下一代防火墙选型指南
- 格式:pdf
- 大小:900.53 KB
- 文档页数:15

6-1华为Eudemon1000E-N 下一代防火墙华为Eudemon1000E-N 下一代防火墙Eudemon1000E-N 下一代防火墙随着互联网技术的不断发展,智能手机、iPad 等终端被更多地应用到办公中,移动应用程序、Web2.0、社交网络应用于生产生活的方方面面。
网络边界变得模糊,信息安全问题日益复杂。
传统的安全网关通常只能通过IP 和端口进行安全防护,难以完全应对层出不穷的应用威胁和Web 威胁。
Eudemon1000E-N 系列是华为公司为解决运营商、企业、政府、数据中心等机构的网络安全问题自主研发的下一代防火墙产品。
它基于业界领先的软、硬件体系架构,通过对应用、用户、威胁、时间、位置的全面感知,将网络环境清晰的映射为业务环境。
在应用识别的基础上提供精准的管控能力,融合了IPS 攻击防护、AV 防病毒、URL 过滤,Web 内容过滤,反垃圾邮件和邮件过滤等行业领先的专业安全技术,支持IPv6防护及过渡技术,为用户提供强大、可扩展、持续的安全能力。
在运营商、政府、金融、电力、石油、教育、工业制造等行业得到广泛应用。
下一代防火墙,地址才能“应用(Application )、时间(Time )、用户多个维度解析企业的业务流量,并结合各种维度进行、行为识别等技术手段,准确识别超过6000个网络应用。
• 用户:通过Radius 、LDAP 、AD 等8种用户识别手段,将流量中的IP 地址与现实世界中的用户信息联系起来。
基于用户对网络流量进行管控。
• 威胁:支持超过5000+特征的攻击检测和防御。
支持Web 攻击识别和防护,如跨站脚本攻击、SQL注入攻击等。
可以识别和防范SYN flood 、UDP flood 等10+种DDoS 攻击,识别500多万种病毒。
采用基于云的URL 分类过滤,预定义的URL 分类库已超过8500万,阻止访问恶意网站带来的威胁。
• 位置:与全球位置信息结合,识别流量及威胁发起的位置信息;使用流量地图和威胁地图快速发现异常,进而制定对应的防护策略。
网康下一代防火墙上线指南
网康下一代防火墙
简易上线指南
1、网线插入设备MGT口
2、浏览器输入:https://192.168.1.23
3、用户名:admin
4、密码:ngfw2012
5、进入设备依次后点击网络设置--->接口与区域-- 物理接口
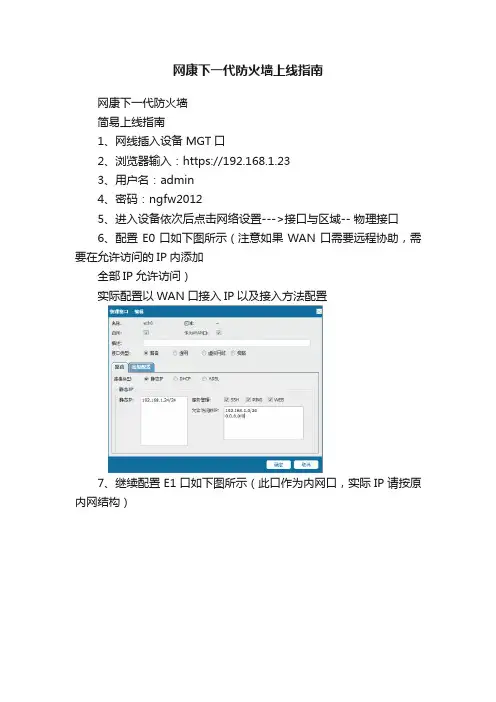
6、配置E0口如下图所示(注意如果WAN口需要远程协助,需要在允许访问的IP内添加
全部IP允许访问)
实际配置以WAN口接入IP以及接入方法配置
7、继续配置E1口如下图所示(此口作为内网口,实际IP请按原内网结构)
8、左边列表选择静态路由设置,点击新建,建立通用默认路由(下一跳IP如果有网关,就指向网关,如果设备自己是网关,不用设置静态路由)
9、如果需要开启LAN内的DHCP,左边列表内设置DHCP功能
10、进入策略配置安全策略然后新建如下图
选择源地址或者目的地址,然后选择新建地址,如下图(做一个全局地址)
选择刚建立的地址(源地址与目的地址都相同)
11、进入地址转换(NAT)新建,按如下设置
12、最后,系统管理的基本配置里把DNS设置好
13、好了,以上设置基本可以上网了。
记得点击右上角的生效。
14、右上角的保存设置是你确认当前配置没问题后,就可以点保存了,否则没有保存的设置在设置重启后将会丢失。

Hillstone山石网科下一代防火墙基础配置手册V5.5版本Hillstone Networks Inc.服务热线:400 828 6655内容提交人审核人更新内容日期陈天骄陈天骄初次编写2016/1/14目录1 设备管理 (3)1.1 终端console登录 (3)1.2 网页WebUI登录 (3)1.3 恢复出厂设置 (5)1.3.1 CLI命令行操作 (5)1.3.2 WebUI图形化界面操作 (5)1.3.3 硬件CLR操作 (6)1.4 设备系统(StoneOS)升级 (6)1.4.1 通过sysloader升级 (6)1.4.2 通过CLI升级 (9)1.4.3 通过WebUI升级 (9)1.5 许可证安装 (10)1.5.1 CLI命令行安装 (10)1.5.2 WebUI安装 (11)2 基础上网配置 (11)2.1 接口配置 (11)2.2 路由配置 (13)2.3 策略配置 (14)2.4 源地址转换配置(SNAT) (15)3 常用功能配置 (16)3.1 PPPoE拨号配置 (16)3.2 动态地址分配(DHCP)配置 (17)3.3 IP-MAC地址绑定配置 (20)3.4 端到端IPSec VPN配置 (21)3.4.1 配置第一阶段P1提议 (22)3.4.2 配置ISAKMP网关 (23)3.4.3 配置第二阶段P2提议 (24)3.4.4 配置隧道 (25)3.4.5 配置隧道接口 (26)3.4.6 配置隧道路由和策略 (28)3.4.7 查看VPN状态 (29)3.5 远程接入SCVPN配置 (30)3.6 目的地址转换DNAT配置 (38)3.6.1 IP映射 (39)3.6.2 端口映射 (41)1设备管理安全网关支持本地与远程两种环境配置方法,可以通过CLI 和WebUI 两种方式进行配置。
CLI同时支持Console、Telnet、SSH等主流通信管理协议。
网康下一代防火墙
简易上线指南
1、网线插入设备MGT口
2、浏览器输入:https://192.168.1.23
3、用户名:admin
4、密码:ngfw2012
5、进入设备依次后点击网络设置--->接口与区域-- 物理接口
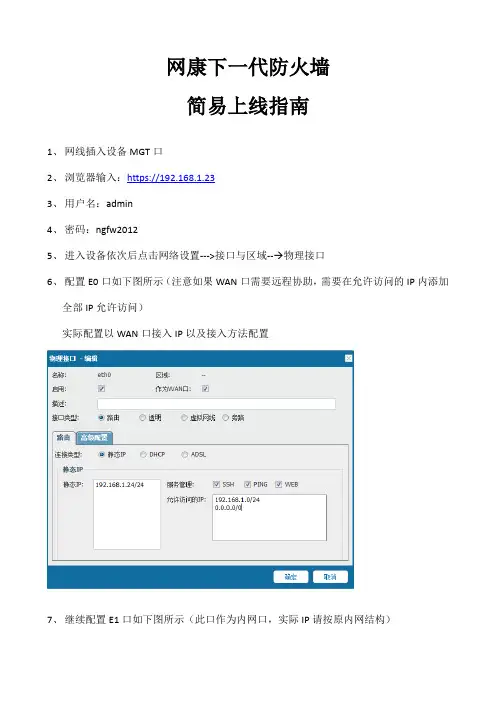
6、配置E0口如下图所示(注意如果WAN口需要远程协助,需要在允许访问的IP内添加
全部IP允许访问)
实际配置以WAN口接入IP以及接入方法配置
7、继续配置E1口如下图所示(此口作为内网口,实际IP请按原内网结构)
8、左边列表选择静态路由设置,点击新建,建立通用默认路由(下一跳IP如果有网关,就指向网关,如果设备自己是网关,不用设置静态路由)
9、如果需要开启LAN内的DHCP,左边列表内设置DHCP功能
10、进入策略配置 安全策略然后新建如下图
选择源地址或者目的地址,然后选择新建地址,如下图(做一个全局地址)
选择刚建立的地址(源地址与目的地址都相同)
11、进入地址转换(NAT)新建,按如下设置
12、最后,系统管理的基本配置里把DNS设置好
13、好了,以上设置基本可以上网了。
记得点击右上角的生效。
14、右上角的保存设置是你确认当前配置没问题后,就可以点保存了,否则没有保存的设置在设置重启后将会丢失。

如何选购下一代企业防火墙作者:作者 Zeus Kerravala 编译:陈琳华来源:《计算机世界》 2019年第19期选择下一代防火墙(NGFW)时,性能、外形和自动化功能是关键的考虑因素。
防火墙已存在多年,并且随着威胁形势的变化,这一技术也在不断发展。
以下是一些在选购下一代防火墙(NGFW)中需要注意的技巧,以便选购的防火墙能够满足企业当前和未来的业务需求。
不要信任防火墙性能统计信息要明白NGFW 的运行方式需要的不仅仅是查看供应商的规范或是让一些流量流经它们。
当流量负载较轻时,大多数防火墙都能正常运行。
重要的是要了解防火墙如何响应大规模流量,尤其是在加密被打开时。
目前大约80%的流量都是加密的,防火墙在处理大量加密流量时维持性能水平的能力至关重要。
此外, 请确保在测试期间打开所有主要功能(包括应用程序和用户识别、IPS、反恶意软件、URL 过滤和日志记录),以查看防火墙在生产环境中的表现。
防火墙供应商经常吹嘘的性能是在关闭核心功能后的单一性能。
市场研究公司ZKResearch 的数据显示,许多IT 专业人员都是在费尽一番周折后才学到这一教训的。
58%的安全专家称,为了保持性能,他们不得不关闭一些功能。
在向供应商提交订单之前,请确保使用尽可能多的不同类型流量和各种类型应用程序展开测试。
要查看的重要指标包括应用程序吞吐量、每秒连接数、IPv4 和IPv6 的最大会话数以及SSL性能。
NGFW 需要适应更广泛的安全平台最佳策略或与单一供应商合作是否可以提供更好的安全性?这个问题多年来一直存在争议。
事实是,这两种方法都不完美。
重要的是要清楚各个地方的最佳策略并不能确保一流的安全性。
拥有太多供应商会导致出现无法管理的复杂性,从而使公司面临风险。
更好的方法是采用安全平台,可以将其视为一种开放式架构,能够插入第三方产品。
任何NGFW 都必须能够插入到平台之中,以便它们能够“看到”从物联网端点到云流量再到最终用户设备的所有内容。

下一代防火墙使用手册第一章:引言随着信息技术的迅猛发展,网络安全问题日益凸显,网络攻击事件层出不穷,为保护企业网络的安全,下一代防火墙成为不可或缺的一环。
本手册旨在帮助用户了解和使用下一代防火墙,提高网络安全防护能力。
第二章:下一代防火墙概述2.1 下一代防火墙的定义下一代防火墙是一种集成了传统防火墙、入侵检测系统、应用程序控制和其他安全功能于一体的网络安全设备。
它可以实现对网络流量、应用程序和用户行为的深度检测和防护。
2.2 下一代防火墙的特点(1)应用层识别:能够识别和控制各种应用程序的访问行为。
(2)多维度防护:结合网络安全、应用层安全、行为安全等多个维度进行综合防护。
(3)威胁情报整合:集成威胁情报,实时更新恶意软件和攻击信息。
2.3 下一代防火墙的优势(1)提供深度安全:能够深入识别和阻断各种网络威胁和攻击。
(2)有效管理应用程序:灵活控制和管理各类网络应用程序的访问和使用。
(3)提升网络性能:能够快速有效地过滤和处理大量网络流量。
第三章:下一代防火墙的部署与配置3.1 部署架构根据网络规模和需求确定下一代防火墙的部署位置,一般可以部署在边界网关、数据中心、分支机构等位置,构建多层次、多维度的网络安全防护体系。
3.2 设备连接连接下一代防火墙的各个接口,包括内部网络、外部网络、DMZ等,配置接口地址及路由信息。
3.3 安全策略配置根据实际需求,配置安全策略,包括访问控制、应用程序控制、反病毒、反垃圾邮件等安全功能。
3.4 VPN 配置如需部署 VPN 服务,配置 VPN 策略、隧道和用户认证等参数。
第四章:下一代防火墙的管理与维护4.1 系统管理对下一代防火墙进行管理和维护,包括设备初始化、软件升级、日志备份、系统监控等功能。
4.2 安全管理监测和分析安全事件,对发现的攻击威胁进行处置和应对。
4.3 策略优化定期对安全策略进行调整和优化,提升防护能力,保障网络安全。
第五章:应急响应与排查5.1 安全事件响应在发生安全事件时,迅速进行安全事件的诊断、核实和处置,减少安全事件造成的损失。

传统防火墙与下一代防火墙的比较与选择防火墙是保护网络安全的重要设备之一,它通过监控和控制进出网络的数据流,起到阻止潜在威胁的作用。
然而,随着网络攻击手段的不断进化,传统防火墙在应对高级威胁和新型攻击方式时可能显得力不从心。
于是,下一代防火墙应运而生,提供更强大的安全性和更灵活的应用控制。
本文将比较传统防火墙和下一代防火墙的优缺点,以及在选择防火墙时的考虑因素。
一、传统防火墙传统防火墙主要基于规则集的匹配,用于检查网络流量并决定是否允许通过。
它可以实现基本的网络访问控制,比如根据源IP地址、目标IP地址、端口号等进行过滤。
传统防火墙可以提供基本的安全性,但存在以下缺点:1. 缺乏应用层识别能力:传统防火墙无法深入分析应用层数据,难以检测和阻止隐藏在应用层数据中的恶意代码或攻击行为。
2. 固定的规则集:传统防火墙的规则集通常是事先定义好的,难以适应复杂的网络环境和不断变化的威胁情况。
同时,配置和管理传统防火墙的规则集也很繁琐。
3. 难以应对高级威胁:传统防火墙在应对高级威胁,如零日攻击和高级持续性威胁(APT)时效果有限。
攻击者可以利用传统防火墙的漏洞绕过检测,对网络进行渗透。
二、下一代防火墙下一代防火墙继承了传统防火墙的基本功能,同时引入了一系列新的安全特性,以满足日益复杂的网络环境和威胁情况。
下一代防火墙相较传统防火墙具有以下优点:1. 应用层识别与控制:下一代防火墙具备深度包检测技术,能够分析应用层协议,并根据具体的应用程序进行精确的访问控制。
它可以识别并阻止潜在的恶意应用和攻击行为。
2. 基于用户的访问控制:下一代防火墙可以根据用户身份和角色来管理访问权限,实现更细粒度的访问控制。
通过身份验证和访问策略的配合,可以保护敏感数据免受未经授权的访问。
3. 全面的威胁防御:下一代防火墙集成了威胁情报、入侵防御系统(IDS)和虚拟私人网络(VPN)等功能,提供全面的威胁防御能力。
它可以检测和阻止零日攻击、恶意软件传播、网络钓鱼等威胁行为。
SANGFOR深信服下⼀代防⽕墙介绍(AF-1120AF-1210)国内下⼀代防⽕墙第⼀品牌深信服下⼀代防⽕墙(Next-Generation Application Firewall)NGAF是⾯向应⽤层设计,能够精确识别⽤户、应⽤和内容,具备完整安全防护能⼒,能够全⾯替代传统防⽕墙,并具有强劲应⽤层处理能⼒的全新⽹络安全设备。
NGAF解决了传统安全设备在应⽤识别、访问控制、内容安全防护等⽅⾯的不⾜,同时开启所有功能后性能不会⼤幅下降。
区别于传统的⽹络层防⽕墙,NGAF具备L2-L7层的协议的理解能⼒。
不仅能够实现⽹络层访问控制的功能,且能够对应⽤进⾏识别、控制、防护,解决了传统防⽕墙应⽤层控制和防护能⼒不⾜的问题。
区别于传统DPI技术的⼊侵防御系统,深信服NGAF具备深⼊应⽤内容的威胁分析能⼒,具备双向的内容检测能⼒为⽤户提供完整的应⽤层安全防护功能。
同样都能防护web攻击,与web应⽤防⽕墙关注web应⽤程序安全的设计理念不同,深信服下⼀代防⽕墙NGAF关注web系统在对外发布的过程中各个层⾯的安全问题,为对外发布系统打造坚实的防御体系。
关键指标(产品参数可能有改动,以深信服公司公告为准)功能参数项⽬具体功能部署⽅式⽀持⽹关、⽹桥、旁路和混杂模式;实时监控实时提供CPU、内存、磁盘占⽤率、会话数、在线⽤户数、⽹络接⼝的鞥设备资源信息;提供安全事件信息,包括最近安全事件、服务器安全事件、终端安全事件等,事件信息提供发⽣事件、源IP、⽬的IP、攻击类型以及攻击的URL等;提供实时智能模块间联动封锁的源IP 以便实现动态智能安全管理;⽹络适应性⽀持静态路由、RIP v1/2、OSPF、策略路由;⽀持ARP、域名解析、DHCP中继、DHCP 服务器、DHCP客户端等IP服务;包过滤与状态检测提供静态的包过滤和动态包过滤功能;⽀持的应⽤层报⽂过滤,包括:应⽤层协议:FTP、HTTP、SMTP、RTSP、H.323(Q.931,H.245,RTP/RTCP)、SQLNET、MMS、PPTP等;传输层协议:TCP、UDP;NAT地址转换⽀持多个内部地址映射到同⼀个公⽹地址、多个内部地址映射到多个公⽹地址、内部地址到公⽹地址⼀⼀映射、源地址和⽬的地址同时转换、外部⽹络主机访问内部服务器、⽀持DNS 映射功能;可配置⽀持地址转换的有效时间;⽀持多种NAT ALG,包括DNS、FTP、H.323、SIP等抗攻击特性可防御Land、Smurf、Fraggle、WinNuke、Ping of Death、Tear Drop、IP Spoofing、SYN Flood、ICMP Flood、UDP Flood、DNS Query Flood等多种DOS/DDOS攻击IPSEC VPN ⽀持AES、DES、3DES、MD5、SHA1、DH、RC4等算法,并且⽀持扩展国密办SCB2等其他加密算法⽀持MD5及SHA-1验证算法;⽀持各种NAT⽹络环境下的VPN组⽹;⽀持第三⽅标准IPSec VPN进⾏对接;*总部与分⽀有多条线路,可在线路间⼀⼀进⾏IPSecVPN 隧道建⽴,并设置主隧道及备份隧道,对主隧道可进⾏带宽叠加、按包或会话进⾏流量平均分配,主隧道断开备份隧道⾃动启⽤,保证IPSecVPN 连接不中断;可为每⼀分⽀单独设置不同的多线路策略;单臂部署下同样⽀持多线路策略;应⽤访问控制策略⽀持应⽤2000种以上的应⽤动作的应⽤识别;⽀持应⽤更新版本后的主动识别和控制的应⽤智能识别;提供基于应⽤识别类型、⽤户名、接⼝、安全域、IP地址、端⼝、时间进⾏应⽤访问控制列表的制定;⼆层协议⽀持802.3、AX25、802.2等多种⼆层协议过滤威胁检测⽀持基于特征匹配、协议异常检测、智能应⽤识别等⽅式针对已知威胁进⾏检测;⽀持基于威胁关联分析的检测机制,针对未知威胁进⾏分析检测;IPS⼊侵防护(选配)微软“MAPP”计划会员,漏洞特征库: 2800+并获得CVE“兼容性认证证书”,能够⾃动或者⼿动升级;防护类型包括蠕⾍/⽊马/后门/DoS/DDoS攻击探测/扫描/间谍软件/利⽤漏洞的攻击/缓冲区溢出攻击/协议异常/ IPS逃逸攻击等;防护对象分为保护服务器和保护客户端两⼤类,便于策略部署;漏洞详细信息显⽰:漏洞ID、漏洞名称、漏洞描述、攻击对象、危险等级、参考信息、地址等内容;⽀持⾃动拦截、记录⽇志、上传灰度威胁到“云端”服务器防护(选配)⽀持web攻击特征数量1000+;⽀持Web⽹站隐藏,包括HTTP响应报⽂头出错页⾯的过滤,web响应报⽂头可⾃定义;⽀持FTP服务应⽤信息隐藏包括:服务器信息、软件版本信息等;⽀持OWASP定义10⼤web安全威胁,保护服务器免受基于Web应⽤的攻击,如SQL注⼊防护、XSS攻击防护、CSRF攻击防护、⽀持根据⽹站登录路径保护⼝令暴⼒破解;⽀持web站点扫描、web站点结构扫描、漏洞扫描等扫描防护;可严格控制上传⽂件类型,检查⽂件头的特征码防⽌有安全隐患的⽂件上传⾄服务器,并⽀持结合病毒防护、插件过滤等功能检查⽂件安全性;⽀持指定URL的⿊名单、加⼊排除URL⽬录,ftp弱⼝令防护、telnet 