浙大研究生 2015-2016学年《计算机理论》期末考试英文版
- 格式:pdf
- 大小:54.01 KB
- 文档页数:5

2015年研究生考试英语一试题(word版)2015年全国硕士研究生入学考试英语(课程)一试题Section I Use of EnglishDirections:Read the following text. Choose the best word(s) for each numbered blank and mark A, B, C or D on ANSWER SHEET 1. (10 points)We have more genes in common with people we pick to be our friends than with strangers.Though not biologically related, friends are as "related" as fourth cousins, sharing about 1% of genes. That is 1 a study publishedfrom the University of California and Yale University in theProceedings of the National Academy of Sciences, has 2 .The study is a genome-wide analysis conducted 3 1932 unique subjects which 4pairs of unrelated friends and unrelated strangers. The same people were used in both 5.While 1% may seem 6 , it is not so to a geneticist. As co-author of the study James Fowler, professor of medical genetics at UC San Diego says, "Most people do not even 7their fourth cousins but somehow manage to select as friends the people who 8 our kin."The team 9 developed a "friendship score" which can predict who will be your friend based on their genes.Directions:Read the following four texts. Answer the questions below each text by choosing A, B, C or D. Mark your answers on ANSWER SHEET 1. (40 points)Text1King JuanCarlos of Spain once insited” kings don’t abdicate, they die in their sleep.” But embarrassing scandals and the popularity of the republican left in the recenet Euro-elections have forced him to eat his words and stand down. So does the Spanish crisis suggestthat monarchy is seeing its last days? Does that mean the writing is on the wall for all European royals, withtheir magnificent uniforms andmajestic lifestyles?The Spanish case provides arguments both for and against monarchy. When public opinion is particularly polarized, as it was following the end of the Franco regime, monarchs can rise above” mere”politics and “embody” a spirit of national unity.Itis this apparenttranscendence of politics that explains monarchs continuing popularity as heads of state. And so, the Middle East excepted, Europe is the mostmonarch- infested region in the world, with 10 kingdoms (not counting Vatican City and Andorra).But unlike their absolutist counterpartsin the Gulf and Asia, most royal families have survived because they allow voters to avoid the difficult searchfor anon-controversial but respected public figure.Even so, kings and queens undoubtedly have a downside. Symbolic of national unity as they claim to be, their very history-and sometimes the way they behave today-embodies outdated and indefensible privileges and inequalities. At a time when Thomas Piketty and other economists are warming of rising inequality and the increasing power of inherited wealth,it is bizarre that wealthy aristocratic families should still be the symbolic heart of modern democratic states.The most successful monarchies strive to abandon or hide their old aristocratic ways. Princes and princesses have day-jobs and ride bicycles, not horses(or helicopters). Even so, these are wealthy families who party with the international 1%, and media intrusiveness makes it increasingly difficult to maintain the right image.While Europe’s monarchies will no doubt be smart enough to survive for some time to come, it is the British royals who have most to fear from the Spanish example.It is only the Queen who has preserved the monarchy’s reputation with her rather ordinary (if well-heeled) granny style.The danger will come with Charles. Who has both an expensive taste of lifestyle and a pretty hierarchical view of theworld. He has failed to understand that monarchies have largely survived because they provide a service- asnon-controversial and non-political heads of state. Charles ought to know that as English history shows, it is kings, not republicans, who are the monarchy’s worst enemies.21.According to the first two paragraphs, King Juan Carlos of Spain[A] used to enjoy high public support[B] was unpopular among European royals[C] eased his relationship with his rivals[D] ended his reign in embarrassment22.Monarchs are kept as heads of state in Europe mostly[A] owing to their undoubted and respectable status[B] to achieve a balance between tradition and reality[C] to give voters more public figures to look up to[D] due to their everlasting political embodiment23.Which of the following is shown to be odd, according to Paragraph 4?[A] Aristocrats’ excessive reliance on inherited wealth[B] The role of the nobility in modern democracies[C] The simple lifestyle of the aristocratic families[D] The nobility’s adherence to their privileges24. The British royals ”have most of fear” because Charles[A] takes a tough line on political issues[B] fails to change his lifestyle as advised[C] takes republicans as his potential allies[D] fails to adapt himself to his future role25.Which of the following is the best title of the text?[A] Carlos, Glory and Disgrace Combined[B] Charles, Anxious to Succeed to the Throne[C] Carlos, a Lesson for All European Monarchs[D] Charles, Slow to React to the Coming Threats.Text2JUST HOW much does the Constitution protect your digital data? The Supreme Court is only just coming to grips with that question. On Tuesday,it will consider whether police can search the contents of a mobile phonewithout a warrant if the phone is on or around a person during an arrest.California has asked the justices to refrain from a sweeping ruling, particularly one that upsets the old assumption that authorities may search through the effects of suspects at the time of their arrest. Even if the justices are tempted, the state argues, it is hard for judges to assess the implications of new and rapidly changing technologies.The court would be recklessly modest if it followed California’s advice. Enough of the implications are discernable, even obvious, that the justices can and should provide updated guidelines to police, lawyers and defendants.They should start by discarding California’s lame argument that exploring the contents of a smartphone — a vast storehouse of digital information — is similar to, say, rifling through a suspect’s purse. The court has ruled that police don’t violate the Fourth Amendment when they sift through the wallet or pocketbook of an arrestee without a warrant.But exploring one’s smartphone is more like entering his or her home.A smartphone may contain an arrestee’s reading history, financial history, medical history and comprehensive records of recent correspondence. The development of “cloud computing,” meanwhile, means that police officers could conceivably access even more information with a few swipes on a touchscreen.Americans should take steps to protect their digital privacy. But keeping sensitive information on these devices is increasingly a requirement of normal life. Citizens still have a right to expect private documents to remain private and protected by the Constitution’s prohibition on unreasonable searches.As so often is the case, stating that principle doesn’t ease the challenge of line-drawing. In many cases, it would not be overly onerous for authorities to obtain a warrant to search through phone contents. They could still trump Fourth Amendment protections when facing severe, exigent circumstances, such as the threat of immediate harm, and they could take reasonable measures to ensure that phone data are not erased or altered while a warrant is pending. The court, though, may want to allow room for police to cite situations where they are entitled to more leeway.But the justices should not swallow California’s argument whole. New, disruptive technology sometimes demands novel applications of the Constitution’s protections. Orin Kerr, a law professor who blogs on The Post’s Volokh Conspiracy,comparesthe explosion and accessibility of digital information in the 21st century with the establishment of automobile use as a virtual necessity of life in the 20th: The justices had to specify novel rules for the new personal domain of the passenger car then; they must sort out how the Fourth Amendment applies to digital information now.26. The Supreme court, will work out whether, during an arrest, it is legitimate to[A] search for suspects’ mobile phones without a warrant.[B] check suspects’ phone contents without being authorized.[C] prevent suspects from deleting their phone contents.[D] prohibit suspects from using their mobile phones.27. The author’s attitude toward California’s argument is one of[A] tolerance.[B] indifference.[C] disapproval.[D] cautiousness.28. The author believes that exploring one’s phone content is comparable to[A] getting into one’s residence.[B] handing one’s historical records.[C] scanning one’s correspondences.[D] going through one’s wallet.29. In Paragraph 5 and 6, the author shows his concern that[A] principles are hard to be clearly expressed.[B] the court is giving police less room for action.[C] phones are used to store sensitive information.[D] citizens’ privacy is not effective protected.30.Orin Kerr’s comparison is quoted to indicate that(A)the Constitution should be implemented flexibly.(B)New technology requires reinterpretation of the Constitution.(C)California’s argument violates principles of the Constitution.(D)Principles of the Constitution should never be altered.Text3The journal Science is adding an extra round of statistical checks to its peer-review process, editor-in-chief Marcia McNutt announced today. The policy follows similar efforts from other journals, after widespread concern that basic mistakes in data analysis are contributing to the irreproducibility of many published research findings.