acm english
- 格式:doc
- 大小:63.50 KB
- 文档页数:13

初中毕业演讲稿英文这是一篇由网络搜集整理的关于初中毕业演讲稿英文的文档,希望对你能有帮助。
初中毕业英文演讲稿【一】Good morning,my dear teachers and schoolmates,It’s a great honor for me to make a speech on behalf of the graduating classes.How time flies! Our junior high school lives will come to an end.In the past three years, we’ve had a beautiful school and it provides us with agood study place. Teachers are our friends. They’ve given us interesting lessons and we all love them.We’ve learned a lot from them, not only knowledge but also the way to solve problems in life. Thanks for our teachers’ training, parents’ support and the helpfrom classmates. Without them, we couldn’t have so much wonderful time.At last, we hope our school will become better, our teachers will be healthy forever and all our dreams will come true.Thank you for listening.初中毕业英文演讲稿【二】I take with me the memory of Friday afternoon ACM happy hours, known not for kegs of beer, but rather bowls of rainbow sherbet punch. Over the severalyears that I attended these happy hours they enjoyed varying degrees of popularity, often proportional to the quality and quantity of the accompanying refreshments - but there was always the rainbow sherbert punch.I take with me memories of purple parking permits, the West Campus shuttle, checking my pendaflex, over-due library books, trying to print from cec, lunches on Delmar, friends who slept in their offices, miniature golf in Lopata Hall, The Greenway Talk, division III basketball, and trying to convince Dean Russel that yet another engineering school rule should be changed.Finally, I would like to conclude, not with a memory, but with some advice. What would a graduation speech be without a little advice, right? Anyway, this advice comes in the form of a verse delivered to the 1977 graduating class of Lake Forest College by Theodore Seuss Geisel, better known to the world as Dr. Seuss - Here's how it goes:My uncle ordered popovers from the restaurant's bill of fare. And when they were served, he regarded them with a penetrating stare . . . Then he spoke great Words of Wisdom as he sat there on that chair: "To eat these things," said my uncle, "you must excercise great care. You may swallow down what's solid . . . BUT . . . you must spit out the air!"And . . . as you partake of the world's bill of fare, that's darned good advice to follow. Do a lot of spitting out the hot air. And be careful what you swallow.Thank you.初中毕业英文演讲稿【三】first of all, we must cultivate students' interest in english study. let students in learning to find joy in joy in the interest of interest, found in the determination of decision and perseverance, namely train drivers + + to + perserve = interest. of course started to learn english, don't be too hard. guiding students from the simple, funny, funny began to enable students to find suitable for their interest in learning. and they decide to "light" surveys. and allow students to go wrong, don't pursue every word is correct. ,secondly, the students have interest, help them to plan. watch english materials and listen to english radio, looking for learning environment, life is much, learn english and have much broader, take every chance to exposure to english. in class, students try to speak in english, usually between classmates exchange, encourage students to use english, don't be afraid of making mistakes the wrong. to establish weekly learning new words in the target, the vocabulary, records recorded all sorts of new words and phrases. because learning english must have vocabulary as the foundation, will play a protracted war, remembering words to guerrilla warfare. can make them more "to" surveys.learning english as friends, in different occasions contact might remember, not isolated words and remember its neighbors. it is necessary to guide students to read, this of learning english is very important to have more understanding of western culture and western learning habit, master of language background is also an important way of learning. then two chinese ppc to achieve. we finally achieved the goal ", two surveys to two chinese to spending."finally, let students enjoy happiness in suffering, more study is interesting, from passive to active, change from me to learn to learn.初中毕业英文演讲稿【四】Opportunities and ChallengesFirst, I would like to know, what does your destiny offer you? Happiness, wisdom, a strong body or something else. If I had asked this question to president Nixon, he would probably had said,”Our destiny offers not the cup of despair, but the chalice of oppor tunity.”Needless to say, one of the biggest opportunities given to China is the XX Olympic Games. Till now, we have used two sevenths of the preparation time. How much changes have you seen? New roads, new subway lines, public-exercising equipments with beautiful colors, large blocks of grass fields, and also lots of modern gyms which are under construction.Other than those, there are even more good effects brought to us by the Olympic Games that cannot be seen directly. For example, more and more people will get to know China. I’m sure the mysterious Chinese culture will attract them strongly. And the games will also do good to the economy and environment, for it is gaining the attention of foreign investors and the awareness of environmental protection is being strengthened. What is more, Olympic Games give a unique opportunity to inspire and educate a new generation of Chinese youth with the Olympic values and the Olympic spirit. Now that we have seen so many advances, could you even imagine us losing the holding rights?I’ve already said a lot about the Olympics and China. But I think everyone should use some time to think of this question, ”Does the Olympic Games have any special meaning to you?”For us, I mean the Chinese youth, XX Olympic Games is a tremendous gift. Because what we are waiting for is to do something significant as repaying the love given to us .The society is just like a ship, and in our dreams the captain is waving his hand and saying ”Hey! Come here and take the helm! ”How ch arming his voice is, but we have never heard of it in our true life. This morning, however, when we wake up, we will see the Olympic Games waving its hand. After chewing, most of us will have at least one plan about what to do for the Olympic Games. And mi ne is to be a “comforter” ----that is someone who will give comfort to others.At the end of my speech, I hope all the preparation will go well, and everyone will show their ability to the world. Let us seize opportunities and give a big smile to challenges.。


第一部分本部分共33题,共40分。
在每题列出的四个选项中,选出最符合题目要求的一项。
一、单项填空(每题0.5分,共6分)从下面各题所给的A 、B 、C 、D 四个选项中,选择可以填入空白处的最佳选项。
