OhwYaa企业知识社区V2.0
- 格式:pptx
- 大小:8.35 MB
- 文档页数:82


企业2.0,即企业社会化网络服务,在美国,企业2.0模式已被验证。
将“企业2.0”带入中国公众视野的是微软以12亿美元现金并购Yamme r。
Yammer是款典型的企业2.0软件,你可以把它视为企业版Facebook,Yammer满足简洁、易用的用户需求,某种程度上它代表着企业软件未来的发展方向。
这款封闭性的企业微博,是“针对你公司的私人社交网络”,主要应用于工作管理、项目团队协同工作。
团队成员可以在群组中实时提出问题,请求帮助,寻求解决方案等。
Yammer上功能和应用程序的逐渐增多,这些新的应用程序包括投票、聊天、活动、链接、主题、问答、想法等等。
Yammer自诞生后,在中国就出现了它的模仿者。
当你了解了yamme r后,你再看国内的企业2.0软件,就会发现国内的打着企业2.0称号的软件,也多是Yammer中文版。
当然,也有微创新者,除了大名鼎鼎的Yammer、Jive外,还有很多优秀的社交类工具可以模仿如baseCAMp、asana、trello等,在国内也就出现了多家相应的模仿者。
国外企业2.0软件之所以被用户接纳并良好使用,是因其文化,美国公司的企业员工们,在互联网世界成长起来的年轻员工们,追求平等、独立、开放,哪怕在公司上下级之间,企业主和员工也可以进行相对平等的沟通,同时也乐意沟通,所以这些设计出简洁、友好的企业2. 0软件备受青睐。
但是面前对于中国的企业而言,在传统的企业1.0的管理软件教育下或者企业固有的管理模式影响下,尤其是大中型企业而言,工作都被固化在指定范围内,“越级、越权”等行为被严厉禁止。
所以目前大部分中国企业要使用那些完全模仿yammer及相关产品的抄袭版企业2.0的企业显然步子有点太大了,也会被企业排斥,认为这些软件所描述的美好前景不符合企业现状,纯属“扯谈”。


WebSphere配置说明1 安装部署中用到的参数 (2)2 数据库客户端准备 (3)3 设置服务器端配置参数 (6)3.1 启动服务前准备 (6)3.1.1 WebSphere 5.1 (6)3.1.2 WebLogic 8.1 (6)3.1.3 WebLogic 6.1 (7)3.2 运行服务器配置工具 (7)3.2.1 WebSphere 5.1 (7)3.2.2 WebLogic 8.1 (8)3.2.3 WebLogic 6.1 (9)3.3 设置服务器参数 (10)3.3.1 WebSphere 5.1 (10)3.3.2 WebLogic 8.1 (12)3.3.3 WebLogic 6.1 (13)3.4 安装系统服务器、业务服务器 (13)3.4.1 WebSphere 5.1 (13)3.4.2 WebLogic 8.1 (14)3.4.3 WebLogic 6.1 (19)3.5 设置数据缓冲池 (20)3.5.1 WebSphere 5.1 (20)3.5.2 WebLogic 8.1 (21)3.5.3 WebLogic 6.1 (24)3.6 配置JDBC数据源 (26)3.6.1 WebSphere 5.1 (26)3.6.2 WebLogic 8.1 (29)3.6.3 WebLogic 6.1 (31)3.7 配置EJBConfig.xml (33)3.7.1 设置服务器间连接参数 (33)3.7.2 设置数据连接的JNDI名称 (35)3.7.3 设置EJBConfig.xml的数据连接和业务数据库的连接参数 (35)3.7.4 部署EJBConfig.xml文件 (39)3.8 重新启动WebSphere服务 (40)4 安装配置Web服务器 (41)4.1 安装Web模块 (41)4.1.1 WebSphere 5.1 (41)4.1.2 WebLogic 8.1 (42)4.1.3 WebLogic 6.1 (46)4.2 复制NewV ersion目录到服务器 (46)4.2.1 WebSphere 5.1 (46)4.2.2 WebLogic 8.1 (47)4.2.3 WebLogic 6.1 (47)5 客户端配置 (48)6 错误处理 (49)7 WebSphere 5.1的安装 (51)8 Weblogic 8.1的安装 (56)8.1 安装 (56)8.2 创建新的域 (61)8.3 启动WebLogic的域服务 (64)9 安装WebLogic 6.1 (66)9.1 安装 (66)9.2 创建域 (70)9.3 启动服务 (71)10 附件 (71)1安装部署中用到的参数这里是本安装说明文件用到的各种参数1.1 WebSphere 5.11.2 WebLogic 8.11.3 WebLogic 6.1 todo2数据库客户端准备2.1 Oracle2.1.1Oracle数据库JDBC驱动安装Oracle客户端,JDBC驱动程序在d:\Oracle\ora92\java\lib目录下JDBC驱动文件classes12.jar、nls_charset12.jar、ocrs12.jarURL jdbc:oracle:oci:@testdbDriver Classname oracle.jdbc.driver.OracleDriverProperties user=BusinessDemo2.1.2weblogic 8.1自带驱动JDBC驱动文件wloracle.jarURL jdbc:bea:oracle://192.168.1.116:1521Driver Classname weblogic.jdbc.oracle.OracleDriverProperties user=BusinessDemoportNumber=1521SID=testdbserverName=192.168.1.1162.2 SQL Server2.2.1SQL Server 2000 Driver for JDBC Service Pack 31.下载安装JDBC驱动●下载,并安装/downloads/details.aspx?FamilyID=07287b11-0502-461a-b138-2aa54bfdc03a&DisplayLang=en●拷贝D:\Program Files\Microsoft SQL Server 2000 Driver for JDBC\SQLServerJTA\sqljdbc.dll 到C:\Program Files\Microsoft SQL Server\MSSQL\Binn目录下●在SQL Analyser中打开并执行D:\Program Files\Microsoft SQL Server 2000 Driverfor JDBC\SQLServer JTA\instjdbc.sql文件●或者在DOS下,执行ISQL -Usa -P sa_password -S server_name -i location\instjdbc.sql注意:大小写区分,而且location目录名不能有空格2.连接参数JDBC驱动文件在D:\Program Files\Microsoft SQL Server 2000 Driver for JDBC\lib目录下JDBC驱动文件mssqlserver.jar、msbase.jar、msutil.jarURL jdbc:microsoft:sqlserver://192.168.0.133:1433Driver Classname: com.microsoft.jdbc.sqlserver.SQLServerDriverproperties user=saselectMethod=cursordataSourceName=SQL2000JDBCuserName=sadatabaseName=Test1554serverName=192.168.0.133注意:在Websphere 5.1下,请删掉数据源v4的定制属性的disable2Phase属性。
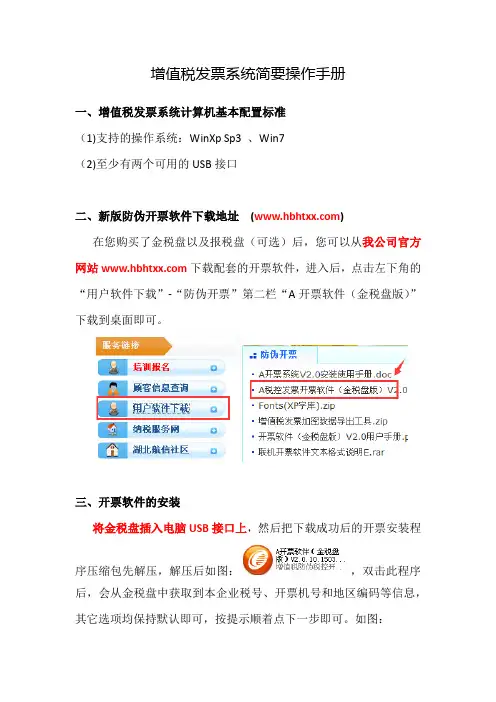
增值税发票系统简要操作手册一、增值税发票系统计算机基本配置标准(1)支持的操作系统:WinXp Sp3 、Win7(2)至少有两个可用的USB接口二、新版防伪开票软件下载地址()在您购买了金税盘以及报税盘(可选)后,您可以从我公司官方网站下载配套的开票软件,进入后,点击左下角的“用户软件下载”-“防伪开票”第二栏“A开票软件(金税盘版)”下载到桌面即可。
三、开票软件的安装将金税盘插入电脑USB接口上,然后把下载成功后的开票安装程序压缩包先解压,解压后如图:,双击此程序后,会从金税盘中获取到本企业税号、开票机号和地区编码等信息,其它选项均保持默认即可,按提示顺着点下一步即可。
如图:注意:开票软件安装包运行后会自动检测系统中是否已经安装Microsoft .net Framework4.0或以上版本,如果检测到未安装,开票软件会自行安装(已集成在开票软件安装程序内,无需手工下载),所以安装时间会比较长,请耐心等待。
四、初次进入开票软件的设置将金税盘插入电脑USB接口上(如购买了报税盘则要插入报税盘),点击“开票软件”图标即可启动开票软件,第一次启动时,系统需要输入管理员密码及证书口令,管理员初始密码为“123456”,初始证书口令为“88888888”。
登录后进入欢迎界面,在1.系统初始化处,输入“主管姓名”以及用户密码(就是管理员密码),该处需设置4位以上的密码,2.基本参数设置处的“营业地址”“电话号码”以及“银行帐号”(银行帐号栏应输入开户行和帐号)输入实际的即可,该处设置的信息,将打印到您开具的发票票面上,在3.上传参数设置处,将“安全接入服务器地址”:设为https:// (https记得要带s,服务器地址要在输入法为英文的状态下输入,电脑右下角输入法的状态应该为),输入完毕后,点击“测试”按钮测试一次,如输入无误,即提示连接成功。
123五、旧版开票数据迁移到新版开票系统如果新版开票软件是安装在旧版开票软件的电脑上,在完成初始设置后,会自动出现数据迁移的提示,如图:,直接点“迁移”,中间会出现“此操作可能需要持续几分钟,是否继续?”的提示,点击“是”继续,请您耐心等待,不要进行任何操作,直到出现数据迁移成功,最后点“完成”。
EWHA providerKOGANEI servo handVersion 1.0.1User's guideJuly 17, 2012【 Remarks 】【 Revision history 】Version Date ContentFirstedition.1.0.0.0 2006-02-241.0.0.1 2010-02-11 Error code was added1.0.1 2012-07-17 Document versioning rules was changed【 Hardware 】Model Version NotesContents1. Introduction (4)2. Outline of provider (5)2.1. Outline (5)2.2. Method and property (6)2.2.1. CaoWorkspace::AddController method (6)2.2.2. CaoController::AddVariable method (7)2.2.3. CaoController::AddCommand method (7)2.2.4. CaoController::Execute method (8)2.2.5. CaoController::Cancel method (8)2.2.6. CaoController::get_CommandNames property (8)2.2.7. CaoController::get_VariableNames property (8)2.2.8. CaoCommand::Execute method (8)2.2.9. CaoCommand::put_Parameter property (9)2.2.10. CaoCommand::get_Parameter property (9)2.2.11. CaoCommand::get_Result property (9)2.2.12. CaoVariable::put_ID property (9)2.2.13. CaoVariable::get_ID property (9)2.2.14. CaoVariable::put_Value property (9)2.2.15. CaoVariable::get_Value property (10)2.3. Variable list (11)2.3.1. Controller class (11)2.4. Error code (11)3. Sample program (12)1.IntroductionThis book is a user's guide of the EWHA provider that is the CAO provider for servo hand (EWHA) manufactured by KOGANEI.The EWHA provider sends and receives the command by RS-232C for the servo hand.2.Outline of provider2.1.OutlineThe EWHA provider executes each command with CaoController::Execute, CaoCommand::Execute, CaoVariable::putValue, and CaoVariable::getValue.In CaoController::Execute, the character string of the command is sent as it is as a command.In CaoCommand::Execute, the command corresponding to the command name is executedIn CaoVariable::putValue or CaoVariable::getValue, the value is set/acquired by the command that corresponding to the variable name.The file format of the EWHA provider is DLL (Dynamic Link Library), and the table 2-1 lists detailsTable2-1EWHA providerFile name CaoProvEWHA.dllProgID CaoProv.KOGANEI.EWHARegistry registration regsvr32 CaoProvEWHA.dllDeregistration regsvr32 /u CaoProvEWHA.dll2.2.Method and property2.2.1.CaoWorkspace::AddController methodEWHA provider refers to the connection parameter for communication and connects the communication at the time of AddController method.Option specifies a communication form and a terminator setting at that time.AddController("< controller name >" // Controller name"CaoProv.KOGANEI.EWHA", // Provider name. Fixed."< machine name >" // Execution machine name of provider."< option >" // Option character string)Following is a list of option string items..Table 1 Option character string of CaoWorkspace::AddControllerOption MeaningConn =< connected parameter > Mandatory. Set the communication form and connectionparametersPlease refer to 2.2.1.1. for detailsTerm =< terminator > Specify the terminator when communicating.1:CR (default)2:LF3:CR+LFTimeOut =< Time-out time > Specify time-out time when communicating.(default: 500ms)2.2.1.1.Conn parameterFollowing is connection parameter strings for Parameter option. The object in the square bracket (“[ ]”) is omittable. The underlined part written in the explanation of each parameter shows the default value that the case of without specifying options.“com:<COM Port>[:<BaudRate>[:<Parity>:<DataBits>:<StopBits>]]"<COM Port> : COM port number. ‘1'-COM1,‘2'-COM2, …Communication speed.