CCNA第二章
- 格式:doc
- 大小:726.50 KB
- 文档页数:9

1. Which statements correctly identify the role of intermediary devices in the network? (Choose three.)determine pathways for data 确定数据通路initiate data communicationsretime and retransmit data signals 重分发originate the flow of datamanage data flows 管理数据final termination point for data flow2. Select the statements that are correct concerning network protocols. (Choose three.)define the structure of layer specific PDU'sdictate how to accomplish layer functionsoutline the functions necessary for communications between layers limit the need for hardware compatibilityrequire layer dependent encapsulationseliminate standardization among vendors3. What are two functions of encapsulation? (Choose two.)tracks delay between end devicesenables consistent network paths for communicationallows modification of the original data before transmissionidentifies pieces of data as part of the same communicationensures that data pieces can be directed to the correct receiving end device4. What is a primary function of the trailer information added by the data link layer encapsulation?supports error detection 支持错误检测‘ensures ordered arrival of dataprovides delivery to correct destinationidentifies the devices on the local networkassists intermediary devices with processing and path selection5. Which statements correctly identify the role of intermediary devices in the network? (Choose three.)determine pathways for datainitiate data communicationsretime and retransmit data signalsoriginate the flow of datamanage data flowsfinal termination point for data flow6. What is a PDU?corruption of a frame during transmissiondata reassembled at the destinationretransmitted packets due to lost communicationa layer specific encapsulation 一个具体的封装层7. Which characteristic correctly refers to end devices in a network?manage data flowsoriginate data flow 原数据流retime and retransmit data signalsdetermine pathways for data8.Refer to the exhibit. "Cell A" at IP address 10.0.0.34 has established an IP session with "IP Phone 1" at IP address 172.16.1.103. Based upon the graphic, which device type best describes the function of wireless device "Cell A?"the destination devicean end devicean intermediate devicea media device9.Refer to the exhibit. Which three labels correctly identify the network types for the network segments that are shown?(Choose three.)Network A -- WANNetwork B -- WANNetwork C -- LANNetwork B -- MANNetwork C -- WANNetwork A -- LAN10. Which three statements best describe a Local Area Network (LAN)? (Choose three.)A LAN is usually in a single geographical area.The network is administered by a single organization.The connection between segments in the LAN is usually through a leased connection.The security and access control of the network are controlled by a service provider.A LAN provides network services and access to applications for users within a common organization.Each end of the network is generally connected to a Telecommunication Service Provider (TSP).11.Refer to the exhibit. Which networking term describes the data interleaving process represented in the graphic?pipingPDUstreamingmultiplexingencapsulation12. What is the primary purpose of Layer 4 port assignment?to identify devices on the local mediato identify the hops between source and destinationto identify to the intermediary devices the best path through the network to identify the source and destination end devices that are communicating to identify the processes or services that are communicating within the end devices13. What device is considered an intermediary device?1.file serve2.IP phone ptop 4.printer 5.switch14.Refer to the exhibit. Which term correctly identifies the device type that is included in the area B? sourceendtransferintermediary 中间设备15.Refer to the exhibit. What type of network is shown?WANMANLANWLAN16. Which layer encapsulates the segment into packets?physicaldata linknetwork 网络层封装的是数据包transport17. What can be identified by examining the network layer header?the destination device on the local mediathe destination host address 网络层头部封装目的主机的地址the bits that will be transferred over the mediathe source application or process creating the data18. What is the purpose of the TCP/IP Network Access layer?path determination and packet switchingdata presentationreliability, flow control, and error detectionnetwork media control 接入层控制网络媒体the division of segments into packets19. During the encapsulation process, what occurs at the data link layer? No address is added.The logical address is added.The physical address is added. 数据链路层添加一个物理地址The process port number is added.20.Refer to the exhibit. Which set of devices contains only end devices? A, C, DB, E, G, HC, D, G, H, I, JD, E, F, H, I, JE, F, H, I, J21. What is the proper order of the layers of the OSI model from the highest layer to the lowest layer?4physical, network, application, data link, presentation, session, transportapplication, physical, session, transport, network, data link, presentationapplication, presentation, physical, session, data link, transport, networkapplication, presentation, session, transport, network, data link, physicalpresentation, data link, session, transport, network, physical, application22. Which two layers of the OSI model have the same functions as the TCP/IP model Network Access Layer? (Choose two.)34NetworkTransportPhysicalData Link TCP/IP 工作在第一层和第二层Session。