1. That is my little brother. _____ is only 2 years old. A. Him B. She C. Her D. He2. — Joe, when do you go to bed every day? — I go to bed _____ half past nine. A. in B. on C. at D. to3. — Jack, is the woman in the photo your mum? — No, she _____ my aunt. A. am B. is C. are D. be4. — Amy, what does your father do? — He is _____ art teacher. A. a B. an C. the D. \5. — Which T-shirt do you like, the black one _____ the blue one? — I like the blue one. A. but B. and C. so D. or6. We have a dog. When we call him, he _____ to us. A. runs B. ran C. run D. is running7. — David, is this your schoolbag? — No, it ’s not _____. I t’s Linda ’s. A. my B. mine C. your D. yours8. — _____ is your brother like?— He is active. He plays lots of ball games.A. WhenB. WhoC. WhatD. Where 9. On Sundays, we usually _____ our grandparents.A. visitB. visitingC. visitsD. will visit 10. — Tina, what ’s your favorite subject?— I am good at running. So my favorite subject is _____. A. science B. music C. Chinese D. PE11. — What time is it?— It’s 7:00. It’s time _____.A. get upB. getting upC. to get upD. gets up12. — Excuse me, _____?— Go straight and turn left. It is the second building on your left.A. where is the libraryB. what is on your leftC. where are you fromD. what can we do in the library二、完形填空(每题1分,共8分)阅读下面的短文,掌握其大意,然后从短文后各题所给的A、B、C、D 四个选项中,选择最佳选项。

计算机科学与技术(数字媒体)专业本科学分制培养方案专业名称:计算机科学与技术(数字媒体)专业代码: 080605一、培养目标本专业旨在培养德、智、体、美全面发展,系统地、较好地掌握计算机科学与技术和数字媒体技术的基本理论、基本知识和基本技能与方法,同时具有较高的外语语言基础和应用技能,能把外语与计算机技术很好的结合,适应社会经济发展需要,能够在各类企事业单位的软件研发、管理部门从事软件系统设计与开发、网络媒体设计与媒体综合表现等领域工作的复合型信息技术人才。
二、培养规格(一)知识要求了解我国有关的方针、政策、法规;了解我国国情和英语国家的社会和文化。
掌握计算机程序设计、网络管理与维护、媒体设计与开发、计算机应用和网站设计与管理等基本理论和专业知识。
要求学生的英语技能达到普通高校同类型专业较高水平;懂得文献检索、社会调查、论文写作等科学研究的基本方法;掌握较宽广的人文社科知识,具有文理渗透、学科交叉的知识结构。
(二)素质要求具有良好的思想道德品质、较强的法制观念和诚信意识;较高的人文、科学和艺术修养;较强的现代意识和人际交往意识;科学的思维方法、求实创新精神、专业学科意识、综合分析的素养;健康的体魄和健全的心理素质。
(三)能力要求能综合运用专业知识进行各类软件设计开发与维护,进行网站设计、网络管理、硬件维护和制作新型交互数字媒体作品;能较熟练地使用英语从事有关计算机技术、数字媒体技术应用与服务的工作;具备在各类企事业单位从事研发、维护、应用以及网络媒体表现等工作的能力。
三、学制本专业基本学制为4学年,并实行3-6年弹性学制。
凡依照培养方案提前修完全部课程并取得相应学分,符合毕业条件者,允许提前毕业(修业年限不得少于3年)。
学生在符合有关规定的条件下,可延长在校学习期限,但不得超过两年延长期。
四、毕业与授予学位学生在规定的学制内修满学分,经考核成绩全部合格,发给本科毕业证书,符合学校关于普通本科学生学士授予相关规定,授予理学学士学位。
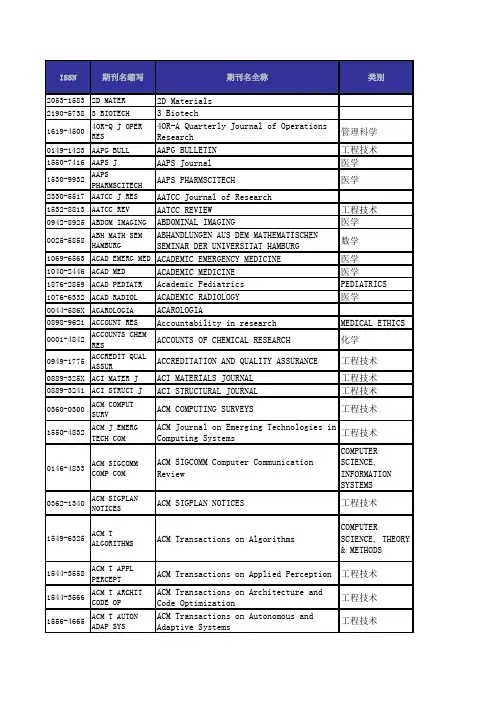
2053-15832D MATER 2D Materials2190-5738 3 BIOTECH 3 Biotech1619-45004OR-Q J OPER RES4OR-A Quarterly Journal of OperationsResearch管理科学0149-1423AAPG BULL AAPG BULLETIN 工程技术1550-7416AAPS J AAPS Journal 医学1530-9932AAPS PHARMSCITECH AAPS PHARMSCITECH 医学2330-5517AATCC J RES AATCC Journal of Research 1532-8813AATCC REV AATCC REVIEW工程技术0942-8925ABDOM IMAGING ABDOMINAL IMAGING医学0025-5858ABH MATH SEM HAMBUABHANDLUNGEN AUS DEM MATHEMATISCHENSEMINAR DER UNIVERSITAT HAMBURG数学1069-6563ACAD EMERG MED ACADEMIC EMERGENCY MEDICINE 医学1040-2446ACAD MED ACADEMIC MEDICINE 医学1876-2859ACAD PEDIATR Academic Pediatrics PEDIATRICS 1076-6332ACAD RADIOL ACADEMIC RADIOLOGY 医学0044-586X ACAROLOGIA ACAROLOGIA 0898-9621ACCOUNT RES Accountability in research MEDICAL ETHICS 0001-4842ACCOUNTS CHEM RES ACCOUNTS OF CHEMICAL RESEARCH 化学0949-1775ACCREDIT QUAL ASSU ACCREDITATION AND QUALITY ASSURANCE 工程技术0889-325X ACI MATER J ACI MATERIALS JOURNAL 工程技术0889-3241ACI STRUCT J ACI STRUCTURAL JOURNAL 工程技术0360-0300ACM COMPUT SURV ACM COMPUTING SURVEYS工程技术1550-4832ACM J EMERG TECH CACM Journal on Emerging Technologies inComputing Systems工程技术0146-4833ACM SIGCOMM COMP CACM SIGCOMM Computer Communication ReviewCOMPUTER SCIENCE,INFORMATION SYSTEMS 0362-1340ACM SIGPLAN NOTICE ACM SIGPLAN NOTICES工程技术1549-6325ACM T ALGORITHMS ACM Transactions on AlgorithmsCOMPUTERSCIENCE, THEORY & METHODS 1544-3558ACM T APPL PERCEPT ACM Transactions on Applied Perception工程技术1544-3566ACM T ARCHIT CODEACM Transactions on Architecture andCode Optimization工程技术1556-4665ACM T AUTON ADAP SACM Transactions on Autonomous andAdaptive Systems工程技术1946-6226ACM T COMPUT EDUC ACM Transactions on Computing Education1529-3785ACM T COMPUT LOG ACM Transactions on Computational Logic 工程技术0734-2071ACM T COMPUT SYST ACM TRANSACTIONS ON COMPUTER SYSTEMS工程技术ISSN 期刊名缩写期刊名全称类别1073-0516ACM T COMPUT-HUM I ACM Transactions on Computer-Human Interaction工程技术0362-5915ACM T DATABASE SYS ACM TRANSACTIONS ON DATABASE SYSTEMS工程技术1084-4309ACM T DES AUTOMATACM TRANSACTIONS ON DESIGN AUTOMATIONOF ELECTRONIC SYSTEMS工程技术1539-9087ACM T EMBED COMPUTACM Transactions on Embedded ComputingSystems工程技术0730-0301ACM T GRAPHIC ACM TRANSACTIONS ON GRAPHICS工程技术1046-8188ACM T INFORM SYST ACM TRANSACTIONS ON INFORMATION SYSTEMS 工程技术1094-9224ACM T INFORM SYSTACM Transactions on Information andSystem Security工程技术2157-6904ACM T INTEL SYST TACM Transactions on Intelligent Systems and Technology COMPUTERSCIENCE,ARTIFICIALINTELLIGENCE1533-5399ACM T INTERNET TEC ACM Transactions on Internet Technology 工程技术1556-4681ACM T KNOWL DISCOVACM Transactions on Knowledge Discovery from Data COMPUTERSCIENCE,INFORMATIONSYSTEMS0098-3500ACM T MATH SOFTWAR ACM TRANSACTIONS ON MATHEMATICALSOFTWARE工程技术1049-3301ACM T MODEL COMPUT ACM Transactions on Modeling andComputer Simulation工程技术1551-6857ACM T MULTIM COMPU ACM Transactions on MultimediaComputing Communications and Applications工程技术0164-0925ACM T PROGR LANG S ACM TRANSACTIONS ON PROGRAMMINGLANGUAGES AND SYSTEMS工程技术1936-7406ACM T RECONFIG TECACM transactions on reconfigurable technology and systems COMPUTERSCIENCE,HARDWARE &ARCHITECTURE1550-4859ACM T SENSOR NETWO ACM Transactions on Sensor Networks 工程技术1049-331XACM T SOFTW ENG ME ACM TRANSACTIONS ON SOFTWAREENGINEERING AND METHODOLOGY工程技术1553-3077ACM T STORAGE ACM transactions on storageCOMPUTER SCIENCE,HARDWARE &ARCHITECTURE1559-1131ACM T WEB ACM Transactions on the Web 工程技术1839-2571ACOUST AUST Acoustics Australia 1063-7710ACOUST PHYS+ACOUSTICAL PHYSICS 物理1944-8244ACS APPL MATER INT ACS Applied Materials & Interfaces 工程技术2373-9878ACS BIOMATER-SCI E ACS Biomaterials-Science & Engineering2155-5435ACS CATAL ACS catalysis CHEMISTRY,PHYSICAL 1554-8929ACS CHEM BIOLACS Chemical Biology生物1948-7193ACS CHEM NEUROSCI ACS Chemical Neuroscience BIOCHEMISTRY &MOLECULAR BIOLOGY 2156-8952ACS COMB SCIACS Combinatorial ScienceCHEMISTRY,APPLIED 2373-8227ACS INFECT DIS ACS Infectious Diseases 2161-1653ACS MACRO LETT ACS Macro Letters化学1948-5875ACS MED CHEM LETT ACS Medicinal Chemistry Letters CHEMISTRY,MEDICINAL 1936-0851ACS NANO ACS Nano工程技术2330-4022ACS PHOTONICSACS Photonics2168-0485ACS SUSTAIN CHEM E ACS Sustainable Chemistry & Engineering CHEMISTRY,MULTIDISCIPLINARY2161-5063ACS SYNTH BIOL ACS Synthetic Biology 生物1091-5397ACSMS HEALTH FIT J ACSMS HEALTH & FITNESS JOURNAL 医学1610-1928ACTA ACUST UNITED ACTA ACUSTICA UNITED WITH ACUSTICA 物理0001-5113ACTA ADRIAT ACTA ADRIATICA 生物0906-4702ACTA AGR SCAND A-A ACTA AGRICULTURAE SCANDINAVICA SECTIONA-ANIMAL SCIENCE农林科学0906-4710ACTA AGR SCAND B-S ACTA AGRICULTURAE SCANDINAVICA SECTIONB-SOIL AND PLANT SCIENCE农林科学0139-3006ACTA ALIMENT HUNG ACTA ALIMENTARIA 农林科学0044-5967ACTA AMAZON ACTA AMAZONICA 0001-5172ACTA ANAESTH SCAND ACTA ANAESTHESIOLOGICA SCANDINAVICA 医学0167-8019ACTA APPL MATH ACTA APPLICANDAE MATHEMATICAE 数学0065-1036ACTA ARITH ACTA ARITHMETICA 数学0094-5765ACTA ASTRONAUT ACTA ASTRONAUTICA 工程技术0001-5237ACTA ASTRONOM ACTA ASTRONOMICA 地学天文1672-9145ACTA BIOCH BIOPH S ACTA BIOCHIMICA ET BIOPHYSICA SINICA 生物0001-527X ACTA BIOCHIM POL ACTA BIOCHIMICA POLONICA 生物1509-409X ACTA BIOENG BIOMEC Acta of Bioengineering and Biomechanics BIOPHYSICS1726-569X ACTA BIOETHActa Bioethica医学0001-5296ACTA BIOL CRACOV BACTA BIOLOGICA CRACOVIENSIA SERIESBOTANICA生物0236-5383ACTA BIOL HUNG ACTA BIOLOGICA HUNGARICA 生物1742-7061ACTA BIOMATER Acta Biomaterialia工程技术0325-2957ACTA BIOQUIM CLIN Acta Bioquimica Clinica Latinoamericana0001-5342ACTA BIOTHEOR ACTA BIOTHEORETICA生物0102-3306ACTA BOT BRAS Acta Botanica Brasilica PLANT SCIENCES 0365-0588ACTA BOT CROAT Acta Botanica Croatica PLANT SCIENCES 1253-8078ACTA BOT GALLICA ACTA BOTANICA GALLICA生物0187-7151ACTA BOT MEX Acta Botanica Mexicana生物0001-5385ACTA CARDIOL