<BaudRate> :4800,9600,19200,38400,57600,115200.‘N'-NONE,‘E'-EVEN,‘O'-ODD<Parity> :Parity.<DataBits> : Number of data bits. ‘7'-7bit, ‘8'-8bit. <StopBits> : Number of stop bits. ‘1'-1bit, ‘2'-2bit.(example 1) “com:1" Communication port COM1 (, 38400bps, None,8bits, 2bit)(example 2) “com:2:9600" Communication port COM2 and 9600bps (, None,8bits, 2bit)(example 3) “com:3:38400:N:8:2" Communication port COM3, 38400bps, and None,8bits, and 2bit2.2.2.CaoController::AddVariable methodGenerate a variable object that acquisition/sets information of EWHA.Only the variable of Table2-3 and Table2-4 can be used for the variable name.2.2.3.CaoController::AddCommand methodGenerate CaoCommand that sends a command to EWHA.Following table shows the list of the command name.AddCommand("< command name >" // Command name"< option >" // Option character string)Table2-2Command name tableCommandnameCommand of EWHA Meaning Parameter Result ORG ORG Returntoorigin ‐‐MOVP MOVP Moves to the specified point VT_I4: Point number ‐MOVD MOVD Executes coordinate specifiedmovement VT_R4: Coordinates positionVT_I4: Speed‐MOVH MOVH Executes coordinate specifiedgripping operation VT_R4: Coordinates positionVT_I4: SpeedVT_I4: Power‐XP X+ +Movement by specified‐‐distance.XM X- - Movement by specified‐‐distance.XINC XINC + Movement at constant speed ‐‐XDEC XDEC - Movement at constant speed ‐‐SRVO SRVO Energizesmotor VT_I4:‐Energizing (1) /de-energizing (0)2.2.4.CaoController::Execute methodSends the character string specified for the parameter as it is. When the execution result is OK/READY, the character string that will be received before OK/READY comes is returned as a string array. When the execution result is NG/STOP, the character string received next to NG/STOP is returned as a string array.In this method, “RAW” is specified in the command name of the first argument, and specify the command of EWHA for the parameter of the second argument. At this time, please specify the parameter by the character string type.Execute("Raw" // Command name. Fixed."<parameter>" // Character string of EWHA command)2.2.5.CaoController::Cancel methodSend the cancellation command (^C)2.2.6.CaoController::get_CommandNames propertyAcquire the command name list. Please refer to Table2-2 for the acquired command name.2.2.7.CaoController::get_VariableNames propertyAcquire the variable name list. Please refer to Table2-5 for the acquired variable name.2.2.8.CaoCommand::Execute methodGenerate a command from the command name and the character string set in 2.2.9, and send.For instance, when the Execute method of command name “ORG" is executed, returns to origin.2.2.9.CaoCommand::put_Parameter propertySet the parameter at the time of command transmission.Please refer to Table2-2 for the parameter of each command. If there are more than one parameters, these parameter must be stored each element in the V ARIANT array, or, be specified in the comma-delimited character stringsAn illegal parameter is not checked in this property. The check on the parameter is judged by the execution result of the command.2.2.10.CaoCommand::get_Parameter propertyThe parameter set in 2.2.9 is acquired. When the parameter is not set, VT_EMPTY is returned.2.2.11.CaoCommand::get_Result propertyThe latest execution result of 2.2.8 is acquired. The acquired content returns the data division of the response from EWHA by the character string.2.2.12.CaoVariable::put_ID propertyThe point number is specified. This property is used when the variable name is only “P". Information on the specified point number can be acquired by setting this property.2.2.13.CaoVariable::get_ID propertyThe value set in 2.2.12 is acquired. When the parameter is not set, VT_EMPTY is restored.2.2.14.CaoVariable::put_Value propertyWrite system command of EHWA is executed.Please refer to Table2-5 for the variable name that can be used.The correspondence table of the command of the variable name and EWHA is shown as follows.Table2-3 The correspondence table of the variable name at put_Value and EWHA command nameVariablenameCommand of EWHA RemarksSRVO SRVO ‐PNO MOVPORG Execute Return to Origin by the ORG command when VT_EMPTY is specified.2.2.15.CaoVariable::get_Value propertyRead system command of EHWA is executed.Please refer to Table2-5 for the variable name that can be used.Table2-4Variable name at get_Value and correspondence table of EWHA command name VariableCommand of EWHA RemarksnameSRVO ?SRVO ‐POS ?POS ‐PNO ?PNO ‐P ?P Specify the acquired point number in the IDproperty.ORG ?ORG ‐VER ?VER ‐DIO ‐DIO READ2.3.Variable list2.3.1.Controller classTable2-5Controller class user variable listAttribute Variable name Data type Explanationget putSRVO VT_BSTR State of motor excitation - -POS VT_BSTRlocationacquisition -Current‐- -PNO VT_BSTR Get: Point numberPut: Point number movementP VT_BSTRinformation -Point‐ORG VT_BSTR State of Return of origin - ‐information -VersionVER VT_BSTR‐DIO VT_BSTR State of I/O- ‐2.4.Error codeIn the EWHA provider, there is no peculiar error code. About the ORiN2 commonness error, Please refer tothe chapter of the error code of "ORiN2 Programming guide".3.Sample programFollowing code shows the way of acquiring Return to origin state and execution of Return to origin of EWHA.Sample.frmDim eng As CaoEngineDim ctrl As CaoControllerDim val As CaoVariablePrivate Sub Form_Load()' generation of CAO engineSet eng = New CaoEngine' connection to EWHASet ctrl = eng.Workspaces(0).AddController("Sample", "CaoProv.KOGANEI.EWHA", "", "Conn=com:1")' generation of variable of Return to originSet val = ctrl.AddVariable("ORG","")End SubPrivate Sub Command1_Click()' setting of valueval = Text1.TextEnd SubPrivate Sub Command2_Click()' acquisition of valueText2.Text = valEnd Sub。

京东方软件企事业单位知识门户系统(EKPS)简介北京京东方软件有限公司2001-9-16目录一、概述 (3)1.1前言 (3)1.2企事业单位实务作业需求面 (4)1.2.1现今企事业单位运作之问题分析(作业面) (5)1.2.2现今企事业单位运作之问题分析(系统面) (7)1.2.3现今企事业单位运作之问题分析(管理面) (8)1.3知识入口服务整体解决方案 (10)1.3.1EKP系统导入成效(效益面) (13)1.3.2EKP系统整体架构(系统面) (14)1.3.3EKP系统应用之角色(角色面) (15)1.3.4EKP系统价值层面(价值面) (17)1.3.5 EKP与知识管理之关系(关连面) (18)二、项目目标 (22)三、功能描述 (23)1、门户管理工具 (23)2、智能化协同办公平台 (24)3、知识管理平台 (27)4、人力资源管理系统 (28)四、系统性能 (29)五、功能模块 (30)六、技术服务 (32)七、技术培训 (32)八、技术文件 (32)一、概述1.1前言随着企事业单位业务的不断增长,公司规模的不断扩大,对于无纸办公和协同作业的要求也越来越迫切。
企事业单位知识门户系统(EKPS)是一个复杂的项目,它涉及到所有部门,各部门相互之间的协调配合等问题,它的实施不仅仅是一种软件的应用,甚至会影响到整个企事业单位管理模式的变更。
其实施原则应当是:“总体规划,分布实施,效益驱动,重点突破。
”“总体规划、分步实施”就是根据企事业单位目前的工作环境、技能水平和应用等方面,从整体上分成若干阶段,在具体操作中有步骤、有目标、详细地制订执行计划、按照功能和模块化一步一步地推进实施,并且在跟踪考核,建立良性的反馈机制,逐渐完善全部功能。
1.2企事业单位实务作业需求面企事业单位面对日新月异的竞争的压力,如何利用本身在市场上的相对竞争优势,运用企事业单位获利之核心竞争力,迅速整合出新一代企事业单位团队的运作模式,将可有效确保企事业单位明日的生存利基。


Yammer企业社交平台的使用指南随着社交网络的发展,企业也逐渐将社交化的思维引入到自身运营中。
Yammer作为专注于企业社交的平台,为企业员工之间的交流、知识共享等活动提供了一个便捷、高效、安全的工具。
本篇文章将介绍Yammer的使用指南并分享如何提高在Yammer中的参与度和贡献度。
一、创建和管理Yammer团队在Yammer中,可以创建和加入不同的团队,每个团队都有独立的讨论区、通知设置和成员管理等功能。
因此,为了更好地利用Yammer,我们需要先了解如何创建和管理一个团队。
创建团队1.在Yammer主页右侧,点击创建团队2.填写团队的名称、描述以及选择隐私设置3.添加成员,可以选择从已有的团队中添加,或者输入邮件地址进行邀请管理团队1.在团队页中,点击设置按钮,可以对团队进行基本设置,如更改团队名称、描述、隐私设置等2.管理成员,可以添加、删除成员,以及设定不同的权限(管理员、普通成员等)3.设置通知,可以设定接收哪些通知、如何接收、频率等等二、如何使用Yammer了解了创建和管理团队的方法,接下来我们来了解如何使用Yammer进行交流和知识共享。
1.发布信息点击首页中的“发布”,可以发布文本、图片、链接、文件等内容,也可以针对特定团队或某些成员发布信息。
此外,还可以为信息设置标签,方便后期查找和分类,还可以评价和评论其他人的信息。
2.查看信息在Yammer的主页上,可以看到自己所在团队的动态,可以根据团队或标签进行过滤筛选。
同时还可以查看个人信息、个人通知等。
3.参与讨论在Yammer中,每个团队有专门的讨论区,可以针对特定话题进行交流。
可以在讨论区中提出问题、分享看法、交流经验,也可以在讨论区中设置投票或问卷等调查工具,以便获取更多的反馈和意见。
三、如何提高在Yammer中的参与度和贡献度明白了如何使用Yammer进行交流和知识共享之后,我们来了解如何提高自己在Yammer中的参与度和贡献度。