CCNA中文笔记第2章:Internet Protocols作者:红头发Chapter2 Internet ProtocolsTCP/IP and the DoD ModelDoD模型被认为是OSI参考模型的浓缩品,分为4层,从上到下是:1.Process/Application layer2.Host-to-Host layer3.Internet layerwork Access layer其中,如果在功能上和OSI参考模型互相对应的话,那么:1.DoD模型的Process/Application层对应OSI参考模型的最高3层2.DoD模型的Host-to-Host层对应OSI参考模型的Transport层3.DoD模型的Internet层对应OSI参考模型的Network层4.DoD模型的Network Access层对应OSI参考模型的最底2层The Process/Application Layer ProtocolsProcess/Application层包含的协议和应用程序有:Telnet,FTP,X Windows,TFTP,SMTP,SNMP,NFS和LPD等等Dynamic Host Configuration Protocol(DHCP)/BootP(Bootstrap Protocol)动态主机配置协议(DHCP)服务器可以提供的信息有:1.IP地址2.子网掩码(subnet mask)3.域名(domain name)4.默认网关(default gateway)5.DNS6.WINS信息The Host-to-Host Layer ProtocolsHost-to-Host层描述了2种协议:1.传输控制协议(Transmission Control Protocol,TCP)2.用户数据报协议(User Datagram Protocol,UDP)Transmission Control Protocol(TCP)当1个主机开始发送数据段(segment)的时候,发送方的TCP协议要与接受方的TCP协议进行协商并连接,连接后即所谓的虚电路(virtual circuit),这样的通信方式就叫做面向连接(connection-oriented).面向连接的最大优点是可靠,但是它却增加了额外的网络负担(overhead)User Datagram Protocol(UDP)UDP协议的最他特点是无连接(connectionless),即不可靠,因为它不与对方进行协商并连接,它也不会给数据段标号,也不关心数据段是否到达接受方Key Concepts of Host-to-Host Protocols现在把TCP协议和UDP协议的一些特性做个比较:1.TCP.协议在传送数据段的时候要给段标号;UDP协议不2.TCP协议可靠;UDP协议不可靠3.TCP协议是面向连接;UDP协议采用无连接4.TCP协议负载较高;UDP协议低负载5.TCP协议的发送方要确认接受方是否收到数据段;UDP反之6.TCP协议采用窗口技术和流控制;UDP协议反之Port NumbersTCP和UDP协议必须使用端口号(port number)来与上层进行通信,因为不同的端口号代表了不同的服务或应用程序.1到1023号端口叫做知名端口号(well-known port numbers).源端口一般是1024号以上随机分配The Internet Layer Protocols在DoD模型中,Internet层负责:路由,以及给上层提供单独的网络接口Internet Protocol(IP)IP协议查找每个数据包(packets)的地址,然后,根据路由表决定该数据包下1段路径该如何走,寻找最佳路径Internet Control Message Protocol(ICMP)ICMP协议一样是工作在DoD模型的Internet层,IP协议使用ICMP协议来提供某些不同的服务,ICMP协议是一种管理协议一些ICMP协议相关信息和事件:1.目标不可达(destination unreachable):假如1个routers不能把IP协议数据报发送到更远的地方去,于是router将发送ICMP协议信息给数据报的发送方,告诉它说目标网络不可达2.缓冲区已满(buffer full):假如router的缓冲区已经存满发送方发来的IP协议数据报了,它将发送ICMP协议信息给发送方并告诉它缓冲区已满,如果再继续接受的话将导致缓冲区溢出,造成数据丢失3.跳(hops):IP协议数据报经过1个router,称为经过1跳4.Ping(Packet Internet Groper):采用ICMP协议信息来检查网络的物理连接和逻辑连接是否完好5.Traceroute:根据ICMP协议信息来跟踪数据在网络上的路径,经过哪些跳Address Resolution Protocol(ARP)地址解析协议(ARP)用于根据1个已知的IP地址查找硬件地址.它把IP地址翻译成硬件地址Reverse Address Resolution Protocol(RARP)RARP协议用于把MAC地址翻译成IP地址IP AddressingIP地址是软件地址,MAC地址是硬件地址,MAC地址是烧录在NIC里的,MAC地址用于在本地网络查找主机地址.IP地址是唯一的,也叫做网络地址(network address);硬件地址也叫节点地址(node address)Network Address网络地址分为5类:1.A类地址:4个8位位组(octets).第一个octet代表网络号,剩下的3个代表主机位.范围是0xxxxxxx,即0到1272.B类地址: 前2个octets代表网络号,剩下的2个代表主机位. 范围是10xxxxxx,即128到1913.C类地址: 前3个octets代表网络号,剩下的1个代表主机位. 范围是110xxxxx,即192到2234.D类地址:多播地址,范围是224到2395.E类地址:保留,实验用,范围是240到255Network Address:Special Purpose一些特殊的IP地址:1.IP地址127.0.0.1:本地回环(loopback)测试地址2.广播地址:255.255.255.2553.IP地址0.0.0.0:代表任何网络4.网络号全为0:代表本网络或本网段5.网络号全为1:代表所有的网络6.节点号全为0:代表某个网段的任何主机地址7.节点号全为1:代表该网段的所有主机广播地址TCP/IP协议规定,主机号部分各位全为1的IP地址用于广播.所谓广播地址指同时向网上所有的主机发送报文,也就是说,不管物理网络特性如何,Internet网支持广播传输.如136.78.255.255就是B类地址中的一个广播地址,你将信息送到此地址,就是将信息送给网络号为136.78的所有主机.有时需要在本网内广播,但又不知道本网的网络号时,TCP/IP协议规定32比特全为1的IP地址用于本网广播,即255.255.255.255Private IP Address私有IP地址(private IP address):节约了IP地址是空间,增加了安全性.处于私有IP地址的网络称为内网,与外部进行通信就必须靠网络地址翻(network address translation,NA T)一些私有地址的范围:1.A类地址中:10.0.0.0到10.255.255.255.2552.B类地址中:172.16.0.0到172.31.255.2553.C类地址中:192.168.0.0到192.168.255.255Broadcast Address广播地址:1.层2广播:FF.FF.FF.FF.FF.FF,发送给LAN内所有节点2.层3广播:发送给网络上所有节点3.单播(unicast):发送给单独某个目标主机4.多播:由1台主机发出,发送给不同网络的许多节点Introduction to Network Address T ranslation(NAT)NA T一般都操作在Cisco router上,用于连接2个网络,同时把私有地址翻译公有地址一些NA T的种类以及特点:1.静态NA T(static NA T):本地地址和全局地址一一对应.这样的方式需要你拥有真正的Internet上的IP地址2.动态NA T(dynamic NA T):把未注册的IP地址对应到已注册IP地址池中的某个IP地址上.你不必需要静态配置你的router使内外地址对应3.超载(overloading):采用的最广泛的NA T配置类型.类似动态NA T,但是它是把1组未注册的IP地址根据不同的端口(ports)对应到1个已注册的IP地址上.因此,它又叫做端口地址翻译(port address translation,PA T)。
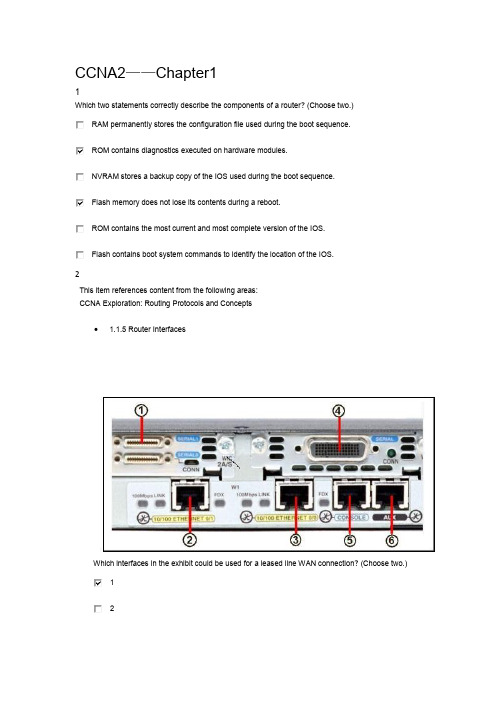
CCNA2——Chapter11Which two statements correctly describe the components of a router? (Choose two.)RAM permanently stores the configuration file used during the boot sequence.ROM contains diagnostics executed on hardware modules.NVRAM stores a backup copy of the IOS used during the boot sequence.Flash memory does not lose its contents during a reboot.ROM contains the most current and most complete version of the IOS.Flash contains boot system commands to identify the location of the IOS.2This item references content from the following areas:CCNA Exploration: Routing Protocols and Concepts1.1.5 Router InterfacesWhich interfaces in the exhibit could be used for a leased line WAN connection? (Choose two.)1234563If a router cannot find a valid configuration file during the startup sequence, what will occur?The startup sequence will reset.The router will prompt the user for a response to enter setup mode.The startup sequence will halt until a valid configuration file is acquired.The router will generate a default configuration file based on the last valid configuration.The router will monitor local traffic to determine routing protocol configuration requirements4Which of the following is the correct flow of routines for a router startup?load bootstrap, load IOS, apply configurationload bootstrap, apply configuration, load IOSload IOS, load bootstrap, apply configuration, check hardwarecheck hardware, apply configuration, load bootstrap, load IOS5What is the default sequence for loading the configuration file?NVRAM, FLASH, ROMFLASH, TFTP,CONSOLENVRAM, TFTP, CONSOLEFLASH, TFTP, ROM6From what location can a router load the Cisco IOS during the boot process? (Choose two.)TFTP serverNVRAMsetup routineFlash memoryterminal7Which are functions of a router? (Choose three.)packet switchingextension of network segmentssegmentation of broadcast domainsselection of best path based on logical addressingselection of best path based on physical addressing8What three processes does a router execute when it receives a packet from one network that is destined for another network? (Choose three.)decapsulates the Layer 3 packet by stripping off the Layer 2 frame headeruses the destination MAC Address in the IP Header to look up the next-hop address in the routing tableleaves the Layer 2 frame header intact when decapsulating the Layer 3 packetuses the destination IP Address in the IP header to look up the next-hop address in the routing tableencapsulates the Layer 3 packet into the new Layer 2 frame and forwards it out the exit interfaceencapsulates the Layer 3 packet into a special Layer 1 frame and forwards it to the exit interface9The network administrator needs to connect two routers directly via their FastEthernet ports. What cable should the network administrator use?straight-throughcross-overserial10Refer to the exhibit. What can be concluded from the output of the