计算机专业英语第4次作业
- 格式:doc
- 大小:63.50 KB
- 文档页数:5

Unit 4 Majors and Subjects / Why Is a Computer So Powerful课后习题答案(Keys to Task 4)1.Oral practice.Work in pairs and exchange the information about your majors and subjects.Omitted.2.Point out the conjunctions used in the following sentences.(1)When(2)If(3)and(4)and(5)but3.Choose the best answer from the given choices.(1) A(2) C(3) B(4) C(5) A习题册答案(Keys to the exercise book)Part One: Vocabulary 词汇用所给的词或短语的正确形式填空。
Part A1.favorite2.not only, but also3.interesting4.overcomemunicatePart B1.powerful2.carry out3.error4.dependable5.outputPart Two: Grammar & Function 语法与功能1.在右列中找出可与左列对应的句子。
(1) E(2) D(3) A(4) B(5) C2.从A、B、C、D选项中选择正确答案。
(1) C(2) D(3) C(4) C(5) C(6) D(7) C(8) A(9) B(10) CPart Three: Translation 翻译1.将下列短语翻译成英文。
(1)not only intelligent but also diligent(2)international language(3)overcome difficulties(4)billions of(5)information flow(6)error-free results2.将下列句子翻译成中文。

计算机专业英语作业:1、请将视频“什么是电脑硬件”中所述内容用英文表示。
2、请将以下英文翻译为中文。
1)Plug and Play, sometimes, abbreviated(简略的、缩写) PnP, is a catchy(动人的、易记住的) phrase( [freiz] 短语、习语) used to describe devices(设备、装备) that work with a computer system as soon as(与……一样)they are connected(链接的、有关系的). The user does not have to manually(手动的、用手) install drivers(驱动) for the device(装置、策略) or even tell the computer that a new device has been added. Instead the computer automatically(自动的、机械的) recognizes the device, loads new drivers for the hardware if needed, and begins to work with the newly connected device(链接设备),即插即用,缩写为PnP,这是一个容易记住的短语,它用来描述与计算机操作系统连接工作有关的设备。
用户不需要为设备手动安装驱动,甚至于不需要告诉计算机已经添加了饿一个新的设备。
计算机自动识别设备,如果需要为硬件加载一个新的驱动,并且开始工作在新的连接设备上。
For example, if you connect a Plug-and-Play mouse to the USB port on your computer, it will begin to work within a few seconds of being plugged(拥塞的、接通电源) in. A non plug-and-play device would require you to go through several steps of installing drivers and setting up the device before it would work.例如,如果你在你的电脑上的USB接口连接了一个即插即用的鼠标,它开始工作时接通电源只需要几秒钟。
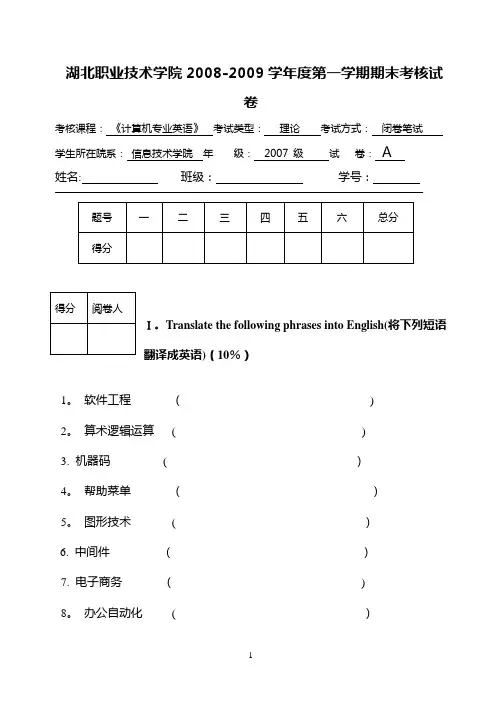
湖北职业技术学院2008-2009学年度第一学期期末考核试卷考核课程: 《计算机专业英语》 考试类型: 理论 考试方式: 闭卷笔试 学生所在院系: 信息技术学院 年 级: 2007 级 试 卷: A姓名: 班级: 学号:Ⅰ。
Translate the following phrases into English(将下列短语翻译成英语)(10%)1。
软件工程 ( )2。
算术逻辑运算 ( )3. 机器码 ( )4。
帮助菜单 ( )5。
图形技术 ( )6. 中间件 ()7. 电子商务 ( )8。
办公自动化 ( )9。
计算机病毒( )10。
可执行文件( )column with those similar in meaning in the right column (将左列的词汇与右列相应的汉语匹配)(10%)1. memory unit a. 半导体存储器2. intelligence b。
机制3。
semiconductor memory c。
存储单元4. data definition language d. 数据定义语言5. mechanism e。
通信6. machine language f。
机器语言7。
communication g。
智能8. element distance h。
桌面操作系统9。
desktop operating system i。
输入/输出设备10。
input/output device j.像素距离1。
() 6. ()2. () 7。
()3。
() 8。
()4. ( ) 9. ()5。
( ) 10。
( )Ⅲ. Fill in the blanks with the corresponding English abbreviations.(根据汉语写出相应的英语缩写) (10%)1. 只读存储器 _________ 6。
超文本标记语言_________2。

计算机专业英语全部答案(第三版)Unit1EX11 F2 T3 T4 F5 T6 F7 T 8 T 9 T 10FEX2Input hardware, storage hardware, processing hardware, output hardware power, speed, memorycentral processing unitinternal, primary, memorykeyboard, central processing unit, main memory, monitorEX3 PARTA1 F2 D3 G4 C5 B6 A7 E 8 HEX3 PART B1 F2 E3 G4 B5 A6 C7D 8 HEX41 input device2 screen3 manipulates4 instructions5 retrieve6 codes7 hardcopy8 functionEX51 T2 T3 F4 F5 T6 F7 T 8 TUNIT2EX11 T2 F3 T4 F5 T6 F7 T 8 FEX21 sizes, shapes, processing capabilities2 supercomputers, mainframe computers, minicomputers, microcomputers3 mainframe computer4 microcomputer, storage locations5 portables, laptop computers, desktop workstations6 semiconductor7 CPU, memory, storage, devices, processing, users8 microprocessor chipEX3 PARTA1 C2 A3 H4 I5 E6 F7 G 8 JEX3 PARTB1 capacity2 device3 laptop computer4 Portable computers5 Silicon6 semiconductor7 workstation8 Voltage, voltage9 RAM10ROMEX41 portable2 access3 main memory4 sophisticated programs5 processing capabilities6 instructions7 computation8 computer professionalEX51 T2 T3 F4 F5 F6 T7 F 8 T 9 T 10T11F 12T 13 T 14 TUNIT3EX11 T2 F3 T4 T5 T6 T7 F 8 F 9 T 10 F11T 12F 13F 14TEX21 microprocessor2 bus3 register 4control unit5 processor6 binary7 arithmetic, logic 8 milliseconds, microseconds9 instruction 10execution 11megahertz 12wordsize EX3 PARTA1 F2 A3 J4 C5 D6 E7 H 8 I 9 B 10GEX3 PARTB1 Storage 2chip3 buses4 ALU5 register 6control unit7 machine language 8 binary system 9 bits 10computer programEX41 configuration2 decodes3 data bus4 characters5 converts6 synchronize7 circuitry8 internal clockEX51 T2 F3 F4 T5 F6 F7 T 8 T 9 F 10 FUNIT4EX11 F2 T3 T4 F5 F6 T7 F 8 T 9 T 10 F11T 12T 13F 14F 15T 16F17T 18F 19T 20F21T 22FEX2memoryRAMdiskettes, diskschipsparityexpanded, extendedmonochromecacheROMupdatedEX3 PART A1 B2 E3 C4 J5 I6 H 7A 8 F 9 G 10DEX3 PART Bsecondary storagebufferaccesscodedisketteslotterminalsmotherboardbytescreenEX4desktopsoftwareanimationtransferredsophisticatedcompatiblecacheupgradeEX51 T2 F3 F4 T5 T6 T7 T8 F9 T 10 F11T 12F 13F 14T 15T 16F17F 18F 19F 20T21T 22TUnit 5Ex1:1 T2 T3 F4 T5 F6 F7 F 8 T 9 T 10 T11F 12T 13F 14F 15T 16T17F 18T 19F 20F21T 22T 23TEX2mail, courierhub, starlocal area networkpacketsEthernetkilobits per second, megabits per second, gigabits per second circuit switchingreassembledinternet protocol, transmission control protocol datagramsframesbinary, decimalEX3 part A1 C2 E3 B4 F5 A6 D7 H 8 GEX3 part Bhubzippeddecimalframebinary numberinternetpacketbandwidthEX4forwardedreassembledare encapsulatedcableburstysubmitare retransmittedprotocolEX5IP addressnotationdotted-decimalcomputer networkbackgroundsharedgeographicprivacyExercise to the Passage for ReadingEX6有意为维修技师使用所留被弃的、丢失的或损坏了的数据都进了数据桶。

计算机专业英语(第四版)课后习题答案Unit 1[Ex 1] 1. F 2. T 3. T 4. F 5. T 6. T 7. T 8. T 9. T 10. F[Ex 2] 1. input, storage, processing, and output 2. power;speed; memory3. central processing unit4. internal;primary; memory5. keyboard; central processing unit; main memory; monitor[Ex 3] A. 1. F 2. D 3. G 4. C 5. B 6. A 7. E 8. HB. 1. user 2. monitor 3. data 4. keyboard 5. data processing6. information7. computer8. memory[Ex 4] 1. input device 2. screen, screen 3. manipulates 4. instructions 5. retrieve6. code7. hard copy8. Function[ Ex. 5 ] 新处理器开始IT 技术的新时代New Processors Open New Era of IT TechnologiesLast week, Intel introduced to the public in Russia and other CIScountries a family of processors Intel Xeon E5-2600. They are more powerful and reliable and, importantly, are very economical in terms of energy consumption. Their presence opens a new era in the field of IT technologies and means that the cloud technology is getting closer.These processors are primarily designed for servers, data centers (DPC) and supercomputers. The emergence of this class of devices is not accidental. According tothe regional director of Intel in Russia and other CIS states Dmitri Konash who spoke at the event, the market of IT-technology is developing so rapidly that, according to forecasts, by 2015 there will be 15 billion devices connected to the Internet, and over 3 billion of active users .上周,英特尔公司向俄罗斯和其它独联体国家的公众推出了英特尔Xeon E5-2600系列处理器,它们更加强大可靠,尤其是在能量消耗方面更加经济实惠。



计算机专业英语教程第四版翻译课后练习题含答案简介《计算机专业英语教程》是针对计算机专业学生编写的一本英语教材。
本书旨在帮助学生通过学习计算机领域的专业英语词汇和语法,提升他们的英语能力和技能。
本文将为读者提供该教材第四版的课后练习题及答案。