ACTA CARDIOLOGICA 医学1011-6842ACTA CARDIOL SIN Acta Cardiologica Sinica 医学0583-6050ACTA CARSOLOGICA ACTA CARSOLOGICA 地学0567-7351ACTA CHIM SINICA ACTA CHIMICA SINICA 化学1318-0207ACTA CHIM SLOV ACTA CHIMICA SLOVENICA 化学0001-5458ACTA CHIR BELG ACTA CHIRURGICA BELGICA医学0001-5415ACTA CHIR ORTHOP TACTA CHIRURGIAE ORTHOPAEDICAE ETTRAUMATOLOGIAE CECHOSLOVACAORTHOPEDICS 1508-1109ACTA CHIROPTEROL ACTA CHIROPTEROLOGICA 生物1233-2356ACTA CHROMATOGR ACTA CHROMATOGRAPHICA 化学0102-8650ACTA CIR BRAS Acta Cirurgica Brasileira 医学1784-3286ACTA CLIN BELG ACTA CLINICA BELGICA 0353-9466ACTA CLIN CROAT Acta Clinica Croatica医学2053-2733ACTA CRYSTALLOGR AActa Crystallographica A-Foundation andAdvances2052-5206ACTA CRYSTALLOGR B Acta Crystallographica Section B-Structural Science Crystal Engineeringand Materials2053-2296ACTA CRYSTALLOGR CActa Crystallographica Section C-Structural Chemistry2059-7983ACTA CRYSTALLOGR DActa Crystallographica Section D-Structural Biology2053-230X ACTA CRYSTALLOGR FActa Crystallographica Section F-Structural Biology Communications1330-027X ACTA DERMATOVENER Acta Dermatovenerologica Croatica 医学0001-5555ACTA DERM-VENEREOL ACTA DERMATO-VENEREOLOGICA 医学0940-5429ACTA DIABETOL ACTA DIABETOLOGICA 医学1841-0987ACTA ENDOCRINOL-BU Acta Endocrinologica-Bucharest医学0374-1036ACTA ENT MUS NAT PActa Entomologica Musei NationalisPragaeENTOMOLOGY 0873-9749ACTA ETHOL ACTA ETHOLOGICA 生物0001-5644ACTA GASTRO-ENT BE ACTA GASTRO-ENTEROLOGICA BELGICA2213-5812ACTA GEOD GEOPHYS Acta Geodaetica et Geophysica GEOCHEMISTRY &GEOPHYSICS 1214-9705ACTA GEODYN GEOMAT Acta Geodynamica et Geomaterialia 地学1581-6613ACTA GEOGR SLOV Acta Geographica Slovenica-GeografskiZbornik地学0001-5709ACTA GEOL POLACTA GEOLOGICA POLONICA地学1000-9515ACTA GEOL SIN-ENGL ACTA GEOLOGICA SINICA-ENGLISH EDITION 地学1895-7455ACTA GEOPHYS Acta Geophysica 1861-1125ACTA GEOTECHActa GeotechnicaENGINEERING,GEOLOGICAL 1854-0171ACTA GEOTECH SLOV Acta Geotechnica Slovenica 地学0001-5792ACTA HAEMATOL-BASE ACTA HAEMATOLOGICA 医学1827-9635ACTA HERPETOLActa HerpetologicaZOOLOGY0065-1281ACTA HISTOCHEM ACTA HISTOCHEMICA 生物0044-5991ACTA HISTOCHEM CYT ACTA HISTOCHEMICA ET CYTOCHEMICA 生物0137-1592ACTA ICHTHYOL PISC Acta Ichthyologica et Piscatoria FISHERIES 0001-5903ACTA INFORM ACTA INFORMATICA工程技术1359-6454ACTA MATER ACTA MATERIALIA工程技术0168-9673ACTA MATH APPL SINActa Mathematicae Applicatae Sinica-English Series数学0236-5294ACTA MATH HUNG ACTA MATHEMATICA HUNGARICA 数学0252-9602ACTA MATH SCI ACTA MATHEMATICA SCIENTIA数学1439-8516ACTA MATH SIN ACTA MATHEMATICA SINICA-ENGLISH SERIES 数学0001-5962ACTA MATH-DJURSHOL ACTA MATHEMATICA 数学0001-5970ACTA MECH ACTA MECHANICA物理0567-7718ACTA MECH SINICA-P ACTA MECHANICA SINICA 物理0894-9166ACTA MECH SOLIDA S ACTA MECHANICA SOLIDA SINICA 物理0386-300X ACTA MED OKAYAMA ACTA MEDICA OKAYAMA 医学0393-6384ACTA MEDICA MEDITE Acta Medica Mediterranea1646-0758ACTA MEDICA PORT Acta médica portuguesa MEDICINE,GENERAL &INTERNAL 0412-1961ACTA METALL SIN ACTA METALLURGICA SINICA 工程技术1006-7191ACTA METALL SIN-ENActa Metallurgica Sinica (EnglishLetters)METALLURGY &METALLURGICAL ENGINEERING 0894-0525ACTA METEOROL SIN Acta Meteorologica Sinica地学1217-8950ACTA MICROBIOL IMM Acta Microbiologica et Immunologica IMMUNOLOGY 0798-4545ACTA MICROSC1335-1788ACTA MONTAN SLOVAC Acta Montanistica Slovaca 地学2075-8251ACTA NATURAE Acta Naturae农林科学0065-1400ACTA NEUROBIOL EXP ACTA NEUROBIOLOGIAE EXPERIMENTALIS 医学0001-6268ACTA NEUROCHIR ACTA NEUROCHIRURGICA 医学0300-9009ACTA NEUROL BELG ACTA NEUROLOGICA BELGICA 医学0001-6314ACTA NEUROL SCAND ACTA NEUROLOGICA SCANDINAVICA 医学0001-6322ACTA NEUROPATHOL ACTA NEUROPATHOLOGICA 医学1601-5215ACTA NEUROPSYCHIAT ACTA NEUROPSYCHIATRICA NEUROSCIENCES 0962-4929ACTA NUMER ACTA NUMERICA0001-6349ACTA OBSTET GYN SCACTA OBSTETRICIA ET GYNECOLOGICASCANDINAVICA医学0253-505X ACTA OCEANOL SIN ACTA OCEANOLOGICA SINICA 地学0001-6357ACTA ODONTOL SCAND ACTA ODONTOLOGICA SCANDINAVICA医学1146-609X ACTA OECOLACTA OECOLOGICA-INTERNATIONAL JOURNALOF ECOLOGY环境科学0284-186X ACTA ONCOL ACTA ONCOLOGICA医学1755-375X ACTA OPHTHALMOL ACTA OPHTHALMOLOGICA 医学0001-6454ACTA ORNITHOL ACTA ORNITHOLOGICA 生物1745-3674ACTA ORTHOP Acta Orthopaedica医学0001-6462ACTA ORTHOP BELG Acta Orthopaedica Belgica 医学1017-995X ACTA ORTHOP TRAUMAActa Orthopaedica et Traumatologica TurcicaORTHOPEDICS 1413-7852ACTA ORTOP BRAS Acta ortopedica brasileira Orthopedics0001-6489ACTA OTO-LARYNGOL ACTA OTO-LARYNGOLOGICA医学0392-100X ACTA OTORHINOLARYN Acta Otorhinolaryngologica Italica OTORHINOLARYNGO LOGY 0803-5253ACTA PAEDIATR ACTA PAEDIATRICA医学0567-7920ACTA PALAEONTOL PO ACTA PALAEONTOLOGICA POLONICA 地学1230-2821ACTA PARASITOL ACTA PARASITOLOGICA 医学0103-2100ACTA PAUL ENFERM Acta Paulista de Enfermagem NURSING 1000-0569ACTA PETROL SIN ACTA PETROLOGICA SINICAGEOLOGY1330-0075ACTA PHARMACEUT Acta Pharmaceutica PHARMACOLOGY &PHARMACY 1671-4083ACTA PHARMACOL SIN ACTA PHARMACOLOGICA SINICA 医学0587-4246ACTA PHYS POL A ACTA PHYSICA POLONICA A 物理0587-4254ACTA PHYS POL B ACTA PHYSICA POLONICA B 物理1000-3290ACTA PHYS SIN-CH E ACTA PHYSICA SINICA 物理0323-0465ACTA PHYS SLOVACA ACTA PHYSICA SLOVACA 物理1000-6818ACTA PHYS-CHIM SIN ACTA PHYSICO-CHIMICA SINICA 化学1748-1708ACTA PHYSIOL Acta Physiologica医学0231-424X ACTA PHYSIOL HUNG ACTA PHYSIOLOGICA HUNGARICA 医学0137-5881ACTA PHYSIOL PLANT ACTA PHYSIOLOGIAE PLANTARUM 生物0001-6837ACTA POL PHARM ACTA POLONIAE PHARMACEUTICA 医学1000-3304ACTA POLYM SIN ACTA POLYMERICA SINICA 化学1785-8860ACTA POLYTECH HUNG ACTA POLYTECHNICA HUNGARICA 0065-1583ACTA PROTOZOOL ACTA PROTOZOOLOGICA 生物0001-690X ACTA PSYCHIAT SCAN ACTA PSYCHIATRICA SCANDINAVICA 医学0284-1851ACTA RADIOL ACTA RADIOLOGICA 医学0303-464X ACTA REUMATOL PORT Acta Reumatologica Portuguesa医学1644-0692ACTA SCI POL-HORTOActa Scientiarum Polonorum-HortorumCultus农林科学1678-0345ACTA SCI VETActa Scientiae VeterinariaeVETERINARY SCIENCES 1807-8621ACTA SCI-AGRON Acta Scientiarum. Agronomy AGRONOMY 1806-2563ACTA SCI-TECHNOL ACTA SCIENTIARUM-TECHNOLOGY综合性期刊0001-6977ACTA SOC BOT POL ACTA SOCIETATIS BOTANICORUM POLONIAE 生物0001-7051ACTA THERIOL ACTA THERIOLOGICA生物0001-706X ACTA TROP ACTA TROPICA医学0001-7213ACTA VET BRNO ACTA VETERINARIA BRNO农林科学0236-6290ACTA VET HUNG ACTA VETERINARIA HUNGARICA 农林科学0044-605X ACTA VET SCAND ACTA VETERINARIA SCANDINAVICA 农林科学0567-8315ACTA VET-BEOGRAD ACTA VETERINARIA-BEOGRAD 农林科学0001-723X ACTA VIROL ACTA VIROLOGICA医学1217-8837ACTA ZOOL ACAD SCIACTA ZOOLOGICA ACADEMIAE SCIENTIARUMHUNGARICAE生物0324-0770ACTA ZOOL BULGAR ACTA ZOOLOGICA BULGARICA ZOOLOGY0001-7272ACTA ZOOL-STOCKHOL ACTA ZOOLOGICA生物1139-9287ACTAS ESP PSIQUIAT ACTAS ESPANOLAS DE PSIQUIATRIA 医学0210-4806ACTAS UROL ESP Actas Urologicas Espanolas UROLOGY &NEPHROLOGY 0964-5284ACUPUNCT MEDAcupuncture in MedicineINTEGRATIVE &COMPLEMENTARY MEDICINE 0360-1293ACUPUNCTURE ELECTR ACUPUNCTURE & ELECTRO-THERAPEUTICS RESEARCH医学1570-8705AD HOC NETW Ad Hoc Networks 工程技术1551-9899AD HOC SENS WIREL Ad Hoc & Sensor Wireless Networks 工程技术1280-8571ADANSONIA ADANSONIA 生物1059-7123ADAPT BEHAV ADAPTIVE BEHAVIOR 工程技术0736-5829ADAPT PHYS ACT Q ADAPTED PHYSICAL ACTIVITY QUARTERLY 医学0306-4603ADDICT BEHAV ADDICTIVE BEHAVIORS 医学1355-6215ADDICT BIOL ADDICTION BIOLOGY 0965-2140ADDICTION ADDICTION医学0214-4840ADICCIONESAdiccionesSUBSTANCE ABUSE 0263-6174ADSORPT SCI TECHNO ADSORPTION SCIENCE & TECHNOLOGY 工程技术0929-5607ADSORPTION ADSORPTION-JOURNAL OF THE INTERNATIONALADSORPTION SOCIETY工程技术0065-2113ADV AGRON ADVANCES IN