RTCAST Lightweight Multicast for Real-Time Process Groups
- 格式:pdf
- 大小:113.75 KB
- 文档页数:10

LANDesk® Management Suite 8.8 Best Practices for Provisioning – Unattended InstallContentsSummary (4)Assumptions (4)Advantages of Provisioning (4)Automating Provisioning (5)Deploying a PXE representative (5)Steps to deploy the PXE Representative (5)About Templates (6)About Provisioning Agent (6)Unattended Install (7)Provisioning History (20)Adding a bare metal device (21)Provisioning Rights (22)Conclusion (22)References (22)Acronyms (22)About LANDesk Software (23)Author (23)This document contains confidential and proprietary information of LANDesk Software, Inc. and its affiliates (collectively “LANDesk”) and is provided in connection with the identified LANDesk® product(s). No part of this document may be disclosed or copied without the prior written consent of LANDesk. No license, express or implied, by estoppel or otherwise, to any intellectua l property rights is granted by this document. Except as provided in LANDesk’s terms and conditions for the license of such products, LANDesk assumes no liability whatsoever. LANDesk products are not intended for use in medical, life saving, or life sustaining applications. LANDesk does not warrant that this material is error-free, and LANDesk reserves the right to update, correct, or modify this material, including any specifications and product descriptions, at any time, without notice.Copyright © 2007, LANDesk Software Ltd. All rights reserved.LANDesk and Targeted Multicast are trademarks or registered trademarks of LANDesk Software, Ltd. and its affiliated companies in the United States and other countries. Other brands and names may be claimed as the property of others.LSI-0614 04/07 JBB/NHThe purpose of this document is to provide a simple approach to setting up and configuring LANDesk® Provisioning for an unattended installation of Windows XP. LANDesk® Provisioning provides a new way to completely install and configure your desktops and servers—from OS installation to application deployment, patching and configuration—all using a single provisioning task. LANDesk Provisioning was built with the IT administrator’s environment and workflow in mind, providing the standardization and repeat ability you need, while allowing for the customization and flexibility you must have to meet your end users’ needs.LANDesk provisioning allows you to split the provisioning tasks the way you split the work when you’re setting up a system manually now. You can:Plan and assess the needsDesign and test the system configurationDeploy to one or to a group of systemsCreate reusable ―building block‖ tasks for common operationsPerform post-OS tasks, such as installing applications, updating the virus definitions file, and updating the OS with patches Ensure the installation worked, perhaps by running sample test applications.You can schedule a provisioning task in advance—even before the hardware arrives on site—or run it dynamically when needed, such as when a system fails and needs to be restored in-line.Provisioning consists of defining the attributes and features to be applied to targeted servers via automation. This is done through provisioning templates. A template is a series of building blocks to be applied to a device. They build upon each other, and can consist of actions, attributes, constraints, and so forth. A template can have one or many actions. Templates can be re-used, and components of a template can be copied to another. LANDesk provides some canned templates for you to download to modify for your environment.Note: This document is not a complete source of all LANDesk provisioning information. For more detailed information, please see the online help when using your LANDesk management solution.AssumptionsThis paper assumes that the reader has a working knowledge of LANDesk® Management Suite, its functionality, profile migration and operating system deployment methods.Advantages of ProvisioningLANDesk Provisioning offers several advantages over the current practice of manual installs or creating and managing a library of images for new devices. Provisioning defines a series of actions and attributes that are applied to a device dynamically, known as templates. Templates can be defined in either large or small portions and can be combined together to be customized for different hardware and application-types.Creating multiple custom templates using LANDesk’s provisioning capabilities is faster and easier than creating multiple cust om images. Say you have to create 30 unique configurations for your environment. Since templates are formatted as XML documents, and actions can be shared between templates, you can easily review and edit templates for consistency rather than rebuilding or recapturing 30 unique images. For example, if you create an action that installs the virus scanner and updates definitions, you can share this action with each of the 30 templates.If you have a library of images already created, LANDesk provisioning can make use of those images, then script actions before the image deployment—such as waking and booting a remote device—and after the image—such as downloading updated definitions files and OS updates.Templates can be created and scheduled in advance—before the hardware arrives on site. Because each system is unique, sharing a general image between systems can lead to performance and compatibility issues that scripted installs can overcome, so doing this kind of pre-arrival prep work with images. Further, by combining various ―building block‖ templates, new templates can quickly and easily be created and customized to meet a system’s exact requirements.Automating ProvisioningManual provisioning traditionally offers some advantages to the IT administrator, allowing him or her to handle odd error conditions or find needed device drivers so the IT admin is assured of a successfully provisioned device, rather than devoting hours to programming ultra-complex custom scripts that may yield little return when the time spent programming and troubleshooting the scripts is taken into account.When you have only a few devices coming online every month or you have a store of images to go on several identical devices, a manual or semi-automated provisioning process can seem manageable, but it still lacks the benefits an automated install offers, including:RepeatabilityRemote installDeployment and installation task logging for expedited problem solvingSingle process for push and pullSavings through fewer on-site visits and waking powered-off machines for installation.This paper walks you through using LANDesk’s management pro ducts to provision systems from a bare metal hardware to fully configured software automatically; or to re-provision existing systems to new software or OS configurations.Deploying a PXE representativePXE is an industry-standard networking protocol that enables devices to be booted and imaged from the network, by downloading and installing an executable image file from an image server before the device boots from the local hard drive. On a PXE-enabled device, the PXE protocol is loaded from either the net work adapter’s flash memory or ROM, or from the system BIOS. The lightweight PXE representatives in LANDesk management solutions eliminate the need for a dedicated PXE server on each subnet.PXE-based deployment provides an alternate method to agent-based deployment for the remote imaging of network servers. With PXE support, administrators can boot both new and existing PXE-enabled devices, and then either execute an OS deployment script at the device from a custom PXE DOS boot menu or use the LANDesk scheduler to schedule an image deployment job.A PXE representative first needs to be deployed because the installation will be run from the PXE WinPE environment. A PXE representative can be deployed to a client that has the distribution management agent installed.Note: We recommend that the PXE representative be deployed to a different machine than the core.Steps to deploy the PXE Representative1.In the console, click Tools | Distribution | OS Deployment.2.In the Operating system deployment window, click the all other scripts tree item. From the PXE representative deploymentscript's shortcut menu, click Schedule.3.In the console's network view, select the target device on which you want to install PXE services.4.Drag and drop the selected device to the PXE Representative Deployment task in the Scheduled tasks window.About TemplatesA template is a series of actions or building blocks to be applied to a device in a particular order. A template can have one or many actions. You can change the task order in a template. The action sequence can be changed where the action makes sense, but cannot be changed where it does not make sense (for example, one cannot place a post-OS-specific action before the installation of the OS). There are numerous pre-configured templates for various vendors (HP, Dell, and so forth). Templates are stored as XML in the database.About Provisioning AgentLANDesk Provisioning is built around an agent called ldProvision that does the following:Provisioning agent that resides on the target systemRequests the provisioning task from the coreThe agent can work with a PXE server, or with Boot Media (physical/virtual).Does not require unique boot media for each targetVersions for both WinPE and LinuxPERecords transactions and reports statusProvides interface to action handlersUnattended InstallThe following steps provide a step by step example of how to prepare the hard drive, start the unattended install and end with installing the LANDesk agent. Additional actions can be added but for simplicity, I have elected to do the basic steps for imaging a machine end to end.Preparing the hard drive1.From the Management Console, open the Operating System Deployment tool and expand the My Templates section underProvisioning Templates.2.Right click on ―All my templates‖ and select New Template.3.Give the Template a name that represents what we are doing such as ―Format Drives‖ and select ―Windows PE‖ for the Bootenvironment and ―Windows XP Pro‖ for the Target OS (This example is for XP Pro) and click OK.4.Right click the Pre-OS installation section and select ―Add Action‖.5.Give the action a name an d select the ―Partition‖ action under the Type section (Partition – Remove All for this example).6.Change the Action type to ―Remove all partitions‖ and type in a ―0‖ for the disk ID as shown below.7.Add a new partition action and select ―Create partition‖under Action type and a ―0‖ for the disk and ―primary‖ for the typeof partition.8.The Size and Offset should be set to ―0‖ to accept the default Offset and the maximum size of disk 0 (These are the wildcardcharacters for these fields).9.Add a new part ition action and select ―Mount partition‖ under Action type and a ―0‖ for the disk, ―1‖ for the Partition ID and―C:‖ for the Logical disk drive-letter to create.10.Add a new partition action and select ―Make bootable‖ under Action type and a ―0‖ for the disk and ―1‖ for the Partition ID.Check the ―Bootable‖ box if this partition should be set to bootable.11.Add a new partition action and select ―Format partition‖ under Action type and a ―C:‖ for the Logical disk drive-letter and―NTFS‖ for the file system. Check the ―Quick Format‖ box for a quick format to be completed instead of a full format.Copy Drivers and Scripted Install1.For this section, it is important to have the unattend.txt file importing into the database and the variables to be used as well.2.Click the ―Public Variables‖ button in the Console as seen below