes is shown in Figure 3(b). Energy consumption of sleeping nodes is in µwatts. Ac- cording to our algorithm 19 nodes set to sleep mode and only one MNMU node is active. While Figure 3(c) shows the separately calculated energy consumption by active nodes when there is no activity and network is in idle mode. Similarly in sleeping mode only MNMU node remains active and rest of the network sets to sleep mode. Figure 4 shows the result of energy consumption of entire network in different rounds. In first 5 rounds we assume that there is no sensed information to send; all the nodes are active in listening mode and keep sensing. In 5 to 10 rounds nodes are transmitting their sensed in- formation to the gateway. After round 10 there is no ac- tivity and nodes set to sleep mode in sleep mode only energy consumed by active nodes are calculated and en- ergy consumed by sleeping nodes which is in µwatts is neglected. Our algorithm gives the minimum energy con- sumption during the transmission in which fewer num- bers of nodes take part in routing and also in sleep mode by keeping only MNMU node active.6. ConclusionWe presented the most nearest most used routing algo- rithm to reduce the energy utilization in wireless sensor networks. Using this algorithm we find the best location of energy harvested node in a network. Our algorithm involves least number of nodes during transmission and keeps one node active in sleep mode. That significantly reduces the energy consumption during the transmissionH. B. KHALIL, S. J. H. ZAIDI 166and sleep mode when there is no activity. An open re- search issue is the heterogeneity of energy resources of the nodes that must be resolved after practical imple- mentation in any network. In our solution there is uneven energy consumption due to the topology of the network and nature of data flow. But that uneven energy con- sumption is helpful to reduce the energy consumption of entire network7. Future DirectionDesired goal in wireless networks is energy efficiency to maximize the network life. Our algorithm can be used to find the location of cluster header quickly in novel clus- tering algorithm for energy efficiency in wireless sensor networks [8]. Further we can implement coding tech- niques to reduce the number of transmissions at MNMU node. Energy consumes per bit or per packet transmis- sion can be reduce. Number of packets can be transmit- ted as a single packet by applying x-or Operations which reduces the energy but may cause of slighter delay. To apply this technique sensor nodes must be smarter and have ability to do this quickly.REFERENCES[1]I. F. Akyildiz, T. Melodia and K. Chowdhury, “A Surveyon Wireless Multimedia Sensor Networks,” ComputerNetworks, Vol. 51, No. 4, 2007, pp. 921-960.doi:10.1016/net.2006.10.002[2]J. M. Kahn, R. H. Katz and K. S. J. Pister, “EmergingChallenges: Mobile Networking for Smart Dust,” Inter-national Journal of Communication Networks, Vol. 2, No.3, 2000, pp. 188-196.[3]M. Cardei and D. Z. Du, “Improving Wireless SensorNetwork Lifetime through Power Aware Organization,”Wireless Networks, Vol. 11, No. 3, 2005, pp. 333-340.doi:10.1007/s11276-005-6615-6[4]Q. Hu and Z. Z. Tang, “An Adaptive Transmit PowerScheme for Wireless Sensor Networks,” 3rd IEEE Inter-national Conference on Ubi-Media Computing, Jinhua, 5-7 July 2010, pp. 12-16.[5]W. Ye, J. Heidemann and D. Estrin, “An Energy-EfficientMAC Protocol for Wireless Sensor Networks,” Proceed- ings of the IEEE INFOCOM, New York, 23-27 June 2002, pp. 1567-1576.[6]W. Ye, J. Heidemann and D. Estrin, “Medium AccessControl with Coordinated Adaptive Sleeping for Wireless Sensor Networks,” IEEE/ACM Transactions on Network- ing, Vol. 12, No. 3, 2004, pp. 493-506.doi:10.1109/TNET.2004.828953[7]Q. Hu and Z. Tang, “ATPM: An Energy Efficient MACProtocol with Adaptive Transmit Power Scheme for Wire- less Sensor Networks,” Journal of Multimedia, Vol. 6, No.2, 2011, pp. 122-128. doi:10.4304/jmm.6.2.122-128[8] A. P. Abidoye and N. A. Azeez, “ANCAEE: A Novel Clus-tering Algorithm for Energy Efficiency in Wireless Sen- sor Networks,” Journal of Wireless Sensor Networks, Vol.3, No. 9, 2011, pp. 307-312. doi:10.4236/wsn.2011.39032 [9]S. R. Gandham, M. Dawande, R. Prakash and S. Venkate-san, “Energy Efficient Schemes for Wireless Sensor Net- works with Multiple Mobile Base Stations,” Global Tele- communications Conference, San Francisco, 1-5 Decem- ber 2003, pp. 377-381.[10]M. A. M. Vieira, C. N. Coelho, D. C. Silva and J. M. Mata,“Survey on Wireless Sensor Network Devices,” Proceed- ings of IEEE International Conference on Emerging Tec- hnologies and Factory Automation (ETFA’03), Lisbon, 16-19 September 2003, pp. 537-544.[11]J. Paradiso and T. Starner, “Energy Scavenging for Mo-bile and Wireless Electronics,” Pervasive Computing, Vol.4, No. 1, 2005, pp. 18-27. doi:10.1109/MPRV.2005.9 [12]V. Gungor and G. Hancke, “Industrial Wireless SensorNetworks: Challenges, Design Principles, and Technical Approaches,” IEEE Transactions on Industrial Electron- ics, Vol. 56, No. 10, 2009, pp. 4258-4265.doi:10.1109/TIE.2009.2015754[13]CrossBow, Mica2 Data Sheet./Products/Product_pdf_files/MICA%20data%20sheet.pdf。