“Readers must have confidence in the conclusions published in our journal,” writes McNutt in an editorial. Working with the American Statistical Association, the journal has appointed seven experts to a statistics board of reviewing editors (SBoRE). Manuscript will be flaggedup for additional scrutiny by the journal’s internal editors, or by its existing Board of Reviewing Editors or by outside peer reviewers. The SBoRE panel will then find external statisticians to review these manuscripts.Asked whether any particular papers had impelled the change, McNutt said: “The creation of the ‘statistics board’ was motivated by concerns broadly with the application of statistics and data analysis in scientific research and is part of Science’s overall drive to increase reproducibility in the research we publish.”Giovanni Parmigiani, a biostatistician at the Harvard School of Public Health, a member of the SBoRE group, says he expects the board to “play primarily an advisory role.” He agreed to join because he “found the foresight behind the establishment of the SBoRE to be novel, unique and likely to have a lasting impact. This impact will not only be through the publications in Science itself, but hopefully through a larger group of publishing places that may want to model their approach after Science.”31.According to Nancy Koehn,office language has become[A]more emotional[B]more object[C]less energetic[D]less stratcgic32.”Team”oriented corporate vocabulary is closely related to[A]historical incidents[B]gender difference[C]sport culture[D]athletic executives33.Khurana believes that the importation of terminology to[A]revive historical terms[B]promote company image[C]foster corporate cooperation[D]strengthen cmployee loyalty34.It can bo inferred that Lean In .[A]voices for working women[B]appeals to passionate workholics[C]triggers debates among mommies[D]parises motivated employees35.Which of the following statements is true about office speak?[A]Managers admire it avoid it[B] Linguists believe it to be nonsense[C]Companies find it to be fundamental[D]Regular people mock it but accept itText4Two years ago, Rupert Murdoch’s daughter, Elisabeth, spoke of the “unsettling dearth of integrity across so many of our institutions”. Integrity had collapsed, she argued, because of a collective acceptance that the only “sorting mechanism” in society should be profit and the market. But “it’s us, human beings, we the people who create the society we want, not profit”.Driving her point home, she continued: “It’s increasingly apparent that the absence of purpose, of a moral language within government, media or business could become one of the most dangerous goals for capitalism and freedom.” This same absence of moral purpose was wounding companies such as News International, she thought, making it more likely that it would lose its way as it had with widespread illegal telephone hacking.As the hacking trial concludes—finding guilty one ex-editor of the News of the World, Andy Coulson, for conspiring to hack phones, and finding his predecessor, Rebekah Brooks, innocent of the same charge—the wider issue of dearth of integrity still stands. Journalists are known to have hacked the phones of up to 5,500 people. This is hacking on an industrial scale, as was acknowledged by Glenn Mulcaire, the man hired by the News of the World in 2001 to be the point person for phone hacking. Others await trial. This saga still unfolds.In many respects, the dearth of moral purpose frames not only the fact of such widespread phone hacking but the terms on which the trial took place. One of the astonishing revelations was how little Rebekah Brooks knew of what went on in her newsroom, how little she thought to ask andthe fact that she never inquired how the stories arrived. The core of her successful defence was that she knew nothing.In today’s world, it has become normal that well-paid executives should not be accountable for what happens in the organisations that they run. Perhaps we should not be so surprised. For a generation, the collective doctrine has been that the sorting mechanism of society should be profit. The words that have mattered are efficiency, flexibility, shareholder value, business-friendly, wealth generation, sales, impact and, in newspapers, circulation. Words degraded to the margin have been justice, fairness, tolerance, proportionality and accountability.The purpose of editing the News of the World was not to promote reader understanding, to be fair in what was written or to betray any common humanity. It was to ruin lives in the quest for circulation and impact. Ms Brooks may or may not have had suspicions about how her journalists got their stories, but she asked no questions, gave no instructions—nor received traceable, recorded answers.36. Accordign to the first two paragraphs, Elisabeth was upset by(A) the consequences of the current sorting mechanism.(B) companies’ financial loss due to immoral practices(C) governmental ineffectiveness on moral issues.(D) the wide misuse of integrity among institutions.37. It can be inferred from Paragraph 3 that(A) Glenn Mulcaire may deny phone hacking as a crime.(B) more journalists may be found guilty of phone hacking.(C) Andy Coulson should be held innocent of the charge.(D) phone hacking will be accepted on certain occasions.38. The author believes that Rebekah Brooks’s defence(A) revealed a cunning personality.(B) centered on trivial issues.(C) was hardly convincing.(D) was part of a conspiracy.39. The author holds that the current collective doctrine shows(A) generally distorted values.(B) unfair wealth distribution.(C) a marginalized lifestyle.(D) a rigid moral code.40 Which of the following is suggested in the last paragraph?(A) The quality of writings is of primary importance.(B) Common humanity is central to news reporting.(C) Moral awareness matters in editing a newspaper.(D) Journalists need stricter industrial regulations.Part BHow does your reading proceed? Clearly you try to comprehend, in the sense of identifying meanings for individual words and working out relationships between them, drawing on your implicit knowledge of English grammar. (41)_____________________________________You begin to infer a context for the text, for instance by making decisions about what kind of speech event is involved: who is making the utterance, to whom, when and where.The ways of reading indicated here are without doubt kinds of comprehension. But they show comprehension to consist not just of passive assimilation but of active engagement in inference and problem-solving. You infer information you feel the writer has invited you to grasp by presenting you with specific evidence and clues;(42)_________________________________Conceived in this way, comprehension will not follow exactly the same track for each reader. What is in question is not the retrieval of an absolute, fixed or ‘true’ meaning that can be read off and checked for accuracy, or some timeless relation of the text to the world.(43)_________________________________________Such background material inevitably reflects who we are.(44)____________________________ This doesn’t, however, make interpretation merely relative or even pointless. Precisely because readers from different historical periods. Place and social experiences produce different but overlapping readings of the same words on the page —including for texts that engage with fundamental human concerns—debates about texts can play an important in the social discussion of beliefs and values.How we read a given text also depends to some extent on our particular interest in reading it. (45)_________________________________________Such dimensions of reading suggest — as other introduced later in the book will also do — that we bring an implicit(often unacknowledged)agenda to any act of reading. It doesn’t then necessarily follow that one kind of reading is fuller, more advanced and more worthwhile than another. Ideally, different kinds of reading inform each other, and act as useful reference points for and counterbalances to one another. Together, they make up the reading component of your overall literacy, or relationship to your surrounding textual environment.A. Are we studying that text and trying to respond in a way that fulfils the requirement of a give course? Reading it simply for pleasure? Skimming it for information? Ways of reading on a train or in bed are likely to differ considerably from reading in a seminar room.B. Factors such as the place and period in which we are reading, our gender, ethnicity, age and social class will encourage us towards certain interpretations but at the same time obscure or even close off others.C. If you are unfamiliar with words or idioms, you guess at their meaning, using clues presented in the context. On the ash emption that they will become relevant later, you make a mental note of discourse entities as well as possible links between them.D. In effect, you try to reconstruct the likely meaning or effects that any given sentence, image or reference might have had: These might be the ones author intended.E. You make further inferences, for instance, about how the text may be significant to you, or about its validity — inferences that from the basis of personal response for which the author will inevitably be far less responsible.F. In plays, novels and narrative poems, characters speak as constructs created the author, not necessarily as mouthpieces for the author’s own thoughts.G. Rather, we ascribe meanings to texts on the basis of interaction between what we might call textual and contextual material: between kinds of organization or pattering we perceive in a text’s formal structures (so especially its language structures) and various kinds of background, social knowledge, belief and attitude that we bring to the text.Part CDirections:Read the following text carefully and then translate the underlined segments into Chinese. Your translation should be written neatly on the ANSWER SHEET. (10 pionts)Within the span of a hundred years, in the seventeenth and early eighteenth centuries, a tide if emigration- one of the great folk wanderings of history- swept from Europe to America. (46) This movement, driven by powerful and diverse motivations, built a nation out of a wilderness and, by its nature, shaped the character and destiny of an uncharted continent.(47) The United States is the product of two principal forces- the immigration of European people with their varied ideas, customs, andnational characteristics and the impact of a new country which modified these traits. Of necessity, colonial America was a projection of Europe. Across the Atlantic came successive groups of Englishmen, Frenchmen, Germans, Scots, Irishmen, Dutchmen, Swedes, and many others who attempt to transplant their habits and traditions to new world. (48) But the force of geographic conditions peculiar to America, the interplay of the varied national groups upon once another, and the sheer difficulty of maintaining old-world ways in a raw, new continent caused significant changes. These changes were gradual and at first scarcely visible. But the result was a new social pattern which, although it resembled European society in many ways, has a character that was distinctly American.