to add some variables that will be needed in later steps.e the Public variables section to view and set global variables that apply to all provisioning templates. Such variables areused to customize template file names to copy, paths to install to, sensitive data such as passwords or product keys or IP addresses to export files from. User variables (variables that apply to only one template) take precedence over publicvariables.4.For this example we will be using variables for the computer name, product ID and password.5.Click ―Add‖ and name the variable ―ldpassword‖, the Type to ―Sensitive data‖ and enter in the password to be used to mapdrives and set the admin password on the device.Note: The benefit of using variables for passwords is that the password will not become compromised and if the password ever changes, the variable can be reset to use the new password instead of having to change it in ever template andconfiguration file.6.Cli ck ―Add‖ and name the variable ―ProductID‖, the Type to ―Sensitive data‖ and enter in the volume license product ID.7.Click the ―Install Scripts‖ button in the Console as seen below to insert the unattend.txt to be used for the scripted instal l.8.The ―unattend.txt‖ script to be imported should have the variables for the password, product ID and device name. For thisexample, we will copy over the PnP drivers to be used before executed the scripted install so the drivers to be added will need to be somewh ere on a share and mentioned in the unattend.txt under the ―OemPnPDriversPath‖ section.Example unattend.txt:9.Browse to the File, name it, select the XP Pro OS and click the ―Import‖ button. This inserts the script into the LANDesk db.10.From the Management Console, open the Operating System Deployment tool and expand the My Templates section underProvisioning Templates.11.Right click on ―All my templates‖ and select New Template.12.Give the Template a name that represents what we are doing such as ―Scripted XP Install‖ and select ―Windows PE‖ for theBoot environment and ―Windows XP Pro‖ for the Target OS (This example is for XP Pro) and click OK.13.Right click the OS installation section and select ―Add Action‖.14.Give the action a name and select the ―Map/Unmap drive‖ action under the Type section.15.Select the ―Map a drive‖ action and enter in the UNC path to where the drivers are located, enter in the drive letter to be u sed,the user name to gain access to the share and the password variable ―%ldpassword%‖.16.Right click the OS installation section and select ―Add Action‖.17.Give the action a name and select the ―Copy File‖ action under the Type section.18.Enter in the Source path to the drivers including the mapped drive letter and then the Destination path where they should becopied to. Check to copy subdirectories assuming that the drivers are more than one folder deep.19.Right click the OS installation section and select ―Add Action‖.20.Give the action a name and select the ―Scripted Install‖ action under the Type section.21.Enter in the UNC path to the installation media ―WINNT32.EXE‖ file, the credentials to gain access and the passwordvariable ―%ldpassword%‖.22.Under the additional parameters, add ―/syspart:C:‖ and point to the installation script imported from an earlier step.Install the LANDesk Agent1.From the Management Console, open the Operating System Deployment tool and expand the My Templates section underProvisioning Templates.2.Right click on ―All my templates‖ and select New Template.3.Give the Template a name that represents what we are doing such as ―Install LANDesk Agent‖ and select ―Not applicable‖for the Boot environment and ―Windows XP Pro‖ for the Target OS (This example is for XP Pro) and click OK.4.Right click the System Configuration s ection and select ―Add Action‖.5.Give the action a name and select the ―Configure Agent‖ action under the Type section.e the drop down menu to specify which LANDesk agent to install, enter in credentials that will have access the passwordvariable ―%ldpassword%‖.Note: Additional actions can be performed such as Software Distribution, Join Domain, Patch System and Install Services. Grouping templates created and schedulingThe Template view displays the templates that are included in the current template (included templates are also known as Child templates). You can view the templates, and add templates to the current template. Once a template is included with a template, it is part of the parent template. If you change the included template in its original stand-alone form, it is changed in the parent template package, too.For this example, a template was create for each section to show that templates can include other templates and is easier to manage and use in the future provisioning tasks.1.From the Management Console, open the Operating System Deployment tool and expand the My Templates section underProvisioning Templates.2.Right click on ―All my templates‖ and select New Template.3.Give the Template a name that represents what we are doing such as ―FormatDrives-ScriptedXP-InstallAgent‖ and select―Win PE‖ for the Boot environment and ―Windows XP Pro‖ for the Target OS (This example is for XP Pro) and click OK.4.From the ―Includes‖ section and click on Include and add the templates created in previou s steps as seen below.5.Go to the ―Action List‖ section and notice that there are templates added to each section instead of the actions.6.Once this template that includes all the actions to be performed is scheduled or executed manually, a new template is createdand time-stamped and will show up as a locked template as seen in the screenshot below.Note: Once a master template is scheduled and you know this is how you want the template to run, the locked template should be the template scheduled to run on client devices. It is designed this way to be able to duplicate the same steps on all systems. Every time a master template is scheduled, a new locked template is created, so do not plan to use the master for all the machines to be provisioned.Provisioning HistoryThe History button lets you view a devices provisioning history by letting you check on the status of a particular task, determining how a particular machine was provisioned, or finding out which devices were provisioned with a particular template. When a system is provisioned, all the actions are recorded in the provisioning history.If you want to put a system back into a known state, you can replay the template that lets you return to that known state. If you want to replay a template, keep in mind that some actions are external to provisioning. Save any software distribution packages, agent configurations, and programs that you download and execute in conjunction with a template. Otherwise you won’t be able to rep lay them.To view a template/device provisioning history1.From the Management Console, open the Operating System Deployment tool and expand the My Templates or Public sectionunder Provisioning Templates.2.Double-click a template.3.In the left navigation pane, click History.4.Double click on the device and view the history of a specific machine.Note: You can also right click on a device in Scheduled tasks to view the provisioning history.Adding a bare metal deviceProvisioning lets you target and re-provision existing managed systems that appear in your LANDesk management solution or you can provision new hardware devices that have just arrived from the manufacturer or that have received a new hard drive.To do so, you enter the MAC address as a hardware identifier in the Identify devices dialog (or other unique identifying information such as the serial number, IPMI GUID or AMT GUID) to record the minimal information required by the automated provisioning agent (ldprovision) in the LANDesk core database.Management Console Steps:1.In Network View, open the Configuration folder.2.Right-click the Bare Metal Server folder, and click Add devices.3.Select MAC address in the Identifier type drop-down list.4.To add a single device, enter the MAC address in the Identifier box to the right and click Add device, or (to add multipledevices) type the location of a text file (CSV) which contains the identifier information in the text box (or click Browse to find the file), and click Import.5.Click OK to add the devices to the database.The n ewly added device shows up in the list of all devices, and is identified as having a ―Bare Metal‖ operating system type. You can also import a list of devices that have been saved to a CVS file if several new systems are arriving simultaneously.Provisioning RightsThe RBA rights for provisioning are divided into two settings: Configure Provisioning and Schedule Provisioning. The Configure right allows the user to edit templates. The Schedule right allows the user to schedule templates that already exist. Since a user who builds provisioning templates should test those templates, the Configure right requires the Schedule right. Companies may want to give the Schedule right to new, untrusted employees. Those employees would be able to schedule a task to provision a server, but the task will only do what the trusted employee (with the Configure right) defined for that template.ConclusionThis is a best practice guide specifically for unattended installations. This is one source of information to get a new or existing user of LANDesk started in the right direction with the Provisioning of devices.ReferencesAdditional resources can be found in the online help and under the Provisioning section in the LANDesk Community.AcronymsBKM – Best Known MethodPXE – Pre-Execution EnvironmentROM – Read Only MemoryBIOS – Basic Input/Output SystemWinPE – Windows Preinstallation EnvironmentLinuxPE – Linux Preinstallation EnvironmentOSD – Operating System DeploymentUNC – Universal Naming ConventionIPMI – Intelligent Platform Management InterfaceMAC address – Media Access Control addressAbout LANDesk SoftwareThe foundation for LANDesk’s leading IT management solutions was laid more than 20 years ago. And LANDesk has been growing and innovating the systems, security, service and process management spaces ever since. Our singular focus and our commitment to unde rstanding customers’ real business needs—and to delivering easy-to-use solutions for those needs—are just a few of the reasons we continue to grow and expand.LANDesk pioneered the desktop management category back in 1993. That same year, IDC named LANDesk the category leader. And LANDesk has continued to lead the systems configuration space: pioneering virtual IT technology in 1999, revolutionizing large-packet distribution with LANDesk® Targeted Multicast™ technology and LANDesk® Peer Download™ technology in 2001, and delivering secure systems management over the Internet and hardware-independent network access control capabilities with LANDesk® Management Gateway and LANDesk® Trusted Access™ Technology in 2005.In 2006, LANDesk added process management technologies to its product line and began integrating the systems, security and process management markets. LANDesk also extended into the consolidated service desk market with LANDesk® Service Desk, and was acquired by Avocent to operate as an independent division.Today, LANDesk continues to lead the convergence of the systems, security, process and service management markets. And our executives, engineers and other professionals work tirelessly to deliver leading solutions to markets around the globe.AuthorCraig MiddelstadtRevision 1.1December, 18 2007。

