RTU教育训练-2D(R2K) (新桃2014)
- 格式:ppt
- 大小:4.32 MB
- 文档页数:133

硬件资料一、ControlwaveMICRO系列ControlwaveMICRO硬件包括1.CPU模块32 位150Mhz CPU 和数学协处理器- 1 或者2 MB 电池备份静态存储器(SRAM)- 4MB,12 或者20 MB 高速并行动态存储器(SDRAM)- 512kB Boot/Downloader BIOS 闪存- 8 或者16 MB 闪存-在6ms内完成AGA8复杂计算-在125us内完成AGA3- 在6us内完成PID 回路计算两个RS-232 和一个RS-485 通讯口10/100自适应以太网接口(可选择)每个通讯端口两个LED灯6 个状态LED灯、idle指示灯和看门狗灯CPU模块配置拨盘:Flash写保护SW1-3:恢复出厂设置CPU Bd. Switch SW2 -用户配置:CPU Module Switch SW3(COM3) –用户配置:CPU模块LEDs:2.电源模块Power Supply/Sequencer Module (PSSM)电源模块LED状态灯十六进制代码:电源模块LED状态灯十六进制代码含义:3.机架4.通讯模块5.I/O模块12DI + 4DO16DI 或者16DO分离的输出配置“保持最后值或者归零”6AI 或者6AI + 2AO8AI 或者4AO跳线选择1-5V 或者4-20mA14 位A/D输入, 12位D/A输出Analog outputs configurable for 'Hold last value or preset value' 模拟量输出可配置为“保持最后值或者设定值”4 HSC3Vdc 到24Vdc 输入I/O模块安装及接线16点DI模块16点DI跳线分配16点DI配置图解16点DO模块8点AI模块8点AI模块跳线分配及配置图解4点AO模块4点AO配置图解RS232通讯端口电缆接线图软件配置Local View运行Local ViewLocal View 初始画面输入名字,点击来到一下画面点击点击点击配置黄色部分即可:写配置文件时,注意蓝色部分应只有RDB_MAX一个用户。

对RTU丢失数据问题的分析及解决办法
孙全熙;王平欢;张栋;贺建伟
【期刊名称】《宁夏电力》
【年(卷),期】2009(000)0z1
【摘要】针对RTU以多个规约向多个主站上传数据时,丢失数据的现象比较严重的问题进行了详细的分析,提出了解决方案.
【总页数】3页(P152-154)
【作者】孙全熙;王平欢;张栋;贺建伟
【作者单位】宁夏电力调度中心,宁夏,银川市,750001;宁夏电力调度中心,宁夏,银川市,750001;宁夏中卫供电局,宁夏,中卫市,755000;宁夏银川供电局,宁夏,银川
市,750001
【正文语种】中文
【中图分类】TM765
【相关文献】
1.常见数据丢失问题的分析及恢复方法 [J], 任兴洲
2.转K6型转向架轴箱橡胶垫铜绞线及组装螺栓丢失问题解决办法 [J], 刘景岩
3.对RTU丢失数据问题的分析及解决办法 [J], 孙全熙;王平欢;张栋;贺建伟
4.高校图书馆现刊丢失破损问题的解决办法 [J], 项冰
5.光驱丢失的硬件设备原因分析及解决办法 [J], 崔新潮
因版权原因,仅展示原文概要,查看原文内容请购买。

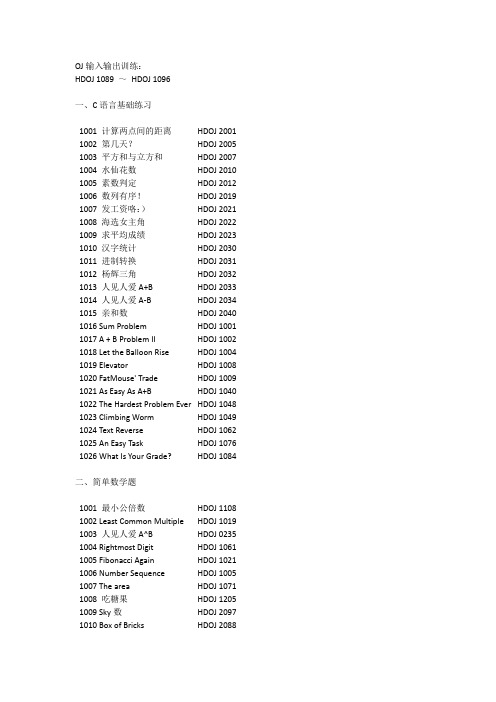
OJ输入输出训练:HDOJ 1089 ~HDOJ 1096一、C语言基础练习1001 计算两点间的距离HDOJ 2001 1002 第几天?HDOJ 2005 1003 平方和与立方和HDOJ 2007 1004 水仙花数HDOJ 2010 1005 素数判定HDOJ 2012 1006 数列有序!HDOJ 2019 1007 发工资咯:)HDOJ 2021 1008 海选女主角HDOJ 2022 1009 求平均成绩HDOJ 2023 1010 汉字统计HDOJ 2030 1011 进制转换HDOJ 2031 1012 杨辉三角HDOJ 2032 1013 人见人爱A+B HDOJ 2033 1014 人见人爱A-B HDOJ 2034 1015 亲和数HDOJ 2040 1016 Sum Problem HDOJ 1001 1017 A + B Problem II HDOJ 1002 1018 Let the Balloon Rise HDOJ 1004 1019 Elevator HDOJ 1008 1020 FatMouse' Trade HDOJ 1009 1021 As Easy As A+B HDOJ 1040 1022 The Hardest Problem Ever HDOJ 1048 1023 Climbing Worm HDOJ 1049 1024 Text Reverse HDOJ 1062 1025 An Easy Task HDOJ 1076 1026 What Is Your Grade? HDOJ 1084二、简单数学题1001 最小公倍数HDOJ 1108 1002 Least Common Multiple HDOJ 1019 1003 人见人爱A^B HDOJ 0235 1004 Rightmost Digit HDOJ 1061 1005 Fibonacci Again HDOJ 1021 1006 Number Sequence HDOJ 1005 1007 The area HDOJ 1071 1008 吃糖果HDOJ 1205 1009 Sky数HDOJ 2097 1010 Box of Bricks HDOJ 20881011 简易版之最短距离HDOJ 20831012 Fibbonacci Number HDOJ 20701013 Coin Change HDOJ 20691014 A + B Again HDOJ 20571015 Lowest Common Multiple Plus HDOJ 20281016 Can you solve this equation? HDOJ 21991017 Strange fuction HDOJ 28991018 Pseudoprime numbers HDOJ 19051019 Delta-wave HDOJ 10301020 月之数HDOJ 25021021 又见GCD HDOJ 25041022 找新朋友HDOJ 12861023 七夕节HDOJ 12151024 完数HDOJ 1406三、递推求解1001 超级楼梯HDOJ 20411002 不容易系列之二HDOJ 20421003 一只小蜜蜂... HDOJ 20441004 不容易系列之(3)——LELE的RPG难题HDOJ 20451005 骨牌铺方格HDOJ 20461006 折线分割平面HDOJ 20501007 母牛的故事HDOJ 20181008 下沙的沙子有几粒?HDOJ 12671009 自共轭Ferrers图HDOJ 12461010 汉诺塔II HDOJ 12071011 悼念512汶川大地震遇难同胞——重建希望小学HDOJ 2190 1012 Children’s Queue HDOJ 12971013 Tiling_easy version HDOJ 25011014 统计问题HDOJ 25631015 Buy the Ticket HDOJ 11331016 Game of Connections HDOJ 11341017 Computer Transformation HDOJ 10411018 Children’s Queue HDOJ 12971019 The Number of Paths HDOJ 12931020 "下沙野骆驼"ACM夏令营HDOJ 129四、简单典型DP1001 数塔HDOJ 20841002 Super Jumping! Jumping! Jumping! HDOJ 10871003 免费馅饼HDOJ 11761004 Common Subsequence HDOJ 11591005 搬寝室HDOJ 14211006 Humble Numbers HDOJ 10581007 Max Sum HDOJ 10031008 Max Sum Plus Plus HDOJ 10241009 FatMouse's Speed HDOJ 11601010 Bone Collector HDOJ 26021011 Piggy-Bank HDOJ 11141012 I NEED A OFFER! HDOJ 12031013 悼念512汶川大地震遇难同胞——珍惜现在,感恩生活HDOJ 2191 1014 Coins HDOJ 2844五、简单博弈1001 Brave Game HDOJ 18461002 Good Luck in CET-4 Everybody! HDOJ 18471003 Fibonacci again and again HDOJ 18481004 Rabbit and Grass HDOJ 18491005 Being a Good Boy in Spring Festival HDOJ 18501006 kiki's game HDOJ 21471007 Public Sale HDOJ 21491008 悼念512汶川大地震遇难同胞——选拔志愿者HDOJ 21881009 丑数游戏1010 YLF's Game六、半程测试1001 CD HDOJ 37631002 Alaska HDOJ 37641003 Celebrity Split HDOJ 37651004 Knight's Trip HDOJ 37661005 Paintball HDOJ 37671006 Shopping HDOJ 37681007 Stack Machine HDOJ 37691008 Ideas HDOJ 37701009 HST HDOJ 37711010 Tunnelling the Earth H DOJ 3772七、母函数1001 Ignatius and the Princess III HDOJ 10281002 Square Coins HDOJ 13981003 Holding Bin-Laden Captive! HDOJ 10851004 Big Event in HDU HDOJ 11711005 Fruit HDOJ 21521006 The Balance HDOJ 1709八、并查集1001 How Many Tables HDOJ 1213 1002 小希的迷宫HDOJ 1272 1003 Is It A Tree? HDOJ 1325 1004 More is better HDOJ 1856 1005 Constructing Roads HDOJ 1102 1006 畅通工程HDOJ 1232 1007 还是畅通工程HDOJ 1233 1008 畅通工程HDOJ 1863 1009 畅通工程再续HDOJ 1875 1010 继续畅通工程HDOJ 1879共26 + 24 + 20 + 14 + 10 + 6 + 10 = 110 题。