(49) The first shiploads of immigrants bound for the territory which is now the United States crossed the Atlantic more than a hundred years after the 15th-and- 16th century explorations of North America. In the meantime, thriving Spanish colonies had been established in Mexico, the West Indies, and South America. These travelers to North America came in small, unmercifully overcrowded craft. During their six-to twelve-week voyage, they survived on barely enough food allotted to them. Many of the ships were lost in storms, many passengers died of disease, and infants rarely survived the journey. Sometimes storms blew the vessels far off their course, and often calm brought unbearably long delay.To the anxious travelers the sight of the American shore brought almost inexpressible relief. Said one recorder of events, “ The air at twelve leagues’ distance smelt as sweet as a new-blown garden.” The colonists’ first glimpse of the new land was a sight of dense woods. (50) The virgin forest with its richness and variety of trees was a real treasure-house which extended from Maine all the way down to Georgia. Here was abundant fuel and lumber……Section III WritingPart A51.Directions:You are going to host a club reading session. Write an email of about 100 words recommending a book to the club members.You should state reasons for you recommendation.You should write neatly on the ANSWER SHEET.Do not sign your own name at the end of the letter. Use “Li Ming”instead.Do not write the address.(10 points)Part B52.Directions:Write an essay of 160-200 words based on the following picture. In your essay, you should(1) Describe the picture briefly,(2) Interpret its intended meaning, and(3) Give your comments.You should write neatly on the ANSWER SHEET.(20 point)2015考研英语(一)参考答案(完整版)I cloze1、What2、Concluded3、On4、Compared5、Samples6、Insignificant7、Know8、Resemble9、Also10、Perhaps11、To12、Drive13、Ratherthan14、Benefits15、Faster16、understand17、Contributory18、Tendency19、Ethnic20、seeII Reading comprehensionPart A21.D ended his reign in embarrassment.22. C owing to the undoubted and respectable status23. A the role of the nobility in modern democracy24. B fails to change his lifestyle as advised.25. D Carlos, a lesson for all Monarchies26. C check suspect's phone contents without being authorized.27.A disapproval28.A getting into one's residence29. C citizens' privacy is not effectively protected30.B new technology requires reinterpretation of the constitution31.B journals are strengthening their statistical checks32.B marked33. D set an example for other journals34. C has room for further improvement35.A science joins Push to screen statistics in papers36. D the consequences of the current sorting mechanism37. A more journalists may be found guilty of phone hacking38. C was hardly convincing39. B generally distorted values40. D moral awareness matters in editing a newspaperPart B41.Cifyouareunfamiliar...42.Eyoumakefurtherinferences...43.D Rather ,we ascribe meanings to...44.Bfactorssuchas...45.Aarewestudyingthat ...Part C46)在多种强大的动机驱动下,这次运动在一片荒野上建起了一个国家,其本身塑造了一个未知大陆的性格和命运。

英文版计算机试题及答案Section 1: Multiple Choice Questions (MCQs)1. Which of the following is NOT a programming language?a) Javab) HTMLc) Pythond) SQLAnswer: b) HTML2. What does CPU stand for?a) Central Processing Unitb) Computer Processing Unitc) Control Processing Unitd) Central Program UnitAnswer: a) Central Processing Unit3. Which of the following is NOT an input device?a) Keyboardb) Mousec) Printerd) ScannerAnswer: c) Printer4. What does RAM stand for?a) Read-Only Memoryb) Random Access Memoryc) Recordable Audio Mediad) Runtime Activity MonitorAnswer: b) Random Access Memory5. Which of the following is NOT a type of computer network?a) LAN (Local Area Network)b) WAN (Wide Area Network)c) MAN (Metropolitan Area Network)d) CAN (Campus Area Network)Answer: d) CAN (Campus Area Network)Section 2: Short Answer Questions1. Define the term "algorithm."Answer: An algorithm is a step-by-step procedure or set of rules for solving a specific problem or completing a specific task.2. What is object-oriented programming (OOP)?Answer: Object-oriented programming is a programming paradigm that organizes code into objects, which are instances of classes. It emphasizes the concept of objects and their interactions to solve complex problems.3. Explain the difference between static and dynamic memory allocation.Answer: Static memory allocation is performed at compile-time, where memory is allocated for variables and objects before the program execution starts. Dynamic memory allocation, on the other hand, is performed at runtime using functions like malloc() or new(). It allows for the allocation and deallocation of memory during program execution.4. What is the purpose of an operating system?Answer: The operating system is responsible for managing computer hardware and software resources, providing an interface between the user and the computer, and ensuring that various programs and applications can run smoothly. It also provides file management, process management, and memory management.5. Name three programming paradigms.Answer: Three programming paradigms are procedural programming, object-oriented programming, and functional programming.Section 3: Coding Questions1. Write a Java program to find the factorial of a given number.```javaimport java.util.Scanner;public class Factorial {public static void main(String[] args) {Scanner input = new Scanner(System.in);System.out.print("Enter a number: ");int number = input.nextInt();int factorial = 1;for (int i = 1; i <= number; i++) {factorial *= i;}System.out.println("The factorial of " + number + " is " + factorial); }}```2. Write a Python program to check if a number is prime or not.```pythondef is_prime(number):if number < 2:return Falsefor i in range(2, int(number/2)+1):if number % i == 0:return Falsereturn Truenumber = int(input("Enter a number: "))if is_prime(number):print(number, "is prime.")else:print(number, "is not prime.")```3. Write a C program to reverse a given string. ```c#include <stdio.h>#include <string.h>void reverse_string(char* str) {int length = strlen(str);for (int i = 0; i < length/2; i++) {char temp = str[i];str[i] = str[length - i - 1];str[length - i - 1] = temp;}}int main() {char str[100];printf("Enter a string: ");gets(str);reverse_string(str);printf("Reversed string: %s", str);return 0;}```Note: The code provided above is just examples for the coding questions. Please ensure to compile and test the programs before using them in production.Conclusion:In this article, we discussed multiple-choice questions, short answer questions, and coding questions related to computer science and programming. These questions cover various aspects of computer knowledge and can be used for self-assessment or preparation for exams or interviews.。
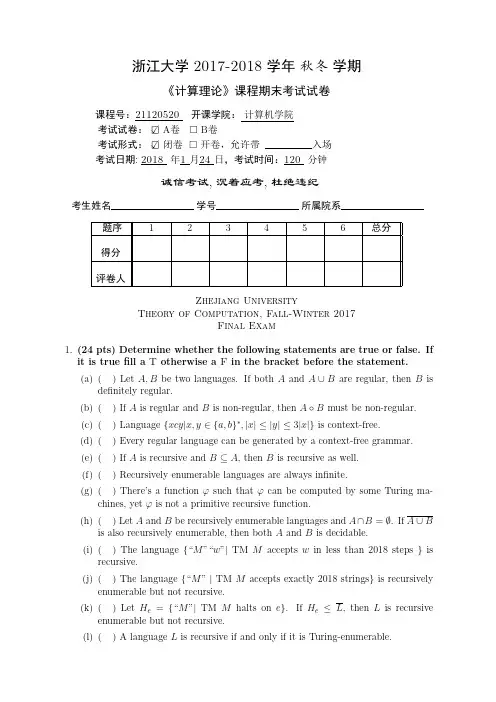
浙江大学2017-2018学年秋冬学期《计算理论》课程期末考试试卷课程号:21120520开课学院:计算机学院考试试卷: A卷 B卷考试形式: 闭卷 开卷,允许带入场考试日期:2018年1月24日,考试时间:120分钟诚信考试,沉着应考,杜绝违纪考生姓名学号所属院系题序123456总分得分评卷人Zhejiang UniversityTheory of Computation,Fall-Winter2017Final Exam1.(24pts)Determine whether the following statements are true or false.Ifit is truefill a T otherwise a F in the bracket before the statement.(a)()Let A,B be two languages.If both A and A∪B are regular,then B isdefinitely regular.(b)()If A is regular and B is non-regular,then A◦B must be non-regular.(c)()Language{xcy|x,y∈{a,b}∗,|x|≤|y|≤3|x|}is context-free.(d)()Every regular language can be generated by a context-free grammar.(e)()If A is recursive and B⊆A,then B is recursive as well.(f)()Recursively enumerable languages are always infinite.(g)()There’s a functionφsuch thatφcan be computed by some Turing ma-chines,yetφis not a primitive recursive function.(h)()Let A and B be recursively enumerable languages and A∩B=∅.If A∪Bis also recursively enumerable,then both A and B is decidable.(i)()The language{“M”“w”|TM M accepts w in less than2018steps}isrecursive.(j)()The language{“M”|TM M accepts exactly2018strings}is recursively enumerable but not recursive.(k)()Let H e={“M”|TM M halts on e}.If H e≤L,then L is recursive enumerable but not recursive.(l)()A language L is recursive if and only if it is Turing-enumerable.2.(18pts)On FA and Regular LanguagesSay whether each of the following languages is regular or not regular?Prove your answers,where{a,b}+={a,b}∗◦{a,b}.(a)L1={wtw|w,t∈{a,b}+}(b)L2={wtw|w,t∈{a,b}∗}3.(20pts)On PDA and Context-Free LanguagesLet L3={ww R ca m b n|w∈{a,b}∗,m,n∈N,m=n}.(a)Construct a context-free grammar that generates the language L3.(b)Construct a pushdown automata that accepts L3.Solution:(a)(b)The PDA M=(K,Σ,Γ,∆,s,F)is defined below:(q,σ,β)(p,γ)K=Σ={a,b,c}Γ=s=F=4.(10pts)On Turing MachineDesign a single tape Turing machine M that decides the language L4L4={uvcww R|u,v,w∈{a,b}∗,|u|=2|v|}When describing the Turing machines above,you can use the elementary Turing machines described in textbook.Always assume that your Turing machine starts from the configuration◃⊔x,where x is the input string.5.(10pts)On Primitive Recursive Function→N,and k∈N,k≥2 Show the following functionφk:N×N×···×Nk{n1,n2,···,n k}φk(n1,n2,···,n k)=maxkis primitive recursive.6.(18pts)On UndecidabilityClassify whether each of the following languages are recursive,recursively enumerable but not recursive,or non-recursively enumerable.Prove your answers,but you may not simply appeal to Rice’s theorem.(a)L5={“M”|M is a TM,and L(M)is uncountable}(b)L6={“M”|TM M accepts at least two strings of different lengths}Enjoy Your Spring Festival!。