AGRONOMY农林科学0301-5556ADV ANAT EMBRYOL CADVANCES IN ANATOMY EMBRYOLOGY AND CELLBIOLOGY生物1072-4109ADV ANAT PATHOL ADVANCES IN ANATOMIC PATHOLOGY 医学1743-6753ADV APPL CERAM Advances in Applied Ceramics工程技术0188-7009ADV APPL CLIFFORD Advances in Applied Clifford Algebras 数学0196-8858ADV APPL MATH ADVANCES IN APPLIED MATHEMATICS数学2070-0733ADV APPL MATH MECHAdvances in Applied Mathematics andMechanicsMATHEMATICS,APPLIED 0065-2156ADV APPL MECH ADVANCES IN APPLIED MECHANICS 工程技术0065-2164ADV APPL MICROBIOL ADVANCES IN APPLIED MICROBIOLOGY 生物0001-8678ADV APPL PROBAB ADVANCES IN APPLIED PROBABILITY数学1687-7969ADV ASTRON Advances in AstronomyASTRONOMY &ASTROPHYSICS 0256-1530ADV ATMOS SCIADVANCES IN ATMOSPHERIC SCIENCES 地学1049-250X ADV ATOM MOL OPT PADVANCES IN ATOMIC MOLECULAR ANDOPTICAL PHYSICS物理0724-6145ADV BIOCHEM ENG BIADVANCES IN BIOCHEMICAL ENGINEERING /BIOTECHNOLOGY工程技术0065-2296ADV BOT RES Advances in Botanical Research生物1864-8258ADV CALC VARAdvances in Calculus of VariationsMATHEMATICS,APPLIED 0065-230X ADV CANCER RES ADVANCES IN CANCER RESEARCH医学0065-2318ADV CARBOHYD CHEM ADVANCES IN CARBOHYDRATE CHEMISTRY ANDBIOCHEMISTRY生物0360-0564ADV CATAL ADVANCES IN CATALYSIS 化学0951-7197ADV CEM RES ADVANCES IN CEMENT RESEARCH 工程技术0065-2385ADV CHEM PHYS Advances in Chemical PhysicsPHYSICS,ATOMIC,MOLECULAR &CHEMICAL0065-2415ADV CHROMATOGR Advances in chromatography 1548-5595ADV CHRONIC KIDNEY ADVANCES IN CHRONIC KIDNEY DISEASE 医学0065-2423ADV CLIN CHEM ADVANCES IN CLINICAL CHEMISTRY 医学1899-5276ADV CLIN EXP MED Advances in Clinical and ExperimentalMedicineMEDICINE,RESEARCH &EXPERIMENTAL0001-8686ADV COLLOID INTERF ADVANCES IN COLLOID AND INTERFACESCIENCE化学0219-5259ADV COMPLEX SYST ADVANCES IN COMPLEX SYSTEMS 综合性期刊0963-6935ADV COMPOS LETT ADVANCED COMPOSITES LETTERS 0924-3046ADV COMPOS MATER ADVANCED COMPOSITE MATERIALS 工程技术0065-2458ADV COMPUT ADVANCES IN COMPUTERS 工程技术1019-7168ADV COMPUT MATH ADVANCES IN COMPUTATIONAL MATHEMATICS 数学1687-8108ADV COND MATTER PH Advances in Condensed Matter Physics PHYSICS,CONDENSED MATTER1862-5347ADV DATA ANAL CLASAdvances in Data Analysis andClassificationSTATISTICS &PROBABILITY 1687-1847ADV DIFFER EQU-NY Advances in Difference Equations MATHEMATICS,APPLIED1079-9389ADV DIFFERENTIAL E BULLETIN OF SYMBOLIC LOGIC MATHEMATICS,APPLIED 0169-409X ADV DRUG DELIVER R ADVANCED DRUG DELIVERY REVIEWS医学0065-2504ADV ECOL RESADVANCES IN ECOLOGICAL RESEARCH环境科学1582-7445ADV ELECTR COMPUTAdvances in Electrical and ComputerEngineering工程技术2199-160X ADV ELECTRON MATER Advanced Electronic Materials1614-6832ADV ENERGY MATER Advanced Energy Materials CHEMISTRY,PHYSICAL 1474-0346ADV ENG INFORM ADVANCED ENGINEERING INFORMATICS 工程技术1438-1656ADV ENG MATER ADVANCED ENGINEERING MATERIALS 工程技术0965-9978ADV ENG SOFTW ADVANCES IN ENGINEERING SOFTWARE工程技术0065-2598ADV EXP MED BIOLAdvances in Experimental Medicine andBiology1616-301X ADV FUNCT MATER ADVANCED FUNCTIONAL MATERIALS 工程技术0065-2660ADV GENET ADVANCES IN GENETICS 生物1615-715XADV GEOM ADVANCES IN GEOMETRY数学0065-2687ADV GEOPHYS Advances in GeophysicsGEOSCIENCES,MULTIDISCIPLINA RY 1382-4996ADV HEALTH SCI EDU ADVANCES IN HEALTH SCIENCES EDUCATION 医学2192-2640ADV HEALTHC MATER Advanced healthcare materials 工程技术0065-2725ADV HETEROCYCL CHE ADVANCES IN HETEROCYCLIC CHEMISTRY 化学1687-7357ADV HIGH ENERGY PH Advances in High Energy PhysicsPHYSICS,PARTICLES &FIELDS 0065-2776ADV IMMUNOL ADVANCES IN IMMUNOLOGY医学0898-8838ADV INORG CHEM ADVANCES IN INORGANIC CHEMISTRY 化学0065-2806ADV INSECT PHYSIOL ADVANCES IN INSECT PHYSIOLOGY生物0065-2881ADV MAR BIOL Advances in Marine BiologyMARINE &FRESHWATER BIOLOGY 0935-9648ADV MATERADVANCED MATERIALS 工程技术2196-7350ADV MATER INTERFAC Advanced Materials Interfaces 0882-7958ADV MATER PROCESS ADVANCED MATERIALS & PROCESSES工程技术1687-8434ADV MATER SCI ENGAdvances in Materials Science andEngineeringMATERIALS SCIENCE,MULTIDISCIPLINA RY 0001-8708ADV MATH ADVANCES IN MATHEMATICS 数学1930-5346ADV MATH COMMUNAdvances in Mathematics ofCommunications工程技术1687-9120ADV MATH PHYS Advances in Mathematical Physics 数学1687-8132ADV MECH ENG Advances in Mechanical Engineering 工程技术1896-1126ADV MED SCI-POLAND Advances in Medical Sciences 医学1687-9309ADV METEOROL Advances in Meteorology 地学天文0065-2911ADV MICROB PHYSIOL ADVANCES IN MICROBIAL PHYSIOLOGY生物2043-6254ADV NAT SCI-NANOSCAdvances in Natural Sciences-Nanoscience and Nanotechnology1536-0903ADV NEONAT CARE Advances in Neonatal Care 2191-9496ADV NONLINEAR ANAL Advances in Nonlinear Analysis 1536-1365ADV NONLINEAR STUD ADVANCED NONLINEAR STUDIES 数学0161-9268ADV NURS SCI ADVANCES IN NURSING SCIENCE医学2161-8313ADV NUTRAdvances in nutrition (Bethesda, Md.)医学2195-1071ADV OPT MATER Advanced Optical MaterialsMATERIALS SCIENCE,MULTIDISCIPLINA RY 1943-8206ADV OPT PHOTONICS Advances in Optics and Photonics OPTICS 0065-3055ADV ORGANOMET CHEM ADVANCES IN ORGANOMETALLIC CHEMISTRY 化学0065-308X ADV PARASIT ADVANCES IN PARASITOLOGY医学0001-8732ADV PHYSADVANCES IN PHYSICS物理0065-3160ADV PHYS ORG CHEM ADVANCES IN PHYSICAL ORGANIC CHEMISTRY 化学1043-4046ADV PHYSIOL EDUC ADVANCES IN PHYSIOLOGY EDUCATION 医学0065-3195ADV POLYM SCI ADVANCES IN POLYMER SCIENCE化学0730-6679ADV POLYM TECH ADVANCES IN POLYMER TECHNOLOGY 工程技术0921-8831ADV POWDER TECHNOL ADVANCED POWDER TECHNOLOGY工程技术1854-6250ADV PROD ENG MANAGAdvances in Production Engineering &Management0065-3276ADV QUANTUM CHEM ADVANCES IN QUANTUM CHEMISTRY 化学0169-1864ADV ROBOTICS ADVANCED ROBOTICS 工程技术2198-3844ADV SCI Advanced Science 1527-7941ADV SKIN WOUND CAR Advances in Skin & Wound Care DERMATOLOGY 0273-1177ADV SPACE RES ADVANCES IN SPACE RESEARCH地学天文1816-112X ADV STEEL CONSTR Advanced Steel Construction CONSTRUCTION &BUILDING TECHNOLOGY 1369-4332ADV STRUCT ENG ADVANCES IN STRUCTURAL ENGINEERING 工程技术0065-3454ADV STUD BEHAV ADVANCES IN THE STUDY OF BEHAVIOR 医学1615-4150ADV SYNTH CATAL ADVANCED SYNTHESIS & CATALYSIS 化学1095-0761ADV THEOR MATH PHY Advances in Theoretical and Mathematical Physics 物理0741-238X ADV THER ADVANCES IN THERAPY医学0972-5768ADV VIB ENGADVANCES IN VIBRATION ENGINEERINGENGINEERING,MECHANICAL 0309-1708ADV WATER RESOUR ADVANCES IN WATER RESOURCES 环境科学1875-9637AEOLIAN RESAeolian ResearchGEOGRAPHY,PHYSICAL 0001-9054AEQUATIONES MATH Aequationes Mathematicae MATHEMATICS,APPLIED 0393-5965AEROBIOLOGIA AEROBIOLOGIA环境科学0001-9240AERONAUT JAERONAUTICAL JOURNAL工程技术1680-8584AEROSOL AIR QUAL R Aerosol and air quality research ENVIRONMENTAL SCIENCES 0278-6826AEROSOL SCI TECH AEROSOL SCIENCE AND TECHNOLOGY 环境科学2375-6314AEROSP MED HUM PER Aerospace Medicine and HumanPerformance1270-9638AEROSP SCI TECHNOL AEROSPACE SCIENCE AND TECHNOLOGY 工程技术0740-722X AEROSPACE AM AEROSPACE AMERICA 工程技术0364-216X AESTHET PLAST SURG AESTHETIC PLASTIC SURGERY 医学1090-820X AESTHET SURG J Aesthetic Surgery JournalSURGERY 1434-8411AEU-INT J ELECTRONAEU-INTERNATIONAL JOURNAL OFELECTRONICS AND COMMUNICATIONS工程技术0001-9704AFINIDAD AFINIDAD 化学1021-3589AFR ENTOMOL AFRICAN ENTOMOLOGY生物1680-6905AFR HEALTH SCI African Health SciencesMEDICINE,GENERAL &INTERNAL1681-5556AFR INVERTEBR AFRICAN INVERTEBRATES生物1608-5914AFR J AQUAT SCI African Journal of Aquatic ScienceMARINE &FRESHWATER BIOLOGY 0141-6707AFR J ECOLAFRICAN JOURNAL OF ECOLOGY环境科学2156-4574AFR J HERPETOL AFRICAN JOURNAL OF HERPETOLOGY ZOOLOGY 1814-232X AFR J MAR SCI AFRICAN JOURNAL OF MARINE SCIENCE生物1022-0119AFR J RANGE FOR SCAfrican Journal of Range and