弱⼝令防护等功能;敏感信息防泄漏内置常见敏感信息的特征,且可⾃定义敏感信息特征,如⽤户名、密码、邮箱、⾝份证信息、MD5密码等,可⾃定义具有特殊特征的敏感信息;⽀持正常访问http连接中⾮法敏感信息的外泄操作;⽀持数据库⽂件敏感信息检测,防⽌数据库⽂件被“拖库”、“暴库”;风险评估⽀持服务器、客户端的漏洞风险评估功能,⽀持对⽬标IP进⾏端⼝、服务扫描;⽀持ftp、mysql、oracle、mssql、ssh、RDP、⽹上邻居NetBIOS、VNC等多种应⽤的弱⼝令评估与扫描;风险评估可以实现与FW、IPS、服务器防护模块的智能策略联动,⾃动⽣成策略;⽹页篡改防护⽹关型⽹页防篡改,⽆需在服务器中安装任何插件;⽀持⽂件⽐对、特征码⽐对、⽹站元素、数字指纹⽐对多种⽐对⽅式,保证⽹站安全;全⾯保护⽹站的静态⽹页和动态⽹页,⽀持⽹页的⾃动发布、篡改检测、应⽤保护、警告和⾃动恢复,保证传输、鉴别、地址访问、表单提交、审计等各个环节的安全,完全实时杜绝篡改后的⽹页被访问的可能性及任何使⽤Web⽅式对后台数据库的篡改;⽀持各级页⾯模糊框架匹配、精确匹配的⽅式适⽤不同的⽹页类型;⽀持提供管理员业务操作界⾯与⽹管管理界⾯分离功能,⽅便业务⼈员更新⽹站内容;⽀持通过替换、重定向等技术⼿段,防护篡改页⾯;⽹站维护管理员必须通过短信认证才可进⾏⽹站更新业务操作(选配);⽀持短信报警、邮件报警、控制台报警等多种篡改报警⽅式;病毒防护(选配)⽀持基于流引擎查毒技术,可以针对HTTP、FTP、SMTP、POP3等协议进⾏查杀;能实时查杀⼤量⽂件型、⽹络型和混合型等各类病毒;并采⽤新⼀代虚拟脱壳和⾏为判断技术,准确查杀各种变种病毒、未知病毒;内置10万条以上的病毒库,并且可以⾃动或者⼿动升级;检测到病毒后⽀持记录⽇志、阻断连接;Web安全防护对⽤户web⾏为进⾏过滤,保护⽤户免受攻击;⽀持只过滤HTTP GET、HTTP POST、HTTPS 等应⽤⾏为;并进⾏阻断和记录⽇志;⽀持针对上传、下载等操作进⾏⽂件过滤;⽀持⾃定义⽂件类型进⾏过滤;⽀持基于时间表的策略制定;⽀持的处理动作包括:阻断和记录⽇志;⽀持基于签名证书的ActiveX过滤;⽀持添加⽩名单和合法⽹站列表;⽀持基于应⽤类型的ActiveX过滤,如视频、在线杀毒、娱乐等;⽀持基于操作类型的脚本过滤,如注册表读写、⽂件读写、变形脚本、威胁对象调⽤、恶意图⽚等;流量管理⽀持同时连接多条外⽹线路,且⽀持多线路复⽤和智能选路技术;⽀持将多条外⽹线路虚拟映射到设备上,实现对多线路的分别流控;⽀持基于应⽤类型、⽹站类型、⽂件类型的带宽划分与分配;⽀持时间和IP的带宽划分与分配;⽤户管理⽀持基于⽤户名/密码、单点登陆以及基于IP地址、MAC地址、计算机名的识别等多种认证⽅式;⽀持AD域结合、Proxy、POP3、web 表单等多种单点登陆⽅式,简化⽤户操作;*可强制指定⽤户、指定IP段的⽤户必须使⽤单点登录;⽀持添加到指定本地组、临时账号和不允许新⽤户认证等新⽤户认证策略;⽀持强制AD域认证,指定⽤户必须⽤AD域账户登录操作系统,否则禁⽌上⽹;认证成功的⽤户⽀持页⾯跳转,包括最近请求页⾯、管理员制定URL、注销页⾯等;⽀持CSV格式⽂件导⼊、扫描导⼊和从外部LDAP服务器上导⼊等账户导⼊⽅式;⽤户分组⽀持树形结构,⽀持⽗组、⼦组、组内套组等组织结构;⽹关管理⽀持SSL加密WEB⽅式管理设备;⽀持邮件、短信(可扩展)等告警⽅式,可提供管理员登陆、病毒、IPS、web攻击以及⽇志存储空间不⾜等告警设置;提供图形化排障⼯具,便于管理员排查策略错误等故障;提供路由、⽹桥、旁路等部署模式的配置引导,提供保护服务器、保护内⽹⽤户上⽹安全、保证内⽹⽤户上⽹带宽、保证遭到攻击及时提醒和保留证据等⽹关应⽤场景的配置引导,简化管理员配置;⽇志管理与报表提供端⼝、服务、漏洞、弱密码等安全风险评估报表;提供DOS攻击、web防护、IPS、病毒、web威胁、⽹站访问、应⽤控制、⽤户登录、系统操作等多种安全⽇志查询;提供可定义时间内安全趋势分析报表;⽀持⾃定义统计指定IP/⽤户组/⽤户/应⽤在指定时间段内的服务器安全风险、终端安全风险等内容,并形成报表;⽀持将统计/趋势等报表⾃动发送到指定邮箱;⽀持导出安全统计/趋势等报表,包括⽹页、PDF等格式;。

下一代防火墙解决方案目录1 网络现状 (3)2 解决方案 (9)2.1 网络设备部署图 (9)2.2 部署说明 (9)2.3 解决方案详述 (9)2.3.1 流量管理 (10)2.3.2 应用控制 (12)2.3.3 网络安全 (12)3 报价 (25)1 网络现状随着网络技术的快速发展,现在我们对网络安全的关注越来越重视。
近几年来,计算机和网络攻击的复杂性不断上升,使用传统的防火墙和入侵检测系统(IDS)越来越难以检测和阻挡。
漏洞的发现和黑客利用漏洞之间的时间差也变得越来越短,使得IT和安全人员得不到充分的时间去测试漏洞和更新系统。
随着病毒、蠕虫、木马、后门和混合威胁的泛滥,内容层和网络层的安全威胁正变得司空见惯。
复杂的蠕虫和邮件病毒诸如Slammer、Blaster、Sasser、Sober、MyDoom 等在过去几年经常成为头条新闻,它们也向我们展示了这类攻击会如何快速的传播——通常在几个小时之内就能席卷全世界。
许多黑客正监视着软件提供商的补丁公告,并对补丁进行简单的逆向工程,由此来发现漏洞。
下图举例说明了一个已知漏洞及相应补丁的公布到该漏洞被利用之间的天数。
需要注意的是,对于最近的一些攻击,这一时间已经大大缩短了。
IT和安全人员不仅需要担心已知安全威胁,他们还不得不集中精力来防止各种被称之为“零小时”(zero-hour)或“零日”(zero-day)的新的未知的威胁。
为了对抗这种新的威胁,安全技术也在不断进化,包括深度包检测防火墙、应用网关防火墙、内容过滤、反垃圾邮件、SSL VPN、基于网络的防病毒和入侵防御系统(IPS)等新技术不断被应用。
但是黑客的动机正在从引起他人注意向着获取经济利益转移,我们可以看到一些更加狡猾的攻击方式正被不断开发出来,以绕过传统的安全设备,而社会工程(social engineering)陷阱也成为新型攻击的一大重点。
图:系统漏洞被黑客利用的速度越来越快带有社会工程陷阱元素的攻击包括间谍软件、网络欺诈、基于邮件的攻击和恶意Web站点等。

下一代防火墙方案引言在当前互联网环境下,网络安全问题日趋严峻。
传统的防火墙方案已经无法满足对信息安全的要求,因此亟需研究和开发下一代防火墙方案,以更好地应对新兴的安全威胁。
1. 传统防火墙的局限性传统防火墙主要采用基于端口、IP地址和协议的访问控制策略,而这种方法已经无法满足当前复杂多变的网络环境和威胁。
以下是传统防火墙的局限性:•无法检测加密流量:传统防火墙只能检测明文流量,而无法对加密的流量进行实时检测。
•无法识别应用层协议:传统防火墙只能基于端口和协议进行访问控制,而无法对应用层协议进行精确识别。
•无法对内部威胁进行防范:传统防火墙主要关注来自外部网络的威胁,而对于内部网络的威胁缺乏有效防范措施。
2. 下一代防火墙的基本特征为了克服传统防火墙的局限性,下一代防火墙应具备以下基本特征:2.1 深度包检测下一代防火墙应能够对加密的流量进行深度包检测,以便于发现隐藏在流量中的恶意行为。
通过引入深度包检测技术,下一代防火墙可以突破传统防火墙只能检测明文流量的限制,提高网络安全性。
2.2 应用层智能下一代防火墙应具备强大的应用层智能,能够对应用层协议进行细粒度的识别和控制。
通过深入理解应用层协议的特征,下一代防火墙可以对协议规范之外的行为进行实时检测,从而提高安全性和灵活性。
2.3 内部网络安全下一代防火墙应对内部网络的威胁给予足够的关注。
通过采用内部威胁检测和内部网络隔离等技术手段,下一代防火墙可以提供全方位的网络安全防护,避免内部网络成为攻击者入侵的桥头堡。
3. 下一代防火墙的技术手段为了实现上述基本特征,下一代防火墙可采用以下技术手段:3.1 深度学习技术深度学习技术具有强大的模式识别和学习能力,可以用于恶意流量检测和应用层协议识别。
通过建立深度学习模型,下一代防火墙可以对网络流量进行实时分类和分析,从而实现更精确的威胁检测和防御。
3.2 可编程数据平面下一代防火墙应引入可编程数据平面技术,使其能够更灵活地处理各类网络流量。

Huawei USG6330/6350/6360 next-generation firewalls are security gateways designed for small- and medium-sized businesses and branch offices with 200 to 800 users. The firewalls provide VPN, intrusion prevention, and antivirus functions for comprehensive and integrated network protection, effectively reducing management costs. Refined bandwidth management improves bandwidth efficiency and ensures quality experiences for key services. These firewalls provide continuous next-generation network security in an easy and efficient way.HighlightsComprehensive and integrated protection• Multiple security functions, including firewall, VPN, intrusion prevention, and online behavior management,for complete versatility• Refined bandwidth management based on application and website category to prioritize bandwidth formission-critical services• Detection and prevention of unknown threats, such as zero-day attacks, using sandboxing and thereputation system*Simple management and rapid deployment• Zero-configuration deployment using USB disks to improve deployment efficiency• Predefined common-scenario defense templates to facilitate security policy deployment • Intelligent detection of redundant and invalid policies• Supports cloud-based management and enables Huawei Agile Controller-Cloud Manager to manage andconfigure the firewalls Flexible bandwidth management, improving Internet access experience•Differentiated user bandwidth and quota management for fair and prioritized bandwidth usageHUAWEI USG6330/6350/6360 Next-Generation Firewalls---Securely and Reliably Connect Small- and Medium-Sized Businesses• Application-based bandwidth management to prioritize bandwidth for mission-critical applications• Modification of URL category priorityDeploymentSecure interconnections between enterprise branches• Inspect services in six dimensions (application, user, content, threat, time, and location) and provide refined service access control at the Internet egress.• Establish IPsec or L2TP over IPsec permanent tunnels for branches and partners with fixed VPN gateways (L2TP over IPsec tunnel is recommended if account authentication is required).• Provide SSL VPN for remote access of people on the move and implement fine-grained control over the resources accessible to users.• Authenticate VPN tunnel users to ensure they are legitimate and authorized.• Enable intrusion prevention, antivirus, file blocking, and data filtering functions to prevent remote access users from introducing network threats or leaking information.HardwareUSG6330/6350/6360Interfaces1. USB Port2. Console Port3. 1 x GE (RJ45) Management Port4. 4 x GE (RJ45) Ports5. 2 x GE (Combo) PortsTable 1. Wide Service Interface Cards (WSICs) for USG6300 SeriesSoftware Features1: I f no hard disk is inserted, you can view and export system and service logs. By inserting a hard disk, you can also view, export, customize, and subscribe to reports.Functions marked with * are supported only in USG V500R001 and later versions.Specifications *System Performance and Capacity1. P erformance is tested under ideal conditions based on RFC 2544 and RFC 3511. The actual result may vary with deployment environments.2. Antivirus, IPS, and SA performances are measured using 100 KB of HTTP files.3. Throughput is measured with the Enterprise Traffic Model.4. SSL inspection throughput is measured with IPS-enabled and HTTPS traffic using TLS v1.2 with AES256-SHA.5. SSL VPN throughput is measured using TLS v1.2 with AES128-SHA.6. USG6000 V100R001 supports only the RESTCONF interface and cannot interwork with sandbox or third-party tools.* SA indicates Service Awareness.* This content is applicable only to regions outside mainland China. Huawei reserves the right to interpret this content. Hardware Specifications*WISC is not hot-swappable.CertificationsRegulatory, Safety, and EMC ComplianceOrdering GuideAbout This PublicationThis publication is for reference only and does not constitute any commitments or guarantees. All trademarks, pictures, logos, and brands mentioned in this document are the property of Huawei Technologies Co., Ltd. or a third party.For more information, visit /en/products/enterprise-networking/security.Copyright©2018 Huawei Technologies Co., Ltd. All rights reserved.。