RTT使⽤问题总结1 ENV下不⽤将stm32fnxx_hal_msp.c拷贝到RTT⼯程⽂件夹下(也不⽤调⽤其中的⽚上外设函数如voidHAL_SPI_MspInit(SPI_HandleTypeDef* hspi),听说KCONFIG⾃⼰会调⽤根据弱定义寻找;studio下根据⽂档说是需要;stm32_spi_init(drv_spi.c line81)-》HAL_SPI_Init(被spi_conifgure 调⽤drv_spi.c line387,代码在hal_spi.c line 310,⼜调⽤了 HAL_SPI_MspInit)-》 HAL_SPI_MspInit(hspi)-》在stm32f4xx_hal_spi.c中弱定义,在stm32f4xx_hal_msp.c 中根据cubumx⽣成,所以需要将cubumx⽣成的 HAL_SPI_MspInit拷贝到board.c下。
HAL_SPI_MspInit在stm32f4xx_hal_spi.c中弱定义;在由cubumx在stm32f4xx_hal_msp.c⽣成。
HAL_SPI_Init调⽤HAL_SPI_MspInitstm32_spi_init()调⽤HAL_SPI_Init()spi_configure调⽤stm32_spi_init()spi_configure通过stm_spi_ops结构体被rt_spi_bus_register调⽤-》⼜被rt_hw_spi_bus_init(void)-》⼜被rt_hw_spi_init(void)调⽤-》通过INIT_BOARD_EXPORT(rt_hw_spi_init)调⽤进⾏初始化。
2 关于SPI配置,当设定最⼤速率后最终发现时钟频率降低2倍的原因,是因为RTT获取时钟源函数stm32_spi_init下的 SPI_APB_CLOCK不正确,没有正确反映外设挂在哪个总线下⾯;解决⽅法有2种:⽅法1 :将struct rt_spi_configuration cfg 的cfg.max_hz*2并做好备注声明(适合共享给其它⼈应⽤的软件包);⽅法2:将下⾯的通过宏定义修改正确,从⽽获得正确的参数时钟(分频值),这种⽅法适合代码⾃⽤(因为别⼈不⼀定⽤该SPI,且时钟源也不⼀定相同(不同系列的STM32));#if defined(SOC_SERIES_STM32F0) || defined(SOC_SERIES_STM32G0)SPI_APB_CLOCK = HAL_RCC_GetPCLK1Freq();#elseSPI_APB_CLOCK = HAL_RCC_GetPCLK2Freq();#endif3 外设的使⽤⼀定要注意打开board.h进⾏类似以下的声明#define BSP_USING_UART1#define BSP_UART1_TX_PIN "PA9"#define BSP_UART1_RX_PIN "PA10"4 ⾃⼰写的驱动⽼是说找不到头⽂件,尽管路径已经设置好了,原因时下⾯的宏没有打开#define PKG_USING_ADE7913#ifdef PKG_USING_ADE79135 studio下从HSI到HSE,将cubmx⽣成的SystemClock_Config 替换 drv_clk.c中的system_clock_config(target_freq)并将该函数的源代码屏蔽;同时在 STM32F4xx_HAL_CONF.H中修改HSE的值//先修改stm32f1xx_hal_conf.h中的 HSE_VALUE与实际的⼀致//然后在drv_clk.c中替换SystemClock_Configvoid clk_init(char *clk_source, int source_freq, int target_freq){//system_clock_config(target_freq);SystemClock_Config();}//最最后同时也修改board.h中的三个宏,尽管原来的HSI时钟配置也没有⽤到其进⾏计算,只是为了提⽰输出*-------------------------- CLOCK CONFIG BEGIN --------------------------*/#define BSP_CLOCK_SOURCE ("HSE")#define BSP_CLOCK_SOURCE_FREQ_MHZ ((int32_t)8)#define BSP_CLOCK_SYSTEM_FREQ_MHZ ((int32_t)72)/*-------------------------- CLOCK CONFIG END --------------------------*/6 studio下SPI的使⽤,按照board.h中所说即可,不⽤显⽰调⽤HAL_SPI_MspInit(&hspix),有的地⽅⾃会调⽤7 对于多个线程共享互斥量时⼀定要注意:1 申请和释放要成对使⽤;2 如果有条件分⽀要么在各⾃分⽀中释放(适⽤于如果分⽀执⾏完需要较长时间。

ethereal汉化版用法目录1 Ethereal介绍 51.1 Ethereal为何物? 51.1.1 Ethereal可以帮人们做什么? 51.1.2 界面功能 51.1.3 实时的从不同网络介质抓取数据包 6 1.1.4 导入来自其它抓包工具的文件 61.1.5 为其它抓包工具导出文件 61.1.6 丰富的协议解码器 71.1.7 开放源代码软件 71.1.8 Ethereal不能做什么? 71.2 Ethereal运行平台 71.2.1 Unix 71.2.2 Linux 81.2.3 Microsoft Windows 81.3 那里可以得到ethereal? 81.4 Ethereal的读法 91.5 Ethereal的历史 91.6 Ethereal的设计和维护 91.7 问题报告和获得帮助 91.7.1 Web网站 91.7.2 WIKI 101.7.3 FAQ 101.7.4 邮件列表 101.7.5 问题报告 101.7.6 liunx/unix平台崩溃报告 111.7.7 Windows平台崩溃报告 112 编译和安装ethereal 112.1 介绍 112.2 获得ethereal源代码和应用发布版本 12 2.3 UNIX平台编译ethereal之前准备工作 12 2.4 UNIX平台编译ethereal源代码 132.5 UNIX平台应用版本安装 132.5.1 RedHat 的RPMs方式安装 142.5.2 Debian的安装方式 142.6 解决UNIX下安装失败问题 142.7 Windows下源代码的编译 142.8 Windows下Ethereal安装 142.8.1 安装ethereal 142.8.2 升级ethereal 152.8.3 卸载ethereal 153 用户操作界面 153.1 介绍 153.2 启动ethereal 153.3 ethereal主界面 153.4 “The Menu”主菜单 163.4.1 “File”文件菜单 183.4.2 “Edit”编辑菜单 193.4.3 “View”视图菜单 213.4.4 “GO”跳转菜单 233.4.5 “Capture”抓包菜单 243.4.6 “Analyze”分析菜单 243.4.7 “Statistics”统计报表菜单 263.4.8 “Help”帮助菜单 273.5 “Main”常用工具栏 283.6 “Filter Toolbar”显示过滤器工具栏 303.7 “Packet List”数据包列表窗格 313.8 “Packet Details”数据包信息树窗格 313.9 “Packet Bytes”数据包字节窗格 323.10 “Statusbar”状态栏 324 网络数据包实时抓取 334.1 介绍 334.2 使用Ethereal前的准备工作 334.3 如何开始抓包? 334.4 “Capture Interfaces”抓包网络接口窗口 344.5 “Capture Options”抓包选项窗口 354.5.1 “Capture”抓包常规框 354.5.2 “Capture File(s)”数据包文件框 364.5.3 “Stop Capture…”停止抓包框 374.5.4 “Display Options”显示选型框 384.5.5 “Name Resolution”名称解析框 384.5.6 “Buttons”按键 394.6 数据包文件和文件模式 394.7 “Link-layer header type”链接层数据头类型 40 4.8 抓包过滤器 404.9 抓包状态信息窗口 424.9.1 停止抓包 424.9.2 重新开始抓取 435 数据包文件导入、导出和打印 435.1 介绍 435.2 “Open”打开数据包文件 435.2.1 “Open Capture File”打开数据包文件窗口 44 5.2.2 支持导入文件格式 455.3 “Save As”存储数据包 455.3.1 输出文件格式 465.4 “Merging”合并数据包文件 475.5 “File Sets”文件系 485.6 “Exporting”导出文件 495.6.1 “Exporting as Plain Text File”导出无格式文件 495.6.2 “Export as PostScript File”导出PS格式文件 505.6.3 “Export as CSV(Comma Seperated Values)File”导出CSV(逗号分割)文件 50 5.6.4 “Export as PSML File”导出PSML格式文件 515.6.5 “Export as PDML File”导出PDML格式文件 515.6.6 “Export selected packet bytes”导出被选择数据包数据 525.7 “Printing”打印数据包 535.8 “Packet Range”数据包范围窗格 556 数据包分析 556.1 如何查看数据包 556.2 显示过滤器 606.3 如何书写显示过滤器表达式 616.3.1 显示过滤器字段 616.3.2 比较操作的数据类型和操作符 626.3.3 组合表达式 626.3.4 显示过滤器常见误解 636.4 “Filter Expression”过滤器表达式窗口 646.5 定义和存储过滤器 656.6 搜索数据包 676.6.1 “Find Packet”搜索数据包窗口 676.6.2 “Find Next”寻找下一个 686.6.3 “Find Previous”寻找上一个 686.7 “GO”跳转 686.7.1 “Go Back”后退 686.7.2 “Go Forward”向前 686.7.3 “Go to Packet”跳转到 686.7.4 “Go to Corresponding Packet”跳转到相关数据包 696.7.5 “Go to First Packet”跳到第一个数据包 696.7.6 “Go to Last Packet”跳到最后一个数据包 696.8 标记数据包 696.9 时间显示格式和时间基准点 706.9.1 时间显示格式 706.9.2 时间基准点 707 高级工具 727.1 介绍 727.2 “Following TCP streams”跟踪TCP数据流 727.2.1 TCP数据流跟踪窗口 737.3 Time Stamps时间标记 747.3.1 Ethereal内部时间格式 747.3.2 数据包文件时间格式 747.3.3 时间正确性 747.4 时区问题 757.4.1 什么是时区? 757.4.2 为你的计算机设置正确时间 757.4.3 Ethereal和时区 767.5 数据包重组 767.5.1 什么是数据包重组? 767.5.2 Ethereal如何实现包重组 767.6 名称解析 777.6.1 以太网名称解析(MAC层) 777.6.2 IP名称解析(网络层) 787.6.3 IPX名称解析(网络层) 787.6.4 TCP/UDP端口名称解析(传输层) 787.7 确保数据完整性 787.7.1 Ethereal核对概要 797.7.2 硬件里的概要计算和确认 798 统计 798.1 介绍 798.2 “Summary”统计窗口 808.3 “Protocol Hierrrchy”协议层次统计窗口 81 8.4 “Endpoint”终端统计 828.4.1 Endpoint终端是什么? 828.4.2 终端统计窗口 838.5 会话统计Conversations 838.5.1 什么是会话 838.5.2 会话窗口 838.6 IO曲线图窗口 858.7 服务响应时间统计 869 Ethereal客户配置 879.1 介绍 879.2 定义数据包颜色 879.3 控制协议解析器 899.3.1 “Enabled Protocols”协议解析开关窗口 89 9.3.2 用户配置解码 909.3.3 查看定义的解码方式 919.4 参数选择 921 Ethereal介绍1.1 Ethereal为何物?Ethereal是开源网络数据包分析软件。

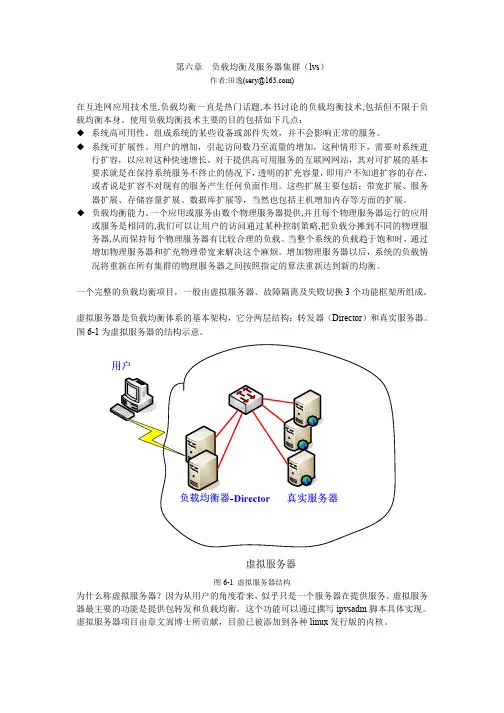
第六章 负载均衡及服务器集群(lvs)作者:田逸(sery@)在互连网应用技术里,负载均衡一直是热门话题,本书讨论的负载均衡技术,包括但不限于负 载均衡本身。
使用负载均衡技术主要的目的包括如下几点: ◆ 系统高可用性。
组成系统的某些设备或部件失效,并不会影响正常的服务。
◆ 系统可扩展性。
用户的增加,引起访问数乃至流量的增加,这种情形下,需要对系统进 行扩容,以应对这种快速增长。
对于提供高可用服务的互联网网站,其对可扩展的基本 要求就是在保持系统服务不终止的情况下, 透明的扩充容量, 即用户不知道扩容的存在, 或者说是扩容不对现有的服务产生任何负面作用。
这些扩展主要包括:带宽扩展、服务 器扩展、存储容量扩展、数据库扩展等,当然也包括主机增加内存等方面的扩展。
◆ 负载均衡能力。
一个应用或服务由数个物理服务器提供,并且每个物理服务器运行的应用 或服务是相同的,我们可以让用户的访问通过某种控制策略,把负载分摊到不同的物理服 务器,从而保持每个物理服务器有比较合理的负载。
当整个系统的负载趋于饱和时, 通过 增加物理服务器和扩充物理带宽来解决这个麻烦。
增加物理服务器以后,系统的负载情 况将重新在所有集群的物理服务器之间按照指定的算法重新达到新的均衡。
一个完整的负载均衡项目,一般由虚拟服务器、故障隔离及失败切换 3 个功能框架所组成。
虚拟服务器是负载均衡体系的基本架构,它分两层结构:转发器(Director)和真实服务器。
图 6-1 为虚拟服务器的结构示意。
图 6-1 虚拟服务器结构为什么称虚拟服务器?因为从用户的角度看来, 似乎只是一个服务器在提供服务。
虚拟服务 器最主要的功能是提供包转发和负载均衡,这个功能可以通过撰写 ipvsadm 脚本具体实现。
虚拟服务器项目由章文嵩博士所贡献,目前已被添加到各种 linux 发行版的内核。
故障隔离指虚拟服务器中的某个真实服务器(或某几个真实服务器)失效或发生故障,系统 将自动把失效的服务器从转发队列中清理出去,从而保证用户访问的正确性;另一方面,当 实效的服务器被修复以后,系统再自动地把它加入转发队列。

砖引玉吧,希望大家不断的补充。
问问题的朋友不要在这里问,为了方便查询,这里不回答。
希望大家一起来维护,有要更新的,请跟帖,我会及时补充上。
跟贴的时候,请写名属于那一类,详细说明功能。
还要麻烦diag也来维护。
硬件系统:1、如何查看cup的状态?作者:南非蜘蛛# psrinfo -v# mpstat 可以列出多cpu负载的状态2、如何查看内存?作者:南非蜘蛛# prtconf | grep 'Memory' 可以查看内存的多少.# /usr/platform/sun4u/sbin/prtdiag3、如何动态添加swap分区?# $su -root ----- 成为超级用户# mkfile 100m /home/swapfile ----- 创建100m的Swap文件# /usr/sbin/swap -a /path/filename ----- 激活Swap文件# /usr/sbin/swap -l ----- 验证swap文件# /usr/sbin/swap -d /path/filename ----- 取消swap文件# rm -rf /home/swapfile ----- 删除swap文件4、如何查看当前网卡是以何种速率起来的?作者:南非蜘蛛# dmesg |grep Link5、如何调整x-window的分辨率和刷新频率?字符界面登陆,运行:#/kdmconfig6、如何使用光、软驱?一般情况下用:# /etc/init.d/volmgt start# volcheck以上方法不行,用:# /etc/init.d/volmgt stop# mount -F hsfs -o ro /dev/dsk/c0t6d0s0 /cdrom --挂接光驱# mount -F pcfs /dev/diskette0 /floppy --挂接软驱solaris定义系统磁盘文件系统说明:ufs – UNIX文件系统。

目录使用OpenSER构建电话通信系统 (1)第一章:SIP介绍(Introduction to SIP) (1)第二章:SIP快速路由器(The SIP Express Router) (28)第三章:OpenSER安装(OpenSER Installation) (42)第四章:OpenSER标准配置(OpenSER Standard Configuration) (58)第五章:用MySQL添加认证(Adding Authentication with MySQL) (85)第六章:使用SerMyAdmin构建用户入口 (121)第七章:与PSTN的连通(Connectivity to the PSTN) (138)第八章:通话前转和语音邮件(call forward and voice mail) (177)使用OpenSER构建电话通信系统Building Telephony Systems with OpenSER第一章:SIP介绍(Introduction to SIP)会话初始化协议是互联网工程任务组(IETF)制定的协议标准,在多个RFC (Request for Comments)文档中被进行了描述说明。
RFC3261是最近的一个RFC,一般称它为SIP版本2。
SIP是一个应用层的协议,用来建立,修改,终止会话(sessions)或是多媒体通话(multimedia calls)。
这些会话可以会议(conferences),e-learning,网络电话和一些相似的应用。
它是同HTTP协议相类似的文本协议并且被设计用来发起,保持,关闭用户之间的交互会话。
目前SIP已经是VoIP领域被广泛使用的协议之一了,市场上几乎每一台IP电话都会支持它。
本章结束的时候你将能够:●描述SIP是什么●描述SIP是干什么的●描述SIP的框架●解释SIP主要部件的意义●理解并比较主要SIP消息●描述INVITE和REGISTER请求消息头部的处理过程在建立和关闭多媒体通话的过程中,SIP协议支持五种要素。

RDP:A Result Delivery Protocol for Mobile ComputingMarkus Endler,Dilma M.Silva and Kunio OkudaDepartment of Computer ScienceUniversity of S˜a o Paulo,Brazilendler,dilma,kunio@p.brAbstractNowadays several information retrieval services are be-ing offered to mobile clients.Many of such services are im-plemented by groups of distributed servers and sometimesemploy time-consuming data location and retrieval proto-cols among the servers.Moreover,many network appli-cations have strong reliability requirements.This meansthat client-server communication in services for mobilecomputing must also be reliable despite the intrinsic non-predictability related to mobile computing.In this paper we present a client-server protocol whichimplements reliable delivery of messages to mobile hosts.Reliability here means that for every request from a mo-bile client to a network service,eventually it will receivethe result,despite its periods of inactivity and any numberof migrations.This protocol is suitable for network servicesbased on request-reply style of communication(e.g.RPC)and with long request processing times,i.e.where there ishigh probability that a client at a mobile host migrates toanother cell while waiting for the reply.The main advantage of our protocol is that the locationof the proxy used to forward messages to a mobile host isnot static(as in Mobile IP),by which it facilitates dynamicglobal load balancing within the set of Mobile Support Sta-tions.1.IntroductionWith the ongoing improvement and spread of cellulartelephony technology,more and more computer networkservices will be supporting wireless communication.Soon,it will be possible to access many sorts of information basesfrom lightweight,inexpensive and hand-held terminals orPDAs,regardless of their current location.Also,many ofthese information bases will be fed with data sent by thesemobile devices,which may range from frequent updatesinteractions and processing within the TIS network.In order to implement efficiently the operations offered by the system to mobile users(such as query,update,sub-scribe1,and multicast2)we are designing and implementing a suite of protocols[7]that handle different aspects of the operations,such as user mobility,data location,data repli-cation,TIS interaction,etc.We hope that the model and the protocols are generic enough to be easily adaptable to a variety of applications,ranging from support systems for strategical actions to electronic mail systems for portable computers.In this paper we focus our attention on a connectionless communication protocol for mobile clients named Result Delivery Protocol(RDP).In our project,this protocol is used for the query and subscription operations mentioned before.The remainder of this paper is organized as follows:In section2we define the system model and the underlying assumptions.In section3we describe the Result Deliv-ery Protocol,focusing on how location updates of migrat-ing clients and retransmissions are handled by the protocol. We then compare our protcol with related work in section 4.Finally,in section5we give informal arguments about its correctness and the incurred overhead and draw some conclusions.2.System Model and AssumptionsThe model of the system consists of two types of ma-chines,the static hosts and the mobile hosts().Static hosts are connected to each other through a static and reli-able network.Among the static hosts,some also serve as Mobile Sup-port Stations()for the mobile hosts and are assumed not to fail.Each defines a geographic region(cell) in which it is able to communicate with the set of mobile