CCNA四考试答案
- 格式:docx
- 大小:154.91 KB
- 文档页数:102
1从什么物理位置起,WAN 连接从由用户负责变为由服务提供商负责?非军事区(DMZ)分界点本地环路网云2一名技术人员正编辑ACL 115,并将其重新应用到路由器,在将ACL 重新应用到路由器时向其中添加access-list 115 permit tcp any 172.16.0.0 0.0.255.255 established命令会产生什么结果?会允许所有来自172.16.0.0/16 的流量。
会允许所有发往172.16.0.0/16 的TCP 流量。
会允许任何发送至172.16.0.0/16 的SYN 数据包。
会允许对网络172.16.0.0/16 所发出流量响应。
3请参见图示。
网络管理员对Router1 和Router2 上发出图示中的命令。
但其后在检查路由表时发现,两个路由器均不能获知相邻路由器的LAN 网络。
RIPng配置最可能发生什么问题?串行接口处于不同的子网上。
接口上未启用RIPng 进程。
Router1 和Router2 的RIPng 进程不匹配。
IPv6 RIP 配置中缺少RIPng network命令。
4参见图示。
网络管理员创建一个标准访问控制列表,以禁止从网络192.168.1.0/24 访问网络192.168.2.0/24 并允许所有网络访问Internet。
应该在哪个路由器接口和方向上应用该列表?Fa0/0 接口,入站Fa0/0 接口,出站Fa0/1 接口,入站Fa0/1 接口,出站5系统管理员必须为某个小型远程办公室中的十台主机提供Internet 连接。
ISP 已为该远程办公室分配了两个公有IP 地址。
系统管理员如何配置路由器才能让十位用户全部同时接入Internet?配置DHCP 和静态NAT。
为十名用户配置动态NAT。
为全部十名用户配置静态NAT。
配置带过载的动态NAT。
6请参见图示。
R1 针对内部网络10.1.1.0/24 执行NAT 过载。
主机A 向web 服务器发送了一个数据包。

CCNA_4_Final11下列哪种类型的网络攻击是利用被入侵的系统中的漏洞在网络中自我传播?病毒蠕虫特洛伊木马中间人2请参见图示。
有一个 FTP 请求数据包需要发往IP 地址为172.16.1.5 的 FTP 服务器。
Router1 的 S0/0/0 接口收到该请求数据包后,会以何种方式处理?路由器认定传入数据包与 access-list 201 permit ip any any 命令创建的语句匹配,从而允许数据包进入路由器。
因为 access-list 101 permit ip any any 命令没有创建任何语句,所以路由器会达到ACL 101 的尾部而找不到匹配的条件,从而丢弃该数据包。
路由器认定传入数据包与 access-list 101 permit ip any 172.16.1.0 0.0.0.255 命令创建的语句匹配,从而忽略 ACL 101 的其余的语句,允许数据包进入路由器。
路由器会认定传入数据包与命令 access-list 201 deny icmp 172.16.1.0 0.0.0.255 any 创建的语句匹配,然后继续将该数据包与 ACL 201 中剩余的语句比对,以确保后续语句均未禁止 FTP,然后路由器将丢弃该数据包。
3 管理员正在使用 RIPng 和双协议栈技术为一路由器配置 IPv6 和 IPv4,他在输入IPv4 路由时收到一条错误消息。
可能是什么原因导致出现错误消息?IPv4 与 RIPng 不兼容RIPng 与双协议栈技术不兼容。
路由器接口的地址配置错误。
在同一接口同时配置 IPv4 和 IPv6 时,所有 IPv4 地址均被禁用,以支持新的技术。
4 帧中继网络中所用的本地管理接口 (LMI) 提供哪两项功能?(选择两项。
)流量控制错误通知拥塞通知映射 DLCI 至网络地址发送 keepalive 数据包以检验 PVC 的工作情况5如果不以纯文本格式发送身份验证信息,在 Cisco 和非 Cisco 路由器之间建立链路连接时,应使用以下哪种第 2 层协议和身份验证的组合?HDLC 与 PAPHDLC 与 CHAPPPP 与 PAPPPP 与 CHAP6 服务提供商自何处开始对客户的 WAN 连接负责?本地环路路由器上的 DTE 电缆分界点非军事区7请参见图示。

计算机四级网络工程师习题库(附参考答案)一、单选题(共82题,每题1分,共82分)1.关于城域网的描述中,错误的是( )。
A、接入网是用户接入城域网主要途径B、可支持语音、视频、数据等多种业务C、通常以卫星信道作为骨干传输线路D、用于城市范围内局域网之间的互联正确答案:C2.关于CSMA/CD的描述中,正确的是( )。
A、是一种介质访问控制方法B、经常被用于无线局域网中C、发送数据前无需侦听总线D、冲突帧的重发次数无限制正确答案:A3.进程间通信时,下列哪一种情形下,发送进程不能再申请互斥锁( )。
A、已满的邮件槽B、未加锁的邮件槽C、已空的邮件槽D、半满的邮件槽正确答案:A4.下列哪一种中断与当前运行的进程有关( )。
A、故障性中断B、程序性中断C、时钟中断D、I/O正确答案:B5.关于SNMP的描述中,正确的是( )。
A、可扩展为SGMP协议B、支持轮询工作模式C、工作于网络层D、只能工作于TCP/IP环境正确答案:C6.在FTP中,有一种数据连接的建立模式,这种模式由客户机打开一个随机选择的端口,并将该端口号通过控制连接传送给服务器。
然后,服务器请求与该端口建立数据连接。
这种模式叫做( )。
A、被动模式B、随机模式C、控制模式D、主动模式正确答案:D7.关于安全管理的描述中,错误的是( )。
A、避免所有安全问题B、进行风险分析C、采用多层防卫手段D、跟踪入侵者正确答案:A8.外部设备按数据传输的方式可分为多种类型,通常键盘是哪一种类型的设备?( )A、独占设备B、块设备C、虚拟设备D、字符设备正确答案:D9.在虚拟页式系统中进行页面置换时,检查进入内存时间最久页面的 R 位,如果是 0,则置换该页;如果是 1,就将 R 位清 0,并把该页面放到链表的尾端,修改其进入时间,然后继续搜索,这一策略称为( )。
A、最近最少使用页面置换算法B、第二次机会页面置换算法C、最近最不常用页面置换算法D、先进先出页面置换算法正确答案:B10.关于网管协议的描述中,错误的是( )。
答案:1、D 2、AE 3、BC 4、E 5、B 6、D 7、AEF 8、A 9、A 10、B 11、D 12、B 13、A 14、D 15、AD 16、A 17、ABF 18、BF 19、B 20、C1收集症状以排查网络故障时,哪个步骤可能会牵涉到外部管理员?缩小范围收集可疑设备的症状分析现有症状确定所有权2逻辑网络图中一般有哪两项要素?(选择两项。
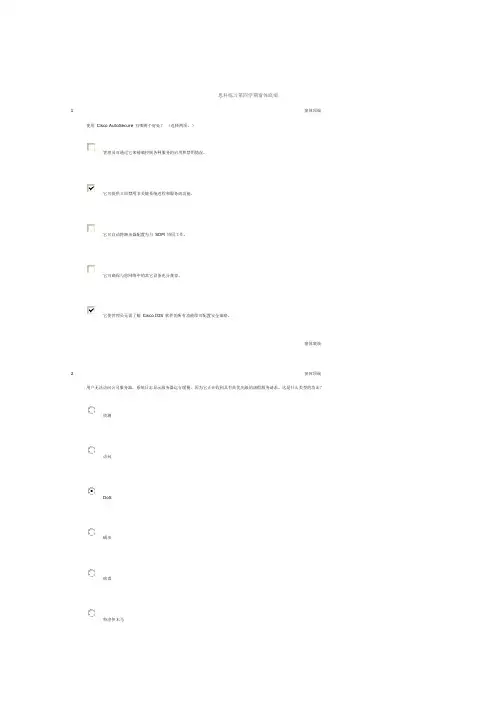
)接口标识符连接器类型操作系统版本电缆类型虚电路3请参见图示。
在创建网络文档的过程中应该进行哪两个步骤?(选择两项。
)记录仅在园区网络中发现的设备的相关信息。
记录在整个网络中(包括远程站点)发现的设备的相关信息。
将网络配置表中与拓扑图所示组件相关的任何设备信息记录下来。
仅将网络配置表中与拓扑图所示组件相关的第2 层和第3 层设备信息记录下来。
将网络配置表中与拓扑图所示组件相关的在网络使用高峰期收集的的设备信息记录下来。
4请参见图示。
图中的图表来自HR-1,它是HR 部门使用的唯一一台应用程序服务器。
基线数据收集开始于8 月1 日。
从图表中可确定什么有用信息?HR-1 上的CPU 资源失衡。
需要调整处理周期。
有两个明显的周末处理周期,它们始于周六夜晚,止于周日早上。
基线图表显示HR-1 明显具有处理问题(尽管问题本质尚不清楚)。
HR-1 上的处理负载重复再现,因此可预测。
HR-1 上的CPU 负载因某种原因受到明显影响,但由于信息不足,无法确定是否存在问题。
5请参见图示。
服务器HR 上的一个应用程序不再响应任何客户端请求。
每件事务都取决于数据中心中的多台服务器。
数据中心内的服务器上运行的为全公司提供服务的应用程序均无问题。
员工没有解决此类故障的经验,且对各种应用程序的了解也有限。
哪些初始故障排除步骤体现了自上而下的故障排除方法?检查所有服务器的电缆连接。
检查每块网卡上的连接指示灯是否为绿色。
Ping 每台服务器的本地地址,然后Ping 相关服务器和典型客户端的地址。

计算机四级网络工程师习题库(附参考答案)一、单选题(共80题,每题1分,共80分)1、下列关于生产者消费者的叙述中,哪一个是正确的( )。
A、生产者往缓冲区放产品前要先用B、生产者往缓冲区放产品前要先使用C、生产者往缓冲区放产品前要先使用D、消费者从缓冲区取产品前要先用正确答案:C2、关于XMPP的描述中,正确的是( )。
A、基于XMLB、工作于网络层C、只被微软支持D、腾讯是制定者之一正确答案:A3、关于IM系统的通信协议的描述中,正确的是( )。
A、MSN采用B、323C、QQ采用JABBERD、AOL采用OSCARE、ICQ采用SIMPLE正确答案:C4、关于数据报交换与虚电路交换的描述中,正确的是( )。
A、数据报交换的数据单元中不需要包含源节点与目的节点地址B、虚电路交换需要在源节点与目的节点之间建立一条逻辑连接C、虚电路交换的数据单元中需要包含源节点与目的节点地址D、数据报交换需要在源节点与目的节点之间建立一条物理连接正确答案:B5、关于X.800的描述中,错误的是( )。
A、包含安全服务B、支持可逆加密C、将攻击分为主动和被动攻击D、保证系统的绝对安全正确答案:D6、简单页式存储管理方案中,若地址用 m 个二进制位表示,页内地址部分占 n 个二进制位,则最大允许进程有多少个页面( )。
A、2 mB、2 (m-n)C、2 nD、2 (n-1)正确答案:B7、进程运行过程中,导致进程从运行态转换为就绪态的典型事件是( )。
A、发生了缺页中断B、时间片到C、程序出错D、访问的数据没有准备好正确答案:B8、邮件服务器之间传递邮件通常使用的协议为( )。
A、SNMPB、SMTPC、TelnetD、HTTP正确答案:B9、int main(){Printf("Hello World\n");Fork();Printf("Hello World\n");}在 UNIX 操作系统中正确编译链接后,其正确的运行结果是( )。

公司与AA2SSH存在不正确的访问控制列表条目。
访问列表中的必须在会防止以明文传输登录信息如果身份验证失败,则会断开PPP 会话连接会发起双向握手容易遭受回送攻击4命令show frame-relay map的输出如下:Serial 0 (up): ip 192.168.151.4 dlci 122, dynamic, broadcast, status defined, active 下列哪三种说法正确描述了所示内容的意义?(选择三项。
)192.168.151.4代表远程路由器的IP 地址192.168.151.4代表本地串行接口的IP 地址DLCI 122代表远程串行接口DLCI 122代表用于连接远程地址的本地编号broadcast表示动态路由协议(例如RIP v1)可通过此PVC 发送数据包active表明ARP 进程正在工作5路由器的SDM 主页会显示哪三点信息?(选择三项。
)ARP 缓存闪存的总容量和可用容量路由表已配置的LAN 接口的数量是否配置了DHCP 服务器该LAN 中路由器的数量6从非军事区分界点本地环路网云确保在确认确保路由器上有通向下列哪三种说法正确描述了CSU/DSU调制解调器用于端接本地数字环路。
CSU/DSU调制解调器用于端接本地模拟环路。
路由器通常被视为路由器通常被视为10在链路质量测试完毕后,路由器在协商第LCPNCP它会被丢弃。
它会被放到队列中,直到主机它会被转换,源端口号保持为它会被分配其端口范围内的第一个可用端口号。
交换虚电路的相关信息将DLCI 映射到网络地址提供流量控制提供错误通知提供拥塞通知发送keepalive 数据包以检验PVC 的工作情况14请参见图示。
下列说法中哪三项正确?(选择三项。
)启用了NAT 过载。
启用了动态NAT。
地址转换会失败。
接口配置不正确。
