Killtest 4A0-107
- 格式:pdf
- 大小:77.31 KB
- 文档页数:4

APK在线检测杀毒推荐⽹址具体操作步骤如下:
⼀、360⼿机app检测:
(⽀持批量在线检测安卓\塞班平台的应⽤,⽂件上限为60M)
⼆、腾讯⼿机管家:
(⽀持sisx\sis\apk\jar的程序包,⽂件最⼤不能超过100M)
三、安全管家查毒:
(除在线上传检测外,还⽀持软件下载链接的安全扫描检测)
四、⽹秦⼿机病毒检测:
(⽀持sisx、sis、apk、jar、cab格式的⼿机软件的病毒检测)
PS:以上地址均需要以上传软件程序包的⽅式进⾏在线病毒扫描,对于⼿机端还是建议⼤家安装专业的安全防护软件。
不过对于智能电视或⽹络机顶盒等设备还是建议⼤家在安装前检测⼀下,以防万⼀,供⼤家参考。

linux下杀死进程(kill)的N种⽅法⽤bash快速杀死进程我正在继续我的bash旅程!我说的是,即使很多也可以在其他⼯作,例如sh和zsh。
说实话,它可以被称为;我的shell旅程。
有时您想杀死⼀个进程⽽不运⾏ps aux,然后将其复制粘贴PID并最终⼀遍⼜⼀遍地杀死它……ps aux | grep puma-dev | awk'{print $2}' | tail -n 1 | xargs kill为什么会有那么多命令?ps aux # 显⽰所有正在运⾏的过程grep puma-dev # 选择其中带有⽂本“ puma-dev”的⾏awk'{print $2}' # 在第⼆列中选择值(即PID使⽤时的位置ps aux)tail -n 1 # 从底部选择⼀⾏,即最后⼀⾏xargs kill # 获取先前提取的值(最后⼀个PID)并将其杀死,例如:kill666如果要杀死所有找到的进程,请删除tail -n 1命令。
最佳化要跳过awk解析的笨拙(双关语意)命令PID,我们可以使⽤pgrep。
pgrep puma-dev | xargs kill我们甚⾄可以使⽤以下命令将命令简化为⼀个pkill:pkill puma-dev我通常结合使⽤这些命令,因为它们pkill不会给您太多有关所发⽣情况的反馈。
有时候我想看到⼀切ps aux。
有时我只是不在乎,或者我更想⼀次⼜⼀次地重复杀死同⼀程序。
⾸先,⽤ps查看进程,⽅法如下:$ ps -ef……smx 1822 1 0 11:38 ? 00:00:49 gnome-terminalsmx 1823 1822 0 11:38 ? 00:00:00 gnome-pty-helpersmx 1824 1822 0 11:38 pts/0 00:00:02 bashsmx 1827 1 4 11:38 ? 00:26:28 /usr/lib/firefox-3.6.18/firefox-binsmx 1857 1822 0 11:38 pts/1 00:00:00 bashsmx 1880 1619 0 11:38 ? 00:00:00 update-notifier……smx 11946 1824 0 21:41 pts/0 00:00:00 ps -ef或者:$ ps -aux……smx 1822 0.1 0.8 58484 18152 ? Sl 11:38 0:49 gnome-terminalsmx 1823 0.0 0.0 1988 712 ? S 11:38 0:00 gnome-pty-helpersmx 1824 0.0 0.1 6820 3776 pts/0 Ss 11:38 0:02 bashsmx 1827 4.3 5.8 398196 119568 ? Sl 11:38 26:13 /usr/lib/firefox-3.6.18/firefox-binsmx 1857 0.0 0.1 6688 3644 pts/1 Ss 11:38 0:00 bashsmx 1880 0.0 0.6 41536 12620 ? S 11:38 0:00 update-notifier……smx 11953 0.0 0.0 2716 1064 pts/0 R+ 21:42 0:00 ps -aux此时如果我想杀了⽕狐的进程就在终端输⼊:$ kill -s 9 1827其中-s 9 制定了传递给进程的信号是9,即强制、尽快终⽌进程。

NZZV ]]] QORRZKYZ IT▲ Ҳ ԟ ԇThe safer , easier way to help you pass any IT exams.Exam : 4A0-102Title :Version : DEMOAlcatel-Lucent Border Gateway Protocol1.Which of the following are Link State protocols?A. BGPB. RIPC. OSPFD. IS-ISAnswer: C, D2.ECMP supports which of the following. Choose the best answer.A. 8 equal-cost paths per destination learned from any protocolB. 16 equal-cost paths per destination learned from any protocolC. 8 equal-cost paths per destination learned from the same protocol and preferenceD. 16 equal-cost paths per destination learned from the same protocol and preferenceE. 4 equal-cost paths per destinationAnswer: D3.Which of the following statements best describes the function of the RTM?A. From the router's route table, select the best routes to be installed in the FIB for forwardingdata.B. Based on the metrics of the routing protocol, chose the lowest cost route to be installed in theroute table.C. Apply the BGP route selection criteria to select the best route to be installed in the route table.D. Select the preferred route from the various routing protocols to be installed as the active routein the route table.E. Apply the assigned import and export policies to determine the routes to be advertised to therouter's neighbors.Answer: D4.What items are carried in a typical classless routing update? Select the best answer.A. Network address, mask and metricB. Network address and metricC. Prefix and maskD. prefix, next-hop and metricE. prefix and next-hopAnswer: A5.Choose the most accurate statement about the connections between eBGP peers.A. eBGP peers are usually directly connected to each other.B. eBGP peers are always directly connected to each other.C. eBGP peers are never directly connected to each other.D. eBGP peers are usually directly connected to each other, unless they are in the same autonomous system.E. eBGP peers are usually not directly connected to each other, additional configuration is required if they are.Answer: A6.What message is issued by a neighbor as a response to a valid Open?A. KeepaliveB. OpenC. ExchangeD. NotificationE. PingAnswer: A7.Which of the following is not exchanged in a BGP Open message?A. BGP version numberB. The local AS numberC. The hold timeD. The keepalive timerE. The Router IDAnswer: D8.The state of one BGP neighbor shows Established, which of the following is false?A. The router has established a complete session with that neighbor.B. BGP can exchange update, notification and keepalive messages with that neighborC. If the keepalive timer expires, the local system sends a keepalive message and restarts itskeepalive timerD. If the local system receives a notification message, it changes its state to OpenConfirmE. Established is the operational stateAnswer: D9.Which of the following is a Well Known Mandatory attribute?A. Origin CodeB. Local PreferenceC. MEDD. AS PathE. (a) and (d)F. (b) and (d)Answer: E10.Which of the following is true, based on the AS Path list shown here? 65206 65111 65100A. AS 65206 originated the routeB. AS 65111 is a transit ASC. AS 65100 is a transit ASD. AS 65100 originated the routeE. (b) and (d)F. (a) and (c)Answer: E。
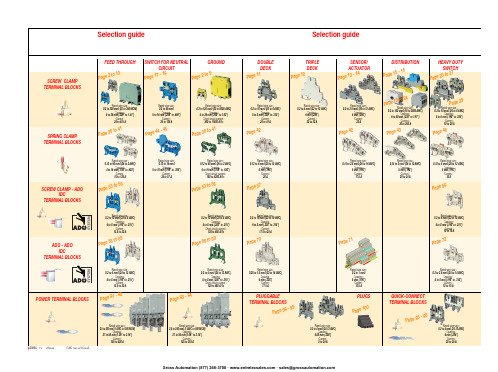
ABB EntrelecSommaireBU0402061SNC 160 003 C0205SummarySelection guide ....................................................................................page 1Screw clamp ........................................................................................page 2Feed through and ground terminal blocks .......................................................page 2 - 5 to 10Single pole, multiclamp terminal blocks..........................................................................page 4Feed through terminal blocks - Double-deck................................................................page 11Feed through terminal blocks - Triple-deck...................................................................page 12Three level sensor, terminal blocks without ground connection...................................page 13Three level sensor, terminal blocks with ground connection ........................................page 14Terminal blocks for distribution boxes, double deck + protection .......................page 15 - 16Interruptible terminal blocks for neutral circuit......................................................page 17 - 18Distribution : phase, ground terminal blocks .......................................................page 19 to 21Single pole or four pole distribution blocks..........................................................page 22 to 24Heavy duty switch terminal blocks with blade......................................................page 25 - 26Heavy duty switch terminal blocks with push-turn knob..............................................page 26Heavy duty switch terminal blocks with contact control pull lever...............................page 29Heavy duty switch terminal blocks with blade - Double-deck .....................................page 27Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.)or 6.35x25.4 