hosts currently located in the cell.The information about the s within a cell is maintained at each in a data structure local1The user specifies an entity and a threshold on any of its attribute val-ues,and the system will notify the user about related changes in the entity.2The user provides its identification,the identification of a group of users(previously configured)and a message to be sent to the group.sends a join message to the in charge for the cell it is currently in,which then becomes the currently responsible for the(respMss).A leaves the system by sending a leave message to its respMss.Mobile hosts are able to move from one cell to an-other.Whenever a enters a new cell it sends a greet(oldMss)message to the responsible for the target cell,where oldMss is the identity of the re-sponsible for the cell which the is leaving.With this information the of the new cell is able to initiate a Hand-off protocol with the previous(see Section3.2).This greet message is also sent by the when it becomes active again within the same cell where it has been before become inactive.In this particular case,however,the will not initiate a Hand-off protocol,since the previous mentioned in message greet is itself.Actually,in this model we abstract from the details of how a learns that it is entering or leaving a cell,assum-ing that this can be achieved in different ways according to the wireless technology in use.Figure1shows a system with three s andfive s (in the corresponding cells or migrating)and where mobile host is issuing a request to server from one cell,but may pick up the server’s reply while visiting another cell.The main assumptions of the model are the following: munication among the s is reliable and mes-sage delivery is in causal order;2.All are reliable and do not fail;3.At any time,each active is associated with exactlyone(respMss).4.If a is active it must send an Ack to all messagesreceived from its respMss,and while it is inactive itmust not reply to any message.When a migrates between cells it may be considered inactive by both the ()or the new Mss()during the period of time of the Hand-off.5.A is able to detect if a message from its respMssis a new one or if it is a retransmission.6.A only leaves the system if it has acknowledgedall messages received by its respMss.3.Result Delivery ProtocolIn the remainder of this paper we present and analyze a protocol which guarantees reliable delivery of reply mes-sages from a server in the network to a mobile client.This protocol,which we called Result Delivery Protocol,is suit-able for network services based on a request-reply style of interaction(e.g.RPC)and with long request processing time.For such services,it is likely that the client(on the mobile host)migrates to another cell while waiting for the result of the request.The protocol can be used with a wide range of existing network services since from the perspec-tive of the server,service access is identical to the one by a static client.Although the presentation of the protocol is focussed on a request-reply style of interaction,like operation query of the traffic information service(Section1),it can be used as well for asynchronous notifications of events to mobile clients.Thus,the RDP may as well be used for implement-ing the operation subscribe(Section1),by which a mobile client is informed of any major change in the traffic situa-tion.The RDP protocol is based on the indirect model for client-server interactions proposed by Badrinath et al.[2]. In this model the mobile support stations act as represen-tatives for all the mobile hosts within their cell,hold part of the’s state,and do the translation between the wired and the wireless communication.3.1.Outline of the ProtocolThe Result Delivery Protocol(RDP)is based on the no-tion of a proxy for requests(or simply proxy).A proxy is created on behalf of a that wishes to interact with servers within the wired network.It is created at the responsible for the’s current cell(respMss)whenever the initiates a new series of service requests.The main purpose of the proxy is to provide afixed location for the re-ception of server replies,to keep track of pending requests, store the request’s results,and to forward the results to the responsible for the cell in which the is currently located.The proxy object exists only until all result for-wards are acknowledged by the corresponding.Then,at a later moment,the same may cause the creation ofa new proxy at the same or a different,depending on whether it has or not migrated.However,at any time each is associated with at most one proxy.In order to decide to which to forward the result of a request,each proxy holds a variable called currentLoc,which is updated with the address of the current respMss of the corresponding whenever it migrates.A proxy alsoholds a requestList containing identifiers of all pend-ing requests issued by the.For being able to update currentLoc at every migra-tion,each has one proxy reference(or simply pRef) associated to it,which is hold by its respMss.As the namesuggests,a pRef contains a reference(the i.e.address ofthe and a proxyID)to the current proxy associated with the.However,when a does not have a proxy(i.e.when it has no pending requests)pRef holds a null ad-dress.A pRef also contains aflag called Ready to Kill pRef(RKpR),which signals whether the proxy has forwarded theresult of its last pending request(see section3.3for more details).Each time a receives a new request from one of its local s it checks the corresponding pRef.If it hasan null address,a new proxy is created locally on behalf of and updates pRef with its own address and the proxy’s objectID.Otherwise,Mss forwards the request tothe proxy whose address is mentioned in pRef.When a migrates from to pRef ishanded over through the Hand-off protocol(see Section3.2) to as part of’s state.After completion of the Hand-off for a,’s new location is updated at the proxy.This is done by having send a special mes-sage(update currentLoc)to the proxy.This message is also sent when a respMss receives a greet message from the announcing its switch from the inactive to the ac-tive state.At the proxy,the arrival of the update cur-rentLoc message causes the variable currentLoc to be updated and any non-acknowledged results from pend-ing requests to be re-sent to the new location.When the result of any of s pending requests(say,re-quest R)arrives at a proxy(located at)it is forwarded by to the address mentioned in currentLoc(i.e. respMss)and then delivered to through wireless com-munication.In normal conditions,i.e.when a is active and staysin its cell for a sufficient long period of time,the arrival ofR’s result is acknowledged by the through a Ack mes-sage,which is forwarded by to.Once it has arrived,the proxy marks that request R has been completed, removes it from the requestList,and possibly sends an acknowledgment to the server,depending on the particular application-level client-server protocol being used.If respMss is unable to reach,because it is migrat-ing or is in inactive state,or simply because wireless com-munication failed,the respMss does not attempt any new forwarding of the result.Instead,it is the proxy that will re-sent the result as soon as it receives the next update of ’s address.At each,higher priority is given to forwarding Ack messages(from s to)than to engaging in any new Hand-off transactions.This avoids that results already ac-knowledged by a are re-sent to the new cell.However, as soon as respMss receives a request(from another) to transfer’s state,as part of the Hand-off protocol,it will ignore all future Ack messages from this.From the viewpoint of the proxy,until it does not receive an Ack message informing that R’s result has been indeed received by the,it keeps re-sending the result to every from which its gets a update currentLoc mes-sage.Notice that this guarantees that every result from a request will eventually reach its destination(the),pro-vided that the does not leave the system with a pending request.The price to pay for this reliability is that eventu-ally a result will be sent more than once to a.3.2.Hand-off ProtocolThe Hand-off protocol is executed between a and whenever a switches cells,and aims at transfer-ring all of’s relevant state to.It works as follows:A entering a new cell registers itself with the cor-responding Mobile Service Station(i.e.)by sending it a greet message containing the identification of its pre-vious respMss.After having announced itself to,a must not reply to any message from any other than.When receiving the greet message,sendsa dereg message,asking it to de-register and send back’s proxy reference(pRef).When re-ceives dereg Mh,it replies to with a deregAck message containing’s pRef,and then removes from its localMhs list and updates’s new location with its proxy,by send-ing the update currLoc message to the proxy,whose address is contained in pRef.The greet message is also sent by a when it be-comes active again within the same cell where it has been before become inactive.In this case,however,message greet carries the identification of s current respMss, and hence no Hand-off is initiated.3.3.The Proxy Life-cycleAlthough every always has at most one proxy that forwards results to it,the location of the proxies in the static network may change over time,by which the protocol facili-tates dynamic global load balancing within the set of s.As mentioned earlier,a proxy is created whenever a issues a new request and no proxy is yet available,i.e.when address in’s pRef is empty.After creation,a proxy is capable of handling several concurrent requests from its .When a proxy(hosted at)forwards the result of the last pending request(say,)to a respMss,flag del-pRef is set to and is piggy-backed on this result mes-sage sent to a’s respMss.It means that if this message is received by the,then the proxy can be deleted.When the respMss receives a result message with del-pRef,it setsflag RKpR true at’s pRef,mean-ing that respMss will confirm the removal of the proxy(and erase proxy’s address in pRef’s)as soon as it receives an Ack from that is not preceded by any new request.If this is the case,respMss sends message Ack withflag del-proxy piggy-backed on it to,by which this one knows that the proxy can in fact be deleted.How-ever,if in the meantime,a new request from arrives at respMss,flag RKpR is re-set to and Ack message is sent with del-proxy,meaning that the old proxy will also be used for this new request.Figure2shows the proxy and pRef objects,and theflags used to control the existence of the proxy.Thus,the removal of the proxy is confirmed by respMss only if the following condition holds:RKpR and for all of’s requests the corresponding Ack has been received.Notice that since will always use respMss as the gateway for new requests,it will never happen that a new request is sent to a which is not hosting a’s proxy.3.4.ExamplesIn this section we present two examples to illustrate how RDP works.Figure3shows a scenario where a mobile host Mh issues a single request to a server at,then migrates toand later to.Assuming that this is’sfirst request,its pRef will contain no address.Hence a new proxy is created at with its variable currentLoc (abbreviated by currL)set to and also the address in pRef is set to.Now each time the migrates(and after the Hand-off protocol is completed)the new sends an update currL message to the proxy in order to update its variable currL.MhrespMssMss pupdate currLupdate currLforward result forward resultserverMss Mss p oproxy MhrequestcurrL:=ppRef:=(Mssp)pRefcurrL:=oresultcurrL:=n?Mss nAckAck