ForageScienceECOLOGY0189-6016AFR J TRADIT COMPL African Journal of TraditionalComplementary and Alternative Medicines医学2305-7963AFR NAT HIST African Natural History1562-7020AFR ZOOL AFRICAN ZOOLOGY 生物0161-9152AGE AGE 医学0002-0729AGE AGEING AGE AND AGEING医学1568-1637AGEING RES REV AGEING RESEARCH REVIEWS 医学0096-140X AGGRESSIVE BEHAV AGGRESSIVE BEHAVIOR 医学1474-9718AGING CELL AGING CELL生物1594-0667AGING CLIN EXP RESAGING CLINICAL AND EXPERIMENTALRESEARCH医学2152-5250AGING DIS Aging and Disease 1368-5538AGING MALE Aging Male 医学1360-7863AGING MENT HEALTH AGING & MENTAL HEALTH 医学1945-4589AGING-US Aging CELL BIOLOGY 0169-5150AGR ECON-BLACKWELL AGRICULTURAL ECONOMICS管理科学0139-570X AGR ECON-CZECHAgricultural Economics-ZemedelskaEkonomikaAGRICULTURAL ECONOMICS &POLICY 0167-8809AGR ECOSYST ENVIRO AGRICULTURE ECOSYSTEMS & ENVIRONMENT 环境科学1459-6067AGR FOOD SCI AGRICULTURAL AND FOOD SCIENCE农林科学1461-9555AGR FOREST ENTOMOL AGRICULTURAL AND FOREST ENTOMOLOGY 农林科学0168-1923AGR FOREST METEORO AGRICULTURAL AND FOREST METEOROLOGY 农林科学0002-1482AGR HIST AGRICULTURAL HISTORY农林科学0889-048X AGR HUM VALUES AGRICULTURE AND HUMAN VALUES 农林科学0308-521X AGR SYST AGRICULTURAL SYSTEMS 农林科学0378-3774AGR WATER MANAGE AGRICULTURAL WATER MANAGEMENT农林科学1663-7852AGRARFORSCH SCHWEI AGRARFORSCH SCHWEIZAGRICULTURE,MULTIDISCIPLINA RY0303-1853AGREKON AgrekonAGRICULTURAL ECONOMICS &POLICY 0742-4477AGRIBUSINESSAgribusiness农林科学1722-6996AGRO FOOD IND HI T AGRO FOOD INDUSTRY HI-TECH 工程技术0002-1857AGROCHIMICA AGROCHIMICA农林科学1405-3195AGROCIENCIA-MEXICO AGROCIENCIA 农林科学2168-3565AGROECOL SUST FOODAgroecology and Sustainable FoodSystemsAGRICULTURE,MULTIDISCIPLINA RY0167-4366AGROFOREST SYST AGROFORESTRY SYSTEMS农林科学0002-1962AGRON J AGRONOMY JOURNAL农林科学1774-0746AGRON SUSTAIN DEV Agronomy for Sustainable Development 农林科学0921-7126AI COMMUN AI COMMUNICATIONS工程技术0890-0604AI EDAM AI EDAM-ARTIFICIAL INTELLIGENCE FORENGINEERING DESIGN ANALYSIS AND MANUFAC工程技术0738-4602AI MAG AI MAGAZINE工程技术0001-1452AIAA J AIAA JOURNAL 工程技术0001-1541AICHE J AICHE JOURNAL 工程技术0269-9370AIDS AIDS 医学1087-2914AIDS PATIENT CARE AIDS PATIENT CARE AND STDS 医学0889-2229AIDS RES HUM RETRO AIDS RESEARCH AND HUMAN RETROVIRUSES医学1742-6405AIDS RES THER AIDS Research and Therapy INFECTIOUS DISEASES 1139-6121AIDS REV AIDS REVIEWS 医学2158-3226AIP ADVAIP AdvancesNANOSCIENCE &NANOTECHNOLOGY 1873-9318AIR QUAL ATMOS HLT Air Quality, Atmosphere and Health ENVIRONMENTAL SCIENCES 1748-8842AIRCR ENG AEROSP TAIRCRAFT ENGINEERING AND AEROSPACETECHNOLOGY工程技术1608-5906AJAR-AFR J AIDS RE AJAR-African Journal of AIDS Research 医学0341-051X AKTUEL RHEUMATOL AKTUELLE RHEUMATOLOGIE 医学0001-7868AKTUEL UROL AKTUELLE UROLOGIE医学0311-5518ALCHERINGA ALCHERINGA 地学0741-8329ALCOHOL ALCOHOL 医学0735-0414ALCOHOL ALCOHOLISM ALCOHOL AND ALCOHOLISM医学0145-6008ALCOHOL CLIN EXP RALCOHOLISM-CLINICAL AND EXPERIMENTALRESEARCH医学0002-5100ALDRICHIM ACTA ALDRICHIMICA ACTA化学1980-0436ALEA-LAT AM J PROB Latin American Journal of Probability and Mathematical Statistics STATISTICS &PROBABILITY 1226-2617ALGAE-SEOUL ALGAE2211-9264ALGAL RES Algal Research-Biomass Biofuels and BioproductsBIOTECHNOLOGY &APPLIEDMICROBIOLOGY 1005-3867ALGEBR COLLOQALGEBRA COLLOQUIUM数学1472-2739ALGEBR GEOM TOPOL Algebraic and Geometric Topology 数学0002-5232ALGEBR LOG+Algebra and Logic 数学1937-0652ALGEBR NUMBER THEO Algebra and Number TheoryMATHEMATICS1386-923X ALGEBR REPRESENT T ALGEBRAS AND REPRESENTATION THEORY数学0002-5240ALGEBR UNIVALGEBRA UNIVERSALIS 数学1748-7188ALGORITHM MOL BIOL Algorithms for Molecular Biology 生物0178-4617ALGORITHMICA ALGORITHMICA工程技术0269-2813ALIMENT PHARM THER ALIMENTARY PHARMACOLOGY & THERAPEUTICS 医学0971-4693ALLELOPATHY J ALLELOPATHY JOURNAL农林科学0301-0546ALLERGOL IMMUNOPAT ALLERGOLOGIA ET IMMUNOPATHOLOGIA 医学1323-8930ALLERGOL INT ALLERGOLOGY INTERNATIONAL 0344-5062ALLERGOLOGIE ALLERGOLOGIE 医学0105-4538ALLERGY ALLERGY医学1710-1484ALLERGY ASTHMA CL Allergy Asthma and Clinical Immunology2092-7355ALLERGY ASTHMA IMM The American Academy of Allergy Asthmaand ImmunologyALLERGY 1088-5412ALLERGY ASTHMA PRO ALLERGY AND ASTHMA PROCEEDINGS 医学0002-5852ALLG FORST JAGDZTG ALLGEMEINE FORST UND JAGDZEITUNG 农林科学1664-2201ALPINE BOT Alpine BotanyPLANT SCIENCES 1078-6791ALTERN THER HEALTHAlternative therapies in health and medicineINTEGRATIVE &COMPLEMENTARY MEDICINE 1868-596X ALTEX-ALTERN ANIMALTEX-ALTERNATIVES TO ANIMAL EXPERIMENTATIONMEDICINE,RESEARCH &EXPERIMENTAL 0893-0341ALZ DIS ASSOC DIS ALZHEIMER DISEASE & ASSOCIATED DISORDERS医学1552-5260ALZHEIMERS DEMENT Alzheimers & Dementia 医学1758-9193ALZHEIMERS RES THE Alzheimer\'s Research and Therapy 医学0002-7685AM BIOL TEACH The American Biology Teacher BIOLOGY 0002-7812AM CERAM SOC BULL AMERICAN CERAMIC SOCIETY BULLETIN 工程技术0002-838X AM FAM PHYSICIAN AMERICAN FAMILY PHYSICIAN 医学0002-8444AM FERN J AMERICAN FERN JOURNAL 生物0002-8703AM HEART J AMERICAN HEART JOURNAL医学0002-9092AM J AGR ECONAMERICAN JOURNAL OF AGRICULTURALECONOMICS管理科学1533-3175AM J ALZHEIMERS DIAmerican Journal of Alzheimer\'sDisease and other DementiasGERIATRICS &GERONTOLOGY 1059-0889AM J AUDIOLAmerican Journal of AudiologyAUDIOLOGY &SPEECH-LANGUAGE PATHOLOGY 1526-5161AM J BIOETHICS AMERICAN JOURNAL OF BIOETHICS 社会科学0002-9122AM J BOT AMERICAN JOURNAL OF BOTANY 生物2156-6976AM J CANCER RES American Journal of Cancer ResearchONCOLOGY 0002-9149AM J CARDIOLAMERICAN JOURNAL OF CARDIOLOGY医学1175-3277AM J CARDIOVASC DRAmerican Journal of CardiovascularDrugs医学0192-415X AM J CHINESE MED AMERICAN JOURNAL OF CHINESE MEDICINE 医学1175-0561AM J CLIN DERMATOLAMERICAN JOURNAL OF CLINICALDERMATOLOGY医学0002-9165AM J CLIN NUTR AMERICAN JOURNAL OF CLINICAL NUTRITION 医学0277-3732AM J CLIN ONCOL-CAAMERICAN JOURNAL OF CLINICAL ONCOLOGY-CANCER CLINICAL TRIALS医学0002-9173AM J CLIN PATHOL AMERICAN JOURNAL OF CLINICAL PATHOLOGY 医学1062-3264AM J CRIT CARE AMERICAN JOURNAL OF CRITICAL CARE 医学0894-8275AM J DENT AMERICAN JOURNAL OF DENTISTRY 医学0193-1091AM J DERMATOPATH AMERICAN JOURNAL OF DERMATOPATHOLOGY 医学0095-2990AM J DRUG ALCOHOLAMERICAN JOURNAL OF DRUG AND ALCOHOLABUSESUBSTANCE ABUSE 0735-6757AM J EMERG MED AMERICAN JOURNAL OF EMERGENCY MEDICINE 医学0002-9254AM J ENOL VITICULT AMERICAN JOURNAL OF ENOLOGY AND VITICULTURE农林科学0002-9262AM J EPIDEMIOL AMERICAN JOURNAL OF EPIDEMIOLOGY医学0195-7910AM J FOREN MED PATAMERICAN JOURNAL OF FORENSIC MEDICINEAND PATHOLOGY医学0002-9270AM J GASTROENTEROL AMERICAN JOURNAL OF GASTROENTEROLOGY医学1064-7481AM J GERIAT PSYCHIAMERICAN JOURNAL OF GERIATRICPSYCHIATRY医学1079-2082AM J HEALTH-SYST PAMERICAN JOURNAL OF HEALTH-SYSTEMPHARMACY医学0361-8609AM J HEMATOL AMERICAN JOURNAL OF HEMATOLOGY医学1049-9091AM J HOSP PALLIAT American Journal of Hospice andPalliative MedicineHEALTH CARE SCIENCES &SERVICES 1042-0533AM J HUM BIOLAMERICAN JOURNAL OF HUMAN BIOLOGY生物0002-9297AM J HUM GENET AMERICAN JOURNAL OF HUMAN GENETICS 生物0895-7061AM J HYPERTENS AMERICAN JOURNAL OF HYPERTENSION医学0271-3586AM J IND MEDAMERICAN JOURNAL OF INDUSTRIAL MEDICINE 医学0196-6553AM J INFECT CONTRO AMERICAN JOURNAL OF INFECTION CONTROL 医学0272-6386AM J KIDNEY DIS AMERICAN JOURNAL OF KIDNEY DISEASES 医学1088-0224AM J MANAG CARE AMERICAN JOURNAL OF MANAGED CARE 医学0002-9327AM J MATH AMERICAN JOURNAL OF MATHEMATICS数学0002-9343AM J MEDAMERICAN JOURNAL OF MEDICINE医学1552-4825AM J MED GENET AAMERICAN JOURNAL OF MEDICAL GENETICSPART A生物1552-4841AM J MED GENET BAMERICAN JOURNAL OF MEDICAL GENETICSPART B-NEUROPSYCHIATRIC GENETICS 医学1552-4868AM J MED GENET CAMERICAN JOURNAL OF MEDICAL GENETICSPART C-SEMINARS IN MEDICAL GENETICS医学。

