References
- 格式:pdf
- 大小:33.29 KB
- 文档页数:6

References引用格式范文赏析Assignment的引用格式国外每所大学在论文或者作业中对reference参照系统要求不一样,比如有的学校要求用哈佛文献标注格式,有的学校要求用CMS芝加哥文献标注格式,当然还有其他类型的格式,这就要求同学们向老师咨询清楚该次作业要求使用哪种文献标注格式,不要到时候白忙活。
下面为大家整理了一篇references写作的范文,大家可以学习一下这篇reference里面的写作方法。
ReferencesAlpert, F, Heaney, J & Kuhn, KL 2009, ‘Internships in marketing: Goals, structures and assessment –Student, company and academic perspectives’, Australasian Marketing Journal, vol. 17, no. 1, May, pp. 36–45.Boud, D 2001, ‘Using journal writing to enhance reflective practice’, New Directions for Adult and Continuing Education, no. 90, Summer, pp. 9–17.Boyatzis, RE 2007, ‘Developing emotional intelligence competencies’, in J Ciarochi & JD Mayer (eds), Applying Emotional Intelligence, Psychology Press, New York, pp. 28–52.Ca rson, L & Fisher, K 2006, ‘Raising the bar on criticality: Students’ critical reflection in an internship’, Journal of Management Education, vol. 30, no. 5, October.Fisher, K n.d., ‘Critical self-reflection: what is it and how do you do it?’, Southern Cross University Teaching and Learning Seminar Notes.Richert, AE 1990, ‘Teaching teachers to reflect: A consideration of programme structure’, Journal of Curriculum Studies, no. 22, pp. 509–527.Schön, DA 1998, The reflective practitioner: How professionals think in action,Ashgate Arena, London.Weighart, S 2009, Learning from experience: A resource book by and for co-op/internship professionals, Mosaic Eye Publishing, USA.。