Organizations of all sizes depend on their networks to access internal and external mission-critical applications. As advances in networking continueto provide tremendous benefits, organizations are increasingly challenged by sophisticated and financially-motivated attacks designed to disrupt communication, degrade performance and compromise data. Malicious attacks penetrate outdated stateful packet inspection firewalls with advanced application layer exploits. Point products add layers of security, but are costly, difficult to manage, limited in controlling network misuse and ineffective against the latest multipronged attacks.By utilizing a unique multi-core design and patented Reassembly-Free Deep Packet Inspection® (RFDPI) technology*, the Dell™ SonicWALL™ Network Security Appliance (NSA) Series of Next-Generation Firewalls offers complete protection without compromising network performance. The low latency NSA Series overcomes the limitations of existing security solutions by scanning the entirety of each packet for current internal and external threats in real-time. The NSA Series offers intrusion prevention, malware protection, and application intelligence, control and visualization, while delivering breakthrough performance. With advanced routing, stateful high-availability and high-speed IPSec and SSL VPN technology, the NSA Series adds security, reliability, functionality and productivity to branch offices, central sites and distributed mid-enterprise networks, while minimizing cost and complexity.Comprised of the Dell SonicWALL NSA 220, NSA 220 Wireless-N, NSA 250M, NSA 250M Wireless-N, NSA 2400, NSA 3500 and NSA 4500, the NSA Series offers a scalable range of solutions designed to meet the network security needs of any organization.Network SecurityAppliance SeriesNext-Generation Firewall• Next-Generation Firewall• Scalable multi-core hardware andReassembly-Free Deep PacketInspection• Application intelligence, controland visualization• Stateful high availability and loadbalancing• High performance and loweredtco• Network productivity• Advanced routing services andnetworking• Standards-based Voice over IP(VoIP)• Dell Sonicwall clean Wireless• onboard Quality of Service (QoS)• Integrated modules support• Border Gateway Protocol (BGP)support• More concurrent SSL VPN sessionsFeatures and benefitsNext-Generation Firewall features integrate intrusion prevention, gateway anti-virus, anti-spyware and URL filtering with application intelligence and control, and SSL decryption to block threats from entering the network and provide granular application control without compromising performance.Scalable multi-core hardware and Reassembly-Free Deep Packet Inspection scans and eliminates threats of unlimited file sizes, with near-zero latency across thousands of connections at wire speed.Application intelligence, control and visualization provides granular control and real-time visualization of applications to guarantee bandwidth prioritization and ensure maximum network security and productivity. Stateful high availability and load balancing features maximize total network bandwidth and maintain seamless network uptime, delivering uninterrupted access to mission-critical resources, and ensuring that VPN tunnels and other network traffic will not be interrupted in the event of a failover. High performance and lowered tcoare achieved by using the processingpower of multiple cores in unison todramatically increase throughput andprovide simultaneous inspectioncapabilities, while lowering powerconsumption.Network productivity increases becauseIT can identify and throttle or blockunauthorized, unproductive andnon-work related applications and websites, such as Facebook® or YouTube®,and can optimize WAN traffic whenintegrated with Dell SonicWALL WANAcceleration Appliance (WXA) solutions.Advanced routing services andnetworking features incorporate 802.1qVLANs, multi-WAN failover, zone andobject-based management, loadbalancing, advanced NAT modes, andmore, providing granular configurationflexibility and comprehensive protectionat the administrator’s discretion.Standards-based Voice over IP (VoIP)capabilities provide the highest levels ofsecurity for every element of the VoIPinfrastructure, from communicationsequipment to VoIP-ready devices suchas SIP Proxies, H.323 Gatekeepers andCall Servers.Dell SonicWALL clean Wirelessoptionally integrated into dual-bandwireless models or via Dell SonicWALLSonicPoint wireless access pointsprovides powerful and secure 802.11a/b/g/n 3x3 MIMO wireless, and enablesscanning for rogue wireless accesspoints in compliance with PCI DSS.onboard Quality of Service (QoS)features use industry standard 802.1pand Differentiated Services Code Points(DSCP) Class of Service (CoS)designators to provide powerful andflexible bandwidth management that isvital for VoIP, multimedia content andbusiness-critical applications.Integrated modules support on NSA250M and NSA 250M Wireless-Nappliances reduce acquisition andmaintenance costs through equipmentconsolidation, and add deploymentflexibility.Border Gateway Protocol (BGP)support enables alternate networkaccess paths (ISPs) if one path fails.More concurrent SSL VPN sessions addscalability, while extending End PointControl to Microsoft® Windows® devicesensures anti-malware and firewalls areup-to-date.Best-in-class threat protection Dell SonicWALL deep packetinspection protects against network risks such as viruses, worms, Trojans, spyware, phishing attacks, emerging threats and Internet misuse. Application intelligence and control adds highly controls to prevent data leakage and manage bandwidth at the application level.The Dell SonicWALL Reassembly-Free Deep Packet Inspection (RFDPI) technology utilizes Dell SonicWALL’s multi-corearchitecture to scan packets in real-time without stalling traffic in memory.This functionality allows threats to be identified and eliminated over unlimited file sizes and unrestricted concurrent connections, without interruption.The Dell SonicWALL NSA Series provides dynamic network protection through continuous, automated security updates, protecting against emerging and evolving threats, without requiring any administrator intervention.Dynamic security architectureand managementMobile users32Application intelligence and control Dell SonicWALL Application Intelligence and Control provides granular control, data leakage prevention, and real-time visualization of applications to guarantee bandwidth prioritization and ensure maximum network security and productivity. An integrated feature of Dell SonicWALL Next-Generation Firewalls, it uses Dell SonicWALL RFDPItechnology to identify and control applications in use with easy-to-use pre-defined application categories (such as social media or gaming)—regardless of port or protocol. Dell SonicWALL Application Traffic Analytics provides real-time and indepth historical analysis of data transmitted through the firewall including application activities by user.1Dell SonicWALL clean VPNDell SonicWALL Clean VPN™ secures the integrity of VPN access for remote devices including those running iOS or Android by establishing trust for remote users and these endpoint devices and applying anti-malware security services, intrusion prevention and application intelligence and control to eliminate the transport of malicious threats• The SonicWALL NSA 2400 is ideal for branch office and small- to medium-sized corporate environments concerned about throughput capacity and performance • The SonicWALL NSA 220, NSA 220 Wireless-N, NSA 250M and NSA 250M Wireless-N are ideal for branch office sites in distributed enterprise, small- to medium-sizedbusinesses and retail environmentscentralized policy managementThe Network Security Appliance Series can be managed using the SonicWALL Global Management System, which provides flexible, powerful and intuitive tools to manage configurations, viewreal-time monitoring metrics andintegrate policy and compliancereporting and application traffic analytics,all from a central location.Server Anti-Virusand Anti-SpywareServers anti-threatprotectionVPNVPNClientRemoteAccessUpgradeServiceWeb siteand contentusage control Enforced ClientAnti-Virusand Anti-SpywareClient PCs anti-threat protectionFlexible, customizable deployment options –NSA Series at-a-glanceEvery SonicWALL Network Security Appliance solution delivers Next-Generation Firewall protection, utilizing a breakthrough multi-core hardware design and Reassembly-Free Deep Packet Inspection for internal and external network protection without compromising network performance. Each NSA Series product combineshigh-speed intrusion prevention, file and content inspection, and powerful application intelligence and controlwith an extensive array of advanced networking and flexible configuration features. The NSA Series offers an accessible, affordable platform that is easy to deploy and manage in a wide variety of corporate, branch office and distributed network environments.