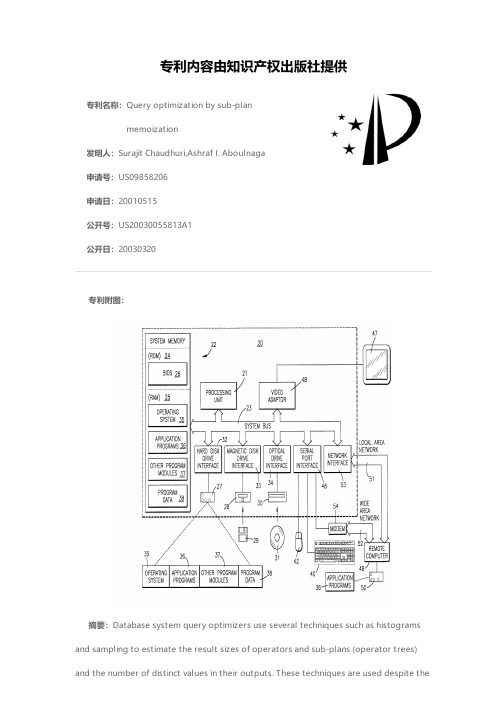
专利名称:Query optimization by sub-planmemoization发明人:Surajit Chaudhuri,Ashraf I. Aboulnaga申请号:US09858206申请日:20010515公开号:US20030055813A1公开日:20030320专利内容由知识产权出版社提供专利附图:摘要:Database system query optimizers use several techniques such as histograms and sampling to estimate the result sizes of operators and sub-plans (operator trees)and the number of distinct values in their outputs. These techniques are used despite thefact that they incur estimation errors because they provide inexpensive estimates and result in query execution plans with acceptable performance. For embedded queries that are frequently executed, users may be willing to accept the use of expensive estimation techniques that result in long query optimization times if this leads to choosing faster query execution plans. Instead of estimates, the invention uses the exact actual values of the result sizes and the number of distinct values in the outputs of sub-plans encountered by the optimizer. This is achieved by optimizing the query in phases. In each phase, newly encountered sub-plans are recorded for which result size and/or distinct value estimates are required. These sub-plans are executed at the end of the phase to determine their actual result sizes and the actual number of distinct values in their outputs. In subsequent phases, the optimizer uses these actual values when it encounters the same sub-plan again. This approach, which is referred to as sub-plan memoization, requires query optimization times that may be much longer than the execution times of the queries, but it leads to choosing much faster query execution plans. This makes it very suitable for frequently executed embedded queries.申请人:MICROSOFT CORPORATION更多信息请下载全文后查看。
DATASHEETOverview IC Compiler™ II is the industry leading place and route solution that delivers best-in-class quality-of-results (QoR) for next-generation designs across all market verticals and process technologies while enabling unprecedented productivity. IC Compiler II includes innovative for flat and hierarchical design planning, early design exploration, congestion aware placement and optimization, clock tree synthesis, advanced node routing convergence, manufacturing compliance, and signoff closure.IC Compiler II is specifically architected to address aggressive performance, power, area (PPA), and time-to-market pressures of leading-edge designs. Key technologies include a pervasively parallel optimization framework, multi-objective global placement, routing driven placement optimization, full flow Arc based concurrent clock and data optimization, total power optimization, multi-pattern and FinFET aware flow and machine learning (ML) driven optimization for fast and predictive design closure. Advanced Fusion technologies offer signoff IR drop driven optimization, PrimeTime ® delay calculation within IC Compiler II, exhaustive path-based analysis (PBA) and signoff ECO within place and route for unmatched QoR and design convergence. F U S I O N D E S I G N P L A T F O R M PrimeTime, StarRC, PrimePower,IC Validator, RedHawk Analysis Fusion Fusion Compiler IC Compiler II Design Compiler NXT TestMAX F o r m a l i t y ECO Fusion S i g n o f f F u s i o n S i g n o f f F u s i o n Test Fusion Figure 1: IC Compiler II Anchor in Synopsys Design PlatformAccelerating DesignClosure on AdvancedDesignsIC Compiler II Industry Leading Place and Route SystemKey BenefitsProductivity• The highest capacity solution that supports 500M+ instances with a scalable and compact data model• A full suite of design planning features including transparent hierarchical optimization• Out-of-the-box simple reference methodology for easy setup• Multi-threaded and distributed computing for all major flow steps• Golden signoff accuracy with direct access to PrimeTime delay calculationPPA• Unified TNS driven optimization framework• Congestion, timing, and power-driven logic re-synthesis• IEEE 1801 UPF/multi-voltage support• Arc-based concurrent clock and data optimization• Global minima driven total power optimizationAdvanced Nodes• Multi-pattern and FinFET aware design flow• Next generation advanced 2D placement and legalization• Routing layer driven optimization, auto