2015年上学期《计算机专业英语》期末考试试卷班级_______ 学号________ 姓名________ 计分_______I. Match the phrases with their Chinese correctly.(3’×6=18’)A.产品发布B.需求阶段C.缺陷报告D.测试计划E.测试设计F.测试执行1.____ product release2._____ bugs reporting3.____test execution4.____ test design5.____ test plan6.____ requirements stageII. Reading comprehension.项目工作计划A project work plan is the schedule of tasks, durations, and dates to accomplish a project.A high level work plan shows the standard deliverables for the process, and detailed project plan shows the project-specific tasks.A project work plan provides a plan of what has to be done, how the work will be organized and who will do it. The following steps will provide you with information to be used in developing a good work plan:List the project objectives and chosen strategies.List the tasks you need to do for those objectives and strategies to be used.Put the tasks in the order that they should occur.Estimate times and dates to create a schedule.Estimate the resources needed for your activities ( including time, money, skills, people, equipment, facilities,information,etc.)Assign responsibilities to people for various activities.A. Reorder the letters.(3’×4=12’)Letters Wordslish comp ac aiver able del djec ob tive oponsi res bility rB. List the steps to get the information for a good work plan.(5’×6=30’)①②③④⑤⑥III.Translation.(5’×4=20’)① Thanks for your help, I can’t tell you how much I appreciate it.② If there are no further questions, then I guess everything is clear.③ List the project objectives and chosen strategies.④ Estimate times and dates to create a schedule.①②③④IV. Cloze.(2’×10=20’)Tina Lin was not like many of her clas smates. She didn’t listen to popular music. She didn’t watch many movies, and she wasn’t interested in nice clothes.When she got 1 with her friends at a party, Tina found her friends preferred rock and pop music. When Tina 2 if they would like to try classical music, they all looked at her strangely.“ 3 music is for old people,” one of her friends said.Tina was 4 that something was wrong with her. She decided to 5 her father. As she entered his study, he could feel something was wrong.“Dad, am I strange?” she asked her 6 .“Of course not,” he answered, “Why do you ask that?”“Because I don’t 7 the same things as my classmates. They want to listen to pop music. I like classical music.”“I think I understand. Never mind, T ina. 8 all right to be your own person. You don’t have to copy what other people do. Everybody 9 different tastes (品味). Some of them are popular, 10 others aren’t.”After Tina spoke with her father, she felt better about herself. She realized that being different made her special. It was an important lesson for her to learn.( ) 1. A. up B. angry C. together( ) 2. A. asked B. found C. noticed( ) 3. A. Pop B. Rock C. Classical( ) 4. A. proud B. worried C. glad( ) 5. A. talk to B. look for C. write to( ) 6. A. friend B. father C. classmate( ) 7. A. have B. know C. like( ) 8. A. It’s B. That’s C. You’re( ) 9. A. have B. has C. had( ) 10. A. but B. so C. for。

计算机英语试题及答案一、选择题(每题2分,共20分)1. The basic unit of data in a computer is:A. ByteB. BitC. KilobyteD. Megabyte答案:B2. Which of the following is not a function of an operating system?A. Memory managementB. Process managementC. Hardware managementD. Web browsing答案:D3. The term "CPU" stands for:A. Central Processing UnitB. Computer Personal UnitC. Computer Programming UnitD. Cybernetic Processing Unit答案:A4. In computer networking, "LAN" refers to:A. Local Area NetworkB. Long-Distance Area NetworkC. Local Access NetworkD. Long-Access Network答案:A5. What is the role of a "router" in a computer network?A. To connect different networksB. To store dataC. To print documentsD. To control access to the internet答案:A6. The process of converting programs into machine language is known as:A. InterpretationB. CompilationC. DebuggingD. Encryption答案:B7. Which of the following is a type of programming language?A. HTMLB. JPEGC. MP3D. DOCX答案:A8. What does "GUI" stand for in computing?A. Graphical User InterfaceB. General User InterfaceC. Graphical User InformationD. Global User Interface答案:A9. A "firewall" is a security device designed to:A. Prevent unauthorized access to a networkB. Control the temperature in a computer roomC. Store firewalls for later useD. Monitor the flow of data in a network答案:A10. The acronym "URL" stands for:A. Uniform Resource LocatorB. Unique Resource LocatorC. Universal Resource LocatorD. User Resource Locator答案:A二、填空题(每题2分,共20分)11. The binary system uses only two digits: 0 and ______.答案:112. A gigabyte is larger than a megabyte, with 1 gigabyte equal to 1,024 megabytes.13. The most common type of connection between a computer and the internet is through a(n) ______.答案:modem14. In programming, a ______ is a sequence of instructions that a computer can execute.答案:program15. A ______ is a type of software that allows users to browse the internet.答案:web browser16. The ______ is the primary component of a computer that performs most of the processing.答案:CPU17. Data encryption is a method of converting data into a code to ______ unauthorized access.答案:prevent18. A ______ is a set of rules governing the structure of data and the way it is transmitted.答案:protocol19. The ______ is a type of software that provides a graphical interface for interacting with the computer.答案:operating system20. A ______ is a hardware device that connects multiple computers together in a network.答案:switch三、简答题(每题10分,共20分)21. Explain the difference between a compiler and aninterpreter in programming.答案:A compiler is a software tool that translates the entire source code of a program into machine language before execution. It processes the code as a whole and produces an executable file that can be run independently of the compiler. On the other hand, an interpreter translates and executes the source code line by line or block by block, without creatinga separate executable file. Interpreters run the codedirectly and are typically used for scripting languages.22. Describe the function of a database management system (DBMS).答案:A database management system (DBMS) is a software system that allows users to create, modify, and manage databases. It provides a way to store, organize, and retrieve data efficiently. The main functions of a DBMS includecreating the structure of a database, entering and retrieving data, maintaining data integrity, and controlling access tothe data. It also supports advanced operations such as querying, indexing, and transaction management.四、翻译题(每题15分,共30分)23. 将以下句子从英文翻译成中文:"The Internet of Things (IoT) is a network of physical objects embedded with electronics, software, sensors, andnetwork connectivity which enables these objects to collect and exchange data."答案:物联网(。

2016年浙江大学研究生入学考试计算机学科专业基础考试大纲2016年浙江大学研究生入学考试《计算机学科专业基础》(878)考试大纲Ⅰ考查目标《计算机专业基础》(878)综合考试涵盖程序设计、数据结构、操作系统和计算机网络等学科专业基础课程。
要求考生比较系统地掌握上述专业基础课程的基本概念、基本原理和基本方法,能够综合运用所学的基本原理和基本方法分析、判断和解决有关理论问题和实际问题。
Ⅱ考试形式和试卷结构一、试卷满分及考试时间本试卷满分为150分,考试时间为180分钟二、答题方式答题方式为闭卷、笔试三、试卷内容结构程序设计基础(C)30分数据结构50分操作系统40分计算机网络30分四、试卷题型结构单项选择题70分(35小题,每小题2分)综合应用题80分Ⅲ考查范围程序设计基础(C)【考查目标】1.理解C程序设计语言结构,掌握数据表示和输入输出的基本方法,掌握流程控制、函数设计与调用方法;2.理解模块化程序设计方法,掌握基本的C语言程序设计过程和技巧;3.掌握初步的算法设计及数据组织方法,具备基本的问题分析和利用C语言进行求解问题的能力。
一、数据表达与组织(一)常量,变量,运算与表达式(二)一维和二维数组,字符数组和字符串(三)指针与数组,结构与数组(四)指针与结构,单向链表二、语句及流程控制(一)复合语句(二)分支控制(if、switch)(三)循环控制(for、while、do—while)三、程序结构和函数(一)C程序结构(二)函数的定义、参数传递和调用(三)函数的递归调用(四)变量的存储类别、作用域,全局变量和局部变量四、输入/输出和文件(一)标准输入和输出(二)文本文件与二进制文件(三)文件打开、关闭、读写和定位五、编译预处理和命令行参数(一)宏定义和宏函数(二)命令行参数和使用六、基本算法设计与程序实现(一)简单排序算法(插入、选择、冒泡)、二分查找(二)链表、文件中查找(三)级数求和、进制转换数据结构【考查目标】1.掌握数据结构的基本概念、基本原理和基本方法;2.掌握数据的逻辑结构、存储结构及基本操作的实现,能够对算法进行基本的时间复杂度与空间复杂度的分析;3.能应用数据结构基本原理和方法进行问题的分析与求解,具备采用C或C++语言设计与实现算法的能力。

《计算机英语》B卷本卷满分100分,90分钟完卷。
得分:一、选出下列单词所缺字母组合(共10小题,每小题2分,共20分)。
1.Parti__lar (特别的)A. ceB. cuC.coD. cr2.Determ___(决定)A. ineB. ingC. innD. ino3.Previ___ly (先前地,以前地)A.ocsB. onsC. ousD.obs4.Functionali__(功能)A.tiB. tyC. ttD. to5.Distri__tion (发行版,发布)A.biB. buC. beD. bo6.Catego___ (种类)A.ryB.riC.rtD.ty7.Sophisti__tion (复杂)A.coB.ceC.ca8.Capa__ty (容量,能力)A.ceB.coC.ciD.cr9.Private__ (私下地,私密地)A.lyB.liC.tyD.il10.Dere__lation (违反规定)A.gaB.goC.ggD.gu二、单项选择题(共10小题,每小题2分,共20分)。
11. I can ____ basketball.A. playedB. playsC. playingD. play12. ---Happy birthday to you.---______________A.The same to youB.good luckC. Not at allD.Thank you.13. Happy life rely on_____ hard.A. workB. workingC. worksD. to work14. She is a ____ girl.A. beautyB. beautiesC. beautifulD. beautifully15.---What`s wrong with you?---____________A. I don`t knowB. I feel terribleC. Don`t worryD. Thanks16. ---How about having bread for lunch?---_____________A.Yes,it isB. That`s greatC .I am fine D.Fine,thanks.and you?17. He expresses an interest ___ reading.A. inB. onC. atD.to18.She _______ English for seven years.A. studyB. studiesC. studiedD. has studied19. ---You are Jack, right?---___________.A. Yes,it isB. yes,I amC. Yes,I wasD.Yes,I do20. She goes to the library ______.A. readB. to readC. readingD. reads三、阅读理解(共5题,每小题4分,共20分)。

学院2007-2008学年度第一学期期末考核试卷考核课程:《计算机专业英语》考试类型: 理论考试方式: 闭卷笔试学生所在院系:计科系年级:20所级试卷:A姓名:班级:学号:题号一二三四五六总分一、Give out the full names for the following abbreviations(写出下阅卷人列缩写词的全称)(15%)ROM _____________________________________________________________CPU _______________________________________________________________BIOS ______________________________________________________________IT ________________________________________________________________WWW _______________________________________________________________HTML ______________________________________________________________PCI _______________________________________________________________HR ________________________________________________________________GUI _______________________________________________________________MHz _______________________________________________________________得分阅卷人二、Match the following words and expressions in the left columnwith those similar in meaning in the rightcolumn(将左列的词汇与右列相应的汉语匹配)(10%)1.memory unit2.intelligence3.semiconductor memon r4.data definition language5.mechanism6.machine languagemunication a.半导体存储器b.机制c.存储单元d.数据定义语言e.通信f.机器语言g・智能四、For each of the following blanks, four choices are given. Choose the most appropriate one (从下面给出的四个选项中选择最恰当的答 案)(30%)1. The basic units of a computer system are as follows:A. CPU, memory and diskB. CPU, input and output unitC. CPU, memory and I/O systemD. CPU, memory and ALU2. Today, can give you a music synthesizei; a fax machine, a CD-ROM drive, ect.A. input devicesB. expansion cardsC. output deviceD. joystick*3. The control unit fetches from memory and decodes them.-------------------------------- VA. dataB. informationC. resultsD. instructions*4. When power is removed, information in the semiconductor memory is A. reliable B. lost C. manipulatedD- remain1. ( ) 6. ( )2. ( ) 7. ( )3. ( ) 8. ( )4. ( ) 9. ( )5.( ) 10.( )8. distance education 9. pattern recognitionlO.enterprise resource planning h.远程教育 i.