• The SonicWALL NSA 4500 is ideal for large distributed and corporate central-site environments requiring high throughput capacity and performance • The SonicWALL NSA 3500 is idealfor distributed, branch office and corporate environments needing significant throughput capacity and performanceSecurity services andupgradesGateway Anti-Virus,Anti-Spyware, IntrusionPrevention and ApplicationIntelligence and controlService delivers intelligent,real-time network security protectionagainst sophisticated application layerand content-based attacks includingviruses, spyware, worms, Trojans andsoftware vulnerabilities such as bufferoverflows. Application intelligence andcontrol delivers a suite of configurabletools designed to prevent data leakagewhile providing granular application-level controls along with tools enablingvisualization of network traffic.Enforced client Anti-Virusand Anti-spyware (McAfee)working in conjunction withDell SonicWALL firewalls,guarantees that allendpoints have the latest versions ofanti-virus and anti-spyware softwareinstalled and active.content Filtering Serviceenforces protection andproductivity policies byemploying an innovativerating architecture, utilizingadynamic database to block up to 56categories of objectionable webcontent.Analyzer is a flexible, easyto use web-basedapplication traffic analyticsand reporting tool thatprovides powerful real-time andhistorical insight into the health,performance and security of the network.Virtual Assist is a remotesupport tool that enablesa technician to assumecontrol of a PC or laptopfor the purpose of providingremote technical assistance. Withpermission, the technician can gaininstant access to a computer using aweb browser, making it easy to diagnoseand fix a problem remotely without theneed for a pre-installed “fat” client.Dynamic Support Servicesare available 8x5 or 24x7depending on customerneeds. Features includeworld-class technicalsupport, crucial firmware updates andupgrades, access to extensive electronictools and timely hardware replacementto help organizations get the greatestreturn on their Dell SonicWALLinvestment.Global VPN clientUpgrades utilize a softwareclient that is installed onWindows-based computersand increase workforce productivity byproviding secure access to email, files,intranets, and applications for remoteusers.provide clientlessLinux-based systems. With integratedSSL VPN technology, Dell SonicWALLfirewall appliances enable seamless andsecure remote access to email, files,intranets, and applications from a varietyof client platforms via NetExtender, alightweight client that is pushed onto theuser’s machine.SonicWALL Mobile connect™,a single unified client app forApple® iOS and Google®Android™, provides smartphone andtablet users superior network-levelaccess to corporate and academicresources over encrypted SSL VPNconnections.comprehensive Anti-SpamService (CASS) offerssmall- to medium-sizedbusinesses comprehensiveprotection from spam andviruses, with instant deployment overexisting Dell SonicWALL firewalls. CASSspeeds deployment, eases administrationand reduces overhead by consolidatingsolutions, providing one-click anti-spamservices, with advanced configuration injust ten minutes.Deep Packet Inspection for of SSL-Encrypted traffic (DPI-SSL) transparentlydecrypts and scans both inbound andoutbound HTTPS traffic for threats usingDell SonicWALL RFDPI. The traffic is thenre-encrypted and sent to its originaldestination if no threats or vulnerabilitiesare discovered.Denial of Service attack prevention 22 classes of DoS, DDoS and scanning attacksKey exchange K ey Exchange IKE, IKEv2, Manual Key, PKI (X.509), L2TP over IPSec Route-based VPN Yes (OSPF, RIP)Certificate support Verisign, Thawte, Cybertrust, RSA Keon, Entrust, and Microsoft CA for Dell SonicWALL-to-Dell SonicWALL VPN, SCEP Dead peer detection Yes DHCP over VPN Yes IPSec NAT TraversalYes Redundant VPN gatewayYesGlobal VPN client platforms supported Microsoft Windows 2000, Windows XP, Microsoft Vista 32/64-bit, Windows 7 32/64-bitSSL VPN platforms supportedMicrosoft Windows 2000 / XP / Vista 32/64-bit / Windows 7, Mac 10.4+, Linux FC 3+ / Ubuntu 7+ / OpenSUSEMobile Connect platforms supported iOS 4.2 and higher, Android 4.0 and higherSecurity servicesDeep Packet Inspection Service Gateway Anti-Virus, Anti-Spyware, Intrusion Prevention and Application Intelligence and Control Content Filtering Service (CFS) HTTP URL,HTTPS IP, keyword and content scanning ActiveX, Java Applet, and cookie blocking bandwidth management on filtering categories, allow/forbid lists Gateway-enforced Client Anti-Virus and Anti-Spyware McAfee Comprehensive Anti-Spam Service Supported Application Intelligence Application bandwidth management and control, prioritize or block application and Control by signatures, control file transfers, scan for key words or phrasesDPI SSL Provides the ability to decrypt HTTPS traffic transparently, scan this traffic for threats using Dell SonicWALL’s Deep Packet Inspection technology (GAV/AS/IPS/ Application Intelligence/CFS), then re-encrypt the traffic and send it to its destination if no threats or vulnerabilities are found. This feature works for both clients and workingIP Address assignment Static, (DHCP, PPPoE, L2TP and PPTP client), Internal DHCP server, DHCP relay NAT modes1:1, 1:many, many:1, many:many, flexible NAT (overlapping IPs), PAT, transparent modeVLAN interfaces (802.1q) 25352550200Routing OSPF, RIPv1/v2, static routes, policy-based routing, MulticastQoS Bandwidth priority, maximum bandwidth, guaranteed bandwidth, DSCP marking, 802.1pIPv6Yes AuthenticationXAUTH/RADIUS, Active Directory, SSO, LDAP, Novell, internal user database, Terminal Services, Citrix Internal database/single sign-on users 100/100 Users150/150 Users250/250 Users300/500 Users1,000/1,000 UsersVoIPFull H.323v1-5, SIP, gatekeeper support, outbound bandwidth management, VoIP over WLAN, deep inspection security, full interoperability with most VoIP gateway and communications devicesSystemZone security Yes SchedulesOne time, recurring Object-based/group-based management Yes DDNSYesManagement and monitoring Web GUI (HTTP, HTTPS), Command Line (SSH, Console), SNMP v3: Global management with Dell SonicWALL GMSLogging and reporting Analyzer, Local Log, Syslog, Solera Networks, NetFlow v5/v9, IPFIX with extensions, real-time visualizationHigh availabilityOptional Active/Passive with State SyncLoad balancing Yes, (Outgoing with percent-based, round robin and spill-over); (Incoming with round robin,random distribution, sticky IP, block remap and symmetrical remap)StandardsTCP/IP, UDP, ICMP, HTTP, HTTPS, IPSec, ISAKMP/IKE, SNMP, DHCP, PPPoE, L2TP, PPTP, RADIUS, IEEE 802.3Wireless standards802.11 a/b/g/n, WPA2, WPA, TKIP, 802.1x, EAP-PEAP, EAP-TTLS WAN acceleration supportYesFlash memory32 MB compact Flash 512 MB compact Flash3G wireless/modem * With 3G/4G USB adapter or modem — With 3G/4G USB adapter or modemPower supply 36W external Single 180W ATX power supplyFansNo fan/1 internal fan 2 internal fans 2 fansPower input10-240V, 50-60Hz Max power consumption 11W/15W 12W/16W 42W 64W 66W Total heat dissipation 37BTU/50BTU 41BTU/55BTU 144BTU 219BTU 225BTUCertificationsVPNC, ICSA Firewall 4.1 EAL4+, FIPS 140-2 Level 2, VPNC, ICSA Firewall 4.1, IPv6 Phase 1, IPv6 Phase 