ad维护管理工具详解目录1. 内容概述 (3)2. AD维护管理的重要性 (4)2.1 用户账号管理 (5)2.2 组策略管理 (6)2.3 资源分配与管理 (8)3. AD维护管理工具的基础知识 (9)4. 常用AD维护管理工具详解 (10)4.1 组策略编辑器 (12)4.1.1 组策略的功能 (13)4.1.2 如何使用gpedit.msc (14)4.2 活动目录用户和计算机 (15)4.2.1 ADUC的界面和功能 (16)4.2.2 管理用户和计算机 (18)4.3 配置文件管理器 (20)4.3.1 应用部署和管理 (21)4.3.2 系统更新与补丁管理 (22)5. 如何选择适合的AD维护管理工具 (23)5.1 根据组织需求选择 (24)5.2 考虑的性能和易用性 (26)5.3 成本因素 (27)6. 最佳实践与常见问题 (28)6.1 最佳维护管理实践 (30)6.2 确保AD的安全性 (31)6.3 常见问题与解决方法 (31)7. 案例研究 (32)7.1 组织A的AD维护管理案例 (33)7.2 组织B的AD问题解决之旅 (34)7.3 如何通过AD维护管理提高效率 (36)8. 技术支持与社区资源 (37)8.1 获取技术支持 (38)8.2 与社区互动 (39)8.3 获取帮助文档和在线论坛 (40)9. 安全与合规性 (41)9.1 AD维护管理的合规要求 (43)9.2 数据保护与隐私 (44)9.3 应对潜在的安全风险 (46)10. 未来趋势 (47)10.1 自动化的作用 (48)10.2 云端的AD管理 (50)10.3 企业和技术的进一步整合 (52)1. 内容概述《AD维护管理工具详解》是一本全面介绍AD维护管理工具的专业书籍,旨在帮助读者深入了解并掌握这些工具在实际工作中的应用。
本书从多个维度详细阐述了AD维护管理工具的核心理念、功能特点、操作流程及最佳实践。

益和VA虚拟应用管理平台产品白皮书2012ver 5.3版权声明本文中出现的任何文字叙述、文档格式、插图、照片、方法、过程等内容,除另有特别注明外,版权均属陕西益和信息技术开发有限责任公司所有,受到有关产权及版权法保护,未经益和公司许可,任何单位或个人不得以任何方式非法使用。
目录前言 (1)产品适用范围 (2)信息处理平台 (2)☆VA商业版 (2)☆EAA应用接入版 (2)☆VA企业版 (2)应用场景 (2)☆信息中心 (2)☆远程接入 (3)☆移动办公 (3)☆信息共享 (3)☆应用加速 (3)☆瘦客户端 (4)☆分时授权 (4)☆其它特殊需求 (4)应用价值 (6)☆信息中心的多功能平台 (6)☆实现远程/移动办公 (6)☆集中统一的用户和应用管理 (6)☆加快应用处理速度 (6)☆信息与文件共享 (6)☆扩大授权软件适用范围 (6)☆降低IT总成本 (6)☆增强保密和安全保障 (6)☆IT系统稳定和高可用性 (7)技术特点 (8)☆虚拟应用通讯协议 (8)☆高可用服务器集群技术 (8)☆高可靠网络安全管理 (8)☆高兼容性数据结构 (8)☆高性能域名解析 (8)☆完整自动登录引擎 (8)☆免驱动智能虚拟打印 (8)☆高安全登录认证 (9)☆广泛兼容客户端操作系统 (9)☆高开放性接口 (9)稳定性保障 (10)☆产品数字证书 (10)☆服务器负载均衡 (10)☆设置应用兼容性 (10)☆动态域名容错 (10)☆程序自动防御 (10)☆服务集群状态监控 (11)☆自动报警和异常处理 (11)☆系统维护辅助工具 (11)安全保密措施及管理 (12)☆数据通讯和服务器资源安全 (12)☆访问控制和接入安全 (12)☆其他安全技术 (12)附录1:产品版本比较 (14)附录2:解决方案参考 (15)☆一般应用 (15)☆局域网应用 (16)☆集中应用 (17)☆文档集中管理 (18)☆单点登陆 (19)☆安全上网 (20)前言尊敬的客户您好!感谢您关注陕西益和信息技术开发有限责任公司的产品。
Scholastic Oracle Cloud Supplier Portal User GuideTable of ContentsIntroduction to the Supplier Portal (3)What is the Supplier Portal? (3)Navigating the Supplier portal (3)Logging in (3)Homepage Navigation (4)Notifications (5)Overview Menu (6)Summary Tab (6)Orders Tab (7)Schedules (8)Negotiations Tab (9)Request for Quote (RFQ) (10)Receiving an Invite for a Negotiation (10)Viewing the RFQ (10)Creating a Response (12)Award Decision (18)Purchase Orders (PO) (20)PO Notification (20)Review PO Details (21)Acknowledge a PO (22)Enter/Revise a Promised Ship Date for a Schedule (24)Manage Schedules (26)Order Life Cycle (27)Invoices (29)Create and Submit an Invoice (29)Miscellaneous Charges (33)Create Invoice without PO (34)View Invoices (36)View Payments (37)Supplier Preferences (39)Introduction to the Supplier PortalWhat is the Supplier Portal?The Scholastic Supplier Portal is a secure, web-based workspace that provides our vendors with full visibility to Scholastic transactions, including request for quotations (RFQ), purchase orders, and invoices.The Supplier Portal plays a key role in Scholastic’s Or acle ERP transformation, as this tool helps improve communication with our suppliers by automating and streamlining the source-to settleprocess.Navigating the Supplier portalLogging inOnce your password has been set, click on the “Oracle Fusion Prod” icon to reach the Supplier Portal home page.Once your password has been set, log in on the home pageHomepage NavigationOn the home page, click on the Supplier Portal icon to open the “Overview” page.NotificationsAt the top right corner of the home page, a bell icon will display your pending notifications. This includes new purchase orders pending acknowledgement as well as invitations to a negotiation.Note: Clicking on the notification brings you to the PO or Negotiation in questionOverview MenuThe overview page provides a snapshot into Scholastic’s most recent transact ions as well as anything requiring attention.Summary TabWorklist: A list of all pending notifications sent to the current supplier user. These are the same notifications found in the bell at the top of the page. Please note that most notifications willalso be sent via email.Watch list: Contains a set of saved searches which display counts of urgent or recenttransactions, possibly requiring action, such as Orders Pending Acknowledgment. Clicking awatch list entry navigates direct to the screen so that user can begin working on the transactions immediately.Contains the header detail of our purchase orders. The header contains the PO issued date andthe total $ amount ordered. The item level detail, quantity, and ship-to locations can be foundin “Schedules”.Orders with Recent Activity: A list of orders that have been Opened, Changed, or Canceledwithin the last week. This date can be manually changed to display more or less orders. Indicates an orderhas been cancelledA purchase order “Schedule” contains the quantity, ship-to location, and promised ship date.An order with a ship date in the past is highlighted with an alert. Schedules must be kept up todate. The promised ship dates that you provide are visible for everyone at Scholastic.At the bottom, “Recent Receipts” will list all purchase order schedules received within the lastweek.Indicates a promisedship date is past dueNegotiations TabRequest for Quotation (RFQ) transactions that the supplier is involved in or is invited to by Scholastic. It provides a quick summary to easily monitor the status and responses.Request for Quote (RFQ)Receiving an Invite for a NegotiationThe Scholastic Sourcing group has the ability to invite vendors to bid on projects through theSupplier Portal. If your organization is invited to a negotiation, you will receive an email as well as a notification in the Supplier Portal.The email invitation will include a PDF overview of the project. There is also a link that will take you directly to the RFQ in the Supplier Portal.Viewing the RFQYou can view the RFQ by clicking on the link the email notification. Another option is to go to the Supplier Portal and navigate to the Negotiations tab. Click on the negotiation number inquestion.This will bring up the RFQ cover page with the time remaining to respond displayed. On the left hand side of the RFQ, you will see links to the different components of the RFQ.Click on the Overview link. This will bring up the Overview page, which has key dates tied to the RFQ. On the right hand side, you will find attachments to the RFQ. The attachment will have the requirements for the RFQ along with instructions, quantities, and any other relevant information.Click on the Lines link. This will bring up the line items tied to the RFQ. In some cases, due to complex requirements, there will be one placeholder line visible with the advanced requirements included in an attachment.Creating a ResponseWhen you decide to bid on an RFQ, you must first acknowledge that you will participate. You can do this from the Negotiations dashboard by scrolling to the “Open Invitations” section. Highlight the negotiation, and click on the Acknowledge Participation button.This will bring up the Acknowledge Participation popup. You can select Yes or No, and enter a comment to the Scholastic buyer.At this point, if you refresh the Negotiations dashboard, you will see YES listed in the ‘Will Participate’ column. You can create your response by highlighting the Negotiation and clicking on the Create Response button.Another way to create a response is to open the RFQ and click on the Create Response button on the upper right hand sideThis will bring up the response page. Enter the quote expiration date, an internal quote number if you have one, and any notes to the buyer. You can also attach any correspondence by clicking on the + sign next to Attachments.You can attach more than one file by clicking on the + sign.Once you attach a file, it will show up on the main screen. You can remove the attachment by clicking on the X next to the file name. Hit Save and then Next.This will bring you to the “Lines” screen. Enter unit costs for the lines along with a Promised Ship Date.For most negotiations, the Scholastic buyer will give the supplier an option to create your own line by clicking on the + sign under Create Alternate. This