地址为192.168.1.255 的主机将被转换。
进入0/0/2 接口的流量先被转换,然后才流出串行接口0/0/0。

1 制作商务案例的目的是什么?AA.用于证明实施技术改进所需的资金投入的合理性B.用于为之前在RFP 中完成的工作提供例子。
C.用于定义网络的技术要求D.用于定义时间表和关键里程碑2 开发网络设计时,为什么必须排列业务目标的优先顺序?DA.为确保首先实现最廉价的技术B.为简化新安装网络的配置、管理和监控工作C.为预测变化和业务增长所带来的影响D.为抓住有助于业务成功的最佳机遇3 Cisco 生命周期服务的哪个阶段会执行网络基线?EA.准备阶段B.规划阶段C.设计阶段D.实施阶段E.运行阶段4 在网络管理体系结构中,哪一项是对管理代理的准确描述?DA.存储网络性能参数的标准数据库B.管理站与被管理设备之间采用的通信协议C.管理员用于监控和配置网络设备的、运行管理应用程序的主机D.在受管设备上运行的软件,用于收集网络信息并使管理站可管理该设备5 Cisco 生命周期服务的哪个阶段会采取主动管理以确认并解决问题,避免组织受到影响?FA.准备阶段B.规划阶段C.设计阶段D.实施阶段E.运行阶段F.优化阶段6 系统级验收测试的目的是什么?CA.为新设计的网络开发安装计划B.在新安装的网络上培训最终用户和支持人员C.检查新安装的网络是否符合业务目标和设计要求D.用于证明实施技术改进所需的资金投入的合理性7 在网络设计中使用自上而下的方法替代自下而上的方法有哪两项优点?(选择两项)A.DA.符合组织要求B.可快速对设计要求作出反应C.减少网络设计的前期准备时间D.从应用程序和网络解决方案的角度明确设计目标E.可根据以往经验选用设备和技术以实现设计8 下列哪项业务制约条件可能影响公司的W AN 设计?DA.公司政策中关于LAN 设备上特定操作系统的规定B.当前在用户设备上实施的监控协议C.实施过程中最终用户无法使用网络D.公司政策因合作关系而要求使用特定厂商的网络设备9 以下哪个组件安装在由SNMP 管理的网络设备上?AA.管理代理B.管理站C.网络管理协议D.管理信息库(MIB)10 SNMP 有何用途?AA.帮助在设备与NMS 之间交换信息B.监视和控制网络中的IP 地址分配C.向监控工作站报告用户登录情况D.检验网络中的流量并记录所有活动11 组织在发出征求建议书(RFP) 或征求报价书(RFQ) 前,通常完成了Cisco 生命周期服务策略的哪个阶段?AA.准备阶段B.规划阶段C.设计阶段D.实施阶段E.运行阶段F.优化阶段12 一家承包公司的网络工程师接到一个会议通知,内容是与潜在客户举行的投标前会谈。

1、如果将命令ip dhcp excluded-address 10.10.4.1 10.10.4.5添加到配置为DHCP 服务器的本地路由器配置中,结果是什么?该路由器将丢弃发往10.10.4.1 和10.10.4.5 的流量。
不会路由地址处于10.10.4.1 到10.10.4.5 之间的客户端所发出的流量。
DHCP 服务器不会分配10.10.4.1 到10.10.4.5 之间的地址。
该路由器将忽略来自地址处于10.10.4.1 到10.10.4.5 之间的DHCP 服务器的流量。
2、请参见图示。
连接到Fa0/0 的主机无法从此DHCP 服务器获取IP 地址。
debug ip dhcp server命令"DHCPD: there is no address pool for 192.168.1.1"。
问题出在哪里?DHCP 地址池中排除了地址192.168.1.1。
192Network 的地址池不正确。
网络地址池的默认路由器不正确。
地址192.168.1.1 已经用在接口Fa0/0 上。
3、请参见图示。
R1 针对内部网络10.1.1.0/24 执行NAT 过载。
主机A 向web 服务器发送了一个数据包。
务器返回的数据包的目的IP 地址是什么?10.1.1.2:1234172.30.20.1:1234172.30.20.1:3333192.168.1.2:804、请参见图示。
网络管理员对Router1 和Router2 上发出图示中的命令。
但其后在检查路由表时发现,两个路由器均不能获知相邻路由器的LAN 网络。
RIPng 配置最可能发生什么问题?串行接口处于不同的子网上。
接口上未启用RIPng 进程。
未配置RIPng 网络命令。
Router1 和Router2 的RIPng 进程不匹配。
5、请参见图示。
使用default-router和dns-server命令指定的TCP/IP 配置信息是如何获得的?TCP/IP 信息先转发至10.0.1.3,再提供给DHCP 客户端。
思科练习第四学期窗体底端1窗体顶端使用 Cisco AutoSecure 有哪两个好处?(选择两项。
)管理员可通过它来精确控制各种服务的启用和禁用情况。
它可提供立即禁用非关键系统进程和服务的功能。
它可自动将路由器配置为与 SDM 协同工作。
它可确保与您网络中的其它设备充分兼容。
它使管理员无需了解 Ci sco I OS 软件的所有功能即可配置安全策略。
窗体底端2窗体顶端用户无法访问公司服务器。
系统日志显示服务器运行缓慢,因为它正在收到具有高优先级的虚假服务请求。
这是什么类型的攻击?侦测访问DoS蠕虫病毒特洛伊木马窗体底端3窗体顶端下列哪两种说法定义了在网络中启用 DNS 服务所带来的安全风险?(选择两项。
)默认情况下,域名查询被发送到广播地址 255.255.255.255。
DNS 域名查询需要在所有路由器的以太网接口上启用ip directed-broadcast命令。
在一台路由器上使用全局配置命令ip nam e-server会在网络中的所有路由器上启用 DNS 服务。
基本 DNS 协议不提供身份验证或完整性保证。
路由器配置不提供用于设置主 DNS 服务器和备份 DNS 服务器的选项。
窗体底端4窗体顶端网络管理员在试图通过 TFTP 服务器升级 Ci sco I OS 映像前,必须检验哪两项?(选择两项。
)使用show h osts命令检验 TFTP 服务器的名称。
使用tftpdnld命令检验 TFTP 服务器是否正在运行。
使用show version命令检验映像的校验和是否有效。
使用ping命令检验路由器与 TFTP 服务器之间的连通性。
使用show fl ash命令检验闪存是否具有足够空间容纳新的 Cisco IOS 映像。
窗体底端5窗体顶端下列关于网络安全的说法中哪两项正确?(选择两项。
)保护网络免受内部威胁侵害具有较低的优先级,因为由公司员工带来的安全风险较低。
无论是能自己编写攻击代码的资深黑客,还是从 Internet 下载攻击程序的入门攻击者都可能对网络安全造成严重威胁。

窗体顶端微波接入全球互通 (WiM AX) 通信技术有哪两项特点?(选择两项。
)支持使用网状技术的市政无线网络可覆盖的面积多达 7,500 平方公里支持点对点链路,但不支持全移动蜂窝式接入通过高带宽连接直接连接到 Internet工作速度比 Wi-Fi 低,但支持的用户更多窗体底端2窗体顶端安全 VPN 有哪三项主要功能?(选择三项。
)记帐身份验证授权数据可用性数据机密性数据完整性窗体底端3窗体顶端请参见图示。
所有用户都拥有访问企业网络的合法目的和必要权限。
根据图中所示的拓扑,哪些地点可与企业网络建立 VPN 连接?地点 C、D 和 E 可支持 VPN 连接。
地点 A 和 B 需要在网络边缘另外安装 PIX 防火墙装置。
地点 C 和 E 可支持 VPN 连接。
地点 A、B 和 D 需要在网络边缘另外安装 PIX 防火墙装置。
地点 A、B、D 和 E 可支持 VPN 连接。
地点 C 需要在网络边缘另外安装路由器。
所有地点均可支持 VPN 连接。
窗体底端4窗体顶端下列关于 DSL 的说法中哪两项正确?(选择两项。
)用户连接到共享介质上使用 RF 信号传输本地环路最长可达 3.5 英里 (5.5km)物理层和数据链路层由 D OCSIS 定义用户连接通过 C O 处的 DSL AM 汇聚窗体底端5窗体顶端VPN 通过哪两种方法实现数据传输的机密性?(选择两项。
)数字证书加密封装哈希密码窗体底端6窗体顶端可使用哪三种加密协议加强 VPN 的数据传输机密性?(选择三项。
)AESDESAH哈希MPLSRSA窗体底端7窗体顶端下列哪项是对称密钥加密的例子?Diffie-Hellman数字证书预共享密钥RSA 签名窗体底端8窗体顶端技术人员应要求为远程工作人员配置宽带连接。
技术人员接到指示,连接所需的所有升级和下载工作都必须使用现有电话线路进行。
应该使用哪种宽带技术?电缆DSLISDNPOTS窗体底端9窗体顶端研究过远程工作人员常用的远程连接方式后,网络管理员决定实施宽带远程接入以通过公共 Interne t 建立 VPN 连接。

计算机四级网络工程师考试题+参考答案一、单选题(共82题,每题1分,共82分)1.关于传统Ethernet帧的数据字段的描述中,正确的是( )。
A、为高层的待发送数据B、不在帧校验的范围内C、最小长度为64字节D、最大长度为512字节正确答案:A2.假设磁头当前位于第 155 道,正在向磁道序号减少的方向移动。
现有一个磁道访问请求序列为 35,45,12,68,110,180,170,195,采用SCAN 调度(电梯调度)算法得到的磁道访问序列是()。
A、110,170,180,195,68,45,35,12B、110,68,45,35,12,170,180,195C、110,170,180,195,12,35,45,68D、12,35,45,68,110,170,180,195正确答案:B3.关于ElGamal算法的描述中,正确的是( )。
A、生成密文的长度与明文相同B、基于椭圆曲线机制C、由IETF设计D、属于对称加密正确答案:B4.关于HTTP协议的描述中,正确的是( )。
A、定义了FTP客户机与服务器之间的传输协议B、建立在传输层UDP协议的基础上C、定义了请求报文和响应报文的格式D、要求客户机和服务器使用相同的操作系统正确答案:C5.下列哪一种文件的物理结构检索速度慢,且不适于随机存取文件( )。
A、索引结构B、链接结构C、顺序结构D、I 节点结构正确答案:B6.系统调用扩充了机器指令,增强了系统功能,方便了用户使用。
下列哪一项不属于系统调用( )。
A、用户程序需要获得当前进程的属性B、将成绩填入学生成绩数据库C、读写硬盘上一个打开的文件D、请求使用光盘驱动器正确答案:B7.一个进程的内存分配页表如下,页的大小为 500B,其中,有效位为 1 表示已装入内存,W 表示可写,R 表示可读。
指令 WRITE[3,100],R1 在执行时会产生什么结果()。
页号有效位页框号存取控制0 0 5 W11 10 R2 1 30 W3 1 80 R4 0 50 RA、越界中断B、缺页中断C、写保护中断D、正常运行正确答案:C8.在一个采用三级索引结构的 UNIX 文件系统中,假设物理块大小为1KB,用 64 位表示一个物理块号。
1下列关于网络安全的说法中哪两项正确?(选择两项。
)保护网络免受内部威胁侵害具有较低的优先级,因为由公司员工带来的安全风险较低。
无论是能自己编写攻击代码的资深黑客,还是从Internet下载攻击程序的入门攻击者都可能对网络安全造成严重威胁。
假设一家公司将其web服务器部署在防火墙之外,并充分备份web服务器,则无需采取其它安全措施来保护web服务器,因为即使它被攻击了也不会造成损失。
公众认可的网络操作系统(例如UNIX)和网络协议(例如TCP/IP)可采用默认设置工作,因为它们没有内在的安全缺陷。
保护网络设备免受水电等外在因素造成的物理破坏是安全策略的必要组成部分。
Option 2 and Option 5 are correct.2下列关于网络攻击的陈述,哪两项是正确的?(选择两项。
)强网络口令可防范大多数DoS攻击。
蠕虫需要人的参与才能扩散,而病毒不需要。
侦测攻击本质上始终是电子攻击,例如ping扫描或端口扫描。
暴力攻击会尝试使用字符集组合来搜索每个可能的口令。
内部设备不应该完全信任DMZ中的设备,应该对DMZ和内部设备之间的通信进行身份验证以防范端口重定向等攻击。
Option 4 and Option 5 are correct.3用户无法访问公司服务器。
