1 MULTIMEDIA TRANSPORT PROTOCOL AND MULTICAST COMMUNICATION
- 格式:pdf
- 大小:73.55 KB
- 文档页数:23

中国移动通信企业标准家庭网关终端技术规范版本号:3.0.0中国移动通信集团公司发布╳╳╳╳-╳╳-╳╳发布 ╳╳╳╳-╳╳-╳╳实施QB-╳╳-╳╳╳-╳╳╳╳ T e c h n i c a l S p e c i f i c a t i o n f o r H o m e G a t e w a y目录3.术语、定义和缩略语 ....................................................................................... 错误!未指定书签。
USB扩展及管理(可选)................................................................................ 错误!未指定书签。
DLNA(可选)............................................................................................................... 错误!未指定书签。
5.6.硬件要求....................................................................................................... 错误!未指定书签。
设备面板标识要求........................................................................................... 错误!未指定书签。
操作管理 ...................................................................................................................... 错误!未指定书签。

音视频流媒体传输与编码技术的教程随着互联网的快速发展,音视频流媒体传输已经成为了网络娱乐和通讯的重要组成部分。
在音视频流媒体传输过程中,编码技术扮演着关键的角色。
本文将介绍音视频流媒体传输以及常用的编码技术,帮助读者更好地理解和应用这些技术。
一、音视频流媒体传输基础1. 流媒体传输的概念流媒体传输是指通过网络将音频和视频数据实时传输到终端用户的技术。
与传统的下载方式不同,流媒体允许用户在数据传输过程中及时播放,而不需要等待所有数据下载完成。
这种实时传输的方式可以提供较低的延迟和更好的用户体验。
2. 音视频流媒体传输协议常见的音视频流媒体传输协议包括RTSP(Real-Time Streaming Protocol)、RTMP(Real-Time Messaging Protocol)以及HTTP(Hypertext Transfer Protocol)。
这些协议都有各自的特点和应用场景,如RTSP适用于实时传输,而RTMP则主要用于视频直播。
3. 音视频压缩编码技术由于音视频数据的体积较大,传输时需要较大的带宽和存储空间。
因此,音视频压缩编码技术应运而生。
常见的音频编码包括MP3、AAC等,而视频编码则包括H.264、H.265等。
这些编码技术可以将原始的音视频数据进行压缩,以减小文件大小和传输时的带宽需求。
二、音视频流媒体传输与编码技术详解1. 流媒体传输协议(1) RTSP协议RTSP(Real-Time Streaming Protocol)是一种实时流媒体传输协议,用于控制音视频流的传输和播放。
它支持客户端与服务器之间的交互,并能够动态调整传输速率和分辨率。
RTSP可以通过RTP(Real-time Transport Protocol)传输音视频数据,使得音视频播放更加流畅和稳定。
(2) RTMP协议RTMP(Real-Time Messaging Protocol)是一种传输音视频流的协议,常用于视频直播。
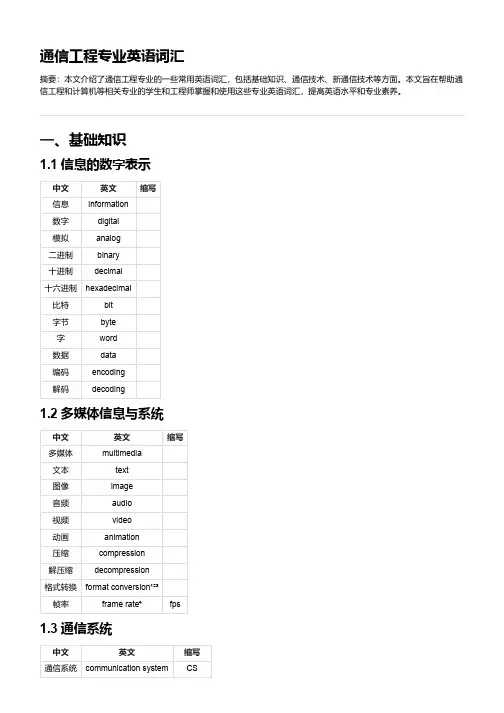
通信工程专业英语词汇摘要:本文介绍了通信工程专业的一些常用英语词汇,包括基础知识、通信技术、新通信技术等方面。
本文旨在帮助通信工程和计算机等相关专业的学生和工程师掌握和使用这些专业英语词汇,提高英语水平和专业素养。
一、基础知识1.1 信息的数字表示中文英文缩写信息information数字digital模拟analog二进制binary十进制decimal十六进制hexadecimal比特bit字节byte字word数据data编码encoding解码decoding1.2 多媒体信息与系统中文英文缩写多媒体multimedia文本text图像image音频audio视频video动画animation压缩compression解压缩decompression格式转换format conversion¹²³帧率frame rate⁴fps1.3 通信系统中文英文缩写通信系统communication system CS中文英文缩写发送端transmitter TX接收端receiver RX信道channel CH信号signal SG噪声noise NS调制modulation MOD解调demodulation DEMOD二、通信技术2.1 有线通信中文英文缩写有线通信wired communication WC电缆cable CB光纤fiber optic FO同轴电缆coaxial cable COAX双绞线twisted pair TP电话线telephone line TL网络线network cable NC屏蔽双绞线shielded twisted pair STP非屏蔽双绞线unshielded twisted pair UTP光纤到户fiber to the home FTTH 2.2 无线通信中文英文缩写无线通信wireless communication WC 无线电波radio wave RW微波microwave MW 红外线infrared IR可见光visible light VL激光laser LS射频radio frequency RF蓝牙Bluetooth BT 红外通信infrared communication IRC 可见光通信visible light communication VLC 射频识别radio frequency identification RFID 近场通信near field communication NFC 蜂窝移动通信cellular mobile communication CMC中文英文缩写卫星通信satellite communication SC全球定位系统global positioning system GPS2.3 网络通信中文英文缩写网络通信network communication NC计算机网络computer network CN局域网local area network LAN广域网wide area network WAN城域网metropolitan area network MAN互联网internet NET互联网协议internet protocol IP传输控制协议transmission control protocol TCP用户数据报协议user datagram protocol UDP超文本传输协议hypertext transfer protocol HTTP超文本标记语言hypertext markup language HTML统一资源定位符uniform resource locator URL网络地址转换network address translation NAT动态主机配置协议dynamic host configuration protocol DHCP 域名系统domain name system DNS三、新通信技术3.1 物联网中文英文缩写物联网internet of things IoT智能家居smart home SH 智能穿戴设备smart wearable device SWD 智能交通系统intelligent transportation system ITS智能电网smart grid SG智慧城市smart city SC 物联网协议栈internet of things protocol stack IoT-PS 物理层physical layer PHY网络层network layer NET传输层transport layer TRA应用层application layer APP 物联网应用协议internet of things application protocol IoT-AP 轻量级传输协议lightweight transport protocol LTP 约束应用协议constrained application protocol CoAP中文英文缩写消息队列遥测传输协议message queue telemetry transport protocol MQTT 物联网安全internet of things security IoT-S 物联网隐私保护internet of things privacy protection IoT-PP3.2 云计算中文英文缩写云计算cloud computing CC云服务提供商cloud service provider CSP云服务用户cloud service user CSU公有云public cloud PC私有云private cloud PC社区云community cloud CC云服务模式cloud service model CSM基础设施即服务infrastructure as a service IaaS平台即服务platform as a service PaaS软件即服务software as a service SaaS函数即服务function as a service FaaS云计算架构cloud computing architecture CCA云端cloud CLD边缘edge EDG3.3 大数据中文英文缩写大数据big data BD数据源data source DS数据清洗data cleaning DC数据转换data transformation DT数据存储data storage DS数据仓库data warehouse DW数据湖data lake DL数据分析data analysis DA数据挖掘data mining DM数据可视化data visualization DV数据安全data security DS数据隐私保护data privacy protection DPP。


物流名词的缩写全称中英文对照(2008-04-29 17:23:57)转载标签:杂谈3G 3rd Generation Networks 第三代網路3PL 3rd Party Logistics 第三方物流4PL 4th Party Logistics 第四方物流5-S Seiri, Seiton, Seiso, Seiketsu, Shitsuke 常組織、常整頓、常規範、常自律AAMPS Administrative Monetary Penalty System 行政罰款制度API Application Programming Interface 程式設定介面ARENA Asia North America Eastbound Rate Agreement 亞洲北美東向運輸協會ASME American Society of Mechanical Engineers 機械工程師美洲協ASP Active Sever Page 動態伺服端網頁AS/RS Automated Storage and Retrieval System 自動化存儲和修復系統操作AWB Air Waybill 空運提單BB2B Business to Business 企業與企業之間的交易B2C Business to Customer 企業與客戶之間的交易BAF Bunker Adjustment Factor 燃油附加費B/B Break Bulk 散件雜貨BCC Blind Carbon Copy 密件抄送BCO Beneficial Cargo Owner 貨物擁有者權益BIMCO The Baltic and International Maritime Council 波羅的海國際海運公會B/L Bill of Lading 海運提單BPO Business Process Outsourcing 企業外判程序BSP British Standard Pipe Tread 英國標準的管子踩踏CCAF Currency Adjustment Factor 幣值附加費CBM Cubic Metre 立方米C&F Cost and Freight 成本和運費CC Carbon Copy 抄送CDMA Code Division Multiple Address 分發(部門)若干位址編碼CEPA Closer Economic Partnership Arrangement 更緊密經貿關系的安排CFM Cubic Feet per Minute 每分鐘的立方尺CFR Cost and Freight 成本和運費CFS Container Freight Station 集裝箱貨物集散站CGI Common Gateway Interface CGI 介面CIF Cost, Insurance and Freight 成本和運費兼付保險費CILT The Chartered Institute of Logisticsand Transport 英國特許物流運輸學會CIM The Chartered Institute of Marketing 英國特許市務學會CIS Commonwealth of Independent States 獨立國家聯合體CLM The Council of Logistics Management 物流管理學會CIP Carriage and Insurance Paid To 兼付指定運費及保險費CLP Container Load Plan 集裝箱/裝載計劃表CNOOC China National Offshore Oil Corp. 中國海洋石油總公司C/O Certificate of Origin 產地來源證C.O.C. Carrier's Own Container 船東提供集裝箱C.D. Cash On Delivery 交貨付現COFC Container-on-flatcar 集裝箱輸送COSCO China Ocean Shipping Company 中國遠洋運輸公司COSL China Oilfield Services Limited 中海油田服務股份有限公司CPFR Collaborative Planning Forecastingand Replenishment 預報和補充合作計劃CPT Carriage Paid To 兼付指定運費CRM Customer Relationship Management 客戶關係管理CSA Customs Self Assessment 海關自我評估程序CSC International Convention for Safe Container 對安全容器的國際規定CY Container Yard 集裝箱堆場DD/A Document Against Acceptance 承兌交單DAF Delivery at Frontier 貨交邊境DDC Destination Delivery Charge 目的地提貨費DDP Delivered Duty Paid 完稅後交貨DDU Delivered Duty Unpaid 未完稅交貨DES Delivered Ex-Ship 貨交指定港口船上DEQ Delivered ex-Quay 貨交指定港口倉庫D.G. Dangerous Good 危險品貨物DNS Domain Name System 網絡領域名字系統D/O Delivery Order 出貨單DOS Disk Operating System 磁盤作業系統D/P Document Against Payment 付款交單DPP Damage Protection Plan 集裝箱損壤保險DRP Distribution Resources Planning 分發資源計劃EECR Efficient Customer Response 有效回應顧客的準則EDI Electronic Data Interchange 電子資訊傳遞E.