is especially useful if you want to incorporate a unique idea or proposal.On the Alternate Line screen, you are required to enter a description, response price, and response quantity. You can enter a note to the buyer and also attach files to the alternate line.After hitting Save and Close, the alternate line will be added to the RFQ response.Hit Save and Next. This will bring you to the Review screen, where you can view the response as a whole. There are tabs for the Overview and Lines. When you are ready to submit the response to Scholastic, hit Submit.You will receive confirmation that the response was submitted.Award DecisionAfter the Scholastic buyer receives all bids, they will award either the whole job, or part of the job.If you are selected, you will receive an email notification as well as an Oracle notification confirming which lines of the negation were awarded to you. If you are not selected, it’s up to the Scholastic buyer if they want to inform the suppliers systematically that were not selected. You would receive a similar alert, but t he awarded lines amount will be “0”.Clicking on the notification will bring up the award decision. In the screenshot below, one line was awarded.Here is a screenshot of an award decision where nothing was awarded:Another way to view the outcome of the RFQ is to go to the Negotiations home screen. Scroll down to Completed Negotiations. The little green circle with a check mark indicates that the bid was awarded, while the note “No award” in the amount signifies that your bid was not accepted.Purchase Orders (PO)PO NotificationWhen a Scholastic purchase order is issued, you will receive an email notification with a PDFattachmentIf an acknowledgment is required, the email subject will include “Requires Acknowledgment”. A notification alert will also be displayed at the top of Supplier Portal to note an action is required.When a “R evised” PO is received, the email subject will include the “Revision #”Review PO DetailsOpen the attachment in the email to view a PDF of the purchase order. Additionally, on the “Orders” overview tab in the Supplier Portal, all recent PO’s will be listed under “Opened”. You will have the option of viewing a PDF, opening the order for acknowledgment, as well as updating the order with a confirmed promised ship date.Acknowledge a POSome Scholastic POs will require a supplier acknowledgment within the Portal. The PO will not be considered “open” until the Supplier completes the acknowledgment process. If a PO requires acknowl edgment, the email subject will note “Requires Acknowledgement”. You can acknowledge the PO from the link in the email or log into the supplier portal and click on the “Pending Acknowledgment” link in the Watch list.Note: A notification alert will pop-up as well as a task in the “Work list”. While both of these serve as links to the PO, it is suggested to acknowledge an order by using the link in the “Watch List”, as this method is most efficient.A “Manage Orders” screen will be displayed with all orders pending acknowledgement. Click on an order #.The PO header and details will be displayed. At the top right of the screen, select the “Acknowledge PO” button.You may need to acknowledge both the order (under “Terms”) and each Schedule line. You are given the option to “Accept” or “Reject”. Please only “Accept” the PO using this process. If there is something wrong with the order, please reach out to your Scholastic buyer via email or phone.In the top right hand corner, hit “Submit”Then hit “OK” and “Done” to close out of the order.The acknowledgment has been sent back to Scholastic and the order status is now “Open”.Enter/Revise a Promised Ship Date for a ScheduleOn every order, we send a “Requested Ship Date”. We expect that every supplier will respond with a “Promised Ship Date” confirming when you can ship. These dates are loaded into the Scholastic system for reporting purposes, so it’s i mportant that they are populated for every order and kept up to date.From the “Orders” or “Schedules” tab, select an order to edit:This brings you to the PO screen. The top part contains the PO header information with your supplier information. The “Lines” and Schedules” tabs at the bottom contain the PO detail.In the previous screenshot, the requested ship date is 4/26/18. However, the promised ship date is blank. In order to enter a new promised ship date or revise an existing promised ship date, click the “Actions” button on the top right of the screen and select “Edit”.A warning message pops up to confirm that any action will create a change order. Click “Yes”.In the “Schedules” tab, enter a new promised ship date and a change reason if applicable.Enter a description of the change order you made at the top o f the PO and then hit “Submit”.Note: Hitting “Save” will save your work, but will not send the updated date back to Scholastic. You must select “Submit”.After hitting “submit”, a popup message confirms that your changes have been sent to Scholastic. We will reach out to you with any questions.Manage SchedulesTo search and view all orders and schedules, select the task button while in the Overview screen in the supplier portalIt opens up a tab on the right side with a number of options. Under “Orders”, select “Manage Schedules”.The Manage Orders screen allows you to search all PO Schedules, open or closed. The default search is “All”, but you can search using a number of parameters, as well as setup custom searches. You can also easily tell which schedules don’t have a “Promised Ship Date” by sorting the field. In fact, all of the fields are sortable.Order Life CycleWhen you select a PO to view or edit, the “Order Life Cycle” graph can be found on the top right of the screen. It is a graphical view of the dollar amount ordered, received, delivered, and invoiced. Select “View Details” for additional information.The Order Life Cycle now displays a complete order summary including in-transit shipment information (pulled in from our OTM module), receipt dates, and invoice status.InvoicesCreate and Submit an InvoiceThe Scholastic Supplier Portal allows you to submit invoices directly to Scholastic. Processing your invoices through the supplier portal will increase the speed that your payment isprocessed. In the task list, select “Create Invoice”.In the “Create Invoice” section, s elect an order from the “Identifying PO” drop down list. This will populate most of the fields. Then enter y our internal “Invoice Number” and today’s date.In the “Items” section, hit the “Select and add” button to choose the PO lines you’d like to add to the invoice.Select the line(s) and hit “Apply”.Then hit “OK”. The item(s) has been added to the invoice.In the quantity field, enter the shipped quantity.Note: This version of Oracle Cloud does not allow overage to be invoiced. Theinvoiced quantity cannot exceed the order quantity. We are working with Oracle to correct this in a future release. For now, please work with the buyer to revise the PO when the shipped quantity exceeds the ordered amount, or add the overage amount as a miscellaneous cost under “Shipping and Handling” at the bottom of the invoice.In the Location of Final Discharge, enter the tax Province to capture the correct tax code.Once all the line items have been added to the Invoice, click on the Calculate Tax Button. Your taxes should now be calculated on the Invoice.Note: if you calculate tax after only one line item is picked, it will not work on anysubsequent line items.Miscellaneous ChargesHit the “Add” button under “Shipping and Handling” and select “Miscellaneous”. Enter an amount and descriptionNote: Freight is not a viable option as all of our