系统日志显示服务器运行缓慢,因为它正在收到具有高优先级的虚假服务请求。
这是什么类型的攻击?侦测访问DoS蠕虫病毒特洛伊木马2 points for Option 34IT主管发起了一项活动,旨在提醒用户避免打开来源可疑的电子邮件。
该IT主管意在保护用户免受哪种攻击?DoSDDoS病毒访问侦测2 points for Option 35下列关于预防网络攻击的说法中哪两项正确?(选择两项。
)现代服务器和PC操作系统具有可以信赖的默认安全设置。
入侵防御系统可以记录可疑的网络活动,但在没有用户干预的情况下无法对抗正在进行的攻击。
物理安全威胁的防范包括控制对设备控制台端口的访问、标识关键电缆、安装UPS系统以及提供温湿控制。
1.下列关于网络安全的说法中哪两项正确?(选择两项。
)25保护网络免受内部威胁侵害具有较低的优先级,因为由公司员工带来的安全风险较低。
无论是能自己编写攻击代码的资深黑客,还是从Internet 下载攻击程序的入门攻击者都可能对网络安全造成严重威胁。
假设一家公司将其web 服务器部署在防火墙之外,并充分备份web 服务器,则无需采取其它安全措施来保护web 服务器,因为即使它被攻击了也不会造成损失。
公众认可的网络操作系统(例如UNIX)和网络协议(例如TCP/IP)可采用默认设置工作,因为它们没有内在的安全缺陷。
保护网络设备免受水电等外在因素造成的物理破坏是安全策略的必要组成部分。
2.下列关于网络攻击的陈述,哪两项是正确的?(选择两项。
)45强网络口令可防范大多数DoS 攻击。
蠕虫需要人的参与才能扩散,而病毒不需要。
侦测攻击本质上始终是电子攻击,例如ping 扫描或端口扫描。
暴力攻击会尝试使用字符集组合来搜索每个可能的口令。
内部设备不应该完全信任DMZ 中的设备,应该对DMZ 和内部设备之间的通信进行身份验证以防范端口重定向等攻击。
3.用户无法访问公司服务器。
系统日志显示服务器运行缓慢,因为它正在收到具有高优先级的虚假服务请求。
这是什么类型的攻击?3侦测访问DoS蠕虫病毒特洛伊木马4.IT 主管发起了一项活动,旨在提醒用户避免打开来源可疑的电子邮件。
该IT 主管意在保护用户免受哪种攻击?3DoSDDoS病毒访问侦测5.下列关于预防网络攻击的说法中哪两项正确?(选择两项。
)35现代服务器和PC 操作系统具有可以信赖的默认安全设置。
入侵防御系统可以记录可疑的网络活动,但在没有用户干预的情况下无法对抗正在进行的攻击。
物理安全威胁的防范包括控制对设备控制台端口的访问、标识关键电缆、安装UPS 系统以及提供温湿控制。
防止网络钓鱼攻击的最好方法是采用防火墙设备。
更改默认的用户名和口令并禁用或取消不必要的服务有助于加强设备安全性。
1Refer to the exhibit. The ACL statement is the only one explicitly configured on the router. Based on this information, which twcan be drawn regarding remote access network connections? (Choose two.)SSH connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are allowed.Telnet connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are allowed.SSH connections from the 192.168.2.0/24 network to the 192.168.1.0/24 network are allowed.Telnet connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are blocked.SSH connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are blocked.Telnet connections from the 192.168.2.0/24 network to the 192.168.1.0/24 network are allowed.ObservableDescriptionMaxValueEarnedValue1correctness of responseOption 1 and Option 4 are correct.1 point for each correct option. 0 points if more options are selected than required.2***The learner response cannot be shown, as there was no answer submitted.2Which two are characteristics of ACLs? (Choose two.)Extended ACLs can filter on destination TCP and UDP ports.Standard ACLs can filter on source TCP and UDP ports.Extended ACLs can filter on source and destination IP addresses.Standard ACLs can filter on source and destination IP addresses.Standard ACLs can filter on source and destination TCP and UDP ports.Observable Description MaxValue1correctness of responseOption 1 and Option 3 are correct.1 point for each correct option.0 points if more options are selected than required.23Which zone-based policy firewall zone is system-defined and applies to traffic destined for the router or originating from the roself zonesystem zonelocal zoneinside zoneoutside zoneObservable DescriptionMax Value1 correctness of response2 points for Option 1 0 points for any other option24Refer to the exhibit. If a hacker on the outside network sends an IP packet with source address 172.30.1.50, destination addrsource port 23, and destination port 2447, what does the Cisco IOS firewall do with the packet?The packet is forwarded, and an alert is generated.The packet is forwarded, and no alert is generated.The initial packet is dropped, but subsequent packets are forwarded. The packet is dropped.ObservableDescriptionMax Value1 correctness of response2 points for Option 40 points for any other option25Which two parameters are tracked by CBAC for TCP traffic but not for UDP traffic? (Choose two.) source portprotocol IDsequence numberdestination portSYN and ACK flagsObservableDescriptionMaxValue1correctness ofresponseOption 3 and Option 5 are correct.1 point for each correct option.0 points if more options are selected thanrequired.26What is the first step in configuring a Cisco IOS zone-based policy firewall using the CLI?Create zones.Define traffic classes.Define firewall policies.Assign policy maps to zone pairs.Assign router interfaces to zones.ObservableDescriptionMaxValue1correctnessof response2 points forOption 10 points forany otheroption27Class maps identify traffic and traffic parameters for policy application based on which three criteria? (Choose three.) access groupaccess classpolicy mapprotocolinterface pairssubordinate class mapObservable DescriptionMaxValue1correctness ofresponseOption 1, Option 4, and Option 6 are correct.1 point for each correct option.0 points if more options are selected thanrequired.38Which statement describes the characteristics of packet-filtering and stateful firewalls as they relate to the OSI model?Both stateful and packet-filtering firewalls can filter at the application layer.A stateful firewall can filter application layer information, while a packet-filtering firewall cannot filter beyond the networkA packet-filtering firewall typically can filter up to the transport layer, while a stateful firewall can filter up to the session laA packet-filtering firewall uses session layer information to track the state of a connection, while a stateful firewall uses apinformation to track the state of a connection.Observable Description Max Value1 correctness of response2 points for Option 30 points for any other option29For