H3C SecPath高端防火墙NAT典型配置举例
- 格式:pdf
- 大小:3.85 MB
- 文档页数:18

1. Firewall的配置#指定GigabitEthernet1/0/1端口的电口被激活,使用双绞线连接<H3C> system-view[H3C] interface gigabitethernet 1/0/1[H3C-GigabitEthernet1/0/1] combo enable copper[H3C-GigabitEthernet1/0/1]quit# 按照组网图配置各接口的 IP 地址。
<Sysname> system-view[Sysname] interface gigabitethernet1/0/1[Sysname-GigabitEthernet1/0/1] port link-mode route [Sysname-GigabitEthernet1/0/1] ip address quit [Sysname] interface gigabitethernet1/0/2[Sysname-GigabitEthernet1/0/2] port link-mode route [Sysname-GigabitEthernet1/0/2] ip address quit# 创建安全域,并将不同的接口加入不同的安全域。
[Sysname]security-zone name Trust[Sysname-security-zone-Trust]import interface gigabitethernet1/0/1[Sysname-security-zone-Trust]quit[Sysname]security-zone name Untrust[Sysname-security-zone-Untrust]import interfacegigabitethernet1/0/2[Sysname-security-zone-Untrust]quit# 配置访问控制列表 2001,仅允许内部网络中网段的用户可以访问 Internet。

SecPath系列防火墙IPSec典型配置举例关键词:IKE、IPSec摘要:本章首先介绍了IKE和IPSec的基本概念,随后说明了防火墙的配置方法,最后给出两种典型应用的举例。
缩略语:缩略语英文全名中文解释IKE Internet Key Exchange 因特网密钥交换Security IP网络安全协议IPsec IP目录1 特性简介 (3)1.1 IPSec基本概念 (3)1.1.1 SA (3)1.1.2 封装模式 (3)2 应用场合 (4)3 配置指南 (4)3.1 配置概述 (4)3.2 配置ACL (6)3.3 配置IKE (6)3.3.1 配置IKE全局参数 (6)3.3.2 配置IKE安全提议 (7)3.3.3 配置IKE对等体 (8)3.4 IPSec安全提议 (10)3.5 配置安全策略模板 (12)3.6 配置安全策略 (14)3.7 应用安全策略组 (16)4 配置举例一:基本应用 (17)4.1 组网需求 (17)4.2 使用版本 (18)4.3 配置步骤 (18)4.4 配置结果验证 (27)4.4.1 查看IPSec安全联盟 (27)4.4.2 查看报文统计 (27)5 配置举例二:与NAT结合 (27)5.1 组网需求 (27)5.2 配置说明 (28)5.3 配置步骤 (28)5.4 配置验证结果 (34)5.4.1 查看IPSec安全联盟 (34)5.4.2 查看报文统计 (35)6 注意事项 (35)7 相关资料 (35)7.1 相关协议和标准 (35)7.2 其它相关资料 (36)1 特性简介IPsec(IP Security)协议族是IETF制定的一系列协议,它为IP数据报提供了高质量的、可互操作的、基于密码学的安全性。
特定的通信方之间在IP层通过加密与数据源验证等方式,来保证数据报在网络上传输时的私有性、完整性、真实性和防重放。
IPsec通过AH(Authentication Header,认证头)和ESP(Encapsulating Security Payload,封装安全载荷)这两个安全协议来实现上述目标,并且还可以通过IKE(Internet Key Exchange,因特网密钥交换协议)为IPsec提供自动协商交换密钥、建立和维护安全联盟的服务,以简化IPsec 的使用和管理。
![[史上最详细]H3C路由器NAT典型配置案例](https://uimg.taocdn.com/882e4d6942323968011ca300a6c30c225801f060.webp)
H3C路由器NAT典型配置案列(史上最详细)神马CCIE,H3CIE,HCIE等网络工程师日常实施运维必备,你懂的。
1.11 NAT典型配置举例1.11.1 内网用户通过NAT地址访问外网(静态地址转换)1. 组网需求内部网络用户10.110.10.8/24使用外网地址202.38.1.100访问Internet。
2. 组网图图1-5 静态地址转换典型配置组网图3. 配置步骤# 按照组网图配置各接口的IP地址,具体配置过程略。
# 配置内网IP地址10.110.10.8到外网地址202.38.1.100之间的一对一静态地址转换映射。
<Router> system-view[Router] nat static outbound 10.110.10.8 202.38.1.100# 使配置的静态地址转换在接口GigabitEthernet1/2上生效。
[Router] interface gigabitethernet 1/2[Router-GigabitEthernet1/2] nat static enable[Router-GigabitEthernet1/2] quit4. 验证配置# 以上配置完成后,内网主机可以访问外网服务器。
通过查看如下显示信息,可以验证以上配置成功。
[Router] display nat staticStatic NAT mappings:There are 1 outbound static NAT mappings.IP-to-IP:Local IP : 10.110.10.8Global IP : 202.38.1.100Interfaces enabled with static NAT:There are 1 interfaces enabled with static NAT.Interface: GigabitEthernet1/2# 通过以下显示命令,可以看到Host访问某外网服务器时生成NAT会话信息。