shipments should route through the Scholastic Logistics group via the OTM system.Hit “Submit” to send the invoice to ScholasticA pop-up message will confirm that the invoice has been submittedCreate Invoice without POFor services completed where a Scholastic PO wasn’t issued, please submit an invoice using the “Create Invoice without PO”.On the invoice header, enter your invoice number, today’s date, and attach any pertinent documents. You must also enter the email address of the buyer at Scholastic who will receive and approve the invoice.Must be TODAYS DATEFor the invoice details, hit the + icon to add a line. Select a ship to and Location of Final Discharge, enter an amount and a description of the services provided.To add taxes, hit the “Calculate Tax” button.Note: Location of Final Discharge much be populated in order to calculate taxes on the invoice.Add miscellaneous charges at the bottom under “Shipping and Handling”.Hit “Submit” at the top of the screen and you’ll receive a confirmation message that your invoice has been submitted.To search for all submitted invoices, o n the Task Menu, select “View Invoices”Select your “Supplier” name, and hit search. You can use the fields to narrow your search as well as create custom searches. You can see the Invoice Status, as well as a Payment Number to confirm that a payment has been made against your invoice. Please note that all of these columns can be sorted.To search for invoice payment status, on the Task Menu, select “View Payments”Select your “Supplier” name, and hit search. You can use the fields to narrow your search as well as create custom searches. You can also see the payment status to confirm that a payment has been made. Select a “Payment Number” to see the complete detai ls of the payment.Complete payment detail will be displayedSupplier PreferencesOn the home page, select “Set Preferences”Select “Regional” in the General Preferences list to review the option to update your date and time format, preferred number format, primary currency, and time zone.Select “Save and Close” when finished.Select “Language” to change the primary language of the website. The default is “American English”。
银河学堂企业微信服务平台答案
银河学堂企业微信服务平台,是一款新型的即时通讯服务,满足了企业用户快捷、安全、便捷的在线交流需求,并且更加贴心地提供数字化、智能化、全球化的企业服务平台,提供更加方便快捷的智慧作业环境,运用现代化的技术手段来实现信息交流,助力企业发展。
银河学堂企业微信服务平台的基础应用,主要包括文本消息、语音消息、视频消息、图片消息甚至可以直接进行文件传输,并且还可以实现消息群发和定向推送等功能,极大地方便了企业之间的信息交流与合作。
银河学堂企业微信服务平台的另一个重要特点就是智能查询和管理功能,无论是查询或是管理上市登记信息,只需要用户输入一组指定的关键字,就可以实现快速检索,并且利用快速检索的结果进行深度的解释及管理,智能查询系统也可以根据企业的需要自定义搜索关键词,使查询更加精准高效,这样不仅节约了企业的大量时间,也简化了界面操作。
银河学堂企业微信服务平台在企业用户交流、查询和管理方面都有优越性,让传统的企业通讯比如短信发送从此可以见长的告别,这款智能化的企业微信服务平台为企业用户提供更加便捷的信息采集、分析、发送与传播,给企业准确、可靠的通讯体系,促进实时、高效、安全的通讯与管理解决方案。
Web-based information service adoption:A comparison of the motivational model and the uses and grati fications theoryMargaret Meiling Luo a ,⁎,Sophea Chea b ,Ja-Shen Chen aa College of Management,Yuan Ze University,Taiwan,ROCbDepartment of Management Information Systems,Temple University,United Statesa b s t r a c ta r t i c l e i n f o Article history:Received 21April 2009Received in revised form 7August 2010Accepted 17November 2010Available online 26November 2010Keywords:Technology adoption Information servicesUses and grati fications theory Partial least squaresThis study compares two user acceptance theories:the motivational model (MM),and the uses and grati fications (U&G)theory.While MM arises from the field of information systems and the U&G theory was developed in the field of communication,both are focused on explaining user acceptance of information technologies using intrinsic and extrinsic motivations.We discuss the theoretical roots of the two theories,and use partial least squares (PLS)analysis to test each in an empirical setting.A comprehensive comparison of the results is also presented,including a discussion about the relative strengths and weaknesses of each model under both theoretical/research and practical contexts.©2010Elsevier B.V.All rights reserved.1.IntroductionAdvances in the Internet have enabled some businesses to transform their products into information services that can be personalized and shipped to customers without the usual logistics costs and delays.With Web technologies,there is tremendous opportunity for businesses to create value by providing customers with additional services,or transforming from a product-based to a service-based company.In pursuing digital channels to sell and distribute products,the major challenge these businesses face is evoking user acceptance of the information service once the digital channels are in place.Information services provide clients the capability to generate,acquire,store,transform,process,retrieve,utilize,and/or make available information via telecommunications [46].Today,Web-based information services (WIS)are growing rapidly,and range from entertainment services (e.g.,video-on-demand service,online computer games and gambling)to business-to-consumer (B2C)services,such as online banking [21].These WIS empower users by enabling them to personalize services,compare and select products,and communicate instantly with others.Recent research on the adoption of WIS has taken a motivational perspective,positing that both hedonic and utilitarian needs drive an individual's information technology (IT)adoption decision.Twomotivation theories,the motivational model (MM)[17]and the uses and grati fications (U&G)theory [32],are increasingly being used to investigate the adoption of WIS (e.g.,[20,35,44,57]).The studies that have employed these two theories have helped advance our understanding of the reasons that people adopt WIS.MM and U&G are derived from similar theoretical roots [19,39].Both assume that hedonic and utilitarian needs motivate an in-dividual's adoption of information technology.Yet,recent research findings have not been discussed from a cross-disciplinary perspec-tive,and a comprehensive comparison of these two theories has not been made.A comparison and examination of the boundary conditions of the two theories will provide important information to researchers and practitioners about which theory best explains and predicts the adoption of WIS.We reviewed the literature on the two theories to provide the necessary background information for comparing the models and examining the boundary conditions and methods typically used to test these models.In addition,we tested and compared the theories under an empirical setting of information service acceptance in a non-workplace environment.A partial least squares (PLS)analysis was performed on the results to examine the psychometric properties of scale.2.Theoretical background 2.1.Motivational modelIn the motivational model [17],motivations related to intrinsic personal goals are contrasted with those related to extrinsic goalsDecision Support Systems 51(2011)21–30⁎Corresponding author.135Yuan-Tung Road,Chungli,Taoyuan,Taiwan,ROC.Tel.:+88634638800x2632;fax:+88634630377.E-mail addresses:luo@.tw (M.M.Luo),sophea@ (S.Chea),jchen@.tw (J.-S.Chen).0167-9236/$–see front matter ©2010Elsevier B.V.All rights reserved.doi:10.1016/j.dss.2010.11.015Contents lists available at ScienceDirectDecision Support Systemsj o ur n a l h o m e p a ge :ww w.e l s e v i e r.c o m/l o c a t e /d s sassociated with job advancement issues.Davis et al.