&O.E. Errors and Omissions Excepted 錯誤和遺漏不在此限ERM Enterprise Resources Management 企業資源管理ERP Enterprise Resources Planning 企業資源計劃ETA Estimated Time of Arrival 預定到達時間ETD Estimated Time of Departure 預定出發時間EXW Ex-Works 到戶取貨FFAF Fuel Adjustment Factor 燃料附加費FAK Freight All Kinds 同一費率FAQ Frequently Asked Question 常見問題FAS Free Alongside Ship 船邊交貨FB/L FIATA Combined Transport Bill of Lading 國際運輸商協會聯運提單FCA Free Carrier 貨交貨運商人FCL Full Container Load 整箱集裝FCR Forwarder's Cargo Receipt 貨運承運人領貨單FEFC Far East Freight Conference 遠東(歐州)運費公會FEU Forty Feet Equivalent Unit 40英呎標準雜裝箱計算單位F.I. Free In 船方負責裝船費用FIATA International Federation of ForwardingAgent Associations 國際運輸商協FIFO First-in, First-out 貨物先進倉和先出倉的安排F.I.O. Free In and Out 船方不負擔裝卸費FIOST Free In, Out, Stowed & Trimmed 船方不負責裝船.卸船.理艙及平艙費用FMC Federal Maritime Commission 美國聯邦海事委員會F.O. Free Out 船方不負責卸船費用FOA Fire Defence Agency (Japanese) 防禦代辦處FOB Free On Board 離岸價格F.O.R. Free On Rail 火車上交貨F.O.T. Free On Truck 貨車上交貨F/R Flat Rack Container 平板集裝箱FRC Fuel Recovery Charge 恢復燃料費FTP File Transfer Protocol 檔案傳輸協定FTZ Free Trade Zones 自由貿易區GGDP Gross Domestic Product 國民生產總值GIF Graphics Interchange Format 圖形學交換版式GPRS General Packet Radio Service 無線電服務GRI General Rate Increasing 全部費率調高GSA General Sales Agent 全球系統之機動通信GSC Global Supply Chain 全球供應鏈GSM Global System for Mobile Communications 總推廣代理GWT Gross Weight 毛重HHAFFA Hong Kong Association of Freight Forwarding and Logistics Ltd. 香港貨運物流業協會有限公司HAWB House Air Waybill 空運代理行提單H/H Half Height Container 半高集裝箱HKIM Hong Kong Institute of Marketing 香港市務學會HTML Hypertext Mark-up Language 超文本記號HTTP Hypertext Transfer Protocol 超文本傳送IIADA Intra Asia Discussion Agreement 亞洲間集裝箱運輸研討協定I.A.Rates Independent Action rates 獨立等級價格IATA International Air Transport Association 國際航空運輸協會IBC Intermediate Bulk Container 中型液體集裝箱ICAO International Civil Aviation Organization 國際民用航空組織ICC International Chamber of Commerce 國際商會ICP Internet Content provider 聯網內容供應商Intranet 企業內聯網Extranet 企業外聯網Internet 企業互聯網ICT Information and Communications Technology 資訊和通信技術IEEE the Institute of Electronic and Electrical Engineering 電子和電的工程學院IICL Institute of International Container Lessors 國際集裝箱出租商學會IMDG International Maritime Dangerous Goods Code 國際危險的商品代碼IMO International Maritime Organization 國際海事組織Incoterms International Commercial terms 國際貿易術語IP Internet Protocol 國際網路議定書IPI Interior Point Intermodal 經美國西岸入內陸運輸IPO Initial Public Offering 首次上市集資項目IRA Informal Rate Agreement 非正式運價協定ISAPI Internet Server Application Programming Interface 網際網路伺服器應用式設計介面ISDN Integrated Server Digital Network 綜合服務數字網路ISO International Standard Organization 國際標準化組織ISP Internet Service Provider 網絡供應商ISPS International Ship and Port Facility Security 國際船舶與港口保安設施規則JJIT Just In Time 運送及時KKbps Kilobits per second 千分之一秒K/T Kilo Tons 公噸LLASH Ligther Aboard Ship 集裝箱子母船LAN Local Area Networking 本區域網絡L/C Letter of Credit 信用證LCL Less (than) container Load 併箱散貨L/G Letter of Guarantee 保函L.I. Liner Inward 入口航線LILO Last-in, Last-out 貨物後進倉和後出倉的安排L.I.O. Liner In and Out 船方負責裝卸費, 但不包碼頭費L.L.M.C Limitation of Liability for Maritime Claims 海事索賠任限制L.O.A. Length Overall 全長Lo-Lo ship Lift-on Lift-off ship 吊裝船LNG Liquefied Natural Gas 液化天然氣LPG Liquefied Petroleum Gas 液化石油汽LTL Less-than-truckload 散貨拼車MMAWB Master Air Waybill 空運提單MB Megabyte 百萬位元MBO Management By Objective 目標管理Mbps Millions of bits per second 數百萬位分之一秒MIS Management Information System 管理資訊系統MLB Mainland Bridge 大陸橋運輸模式MLO Main Line Operators 遠洋船公司MMS Multimedia Messaging Services 多型通訊聯繫服務MPEG Motion Picture Experts Group 活動圖片小組專家MQC Minimum Quantity Commitment 最小數量承諾MRP Material Requirements Planning 材料需要計劃M/S Motor Ship 輪船MSDS Material Safety Data Sheet 材料安全資料表MTO Multimode Transport Operator 聯運商NN/A Not Applicable/Not Available 不適用╱無資料NAP Network Access Point 網路途徑點N.O.E. Not Otherwise Enumerated 除非另有列名N.O.S. Not Otherwise Specified 除非另有指定NVOCC Non Vessel Operating Common Carrier 無船舶公共承運商OOCP Overland Common Point 內陸公共交貨點OEM Original Equipment Manufacturer 原產商O/H Over Height 超出正常高度OPM Other People's Money 籌集資金ORC Origin Receiving Charge 始發港付加費O/S Open Side Container 開邊集裝箱O/T Open Top Container 開頂集裝箱O/W Over Width 超出正常闊度PP2P Path to Profit 對得益的路徑PCD Pitch Circle Diameter 間隔圓圈直徑PCS Port Congestion Surcharge 港口擠塞附加費PDA Personal Digital Assistant 電子手賬PDF Portable Document Format 便攜式文件版式PENAVICO China Ocean Shipping Company 中國外輸代理公司(外代)P&I Club Protection and Indemnity Club 英國標準保賠會PKI Public Key Infrastructure 公開鑰匙基礎POD Port of Discharge 卸貨港POL Port of Loading 裝貨港POP Point of Presence 存在的點PPP Point-to-Point Protocol 點對點的草案PSS Peak Season Surcharge 季節附加費PSTN Public Switched Telephone Network 公開轉換電話網路PTO Please Turn Overleaf 請閱後頁PWS Personal Web Server 私人伺服器QQDII Qualified Domestic Institutional Investors 國內機構投資者赴海外投資資格認定制度QFII Qualified Foreign Institutional Investors 國外機構投資者到內地投資資格認定制度RRAM Random Access Memory 隨機途徑記憶(存儲器)RF Reefer Container 冷藏集裝箱RFP Request For proposal 書面建議要求RFQ Request For Quotation 書面報價要求RFRC Rail Fuel Recovery Charge 軌道燃料恢復費用RMB Renminbi 人民幣Ro-Ro ship Roll-on Roll-off ship 滾裝船ROA Return On Assets 資產回報ROI Return On Investment 投資回報RRS Rate Restoration Surcharge 比率修復附加費R/T Revenue Tons 計費噸SSAN Storage Area Network 網路存儲SET Secure Electronic Transaction 安全電子交易S/C Service Contract 貨量簽訂合同SCM Supply Chain Management 鏈鎖供給管理S.G. Specific Gravity 特殊的重力SKU Stock Keeping Unit 儲備保持的單位SINOTRANS China National Foreign trade and Transportation Corporation 中國對外貿易運輸公司(外運)SNMP Simple Network Management Protocol 簡單網路管理草案SME Small and Medium-size Enterprises 中、小型企業SMS Short Message Services 短訊服務SMTP Simple Mail Transport Protocol 簡單郵件運輸草案S/O Shipping Order 裝船單S.O.C Shipper's Own Container 付貨人所屬集箱SQL Structure Query Language 架構疑問語S/S Steamship 言輪船SSL Secure Socket Layer 付款加密法S.T.C. Said To Contain 據報內裝TTACA Transatlantic Conference Agreement 跨大西洋公會協定TCP Transmission Control Protocol 傳輸控制草案TEU Twenty-foot Equivalent Unit 20英呎標準集裝箱計算單位T.H.C. Terminal Handling Charge 碼頭操作費TMS Transportation Management System 運輸管理系統TOFC Trailer-on-Flatcar 集裝箱車架輸送TQC Total Quality Control 全面品質控制TQM Total Quality Management 全面品質管理T.R.S. Terminal Receiving Station 碼頭收貨站TSA Transpacific Stabilization Agreement 跨太平洋穩定協議TSR Trans Siberian Railway 西伯利亞大鐵路T/T Telegraphic Transfer 電匯TVC Time Volume Contract 時間貨量合同TWRA Transpacific Westbound Rate Agreement 泛太平洋西向運費協會UUCP500 Uniform Customs and practice forDocumentary Credits 跟單信用證統一慣例和實務UHF Ultra High frequency 特高頻ULCC Ultra Large Crude Carrier 50萬噸油輸ULD Unit Load Device 成組器UNCTAD United Nations Conference of Tradeand Development 聯合國貿發會議URL Uniform Resource Locator 網址VV.A.T Value Added Tax 增值稅VHF Very High Frequency 甚高頻VLCC Very Large Crude Carrier 20萬噸油輪VMI Vendor Managed Inventory 供應商的存貨管理系統VOC Vessel Operating Carrier 船舶承運商V.O.W. Vehicle On Wheel 可駕駛的車輛VPN Virtual Private Network 虛擬網路VSL Vessel 輪船WWAP Wireless Appreciation Protocol 無線應(運)用草案WCS Wireless Communications Service 無線通信服務WMS Warehouse Management System 倉庫管理系統W.R. War Risks 兵險W.W. Warehouse Warrant 倉單WWW World Wide Web 全球資訊網XXML Extensible Mark-up Language 可延長的記號語言YYAS Yen Appreciate Surcharge 日圓調整費。