a stateful firewall, which information is stored in the stateful session flow table?TCP control header and trailer information associated with a particular sessionTCP SYN packets and the associated return ACK packetsinside private IP address and the translated inside global IP addressoutbound and inbound access rules (ACL entries)source and destination IP addresses, and port numbers and sequencing information associated with a particular session Observable Description Max Value1 correctness of response2 points for Option 50 points for any other option210What is a limitation of using object groups within an access control entry?It is not possible to append additional objects to a preexisting object group.It is not possible to delete an object group or make an object group empty if the object group is already applied to an ACTo append additional objects to a preexisting object group that is applied to an ACE, the original object group must be re the no object group command, and then recreated and reapplied to the ACE.To append additional objects to a preexisting object group that is applied to an ACE, the access control list must be rem the no access-list command, and then reapplied.Observable Description Max Value1 correctness of response2 points for Option 20 points for any other option211When using CCP to apply an ACL, the administrator received an informational message indicating that a rule was already ass the designated interface in the designated direction. The administrator continued with the association by selecting the merge statement describes the effect of the option that was selected?Two separate access rules were applied to the interface.A new combined access rule was created using the new access rule number. Duplicate ACEs were removed.A new combined access rule was created using the new access rule number. Duplicate ACEs and overriding ACEs were allow the administrator to make adjustmentsThe existing rule was placed in a preview pane to allow the administrator to select specific ACEs to move to the new acc Observable Description Max Value1 correctness of response2 points for Option 20 points for any other option212Which statement correctly describes how an ACL can be used with the access-class command to filter vty access to a routeIt is only possible to apply a standard ACL to the vty lines.An extended ACL can be used to restrict vty access based on specific source addresses, destination addresses, and pro An extended ACL can be used to restrict vty access based on specific source and destination addresses but not on protAn extended ACL can be used to restrict vty access based on specific source addresses and protocol but the destination specify the keyword any.Observable Description Max Value1 correctness of response2 points for Option 40 points for any other option213To facilitate the troubleshooting process, which inbound ICMP message should be permitted on an outside interface?echo requestecho replytime-stamp requesttime-stamp replyrouter advertisementObservable Description Max Value1 correctness of response2 points for Option 20 points for any other option214Which command is used to activate an IPv6 ACL named ENG_ACL on an interface so that the router filters traffic prior to acc routing table?access-group ipv6_ENG_ACL inaccess-group ipv6_ENG_ACL outipv6 access-class ENG_ACL inipv6 access-class ENG_ACL outipv6 traffic-filter ENG_ACL inipv6 traffic-filter ENG_ACL outObservable Description Max Value1 correctness of response2 points for Option 50 points for any other option215Which statement describes a typical security policy for a DMZ firewall configuration?Traffic that originates from the outside interface is permitted to traverse the firewall to the inside interface with little or no Traffic that originates from the DMZ interface is permitted to traverse the firewall to the outside interface with little or no r Traffic that originates from the inside interface is generally blocked entirely or very selectively permitted to the outside inReturn traffic from the outside that is associated with traffic originating from the inside is permitted to traverse from the ou to the DMZ interface.Return traffic from the inside that is associated with traffic originating from the outside is permitted to traverse from the in to the outside interface.Observable Description Max Value1 correctness of response2 points for Option 2 20 points for any other option16When configuring a Cisco IOS zone-based policy firewall, which two actions can be applied to a traffic class? (Choose two.)logholddropinspect copyforwardObservableDescriptionMax Value1correctness of responseOption 3 and Option 4 are correct.1 point for each correct option.0 points if more options are selected than required.217Refer to the exhibit. Which statement describes the function of the ACEs?These ACEs allow for IPv6 neighbor discovery traffic.These ACEs must be manually added to the end of every IPv6 ACL to allow IPv6 routing to occur.These ACEs automatically appear at the end of every IPv6 ACL to allow IPv6 routing to occur. These are optional ACEs that can be added to the end of an IPv6 ACL to allow ICMP messages that are defined in obje named nd-na and nd-ns .Observable Description