2Certifications pending EAL4+, FIPS 140-2 Level 2, IPv6 Phase 1, IPv6 Phase 2 —Form factor 1U rack-mountable/ 1U rack-mountable/ 1U rack-mountable/ and dimensions 7.125 x 1.5 x 10.5 in/ 17 x 10.25 x 1.75 in/ 17 x 13.25 x 1.75 in/18.10 x 3.81 x 26.67 cm 43.18 x 26 x 4.44 cm 43.18 x 33.65 x 4.44 cmWeight 1.95 lbs/0.88 kg/ 3.05 lbs/1.38 kg/ 8.05 lbs/ 3.65 kg 11.30 lbs/ 5.14 kg2.15 lbs/0.97 kg3.15 lbs/1.43 kg WEEE weight V 3.05 lbs/1.38 kg/4.4 lbs/2.0kg/ 8.05 lbs/ 3.65 kg 11.30 lbs/5.14 kg3.45 lbs/1.56 kg4.65 lbs/2.11 kgMajor regulatoryF CC Class A, CES Class A, CE, C-Tick, VCCI, Compliance MIC, UL, cUL, TUV/GS, CB, NOM, RoHS, WEEE Environment 40-105° F, 0-40° C 40-105° F, 5-40° CMTBF 28 years/15 years 23 years/14 years 14.3 years 14.1 years 14.1 yearsHumidity5-95% non-condensing 10-90% non-condensingcertificationsSpecificationsTesting methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services. Full DPI Performance/Gateway AV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs. Actual maximum connection counts are lower when Next-Generation Firewall services are enabled. VPN throughput measured using UDP traffic at 1280 byte packet size adhering to RFC 2544. Supported on the NSA 3500 and higher. Not available on NSA 2400. *USB 3G card and modem are not included. See http://www.Dell /us/products/cardsupport.html for supported USB devices. The Comprehensive Anti-Spam Service supports an unrestricted number of users but is recommended for 250 users or less. With Dell SonicWALL WXA Series Appliance.Network Security Appliance 3500 01-SSC-7016NSA 3500 TotalSecure* (1-year) 01-SC-7033Network Security Appliance 450001-SSC-7012NSA 4500 TotalSecure* (1-year) 01-SC-7032Network Security Appliance 2400 01-SSC-7020NSA 2400 TotalSecure* (1-year) 01-SC-7035Network Security Appliance 250M 01-SSC-9755Network Security Appliance 250M Wireless-N 01-SSC-9757 (US/Canada)Network Security Appliance 250M TotalSecure* 01-SSC-9747Network Security Appliance 250M Wireless-N TotalSecure*01-SSC-9748 (US/Canada)Network Security Appliance 220 01-SSC-9750Network Security Appliance 220 Wireless-N 01-SSC-9752 (US/Canada)Network Security Appliance 220 TotalSecure* 01-SSC-9744Network Security Appliance 220 Wireless-N TotalSecure*01-SSC-9745 (US/Canada)For more information on Dell SonicWALL network security solutions, please visit .*Includes one-year of Gateway Anti-Virus, Anti-Spyware, Intrusion Prevention, andApplication Intelligence and Control Service, Content Filtering Service and Dynamic Support 24x7.Security Monitoring Services from Dell SecureWorks are available for thisappliance Series. For more information, visit /secureworks。
Data SheetCisco Firepower Next-Generation Firewall (NGFW) Prevent breaches, get deep visibility to detect and stop threats fast, and automate your network and security operations to save time and work smarter.Model OverviewCisco Firepower 2100 SeriesThe industry’s first midrange NGFWs delivering sustainable performance when threat inspection is enabledCisco Firepower 4100 Series:The industry’s first 1RU NGFWs with 40-GbpsinterfacesCisco Firepower 9300:Ultra-high-performance NGFW, expandable as yourneeds growCisco ASA 5500-X Series:Models for branch offices, industrial applications, and the Internet edgeFirepower NGFWv:The NGFW for virtual and cloud environmentsPlatform Image SupportThe Cisco Firepower NGFW includes Application Visibility and Control (AVC), optional Next-Gen IPS (NGIPS), Cisco® Advanced Malware Protection (AMP) for Networks, and URL Filtering. The Cisco Firepower 2100 Series, 4100 Series, and 9300 appliances use the Cisco Firepower Threat Defense software image. Alternatively, Cisco Firepower 2100 Series, 4100 Series, and 9300 appliances can support the Cisco Adaptive Security Appliance (ASA) software image.Management OptionsCisco Firepower NGFWs may be managed in a variety of ways depending on the way you work, your environment, and your needs.The Cisco Firepower Management Center (formerly FireSIGHT) provides centralized management of the Cisco Firepower NGFW, the Cisco Firepower NGIPS, and Cisco AMP for Networks. It also provides threat correlation for network sensors and Advanced Malware Protection (AMP) for Endpoints.The Cisco Firepower Device Manager is available for local management of 2100 Series and select 5500-X Series devices running the Cisco Firepower Threat Defense software image.The Cisco Adaptive Security Device Manager is available for local management of the Cisco Firepower 2100 Series, 4100 Series, Cisco Firepower 9300 Series, and Cisco ASA 5500-X Series devices running the ASA software image.Cisco Defense Orchestrator cloud-based management is also available for consistent policy management across Cisco security devices running the ASA software image, enabling greater management efficiency for the distributed enterprise.Firepower DDoS MitigationAlso available on the Cisco Firepower 4100 Series and 9300 appliances is tightly integrated, comprehensive, behavioral DDoS mitigation for both network and application infrastructure protection. This DDoS mitigation is Radware’s Virtual DefensePro (vDP). It is available from and supported directly by Cisco.Cisco Firepower 2100 Series AppliancesThe Cisco Firepower 2100 Series is a family of four threat-focused NGFW security platforms that deliver business resiliency through superior threat defense. It offers exceptional sustained performance when advanced threat functions are enabled. These platforms uniquely incorporate an innovative dual multicore CPU architecture that optimizes firewall, crypto graphic, and threat inspection functions simultaneously. The series’ firewall throughput range addresses use cases from the Internet edge to the data center. Network Equipment Building Standards (NEBS)- compliance is supported by the Cisco Firepower 2100 Series platform.Cisco Firepower 4100 Series AppliancesThe Cisco Firepower 4100 Series is a family of four threat-focused NGFW security platforms. Their throughput range addresses data center and internet edge use cases. They deliver superior threat defense, at faster speeds, with a smaller footprint. Cisco Firepower 4100 Series supports flow-offloading, programmatic orchestration, and the management of security services with RESTful APIs. Network Equipment Building Standards (NEBS)-compliance is supported by the Cisco Firepower 4120 platform.Cisco Firepower 9300 Security ApplianceThe Cisco Firepower 9300 is a scalable (beyond 1 Tbps when clustered), carrier-grade, modular platform designed for service providers, high-performance computing centers, large data centers, campuses, high-frequency trading environments, and other environments that require low (less than 5-microsecond offload) latency and exceptional throughput. Cisco Firepower 9300 supports flow-offloading, programmatic orchestration, and the management of security services with RESTful APIs. It is also available in Network Equipment Building Standards (NEBS)-compliant configurations.Cisco ASA 5500-FTD-X Series AppliancesThe Cisco ASA 5500-FTD-X Series is a family of eight threat-focused NGFW security platforms. Their throughput range addresses use cases from the small or branch office to the Internet edge. They deliver superior threat defense in a cost-effective footprint.Cisco Firepower NGFW Virtual (NGFWv) AppliancesCisco Firepower NGFWv is available on VMware, KVM, and the Amazon Web Services (AWS) and Microsoft Azure environments for virtual, public, private, and hybrid cloud environments. Organizations employing SDN can rapidly provision and orchestrate flexible network protection with Firepower NGFWv. As well, organizations using NFV can further lower costs utilizing Firepower NGFWv.Performance Testing MethodologiesCisco uses a variety of testing methodologies in a lab environment to ensure the performance specifications we report are as close to real world as possible. Firewall performance is affected by