外文资料和中文翻译外文资料:Review of UMTS1.1 UMTS Network ArchitectureThe European/Japanese 3G standard is referred to as UMTS. UMTS is one of a number of standards ratified by the ITU-T under the umbrella of IMT-2000. It is currently the dominant standard, with the US CDMA2000 standard gaining ground, particularly with operators that have deployed cdmaOne as their 2G technology. At time of writing,Japan is the most advanced in terms of 3G network deployment. The three incumbent operators there have implemented three different technologies: J-Phone is using UMTS,KDDI has a CDMA2000 network, and the largest operator NTT DoCoMo is using a system branded as FOMA (Freedom of Multimedia Access). FOMA is based on the original UMTS proposal, prior to its harmonization and standardization.The UMTS standard is specified as a migration from the second generation GSM standard to UMTS via the General Packet Radio System (GPRS) and Enhanced Data for Global Evolution (EDGE), as shown in Figure. This is a sound rationale since as of April 2003, there were over 847 Million GSM subscribers worldwide1, accounting for68% of the global cellular subscriber figures. The emphasis is on keeping as much ofthe GSM network as possible to operate with the new system.We are now well on the road towards Third Generation (3G), where the network will support all traffic types: voice, video and data, and we should see an eventual explosion in the services available on the mobile device. The driving technology for this is the IP protocol. Many cellular operators are now at a position referred to as 2.5G, with the deployment of GPRS, which introduces an IP backbone into the mobile core network.The diagram below, Figure 2, shows an overview of the key components in a GPRS network, and how it fits into the existing GSM infrastructure.The interface between the SGSN and GGSN is known as the Gn interface and uses the GPRS tunneling protocol (GTP, discussed later). The primary reason for the introduction of this infrastructure is to offer connections to external packet networks, such as the Internet or a corporate Intranet.This brings the IP protocol into the network as a transport between the SGSN and GGSN. This allows data services such as email or web browsing on the mobile device,with users being charged based on volume of data rather than time connected.The dominant standard for delivery of 3G networks and services is the Universal Mobile Telecommunications System, or UMTS. The first deployment of UMTS is the Release ’99 architecture, shown below in Figure 3.In this network, the major change is in the radio access network (RAN) with the introduction of CDMA technology for the air interface, and ATM as a transport in the transmission part. These changes have been introduced principally to support the transport of voice, video and data services on the same network. The core network remains relatively unchanged, with primarily software upgrades. However, the IP protocol pushes further into the network with the RNC now communicating with the 3G SGSN using IP.The next evolution step is the Release 4 architecture, Figure 4. Here, the GSM core is replaced with an IP network infrastructure based around Voice over IP technology.The MSC evolves into two separate components: a Media Gateway (MGW) and an MSC Server (MSS). This essentially breaks apart the roles of connection and connection control. An MSS can handle multiple MGWs, making the network more scaleable.Since there are now a number of IP clouds in the 3G network, it makes sense to merge these together into one IP or IP/ATM backbone (it is likely both options will be available to operators.) This extends IP right across the whole network, all the way to the BTS.This is referred to as the All-IP network, or the Release 5 architecture, as shown in Figure 5. The HLR/VLR/EIR are generalised and referred to as the HLR Subsystem(HSS).Now the last remnants of traditional telecommunications switching are removed, leaving a network operating completely on the IP protocol, and generalised for the transport of many service types. Real-time services are supported through the introduction of a new network domain, the IP Multimedia Subsystem (IMS).Currently the 3GPP are working on Release 6, which purports to cover all aspects not addressed in frozen releases. Some call UMTS Release 6 4G and it includes such issues as interworking of hot spot radio access technologies such as wireless LAN.1.2 UMTS FDD and TDDLike any CDMA system, UMTS needs a wide frequency band in which to operate to effectively spread signals. The defining characteristic of the system is the chip rate, where a chip is the width of one symbol of the CDMA code. UMTS uses a chip rate of 3.84Mchips/s and this converts to a required spectrum carrier of 5MHz wide. Since this is wider than the 1.25MHz needed for the existing cdmaOne system, the UMTS air interface is termed ‘wideband’ CDMA.There are actually two radio technologies under the UMTS umbrella: UMTS FDD and TDD. FDD stands for Frequency Division Duplex, and like GSM, separates traffic in the uplink and downlink by placing them at different frequency channels. Therefore an operator must have a pair of frequencies allocated to allow them to run a network, hence the term ‘paired spectrum’. TDD or Time Division Duplex requires only one frequency channel, and uplink and downlink traffic are separated by sending them at different times. The ITU-T spectrum usage, as shown in Figure 6, for FDD is 1920- 980MHz for uplink traffic, and 2110-2170MHz for downlink. The minimum allocation an operator needs is two paired 5MHz channels, one for uplink and one for downlink, at a separation of 190MHz. However, to provide comprehensive coverage and services, it is recommended that an operator be given three channels. Considering the spectrum allocation, there are 12 paired channels available, and many countries have now completed the licencing process for this spectrum, allocating between two and four channels per licence. This has tended to work out a costly process for operators, since the regulatory authorities in some countries, notably in Europe, have auctioned these licences to the highest bidder. This has resulted in spectrum fees as high as tens of billions of dollars in some countries.The Time Division Duplex (TDD) system, which needs only one 5MHz band in which to operate, often referred to as unpaired spectrum. The differences between UMTS FDD and TDD are only evident at the lower layers, particularly on the radio interface. At higher layers, the bulk of the operation of the two systems is the same. As the name suggests, the TDD system separates uplink and downlink traffic by placing them in different time slots. As will be seen later, UMTS uses a 10ms frame structure which is divided into 15 equal timeslots. TDD can allocate these to be either uplink or downlink,with one or more breakpoints between the two in a frame defined. In this way, it is well suited to packet traffic, since this allows great flexibility in dynamically dimensioning for asymmetry in traffic flow.The TDD system should not really be considered as an independent network, but rather as a supplementfor an FDD system to provide hotspot coverage at higher data rates. It is rather unsuitable for large scale