ReferencesBan Gu 班固. 1962 [1975]. Hanshu漢書. Beijing: Zhonghua.Baxter, William H. 1992. A Handbook of Old Chinese Phonology. Berlin: Mouton de Gruyter. Baxter, William H. and Laurent Sagart. 2008. “Old Chinese: The Baxter-Sagart reconstruction (Version 0.98)”, paper presented at the 41st International Conference on Sino-Tibetan Languages and Linguistics, SOAS, 20 September 2008.Baxter, William H. 2010. “Yi” “Shi” “She” deng zi de gouni he zhonggu sy- de laiyuan “埶” “勢”“設” 等字的搆擬和中古sy- (書母-審三)的來源. Jianbo簡帛no.5 (2010), 161-177. Baxter, William H., and Laurent Sagart. 2011. “Baxter-Sagart Old Chinese reconstruction, ver-sion 1.0, February 20, 2011.” <http://crlao.ehess.fr/document.php?id=1217>, accessed 4 May, 2011.Benedict, Paul K. 1972. Sino-Tibetan: a Conspectus. Cambridge: Cambridge University Press. Bischoff , Bernhard. 1986. Latin Palaeography. Cambridge: Cambridge University Press. Paläo-graphie des römischen Altertums und des abendländischen Mittelalters, Erich Schmidt Verlag, 2nd rev. ed., 1986.Boltz, William G. 2014. Hand-writing styles in early Chinese manuscripts. Manuscript Cultures 5, 11-23.Chai, Ch’u and Winberg Chai eds. 1976. Li Chi translated by James Legge. Vol.2. New HydePark, New York: University Book.Chen Chusheng 陳初生. 2004. Jinwen Changyong Zijian金文常用字典. Xian: Shaanxi renmin chuban.鼎及Chen Peifen 陳佩芬. 1982. Fan you, Ma ding ji Liangqi zhong mingwen quanshi 繁卣, 梁其鐘銘文詮釋. Shanghai Bowuguan Jikan 2, 15-25.Chen Pengnian 陳彭年. 1966 [2003]. Guangyun廣韻. Taipei: Liming wenhua.Chen Songchang 陳松長. 2001. Mawangdui Jianbo Wenzi bian馬王堆簡帛文字編. Beijing: Wenwu.Chen Zhaorong 陳昭容. 2003. Qin xi Wenzi Yanjiu: Cong Hanzi shi de Jiaodu Kaocha秦系文字研究: 從漢字史的角度考察. Taipei: Academia Sinica.Dong Tonghe 董同龢. 1944. Shangguyin Biaogao上古音表稿. Lizhuang 李庄 (Sichuan): Lizhuang Shiyin 李庄石印. Reprint in Shiyusuo Jikan 史語所集刊no.18 (1948), Taipei: Aca-demia Sinica.Duan Yucai 段玉裁. 1981 [2003]. Shuowen Jiezi zhu說文解字注. Shanghai: Shanghai guji.Gao Heng 高亨. 1947 [1973]. Zhouyi Gujing Jinzhu周易古經今注. Hong Kong: Zhonghua.Gao Heng 高亨. 1963. Zhouyi Gujing Tongshuo周易古經通說. Hong Kong: Zhonghua.Gao Heng 高亨. 1989 [1997]. Guzi Tongjia Huidian古字通假會典. Jinan: Qi Lu Shushe.Gao Ming 高明. 1987. Zhongguo Guwenzixue Tonglun中國古文字學通論. Beijing: Wenwu. Gassmann, Robert H. 2005. Preliminary thoughts on the relationship between lexicon and writ-ing in the Guodian Texts. Asiatische Studien LIX:1 (Methodological Issues in the Study of Early Chinese Manuscripts: Papers from the Second Hamburg Tomb Text Workshop, edited by Matthias Richter), 233-260.Gao Ming 高明. 1980. Luelun hanzi xingti yanbian de yiban guilu 略论汉字形体演变的一般规律. Kaogu yu Wenwu 1980.2, 118-125.Graham, A. C. 1990. Studies in Chinese Philosophy and Philosophical Literature. Albany: State University of New York Press.324 | ReferencesGuo Moruo 郭沫若. 1935. Liang Zhou Jinwen ci Daxi Kaoshi 兩周金文辭大系攷釋. Tokyo: Bunkyudo.Handel, Zev. 2012. Valence-Changing Prefixes and Voicing Alternation in Old Chinese and Proto-Sino-Tibetan: Reconstructing *s- and *N- Prefixes. Language and Linguistics 13.1, 61-82.Han Ziqiang 韓自強. 2004. Fuyang Han jian Zhouyi Yanjiu阜陽漢簡周易研究. Shanghai: Shanghai guji.He Linyi 何琳仪. 1998 [2004]. Zhanguo Guwen Zidian; Zhanguo Wenzi Shengxi戰國古文字典-戰國文字聲系. Beijing: Zhonghua.He Linyi 何琳仪. 2003. Zhanguo Wenzi Tonglun Dingbu战国文字通论订补. Nanking: Jiangsu jiaoyu.He Linyi何琳仪, Cheng Yan 程燕and Fang Zhensan 房振三. 2006. Hujian Zhouyi xuanshi (xiuding) 沪简周易选释(修订). Zhouyi Yanjiu 75 (2006, no.1), 3-6.Huang Xiquan 黃錫全. 1990. Chu xi wenzi lüe lun 楚系文字略論. Huaxia Kaogu 1990.3, 99-108. Jacques, Guillaume. 2012. An internal reconstruction of Tibetan stem alternations. Transac-tions of the Philological Society Volume 110:2 (2012), 212-224.Jiang Liangfu 姜亮夫. 1999. Guwenzi xue古文字學. Kunming: Yunnan renmin.Karlgren, Bernhard. 1954. Compendium of Phonetics in Ancient and Archaic Chinese. Bulletin of the Museum of Far Eastern Antiquities 26, 211-367.Karlgren, Bernhard. 1956. Cognate words in the Chinese phonetic series. Bulletin of the Mu-seum of Far Eastern Antiquities 28, 1-18.Karlgren, Bernhard. 1957. Grammata Serica Recensa. Stockholm: Museum of Far Eastern Antiq-uities. Reprinted from Bulletin of the Museum of Far Eastern Antiquities 29.Lai Guolong 來國龍. 2014. Shi zhen yu zhen jian shuo Chu jian “丨”zide guyun guibu ji guwenzi tongyii ziru de yizhong teshu gouxing fangshi 釋謹與慎—兼說楚簡“丨”字的古韻歸部及古文字同義字孳乳的一種特殊構形方式 . Wuhan Daxue Jianbo Yanjiu Zhongxin武漢大學簡帛研究中心 </show_article.php?id=2003> , accessed 17 June, 2014 Legge, James. n.d., preface dated 1872. The Chinese Classics with a translation, critical and ex-egetical notes, prolegomena, and copious indexes, Vol. V.-Part I. Hong Kong: London mis-sionary’s Printing office.Li Fang-kuei (F.K. Li) 李方桂. 1971 [1982]. Shangguyin Yanjiu上古音研究. Beijing: Shangwu.Li Ling 李零. 2006. Du Shangbo Chu jian Zhouyi 读上博楚简周易. Zhonguo Lishi Wenwu 2006.4, 54-67.Li Ling 李零. 2008. Shiri, rishu he yeshu-san zhong jianbo wenxian de qubie he dingming 視日,日書和葉書三種簡帛文献的區别和定名. Wenwu 2008.12, 73-80.Li Rong 李荣. 1965. Cong xiandai fangyan lun gu qunmu you yi, er, si deng 从现代方言论古群母有一,二,四等. Zhonguo yuwen 1965.5, 337-342, 355.Li Shoukui 李守奎. 2003. Chu Wenzi bian楚文字編. Shanghai: Huadong Shifan daxue.Li Xinkui 李新魁. 1982 [2006]. Yunjing Jiaozheng韻鏡校證. Beijing: Zhonghua.Li Xueqin李學勤. 1959. Zhanguo timing gaishu (shang), (zhong), (xia) 战国题铭概述 (上), (中), (下). Wenwu 1959.7, 50-54 (上), Wenwu 1959. 8, 60-63 (中), Wenwu 1959. 9, 58-61 (下).Li Xueqin 李學勤 et al. ed. 2000. Shisanjing Zhushu十三經注疏 . Beijing: Beijing Daxue chu-ban.Li Yu 李玉. 1994. Qin Han Jiandu Boshu Yinyun Yanjiu秦漢簡牘帛書音韻研究. Beijing: Dangdai zhongguo.325| ReferencesLi Yunfu 李運富. 1997. Cong wenzi de gouxing xitong kan zhanguo wenzi zai hanzi fazhanshishang de diwei 从文字的构形系统看战国文字在汉字发展史上的地位. Xuzhou ShifanDaxue Xuebao 1997.3, 35-39.Liao Mingchun 廖明春. 2001. Zhouyi Jingzhuan yu Yixue shi Xinlun周易经传与易学新论. Jinan:Qi Lu shushe.Liu Baojun 刘宝俊. 1986. Qin Han boshu yinxi gaishu 秦汉帛书音系概述. Zhongnan MinzuXueyuan Xuebao 1986.1, 126-131.Liu Xiang劉翔. 1986. Fu qi lüe shuo 簠器略說. Guwenzi Yanjiu 13, 458-463.Lu Deming 陸德明. 1985. Jingdian Shiwen經典釋文 (3 vols). Shanghai: Shanghai guji.Lü Dalin 呂大臨. 1991. Kao gu tu考古圖 (10 juan). Huang Xiaofeng 黃曉峰 edition (1753), photo-copy reprint by Jiangsu, Guangling 廣陵 guji.Ma Chengyuan 馬承源 ed. 1987-1990. Shang Zhou Qingtongqi Mingwen xuan商周青銅器銘文選. Beijing: Wenwu.Ma Chengyuan 馬承源, ed. 2001-2012. Shanghai Bowuguan cang Zhanguo Chu zhushu上海博物館藏戰國楚竹書vols. 1-9. Shanghai: Shanghai guji.Ma Chengyuan馬承源ed. 2003. Shanghai Bowugan cang Zhanguo Chu zhushu (San) 上海博物館藏戰國楚竹書 (三). Shanghai: Shanghai guji.Ma Xulun 馬叙倫. 1970. Shuowen Jiezi Yanjiu說文解字研究. Hong Kong: Taiping.Matisoff, James A. 2003. Handbook of Proto-Tibeto-Burman: System and Philosophy of Sino-Tibetan reconstruction. Berkeley and Los Angeles: University of California Press.Matisoff, James A. 2006. “Deltacism of laterals in Sino-Tibetan and elsewhere”,</pdf/JAM/DinguistDilemma-2006.pdf>, accessed on May 8,2014; a revised version of “Dinguist’s Dilemma: deltacism of laterals in Sino-Tibetan”, apaper presented at the 23rd International Conference on Sino-Tibetan Languages and Lin-guistics, University of Texas at Arlington, Oct., 3-6, 1990.Mei Tsu-lin 梅祖麟. 1979. Sino-Tibetan “year”, “month”, “foot” and “vulva”. Ch’inghuaHsuehpao new series 12.1-2, 117-134.Mei, Tsu-lin. 2012. The causative *s- and nominalizing *-s in Old Chinese and related matters inProto-Sino-Tibetan. Language and Linguistics 13.1, 1-28.Norman, Jerry. 1994. Pharyngealization in Early Chinese, Journal of the American Oriental Soci-ety 114.3, 397-408.Pan Wuyun 潘悟云. 1997. Houyinkao 喉音考. Minzu Yuwen 1997.5, 10-24.Park, Haeree. 2008. A revision of the chuan 川 phonetic series through discovered texts. Chi-nese Linguistics in Leipzig. Paris: Centre de Recherches Linguistiques sur l’Asie Orientale,39-51.Park, Haeree. 2009. The Shanghai Museum Zhouyi Manuscript and the Warring States WritingSystem. Ph.D. dissertation. University of Washington, Seattle.Park, Haeree. 2011. Shuping 书评: Zhanguo Chu fangyan yinxi 战国楚方言音系 (Review articleof Zhao Tong’s Chu Fangyan Yinxi, 2006). Yuyanxue Luncong 44, (Peking Univeristy), 356-381.Pu Maozuo 濮茅左. 2003. Transcription and annotation of the “Zhouyi 周易” in ShanghaiBowugan cang Zhanguo Chu zhushu (san)上海博物館藏戰國楚竹書 (三) edited by MaChengyuan馬承源, 131-260. Shanghai: Shanghai guji.Pulleyblank, Edwin G. 1962. The Consonantal system of Old Chinese, Part I, Asia Major New se-ries 9, 58-144.326 | ReferencesPulleyblank, Edwin G. 1978. Emphatic negatives in classical Chinese. Ancient China: Studies in Early Civilization edited by David T. Roy and Tsuen-hsuin Tsien, 115-136. Hong Kong: Chi-nese Univiversity Press.Qiu Xigui 裘锡圭. 1988 [2002]. Wenzixue Gaiyao文字学概要. Beijing: Shangwu.Qiu Xigui裘锡圭. 1992. Guwenzi Lunji古文字論集. Beijing: Zhonghua.Qiu Xigui 裘锡圭. 1998. Jiaguwen zhong de jian yu shi 甲骨文中的見與視. Jiaguwen faxian yibai zhounian xueshu yantaohui lunwenji甲骨文發現一百周年學術研討會論文集edited by Taiwan Shifan Daxue guowenxue xi and Academia Sinica, Institute of History and linguis-tics, 1-7. Taipei.Richter, Matthias. 2005. Towards a profile of graphic variation: on the distribution of graphic variants within the Mawangdui Laozi manuscript. Methodological Issues in the Study of Early Chinese Manuscripts: Papers from the Second Hamburg Tomb text Workshop, Mat-thias Richter ed., AsiatischeStudien/ Etudes Asiatiques LIX∙1∙2005. Bern: Peter Lang. Richter, Matthias, 2006. Tentative criteria for discerning individual hands in the Guodian Manuscripts. Manuscript. 28 pages. Published in: Rethinking Confucianism: Selected Pa-pers from the Third International Conference on Excavated Chinese Manuscripts, Mount Holyoke College, April 2004, edited by Xing Wen, San Antonio: Trinity University, 132-147. Richter, Matthias. forthcoming. Punctuation. Manuscript. 80 pages. To appear in Reading Early Chinese Manuscripts: Texts, Contexts, Methods, edited by Wolfgang Behr, MartinKern and Dirk Meyer. Leiden: Brill.Rong Geng 容庚. 1985 [2005]. Jinwen bian金文編. Beijing: Zhonghua.Ruan Yuan 阮元. 1980 [2003]. Shisan jing Zhushu十三經注疏. Beijing: Zhonghua.Sagart, Laurent. 2003. Sources of Middle Chinese manner types: Old Chinese pre-nasalized initials in Hmong-Mien and Sino-Tibetan perspective. Language and Linguistics 4.4, 757-768.Sagart, Laurent. 2006. On intransitive nasal prefixation in Sino-Tibetan languages. Cahiers de Linguistique – Asie Orientale 35.1, 57-70.Sagart, Laurent. 2007. “Reconstructing Old Chinese uvulars in the Baxter-Sagart system”, pa-per presented at the 40th ICSTLL, Harbin, September 27-29, 2007.Sagart, Laurent, and William H. Baxter. 2009. Reconstructing Old Chinese uvulars in the Bax-ter-Sagart system (Version 0.99). Cahiers de Linguistique – Asie Orientale 38.2, 221-244. Sagart, Laurent, and William H. Baxter. 2012. Reconstructing the *s- prefix in Old Chinese. Lan-guage and Linguistics 13.1, 29-59.Schuessler, Axel. 1974. R and L in Archaic Chinese. Journal of Chinese Linguistics 2, 186-199. Shadong sheng wenwu gongzuo weiyuanhui 山东省文物工作委员会. 1976. Houma Mengshu 侯马盟书. Shanghai: Wenwu.Shao Rongfen 邵榮芬. 1991. Xiamuzi shanggu yi fen wei er shixi 匣母上古一分爲二试析. Yuyan Yanjiu 20.1, 118-127.Shaughnessy, Edward L. 1993. I Ching 易經 (Chou I 周易). Early Chinese texts: A Bibliographical Guide edited by Michael Loewe, 216-228. Berkeley: The Society for the study of EarlyChina and the institute of East Asian studies, University of California, Berkeley. Shaughnessy, Edward L. 2006. Α first Reading of the Shanghai Museum Bamboo-Strip Manu-script of the Zhouyi, Early China 30 (2005-2006), 1-24.Shaughnessy, Edward L. 2014. Unearthing the “Changes”: Recently Discovered Manuscripts of the Yi Jing (I Ching) and Related Texts. New York: Columbia University Press.Sima Qian 司馬遷. 1959 [1962]. Shiji史記. Beijing: Zhonghua.327| ReferencesStarostin, Sergei Anatolyevich. 1989 [2010]. Gudai Hanyu Yinxi de gouni古代漢語音系的構擬(Chinese translation of Rekonstruckcija drevnekitajskoj fonologic̆e skoj sistemy. Moscow:Nauka, Glavnaja Redakcija vostoc̆n oj Literatury, 1989). Shanghai: Shanghai jiaoyu chuban上海敎育出版.Sun Shuxia 孫淑霞. 2013. Chutu Cang Jie pian gaishu 出土蒼頡篇概述. Wuhan Daxue JianboYanjiu Zhongxin 武漢大學簡帛研究中心 </show_arti-cle.php?id=1948>, accessed 6 June, 2014.Tang Lan 唐蘭. 1965. Guwenzixue Daolun古文字學導論 (2 vols). Hong Kong: Taiping.Tang Yuhui 湯余惠. 1986. Lüelun Zhanguo wenzi xingti yanjiu zhong de jige wenti 略論戰國文字形體研究中的幾個問題. Guwenzi Yanjiu 15, 9-101.Teng Rensheng 滕壬生. 2008. Chu xi Jianbo Wenzi bian, Zengding ben楚系簡帛文字編: 增訂本Wuhan: Hubeijiaoyu 湖北教育出版社.Ting Pang-hsin. 1977. Archaic Chinese *g, *gw, *γ and *γw. Monumeta Serica 33 (1977-1978),171-179.Wang Chong 王充. 1974. Lunheng論衡. Shanghai: Shanghai renmin.Wang Guowei 王國維. 1976. Shi Zhou pian Xulu史籀篇叙錄. Taipei: Taiwan Shangwu.Wang Li 王力. 2000. Wang Li Guhanyu Zidian王力古漢語字典. Beijing: Zhonghua.Watson, William. 1961. China before the Han Dynasty. New York: Frederick A. Praeger.Wu Zhenfeng 吳鎭烽. 2006. Jinwen Renming Huibian金文人名彙編. Beijing: Zhonghua.Xiao Congli 肖從禮. 2011. Qin Han jiandu “zhiri” kao 秦漢簡牘“質日”考. Fudan Daxue Guwen-xian yu Guwenzi Yanjiu Zhongxin 复旦大学古文献与古文字研究中心,</SrcShow.asp?Src_ID=1427>, accessed 4 June, 2014.Xin Ting 新亭. 2014. Qishan Zhougong miao bu jia “Wang Si Mei Ke ben yi yu miao” de guanchahe sikao 岐山周公廟卜甲“王斯妹克奔逸于廟”的觀察和思考. Fudan Daxue chutu wenxianyu guwenzi yanjiu zhongxin 复旦大学出土文献与古文字研究中心. <http://www.gwz.fu-/SrcShow.asp?Src_ID=2254>, accessed 17 June, 2014Xu Dan 徐丹. 2004. Shanggu hanyu houqi foudingci ‘wu’ daiti ‘wang’ 上古漢語後期否定詞無代替亡. Hanyu shi Xuebao 5, 64-72.Xu Xiongzhi 許雄志. 2001. Qin yin Wenzi Huibian秦印文字彙編. Zhengzhou: Henan meishu.Xu Zhongshu 徐中舒. 1981. Hanyu Guwenzi Zixing biao漢語古文字字形表. Sichuan, HongKong: Sichuan renmin, Zhonghua.Yakhontov, S. E. 1976 [1986]. Shanggu Hanyude kaitou fuyin L he R 上古汉语的开头辅音L和 Rin Hanyushi Lunji汉语史论集 edited by Tang Zuofan 唐作藩and Hu Shuangbao 胡双宝,156-165. Beijing: Beijing Daxue.Yakhontov, S. E. 1960 [1986]. Shanggu hanyude chunhua yuanyin 上古汉语的唇化元音Hanyu-shi Lunji edited by Tang Zuofan and Hu Shuangbao, 42-51. Beijing: Beijing Daxue.Zeng Xiantong 曾憲通. 1982. Santi shijing guwen yu Shuowen guwen hezheng 三體石經古文與說文古文合證. Guwenzi Yanjiu 7, 273-87.Zeng Xiantong 曾憲通. 2005. Guwenzi yu Chutu Wenxian Congkao 古文字与出土文献丛考.Guangzhou: Zhongshan daxue.Zhang Ru 张儒. 1988. Guanyu zhushu, boshu tongjiazi de kaocha 关于竹书帛书通假字的考察.Shanxi Daxue Xuebao 1988.2, 37-43.Zhang Shouzhong 張守中. 1981. Zhongshan Wang Cuo qi Wenzi bian中山王器文字編. Bei-jing: honghua.Zhang Shouzhong 張守中. 1994. Shuihudi Qin jian Wenzi bian睡虎地秦簡文字編. Beijing:Wenwu.328 | ReferencesZhang Zhenlin 張振林. 1982. Xian Qin guwenzi cailiao zhong de yuqici 先秦古文字材料中的語氣詞. Guwenzi Yanjiu 7, 289-307.Zhang Zhenglang张政烺. 1984. Mawangdui Liu shi si Gua ba 马王堆六十四卦拔. Wenwu 1984.3, 9-14.Zhao Chao 趙超. 2006. Shike Guwenzi石刻古文字. Beijing: Wenwu.Zhao Cheng 赵诚. 1986. Linyi Hanjiande tongjiazi 临沂汉简的通假字. Yinyunxue Yanjiu (er)音韵學研究edited by Zhongguo yinyunxue yanjiuhui, 17-26. Beijing: Zhonghua.Zhao Liwei 趙立偉. 2002. Shuihudi Qin mu zhujian tongjiazi yanjiu 睡虎地秦墓竹簡通假字研究. Jianbo Yuyan Wenzi Yanjiu di yi ji簡帛語言文字研究第一輯 edited by Zhang Xian-cheng 張顯成, 326-73. Chengdu: Bashu.Zhao Tong 赵彤. 2006. Zhanguo Chu Fangyan Yinxi战国楚方言音系. Beijing: Zhonguo xiju chu-banshe.Zhongguo shehui kexueyuan kaogu yanjiusuo 中國社會科學院考古研究所.1984-1994. Yin Zhou Jinwen Jicheng 殷周金文集成. Beijing: Shangwu.Zhongguo kexueyuan kaogu yanjiusuo 中國科學院考古研究所. 1965. Jiagu wen bian甲骨文編.Beijing: Zhonghua.Zhouyuan kaogu dui 周原考古隊. 2006. 2003 nian Shanxi Qishan Zhougong miao yizhi diao-cha baogao 2003年陝西岐山周公廟遺址調查報告. Gudai Wenming古代文明, vol. 5(2006), 151-186, Beijing: Wenwu.Zhou Zumo 周祖謨. 1983. Tang Wudai Yunshu Jicun唐五代韻書集存. 2 vols. Beijing: Zhong-hua.Zhou Zumo 周祖謨. 1984. Handai Zhushu yu boshu zhong de tongjiazi yu guyinde kaoding 汉代竹书与帛书中的通假字与古音的考订in Yinyunxue Yanjiu (yi) 音韵學研究(一), edited by Zhongguo yinyunxue yanjiuhui, 78-91. Beijing: Zhonghua.Zhou Zumo 周祖謨. 1993 [2004]. Fangyan Jiaojian 方言校箋. Beijing: Zhonghua.。

