Juniper SRX防火墙Virtual Router配置实例
- 格式:pdf
- 大小:361.21 KB
- 文档页数:15

前言、版本说明 (2)一、界面菜单管理 (4)2、WEB管理界面 (4)(1)Web管理界面需要浏览器支持Flash控件。
(4)(2)输入用户名密码登陆: (4)(3)仪表盘首页 (5)3、菜单目录 (7)二、接口配置 (12)1、接口静态IP (12)2、PPPoE (13)3、DHCP (14)三、路由配置 (16)1、静态路由 (16)2、动态路由 (16)四、区域设置Zone (18)五、策略配置 (20)1、策略元素定义 (20)2、防火墙策略配置 (22)3、安全防护策略 (25)六、地址转换 (26)1、源地址转换-建立地址池 (26)2、源地址转换规则设置 (27)七、VPN配置 (30)1、建立第一阶段加密建议IKE Proposal (Phase 1) (或者用默认提议) (30)2、建立第一阶段IKE策略 (31)3、建立第一阶段IKE Gateway (32)4、建立第二阶段加密提议IKE Proposal (Phase 2) (或者用默认提议) (33)5、建立第一阶段IKE策略 (34)6、建立VPN策略 (35)八、Screen防攻击 (38)九、双机 (39)十、故障诊断 (39)前言、版本说明产品:Juniper SRX240 SH版本:JUNOS Software Release [9.6R1.13]注:测试推荐使用此版本。
此版本对浏览速度、保存速度提高了一些,并且CPU占用率明显下降很多。
9.5R2.7版本(CPU持续保持在60%以上,甚至90%)9.6R1.13版本(对菜单操作或者保存配置时,仍会提升一部分CPU)一、界面菜单管理1、管理方式JuniperSRX系列防火墙出厂默认状态下,登陆用户名为root密码为空,所有接口都已开启Web管理,但无接口地址。
终端连接防火墙后,输入用户名(root)、密码(空),显示如下:root@srx240-1%输入cli命令进入JUNOS访问模式:root@srx240-1% cliroot@srx240-1>输入configure进入JUNOS配置模式:root@srx240-1% cliroot@srx240-1> configureEntering configuration mode[edit]root@srx240-1#防火墙至少要进行以下配置才可以正常使用:(1)设置root密码(否则无法保存配置)(2)开启ssh/telnet/http服务(3)添加用户(root权限不能作为远程telnet帐户,可以使用SHH方式)(4)分配新的用户权限2、WEB管理界面(1)Web管理界面需要浏览器支持Flash控件。

juniper SRX系列防火墙高级安全设置Part2 security zone and interfaces创建安全zoneuser@host# set interfaces ge-0/0/1 unit 1 family inet address 10.12.12.1/24user@host# set security zones security-zone ABC interfaces ge-0/0/1.1配置接口的管理方式user@host# set security zones security-zone ABC interfaces ge-0/0/1.3host-inbound-traffic system-services ftpuser@host# set security zones security-zone ABC interfaces ge-0/0/1.3host-inbound-traffic system-services telnetuser@host# set security zones security-zone ABC interfaces ge-0/0/1.1host-inbound-traffic system-services snmp或者user@host# set security zones security-zone ABC interfaces ge-0/0/1.1host-inbound-traffic system-services alluser@host# set security zones security-zone ABC interfaces ge-0/0/1.1host-inbound-traffic system-services http exceptuser@host# set security zones security-zone ABC interfaces ge-0/0/1.3host-inbound-traffic system-services ftp except同时可以用protocol替换system-servicesAddress Books and Address Sets每一个安全zone包含一个address book。
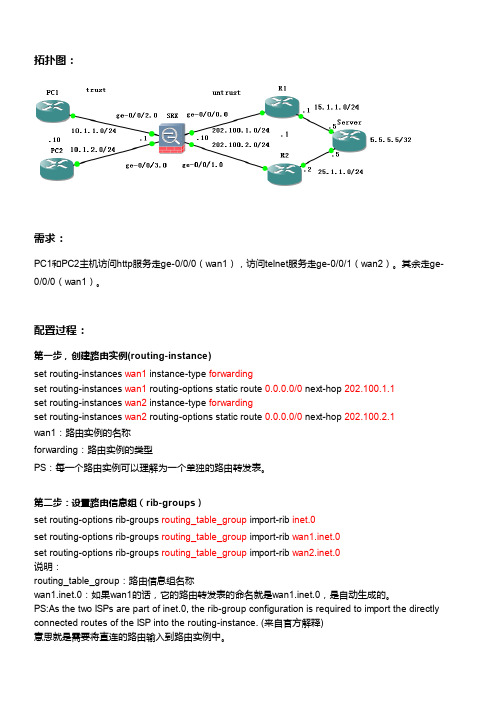
拓扑图:需求:PC1和PC2主机访问http服务走ge-0/0/0(wan1),访问telnet服务走ge-0/0/1(wan2)。
其余走ge-0/0/0(wan1)。
配置过程:第一步,创建路由实例(routing-instance)set routing-instances wan1 instance-type forwardingset routing-instances wan1 routing-options static route 0.0.0.0/0 next-hop 202.100.1.1set routing-instances wan2 instance-type forwardingset routing-instances wan2 routing-options static route 0.0.0.0/0 next-hop 202.100.2.1wan1:路由实例的名称forwarding:路由实例的类型PS:每一个路由实例可以理解为一个单独的路由转发表。
第二步:设置路由信息组(rib-groups)set routing-options rib-groups routing_table_group import-rib inet.0set routing-options rib-groups routing_table_group import-rib wan1.inet.0set routing-options rib-groups routing_table_group import-rib wan2.inet.0说明:routing_table_group:路由信息组名称wan1.inet.0:如果wan1的话,它的路由转发表的命名就是wan1.inet.0,是自动生成的。
PS:As the two ISPs are part of inet.0, the rib-group configuration is required to import the directly connected routes of the ISP into the routing-instance. (来自官方解释)意思就是需要将直连的路由输入到路由实例中。

关于Juniper 防火墙设备虚拟路由和策略路由的应用说明来源:作者:netscreen时间:01-03 06:09:20浏览:147【大中小】在Juniper防火墙设备的OS中,集成了虚拟路由和策略路由功能,在一般的情况下,这两个功能都很少使用,但是,在某些特殊的环境中就需要这两个功能的应用了。
虚拟路由在逻辑上,可以看做是一个独立的路由器,并有独立的路由列表。
在Juniper 防火墙的OS中,默认有两个虚拟路由:trust-vr和untrust-vr。
防火墙中的各种基于流量转发的安全区(ZONE),则默认工作在trust-vr中。
虚拟路由的功能在一些特殊的环境下,可以将一个独立的多端口防火墙,在逻辑上作为两台独立的防火墙使用(不启用虚拟系统:VSYS),则两个拥有独立路由列表的安全设备可以拥有各自独立的外网线路,并且,互相之间不受影响。
策略路由,在Juniper的防火墙中也被称为源地址路由,该路由的作用是:对内部地址外出访问互联网或其它网络时,进行外出线路选择。
策略路由一般的应用环境是:在防火墙设备实现多链路接入应用并有负载分配需求时,对内部网络IP地址的外出访问互联网时进行人为指定方式的外出链路选择。
策略路由的优先级别在默认的情况下为最高,所以在使用策略路由时,如果防火墙设备还定义了基于trust-vr 的DMZ区应用时,一定会受到策略路由优先的影响,从而导致对DMZ区访问的失败。
为了解决这个问题,则需要对防火墙的安全域进行调整,从而,应用到了另外一个虚拟路由:untrust-vr。
具体的实例说明:某客户的网络环境描述:电信和网通的两条专线连接,内部有若干台服务器,若干台内部办公计算机。
某客户的网络应用需求:1、服务器需要与内部办公网络进行隔离;2、内部办公网络中的计算机在访问互联网时,指定部分计算机强制使用网通线路,部分计算机强制使用电信线路。
3、实现访问控制。
仔细分析客户的网络环境和应用需求我们可以知道确定防火墙应用中的如下信息:1)防火墙设备要工作在三层的NAT/ROUTE模式下。

J u n i p e r S R X防火墙简明配置手册卞同超Juniper服务工程师JuniperNetworks,Inc.北京市东城区东长安街1号东方经贸城西三办公室15层1508室邮编:100738目录JuniperSRX防火墙简明配置手册SRX系列防火墙是Juniper公司基于JUNOS操作系统的安全系列产品,JUNOS集成了路由、交换、安全性和一系列丰富的网络服务。
目前Juniper公司的全系列路由器产品、交换机产品和SRX安全产品均采用统一源代码的JUNOS操作系统,JUNOS 是全球首款将转发与控制功能相隔离,并采用模块化软件架构的网络操作系统。
JUNOS作为电信级产品的精髓是Juniper真正成功的基石,它让企业级产品同样具有电信级的不间断运营特性,更好的安全性和管理特性,JUNOS软件创新的分布式架构为高性能、高可用、高可扩展的网络奠定了基础。
基于NP架构的SRX系列产品产品同时提供性能优异的防火墙、NAT、IPSEC、IPS、SSLVPN和UTM等全系列安全功能,其安全功能主要来源于已被广泛证明的ScreenOS操作系统。
本文旨在为熟悉Netscreen防火墙ScreenOS操作系统的工程师提供SRX防火墙参考配置,以便于大家能够快速部署和维护SRX防火墙,文档介绍JUNOS操作系统,并参考ScreenOS配置介绍SRX防火墙配置方法,最后对SRX防火墙常规操作与维护做简要说明。
一、JUNOS操作系统介绍1.1层次化配置结构JUNOS采用基于FreeBSD内核的软件模块化操作系统,支持CLI命令行和WEBUI 两种接口配置方式,本文主要对CLI命令行方式进行配置说明。
JUNOSCLI使用层次化配置结构,分为操作(operational)和配置(configure)两类模式,在操作模式下可对当前配置、设备运行状态、路由及会话表等状态进行查看及设备运维操作,并通过执行config或edit命令进入配置模式,在配置模式下可对各相关模块进行配置并能够执行操作模式下的所有命令(run)。