running-configuration of a router?The passwords are encrypted.The current configuration was saved to NVRAM.The configuration that is shown will be the one used on the next reboot.The commands that are displayed determine the current operation of the router.11Which two statements describe characteristics of load balancing? (Choose two.)Load balancing occurs when a router sends the same packet to different destination networks.Load balancing occurs when the same number of packets are sent over static and dynamic routes.Load balancing allows a router to forward packets over multiple paths to the same destinationnetwork.Unequal cost load balancing is supported by EIGRP.If multiple paths with different metrics to a destinations exist, the router cannot support loadbalancing.12Refer to the exhibit. What can be concluded from the routing table output in the exhibit? (Choose two.)This router only has two interfaces.The router interfaces are not operational yet.This router is configured to forward packets to remote networks.The FastEthernet0/0 and Serial0/0/0 interfaces of this router were configured with an IP address and the no shutdowAn IP packet received by this router with a destination address of 198.18.8.2 will be forwarded out of the Serial0/0/0 in 13The serial connection shown in the graphic needs to be configured. Which configuration commands must be made on the S to establish connectivity with the Melbourne site? (Choose three.)Sydney(config-if)# ip address 201.100.53.2 255.255.255.0Sydney(config-if)# no shutdownSydney(config-if)# ip address 201.100.53.1 255.255.255.224Sydney(config-if)# clock rate 56000Sydney(config-if)# ip host Melbourne 201.100.53.214What is the outcome of entering these commands?R1(config)# line vty 0 4R1(config-line)# password check123R1(config-line)# loginensures that a password is entered before entering user EXEC modesets the password to be used for connecting to this router via Telnetrequires check123 to be entered before the configuration can be savedcreates a local user account for logging in to a router or switch15Passwords can be used to restrict access to all or parts of the Cisco IOS. Select the modes and interfaces that can be protected with passwords. (Choose three.)VTY interfaceconsole interfaceEthernet interfacesecret EXEC modeprivileged EXEC moderouter configuration mode16Refer to the exhibit. The network administrator has configured the router with the interface IP addresses shown for the direc networks. Pings from the router to hosts on the connected networks or pings between router interfaces are not working. Wh likely problem?The destination networks do not exist.The IP addresses on the router interfaces must be configured as network addresses and not host addresses.The interfaces must be enabled with the no shutdown command.Each interface must be configured with the clock rate command.17Refer to the exhibit. The network administrator has configured the router with the interface IP addresses shown for the direc networks. Pings from the router to hosts on the connected networks or pings between router interfaces are not working. Wh likely problem?The destination networks do not exist.The IP addresses on the router interfaces must be configured as network addresses and not host addresses.The interfaces must be enabled with the no shutdown command.Each interface must be configured with the clock rate command.18Refer to the exhibit. All routers have a route in its routing table to each network that is shown in the exhibit. Default routes h issued on these routers. What can be concluded about how packets are forwarded in this network? (Choose two.)If RouterC receives a packet that is destined for 10.5.1.1, it will be forwarded out interface Fa0/0.If RouterA receives a packet that is destined for 192.168.3.146, it will be forwarded out interface S0/0/1.If RouterB receives a packet that is destined for 10.5.27.15, it will be forwarded out interface S0/0/1.If RouterB receives a packet that is destined for 172.20.255.1, it will be forwarded out interface S0/0/0.If RouterC receives a packet that is destined for 192.16.5.101, it will be forwarded out interface S0/0/1.19What header address information does a router change in the information it receives from an attached Ethernet interface be information is transmitted out another interface?only the Layer 2 source addressonly the Layer 2 destination addressonly the Layer 3 source addressonly the Layer 3 destination addressthe Layer 2 source and destination addressthe Layer 3 source and destination address20Refer to the exhibit. Host A pings host B. When R4 accepts the ping into the Ethernet interface, what two pieces of header in included? (Choose two.)source IP address: 192.168.10.129source IP address: BBBB.3333.5677source MAC address: 5555.AAAA.6666destination IP address: 192.168.10.33destination IP address: 192.168.10.134destination MAC address: 9999.DADC.123421Refer to the exhibit. After host 2 is connected to the switch on the LAN, host 2 is unable to communicate with host 1. What i this problem?The subnet mask of host 2 is incorrect.Host 1 and host 2 are on different networks.The switch needs an IP address that is not configured.The router LAN interface and host 1 are on different networks.The IP address of host 1 is on a different network than is the LAN interface of the router.CCNA2——chapter21The output of the Router# show interfaces serial 0/1 command displays the following:Serial0/1 is up, line protocol is down.What is the most likely cause for the line protocol being down?Serial0/1 is shutdown.There is no cable connecting the routers.The remote router is using serial 0/0.No clock rate has been set.2Which address can be used to summarize networks 172.16.0.0/24 thru 172.16.7.0/24?172.16.0.0/21172.16.1.0/22172.16.0.0 255.255.255.248172.16.0.0 255.255.252.03Refer to the exhibit. How will packets destined to the 172.16.0.0 network be forwarded?Router1 will perform recursive lookup and packet will exit S0/0.Router1 will perform recursive lookup and