第一课练习题1.将下列单词从易到难排序:chip, computer, algorithm, software,desktop2.将下列单词从中文翻译为英文:程序设计,硬件,操作系统,输入,输出3.请解释下列缩略语的全称:RAM,CPU,OS答案1.desktop, chip, computer, software, algorithm2.programming, hardware, operating system, input, output3.RAM(Random Access Memory),CPU(Central Processing Unit),OS(Operating System)第二课练习题1.请翻译下列句子:计算机的功能越来越强大,它可以执行许多任务。
2.请解释下列单词的意思:interface,protocol,server,router答案puters are becoming more and more powerful and they canperform many tasks.2.interface(接口), protocol(协议),server(服务器),router(路由器)第三课练习题1.请将下列单词按字母顺序排列:database,file,program,server,storage2.请填写下列句子的空格:计算机会读取从硬盘 __ (into)内存。
3.请解释下列单词的意思:database,algorithm,client,browser答案1.algorithm,database,file,program,server,storage2.into3.database(数据库),algorithm(算法),client(客户端),browser(浏览器)第四课练习题1.请翻译下列句子:今天我学会了如何编写计算机程序。

《计算机专业英语》习题参考答案Lesson 1I.1. Operating System2. Fetch-evaluate-execute3. Front-side bus4. Dual-core processor5. Basic Input/Output System(BIOS)II.1. 指令是特定各式的二进制数列,它们对于每台机器都是唯一的。
2. CPU是中央处理单元的简称,每个字母分开发音。
3. 大多数计算在中央处理器中进行。
4. 双核是指一个处理器上有两个完整运算内核的CPU。
5. 处理器:是微处理器或CPU的缩写。
6. 集成电路:即芯片,是由半导体材料制成的一种电子设备。
III.1. F2. T3. TIV.1.ALU, CU, Register2.memory3.processor4.the CPULesson 2I.1.Static Random Access Memory(SRAM)2.Dynamic Random Access Memory(DRAM)3.Virtual Memory4.Physical Memory5.Level 1 Cache6.Level 2 Cache7.HDD access speedII.1.动态随机存储器之所以称为“动态”是因为它每秒钟被刷新数千次。
2.RAM:是计算机中存储操作系统、应用程序和当前正是用数据的地方。
3.ROM由计算机中一小块长寿命电池供电。
4.RAM缓存是由高速静态随机存储器构成的存储器。
III.1. F2. F3. F4. TIV.1. non-volatile2. compiler3. volatile4. DRAMLesson 3I.1. Motherboard2. PC Case3. Hard Disk Drive(HDD)4. Optical mouse5. RAM6. Mobile DiskII.1.PC是有很多组件构成的一个系统。

中译英参考答案Unit 1A computer system consists of hardware system and software system. The hardware of the computer is usually divided into three major parts or three primary subsystems: the CPU, the memory subsystem, and the I/O subsystem.The CPU performs many operations and controls computer. The memory subsystem is used to store program being executed by the CPU, along with the program’s data. The I/O subsystem allows the CPU to interact with input and output devices such as the keyboard and monitor of a personal computer. The components of the computer are connected to the buses.The part of the computer that performs the bulk of data processing operations is called the central processing unit and is referred to as the CPU. In microcomputer, it is often called the microprocessor. The CPU is made up of three major parts: control unit, ALU, and register set.Memory is also known as internal memory or main memory. It refers to the circuits in the computer that hold whatever programs and data are available for immediate use by the CPU.I/O subsystem includes I/O devices and interface. There are a wide variety of I/O devices, such as mouse, printer, sensor, disk, and so on. Input-output interface provides a method for transferring information between internal storage and external I/O devices. Peripherals connected to a computer need special communication links for interfacing them with the CPU. The purpose of the communication link is to resolve the differences that exist between the central computer and each peripheral.Unit 2Storage hardware provides permanent storage of information and programs for retrieval by the computer. Hard disk drives store information in magnetic particles embedded in a disk. Usually a permanent part of the computer, hard disk drives can store large amounts of information and retrieve that information very quickly.Although fixed hard drive systems offer faster access and have a higher storage capacity than optical discs, optical disc systems use removable media –a distinct benefit. Optical discs –primary CDs and DVDs – are much more widely used than removable hard drive systems. They are the standard today for software delivery, as well as commonly used for storing high-capacity music and video files. There are also versions of both CD and DVD drives available for home audio and home theater use. Optical discs are commonly referred to as compact discs.CD and DVD discs are read by CD and DVD drives. The speed of a CD or DVD drive is rated as 24x, 32x, 36x, and so on. These labels describe how fast the drive is compared to the first version of that drive. For example, a 36x drive is 36 times the speed of the baseline unit that was originally manufactured. Most optical discs have a title and other text printed only on one side and they are inserted into the drive with the printed side facing up. When inserting such a CD or DVD, be careful not to get dirt, fingerprints, scratches, or anything else that might hinder light reflectivity on the disc’s surface.Unit 3(a) A program is a list of instructions or statements for directing the computer to perform arequired data processing task. Programming is a multistep process for creating that list of instructions.(b) It is important to understand the difference between a class and an object of that class. A class is simply a specification for creating objects. Thus, a single class may create multiple objects.(c) Java is an object-oriented, network-friendly high-lever programming language that allows programmers to build applications that can run on almost any operating system.(d) ActiveX is a set of controls, or reusable components that enables programs or content of almost any type to be embedded within a Web page. Whereas a Java must be downloaded each time you visit a Web site, with ActiveX the component is downloaded only once, then stored on your hard disk for later, repeated use.(e) Programming involves a great deal of creativity. The design is guide to the function or purpose of each component, but the programmer has great flexibility in implementing the design as code. No matter what language is used, each program component involves at least three major aspects: control structures, algorithms, and data structures.Unit 4The software system can be divided into two broad categories: application software and system software. Application software consists of the program for performing tasks particular to the machine’s utilization. In contrast to application software, system software comprises a large number of programs. These programs start up the computer and function as the principle coordinator of all hardware components and application software. Without system software loaded into RAM of your computer, your hardware and application software are useless.System software can be grouped into three basic parts: operating system, utility software, and language translators. The majority of an installation’s utility software consists of programs for performing activities that are fundamental to computer installations yet not included in the operating system. In a sense, utility software consists of software units that extend the capabilities of the operating system.A computer’s OS is the main collection of programs that manage its activities. The primary chores of an OS are management and control. The OS ensures that all actions requested by a user are valid and processed in an orderly fashion. It also manages the computer system’s resources to perform these operations with efficiency and consistency.Application software is