Hand-offHand-off+greetgreet++dereg+pRefdel-pRefdel-pRefdel-proxyderegAckWhen the response of the request (result )arrives atthe proxy,forwards it to the Mss metioned in currL ,even if in the meantime has migrated,as suggested by the question mark in the figure.Piggy-backed on the re-sult message goes del-pRef,because proxy’s requestList has a single entry.Because Mh has mean-while migrated to another cell,the proxy does not receivean Ack from,hence will repeat the forwarding every time its variable currL is updated,until it finally receives an Ack from the Mh .When receives the result with del-pRef ,it sets the flag RKpR at ’s pRef ,forwardsresult to Mh and waits for an Ack from.As soon as this message arrives,and since still RKpR ,erases the address at ’s pRef and also sends message Ack piggy-backed with flag del-proxy to .Finally,when this message arrives at the proxy is deleted.Figure 4depicts a scenario where a Mh issues several requests through its proxy,showing when the proxy is actu-ally deleted.In this scenario,the mobile host Mh first issues requestA at (creating a new proxy),and then mi-grates to Mss .Thus,initially the proxy’s requestListcontains only requestA and when resultA arrives fromthe server,forwards resultA with del-pRef to .When this message arrives,sets flag RKpR =true at ’s pRef ,and forwards resultA to Mh .However,since Mh issues a new requestB before send-ing an Ack for resultA (AckA )flag RKpR is set to false.Since now Mss receives AckA when RKpR,it leaves pRef ’s address unchanged.After receiving requestB followed by AckA ,the proxy’s requestList ends up holding only requestB ,and resultB is forwarded to .Assume that meanwhile a new requestC arrives at the proxy,causing its requestList to hold both requestB and requestC .When AckB is received by the proxy,and resultC is received and forwarded,requestB can be removed from requestList ,leaving only the single pending requestC .In this particular case,the proxy does not forward again resultB (which has already been sent),but sends a spe-cial message containing only del-pRef to ,where it causes flag RKpR at ’s pRef to be set to .Finally,when AckC arrives from ,pRef ’s address isset to null,and message AckC with del-proxyisAresultCAck BAck AresultAresultBresultBresultCrequestC resultA+requestBresultA Ack BAckCrequestBrequestCAck +AckC resultBresultCrequestBrequestCupdate currLMssrequestAMhrequestAproxy serverMsspHand-offdel-pRefdel-pRefdel-proxysent to proxy,which causes its deletion.This means that at the next time issues a new request,a new proxy will be created at its current respMss .However,suppose that the last del-pRef message hadarrived at Mss after AckC .Since RKpR,pRef would be left unchanged and AckC would be sent to with del-proxy ,avoiding the removal of the proxy.4.Related WorkIn our work,we adopt the indirect model for client-server interactions originally proposed by Badrinath et al.[2]and now adopted also in many other works [14,3,8].In this model mobility is made explicit to all protocol layers (up to the application layer)and the s serve as static interme-diates for any communication between the mobile clients and the servers executing on the pared to other approaches that make mobility explicit only to the protocol layers up to the network layer (e.g.Mobile IP and its optimizations [10]),the indirect model has as its main advantage the possibility to build mobility-aware higher-level protocols which use locality information to dynami-cally adapt themselves to variant transmission and/or net-work access conditions,such as communication bandwidth of wireless media,closest server,etc.Moreover,this model has the advantage of allowing the s to perform trans-lations between the wired and wireless medium,and also to store application-specific data related to the state of the‘local’s.Based on the indirect model,Bakre [3]proposes an in-direct TCP protocol (I-TCP)and protocols at higher layers,all of which take mobility into account.In his approachthe fixed host only ‘sees’an image of its peer,which is actually stored at its respMss and is transferred to otherwhen a moves between cells.However,since during a Hand-Off the wireless component of I-TCP sim-ply resets congestion-related parameters,I-TCP cannot rely on transport-layer acknowledgments and defers this respon-sibility to higher protocol layers.Moreover,the fixed host(the server)must be informed that a new is now hold-ing ’s image.Although our protocol is not aimed for connection-oriented services,and hence does not require maintaining the status of a connection,it proposes a solu-tion to minimize the disruption caused by the Hand-off.Although RDP is not a generic network protocol (since it is suited only for connectionless request-reply communica-tion,rather than for generic datagram delivery),it is useful to compare it with Mobile IP due to some common char-acteristics.In both protocols messages (or datagrams)are delivered to mobile hosts via intermediate elements.In Mo-bile IP they are called home and foreign agent and in RDP these are the proxy and the respMss .In both protocols,thecurrentlocation (in Mobile IP terminology,care-of ad-dress )is stored at the proxy and updated whenever the registers at a new .The main differences between the protocols are as fol-lows:In Mobile IP the home agent is fixed rather than dy-namic,making dynamic load balancing impossible.In RDP the proxy remains at a same location only while there are some pending requests,and as soon as all results of pend-ing requests have been delivered successfully to the corre-sponding ,the proxy removes itself.Thus,in RDP the proxy must keep track of the pending requests,meaning thatall new requests must be forwarded to thehosting the proxy ,which is not the case in Mobile IP.Another conse-quence of the proxy ’s dynamic address is that the proxy ref-erence (pRef)has to be handed over betweens at every migration.Since in Mobile IP the address of home agent isstatic,it can be included byinto each request.However,Mobile IP does not guarantee reliable data de-livery to the s.For example,IP datagrams may be lost while a new care-of address change is on its way to the home agent,or during the periods of inactivity of the mo-bile host.In fact,Mobile IP delegates the task of detect-ing and re-transmitting lost datagrams to upper network lay-ers,such as TCP.However,it has been shown that conven-tional transport-level protocols without mobility-awareness present bad performance when used in a wireless environ-ment[4].In RDP,on the other hand,Hand-Off is tightly integrated with the message delivery,ensuring that no mes-sages(i.e.request results)are lost despite migration or inactivity.Many other works have investigated the issue of dis-connected data access.In Project Dataman,from Rutgers, Imielinski and Badrinath[9]proposed several query and up-date strategies for distributed information services that store frequently modified data,such as the geographic location of individual mobile hosts.Project Rover[11],from M.I.T.,is a well-known dis-tributed object development environment for disconnected operation.It provides mobile computing support based on two concepts:Queued Remote Procedure Calls(QRPC) and Relocable Dynamic Objects(RDOs).In QRPC(asyn-chronous RPC)the actual sending of the RPC request is de-coupled from the QRPC invocation and is performed as soon as the has established a good communication link with a base station.A RDO is an object encapsulating both code and data that can execute either at the client or the server.In some sense,QRPC and RDP perform comple-mentary tasks.While thefirst guarantees reliable sending of requests,RDP guarantees reliable result delivery.Pitoura et al.[12]describe a general architecture of an information system for mobile environment,and in[13] propose support for transactions management for wireless environments.Although recently much attention has been given to the problems of database transaction management [6]with disconnection requirements,this issue is not ad-dressed by our work.In Project Wireless-View[15](U.Illinois-Chicago)sev-eral data allocation schemes are studied and specific cost models for access to continuously changing databases from clients at mobile hosts were proposed.Bayou[5](Xerox)is a weakly consistent storage system designed for a mobile computing environment that supports the development of a variety of collaborative applications, such as shared calendars,mail,databases,etc.Unlike our system model,Bayou treats mobile units as peers in a peer-to-peer model,where a mobile host may be both a Bayou client and server.In Bayou,collections of data items are fully replicated at a group of Bayou servers, and clients can read or write any copy residing on any server with which they are able to communicate.The main contri-butions of this system are its mechanisms for dependency checks and merge procedures,necessary for maintaining high availability of Bayou system with weak replica con-sistency.5.Protocol Analysis and ConclusionThe protocol presented in this paper guarantees delivery (of the result)with at least-one semantics,since the proxy keeps re-transmitting the result until an Ack message ar-rives,signaling that the has indeed received the re-sponse.However,a that becomes inactive right after reception of the result message(but does not send an Ack message)will receive this message again when it be-comes active again,either in the previous or in a new cell.If the already sent an Ack to its respMss and if wired communication guarantees delivery of messages in causal order,then the protocol ensures delivery of messages with exactly once semantics.This is because eachis supposed to handle Ack forwards with highest priority, and therefore the following sequence of causal dependen-cies among events(where denotes the sending of message from server)always holds:send(Ack)@Mss send(Ack+del-proxy)@Mss send(update currL)@Mss.Hence,the proxy will re-ceive the Ack message(forwarded by)before the message update currL,from,and will thus re-move the proxy instead of re-transmitting result.In any case,delivery of redundant messages is not a ma-jor problem,since it can be assumed that the is able to identify duplicated messages.If the wireless communication is reliable,re-transmissions of the result with the Result Delivery Protocol(RDP)occur only if the mean time period a spends in a cell is less than,where and are the average transmission times for the wired and wireless communication,respectively. This is unlikely to be the case for current mobile support systems where the diameter of the cells is of reasonable size,e.g.some kilometers.The major advantage is that,except for the proxy ref-erence,neither result forwarding pointers nor other residue (e.g.copies of the result message)need to be kept at the,i.e.the can discard the result message after a single attempt to forward it to the local3.The overhead of this protocol is limited to the follow-ing extra messages:(1)one update currL whenever the mobile host migrates or becomes active again;and(2)one extra Ack message sent from respMss to the proxy when-ever acknowledges the receipt of result.Besides,every request from the mobile host to an application server has to pass through the proxy,so that the proxy can hold it as pending.Our work extends the indirect model of Badrinath et al.