mm (1/4x1 in.) and 6.35x32 mm (1/4x11/4 in.) fuse s.........................................page 28 - 29Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.) fuses -Double-dec k.....................................................................................................................page 27Terminal blocks for test circuits with sliding bridge ......................................................page 30Terminal blocks for metering circuits.............................................................................page 31ESSAILEC terminal blocks.............................................................................................page 32Safety connection terminal blocks ................................................................................page 33Miniblocks for EN 50045 (DIN 46277/2) rail ..........................................................page 34 - 35Spring clamp ......................................................................................page 36Angled terminal blocks - Feed through and ground .....................................................page 36Feed through and ground terminal blocks ...........................................................page 37 to 41Feed through terminal blocks - Double deck ................................................................page 42Terminal blocks for sensors / actuators ........................................................................page 42Terminal blocks for distribution boxes...........................................................................page 43Switch terminal blocks for neutral conductor........................................................page 44 - 45Heavy duty switch terminal blocks with blade..............................................................page 46Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.) fuse s....page 47Miniblocks Spring clamp ......................................................................................page 48 to 52ADO - Screw clamp ...........................................................................page 53Feed through and ground terminal blocks ...........................................................page 53 to 56Feed through and ground terminal blocks - Double-deck............................................page 57Heavy duty switch terminal blocks with blade..............................................................page 58Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.) fuse s ......page 59 - 60Miniblocks ADO - Screw clamp............................................................................page 61 to 65ADO - ADO .........................................................................................page 66Feed through and ground terminal blocks ...........................................................page 66 to 69Feed through and ground terminal blocks - Double-deck............................................page 70Terminal blocks for sensors / actuators ........................................................................page 71Heavy duty switch terminal blocks with blade..............................................................page 72Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.) fuse s ......page 73 - 74Miniblocks ADO - ADO .........................................................................................page 75 to 79Accessories ADO ...........................................................................................................page 80Power terminal blocks .............................................................page 81 to 84Quick-connect terminal blocks .................................................page 85 - 86Terminal blocks for railway applications ................................page 87 to 97Pluggable terminal blocks .....................................................page 98 to 100Accessories......................................................................................page 101Marking..................................................................................page 102 to 104GrossAutomation(877)268-3700··*************************PR30PR3.Z2PR3.G2PR5PR4PR1.Z2Rated wire size :Rated wire size :Rated wire size :Rated wire size :Mounting railsShield terminals forcollector barMarking tableHorizontal Rated wire size :0.5 to 16 mm² (22 to 8 AWG)Rated wire size :Rated wire size :Rated wire size :P a g e t o 29e30 t o 32ag e e3P a ge 8 t o 60a g e6t o 6574P a ge 7 t o 79P a ge 9P a g P a gGrossAutomation(877)268-3700··*************************2ABB Entrelecd010830402051SNC 160 003 C0205MA 2,5/5 - 2.5 mm² blocks - 5 mm .200" spacingAccessoriesGrossAutomation(877)268-3700··*************************3ABB Entrelec D010740402051SNC 160 003 C0205M 4/6 - 4 mm² blocks - 6 mm .238" spacingAccessoriesGrossAutomation(877)268-3700··*************************4ABB EntrelecD011030402051SNC 160 003 C0205M 4/6.3A - 4 mm² blocks - 6 mm .238" spacingM 4/6.4A - 4 mm² blocks - 6 mm .238" spacingGrossAutomation(877)268-3700··*************************5ABB Entrelec D010840402051SNC 160 003 C0205M 6/8 - 6 mm² blocks - 8 mm .315" spacingAccessoriesGrossAutomation(877)268-3700··*************************6ABB EntrelecD010850402051SNC 160 003 C0205M 10/10 - 10 mm² blocks - 10 mm .394" spacingAccessoriesGrossAutomation(877)268-3700··*************************7ABB Entrelec D010860402051SNC 160 003 C0205M 16/12 - 16 mm² blocks - 12 mm .473" spacingAccessoriesGrossAutomation(877)268-3700··*************************8ABB EntrelecD010870402051SNC 160 003 C0205M 35/16 - 35 mm² blocks - 16 mm .630" spacingGrossAutomation(877)268-3700··*************************M 95/26 - 95 mm² blocks - 26 mm 1.02" spacingM 70/22.P - 70 mm² ground block with rail contact - 22 mm .630" spacingSelection35 mm / 1.37"12 mm / 0.47"14-30 Nm / 124-260 Ib.in 1.2-1.4 Nm / 10.6-12.3 Ib.in1000600600415400400577070240 mm 2500 MCM 500 MCM 10 mm 2 6 AWG 6 AWG IEC UL CSANFC DIN0.5 - 160.5 - 100 AWG-600 MCM 2 AWG-500 MCM 50 - 30035 - 24018-6 AWGD 150/31.D10 - 150 mm² blocks - 31 mm 1.22" spacingCharacteristicsD 240/36.D10 - 240 mm² blocks - 36 mm 1.41" spacingSelectionWire size main circuit mm² / AWG VoltageV Current main circuit A Current outputARated wire size main circuit mm² / AWG Rated wire size outputmm² / AWG Wire stripping length main circuit mm / inches Wire stripping length output mm / inches Recommended torque main circuit Nm / Ib.in Recommended torque outputNm / Ib.inSolid Stranded Solid Stranded Wire size output mm² / AWG9.5 mm / .37"0.5-0.8 Nm / 4.4-7.1 Ib.in5003003003220204 mm 212 AWG12 AWG0.2 - 422-12 AWG 22-12 AWG 0.22 - 4IEC ULCSANFC DINCharacteristicsWire size mm² / AWGSolid Stranded D 4/6.T3 - 4 mm² blocks - 6 mm .238" spacingSelectionVoltage V CurrentARated wire sizemm² / AWG Wire stripping length mm / inches Recommended torqueNm / Ib.inM 4/6.T3.P - 4 mm² block - 6 mm .238" spacingD 