英文简历的模板3篇 随着世界经济全球化的加剧,人们的职业发展道路越来越国际化,对于求职者来说,一份好的英文简历是非常重要的。以下是店铺整理的英文简历的模板3篇,以供大家参考。 英文简历的模板一: Name: Mr. Nationality: China Current residence: Guangzhou, China: Han Domicile: Heyuan stature: 175 cm 70 kg Job search intention and work experience Personnel types: ordinary job Position: electrician, Work Experience: 3 Job Title: Intermediate Job type: Full-time Date Available: Anytime Salary requirements :3500 - 5000 hope Working Area: Guangzhou Work Experience Company Name: New XX company and end date: 2010.1 ~ 2013-05 Positions: Head of Engineering Educational Background Graduated: XXX Technical College Highest Level of Education: College Graduation date :2010 -07-01 By Major: equipment maintenance Language skills Foreign Language: General Mandarin level: Average Cantonese: Good Self-evaluation I have in the property industrial park, restaurants, construction sites and other companies working to quickly adapt to the work environment, responsibilities strong, complete tasks, work carefully, to obey the unit arrangement can be hard, hope to have the opportunity to jointly development! 英文简历的模板二: Basic information: Name: Gender: Male Age: 21 Nationality: Chinese Residence: Guangdong - Huizhou height and weight: 178cm 60KG Marital status: Single Education: Bachelor School: Hunan University Major: Computer Science and Technology Current residence: Hunan - Zhuzhou political landscape: Komsomolets IT Skills: 1): Familiar with C / C + +,, proficient in Linux environment, familiar with Linux platform development environment set up. 2): proficient commonly used algorithm data structure, and process design Design Contest ACM Awards. 3): Familiar QT, QT practical development experience with the boost libraries have a certain understanding. 4): Familiar with TCP / IP protocol principles, and learn to achieve, and multi-threaded programming familiar with Socket 5): Familiar with Shell programming, familiar with gcc / g+ + / gdb / vim / emacs / git and write a Makefile 6): English CET4 level, able to read English fluently technical documentation, and carry out simple English Time: 2011/11 - 2011/12 Project Name: Qt + MySql College Students scoring system Billiton China Title / Role: Analysis + Design + Code + test Project job responsibilities: This system is responsible for the school from 2010 to 2013 freshman quality Billiton extracurricular achievements are management, performance as a reference when graduation, graduation, student achievement based on its final validation. Background using MySQL storage, the client uses QT development, complete interaction with the customer. Basic Course: C / C + +, data structures, software engineering, operating systems, computer networks, databases, 8086 compilation, compiler theory, computer architecture, Microcomputer Principle and Interface Technology, Computer English, Java, ASP, etc. Self-evaluation: Life, I was a sunny, positive people; learning, I am a patient and willing to learn practical man; interpersonal, and I am an easy person to communicate; 英文简历的模板三: Basic information Name: Mr. Gender: Male Education: College Height: 169 CM Birthplace: Guizhou Date of birth: 1989 Skills expertise: proficient use of Word. Excel, ppt. Program. There are insurance agents certificate Career errorobjective Seeking Position: Health Consultant Job Location: Bao'an District Salary: 2500 (negotiable) Work Experience: Any hillock Self-evaluation: a strong self-learning ability and adaptability, diligence and optimistic and positive Direction of development: Skills expertise ------ Computer Skills: NCRE a foreign language skills: 1. ~ 2 ~ Putonghua proficiency: Cantonese Capacity: Education Training Beginning and ending time academic majors Institution Name 2007.09 ~ 2010.06 Guizhou Commercial College Associate investment and finance Work Experience Inauguration Company: Alliance positron Co. Industry: Electrical Engineering Inauguration Date: March 2010 to May 2011 inauguration Department: Production Department Company: Foreign-owned (European companies) Inaugural Job: Technician Job Description: Responsible for production work Work Experience Inauguration Company: Enterprise Management Consulting Co., Ltd., Chongqing Gordon Guiyang Branch Company Industry: Finance (banks, venture funds) Inauguration Date: September 2009 to December 2009 inauguration Department: Marketing Department Company Type: Joint Ventures / Cooperation (Africa, Europe

简介Online Judge系统(简称OJ)是一个在线的判题系统。
用户可以在线提交程序多种程序(如pC、C++)源代码,系统对源代码进行编译和执行,并通过预先设计的测试数据来检验程序源代码的正确性。
一个用户提交的程序在Online Judge系统下执行时将受到比较严格的限制,包括运行时间限制,内存使用限制和安全限制等。
用户程序执行的结果将被Online Judge系统捕捉并保存,然后再转交给一个裁判程序。
该裁判程序或者比较用户程序的输出数据和标准输出样例的差别,或者检验用户程序的输出数据是否满足一定的逻辑条件。
最后系统返回给用户一个状态:通过(Accepted,AC)、答案错误(Wrong Answer,WA)、超时(Time Limit Exceed,TLE)、超过输出限制(Output Limit Exceed,OLE)、超内存(Memory Limit Exceed,MLE)、运行时错误(Runtime Error,RE)、格式错误(Presentation Error,PE)、或是无法编译(Compile Error,CE),并返回程序使用的内存、运行时间等信息。
Online Judge系统最初使用于ACM-ICPC国际大学生程序设计竞赛和OI信息学奥林匹克竞赛中的自动判题和排名。
现广泛应用于世界各地高校学生程序设计的训练、参赛队员的训练和选拔、各种程序设计竞赛以及数据结构和算法的学习和作业的自动提交判断中。
知名的OJ有:RQNOJ,URAL,SPOJ,vijos,USACO,sgu,pku(poj),zju(toj),tju,uva等。
著名OJ网址中文OJ:任青网络在线测评系统RQNOJ:/高效信息学评测系统vijos: 英文OJ:北京大学pku: /OnlineJudge/ (most English)美国官方USACO: /usacogate/ (English)南开大学nkpc: (most English)浙江大学OJ:/ (English)详细介绍:1.USA Computing Olympiad美国高效的信息学测评网站,也是美国中学生的官方竞赛网站。
it职业规划英文范文Certainly, here's a professional career plan essay in English tailored for an IT professional:Career Planning in the IT Industry: Embracing the Future of TechnologyIn the rapidly evolving landscape of the Information Technology (IT) industry, a well-crafted career plan is not just a necessity, but a strategic tool for success. As an IT professional, my career plan is designed to leverage my skills, stay abreast of technological advancements, and contribute meaningfully to the field.Objective:My primary objective is to become a leading expert in cloud computing and cybersecurity, two domains that are pivotal to modern IT infrastructure. I aim to achieve this by acquiring advanced certifications, participating in cutting-edge projects, and staying informed about the latest industry trends.Education and Certifications:To achieve my career goals, I plan to pursue a Master'sdegree in Information Technology with a focus on cloud computing. Additionally, I will obtain certifications such as CompTIA Security+, Certified Information Systems Security Professional (CISSP), and AWS Certified Solutions Architect – Associate to bolster my credentials and expertise.Professional Development:I will engage in continuous professional development by attending IT conferences, webinars, and workshops. Networking with industry leaders and participating in professional organizations like the Association for Computing Machinery (ACM) and the Institute of Electrical and Electronics Engineers (IEEE) will also be integral to my growth.Technical Proficiency:To stay at the forefront of my field, I will commit to learning new programming languages, such as Python and Java, and mastering tools like Kubernetes for container orchestration and Git for version control. Understanding and implementing the latest security protocols will be a priority