[17]associated perceived usefulness with performance as a consequence of use(i.e., as an extrinsic motivation).Intrinsic motivation,in contrast,is con-cerned with the reinforcement and enjoyment of the process of performing a behavior.System use,therefore,is determined not only by extrinsic motives(i.e.,perceived usefulness)but also intrinsic motives(i.e.,perceived enjoyment).Several studies have confirmed that both intrinsic and extrinsic motives are significant predictors of behavioral usage[1,3,37,44,55,56,63–65].The conceptual model of MM is shown in Fig.1.es and gratifications theoryThe uses and gratifications theory is a media use paradigm that inquires into the reasons why people use certain media and the gratifications derived from usage and access.It posits that media consumption is purposive,and that users actively seek to fulfill their needs via a variety of uses[32].U&G has been considered a useful approach for understanding users'motivations in the context of traditional media,such as TV and radio[8,43,53].Its application to interactive media,such as the Internet,is promising[38,54].A large body of literature suggests that motivations predict media usage and that media usage influences gratifications/satisfaction[7,22,35,36,49–51,53].The motivations identified in U&G studies are more diverse than those in MM studies.As can be seen in Table1,intrinsic motivations(engaging in an activity out of pleasure and satisfaction) and extrinsic motivations(engaging in an activity to obtain something outside the activity[62,p.273])of media/IT usage include the need to search for information,to interact socially,and for escapism.In particular,recent studies have reported the following motivations of using the Internet:convenience,information seeking,interpersonal utility,to pass time,entertainment,escapism,peer identity,and social interaction[11,33,50].Thesefindings suggest that using a media perspective to investigate the WIS use may potentially broaden theview of IS researchers who commonly take an information system perspective to examine Web adoption because today a WIS has characteristics and features of not only an information system but also a medium.Recent U&G studies on the Internet have identified a set of common underlying dimensions of Internet usage motivations that reflect the inherent interactivity and user-directed nature of Internet media.Thesefindings also suggested that the U&G approach provides the theoretical framework for understanding what specifically drives user adoption of the Internet.Hence,the U&G approach is particularly well suited for examining Internet use in a customer context.Among the U&G studies,Kaye[33]used motivation items of TV and identified six factors:entertainment,to pass time,escapism,social interaction, information seeking,and Web site preference.Ferguson and Perse [22]suggested that people use the Internet for entertainment,to pass time,relaxation,and social information.Papacharissi and Rubin[50] developed a scale of Internet usage motivation consisting offive motives:entertainment,to pass time,interpersonal utility,informa-tion seeking,and convenience;these draw from interpersonal,media, and new technology motives,supporting informative and interactive capabilities of the Internet.The most salient use of the Internet was information seeking,which reflected an instrumental orientation of media use(Fig.2).The Internet possesses unique characteristics,including machine interactivity,telepresence,hypermedia,and network navigation,that distinguish it from tradition media and some other interactive multimedia[45]these characteristics gratify entertainment and information needs[54,58].Because of these unique characteristics, researchers have stressed the need to develop a rigorous researchFig.1.The motivational model.Table1Intrinsic and extrinsic motivations of technology use.Authors Medium Intrinsic ExtrinsicBerelson[5]Newspaper Source of security Searching forinformationCeremonialRitualisticTool for everyday living Social contact forconversationalpurposeEscapeSocial prestigeRubin[53]TV Pass time/Habit InformationEntertainment CompanionshipEscapeKaye[33]WWW Entertainment Social interactionPass time InformationEscape Web site preference Papacharissi andRubin[50]Internet Entertainment Information seekingPass time ConvenienceInterpersonal utilityFerguson andPerse[22]TV-relatedweb surfingmotivationsEntertainment Social informationPass timeRelaxationStafford andStafford[57]Commercial Entertainment Search factorWeb sites Cognitive factorNews and uniquefactorsCharney andGreenberg[11]Internet Division entertainment Keep informedPeer identity CommunicationGood feelings Sights and soundsCoolness CareerKo,Cho,andRoberts[35]MarketingwebsiteEntertainment InformationSocial interaction ConvenienceDiddi andLaRose[20]Internet news Escapism SurveillanceEntertainmentHabitNews quizzesPass timeFig.2.The uses and gratifications of internet usage.22M.M.Luo et al./Decision Support Systems51(2011)21–30framework for both theory and practice[25].A comparison of the two theories(two lines of investigation)would show to what degree IT and its intrinsic qualities correlate with the pursuit of certain gratifications that lead to the acceptance of IT.Among the media/IT acceptance theories(e.g.,diffusion of innovation[52],technology acceptance model[15],and theory of planned behavior[2]),U&G is distinct in its applicability to media of all kinds[38].The U&G paradigm's comprehensive nature enables us to understand electronic communication in a media environment where computers have not only home and business applications but also work and play functions [58].In contrast,IT acceptance models such as MM and the technology acceptance model(TAM)regard information systems like the Internet as tools of improving user performance at work.Applying MM to the Internet is therefore limited in scope.Therefore,while it could be argued that U&G brings a new perspective to understanding the adoption decision in a customer context,such an argument should be made only with supporting evidence from a fair comparison of the two models.In the following section,we compare the two models and discuss how the comparison contributes to our understanding of the nature of the two theories.parison of MM and U&GA comprehensive comparison of MM and U&G has not yet been conducted,but such a comparison is plausible and valuable for the following reasons.First,both theories posit that intrinsic and extrinsic motivations drive an individual's behavior.MM associates these motivations with the use of IT,while U&G similarly links them to media usage behaviors.This similarity provides a baseline for comparing the models,since they use the same approach,namely an information-process approach[23,48],to explain IT usage.Secondly,the two theories propose distinct constructs to explain the use of IT.For example,the intrinsic motivation“to pass time”is unique to U&G studies and not discussed in MM ing media/ IT may sometimes be habitual[33,53].This is a whole new perspective to MM because the model neglects hedonic factors of system use where a ritual pattern of usage is plausible.Another example is entertainment,which is an intrinsic motivation in U&G that explains the substantial variability in Internet usage[50].The entertainment motive is somewhat different from the perceived enjoyment motive in MM,but they are both intrinsic motivations associated with fun and playfulness inherent to the adoption decision process.According to its conceptual definition,the entertainment motive drives media use when customers get pleasure from consuming media content and the process of that consumption[53].Perceived enjoyment,by definition, is pleasure from experiencing the process,but not the specific use of the media/IT application content.Several studies have suggested that this motive has a significant impact on behavior intention to use personal computers and the Web[17,30,31,63].Note that these findings of MM concern the application,but not the content of the application.Given that the entertainment motive