deployment due to interference between sites, since a BTS may be trying to detect a weak signal from a UE, which is blocked out by a relatively strong signal at the same frequency from a nearby BTS. TDD is ideal for indoor coverage over small areas.Since FDD is the main access technology being developed currently, the explanations presented here will focus purely on this system.1.3 UMTS Bearer ModelThe procedures of a mobile device connecting to a UMTS network can be split into two areas: the access stratum (AS) and the non-access stratum (NAS). The access stratum involves all the layers and subsystems that offer general services to the non-access stratum. In UMTS, the access stratum consists of all of the elements in the radio access network, including the underlying ATM transport network, and the various mechanisms such as those to provide reliable information exchange. All of the non-access stratum functions are those between the mobile device and the core network, for example, mobility management. Figure 7 shows the architecture model. The AS interacts with the NAS through the use of service access points (SAPs).UMTS radio access network (UTRAN) provides this separation of NAS and AS functions, and allows for AS functions to be fully controlled and implemented within the UTRAN. The two major UTRAN interfaces are the Uu, which is the interface between the mobile device, or User Equipment (UE) and the UTRAN, and the Iu, which is the interface between the UTRAN and the core network. Both of these interfaces can be divided into control and user planes each with appropriate protocol functions.A Bearer Service is a link between two points, which is defined by a certain set of characteristics. In the case of UMTS, the bearer service is delivered using radio access bearers.A Radio access bearer (RAB) is defined as the service that the access stratum (i.e.UTRAN) provides to the non-access stratum for transfer of user data between the User Equipment and Core Network. A RAB can consist of a number of subflows, which are data streams to the core network within the RAB that have different QoS characteristics,such as different reliabilities. A common example of this is different classes of bits with different bit error rates can be realised as different RAB subflows. RAB subflows are established and released at the time the RAB is established and released, and are delivered together over the same transport bearer.A Radio Link is defined as a logical association between a single User Equipment (UE) and a single UTRAN access point, such as an RNC. It is physically comprised of one or more radio bearers and should not be confused with radio access bearer.Looking within the UTRAN, the general architecture model is as shown in Figure 8 below. Now shown are the Node B or Base Station (BTS) and Radio Network Controller (RNC) components, and their respective internal interfaces. The UTRAN is subdivided into blocks referred to as Radio Network Subsystems (RNS), where each RNS consists of one controlling RNC (CRNC) and all the BTSs under its control. Unique to UMTS is the interface between RNSs, the Iur interface, which plays a key role in handover procedures. The interface between the BTS and RNC is the Iub interface.All the ‘I’ interfaces: Iu, Iur and Iub, currently3 use ATM as a transport layer. In the context of ATM, the BTS is seen as a host accessing an ATM network, within which the RNC is an ATM switch. Therefore, the Iub is a UNI interface, whereas the Iu and Iur interfaces are considered to be NNI, as illustrated in Figure 9.This distinction is because the BTS to RNC link is a point-to-point connection in that a BTS or RNC will only communicate with the RNC or BTS directly connected to it, and will not require communication beyond that element to another network element.For each user connection to the core network, there is only one RNC, which maintains the link between the UE and core network domain, as highlighted in Figure 10. This RNC is referred to as the serving RNC or SRNC. That SRNC plus the BTSs under its control is then referred to as the SRNS. This is a logical definition with reference to that UE only. In an RNS, the RNC that controls a BTS is known as the controlling RNC or CRNC. This is with reference to the BTS, cells under its control and all the common and shared channels within.As the UE moves, it may perform a soft or hard handover to another cell. In the case of a soft handover, the SRNC will activate the new connection to the new BTS. Should the new BTS be under the control of another RNC, the SRNC will also alert this new RNC to activate a connection along the Iur interface. The UE now has two links, one directly to the SRNC, and the second, through the new RNC along the Iur interface. In this case, this new RNC is logically referred to as a drift RNC or DRNC, see Figure 10. It is not involved in any processing of the call and merely relays it to the SRNC for connection to the core. In summary, SRNC and DRNC are usually associated with the UE and the CRNC is associated with the BTS. Since these are logical functions it is normal practice that a single RNC is capable of dealing with all these functions.A situation may arise where a UE is connected to a BTS for which the SRNC is not the CRNC for that BTS. In that situation, the network may invoke the Serving RNC Relocation procedure to move the core network connection. This process is described inSection 3.中文翻译:通用移动通信系统的回顾1.1 UMTS网络架构欧洲/日本的3G标准,被称为UMTS。

中国移动通信企业标准 家庭网关终端技术规范版本号:3.0.0 中国移动通信集团公司 发布╳╳╳╳-╳╳-╳╳发布 ╳╳╳╳-╳╳-╳╳实施 QB-╳╳-╳╳╳-╳╳╳╳T e c h n i c a l S p e c if i c a t i o n f o r H o m e G a t e w a y目录1. 范围 ................................................................................................................................................2. 规范性引用文件 .............................................................................................................................3. 术语、定义和缩略语 .....................................................................................................................4. 设备总体定义.................................................................................................................................4.1.设备在网络中的位置 ..................................................................................................................4.2.接口定义 ......................................................................................................................................4.3.设备类型 ......................................................................................................................................5. 接入型家庭网关 .............................................................................................................................5.1.接口要求 ......................................................................................................................................网络侧接口......................................................................................................................................网络侧接口描述..........................................................................................................................................