阿尔卡特软件开局步骤目录1. 从笔记本电脑下载SDH设备原始软件至SDH (3)2. 1320CT终端调试软件操作 (7)2.1. 启动1320CT,进入网元分析器 (7)2.2. 进入设备界面 (8)2.3. 网元初始时间设置 (11)2.4. 激活工作软件(DOWNLOAD-‐-‐-‐U NITS I NFO) (12)2.5. 时钟配置 (13)2.6. 打开告警 (15)2.7. 业务配置 (16)2.8. MSP保护 (21)2.9. 地址设置 (23)2.10. 退出1320CT (23)3. 2M业务穿通与落地 (24)1.从笔记本电脑下载SDH设备原始软件至SDH(1)下载数据线缆连接:DB9(一边公头一边母头)的RS232串口线母头接电脑,母头接监控盘EQUICO (SL22:22曹位)。
如果是1650smc接在SYNTH1N (SL09曹位) (2)准备一根交叉网线:一边与电脑的网卡相连,一边与电源盘CONGI (SL11:11曹位)相连。
(如果是1650smc接在SL04曹位)(3)SDH设备加电,同时启动 SIBDL出现下图命令行窗口拖拽进去之后路径会显示在source file的下方输入大写的TELNET,回车,然后输入本机的ip地址,回车输入小写 y回车待进度条走到100,写入成功选择选项4,回车,退出SIBDL最后退出SIBDL下载程序。
SDH设备关电,然后重新加电;SDH设备再次关电,重新加电。
等待SL22槽位监控盘、SL23槽位MATRIXN矩阵盘、SL11槽位CONGI盘工作指示等变绿。
2.1320CT终端调试软件操作2.1.启动1320CT,进入网元分析器,如下图:单击右键然后左键单击startsupervision2.2.进入设备界面 单击右键然后左键单击show equipment,然后输入用户名密码,均为大写的ADMIN,回车后进入设备监控页面蓝叉处代表需要添加相关的板卡添加板卡步骤注:配置单板时候如需删除单板再重新添加,需先把单板状态设定成set out of service, 然后remove, 之后就可以重新添加单板了。


DSTR培训资料DSTR培训资料(一)自古以来,人们一直追求知识和技能的提升。
随着现代科技的飞速发展,培训已经成为了人们不可或缺的一部分。
DSTR培训资料作为一种高质量的学习资源,为学员提供了各种各样的教育和训练,帮助他们提升专业技能和实现个人成长。
首先,DSTR培训资料提供了全面且系统的课程内容。
无论是初学者还是已经有一定经验的人员,都可以从中找到适合自己的培训课程。
这些课程通常覆盖了相关行业的基础知识和技术,帮助学员建立坚实的基础。
此外,DSTR培训资料还会根据市场需求和行业动态不断更新课程内容,保持与时俱进,确保学员学习到最新、最有效的知识。
其次,DSTR培训资料强调实践和实战能力的培养。
在课程中,学员会有机会参与各种实际案例的分析和解决,通过模拟真实场景来训练自己的应对能力。
这种实践性的学习方式可以帮助学员更好地理解所学知识,并能够将其应用到实际工作中。
通过反复练习和实践,学员可以逐渐提升自己的技能水平,更加熟练地应对各种挑战。
此外,DSTR培训资料还注重培养学员的创新和思考能力。
在学习过程中,学员会被鼓励思考问题的本质和解决问题的不同方法。
培训资料中通常会提供一些案例和讨论,激发学员的思维,帮助他们培养批判性思维和创新思维能力。
这些培养可以使学员在工作中更好地应对复杂的情况和问题,提出创新的解决方案,从而在职场中取得更好的发展。
最后,DSTR培训资料还提供了学习资源的灵活性和便捷性。
学员可以根据自己的时间和需求,自由选择学习的时间和地点。
培训资料通常以电子书籍、音频和视频的形式提供,学员可以随时随地通过电脑、手机等设备进行学习。
这种灵活性不仅方便了学员的学习,还可以让学员根据自己的进度进行学习,提高学习效率。
综上所述,DSTR培训资料通过全面的课程内容、实践和实战能力的培养、创新思维的培养以及学习资源的灵活性和便捷性,为学员提供了高效、便捷、灵活的学习方式和资源,帮助他们提升专业技能和实现个人成长。


S802.1X/EAP AUTHENTICATION GUIDE802.1X/EAP AUTHENTICATION GUIDERADIUSNT/X V5.1IEA Software, Inc.Administrative and Support OfficePO BOX 1170Veradale, Washington 99037Phone: (509) 444-BILLSales@Support@Software License AgreementBy purchasing or installing RadiusNT or RadiusX, you indicate your acceptance of the following License Agreement.Ownership of Software You acknowledge and agree that the computer program(s) and associated documentation contained with RadiusNT or RadiusX (collectively, the Software) are owned exclusively by IEA Software, Inc. and/or its licensors. The Software contained in the package is protected under copyright laws and all copyright and other intellectual property rights relating to the Software are and remain the exclusive property of IEA Software, Inc. and/or its licensors. You may not rent or lease the Software, but you may transfer the Software and accompanying materials on a permanent basis provided you retain no copies and the recipient agrees to the terms of this Agreement.License IEA Software, Inc. grants to you, and you accept, a limited, non-exclusive and revocable license to use the Software. You agree to use the Software in machine-readable object code form only as authorized in this License Agreement. This License Agreement does not convey any title or interest in the Software to you.Scope of License You may not make any changes or modifications to the Software, and you may not de-compile, disassemble, or otherwise reverse engineer the Software. You may not lend, rent, lease or sublicense the Software or any copy to others for any purpose. RadiusNT or RadiusX may only be installed on a single WindowsNT, Solaris, Linux or Cobalt Networks workstation or server. Additional servers may be purchased separately. You agree to use reasonable efforts to protect the Software from unauthorized use, modifications, reproduction, distribution and publication. You are not permitted to make any uses or copies of the Software that are not specifically authorized by the terms of this License Agreement. Your adherence to this License Agreement will allow IEA Software, Inc. to continue developing innovative and useful products and providing a high level of customer service and support. If you do not comply with the terms of this License