NDR, and via pillar optimization• Machine learning driven congestion prediction and DRC closure• Highest level of foundry support and certification for advanced process nodes• IC Validator in the loop signoff driven DRC validation and fixingAdvanced Fusion Technology• Physically aware logic re-synthesis• IR drop driven optimization during all major flow steps• PrimeTime delay calculation based routing optimization for golden accuracy• Integrated PrimeTime ECO flow during routing optimization for fastest turnaround timeEmpowering Design Across Diversified ApplicationsThe dizzying pace of innovation and highly diversified applications across the design spectrum is forcing a complete rethink of the place and route systems to design and implement differentiated designs in a highly competitive semiconductor market on schedule. Designers on emerging process nodes must meet aggressive PPA and productivity goals. It essentially means efficient and intelligent handling of 100s of millions of place-able instances, multiple levels of hierarchy, 1000s of hard macros, 100s of clocks, wide busses, and 10s of modes and corners power domains and complex design constraints and process technology mandates. Emphasis on Designer ProductivityIC Compiler II is architected from the ground up for speed and scalability. Its hierarchical data model consumes 2-3X less memory than conventional tools, boosting the limits of capacity to 500M placeable instances and beyond. Adaptive abstraction and on-the-fly data management minimize memory requirements and enable fast responsive data manipulation. Near-linear multi-core threading of key infrastructural components and core algorithms such as database access and timing analysis speed up optimization at all phases of design. Patented, lossless compact modeling and independent R and C extraction allow handling more modes and corners (MCMM scenarios) with minimal runtime impact.IC Compiler II has built-in Reference Methodology(RM) that ensures fast flow bring up. This RM Flow is Foundry Process/Design Type specific to ensure a robust starting point and seamless bring up. IC Compiler II has direct access to the Golden PrimeTime delay calculation engine to minimize ECO iterations.IC Compiler II’s new data model enables designers to perform fast exploration and floorplanning with complex layout requirements. IC Compiler II can create bus structures, handle designs with n-levels of physical hierarchy, and support Multiply Instantiated Blocks (MIBs) in addition to global route driven pin assignment/feedthrough flow, timing driven macro placement, MV area design planning.A design data mismatch inferencing engine analyzes the quality of inputs and drives construct creation on the fly, delivering design insights even with “incomplete” data early in the design cycle. Concurrent traversal of logical and physical data models enables hierarchical Data-Flow Analysis (DFA) and fast interactive analysis through multi-level design hierarchies and MIBs. Data flow and feedthrough paths highlighted in Figure 2 allow analysis and manipulation through n-levels of hierarchy to complete early design exploration and prototyping.Figure 2: Fast interactive analysis through multiple-levels of physical hierarchy and MIBPipeline-register-planning shown in Figure 3, provides guidance for optimal placement to meet the stringent timing requirementsof high-performance designs. Interactive route editor integrated which is advanced node aware shown in Figure 4, allows intricate editing and routing functions, including the creation of special signal routes, buses, etc.Figure 3: Pipeline register placement enables superior QoR for designs with complex busesAchieving Best Performance, Power, Area, and TATIC Compiler II features a new optimization framework built on global analytics. This Unified TNS Driven Optimization framework is shared with Design Compiler NXT synthesis to enable physically-aware synthesis, layer assignment, and route-based optimization for improved PPA and TAT. Multi-Corner Multi-Mode (MCMM) and Multi-Voltage (MV) aware, level-based analytical algorithms continuously optimize using parallel heuristic algorithms. Multi-factor costing functions deliver faster results on both broad and targeted design goals. Concurrent PPA driven logic remapping, rewiring, and legalization interleaved with placement minimizes congested logic, resulting in simple localized logic cones that maximize routability and QoR.IC Compiler II minimizes leakage with fast and efficient cell-by-cell power selection across HVT, SVT and LVT cells and varying channel lengths. Activity-driven power optimization uses VCD/ SAIF, net toggle rates, or probability