of U&G and the perceived enjoyment motive of MM share a similar attribute,an empirical comparison of these intrinsic factors of IT usage will enhance our understanding of Web-based services adoption.Thirdly,both theories have been tested extensively under various empirical settings,and their scales have been shown to be reliable and valid.Given the maturity of this research domain and rigor associated with the methodological details of the two theories,the results of each model are comparable.While there are some inherent boundary conditions imposed by the empirical setting that we used,the comparison should be meaningful.The conceptual definitions of the main constructs of each theory are listed in Appendix A.The models were compared using the three criteria used by Mathieson[40].First,we examined how well the two models predict behavioral usage of an information service.If the factors of each model largely account for the observed variance,we can argue that these factors provide an accurate picture of the issues that system developers should consider to increase system paring the models'respective levels of variance as explained also provides evidence on which model is superior.Secondly,we compared the value of the information provided by the models.Under the assumption that the comparison should not be biased to favor one model or the other,we examined the empirical evidence on which factors better predict behavioral usage.This identifies which factors are most important to users when adopting the WIS.Thirdly,it is important that a model provides valuable information at low cost and ideally a minimum of effort.To ensure a fair comparison,we examined both procedure and distributional equivalence[14].Procedure equivalence was assessed under two conditions.First,the boundary conditions of both theories were observed.When performing a procedure equivalent test,it is important to obtain equally careful measures of each theory's constructs and equivalentfidelity to the boundary conditions of each theory.Secondly,equal attention was given to measurement. Distributional equivalence aims to ensure that the factors or variables vary over equivalent ranges of values in their respective populations ([14]).However,establishing distributional equivalence directly is difficult because knowledge of population variance is required.When population variances are unknown,establishing distributional equiv-alence is not certain.An alternative is to examine the standard deviations of variables that are not common to both models,which helps identify obvious cases of range restriction[40].An important aspect of this study is that we tested both models in the same context,using subjects sampled from the same population. All subjects faced the same adoption decision about the same information service.This allowed us to observe the differences between the models that are likely due to the models themselves, rather than differences in the contexts under investigation.To test and compare the two theories under an empirical setting of Web service acceptance in the non-workplace environment,we conducted a lab experiment to collect data and used PLS analysis to examine the extent to which the modelsfit the data.In the following sections,we present the methods,measures,and results of that experiment,and discuss the limitations of this study and the implica-tions of ourfindings.3.Method3.1.Data collection procedureThe lab experiment was conducted in Spring,2006,and involved a questionnaire to collect the data.The empirical setting was a WIS, namely,online newspapers,whose primary offering is news content. Prior to the experiment,we conducted two pilot studies to develop pertinent scales.The studies were performed at a major U.S. university.More details of these pilot studies are presented in the next subsection.The participants in the lab experiment were business school undergraduate students enrolled in two sections of statistic classes at a major U.S.university.Extra credit was granted for participation,and participants were allowed to decline to participate or withdraw from the study at any time.Participants were randomly assigned to networked computers to systematically prevent cross-talking.After afive-minute introduction,73participantsfilled out an online questionnaire,which included all of the measures of MM and U&G.All73responses were valid.Two weeks later,the same group of participants completed a follow-up paper-based questionnaire with only measures of behavioral usage.A total of63responses were deemed usable for data analysis.Thefirst survey focused on collecting data on motivation and behavioral intention variables while the second survey on reported usage data.The practice of deploying a two-stage survey is a widely accepted in technology acceptance research[15,59].Because both models need the usage data to run the23M.M.Luo et al./Decision Support Systems51(2011)21–30full model,only the63responses that were deemed usable were included in the analysis.The63participants who completed the questionnaire were comprised of32(50.8%)males and31(49.2%)females between19 and35years of age.The majority(81.5%)was between18and 23years of age,and98%were in their junior and senior years of college.Note that ourfindings might only be applicable to the information service population thatfits these characteristics.3.2.MeasuresMM includes perceived enjoyment and measures used in TAM.The measures of intention to use,perceived ease of use,perceived use-fulness,and behavioral usage were adopted from Davis[15].Items of perceived ease of use and perceived usefulness were measured using a seven-point Likert-type scale(1=Likely,7=Unlikely).Perceived enjoyment was measured by four semantic differential scales (ranging from one to seven)taken from[10]and[30]and re-adapted by van der Heijden[63].Attitude,adapted from Wixom and Todd[67], was measured by three items using semantic differential scales, ranging from one to seven.The predictors in the U&G model(i.e.,extrinsic and intrinsic motivations)were measured using the scales developed by Papachar-issi and Rubin[50].The reason to adopt these items is twofold.First, their validity is well-established in previous research.Second,these items are derived from previous researchfindings on interpersonal communication,mediated communication,and new technology motives,which reflect the motives of using the Internet that is similar to our research context.Furthermore,they are the most current Internet motive scales.Four items elicited by open-ended questions in thefirst pilot study,which involved23business school students in a junior-level IT course,were included.These items reflect the motives of using news WIS.We expect these items to complement Papacharissi and Rubin's Internet motive items.All motive items were measured on afive-point Likert-type scale.The second pilot study tested behavioral usage and behavioral intention items of30college students enrolled in an undergraduate junior-level IT course.A total of 29responses were collected.The pilot study tested the measures in a customer context,and the results suggested that these items were adoptable.4.ResultsA partial least squares(PLS)analysis using PLS Graph(Version3.0) was conducted to examine the reliability and validity of the mea-sures.The loading pattern of all items was highly consistent,with most loadings above0.70[61]on their intended constructs with relatively small cross loadings and significant t-values at p b0.001. However,there were two exceptions.One item in attitude towards usage loaded poorly at−0.434and was subsequently dropped from the model(Tables2and3).Another item for pass time loaded at0.502 but was kept in