Agreement, your license will be revoked.Updates and Support All software updates and fixes are available via the IEA Software, Inc. Web site. Major version upgrades are not included or covered as part of the basic purchase agreement. Technical support is currently available via methods listed on our Web site Support section at /support.Restricted Rights The Software is provided with U.S. Governmental Restricted Rights. Use, duplication, or disclosure by the Government is subject to restrictions set forth in subparagraph ©(1)(ii) of The Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 or subparagraphs ©(1) and (2) of the Commercial Computer Software - Restricted Rights at 48 CFR 52.227-19 as applicable. The Software is also protected by International Treaty Provisions. Manufacturer is IEA Software, Inc. PO BOX 1170 Veradale WA, 99037.Miscellaneous This License Agreement shall be construed, interpreted and governed by the laws of the State of Washington. Should any term of this License Agreement be declared void or unenforceable by any court of competent jurisdiction, enforcement of the remaining terms shall not be affected. Failure of either party to enforce any rights or to take action against the other party in the event of any breach of this Licensing Agreement shall not be deemed a waiver of any subsequent enforcement of rights.Limitations of Liability and Remedies In no event shall IEA Software, Inc. or its licensors be liable for any loss of profit or any other commercial damage, including but not limited to special, incidental, consequential or other damage, even if IEA Software, Inc. or its licensors are advised, in advance, of the possibility of such damages. IEA Software, Inc. and its licensor’s entire liability and your exclusive remedy shall be, at IEA Software’s option, either (a) return of the price paid, or (b) repair or replacement of the Software. To the maximum extent permitted by applicable law, IEA Software, Inc. and its licensors disclaim all other warranties, either express or implied, including but not limited to, implied warranties with regard to the Software and the accompanying material. This Limited Warranty is void if failure of the Software has resulted from accident, abuse or misapplication. You may have other specific legal rights, which vary from state/jurisdiction to state/jurisdiction.Return Policy It is our goal to provide customers with the highest level of satisfaction possible. In order to ensure that our products work well in your environment, IEA Software offers a 30-day FULL functioning software trial that includes documentation and support. If you require more than 30 days to evaluate the software, we are happy to work with you to extend the trial to a length that fits your timetable. This gives you, the user, an opportunity to ensure that the product fully meets your needs. (Please test the software in a non-production environment.) In light of the trial period and opportunity to fully test our software, IEA Software maintains the policy that no refunds will be offered. We will, however, address any problems with the software.Should a software anomaly occur, our Development and Support Teams will work to correct the problem. Please note that you must be using the application normally, as defined, and you must ensure that the bug is not due to anomalies in other programs, the operating system, your hardware, or data.In order to address any problems, please note that the bug must be able to be reproduced. Our Development and Support Teams will require full documentation of the steps taken by the user that caused the error in the software as well as necessary data and scenario files to reproduce the error. Contact Should you have any questions concerning this license agreement, please contact IEA Software, Inc. PO BOX 1170 Veradale, WA 99037 U.S.A. (509) 444-BILL (2455).Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, without the express written consent of IEA Software, Inc.TrademarksEmerald Management Suite, RadiusNT and RadiusX are trademarks of IEA Software, Inc. All images, photographs, animations, audio, video and text incorporated into the Software are owned by IEA Software, Inc., unless otherwise noted by Trademark. Intel is a registered trademark of Intel Corporation. Transact-SQL is a registered trademark and DB-Library is a trademark of Sybase, Inc. Cobalt, RAQ, and Solarisare trademarks of Sun Microsystems. Cisco is a trademark of Cisco Systems. All other trademarks are the property of their respective owners.