Max Value1 correctness of response2 points for Option 10 points for any other option218When implementing an inbound Internet traffic ACL, what should be included to prevent the spoofing of internal networks?ACEs to prevent HTTP trafficACEs to prevent ICMP trafficACEs to prevent SNMP trafficACEs to prevent broadcast address trafficACEs to prevent traffic from private address spacesObservable Description Max Value1 correctness of response2 points for Option 50 points for any other option219Which statement describes one of the rules governing interface behavior in the context of implementing a zone-based policy configuration?An administrator can assign an interface to multiple security zones.An administrator can assign interfaces to zones, regardless of whether the zone has been configured.By default, traffic is allowed to flow among interfaces that are members of the same zone.By default, traffic is allowed to flow between a zone member interface and any interface that is not a zone member.Observable Description Max Value1 correctness of response2 points for Option 30 points for any other option220Refer to the exhibit. Which statement is true about the effect of this Cisco IOS zone-based policy firewall configuration?The firewall will automatically drop all HTTP, HTTPS, and FTP traffic.The firewall will automatically allow HTTP, HTTPS, and FTP traffic from s0/0 to fa0/0 and will track the connections. Trac connection allows only return traffic to be permitted through the firewall in the opposite direction.The firewall will automatically allow HTTP, HTTPS, and FTP traffic from fa0/0 to s0/0 and will track the connections. Trac connection allows only return traffic to be permitted through the firewall in the opposite direction.The firewall will automatically allow HTTP, HTTPS, and FTP traffic from fa0/0 to s0/0, but will not track the state of conne corresponding policy must be applied to allow return traffic to be permitted through the firewall in the opposite direction.The firewall will automatically allow HTTP, HTTPS, and FTP traffic from s0/0 to fa0/0, but will not track the state of conne corresponding policy must be applied to allow return traffic to be permitted through the firewall in the opposite direction.Observable Description Max Value1 correctness of response2 points for Option 30 points for any other option2。
1. What functionality do access control lists provide in the implementation of dynamic NAT on a Cisco router?define which addresses can be translateddefine which addresses are assigned to a NAT pooldefine which addresses are allowed out the routerdefine which addresses can be accessed from the inside network2. Which three guidelines would help contribute to creating a strong password policy? (Choose three.)Once a good password is created, do not change it.Deliberately misspell words when creating passwords.Create passwords that are at least 8 characters in length.Use combinations of upper case, lower case, and special characters.3.Refer to the exhibit. Every time the administrator reboots this router, the boot process ends in setup mode. What is a possible problem?There is insufficient RAM for the IOS to load on this router.A password recovery process should be done on this router.The bootstrap version and the version of the IOS are different.The IOS image is damaged and must be reloaded using tftpdnld.The configuration register is set to ignore the startup configuration.4. Which option correctly defines the capacity through the local loop guaranteed to a customer by the service provider?BEDECIRCBIR5.Refer to the exhibit. A host connected to Fa0/0 is unable to acquire an IP address from the DHCP server. The output of the debug ip dhcp server command shows "DHCPD: there is no address pool for 10.1.1.1". What is the problem?The 10.1.1.1 address is already configured on Fa0/0.The default router for the 10Network pool is incorrect.The ip helper-address must be added to Fa0/0 interface.The pool of addresses for the 10Network pool is incorrect.6. Which data link layer encapsulation protocol is used by default for serial connections between two Cisco routers?ATMFrame RelayHDLCPPPSDLCRefer to the exhibit. Which statement correctly describes how Router1 processes an FTP request that enters interface s0/0/0 and is destined for an FTP server at IP address 192.168.1.5?The router matches the incoming packet to the statement that was created by the access-list 201 deny icmp 192.168.1.0 0.0.0.255 any command, continues comparing the packet to the remaining statements in ACL 201 to ensure that no subsequent statements allow FTP, and then the router drops the packet.The router reaches the end of ACL 101 without matching a condition and drops the packet because there is no statement that was created by the access-list 101 permit ip any any command.The router matches the incoming packet to the statement that was created by the access-list 101 permit ip any 192.168.1.0 0.0.0.255 command and allows the packet into the router.It matches the incoming packet to the statement that was created by the access-list 201 permit ip any any command and allows the packet into the router.8. Compared with IDS systems, what can IPS systems do to provide further