functions to drive placement decisions and minimize pin capacitances. Multi-bit register banking optimizes clock tree structures, reduces area, and net length, while automatically managing clock, data, and scan chain connections.Advanced modeling of congestion across all layers highlighted in Figure 4 provides accurate feedback throughput the flow from design planning to post- route optimization.Figure 4: Intelligent and accurate analysis for congestion and powerIC Compiler II introduces a new Concurrent Clock and Data (CCD) analysis and optimization engine that is built-in to every flow step resulting in meeting both aggressive performance and minimizing total power footprint. ARC-based CCD optimization performs clock tree traversal across all modes/corners in path-based fashion to ensure optimal delay budgeting.Robust support for clock distribution enables virtually any clock style, including mesh, multi-source, or H-tree topologies. Advanced analysis and debugging features perform accurate clock QoR analysis and debugging as highlighted in Figure 5.Figure 5: Accurate clock QoR analysis and debugging (a & b) Abstracted clock graph and schematic.(c) Latency clock graph. (d) Colored clock tree in layout.IC Compiler II features many innovative technologies that make it the ideal choice for high-performance, energy-efficient Arm®processor core implementation, resulting in industry-best milliwatts/megahertz (mW/MHz) for mobile and other applications across the board. Synopsys and Arm work closely together to offer optimized implementation of popular Arm cores for IC Compiler II,with reference flows available for Arm Cortex®-A high-performance processors and Mali GPUs. In addition, Arm offers off-the-shelf Artisan® standard cell and memory models that have been optimally tuned and tested for fast deployment in an IC Compiler II environment. Continuous technology innovation and close collaboration makes IC Compiler II the leading choice for Arm-based high- performance design.Highest Level of Advanced Node Certification and SupportIC Compiler II provides advanced node design enablement across major foundries and technology nodes—including 16/14nm,12/10nm, 7/5nm, and sub-5nm geometries. Zroute digital router technology ensures early and full compliance with the latest design rules required for these advanced node technologies. Synopsys collaborates closely with all the leading foundries to ensure that IC Compiler II is the first to deliver support for early prototype design rules and support for the final production design rules. IC Compiler II design technologies maximize the benefits of new process technologies and offer optimal return on investment for cutting-edge silicon applications.IC Compiler II advanced node design support includes multi-pattern/FinFET aware placement and routing, Next-generation advanced 2D placement and legalization, routing layer driven optimization, auto NDR, and via pillar optimization. IC Validator in the loop provides signoff DRC feedback during Implementation.Foundry fill Track based fillFigure 6: IC Validator In-Design metal fill color aware metal fill, optimized for density and foundry requirementsMachine learning driven congestion prediction and DRC closure allow for fastest routing convergence with best PPA. Multiple sets of training data are used to extract key predictive elements that guide the pre-route flow.Advanced Fusion TechnologyThe Fusion Design Platform™ delivers unprecedented full-flow QoR and time-to-results (TTR) to accelerate the next wave of semiconductor industry innovation. The industry’s first AI-enhanced, cloud-ready Design Platform with Fusion Technology™ isbuilt from Synopsys’ market-leading, massively-parallel digital design tools, and augmented with innovative capabilities to tacklethe escalating challenges in cloud computing, automotive, mobile, and IoT market segments and accelerate the next wave of industry innovation.Fusion Technology redefines conventional EDA tool boundaries across synthesis, place-and-route, and signoff, sharing integrated engines across the industry’s premier digital design products. It enables designers to accelerate the delivery of their next-generation designs with the industry-best QoR and the TTR.©2019 Synopsys, Inc. All rights reserved. Synopsys is a trademark of Synopsys, Inc. in the United States and other countries. A list of Synopsys trademarks isavailable at /copyright.html . All other names mentioned herein are trademarks or registered trademarks of their respective owners.。