© 1995-2010 IEA Software, Inc.All Rights Reserved, World WideTable Of ContentsSOFTWARE LICENSE AGREEMENT (1)T RADEMARKS (2)EAP AUTHENTICATION, WHAT IS IT AND HOW DOES IT WORK? (4)WHICH EAP TYPE (AUTHENTICATION PROTOCOL) IS RIGHT FOR ME? (6)VERSIONS AND EDITIONS OF RADIUSNT/X SUPPORTING EAP AUTHENTICATION (7)CONFIGURING RADIUSNT/X FOR EAP AUTHENTICATION (8)PEAP CERTIFICATES, SIGNING REQUIREMENTS AND EXAMPLES (9)E XAMPLE CREATING A CERTIFICATE SIGNING REQUEST FOR A CERTIFICATE AUTHORITY (9)E XAMPLE CREATING A ‘SELF-SIGNED’ CERTIFICATE (9)WINDOWS SUPPLICANT CONFIGURATION EXAMPLE (11)WIRELESS LAN SUPPLICANT INTEROPERABILITY (12)QUESTIONS & ANSWERS (13)EAP Authentication, what is it and how does it work?In the RADIUS world several standard authentication protocols exist such as PAP, CHAP andMSCHAPv1/2. Normally to authenticate -- The Access server and end user client first negotiate the authentication protocol to be used. After choosing one (PAP, CHAP, MSCHAPv1/2, EAP, ) theappropriate data for the choosen authentication protocol is sent to the RADIUS server for authentication.In this standard scenario all three systems (RADIUS, Access Server, End User client) must agree with and have specific knowledge of the authentication protocol being used.Access Server (RADIUS Client)EAP: Pass-ThruRadiusNT/X (RADIUS Server)EAP:AuthenticatorEnd User (Client)EAP: SupplicantAs the complexity of relationships between systems and increasing need for more elaborate and secure authentication methods grows the problems associated with this solution become difficult to manage. The Extensible Authentication Protocol (EAP) protocol attempts to solve the following problems with minimal change to existing network infrastructure.1. Authentication protocol negotiation between access server and end user does not consult theRADIUS authentication in the initial authentication step. The RADIUS server may not allow or agree with the authentication protocol negotiated between access server and end user. If this happens the authentication fails. A classic example of this problem can be found with RADIUS servers configured to authenticate against a one-way encrypted backend database. This was common with many UNIX and Windows user databases. Since the RADIUS CHAP protocol requires access to plain text unencrypted passwords, a client and server that unknowingly agree on CHAP are in for quite a surprise when the RADIUS server finds its impossible to authenticate their request.2. Today the variety of RADIUS capable access servers number in the hundreds, many have verylimited processing and memory capacity available for client authentication. Allowingauthentication details to pass through the access server allows newer authentication protocols to be deployed with fewer changes and with less interoperability problems.3. Trust is the foundation of every network security system. Historically RADIUS in the dialupenvironment trusted the public telephone network enough to enable most applications to be considered secure. Given today’s wireless networks, global roaming environments and large areas on shared cable networks there is no clear single entity providing services over the avaliable medium. Therefore in many cases the End User cannot trust the Access Server or intermediate proxies with the task of handling passwords or authentication protocol negotiation.In order to solve these and other problems with minimal change to existing systems the EAP and later Protected-EAP protocols were designed. EAP simply provides a conduit between the Authenticator and Supplicant (RADIUS and End-User client) where they discuss the best way to authenticate and then actually go about the task of authenticating. This removes the Access Server from taking part in the authentication process. Since EAP itself is merely a conduit, it can be thought of as a computers operating system. An operating system in itself is useless without applications to run. EAP types provide these ‘applications’ by providing the authentication protocol used to perform the actual authentication step. In this way future authentication protocols can be easily added by adding new EAP types to the Authenticator and Supplicant.Protected-EAP (PEAP) is an EAP type providing the EAP