the software designed to help you solve problems specific to business or perform specific business tasks. Application software then is the layer of software closest to you. Basically, there are four categories of application software: productivity software, business and specialty software, entertainment software and education/reference software.Unit 5A computer network is often classified as being either a local area network (LAN), a metropolitan area network (WAN), or a wide area network (WAN). The connection of two or more networks is called an internetwork. The worldwide Internet is a well-known example of an internetwork.LANs are privately owned networks within a single building or campus of up to a few kilometers in size. They are widely used to connect personal computers and workstations incompany offices and factories to share resources and exchange information.In general, a given LAN will use only one type of transmission medium. Various topologies are possible for LANs. The most common LAN topologies are bus, ring and star.A MAN is basically a bigger version of a LAN and normally uses similar technology. MAN is designed to extend over an entire city. It may be a single network such as a cable television network, or it may be a means of connecting a number of LANs into a large network so that resources may be shared LAN-to-LAN as well as device-to-device. For example, a company can use a MAN to connect the LANs in all of its offices throughout a city.A W AN spans a large geographical area that may comprise a country, a continent, or even the world. It provides long-distance transmission of data, voice, image, and video information over large geographical area.In contrast to LANs, W ANs may utilize public leased, or private communication devices, usually in combinations, and can therefore span an unlimited number of miles.Unit 6Transmission media are used to transfer messages over a network. For instance, the transmission media used in a network may be a privately owned set of cables, the public phone lines, or a satellite system. Transmission media can either be wired or wireless.The three types of wired media most commonly used to carry messages are twisted-pair wire, coaxial cable, and fiber-optic cable. One of the most successful developments in transmission media in recent years has been fiber optics. Fiber-optic cable is commonly used for the high-speed backbone lines of a network, or for Internet infrastructure.Wireless transmission media have become especially popular in recent years. They support communications in situations in which physical wiring is impractical or inconvenient, as well as facilitate mobility. Wireless media are commonly used to connect devices to a network, to share information between computers, to connect wireless mice to a computer, and for handheld PCs, wireless phones, and other mobile devices. Radio signals transferred through the air are the heart of most types of wireless media. In addition to conventional broadcast radio application, the microwave, cellular, and satellite transmission media also use radio signals to transmit data.Radio transmissions require the use of a transmitter to send the radio signals through the air.A receiver (usually containing some type of antenna) accepts the date at the other end. When a device functions as both a receiver and transmitter, it is commonly called a transceiver or transmitter-receiver.Unit 7(a) Since many database systems users are not computer trained, developers hide the complexity from users through several levels of abstraction, to simplify user’s interactions with the system: physical level, logical level, and view level.(b) A database schema is specified by a set of definitions expressed by a special language called a data-definition language (DDL). The result of compilation of DDL statements is a set of tables that is stored in a special file called data dictionary, or data directory.(c) The structured query language (SQL) is the most widely used and standard query language for relational database management systems. It is a kind of non-procedural language.(d) An entity is a “thing”or “object”in the real world that is distinguishable from otherobjects. For example, each person is an entity, and bank accounts can be considered to be entities. Entities are described in a database by a set of attributes.(e) Data warehouse is one of the newest and hottest buzzwords and concepts in the IT field and the business environment. A data warehouse is a logical collection of information——gathered from many different operational databases——that supports business analysis activities and decision-making tasks.Unit 8Animation is the term used to describe a series of graphical images that are displayed one after the other to simulate movement. Cartoons on television are one example of animation.Video differs from animation in that it usually begins as a continuous stream of visual information that is broken into separate images or frames when the video is recorded. When the frames are projected—typically at a rate of 30 frames per second—the effect is a smooth reconstruction of the original continuous stream of information. As you might imagine, at 30 frames per second, the amount of data involved in displaying a video during a multimedia presentation can require a substantial amount of storage space. Consequently, video data—like audio data—is often compressed. A variety of compression standards exist. Some of the most common video file formats are .avi, .mpeg, .mov, .rm.For multimedia presentation, video may be recorded using a standard (analog) video camera and then converted to digital form as it is input into a computer. Alternatively, the film can be recording digitally using a digital video camera. Streaming video is frequently used on Web pages to reduce file size. Similar to streaming audio, Streaming video files can begin playing once a portion of the video has been downloaded.Unit 9(a) AI is currently being applied in business in the form of knowledge systems, which use human knowledge to solve problems. The most popular type of knowledge-based system is the expert system. An expert system is a computer program that attempts to represent the knowledge of human experts in the form of heuristics. The term heuristic is derived from the same Greek root as the word eureka, which means “to discover”.(b) The user interface enables the manager to enter instructions and information into the expert system and to receive information from it. The instructions specify the parameters that guide the expert system through its reasoning processing. The information is in the form of values assigned to certain variables.(c) The knowledge base contains both facts that describe the problem area and knowledge representation techniques that describe how the facts fit together in a logical manner. The term problem domain is used to describe the problem area.(d) An expert system, also called a knowledge-based system, is an artificial intelligence system that applies reasoning capabilities to reach a conclusion. Expert systems are excellent for diagnostic and prescriptive problems.