目录1 GRE ··················································································································································· 1-11.1 概述 ··················································································································································· 1-11.1.1 协议简介 ································································································································· 1-11.1.2 GRE的安全选项······················································································································ 1-21.1.3 应用范围 ································································································································· 1-31.1.4 协议规范 ································································································································· 1-41.2 配置GRE over IPv4隧道··················································································································· 1-41.2.1 配置准备 ································································································································· 1-41.2.2 配置概述 ································································································································· 1-41.2.3 新建GRE over IPv4隧道接口 ································································································· 1-51.3 GRE over IPv4隧道典型配置举例 ···································································································· 1-6 2点到多点GRE隧道 ····························································································································· 2-12.1 点到多点GRE隧道简介 ····················································································································· 2-12.1.1 点到多点GRE隧道产生背景···································································································· 2-12.1.2 点到多点GRE隧道的工作原理 ································································································ 2-12.1.3 点到多点GRE隧道备份 ··········································································································· 2-32.1.4 点到多点GRE隧道的优缺点···································································································· 2-42.2 配置点到多点GRE隧道 ····················································································································· 2-52.2.1 配置准备 ································································································································· 2-52.2.2 配置概述 ································································································································· 2-52.2.3 新建点到多点GRE隧道接口···································································································· 2-52.2.4 查看已建立的点到多点GRE隧道信息 ····················································································· 2-72.3 点到多点GRE隧道典型配置举例 ······································································································· 2-82.3.1 基本点到多点GRE隧道配置举例 ···························································································· 2-82.3.2 双中心节点网中的点到多点GRE隧道配置举例····································································· 2-122.3.3 分支节点备份的点到多点GRE隧道配置举例 ········································································ 2-221 GRE1.1 概述1.1.1 协议简介GRE (Generic Routing Encapsulation ,通用路由封装)协议是对某些网络层协议(如IP )的数据报文进行封装,使这些被封装的数据报文能够在另一个网络层协议(如IP )中传输。