protection of computer systems?detect potential attacksstop the detected attack from executingupdate OS patches for computer systemsscan computer systems for viruses and spyware9. Which IEEE 802.16 broadband wireless technology allows users to connect to the ISP at speeds comparable to DSL and cable?Wi-FisatelliteWiMAXMetro Ethernet10. A network administrator has changed the VLAN configurations on his network switches over the past weekend. How can the administrator determine if the additions and changes improved performance and availability on the company intranet?Conduct a performance test and compare with the baseline that was established previously.Interview departmental secretaries and determine if they think load time for web pages has improved.Determine performance on the intranet by monitoring load times of company web pages from remote sites.Compare the hit counts on the company web server for the current week to the values that were recorded in previous weeks.11.Refer to the exhibit. What is the meaning of the term dynamic in the output of the command?The bandwidth capability of the interface increases and decreases automatically based on BECNs.The Serial0/0/1 interface acquired 172.16.3.1 from a DHCP server.The mapping between DLCI 100 and 172.16.3.1 was learned through Inverse ARP.DLCI 100 will automatically adapt to changes in the Frame Relay cloud.12. Which type of ACL will permit traffic inbound into a private network only if an outbound session has already been established between the source and destination?extendedreflexivestandardtime-based13. Which two statements are true about IPv6 link local addresses? (Choose two.)They begin with the 2000::/3 prefix.They begin with the FE80::/10 prefix.They are assigned by IANA to an organization.They must be manually configured by the administrator.They are assigned to a host by a stateless autoconfiguration process.14. A company is looking for a WAN solution to connect its headquarters site to four remote sites. What are two advantages that dedicated leased lines provide compared to a shared Frame Relay solution? (Choose two.)reduced jitterreduced costsreduced latencythe ability to burst above guaranteed bandwidththe ability to borrow unused bandwidth from the leased lines of other customers15.Refer to the exhibit. A network administrator is trying to connect R1 remotely to make configuration changes. Based on the exhibited command output, what will be the result when attempting to connect to R1?failure to connect due to Telnet not being enabledfailure to connect due to incomplete configuration for Telneta successful connection and ability to make configuration changesa successful connection but inability to make configuration changes because of the absence of an enable secret password16. What are two effective measures for securing routers? (Choose two.)Protect all active router interfaces by configuring them as passive interfaces.Configure remote administration through VTY lines for Telnet access. Use quotes or phrases to create pass phrases.Disable the HTTP server service.Enable SNMP traps.17. An issue of response time has recently arisen on an application server. The new release of a software package has also been installed on the server. The configuration of the network has changed recently. To identify the problem, individuals from both teams responsible for the recent changes begin to investigate the source of the problem. Which statement applies to this situation?Scheduling will be easy if the network and software teams work independently.It will be difficult to isolate the problem if two teams are implementing changes independently.Results from changes will be easier to reconcile and document if each team works in isolation.Only results from the software package should be tested as the network is designed to accommodate the proposed software platform.Refer to the exhibit. From the output of the show interfaces and ping commands, at which layer of the OSI model is a fault indicated?applicationtransportnetworkdata linkphysical19. Which technology is used to dynamically map next hop, network layer addresses to virtual circuits in a Frame Relay network?Inverse ARPLMIDLCI20. An administrator learns of an e-mail that has been received by a number of users in the company. This e-mail appears to come from the office of the administrator. The e-mail asks the users to confirm their account and password information. Which type of security threat does this e-mail represent?crackingphishingphreakingspamming21.Refer to the exhibit. Which data transmission technology is being represented?TDMPPPHDLCSLIP22.Refer to the exhibit. Results of the show vlan and show vtp status commands for switches S1 and S2 are displayed in the exhibit. VLAN 11 was created on S1. Why is VLAN 11 missing from S2?There is a Layer 2 loop.The VTP domain names do not match.Only one switch can be in server mode.S2 has a higher spanning-tree priority for VLAN 11 than S1 does.23. What is the result of adding the global command servicepassword-encryption to the configuration of a router?Line passwords are encrypted with type 7 encryption.Enable passwords are encrypted with type 5 encryption.All services must provide an encrypted password