英文文献的引用方法与格式-- APA格式所谓APA格式是指美国心理学会(American Psychological Association) 所出版的出版手册(Publication Manual)中,有关投稿该协会旗下所属二十九种期刊时必须遵守的规定而言。
学术界通称为APA格式。
APA引证格式由两部分组成:论文中的文献引用与论文后面的参考文献。
必须注意的是,参考文献部份与文献引用部份息息相关,引用过的文献必须出现在参考文献中,而且参考文献中的每一项文献都被引用过,两者的作者姓氏以及发表年代也必须完全一致。
一、文献引用(Citation in Text)文献引用的目的,一方面是帮助读者进一步直接查阅有关文献的内容,另一方面是尊重与保障他人的知识产权。
文献引用的方式主要有两种,一种是在行文当中直接引用作者姓氏,如:Widdowson (1978) has claimed that native speakers can better understand ungrammatical utterances with accurate vocabulary than those with accurate grammar and inaccurate vocabulary.另一种是直接引用研究的结果或论点,如:Communicative methods have the common goals of bringing language learners into closer contact with the target language (Stern, 1981). APA文献引用的格式主要有下列几种,分述如下:(一)作者为一个人时例1:Stahl (1983) has demonstrated that an improvement in reading comprehension can be attributed to an increase in vocabulary knowledge.[注:若行文中提到作者姓氏,用此例所示格式引用]例2:During the period of Grammar Translation methodology, bilingual dictionaries became common as reference tools (Kelly, 1969). [注:行文中未提到作者姓氏,用此例所示格式引用;句子本身的标点符号位于括号的后面。

·reference·n. ['refrəns] ( references )··双解释义·C U 提及,涉及(an example of) mentioning·U 参考,查阅(an example of) looking at sth for information·C 引文; 参考书目 a piece of written information about sb's character, ability, etc. especially when they are looking for employment·C 证明书; 证明人; 推荐信; 推荐人 a person who provides such information ·U 关联,关系relation, correspondence (to)·词汇搭配••contain〔give, provide〕 a reference 包含〔提及,提供〕参考•cross reference (同一书或文件中的)相互参照•have a reference to 和…有关•make a reference 提及••constant〔further〕 reference 经常〔进一步〕查阅•direct〔indirect〕 reference 直接〔间接〕提到•future reference 将来参考•good reference 很好的推荐信•negative〔positive〕 reference 否定〔肯定〕(某人)的证明书•passing reference 稍稍涉及•excellent〔satisfactory〕 references 有力〔令人满意〕的证明书••for reference 作参考•keep it for reference 备作参考•in reference to that incident 关于那件事• a frame of reference 参照标准,准则• a list of references 参考书目•load one's pages with references 旁征博引•without reference to 不管,不论,与…无关•without reference to age and sex 不论男女老少••reference to 说到,提到,参考,查看•references to the opponents 提到对手•reference to this point 提及这一点·常用短语•without reference to不考虑…,置…于不顾not taking account of sb/sthThis test is to be taken by all pupils without reference to age or grade.这次测验的对象是全体小学生,不论年龄和年级。

数据库中references的用法数据库中references什么是references?在数据库中,references是用于建立表与表之间关联的机制。
当一个表中的某个列(外键)引用另一个表中的主键时,我们称之为references关系。
references的作用•建立表之间的关联关系:通过使用references,可以在表之间建立关联关系,从而方便进行数据的查询和操作。
•维护数据一致性:通过定义外键关系,可以保证参照表中的数据被正确引用,避免了数据的冗余和不一致。
使用references的语法CREATE TABLE 表名 (列1 数据类型,列2 数据类型,列3 数据类型,...FOREIGN KEY (外键列) REFERENCES 参照表名 (参照列));其中,外键列对应当前表中需要引用另一个表的列,参照表名是被引用的表的名称,参照列是被引用的表中的主键列。
references的用法1.一对一关系:当两个表之间存在一对一的关系时,可以使用references来建立关联。
例如,有一个表存储员工信息,另一个表存储员工的办公室信息。
可以通过在员工表中建立外键引用办公室表的主键,来表示每个员工只能拥有一个办公室。
2.一对多关系:当一个表中的某个列需要引用另一个表中的多个行时,可以使用references来建立关联。
例如,在一个学生表中,每个学生可以有多个课程。
可以在学生表中建立外键引用课程表的主键,来表示每个学生可以参加多门课程。
3.多对多关系:当两个表之间存在多对多的关系时,需要通过中间表来建立关联。
例如,有一个商品表和一个订单表,一个商品可以出现在多个订单中,一个订单中可以包含多个商品。
可以通过在中间表中建立外键分别引用商品表和订单表的主键,来表示商品和订单之间的关系。
4.级联操作:通过定义外键的级联操作,可以自动更新或删除关联表中的数据。
例如,当删除一个课程时,可以通过设置外键的级联操作将学生表中关于该课程的记录一并删除。