protocol over an encrypted, certificate-authenticated conduit. In addition to the encryption it also offers keying material that can be used by the RADIUS server and End-User client to establish a secure link for all future network traffic (WEP,WPA/AES, etc). Since PEAP itself implements the EAP protocol, just over a more secure, encrypted channel, it too requires an EAP type of its own to execute. The diagram below illustrates this relationship.PEAP uses the same technology used today to protect secure web sites on the Internet. The PEAP protocol uses TLS v1 (essentially SSL) and utilizes the same trusted third party public key infrastructure (PKI) as secure web sites.EAP-TTLS is identical to PEAP using PKI infustructure to protect PAP, CHAP and MSCHAPv2 authentication protocols.Which EAP Type (authentication protocol) is right for me?Typically for 802.1x/EAP you choose EAP types supported by client software your end users already have or can reasonably be made available to them. EAP-PEAPv0-MSCHAPv2 is a popular choice as it is included with all currently available versions of Microsoft windows and supported by major competing platforms such as Linux and MAC.When using a backend authentication database containing UNIX or LDAP passwords choices for authentication may be limited to PAP, EAP-TTLS-PAP or EAP-PEAP-GTC. This is because CHAP requires access to password plaintext and MSCHAP requires access to plaintext or NT Hash.The following table provides a simple listing of all supported authentication protocols and their realitive strengths and weaknesses. Detailed evaluations of each protocol can be found on the Internet.Protocol Offlineattack Severe flawsknownUNIX/NT/LDAPcompatibilityMutual auth EncryptionkeysPAP See #1 See #1 Yes No NoCHAP Yes No See #4 No No MSCHAPV1 Yes Yes See #3 No Yes MSCHAPV2 Yes No See #3 Yes YesHTTP Digest Yes No See #4 Yes NoEAP-MD5 Yes No See #4 No NoEAP-GTC See #2 See #2 Yes No NoEAP-LEAP Yes Yes See #3 Yes YesEAP-PEAP-MSCHAPv2 No No See #3 Yes YesEAP-PEAP-GTC No No Yes No YesEAP-PEAP-MD5 No No See #4 No YesEAP-TTLS-MSCHAPv2 No No See #3 Yes YesEAP-TTLS-PAP No No See #3 No YesEAP-TTLS-CHAP No No See #4 No YesEAP-TTLS-MSCHAPv1 No No See #3 No Yes#1. PAP passwords are encrypted between RADIUS server and access server. Password security is dependant upon link between access server and client over which the password travels. RADIUS encryption can be improved by choosing RADIUS shared secrets with 16 or more characters. It can be further improved by using additional layer2/3 security such as a physically secure switched network and IPSec.#2. GTC information is not encrypted between RADIUS server and access server providing less security than standard RADIUS PAP. Security can be improved by using additional layer2/3 security such as a physically secure switched network and IPSec.#3. While possible RadiusNT/X v4 and v5 does not currently support authentication against Active directory or NT SAM using this protocol. UNIX password authentication is not possible using this protocol. LDAP authentication is possible provided clear text passwords are made available to RadiusNT/X by the directory server.#4. Of the three only LDAP authentication is possible provided clear text passwords are made available to RadiusNT/X by the directory server.Versions and editions of RadiusNT/X supporting EAP Authentication We recommend at least RadiusNT/X 5.1.36 to authenticate and proxy EAP authentication requests. While previous versions of RadiusNT 5 work successfully in most environments, additional EAP types, EAP proxy and compatibility improvements have since been made to better support EAP in a variety of environments. If you are using a prior version of RadiusNT/X v5 contact our support department (support@) to obtain an update or visit the IEA Software download center.If you are evaluating Emerald v5 standard or RadiusNT/X standard EAP feature licensing is available which allows you to take advantage of EAP features without having to move to the professional or hotspot editions of the software. Please contact your sales representative or sales@ to discuss EAP feature licensing.Customers using the previous versions of Emerald 4.5 /w RadiusNT/X version 4 must purchase a RadiusNT/X version 5 upgrade licenses. If you have purchased Emerald 4.5 in December of 2003 or later and are currently using RadiusNT/X v4, contact our