packet will exit S0/1.There is no matching interface associated with network 172.16.0.0 so packets will be dropped.There is no matching interface associated with network 172.16.0.0 so packets will take gateway of last resort and exit4A static route that points to the next hop IP will have what administrative distance and metric in therouting table?administrative distance of 0 and metric of 0administrative distance of 0 and metric of 1administrative distance of 1 and metric of 0administrative distance of 1 and metric of 15Hosts on two separate subnets cannot communicate. The network administrator suspects a missingroute in one of the routing tables. Which three commands can be used to help troubleshoot Layer 3connectivity issues? (Choose three.)pingshow arptracerouteshow ip routeshow controllersshow cdp neighbor6Refer to the exhibit. Which static route should be configured on Router1 so that host A will be able to reach host B on the 1 network?ip route 192.168.0.0 172.16.0.0 255.255.0.0ip route 172.16.0.0 255.255.0.0 192.168.0.1ip route 172.16.0.0 255.255.0.0 S0/0/1ip route 172.16.0.0 255.255.0.0 S0/0/07Which of the following are displayed by the Router# show cdp neighbors command? (Choose three.)loadplatformreliabilityholdtimelocal interface8Why is it advisable to enter a next-hop IP address when creating a static route whose exit interface is anEthernet network?Adding the next-hop address eliminates the need for the router to do any lookups in the routing tablebefore forwarding a packet.In a multi-access network, the router cannot determine the next-hop MAC address for the Ethernetframe without a next-hop address.Using a next-hop address in a static route provides a route with a lower metric.In multi-access networks, using a next-hop address in a static route makes that route a candidatedefault route.9Refer to the exhibit. Which set of commands will configure static routes that will allow the WinterPark and the Altamonte rou packets from each LAN and direct all other traffic to the Internet?WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 0.0.0.0 0.0.0.0 s0/1WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 198.18.222.0 255.255.255.255 s0/1WinterPark(config)# ip route 172.191.67.0 255.255.255.0 192.168.146.1WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2WinterPark(config)# ip route 172.191.67.0 255.255.255.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 0.0.0.0 0.0.0.0 s0/010What happens to a static route entry in a routing table when the outgoing interface is not available?The route is removed from the table.The router polls neighbors for a replacement route.The route remains in the table because it was defined as static.The router redirects the static route to compensate for the loss of the next hop device.11Refer to the exhibit. Given the output in the exhibit, how would a clock rate be determined for this link?The rate would be negotiated by both routers.A rate would not be selected due to the DCE/DTE connection mismatch.The rate configured on the DTE determines the clock rate.The rate configured on the DCE determines the clock rate.12Which piece of information is available from examining the output of the command show ip interface brief?Interface speed and duplexInterface MTUErrorsInterface MAC addressInterface IP address13What two devices are responsible for converting the data from the WAN service provider into a form acceptable by the router? (Choose two).the serial port of the routera modema switchthe ethernet port of the routera CSU/DSU devicea DTE device14Refer to the exhibit. What two commands are required to provide connectivity between the 192.168.1.0 and 10.0.0.0 netwo requiring recursive lookup? (Choose two.)A(config)# ip route 10.0.0.0 255.0.0.0 s 0/1/0A(config)# ip route 10.0.0.0 255.0.0.0 172.16.40.2A (config)# ip route 10.0.0.0 255.0.0.0 s 0/0/0B(config)# ip route 192.168.1.0 255.255.255.0 s 0/0/0B (config)# ip route 192.168.1.0 255.255.255.0 172.16.40.1B(config)# ip route 192.168.1.0 255.255.255.0 s 0/1/015A router has one static route configured to each destination network. Which two scenarios would requirean administrator to alter the static routes that are configured on that router? (Choose two.)The destination network no longer exists.The destination network is moved to a different interface on the same router.The path between the source and destination is upgraded with a higher bandwidth link.The remote destination network interface has to be down for 15 minutes of maintenance.A topology change occurs where the existing next-hop address or exit interface is not accessible.16A network administrator enters the following command into Router1: ip route 192.168.0.0 255.255.255.0S0/1/0. Router1 then receives a packet that is destined for 192.168.0.22/24. After finding the recentlyconfigured static route in the routing table, what does Router1 do next to process the packet?drops the packet because the destination host is not listed in the routing tablelooks up the MAC address of the S0/1/0 interface to determine the destination MAC address of thenew frameperforms a recursive lookup for the IP address of the S0/1/0 interface before forwarding the packetencapsulates the packet into a frame for the WAN link and forwards the packet out the S0/1/0interface17Refer to the exhibit. A company network engineer is assigned to establish connectivity between the two Ethernet networks on the 10.1.1.0/24 subnet can contact hosts on the 10.1.2.0/24 subnet. The engineer has been told to use only static routin company routers. Which set of commands will establish connectivity between the two Ethernet networks?R1(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.1R2(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.2R1(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.2R2(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.1R1(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.2R2(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.1R1(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.1R2(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.2R1(config)# ip