to function.Only encrypted messages are allowed for router communication.24. While troubleshooting a problem with an e-mail server, an administrator observes that the switch port used by the server shows "up, line protocol up". The administrator cannot ping the server. At which layer of the OSI model is the problem most likely to be found?application layernetwork layerdata link layerphysical layer25. Where does a service provider assume responsibility from a customer for a WAN connection?local loopDTE cable on routerdemarcation pointdemilitarized zone26. What will be the result of adding the command ip dhcp excluded-address 192.168.24.1 192.168.24.5to the configuration of a local router that has been configured as a DHCP server?Traffic that is destined for 192.168.24.1 and 192.168.24.5 will be dropped by the router.Traffic will not be routed from clients with addresses between192.168.24.1 and 192.168.24.5.The DHCP server will not issue the addresses ranging from 192.168.24.1 to 192.168.24.5.The router will ignore all traffic that comes from the DHCP servers with addresses 192.168.24.1 and 192.168.24.5.27.Refer to the exhibit. Partial results of the show access-lists and show ip interface FastEthernet 0/1 commands for router Router1 are shown. There are no other ACLs in effect. Host A is unable to telnet to host B. Which action will correct the problem but still restrict other traffic between the two networks?Apply the ACL in the inbound direction.Apply the ACL on the FastEthernet 0/0 interface.Reverse the order of the TCP protocol statements in the ACL.Modify the second entry in the list to permit tcp host 172.16.10.10 any eq telnet .28.Refer to the exhibit. The corporate network that is shown has been assigned network 172.16.128.0/19 for use at branch office LANs. If VLSM is used, what mask should be used for addressing hosts at Branch4 with minimal waste from unused addresses?/19/20/21/22/23/2429.Refer to the exhibit. RIPv2 has been configured on all routers in the network. Routers R1 and R3 have not received any RIP routing updates. What will fix the issue?Enable RIP authentication on R2.Issue the ip directed-broadcast command on R2.Change the subnet masks to 10.11.12.0/8 and 172.16.40.0/16 on R2.Enable CDP on R2 so that the other routers will receive routing updates.30.Refer to the exhibit. This serial interface is not functioning correctly. Based on the output shown, what is the most likely cause?improper LMI typeinterface resetPPP negotiation failureunplugged cable31. Which statement is true about PAP in the authentication of a PPP session?PAP uses a two-way handshake.The password is unique and random.PAP conducts periodic password challenges.PAP uses MD5 hashing to keep the password secure.32. An administrator is configuring a dual stack router with IPv6 and IPv4 using RIPng. The administrator receives an error message when trying to enter the IPv4 routes into RIPng. What is the cause of the problem?When IPv4 and IPv6 are configured on the same interface, all IPv4 addresses are over-written in favor of the newer technology.Incorrect IPv4 addresses are entered on the router interfaces.RIPng is incompatible with dual-stack technology.IPv4 is incompatible with RIPng.33. What is tunneling?using digital certificates to ensure that data endpoints are authentic creating a hash to ensure the integrity of data as it traverses a networkusing alternate paths to avoid access control lists and bypass security measuresencapsulating an entire packet within another packet for transmission over a network34. Which statement is true about NCP?Link termination is the responsibility of NCP.Each network protocol has a corresponding NCP.NCP establishes the initial link between PPP devices.NCP tests the link to ensure that the link quality is sufficient. 35.Refer to the exhibit. A network administrator is creating a prototype to verify the new WAN design. However, the communication between the two routers cannot be established. Based on the output of the commands, what can be done to solve the problem?Replace the serial cable .Replace the WIC on RA.Configure RA with a clock rate command.Issue a no shutdown interface command on RB.36.Refer to the exhibit. Based on the output as shown, which two statements correctly define how the router will treat Telnet traffic that comes into interface FastEthernet 0/1? (Choose two).Telnet to 172.16.10.0/24 is denied.Telnet to 172.16.20.0/24 is denied.Telnet to 172.16.0.0/24 is permitted.Telnet to 172.16.10.0/24 is permitted.Telnet to 172.16.20.0/24 is permitted.37. Which Frame Relay flow control mechanism is used to signal routers that they should reduce the flow rate of frames?DEBECIRFECNCBIR38.Refer to the exhibit. A network administrator configures a standard access control list on Router1 to prohibit traffic from the 192.168.0.0/24 network from reaching the Internet. The access control list also permits traffic from the 192.168.0.0/24 network to reach the 192.168.1.0/24 network. On which interface and in which direction should the access control list be applied?interface Fa0/0, inboundinterface Fa0/0, outboundinterface S0/0/0, inboundinterface S0/0/0, outbound39. Which configuration on the vty lines provides the best