SecPath高端防火墙二三层转发配置举例关键词:二三层转发、PAT、私有地址、公有地址、地址池摘要:本文简单描述了高端多核防火墙二三层转发模块相关业务的特点,详细描述了二三层转发测试的基本方法和详细步骤,给出二三层转发基本的配置案例。
缩略语:目录1 介绍 (1)1.1 普通二三层转发的工作机制 (1)1.2 INLINE转发的工作机制 (1)1.3 跨VLAN二层转发的工作机制 (1)2 特性使用指南 (2)2.1 使用场合 (2)2.2 配置指南 (2)2.3 注意事项 (3)3 支持的设备和版本 (3)3.1 设备版本 (3)3.2 支持的设备 (3)4 配置举例 (4)4.1 组网需求 (4)4.2 设备基本配置 (5)4.3 二三层转发业务典型配置举例 (5)5 相关资料 (26)5.1 相关协议和标准 (26)5.2 其它相关资料 (26)1 介绍二三层混合转发包括了普通二三层转发、INLINE转发和跨VLAN二层转发。
1.1 普通二三层转发的工作机制如果设备接收到的报文目的MAC地址匹配三层VLAN接口的MAC,则通过设备的VLAN接口进行三层转发;否则通过设备的二层以太网接口进行二层转发。
普通的二三层转发是设备默认启用的特性,不需要配置。
1.2 INLINE转发的工作机制高端防火墙支持二层INLINE转发,即用户通过配置直接指定从某接口入的报文从特定接口出。
这种方式下,报文转发不再根据MAC表进行,而是根据用户已经配置好的一组配对接口进行转发,发送到设备的报文从其中一个接口进入后从另一个接口转发出去。
INLINE转发只支持二层接口,不支持逻辑接口,包括子接口;1.3 跨VLAN二层转发的工作机制跨VLAN二层转发,顾名思义,就是由数据链路层来完成不同VLAN间的通信。
目前这种技术主要应用在防火墙插卡上。
防火墙插卡是H3C为了适应灵活多变的网络应用而推出的新的防火墙形态。
防火墙插卡和交换机配合使用,经过交换机的二层网络流量由防火墙插卡过滤后再进行转发。
H3C SecPath UTM系列NAT典型配置举例关键词:NAT NAPT摘要:NAT(Network Address Translation,网络地址转换)是将IP数据报报头中的IP地址转换为另一个IP地址的过程。
在实际应用中,NAT主要用于实现私有网络访问公共网络的功能。
这种通过使用少量的公有IP地址代表较多的私有IP地址的方式,将有助于减缓可用IP地址空间的枯竭。
缩略语:缩略语英文全名中文解释NAPT Network Address Port Translation 网络地址端口转换网络地址转换TranslationNAT NetworkAddress目录1 特性简介 (1)1.1 多对多地址转换及地址转换的控制 (1)1.2 NAPT (1)1.3 Easy IP (2)1.4 内部服务器 (2)2 应用场合 (2)3 注意事项 (2)4 配置举例 (3)4.1 组网需求 (3)4.2 配置思路 (3)4.3 使用版本 (3)4.4 配置步骤 (4)4.4.1 基本配置 (4)4.4.2 配置域和域间策略 (5)4.4.3 配置地址池 (7)4.4.4 配置动态地址转换 (7)4.4.5 配置静态地址转换 (8)4.4.6 配置内部服务器 (9)4.5 验证结果 (9)4.5.1 PAT方式 (9)4.5.2 NO PAT方式 (10)4.5.3 Easy IP方式 (10)4.5.4 静态地址方式 (10)4.5.5 内部服务器方式 (11)5 相关资料 (11)5.1 相关协议和标准 (11)5.2 其它相关资料 (12)1 特性简介NAT(Network Address Translation,网络地址转换)是将IP数据报报头中的IP地址转换为另一个IP地址的过程。
私有IP地址是指内部网络或主机的IP地址,公有IP地址是指在因特网上全球唯一的IP地址。
RFC 1918为私有网络预留出了三个IP地址块,如下:z A类:10.0.0.0~10.255.255.255z B类:172.16.0.0~172.31.255.255z C类:192.168.0.0~192.168.255.255上述三个范围内的地址不会在因特网上被分配,因此可以不必向ISP或注册中心申请而在公司或企业内部自由使用。

H3C SecPath防火墙系列产品混合模式的典型配置
一、组网需求:
组网图中需要三台PC, PC1和PC4在Trust区域;PC2处于DMZ区域,其IP地址与PC1和PC4在同一网段,PC3位于Untrust区域,为外部网络。
G0/0接口和G1/0接口属于同一个桥组Bridge1。
对于访问控制有如下要求:
在防火墙G0/1接口上配置NAT,使Trust区域与DMZ区域通过地址转换才能访问Untrust区域;
通过NAT Server使DMZ区域对Untrust区域提供WWW服务;
在G1/0接口绑定ASPF策略并配合包过滤,使得Trust区域用户可以访问DMZ区域设备;但DMZ区域不能访问Trust区域;
在G0/0接口上绑定基于MAC地址的访问控制列表禁止PC4访问其他任何区域。
二、组网图:
支持混合模式的产品型号有:Secpath F1000-A/F1000-S/F100-E/F100-A;版本要求Comware software, Version 3.40, ESS 1622及以后。
四、配置关键点:
1、每一个桥组都是独立的,报文不可能在分属不同桥组的端口之间
传输。
换句话说,从一个桥组端口接收到的报文,只能从相同桥
组的其他端口发送出去。
防火墙上的一个接口不能同时加入两个
或两个以上的桥组。
2、要实现不同桥组之间或二层接口和三层接口之间数据转发,需要
创建桥组虚接口,并且将桥组虚接口加入到相应的区域。