route 0.0.0.0 0.0.0.0 10.1.2.1R2(config)# ip route 0.0.0.0 0.0.0.0 10.1.1.118Refer to the exhibit. What is the significance of the /8 in the route to the 10.0.0.0 network?It indicates that there are 8 hops between this router and the 10.0.0.0 network.It represents the time, in milliseconds, it takes for a ping to reply when sent to the 10.0.0.0 network.It indicates that there are 8 subnets in the destination network to which the router can forward packets.It indicates the number of consecutive bits, from the left, in the destination IP address of a packet that must match 10.that route.Refer to the exhibit. What two commands will change the next-hop address for the 10.0.0.0/8 networkfrom 172.16.40.2 to 192.168.1.2? (Choose two.)A(config)# no network 10.0.0.0 255.0.0.0 172.16.40.2A(config)# no ip address 10.0.0.1 255.0.0.0 172.16.40.2A(config)# no ip route 10.0.0.0 255.0.0.0 172.16.40.2A(config)# ip route 10.0.0.0 255.0.0.0 s0/0/0A(config)# ip route 10.0.0.0 255.0.0.0 192.168.1.220Which two statements describe functions or characteristics of CDP? (Choose two.)It starts up automatically and allows the device to detect directly connected neighbor devices that use CDP.It operates at the network layer and allows two systems to learn about each other.It creates a topology map of the entire network.It allows systems to learn about each other even if different network layer protocols are configured.It forwards advertisements about routes for faster convergence.21Which of the following is true regarding CDP and the graphic shown?CDP running on Router D will gather information about routers A, B, C, and E.By default, Router A will receive CDP advertisements from routers B and C.If routers D and E are running different routing protocols, they will not exchange CDP information.Router E can use CDP to identify the IOS running on Router B. CCNA——Chapter3Which two statements correctly describe the concepts of administrative distance and metric? (Choose two.)Administrative distance refers to the trustworthiness of a particular route.A router first installs routes with higher administrative distances.The value of the administrative distance can not be altered by the network administrator.Routes with the smallest metric to a destination indicate the best path.The metric is always determined based on hop count.The metric varies depending which Layer 3 protocol is being routed, such as IP or IPX.Refer to the exhibit. Which statement correctly describes how R1 will determine the best path to R2?R1 will install a RIP route using network A in its routing table because the administrative distance of RIP is higher than EIGRP.R1 will install a RIP route using network A in its routing table because the path cost from RIP is lower than EIGRP.R1 will install an EIGRP route using network B in its routing table because the administrativedistance of EIGRP is lower than RIP.R1 will install an EIGRP route using network B in its routing table because the path cost from EIGRP is lower than RIP.R1 will install an EIGRP route and a RIP route in its routing table and load balance between them.3Which two statements are true regarding classless routing protocols? (Choose two.)sends subnet mask information in routing updatessends complete routing table update to all neighborsis supported by RIP version 1allows for use of both 192.168.1.0/30 and 192.168.1.16/28 subnets in the same topologyreduces the amount of address space available in an organization4Which command would the network administrator issue to determine if load balancing is in effect on a router?show ip protocolsshow ip routeshow ip interface briefshow ip interface5Which two conditions would create a setting where the use of a distance-vector routing protocol would be efficient? (Choose two.)the network requires a special hierarchical designfast convergence of the network is crucialthe network is using a hub and spoke topologythe network is using a flat designthere are more than 15 hops between the most distant routers6What is the purpose of a routing protocol?It is used to build and maintain ARP tables.It provides a method for segmenting and reassembling data packets.It allows an administrator to devise an addressing scheme for the network.It allows a router to share information about known networks with other routers.It provides a procedure for encoding and decoding data into bits for packet forwarding.7Which of the following best describes the operation of distance vector routing protocols?They use hop count as their only metric.They only send out updates when a new network is added.They send their routing tables to directly connected neighbors.They flood the entire network with routing updates8When multiple routing protocols have a route to the same destination network, what determines which route is installed in the routing table?best metriclowest hop countgreatest available bandwidthlowest administrative distancelowest cost9Why is fast convergence desirable in networks that use dynamic routing protocols?Routers will not allow packets to be forwarded until the network has converged.Hosts are unable to access their gateway until the network has converged.Routers may make incorrect forwarding decisions until the network has converged.Routers will not allow configuration changes to be made until the network has converged.10Which of the following conditions must be met in order for a network to have converged?The routers in the network are operating with dynamic routing protocols.The routers in the network are operating with compatible versions of IOS.The routers in the network are operating with the same routing tables.The routers in the network are operating with consistent routing knowledge.11Which two statements are true regarding metrics? (Choose two.)RIP uses bandwidth as a metric.OSPF uses delay as a metric.EIGRP uses bandwidth as a metric.OSPF uses cost based on bandwidth as a metric.RIP uses delay as a metric.EIGRP