企业资源计划 J-模式识别得分阅卷人三、 T ranslate the following phrases into English (将下列短语翻译成板逻码菜技 统术器助形系算机帮图得分阅卷人英语)(10%)*5. Please find the Item that is not belong to the DBA )A. storage structure and access method definitionB. schema definitionC. integrity constrain specificationD. DDL6.is designed to manage large bodies of information.A. a file systemB. a transactionC. a database systemD. a database language7. A characteristic of operating system is•A. resource managementB. memory managementC. error recoveryD. all the above8.Assembly-language instructions are a series of•A. Os and IsB. abstract codesC. machine codesD. words9.program also has potential benefits in parallel processing.A. MachineB. AssemblyC. Object-orientedD.Process-oriented10.An advantage of a ring network is that it needs less•A. computerB. networkC. cableD. information11.An ISP supplies a that you can dial from your computer to logon the internet server.A. public keyB. private keyC. service numberD. help file12.To open Internet Explorer, Just click Start, point to, and then click Internet Explorer.A. ProgramsB. ViewC. LayoutD. Control Panel13.Electronic bulletin boards are communication platforms.A. one-to-manyB. one-to-oneC. many-to-manyD. all above14.Followings are some image data file formats, which is wrong?A.*. TIFB. *. DOCC. *. BMPD.*. GIFC.it can rotate a three-dimensional modeLD.it can do all above at the same time.15.By adding to your programs, you can make computers moreinteresting and much more fun for the user.五.To Identify the following to be True or False according to computer knowledge(根据计算机知识判别是非题)(10%)1. Registers in the control unit are used to keep track of the overall status of the program.()2. The basic resources of a computer system are software and data. (3. The chipset consists of two parts: North Bridge and South Bridge.()4. The *.BMP file can only be used in the IBM system. ( )5. ROM does not have the inputs and writing controls. ( )6. “ADD AX, BX” is a instruction of machine language.() 7. A data definition language can be used to define a database schema.( ) 8. People can only use the ISP to connect Internet. ( ) 9. We can use E-mail only as a one-to-one platform. ( ) 10. Hypermedia is the same as multimediae( ) 六.Reading comprehension(阅读理解)(25%)(一)Fill in the blanks with suitable words or expressions from thelist given below, and change the form where necessary (从下面所列词语中选择合适的 词语,以其适当的形式填空)(10%)high-level language assembly language written machine language notationA programming language, designed to facilitate the communication between human and computers, is a for describing computationin readable form. There are 3 levels of programming languages, they are , which can be run directly by computer; and • There are different high-level programming languages. Fortunately, most of them have many kinds of construct in common and varv onlv in the wav that these must be • Therefore^ first thing to be decided about a task is to choose which programming language is best suited for the job. Passage AThe central processing unit (CUP) is the heart of the computer systems. Among other things, its configuration determines whether a computer is fast or slow in relation to other computers. The CPU is the most complex computer system component, responsible forA. multimedia C. musicB.text D. picturedirecting most of the computer system activities based on the instructions provided. As one computer generation has evolved to the next, the physical size of the CPU has often become smaller and smaller9 which its speed and capacity have increased tremendously. Indeed, these changes have resulted in mlcro-Computers that are small enough to fit on your desk and your lap.The CPU comprise the control unit and the arithmetic/Iogic unit (ALU).The control unit is responsible for directing and coordinating most of the computer systems activities. It determines the movement of electronic signals between main memory and the arithmetic/Iogic unit, as well as the control signals between the CPU and input/output devices.The ALU perforins all the arithmetic and logical(comparison) functions—that is, it adds, subtracts, multiplies, divides, and does comparison. These comparisons9 which are basically “less than”,“greater than”, and “equal to”, can be combined into several common expres sions, such as “greater than or equal to”. The objective of most instructions that use comparisons is to determine which instruction should be executed next.(二)Tell whether the following statements are true(T) or false(F) according to the passage A(根据上文的内容判断下列句子的正误)(15%)1.With the development of computer, the physical size of the CPU has often become bigger and bigger ( )2.The movement of electronic signals between main memory and the ALU as well as the control signal between the CPU and input/output devices are controlled by the control unit of the CPU. ( )3.The CPU comprises the control unit and memory. ( )4.The control unit performs all the arithmetic and logical functions.( )5.The central processing unit (CPU) is the heart of the computer systems. ( )【第页共页】学院2007-2008学年度第一学期期末考核试卷参考答案及评分标准考核课程:计算机英语考试类型:理论 考试方式:闭卷笔试学生所在院系:计科系 年 级: 2016 试卷:A 执笔人: ______________要求:明确标注每小题或每步骤得分点一• Give out the full names for the following abbreviations (写出下列缩写词 的全称)(15%)(本题共15分,每小题1.5分)ROM: Read Only Memory CPU: Central Processing Unit BIOS: Basic Inpiit/Output Unit IT: Information Technology WWW: World Wide WebHTML: Hypertext Markup Language PCI: Peripheral Component Interconnect HR: Human ResourceGUI: Graphical User Interface MHz: Megahertz二.Match the following words and expressions in the left column with those similar inmeaning in the right column (将左列的词汇与右列相应的汉语匹配) (10%)(本题共10分,每小题1分)1. ( C ) 6. ( f) 2. ( g ) 7. ( e ) 3. ( a ) 8. ( h ) 4. ( d ) 9. ( J ) 5.(b) 10. (• 1 )三. Translate the following phrases into English(将下列短语翻译成英语)(10% )(本题共10分,每小题2分)1.the system board2.Arithmetic logical operations3.machine code4.Help menu5.graphics technology四.For each of the following blanks, four choices are given. Choose the most appropriate one(从下面给出的四个选项中选择最恰当的答案)(30%)(本题共30分,每小题2分)1. C 2,B 3.D 4.B 5.D 6 C 7. A 8. B 9. C 10. C IL C 12. A 13. A 14. B 15. A五.To identify the following to be True or False according to computer knowledge(根M计算机知识判别是非题)(10%)(本题共10分,每小题1分)1. ( T )2. ( F)3. (T)4. ( F )5. (T )6. ( F )7. (T )8. ( F )9. ( F )10.( F )六.Reading comprehensk)n(阅读理解)(25%)(一)Fill in the blanks with suitable words or expressions from the list given below, and change the form where necessary (从下面所列词语中选择合适的词语,以其适当的形式填空)(10%)(本题共10分,每空2分)notation machine language assembly language high-level language written(3空和4空答案可互换)(二)Tell whether the following statements are true(T) or false(F) according to thepassage A(根据上文的内容判断下列句子的正误)(15%)(本题共15分,每小题3分)l.(F) 2. (T ) 3. ( F ) 4.(F) 5. ( T )1、_b ___ refers to the parts of the computer that you can see and touch.A. SoftwareB. HardwareC. HardshipD. Instruction 2、primary memory which is stored on chips located_a_。

2014年下学期《计算机专业英语》期中考试试卷班级:_________ 姓名:________ 学号:________ 计分:________ I. 根据图片把方框里的单词或词组填入对应的空格。
(14分)1. __________________2. _________________3. __________________4. _________________5. __________________6. _________________7. __________________II. 中英文配对:将中文前的字母填入其对应的英文前的空格里。
(20分)_____ 1. input device a. 闪盘_____ 2. RAM b. 只读光盘_____ 3. floppy disk c. 芯片_____ 4. memory bank d. 移动硬盘_____ 5. output device e. 输入设备_____ 6. flash disk f. 随机存储器_____ 7. chip g. 软盘_____ 8. mobile hard disk h. 输出设备_____ 9. motherboard i. 内存条_____ 10. CD-ROM j. 主板III. 阅读理解:AMary: Hello, PC Support Center. This is Mary. What can I do for you? Customer: Hello. this is Chen Lin. I’m calling because I have some questions about my disk.Mary: Hi, Chen Lin. You can tell me one by one.Customer: I’m afraid I’ll run out of disk space. What shall I do?Mary: OK, running out of hard disk space is no big deal. You can just start moving old junks off to the CDs or you can just add a second hard disk. Customer: Oh, I see. Are there any signs before the hard drive fails?Mary: Yes, the signs may include strange sounds, noise, popping or similar problems.Customer: Thanks for your helpMary: You’re welcome.根据上文判断以下句子是否正确,正确的写“T”,错误的写“F”。

计算机网络(全英文版)期末复习As an AI language model, I can help you with the content of your article on "Computer Networks - Final Exam Review". However, please note that I am unable to format the document according to specific requirements, such as adding a word count or creating sections with headings. I will provide you with a comprehensive overview of computer networks in English, covering the essential concepts and topics that are typically covered in a final exam review. Here is the article:Computer Networks - Final Exam ReviewIntroduction:Computer networks are an integral part of modern society, facilitating communication and enabling the exchange of information between devices and users. Understanding the fundamentals of computer networks is crucial for professionals in the field of IT and related disciplines. This article aimsto provide a comprehensive review of key concepts and topics in computer networks to help you prepare for your final exam.Network Topologies:A network topology refers to the physical or logical layout of devices in a network. Several common network topologies include bus, star, ring, mesh, and hybrid topologies. Each topology has advantages and disadvantages, and understanding these can help network administrators design and maintain efficient networks.Network Protocols:Network protocols provide a set of rules and guidelines for devices to communicate with each other in a network. The TCP/IP protocol suite is the foundation of modern network communication, consisting of protocols such as IP (Internet Protocol), TCP (Transmission Control Protocol), and UDP (User Datagram Protocol). These protocols ensure reliable and efficient data transfer over networks.OSI Model:The Open Systems Interconnection (OSI) model is a conceptual framework that standardizes the functions of a network into several layers. These layers - physical, data link, network, transport, session, presentation, and application - define how data is transmitted, processed, and presented across a network. Understanding the OSI model aids in troubleshooting network issues and implementing effective network solutions.Network Addressing:In computer networks, devices are identified and addressed using unique addresses. IP addressing, specifically IPv4 and IPv6, allow devices to establish connections and route data packets across networks. IP addressing includes both network and host addresses, enabling