JUNIPer配置说明〉操作模式#配置模式#show interface#show interface deatil | math fe‐0/0/0>hlpe apropes arp>config 3种模式#edit interface 一层一层配置#up 退出#show |display set (显示所有可刷的命令)#edit security nat source#rename rule‐set trust‐to‐untrust to rule‐set inside‐to‐outside (重命令nat名字) #rollback (恢复到以前的配置,可选50份)#commit at 201207200800(定时提交)>clear system commit (清除未提交的配置)#commit comment "beyond"(为提交的配置进行说明)# run show system commit(查看提交的配置说明,用于快速恢复的配置) #commit confirmed (十分钟之内不对配置进行确认,自动恢复配置到提交之前) #copy interface ge‐0/0/1 to ge0/0/3 (复制配置)#show system update (查看系统时间)>request system reboot (重启系统)>request system power‐off (关闭系统)#edit sytem login user class ? (设置用户,有4种权限)#edit system service (设置系统服务)#set ssh /telnet /web‐ma….>show system license (查看授权)>request system license add terminal (加载授权信息)> show system processes extensive(查看系统进程)> restart chassis‐control gracefully(重启系统进程)> load update xxx (加载以前的配置文件)run show security flow session summary(查看防火墙会话数)run show security flow session(查看防火墙具体会话数)1, root密码设置set system root‐authentication plain‐text‐passworderpo@66982, 远程登录用户set system login user erpo class super‐user authentication plain‐text‐passworderpo66983,设置时间run set date 2012070919084,设置时区为上海set system time‐zone Asia/shanghai5,设置主机名set system host‐name FW6,设置NDS服和器Set system name‐server 208.67.222.222; 208.67.220.220;7,端口交换机属性设置root@ex2200# edit vlans test #新建vlan名称为testroot@ex2200# set vlan-id 10 #设置vlan idroot@ex2200# set description “Test VLAN” #设置vlan描述root@ex2200# set mac-limit 200 #设置mac数量,范围是(1..65535),通常可以不配置root@ex2200# set mac-table-aging-time 600 #”设置mac生存时间(秒),范围是(60-1000000) ”root@ex2200# set l3-interface vlan.10 #”将绑定三层逻辑子端口”root@ex2200# set interface ge-0/0/1.0 #”将端口加入到VLAN中”root@ex2200# set interface ge-0/0/2.0 #”将端口加入到VLAN中”(2)创建三层逻辑子端口root@ex2200# top #”回到最外层菜单”root@ex2200# set interfaces vlan unit 10 family inet address 192.168.1.1/24 #设置网关(3)将交换机端口修改为access模式并加入到新创建的VLAN中root@ex2200# top #”回到最外层菜单”root@ex2200# set interfaces ge-0/0/1 unit 0 family ethernet-switching port-mode accessroot@ex2200# set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members 10root@ex2200# set interfaces ge-0/0/2 unit 0 family ethernet-switching port-mode accessroot@ex2200# set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members 10(4)commit提交:root@ex2200#commit8, DHCP 配置(DHCP Server)set system services dhcp pool 192.168.1.0/24 address-range low 192.168.1.33set system services dhcp pool 192.168.1.0/24 address-range high 192.168.1.64et system services dhcp pool 192.168.1.0/24 domain-name set system services dhcp pool 192.168.1.0/24 name-server 192.168.1.1set system services dhcp pool 192.168.1.0/24 router 192.168.1.1set system services dhcp pool 192.168.1.0/24 default-lease-time 3600set security zones security-zone untrust interfaces fe-0/0/5.0 host-inbound-traffic system-services dhcpuser@host# set security zones security-zone untrust interfaces fe-0/0/6.0 host-inbound-traffic system-services dhcp user@host# set interfaces fe-0/0/6 unit 0 family inet address 192.168.1.1/24DHCP设置(DHCP Client)user@host# set interfaces fe‐0/0/7 unit 0 family inet dhcpuser@host# set security zones security‐zone untrust interfaces fe‐0/0/7.0 host‐inbound‐traffic system‐services dhcpDHCP设置(DHCP Relay)user@host# set forwarding‐options helpers bootp description "Global DHCP relay service"user@host# set forwarding‐options helpers bootp server 192.18.24.38user@host# set forwarding‐options helpers bootp maximum‐hop‐count 4user@host# set forwarding‐options helpers bootp interface fe‐0/0/7.0user@host# set security zones security‐zone untrust interfaces fe‐0/0/7 host‐inbound‐traffic system‐services dhcpuser@host# set security zones security‐zone untrust interfaces fe‐0/0/8 host‐inbound‐traffic system‐services dhcp9,接口设置user@host# set interfaces ge-0/0/1 unit 0 family inet address 192.168.20.2/24或者set interfaces ge-0/0/1.0 family inet address 192.168.20.2/249.2 设置区域user@host# set security zones security-zone trustuser@host# set security zones security-zone trust interfaces ge-0/0/1.0…ge-0/0/1.0 host-inbound-traffic system-services http (允许的服务)10, 静态路由user@host# set routing-options static route 10.2.2.0/24 next-hop 10.1.1.254user@host# set routing-options static route 0.0.0.0/0 next-hop 10.1.1.25411,在系统级开启ftp/telnet/http远程接入管理服务Set system services ftpSet system services sshSet system services telnetSet system services web‐management http12, 在untrust zone 打开允许远程登录管理服务Set security zones security‐zone untrnst host‐inbound‐traffic system‐services ssh13,防火墙策略安全设备的缺省行为是拒绝安全区段之间的所有信息流,允许绑定到同一区段的接口间的所有信息流。
JuniperSRX3400 Routing-instance AAA、NTP、SYSLOG实验配置手册目录1.实验需求 (3)2.实验环境 (3)3.实验拓扑 (4)3.1.创建虚拟机 (4)3.2.虚拟机之间网络连接 (4)4.防火墙配置 (7)5.AAA配置验证 (14)5.1.1.若将防火墙source-address定义为172.16.1.1 (14)5.1.2.删除环回口lo0地址 (16)6.NTP配置验证 (17)6.1.1.若将ntp源地址设为172.16.1.1, (18)6.1.2.删除环回口lo0地址 (18)7.SYSLOG配置验证 (19)7.1.1.若将SYSLOG源地址设为172.16.1.1 (19)7.1.2.删除防火墙上lo0接口地址 (20)8.最终结论 (21)为了能够充分理解Juniper SRX 防火墙在运行routing-instance 情况下配置AAA、syslog、ntp的运行机制,通过虚拟机搭建试验环境来验证。
2.实验环境Juniper 防火墙使用虚拟机来搭建,Radius服务器使用windows 2003 + ACS v4.2,将windows 2003作为ntp server, 在windows 2003上安装Kiwi_Syslog_Server 作为syslog软件。
实验工具如下:3.1.创建虚拟机创建2个虚拟机:SRX:juniper 防火墙Radius_NTP_Syslog_server:作为radius、NTP、syslog服务器;3.2.虚拟机之间网络连接各虚拟机网卡连接方式如下:1)将虚拟机SRX网卡1与物理机网卡桥接2)将虚拟机SRX网卡3采用自定义方式,用于与两台服务器连接3)服务器网卡也采用自定义的方式,用于与SRX连接:4)配置IP地址,测试联通性按照以上拓扑图对防火墙接口、服务器网口的IP地址进行配置,并测试连通性。