many factors including network environment, packet sizes, packet type, TLS encryption, and more.Two modes of firewall testing exist: static or real world. Static testing leverages performance and security testing tools in a simulated environment. Real-world testing uses samples of live traffic on a production or side-car network. While static testing does not completely mimic performance in a real-world networking environment, we review and modify the static methodology to ensure the results are as close to real-world as possible.The following are test methodologies used for measurements listed in Table 1. Change in performance vs change in packet size is not linear, so extrapolation from a single test is not possible for the almost unlimited variety of network environments. Testing security efficacy or security service performance under loaded conditions adds even more complexity. For these reasons we rely on the 1024B HTTP Test.1024B HTTP Test (256KB Object)This number is to compare with other vendors at a 256KB object size. It uses a larger and commonly tested packet size for every simulated session. With the protocol overhead, the average frame size is around 1024 bytes. This represents typical production conditions for most firewall deployments.1500B UDP vs 64B UDPThis test uses a transactional UDP profile with either 1500B or 64B frames. Due to the stateless nature of UDP, it creates very little impact on a stateful NGFW. Many vendors use this profile to measure maximum firewall performance, however it is only practical as a comparison point. This test does not represent real-world conditions, therefore Cisco only uses it as a legacy metric for ASA performance. For NGFW products, various UDP packet size should only be used to test latency and not overall performance.Performance Specifications and Feature HighlightsTable 1 summarizes the capabilities of the Cisco Firepower NGFWv, Firepower 2100 Series, and 4100 Series and 9300 appliances as well as the Cisco ASA 5500-FTD-X appliances when running the Cisco Firepower Threat Defense image. All numbers are derived with two-way traffic evaluation to replicate the best security posture.Table 1. Cisco Firepower Threat Defense (FTD) Performance Specifications and Feature Highlights for Physical and Virtual AppliancesNote: Throughput assumes HTTP sessions.Performance will vary depending on features activated, and network traffic protocol mix, packet size characteristics and hypervisor employed (NGFWv). Performance is subject to change with new software releases. Consult your Cisco representative for detailed sizing guidance.Table 2 summarizes the performance and capabilities of the Cisco Firepower 2100, 4100 Series and 9300 appliances when running the ASA image. For Cisco ASA 5500-X Series performance specifications with the ASA image, please visit the Cisco ASA with FirePOWER Services data sheet.Table 2. ASA Performance and Capabilities on Firepower Appliances211021202130214041104120414041509300 9300 9300 9300Newconnections per second 18000 28000 40000 75000 150,000 250,000 350,000 800,000 800,0001.2 million 1.8 million 4 millionIPsec VPN throughput (450B UDP L2L test) 500 Mbps 700 Mbps 1 Gbps 2 Gbps 8 Gbps 10 Gbps 14 Gbps 15 Gbps 15 Gbps 18 Gbps 20 Gbps60 Gbps 3/ 40 GbpsIPsec/Cisco AnyConnect/Apex site-to-site VPN peers 1500 3500 7500 10000 10,000 15,000 20,000 20,000 20,000 20,000 20,000 60,0003/ 20,000Maximum number of VLANs 400 600 750 1024 1024 1024 1024 1024 1024 1024 1024 1024Security contexts (included; maximum) 2; 25 2; 25 2; 30 2; 40 10; 250 10; 250 10; 250 10; 250 10; 250 10; 250 10; 250 10; 250HighavailabilityActive/acti ve and active/sta ndby Active/acti ve and active/sta ndby Active/acti ve and active/sta ndbyActive/a ctive and active/st andby Active/acti ve and active/stan dby Active/acti ve and active/stan dby Active/acti ve and active/stan dby Active/acti ve and active/stan dby Active/acti ve and active/sta ndby Active/acti ve and active/sta ndby Active/acti ve and active/sta ndby Active/acti ve and active/sta ndbyClustering - - --Up to 16 appliances Up to 16 appliances Up to 16 appliances Up to 16 appliances Up to 5 appliances with 3 security modules each Up to 5 appliance s with three security modules each Up to 5 appliance s with three security modules eachUp to 5 appliance s with 3 security modules eachScalability VPN Load BalancingVPN Load Balancing, Firewall ClusteringCentralized management Centralized configuration, logging, monitoring, and reporting are performed by Cisco Security Manager or alternatively in the cloud with Cisco Defense Orchestrator Adaptive Security Device ManagerWeb-based, local management for small-scale deployments1 Throughput measured with 1500B User Datagram Protocol (UDP) traffic measured under ideal test conditions.2“Multiprotocol” refers to a traffic profile consisting primarily of TCP -based protocols and applications like HTTP, SMTP, FTP, IMAPv4, BitTorrent, and DNS. 3In unclustered configuration.Table 3.Operating Requirements for Firepower NGFWv Virtual AppliancesHardware SpecificationsTables 4, 5, and 6 summarize the hardware specifications for the 2100 Series, 4100 Series, and 9300 Series, respectively. Table 7 summarizes regulatory standards compliance. For Cisco ASA 5500-X Series hardware specifications, please visit the Cisco ASA with FirePOWER Services data sheet.Table 4. Cisco Firepower 2100 Series Hardware Specifications1 Dual power supplies are hot-swappable.2 Fans operate in a 3+1 redundant configuration where the system will continue to function with only3 operational fans. The 3 remaining fans will run at full speed.3 FPR-2130 platform is designed to be NEBS ready. The availability of NEBS certification is pending.Table 5. Cisco Firepower 4100 Series Hardware Specifications1 Dual power supplies are hot-swappable.Table 6. Cisco Firepower 9300 Hardware Specifications* Minimum turn-on voltage is -44V DCTable 7. Cisco Firepower 2100 Series, 4100 Series and Cisco Firepower 9300 NEBS, Regulatory, Safety, and EMC ComplianceCisco Trust Anchor TechnologiesCisco Trust Anchor Technologies provide a highly secure foundation for certain Cisco products. They enable hardware and software authenticity assurance for supply chain trust and strong mitigation against a man-in-the-middle compromise of software and firmware.Trust Anchor capabilities include:●Image signing: Cryptographically signed images provide assurance that the firmware, BIOS, and othersoftware are authentic and unmodified. As the system boots, the system’s software signatures are checked for integrity.●Secure Boot: Secure Boot anchors the boot sequence chain of trust to immutable hardware, mitigatingthreats against a system’s foundational state and the software that is to be loaded, regardless of a user’s privilege level. It provides layered protection against the persistence of illicitly modified firmware.