efficient communication within and between networks.Routing and Switching:Routing involves determining the optimal path for data packets to travel from source to destination across interconnected networks. Routers, using routing tables and protocols such as OSPF (Open Shortest Path First) and BGP (Border Gateway Protocol), facilitate this process. Switching, on theother hand, involves the efficient forwarding of data packets within a local area network (LAN) using MAC addresses.Network Security:As networks become increasingly complex and interconnected, ensuring network security is paramount. Network security measures include firewalls, intrusion detection systems, encryption, and authentication protocols. Protecting networks from unauthorized access, data breaches, and other threats is essential to maintain data integrity and user privacy.Wireless Networks:Wireless networks have revolutionized connectivity, allowing devices to communicate without physical cables. Wi-Fi, Bluetooth, and cellular networks are examples of wireless technologies widely used today. Understanding wireless networking protocols, security considerations, and challenges is important in a world where wireless connectivity is pervasive.Network Troubleshooting:Network administrators often encounter issues that require troubleshooting skills. Effective troubleshooting involves using diagnostic tools, analyzing network logs, and understanding common network issues such as connectivity problems, latency, and bandwidth constraints. By following logical steps and employing best practices, network administrators can identify and resolve network problems efficiently.Conclusion:Computer networks are the backbone of modern communication and information exchange. This article has provided an overview of key concepts and topics in computer networks, including network topologies, protocols, the OSI model, addressing, routing and switching, network security, wireless networks, and network troubleshooting. Remember to review these concepts thoroughly to prepare for your final exam.。

1.自我介绍Question: Please introduce yourself.A:Good Morning, My dear teachers. I am glad to be here for this interview. Firstly let me introduce myself. My name is ZZY, 22 years old. I am senior student from SCUT majoring in CS. For the pass three year I learn how to self-study and make friends; I come from suixi, a very beautiful and famous county of guang dong.It’s called the sweetest county of china.I am easy to get along with, and good at thinking.I am skillful in coding some simple programs and searching for information on the Internet for study or research.for the one past year I mainly do my research on stream-media and Network architecture.I’m good at network programming.In my spare time, I like reading book about Philosophy and Science.and, Besides, solving the problems on a ACM online judge system is my hobby. Ok, that is all, thank you for your patience and attention. 2.介绍自己的家庭。
计算机专业英语期末测试卷计算机专业英语试题命题⼈:王晓萍姓名:__________ 班级:___________ 分数:__________________ ⼀、英汉互译并写出缩写的全称(20分)1.Operating system_____________ 2.Network security_____________ 3.Tree structure_______________ 4.Supervisor password____________ 5.Application software____________ 6.PC _________________________ 7.Computer virus________________ 8.BIOS__________________ 9.CPU________________________10.计算机程序____________________11.软件测试_____________________ 12. ⼦⽂件夹________________13. 主菜单__________________14. 微处理器________________15. 升级软件________________16. 副作⽤__________________17. 搜索引擎________________18. 备份____________________19. ⾜够内存________________20. 域名____________________⼆、判断题(对的填T, 错的填F)(5分)1 计算机病毒是⼀种程序()2 病毒通常会具有副作⽤()3 反病毒软件只可以扫描病毒()4 假如想要进⾏表格计算,我们要选择PowerPoint.()5 Microsoft Office是⼀款办公⾃动化软件。
()三、选择题(25分其中英语的每题2分)1 “firewall”的意思是()A 防⽕墙B 防盗⽹C 核导弹D 不锈钢2 假如想要进⾏⽂本编辑,我们需要选择的程序是()A PPTB ExcelC PSD Word3 ISP代表的是()A 游戏玩家B 等级C 因特⽹服务提供商D QQ4 下列哪种邮箱的写法是正确的()A 123445566677B dihgoojgngjjpngn@C 845446738@/doc/b0a025e8c8d376eeaeaa31ae.htmlD 都努⼒及格哈@/doc/b0a025e8c8d376eeaeaa31ae.html5 下列说法正确的是()A骇客是指对计算机感兴趣且精通的狂热分⼦B⿊客是指侵⼊别⼈计算机,进⾏破坏的⼈C⿊客是指长的很⿊的⼈DAB都对6. The basic units of a computer system are as follows: _________A. CPU, memory and diskB. CPU, input and output unitC. CPU, memory and I/O systemD. CPU, memory and ALU7. Today, ______can give you a video camera, a fax machine, a CD-ROM drive, ect.A. input devicesB. expansion cardsC. output deviceD. joystick8. When power is removed, information in the semiconductor memory is ________ .A. reliableB. lostC. manipulatedD. remain9. _________ is designed to manage large bodies of information.A. a file systemB. a transactionC. a database systemD. a database language10. A characteristic of operating system is _________ .A. resource managementB. memory managementC. error recoveryD. all the above11. An ISP supplies a _________ that you can dial from your computer to log on the internet server.A. public keyB. private keyC. service numberD. help file12. To open Internet Explorer, just click Start, point to _________ , and then click Internet Explorer.A. ProgramsB. ViewC. LayoutD. Control Panel13. Followings are some image data file formats, which is wrong? _______A.*.TIFB. *.DOCC. *.BMPD. *.GIF14. By adding _________ to your programs, you can make computers more interesting and much more fun for the user.A. multimediaB. textC. musicD. picture15. Followings are all software, which is not the antivirus software?A Kaspersky Antivirus B. Jiangming softwareC. Rising softwareD. Spyware四、将左列的词汇与右列相应的汉语匹配。
浙江大学2012-2013学年秋冬学期《计算理论》课程期末考试试卷答案课程号:21120520开课学院:计算机学院考试试卷: A卷 B卷考试形式: 闭卷 开卷,允许带入场考试日期:2013年1月18日,考试时间:120分钟诚信考试,沉着应考,杜绝违纪考生姓名学号所属院系题序123456总分得分评卷人Zhejiang UniversityTheory of Computation,Fall-Winter2012Final Exam(Solution)1.(24%)Determine whether the following statements are true or false.Ifit is truefill a⃝otherwise a×in the bracket before the statement.(a)(⃝)Language{xyz|x,y,z∈{a,b}∗and x=z R and|x|≥1}is regular.(b)(⃝)Let A and B be two regular languages,then A⊕B is also regular,whereA⊕B=(A−B)∪(B−A).(c)(×)Just as Turing Machine’s encoding,every DFA M can also be encoded asstrings“M”,then the language{“M”|DFA M rejects“M”}is regular.(d)(×)Language{a m b n c k d l|m,n,k,l∈N,m≥l and n≤k}is not context free.(e)(×)For languages L1,L2and L3,if L1⊆L2⊆L3and both L1and L3arecontext free,then L2is also context free.(f)(×)k-tapes Turing Machines can decide more languages than1-tape TuringMachines.(g)(⃝)Language{“M”|Turing machine M halts on at least2013inputs}isrecursively enumerable,but not recursive.(h)(⃝)The set of all primitive recursive functions is a proper subset of the setof all recursive functions.(i)(⃝)There exists a language L such that L is recursively enumerable,and Lis recursive.(j)(×)Language{“M”|Turing machine M does not halt on“M”}is recursively enumerable.(k)(⃝)The recursively enumerable languages are closed under intersection,but not closed under complement.(l)(⃝)There are countably many Turing machines,and uncountably many lan-guages,so most languages are not recursively enumerable.2.(20%)Decide whether the following languages are regular or not and provide aformal proof for your answer.(a)L1={a m b n c k|m,n,k∈N and m=n+k}.(b)L2={a m b n c k|m,n,k∈N and(m≡(n+k))mod2}.Solution:(a)L1is not regular.······5ptAssume L1is regular,then L1is also regular,therefore so is L1∩a∗b∗.Let n be the constant whose existence the pumping theorem guarantees.−Choose string w=a n b n∈L1∩a∗b∗,where n∈N and n≥1.So the pumping theorem must hold.−Let w=xyz such that|xy|≤n and y=e,then y=a i where i>0.But then xz=a n−i b n∈L1∩a∗b∗.The theorem fails,therefore L1∩a∗b∗is not regular,hence L1is not regular.······5pt(b)L2is regular.······5ptSince L2can be represented by the following regular expression:(aa)∗((bb)∗b(cc)∗∪(bb)∗(cc)∗c)∪(aa)∗a((bb)∗b(cc)∗c∪(bb)∗(cc)∗).······5pt3.(20%)LetΣ={a,b,c}.Let L3={w|w∈{a,b,c}∗,#b(w)=#c(w)}.Where#z(w)is the number of appearances of the character z in w.For example,the string x=baccabcbcb∈L3,since#b(x)=#c(x)=4.Similarly,the string x=abcaba∈L3,since#b(x)=2and#c(x)=1.(a)Construct a context-free grammar that generates the language L3.(b)Construct a pushdown automata that accepts L3.Solution:(a)The CFG for L3is G=(V,Σ,S,R),where V={S,A,a,b,c},Σ= {a,b,c},and······3ptR={S→bSc|cSb|SS|AS|e,A→aA|e}.······7pt(b)The PDA M=(K,Σ,Γ,∆,s,F)is defined below:K={p,q}Σ={a,b,c}Γ={S,A,a,b,c}s=pF={q}(q,σ,β)(p,γ) (p,e,e)(q,S) (q,e,S)(q,aSb) (q,e,S)(q,bSa) (q,e,S)(q,SS) (q,e,S)(q,AS) (q,e,S)(q,e) (q,e,A)(q,Aa) (q,e,A)(q,e) (q,e,a)(q,a) (q,e,b)(q,b) (q,e,c)(q,c)······10pt4.(20%)The functionφ:N→N given byφ(x)={x,if x<84x+1,if x≥8(a)Try to construct a Turing Machine to compute the functionφ(x).When describ-ing the Turing machines,you can use the elementary Turing machines described in textbook.Always assume that the Turing machines start computation from the configuration◃⊔x where x is represented by binary string,i.e.x∈{0,1}∗.(b)Show that the functionφ(x)is primitive recursive.Solution:(a)We can design the following Turing Machine to computeφ(x):······10pt(b)Sinceφ(x)can be expressed byφ(x)=(x<8)·x+(1∼(x<8))·(4x+1)where x<8is a primitive recursive predicate and x and4x+1are primitive recursive,therefore so isφ(x).······10pt5.(16%)LetL4={“M1”“M2”|M1and M2are TMs,both M1and M2halt on the string ab}.(a)Show that L4is recursively enumerable.An informal description suffices.(b)Show that L4is not recursive.Solution:(a)On input“M1”“M2”,we can use Universal Turing machine to simulate both M1and M2on the string ab.If both M1and M2halt then we halt and“M1”“M2”∈L4,otherwise continuous to simulation and the Universal Turing machine U always check the halting computation of M1and M2on string ab.Hence,L4is recursively enumerable.······10pt(b)We show that if there were an algorithm for L4,then there would be an algo-rithm for solving the unsolvable halting problem H={“M”|M halts on e}.Assume L4is decidable.Then,there exists a TM T that decides L4.We can construct T H that decides H using T:T H(“M”):1.Construct TM M1:Input y,if y=ab reject;otherwise,simulateM on e,and if M halts on e,accept.2.Construct TM M2:Input y,if y=ab and y=e reject;otherwise,simulate M on e,and if M halts on e,accept.3.Simulate T on“M1”“M2”.4.If T accepts“M1”“M2”,accept.5.If T rejects“M1”“M2”,reject.Then L(M1)={ab}if M halts on e;L(M1)=∅otherwise.L(M2)={e,ab}if M halts on e;L(M2)=∅otherwise.This correctly decides H.If“M”∈H,then M halts on e,then L(M1)={ab}, and L(M2)={e,ab},hence both M1and M2halt on ab,so T accepts“M1“”M2”and then T H accepts“M”in step4.If“M”∈H,then M does not halt on e,then neither M1nor M2halts on ab.So,T rejects“M1“”M2”and then T H rejects in step5.But the halting language H is known to be undecidable,this is a contradiction.Thus our assumption that there was a machine T deciding L4must have been incorrect.There is no machine deciding L4.L4is not recursive.······6ptEnjoy your Spring Festival!。