新手可以根据下面的配置一步一步操作,仔细一点儿就没问题了~!可以用超级终端配置,也可以用CRT配置如果配置了,还是不能上网,可以加我的QQ:1恢复出厂设置:Reset saved-configuration配置防火墙缺省允许报文通过:system-viewfirewall packet-filter default permit为防火墙的以太网接口(以Ethernet0/0为例)配置IP地址,并将接口加入到安全区域:interface Ethernet0/0ip address IP地址子网掩码quitfirewall zone trustadd interface Ethernet0/0quit添加登录用户为使用户可以通过Web登录,并且有权限对防火墙进行管理,必须为用户添加登录帐户并且赋予其权限:local-user 登录账号password simple 登录密码service-type telnetlevel 3quitquitsysfirewall packet-filter default permitdialer-rule 1 ip permitacl number 3000rule 0 permit ipquitinterface Dialer1link-protocol pppppp chap user PPPOE账号ppp chap password simple PPPOE密码ip address ppp-negotiatedialer-group 1dialer bundle 1nat outbound 3000quitinterface Ethernet0/4pppoe-client dial-bundle-number 1firewall zone untrustadd interface Ethernet0/4add interface Dialer1quitfirewall zone trustadd interface Ethernet0/0quitip route-static Dialer 1 preference 60 save。

新手可以根据下面的配置一步一步操作,仔细一点儿就没问题了~!可以用超级终端配置,也可以用CRT配置如果配置了,还是不能上网,可以加我的QQ:957602411恢复出厂设置:Reset saved-configuration配置防火墙缺省允许报文通过:system-viewfirewall packet-filter default permit为防火墙的以太网接口(以Ethernet0/0为例)配置IP位置,并将接口加入到安全区域:interface Ethernet0/0ip address IP位置子网掩码quitfirewall zone trustadd interface Ethernet0/0quit添加登录用户为使用户可以通过Web登录,并且有权限对防火墙进行管理,必须为用户添加登录帐户并且赋予其权限:local-user 登录账号password simple 登录密码service-type telnetlevel 3quitquitsysfirewall packet-filter default permitdialer-rule 1 ip permitacl number 3000rule 0 permit ipquitinterface Dialer1link-protocol pppppp chap user PPPOE账号ppp chap password simple PPPOE密码ip address ppp-negotiatedialer-group 1dialer bundle 1nat outbound 3000quitinterface Ethernet0/4pppoe-client dial-bundle-number 1firewall zone untrustadd interface Ethernet0/4add interface Dialer1quitfirewall zone trustadd interface Ethernet0/0quitip route-static 0.0.0.0 0.0.0.0 Dialer 1 preference 60save友情提示:部分文档来自网络整理,供您参考!文档可复制、编辑,期待您的好评与关注!。
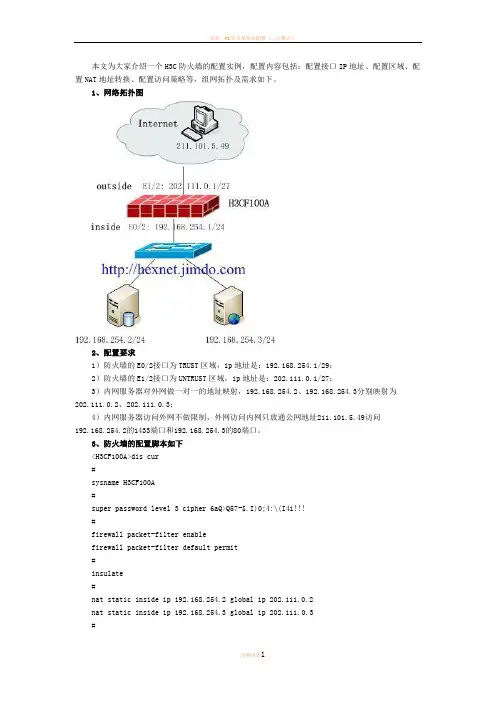
本文为大家介绍一个H3C防火墙的配置实例,配置内容包括:配置接口IP地址、配置区域、配置NAT地址转换、配置访问策略等,组网拓扑及需求如下。
1、网络拓扑图2、配置要求1)防火墙的E0/2接口为TRUST区域,ip地址是:192.168.254.1/29;2)防火墙的E1/2接口为UNTRUST区域,ip地址是:202.111.0.1/27;3)内网服务器对外网做一对一的地址映射,192.168.254.2、192.168.254.3分别映射为202.111.0.2、202.111.0.3;4)内网服务器访问外网不做限制,外网访问内网只放通公网地址211.101.5.49访问192.168.254.2的1433端口和192.168.254.3的80端口。
3、防火墙的配置脚本如下<H3CF100A>dis cur#sysname H3CF100A#super password level 3 cipher 6aQ>Q57-$.I)0;4:\(I41!!!#firewall packet-filter enablefirewall packet-filter default permit#insulate#nat static inside ip 192.168.254.2 global ip 202.111.0.2nat static inside ip 192.168.254.3 global ip 202.111.0.3#firewall statistic system enable#radius scheme systemserver-type extended#domain system#local-user net1980password cipher ######service-type telnetlevel 2#aspf-policy 1detect h323detect sqlnetdetect rtspdetect httpdetect smtpdetect ftpdetect tcpdetect udp#object address 192.168.254.2/32 192.168.254.2 255.255.255.255object address 192.168.254.3/32 192.168.254.3 255.255.255.255#acl number 3001description out-insiderule 1 permit tcp source 211.101.5.49 0 destination 192.168.254.2 0 destination-port eq 1433rule 2 permit tcp source 211.101.5.49 0 destination 192.168.254.3 0 destination-port eq wwwrule 1000 deny ipacl number 3002description inside-to-outsiderule 1 permit ip source 192.168.254.2 0rule 2 permit ip source 192.168.254.3 