security measure for network administrators to remotely access the core routers at headquarters?Answer: 3nd option 40.Refer to the exhibit. What can be concluded from the exhibited output of the debug ip nat command?The 10.1.1.225 host is exchanging packets with the 192.168.0.10 host.The native 10.1.200.254 address is being translated to 192.168.0.10.The 192.168.0.0/24 network is the inside network.Port address translation is in effect.41. A network administrator is instructing a technician on best practices for applying ACLs. Which suggestion should the administrator provide?Named ACLs are less efficient than numbered ACLs.Standard ACLs should be applied closest to the core layer.ACLs applied to outbound interfaces are the most efficient.Extended ACLs should be applied closest to the source that is specified by the ACL.42.Refer to the exhibit. Headquarters is connected through the Internet to branch office A and branch office B. Which WAN technology would be best suited to provide secure connectivity between headquarters and both branch offices?ATMVPNISDNFrame Relaybroadband DSL43. Which three physical network problems should be checked when a bottom-up troubleshooting approach has been chosen to troubleshoot network performance? (Choose three.)cable connectivityhigh collision countsSTP failures and loopsaddress mapping errorshigh CPU utilization ratesexcess packets that are filtered by the firewall44.Refer to the exhibit. A network administrator is attempting to configure a Frame Relay network. The administrator enters the commands as shown in the exhibit on R2, but the Frame Relay PVCs are inactive. What is the problem?The incorrect DLCI numbers are being configured on R2.The S0/0/0 interface on R2 needs to be point-to-point.The frame-relay map commands are missing the cisco keyword at the end.A single router interface cannot connect to more than one Frame Relay peer at a time.45. Which IP address and wildcard mask would be used in an ACL to block traffic from all hosts on the same subnet as host 192.168.16.43/28?access-list 10 deny 192.168.16.0 0.0.0.31access-list 10 deny 192.168.16.16 0.0.0.31access-list 10 deny 192.168.16.32 0.0.0.16access-list 10 deny 192.168.16.32 0.0.0.15access-list 10 deny 192.168.16.43 0.0.0.1646. Which combination of Layer 2 protocol and authentication should be used to establish a link without sending authentication information in plain text between a Cisco and a non-Cisco router?PPP with PAPPPP with CHAPHDLC with PAPHDLC with CHAP47. When would the multipoint keyword be used in Frame Relay PVCs configuration?when global DLCIs are in usewhen using physical interfaceswhen multicasts must be supportedwhen participating routers are in the same subnet48. A network technician analyzes the network and notices late collisions. The collisions occur accompanied by jabber that originates from the server. What is the likely cause of the problem?faulty switch portweb server CPU overloadfaulty NIC in the web servermisconfiguration of web server services49.Refer to the exhibit. R1 is performing NAT overload for the 10.1.1.0/24 inside network. Host A has sent a packet to the web server. What is the destination IP address of the return packet from the web server?10.1.1.2:1234172.30.20.1:1234172.30.20.1:3333192.168.1.2:8050.Refer to the exhibit. All devices are configured as shown in the exhibit. PC1 is unable to ping the default gateway. What is the cause of the problem?The default gateway is in the wrong subnet.STP has blocked the port that PC1 is connected to.Port Fa0/2 on S2 is assigned to the wrong VLAN.S2 has the wrong IP address assigned to the VLAN30 interface.51. When Frame Relay encapsulation is used, what feature provides flow control and exchanges information about the status of virtual circuits?LCPLMIDLCIInverse ARP52. A network administrator is tasked with maintaining two remote locations in the same city. Both locations use the same service provider and have the same service plan for DSL service. When comparing download rates, it is noticed that the location on the East side of town has a faster download rate than the location on the West side of town. How can this be explained?The West side has a high volume of POTS traffic.The West side of town is downloading larger packets.The service provider is closer to the location on the East side.More clients share a connection to the DSLAM on the West side.。
下列哪项最准确地描述了采用帧中继与采用租用线路或 ISDN 服务相比的优势?客户可以更精确地定义其虚电路需求,且带宽需求之间的差别可低至 64 kbps。
客户只需支付包含本地环路和网络链路的端对端连接的费用。
客户只需支付本地环路以及网络提供商所提供的带宽的费用。
连接新站点时,所需的新电路安装成本要低于 ISDN 拨号的成本或因租用服务而添加额外硬件的成本。
帧中继技术使用哪两种方法处理包含错误的帧?(选择两项。
)帧中继服务依靠上层协议来处理错误恢复工作。
它要求接收设备请求发送方重新传输错误帧。
设置帧中的 FECN、BECN 和 DE 位以尽量减少错误。
接收设备会丢弃所有包含错误的帧而不会通知发送方。
帧中继交换机会通知发送方检测到了错误。
哪种说法是对数据链路连接标识符 (DLCI) 的最佳描述?用于标识通过帧中继网络连接的目的路由器的本地地址用于标识虚电路的具有本地意义的地址用于标识路由器和帧中继交换机之间的接口的逻辑地址用于标识 DCE 的逻辑地址在帧中继网络两个 DTE 之间创建的是什么?ISDN 电路有限访问电路交换并行电路虚电路在帧中继网络中,下列哪两项使路由器可将数据链路层地址映射到网络层地址?(选择两项。
)ARP在线代理|网页代理|代理网页|RARP代理ARP逆向ARPLMI 状态消息ICMP请参见图示。
从路由器 Peanut 向地址 192.168.50.10 发出了一次 ping 命令。
发送该 ping 命令时将使用什么 DLCI?110115220225请参见图示。
子接口 S0/0.110 上的点对点配置对路由器的运作有什么影响?它有助于节约 IP 地址。
在线代理|网页代理|代理网页|它与多个物理接口建立多个 PVC 连接。
它既消除了水平分割问题,又不增大出现路由环路的可能性。
它需要在子接口上配置encapsulation命令。
当帧中继交换机检测到队列中含有过多待处理帧时,会进行哪三项操作?(选择三项。