INDUSTRY-LEADING CLOUD MANAGEMENT• Unified firewall, switching, wireless LAN, and mobile device man-agement through an intuitive web-based dashboard• Template based settings scale easily from small deployments to tens of thousands of devices• Role-based administration, configurable email alerts for a variety of BRANCH GATEWAY SERVICES• Built-in DHCP, NAT, QoS, and VLAN management services • Web caching: accelerates frequently accessed content• Load balancing: combines multiple WAN links into a single high-speed interface, with policies for QoS, traffic shaping, and failover FEATURE-RICH UNIFIED THREAT MANAGEMENT (UTM) CAPABILITIES• Application-aware traffic control: bandwidth policies for Layer 7 application types (e.g., block Y ouTube, prioritize Skype, throttle BitTorrent)• Content filtering: CIPA-compliant content filter, safe-seach enforcement (Google/Bing), and Y ouTube for Schools• Intrusion prevention: PCI-compliant IPS sensor using industry-leading SNORT® signature database from Cisco• Advanced Malware Protection: file reputation-based protection engine powered by Cisco AMP• Identity-based security policies and application managementINTELLIGENT SITE-TO-SITE VPN WITH MERAKI SD-WAN• Auto VPN: automatic VPN route generation using IKE/IPsec setup. Runs on physical MX appliances and as a virtual instance within the Amazon AWS or Microsoft Azure cloud services• SD-WAN with active / active VPN, policy-based-routing, dynamic VPN path selection and support for application-layer performance profiles to ensure prioritization of the applications types that matter • Interoperates with all IPsec VPN devices and services• Automated MPLS to VPN failover within seconds of a connection failure• Client VPN: L2TP IPsec support for native Windows, Mac OS X, iPad and Android clients with no per-user licensing feesOverviewCisco Meraki MX Security & SD-WAN Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution fordistributed sites, campuses or datacenter VPN concentration. Since the MX is 100% cloud managed, installation and remote management are simple. The MX has a comprehensive suite of network services, eliminating the need for multiple appliances. These services includeSD-WAN capabilities, application-based firewalling, content filtering, web search filtering, SNORT® based intrusion detection and prevention, Cisco Advanced Malware Protection (AMP), web caching, 4G cellular failover and more. Auto VPN and SD-WAN features are available on our hardware and virtual appliances, configurable in Amazon Web Services or Microsoft Azure.Meraki MXCLOUD MANAGED SECURITY & SD-WANRedundant PowerReliable, energy efficient design with field replaceable power suppliesWeb Caching 128G SSD diskDual 10G WAN Interfaces Load balancing and SD-WAN3G/4G Modem Support Automatic cellular failover1G/10G Ethernet/SFP+ Interfaces 10G SFP+ interfaces for high-speed LAN connectivityEnhanced CPU Layer 3-7 firewall and traffic shapingAdditional MemoryFor high-performance content filteringINSIDE THE CISCO MERAKI MXMX450 shown, features vary by modelModular FansHigh-performance front-to-back cooling with field replaceable fansManagement Interface Local device accessMulticolor Status LED Monitor device statusFRONT OF THE CISCO MERAKI MXMX450 shown, features vary by modelCryptographic AccelerationReduced load with hardware crypto assistCisco Threat Grid Cloud for Malicious File SandboxingIdentity Based Policy ManagementIronclad SecurityThe MX platform has an extensive suite of security features including IDS/IPS, content filtering, web search filtering, anti-malware, geo-IP based firewalling, IPsec VPN connectivity and Cisco Advanced Malware Protection, while providing the performance required for modern, bandwidth-intensive yer 7 fingerprinting technology lets administrators identifyunwanted content and applications and prevent recreational apps like BitT orrent from wasting precious bandwidth.The integrated Cisco SNORT® engine delivers superior intrusion prevention coverage, a key requirement for PCI 3.2 compliance. The MX also uses the Webroot BrightCloud® URL categorization database for CIPA / IWF compliant content-filtering, Cisco Advanced Malware Protection (AMP) engine for anti-malware, AMP Threat Grid Cloud, and MaxMind for geo-IP based security rules.Best of all, these industry-leading Layer 7 security engines and signatures are always kept up-to-date via the cloud, simplifying network security management and providing peace of mind to IT administrators.Organization Level Threat Assessment with Meraki Security CenterSD-WAN Made SimpleTransport independenceApply bandwidth, routing, and security policies across a vari-ety of mediums (MPLS, Internet, or 3G/4G LTE) with a single consistent, intuitive workflowSoftware-defined WAN is a new approach to network connectivity that lowers operational costs and improves resource us-age