2,5/6.D - 2.5 mm² blocks - 6 mm .238" spacingD 2,5/6.DL - 2.5 mm² blocks - 6 mm .238" spacingD 2,5/6.DPA1 - 2.5 mm² blocks - 6 mm .238" spacingD 2,5/6.DPAL1 - 2.5 mm² blocks - 6 mm .238" spacingD 4/6... - 4 mm² blocks - 6 mm .238" spacingD 4/6.LNTP - 4 mm² closed blocks - 17.8 mm .700" spacingMA 2,5/5.NT- 2.5 mm² block - 5 mm .200" spacingAccessories**SFB2 : 16 to 35 mm² 6 to 2 AWG H= 3 mm/.12"M 10/10.NT- 10 mm² block - 10 mm .394" spacingAccessories(1) Except for M 35/16 NT (closed block)*SFB1 : 0.5 to 35 mm² 18 to 2 AWG H= 7 mm/.28"**SFB2 : 16 to 35 mm² 6 to 2 AWG H= 3 mm/.12"MB 4/6... - 4 mm² blocks - 6 mm .238" spacingMB 6/8... - 6 mm² blocks - 8 mm .315" spacingMB 10/10... - 10 mm² blocks - 10 mm .394" spacingBRU 125 A - 35 mm² block - 27 mm 1.063" spacingBRU 160 A - 70 mm² block - 35.2 mm 1.388" spacingBRU 250 A - 120 mm² blocks - 44.5 mm 1.752" spacingBRU 400 A - 185 mm² block - 44.5 mm 1.752" spacingAccessoriesAccessoriesBRT 80 A - 16 mm² block - 48 mm 1.89" spacingBRT 125 A - 35 mm² block - 48 mm 1.89" spacingBRT 160 A - 50 mm² block - 50 mm 1.97" spacing9.5 mm / .37"0.5-0.6 Nm / 4.4-5.3 Ib.in4003003002010104 mm 210 AWG 12 AWG 0.5 - 422-10 AWG20-12 AWG0.5 - 2.5IEC ULCSANFC DINMA 2,5/5.SNB - 2.5 mm² blocks - 5 mm .200" spacingCharacteristicsM 4/6.SNB - 4 mm² blocks - 6 mm .238" spacingSelectionWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping length mm / inches Recommended torqueNm / Ib.inSolid StrandedM 6/8.SNB - 6 mm² blocks - 8 mm .315" spacing - blade switchingSelectionAccessoriesM 4/8.D2.SF - for fuses 5x20 mm .197x.787 in. and 5x25 mm .197x.984 in. -4 mm² blocks - 8 mm .315" spacingM 4/6.D2.SNBT - 4 mm² blocks - 6 mm .238" spacing - blade switchM 4/8.SF- 4 mm² blocks - 8 mm .315" spacingM 4/8.SFL - 4 mm² blocks - 8 mm .315" spacing12 mm / .472"1.2-1.4 Nm / 10.6-12.3 Ib.in800(1)60060016252510 mm 210 AWG8 AWG0.5 - 1622-10 AWG 22-8 AWG 0.5 - 10IEC ULCSANFC DINCBD2SML 10/13.SF - for fuses 6.35x25.4 mm 1/4x1 in. and 6.35x32 mm 1/4x11/4 in. -10 mm² blocks - 13 mm .512" spacingSelectionAccessoriesCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping length mm / inches Recommended torqueNm / Ib.inSolid Stranded (1) Insulation voltage of terminal block - operating voltage : according to fuse.M 4/6.D2.2S2... - 4 mm² blocks - 6 mm .238" spacing11 mm / .43"0.8-1 Nm / 7.1-8.9 Ib.in50060030306 mm 28 AWG0.5 - 1022-8 AWG0.5 - 6IECULCSANFC DINM 6/8.ST... - 6 mm² blocks - 8 mm .315" spacingCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping length mm / inches Recommended torqueNm / Ib.inSolid Stranded M 6/8.STA - 6 mm² blocks - 8 mm .315" spacing(3)Only for M 6/8.STAM 4/6.ST- 4 mm² blocks - 6 mm .236" spacingBNT...PC...(2) Only for M10/10.ST-SnThe PREM IUM solution for testing the secondary circuits of current or voltage transformers.ESSAILEC, approved by the major electricity utilities, remains the premium choice for the energy market.Implemented in the transformers secondary circuits, ESSAILEC thanks to its intelligent “make before break” design eases and secures any intervention. Cutting the energy supply is avoided with zero risk for the operator.The plug and socket connection cuts cost installation as well as in-situ wiring errors. ESSAILEC is ideal for the wiring of sub-assemblies in the secondary circuits.ESSAILEC terminal blocksProtection relays,Protection relays,Testing :The ESSAILEC socket supplies energy to the protection or counting devices. The insertion of the test plug, which is connected to the measurement equipment, allows the testing of the devices, without perturbing the circuit.ESSAILEC blocks are well adapted to current or voltage measurement :-Current sockets with make before break contacts and pre-wired test plug for current measures-Voltage sockets with open contacts and pre-wired test plug for voltage measures-Up to 4 ammeters or 4 voltmeters connected to the test plugDistributing :The ESSAILEC plug is continuously mounted on the socket to supply current or voltage to secondary circuits sub assemblies.ESSAILEC blocks extreme versatility allow :-Safe current distribution with current socket with mobile contacts since the secondary circuit is not cut when plug is removed-Voltage or polarity distribution with dedicated voltage or polarity socket with closed contactESSAILEC is designed to offer :Great flexibility :-Connection multi contacts « plug and play »-Panel, rail, rack fixed mounting or stand-alone connector -Two wiring technologies, up to 10 mm²Extreme reliability :-Non symmetric blocks -Coding accessories -IP20 design -Locking system -Sealed coverR S T NFor technical characteristics and complete part numbers list, please ask for the ESSAILEC catalog10005006003225254 mm 21.65 mm²12 AWG 13 mm / .51"IECB.SCSANFC DINTS 50-180.5 - 0.8 Nm /4.4 - 7.1 Ib.in0.2 - 422-12 AWG0.22 - 40.5 - 1.50.28 - 1.6580050060041252562.512 AWG 13 mm / .51"0.8 - 1 Nm / 7.1 - 8.9 Ib.inIECB.S CSANFC DINTS 50-180.5 - 1020-12 AWG0.5 - 60.28 - 2.590050060046406510 mm 26 mm² 6 AWG 14 mm / .55"IECB.S UL/CSANFC DINTS 50-181.2 - 1.4 Nm / 10.6 - 12.3 Ib.in0.5 - 1620 - 6 AWG0.5 - 100.28 - 6M 4/6.RS - 4 mm² blocks - 6 mm .238" spacingCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping lengthmm / inches Recommended torque (screw)Nm / Ib.inSolid wire Stranded wire Solid wire Stranded wire Screw clampLugsM 6/8.RS - 6 mm² blocks - 8 mm .315" spacingCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping lengthmm / inches Recommended torque (screw)Nm / Ib.inSolid wire Stranded wire Solid wire Stranded wire Screw clampLugspending M 10/10.RS - 10 mm² blocks - 10 mm .394" spacingCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping lengthmm / inches Recommended torque (screw)Nm / Ib.inSolid wire Stranded wire Solid wire Stranded wire Screw clampLugspending SelectionAccessories(1) Only for block M 4/6.RS (4) For blocks M 4/6.RS and M 6/8.RS(2) Only for block M 6/8.RS(3) Only for block M 10/10.RSDR 1,5/4 - 1.5 mm² blocks - 4 mm .157" spacingDR 1,5/5... - 1.5 mm² blocks - 5 mm .200" spacing。
linux kill命令参数及用法详解功能说明:删除执行中的程序或工作。
语法:kill [-s <信息名称或编号>][程序]或kill [-l <信息编号>]补充说明:kill可将指定的信息送至程序。
预设的信息为SIGTERM(15),可将指定程序终止。
若仍无法终止该程序,可使用SIGKILL(9)信息尝试强制删除程序。
程序或工作的编号可利用ps指令或jobs指令查看。
参数:-l <信息编号> 若不加<信息编号>选项,则-l参数会列出全部的信息名称。
-s <信息名称或编号> 指定要送出的信息。
[程序] [程序]可以是程序的PID或是PGID,也可以是工作编号。
kill命令可以从kill这个词来大致了解下它的作用,是的,它用来杀死(kill)一个进程。
下面是kill命令的详解。
1.作用kill命令用来中止一个进程。
2.格式kill [ -s signal | -p ] [ -a ] p id…kill -l [ signal ]3.参数-s:指定发送的信号。
-p:模拟发送信号。
-l:指定信号的名称列表。
pid:要中止进程的ID号。
Signal:表示信号。
4.说明进程是Linux系统中一个非常重要的概念。
Linux是一个多任务的操作系统,系统上经常同时运行着多个进程。
我们不关心这些进程究竟是如何分配的,或者是内核如何管理分配时间片的,所关心的是如何去控制这些进程,让它们能够很好地为用户服务。
Linux 操作系统包括三种不同类型的进程,每种进程都有自己的特点和属性。
交互进程是由一个Shell启动的进程。
交互进程既可以在前台运行,也可以在后台运行。
批处理进程和终端没有联系,是一个进程序列。
监控进程(也称系统守护进程)是Linux系统启动时启动的进程,并在后台运行。
例如,httpd是著名的Apache服务器的监控进程。
kill 命令的工作原理是,向Linux系统的内核发送一个系统操作信号和某个程序的进程标识号,然后系统内核就可以对进程标识号指定的进程进行操作。

如何杀死僵⼫进程?