●Trust Anchor module: A tamper-resistant, strong-cryptographic, single-chip solution provides hardwareauthenticity assurance to uniquely identify the product so that its origin can be confirmed to Cisco, providing assurance that the product is genuine.Firepower DDoS MitigationFirepower DDoS Mitigation is provided by Radware Virtual DefensePro (vDP), available and supported directly from Cisco on the following Cisco Firepower 9300 and 4100 series appliances:Radware vDP is an award-winning, real-time, behavioral DDoS attack mitigation solution that protects organizations against multiple DDoS threats. Firepower DDoS mitigation defends your application infrastructure against network and application degradation and outage.DDoS Mitigation: Protection SetFirepower’s vDP DDoS mitigation consists of patent-protected, adaptive, behavioral-based real-time signature technology that detects and mitigates zero-day network and application DDoS attacks in real time. It eliminates the need for human intervention and does not block legitimate user traffic when under attack.The following attacks are detected and mitigated:●SYN flood attacks●Network DDoS attacks, including IP floods, ICMP floods, TCP floods, UDP floods, and IGMP floods●Application DDoS attacks, including HTTP floods and DNS query floods●Anomalous flood attacks, such as nonstandard and malformed packet attacksPerformanceThe performance figures in Table 8 apply to all Cisco Firepower 4100 series models.Table 8. Key DDoS Performance Metrics for Cisco Firepower 4100 SeriesThe performance figures in Table 9 are for Cisco Firepower 9300 with 1 to 3 Security Modules irrespective of Security Module type (SM-24, SM-36 or SM-44).Table 9. Key DDoS Performance Metrics for Cisco Firepower 9300 with 1, 2, or 3 Security Modules.Ordering InformationCisco Smart LicensingThe Cisco Firepower NGFW is sold with Cisco Smart Licensing. Cisco understands that purchasing, deploying, managing, and tracking software licenses is complex. As a result, we are introducing Cisco Smart Software Licensing, a standardized licensing platform that helps customers understand how Cisco software is used across their network, thereby reducing administrative overhead and operating expenses.With Smart Licensing, you have a complete view of software, licenses, and devices from one portal. Licenses are easily registered and activated and can be shifted between like hardware platforms. Additional information is available here: https:///web/ordering/smart-software-licensing/index.html. Related information, on Smart Licensing Smart Accounts, is available here: https:///web/ordering/smart-software-manager/smart-accounts.html.Cisco Smart Net Total Care Support: Move Quickly with Anytime Access to Cisco Expertise and ResourcesCisco Smart Net Total Care™ is an award-winning technical support service that gives your IT staff direct anytime access to Technical Assistance Center (TAC) engineers and resources. You receive the fast, expert response and the dedicated accountability you require to resolve critical network issues.Smart Net Total Care provides the following device-level support:●Global access 24 hours a day, 365 days a year to specialized engineers in the Cisco TAC●Anytime access to the extensive online knowledge base, resources, and tools●Hardware replacement options include 2-hour, 4-hour, Next-Business-Day (NDB) advance replacement, aswell as Return For Repair (RFR)●Ongoing operating system software updates, including both minor and major releases within your licensedfeature set●Proactive diagnostics and real-time alerts on select devices with Smart Call HomeIn addition, with the optional Cisco Smart Net Total Care Onsite Service, a field engineer installs replacement parts at your location and helps ensure that your network operates optimally. For more information on Smart Net Total Care please visit: https:///c/en/us/services/portfolio/product-technical-support/smart-net-total-care.html.Select Part NumbersTables 10, 11, and 12 provide details on part numbers for Cisco Firepower NGFW solutions. Please consult the Ordering Guide for additional configuration options and accessories.Table 10. Cisco Firepower 2100 Series: Select Product ComponentsTable 11. Cisco Firepower 4100 Series: Select Product ComponentsTable 12. Cisco Firepower 9300: Select Product Components*Note: Firepower 9300 may also be deployed as a dedicated threat sensor, with fail-to-wire network modules. Please contact your Cisco representative for details.Table 13. Cisco Firepower NGFW VirtualNote: These optional security services licenses can be ordered with 1-, 3-, or 5-year subscriptions.Warranty InformationFind warranty information on at the Product Warranties page.Cisco ServicesCisco offers a wide range of service programs to accelerate customer success. These innovative services programs are delivered through a unique combination of people, processes, tools, and partners, resulting in high levels of customer satisfaction. Cisco Services help you protect your network investment, optimize network operations, and prepare your network for new applications to extend network intelligence and the power of your business. For more information about Cisco services for security, visit https:///go/services/security.Cisco CapitalFlexible payment solutions to help you achieve your objectivesCisco Capital makes it easier to get the right technology to achieve your objectives, enable business transformation and help you stay competitive. We can help you reduce the total cost of ownership, conserve capital, and accelerate growth. In more than 100 countries, our flexible payment solutions can help you acquire hardware, software, services and complementary third-party equipment in easy, predictable payments. Learn more.More Information for Service ProvidersFor information about Cisco Firepower in service provider environments, please visit:●https:///c/en/us/solutions/enterprise-networks/service-provider-security-solutions/More Information about Firepower NGFWsFor further information about Cisco Firepower NGFWs, please visit:●https:///go/ngfwMore Information about Cisco Anyconnect●Cisco AnyConnect Secure Mobility Clienthttps:///go/anyconnect●Cisco AnyConnect Ordering Guidehttps:///c/dam/en/us/products/security/anyconnect-og.pdf。
白皮书新型数据中心防火墙如今,位于数据中心边界的大量传统状态安全设备都面临着日趋复杂、频繁和多样化的网络攻击。
以F5 BIG-IP LTM 本地流量管理器所提供的防火墙服务为基础的全新的数据中心架构,既能够有效地抵御现代攻击,又可以节省大量的建设成本(CapEx)。
Lori MacVittie高级技术营销经理David Holmes高级技术营销经理目录简介3防火墙的限制4新型数据中心架构6本地应用协议的流畅性8高级DNS保护9高级web应用保护9 Web接入管理10累计收益10总结11简介在大部分企业中,防火墙都是网络与应用服务的第一道防线。
防火墙一直是构建传统网络安全架构的首要基础。
对关键业务服务的有效保护主要是通过简单而强大的访问控制工具——数据中心防火墙所进行的访问控制来完成的。
传统架构已经走向成熟,因此许多安全标准都要求部署经认证的防火墙。
例如,任何处理信用卡号的数据中心均必须符合支付卡行业(PCI)标准,而该标准要求安装一个网络防火墙。
PCI行业审计师所参考的公认标准是国际计算机安全协会(ICSA)的网络防火墙标准,该标准定义了可用于处理信用卡的少数防火墙。
这一合规性要求强调了使用成熟的数据中心防火墙架构的重要性。
但成熟意味着使用时间较长,而数据中心防火墙已经开始显露出自身在检测和抵御现代攻击方面的局限性。
针对应用层或网络层的攻击正在导致这些昂贵的状态防火墙发生故障,并且此类攻击的数量正在不断上升。
图1: 在Applied Research公司于2011年进行的调查中,很多受调查者都表示他们遇到过因应用层或网络层攻击而引起的状态防火墙故障。
11 Applied Research公司2011年ADC安全研究如果考虑到攻击者所面临的有利情形,这些防火墙故障更加令人担忧。
虽然匿名攻击和LulzSec攻击已得到行业的密切关注并且需要攻击者进行预先规划,但现在的许多攻击都不需要进行这样的准备,因为攻击者可以利用所创建的庞大资源池来攻击所选定的目标。
下一代防火墙解决方案摘要随着网络安全威胁日益增加,传统的防火墙已经不能满足企业的需求。
为了应对新的安全挑战,下一代防火墙解决方案应运而生。
本文将介绍下一代防火墙的概念、特点以及如何选择和部署该解决方案。
1. 简介传统防火墙主要依靠端口和IP地址等基础技术进行安全策略的设定与过滤,然而这些方法已经无法阻挡先进的网络威胁和攻击手段。
下一代防火墙是一种结合了多种安全功能的网络安全设备,旨在提供更高级别的安全保护。
2. 下一代防火墙的特点2.1 深度包检测传统防火墙主要关注网络流量的源和目的地,而下一代防火墙通过深度包检测技术可以对数据包的内容进行细致的分析。
这种技术可以检测和阻止恶意代码和威胁,从而提供更全面的保护。
2.2 应用识别和控制下一代防火墙可以通过应用识别技术对网络流量中的各种应用进行识别和分类。
这样可以更精细地控制不同应用的访问权限,提高网络的安全性和管理效率。
2.3 终端安全传统防火墙主要关注网络层面的安全,而下一代防火墙增加了对终端设备的安全保护。
例如,可以实施终端防病毒、终端防恶意软件和终端权限管理等功能,从而有效降低终端设备受攻击的风险。
2.4 可视化管理下一代防火墙提供基于图形化界面的管理平台,可以直观地展示网络流量和安全事件信息。
管理员可以通过这个平台进行安全策略的配置和监控,及时发现和应对安全问题。
3. 如何选择下一代防火墙解决方案3.1 功能覆盖范围在选择下一代防火墙解决方案时,首先需要确保所选方案能够满足企业的安全需求。
不同的方案可能提供不同的功能和服务,例如入侵检测系统(IDS)、虚拟专用网络(VPN)、入侵防御系统(IPS)等。
企业需要根据具体需求选择适合自己的方案。
3.2 性能和扩展性由于下一代防火墙需要进行深度包检测和流量分析,因此其性能对网络的影响较大。
选择方案时,需要考虑其处理能力和扩展性,以确保能够满足未来业务的发展需求。
3.3 技术支持和更新网络安全环境日新月异,新的威胁和攻击手段不断涌现。
产品手册Cisco AnyConnect 安全移动客户端和 Cisco ASA 5500-X 系列下一代防火墙 (VPN)思科® ASA 5500-X 系列下一代防火墙是专门构建的平台,兼具一流的安全功能和 VPN 服务。
组织可以获得互联网传输的连接和成本收益,且不会影响公司安全策略的完整性。
通过将安全套接字层 (SSL) 和 IP 安全 (IPsec) VPN 服务与全面威胁防御技术相结合,思科 ASA 5500-X 系列下一代防火墙可以提供高度可定制的网络接入,满足各种部署环境的要求,同时提供高级终端和网络级安全性(图 1)。
图 1.适合任意部署方案的可定制 VPN 服务AnyConnect 与思科 ASA 5500-X 系列自适应安全设备自适应安全设备可以为任意连接场景提供灵活的技术,每台设备最多可扩展至支持 10,000 个并发用户。
它通过以下方面提供易于管理的全隧道网络接入:●SSL(DTLS 和 TLS)●IPsec VPN 客户端技术●针对统一合规性和思科 Web 安全设备进行了优化的 AnyConnect®安全移动客户端●高级无客户端 SSL VPN 功能●网络感知站点到站点 VPN 连接此解决方案为移动用户、远程站点、承包商和业务合作伙伴提供高度安全的公共网络连接。
无需辅助设备即可轻松扩展 VPN 和保证其安全,从而降低 VPN 部署和运营相关的成本。
AnyConnect 安全移动客户端的优点包括:●SSL(TLS 和 DTLS)和基于 IPsec 的全网络访问:全网络访问可以为几乎所有的应用或网络资源提供网络层远程用户连接,而且通常用于将访问扩展至被管理的计算机,例如属于公司的笔记本电脑。
通过AnyConnect 安全移动客户端、Microsoft 第 2 层隧道协议 (L2TP) IPsec VPN 客户端、Apple iOS 和 Mac OS X 内置 IPsec VPN 客户端和各种支持 IPsec IKEv2 的第三方远程访问 VPN 客户端,均可获得连接。