网络侧以太网接口要求..............................................................................................................................接口要求 .......................................................................................................................................................接口要求 .......................................................................................................................................................接口要求 .......................................................................................................................................................用户侧接口......................................................................................................................................用户侧以太网接口要求..............................................................................................................................接口 ...............................................................................................................................................................接口(可选)................................................................................................................................................5.2.功能要求 ......................................................................................................................................数据通信要求..................................................................................................................................协议要求 .......................................................................................................................................................数据转发功能要求......................................................................................................................................功能要求 .......................................................................................................................................................地址管理及拨号管理功能要求....................................................................................................................地址管理及拨号管理功能要求....................................................................................................................要求 ...............................................................................................................................................................要求 ...............................................................................................................................................................组播要求 .....................................................................................................................................................其他功能要求..............................................................................................................................................安全要求..........................................................................................................................................防火墙 .........................................................................................................................................................登陆WEB页面的安全要求..........................................................................................................................设备安全性 .................................................................................................................................................要求....................................................................................................................................................功能要求............................................................................................................................................扩展及管理(可选)........................................................................................................................设备发现要求.........................................................................................................................................................................................................................................................................................................(可选) .......................................................................................................................................................支持WLAN的开启和禁用............................................................................................................................基本要求 .....................................................................................................................................................多SSID要求................................................................................................................................................安全要求 .......................................................................................................................................................5要求 ............................................................................................................................................................要求 ...............................................................................................................................................................基本应用要求................................................................................................................................... WLAN共享 ..................................................................................................................................................家庭存储(可选)......................................................................................................................................5.3.性能要求 ......................................................................................................................................路由转发性能要求..........................................................................................................................吞吐量 .........................................................................................................................................................地址学习 .....................................................................................................................................................缓存大小 (23)连接数量要求.............................................................................................................................................. 无线性能要求....................................................................................................................................吞吐量性能要求 (23)覆盖性能要求................................................................................................................................................接收灵敏度要求............................................................................................................................................5.4.管理和维护要求 (24)本地管理和配置要求......................................................................................................................本地管理基本要求......................................................................................................................................用户分级管理 (24)系统信息管理..............................................................................................................................................