Juniper SRX系列防火墙配置管理手册目录一、JUNOS操作系统介绍 (3)层次化配置结构 (3)JunOS配置管理 (4)SRX主要配置内容 (4)二、SRX防火墙配置操作举例说明 (5)初始安装 (5)设备登陆 (5)设备恢复出厂介绍 (5)设置root用户口令 (5)设置远程登陆管理用户 (6)远程管理SRX相关配置 (6)配置操作实验拓扑 (7)策略相关配置说明 (7)策略地址对象定义 (8)策略服务对象定义 (8)策略时间调度对象定义 (8)添加策略配置举例 (9)策略删除 (10)调整策略顺序 (10)策略失效与激活 (10)地址转换 (10)Interface based NAT 基于接口的源地址转换 (11)Pool based Source NAT基于地址池的源地址转换 (12)Pool base destination NAT基于地址池的目标地址转换 (12)Pool base Static NAT基于地址池的静态地址转换 (13)路由协议配置 (14)静态路由配置 (14)OSPF配置 (15)交换机Firewall限制功能 (22)限制IP地 (22)限制MAC地址 (22)三、SRX防火墙常规操作与维护 (23)设备关机 (23)设备重启 (23)操作系统升级 (24)密码恢复 (24)常用监控维护命令 (25)Juniper SRX Branch系列防火墙配置管理手册说明SRX系列防火墙是Juniper公司基于JUNOS操作系统的安全系列产品,JUNOS集成了路由、交换、安全性和一系列丰富的网络服务。
目前Juniper公司的全系列路由器产品、交换机产品和SRX安全产品均采用统一源代码的JUNOS操作系统,JUNOS是全球首款将转发与控制功能相隔离,并采用模块化软件架构的网络操作系统。
JUNOS作为电信级产品的精髓是Juniper真正成功的基石,它让企业级产品同样具有电信级的不间断运营特性,更好的安全性和管理特性,JUNOS软件创新的分布式架构为高性能、高可用、高可扩展的网络奠定了基础。
Juniper-SRX防火墙Web配置说明Juniper SRX防火墙配置说明1系统配置 (1)1.1配置ROOT帐号密码 (1)1.2配置用户名和密码 (2)2接口配置 (9)2.1IPV4地址配置 (9)2.2接口T RUNK模式配置 (13)2.3接口A CCESS模式配置 (14)3VLAN配置 (15)3.1创建VLAN配置 (15)4路由配置 (19)4.1静态路由配置 (21)5自定义应用配置 (22)5.1自定义服务配置 (22)5.2应用组配置 (23)6地址组配置 (24)6.1地址簿配置 (24)6.2地址组配置 (25)7日程表配置 (27)8NAT配置 (30)8.1S TATIC NAT配置 (30)1 系统配置1.1 配置root帐号密码首次登陆设备时,需要采用console方式,登陆用户名为:root,密码为空,登陆到cli下以后,执行如下命令,设置root帐号的密码。
root# set system root-authentication plain-text-passwordroot# new password : root123root# retype new password: root123密码将以密文方式显示。
注意:必须要首先配置root帐号密码,否则后续所有配置的修改都无法提交。
SRX系列低端设备在开机后,系统会加载一个默认配置,设备的第一个接口被划分在trust区域,配置一个ip地址192.168.1.1,允许ping、telnet、web等管理方式,可以通过该地址登陆设备。
登陆后显示页面如下:在该页面上,可以看到设备的基本情况,在左边的chassis view 中可以看到端口up/down情况,在system identification中可以看到设备序列号、设备名称、软件版本等信息,在resource utilization 中可以看到cpu、menory、session、存储空间等信息,在security resources中可以看到当前的会话统计、策略数量统计等信息。
Juniper SRX防火墙配置手册一、JUNOS操作系统介绍1.1 层次化配置结构JUNOS采用基于FreeBSD内核的软件模块化操作系统,支持CLI命令行和WEBUI两种接口配置方式,本文主要对CLI命令行方式进行配置说明。
JUNOS CLI使用层次化配置结构,分为操作(operational)和配置(configure)两类模式,在操作模式下可对当前配置、设备运行状态、路由及会话表等状态进行查看及设备运维操作,并通过执行config或edit命令进入配置模式,在配置模式下可对各相关模块进行配置并能够执行操作模式下的所有命令(run)。
在配置模式下JUNOS采用分层分级模块下配置结构,如下图所示,edit命令进入下一级配置(类似unix cd 命令),exit命令退回上一级,top命令回到根级。
1.2 JunOS配置管理JUNOS通过set语句进行配置,配置输入后并不会立即生效,而是作为候选配置(Candidate Config)等待管理员提交确认,管理员通过输入commit命令来提交配置,配置内容在通过SRX 语法检查后才会生效,一旦commit通过后当前配置即成为有效配置(Active config)。
另外,JUNOS 允许执行commit命令时要求管理员对提交的配置进行两次确认,如执行commit confirmed 2命令要求管理员必须在输入此命令后2分钟内再次输入commit以确认提交,否则2分钟后配置将自动回退,这样可以避免远程配置变更时管理员失去对SRX的远程连接风险。
在执行commit命令前可通过配置模式下show命令查看当前候选配置(Candidate Config),在执行commit后配置模式下可通过run show config命令查看当前有效配置(Active config)。
此外可通过执行show | compare比对候选配置和有效配置的差异。
SRX上由于配备大容量硬盘存储器,缺省按先后commit顺序自动保存50份有效配置,并可通过执行rolback和commit命令返回到以前配置(如rollback 0/commit可返回到前一commit配置);也可以直接通过执行save configname.conf手动保存当前配置,并执行load override configname.conf / commit调用前期手动保存的配置。
Juniper SRX防火墙Virtual Router配置实例实例拓扑图:一虚拟路由器(记住来流量入口);需求:外网用户访问防火墙的外网接口3389端口NAT到内网服务器192.168.3.5:3389,流量按原路返回;放行所有外网用户到主机192.168.3.5的3389端口;(双线接入)配置:set routing-instances Tel instance-type virtual-routerset routing-instances Tel interface ge-0/0/4.0set routing-instances Tel routing-options interface-routes rib-group inet Big-ribset routing-instances Tel routing-options static route 0.0.0.0/0 next-hop 192.168.4.2set routing-instances CNC instance-type virtual-routerset routing-instances CNC interface ge-0/0/5.0set routing-instances CNC routing-options interface-routes rib-group inet Big-ribset routing-instances CNC routing-options static route 0.0.0.0/0 next-hop 192.168.5.2set interfaces ge-0/0/3 unit 0 family inet address 192.168.3.1/24set interfaces ge-0/0/4 unit 0 family inet address 192.168.4.1/24set interfaces ge-0/0/5 unit 0 family inet address 192.168.5.1/24set interfaces ge-0/0/6 unit 0 family inet address 10.10.30.189/24set routing-options interface-routes rib-group inet Big-ribset routing-options static route 10.0.0.0/8 next-hop 10.10.30.1set routing-options static route 0.0.0.0/0 next-hop 192.168.4.2set routing-options static route 0.0.0.0/0 installset routing-options static route 0.0.0.0/0 no-readvertiseset routing-options rib-groups Big-rib import-rib inet.0set routing-options rib-groups Big-rib import-rib CNC.inet.0set routing-options rib-groups Big-rib import-rib Tel.inet.0set security nat destination pool 111 address 192.168.3.5/32set security nat destination rule-set 1 from zone Tel-trustset security nat destination rule-set 1 rule 111 match source-address 0.0.0.0/0set security nat destination rule-set 1 rule 111 match destination-address 192.168.4.1/32set security nat destination rule-set 1 rule 111 match destination-port 3389set security nat destination rule-set 1 rule 111 then destination-nat pool 111set security nat destination rule-set 2 from zone CNC-trustset security nat destination rule-set 2 rule 222 match source-address 0.0.0.0/0set security nat destination rule-set 2 rule 222 match destination-address 192.168.5.1/32set security nat destination rule-set 1 rule 111 match destination-port 3389set security nat destination rule-set 2 rule 222 then destination-nat pool 111set applications application tcp_3389 protocol tcpset applications application tcp_3389 destination-port 3389set security zones security-zone trust address-book address H_192.168.3.5 192.168.3.5/32set security policies from-zone Tel-trust to-zone trust policy default-permit