0rule 1000 deny ip#interface Aux0async mode flow#interface Ethernet0/0shutdown#interface Ethernet0/1shutdown#interface Ethernet0/2speed 100duplex fulldescription to serverip address 192.168.254.1 255.255.255.248 firewall packet-filter 3002 inbound firewall aspf 1 outbound#interface Ethernet0/3shutdown#interface Ethernet1/0shutdown#interface Ethernet1/1shutdown#interface Ethernet1/2speed 100duplex fulldescription to internetip address 202.111.0.1 255.255.255.224 firewall packet-filter 3001 inbound firewall aspf 1 outboundnat outbound static#interface NULL0#firewall zone localset priority 100#firewall zone trustadd interface Ethernet0/2set priority 85#firewall zone untrustadd interface Ethernet1/2set priority 5#firewall zone DMZadd interface Ethernet0/3set priority 50#firewall interzone local trust#firewall interzone local untrust#firewall interzone local DMZ#firewall interzone trust untrust#firewall interzone trust DMZ#firewall interzone DMZ untrust#ip route-static 0.0.0.0 0.0.0.0 202.111.0.30 preference 60 #user-interface con 0user-interface aux 0user-interface vty 0 4authentication-mode scheme#return。
H3C SecPat h F100系列防火墙配置教程初始化配置〈H3C〉system-view开启防火墙功能[H3C]firewa ll packet-filter enable[H3C]firewa ll packet-filter defaul t permit分配端口区域[H3C] firewa ll zone untrus t[H3C-zone-trust] add interf ace Gigabi tEthe rnet0/0[H3C] firewa ll zone trust[H3C-zone-trust] add interf ace Gigabi tEthe rnet0/1工作模式firewa ll mode transp arent透明传输firewa ll mode route路由模式http 服务器使能HTTP服务器 undo ip http shutdo wn关闭HTTP服务器 ip http shutdo wn添加WEB用户[H3C] local-user admin[H3C-luser-admin] passwo rd simple admin[H3C-luser-admin] servic e-type telnet[H3C-luser-admin] level3开启防范功能firewa ll defend all 打开所有防范切换为中文模式 langua ge-mode chines e设置防火墙的名称 sysnam e sysnam e配置防火墙系统IP 地址 firewa ll system-ip system-ip-addres s [ addres s-mask ] 设置标准时间 clockdateti me time date设置所在的时区 clocktimezo ne time-zone-name { add | minus} time取消时区设置 undo clocktimezo ne配置切换用户级别的口令 superpasswo rd [ leveluser-level] { simple | cipher } passwo rd取消配置的口令 undo superpasswo rd [ leveluser-level]缺缺省情况下,若不指定级别,则设置的为切换到3 级的密码。
目录1路由设置 ············································································································································ 1-11.1 概述 ··················································································································································· 1-11.2 配置静态路由····································································································································· 1-11.3 查看激活路由表 ································································································································· 1-21.4 静态路由典型配置举例 ······················································································································ 1-31.5 注意事项············································································································································ 1-61 路由设置•本章所指的路由器代表了一般意义下的路由器,以及运行了路由协议的三层交换机。