基本配置 .....................................................................................................................................................高级配置 .....................................................................................................................................................设备管理 .....................................................................................................................................................网络诊断 .....................................................................................................................................................设备认证注册功能......................................................................................................................................远程管理要求..................................................................................................................................远程管理基本要求......................................................................................................................................远程参数配置和性能监测..........................................................................................................................远程故障诊断功能......................................................................................................................................设备告警功能..............................................................................................................................................远程链路维持功能......................................................................................................................................软件远程管理..............................................................................................................................................业务部署和控制..........................................................................................................................................上行家庭网关远程管理实现方式 ................................................................................................................日志功能要求..................................................................................................................................5.5.预配置要求 ..................................................................................................................................预配置要求......................................................................................................................................5.6.硬件要求 ......................................................................................................................................基本要求..........................................................................................................................................硬件基本框图示例..........................................................................................................................5.7.软件要求 ......................................................................................................................................基本要求..........................................................................................................................................软件基本架构................................................................................................. 错误!未定义书签。

1.1音视频编解码技术1.1.1 MPEG4MPEG全称是Moving Pictures Experts Group,它是“动态图象专家组”的英文缩写,该专家组成立于1988年,致力于运动图像及其伴音的压缩编码标准化工作,原先他们打算开发MPEG1、MPEG2、MPEG3和MPEG4四个版本,以适用于不同带宽和数字影像质量的要求。
目前,MPEG1技术被广泛的应用于VCD,而MPEG2标准则用于广播电视和DVD等。
MPEG3最初是为HDTV开发的编码和压缩标准,但由于MPEG2的出色性能表现,MPEG3只能是死于襁褓了。
MPEG4于1999年初正式成为国际标准。
它是一个适用于低传输速率应用的方案。
与MPEG1和MPEG2相比,MPEG4更加注重多媒体系统的交互性和灵活性MPEG1、MPEG2技术当初制定时,它们定位的标准均为高层媒体表示与结构,但随着计算机软件及网络技术的快速发展,MPEG1、MPEG2技术的弊端就显示出来了:交互性及灵活性较低,压缩的多媒体文件体积过于庞大,难以实现网络的实时传播。
而MPEG4技术的标准是对运动图像中的内容进行编码,其具体的编码对象就是图像中的音频和视频,术语称为“AV对象”,而连续的AV对象组合在一起又可以形成AV场景。
因此,MPEG4标准就是围绕着AV对象的编码、存储、传输和组合而制定的,高效率地编码、组织、存储、传输AV 对象是MPEG4标准的基本内容。
在视频编码方面,MPEG4支持对自然和合成的视觉对象的编码。
(合成的视觉对象包括2D、3D动画和人面部表情动画等)。
在音频编码上,MPEG4可以在一组编码工具支持下,对语音、音乐等自然声音对象和具有回响、空间方位感的合成声音对象进行音频编码。
由于MPEG4只处理图像帧与帧之间有差异的元素,而舍弃相同的元素,因此大大减少了合成多媒体文件的体积。
应用MPEG4技术的影音文件最显著特点就是压缩率高且成像清晰,一般来说,一小时的影像可以被压缩为350M左右的数据,而一部高清晰度的DVD电影, 可以压缩成两张甚至一张650M CD光碟来存储。

IP多媒体子系统IMSIP多媒体子系统(IMS)是一种基于IP网络的集成电信解决方案,它将多种通信和媒体服务整合到一个统一的平台上。
IMS 是现代电信网络的核心,为用户提供了丰富的通信体验和更高质量的服务。
IMS的核心功能是实现多媒体通信服务,它支持语音、视频、短信和数据等不同形式的通信。
IMS通过使用IP协议,提供了一种开放的通信环境,可以与其他服务进行集成,如VoIP (Voice over IP)和视频通话。
IMS的设计基于多种协议和技术,包括SIP(Session Initiation Protocol)、SDP(Session Description Protocol)、RTP(Real-time Transport Protocol)、H.323(ITU-T推荐的一种多媒体传输协议)和MPEG(Moving Picture Experts Group)等。
这些协议和技术共同构成了IMS的基础架构,使其支持多种媒体通信服务。
IMS的架构包括以下几个核心组件:1. P-CSCF(Proxy-Call Session Control Function):作为用户和IMS网络间的接口,负责呼叫的鉴权、路由和策略控制等功能。
2. S-CSCF(Serving-Call Session Control Function):负责处理用户的呼叫请求,包括鉴权、会话管理、策略和访问控制等。
3. I-CSCF(Interrogating-Call Session Control Function):负责处理呼叫路由以及用户鉴权请求,并将呼叫请求传递给适当的S-CSCF。
4. MGCF(Media Gateway Control Function):负责控制语音和视频通信等媒体流的转发和转码。
5. HSS(Home Subscriber Server):存储用户的个人信息和权限,辅助IMS进行会话管理和鉴权。
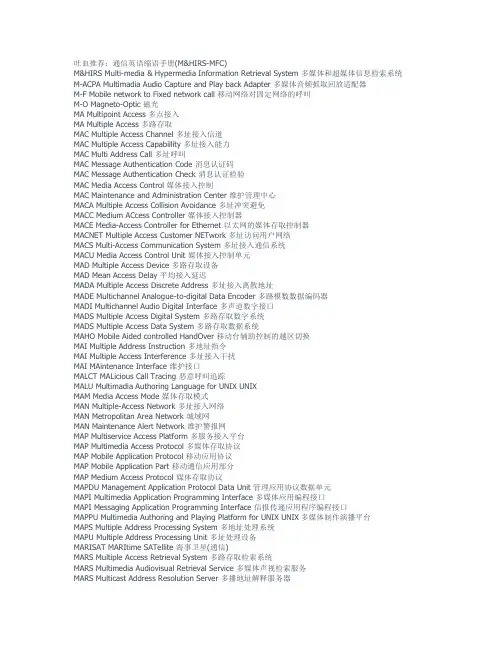
吐血推荐:通信英语缩语手册(M&HIRS-MFC)M&HIRS Multi-media & Hypermedia Information Retrieval System 多媒体和超媒体信息检索系统M-ACPA Multimadia Audio Capture and Play back Adapter 多媒体音频抓取回放适配器M-F Mobile network to Fixed network call 移动网络对固定网络的呼叫M-O Magneto-Optic 磁光MA Multipoint Access 多点接入MA Multiple Access 多路存取MAC Multiple Access Channel 多址接入信道MAC Multiple Access Capabillity 多址接入能力MAC Multi Address Call 多址呼叫MAC Message Authentication Code 消息认证码MAC Message Authentication Check 消息认证检验MAC Media Access Control 媒体接入控制MAC Maintenance and Administration Center 维护管理中心MACA Multiple Access Collision Avoidance 多址冲突避免MACC Medium ACcess Controller 媒体接入控制器MACE Media-Access Controller for Ethernet 以太网的媒体存取控制器MACNET Multiple Access Customer NETwork 多址访问用户网络MACS Multi-Access Communication System 多址接入通信系统MACU Media Access Control Unit 媒体接入控制单元MAD Multiple Access Device 多路存取设备MAD Mean Access Delay 平均接入延迟MADA Multiple Access Discrete Address 多址接入离散地址MADE Multichannel Analogue-to-digital Data Encoder 多路模数数据编码器MADI Multichannel Audio Digital Interface 多声道数字接口MADS Multiple Access Digital System 多路存取数字系统MADS Multiple Access Data System 多路存取数据系统MAHO Mobile Aided controlled HandOver 移动台辅助控制的越区切换MAI Multiple Address Instruction 多地址指令MAI Multiple Access Interference 多址接入干扰MAI MAintenance Interface 维护接口MALCT MALicious Call Tracing 恶意呼叫追踪MALU Multimadia Authoring Language for UNIX UNIXMAM Media Access Mode 媒体存取模式MAN Multiple-Access Network 多址接入网络MAN Metropolitan Area Network 城域网MAN Maintenance Alert Network 维护警报网MAP Multiservice Access Platform 多服务接入平台MAP Multimedia Access Protocol 多媒体存取协议MAP Mobile Application Protocol 移动应用协议MAP Mobile Application Part 移动通信应用部分MAP Medium Access Protocol 媒体存取协议MAPDU Management Application Protocol Data Unit 管理应用协议数据单元MAPI Multimedia Application Programming Interface 多媒体应用编程接口MAPI Messaging Application Programming Interface 信报传递应用程序编程接口MAPPU Multimedia Authoring and Playing Platform for UNIX UNIX多媒体制作演播平台MAPS Multiple Address Processing System 多地址处理系统MAPU Multiple Address Processing Unit 多址处理设备MARISAT MARItime SATellite 海事卫星(通信)MARS Multiple Access Retrieval System 多路存取检索系统MARS Multimedia Audiovisual Retrieval Service 多媒体声视检索服务MARS Multicast Address Resolution Server 