for multisite deployments to use bandwidth more efficiently. This allows service providers to offer their customers the highest possible level of performance for critical applications without sacrificing security or data privacy.Application optimizationLayer 7 traffic shaping and appli-cation prioritization optimize the traffic for mission-critical applica-tions and user experienceIntelligent path controlDynamic policy and perfor-mance based path selection with automatic load balancing for maximum network reliability and performanceSecure connectivityIntegrated Cisco Security threat defense technologies for direct Internet access combined with IPsec VPN to ensure secure communication with cloud applications, remote offices, or datacentersCloud Managed ArchitectureBuilt on Cisco Meraki’s award-winning cloud architecture, the MX is the industry’s only 100% cloud-managed solution for Unified Threat Management (UTM) and SD-WAN in a single appliance. MX appliances self-provision, automatically pulling policies and configuration settings from the cloud. Powerful remote management tools provide network-wide visibility and control, and enable administration without the need for on-site networking expertise.Cloud services deliver seamless firmware and security signature updates, automatically establish site-to-site VPN tunnels, and provide 24x7 network monitoring. Moreover, the MX’s intuitive browser-based management interface removes the need for expensive and time-consuming training.For customers moving IT services to a public cloud service, Meraki offers a virtual MX for use in Amazon Web Services and Microsoft Azure, enabling Auto VPN peering and SD-WAN for dynamic path selection.The MX67W, MX68W, and MX68CW integrate Cisco Meraki’s award-winning wireless technology with the powerful MX network security features in a compact form factor ideal for branch offices or small enterprises.• Dual-band 802.11n/ac Wave 2, 2x2 MU-MIMO with 2 spatial streams • Unified management of network security and wireless • Integrated enterprise security and guest accessIntegrated 802.11ac Wave 2 WirelessPower over EthernetThe MX65, MX65W, MX68, MX68W, and MX68CW include two ports with 802.3at (PoE+). This built-in power capability removes the need for additional hardware to power critical branch devices.• 2 x 802.3at (PoE+) ports capable of providing a total of 60W • APs, phones, cameras, and other PoE enabled devices can be powered without the need for AC adapters, PoE converters, or unmanaged PoE switches.MX68 Port ConfigurationVirtual MX is a virtual instance of a Meraki security appliance, dedicated specifically to providing the simple configuration benefits of site-to-site Auto VPN for customers running or migrating IT services to the public cloud. A virtual MX is added via the Amazon Web Services or Azure marketplace and then configured in the Meraki dashboard, just like any other MX. It functions like a VPN concentrator, and features SD-WAN functionality like other MX devices.• An Auto VPN to a virtual MX is like having a direct Ethernetconnection to a private datacenter. The virtual MX can support up to 500 Mbps of VPN throughput, providing ample bandwidth for mission critical IT services hosted in the public cloud, like Active Directory, logging, or file and print services.• Support for Amazon Web Services (AWS) and AzureMeraki vMX100MX68CW Security ApplianceLTE AdvancedWhile all MX models feature a USB port for 3G/4G failover, the MX67C and MX68CW include a SIM slot and internal LTE modem. This integrated functionality removes the need for external hardware and allows for cellular visibility and configuration within the Meraki dashboard.• 1 x CAT 6, 300 Mbps LTE modem • 1 x Nano SIM slot (4ff form factor)• Global coverage with individual orderable SKUs for North America and WorldwideMX67C SIM slotSmall branch Small branch Small branch Small branch50250 Mbps250 Mbps250 Mbps200 Mbps1Requires separate cellular modemMX67MX67C MX68MX68CW 1Requires separate cellular modemMedium branch Large branch Campus orVPN concentrator Campus orVPN concentratorRack Mount Models 1Requires separate cellular modemVirtual AppliancesExtend Auto-VPN and SD-WAN to public cloud servicesAmazon Web Services (AWS) and Microsoft Azure1 + VirtualIncluded in the BoxPackage Contents Platform(s)Mounting kit AllCat 5 Ethernet cable (2)AllAC Power Adapter MX64, MX64W, MX65, MX65W, MX67, MX67W, MX67C, MX68, MX68W, MX68CWWireless external omni antenna (2)MX64W, MX65W, MX67W, MX68W250W Power Supply (2)MX250, MX450System Fan (2)MX250, MX450SIM card ejector tool MX67C, MX68CWFixed external wireless and LTE paddle antennas MX68CWRemovable external LTE paddle antennas MX67CLifetime