uses hop count only as a metric.12Which two statements are true regarding the advantages of the use of static routes? (Choose two).increased securityreduced effort in configuring routesthe administrator maintains control over routingeasier to implement in a growing networkreduces the chance of routing errorsincreased router resource usage13What will be the result of the following commands?ORL(config)# interface fastethernet 0/0ORL(config-if)# ip address 172.16.3.1 255.255.255.0ORL(config-if)# no shutdownThe 172.16.3.0 network will be routed by any dynamic routing protocol automatically.A routing table entry is made to the 172.16.3.0 network with a code of "C".A static route is required to route traffic to the 172.16.3.0 network.The commands will be saved to the startup-configuration automatically.14The following line of code is displayed in a routing table:R 209.165.201.0/24 [120/2] via 192.168.252.2, 00:00:16, S0/0/0What can be concluded from this output?A packet destined for host 192.168.252.2 will be forwarded out the interface connected to network209.165.201.0/24.The value, 120, is used to determine the best path when a router has more than one routingprotocol configured for the same destination network.This route was manually configured using the ip route command.192.168.252.2 is an interface on the router that produced this output.15An engineer creates a static route by entering the Router(config)# ip route 10.0.0.0 255.255.255.0192.168.1.2 command. What can be concluded about this route?The administrative distance of this route is 1.192.168.1.2 is the address of an interface on this router.This route will display as a directly connected network in the routing table.Packets with a destination IP address of 192.168.1.2 will be forwarded to the 10.0.0.0/24 networkfirst.16Refer to the exhibit. Router1 and Router2 are running EIGRP. All interfaces are operational and packets can be forwarded networks. What information will be found in the routing table for Router1?Router1 will have 6 directly connected networks.The administrative distance of the route to network 172.16.0.0 will be 90.The metric for routes to 172.16.0.0 will be 1.The interface that is used to forward packets to 172.16.0.0 will always be the S0/1 interface.17The following line of code is present in the routing table:O 10.16.1.0/27 [110/129] via 192.168.1.5, 00:00:05, Serial0/0/1What does the number 129 indicate in this output?The cost for this link has a value of 129.The clock rate on this serial interface is set to 129,000.The next-hop router is 129 hops away from this router.This route has been updated 129 times in this routing table.18A growing medium-sized manufacturing company recently began to have routing instability issues. The company uses statihas a mixture of over 30 Cisco and non-Cisco routers. The network administrator has decided to convert the network to dyn What characteristics of protocols should be considered in this selection process?Distance vector routing protocols, such as RIP, converge more quickly than do link-state routing protocols.EIGRP can be used on all of the routers in the company.OSPF can be used between the routers.An exterior routing protocol, such as BGP, is recommended for growing companies.Refer to the exhibit. If RIP is the routing protocol, what is the value of the metric from router A to network192.168.5.0/24?345662472420A router learns two paths with equal metrics to a destination network via the RIP routing protocol. How will the router handle packets to the destination network?The router will install the first route it learned into the routing table.The router will install both routes in the routing table and load balance between the two.The router will put the first route in the routing table, and denote the second route as a backup route.The router will pick the path with the higher bandwidth and will place it in the routing table.CCNA2_41Which event will cause a triggered update?an update routing timer expiresa corrupt update message is receiveda route is installed in the routing tablethe network is converged2Three routers running a distance-vector routing protocol lost all power, including the battery backups. When the routers reload, what will happen?They will share all routes saved in NVRAM prior to the power loss with their directly connected neighbors.They will multicast hello packets to all other routers in the network to establish neighboradjacencies.They will send updates that include only directly connected routes to their directly connectedneighbors.They will broadcast their full routing table to all routers in the network.3What does the RIP holddown timer do?ensures an invalid route has a metric of 15prevents a router from sending any updates after it has introduced a routing loop into the network ensures every new route is valid before sending an updateinstructs routers to ignore updates, for a specified time or event, about possible inaccessible routes4Which two statements are true regarding the function of the RIPv1 routing updates? (Choose two).updates are broadcast only when there are changes to the topologyupdates are broadcast at regular intervalsbroadcast are sent to 0.0.0.0broadcasts are sent to 255.255.255.255updates contain the entire network topologyonly changes are included in the updates5Which of the following statements are correct about RIP?uses a broadcast to update all other routers in the network every 60 secondsuses a multicast address to update other routers every 90 secondswill send out an update if there is a failure of a linkupdates only contain information about routes that have changed since last update6Which two statements describe EIGRP? (Choose two.)EIGRP can be used with Cisco and non-Cisco routers.。



在这个拓扑图中,交换机就成了一个单点故障,如果交换机坏了,此时的几个模块之间都无法进行正常的工作,客户机不能访问服务器,不能连接i n t e r n e t,不能访问打印机,反之都一样。
所谓单点故障,也就是一点发生故障,则整网络无法正常工作。
所以在一般的交换式网络中,我们都需要对交换机进行冗余,但是引入冗余又会发生一个问题,一个很严重的问题,就是网络环路。