僵⼫进程定义?
查看僵⼫进程,利⽤命令ps,可以看到有标记为Z(zombie)的进程就是僵⼫进程。
僵⼫进程的危害?
僵⼫进程会占⽤系统资源,如果很多,则会严重影响服务器的性能;
僵⼫进程产⽣的原因?
⼦进程结束后向⽗进程发出SIGCHLD信号,⽗进程默认忽略了它
⽗进程没有调⽤wait()或waitpid()函数来等待⼦进程的结束
⽹络原因有时会引起僵⼫进程;
如何杀死僵⼫进程?
僵⼫进程⽤kill命令是⽆法杀掉的,但是我们可以结果掉僵⼫进程的爸爸,僵⼫daddy挂了之后,僵⼫进程就成了孤⼉进程,孤⼉进程不会占⽤系统资源,会被init程序收养,然后init程序将其回收。
ps -A -o stat,ppid,pid,cmd |grep -e "^[Zz]" //先查看具体进程:
kill -9 pid号 //杀死z进程(这些动作是⽐较危险的,希望在真正的服务器上⾯慎⽤)
1.查看所有R相关的进程
2.查看僵⼫进程的⽗进程
3.杀死僵⼫进程对应的⽗进程
4.僵⼫进程被回收
参考:
1.
2.
3.
4.。

NZZV ]]] QORRZKYZ IT▲ Ҳ ԟ ԇThe safer , easier way to help you pass any IT exams. Exam: PK0-003Project+ (2009)Title:Version: Demo1.You are the project manager for your organization and are coaching Sam on the differences between a project and operations. Which one of the following is the best definition of a project?A. A project is a short-term endeavor to create a unique product or service.B. A project moves through five phases:initiating, planning, executing, monitoring and controlling, and closing.C. A project creates a unique product or service for the organization's customers.D. A project provides a service to the organization.Answer: A2.Which of the following processes involves monitoring the progress of the project to identify any variances in the project plan?A. ClosingB. ControllingC. ExecutingD. PlanningAnswer: B3.You are the project manager for the HNG Project. Your project is slated to last eight months but management has asked that you create a method for reducing the project duration. You elect to allow certain phases of the project to overlap. What schedule compression technique have you used in this instance?A. CrashingB. Lag timeC. Resource levelingD. Fast trackingAnswer: D4.You are a project manager for GTX project. The project has ten active stakeholders. How many communication channels will be required for effective communication with the stakeholders?A. 45B. 2C. 10D. 9Answer: A5.You are the project manager of manufacturing process. Your project will focus on the creation of 987,600 handheld printers to be used in grocery stores around the world. The printers are manufactured largely by machine though there are several steps in the process where project team members will need to manually configure the devices. Management will be completing statistical sampling of the printers and they have established an upper control limit of 980 correct out of 1,000 and a lower control limit of 970 out of 1,000. Your expected mean is 975. On a control chart, which is what management expects you to create, what is called should your results exceed 980 correct out of a 1,000 in any given measurements?A. Out of controlB. Failure modeC. ImprovementD. VarianceAnswer: A6.Which of the following is the last deliverable at the close out meeting?A. Customer FeedbackB. Project approvalC. Lessons LearnedD. Source code of applicationAnswer: C7.You are the project manager of the NGQ Project and are reviewing the assignments for yourproject team. You have decided to use a RACI chart as your responsibility assignment matrix.What does RACI mean?A. Responsible, Active, Confirmed, InactiveB. Resource, Action, Communicate, InformC. Responsible, Accountable, Communicate, InformD. Responsible, Accountable, Consult, InformAnswer: D8.You are the project manager of the NHH Project and you have 22 project team members on the project. You need to identify a method to promote performance on your project and are examining Herzberg's Theory of Motivation. What will happen in this theory to your project team's motivationif you can remove the hygiene agents according to Herzberg's Theory?A. The motivation of the team will excel once the hygiene agents are removed.B. The motivation of the team will excel - if they're interested in the project's goals.C. There will be no change in the team's motivation.D. The motivation of the team will decrease.Answer: D9.Which of the following process groups of the project management processes utilizes the mostproject time and resource?A. PlanningB. InitiationC. ClosingD. ExecutingE. ControllingAnswer: D10.A construction company is about to start a new project. It requires hiring a project manager for this project. Which of the following are the most important skills that a person must have to be selected as a project manager?A. Team building and human resourcesC. Problem solvingD. Negotiation and influentialE. CommunicationAnswer: E11.Samantha is the project manager of the KWK Project and she has completed the project deliverables. She needs the project customers to inspect the project work to gain their formal acceptance of what she and her project team have created. What process does Samantha need to initiate?A. Verify scopeB. Perform quality controlC. Project closureD. Scope validationAnswer: A12.You are the project manager in a matrix structure. Your project team comes from all over the organization and many of your project team members report to several project managers besides you. There are total 89 project team members on your project that you need to communicate with and you'll need to communicate with the other project managers and functional managers for each resource on the project team. What type of a chart can you create to help track the reporting relationships of all your project team members in this matrix structure?A. Project Organization ChartB. Resource Assignment MatrixC. Communications matrixD. Role and responsibility matrixAnswer: A13.Brent is the project manager of the NYE Project and he has just completed the first phase of the project. Before the project may move forward the project customer must inspect the project workto determine completeness of the work so far. This activity is part of the closing the project phase. What process will Brent and the project stakeholders do at the end of each project phase?A. Phase gate reviewB. Inspection of key resultsC. Quality controlD. Verify scopeAnswer: D14.You have been hired as a contract project manager for Tech Perfect Inc. The project has already been started. Sufficient details of the project have already been structured. You are working withyour team for cost estimation of the project. Which of the following estimating techniques will youuse for the highest degree of accuracy?A. Parametric modelingB. AnalogousD. Top-downAnswer: C15.You are the project manager for the NHQ Project and are working with Patty, a junior project manager on the project. Patty is curious about the project's critical path and the