(e) The DSS is not intended to replace the manager. The computer can be applied to the structured portion of the problem, but the manager is responsible for the unstructured portion——applying judgment or intuition and conducting analyses.Unit 10The linked list (see figure 1) consists of a series of nodes, which are not necessarily adjacent in memory. Each node contains the element and a link to a node containing its successor. We call this the next link. The last cell’s next link references null.To execute printList or find(x) we merely start at the first node in the list and then traverse the list by following the next links. This operation is clearly linear-time, as in the array implementation, although the constant is likely to be larger than if an array implementation were used. The findKth operation is no longer quite as efficient as an array implementation; findKth(i) takes O(i) time and works by traversing down the list in the obvious manner. In practice, this bound is pessimistic, because frequently the calls to findKth are in sorted order (by i). As an example, findKth(2), findKth(3), findKth(4), and findKth(6) can all be executed in one scan down the list.The remove method can be executed in one next reference change. Figure 2 shows the result of deleting the second element in the original list.The insert method requires obtaining a new node from the system by using a new call and then executing two reference maneuvers. The general idea is shown in figure 3. The dashed line represents the old next reference.figure 1figure 2figure 3Unit 11(a) A set is pure if all of its members are sets, all members of its members are sets, and so on. For example, the set containing only the empty set is a nonempty pure set.(b) A language is a describable set of finite strings, drawn from a fixed alphabet. A grammar is one way to "describe" the language. The grammar consists of a finite list of rules, where each rule replaces one substring with another. The string on the left must contain at least one nonterminal. The first string "produces" or "generates" the second. Thus a rule is also called a production.(c) A finite-state machine (FSM) or finite-state automaton(FA)is a mathematical abstraction sometimes used to design digital logic or computer programs. It is a behavior model composed of a finite number of states, transitions between those states, and actions, similar to a flow graph in which one can inspect the way logic runs when certain conditions are met.(d) Sometimes it is inconvenient or impossible to describe a set by listing all of its elements. Another useful way to define a set is by specifying a property that the elements of the set have in common. The notation P(x) is used to denote a sentence or statement P concerning the variable object x. The set defined by P(x) written {x | P(x)}, is just a collection of all the objects for whichP is true.Unit 12(a) Because drawings are typically displayed in 3D, CAD is especially helpful in designing automobiles, aircraft, ships, buildings, electrical circuits (including computer chips), and even clothing.(b) Computer-integrated manufacturing (CIM) is the manufacturing approach of using computers to control the entire production process. This integration allows individual processes to exchange information with each other and initiate actions. Through the integration of computers, manufacturing can be faster and less error-prone, although the main advantage is the ability to create automated manufacturing processes.(c) In addition to supporting decision making, coordination, and control, information system may also help managers and workers analyze problems, visualize complex subjects, and create new products.(d) Knowing the history and evolution of ERP is essential to understanding its current application and its future developments.(e) In addition to monitoring operational activities such as tracking the status of orders and inventory levels, enterprise system also improve organization-wide reporting and decision making.Unit 13(a) There are a wide variety of educational application programs available. Educational software is designed to teach one or more skills, such as reading, math, spelling, a foreign language, world geography, or to help prepare for standardized tests.(b) Electronic business (e-business) is the use of information technology and electronic communication networks to exchange business information and conduct transactions in electronic, paperless form.(c) Word processing software allows you to use computers to create, edit, store, and print documents. You can easily insert, delete, and move words, sentences, and paragraphs——without ever using an eraser.(d) What is a spreadsheet? Spreadsheet software takes its name from the accountant’s columnar worksheet, which it imitates. A spreadsheet is a worksheet consisting of a collection of cells formed by the intersection of rows and columns. Each cell can store one piece of information: a number, word or phrase, or formula.Unit 14(a) A geographic information system (GIS) is a system that captures, stores, analyzes, manages and presents data with reference to geographic location data. In the simplest terms, GIS is the merging of cartography, statistical analysis and database technology.(b) The GPS receiver uses the messages it receives to determine the transit time of each message and computes the distance to each satellite. These distances along with the satellites' locations are used to compute the position of the receiver. This position is then displayed, perhaps with a moving map display or latitude and longitude; elevation information may be included.(c) Virtual reality (VR) is a term that applies to computer-simulated environments that can simulate physical presence in the real world. Most current virtual reality environments areprimarily visual experiences, displayed either on a computer screen or through special stereoscopic displays, but some simulations include additional sensory information, such as sound through speakers or headphones.Unit 15(a) The software development process is sometimes called the software development life cycle (SDLC), because it describes the life of a software product from its conception to its implementation, delivery, use, and maintenance.(b) How can the CMM help your organization? There are three key roles the CMM plays. First, the CMM helps build an understanding of software process by describing the practices that contribute to a level of process maturity. The second role of the CMM is to provide a consistent basis for conducting appraisals of software processes. The CMM’s third key role is to serve as a blueprint for software process improvement.(c) The UML offers a standard way to write a system’s blueprints, including conceptual things such as business processes and system functions as well as concrete things such as programming language statements, database schemas, and reusable software components. The UML represents a collection of the best engineering practices that have proven successful in the modeling of large and complex systems.