英文assignment的写作细节(请各位愿意长期合作的朋友,尽量仔细阅读,在行文中注意这些要求)我们的assignment通常分为两种形式,一是essay, 一是report.二者在形式上有所差别,essay 偏向于理论论述,report则大都结合case进行理论应用。
一篇assignment上面会对写成essay 还是report格式作出明确要求。
在阅读题目时,请尽量仔细。
相同点:1、字体:Times New Roman或者Arial, 字号:小四,行距:1.5倍。
请在写作之前就把这些格式调好,以避免写好后再调会出现一些意相不到的情况。
2、段与段之间隔行。
每段不要求像中文写作那样空两格,而是直接顶格写。
区别:Essay:Essay的写作相对report要简单一些。
通常只包括三个部分,Introduction, Main Body, Conclusion. Introduction 包括topic的背景介绍和论文的结构。
一般占总字数的10%左右。
Main Body是主体部分,占总字数80%左右。
如果题目中作了具体要求,就根据题目提到的几个方面来逐一讨论就可以了。
有的题目没有作具体要求,就根据自己的构思来写。
但要求有逻辑性。
Conclusion也是占10%,在这一段里把文章中的主要观点用一到两句话概括出来。
Essay的body部分不提倡用太多的标题,有的作业要求甚至会直接写明不能用任何的标题,所以为了保证文章结构的清晰性,段落间要有承上启下的句子,使结构清晰明了,文章结构很重要,老师非常重视,直接影响分数的好坏。
Reference的写作是essay和report都要涉及的,我放在最后来详细说。
Report:它的写法大体上和essay差不多,但要求要严格一些。
第一:标题页:顾名思义,将report的题目写在此页第二:Executive summary,是对文章的摘要,要把写这篇报告的目的(也就是为什么要写这篇报告),报告得出的结果,最后的结论,以及报告给出的建议一一交代清楚,但不需要交代题目背景,摘要的目的是让busy reader能快速掌握报告的全部内容。

科学引用格式(SCI的References格式)1.引言科学引用格式(SCI)是一种用于在学术出版物中引用参考文献的标准格式。
SCI格式由美国化学学会(ACS)领导的一组学术出版组织共同制定,目的是为了使学术论文的引用标准化、规范化,方便读者查找和理解参考文献的信息。
2.SCI格式的特点SCI格式的引用特点主要包括以下几点:(1)作者姓氏在前,名字在后,用逗号隔开,而非中文的姓在前,名在后的格式。
(2)标题使用“斜体”,刊物名称用“正体”。
(3)引用的序号要用方括号括起来,而非使用括号。
这些规范的要求使得学术论文的引用信息更加清晰、规范,方便读者查找和理解引用的参考文献。
3.SCI格式的应用范围SCI格式广泛应用于自然科学和工程技术领域的学术出版物中,如物理学、化学、生物学、材料科学等领域。
SCI格式的引用标准被认为是国际上学术界最权威的引用标准之一,因此在相关领域的学术出版物中广泛使用。
4.SCI格式的引用要求SCI格式的引用要求非常严格,引用时需要按照一定的格式和顺序来列出参考文献的信息。
一般来说,SCI格式的引用要求包括以下内容:(1)作者的尊称(姓氏在前,名字在后)。
(2)文献的标题(使用斜体)。
(3)刊物的名称(使用正体)。
(4)刊物的卷号、期号和页码。
(5)出版年份。
5.SCI格式的示例以下是一篇使用SCI格式引用的参考文献示例:[1] Smith, J. A. The effects of climate change on marine ecosystems. Nature, 2015, 523(7561): 418-420.上面的引用示例中,方括号内的数字1表示引用的序号,Smith, J. A.是作者的尊称,The effects of climate change on marine ecosystems是文献的标题,Nature是刊物的名称,2015是出版年份,523是卷号,7561是期号,418-420是页码。

英语书信格式如何提供你工作的Reference?问:当潜在雇主要求我提供一份推荐人(References)的清单时,我应该提供几个人的名字?我刚毕业工作不久,而亲戚又不能算在内,没有太多选择,我该怎幺办?答:简单地说,至少提供一到两个人的姓名,而这两个人能够证明给未来的雇主你将会是个好员工。
同时这又带出了和Reference有关的几个问题。
首先是你应该找谁做Reference。
一般来说,找亲戚来证明是不适宜的。
除非你的亲戚自己主持一盘生意,而你为他/她的公司设计了一个网站进行线上交易,那又是另一码事。
你必须在你亲戚的公司中有正式的工作成绩和贡献。
除了受薪的工作以外,你还可以把自己在校参与过的项目,义务工作,其它业余活动的有说服力的人物列出来,只要这些活动能够反映你的相关业务水平。
比如你为你所在的体育俱乐部设计和维护网站,为你做义工的社区中心写了一个程序来管理信息,为你做业余老师的学校提供了电脑培训等等,这些都符合条件,而你一起工作过的人就可以做你的Reference。
其次是为你做Reference的人应该对你的表现说些什幺。
他们的评语很重要,对你的看法大体上应该一致。
最好的办法是,在你列出可以做自己Reference的名单时,给他们逐个打电话,征求他们的同意。
然后你把自己想要应聘的工作梗概,你的简历,以及你个人的一些情况发一份给每个人,让他们看过后有所参照。
在提供给未来雇主的Reference的大概格式如下:他们的姓名头衔(做什么的)在哪里工作怎么认识你的他们推荐你做哪类工作你和他们一起工作时做什么你和他们一起工作时取得的最大的成绩一起完成过的项目雇主怎么可以联络到他们。

论⽂reference格式写作规范英⽂assignment的写作细节(请各位愿意长期合作的朋友,尽量仔细阅读,在⾏⽂中注意这些要求)我们的assignment通常分为两种形式,⼀是essay, ⼀是report.⼆者在形式上有所差别,essay 偏向于理论论述,report则⼤都结合case进⾏理论应⽤。
⼀篇assignment上⾯会对写成essay 还是report格式作出明确要求。
在阅读题⽬时,请尽量仔细。
相同点:1、字体:Times New Roman或者Arial, 字号:⼩四,⾏距:1.5倍。
请在写作之前就把这些格式调好,以避免写好后再调会出现⼀些意相不到的情况。
2、段与段之间隔⾏。
每段不要求像中⽂写作那样空两格,⽽是直接顶格写。
区别:Essay:Essay的写作相对report要简单⼀些。
通常只包括三个部分,Introduction, Main Body, Conclusion. Introduction 包括topic的背景介绍和论⽂的结构。
⼀般占总字数的10%左右。
Main Body是主体部分,占总字数80%左右。
如果题⽬中作了具体要求,就根据题⽬提到的⼏个⽅⾯来逐⼀讨论就可以了。
有的题⽬没有作具体要求,就根据⾃⼰的构思来写。
但要求有逻辑性。
Conclusion也是占10%,在这⼀段⾥把⽂章中的主要观点⽤⼀到两句话概括出来。
Essay的body部分不提倡⽤太多的标题,有的作业要求甚⾄会直接写明不能⽤任何的标题,所以为了保证⽂章结构的清晰性,段落间要有承上启下的句⼦,使结构清晰明了,⽂章结构很重要,⽼师⾮常重视,直接影响分数的好坏。
Reference的写作是essay和report都要涉及的,我放在最后来详细说。
Report:它的写法⼤体上和essay差不多,但要求要严格⼀些。
第⼀:标题页:顾名思义,将report的题⽬写在此页第⼆:Executive summary,是对⽂章的摘要,要把写这篇报告的⽬的(也就是为什么要写这篇报告),报告得出的结果,最后的结论,以及报告给出的建议⼀⼀交代清楚,但不需要交代题⽬背景,摘要的⽬的是让busy reader能快速掌握报告的全部内容。

reference的用法总结大全(学习版)编制人:__________________审核人:__________________审批人:__________________编制学校:__________________编制时间:____年____月____日序言下载提示:该文档是本店铺精心编制而成的,希望大家下载后,能够帮助大家解决实际问题。
文档下载后可定制修改,请根据实际需要进行调整和使用,谢谢!并且,本店铺为大家提供各种类型的经典范文,如英语单词、英语语法、英语听力、英语知识点、语文知识点、文言文、数学公式、数学知识点、作文大全、其他资料等等,想了解不同范文格式和写法,敬请关注!Download tips: This document is carefully compiled by this editor.I hope that after you download it, it can help you solve practical problems. The document can be customized and modified after downloading, please adjust and use it according to actual needs, thank you!In addition, this shop provides various types of classic sample essays, such as English words, English grammar, English listening, English knowledge points, Chinese knowledge points, classical Chinese, mathematical formulas, mathematics knowledge points, composition books, other materials, etc. Learn about the different formats and writing styles of sample essays, so stay tuned!reference的用法总结大全reference的意思n. 参考;参考书;提及,涉及;证明人,介绍人v. 引用;参照;reference的用法用作名词(n.)The play is full of references to the political events of those days.这剧本涉及当时的许多政治事件。

Master thesis project in telecommunications at Dalarna UniversityDuration: 3-5 monthsNumber of students: 1Supervisor: Ernst Nordström, Department of Economics and Social SciencesAssistant supervisor: Ming Fan, School of Industrial LeadershipIntradomain statistical QoS routing in IP networksSome Internet domains are currently being upgraded with functionality to provide Quality of Service (QoS) guarantees on packet loss and delay. The problem of routing in QoS-enhanced IP networks can be formulated as a problem of finding an optimal path from a set of feasible paths.The task in this thesis is to review the litterature on IP network routing with statistical QoS bounds. A set of promising algorithms should be selected and implemented using the C programming language. The overall system performance should be evaluated by call level simulation.References1. E. Biton, A. Orda, “QoS provisioning and routing with stochastic guarantees”, In Proc. 1st InternationalConference on Quality of Service in Heterogeneous Wired/Wireless Networks, Vol. 00, pp. 112-119,2004.2.S. Chen, K. Nahrstedt, “Distributed QoS routing with imprecise state information”, In Proc. of IEEEICCN, pp. 614-621, Oct. 1998.3.R. Guerin, A. Orda, “QoS routing in networks with inaccurate information: theory and algorithms”,IEEE/ACM Transactions on Networking, Vol. 7, No. 3, Jun. 1999.4.G. Hoogiemstra, P. Van Mieghem, “Delay distributions on fixed Internet paths”, Delft University ofTechnology, report20011020, on http://www.nas.its.tudelft.nl/people/Piet/TUDelftReports.html5.T. Korkmaz, M. Krunz,”Bandwidth-delay contstrained path selection under inaccurate stateinformation”, IEEE/ACM Transactions on Networking, Vol. 11, No. 3, pp. 384-398, 2003.6.I. Korpeoglu, M. Ebersprächer, H. Theimer, P. Kuhn, U. Briem, “Approximate analysis of the end-to-end delay in ATM networks”, In Proc. of Infocom’92, pp. 978-986, 1992.7. D. Lorentz, A. Orda, “QoS routing in networks with uncertain parameters”, IEEE/ACM Transactions onNetworking, Vol. 6, No. 6, Dec. 1998.8.R.P. Loui, “Optimal paths in graphs with stochastic or multidimensional weights”, Communications ofthe ACM, Sept. 1983.9.P. Van Mieghem, (ed), F. Kuipers, T. Kormaz, M. Krunz, M. Curado, E. Monteiro, X. Masip-Bruin, J.Sole-Pereta, S. Sanchez-Lopez, “Quality of service routing”, Chapter 3 of Future Internet Services, EU-COST 263 Final Report, edited by Smirnow et al in Springer LNCS 2856, pp. 80-117, 2003.10.P. Van Mieghem, “A lower bound for the end-to-end delay in networks: applications to voice over IP”,In Proc. Globecom’98, pp. 2508-2512, Sydney, Australia, 1998.11. A. Shaikh, J. Rexford, K. Shin, “Evaluating the impact of stale link state on Quality-of-Servicerouting”, IEEE/ACM Transactions on Networking, Vol. 9, No. 2, Apr. 2001.12.Y. Zheng, T. Korkmaz, W. Dou,”Two additive-constrained path in the presence of inaccurateinformation”, Computer Communications (COMCOM) Journal, Vol. 30, pp. 2096-2112, 2007.。