多播地址解释服务器MARS Military Affliated Radio System 军用附属无线电系统MARS MAchine Retrieval System 机器检索系统MAS Multiple Access System 多路存取系统MAS MASs calling 大众呼叫业务MASC Mobitex ASynchronous Communication 移动图文信息异步通信MASE Message Administration Service Element 消息管理服务单元MASS Multimedia Application Shared Service 多媒体应用共享业务MASS MAintenance SubSystem 维护子系统MASTER Multiple Access Shared Time Executive Routine 多路存取分时执行程序MAT Multidrop Access Trunk 多点分出接入中继线MAT Metropolitan Area Trunk 大城市中继线MAT Maintenance Access Terminal 维护接入终端MATD Maximum Acceptable Transit Delay 最大可接受转接时延MAU Multistation Access Unit 多站点存取单元MAU Multiple Access Unit 多重接入单元MAU Media Attachment Unit 媒体连接器MAU Media Access Unit 媒体存取设备MAU MAintenance Unit 维护单元MAUI Multimedia Application User Interface 多媒体应用用户接口MAVC Multimedia Audio Video Connection 多媒体音像连接MAVIX Multimedia Audio Video Information eXchange 多媒体音频视频信息交换MB MegaBytes 兆字节Mb Megabit 兆位MBA Multipoint Broadband Access 多点宽带接入MBAA Multiple-Beam Adaptive Array 多波束自适应阵列MBAN Multimedia Broadband Access Network 多媒体宽带接入网MBC Multicasting Balancing Circuit 多播平衡电路MBC Meteor Burst Communication 流星余迹通信MBHCA Million Busy Hour Call Attempt 百万次忙时试呼MBN Mesh-Bonding Network 网状网络MBONE Multicast backBONE 多播主干网MBPS MegaBytes Per Second 兆字节/秒MBS MoBile Station 移动站MBS Mobile Broadband System 移动宽带系统MBSU Multi Block Synchronization signal Unit 多信息组同步信号单元MBTP Multiple Buffer Transfer Protocol 多缓冲传递协议MC Multipoint Controller 多点控制器MC Multipoint Connection 多点连接MC Multimedia Computer 多媒体计算机MC Multimedia Communication 多媒体通信MC Module Control 模块控制MC Mobile Computer 移动式计算机MC Micro Cell 微小区MC Message Center 消息中心MC Message Categories 消息种类MC Media Control 媒体控制MC Master Clock 主时钟MC Maintenance Center 维护中心MC-CDMA MultiCode CDMA 多码CDMAMC-TDMA MultiCarrier Time Division Multiplexing Access 多载频时分多址接入MCA MultiChannel Access 多路接入MCA Micro Channel Architecture 微通道体系结构MCAL Malicious CALl 恶意呼叫MCAS MultiChannel Access System 多路接入系统MCC Multimedia Communication Channel 多媒体通信频道MCC Multichhannel Communication Center 多信道通信中心MCC Multicast Coordination Center 多播协调中心MCC Mobile Country Code 移动台国家码MCC Mobile Call Control 移动呼叫控制MCC Master Control Center 主控制中心MCC MAN Control Center 城域网络控制中心MCC Maintenance Control Center 维护控制中心MCC Main Communication Center 主通信中心MCCC Multi-Connection Call Control 多连接呼叫控制MCCP Multimedia Computing and Communication Platform 多媒体计算及通信平台MCCU Multiple Communication Control Unit 多路通信控制单元MCD Maximum Cell Delay 最大信元时延MCDN Micro-Cellular Data Network 微蜂窝数据通信网MCDQDB MultiChannel DQDB 多信道双队列数据总线MCDT Multimedia CD-ROM Title 多媒体光盘标题MCE Master Communication Equipment 主通信设备MCF Mobile Control Function 移动控制功能MCF Message Communication Function 消息通信功能MCF Management Communication Function 管理通信功能MCGA Multi-Color Graphics Array 多色彩图形阵列MCGA Multi-Color Graphics Adapter 多彩色图形适配卡MCHO Mobile Controlled HandOver 移动控制切换MCI Mobile Communication Interface 移动通信接口MCI Media Control Interface 媒体控制接口MCI Malicious Call Identification 恶意呼叫识别MCIC MultiChip Integrated Circuit 多芯片集成电路MCL Message Control Language 报文控制语言MCLR Mean Cell Loss Rate 平均信元丢失率MCM MultiCarrier Modulation 多载波调制MCM Maintenance Control Module 维护控制模块MCMF MultiCommodity Maximum Flow 多商品最大流量MCN Mobile Control Node 移动控制节点MCNS Multimedia Cable Network System 多媒体有线网系统MCP Multiflow Conversation Protoco 多流对话协议MCP Mass Calling Platform 大众呼叫平台MCPA MultiCarrier Power Amplifier 多载波功率放大器MCPC Multiple Channel Per Carrier 多信道单载波MCPN Mobile Customer Premises Network 移动用户驻地网MCPU Multiple Channel Processing Unit 多信道处理单元MCPU Multiple Call Processing Unit 多呼叫处理单元MCR Minimum Cell Rate 最低信元速率MCR Mean Cell Rate 平均信元率MCS Multipoint Conferencing Server 多点会议服务器MCS Multipoint Communication Service 多点通信业务MCS Multimedia Conferencing System 多媒体会议系统MCS Multimedia Chatting System 多媒体交谈系统MCS MultiCast Server 多播服务器MCS Microwave Communication System 微波通信系统MCS Message Control System 消息控制系统MCS Master Control Station 主控制站MCS Mass Calling Service 大众呼叫业务MCS Maritime Communications Subsystem 海事通信子系统MCS Maintenance-data Collection System 维护数据收集系统MCS Maintenance Control Subsystem 维护控制子系统MCSO Multimedia Communication Service Object 多媒体通信业务对象MCSS Military Communication Satellite System 军事通信卫星系统MCT Multicast Channel Translator 多播信道转换器MCTD Mean Cell Transfer Delay 平均信元传递时延MCU Multipoint Conference Unit 多点会议单元MCU Multipiont Control Unit 多点控制单元MCU Module Control Unit 模块控制单元MCU Mobile Control Unit 移动控制单元MCU Minimum Coding Unit 最小编码单元MCU Master Controller Unit 主控制器单元MCU Management and Communication Unit 管理和通信单元MD Multimode Distortion 多模失真MD Message Discrimination 消息鉴别MD Mediation Device 中介设备MD-IS Mobile Data Intermediate System 移动数据中间系统MDB Multimedia DataBase 多媒体数据库MDBMLS Multimedia DataBase Machine Learning System 多媒体数据库机器学习系统MDD Multimedia Database Design 多媒体数据库设计MDD Multi-Dimensional Database 多维数据库MDF Main Distribution Frame 主配线架MDI Medium Dependent Interface 媒体相关接口MDK Multimedia Development Kit 多媒体开发工具MDL Mirrored Data Links 镜像数据链接MDL Management entitiy and Data Link layer 管理实体与数据链路层(的通信) MDLP Mobile Data Link Protocol 移动数据链路协议MDM Multiplexer-DeMultiplexer 复用器-解复用器MDM Multimedia Data Management 多媒体数据管理MDM Media Device Manager 媒体设备管理程序MDNEXT Multiple-Disturber NEXT 多干扰近端串话MDOP Multimedia Data Operation Platform 多媒体数据*作平台MDR Message Detail Recorder 详细消息记录器MDS Multipoint Distribution System 多点分布系统MDS Multiple Data Stream 多数据流MDSE Message Delivery Service Element 消息传递服务单元MDSL Medium bit-rate Digital Subscriber Line 中比特率数字用户线MDSO Multimedia Data Storage and Organization 多媒体数据存储和组织MDSS Mass Digital Storage System 大容量数字存储系统MDU Management Data Unit 管理数据单元MDX Multiplexer-DemultipleXer 复用器-解复用器ME Maintenance Entity 维护实体ME Measurement Entity 测量实体MEF Maintenance Entity Function 维护实体功能MEI Maintenance Event Information 维护事件信息MEO Middle Earth Orbit 中地球轨道卫星MES Mobile Earth Station 移动地球站METON METropolitan Optical Network 都市光网络MexE Mobile station application execution Environment 移动基站应用执行系统MF Maintenance Funcation 维护功能MF Mediation Function 中介功能MF Medium Frequency 中频MF Multi-Frequency 多频MF-TDMA MultiFrequency Time Division Multiple Access 多频时分多址接入MFA Multi-Frame Alignment 多帧定位MFBT Multicast Forward / Backward Tree 多播前向/反向树形网络MFC Multicore-Fiber Cable 多芯光缆MFC Multi-Frame Code 多帧编码MFC Multi-Frequency Code 多频码MFC Multi-Frequency Code signaling 多频码信令MFC Multi-Frequency Control 多频控制吐血推荐:通信英语缩语手册(MFCR-MP3)MFCR Minimum Free Capacity Routing 最小自由容量选路MFOTS Military Fiber-Optic Transmission System 军用光纤传输系统MFREC Multi-Frequency RECeiver 多频接收器MFS Metropolitan Fiber Syster 都市光纤系统MFS Multi-Frame Structure 复帧结构MFS Multi-Frame Synchronizer 复帧同步器MFS Multiple Frequency Shift 多频位移MFSND Multi-Frequency SeNDer 多频发送器MFT Multi-Function Terminal 多功能终端MG Media Gateway 媒体网关MG Multicast Grouping 多播分组MGCP Media Gateway Control Protocol 媒体网关控制协议MGF Mobile Gateway Function 移动网关功能MGPF Mobile Geographic Position Function 移动地理定位功能MGS Mobile Gateway Switch 移动网关交换MGS Multimedia Gateway Server 多媒体网关服务器MGW Media GateWay 媒体网关MH Message Handler 报文处理程序MH Message Handling 消息处理MH Mobile Host 移动式主机MHE Message Handling Environment 消息处理环境MHEG Multimedia Hypermedia Expert Group 多媒体超媒体专家组标准MHN Multimedia Handling Node 多媒体处理节点MHS Message Handling Systems 消息处理系统MHS-SE Message Handling System Service Element 消息处理系统业务单元MI Mutiplex Interface 复用接口MIAS Multipoint Interactive Audiovisual System 多点交互式声视系统MIB