concept of float. Patty doesn't understand what the critical path is. Which one of the following statements best describes the critical path?A. It's the path that contains the riskiest project activities.B. It's the path in the project network diagram with the most important activities.C. It's the path in the project network diagram that reveals the earliest date the project can be completed.D. It's always the one path with the least amount of float.Answer: C16.You are the project manager of the BGY Project. A new issue has been identified in the project and this issue could prove to be costly for the project. The issue affects Anna's project deliverable and she is a negative stakeholder for the project. Considering these elements of the project, what type of communication would be the most effective to share this news with Anna?A. Documented review of the issueB. Face-to-face meetingC. Informal presentation meetingD. Immediate telephone callAnswer: B17.You are the project manager of the NGH Project and are predicting the costs for your project work. You have determined that an activity in your project has the following cost attributes assigned to it: Optimistic - $3,500; Most Likely - $7,500; Pessimistic - $12,500.What is the amount that you'll record for the project's cost in the cost management plan and estimate?A. $7666B. $12500C. $3500, $7500, $12500D. $7500Answer: A18.Which of the following types of floats are available? Each correct answer represents a complete solution. Choose two.A. Half floatB. Free floatC. Full floatD. Total floatAnswer: B,D19.In what organizational structure is the project manager often referred to as a project coordinator or expeditor?A. Weak matrixB. Balanced matrixC. ProjectizedD. Strong matrixAnswer: A20.You are the project manager of the NHQ Project for your organization. You are working on creating the project management plan for the NHQ Project and need to identify the costs of the resources needed in the project. All of the following are examples of resources except for which one?A. Network cableB. SoftwareC. Staffing management planD. Electrical engineerAnswer: C21.Which of the following is responsible to sign off on the closure documents of a project?A. End userB. Project team membersC. SponsorD. Project ManagerAnswer: C22.Ned is the project manager for a new project. Ned is determining what project team members should be recruited in the project that will likely last for eight months. All of the following are enterprise environmental factors that should be considered when acquiring project team members except for which one?A. Interest in working on the projectB. Cost to use the resourceC. Duration as an employeeD. Availability to work on the projectAnswer: C23.Jane is a project manager that is working with her project team. Some of the project stakeholders have been circumventing the change control process and approaching the project team members directly. Jane wants to inform the project team that stakeholders should use the approved change control form. What is it called when the project team members completed unapproved change requests for stakeholders?A. Scope creepB. Gold platingC. Cost of qualityD. Integrated change controlAnswer: A24.Julie is the project manager of the JUUY Project, which will create photography scanners for sale around the world. Her project team is tracking categories of failure for detailed analysis. Management has required in the project quality management plan that all defects be shown in a histogram for detailed evaluation. What type of a chart is management requesting?A. Process flowchartB. Cause-and-effect chartC. Pareto chartD. Control chartAnswer: C25.Violet is the project manager for her organization and she is working with Teddy on the quality control processes for their project. Teddy is confused on the difference between prevention and inspection when it comes to quality and customer acceptance of the project deliverables. Which statement best defines quality and customer acceptanceA. Prevention keeps errors out of the process. Inspection keeps errors out of the hands of the customer.B. Prevention and inspection work together to keep mistakes out of the customer's hands.C. Prevention is a management-driven process and inspection is a project team-driven process.D. Prevention is keeping errors out of the customer hands. Inspection keeps errors out of the project26.What theory of human resources states that people are driven primarily by one of three needs?A. McClelland's Theory of NeedsB. Ouchi's Theory ZC. Hertzberg's Theory of MotivationD. Maslow's Hierarchy of NeedsAnswer: A27.The cost variance (CV) value of a project is less than zero or negative. What does this value indicate?A. Costs are according to the budget.B. The budget for the project is insufficient.C. Costs are higher than originally planned for the project.D. Costs are less than budgeted.Answer: C28.You are the project manager of a high-priority project that will require the project team to work on the project for 18 months. The project cannot be late or the organization will face sizeable fines. You need a method to ensure that the project team will work towards the project with little defects and much accuracy to reach the project deadline.Which one of the following are methods for ensuring project team work accuracy in the project execution?A. Risk management meetingsB. Recognition and rewardsC. Management by walking aroundD. Coercive powerAnswer: B29.You are a project manager in a matrix environment. You and another project manager are in conflict over a particular resource that you both need on your project. Who has the authority in this environment to determine where and how the resource will be utilized in the projects?A. The functional management of the organizationB. The project manager whose project started firstC. The project team resourceD. The project manager with the most experienceAnswer: A30.Holly is the project manager for her organization. Two of her resources are in a heated argument over which database server the project should use. Holly interjects to calm down the scenario.She reminds them that they're on the same team, both have good points, and that the database will be selected in the project planning. The team members agree and move on with the project planning. What type of conflict resolution has Holly done in this instance?A. SmoothingB. AvoidingC. CompromisingD. ForcingAnswer: A。