Warranty with Next-day Advanced ReplacementCisco Meraki MX appliances include a limited lifetime hardware warranty that provides next-day advance hardware replacement. Cisco Meraki’s simplified software and support licensing model also combines all software upgrades, centralized systems management, and phone support under a single, easy-to-understand model. For complete details, please visit /support.ACCESSORIES / SFP TRANSCEIVERSSupported Cisco Meraki accessory modulesNote: Please refer to for additional single-mode and multi-mode fiber transceiver modulesPOWER CABLES1x power cable required for each MX, 2x power cables required for MX250 and MX450. For US customers, all required power cables will beautomatically included. Customers outside the US are required to order power cords separately.SKUMA-PWR-CORD-AUThe Cisco Meraki MX84, MX100, MX250, MX450 models support pluggable optics for high-speed backbone connections between wir-ing closets or to aggregation switches. Cisco Meraki offers several standards-based Gigabit and 10 Gigabit pluggable modules. Each appliance has also been tested for compatibility with several third-party modules.Pluggable (SFP) Optics for MX84, MX100, MX250, MX450AccessoriesManagementManaged via the web using the Cisco Meraki dashboardSingle pane-of-glass into managing wired and wireless networksZero-touch remote deployment (no staging needed)Automatic firmware upgrades and security patchesTemplates based multi-network managementOrg-level two-factor authentication and single sign-onRole based administration with change logging and alertsMonitoring and ReportingThroughput, connectivity monitoring and email alertsDetailed historical per-port and per-client usage statisticsApplication usage statisticsOrg-level change logs for compliance and change managementVPN tunnel and latency monitoringNetwork asset discovery and user identificationPeriodic emails with key utilization metricsDevice performance and utilization reportingNetflow supportSyslog integrationRemote DiagnosticsLive remote packet captureReal-time diagnostic and troubleshooting toolsAggregated event logs with instant searchNetwork and Firewall ServicesStateful firewall, 1:1 NAT, DMZIdentity-based policiesAuto VPN: Automated site-to-site (IPsec) VPN, for hub-and-spoke or mesh topologies Client (IPsec L2TP) VPNMultiple WAN IP, PPPoE, NATVLAN support and DHCP servicesStatic routingUser and device quarantineWAN Performance ManagementWeb caching (available on the MX84, MX100, MX250, MX450)WAN link aggregationAutomatic Layer 3 failover (including VPN connections)3G / 4G USB modem failover or single-uplinkApplication level (Layer 7) traffic analysis and shapingAbility to choose WAN uplink based on traffic typeSD-WAN: Dual active VPN with policy based routing and dynamic path selection CAT 6 LTE modem for failover or single-uplink1MX67C and MX68CW only Advanced Security Services1Content filtering (Webroot BrightCloud CIPA compliant URL database)Web search filtering (including Google / Bing SafeSearch)Y ouTube for SchoolsIntrusion-prevention sensor (Cisco SNORT® based)Advanced Malware Protection (AMP)AMP Threat Grid2Geography based firewall rules (MaxMind Geo-IP database)1 Advanced security services require Advanced Security license2 Threat Grid services require additional sample pack licensingIntegrated Wireless (MX64W, MX65W, MX67W, MX68W, MX68CW)1 x 802.11a/n/ac (5 GHz) radio1 x 802.11b/g/n (2.4 GHz) radioMax data rate 1.2 Gbps aggregate (MX64W, MX65W), 1.3Gbps aggregate (MX67W,MX68W, MX68CW)2 x 2 MU-MIMO with two spatial streams (MX67W, MX68W, MX68CW)2 external dual-band dipole antennas (connector type: RP-SMA)Antennagain:*************,3.5dBi@5GHzWEP, WPA, WPA2-PSK, WPA2-Enterprise with 802.1X authenticationFCC (US): 2.412-2.462 GHz, 5.150-5.250 GHz (UNII-1), 5.250-5.350 GHZ (UNII-2), 5.470-5.725 GHz (UNII-2e), 5.725 -5.825 GHz (UNII-3)CE (Europe): 2.412-2.484 GHz, 5.150-5.250 GHz (UNII-1), 5.250-5.350 GHZ (UNII-2)5.470-5.600 GHz, 5.660-5.725 GHz (UNII-2e)Additional regulatory information: IC (Canada), C-Tick (Australia/New Zealand), RoHSIntegrated Cellular (MX67C and MX68CW only)LTE bands: 2, 4, 5, 12, 13, 17, and 19 (North America). 1, 3, 5, 7, 8, 20, 26, 28A, 28B, 34, 38, 39, 40, and 41 (Worldwide)300 Mbps CAT 6 LTEAdditional regulatory information: PTCRB (North America), RCM (ANZ, APAC), GCF (EU)Power over Ethernet (MX65, MX65W, MX68, MX68W, MX68CW)2 x PoE+ (802.3at) LAN ports30W maximum per portRegulatoryFCC (US)CB (IEC)CISPR (Australia/New Zealand)PTCRB (North America)RCM (Australia/New Zealand, Asia Pacific)GCF (EU)WarrantyFull lifetime hardware warranty with next-day advanced replacement included.Specificationsand support). For example, to order an MX64 with 3 years of Advanced Security license, order an MX64-HW with LIC-MX64-SEC-3YR. Lifetime warranty with advanced replacement is included on all hardware at no additional cost.