(d) Object modeling is a technique for identifying objects within the system environment and the relationships between those objects. The object-oriented approach to system development is based on several concepts, such as object, attribute, behavior, encapsulation, class, inheritance, polymorphism, persistence, etc.Unit 16“Security” is an all-encompassing term that describes all the concepts, techniques, and technologies to protect information from unauthorized access. There are several requirements for information security.Confidentiality: hiding data, usually with encryption, to prevent unauthorized viewing and access.Authenticity: the ability to know that the person or system you are communicating with is who or what you think it is.Access control: once a person or system has been authenticated, their ability to access data and use systems is determined by access controls.Data integrity: providing assurance that an information system or data is genuine.Availability: making sure that information is available to users in a secure way.To prevent unauthorized access, some type of identification procedure must be used. These vary from passwords to physical access object (access cards, etc.) to biometric devices that verify some type of personal characteristic, such as a fingerprint.Some of the most secure access control systems address both identification and authentication. Identification involves verifying that the person’s name or other identifying feature is listed as an authorized user; authentication refers to determining whether or not the person is actually who he or she claims to be.Unit 17A distributed system is a collection of independent computers which appear to the users of system as a single computer. Nearly all large software systems are distributed. For example, enterprise-wide business systems must support multiple users running common applications across different sites.A distributed system encompasses a variety of applications, their underlying support software, the hardware they run on, and the communication links connecting the distributed hardware. The largest and best-known distributed system is the set of computers, software, and services comprising the World Wide Web, which is so pervasive that it coexists with and connects to most other existing distributed systems. The most common distributed systems are networked client/server systems. Distributed systems share the general properties described below.●Multiple nodes●Message passing or communication●Resource sharing●Decentralized control●Concurrency or parallelism●Fault tolerance●Heterogeneity●OpennessDistributed systems have many inherent advantages, especially over centralized systems. Some applications are inherent distributed as well. In general, distributed systems:●Yield higher performance●Allow incremental growth●Allow one user to run a program on many different machines in parallel●Provide higher reliability。

软件设计师-计算机专业英语(四)(总分:30.00,做题时间:90分钟)一、综合知识试题(总题数:6,分数:30.00)It should go without saying that the focus of UML is modeling. However, what that means, exactly, can be an open-ended question. (1) is a means to capture ideas, relationships,decisions, and requirements in a well-defined notation that can be applied to many different domains. Modeling not only means different things to different people, but also it can use different pieces of UML depending on what you are trying to convey. In general, a UML model is made up of one or more(2) . A diagram graphically represents things, and the relationships between these things. These(3) can be representations of realworld objects,pure software constructs, or a description of the behavior of some other objects. It is common for an individual thing to show up on multiple diagrams; each diagram represents a particular interest, or view, of the thing being modeled. UML 2.0 divides diagrams into two categories: structural diagrams and behavioral diagrams. (4) are used to capture the physical organization of the things in your system, i.e., how one object relates to another. (5) focus on the behavior of elements in a system. For example, you can use behavioral diagrams to capture requirements, operations, and internal state changes for elements.(分数:5.00)A.ProgrammingB.AnalyzingC.DesigningD.Modeling √解析:A.viewsB.diagrams √erviewsD.structurepictures解析:A.things √B.picturesnguagesD.diagrams解析:A.Activitydiagramse-casediagramsC.Structuraldiagrams √D.Behavioraldiagrams解析:A.Activity diagramse-case diagramsC.Structural diagramsD.Behavioral √解析:[参考译文] 不用说,UML的聚焦点是建模。
计算机专业英语作业答案(供参照)计算机专业英语作业1第 1-3 章作业一.Vocabulary( 词汇 )(一 ).Translate the following words and expressions into Chinese(写出以下词组的汉语。
) 1. central processing unit ( CPU)中央办理器 2.title bar标题栏3. operating system操作系统4. personal computer个人计算机5. menu bar菜单栏6.desk publishing桌面排版7. electronic spreadsheet电子表格8. hard disk硬盘9. database数据库10. Cursor光标(二 ).Fill in the blanks with the corresponding English abbreviations.(依据汉语写出相应的英语缩写。
)1.随机储存器RAM2.只读储存器ROM3.传输控制协议TC P4.数字视频光盘DVD5.通用串行总线USB6.计算机协助设计CAD7.计算机协助制造CAM8.中央办理器CPU(三 ).Translate the following Chinese into English.(依据汉语写出相应的英语。
)1.键盘keybord2.鼠标mouse3.扫描仪scanner4.打印机printer5.输入input6.输出output7.显示器monitor8.储存器storage9.数据库database 10.操作系统operating system11.应用软件application software 12.字办理器word processor13.网络阅读器web browser二.Tell whether the following statements are true(T) or false(F)判.(断正误。
Unit 4 The Fundamentals of ComputerHardwareText 1 O rganization of Computer System Components Exercises1. Fill in the blanks with appropriate words according to the text.(根据课文内容填空)(1)A computer is a fast and accurate symbol manipulating system.(2)The keyboard of a workstation connected online to a computer is an example of device.(3)The input/output and secondary storage units are sometimes called peripheral devices.(4)The heart of a computer system is cpu.(5)Key elements of a computer system include memory, input devices, central processingunit and output devices.(6)The popular output devices used for personal computer are printer.2. Translate and analyze the following sentences.(翻译并分析下面的句子)(1)It is organized to accept, store, and process data and produce output results.句子组成:is organized表是被动,to表目的,and连接并列宾语。