NZZV ]]] QORRZKYZ IT▲ Ҳ ԟ ԇThe safer , easier way to help you pass any IT exams. Exam: 3X0-103Linux Networking (Level 1) Title:Version: DEMO1.You wish to communicate with hosts on your wide-area network. Which of the following is the exact sequence of commands used to manually configure an Ethernet interface, assuming driver modules are not loaded?A. lsmod, insmod, ifconfigB. insmod, ifconfig, routeC. lsmod, rmmod, insmod, ifconfigD. ifconfig, routeAnswer: B2.Which of the following are TRUE about buffer size? (Choose two.)A. A large buffer can lead to wasted system memory.B. A small buffer can lead to slower data transfer lines.C. Having a small buffer will free system memory, allocating fewer registers.D. The larger the buffer, the faster the transfer rate, reducing time arrival jitter.Answer: AB3.Which of the following is TRUE concerning the Address Resolution Protocol (ARP)?A. It binds a physical address to a broadcast address.B. It binds a MAC (Media Access Control) address to a logical address.C. It binds a logical address to an IP address.D. It binds a MAC (Media Access Control) address to a physical address.Answer: B4.Which of the following can tunneling be used for?A. It can connect two IPX networks separated by some different network.B. It can connect two IPv4 networks separated by some different network.C. It can provide mobile IP support and amateur radio support.D. It can connect two IPv6 networks separated by some different network.E. All of the above.Answer: E5.Which of the following commands will allow you to view the ARP table when the configured name server is not functioning? (Choose the best answer.)A. arp -vB. arp -aC. arp -nD. arp -sAnswer: C6.Which of the following can you do with the "ping" command? (Choose two.)A. Determine if a remote host can be contacted.B. Create and modify (n)x-u NIS network maps.C. View the MAC address of a given host.D. Display the route along which an IP packet travels.Answer: AD7.A default policy of DENY and ACCEPT may be implemented for a system's ipchains. Which of the following options will change the default input policy to DENY?A. ipchains -a input DENYB. ipchains -a output DENYC. ipchains -P input DENYD. ipchains -all input DENYE. ipchains -input DENYAnswer: C8.inetd is responsible for waiting for new network requests and authenticating users based on the contents of the "inetd.conf" file.A. TRUEB. FALSEAnswer: B9.Telnet was developed as a continuation of what other communications program developed for ARPANET? (Select the best answer.)A. rpcB. teleC. loginD. ftpE. muttF. None of the aboveAnswer: D10.Which path accurately depicts a three-way handshake between Network X and Network Y for establishing a TCP connection? (Select the best answer.)A. X sends SYN to Y; Y sends SYN to X; X sends ACK to YB. X sends SYN to Y; Y sends two SYNs to X; X sends ACK to YC. X sends ACK to Y; Y sends SYN to X ; X sends ACK to YD. X sends SYN to Y; Y sends ACK to X ; X sends ACK to YE. X sends ACK to Y; Y sends SYN and ACK to X; X sends ACK to YAnswer: D11.Which of the following is FALSE concerning TCP, IP, and UDP? (Select the best answer.)A. Transport Control Protocol (TCP) supports unicast addressing.B. User Datagram Protocol (UDP) supports unicast addressing.C. TCP supports multicasting.D. UDP supports multicasting.E. Internet Protocol (IP) supports multicasting.Answer: C12.Typical implementations of ping use the _____ to send echo requests to other hosts.A. Internet Protocol (IP)B. Internet Control Message Protocol (ICMP)C. User Datagram Protocol (UDP)D. Transport Control Protocol (TCP)Answer: B13.Because of flow control, UDP will generally lead to network congestion, while TCP helps prevent congestion.A. TrueB. FalseAnswer: A14.Assume that a software company has a subnet address 192.168.1.0/255.255.255.0. How many possible hosts can this subnet support, and what is the network address for the subnet?A. 64; 192.168.1.255B. 254; 192.168.1.0C. 255; 192.168.1.0D. 256; 192.168.1.255E. 128; 192.168.1.1Answer: B15.If a machine has an IP address of 192.168.1.61 and the netmask is 255.255.255.0, what is its subnet address?A. 192.0.0.0B. 192.168.0.0C. 192.168.1.0D. 0.0.0.61Answer: CThe safer , easier way to help you pass any IT exams.16.Which of the following subnet masks is usually associated with a Class A IP address?A. 255.255.0.0B. 255.255.255.0C. 255.0.0.0D. 255.255.255.255Answer: C17.Which of the following host IP addresses are on networks normally reserved for intranets? (Choose three.)A. 10.1.220.1B. 12.1.2.4C. 172.16.0.30D. 192.168.0.18E. 187.10.30.200Answer: ACD18.For a Class C network, which of the following denotes a valid host address on the 192.168.3.0 network?A. 192.168.3.255B. 192.168.3.1C. 192.168.3.0D. 192.168.3.256Answer: B19.Which of the following statements is TRUE about the subnet mask?A. Another name for the subnet mask is the subnet address.B. In the subnet mask, zeros represent the host ID and ones represent the network ID.C. In the subnet mask, ones represent the host ID and zeros represent the network ID.D. The subnet mask is used to aid in name resolution for root name servers.Answer: B20.Which Resource Record allows the redirecting of mail to another host, assuming the correct accounts exist?A. TXTB. PTRC. SOAD. MAILE. MXAnswer: EThe safer , easier way to help you pass any IT exams.。

杀软检查规则
杀软检查规则主要包括以下几种:
1. 静态查杀:主要基于hash 和特征码,hash 可以是文件的hash 或导入表之类的hash,特征码可以是PE 头、pdb、全局字符串、互斥体之类的信息。
2. 动态查杀:基于API 的监控和沙箱执行,杀软会通过对ntdll 的关键API 进行hook,实现对程序的API 监控。
另外可以在内核中注册一系列的回调函数实现对行为的监控。
3. 启发式:就是一套加减分的规则,用于检测程序的潜在恶意行为,如程序中有操作端口和通讯的函数,并将自身加载到启动项中等上述行为,则很有可能被判定为恶意。
4. 客户端提取特征上传,在云端检测到对应特征所标明的是否病毒状态,并返回。
5. 客户端上传特征,在云端无法检测到,则上传文件,文件通过杀软系统进行评判,得出总评分,对于无结果的,进行鉴定系统评分,总共得出结果返回给用户,并入云端库。
此外,杀软检查规则还包括对软件行为进行排查,比如注册表、文件、网络、以及进程操作等。
如果没有可疑行为,那么应该会认定这个软件是安全的,也就是不会报毒了。
如果有可疑行为,应该还是以人工
判断为主。
以上内容仅供参考,建议查阅专业杀毒软件的使用说明获取更全面和准确的信息。



Linux查找并杀死僵⼫进程
1、查看系统是否有僵⼫进程
使⽤Top命令查找,当zombie前的数量不为0时,即系统内存在相应数量的僵⼫进程。
2、定位僵⼫进程
使⽤命令ps -A -ostat,ppid,pid,cmd |grep -e '^[Zz]'定位僵⼫进程以及该僵⼫进程的⽗进程
僵⼫进程ID:3457,⽗进程ID:3425
僵⼫进程ID:3533,⽗进程ID:3511
3、使⽤Kill -HUP 僵⼫进程ID来杀死僵⼫进程,往往此种情况⽆法杀死僵⼫进程,此时就需要杀死僵⼫进程的⽗进程kill -HUP 僵⼫进程⽗ID
然后使⽤上⾯的语句查询该僵⼫进程是否被杀死
4、参数解读
ps -A -ostat,ppid,pid,cmd |grep -e '^[Zz]'
-A 参数列出所有进程
-o ⾃定义输出字段 stat(状态)、ppid(进程⽗id)、pid(进程id)、cmd(命令)
因为状态为z或者Z的进程为僵⼫进程,所以我们使⽤grep抓取stat状态为zZ进程。