match source-address anyset security policies from-zone Tel-trust to-zone trust policy default-permit match destination-address H_192.168.3.5set security policies from-zone Tel-trust to-zone trust policy default-permit match application tcp_3389set security policies from-zone Tel-trust to-zone trust policy default-permit then permitset security policies from-zone CNC-trust to-zone trust policy default-permit match source-address anyset security policies from-zone CNC-trust to-zone trust policy default-permit match destination-address H_192.168.3.5set security policies from-zone CNC-trust to-zone trust policy default-permit match application tcp_3389set security policies from-zone CNC-trust to-zone trust policy default-permit then permitset security zones security-zone trust host-inbound-traffic system-services allset security zones security-zone trust host-inbound-traffic protocols allset security zones security-zone trust interfaces ge-0/0/3.0set security zones security-zone Tel-trust host-inbound-traffic system-services allset security zones security-zone Tel-trust host-inbound-traffic protocols allset security zones security-zone Tel-trust interfaces ge-0/0/4.0set security zones security-zone CNC-trust host-inbound-traffic system-services allset security zones security-zone CNC-trust host-inbound-traffic protocols allset security zones security-zone CNC-trust interfaces ge-0/0/5.0set security zones security-zone MGT host-inbound-traffic system-services allset security zones security-zone MGT host-inbound-traffic protocols allset security zones security-zone MGT interfaces ge-0/0/6.0验证:root@SRX-Ipsec-A> show security flow sessionSession ID: 9696, Policy name: default-permit/5, Timeout: 1794, ValidIn: 192.168.100.211/57408 --> 192.168.5.1/3389;tcp, If: ge-0/0/5.0, Pkts: 2, Bytes: 112Out: 192.168.3.5/3389 --> 192.168.100.211/57408;tcp, If: ge-0/0/3.0, Pkts: 1, Bytes: 60 ============================================================================ root@SRX-Ipsec-A> show security flow sessionSession ID: 9697, Policy name: default-permit/4, Timeout: 1796, ValidIn: 192.168.100.211/57409 --> 192.168.4.1/3389;tcp, If: ge-0/0/4.0, Pkts: 2, Bytes: 112Out: 192.168.3.5/3389 --> 192.168.100.211/57409;tcp, If: ge-0/0/3.0, Pkts: 1, Bytes: 60配置解析:set routing-instances Tel instance-type virtual-router //创建虚拟VR Telset routing-instances Tel interface ge-0/0/4.0 //把逻辑接口加入虚拟VRset routing-instances Tel routing-options interface-routes rib-group inet Big-rib //定义新增的路由表属于路由组“Big-rib” set routing-instances Tel routing-options static route 0.0.0.0/0 next-hop 192.168.4.2 //为Tel路由表配置路由set routing-instances CNC instance-type virtual-router set routing-instances CNC interface ge-0/0/5.0set routing-instances CNC routing-options interface-routes rib-group inet Big-ribset routing-instances CNC routing-options static route 0.0.0.0/0 next-hop 192.168.5.2 //配置路由表CNC相关信息set interfaces ge-0/0/3 unit 0 family inet address 192.168.3.1/24set interfaces ge-0/0/4 unit 0 family inet address 192.168.4.1/24set interfaces ge-0/0/5 unit 0 family inet address 192.168.5.1/24set interfaces ge-0/0/6 unit 0 family inet address 10.10.30.189/24 //配置逻辑接口的IP地址set routing-options interface-routes rib-group inet Big-rib //定义路由表组,并把接口路由加入到Big-rib路由组中set routing-options static route 10.0.0.0/8 next-hop 10.10.30.1set routing-options static route 0.0.0.0/0 next-hop 192.168.4.2 //配置全局路由表路由信息set routing-options static route 0.0.0.0/0 install //把路由表安装到转发表set routing-options static route 0.0.0.0/0 no-readvertise //set routing-options rib-groups Big-rib import-rib inet.0set routing-options rib-groups Big-rib import-rib CNC.inet.0set routing-options rib-groups Big-rib import-rib Tel.inet.0 //导入三张路由表之间的直连路由到路由表组set security nat destination pool 111 address 192.168.3.5/32 //定义目的NAT后的内部服务器的IP地址set security nat destination rule-set 1 from zone Tel-trustset security nat destination rule-set 1 rule 111 match source-address 0.0.0.0/0set security nat destination rule-set 1 rule 111 match destination-address 192.168.4.1/32set security nat destination rule-set 1 rule 111 match destination-port 3389set security nat destination rule-set 1 rule 111 then destination-nat pool 111 //配置ZONE Tel-trust的目的NATset security nat destination rule-set 2 from zone CNC-trustset security nat destination rule-set 2 rule 222 match source-address 0.0.0.0/0set security nat destination rule-set 2 rule 222 match destination-address 192.168.5.1/32set security nat destination rule-set 1 rule 111 match destination-port 3389set security nat destination rule-set 2 rule 222 then destination-nat pool 111 //配置ZONE CNC-trust的目的NAT set applications application tcp_3389 protocol tcpset applications application tcp_3389 destination-port 3389set security zones security-zone trust address-book address H_192.168.3.5 192.168.3.5/32 //自定义端口和配置地址表set security policies from-zone Tel-trust to-zone trust policy default-permit match source-address anyset security policies from-zone Tel-trust to-zone trust policy default-permit match destination-address H_192.168.3.5 set security policies from-zone Tel-trust to-zone trust policy default-permit match application tcp_3389set security policies from-zone