第四章课后习题Circle the correct answer:1.These specialized graphics programs combine text and graphics to create publications of professional quality:A.desktop publishing programs c.image galleriesB.image editors d.illustration programs2.Also known as drawing programs.a.desktop publishing programs c.image galleriesb.image editors d.illustrarion programs3.Graphics programs used to ctreate and edit vector images.a.desktop publishing programs c.image galleriesb.image editors d.illustrarion programs4.An essential multimedia feature that allowa user participationa.Flash c.immersionb.interactivity d.raster5.Special programs used to create multimedia presentations.a.desktop publishing programs c.immersionb.interactivity d.multimedia authoring programs6.A widly used interactive animation application from Adobe.a.ACTION c.Fuzzyb.Flash d.WYSIWYG7.Programs for Web site design and HTML coding are called Web page editors ora.apps c.VR programsb.HTML editors d.Web editors8.This area of artificial intelligence is also known as expert systems.a.acoustics c.roboticsb.knowledge-bassed systems. D.virtual reality9.A type of artificial intelligence that uses a database to provide assistance to users.a.acoustics c.roboticsb.expert systems d.virtual reality10.Another name for the database used in expert sysrems that contains specific facts and rules.a.access table c.knowledge baseb.expert table d.rule baseMatch each numbered item with the most closely related lettered item.Write your answers in the spaces provided.a.audio editing e 1.Specialized graphics programs for editing or modifying digital imagesb.bitmap images b 2.Another name for raster images.c.blog g 3.Raster images contain thousands of dots known as .d.button a 4.Type of software used to create and edit audio clips.e.image editors d 5.A link on amultimedia page used to locate and discover information.f.mobile c 6.Personal Web site created by an individualg.pixels j 7.The process of creating a Web site.h.virtual reality h 8.Also known as artificial reality or virtual environments.I.robots i puter-controlled machines that mimichuman activitiesj.Web authoring f 10.The type of app designed for smartphones,netbooks,and tablets.Circle the correct answer:1.What type of software works with users,application software,and computer hardware to handle the majority of technical details?a.application c.Linuxb.desktop d.system2.The programs that convert programming instructions written by programmers into a language that computers understand and process are language:a.converters c.managersb.linguists d.translators3.The ability to switch between different applications stored in memory is called :a.diversion c.operational interferenceb.multitasking d.programming4.Graphic representations for a program,type of file,or function:a.app c.imageb.icon d.software5.This operating system feature is controlled by a mouse and changes shape depending on its current functiona.dialog box c.mouseb.menu d.pointer6.The operating system based on Linux,designed for Netbook computers,and focused on Inernet connectivity through cloud computing:a.Chrome c. UNIXb.Mac d.Windows7.The mobile operating system develop by Apple and originally called iPhone OS :a.Android c.IOSb.BlackBerry OS d.Mac OS8.A utility program that makes copies of files to be used in case the originals are lost or damaged:a.Backup and Restore c.Disk Defragmenterb.Disk Cleanup pactor9.A troubleshooting utility that identifiles and eliminates nonessential files,frees up valuable disk space ,and improves system performance:a.Backup and Restore c.Disk Defragmenterb.Disk Cleanup pactor10.Windows makes it easy to update drivers with Windows:a.Backup c.Driverb.Restore d. UpdateMatch each numbered item with the most closely related lettered item. Write your answers in the spaces provided.a.antivirus h 1.Programs that perform specific tasks related to managing computer resourcesb.Boot Camp j 2.Restarting a running computer without turning off the powerc.driver e 3.Type of operating system that controls and coordinates networked computers.d.fragmented f 4.An operating system is often referred to as the software environment ore.NOS b 5.Allows Macintosh computers toren both Mac OS and the Windows operating system.f.platform i 6.A type of software that allows a single physical computer to operate as though it were two or more separate andindependent computers.g.Anddroid g 7.Mobile operating system that is owned by Google and is one of the fastest-growing mobile operating systems.h.utilities a 8.Type of program that guards computer systems fromviruses and other damaging programs.I. virtualization d 9.If a file cannot be saved on a single track ,it has to bej.warm boot c 10.Program that works with the operating system to allow communication between a device and the rest of a computer system is called a device第六章选择题1. this container houses most of the electrical components for a computer system.a. carrier package c. system unitb. system board d. TV tuner2. similar to notebooks, this system unit specializes in on-the-go Web browsing and e-mail access.a. chassis c. media centerb. desktop d. netbook3. computers can only recognize this type of electronic signal.a. analog c. digitalb. bus d. maximum4. the main or motherboard is also known as the:a. computer c. mobile systemb. board processor d. system board5. how many bytes can a 32-bit-wrd computer access at a time?a. 1 c. 8b. 4 d. 166. in a microcomputer system , the central processing unit is contained on a single:a. bus c. moduleb. chip d. RAM7. this type of memory divides large programs into parts and stores the parts on a secondary storage device.a. direct c. random-accessb. expanded d. virtual8. also known as NIC, this adapter card is used to connect a computer to a :a. AIA c. graphicsb. expansion d. network9. this provides a pathway to connect parts of the CPU to each other:a. bus c. wiredb. Plug and Play d. wireless10. older ports that have largely been replaced by faster, more flexible ports are called:a. buses c. legacyb. expandable d. rednered匹配题1. The category of system units that blurs the line between desktop computers and dedicated entertainment devices. Media center2. The newer type of tablet PC that is almost all monitor. slate3. System board component that provides a connection point for specialized cards or circuit boards. slots4. Plastic cards the size of a regular credit card that have an embedded specialty chip. Smart cards5. A type of memory that improves processing by acting as a temporary high-speed holding area between the memory and the CPU. cache6. A type of memory that provides a combination of features of RAM and ROM. Flash7. A generic term that is associated with the ability to attach any device onto a computer and have it play or work immediately. Plug and Play8. This bus connects the CPU to memory on the system board. system9. This port can be used to connect many USB devices to the system. USB10. This unit plugs into s standard wall outlet and converts AC to DC. Power supply第七章选择题1. Most keyboards use an arrangement of keys known as:a. Alpha c. OptiKeyb. Daisy d. QWERTY2. The device that controls a pointer displayed on the monitor.a. cord c. printerb. mouse d. scanner3. Also known as a roller ball, this device controls the pointer by rotating a ball with your thumb.a. trackball c. cordless mouseb. joystick d. stylus4. The type of screen that can be touched with more than one finger and supports zooming in and out by pinching and stretching your fingers.a. digital c. multitouchb. dynamic d. OLED5. Flatbed and document are types of:a. headsets c. monitorsb. HDTVs d. scanners6. Device used by banks to automatically read those unusual numbers on the bottom of checks and deposit slips.a. MICR c. OMRb. FDIC d. UPC7. The most widely used audio-input device.a. mouse c. microphoneb. VR d. TFT8. The monitor feature that specifies how often a displayed image is updated.a. aspect ratio c. refresh rateb. dot pitch d. resolution rate9. Handheld, book-sized devices that display text and graphicsa. e-book-readers c. lasersb. HDTV d. whiteboards10. This technology allows television stations to broadcast their programming directly to smartphones, computers, and digital media players.a. CRT c. LEDb. HDTV d. Mobile DTV匹配题1. Pressing this key turns this feature on or off. Caps lock2. This type of mouse has a ball on the bottom and is attached with a cord to the system unit. Mechanical3. A penlike device commonly use with tablet PCs and PDAs. stylus4. Bar code readers use either handheld wand readers or platform. scanners5. Bar code system used by many electronic cash registers. UPC6. Records images digitally on a disk or in its memory. Digital camera7. The distance between each pixel. Dot pitch8. A type of monitor that activates each pixel independently. Active-matrix9. Special-purpose printers for creating maps, images, and architectural and engineering drawings. plotters10. A type of Internet telephone service that requires a small adapter that connects directly to your computer’s USB port. MagicJack。