[2]in the sense that the proxy represents yet another communication mediator between the mobile client and the server.The main advantage of using a proxy is that from the server’s point of view,the service is being requested from a fixed client(i.e.the proxy),which transparently handles all the mobility of the client it pared with sim-ilar approaches[3,1]our protocol aims at minimizing the transfer of a’s state between the old and new dur-ing Hand-off,because most of the data related to the request (e.g.the result)is kept at the proxy.The Result Delivery Protocol is being implemented as a prototype system in the scope of the SIDAM Project.In this prototype,we are simulating host mobility through ran-dom communication between distributed processes(repre-senting s,and servers)within a Linux network. Using this prototype,we will test this protocol concerning its efficiency with respect to several patterns of mobility, queries and subscriptions.At a future step,we intend to re-implement it in a network with real wireless communication support.The main advantage of the RDP protocol is that although at each moment only a single is responsible for re-transmitting the request results for a given,the proto-col facilitates dynamic global load balancing within the set of s.Moreover,the protocol guarantees that eventually every result will be delivered to the requesting despite any number of migrations and periods of inactivity. AcknowledgmentsWe gratefully acknowledge Ricardo da Rocha and our colleagues from project SIDAM for their valuable com-ments and suggestions.Project SIDAM is being supported by FAPESP(Grant no.98/06138-2).References[1]Arup Acharya and B.R.Badrinath.Delivering multi-cast messages in networks with mobile hosts.In13th International Conference on Distributed Computing Systems,pages292–299,Pittsburgh,US,May1993.[2]B.R.Badrinath, A.Bakre,T.Imielinski,andR.Marantz.Handling Mobile Clients:A Case for In-direct Interaction.In Proc.4th Workstation Operating Systems,October1993.[3]A.Bakre.Design and Implementation of Indirect Pro-tocols for Mobile Wireless Environments.PhD thesis, Rutgers University,October1996.[4]S.Biaz and N.H.Vaidya.Tolerating visitor locationregister failures in mobile environments.In Seven-teenth IEEE Symposium on Reliable Distributed Sys-tems(SRDS’98),pages109–117,Washington-Brus-sels-Tokyo,October1998.IEEE.[5]A.Demers,K.Petersen,M.Spreitzer, D.Terry,M.Theimer,and B.Welch.The Bayou Architecture: Support for Data Sharing Among Mobile Users.In Workshop on Mobile Computing Systems and Appli-cations,Santa Cruz,CA,U.S.,94.[6]M.H.Dunham and V.Kumar.Impact of Mobil-ity on Transaction Management.In Proc.of Mo-biDE/Mobicom99Workshop,Seattle,WA,pages14–21.ACM,August1999.[7]M.Endler.A protocol for atomic multicast amongmobile hosts.In Dial M Workshop/Mobicom’99,Sea-tle(USA),pages56–63.ACM,August1999.[8]M.Haar,R.Cunningham,and V.Cahill.Supportingcorba applications in a mobile environment.In Proc.of MobiCom99,Settle,WA,pages36–47.ACM,Au-gust1999.[9]T.Imielinski and B.R.Badrinath.Querying in highlymobile distributed environments.In Proc.of the18th VLDB Conference,1992.[10]David B.Johnson and David A.Maltz.Protocols foradaptive wireless and mobile networking.IEEE Per-sonal Comunications,3(1),February1996.[11]A.D.Joseph,J.A.Tauber,and M.F.Kaashoek.MobileComputing with the Rover Toolkit.IEEE Transactions on Computers,February1997.[12]E.Pintoura and B.Bhargava.Building informationsystems for mobile environments.In Proc.3rd Inter-national Conference on Information and Knowledge Management,pages371–378,1994.[13]E.Pintoura and B.Bhargava.Revising transactionconcepts for mobile computing.In Proc.IEEE Work-shop on Mobile Computing Systems and Applications, pages164–168,1994.[14]E.A.Brewer R.H.Katz.The Case for Wireless Over-lay Networks.In Proc.of the SPIE Conference on Multimedia and Networking,(MMCM’96),San Jose, CA,January1996.[15]O.Wolfson Y.Huang.Allocation in DistributedDatabases and Mobile Computers.IEEE Transactions on Parallel and Distributed Systems,9(4),April1998.。


AIX6.1系统安装配置手册一、检查收集 (3)二、准备 (3)三、AIX系统安装 (3)3.1 AIX安装方式简介 (3)3.2 AIX系统光盘安装具体步骤 (4)3.3通过定制的mksysb磁带安装 (6)3.3.1设置启动顺序 (7)3.3.2选择install from a System Backup的安装方式 (10)3.3.3开始安装 (11)3.3.4安装完成后操作系统自动重启动 (12)3.4安装bundles软件 (12)3.5安装单独的软件包 (13)3.6安装中文环境软件包 (15)3.7打Fix packs补丁 (16)3.8验证软件安装 (17)3.9完成操作系统安装 (17)3.10镜像rootvg (18)四、AIX系统配置及参数修改 (20)4.1设置主机名 (20)4.1.1hostname设置 (20)4.1.2登陆提示符PS1设置 (21)4.2配置网卡绑定、IP地址 (21)4.2.1网卡绑定配置 (21)4.2.2解绑网卡 (23)4.2.3IP地址配置 (24)4.2.4IPV4升级IPV6 (25)4.3配置网络路由 (27)4.3.1配置default gateway (27)4.3.2配置静态路由 (27)4.3.3检查路由配置 (28)4.4设置系统时区及时间 (28)4.5参数设置 (30)4.6安全设置 (31)4.6.1关闭不使用的系统服务 (31)4.6.2禁止不用的用户登录 (31)4.6.3通过IP限制用户远程登录 (32)4.6.4 FTP配置 (34)4.7SSH安装 (36)4.7.1软件安装 (36)4.7.2配置SSH (38)4.8LVM管理 (46)4.8.1添加硬盘 (47)4.8.2修改磁盘属性的命令chpv (47)4.8.3显示物理卷的信息 (48)4.8.4删除物理卷 (48)4.8.5卷组相关 (48)4.8.6逻辑卷文件系统 (50)4.9创建用户、组 (51)4.10 Paging Space (52)4.11 安装中文语言包 (55)4.12安装Bash shell (58)4.13 NTP服务配置 (59)4.14NFS配置 (62)4.14.1常规配置 (62)4.14.2做光驱NFS映射 (64)4.14.3AIX中NFS的配置示例 (66)4.15常用备份恢复命令 (72)4.16限制root用户通过telnet/ssh/rlogin登录至power服务器 (75)4.17ASMI(超级系统管理口)的使用 (75)4.18 数据库和应用自启动脚本配置 (78)4.19 AIX中samba Server的配置方法 (78)4.20AIX中普通用户拥有sqlplus的执行权限配置方法 (79)五、附录.系统补丁介绍及安装下载步骤 (80)TL是什么? (80)SP是什么? (81)CSP是什么? (81)IF是什么? (82)Fileset是什么? (82)PTF是什么? (82)APAR是什么? (83)怎么样安装AIX 补丁或者补丁集 (83)安装文件集 (84)安装补丁 (85)安装补丁集 (85)下载61-03-06-1034的示列 (86)一、检查收集检查设备外观完整性,加电测试,检查附带软件、光盘证书齐全性。
计算机缩写术语完全介绍计算机专业英语, 缩写在使用计算机的过程中,你可能会碰到各种各样的专业术语,特别是那些英文缩写常让我们不知所云,下面收集了各方面的词组,希望对大家有帮助。
一、港台术语与内地术语之对照由于港台的计算机发展相对快一些,许多人都去香港或台湾寻找资料,但是港台使用的电脑专业术语与内地不尽相同,你也许曾被这些东西弄得糊里糊涂的。
---------------------------港台术语内地术语埠接口位元位讯号信号数码数字类比模拟高阶高端低阶低端时脉时钟频宽带宽光碟光盘磁碟磁盘硬碟硬盘程式程序绘图图形数位数字网路网络硬体硬件软体软件介面接口母板主板主机板主板软碟机软驱记忆体内存绘图卡显示卡监视器显示器声效卡音效卡解析度分辨率相容性兼容性数据机调制解调器---------------------------二、英文术语完全介绍在每组术语中,按照英文字母的排列顺序来分类。
1、CPU3DNow!(3D no waiting,无须等待的3D处理)AAM(AMD Analyst Meeting,AMD分析家会议)ABP(Advanced Branch Prediction,高级分支预测)ACG(Aggressive Clock Gating,主动时钟选择)AIS(Alternate Instruction Set,交替指令集)ALAT(advanced load table,高级载入表)ALU(Arithmetic Logic Unit,算术逻辑单元)Aluminum(铝)AGU(Address Generation Units,地址产成单元)APC(Advanced Power Control,高级能源控制)APIC(Advanced rogrammable Interrupt Controller,高级可编程中断控制器)APS(Alternate Phase Shifting,交替相位跳转)ASB(Advanced System Buffering,高级系统缓冲)ATC(Advanced Transfer Cache,高级转移缓存)ATD(Assembly Technology Development,装配技术发展)BBUL(Bumpless Build-Up Layer,内建非凹凸层)BGA(Ball Grid Array,球状网阵排列)BHT(branch prediction table,分支预测表)Bops(Billion Operations Per Second,10亿操作/秒)BPU(Branch Processing Unit,分支处理单元)BP(Brach Pediction,分支预测)BSP(Boot Strap Processor,启动捆绑处理器)BTAC(Branch Target Address Calculator,分支目标寻址计算器)CBGA (Ceramic Ball Grid Array,陶瓷球状网阵排列)CDIP (Ceramic Dual-In-Line,陶瓷双重直线)Center Processing Unit Utilization,中央处理器占用率CFM(cubic feet per minute,立方英尺/秒)CMT(course-grained multithreading,过程消除多线程)CMOS(Complementary Metal Oxide Semiconductor,互补金属氧化物半导体)CMOV(conditional move instruction,条件移动指令)CISC(Complex Instruction Set Computing,复杂指令集计算机)CLK(Clock Cycle,时钟周期)CMP(on-chip multiprocessor,片内多重处理)CMS(Code Morphing Software,代码变形软件)co-CPU(cooperative CPU,协处理器)COB(Cache on board,板上集成缓存,做在CPU卡上的二级缓存,通常是内核的一半速度))COD(Cache on Die,芯片内核集成缓存)Copper(铜)CPGA(Ceramic Pin Grid Array,陶瓷针型栅格阵列)CPI(cycles per instruction,周期/指令)CPLD(Complex Programmable Logic Device,?}?s可程式化元件)CPU(Center Processing Unit,中央处理器)CRT(Cooperative Redundant Threads,协同多余线程)CSP(Chip Scale Package,芯片比例封装)CXT(Chooper eXTend,增强形K6-2内核,即K6-3)Data Forwarding(数据前送)dB(decibel,分贝)DCLK(Dot Clock,点时钟)DCT(DRAM Controller,DRAM控制器)DDT(Dynamic Deferred Transaction,动态延期处理)Decode(指令解码)DIB(Dual Independent Bus,双重独立总线)DMT(Dynamic Multithreading Architecture,动态多线程结构)DP(Dual Processor,双处理器)DSM(Dedicated Stack Manager,专门堆栈管理)DSMT(Dynamic Simultaneous Multithreading,动态同步多线程)DST(Depleted Substrate Transistor,衰竭型底层晶体管)DTV(Dual Threshold Voltage,双重极限电压)DUV(Deep Ultra-Violet,纵深紫外光)EBGA(Enhanced Ball Grid Array,增强形球状网阵排列)EBL(electron beam lithography,电子束平版印刷)EC(Embedded Controller,嵌入式控制器)EDEC(Early Decode,早期解码)Embedded Chips(嵌入式)EPA(edge pin array,边缘针脚阵列)EPF(Embedded Processor Forum,嵌入式处理器论坛)EPL(electron projection lithography,电子发射平版印刷)EPM(Enhanced Power Management,增强形能源管理)EPIC(explicitly parallel instruction code,并行指令代码)EUV(Extreme Ultra Violet,紫外光)EUV(extreme ultraviolet lithography,极端紫外平版印刷)FADD(Floating Point Addition,浮点加)FBGA(Fine-Pitch Ball Grid Array,精细倾斜球状网阵排列)FBGA(flipchip BGA,轻型芯片BGA)FC-BGA(Flip-Chip Ball Grid Array,反转芯片球形栅格阵列)FC-PGA(Flip-Chip Pin Grid Array,反转芯片针脚栅格阵列)FDIV(Floating Point Divide,浮点除)FEMMS:Fast Entry/Exit Multimedia State,快速进入/退出多媒体状态FFT(fast Fourier transform,快速热欧姆转换)FGM(Fine-Grained Multithreading,高级多线程)FID(FID:Frequency identify,频率鉴别号码)FIFO(First Input First Output,先入先出队列)FISC(Fast Instruction Set Computer,快速指令集计算机)flip-chip(芯片反转)FLOPs(Floating Point Operations Per Second,浮点操作/秒)FMT(fine-grained multithreading,纯消除多线程)FMUL(Floating Point Multiplication,浮点乘)FPRs(floating-point registers,浮点寄存器)FPU(Float Point Unit,浮点运算单元)FSUB(Floating Point Subtraction,浮点减)GFD(Gold finger Device,金手指超频设备)GHC(Global History Counter,通用历史计数器)GTL(Gunning Transceiver Logic,射电收发逻辑电路)GVPP(Generic Visual Perception Processor,常规视觉处理器)HL-PBGA: 表面黏著,高耐热、轻薄型塑胶球状网阵封装HTT(Hyper-Threading Technology,超级线程技术)Hz(hertz,赫兹,频率单位)IA(Intel Architecture,英特尔架构)IAA(Intel Application Accelerator,英特尔应用程序加速器)ICU(Instruction Control Unit,指令控制单元)ID(identify,鉴别号码)IDF(Intel Developer Forum,英特尔开发者论坛)IEU(Integer Execution Units,整数执行单元)IHS(Integrated Heat Spreader,完整热量扩展)ILP(Instruction Level Parallelism,指令级平行运算)IMM: Intel Mobile Module, 英特尔移动模块Instructions Cache,指令缓存Instruction Coloring(指令分类)IOPs(Integer Operations Per Second,整数操作/秒)IPC(Instructions Per Clock Cycle,指令/时钟周期)ISA(instruction set architecture,指令集架构)ISD(inbuilt speed-throttling device,内藏速度控制设备)ITC(Instruction Trace Cache,指令追踪缓存)ITRS(International Technology Roadmap for Semiconductors,国际半导体技术发展蓝图)KNI(Katmai New Instructions,Katmai新指令集,即SSE)Latency(潜伏期)LDT(Lightning Data Transport,闪电数据传输总线)LFU(Legacy Function Unit,传统功能单元)LGA(land grid array,接点栅格阵列)LN2(Liquid Nitrogen,液氮)Local Interconnect(局域互连)MAC(multiply-accumulate,累积乘法)mBGA (Micro Ball Grid Array,微型球状网阵排列)nm(namometer,十亿分之一米/毫微米)MCA(machine check architecture,机器检查体系)MCU(Micro-Controller Unit,微控制器单元)MCT(Memory Controller,内存控制器)MESI(Modified, Exclusive, Shared, Invalid:修改、排除、共享、废弃)MF(MicroOps Fusion,微指令合并)mm(micron metric,微米)MMX(MultiMedia Extensions,多媒体扩展指令集)MMU(Multimedia Unit,多媒体单元)MMU(Memory Management Unit,内存管理单元)MN(model numbers,型号数字)MFLOPS(Million Floating Point/Second,每秒百万个浮点操作)MHz(megahertz,兆赫)mil(PCB 或晶片?丫值拈L度?挝唬?1 mil = 千分之一英寸)MIPS(Million Instruction Per Second,百万条指令/秒)MOESI(Modified, Owned, Exclusive, Shared or Invalid,修改、自有、排除、共享或无效)MOF(Micro Ops Fusion,微操作熔合)Mops(Million Operations Per Second,百万次操作/秒)MP(Multi-Processing,多重处理器架构)MPF(Micro processor Forum,微处理器论坛)MPU(Microprocessor Unit,微处理器)MPS(MultiProcessor Specification,多重处理器规范)MSRs(Model-Specific Registers,特别模块寄存器)MSV(Multiprocessor Specification Version,多处理器规范版本)NAOC(no-account OverClock,无效超频)NI(Non-Intel,非英特尔)NOP(no operation,非操作指令)NRE(Non-Recurring Engineering charge,非重?}性工程?M用)OBGA(Organic Ball Grid Arral,有机球状网阵排列)OCPL(Off Center Parting Line,远离中心部分线队列)OLGA(Organic Land Grid Array,有机平面网阵包装)OoO(Out of Order,乱序执行)OPC(Optical Proximity Correction,光学临近修正)OPGA(Organic Pin Grid Array,有机塑料针型栅格阵列)OPN(Ordering Part Number,分类零件号码)PAT(Performance Acceleration Technology,性能加速技术)PBGA(Plastic Pin Ball Grid Array,塑胶球状网阵排列)PDIP (Plastic Dual-In-Line,塑料双重直线)PDP(Parallel Data Processing,并行数据处理)PGA(Pin-Grid Array,引脚网格阵列),耗电大PLCC (Plastic Leaded Chip Carriers,塑料行间芯片运载)Post-RISC(加速RISC,或后RISC)PR(Performance Rate,性能比率)PIB(Processor In a Box,盒装处理器)PM(Pseudo-Multithreading,假多线程)PPGA(Plastic Pin Grid Array,塑胶针状网阵封装)PQFP(Plastic Quad Flat Package,塑料方块平面封装)PSN(Processor Serial numbers,处理器序列号)QFP(Quad Flat Package,方块平面封装)QSPS(Quick Start Power State,快速启动能源状态)RAS(Return Address Stack,返回地址堆栈)RAW(Read after Write,写后读)REE(Rapid Execution Engine,快速执行引擎)Register Contention(抢占寄存器)Register Pressure(寄存器不足)Register Renaming(寄存器重命名)Remark(芯片频率重标识)Resource contention(资源冲突)Retirement(指令引退)RISC(Reduced Instruction Set Computing,精简指令集计算机)ROB(Re-Order Buffer,重排序缓冲区)RSE(register stack engine,寄存器堆栈引擎)RTL(Register Transfer Level,?