the model because its cross loadings on other constructs were relatively small.Note that the attitude measures loaded very high on their intended constructs(0.977and0.977), suggesting that these items were a good measure of attitude.How-ever,these items loaded relatively high(0.671and0.693)on per-ceived enjoyment.A possible explanation is that attitude consists of both affective and cognitive structures[6,29,47,68]and perceived enjoyment reflects a person's affective evaluation of system use. Therefore,the two constructs have some commonality,and conse-quently high loadings and inter-correlation(see Table4)can be expected.The major distinction between these two constructs is that the former represents the evaluation of emotion(i.e.,[2,47])while the latter the information an individual has about an object[48]. Therefore,they are still different conceptually but some similarities can be anticipated.4.1.Scale validity and instrument reliabilityWe employed the bootstrapping method(200sub-samples)to test the validity of the constructs and the level of significance of the regression path coefficients.The internal composite reliability,squareTable2Item loadings(MM).Latent constructs Item Latent constructsPEU PU PE ATT BI BUPerceived ease of use(PEU)PEU010.811⁎⁎⁎0.4530.1920.2810.1530.198PEU020.901⁎⁎⁎0.4110.2050.3280.1680.229PEU030.869⁎⁎⁎0.5050.1510.2770.1500.268PEU040.916⁎⁎⁎0.5030.1760.2900.2120.225PEU050.901⁎⁎⁎0.4930.1930.3840.2540.204PEU060.926⁎⁎⁎0.5770.2830.3960.2010.231 Perceived usefulness(PU)PU010.5510.845⁎⁎⁎0.3340.4820.3370.429PU020.4590.920⁎⁎⁎0.3100.4720.2570.384PU030.5280.905⁎⁎⁎0.2160.3320.1980.248PU040.5510.929⁎⁎⁎0.3680.5020.3260.391PU050.4470.845⁎⁎⁎0.3330.3640.2100.209PU060.3710.833⁎⁎⁎0.3110.4300.3360.240 Perceived enjoyment(PE)PE010.2510.3010.947⁎⁎⁎0.6810.5780.418PE020.0920.2970.904⁎⁎⁎0.6430.4860.359PE030.1980.3290.940⁎⁎⁎0.6750.5860.469PE040.2940.3780.838⁎⁎⁎0.5210.6110.610 Attitude towards use(ATT)ATT010.3390.5230.6710.977⁎⁎⁎0.4440.478ATT020.3860.4410.6930.977⁎⁎⁎0.4180.349 Behavioral intention(BI)BI010.1120.2410.5610.2780.894⁎⁎⁎0.356BI020.2170.3300.6320.4320.973⁎⁎⁎0.462BI030.1900.2860.6520.4300.941⁎⁎⁎0.382BI040.2650.3140.3870.5120.793⁎⁎⁎0.311BI050.1570.2350.5630.2730.898⁎⁎⁎0.346 Behavioral usage(BU)BU010.2740.4460.5050.4980.4250.877⁎⁎⁎BU020.0760.1050.3160.1970.2990.800⁎⁎⁎BU030.2820.2640.2990.1630.1210.600⁎⁎⁎Note:N=63.Item loadings higher than0.5are in bold.⁎:p b0.05,⁎⁎:p b0.01,⁎⁎⁎:p b0.001.24M.M.Luo et al./Decision Support Systems51(2011)21–30roots of average variance extracted(AVE),and the inter-construct correlations were all at acceptable levels(Tables4and5).In PLS, convergent and discriminant validity of the measurement were assessedfirst by examining the square root of AVE for each construct to see whether they are larger than0.7and larger than the correlation to other constructs,and secondly by comparing each item's loading on its construct against its cross loadings on other constructs to make sure the latter is relatively smaller than the former[24].Our sample met both criteria,signifying the validity of the constructs.Further-more,the internal composite reliability(ICR)of all constructs was greater than0.80(except for PT which has ICR of0.78)which is an indication of construct reliability.These results suggest that the constructs were reliable and valid.4.2.Explaining behavioral usageThe PLS analysis estimated the path coefficients of the two models. Tables6and7present the path coefficients for each relationship,their respective t-value,and the variance explained for each dependent variable.In MM,and perceived enjoyment significantly influenced attitude towards usage,whereas perceived usefulness and perceived ease of use did not have a significant impact on attitude towards usage.The causal links between attitude,behavioral intention,and behavioral usage were supported by the data.On the other hand,in U&G,information seeking,entertainment,and interpersonal utility were the most salient predictors of behavioral usage.The remaining two motivation factors did not have a significant impact on behavioral usage.In PLS analysis,a good modelfit is established with significant path coefficients,acceptably high R2,and internal composite reliability of constructs[24].As supported by the results of our PLS analysis,the data fairlyfit both models.The strength of all relationships among the MM and U&G constructs was high(standard path greater than0.2 [42]),indicating that all relationships were meaningful.We were particularly interested in the variance in behavioral usage explained by each model.We found that U&G theory explained more variance (R2=0.367)than MM did(R2=0.173).The difference may be attributed to the use of more variables in U&G to explain behavioral usage.The items of both models have comparable internal composite reliability and square root of AVE.Therefore,we conclude that both models predict behavioral usage well,though U&G explains more variance than does MM.We will further discuss the results in the discussion section.Table3Item loadings(U&G theory).Latent constructs Item Latent constructsIU C PT E IS BUInterpersonal utility(IU)M010.725⁎⁎⁎0.291−0.0300.275−0.0330.170 M020.746⁎⁎⁎0.1760.0500.3090.1190.351M030.867⁎⁎⁎0.3250.0970.2740.0530.339M040.787⁎⁎⁎0.3420.1200.2590.1170.276M050.829⁎⁎⁎0.3700.1740.4720.1560.369 Convenience(C)M160.3700.954⁎⁎⁎0.0260.3970.3040.223 M170.3390.937⁎⁎⁎0.1000.3400.3230.190 Pass time(PT)M070.097−0.0590.909⁎⁎⁎0.1630.3020.148 M090.0450.1920.769⁎⁎⁎0.1570.3800.113M08−0.1000.0050.502⁎⁎⁎0.0800.403−0.043 Entertainment(E)M180.3990.4240.3160.844⁎⁎⁎0.2440.371 M190.3210.3150.2120.911⁎⁎⁎0.3430.359M200.3820.3440.1450.927⁎⁎⁎0.3130.422M220.3150.2770.0220.772⁎⁎⁎0.4260.443 Information seeking(IS)M100.0760.2930.2860.3570.678⁎⁎⁎0.323 M110.1610.2170.3000.2100.747⁎⁎⁎0.329M120.1360.2650.3410.1960.814⁎⁎⁎0.357M13−0.0010.2410.1620.4320.828⁎⁎⁎0.363 Behavioral usage(BU)BU010.3690.2110.1840.5360.4580.866⁎⁎⁎BU020.2090.0940.0900.2320.3330.771⁎⁎⁎BU030.3370.1990.1320.2020.1720.676⁎⁎⁎Note:N=63.Item loadings higher than0.5are in bold.⁎:p b0.05,⁎⁎:p b0.01,⁎⁎⁎:p b0.001.Table4Measurement model estimation(MM).AVE/correlation Latent constructsLatent constructs ICR(1)(2)(3)(4)(5)(6)(1)Perceived ease of use0.960.89(2)Perceived usefulness0.950.560.88(3)Perceived enjoyment0.950.230.360.91(4)Attitude towards use0.980.370.490.700.98(5)Behavioral intention0.960.220.320.620.440.90(6)Behavioral usage0.810.250.370.510.420.420.77Notes:1.ICR:internal composite reliability.2.Diagonal elements are the square root of the shared variance between the constructs and their measures;the square root of the shared variance higher than0.7is in bold.Square root of the shared variance across items measuring a construct was higher than correlations across constructs shows that discriminant validity across constructs is supported.off-diagonal elements are correlations between constructs.Table5Measurement model estimation(U&G theory).AVE/correlation Latent constructLatent construct ICR(1)(2)(3)(4)(5)(6)(1)Interpersonal utility0.890.79(2)Convenience0.940.380.95(3)Pass time0.780.120.060.75(4)Entertainment0.920.410.390.190.87(5)Information seeking0.850.120.330.350.390.77(6)Behavioral usage0.820.400.220.180.470.450.77Notes:1.ICR:internal composite reliability.2.Diagonal elements are the square root of the shared variance between the constructs and their measures;the square root of the shared variance higher than0.7is in bold.Square root of the shared variance across items measuring a construct was higher than correlations across constructs shows that discriminant validity across constructs is supported.off-diagonal elements are correlations between constructs.25M.M.Luo et al./Decision Support Systems51(2011)21–30。