云南开放大学-计算机专业英语(20秋)形考作业4试卷总分:100 得分:100一、单选题 (共 5 道试题,共 50 分)1.In C Language, a ______is a series of characters enclosed in double quotes.A.matrixB.stringC.programD.tream提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是:B2.____ is the study of the principles of valid reasoning and inference, as well as of consistency, soundness, and completeness.A.Graph theoryB.LogicC.TopologyD.Operation research提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是:B3.The________ storage area that you can use to copy or move selected text or object among applications.A.exponentB.orderC.temporaryD.superior提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是:C4.Very long, complex expres-sions in program are difficult to write correctly and difficult to _____.A.defendB.detectC.defaultD.debug提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是:D5.Software design is a _____ process. It requires a certain mounted of flair on the part of the designer.A.createB.createdC.creatingD.creative提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是:D二、阅读理解 (共 1 道试题,共 50 分)10.A software process is a set of activities that leads to the production of a software product. These activities may involve the development of software from scratch in a standard programming language like Java or C. Increasingly, however, new software is developed by extending and modifying existing systems and by configuring and integrating off-the-shelf software or system components.Software processes are complex and, like all intellectual and creative processes, rely on people making decisions and judgments. Because of the need for judgment and creativity, attempts to automate software processes have met with limited success. Computer-aided software engineering (CASE) tools can support some process activities. However, there is no possibility, at least in the next few years, of more extensive automation where software takes over creative design from the engineers involved in the software process.Although there are many software processes, some fundamental activities are common to all software processes:1). Software specification The functionality of the software and constraints on its operation must be defineD.2). Software design and implement-ation The software to meet the specification must be produceD.3). Software validation The software must be validated to ensure that it does what the customer wants.4). Software evolution The software must evolve to meet changing customer Needs.Although there is no ‘ideal’ software process, there is scope for improving the software process in many organizations. Processes may include outdated techniques or may not take advantage of the best practice in industrial software engineering. Indeed, many organizations still do not take advantage of software engineering methods in their software development.(1).A software process is _______.A.software productB.a set of activitiesC.a standard programming languageD.an existing system提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是:B(2).Software processes ___________.A.are too complex and intellectual to be developed by Computer-aided software engineering (CASE) tools.B.are complex and intellectual enough to be developed by Computer-aided software engineering (CASE) tools.C.are rely on Computer-aided software engineering(CASE) tools.D.don’t depend on the people making decisions and judgments提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是:A(3).software processes usually include ________ activities.A.twoB.threeC.fourD.five提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是:C(4).Improving the software process in many organizations is ______.A.unnecessaryB.idealC.outdatedD.limited提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是:D(5).Software design and implementat-ion means that _________.A.the functionality of the software and constraints on its operation must be defineD.B.the software to meet the specification must be produceD.C.the software must be validated to ensure that it does what the customer wants.D.the software must evolve to meet changing customer Needs.提问:认真复习云南开放课程知识,并回答上述试题标准正确答案是: B。
Unit Four/Section BI. Fill in the blanks with the information given in the text:1. Information engineering emphasizes a modeling tool called entityrelationship diagrams.2. One of the disadvantages of model-driven development is the long durationof projects.3. Unlike structured analysis and design and information engineering,object-oriented analysis and design attempt to emerge the data and process concerns into singular constructs called objects.4. Unlike logical models, physical models show not only what a system is ordoes , but also how the system is physically and technically implemented.II. Translate the following terms or phrases from English into Chinese and vice versa:1. check box 复选框.选择框.校验框2. structured design 结构化设计3. building block 积木块.构建模块.构件4. database schema 数据库模式5. radio button 单选(按)钮6. 系统建模技术 system modeling technique7. 模型驱动开发 model-driven development8. 数据流程图 data flow diagram9. 下拉式菜单 drop-down (或pull-down) menu10. 滚动条 scroll barUnit Five: Software ProcessUnit Five/Section AI. Fill in the blanks with the information given in the text:1. New software may be developed from scratch or through the use of existingsystems and off-the-shelf software or system components.2. The three generic process models discussed in the text are often complementaryrather than mutually exclusive, especially for large system development.3. The waterfall model is so named because of the cascade from one phase to anotherin the software development process.4. The fundamental development activities of the waterfall model arerequirements analysis and definition, system and software design, implementation and unit testing, integration and system testing, and operation and maintenance.5. The two fundamental types of evolutionary development are exploratorydevelopment and throwaway prototyping.6. The evolutionary approach is often more effective than the waterfall approachin producing systems that meet the immediate needs of customers, but it is difficult to establish a(n) stable system architecture using this approach.7. CBSE is a(n) reuse-oriented approach to software development, which relieson a large base of reusable software components and an integrating framework for these components.8. While CBSE can reduce the amount of software to be developed and the associatedcost and risks, it cannot avoid requirements compromises which may lead to a system that does not meet the real needs of users.II. Translate the following terms or phrases from English into Chinese and vice versa:1. system specification 系统规格说明2. unit testing 单位(或单元、部件)测试3. software life cycle 软件生命周期(或生存周期)4. system validation testing 系统验证测试5. evolutionary development process 演化开发过程6. linear model 线性模型7. program unit 程序单元8. throwaway prototype 抛弃式原型9. text formatting 正文格式编排.