References (in APA style papers)In an APA style paper, the citation sources are listed in References on a separate page, which follows the final page of the text. Entries appear alphabetically according to the last name of the author; two or more works by the same author are listed in chronological order by the date of publication. All entries in the References page must correspond to the sources cited in the main text. The writers are supposed to observe the following rules:(1)All lines after the first line of each entry in the reference list should have one-half-inchhanging indentation from the left margin.(2)Authors’ names are inverted (last name first). If the work has more than seven authors, list thefirst six authors and then use ellipses after the sixt h author’s name. After the ellipses, list the last author’s name of the work.(3)Reference list entries should be alphabetized by the last name of the first author of each work.(4)If you have more than one article by the same author, single-author references ormultiple-author references with the exact same authors in the exact same order are listed in order by the year of publication, starting with the earliest.(5)All major words in journal titles are capitalized.(6)When referring to books, chapters, articles, or Web pages, capitalize only the first letter of thefirst word of a title and subtitle, the first word after a colon or a dash in the title, and proper nouns. Do not capitalize the first letter of the second word in a hyphenated compound word.(7)Italicize titles of longer works such as books and journals.(8)Do not italicize, underline, or put quotes around the titles of shorter works such as journalarticles or essays in edited collections.1. Single-Author BookAitchison, J. (1987). Words in the mind: An introduction to the mental lexicon. Oxford: Basil Blackwell Ltd.Bach, K. (1987). Thought and reference. Oxford: Oxford University Press.2. Book with Two or More AuthorsFodor, J., & Lepore, E. (2002). The compositionality papers. Oxford: Oxford University Press. Hatch, E., & Brown, C. (1995). Vocabulary, semantics, and language education. Cambridge: Cambridge University Press.3. An Edited VolumeCole, P. (Ed). (1981). Radical pragmatics. New York: Academic Press.4. Book without Author or Editor ListedWebster’s new collegiate dictionary. (1961). Springfield, MA: G. & C. Merriam.5. Secondary ResourcesSperber, D. (1994). The modularity of thought and the epistemology of representation. In L. A.Hirschfeld, & S. A. Gelman (Eds.), Mapping the mind: Domain specificity in cognition and culture (pp.39-67). Cambridge: Cambridge University Press.6. JournalsBarsalou, L. W. (1982). Context-independent information and context-dependent information in concepts. Memory & Cognition, 10, 82-93.Hu, Y., Wood, J. F., Smith, V., & Westbrook, N. (2004). Friendships through IM: Examining the relationship between instant messaging and intimacy. Journal of Computer-Mediated Communication, 10(1), 38-48.7. DissertationMarunowski, K. R. (2006). The Euro: a multimodal study in presence. Unpublished doctoral dissertation, Kent State University, Kent, Ohio.8. An Entry in an EncyclopediaBergmann, P. G. (1993). Relativity. In The new encyclopedia britannica (Vol. 26, pp. 501-508).Chicago, IL: Encyclopedia Britannica.9. Conference ProceedingsRichardson, J. F., & Richardson, A. W. (1990). On predicting pragmatic relations. In Proceedings of the 16th Annual Meeting of the Berkeley Linguistic Society, Parasession on the Legacy of Grice (pp. 498-508).Berkeley: Berkeley Linguistic Society.10. Article in a MagazineHenry, W. A., III. (1990, April 9). Making the grade in today’s schools. Time, 135, 28-31.11. Article in a NewspaperSchultz, S. (2005, December 28). Calls made to strengthen state energy policies. The Country Today, pp. 1A, 2A.12. Article From an Online PeriodicalBernstein, M. (2002). 10 tips on writing the living Web. A list apart: For people who make websites, 149. Retrieved from /articles/writelivingSample ReferencesReferencesBergmann, P. G. (1993). Relativity. In The new encyclopedia britannica (Vol. 26, pp. 501-508).Chicago, IL: Encyclopedia Britannica.Bernstein, M. (2002). 10 tips on writing the living Web. A list apart: For people who makewebsites, 149. Retrieved from /articles/writelivingCarston, R.(1998). Informativeness, Relevance and Scalar Implicature. In R. Carston & S. Uchida(Eds.), Relevance theory: applications and implications(pp. 179-236). Amsterdam: JohnBenjamins.Carston, R. (2002). Thoughts and utterances: the pragmatics of explicit communication. Oxford:Blackwell.Castle, G. (2007). New millennial Joyce [Review of the books Twenty-first Joyce, Joyce’s critics:Transitions in reading and culture,and Joyce’s mes sianism: Dante, negative existence, and the messianic self]. Modern Fiction Studies, 50(1), 163-173. Available from Project MUSE Web site: /journals/modern_fiction_studies/toc/mfs52.1.htmlGreen, G. (1989). Pragmatics and natural language understanding. Hillsdale, NJ: Erlbaum. Grice, H. P. (1975). Logic and Conversation. In P. Cole & J. Morgan (Eds.), Syntax & semantics: speech acts (vol.3) (pp. 41-58). New York: Academic Press.Henry, W. A., III. (1990, April 9). Making the grade in toda y’s schools. Time, 135, 28-31. Hirschberg, J. (1985). A theory of scalar implicature. Doctoral dissertation, University of Pennsylvania.Horn, R. (1984). Towards a New Taxonomy for Pragmatic Inference: Q-based and R-based Implicature. In D. Schiffrin (Ed.), Meaning, form, and use in context: linguistic applications (pp. 11-42). Washington, DC: Georgetown University Press.Horn, R. (1989). A nature history of negation. Chicago: University of Chicago Press.Huang, Y. (2004). Neo-Gricean Pragmatic Theory: Looking Back on the Past; Looking Ahead to the Future. Journal of Foreign Languages, 149, 2-25.Huang, Y. (2007). Pragmatics. Cambridge: Cambridge University Press.Jiang, W. Q. (2000). Pragmatics: Theories and applications. Beijing: Beijing University Press. Leech, G. N. (1983). Principles of pragmatics. London: Longman.Levinson S. C.(1991). Pragmatic Reduction of the Binding Conditions Revisited. Journal of Linguistics, 27, 107-61.Levinson, S. C. (1987 a). Minimization and Conversational Inference. In J. Verschueren & M.Bertuccelli-Papi (Eds.),The pragmatic perspective(pp. 61-129). Amsterdam: JohnBenjamins.Levinson, S. C. (1987 b). Pragmatics and the Grammar of Anaphora: a Partial Pragmatic Reduction of Binding and Control Phenomena. Journal of Linguistics, 23, 379-434. Matsui, T. (1993). Bridging reference and the notions of “topic” and “focus”. Lingua, 90, 49 - 68. Matsui, T. (2000). Bridging and relevance. Amsterdam: John Benjamins.Mey, J. L. (1993). Pragmatics. Oxford: Blackwell.Morgan, J. L. (1978). Two types of convention in indirect speech acts. In P. Cole (Ed.), Syntax and semantics, vol. 9 (pp. 261-280). New York: Academic Press.Neale, S. (1992). Paul Grice and the Philosophy of Language. Linguistics and Philosophy, 15, 509-559.Parker-Pope, T. (2008, May 6). Psychiatry handbook linked to drug industry. The New York Times.Retrieved from Recanati, F. (1989). The pragmatics of what is said. Mind and Language, 4, 295-329. Recanati, F. (2002). Does linguistic communication rest on inference? Mind and Language, 17, 105-26.Recanati, F. (2004). Literal meaning. Cambridge: Cambridge University Press.Richardson, J. F., & Richardson, A. W. (1990). On predicting pragmatic relations. In Proceedings of the 16th Annual Meeting of the Berkeley Linguistic Society, Parasession on the Legacy of Grice (pp. 498-508).Berkeley: Berkeley Linguistic Society.Sadock, I. (1986). Remarks on the Paper by Deirdre Wilson and Dan Sperber. Chicago Linguistics Society, 22, 85-90.Schultz, S. (2005, December 28). Calls made to strengthen state energy policies.The CountryToday, pp. 1A, 2A.Sperber, D., & Wilson, D. (1986). Relevance: Communication and cognition. Oxford: Blackwell. Sperber, D., & Wilson, D. (1998). Relevance theory. In L. Horn & G. Ward (Eds.), Handbook of pragmatics. Oxford: Blackwell.Welker, K. (1994). Plans in the common ground: toward a generative account of conversational implicature. Doctoral dissertation, Ohio State University.Yuan, Y. L. (1993). On the valence of nouns in Mandarin. Linguistics, 3, 137-206.。

reference是什么意思
英语单词reference有两层含义:
做名词时,它的意思是说到或写到的事;提到,谈及,涉及;参考,查询,查阅;征求,征询。
其复数形式为:references。
做动词时,它的意思是查阅,参考;给......附参考资料。
扩展资料
第三人称单数:references;现在分词:referencing;过去式:referenced;过去分词:referenced。
一般用法
reference可以与以下词性连用:
1、动词,如:have a reference to 和…有关;make a reference 提及
2、形容词,如:future reference 将来参考;good reference 很好的推荐信
3、介词,如:keep it for reference 备作参考;without reference to 不管,不论,与…无关
向你推荐的相关文章
相关文章列表
微信扫码分享。