Tel-trust to-zone trust policy default-permit then permit //配置Tel-trust到trust策略set security policies from-zone CNC-trust to-zone trust policy default-permit match source-address anyset security policies from-zone CNC-trust to-zone trust policy default-permit match destination-address H_192.168.3.5set security policies from-zone CNC-trust to-zone trust policy default-permit match application tcp_3389set security policies from-zone CNC-trust to-zone trust policy default-permit then permit //配置CNC-trust到trust策略set security zones security-zone trust host-inbound-traffic system-services allset security zones security-zone trust host-inbound-traffic protocols allset security zones security-zone trust interfaces ge-0/0/3.0set security zones security-zone Tel-trust host-inbound-traffic system-services allset security zones security-zone Tel-trust host-inbound-traffic protocols allset security zones security-zone Tel-trust interfaces ge-0/0/4.0set security zones security-zone CNC-trust host-inbound-traffic system-services allset security zones security-zone CNC-trust host-inbound-traffic protocols allset security zones security-zone CNC-trust interfaces ge-0/0/5.0set security zones security-zone MGT host-inbound-traffic system-services allset security zones security-zone MGT host-inbound-traffic protocols allset security zones security-zone MGT interfaces ge-0/0/6.0 //定义逻辑接口到ZONE,并开放所有的协议及服务来访问防火墙的直连接口二虚拟路由器(多链路负载冗余);需求:内网用户访问端口22.3389.8080,走电信,其他所有流量走CNC;所有内网访问外网的流量NAT为对应外网接口IP地址;实现负载冗余的功能;放行所有服务;(双线接入)配置:set routing-instances Tel instance-type virtual-routerset routing-instances Tel interface ge-0/0/4.0set routing-instances Tel routing-options interface-routes rib-group inet Big-ribset routing-instances Tel routing-options static route 0.0.0.0/0 next-hop 192.168.4.2set routing-instances Tel routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.5.2 preference 100set routing-instances CNC instance-type virtual-router set routing-instances CNC interface ge-0/0/5.0set routing-instances CNC routing-options interface-routes rib-group inet Big-ribset routing-instances CNC routing-options static route 0.0.0.0/0 next-hop 192.168.5.2set routing-instances CNC routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.4.2 preference 100 set interfaces ge-0/0/3 unit 0 family inet address 192.168.3.1/24set interfaces ge-0/0/4 unit 0 family inet address 192.168.4.1/24set interfaces ge-0/0/5 unit 0 family inet address 192.168.5.1/24set interfaces ge-0/0/6 unit 0 family inet address 10.10.30.189/24set routing-options interface-routes rib-group inet Big-ribset routing-options static route 10.0.0.0/8 next-hop 10.10.30.1set routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.5.2 preference 100set routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.4.2 preference 10set routing-options static route 0.0.0.0/0 installset routing-options static route 0.0.0.0/0 no-readvertiseset routing-options rib-groups Big-rib import-rib inet.0set routing-options rib-groups Big-rib import-rib CNC.inet.0set routing-options rib-groups Big-rib import-rib Tel.inet.0set security nat source rule-set Soure-NAT-Policy from zone trustset security nat source rule-set Soure-NAT-Policy to zone Tel-trustset security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match source-address 192.168.3.0/24 set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match destination-address 0.0.0.0/0set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 then source-nat interfaceset security zones security-zone trust address-book address Net_192.168.3.0 192.168.3.0/24set security policies from-zone trust to-zone Tel-trust policy 1 match source-address Net_192.168.3.0set security policies from-zone trust to-zone Tel-trust policy 1 match destination-address anyset security policies from-zone trust to-zone Tel-trust policy 1 match application anyset security policies from-zone trust to-zone Tel-trust policy 1 then permitset security policies from-zone trust to-zone Tel-trust policy 1 then log session-initset security policies from-zone trust to-zone Tel-trust policy 1 then log session-closeset security nat source rule-set Soure-NAT-Policy-2 from zone trustset security nat source rule-set Soure-NAT-Policy-2 to zone CNC-trustset security nat source rule-set Soure-NAT-Policy-2 rule Source-nat-2 match source-address 192.168.3.0/24 set security nat source rule-set Soure-NAT-Policy-2 rule Source-nat-2 match destination-address 0.0.0.0/0 set security nat source rule-set Soure-NAT-Policy-2 rule Source-nat-2 then source-nat interfaceset security policies from-zone trust to-zone CNC-trust policy 2 match source-address Net_192.168.3.0set security policies from-zone trust to-zone CNC-trust policy 2 match destination-address anyset security policies from-zone trust to-zone CNC-trust policy 2 match application anyset security policies from-zone trust to-zone CNC-trust policy 2 then permitset security policies from-zone trust to-zone CNC-trust policy 2 then log session-initset security policies from-zone trust to-zone CNC-trust policy 2 then log session-closeset interfaces ge-0/0/3 unit 0 family inet filter input filter-1set firewall filter filter-1 term