sales group to receive a complimentary RadiusNT/X version 5 upgrade license.If you have a RadiusNT/X v5 license, it must be a RadiusNT/X v5 professional or enterprise license. RadiusNT/X v5 standard does NOT support EAP without the EAP feature enabled.In summary EAP requires at least RadiusNT/X 5.0.42 Professional, Enterprise or the standard edition with the EAP license feature enabled.If you have RadiusNT 2.5, 3.0, or 4.0 and would like to take advantage of EAP features please contact our sales group about purchasing an upgrade license (sales@)Configuring RadiusNT/X for EAP AuthenticationGenerally very little if any configuration is necessary to support most end user clients. EAP support is automatically enabled as long as you’re licensed for EAP features. To configure EAP Authentication, open the RadiusNT/X admin and select the EAP menu option.Option DescriptionPreferred EAP method This should reflect the EAP method most of your clients will be using. Thisimproves latency of requests slightly by making protocol negotiation easierfor the client and server.Preferred PEAP method This should reflect the PEAP method most of your clients will be using.This improves latency of requests slightly by making protocol negotiationeasier for the client and server.PEAP/TTLS Certificate SSL certificate file containing a public and private key in PEM (Base64)format concatenated together in a single file. Please see the section onPEAP certificates below for more information.PEAP/TTLS CA Certificate Your CA’s certificate chain file in PEM (Base64) format.PEAP version negotiation PEAP protocol version negotiation, the default setting is ‘PEAP v0 or v1’ toallow either version client to authenticate. Typically limiting negotiation toversion 0 provides the best compatibility between clients.Note: We have tested RadiusNT/X with some older supplicants that do not support EAP Type negotiation. If newer versions cannot be obtained you should set the Preferred EAP and Preferred PEAP methods to match these clients EAP or PEAP Types to prevent authentication failure. If all clients are capable of negotiating EAP and PEAP types you should set the preferred methods to the one that most of your clients will be using to speed the authentication process.A PEAP certificate file is required before the EAP-PEAP type is available to clients for authentication. See the next section on PEAP certificates for information on PEAP and how to create the required certificates. If you’ve installed Emerald with RadiusNT you can use Emeralds default sample certificate file ‘ieas.pem’ located in your Emerald folder as a PEAP certificate. Doing this will provide data encryption but will not provide certificate validation. You must disable certificate validation on the end users supplicant (client) when using the sample certificate. We recommend the included sample certificate be used for testing purposes only.PEAP certificates, signing requirements and examplesThere are only minor differences between standard SSL certificates used by secure web sites and those used with PEAP on 802.1x wireless networks.With PEAP the SID of the network, rather than your organizations domain must match the common name (cn) of the certificate. Additionally an EKU (Enhanced Key Usage) for Server Authentication (OID1.3.6.1.5.5.7.3.1) must be specified when creating your public certificate or signing request.In these examples we will use the OpenSSL utility to create a Certificate Signing Request (CSR) used with a third party certificate authority such as Verisign or Thawte. We will also generate a ‘self-signed’ certificate that does not require a certificate authority but does require users to first accept your certificate as valid on a one time basis depending on the supplicant and its configuration.The openssl utility used to create the certificates in this example is available from the IEA Software web site: /ftp/emeraldv4/winnt/sslcert.zipExample creating a certificate signing request for a certificate authorityopenssl req -new -nodes -keyout private.pem -out public.csr -extensions PEAP -config fUsing configuration from fLoading 'screen' into random state - doneGenerating a 1024 bit RSA private key.....++++++..............