英文简历十大元素之(10)证明人References在英语简历的最后写出证明人,可以让雇主感觉到你的简历是真实可靠经得起查询的。
如果你的证明人有名望,会对雇主产生一定的影响。
以下几种人可作为证明人的人选:a.校长、系主任、任课老师,这些人可以证明你的学业情况及性格。
b.单位的领导,以便证明你的工作能力、业务成就和个性。
c.同事或同学,通常证明你的个性与爱好。
写证明人应包括姓名、职位、单位、电话及地点。
例如:ReferencesGaoxu Dai, Chairman Prof. Dahai LiDept. of Computers Dept. of ComputersGuangdong Institute of guangdong InstituteCommerce of CommerceGuangzhou GuangzhouTel: 4561790 Tel: 4561791证明人广州广东商学院广州广东商学院计算机系计算机系戴高旭主任李大海教授电话:4561790电话:4561791以上这个例子,适应于大学应届毕业生,证明人一位是系主任,一位是任课教师。
ReferencesMr. Yingming Ma Prof. Fucheng LiuManager Export Dept. Dept. of Interna-Jiangsu Arts and Crafts Corp. tional TradeNanjing Nanjing UniversityTel: 6539402 Tel: 3695718证明人南京江苏工艺品进出口公司南京大学出口部经理国际贸易系马英明先生刘府城教授电话:6539402电话:3695718以上这个例子,适应于大学毕业后才工作一两年的应聘者,证明人一个是工作单位的领导,一个是毕业学校的任课老师。
ReferencesMr. *** Ms. *****Manager, Import Dept. Manager, Export Dept.**************and Export Corp. Co., LtdBeijing NanhaiTel: 88888888证明人***************有限公司进口部经理出口部经理*****先生*****女士电话:88888888以上这个例子,适应于已工作多年的应聘者,所以两个证明人都是自己曾经工作过的单位的负责人。

一.Reference的三种类型: 从书上引用,从杂志里的文章中引用,从网站引用1, 从书上引用的ref,格式:作者名字.年代.书名(斜体).出版社地址: 出版社名Example:Davidson, M. and Cooper, C. (1992). Shattering The Glass Ceiling: The Woman Manger. London: Paul Chapman.2, 从杂志里的文章中引用的ref,格式:作者名字.年代.文章名. 杂志名(斜体): 第几期, 页数Example:Pringle, J. (2004). Women Senior Managers: Successful Individuals Or Markers Of Collective Change. Women’s Studies Journal, 18, (2), 79-963,从网站引用的ref, 格式作者名字.年代.书名(斜体).Retrieved on年月日. from:网站Example:Adler, M. (2005). Women's Employment Concentrated In Service Industries. Retrieved on 20th September, 2005 from:.(注意: 网站另起一行)二, reference 的注意事项:1, 如果reference有两行或两行以上, 从第二行起,向内缩进五到七个字符Example:Rosener, J. (1995). America’s competitive secret: Utilizing women as a management strategy.USA: Oxford University Press.2, reference与reference中间要隔一行3文章名和杂志名:每个单词的首字母大写,虚词除外4,文章后面列出的所有reference必须与加进文章中的reference一一对应5, reference做完以后,以作者的首字为准,按字母顺序进行排列6,一般情况下,1000字,至少四个reference.这里需要强调一点:国外治学严谨,reference一定要做好!!我们的作业严禁直接抄书或从网上直接复制粘贴(这在国外被界定为抄袭)国外的学校有强大的数据库,抄袭的地方,数据库一搜就发现了一旦发现抄袭,轻则挂科,重则拿不到学位,诚信记录还要被写上一笔你可以翻译中文也可以用自己的话把句子转述一遍但是直接引用和一个句子只改2、3个单词是一样会被判抄袭的!To develop a community profile (社区分布)for one Australian Local Government Area (LGA) of your choice, (excluding the City of Boroondara) using data from the 2001 and 2006 Census available from the ABS website. The focus of the demographic profile will be to describe up to three cultural characteristics of the population within your chosen LGA, and look at changes that have occurred from 2001 to 2006.Examples of cultural characteristics are ancestry, birthplace, language spoken, year of arrival in Australia, religious affiliation, English proficiency, and indigenous status. You are expected to synthesise (综合)the information available, not just replicate (折叠,复制)the tables that you can download. For example, you may choose to group a Census table detailing individual birthplaces into categories, and then show the proportional distribution - not just the number by birthplace; or from Year of Arrival in Australia you may derive the number of years living in Australia. In other words, you are required to analyse and summarise the information you find into your own summary tables and charts. In your demographic profile you should include summary tables, charts and commentary to support the graphs and tables. You should make use of data from both the 2001 Census and the 2006 Census (e.g. using a combination QuickStats, MapStats and Census Tables.制定一个社会形象之一澳大利亚地方政府区(儿)您的选择,(不包括城市Boroondara )使用数据从2001年和2006年人口普查可从澳大利亚统计局的网站上。