捍嫫鬓D?Q?印S搀w描述?Z言的一?N描述?哟危? SC242(242-contact slot connector,242脚金手指插槽连接器)SE(Special Embedded,特别嵌入式)SEC(Single Edge Connector,单边连接器)SECC(Single Edge Contact Cartridge,单边接触卡盒)SEPP(Single Edge Processor Package,单边处理器封装)Shallow-trench isolation(浅槽隔离)SIMD(Single Instruction Multiple Data,单指令多数据流)SiO2F(Fluorided Silicon Oxide,二氧氟化硅)SMI(System Management Interrupt,系统管理中断)SMM(System Management Mode,系统管理模式)SMP(Symmetric Multi-Processing,对称式多重处理架构)SMT(Simultaneous multithreading,同步多线程)SOI(Silicon-on-insulator,绝缘体硅片)SOIC (Plastic Small Outline,塑料小型)SONC(System on a chip,系统集成芯片)SPGA(Staggered Pin Grid Array、交错式针状网阵封装)SPEC(System Performance Evaluation Corporation,系统性能评估测试)SQRT(Square Root Calculations,平方根计算)SRQ(System Request Queue,系统请求队列)SSE(Streaming SIMD Extensions,单一指令多数据流扩展)SFF(Small Form Factor,更小外形格局)SS(Special Sizing,特殊缩放)SSP(Slipstream processing,滑流处理)SST(Special Sizing Techniques,特殊筛分技术)SSOP (Shrink Plastic Small Outline,缩短塑料小型)STC(Space Time Computing,空余时间计算)Superscalar(超标量体系结构)TAP(Test Access Port,测试存取端口)TBGA(Tie Ball Grid Array,带状球形光栅阵列)TCP: Tape Carrier Package(薄膜封装),发热小TDP(Thermal Design Power,热量设计功率)Throughput(吞吐量)TLB(Translate Look side Buffers,转换旁视缓冲器)TLP(Thread-Level Parallelism,线程级并行)TMP(Threaded Multi-Path,线程多通道)TPI(True Performance Initiative/index,真实性能为先/指标)TQFP (Thin Plastic Quad Flat Pack,薄型方面平面封装)Trc(Row Cycle Time,列循环时间)TrD(Transistor Density,晶体管密度)TSOP(Thin Small Outline Plastic,薄型小型塑料)USWC(Uncacheabled Speculative Write Combination,无缓冲随机联合写操作)VALU(Vector Arithmetic Logic Unit,向量算术逻辑单元)VFSD(Vertex Frequency Stream Divider,顶点频率流分隔)VID(VID:Voltage identify,电压鉴别号码)VLIW(Very Long Instruction Word,超长指令字)VPU(Vector Permutate Unit,向量排列单元)VPU(vector processing units,向量处理单元,即处理MMX、SSE等SIMD指令的地方)VSA(Virtual System Architecture,虚拟系统架构)VTF(VIA Technical Forum,威盛技术论坛)XBar(Crossbar,交叉口闩仲载逻辑单元)XP(Experience,体验)XP(Extra performance,额外性能)XP(eXtreme Performance,极速性能)散热器TFT(Tiny Fin Technology,微型鳍片技术)2、主板3GIO(Third Generation Input/Output,第三代输入输出技术)ACR(Advanced Communications Riser,高级通讯升级卡)ADIMM(advanced Dual In-line Memory Modules,高级双重内嵌式内存模块)AGTL+(Assisted Gunning Transceiver Logic,援助发射接收逻辑电路)AIMM(AGP Inline Memory Module,AGP板上内存升级模块)AMR(Audio/Modem Riser;音效/调制解调器主机板附加直立插卡)AHA(Accelerated Hub Architecture,加速中心架构)AOI(Automatic Optical Inspection,自动光学检验)APU(Audio Processing Unit,音频处理单元)ARF(Asynchronous Receive FIFO,异步接收先入先出)ASF(Alert Standards Forum,警告标准讨论)ASK IR(Amplitude Shift Keyed Infra-Red,长波形可移动输入红外线)AT(Advanced Technology,先进技术)ATX(AT Extend,扩展型AT)BIOS(Basic Input/Output System,基本输入/输出系统)CNR(Communication and Networking Riser,通讯和网络升级卡)CSA(Communication Streaming Architecture,通讯流架构)CSE(Configuration Space Enable,可分配空间)COAST(Cache-on-a-stick,条状缓存)DASP(Dynamic Adaptive Speculative Pre-Processor,动态适应预测预处理器)DB: Device Bay,设备插架DMI(Desktop Management Interface,桌面管理接口)DOT(Dynamic Overclocking Technonlogy,动态超频技术)DPP(direct print Protocol,直接打印协议DRCG(Direct Rambus clock generator,直接RAMBUS时钟发生器)DVMT(Dynamic Video Memory Technology,动态视频内存技术)E(Economy,经济,或Entry-level,入门级)EB(Expansion Bus,扩展总线)EFI(Extensible Firmware Interface,扩展固件接口)EHCI(Enhanced Host Controller Interface,加强型主机端控制接口)EISA(Enhanced Industry Standard Architecture,增强形工业标准架构)EMI(Electromagnetic Interference,电磁干扰)ESCD(Extended System Configuration Data,可扩展系统配置数据)ESR(Equivalent Series Resistance,等价系列电阻)FBC(Frame Buffer Cache,帧缓冲缓存)FireWire(火线,即IEEE1394标准)FlexATX(Flexibility ATX,可扩展性ATX)FSB(Front Side Bus,前端总线)FWH(Firmware Hub,固件中心)GB(Garibaldi架构,Garibaldi基于ATX架构,但是也能够使用WTX构架的机箱)GMCH(Graphics & Memory Controller Hub,图形和内存控制中心)GPA(Graphics Performance Accelerator,图形性能加速卡)GPIs(General Purpose Inputs,普通操作输入)GTL+(Gunning Transceiver Logic,发射接收逻辑电路)HDIT(High Bandwidth Differential Interconnect Technology,高带宽微分互连技术)HSLB(High Speed Link Bus,高速链路总线)HT(HyperTransport,超级传输)I2C(Inter-IC)I2C(Inter-Integrated Circuit,内置集成电路)IBASES(Intel Baseline AGP System Evaluation Suite,英特尔基线AGP系统评估套件)IC(integrate circuit,集成电路)ICH(Input/Output Controller Hub,输入/输出控制中心)ICH-S(ICH-Hance Rapids,ICH高速型)ICP(Integrated Communications Processor,整合型通讯处理器)IHA(Intel Hub Architecture,英特尔Hub架构)IMB(Inter Module Bus,隐藏模块总线)INTIN(Interrupt Inputs,中断输入)IPMAT(Intel Power Management Analysis Tool,英特尔能源管理分析工具)IR(infrared ray,红外线)IrDA(infrared ray,红外线通信接口,可进行局域网存取和文件共享)ISA(Industry Standard Architecture,工业标准架构)ISA(instruction set architecture,工业设置架构)K8HTB(K8 HyperTransport Bridge,K8闪电传输桥)LSI(Large Scale Integration,大规模集成电路)LPC(Low Pin Count,少针脚型接口)MAC(Media Access Controller,媒体存储控制器)MBA(manage boot agent,管理启动代理)MC(Memory Controller,内存控制器)MCA(Micro Channel Architecture,微通道架构)MCH(Memory Controller Hub,内存控制中心)MDC(Mobile Daughter Card,移动式子卡)MII(Media Independent Interface,媒体独立接口)MIO(Media I/O,媒体输入/输出单元)MOSFET(metallic oxide semiconductor field effecttransistor,金属氧化物半导体场效应晶体管)MRH-R(Memory Repeater Hub,内存数据处理中心)MRH-S(SDRAM Repeater Hub,SDRAM数据处理中心)MRIMM(Media-RIMM,媒体RIMM扩展槽)MSI(Message Signaled Interrupt,信息信号中断)MSPCE(Multiple Streams with Pipelining and Concurrent Execution,多重数据流的流水线式传输与并发执行)MT=MegaTransfers(兆传输率)MTH(Memory Transfer Hub,内存转换中心)MuTIOL(Multi-Threaded I/O link,多线程I/O链路)NGIO(Next Generation Input/Output,新一代输入/输出标准)NPPA(nForce Platform Processor Architecture,nForce平台处理架构)OHCI(Open Host Controller Interface,开放式主控制器接口)ORB(operation request block,操作请求块)ORS(Over Reflow Soldering,再流回焊接,SMT元件的焊接方式)P64H(64-bit PCI Controller Hub,64位PCI控制中心)PCB(printed circuit board,印刷电路板)PCBA(Printed Circuit Board Assembly,印刷电路板装配)PCI(Peripheral Component Interconnect,互连外围设备)PCI SIG(Peripheral Component Interconnect Special Interest Group,互连外围设备专业组)PDD(Performance Driven Design,性能驱动设计)PHY(Port Physical Layer,端口物理层)POST(Power On Self Test,加电自测试)PS/2(Personal System 2,第二代个人系统)PTH(Plated-Through-Hole technology,镀通孔技术)RE(Read Enable,可读取)QP(Quad-Pumped,四倍泵)RBB(Rapid BIOS Boot,快速BIOS启动)RNG(Random number Generator,随机数字发生器)RTC(Real Time Clock,实时时钟)KBC(KeyBroad Control,键盘控制器)SAP(Sideband Address Port,边带寻址端口)SBA(Side Band Addressing,边带寻址)SBC(single board computer,单板计算机)SBP-2(serial bus protocol 2,第二代串行总线协协)SCI(Serial Communications Interface,串行通讯接口)SCK (CMOS clock,CMOS时钟)SDU(segment data unit,分段数据单元)SFF(Small Form Factor,小尺寸架构)SFS(Stepless Frequency Selection,步进频率选项)SMA(Share Memory Architecture,共享内存结构)SMT(Surface Mounted Technology,表面黏贴式封装)SPI(Serial Peripheral Interface,串行外围设备接口)SSLL(Single Stream with Low Latency,低延迟的单独数据流传输)STD(Suspend To Disk,磁盘唤醒)STR(Suspend To RAM,内存唤醒)SVR(Switching Voltage Regulator,交换式电压调节)THT(Through Hole Technology,插入式封装技术)UCHI(Universal Host Controller Interface,通用宿主控制器接口)UPA(Universal Platform Architecture,统一平台架构)UPDG(Universal Platform Design Guide,统一平台设计导刊)USART(Universal Synchronous Asynchronous Receiver Transmitter,通用同步非同步接收传送器)USB(Universal Serial Bus,通用串行总线)USDM(Unified System Diagnostic Manager,统一系统监测管理器)VID(Voltage Identification Definition,电压识别认证)VLB(Video Electronics Standards Association Local Bus,视频电子标准协会局域总线)VLSI(Very Large Scale Integration,超大规模集成电路)VMAP(VIA Modular Architecture Platforms,VIA模块架构平台)VSB(V Standby,待命电压)VXB(Virtual Extended Bus,虚拟扩展总线)VRM(Voltage Regulator Module,电压调整模块)WE(Write Enalbe,可写入)WS(Wave Soldering,波峰焊接,THT元件的焊接方式)XT(Extended Technology,扩充技术)ZIF(Zero Insertion Force, 零插力插座)芯片组ACPI(Advanced Configuration and Power Interface,先进设置和电源管理)AGP(Accelerated Graphics Port,图形加速接口)BMS(Blue Magic Slot,蓝色魔法槽)I/O(Input/Output,输入/输出)MIOC: Memory and I/O Bridge Controller,内存和I/O桥控制器NBC: North Bridge Chip(北桥芯片)PIIX: PCI ISA/IDE Accelerator(加速器)PSE36: Page Size Extension 36-bit,36位页面尺寸扩展模式PXB: PCI Expander Bridge,PCI增强桥RCG: RAS/CAS Generator,RAS/CAS发生器SBC: South Bridge Chip(南桥芯片)SMB(System Management Bus,全系统管理总线)SPD(Serial Presence Detect,连续存在检测装置)SSB: Super South Bridge,超级南桥芯片TDP: Triton Data Path(数据路径)TSC: Triton System Controller(系统控制器)QPA: Quad Port Acceleration(四接口加速)3、显示设备AD(Analog to Digitalg,模拟到数字转换)ADC(Apple Display Connector,苹果专用显示器接口)ASIC(Application Specific Integrated Circuit,特殊应用积体电路)ASC(Auto-Sizing and Centering,自动调效屏幕尺寸和中心位置)ASC(Anti Static Coatings,防静电涂层)ASD(Auto Stereoscopic Display,自动立体显示)AGC(Anti Glare Coatings,防眩光涂层)AG(Aperture Grills,栅条式金属板)ARC(Anti Reflect Coating,防反射涂层)BLA: Bearn Landing Area(电子束落区)BMC(Black Matrix Screen,超黑矩阵屏幕)CCS(Cross Capacitance Sensing,交叉电容感应)cd/m^2(candela/平方米,亮度的单位)CDRS(Curved Directional Reflection Screen,曲线方向反射屏幕)CG-Silicon(Continuous Grain Silicon,连续微粒硅)CNT(carbon nano-tube,碳微管)CRC(Cyclical Redundancy Check,循环冗余检查)CRT(Cathode Ray Tube,阴极射线管)CVS(Compute Visual Syndrome,计算机视觉综合症)DA(Digital to Analog,数字到模拟转换)DDC(Display Data Channel,显示数据通道)DDWG(Digital Display Working Group,数字化显示工作组)DEC(Direct Etching Coatings,表面蚀刻涂层)Deflection Coil(偏转线圈)DFL(Dynamic Focus Lens,动态聚焦)DFP(Digital Flat Panel,数字平面显示标准)DFPG(Digital Flat Panel Group,数字平面显示标准工作组)DFS(Digital Flex Scan,数字伸缩扫描)DIC: Digital Image Control(数字图像控制)Digital Multiscan II(数字式智能多频追踪)DLP(digital Light Processing,数字光处理)DOSD: Digital On Screen Display(同屏数字化显示)DPMS(Display Power Management Signalling,显示能源管理信号)Dot Pitch(点距)DQL(Dynamic Quadrapole Lens,动态四极镜)DSP(Digital Signal Processing,数字信号处理)DSTN(Double layers Super Twisted Nematic,双层超扭曲向列,无源矩阵LCD)DTV(Digital TV,数字电视)DVI(Digital Visual Interface,数字化视像接口)ECD(ElectroChromic Display,电铬显示器)EFEAL(Extended Field Elliptical Aperture Lens,可扩展扫描椭圆孔镜头)FED(Field Emission Displays,电场显示器)Flyback Transformer(回转变压器)FPD(flat panel display,平面显示器)FRC: Frame Rate Control(帧比率控制)GLV(grating-light-valve,光栅亮度阀)HDMI(High Definition Multimedia Interface,高精度多媒体接口)HDTV(high definition television,高清晰度电视)HVD(High Voltage Differential,高分差动)IFT(Infinite FlatTube,无限平面管,三星丹娜)INVAR(不胀铜)IPS(in-plane switching,平面开关)LCD(liquid crystal display,液晶显示屏)LCOS: Liquid Crystal On Silicon(硅上液晶)LED(light emitting diode,光学二级管)L-SAGIC(Low Power-Small Aperture G1 wiht Impregnated Cathode,低电压光圈阴极管)LTPS(Low-Temperature Poly-Si,低温多晶硅)LVD(Low Voltage Differential,低分差动)LVDS(Low Voltage Differential Signal,低分差动信号)LRTC(LCD Response Time Compensation,液晶响应时间补偿)LTPS(Low Temperature Polysilicon,低温多硅显示器)MALS(Multi Astigmatism Lens System,多重散光聚焦系统)MDA(Monochrome Adapter,单色设备)Monochrome Monitor(单色显示器)MS: Magnetic Sensors(磁场感应器)MVA(multi-domain vertical alignment,广域垂直液晶队列)OEL(organic electro-luminescent,有机电镀冷光)OLED(Organic light-emitting diode,有机电激发光显示器)OSD(On Screen Display,同屏显示)PAC(psycho-acoustic compensation,心理声学补偿)P&D(Plug and Display,即插即显)PDP(Plasma Display Panel,等离子显示器)Porous Tungsten(活性钨)PPI(Pixel Per Inch,像素/英寸)RGB(Red、Blue、Green,红、蓝、绿三原色)ROP(raster operations,光栅操作)RSDS: Reduced Swing Differential Signal(小幅度摆动差动信号)SC(Screen Coatings,屏幕涂层)Single Ended(单终结)Shadow Mask(点状阴罩)SXGA(Super eXtended Graphics Array,超级扩展型图形阵列)STN(Super Twisted Nematic,超扭曲向列,无源矩阵)TCO(The Swedish Confederation of Professional Employees,瑞典专业工作人员联合会)TDT(Timeing Detection Table,数据测定表)TMDS(Transition Minimized Differential Signaling,转换极低损耗微分信号)TN(Twisted Nematic,扭曲液晶向列,无源矩阵LCD)TN+film(twisted nematic and retardation film,扭曲液晶向列+延迟薄膜)TICRG: Tungsten Impregnated Cathode Ray Gun(钨传输阴级射线枪)TFT(thin film transistor,薄膜晶体管,有源矩阵LCD)Trinitron(特丽珑)UCC(Ultra Clear Coatings,超清晰涂层)UFB(Ultra-Fine&Bright,新概念超亮度液晶显示屏)UXGA (Ultra Extended Graphics Array,极速扩展图形阵列)VAGP: Variable Aperature Grille Pitch(可变间距光栅)VBI: Vertical Blanking Interval(垂直空白间隙)VESA(Video Electronics Standards Association,视频电子标准协会)VGA(video graphics array,视频图像阵列)VDT(Video Display Terminals,视频显示终端)VRR: Vertical Refresh Rate(垂直扫描频率)VW(Virtual Window,虚拟视窗)XGA(eXtended Graphics Array,扩展型图形阵列)YUV(亮度和色差信号)4、视频3D:Three Dimensional,三维3DCG(3D computer graphics,三维计算机图形)3DS(3D SubSystem,三维子系统)A-Buffer(Accumulation Buffer,积聚缓冲)AA(Accuview Antialiasing,高精度抗锯齿)ADC(Analog to Digital Converter,模数传换器)ADI(Adaptive