文本格式化10. system evolution 系统演变11. 系统设计范例 system design paradigm12. 需求分析与定义 requirements analysis and definition13. 探索式编程方法 exploratory programming approach14. 系统文件编制 system documentation15. 瀑布模型 waterfall model16. 系统集成 system integration17. 商用现成软件 commercial off-the-shelf (或COTS) software18. 基于组件的软件工程 component-based software engineering (CBSE)19. 软件维护工具 software maintenance tool20. 软件复用 software reuseIV. Translate the following passage from English into Chinese:Software processes are complex and, like all intellectual and creative processes, rely on people making decisions and judgments. Because of the need for judgment and creativity, attempts to automate software processes have met with limited success. Computer-aided software engineering (CASE) tools can support some process activities. However, there is no possibility, at least in the next few years, of more extensive automation where software takes over creative design from the engineers involved in the software process.One reason the effectiveness of CASE tools is limited is because of the immense diversity of software processes. There is no ideal process, and many organization have developed their own approach to software development.Processes have evolved to exploit the capabilities of the people in an organization and the specific characteristics of the systems that are being developed. For some systems, a very structured development process is required while for others a flexible, agile process is likely to be more effective.软件过程比较复杂.而且像所有其他的智能和创造性过程一样.依靠人们作出决定和判断。
计算机专业英语第4次作业1.Windows gives you more control over the__A___ your work.A:operationB:wayC:energyD:power2.Tea or coffee ? Which is your___A___?A:preferenceB:confusionC:puzzleD:mixture3.Programs that can destroy another computer's programs are called__D_.A:gamesB:computer languagesC:bugsD:viruses4.You were _C___ to us by our associates.A:toldB:suggestC:recommendedD:informed5.You should be able to tell the meaning of this word from its ___C____.A:companyB:conclusionC:contextD:communication6.___B___ refers to the parts of the computer that you can see and touch.A:SoftwareB:HardwareC:HardshipD:Instruction7.___C______that, I could do it much better.A:If I doB:If I were doC:Were I to doD:Were I do8.A network is a group of computers linked by communication lines .正确9.Most RAM is temporary, losing its contents when the computer's power is turned off.正确10.A program is a series of instruction that guides a computer through a process.正确11.写出下列术语的英文或中文意思。
1 message encryption 参考答案: 1 信息加密(术)2 客户机-服务器结构 2 client-server architecture3 关系数据库 3 relational database4 microwave radio 4 微波无线电5 digital television 5 数字电视12:[论述题]12.阅读下列短文,从A、B、C、D四个选项中,选出最佳选项。
For every man in the Civil War who died in battle, two or three men died of disease. Doctors of that time knew very little about causes of sickness or ways of preventing it. Thousands of men in poor health became soldiers. Hundreds of others had never had childhood diseases. Many of these soldiers could not withstand the epidemics of measles, mumps, and whooping cough that went through the camps.Army life was hard. Soldiers got few fruits or vegetables. There was no milk unless they happened to find a cow. Neither their clothes nor their shelters protected the troops from rain, snow, and cold. Sickness and disease were spread by insects, rats, and impure drinking water. Often the men drank straight from muddy streams. Gunshot wounds were serious, as in any war,but they did not cause as much death and suffering as disease did.1. Disease caused__________A.only a few deaths.B.Fewer deaths than wounds did.C. More deaths than wounds did.D.Both A and B2. Doctors at the time of the Civil War knew____________A.a lot about curing disease.B.Little about the causes of disease.C.Only how to prevent disease.D.Both A and C3. Men who were accepted as Civil War soldiers were___________A.known to have already had measles and mumps.B. Required to be in perfect healthC. Able to withstand epidemics easilyD.Sometimes in poor health4. Army life was hard on the troops because____________A.they were not sheltered from the coldB.they had no warm clothing.C.Their diets lacked good, healthful foodD.All of the above5. The best title for this selection is__________A. Disease.B. The Greatest DangerC.Insects, Rats, and Gunshot WoundsD. The History of Epidemics Passage 2Can you imagine ice that does not melt and is not wet? Have you ever heard of dry ice? Dry ice is made by freezing a gas. It is quite different from ordinary ice, which is simply frozen water.Dry ice was first manufactured in 1925.It has since fulfilled the hopes of its inventor. It can be used for making artificial fog in the movies. When steam is passed over dry ice, a very dense vapor rises. It can also be used for destroying insects in grain supplies. It is more practical than ordinary ice because it takes less space and is 142 degrees colder. Since it turns into steam instead of melting into water, it is cleaner to use. For these reasons it is extremely popular, and many people prefer it to ordinary ice.Dry ice is so cold that, if you touch it with your bare fingers, in will burn you.6. When was dry ice was first made ?A.1925B.1920C.1924D.19237.What is ice made of ?A. ChemicalsB. VaporC. WaterD. Gas8.How is an artificial fog made in the movies ?A. by passing steam over dry iceB. by turning ordinary ice into steamC. by heating dry iceD. by mixing dry ice with ordinary ice.9.What is the advantages of dry ice over ordinary ice ?A. It takes a longer time to meltB. It is cleaner to useC. It is not so cold as ordinary iceD. It is colder as ordinary ice10. According to the passage, which of the following statement is true ?A. dry ice is made of vaporB. Dry ice is not able to burn you.C. dry ice is not so cold as ordinary iceD. dry ice is colder than 142 degree.参考答案:1-5CBDDB 6-10 ADABC13:[论述题]13.请将下列英语句子翻译成汉语,要求内容忠实原文,语句通顺,逻辑清楚,表达正确。
1.To be part of the Internet a computer must have a unique Internet Protocol (IP) network address so that messages can be correctly routed to and from the machine over the Internet. Internet addresses are called URLs(Uniform Resource Locators).2.The amount of data that a computer network can transmit is called the bandwidth of the network and is usually measured in kilobits per second (Kbps) or megabitsper second (Mbps).3.Disgruntled employees sometimes attempt to destroy computers, programs, or files. In recent years, computer viruses have gained wide notoriety. Viruses are programs that "migrate” through networks and operating systems and attach themselves to different programs and databases.参考答案:1.作为互联网的一部分,一台计算机必须有一个单独的互联网协议(IP)网络地址,以便使信息通过正确的路由从计算机发送到互联网上。