reference名词解释概述及解释说明1. 引言1.1 概述在撰写学术论文、研究报告、专业文章等过程中,不可避免地需要参考和引用其他已有的文献资料。
为了保证文章的准确性和可信度,提供相关领域的背景知识,并向读者展示作者对文献资源的掌握能力,我们需要使用reference(参考文献)作为支持和证明。
因此,本篇长文将深入解释reference的定义、作用和重要性,并说明其在不同领域的应用。
1.2 文章结构本篇长文将主要分为以下几个部分进行阐述:引言、正文、主要解释说明、实例分析以及结论。
引言部分着重介绍本文的目的和结构概述,让读者对接下来内容有一个清晰的认识。
1.3 目的本篇长文旨在全面而详细地介绍reference并解释其作用和重要性。
通过对reference与引用之间的区别进行阐述,读者将更好地理解如何正确使用reference来支持自己的观点,并规范参考文献的引用方式。
此外,我们还将探讨不同类型reference及其在学术论文中应遵循的标准和规范。
最后,通过实例分析说明reference在实际应用中的价值与意义。
综上所述,本篇长文将帮助读者全面了解reference的定义及其在学术领域的重要作用,并提供正确使用reference以及引用规范的指导,从而提升写作质量和可信度。
一起深入探讨并理解这一有关文献资源的重要主题吧!2. 正文:2.1 定义reference:Reference是一个常见的英语单词,作为名词使用时,它表示对某个实体、事物或概念的引用或提及。
Reference可以是一个书面文献、资源、材料或信息源,也可以是对特定领域中的某个理论、概念或事实的引述。
在学术和研究领域中,reference通常指代与论题相关的参考资料、引文和引用。
2.2 reference的作用和重要性:Reference在各个领域中具有重要作用。
首先,它提供了对已有知识和观点的背景支持,让读者了解特定主题的上下文并深入理解内容。
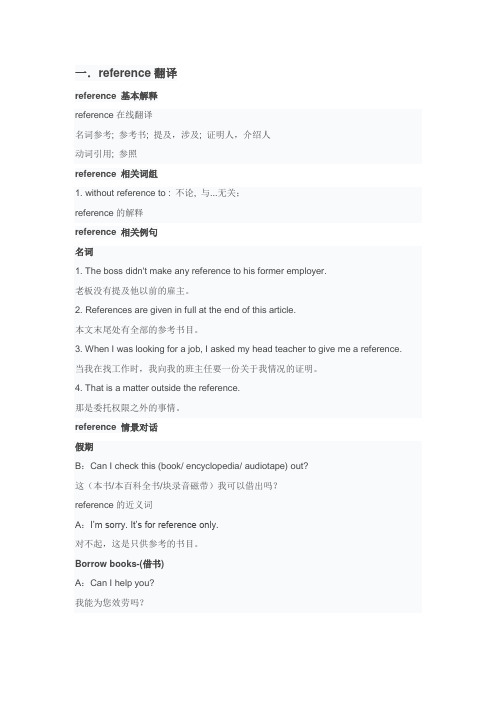
一.reference翻译reference 基本解释reference在线翻译名词参考; 参考书; 提及,涉及; 证明人,介绍人动词引用; 参照reference 相关词组1. without reference to : 不论, 与...无关;reference的解释reference 相关例句名词1. The boss didn't make any reference to his former employer.老板没有提及他以前的雇主。
2. References are given in full at the end of this article.本文末尾处有全部的参考书目。
3. When I was looking for a job, I asked my head teacher to give me a reference. 当我在找工作时,我向我的班主任要一份关于我情况的证明。
4. That is a matter outside the reference.那是委托权限之外的事情。
reference 情景对话假期B:Can I check this (book/ encyclopedia/ audiotape) out?这(本书/本百科全书/块录音磁带)我可以借出吗?reference的近义词A:I’m sorry. It’s for reference only.对不起,这是只供参考的书目。
Borrow books-(借书)A:Can I help you?我能为您效劳吗?B:Yes, I’m doing some research on Roman civilization. Do you have any books on the subject?我在做一些关于罗马文明方面的研究,这方面有没有什么书?A:These books over here are about ancient history. They might be helpful.这里的这些书是关于古代历史的。
ConclusionsA SSERT demonstrates how theory refinement techniques developed in machine learning can be used to effec-tively build student models for intelligent tutoring sys-tems. This application is unique since it inverts the normal goal of theory refinement from correcting errors in a knowledge base to introducing them. A comprehen-sive experiment involving a large number of students interacting with an automated tutor for teaching con-cepts in C++ programming was used to evaluate the approach. This experiment demonstrated the ability of theory refinement to generate more accurate student models than raw induction, as well as the ability of the resulting models to support individualized feedback that actually improves students’ subsequent performance.AcknowledgmentsThis research was supported by the NASA Graduate Student Researchers Program, grant NGT-50732. ReferencesBaffes, P. (1994). Automatic student modeling and bug library construction using theory refinement. Ph.D. diss., Department of Computer Sciences, The University of Texas at Austin. URL: /users/ ml/Baffes, P. and Mooney, R. (1993). Symbolic revision of theories with M-of-N rules. In Proceedings of the Thir-teenth International Joint Conference on Artificial intel-ligence, pages 1135-1140. Chambery, France. Brown, J. S. and Burton, R. R. (1978). Diagnostic mod-els for procedural bugs in basic mathematical skills. Cognitive Science, 2:155-192.Carbonell, J. R. (1970). AI in CAI: an artificial intelli-gence approach to computer-assisted instruction.IEEE Transactions on Man-Machine Systems, 11(4):190-202. Carr, B. and Goldstein, I. (1977). Overlays: a theory of modeling for computer-aided instruction. Technical Report A. I. Memo 406, Cambridge, MA: MIT. Ginsberg, A. (1990). Theory reduction, theory revision, and retranslation. In Proceedings of the Eighth National Conference on Artificial Intelligence, pages 777-782. Detroit, MI.Langley, P., and Ohlsson, S. (1984). Automated cogni-tive modeling. In Proceedings of the National Confer-ence on Artificial Intelligence, pages 193-197, Austin, TX.Langley, P., Wogulis, J. and Ohlsson, S. (1990). Rules and principles in cognitive diagnosis. In Frederiksen,N., Glaser, R., Lesgold, A. and Shafto, M., editors, Diagnostic Monitoring of Skill and Knowledge Acquisi-tion, chapter 10, pages 217-250. Hillsdale, NJ: Lawrence Erlbaum Associates.Nicolson, R. I. (1992). Diagnosis can help in intelligent tutoring. In Proceedings of the Thirteenth Annual Con-ference of the Cognitive Science Society, pages 635-640. Bloomington, IN.Ourston, D. and Mooney, R. (1994). Theory refinement combining analytical and empirical methods.Artificial Intelligence. 66:311-394.Ourston, D. and Mooney, R. (1990). Changing the rules: A comprehensive approach to theory refinement. In Pro-ceedings of the Eighth National Conference on Artificial Intelligence, pages 815-820. Detroit, MI.Quinlan, J. (1990). Learning logical definitions from relations.Machine Learning, 5(3):239-266. Richards, B. and Mooney, R. (1995). Refinement of first-order Horn-clause domain theories.Machine Learning, 19(2):95-131.Sandberg, J. and Barnard, Y. (1993). Education and technology: What do we know? And where is AI?Artifi-cial Intelligence Communications, 6(1):47-58. Sleeman, D. (1987). Some challenges for intelligent tutoring systems. In Proceedings of the Tenth Interna-tional Joint conference on Artificial Intelligence, pages 1166-1168. Milan.Sleeman, D. H. and Smith, M. J. (1981). Modelling stu-dents' problem solving.Artificial Intelligence, 16:171-187.Sleeman, D., Hirsh, H., Ellery, I., and Kim, I. (1990). Extending domain theories: two case studies in student modeling.Machine Learning, 5:11-37.Soloway, E., Rubin, E., Wolf, B., Bonar, J., and Johnson, W. (1983). MENO-II: an AI-based program-ming tutor.Journal of Computer-Based Instruction, 10(1):20-34.Tennyson, R. D. and Park, O. (1980). The teaching of concepts: A review of instructional design research lit-erature.Review of Educational Research, 50(1):55-70. Towell, G. G., Shavlik, J. W., and Noordewier, M. O. (1990). Refinement of approximate domain theories by knowledge-based artificial neural networks. In Proceed-ings of the Eighth National Conference on Artificial Intelligence, pages 861-866. Boston, MA.group.Since the four groups of students each had a different average accuracy on the pre-test and post-test, they were compared using the average improvement in accuracy between pre-test and post-test. Also because each group consisted of different students with no pairing between groups, significance was measured using an ANOVA test. As the only variable between groups was the feed-back received, the significance test used was a 1-way unpaired ANOVA test at the 0.05 level of confidence.The average improvement in performance for the four groups is shown in Table 1. As predicted, the average performance decreased as the feedback varied from A SSERT to reteaching to nothing and the A SSERT group performed significantly better than the other two groups.Accuracy of Student ModelsTo test the accuracy of the learned models at predicting subsequent student behavior, the data from the No Feed-back group was used. This is because no remediation occurred between the pre-test and post-test for the stu-dents in this group; thus, their 20 questions could be treated as a single unit from which training set and test set examples could be drawn. Training-test splits were generated so as to be equivalently representative across both data sets. The 20 examples from the pre-test and post-test were grouped into 10 pairs, where each pair consisted of the two examples (one from the pre-test and one from the post-test) which covered the same domain rule. Then, training and test set splits were generated by randomly dividing each pair.The result was 210 possible training-test set splits. For each of the 25 No Feedback students, 25 training-test splits were generated, yielding 625 samples. For com-parison purposes, we also measured the accuracy of both an inductive learner, using the same training and test set splits, and the correct domain rules. The induc-tive learner was run by starting N EITHER with no initial theory, in which case N EITHER builds rules by induction over the training examples using a propositional version of the F OIL algorithm (Quinlan, 1990). Each system was trained with the training set and accuracy was measured on the test set by comparing what the system predictedGroup Average Pre-test Score Average Post-test Score Average IncreaseA SSERT 44.467.623.2Reteaching 50.858.07.2No Feedback54.856.82.0Table 1: C ++ Tutor remediation test. Scores are percentage of post-test problems answered correctly. Increase is significantbetween A SSERT and the other two groupswith what the student from the No Feedback group actu-ally answered. For the correct theory, no learning was performed, i.e. the correct domain rules were used with-out modification to predict the students’ answers. The results are shown in Table 2. Statistical significance was measured using a two-tailed Student t-test for paired difference of means at the 0.05 level of confidence. As predicted,A SSERT produced more accurate models.Note that induction was even less accurate than simply assuming the student possessed totally correct knowl-edge, clearly indicating the problems with this approach in the typical, limited-data situation.Future WorkThe form of reteaching used in the current experiment is very simple and does not employ any knowledge about the individual student or any knowledge of common mistakes or misconceptions. It does not even consider which questions were answered incorrectly. The experi-ment was designed to test if models constructed by A SSERT were better than no model at all. Experiments comparing A SSERT ’s approach to alternative model-based methods are needed to evaluate the specific advantages of the refinement-based approach with respect to remediation.Unlike previous modeling efforts which focus on pro-cedural tasks,A SSERT is designed for classification domains. As an example of this difference, several pre-vious student modeling efforts have focused on the domain of writing computer programs (Soloway et al.,1983), whereas this research was tested using a classifi-cation task where students were asked to judge the cor-rectness of program segments. This tie to classification domains is largely due to the fact that the most mature theory-refinement algorithms developed thus far are designed for classification and is not a limitation of the general framework of A SSERT per se. As first-order logic refinement methods are enhanced (Richards and Mooney, 1995),A SSERT can be updated accordingly,enabling it to address a wider range of applications.However, note that it is not immediately clear how easy it would be to map A SSERT to a procedural domain.System Average Accuracy A SSERT62.4Correct Theory 55.8Induction49.4Table 2: Results of accuracy test. All differences significantC++ Tutor TestsThe C++ Tutor was developed in conjunction with an introductory C++ course at the University of Texas. The tutorial covered two concepts historically difficult for beginning C++ students: ambiguity involving statements with lazy operators and the proper declaration and use of constants. These two concepts plus examples of cor-rect programs formed three categories into which exam-ple programs could be classified. A set of 27 domain rules was developed to classify problems, using a set of 14 domain features, as being either ambiguous, a com-pile error (for incorrectly declared or used constants) or correct. The latter category was the default category assumed for any example which could not be proved as ambiguous or a compile error.Students who used the tutorial did so on a voluntary basis and received extra credit for their participation. As an added incentive, the material in the tutorial reviewed subjects which would be present on the course final exam. This established a high level of motivation among the students who participated in the test. Due to the large number of students involved (75), the tutorial was made available over a period of four days and students were encouraged to reserve time slots to use the pro-gram.Three major questions were the focus of the test. First, it was important to establish whether or not A SSERT could be an effective modeler for students in a realistic setting. This was measured by testing the model produced for a student on a set of examples taken from the student which had not been given to A SSERT. The predictive accuracy of the model on such novel exam-ples was expected to be higher than simply using the correct rule base or one induced from scratch from stu-dent behavior. Second, even with a perfect model one may not see any increase in student performance. Our hypothesis was that remediation generated using models built by A SSERT would result in increased student per-formance over a control group which received no feed-back. Third, as in previous student modeling studies, we wanted to test how students receiving feedback based on student models would compare against students receiv-ing a simple form of reteaching feedback. The expecta-tion was that remediation based on modeling would result in greater post-test performance. Testing these hypotheses was accomplished with two experiments: one to measure the effects of remediation and another to measure the accuracy of modeling.Effect of Remediation on Student Performance For the remediation test, students who used the C++ Tutor were divided into three groups. One group received the benefits of A SSERT, the second received a very simple form of reteaching, and the third was a con-trol group given no feedback.To test whether A SSERT can impact student perfor-mance, one needs to collect information for each student that has certain characteristics. To begin with, data must be collected both before and after any feedback given to the student to detect any change in performance. Thus the C++ Tutor was constructed as a series of two tests with a remediation session in between. Secondly, the data from the two tests must be equally representative of the student’s capability and must be collected in similar ways.To that end, a program was written to generate 10 example questions as follows. The questions were divided equally among the categories: three questions were correctly labeled as compilation errors, four were examples of ambiguous programs, and three were ques-tions with no errors. This process was used to generate two sets of 10 questions, both of which covered the same subset of the correct rule base. This ensured that the two sets of questions covered the same concepts at the same level of difficulty, though no two questions were identical. These two sets of questions represented the pre-test and post-test to be given to each student. One set of questions was used as the pre-test for all the students, the other as the post-test, thus the same pre-test and post-test was given to every student. To dis-courage cheating, the order in which the 10 questions were presented was randomized. Thus every student answered the same questions, and the only difference was the feedback given between the pre-test and post-test.Students were randomly assigned to three groups