term-1 from destination-port 22set firewall filter filter-1 term term-1 from destination-port 3389set firewall filter filter-1 term term-1 from destination-port 8080set firewall filter filter-1 term term-1 then routing-instance Telset firewall filter filter-1 term default then routing-instance CNCset security zones security-zone trust host-inbound-traffic system-services allset security zones security-zone trust host-inbound-traffic protocols allset security zones security-zone trust interfaces ge-0/0/3.0set security zones security-zone Tel-trust host-inbound-traffic system-services all set security zones security-zone Tel-trust host-inbound-traffic protocols allset security zones security-zone Tel-trust interfaces ge-0/0/4.0set security zones security-zone CNC-trust host-inbound-traffic system-services all set security zones security-zone CNC-trust host-inbound-traffic protocols allset security zones security-zone CNC-trust interfaces ge-0/0/5.0set security zones security-zone MGT host-inbound-traffic system-services allset security zones security-zone MGT host-inbound-traffic protocols allset security zones security-zone MGT interfaces ge-0/0/6.0验证:基于目标端口路由验证:Session ID: 9693, Policy name: 1121/6, Timeout: 1790, ValidIn: 192.168.3.5/52562 --> 192.168.100.211/3389;tcp, If: ge-0/0/3.0, Pkts: 2, Bytes: 112 Out: 192.168.100.211/3389 --> 192.168.4.1/28262;tcp, If: ge-0/0/4.0, Pkts: 1, Bytes: 60 Session ID: 9703, Policy name: 1121/7, Timeout: 2, ValidIn: 192.168.3.5/6252 --> 192.168.100.211/1;icmp, If: ge-0/0/3.0, Pkts: 1, Bytes: 60Out: 192.168.100.211/1 --> 192.168.5.1/4217;icmp, If: ge-0/0/5.0, Pkts: 1, Bytes: 60查看当前路由表:root@SRX-Ipsec-A> show route双线冗余验证:root@SRX-Ipsec-A> show security flow sessionSession ID: 10321, Policy name: 1121/7, Timeout: 48, ValidIn: 192.168.3.2/188 --> 192.168.100.211/59209;icmp, If: ge-0/0/3.0, Pkts: 1, Bytes: 84Out: 192.168.100.211/59209 --> 192.168.5.1/13586;icmp, If: ge-0/0/5.0, Pkts: 0, Bytes: 0Session ID: 10322, Policy name: 1121/6, Timeout: 50, Valid手动拔掉CNC广域网线路(模拟CNC线路故障)In: 192.168.3.2/189 --> 192.168.100.211/59209;icmp, If: ge-0/0/3.0, Pkts: 1, Bytes: 84Out: 192.168.100.211/59209 --> 192.168.4.1/19350;icmp, If: ge-0/0/4.0, Pkts: 0, Bytes: 0 Session ID: 10330, Policy name: 1121/6, Timeout: 2, ValidIn: 192.168.3.2/197 --> 192.168.100.211/59209;icmp, If: ge-0/0/3.0, Pkts: 1, Bytes: 84Out: 192.168.100.211/59209 --> 192.168.4.1/3661;icmp, If: ge-0/0/4.0, Pkts: 1, Bytes: 84配置解析:set routing-instances Tel instance-type virtual-router set routing-instances Tel interface ge-0/0/4.0set routing-instances Tel routing-options interface-routes rib-group inet Big-ribset routing-instances Tel routing-options static route 0.0.0.0/0 next-hop 192.168.4.2set routing-instances CNC routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.5.2 preference 100 //配置Tel路由表并配置相关信息,通过优先级来实现双广域网冗余,优先级值越小,优先级越高set routing-instances CNC instance-type virtual-router set routing-instances CNC interface ge-0/0/5.0set routing-instances CNC routing-options interface-routes rib-group inet Big-ribset routing-instances CNC routing-options static route 0.0.0.0/0 next-hop 192.168.5.2set routing-instances CNC routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.4.2 preference 100 //配置CNC路由表并配置相关信息set interfaces ge-0/0/3 unit 0 family inet address 192.168.3.1/24set interfaces ge-0/0/4 unit 0 family inet address 192.168.4.1/24set interfaces ge-0/0/5 unit 0 family inet address 192.168.5.1/24set interfaces ge-0/0/6 unit 0 family inet address 10.10.30.189/24 //配置逻辑接口对应IP地址set routing-options interface-routes rib-group inet Big-rib //定义路由表组,并把接口路由加入到Big-rib路由组中set routing-options static route 10.0.0.0/8 next-hop 10.10.30.1set routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.5.2 preference 100set routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.4.2 preference 10 //配置全局路由表路由信息,通过指定优先级来实现双广域网的冗余set routing-options static route 0.0.0.0/0 install //把路由表安装到转发表set routing-options static route 0.0.0.0/0 no-readvertise //set routing-options rib-groups Big-rib import-rib inet.0set routing-options rib-groups Big-rib import-rib CNC.inet.0set routing-options rib-groups Big-rib import-rib Tel.inet.0 //导入三张路由表之间的直连路由到路由表组set security nat source rule-set Soure-NAT-Policy from zone trustset security nat source rule-set Soure-NAT-Policy to zone Tel-trustset security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match source-address 192.168.3.0/24set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match destination-address 0.0.0.0/0set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 then source-nat interface //配置ZONE Tel-trust基于接口的源NATset security zones security-zone trust address-book address Net_192.168.3.0 192.168.3.0/24 //定义地址表set security policies from-zone trust to-zone Tel-trust policy 1 match source-address Net_192.168.3.0set security policies from-zone trust to-zone Tel-trust policy 1 match destination-address anyset security policies from-zone trust to-zone Tel-trust policy 1 match application anyset security policies from-zone trust to-zone Tel-trust policy 1 then permitset security policies from-zone trust to-zone Tel-trust policy 1 then log session-initset security