to protect against cyber threats.Leadership and Teamwork:Recognizing the collaborative nature of IT projects, I will develop my leadership and teamwork skills. This includes effective communication, project management, and the ability to mentor and guide junior team members. I aim to lead cross-functional teams on complex IT projects, fostering a cultureof innovation and excellence.Adaptability and Lifelong Learning:The IT industry is characterized by its constant change. I am committed to embracing this dynamism by being adaptable and open to new learning opportunities. This includes staying informed about emerging technologies such as artificial intelligence, machine learning, and the Internet of Things (IoT), and integrating them into my skill set.Career Progression:My short-term goal is to work in a role that allows me toapply my skills in cloud architecture and cybersecurity. Inthe medium term, I aspire to become a project manager, overseeing the deployment of secure and scalable IT solutions. Long-term, I envision myself as a Chief Information Security Officer (CISO), shaping the strategic direction of an organization's IT security posture.Conclusion:In summary, my career plan in the IT industry is to become a well-rounded professional with a deep understanding of both cloud computing and cybersecurity. By focusing on continuous learning, professional development, and leadership, I am confident that I can make a significant impact in the ITfield and contribute to the advancement of technology.This essay provides a comprehensive view of a career plan in the IT sector, highlighting the importance of education, professional development, technical skills, and adaptability.。
Beijing University of Posts and Telecommunications (BUPT)School of Computer Science and TechnologySyllabus for Operating Systems1. OverviewsCourse No.: 313.04103 Course Title: Operating Systems Course Credit: 4 Credits, required courseSemester and Year: Fall 2008 Class: 06406—06410 Teaching hours:z Class teaching: 64 hoursz After-class experiments: 17 hoursz Course design, or professional practice for this course:(操作系统综合课程设计), 30 hours, 1 credits, conducted inthe 3rd semester.Prerequisites:z Data Structurez Computer Organization Principles2. Lecture MeetingsTime: Monday AM: 10:00 – 12:00Wensday AM: 10:00 – 12:00Location: Room 402, 4th Teaching Building3. FacultyInstructorz Name: Dr. Wen YE (叶文)z Office: Room 918, 3rd Teaching Buildingz Office Hours: Wednesday 3:00 to 4:30 PM,I am also available by appointment at a time more convenientfor you, especially at the end of this semesterz Phone: 86-10-62282633 (O)z E-mail: gryew@, yewen@Graduate Teaching Assistant:z Name: Cheng Yan (成艳),chengy352@Ma Haiying(马海印),mahaiyinmhy@ z Responsibility: checking homework, directing experimentsz Office: Room 918, 3rd Teaching Buildingz Office Hours: Wednesday 3:00 to 4:30 PM, or by appointment 4. Text Book1. Abraham Silberschatz, Peter Baer Galvin, Greg Gagne, Operating System Concepts(Seventh Edition), Higher Education Press and McGraw-Hill Companies, Beijing, May, 2007.References1.Andrew S.Tanenbaum, Modern Operating Systems, ChinaMachine Press and Prentice Hall, Beijing, Jan.1999.2.孙钟秀,费翔林,洛斌,谢立,操作系统教程(第3版),高等教育出版社,北京,2003年8月3.曹聪, 范廉明,操作系统原理与分析,科学出版社,北京,2003年9月。
国别及团队英文名)2009-6-23 23:3:10 | 分类:QQ个性网名 | 浏览:达;卡达国 Qatar; State of Qatar古巴;古巴共和国 Cuba; Republic of Cuba尼日;尼日共和国 Niger; Republic of Niger伊朗;伊朗伊斯兰共和国 Iran; Islamic Republic of Iran冰岛;冰岛共和国 Iceland; Republic of Iceland印度;印度共和国 India; Republic of India多哥;多哥共和国 Togo; Republic of Togo希腊;希腊共和国 Greece; Hellenic Republic贝南;贝南共和国 Benin; People's Republic of Benin东加;东加王国 Tonga; Kingdom of Tonga波兰;波兰共和国 Poland; Republic of Poland法国;法兰西共和国 France; French Republic人民:芳人 Fang 丰人 Fon 掸人 Shan丁卡人 Dinka 干达人 Ganda 中国人 Chinese丹麦人 Dane巴西人 Brazilian巴里人 Balinese日本人 Japanese比尼人 Bini比尔人 Bhili爪哇人 Javanese加拉人 Galla古巴人 Cuban布吉人 Bugi布拉人 Bura布尔人 Boer本巴人 Bemba瓦尧人 Wayao*******此内容由Www.Duan-xin.Com首发,祝大家天天快乐******** 语言 (1)所属分类∶总目录 >> 百科便览 >> 世界各国英语 English法语 French德语 German日语 Japanese俄语 Russian丹麦语 Danish荷兰语 Dutch芬兰语 Finnish希腊语 Greek印地语 Hindi拉丁语 Latin朝鲜语 Korean马来语 Malay挪威语 Norwegian波兰语 Polish瑞典语 Swedish土耳其语 Turkish阿拉伯语 Arabic爱尔兰语 Irish意大利语 Italian城市 (1)所属分类∶总目录 >> 百科便览 >> 世界各国北京 Beijing; Peking上海 Shanghai天津 Tianjin重庆 Chongqing深圳 Shenzhen香港 Hong Kong台北 Taipei高雄 Kaohsiung大阪 Osaka丹佛 Denver巴黎 Paris比萨 Pisa牛津 Oxford尼斯 Nice平壤 Heijo札幌 Sapporo仰光 Yangon安曼 Amman米兰 Milan伯恩 Bern国花 (1)所属分类∶总目录 >> 百科便览 >> 世界各国澳大利亚 acacia孟加拉 water lily比利时 corn poppy玻利维亚 sunflower保加利亚 rose加拿大 sugar maple中国 plum blossom智利 lily古巴 lily丹麦 Chinese ilex埃及 lotus英国 rose芬兰 lily of the valley; spiraea法国 iris; rose德国 bluebottle希腊 olive盖亚那 water lily荷兰 tulip匈牙利 tulip印度 lotus美国州名 (1)所属分类∶总目录 >> 百科便览 >> 世界各国缅因州 Maine纽约州 New York犹他州 Utah内华达州 Nevada田纳西州 Tennessee伊利诺州 Illinois佛蒙特州 Vermont肯塔基州 Kentucky阿肯色州 Arkansas俄亥俄州 Ohio夏威夷州 Hawaii马里兰州 Maryland密西根州 Michigan密苏里州 Missouri乔治亚州 Georgia堪萨斯州 Kansas华盛顿州 Washington奥勒冈州 Oregon爱荷华州 Iowa爱达荷州 Idaho国际组织 (1)所属分类∶总目录 >> 百科便览 >> 世界各国十国集团 Group of Ten; G10西欧联盟 Western European Union [=WEU]国际商会 International Chamber of Commerce [=ICC] 国际笔会 International Pen欧洲集团 Eurogroup北欧理事会 Nordic Council伊斯兰会议 Islamic Conference东非共同体 East African Community [=EAC]世界贸易组织 World Trade Organization [=WTO]二十国委员会 Committee of Twenty [=Paris Club]日中经济协会 Japan-China Economic Association加勒比共同体 Caribbean community [=CARICOM]各国议会联盟 Inter-Parliamentary Union [=IPU]亚太经合会议 Asia Pacific Economic Cooperation [=APEC] 亚非作家协会 Afro-Asian Writers' Association [=AAWA] 东非共同市场 East African Common Market [=EACM]法兰西共同体 French Community非洲统一组织 Organization of African Unity [=OAU]红十字会协会 League of Red Cross Societies [=LRCS]美洲国家组织 Organization of American States [=OAS]银行机构 (1)所属分类∶总目录 >> 百科便览 >> 世界各国大通银行 The Chase Bank中国银行 Bank of China世界银行 World Bank米兰银行 Midland Bank, Ltd.花旗银行 National City Bank of New York美丰银行 American Oriental Banking Corporation中国人民银行 People's Bank of China日本东京银行 Bank of Tokyo, Ltd.亚洲开发银行 Asian Development Bank [=ADB]泛美开发银行 Inter-American Development Bank [=IDB]非州开发银行 African Development Bank [=AFDB]美洲开发银行 Inter-American Development Bank [=IADB] 美国交通银行 American Epress Co., Inc.香港汇丰银行 Hongkong and Shanghai Banking Corporation 国际结算银行 Bank for International Settlements [=BIS] 瑞士联合银行 United Bank of Switzerland德勒斯登银行 Dresden Bank A. G.欧洲投资银行 European Investment Bank [=EIB]加勒比开发银行 Caribbean Development Bank [=CDB]伊斯兰开发银行 Islamic Development Bank [=IDB]联合国专门机构 (1)所属分类∶总目录 >> 百科便览 >> 世界各国总务处 Office of General Services会议局 Department of Conference Services法务局 Office of Legal Affairs秘书处 Secretariat国际法院 International Court of Justice人口委员会 Population Commission人权委员会 Commission on Human Rights安全理事会 Security Council公共资料处 Office of Public Information政治安全局 Department of Political and Security Council Affairs 统计委员会 Statistical Commission经济社会局 Department of Economic and Social Affairs联合国大会 General Assembly*******此内容由Www.Duan-xin.Com首发,祝大家天天快乐******** 国际劳工组织 International Labor Organization [=ILO]国际开发协会 International Development Association [=IDA]国际电信同盟 International Telecommunications Union [=ITU]麻醉药委员会 Commission on Narcotic Drugs万国邮政联盟 Universal Postal Union [=UPU]诸国会议同盟 Inter-Parliamentary Union [=IPU]秘书长办公室 Office of the Secretary General不丹;不丹王国 Bhutan; Kingdom of Bhutan丹麦;丹麦王国 Denmark; Kingdom of Denmark巴西;巴西联邦共和国 Brazil; Republic of Brazil巴林;巴林国 Bahrain; State of Bahrain文莱;文莱达鲁萨兰国 Brunei; State of Brunei日本;日本国 Japan*******此内容由Www.Duan-xin.Com首发,祝大家天天快乐******** 加彭;加彭共和国 Gabon; Republic of Gabon北韩;朝鲜民主主义人民共和国 North Korea; Democratic People's Republic of Korea。