下面我们来看看环路对我们的网络到底造成了什么影响,影响主要有三:1B r o a d c a s t s t o r m s广播风暴2M u l t i p l e F r a m e C o p i e s多重复数据帧3M A C D a t a b a s e I n s t a b i l i t y M A C地址表不稳定咱们一一来看广播风暴:我们看一个图,大家就明白什么是广播风暴了:分析:如果主机X希望跟网络上的其他主机通讯,将数据报传给交换机A,但交换机仍然会将此报再一次传给交换机A,依次类似,构成了一个环,而且这个环后面比较严重,为什么?我们在讲网络基础的时候,我们讲了数据帧的格式,大家可以回忆一下,但在这个格式中,没有类似于三层I P报头中T T L机制,所以数据帧在网络中将被无限次数的传递,从面造成了广播风暴,如果是单播的数据还要好一些,如果是广播或者组播数据在这样一个环路网络中传递则广播风暴更加明显。
多重数据帧:也称为重复数据帧分析:主机X准备发一个单播帧给路由器Y,数据报发出后,发现有两条路可以到达路由器Y,一个是直接发过去,还有一条就是通过交换机A转给交换机B,然后再交给路由器Y,此时路由器Y就收到了两位一模一样的数据帧。
还有一个就是M A C地址表的不稳定:分析:还是主机X发送数据帧给路由器Y,路由器的M A C地址表还没有被交换机学习到,数据帧沿链路发送到交换A和交换机B的端口0,那么交换机A和交换机B都将主机X的M A C地址记录在p o r t0。
CCNA 1 - Chapter 2Posted by beotron at 3:06 PM1. Which two layers of the OSI model have the same functions as the TCP/IP model Network Access Layer? (Choose two.)• Network• Transport• Physical• Data Link• Session2. What is a primary function of the trailer information added by the data link layer encapsulation? • supports error detection• ensures ordered arrival of data• provides delivery to correct de stination• identifies the devices on the local network• assists intermediary devices with processing and path selection3. During the encapsulation process, what occurs at the data link layer?• No address is added.• The logical address is added.• The physical address is added.• The process port number is added.4. What device is considered an intermediary device?• file server• IP phone• laptop• printer• switch5.Which layer encapsulates the segment into packets?• physical• data link• network• transport6. Which statements correctly identify the role of intermediary devices in the network? (Choose three.) • determine pathways for data• initiate data communications• retime and retransmit data signals• originate the flow of data• manage data flows• final termination point for data flow7. What can be identified by examining the network layer header?• the destination device on the local media• the path to use to reach the destination host• the bits that will be transferred over the media• the source application or process creating the data8. What is the proper order of the layers of the OSI model from the highest layer to the lowest layer? • physical, network, application, data link, presentation, session, transport• application, physical, session, transport, network, data link, presentation• application, presentation, physical, session, data link, transport, network• application, presentation, session, transport, network, data link, physical• presentation, data link, session, transport, network, physical, application9. Refer to the exhibit. Which three labels correctly identify the network types for the network segments that are shown? (Choose three.)• Network A — WAN• Network B — WAN• Network C — LAN• Network B — MAN• Network C — WAN• Network A — LAN10. What are the key functions of encapsulation? (Choose three.)• allows modification of the original data before transmission• identifies pieces of data as part of the same communication• enables consistent network paths for comm unication• ensures that data pieces can be directed to the correct receiving end device• enables the reassembly of complete messages• tracks delay between end devices11. Refer to the exhibit. Which networking term describes the data interleaving process represented in the graphic?• piping• PDU• streaming• multiplexing• encapsulation12. What is a PDU?• corruption of a frame during transmission• data reassembled at the destination• retransmitted packets due to lost communication• a layer specific encapsulation13. Refer to the exhibit. “Cell A” at IP address 10.0.0.34 has established an IP session with “IP Phone 1″ at IP address 172.16.1.103. Based upon the graphic, which device type best describes the function of wireless device “Cell A?”• the destination device• an end device• an intermediate device• a media device14. Refer to the exhibit. Which set of devices contains only end devices?• A, C, D• B, E, G, H• C, D, G, H, I, J• D, E, F, H, I, J• E, F, H, I, J15. Refer to the exhibit. Which term correctly identifies the device type that is included in the green area? • source• end• transfer• intermediary16. Which three statements best describe a Local Area Network (LAN)? (Choose three.)• A LAN is usually in a single geographic al area.• The network is administered by a single organization.• The connection between segments in the LAN is usually through a leased connection.• The security and access control of the network are controlled by a service provider.• A LAN provides ne twork services and access to applications for users within a common organization.• Each end of the network is generally connected to a Telecommunication Service Provider (TSP).17. Refer to the exhibit. What type of network is shown?• WAN• MAN• LAN• W LAN18. What is the purpose of the TCP/IP Network Access layer?• path determination and packet switching• data representation, encoding, and control• reliability, flow control, and error detection• detailing the components that make up the physical lin k and how to access it• the division of segments into packets19. Which characteristic correctly refers to end devices in a network?• manage data flows• originate data flow• retime and retransmit data signals• determine pathways for data20. What is the primary purpose of Layer 4 port assignment?• to identify devices on the local media• to identify the hops between source and destination• to identify to the intermediary devices the best path through the network• to identify the source and destinati on end devices that are communicating• to identify the processes or services that are communicating within the end devices21. Select the statements that are correct concerning network protocols. (Choose three.) • define the structure of layer specific PDU’s• dictate how to accomplish layer functions• outline the functions necessary for communications between layers• limit hardware compatibility• require layer dependent encapsulations• eliminate standardization among vendors。
下列哪些陈述正确指出了中间设备在网络中的作用?(选择三项)
确定数据传输路径
发起数据通信
重新定时和重新传输数据信号
发送数据流
管理数据流
数据流最后的终止点
2什么是PDU?