policies from-zone trust to-zone Tel-trust policy 1 then log session-close //根据需求配置策略并记录LOG信息set security nat source rule-set Soure-NAT-Policy-2 from zone trustset security nat source rule-set Soure-NAT-Policy-2 to zone CNC-trustset security nat source rule-set Soure-NAT-Policy-2 rule Source-nat-2 match source-address 192.168.3.0/24set security nat source rule-set Soure-NAT-Policy-2 rule Source-nat-2 match destination-address 0.0.0.0/0set security nat source rule-set Soure-NAT-Policy-2 rule Source-nat-2 then source-nat interface //配置ZONE CNC-trust基于接口的源NATset security policies from-zone trust to-zone CNC-trust policy 2 match source-address Net_192.168.3.0set security policies from-zone trust to-zone CNC-trust policy 2 match destination-address anyset security policies from-zone trust to-zone CNC-trust policy 2 match application anyset security policies from-zone trust to-zone CNC-trust policy 2 then permitset security policies from-zone trust to-zone CNC-trust policy 2 then log session-initset security policies from-zone trust to-zone CNC-trust policy 2 then log session-close //根据需求配置策略并记录LOG信息set interfaces ge-0/0/3 unit 0 family inet filter input filter-1 //从接口ge-0/0/3进入的数据进行包过滤操作,并定义名称” filter-1”set firewall filter filter-1 term term-1 from destination-port 22set firewall filter filter-1 term term-1 from destination-port 3389set firewall filter filter-1 term term-1 from destination-port 8080 //对符合包过滤名称”filter-1”的且符合目标端口22,3389,8080数据进行打标记,标记为term-1 set firewall filter filter-1 term term-1 then routing-instance Tel //定义标记为term-1的数据,使用Tel路由表来转发数据set firewall filter filter-1 term default then routing-instance CNC //定义符合标记default数据使用CNC路由表来转发数据(default为自定义标记的名称,根据习惯随便取,如果没有指定符合条件则代表所有流量都匹配)set security zones security-zone trust host-inbound-traffic system-services allset security zones security-zone trust host-inbound-traffic protocols allset security zones security-zone trust interfaces ge-0/0/3.0set security zones security-zone Tel-trust host-inbound-traffic system-services allset security zones security-zone Tel-trust host-inbound-traffic protocols all set security zones security-zone Tel-trust interfaces ge-0/0/4.0set security zones security-zone CNC-trust host-inbound-traffic system-services allset security zones security-zone CNC-trust host-inbound-traffic protocols all set security zones security-zone CNC-trust interfaces ge-0/0/5.0set security zones security-zone MGT host-inbound-traffic system-services allset security zones security-zone MGT host-inbound-traffic protocols allset security zones security-zone MGT interfaces ge-0/0/6.0 //定义逻辑接口到ZONE,并开放所有的协议及服务来访问防火墙的直连接口三虚拟路由器(双线接入);需求:ZONE trust访问目标端口为22.3389.8080,走Tel;ZONE trust主机192.168.3.2的所有流量走Tel;所有未明确的指定的流量走CNC;ZONE trust主机192.168.3.5对外发布远程桌面应用Tel-trust(192.168.4.5),CNC-trust(192.168.5.5)实现从哪家运行商来的流量从哪家运行商返回;(主动发起的流量)放行ZONE trust所有主机访问外网的流量;放行所有从外网来访问内网主机192.168.3.5的远程桌面服务;实现负载冗余;配置:set interfaces ge-0/0/3 unit 0 family inet address 192.168.3.1/24set interfaces ge-0/0/4 unit 0 family inet address 192.168.4.1/24set interfaces ge-0/0/5 unit 0 family inet address 192.168.5.1/24set interfaces ge-0/0/6 unit 0 family inet address 10.10.30.189/24set routing-options interface-routes rib-group inet Big-ribset routing-options static route 10.0.0.0/8 next-hop 10.10.30.1set routing-options static route 0.0.0.0/0 next-hop 192.168.4.2set routing-options static route 0.0.0.0/0 installset routing-options static route 0.0.0.0/0 no-readvertiseset routing-options rib-groups Big-rib import-rib inet.0set routing-options rib-groups Big-rib import-rib CNC.inet.0set routing-options rib-groups Big-rib import-rib Tel.inet.0set security nat destination pool 111 address 192.168.3.5/32set security nat destination rule-set 1 from zone Tel-trustset security nat destination rule-set 1 rule 111 match source-address 0.0.0.0/0set security nat destination rule-set 1 rule 111 match destination-address 192.168.4.5/32set security nat destination rule-set 1 rule 111 match destination-port 3389set security nat destination rule-set 1 rule 111 then destination-nat pool 111set security nat destination rule-set 2 from zone CNC-trustset security nat destination rule-set 2 rule 222 match source-address 0.0.0.0/0set security nat destination rule-set 2 rule 222 match destination-address 192.168.5.5/32set security nat destination rule-set 2 rule 222 match destination-port 3389set security nat destination rule-set 2 rule 222 then destination-nat pool 111set security zones security-zone trust address-book address Net_192.168.3.0 192.168.3.0/24set security zones security-zone trust address-book address H_192.168.3.5 192.168.3.5/32set applications application tcp_3389 protocol tcpset applications application tcp_3389 destination-port 3389set security nat proxy-arp interface ge-0/0/4.0 address 192.168.4.5/32set security nat proxy-arp interface ge-0/0/5.0 address 192.168.5.5/32set security policies from-zone Tel-trust to-zone trust policy default-permit match source-address anyset security policies from-zone Tel-trust to-zone trust policy default-permit match destination-address H_192.168.3.5 set security policies from-zone Tel-trust to-zone trust policy default-permit match