*Note: For each MX product, additional 7 or 10 year Enterprise or Advanced Security licensing options are also available (ex: LIC-MX100-SEC-7YR).and support). For example, to order an MX64 with 3 years of Advanced Security license, order an MX64-HW with LIC-MX64-SEC-3YR. Lifetime warranty with advanced replacement is included on all hardware at no additional cost.*Note: For each MX product, additional 7 or 10 year Enterprise or Advanced Security licensing options are also available (ex: LIC-MX100-SEC-7YR).and support). For example, to order an MX64 with 3 years of Advanced Security license, order an MX64-HW with LIC-MX64-SEC-3YR. Lifetime warranty with advanced replacement is included on all hardware at no additional cost.*Note: For each MX product, additional 7 or 10 year Enterprise or Advanced Security licensing options are also available (ex: LIC-MX100-SEC-7YR).。
CCIE SECURITY V4.0 350-018186Q注:本文全部为个人手打,目的是为了方便记忆。
中文注释为个人翻译,不一定正确,仅供参考!1,which two EIGRP packet tpes are considered to be unreliable packets?(那俩类型的EIGRP 包的是不可靠的包)A,updateB,queryC,replyD,helloE,acknowledgement(明显hello不一定有人回所以不会需要确认,ack为确认包也不再一直确认)2,before BGP update messages may be sent,a neighbor must stabilize into which neighbor state?(BGP的邻居必须稳定在那种状态时可能会发送更新包)A,activeB, idleC,connectedD,established(established状态为BGP对等体建立完成,这时才可以交换update)3,which three statements are cortect when comparing mobile IPv6 and mobile IPv4 support?(那三句话正确的对比了移动IPV6 和移动IPV4)A,mobile ipv6 does not require a foreign agent,but mobile ipv4 doesB,mobile ipv6 supports route optimization as a fundamental part of the protocol;ipv4 requires extensionsC,mobile ipv6 and mobile ipv4 use a directed broadcast approach for home agent address discoveryD,mobile ipv6 makes ues of its own routing header, mobile ipv4 uses only ip encapsulationE,mobile ipv6 and mobile ipv4 use arp for neighbor discoveryF,mobile ipv4 has adopted the use of ipv6 ND(v6不需要外地代理v4需要, 路由优化是v6基本协议的一部分,v4在扩展协议里,v6有自己的路由头v4只有ip封装)4,which protocol does 802.1x use between the supplicant and the authenticator to authenticate users wish to access the network?(在802.1x的请求者和认证者间认证协议是那个)A,snmpB,tacacs+C,radiusD,eap over lanE,pppoe(802.1x主要用于请求者和认证者间封装EAP的二层协议,简称EAPOL)5,refer to the exhibit. Which message could contain an authenticated initial_contact notifyduring IKE main mode negotiation?(参考下图,那条信息包含IKE主模式认证初始接触通知)A,message3B,message5C,message1D,none,initial_contact is sent only during quick modeE,none,notify messages are sent only as independent message types(1、2个包为认证和加密模式交换,3、4为DH交换,第5个包开始是认证信息) 6,which two statements are correct regarding the AES encryption algorithm?(关于AES加密下面那两个说法正确)A,it is a FIPS-approved symmetric block cipherB,it supports a block size of 128,192or 256 bitsC,it supports a variable length block size from 16 to 448 bitsD, it supports a cipher key size of 128,192or256 bitsE,the AES encryption algorithm is based on the presumed difficulty of factoring large integers(AES是FIPS认可的一个块加密的对称密钥算法,块大小为128位,密钥大小可以为128、192或256)7,what are two benefits of using IKEv2 instead of IKEv1 when deploying remot-access IPsec VPN?(用IKEV2代替IKEV1部署远程访问IPSECVPN的两个好处是什么)A,IKEv2 supports EAP authentication methods as part of the protocolB, IKEv2 inherently supports NAT traversalC,IKEv2 messages use random message IDsD,the IKEv2 SA plus the IPsec SA can be established in six messages instead of nine messagesE,all IKEv2 messages are encryption-protected(EAP和NAT-T是IKEv2的标准组件,对于远程访问是对较方便的)8,DNSSEC was designed to overcome which security limitation of DNS? (DNSSEC是被设计用于克服那种安全攻击的)A,DNS man-in-the-middle attacksB,DNS flood attacksC,DNS fragmentation attacksD,DNS hash attacksE,DNS replay attacksF,DNS violation attacks(DNSSEC提供了源验证和数据完整性校验,可以有效的抵御中间人攻击)9,which three statements true about MAC sec?(关于MACsec那三个描述是正确的)A,it supports GCM modes of AES and 3DESB,it is defined under IEEE 802.1AEC,it provides hop-by-hop encryption at layer 2D,MACsec expects a strict order of frames to prevent anti-replayE,MKA is used for session and encryption key managementF,it uses EAP PACs to distribute encryption keys(MACsec是遵循dot1ae的二层加密协议,加密点到点的数据,也就是说加密流量不会穿越二层设备,使用MKA协商和管理密钥)10,which SSL protocol takes an application message to be transmitted,fragments the data into manageable blocks, optionally compresses the data,applies a MAC,encrypts,adds a header,and transmits the resulting unit in a TCP segment?A,SSL handshake protocolB,SSL alert protocolC,SSL record protocolD,SSL change cipherspec protocol(SSL协议可分为两层:SSL记录协议(SSL Record Protocol):它建立在可靠的传输协议(如TCP)之上,为高层协议提供数据封装、压缩、加密等基本功能的支持。