of 25, each of which received a different kind of feedback from the C++ Tutor. One group of 25 received no feed-back, acting as the control group. The other two groups were given feedback using explanations and examples as described previously. To ensure that the only differ-ence between feedback groups was the type of feedback received, both groups were given the same amount of feedback; specifically, four examples and four explana-tions for each student.For the “Reteaching” group,A SSERT selected four rules at random from the rule base, and an explanation and example was generated for each rule. The A SSERT group received feedback based on the models con-structed for the student from his or her answers to the pre-test questions. Bugs were selected for remediation based on the order they were found by N EITHER.2 If fewer than four bugs were found, the remainder of the feedback was selected at random as with the Reteaching 2.N EITHER orders its refinements by preferring those which increase accuracy the most with the smallest change.feature vector presented to the student in a multiple-choice format, where the answers available to the stu-dent are taken from among a list of possible categories. This allows A SSERT to be used in concept learning domains, which are common applications for automated training systems. It also means that student actions will translate directly into a form usable by theory refine-ment. Once collected, the labeled examples generated by the student are passed to the N EITHER theory-refine-ment system which modifies the rule base until it repro-duces the same answers as the student.Using the refinements produced by N EITHER,A SSERT generates explanations and examples to reinforce the correct form of the rule or rules modified. The underly-ing approach, called refinement-based remediation, is based on fundamental units of explanation called units of remediation. Rather than implementing any particular pedagogy,A SSERT supplies the most elementary infor-mation required: an explanation with one or more exam-ples. For each refinement detected by N EITHER,A SSERT provides two functions: the ability to explain a correct use of the rule which was changed, and the ability to generate an example which uses the rule. The designer of a tutoring system using A SSERT has the option to gen-erate multiple explanations or examples, to determine the circumstances when such feedback is given, and to decide whether the system or the student controls which explanations and examples are generated. Explanations focus on describing how the correct form of the rule (not the revised version) fits into theoriginally correct rule base. Each rule has an associated piece of stored text, describing its role in the rule base.A full explanation is generated by chaining together the stored text for the rules lying on the proof path for the correct label (not the student’s label) for the example, i.e., the label which is produced by the correct rule base for the given feature vector.Examples are constructed dynamically rather than being drawn from storage. Recall that each refinement made by N EITHER results in the addition or deletion of literals from a rule in the theory. Using normal deduc-tive methods, the added and removed literals can be traced down to the feature vector. The result is a set of conditions in the feature vector which the student is ignoring or a set of extra conditions not present in the feature vector which the student thinks are necessary.A SSERT can thus generate an example which is correct in every way except for the added or missing conditions in the refinement. The result is then presented as a counter example to the student, and the various added or missing conditions highlighted. Note that this corre-sponds very closely to tutorial methods outlined for conceptual domains by (Tennyson and Park 1980). An explanation and example pair is shown in Figure3. This is the explanation generated for the deleted antecedent of the last rule of Figure1.Experimental ResultsThe ultimate test of any tutoring system design is whether or not it enhances student performance. This is especially true for student modeling; if the use of a model cannot significantly impact the educational expe-rience, then there is little reason to construct one. Fur-thermore, this evidence must come from experiments involving large numbers of students in a realistic setting so that the significance of the data can be determined. The importance of student modeling is currently a con-troversial issue (Sandberg & Barnard, 1993); however there are very few controlled studies, with somewhat contradictory results (Sleeman, 1987; Nicolson, 1992). In this section, we presented evidence supporting the claim that A SSERT can be used to construct tutorials which significantly impact student performance. EXPLANATIONOne way to detect a compilation error is to look for an identifier which is declared constant and initialized, then later assigned.A constant identifier is erroneously assigned when it is declared as a constant pointer to an integer, initialized to the address of some integer, and later set to the address of another integer. It does not matter if the identifier is a pointer declared to point to a constant integer or a non-constant integer; once a constant pointer is initialized it cannot be reset to another address.Specifically, note the following which contribute to this error:* There must be a pointer declared to be constant.* A pointer declared constant must be initialized.* A pointer declared constant and initialized must be set after its initialization.Here is an example to illustrate these points:ExampleHere is an example which might appear to be a compile error but is actually CORRECT:void main() {const int x = 5, y, w, *z = &x;z = &w;cin>>w>>y;cout<<((y *= x) || (y > w)); cout<<(w -= x);}This example is NOT a compile error because:* The pointer ‘z’ is declared as a NON-CONSTANT pointer to a constant integer, so it does not have to be initialized and can be reset.Figure3: Example remediation given to a studentrequire user interaction to determine which new bugs to add to an initial hand-constructed library (Sleeman et al., 1990). By contrast, the theory-refinement approach implemented in A SSERT is completely automatic, and by taking advantage of existing correct domain knowledge,it is able to learn more accurate models from limited training data compared to inducing a complete model from scratch.Background on Theory RefinementFor its theory refinement component,A SSERT uses N EI-THER (Baffes & Mooney, 1993) a successor to the E ITHER system developed by Ourston & Mooney (1990,1994).N EITHER employs a propositional Horn-clause knowledge representation. It takes two inputs, a propo-sitional rule base called the theory , which is repaired using a set of input examples . The examples are lists of feature-value pairs chosen from a set of observable domain features. Each example has an associated label or category which should be provable using the theory given the feature values in the example.N EITHER can generalize or specialize a theory, without user interven-tion, and is guaranteed to produce a set of refinements that are consistent with the training examples.Although space limitations prevent us from providing details on theory refinement (see Baffes, 1994), a sum-mary of the technique is as follows. Propositional Horn-clause theories can have four types of errors. An overly-general theory is one that causes an example to be proven in an incorrect category, i.e. a false positive.N EITHER adds new antecedents and deletes rules to fix such problems. An overly-specific theory causes an example not to be proven in its own category, i.e., a false negative.N EITHER deletes existing antecedents and learns new rules to fix these problems. By making these four kinds of syntactic rule changes,N EITHER can correct the semantics of the theory by altering the condi-tions under which rules are satisfied.1 A sample theory and examples are shown in Figure 1.Description of A SSERTA SSERT views tutoring as a process of communicating knowledge to a student, where the contribution of the modeling subsystem is to pinpoint elements of the inter-nal knowledge base to be communicated. Figure 2shows a schematic of the A SSERT algorithm. It is assumed that all actions taken by a student can be bro-ken down to a set of classification decisions . That is,given a set of inputs, called problems , the student will produce a set of labeled examples which classify each of the problems into one category. Each problem consists of one or more feature vectors describing some aspect of the problem. The task of the student is to produce a label for each feature vector, selected from among some predetermined set of legal labels given to the student.In its simplest form, a problem consists of a single1.N EITHER ’s running time is linear in the size of the theory.StudentLabeled Correct Theory Rule ChangesRefinement-Based Explanation & Examples Rule BaseExamples RefinementRemediationFigure 2: Basic design of the A SSERT algorithmExample 1Example 2Example 3Example 4category compile-error not compile-error compile-error compile-errorpointer constant non-constant non-constant non-constant pointer-init true false true falsepointer-settrue true true trueinteger constant non-constant non-constant non-constant integer-inittrue true true trueinteger-setby-pointer yes no no Figure 1: Sample theory and examples. The original theory,shown in plain text, misclassifies examples 3 and 4. The corrected theory is shown with two deleted antecedentsunderlined and an added antecedent in boldface.R1: compile-error ← constant-not-init R2: compile-error ← constant-assignedR3: constant-not-init ←(pointer constant)∧ (pointer-init false)∧R4: constant-not-init ← (integer constant)∧ (integer-init false)R5: constant-assigned ← (integer constant)∧ integer-init ∧ (integer-set yes)R6: constant-assigned ← (integer constant)∧ integer-init ∧R7: constant-assigned ←(pointer constant) ∧ pointer-init ∧ pointer-set(integer-set by-pointer)(integer-set no)Appears in Proceedings of the Thirteenth National Conference on Artificial Intelligencepp. 403-408, Portland, OR, August 1996 (AAAI-96 Best Paper Award)A Novel Application of Theory Refinement to Student ModelingPaul T. BaffesSciComp Inc5806 Mesa Drive, Suite 250 Austin Texas 78731baffes@Raymond J. MooneyUniversity of Texas at Austin Department of Computer Sciences, Taylor Hall 2.124Austin Texas 78712mooney@AbstractTheory refinement systems developed in machine learn-ing automatically modify a knowledge base to render it consistent with a set of classified training examples. We illustrate a novel application of these techniques to the problem of constructing a student model for an intelli-gent tutoring system (ITS). Our approach is implemented in an ITS authoring system called A SSERT which uses theory refinement to introduce errors into an initially correct knowledge base so that it models incor-rect student behavior. The efficacy of the approach has been demonstrated by evaluating a tutor developed withA SSERT with 75 students tested on a classification taskcovering concepts from an introductory course on the C++ programming language. The system produced rea-sonably accurate models and students who received feedback based on these models performed significantly better on a post test than students who received simple reteaching.IntroductionTheory refinement methods developed in machine learn-ing were designed to aid knowledge acquisition by using a database of classified examples to automatically make revisions that improve the accuracy of a knowl-edge base (Ginsberg, 1990; Ourston & Mooney, 1990 Towell & Shavlik, 1990). These learning techniques have been used to correct errors in an imperfect rule base elicited from an expert and thereby produce a more accurate knowledge base than purely inductive learning methods. In this paper, we present a particularly novel application of theory refinement to a very different problem, that of producing a student model for an intel-ligent tutoring system (ITS). By inverting the standard goal of theory refinement, we show how it can be used to produce a model of a student’s knowledge that is use-ful for automated tutoring.Typically, the knowledge base in theory refinement is considered incorrect or incomplete and the examples represent correct behavior which the knowledge base should be able to emulate. However, the refinement pro-cedure itself is blind to whether or not the initial knowl-edge base is “correct” in any absolute sense; the theory-refinement process merely modifies the knowledge until it is consistent with the examples. Thus, one can also start with a correct knowledge base and examples of erroneous conclusions, and use theory refinement to introduce errors that cause the knowledge base to model the incorrect conclusions illustrated in the examples. In this way, theory refinement provides a basis for refine-ment-based student modeling. Starting with a represen-tation of the correct knowledge of the domain, and examples of erroneous student behavior, theory refine-ment can introduce “faulty” knowledge that accounts for the student’s mistakes. The resulting changes consti-tute a model of the student which can be used directly to guide tutorial feedback by comparing the refinements with the elements of correct knowledge they replaced. We have implemented this approach in an ITS author-ing system called A SSERT,which was then used to develop a tutor for teaching concepts in C++ program-ming. A controlled experiment with 75 students was conducted to evaluate the resulting tutor. The system produced reasonably accurate models, and students who received directed feedback based on these models per-formed significantly better on a post test than students who received simple reteaching.Background on Student modelingIn order to tailor instruction to individual students, one of the primary tasks of most intelligent tutoring systems is to construct a model of the student’s knowledge which is then used to guide the feedback and informa-tion presented. The simplest type of model is an overlay model (Carbonell, 1970; Carr & Goldstein, 1977) which assumes that a student's knowledge is a subset of the correct domain knowledge. Unfortunately, this approach is unable to model incorrect student knowledge. Other researchers have focused on constructing databases of student misconceptions typically termed bug libraries (Brown & Burton, 1978; Sleeman & Smith, 1981). However, hand-constructing such libraries by analyzing student protocols is a difficult, time-consuming task and the result is incapable of modeling unanticipated student behavior. More recent work has focussed on using machine learning techniques to automate the construc-tion of student models. However, existing methods require inducing a complete model of student knowl-edge (both correct and incorrect) from limited training data (Langley & Ohlsson, 1984; Langley et al., 1990) or。