++++++writing new private key to 'private.pem'-----You are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [AU]:USState or Province Name (full name) [Some-State]:WashingtonLocality Name (eg, city) []:SpokaneOrganization Name (eg, company) [Internet Widgits Pty Ltd]:IEA Software, Inc.Organizational Unit Name (eg, section) []:Common Name (eg, YOUR name) []:ieasEmail Address []:support@The output file public.csr is processed by your certificate authority (CA), which will return a signed certificate file to you. Combine private.pem with the certificate returned from the CA into a single file. This file becomes the ‘PEAP Certificate’ file. You will likely also need the CA’s certificate chain file if one is required. This file becomes the ‘PEAP CA Certificate’. The full pathnames for both files must be configured in the EAP section of the RadiusNT/X administrator.Example creating a ‘self-signed’ certificateopenssl genrsa -out private.pemLoading 'screen' into random state - donewarning, not much extra random data, consider using the -rand optionGenerating RSA private key, 512 bit long modulus ..........................++++++++++++..++++++++++++e is 65537 (0x10001)openssl req -new -x509 -key private.pem -out public.pem -extensions PEAP -config f -days 5000 Using configuration from fYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [AU]:USState or Province Name (full name) [Some-State]:WashingtonLocality Name (eg, city) []:SpokaneOrganization Name (eg, company) [Internet Widgits Pty Ltd]:IEA Software, Inc.Organizational Unit Name (eg, section) []:Common Name (eg, YOUR name) []:ieasEmail Address []:support@Combine the two files private.pem and public.pem into one. The full pathname of this file becomes the‘PEAP Certificate’ file configured in the EAP section of the RadiusNT/X administrator. ‘PEAP CA Certificate’ is not used and should be left blank.After configuring the PEAP certificate file locations, save your changes. Stop RadiusNT if running as a windows service and start RadiusNT/X in debug ‘radius –x15 –X4’. At startup you should see all supported EAP types being registered.Registered: EAP-IdentityRegistered: EAP-GTCRegistered: EAP-MD5Registered: EAP-LEAPRegistered: EAP-MSCHAPV2Registered: EAP-PEAPRegistered: EAP-TTLSRegistered: EAP-PEAP-IdentityRegistered: EAP-PEAP-GTCRegistered: EAP-PEAP-MSCHAPV2If EAP-PEAP fails to register with a reason of N/A or missing file, check the file locations of the certificate files you created with the full pathname+filename entered for PEAP Certificate and PEAP CA Certificate in the RadiusNT/X admin.Windows supplicant configuration exampleSelect PEAP as the eap type and EAP-MSCHAPv2 as the PEAP authentication method. If you created a PEAP certificate for use with your wireless network make sure the ‘validate server certificate’ checkbox is checked. If you are using the default ieas.pem certificate ‘validate server certificate’ must not be checked.Wireless LAN supplicant interoperabilityWhile our aim is maximum compatibility with all 802.1x supplicants unfortunately inconsistencies between clients sometimes require manual and confusing configuration of technical items to account for differences between implementations.If you are experiencing compatibility problems with supplicants that have negotiated PEAP v1 our recommendation is to configure RadiusNT/X so that it is only able to negotiate PEAPv0 (Microsoft). Version 0 may tend to be more consistant between implementations due to Microsofts support of PEAPv0. Most supplicants capable of negotiating version 1 are also capable of negotiating version 0. Both versions offer the same features and security.If you are experiencing a problem with a particular supplicant we recommend trying a different EAP protocol supported by RadiusNT/X such as EAP-TTLS. If there are still problems please follow the troubleshooting steps in the next section to help resolve or isolate and report the problem.Questions & AnswersQ. Does RadiusNT/X support certificate only authentication such as EAP-TLS or EAP-PEAP phase 1 only?A. No, while RadiusNT/X supports validating server and client certificates it also requires password authentication be performed before a client will successfully authenticate.Q. I’m getting an error NO PASSWORD when authenticating using EAP, what could be wrong?A. The most likely cause is that you are using a version of RadiusNT/X that does not support EAP or are not licensed for the feature. See the Versions and editions of RadiusNT/X supporting EAP Authentication section above.Q. I’m getting an error SSL