application tcp_3389set security policies from-zone Tel-trust to-zone trust policy default-permit then permitset security policies from-zone CNC-trust to-zone trust policy default-permit-2 match source-address anyset security policies from-zone CNC-trust to-zone trust policy default-permit-2 match destination-address H_192.168.3.5set security policies from-zone CNC-trust to-zone trust policy default-permit-2 match application tcp_3389set security policies from-zone CNC-trust to-zone trust policy default-permit-2 then permitset security policies from-zone trust to-zone Tel-trust policy 1121 match source-address Net_192.168.3.0set security policies from-zone trust to-zone Tel-trust policy 1121 match destination-address anyset security policies from-zone trust to-zone Tel-trust policy 1121 match application anyset security policies from-zone trust to-zone Tel-trust policy 1121 then permitset security policies from-zone trust to-zone CNC-trust policy 1122 match source-address Net_192.168.3.0set security policies from-zone trust to-zone CNC-trust policy 1122 match destination-address anyset security policies from-zone trust to-zone CNC-trust policy 1122 match application anyset security policies from-zone trust to-zone CNC-trust policy 1122 then permitset security zones security-zone trust host-inbound-traffic system-services allset security zones security-zone trust host-inbound-traffic protocols allset security zones security-zone trust interfaces ge-0/0/3.0set security zones security-zone Tel-trust host-inbound-traffic system-services allset security zones security-zone Tel-trust host-inbound-traffic protocols allset security zones security-zone Tel-trust interfaces ge-0/0/4.0set security zones security-zone CNC-trust host-inbound-traffic system-services allset security zones security-zone CNC-trust host-inbound-traffic protocols allset security zones security-zone CNC-trust interfaces ge-0/0/5.0set security zones security-zone MGT host-inbound-traffic system-services allset security zones security-zone MGT host-inbound-traffic protocols allset security zones security-zone MGT interfaces ge-0/0/6.0set routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.5.2 preference 100set routing-options static route 0.0.0.0/0 qualified-next-hop 192.168.4.2 preference 10set security nat source rule-set Soure-NAT-Policy from zone trustset security nat source rule-set Soure-NAT-Policy to zone Tel-trustset security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match source-address 192.168.3.0/24set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match destination-address 0.0.0.0/0set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 then source-nat interfaceset security policies from-zone trust to-zone Tel-trust policy 1 match source-address Net_192.168.3.0set security policies from-zone trust to-zone Tel-trust policy 1 match destination-address anyset security policies from-zone trust to-zone Tel-trust policy 1 match application anyset security policies from-zone trust to-zone Tel-trust policy 1 then permitset security policies from-zone trust to-zone Tel-trust policy 1 then log session-initset security policies from-zone trust to-zone Tel-trust policy 1 then log session-closeset security nat source rule-set Soure-NAT-Policy-2 from zone trustset security nat source rule-set Soure-NAT-Policy-2 to zone CNC-trustset security nat source rule-set Soure-NAT-Policy-2 rule Source-nat-2 match source-address 192.168.3.0/24set security nat source rule-set Soure-NAT-Policy-2 rule Source-nat-2 match destination-address 0.0.0.0/0set security nat source rule-set Soure-NAT-Policy-2 rule Source-nat-2 then source-nat interfaceset security policies from-zone trust to-zone CNC-trust policy 2 match source-address Net_192.168.3.0set security policies from-zone trust to-zone CNC-trust policy 2 match destination-address anyset security policies from-zone trust to-zone CNC-trust policy 2 match application anyset security policies from-zone trust to-zone CNC-trust policy 2 then permitset security policies from-zone trust to-zone CNC-trust policy 2 then log session-initset security policies from-zone trust to-zone CNC-trust policy 2 then log session-closeset interfaces ge-0/0/3 unit 0 family inet filter input filter-1set firewall filter filter-1 term term-1 from destination-port 22set firewall filter filter-1 term term-1 from destination-port 3389set firewall filter filter-1 term term-1 from destination-port 8080set firewall filter filter-1 term term-1 from source-address 192.168.3.2/32set firewall filter filter-1 term term-1 then routing-instance Telset firewall filter filter-1 term sour-add from source-address 192.168.3.2/32set firewall filter filter-1 term sour-add then routing-instance Telset firewall filter filter-1 term default from source-address 0.0.0.0/0set firewall filter filter-1 term default then routing-instance CNC验证:验证主机192.168.3.2流量Session ID: 19710, Policy name: 1121/6, Timeout: 4, ValidIn: 192.168.3.2/4101 --> 192.168.100.211/1;icmp, If: ge-0/0/3.0, Pkts: 1, Bytes: 60Out: 192.168.100.211/1 --> 192.168.4.1/1160;icmp, If: ge-0/0/4.0, Pkts: 1, Bytes: 60 Session ID: 19715, Policy name: 1121/6,。