NZZV ]]] QORRZKYZ IT▲ Ҳ ԟ ԇThe safer , easier way to help you pass any IT exams.Exam : NS0-153Title :Version : DEMONetwork Appliance Storege Networking1.If you change the setting for the option cifs.neg_buf_size, you need to terminate CIFS on the storage appliance and do a restart for the changes to take effect.A.TrueB.FalseCorrect:A2.If the client is a CIFS client, locks are __________.A.advisoryB.mandatoryC.orderedD.optionalCorrect:B3.To view per client NFS statistics on the storage appliance, options nfs.per_client_stats.enable must be turned on.A.TrueB.FalseCorrect:A4.Three methods of creating a LUN are: *lun setup *lun map *FilerViewA.TrueB.FalseCorrect:A5.Applications, such as databases, running on NAS or iSCSI or FC SAN must be __________________.A.prepared for snapshots by flushing buffers to disk and momentarily suspending activity.B.disconnected from their storage resources during the snapshot.ing dynamic multipathing during a backup.D.mirrored with a host-based volume manager to be backed-up.Correct:A6.To export volumes and directories automatically on reboot, include them in the /etc/exports file.A.TrueB.FalseCorrect:Aing the output below, a co-worker determined that these are type "Solaris" LUNs. What would your determination be? lun show -m LUN pathMapped to LUN ID --------------------------------------------------- /vol/vol1/lun0 solaris-igroup0 0 /vol/vol1/lun1 solaris-igroup10 /vol/vol1/qtree1/lun2 solaris-igroup2 0 /vol/vol1/qtree1/lun3 solaris-igroup3 0A.These are type "Solaris" LUNs.B.These are NFS LUNs, but the exact OS cannot be determined.C.Not enough information is given here. Run the lun show -v command to get the information requested.D.Not enough information is given here. Run the lun map command to get the information requested. Correct:C8.Which one of the following will enable "symlink_strict_security"?A.options cifs.symlink_strict_security onB.cifs shares -change -symlink_strict_securityC.options symlink_strict_security=trueD.options symlink_strict_security=onCorrect:B9.To configure a storage system as a member of an active directory, the time on the storage system must be synchronized with the time on the Domain Controller.A.TrueB.FalseCorrect:A10.The writeable snapshot that is created for a LUN clone depends on ___________.A.mirroring.B.the snapshot taken at the time the clone was created.C.exclusive access to the volume.D.the data in the original LUN not changing.Correct:B11.Which command is the most appropriate for troubleshooting a multiprotocol authentication problem?A.wccB.rdfile /etc/rcC.priv set advancedD.sysstat 1Correct:A12.A quota target can be defined as _______________.A.the maximum amount of disk space in a volume.B.the maximum number of files in a disk.C.a user, group, or qtree to which a quota is applied.D.a specific disk space threshold.Correct:C13.Which three are used for creating LUNs on the storage appliance? (Choose 3)A.lun createB.lun setupC.FilerViewD.lun configCorrect:A B C14.What is the outcome of this command? lun create -b /vol/vol2/.snapshot/testsnap/lun0 /vol/vol2/lun0.cloneA.It creates a duplicate of the clone process of lun0.B.It creates a clone of the writeable snapshot of lun0.C.It creates a writeable snapshot of lun0.D.It creates a snapshot "testsnap" of vol2.Correct:C15.Which security method encrypts the data?A.IPSecB.CHAPC.LUN maskingD.Header and Data DigestsCorrect:A16.____________ is the default cfmode for new installations of Data ONTAP 7.2.A.single imageB.mixedC.partnerD.dual fabricCorrect:A17.Which command would you use to verify that the iSCSI service is running?A.license add iSCSIB.iscsi serviceC.iscsi statusD.iscsi protocolCorrect:C18.If you believe you have a FC SAN performance problem, which NetApp utility or command would gather both your Solaris host and storage appliance data for analysis?A.poststatB.perfstatC.prestatD.sio_ntap.exeCorrect:B19.What is the definition of the cifs setup command?A.It displays the mount point of all shared directories.B.It displays the names of all mounted directories on the storage system.C.It displays the prompts for CIFS configuration information.D.It displays a list of the users on the storage system.Correct:C20.UNIX allow file access based on __________.A.GID or UID and UNIX permissions.B.NT ACLs and UNIX permissions.C.NT ACLs and SID.D.GID or UID and ACLs.Correct:A。

KILL邮件安全服务说明北京冠群金辰软件有限公司2009年9月目录一、垃圾邮件安全状况及危害....................................................................... 错误!未定义书签。
二、反垃圾邮件工作原理............................................................................... 错误!未定义书签。
三、KILL如何过滤垃圾邮件......................................................................... 错误!未定义书签。
四、KILL邮件安全服务是什么..................................................................... 错误!未定义书签。
五、KILL邮件安全服务的优势..................................................................... 错误!未定义书签。
六、为何选择KILL邮件安全服务................................................................ 错误!未定义书签。
一、垃圾邮件安全状况及危害那些不请自来、不受欢迎的电子邮件,通常被称作“垃圾邮件”。
垃圾邮件被称为Spam,又叫UCE(Unsolicited Commercial Email)。
典型的垃圾邮件形式有:推销产品、恶意骚扰、非法传播、其它来历不明的信件。
垃圾邮件给邮箱用户以及邮箱供应商都带了麻烦以及经济损失,其危害远远超出了公众的认知程度,具体表现为:降低效率。
员工为处理大量无用的垃圾邮件信息浪费时间,导致工作效率下降;危害社会。

Kill杀死进程方法大全名称:kill使用权限:所有使用者使用方式:kill [ -s signal | -p ] [ -a ] pid ...kill -l [ signal ]说明:kill 送出一个特定的信号 (signal) 给行程 id 为 pid 的行程根据该信号而做特定的动作, 若没有指定, 预设是送出终止(TERM) 的信号把计-s (signal) : 其中可用的讯号有 HUP (1), KILL (9), TERM (15), 分别代表着重跑, 砍掉, 结束; 详细的信号可以用 kill -l-p : 印出 pid , 并不送出信号-l (signal) : 列出所有可用的信号名称范例:将 pid 为 323 的行程砍掉 (kill) :kill -9 323将 pid 为 456 的行程重跑 (restart) :kill -HUP 456--------------------------------------------------------------------------------*杀死进程最安全的方法是单纯使用kill命令,不加修饰符,不带标志首先使用ps -ef命令确定要杀死进程的PID,然后输入以下命令:# kill -pid注释:标准的kill命令通常都能达到目的。
终止有问题的进程,并把进程的资源释放给系统。
然而,如果进程启动了子进程,只杀死父进程,子进程仍在运行,因此仍消耗资源。
为了防止这些所谓的“僵尸进程”,应确保在杀死父进程之前,先杀死其所有的子进程。
--------------------------------------------------------------------------------*确定要杀死进程的PID或PPID# ps -ef | grep httpd--------------------------------------------------------------------------------*以优雅的方式结束进程# kill -l PID-l选项告诉kill命令用好像启动进程的用户已注销的方式结束进程。

windows下批量杀死进程-电脑资料有时候由于病毒或其他原因,启动了一系列的进程,并且有时杀了这个,又多了那个,。
使用命令taskkill可将这些进程一下子全部杀光:C:\\Users\\NR>taskkill /F /im frontpg.exe成功:已终止进程 "FRONTPG.EXE",其 PID 为 3732.成功:已终止进程 "FRONTPG.EXE",其 PID 为 24544.成功:已终止进程 "FRONTPG.EXE",其 PID 为 3612.错误:无法终止进程 "FRONTPG.EXE",其 PID 为 8268.原因:操作不被支持。