传输期间的帧损坏
在目的设备上重组的数据
因通信丢失而重新传输的数据包
特定层的封装
3封装的关键功能是什么?(选择三项)
供传输前修改原始数据
标识数据片段属于同一通信
为通信提供统一的网络路径
确保数据片段可以转发到正确的接收端设备
实现完整消息的重组
跟踪终端设备之间的延迟
4O SI 模型各层从最高层到最低层的正确顺序如何?
物理层、网络层、应用层、数据链路层、表示层、会话层、传输层
应用层、物理层、会话层、传输层、网络层、数据链路层、表示层
应用层、表示层、物理层、会话层、数据链路层、传输层、网络层
应用层、表示层、会话层、传输层、网络层、数据链路层、物理层
表示层、数据链路层、会话层、传输层、网络层、物理层、应用层
5
请参见图示。
所示网络属于哪一类型?
WAN
MAN
LAN
WLAN
6选择关于网络协议的正确陈述。
(选择三项)
定义特定层PDU 的结构
规定实现协议层功能的方式
概述层与层之间通信所需的功能
限制了硬件兼容性
需要取决于协议层的封装过程
杜绝厂商之间的标准化
7第4 层端口指定的主要作用是什么?
标识本地介质中的设备
标识源设备和目的设备之间的跳数
向中间设备标识通过该网络的最佳路径
标识正在通信的源终端设备和目的终端设备
标识终端设备内正在通信的进程或服务
8哪种设备被视为中间设备?
文件服务器
IP 电话
笔记本电脑
打印机
交换机
9OSI 模型哪两层的功能与TCP/IP 模型的网络接入层相同?(选择两项)
网络层
传输层
物理层
数据链路层
会话层
10以下哪种特征正确代表了网络中的终端设备?
管理数据流
发送数据流
重新定时和重新传输数据信号
确定数据传输路径
11哪一层负责将数据段封装成数据包?
物理层
数据链路层
网络层
传输层
12通过检查网络层报头可以确定什么?
本地介质上的目的设备
用于到达目的主机的路径
将要通过介质传输的比特
创建数据的源应用程序或进程
13数据链路层封装添加的报尾信息有何主要功能?
支持差错校验
确保数据按照顺序到达
确保送达正确目的
标识本地网络中的设备
帮助中间设备进行处理和路径选择
14
请参见图示。
哪个网络术语描述了图中所示的数据交替发送过程?
通道
PDU
流传输
多路复用
封装
15
请参见图示。
下列哪组设备仅包含终端设备?
A、C、D
B、E、G、H
C、D、G、H、I、J
D、E、F、H、I、J
E、F、H、I、J
下列哪三项陈述是对局域网(LAN) 最准确的描述?(选择三项)
LAN 通常位于一个地域内。
此类网络由由一个组织管理。
LAN 中的不同网段之间一般通过租用连接的方式连接。
此类网络的安全和访问控制由服务提供商控制。
LAN 为同一个组织内的用户提供网络服务和应用程序访问。
此类网络的每个终端通常都连接到电信服务提供商(TSP)。
17在封装过程中,数据链路层执行什么操作?
不添加地址。
添加逻辑地址。
添加物理地址。
添加进程的端口号。
18
请参见图示。
IP 地址为10.0.0.34 的“手机A”已经与IP 地址为172.16.1.103 的“IP 电话1”建立了IP 会话。
请根据图哪个设备类型是对无线设备“手机A”功能的最准确描述?
目的设备
终端设备
中间设备
介质设备
19T CP/IP 网络接入层有何作用?
路径确定和数据包交换
数据表示、编码和控制
可靠性、流量控制和错误检测
详细规定构成物理链路的组件及其接入方法
将数据段划分为数据包
20
请参见图示。
下列哪三个标签正确标识了图示网段的网络类型?(选择三项)
网络 A -- WAN
网络 B -- WAN
网络 C -- LAN
网络 B -- MAN
网络 C -- WAN
网络 A -- LAN
21
请参见图示。
哪个术语正确判断出了包含于绿色区域中的设备类型?
源
终端
中间。