routines:SSL3_GET_CLIENT_HELLO when authenticating using PEAP. How can I fix this problem?A. The most common cause of this error is not having a PEAP certificate installed. PEAP certificates are required to use EAP-PEAP. See the section above on PEAP certificates, signing requirements and examples for more information on creating a PEAP certificate.Q. While authenticating clients RadiusNT/X reports the error 'PEAP err - SSL_write wants read, however the protocol has no provision for it'. What can I do to fix this problem?A. The most likely cause is the client’s failure to successfully validate the server’s certificate. If your clients have certificate validation enabled and you have chosen a ‘self-signed’ server certificiate make sure clients have the RadiusNT/X servers public key installed as a trusted certificate. On the windows platform this can be done by distributing the server’s public key in a file with an extension of .cer. The user simply needs to right-click over the file and select ‘Install certificate’. Disabling the clients certificate validation will also prevent the error however it bypasses the benefits associated with certificates. If you’re using a third party Certificate Authority (CA) such as Verisign or Thawte make sure your CA’s certificate chain file if required has also been installed in the RadiusNT/X administrator.Q. I can’t seem to authenticate using EAP, where should I look to find and solve this problem?A. There are several possible sources of clues about EAP authentication failures. First and foremost run RadiusNT/X in debug mode using the following command-line parameters ‘radius –x15 –X4’. Save a copy of all data shown during the authentication attempt. Another good source of information is debug or trace data from the supplicant (client). If not obvious from this data our support staff (support@iea-) can assist you to further trouble shooting the problem. Possible authentication problems may be related to one of the following:• Wrong default EAP type selected and supplicant (client) does not support EAP type negotiation.• RadiusNT/X has multiple IP addresses on the same subnet and is not configured to bind to one of the two addresses.• RadiusNT/X shared secret does not match access server shared secret• Using PEAP without having first defined a PEAP certificate file in RadiusNT/X admin• Client configured to validate server certificate when the server certificate is the default cert included with Emerald (ieas.pem) or another SSL certificate which does not have a ClientAuthentication EKU.• RadiusNT is running as a service as well as debug mode.• EAP type being used is not compatible with the backend authentication database.。


一、引言随着社会的不断发展,人们对于专注力、反应速度和视觉搜索能力的要求越来越高。
舒尔特方格作为一种简单、科学、高效的注意力训练方法,被广泛应用于飞行员、航天员、学生等群体的训练中。
为了提高自己的注意力水平和反应速度,我参加了舒尔特方格实训课程,以下是我对实训过程的总结和心得体会。
二、实训内容1. 舒尔特方格简介舒尔特方格是一种注意力训练工具,由1cm×1cm的25个方格组成,格子内任意填写1-25的数字。
测试时,被测者需用手指按顺序指出数字的位置,同时诵读出声。
测试者记录所用时间,时间越短,代表专注力越集中。
2. 实训过程(1)初识舒尔特方格在实训开始前,我首先了解了舒尔特方格的原理和操作方法。
通过学习,我了解到舒尔特方格不仅能够提高注意力,还能锻炼反应速度、视觉搜索能力和大脑反应能力。
(2)实训操作在实训过程中,我按照以下步骤进行操作:a. 确定舒尔特方格的大小,本实训使用的是5cm×5cm的方格。
b. 在方格内随机填写1-25的数字。
c. 保持眼睛与方格的距离为30-35厘米,将注意力集中在方格的中心点。
d. 按顺序用手指指出数字的位置,同时诵读出声。
e. 记录所用时间。
f. 重复以上步骤,直至完成所有方格。
(3)数据分析在实训过程中,我记录了每次测试的时间,并进行了统计分析。
通过分析,我发现自己在前几次测试中的时间较长,但随着训练的深入,时间逐渐缩短,说明注意力水平有所提高。
三、实训心得1. 训练注意力的重要性通过舒尔特方格实训,我深刻认识到注意力对于日常生活和工作的重要性。
在现代社会,我们面临着各种各样的干扰,如手机、电脑、电视等,这些干扰都会影响我们的注意力。
因此,提高注意力水平,对于我们提高工作和学习效率具有重要意义。
2. 舒尔特方格的实用性舒尔特方格操作简单,易于实施,且不受时间和地点的限制。
这使得舒尔特方格成为一种非常实用的注意力训练方法。
在实训过程中,我发现舒尔特方格不仅能够提高注意力,还能锻炼反应速度和视觉搜索能力。


分站培训RTU的概念:Remote Terminal Unit 字面意思‘远动终端单元’或‘远动终端’电力系统习惯称为RTU 不叫中文(如同CPU)是一种装置用来测量变电站或电厂的模拟信号量,数字信号量,执行调度主站下发的控制命令。
RTU四遥功能遥测测量对象VIPQ,要求:精度。
遥信采集对象开关刀闸,信号要求:响应速度无误报,漏报遥控控制目标:开关,刀闸,挡位升降。
要求:可靠无故障,无误控遥调模拟控制量输出,一般用在发电厂,遥脉(电度)采集脉冲电度表输出要求:掉电采集,分时电度保存。
无漏数通信功能:首先应有的功能。
RTU在电力调度自动化系统中所处的位置最前端,和变电站电气二次回路,信号回路,控制回路直接连接。
和主站用串行通信连接功能相对主站简单,最早期远动终端是硬件实现。
施工工作在电气回路较多的现场,要有安全意识,具有一定电气二次回路知识。
养成正确现场工作的习惯。
对RTU的性能要求可靠性A:设备工作在无人的现场,或有人值班但该人不负责检查,维护,操作该设备。
B:电力调度要求该设备不停机运行,随着时间推移,远动工作更加重要。
C:现场离远动工作人员办公地一般有几十公里。
易于施工维护现场工作条件艰苦,放电缆,处理电缆接头工作量巨大。
如RTU施工困难无疑是雪上加霜。
出现故障时如能快速修复可大大提高RTU可用率。
降低用户的不满情绪,减少出差次数。
适应性:遥测,遥信,遥控等信号形式多样。
各个用户对功能要求各有侧重。
环境适应性:气候,电网情况。
因地而异。
变电站内越来越多的智能设备。
互连要求多样。
不断出现的新的管理要求。
技术热点。
易用性使用方便,界面友好。
可令用户更好掌握该设备。
减少许多不必要的麻烦。
RTU 的结构形式一到数个标准机柜,800*600*2360mm,安装于变电站控制室,分散式一般为一个主机柜和几十个模块(小盒子),功能模块一般安装在控制柜或开关柜上。
RTU发展趋势和保护,计量,及其它智能装置融为一体,以综合自动化形式出现。