2016-----2017学年度第二学期期末15级计算机班英语试题(卷)温馨提示:(1)本试题分客观题和主观题两大类,总分100分。
(2)客观题答案请写在答题卷内,考试结束不缴客观题部分页。
I.语音知识:从A、B、C、D四个选项中找出其划线部分与所给单词 (10’)( )1. rude A. human B. huge C. June D. customer( )2. Maybe A. forget B. response C. welcome D. Bless( )3. correct A .God B. nod C. person D. only( )4. native A. Polite B. life C. holiday D. switch( )5. Southern A. soup B. enough C. Proud D. cough( )6. post A. focus B. positive C. position D. bottom( ) 7. hopes A.jeans B. story C.boys D. cats( ) 8. Support A. Student B. Usually C. Succeed D. upset( ) 9. Trouble A. loudly B. Enough C. Found D. proud( ) 10.father A. thank B. wealthy C. three D withII、单项选择题:( 30’)( )1.We can’t afford a big house.A. To buyB.buyC.buyingD.to buying( )2.He pretended when his mother came back.A.readingB.to readC.to be readingD.to be read( )3.What impressed me most was that they never lost .A.heartsB.heartC.their heartD.their hearts( )4.Let the children go away. They are making too muchHere.A.noiseB.voiceC.noisyD.sound( )5.--Whose room is this? --It’s .A.Li MingB.Li Ming’sC.Li MingD.Li Mings’( )6.Australia is English-speaking country.A.aB.anC.theD./( )7.We should look after old.A these B/ C.the D.an( )8.He stole the money and they put him .A. In prisonB.to prisonC.at the prisonD.in the prison( )9.Please turn to .A.page 11B.the 11st pageC.the page 11D.page the 11th( )10.The story happened . A.in 1960’s B.in his 60’s C.in 60’s D.in the 1960’s( )11. Workers in the factory are men,others are women.A.two thirdB.two thirdsC.two threeD.two threes( )12.The little boy won’t go to sleep his mother tells him a story.A.orB.unlessC.butD.whether( )13.The artist was born poor, he remained poor all his life.A.andB.orC.butD.so( )14.Leave your key with a neighbor ,you lock yourself out one day.A.ever sinceB.even ifC.soon afterD.in case( )15.Engines are to cars hearts are to animals.A.asB.thatC.whatD.which( )16. Will be sent to Germany for the training.A.I,you and heB.He,I and youC. You, she and ID.I, you and they( )17. Student in the class made some suggestions except Mary.A.EveryB.Each ofC.AnotherD.All the( )18.This pair of glasses is too dark.Could you show meA.the othersB.another oneC.the otherD.another pair( )19.Which is the ,the train station,the bus station or the airport?A.farB.fartherC.farthestD.more far( )20. We work, we feel.A.The more;the happierB.More; happierC.The much; the happierD.Much; more happyIII、阅读理解:(10’)阅读下列短文,从每题所给的A、B、c、D四个选项中,选出最恰当的答案AIn 1993 an unknown American called Clarence Nash went to see the filmmaker Walt D isney. He had an unusual voice and he wanted to work in Disney’s cartoon(动画片) fil m for children. When Walt Disney heard Nash’s voice, he said ‛Stop! That’s our duc k!‛The duck was the now-famous Donald Duck, who first appeared in 1934 in the firm T he Wise Little Hen. Donald lived in an old houseboat(水上住家) and wore his sailor ja cket and hat. Later that year he became a star after an eight – minute Mickey Mouse film. The cinema audience liked him because he was lazy and greedy(贪婪的), and becau se he lost his temper (发脾气) very quickly. And they loved his voice when he became angry with Mickey’s eight nephews(侄子). Soon Donald was more popular than Mickey Mo use himself, probably because he wasn’t a goody-goody like Mickey.In the 1930S, ‘ 40s and ‘ 50s Donald and his friends Mickey, Goofy and Pluto mad e hundreds of Disney cartoons. He also made educational films about the place of theUSA in the world, and safety in the home. Then in 1966 Donald Duck and his voice disa ppeared – there were no more new cartoons.Clarence Nash died in February, 1985. But today’s children can still see the old cartoons on television and hear that famous voice.( )1. Who made Donald Duck film? ______A. Mickey Mouse.B. Clarence Nash.C. Walt Disney.D. Pluto.( )2. When was the first Donald Duck film made? ______A. In 1933.B. In 1934.C. In 1966.D. In 1930.( )3. Who was Clarence Nash? ______A. A cartoonist.B. Donald Duck’s voice.C. A film-maker.D. A film star.( )4. Where do today’s children see Donald Duck ? ______A. In new film.B. At the cinema.C. On television.D. At concerts.( )5. The underlined word ‛audience‛ in the second paragraph means______ .A. readsB. formal interviewC. law freedomD. the people who watch a film at a cinemaBMany children use the Internet to get useful knowledge and information, and to re lax in their free time. But some of them are not using in a good way. Here are some r ules to make sure you are safe and have fun on the Internet.Make rules for Internet use with your parents. For example, when you can go onlin e, for how long and what activities you can go online.Don’t give your password (密码) to anyone else, and never leak out the following information---your real name, home address, age, school, phone number or other person al information.Check with your parents before giving out a credit (信用) card number.Never send a photo of yourself to someone in e-mail unless your parents say it’s OK.Check with your parents before going into a chat room. Different chat rooms have different rules and attract different kinds of people. You and your parents must make sure it’s a right place for you.Never agree to meet someone you met on the Internet without your parent’s permiss ion (允许). Never meet anyone you met on line alone.Always remember that people online may not be who they say they are. Treat everyo ne online as strangers.If something you see or read online makes you uncomfortable, leave the site. Tell a parent or teacher right away.Treat other people as you’d like to be treated. Never use bad language.Remember—not everything you read on the Internet is true.( )6. If you want a true friend on the Internet , you can ____________ .A tell the people what your name is .B meet the people on line alone.C write an e-mail about yourself .D get your parent’s permission.( )7. It’s good for children to ________ on the Internet.A. give password to othersB. get useful knowledge and informationC. give out a credit card numberD. go into a chat room as they’d like to( )8. The underlined phrase ‚leak out‛ in the third paragraph may mean ‚____ ____.‛A. give awayB. leave outC. give outD. put away( )9. If your parents don’t agree, never ________.A. read anything on the InternetB. relax in your free timeC. have a face-to face meeting with anyone you met onlineD. treat other people as you’d like to be treated( )10. This passage is mainly about ‚________‛.A. How to use ComputersB. Surfing on the InternetC. Information on the InternetD. Internet Safety RulesIV、完形填空:(10’)One of Charlie Chaplin's most famous films was "The Gold Rush" The film was set in California in the middle of the 1 century. At that time, gold was discovered in California and thousands of people 2 there to look for gold, so it became 3 as "the gold rush" People said gold could 4 be picked up by washing sand from the river in a pan of water. This was known as "panning for gold"In the film, Chaplin and his friend are in California. So far, they have been 5 in their search for gold and have no money at all. They 6 in a snow storm in a small wooden house. They have 7 They are so hungry that they 8 a pair of shoes, by boiling them in a pan of water. Chaplin sits down 9 the table and eats the shoe. He makes it seem as if this is one of the 10 meals that he has ever enjoyed.1.A.nineteen B.ninetieth C.nineteenth D.ninth2.A.went B.left C.climb D.found3.A.famous B.known C.wonderful D.great4.A.hard B.easily C.difficulty D.slowly5.A.unhappy B.unsuccessfully C.unlucky D.unluckily6.A.have got B.meet C.are caught D.live7.A.a little food B.some water C.nothing D.nothing to eat8.A.wear B.cook C.make D.mend 9.A.at B.by C.near D.beside10.A.biggest B.dearest C.cheapest D.most delicious(交卷页)2016-----2017学年度第二学期期末试题(卷)15级计算机班英语班级姓名总分(客观题答题页)I、语音知识题:(每小题1分,共10分)1--5 6--10II、单项选择题:(每小题1.5分,共30分)1--5 6--1011--15 16--20III、阅读理解题:(每小题1分,10分)1--5 6--10IV、完形填空题:(每小题1分,10分)1--5 6--10V、完成句子:(10分)1. No matter what we said, he p______(假装)that he knew nothing about it.2. The a________( 观众) enjoyed every minute of the performance.3. The naughty boy ________(承认)that did it with his father’s help.4. Sorry,I can’t e__________(解释)why I am engaged in that job.5. The best way to practice English is to talk with a n_______( 本国的) speaker.6、 It is p_______(礼貌的)to offer seats to the old on the bus.7、 When swimming, you should put s_______(安全)first.8、 The newly-opened museum is certainly w_______(值得)a visit.9、 Could you please l_______(借)me your dictionary?10、 Please accept our best w_______(祝愿)for your exams. VI、改错题:从每题A、B、C、D划线处找出一处有错误的选项,填入题后相应的括号内,并在横线上写出正确答案. (10分)1、I like driving, but I don’t dare drive in the desert.A B C D2. It is so a good chance that we mustn’t miss it.A B C D3. Although the task is difficult, but we’ll have it finished soon.A B C D4. Please let me to do it for both of youA B C D5. I wish I can speak English so that I can express my idea clearly.A B C D1. ( ) 应为_________2. ( ) 应为 __________3. ( ) 应为___________4. ( ) 应为 _________5. ( ) 应为 _________VII 、翻译句子:(20分)1)、汉译英:1、老师分发了试卷。
计算机英语试题一、词汇(选择一个最合适的词汇,将对应的英文字母填入空格内。
每题1分,共10分)1、____ refers to the parts of the computer that you can see and touch.A. SoftwareB. HardwareC. HardshipD. Instruction2、primary memory which is stored on chips located ____.A. on the motherboardB. outsideC. inside the processorD. on the CPU3、The display screen is the most common ____ device used to show you what the computer is doing.A. inputB. printingC. outputD. electronic4、Windows gives you more control over the ____ you work.A. operationB. wayC. energyD. power5、The most important program on any computer is ____.A. Operating SystemB. VirusC. softwareD. Office 20006、There are ____ separate products that form the Windows 2000。