Hillstone T-Series Intelligent Next-Generation FirewallT3860 / T5060 / T5860According to the latest research 66 percent of security breaches go undetected for 7-8 months. And, more than 85 percent of breaches originate from the web with drive-by downloads being the top web threat. This implies two things: First, a user does not have to click on anything to become infected with malware; and second, all organizations have infected hosts inside their network.Hillstone ,s T-Series intelligent Next-Generation Firewall (iNGFW) is an application-aware firewall that continuously monitors the network. It can identify attacks on all operating systems, applications, devices and browsers. It provides visibility into every stage of an attack and it can detect security breaches within minutes/seconds. It prioritizes hosts with the greatest security risks and provides contextual information about the threat. Security administrators can drill-down into the attack, including packet captures, to analyze all threat details.Hillstone ,s T-Series is designed for mid to large sized enterprises that need advanced levels of security, enhanced visibility, and continuous network uptime.TM- Outbound link load balancing includes policy based routing, ECMPand weighted, embedded ISP routing and dynamic detection- Inbound link load balancing supports SmartDNS and dynamicdetection- Automatic link switching based on bandwidth and latency- Link health inspection with ARP, PING, and DNSVPN• IPSec VPN:- IPSEC Phase 1 mode: aggressive and main ID protection mode- Peer acceptance options: any ID, specific ID, ID in dialup user group - Supports IKEv1 and IKEv2 (RFC 4306)- Authentication method: certificate and pre-shared key- IKE mode configuration support (as server or client)- DHCP over IPSEC- Configurable IKE encryption key expiry, NAT traversal keep alivefrequency- Phase 1/Phase 2 Proposal encryption: DES, 3DES, AES128, AES192,AES256- Phase 1/Phase 2 Proposal authentication: MD5, SHA1, SHA256,SHA384, SHA512- Phase 1/Phase 2 Diffie-Hellman support: 1,2,5- XAuth as server mode and for dialup users- Dead peer detection- Replay detection- Autokey keep-alive for Phase 2 SA• IPSEC VPN realm support: allows multiple custom SSL VPN logins associated with user groups (URL paths, design)• IPSEC VPN configuration options: route-based or policy based• IPSEC VPN deployment modes: gateway-to-gateway, full mesh,hub-and-spoke, redundant tunnel, VPN termination in transparent mode• One time login prevents concurrent logins with the same username • SSL portal concurrent users limiting• SSL VPN port forwarding module encrypts client data and sends the data to the application server• SSL VPN tunnel mode supports clients that run iOS, Android, and Windows XP/Vista including 64-bit Windows OS’• Host integrity checking and OS checking prior to SSL tunnel connections • MAC host check per portal• Cache cleaning option prior to ending SSL VPN session• L2TP client and server mode, L2TP over IPSEC, and GRE over IPSEC• View and manage IPSEC and SSL VPN connectionsUser and Device Identity• Local user database• Remote user authentication: LDAP, Radius, Active Directory• Single-sign-on: Windows AD• 2-factor authentication: 3rd party support, integrated token server with physical and SMS• User and device-based policiesIPS• 7,000+ signatures, protocol anomaly detection, rate-based detection, custom signatures, manual, automatic push or pull signature updates, integrated threat encyclopedia• IPS Actions: default, monitor, block, reset (attackers IP or victim IP, incoming interface) with expiry time• Packet logging option• Filter Based Selection: severity, target, OS, application or protocol• IP exemption from specific IPS signatures• IDS sniffer mode• IPv4 and IPv6 rate based DOS protection with threshold settings against TCP Syn flood, TCP/UDP/SCTP port scan, ICMP sweep,TCP/UDP/SCIP/ICMP session flooding (source/destination)• Active bypass with bypass interfaces• Provides predefined template of defense configuration• Predefined prevention configurationThreat Protection• Breach Detection- Near real-time breach detection (seconds/minutes)- Detailed description and severity of malware closely resembling attack - Pcap files and log files provide corroborating evidence- Confidence level provides certainty of attack• Network Behavior Analysis- L3-L7 baseline traffic compared to real-time traffic to revealanomalous network behavior- Built-in mitigations technologies include: session limits, bandwidthlimits and blocking- Graphical depiction of anomalous behavior compared to baseline and upper and lower thresholds• Network Risk Index quantifies the threat level of the network based on the aggregate host index.• Host Risk Index quantifies the host threat level based on attack severity, detection method, and confidence level.• Over 1.3 million AV signatures• Botnet server IP blocking with global IP reputation database• Flow-based Antivirus: protocols include HTTP, SMTP, POP3, IMAP,FTP/SFTP• Flow-based web filtering inspection• Manually defined web filtering based on URL, web content and MIME header• Dynamic web filtering with cloud-based real-time categorization database: over 140 million URLs with 64 categories (8 of which are security related)• Additional web filtering features:- Filter Java Applet, ActiveX or cookie- Block HTTP Post- Log search keywords- Exempt scanning encrypted connections on certain categories forprivacy• Web filtering profile override: allows administrator to temporarily assign different profiles to user/group/IP• Web filter local categories and category rating override• Proxy avoidance prevention: proxy site category blocking, rate URLs by domain and IP address, block redirects from cache & translation sites, proxy avoidance application blocking, proxy behavior blocking (IPS)• Inspect SSL encrypted traffic.Application Control• Over 3,000 applications that can be filtered by name, category, subcategory, technology and risk• Each application contains a description, risk factors, dependencies, typical ports used, and URLs for additional reference• Actions: block, reset session, monitor, traffic shapingHigh Availability• Redundant heartbeat interfaces• Active/Passive• Standalone session synchronization• HA reserved management interface• Failover:- Port, local & remote link monitoring- Stateful failover- Sub-second failover- Failure notification• Deployment Options:- HA with link aggregation- Full mesh HA- Geographically dispersed HAAdministration• Management access: HTTP/HTTPS, SSH, telnet, console• Central Management: Hillstone Security Manager (HSM), web service APIs• System Integration: SNMP, syslog, alliance partnerships• Rapid deployment: USB auto-install, local and remote script execution • Dynamic real-time dashboard status and drill-in monitoring widgets • Language support: EnglishLogs & Reporting• Logging facilities: local memory and storage (if available), multiple syslog servers and multiple Hillstone Security Audit (HSA) platforms • Encrypted logging and log integrity with HSA scheduled batch log uploading• Reliable logging using TCP option (RFC 3195)• Detailed traffic logs: forwarded, violated sessions, local traffic, invalid packets• Comprehensive event logs: system and administrative activity audits, routing & networking, VPN, user authentications, WiFi related events • IP and service port name resolution option• Brief traffic log format optionProduct Specification4GE Bypass Extension ModuleIOC-4XFP8SFP+ Extension Module4SFP+ Extension Module4 x SFP+, SFP+ module not included(1)IPS Throughput data is obtained under 1M-byte-payload HTTP traffic with test of 32K-byte scanning.(2) AV Throughput data is obtained under 1M-byte-payload HTTP traffic with file attachment.(3) IPSec Throughput data is obtained under Preshare Key AES256+SHA-1 configuration and 1400-byte packet size packet .Unless specified otherwise, all performance, capacity and functionality are based on StoneOS 5.5R1. Results may vary based on StoneOS® version and deployment.。