De-Interlacing,自适应交错化技术)AE(Atmospheric Effects,大气雾化效果)AFC(Advanced Frame Capture、高级画面捕获)AFR(Alternate Frame Rendering,交替渲染技术)Anisotropic Filtering(各向异性过滤)APPE(Advanced Packet Parsing Engine,增强形帧解析引擎)AR(Auto-Resume,自动恢复)AST(amorphous-silicon TFT,非晶硅薄膜晶体管)AV(Analog Video,模拟视频)AV(Audio & Video,音频和视频)B Splines(B样条)BAC(Bad Angle Case,边角损坏采样)Back Buffer,后置缓冲Backface culling(隐面消除)Battle for Eyeballs(眼球大战,各3D图形芯片公司为了争夺用户而作的竞争)Bilinear Filtering(双线性过滤)B.O.D.E(Body、Object、Design、Envioment,人体、物体、设计、环境渲染自动识别)BSP(Binary Space Partitioning,二进制空间分区)CBMC(Crossbar based memory controller,内存控制交叉装置)CBU(color blending unit,色彩混和单位)CEA(Critical Edge Angles,临界边角)CEM(cube environment mapping,立方环境映射)CG(C for Graphics/GPU,用于图形/GPU的可编程语言)CG(Computer Graphics,计算机生成图像)Clipping(剪贴纹理)Clock Synthesizer,时钟合成器compressed textures(压缩纹理)Concurrent Command Engine,协作命令引擎CSC(Colorspace Conversion,色彩空间转换)CSG (constructive solid geometry,建设立体几何)CSS(Content Scrambling System,内容不规则加密)DAC(Digital to Analog Converter,数模传换器)DCD(Directional Correlational De-interlacing,方向关联解交错)DCT(Display Compression Technology,显示压缩技术)DDC(Dynamic Depth Cueing,动态深度暗示)图像DDP(Digital Display Port,数字输出端口)DDS(Direct Draw Surface,直接绘画表面)Decal(印花法,用于生成一些半透明效果,如:鲜血飞溅的场面)DFP(Digital Flat Panel,数字式平面显示器)DFS: Dynamic Flat Shading(动态平面描影),可用作加速Dithering(抖动)Directional Light,方向性光源DM(Displacement mapping,位移贴图)DME(Direct Memory Execute,直接内存执行)DOF(Depth of Field,多重境深)dot texture blending(点型纹理混和)DOT3(Dot product 3 bump mapping,点乘积凹凸映射)Double Buffering(双缓冲区)DPBM(Dot Product Bump Mapping,点乘积凹凸映射)DQUICK(DVD Qualification and Integration Kit,DVD资格和综合工具包)DRA(deferred rendering architecture,延迟渲染架构)DRI(Direct Rendering Infrastructure,基层直接渲染)DSP(Dual Streams Processor,双重流处理器)DVC(Digital Vibrance Control,数字振动控制)DVI(Digital Video Interface,数字视频接口)DVMT(Dynamic Video Memory Technology,动态视频内存技术)DxR: DynamicXTended Resolution(动态可扩展分辨率)DXTC(Direct X Texture Compress,DirectX纹理压缩,以S3TC为基础)Dynamic Z-buffering(动态Z轴缓冲区),显示物体远近,可用作远景E-DDC(Enhanced Display Data Channel,增强形视频数据通道协议,定义了显示输出与主系统之间的通讯通道,能提高显示输出的画面质量)Edge Anti-aliasing(边缘抗锯齿失真)E-EDID(Enhanced Extended Identification Data,增强形扩充身份辨识数据,定义了电脑通讯视频主系统的数据格式)eFB(embedded Frame Buffer,嵌入式帧缓冲)eTM(embedded Texture Buffer,嵌入式纹理缓冲)Execute Buffers,执行缓冲区Embosing,浮雕EMBM(environment mapped bump mapping,环境凹凸映射)Extended Burst Transactions,增强式突发处理Factor Alpha Blending(因子阿尔法混合)Fast Z-clear,快速Z缓冲清除FB(fragment buffer,片段缓冲)FL(fragment list,片段列表)FW(Fast Write,快写,AGP总线的特殊功能)Front Buffer,前置缓冲Flat(平面描影)FL(Function Lookup,功能查找)FMC(Frictionless Memory Control,无阻内存控制)Frames rate is King(帧数为王)FRC(Frame Rate Control,帧率控制)FSAA(Full Scene/Screen Anti-aliasing,全景/屏幕抗锯齿)Fog(雾化效果)flip double buffered(反转双缓存)fog table quality(雾化表画质)F-Buffer(Fragment Stream FIFO Buffer,片段流先入先出缓冲区)GPT(Graphics Performance Toolkit,图形性能工具包)FRJS(Fully Random Jittered Super-Sampling,完全随机移动式超级采样)Fur(软毛效果)GART(Graphic Address Remappng Table,图形地址重绘表)GI(Global Illumination,球形光照)GIC(Gold Immersion Coating,化金涂布技术,纯金材质作为PCB最终层,提升信号完整性)GIF(Graphics Interchange Format,图像交换格式)Gouraud Shading,高洛德描影,也称为内插法均匀涂色GPU(Graphics Processing Unit,图形处理器)GTF(Generalized Timing Formula,一般程序时间,定义了产生画面所需要的时间,包括了诸如画面刷新率等)GTS(Giga Textel Sharder,十亿像素填充率)Guard Band Support(支持保护带)HAL(Hardware Abstraction Layer,硬件抽像化层)HDR(High Dynamic Range,高级动态范围)HDRL(high dynamic-range lighting,高动态范围光线)HDVP(High-Definition Video Processor,高精度视频处理器)HEL: Hardware Emulation Layer(硬件模拟层)HLSL(High Level Shading Language,高级描影语言)HMC(hardware motion compensation,硬件运动补偿)Hierarchical Z(Z分级)high triangle count(复杂三角形计数)HOS(Higher-Order Surfaces,高次序表面)HPDR(High-Precision Dynamic-Range,高精度动态范围)HRAA(High Resolution Anti-aliasing,高分辨率抗锯齿)HSI(High Speed Interconnect,高速内连)HSR(Hidden Surface Removal,隐藏表面移除)HTP(Hyper Texel Pipeline,超级像素管道)HWMC(Hardware Motion Compensation,硬件运动补偿)ICD(Installable Client Driver,可安装客户端驱动程序)iDCT(inverse Discrete Cosine Transformation,负离散余弦转换)IDE(Integrated Development Environment,集成开发环境)Immediate Mode,直接模式IMMT(Intelligent Memory Manager Technology,智能内存管理技术)Imposters(诈欺模型)IPEAK GPT(Intel Performance Evaluation and Analysis Kit - Graphics Performance Toolkit,英特尔性能评估和分析套件 - 图形性能工具包)IPPR: Image Processing and Pattern Recognition(图像处理和模式识别)IR(Immediate Rendering,直接渲染)IRA(immediate-mode rendering architecture,即时渲染架构)IQ(inverse quantization,反转量子化)ITC(Internal True Color,内部真彩色)IVC(Indexed Vertex Cache,索引顶点缓存)JFAA(Jitter Free Anti Aliasing,自由跳跃进抗锯齿)JGSS(Jittered Grid Super-Sampling,移动式栅格超级采样)JPRS(Jittered pseudo random sampling,抖动假取样)Key Frame Interpolation,关键帧插补large textures(大型纹理)LE(low end,低端)LF(Linear Filtering,线性过滤,即双线性过滤)LFB(Linear Frame-Buffer,线性帧缓冲)LFM(Light Field Mapping,光照区域贴图)lighting(光源)lightmap(光线映射)LMA(Lightspeed memory Architecture,光速内存架构)Local Peripheral Bus(局域边缘总线)LOD(Levels-of-Detail,细节级)Lossless Z Compression,无损Z压缩LPF(Low-past filter,低通道滤波器)LSR(Light Shaft Rendering,光线轴渲染)mipmapping(MIP映射)MAC(Mediocre Angle Case,普通角采样)Matrix Vertex Blending,矩阵顶点混和MCM(Multichip Module,多芯片模块)Membrane lighting,隔膜光线Mipmap LOD Bias Adjustment(映射LOD偏移调节)Modulate(调制混合)Motion Compensation,动态补偿motion blur(模糊移动)MPPS:Million Pixels Per Second,百万个像素/秒MRT(Multiple Render Targets,多重渲染目标)MSAA(multisampling Scene/Screen Anti-aliasing,多重采样抗锯齿)Multiplicative Texture Blending(乘法纹理混合)Multi-Resolution Mesh,多重分辨率组合Multi Threaded Bus Master,多线程主控Multitexture(多重纹理)MVSD(Motion Vector Steered de-interlacing,移动向量控制解交错)MXM(Mobile PCI Express Module,移动PCI Express模块)NURBS(Non Uniform Relational B Splines,非统一相关B样条)nerest Mipmap(邻近MIP映射,又叫点采样技术)NGP(Next-Generation Graphics Port,下一代图形接口)NSR(nVidia Shading Rasterizer,nVidia描影光栅引擎)NXL(NVIDIA XPress Link,nViadia X紧迫链路)OGSS(Ordered Grid Super-Sampling,顺序栅格超级采样)ORB(Online ResultBrowser,在线分数浏览)OTES(Outside Thermal Exhaust System,向外热排气系统)Overdraw(透支,全景渲染造成的浪费)partial texture downloads(并行纹理传输)Parallel Processing Perspective Engine(平行透视处理器)。
RTCAST:LightweightMulticastforReal-TimeProcessGroupsTarekAbdelzaher,AneesShaikh,FarnamJahanian,andKangShinReal-timeComputingLaboratoryDepartmentofElectricalEngineeringandComputerScienceTheUniversityofMichiganAnnArbor,Michigan48109–2122zaher,ashaikh,farnam,kgshin@eecs.umich.edu
AbstractWeproposealightweightfault-tolerantmulticastandmem-bershipserviceforreal-timeprocessgroupswhichmayex-changeperiodicandaperiodicmessages.Theservicesup-portsbounded-timemessagetransport,atomicity,andorderformulticastswithinagroupofcommunicatingprocessesinthepresenceofprocessorcrashesandcommunicationfailures.Itguaranteesagreementonmembershipamongthecommunicatingprocessors,andensuresthatmember-shipchanges(e.g.,resultingfromprocessorjoinsordepar-tures)areatomicandorderedwithrespecttomulticastmes-sages.Weprovidetheflexibilityofanevent-triggeredap-proachwiththefastmessagedeliverytimeoftime-triggeredprotocols,suchasTTP[13],wheremessagesaredeliv-eredtotheapplicationimmediatelyuponreception.Thisisachievedwithoutcompromisingagreement,orderandatom-icityproperties.Inadditiontothedesignanddetailsofthealgorithm,wedescribeourimplementationoftheprotocolusingthe-KernelprotocolarchitecturerunningunderRTMach3.0.
1.IntroductionProcessgroupsareawidely-studiedparadigmfordesign-ingdependabledistributedsystemsinbothasynchronous[6,3,19,15]andsynchronous[13,4,11]environments.Inthisapproach,adistributedsystemisstructuredasagroupofcooperatingprocesseswhichprovideservicetotheapplica-tion.Aprocessgroupmaybeused,forexample,toprovideactivereplicationofsystemstateortorapidlydisseminateinformationfromanapplicationtoacollectionofprocesses.MulticastCommunication
Clock Syncronization
GroupMembershipService
Timed Atomic
Real-Time Process Groups
Virtual Network InterfaceUnreliable Unicast CommunicationFigure1.Ageneralframeworkforamiddle-waregroupcommunicationservice
posedprotocolaspartofalargersuiteofmiddlewaregroupcommunicationservicesthatformacomposablearchitec-tureforthedevelopmentofembeddedreal-timeapplica-tions.ShadedblocksinFigure1indicatethoseserviceswhosedesignandimplementationwepresentinthispaper.Theseservicesconsistoftwomajorcomponents,atimedatomicmulticast,andagroupmembershipservice.Theyaretightlycoupledandthusconsideredasingleservice,re-ferredtoasRTCastintheremainderofthepaper.Clocksyn-chronizationisassumedintheprotocolandenforcedbytheclocksynchronizationservice.Tosupportportability,RT-Castmightlieatopalayerexportinganabstractiontermedavirtualnetworkinterface.Ideally,thisinterfacewouldtrans-parentlyhandledifferentnetworktopologies,eachhavingdifferentconnectivityandtimingorbandwidthcharacter-istics.Thenetworkisassumedtosupportunreliableuni-cast.Finally,thetoplayerprovidesfunctional(API)supportforthereal-timeprocessgroupserviceandinterfacestothelowerRTCastprotocol.RTCastproceedsassendersinalogicalringtaketurnsinmulticastingmessagesoverthenetwork.Aprocessor’sturncomeswhenthelogicaltokenarrives,orwhenittimesoutwaitingforit.Afteritslastmessage,eachsendermulticastsaheartbeatthatisusedforcrashdetection.Theheartbeatreceivedfromanimmediatepredecessoralsoservesasthelogicaltoken.Destinationsdetectmissedmessagesusingsequencenumbersandwhenaprocessoredetectsareceiveomission,itcrashes.Eachprocessor,whenitsturncomes,checksformissingheartbeatsandeliminatesthecrashedmembers,ifany,fromgroupmembershipbymulticastingamembershipchangemessage.AkeyattributeofRTCastisthatprocesseswhichdetectreceiveomissionstakethemselvesoutofthegroup.Thispaperarguesthatinareal-timesystemboundedmessagetransmissiontimemustbeachieved.Ifamessage(oritsre-
transmission)doesnotreachadestinationwithinaspecifiedtimebound,thedestinationfailstomeetitsdeadline(s)andshouldbeeliminatedfromthegroup.Inthenextsectionwediscusstherelatedworkonfault-tolerantmulticastandgroupmembershipprotocols.Sec-tions3and4presentoursystemmodelandthedesignoftheRTCastprotocol,respectively.Real-timeschedulabil-ityandadmissioncontrolaredescribedinSection5.Sec-tion6discussesthecurrentimplementationoftheprotocolinthex-KernelprotocoldevelopmentenvironmentandourPC-baseddevelopmenttestbed.Section7concludesthepa-perbydiscussingthelimitationsofthisworkandfuturere-searchdirections.
2RelatedworkSeveralfault-tolerant,atomicorderedmulticastandmem-bershipprotocolshavebeenproposedforuseinasyn-chronousdistributedsystems.Insomeoftheearliestwork,ChangandMaxemchuk[7]proposedatokenbasedalgo-rithmforaprocessgroupwhereeachmembersendsitsmes-sagestoatokensitewhichordersthemessagesandbroad-castsacknowledgments.Destinationsusetheacknowledg-mentstoordermessagesasspecifiedbythetokensite.Thoughthealgorithmprovidesgoodperformanceatlowloads,acknowledgingeachmessagebeforesendingthenextincreaseslatencyathigherloads.Moreover,introducingathirdnode(thetokensite)inthepathofeverymessagemakestheservicelessavailable.Failureofthetokensitewilldelaymessagereceptionevenifboththesourceanddestinationareoperational.Incontrast,RTCastdoesnotac-knowledgeeachmessage,andneednotinvolveaninterme-diatenodeonthepathofeachmessage.ISIS[5,6]introducedtheconceptofvirtualsynchrony,andintegratedamembershipprotocolintothemulticastcommunicationsubsystem,wherebymembershipchangestakeplaceinresponsetocommunicationfailure.ISISim-plementsanatomicorderedmulticastontopofavectorclock-based[14]causalmulticastservice,usinganideasim-ilartothatofChangandMaxemchuk.Whileweintegratemembershipandmulticastservices,weimplementorderedatomicmulticastdirectlywithoutconstructingapartialor-derfirst.Theorderingtask,however,issimplifiedbyas-sumingaringnetwork.InadditiontoISIS,severalothersystemshaveadoptedthenotionoffault-tolerantprocessgroups,usingsimilarabstractionstosupportdistributedap-plications.SomeoftheseincludeConsul[15],Transis[3],andHorus[19].TheStrongGroupMembershipprotocol[12]performsatomicorderedgroupmembershipchangesusingatwophasecommitprotocolwherebyaleaderfirstmulticastsapreparetocommitmessage,andthenmulticastsacommitmessagetoinstallthechangeafterreceivingacknowledg-