成功:已终止进程 "FRONTPG.EXE",其 PID 为 7532.成功:已终止进程 "FRONTPG.EXE",其 PID 为 14184.成功:已终止进程 "FRONTPG.EXE",其 PID 为 18384.成功:已终止进程 "FRONTPG.EXE",其 PID 为 16888.成功:已终止进程 "FRONTPG.EXE",其 PID 为 3280.成功:已终止进程 "FRONTPG.EXE",其 PID 为 18660.成功:已终止进程 "FRONTPG.EXE",其 PID 为 26440.成功:已终止进程 "FRONTPG.EXE",其 PID 为 20764.成功:已终止进程 "FRONTPG.EXE",其 PID 为 15572.成功:已终止进程 "FRONTPG.EXE",其 PID 为 4292.成功:已终止进程 "FRONTPG.EXE",其 PID 为 19844.成功:已终止进程 "FRONTPG.EXE",其 PID 为 25036.成功:已终止进程 "FRONTPG.EXE",其 PID 为 13736.成功:已终止进程 "FRONTPG.EXE",其 PID 为 15024.成功:已终止进程 "FRONTPG.EXE",其 PID 为 14948.成功:已终止进程 "FRONTPG.EXE",其 PID 为 23048.成功:已终止进程 "FRONTPG.EXE",其 PID 为 9864.成功:已终止进程 "FRONTPG.EXE",其 PID 为 22948.成功:已终止进程 "FRONTPG.EXE",其 PID 为 14872.成功:已终止进程 "FRONTPG.EXE",其 PID 为 7708.成功:已终止进程 "FRONTPG.EXE",其 PID 为 21956.成功:已终止进程 "FRONTPG.EXE",其 PID 为 21884.成功:已终止进程 "FRONTPG.EXE",其 PID 为 6212.成功:已终止进程 "FRONTPG.EXE",其 PID 为 6948.成功:已终止进程 "FRONTPG.EXE",其 PID 为 17016.成功:已终止进程 "FRONTPG.EXE",其 PID 为 9436.成功:已终止进程 "FRONTPG.EXE",其 PID 为 15808.成功:已终止进程 "FRONTPG.EXE",其 PID 为 14692.成功:已终止进程 "FRONTPG.EXE",其 PID 为 10044.成功:已终止进程 "FRONTPG.EXE",其 PID 为 13520.成功:已终止进程 "FRONTPG.EXE",其 PID 为 11508.成功:已终止进程 "FRONTPG.EXE",其 PID 为 17388.成功:已终止进程 "FRONTPG.EXE",其 PID 为 23544.成功:已终止进程 "FRONTPG.EXE",其 PID 为 13896.成功:已终止进程 "FRONTPG.EXE",其 PID 为 14728.成功:已终止进程 "FRONTPG.EXE",其 PID 为 2996.成功:已终止进程 "FRONTPG.EXE",其 PID 为 4536.成功:已终止进程 "FRONTPG.EXE",其 PID 为 18868.成功:已终止进程 "FRONTPG.EXE",其 PID 为 14124.参数说明:/F 强制终止/IM 进程映像名frontpg.exe 进程名参考:Taskkill命令详解"Tasklist"命令是一个用来显示运行在本地或远程计算机上的所有进程的命令行工具,带有多个执行参数,电脑资料《windows下批量杀死进程》(https://www.)。

KILL服务器的安装步骤1.将安装光盘放入光驱,自动运行2.选择安装语言“简体中文”点击确定3.主菜单点“安装”4.阅读安装声明,点“我接受”,然后继续安装5.阅读第三方许可协议,将滚动条拖到最下,点“我接受”,然后继续安装6.填写用户真实注册信息,(注意:用户注册信息是验证该用户是否可被授权升级的重要信息,请务必填写真实信息,以保证日后的使用正常,如重新安装后,需填入与之前安装注册时填写的相同信息方可正常使用,否则授权信息会提示无效!)公司:XX 名字:XX 姓氏:XX 电子邮件地址:XX电话:XX 密码/重复/密码提示:XX 地址/城市:XX 邮编:0500007.安装许可密钥(这一步一定要连接外网进行注册)8.代理信息:我不通过代理服务器进行连接:打上勾9. 出现安装选项界面,选择“安装KILL8.1”10.选择安装KILL服务器11.点击完成12.重新启动计算机13.双击右下角kill图标14.选择更新-排定-配置更新频率15.点更新-重新分发-勾中重新分发服务器-应用16. 点更新-重新分发-旧组件-勾中最后五项-应用KILL客户端安装步骤1.将安装光盘放入光驱,自动运行2.选择安装语言“简体中文”点击确定3.主菜单点“安装”4.阅读安装声明,点“我接受”,然后继续安装5.阅读第三方许可协议,将滚动条拖到最下,点“我接受”,然后继续安装6.代理信息:我不通过代理服务器进行连接:打上勾7.出现安装选项界面,选择“远程安装工具”,点击“安装/打开”,开始安装。
8.系统提示程序安装路径,点击“完成”后,开始安装9.安装完毕后在“远程安装工具”—“文件”—“修改ICF文件”,选择:系统所在分区才:C:\PROGRAM FILE\CA\InoRemote\Image\Client\inoc6.icf文件(如图41)打开,进行初始化设置。
(必须是C:\PROGRAM FILE\CA\InoRemote\Image\Client\inoc6.icf而不是默认的C:\PROGRAM FILE\CA\InoRemote\Image\data\inoc6.icf)10. 设置管理服务器IP地址:修改Phonehome/serverlist = 实际管理服务器的IP地址,输入|192.168.2.200| 点保存修改License/HostServer = 管理服务器的IP地址,输入192.168.2.200 点保存修改ContentUpdate/bDownloadNow =YES(客户端安装完之后将立即自动升级最新的病毒特征码)修改ContentUpdate/server1 192.168.2.200修改ContentUpdate/server port 将80改为4251111.建立安装包制作自解压安装包a.在已经修改好了inoc6.icf的客户端初始化配置文件的前提下。


使用kill命令终止进程或发送信号在Linux系统中,进程是操作系统中最基本的执行单元。
有时候,我们需要终止某个进程或向其发送信号,以便进行管理或控制。
在Linux中,kill命令就是一个常用的工具,用于终止进程或发送信号。
一、kill命令的基本用法kill命令的基本语法如下:kill [选项] [进程号]其中,选项用于指定kill命令的操作方式,进程号是指要终止或发送信号的进程的唯一标识。
1. 终止进程要终止一个进程,可以使用kill命令加上进程号。
例如,要终止进程号为1234的进程,可以使用以下命令:kill 1234这样,进程号为1234的进程就会被终止运行。
2. 发送信号除了终止进程,kill命令还可以向进程发送信号。
常用的信号有以下几种:- 停止信号(SIGSTOP):将进程暂停执行。
示例命令:kill -STOP 进程号- 终止信号(SIGTERM):正常终止一个进程。
示例命令:kill -TERM 进程号- 强制终止信号(SIGKILL):强制终止一个进程,即使进程无法响应。
示例命令:kill -KILL 进程号- 用户自定义信号(SIGUSR1、SIGUSR2):可以用于用户自定义的操作。
示例命令:kill -USR1 进程号二、kill命令的常见选项除了基本的用法,kill命令还提供了一些选项,用于指定不同的操作方式。
1. -l选项-l选项用于列出所有可用的信号名称和编号。
只需执行以下命令即可:kill -l命令输出将显示所有信号的名称和对应的编号,以供参考。
2. -s选项-s选项用于指定要发送的信号。
可以通过信号名称或信号编号来指定。
例如,要向进程号为1234的进程发送SIGTERM信号,可以使用以下命令:kill -s SIGTERM 1234这样,信号SIGTERM将发送给进程号为1234的进程。
3. -a选项-a选项用于从父进程到子进程递归地发送指定信号。
这在需要终止一组相关联进程时非常有用。
NZZV ]]] QORRZKYZ IT
▲ Ҳ ԟ ԇ
The safer , easier way to help you pass any IT exams.
Exam : 4A0-107
Title :
Version : DEMO
Alcatel-Lucent Quality of Service
1. True of False: A proper end-to-end QoS solution is becoming more of an issue even as more bandwidth is being made available to today's bandwidth-intensive, interactive multimedia applications.
A. True
B. False
Answer: A
2. Which of the following are examples of metrics for QoS?
A. delay, jitter, packet loss
B. latency, FIFO, WRED
C. signal degradation, attenuation, line loss
D. SNR, radial CODEC inversion, latency
E. Inverse Queue Depletion, delay, packet loss
Answer: A
3. Which of the following are Ethernet SAP encapsulation types? Choose all that apply.
A. Null
B. Dot1Q
C. Q-in-Q
D. IPCP
E. BCP-Null
F. BCPdot1.q
G. Frame Relay
Answer: ABC
4. Which of the following are not considered a differentiator/classifier of customer traffic at layer 2 or 3 of the OSI model? Choose all that apply.
A. DSCP
B. 802.1p
C. IP Precedence
D. TCP/UDP Port numbers
E. HTML version
Answer: DE
5. Which of the following statements are true regarding the DSCP bits? Choose 3 answers.
A. The precedence level bits define 4 Assured Forwarding Classes
B. The three least significant bits of the DSCP bits specify the drop probability
C. The 8 bits of the TOS field are used for DSCP
D. To convert DSCP to IP Precedence the three most significant bits are matched
E. DSCP provides for 64 precedence levels with 3 drop probabilities
Answer: ABD
6. Pick from the following list the 3 major components of the QoS features on the Alcatel-Lucent 7750 SR.
A. virtual inflow classification
B. real-time QoS shaping
C. traffic classification
D. 802.1q p-bit rate-limiting
E. buffer memory management
F. traffic scheduling
Answer: CEF
7. The IOM is responsible for which of the tasks listed below? Choose 3 answers.
A. local processing of critical control plane functions
B. IPSec VPN hardware accelerated encryption
C. queuing, scheduling, and buffer management
D. IP/MPLS/MAC forwarding lookup
E. Layer 2 / Layer 3 encapsulation
Answer: CDE
8. Which of the following statement is true with regards to Q-in-Q on the Alcatel-Lucent 7750 SR?
A. Q-in-Q defines a mechanism for encapsulating queued DSCP traffic at the provider edge
B. Q-in-Q is a new protocol that supercedes 802.1p priority-bit mapping in a QoS-aware network
C. The use of either the inner or outer 802.1p bits in the 802.1q frames for QoS classification can be configured on the Alcatel-Lucent 7750 SR
D. Q-in-Q is a protocol which re-encapsulates trunked p-bits in an outer label that is mapped into the EXP bits in an MPLS backbone
E. none of the above
Answer: C
9. Which of the following are not categories of forwarding classes on the Alcatel-Lucent 7750 SR? Choose 3 answers.
A. Real-time
B. Assured
C. Non-conforming
D. High Priority
E. Expedited
Answer: ACE
10. Which of the following are Trusted boundaries by default? Choose 2 answers.
A. An IES SAP
B. A VPLS SAP
C. A network port
D. A VPRN SAP
E. An access port
Answer: CD。