Don’t wait for a smile to be nice...不要等到了一个笑容才面露慈善Don’t wait to be loved, to love.不要等被爱了以后,才要去爱Don’t wait to be lonely, to recognize the value of a friend.不要等到寂寞了,才明白朋友的价值。
Don’t wait for the best job, to begin to work.不要非要等到一份最好的工作,才要开始工作Don’t wait to have a lot, to share a bit.不要等拥有许多后,才开始分享一些Don’t wait for the fall, to remember the advice.不要等到失败后,才记得别人的忠告Don’t wait for pain, to believe in prayer.不要等到受伤了,才相信愿意祈祷Don’t wait to have time, to be able to serve.不一定要等到有时间,才能够去付出服务Don’t wait for anybody else pain, to ask for apologies...不要等别人受伤了,才来乞求原谅... neither separation to make it up.不要等到分开了,才想到去挽回Don’t wait...Because you don’t know how l ong it will take.不要等待,因为,你不知道等待需要花费多少的时间Remember: Friendship is like wine, it gets better as it grows older.记得:友谊像醇酒,越久越浓。
friend walk in when the rest of the world walks out.Sometimes in life,You find a special friend;Someone who changes your life just by being part of it.Someone who makes you laugh until you can't stop;Someone who makes you believe that there really is good in the world.Someone who convinces you that there really is an unlocked door just waiting for you toopen it.This is Forever Friendship.when you're down,and the world seems dark and empty,Your forever friend lifts you up in spirits and makes that dark and empty worldsuddenly seem bright and full.Your forever friend gets you through the hard times, the sad times, and the confusedtimes.If you turn and walk away,Your forever friend follows,If you lose you way,Your forever friend guides you and cheers you on.Your forever friend holds your hand and tells you that everything is going to be okay.And if you find such a friend,You feel happy and complete,Because you need not worry,Your have a forever friend for life金融危机We all knew that, now the world all is suffering the financial crisis, and many factories all al ready went out of business the bankruptcy, this also meant could have many people to face is coming off sentry duty.Perhaps in school we regarding this realized is not very big, however we soon face the grad uation, also meant must look for the work.Already some people commented: the next several year university graduate, the graduation a lso on meant unemployment! although i not like this believed, but i still felt we should have one kind of crisis feeling, by faces the worst possible occurrence.Therefore, also cannot again continue to waste in the university period time, that already wa s may not obtain extremely! therefore i hoped schoolmates, all can learn own diligently speci al course, in order to might find from now on most suits own work.无论成败 但求做最好的自己Be the best of whatever you are!If you can't be a pine on the top of the hill,如果你当不成山巅的一棵劲松,Be a scrub in the valley---but be就做山谷里的小树吧---但务必The best little scrub by the side of the rill;做溪流边最棒的一棵小树;Be a bush if you can't be a tree.当不了树就做一丛灌木,If you can't be a bush be a bit of grass--当不成灌木还可以做小草--但务必And some highway happier make.做路边最快乐的一株小草。
Financial Management Time Limit: 1000MS Memory Limit: 10000K Total Submissions: 70812 Accepted: 34466
Description Larry graduated this year and finally has a job. He's making a lot of money, but somehow never seems to have enough. Larry has decided that he needs to grab hold of his financial portfolio and solve his financing problems. The first step is to figure out what's been going on with his money. Larry has his bank account statements and wants to see how much money he has. Help Larry by writing a program to take his closing balance from each of the past twelve months and calculate his average account balance. Input
The input will be twelve lines. Each line will contain the closing balance of his bank account for a particular month. Each number will be positive and displayed to the penny. No dollar sign will be included. Output
The output will be a single number, the average (mean) of the closing balances for the twelve months. It will be rounded to the nearest penny, preceded immediately by a dollar sign, and followed by the end-of-line. There will be no other spaces or characters in the output. Sample Input
100.00 489.12 12454.12 1234.10 823.05 109.20 5.27 1542.25 839.18 83.99 1295.01 1.75 Sample Output
$1581.42 Source
Mid-Atlantic 2001 Exponentiation Time Limit: 500MS Memory Limit: 10000K Total Submissions: 80630 Accepted: 19125
Description Problems involving the computation of exact values of very large magnitude and precision are common. For example, the computation of the national debt is a taxing experience for many computer systems.
This problem requires that you write a program to compute the exact value of Rn where R is a real number ( 0.0 < R < 99.999 ) and n is an integer such that 0 < n <= 25. Input
The input will consist of a set of pairs of values for R and n. The R value will occupy columns 1 through 6, and the n value will be in columns 8 and 9. Output
The output will consist of one line for each line of input giving the exact value of R^n. Leading zeros should be suppressed in the output. Insignificant trailing zeros must not be printed. Don't print the decimal point if the result is an integer. Sample Input
95.123 12 0.4321 20 5.1234 15 6.7592 9 98.999 10 1.0100 12
Sample Output 548815620517731830194541.899025343415715973535967221869852721 .00000005148554641076956121994511276767154838481760200726351203835429763013462401 43992025569.928573701266488041146654993318703707511666295476720493953024 29448126.764121021618164430206909037173276672 90429072743629540498.107596019456651774561044010001 1.126825030131969720661201 Hint
If you don't know how to determine wheather encounted the end of input: s is a string and n is an integer C++ while(cin>>s>>n) { ... } c while(scanf("%s%d",s,&n)==2) //to see if the scanf read in as many items as you want /*while(scanf(%s%d",s,&n)!=EOF) //this also work */ { ... } Source
East Central North America 1988 487-3279 Time Limit: 2000MS Memory Limit: 65536K Total Submissions: 150408 Accepted: 25634
Description Businesses like to have memorable telephone numbers. One way to make a telephone number memorable is to have it spell a memorable word or phrase. For example, you can call the University of Waterloo by dialing the memorable TUT-GLOP. Sometimes only part of the number is used to spell a word. When you get back to your hotel tonight you can order a pizza from Gino's by dialing 310-GINO. Another way to make a telephone number memorable is to group the digits in a memorable way. You could order your pizza from Pizza Hut by calling their ``three tens'' number 3-10-10-10.
The standard form of a telephone number is seven decimal digits with a hyphen between the third and fourth digits (e.g. 888-1200). The keypad of a phone supplies the mapping of letters to numbers, as follows:
A, B, and C map to 2 D, E, and F map to 3 G, H, and I map to 4 J, K, and L map to 5 M, N, and O map to 6 P, R, and S map to 7 T, U, and V map to 8 W, X, and Y map to 9
There is no mapping for Q or Z. Hyphens are not dialed, and can be added and removed as necessary. The standard form of TUT-GLOP is 888-4567, the standard form of 310-GINO is