A. only oneB. twoC. threeD. four7、C might best be ____ as a 'medium-level language'.A. developedB. decodedC. programmedD. described8、Anti-Virus protects your computer from viruses by ____ your computer's memory and disk devices.A. deletingB. changingC. scanningD. replacing9、Multimedia will become increasingly ____ throughout every aspect of our lives.A. passB. preciseC. permitD. pervasive10、Communication through the Internet, the____performs the reverse function.A. A station controller (STACO)B. DTEC. Data communications equipment (DCE)D. CRT一、词汇(选择一个最合适的词汇,将对应的英文字母填入空格内。
诚信应考 考出水平 考出风格浙江大学城市学院2015 — 2016 学年第 一 学期期末考试试卷《大学计算机应用基础 》开课单位: 计算学院 ;考试形式:闭卷;考试时间:_2016__年_1__月_12_日; 所需时间: 120 分钟注:请把答案写在答卷上。
一. 单项选择题 (本大题共__50__题,每题__1__分,共___50___分。
) 1. 在计算机领域中,通常用英文单词“BYTE ”来表示_________。
A.二进制位B.字C.字节D.字长2. 当今的计算机已经能够处理文字、声音、图形图像等信息,这要归功于信息的__________。
A.娱乐化B.网络化C.电子化D.数字化3.现在通用的编码方案是UCS 的子集(UCS-2),即Unicode 编码,基本覆盖了世界上主要的语言文字。
它的编码长度为16位,即每个字符占用两个字节,共可表示________字符? A.65536个B.131072个C.262144个D.1114112个4.6位二进制数最大能表示的十进制整数是________。
A.32B.128C.256D.635.条码信息由条和空的不同宽度和位置来表示,__________则传递的信息量越大。
A .条码越宽,条码印刷的精度越高 B .条越多,空越少 C. 条越少,空越多 D. 条和空越均衡6.计算思维最根本的内容是_________。
A.抽象与计算B.概括与计算C.抽象与自动化D.计算与思考7.数据库管理系统又称为______。
A.DOSB.UPSC.DXSD.DBMS8.下列关于栈的叙述正确的是______。
A.栈按"先进先出"组织数据 B.栈按"先进后出"组织数据 C.只能在栈底插入数据D.不能删除数据9.下列叙述中正确的是______。
A.栈不是一种线性表B.队列是"先进后出"的线性表C.队列是非线性结构D.有序线性表既可以采用顺序存储结构,也可以采用链式存储结构10.用于描述内存性能优劣的两个重要指标是______。
浙江大学历年机试真题2011 A+B forMatricesGrading MedianGraduateAdmission2010 A+B ZOJ问题奥运排序问题最短路径问题二叉搜索树2009 xxx定律ZOJ 继续xxx定律寻找大富翁找出直系亲属2008 又一版A+B欧拉回路继续畅通工程魔咒词典毕业bg2007 最小长方形统计字符游船出租EXCEL排序畅通工程最大报销额2006 还是A+B 火星A+B 还是畅通工程统计同成绩学生人数简单计算器2005 A + B 最大连续子序列畅通工程开门人和关门人排名2011年题目1001:A+B for Matrices时间限制:1 秒内存限制:32 兆特殊判题:否提交:2490 解决:1130题目描述:This time, you are supposed to find A+B where A and B are two matrices, and then count the number of zero rows and columns.输入:The input consists of several test cases, each starts with a pair of positive integers M and N (≤10) which are the number of rows and columns of the matr ices, respectively. Then 2*M lines follow, each contains N integers in [-100, 100], separated by a space. The first M lines correspond to the elements of A and the second M lines to that of B.The input is terminated by a zero M and that case must NOT be processed.输出:For each test case you should output in one line the total number of zero rows and columns of A+B.样例输入:2 21 11 1-1 -110 92 31 2 34 5 6-1 -2 -3-4 -5 -6样例输出:15题目1002:Grading题目描述:Grading hundreds of thousands of Graduate Entrance Exams is a hard work. It is even harder to design a process to make the results as fair as possible. One way is to assign each exam problem to 3 independent experts. If they do not agree to each other, a judge is invited to make the final decision. Now you are asked to write a program to help this process.For each problem, there is a full-mark P and a tolerance T(<P) given. The grading rules are: • A problem will first be assigned to 2 experts, to obtain G1 and G2. If the differenc e is within the tolerance, that is, if |G1 - G2| ≤ T, this problem's grade will be the average of G1 and G2.• If the difference exceeds T, the 3rd expert will give G3.• If G3 is within the tolerance with either G1 or G2, but NOT both, then this p roblem's grade will be the average of G3 and the closest grade.• If G3 is within the tolerance with both G1 and G2, then this problem's grade will be the maximum of the three grades.• If G3 is within the tolerance with neither G1 nor G2, a judge will give the final grade GJ.输入:Each input file may contain more than one test case.Each case occupies a line containing six positive integers: P, T, G1, G2, G3, and GJ, as described in the problem. It is guaranteed that all the grades are valid, that is, in the interval [0, P]. 输出:For each test case you should output the final grade of the problem in a line. The answer must be accurate to 1 decimal place.样例输入:20 2 15 13 10 18样例输出:14.0题目1004:Median题目描述:Given an increasing sequence S of N integers, the median is the number at the middle position. For example, the median of S1={11, 12, 13, 14} is 12, and the median of S2={9, 10, 15, 16, 17} is 15. The median of two sequences is defined to be the median of the non-decreasing sequence which contains all the elements of both sequences. For example, the median of S1 and S2 is 13.Given two increasing sequences of integers, you are asked to find their median.输入:Each input file may contain more than one test case.Each case occupies 2 lines, each gives the information of a sequence. For each sequence, the first positive integer N (≤1000000) is the size of that sequence. Then N integers follow, separated by a space.It is guaranteed that all the integers are in the range of long int.输出:For each test case you should output the median of the two given sequences in a line.样例输入:4 11 12 13 145 9 10 15 16 17样例输出:13题目1005:Graduate Admission题目描述:It is said that in 2011, there are about 100 graduate schools ready to proceed over 40,000 applications in Zhejiang Province. It would help a lot if you could write a program to automate the admission procedure.Each applicant will have to provide two grades: the national entrance exam grade GE, and the interview grade GI. The final grade of an applicant is (GE + GI) / 2. The admission rules are: • The applicants are ranked according to their final grades, and will be admitted one by one from the top of the rank list.• If there is a tied final grade, the applica nts will be ranked according to their national entrance exam grade GE. If still tied, their ranks must be the same.• Each applicant may have K choices and the admission will be done according to his/her choices: if according to the rank list, it is one's turn to be admitted; and if the quota of one's most preferred shcool is not exceeded, then one will be admitted to this school, or one's other choices will be considered one by one in order. If one gets rejected by all of preferred schools, then this unfortunate applicant will be rejected.• If there is a tied rank, and if the corresponding applicants are applying to the same school, then that school must admit all the applicants with the same rank, even if its quota will be exceeded.输入:Each input file may contain more than one test case.Each case starts with a line containing three positive integers: N (≤40,000), the total number of applicants; M (≤100), the total number of graduate schools; and K (≤5), the number of choices an applicant may have.In the next line, separated by a space, there are M positive integers. The i-th integer is the quota of the i-th graduate school respectively.Then N lines follow, each contains 2+K integers separated by a space. The first 2 integers are the applicant's GE and GI, respectively. The next K integers represent the preferred schools. For the sake of simplicity, we assume that the schools are numbered from 0 to M-1, and the applicants are numbered from 0 to N-1.输出:For each test case you should output the admission results for all the graduate schools. The results of each school must occupy a line, which contains the applicants' numbers that school admits. The numbers must be in increasing order and be separated by a space. There must be no extra space at the end of each line. If no applicant is admitted by a school, you must output anempty line correspondingly.样例输入:11 6 32 1 2 2 2 3100 100 0 1 260 60 2 3 5100 90 0 3 490 100 1 2 090 90 5 1 380 90 1 0 280 80 0 1 280 80 0 1 280 70 1 3 270 80 1 2 3100 100 0 2 4样例输出:0 1035 6 72 81 42010题目1003:A+B题目描述:给定两个整数A和B,其表示形式是:从个位开始,每三位数用逗号","隔开。
浙江大学2015-2016学年秋冬学期
研究生《计算理论》课程期终考试试卷
考试形式:闭卷,考试时间:2016年1月15日,所需时间:120分钟
学号:姓名:专业:任课教师:金小刚题序1234567总分
得分
评卷人
Zhejiang University
Theory of Computation,Fall-Winter2015
Final Exam
1.(20%)Determine whether the following statements are true or false.If
it is true write a⃝otherwise a×in the bracket before the statement.
(a)()Let L be any regular language.Then the number of equivalence classes
respect to language L(i.e.x≈L y,if for all z∈Σ∗,xz∈L iffyz∈L)isfinite.
(b)()The language{a n b n w|w∈{a,b}∗,n∈N,and|w|=2n}is context-free.
(c)()The language{“M”“w”|M accepts w in less than2016steps}is not
recursive.
(d)()The language{“M”|M is a TM and L(M)is Context-free but L(M)is
not regular}is not recursive.
(e)()The language{“M1”“M2”|M1and M2are TMs,and M1halts on e but
M2doesn’t halt on e}is recursively enumerable,but not recursive.
(f)()The set of all primitive recursive functions is a proper subset of the set of
allµ-recursive functions.
(g)()Let A and B be two disjoint recursively enumerable languages.If A∪B
is also be recursively enumerable,then it is possible that neither A nor B is
decidable.
(h)()Let H10={“M”|M is a TM and10∈L(M)}andτ1andτ2are recursive
functions.If H10≤τ1L and H10≤τ2L,then L is recursive enumerable but not
recursive.
(i)()Suppose SAT≤P L and L∈P.Then P=NP.
(j)()Let H={“M”“w”|TM M halts on input string w},then H is NP-complete.
2.(18%)On F A and Regular Languages
Say whether each of the following languages is regular or not regular?Prove your answers.
(a)L1={w|w∈{0,1}∗and w has an equal number of0s and1s}.
(b)L2={w|w∈{0,1}∗and w has an equal number of01s and10s}.
3.(20%)On PDA and Context-Free Languages
Let L3={wca m b n|w∈{a,b}∗,where w=w R,and m,n∈N,n≤m≤2n}.
(a)Give a context-free grammar for the language L3.
(b)Design a PDA M=(K,Σ,Γ,∆,s,F)accepting the language L3.
Solution:(a)
(b)The PDA M=(K,Σ,Γ,∆,s,F)is defined below:
(q,σ,β)(p,γ)
K={}
Σ={a,b,c}
Γ={}
s=
F={}
4.(18%)On Undecidability
Classify whether each of the following languages are recursive,recursively enumerable but-not-recursive,or non-recursively-enumerable.Prove your answers,but you may not simply appeal to Rice’s theorem.
(a)L4={“M”|M is a Turing Machine,and|L(M)|>2}.
(b)L5={“M”|M is a Turing Machine,and|L(M)|≤2}.
5.(15%)On P and NP Problems
In an undirected graph G=(V,E),a Sovereign set is a vertex subset S⊆V such every edge in E has at most one endpoint in S.Let Sovereign Set={(G,k):
G is an undirected graph that contains a sovereign set of at least k vertices}.
(a)Give the definition of the class P and NP.
(b)Show that Sovereign Set is a NP problem.
(c)Prove that Sovereign Set is NP-complete.You may reduce from Clique
problem.
6.(9%)On Computability and Computational Complexity
(a)Draw a diagram illustrating the relations between P,NP,recursive,recursively
enumerable(r.e.),co-r.e.on the hypothesis that P=NP,where co-r.e.is the set of languages that its complement is recursively enumerable;
(b)Try to mark the languages H,H,H1and H1in the given diagram in part(a),
where H={“M”“w”|Turing Machine M halts on w}and H1={“M”|Turing Machine M halts on“M”},respectively.
Enjoy your Spring Festival!。