Management Information Base 管理信息库MIBC Management Information Base Chip 管理信息库芯片MIC Media Interface Connector 媒体接口连接器MIC Message Identification Code 消息识别码MIC Module Interface Circuit 模块接口电路MIC Multimode Image Coding 多模图像编码MICA Media Informetion Communication Application 媒体信息通信应用程序MICE Mamagement Information Control Exchang 管理信息控制交换MID Message IDentification 报文标志MID Multiplexing IDentifier 复用标志MIDI Musical Instrument Digital Interface 乐器数字化接口MIDS Management Information Dataflow System 管理信息数据流系统MIDS Multimedia Intelligent Database Systems 多媒体智能数据库系统MIE Micromedia Information Exchange 微媒体信息交换MIE Multipurppose Internet Extensions 多用途因特网扩充MIF Management Information Format 管理信息格式MII Media-Independent Interface 与媒体无关的接口MII Mobile Information Infrastructure 移动通信信息基础设施MILS MAC Internal Layer Service MAC层内服务MIM Management Information Model 管理信息模型MIMD Multiple Instruction Multiple-Data 多指令多数据流MIME Multipurpose Internet Mail Extension 多用途因特网邮件扩展MIN Mobile Intelligent Network 移动智能网MIN Multistage Interconnected Network 多级互连网MIP Multimedia Information Provider 多媒体信息提供者MIP Multiple Information Passageway 多信息通道方式MIPS Million Instructions Per Second 每秒百万指令MIRS Multimedia Information Recall System 多媒体信息检索系统MIS Management Information Services 管理信息服务MIS Management Information System 管理信息系统MIS Multiple Interactive Screen 多交互式屏幕MISDN Mobile Integrated Service Digital Network 移动综合业务数字网MIT Management Information Tree 管理信息树MIT Modular Intelligent Terminal 模块化智能终端MITS Multimedia Interactive Telelearning System 多媒体交互远程学习系统MIU Multi-Interface Unit 多接口装置MIU Multimedia Information User 多媒体信息用户MIU Multistation Interface Unit 多站接口装置MJP Micro Java Processor 微型Java处理器MK Master Key 主密钥MKS Multimedia Kiosk Service 多媒体触摸屏服务ML-EDF Mode-Locked Erbium Doped Fiber 锁模掺铒光纤ML-FRL Mode-Locked Fiber Ring Laser 锁模光纤环型激光器MLAN Multichannel Local Area Network 多通道局域网MLAP MAC Level Access Protocol 媒体接入控制层接入协议MLC Mobile Local Circuit 移动通信本地电路MLLR Multi-rate Least-Loaded Routing 多速率最低负载选路MLLRP Multi-rate Least-Loaded Routing with Packing 多速率最低负载分组选路MLN Middle Level Network 中级网络MLP Machine Language Program 机器语言程序MLP Message Link Protocol 报文链路协议MLP Multi-Layer Protocol 多层协议MLP MultiLink Procedure 多链路规程MLR Most-Loaded Routing 最多负载选路MLS Multimedia Learning Station 多媒体学习站MLT MultiLink Trunking 多链路骨干技术MM Maintenance Management 维护管理MM Maintenance Module 维护模块MM Mass Memory 大容量存储器MM Mixed Mode 混合方式MM Mobility Management 移动性管理MM Modelling Multimedia 建模多媒体MM MultiMedia 多媒体MM MultiMode 多模MM/MMI MultiMedia / MultiModel Interface 多媒体/多方式接口MMA Multiple Module Access 多模块存取MMAC MultiMedia Access Center 多媒体访问中心MMAP Mobility Management Application Protocol 移动性管理应用协议MMC Maintanance, Monitoring and Control 维护和监控MMC Man-Machine Communication 人机通信MMC Man-Machine Controller 人机控制器MMC Meet-Me Conference 会聚式会议电话MMC MultiMedia Communication 多媒体通信MMC MultiMedia Communicator 多媒体通信体MMC MultiMedia Controller 多媒体控制器MMC Multimedia Marketing Council 多媒体市场委员会MMC Multimedia Multiparty Conferencing 多媒体多方会议MMC MultiMedia Collaboration 多媒体协作MMCA Message-Mode Communication Adapter 报文方式通信适配器MMCC MultiMedia Conference Control 多媒体会议控制MMCD MultiMedia Compact Disc 多媒体光盘MMCF MultiMedia Communications Forum 多媒体通信论坛MMCM MultiMedia Control Manager 多媒体控制管理器MMCP Multimedia Mail Content Protocol 多媒体邮件内容协议MMCS Multimedia Mobile Communication System 多媒体移动通信系统MMCX MultiMedia Communicaton eXchange 多媒体通信交换MMDD Management Multimedia Dynamic Data 多媒体动态数据管理MMDS Multichannel Microwave Distribution System 多频道微波分配系统MMDS Multichannel Multipoint Distribution Service 多信道多点分配服务MMDS Multipoint Multichannel Distribution System 多点多信道分配系统MME MultiMedia E-mail system 多媒体电子邮件系统MMEM MultiMedia Electronic Mail 多媒体电子函件MMF MultiMode Fiber 多模光纤MMH MultiMedia Hub 多媒体集线器MMI Man-Machine Interaction 人机交互MMI Man-Machine Interface 人机接口MMI MultiMedia Input 多媒体输入MMI Multi-Mode Interference 多模干扰MMIC Monolithic Microwave Integrated Circuit 单片微波集成电路MMIO MultiMedia I / O 多媒体输入/输出MMIS Multimedia Management Information System 多媒体管理信息系统MML Man-Machine Language 人机语言MML Multimedia Mechanism Layer 多媒体结构层MML Multimedia Module Library 多媒体模块库MMM Multi Modem Manager 多调制解调器管理器MMM MultiMedia Mail 多媒体邮件MMM MultiMedia Multiplexer 多媒体复用器MMM Multiunit network Management and Maintenance message 多单元网络管理和维护消息MMMD MultiMedia Multi-Database 多媒体多数据库MMMS Multimedia Mail Messaging Service 多媒体邮件报文服务MMMS MultiMedia Mail Service 多媒体邮政业务MMN MultiMedia Network 多媒体网MMNI Message Memory Network Interface 消息存储器网络接口MMP Maritime Mobile Phone 海上移动电话MMP Module Message Processor 模块消息处理器MMP Multiplexed Message Processor 复用信息处理器MMPC MultiMedia PC 多媒体个人计算机MMPDLL Multimedia Movie Player DLL 多媒体电影放映机DLL MMPM MultiMedia Picture Management 多媒体图像管理MMS Maritime Mobile Satellite system 海上移动卫星系统MMS Middleware Message Service 中间件消息业务MMS Model Management System 模型管理系统MMS MultiMedia Service 多媒体业务MMS Multi-Modular Storage 多模块存储器MMS Multiport Memory System 多端口存储器系统MMSAF MultiMedia Services Affiliate Forum 多媒体业务会员论坛MMSE Man-Machine System Engineering 人机系统工程学MMSE Minimum Mean Square Error 最小均方误差MMSER Minimum Mean Square Error Restoration 最小均方误差复原MMT MultiMedia Terminal 多媒体终端MMTS MultiMedia Transport System 多媒体传送系统MMU Mass Memory Unit 大容量存储器MMUI MultiMedia User Interface 多媒体用户接口MMV MultiMedia Viewer 多媒体观赏器MMW MultiMedia World 多媒体世界MMX MultiMedia eXtension 多媒体扩展MN/MX MiNimum / MaXimum 最小值/最大值MNC Mobile Network Code 移动网络代码MNC MultiNational Company 多国公司MNCS Multipoint Network Control System 多点网络控制系统MNF Multisystem Networking Facility 多系统连网设施MNH Minimum Number of Hops 最小跳频数MNP Microcom Network Protocol 微通网协议MNP Mobile telephone Number Portability 移动电话号码可携MNRU Modulated Noise Reference Unit 调制噪声参考单位MNSC Main-Network Switching Centre 主网络交换中心MNU MainteNance Unit 维护单元MO Managed Object 被管对象MO Memory Object 存储对象MOA Maintenance, Operation, Administration 维护、运行和管理MOAR Measurable One-way Attenuation Range 可测单向衰减范围MOAS Multimedia Office Automatic System 多媒体办公自动化系统MOC Maintenance Operations Center 维护运行中心MOD Magneto-Optic Disc 磁光碟片MOD Movies On-Demand 电影点播MOD Music On Demand 音乐点播MODAL Microwave Optical Duplex Antenna Link 微波光双工天线链路MODEM MOdulator-DEModulator 调制解调器MODI MODule Interface 模块接口MODID MODule IDentity 模块识别MODIF Modular Optical Digital InterFace 模块化光数字接口MOM Magneto-Optical Modulation 磁光调制MOM Maintenance Operation Modules 维护*作模式MOM Mass Optical Memory 大容量光存储器MOM Message Oriented Media 面向消息的媒体MOM Message Oriented Middleware 面向消息中间件MOMS Multiple Orbit-Multiple Satellite 多轨道,多卫星MONET MObile NETwork 移动网MONET Multi-wavelength Optical NETwork 多波长光网络MOOS Maintenance Out Of Service 停业维护MOP Maintenance and Operation Processing 维护和运行处理MOPS Million Operations Per Second 每秒百万次运算MOS Maintenance Operation Subsystem 维护运行子系统MOS Management Operating System 管理运行系统MOS Master Operating System 主*作系统MOS Mean Opinion Score 平均意见评分MOS Metal Oxide Semiconductor 金属-氧化物-半导体MOS Multimedia Operation Software 多媒体*作软件MOSPF Multicast Open Shortest Path First 多播开放式最短路径优先MOTIS Message-Oriented Text Interexchange System 面向报文的文本交换系统MOU Memorandum Of Understanging 谅解备忘录MP Main Processor 主处理器MP Maintenance Processor 维护处理器MP Management Point 管理点MP Management Process 管理过程MP Memory Protection 存储器保护 MP Message Passing 信息传递MP Message Priority 消息优先级MP Misrouting Probability 错接概率MP Module Processor 模块处理器MP Multipath Propagation 多径传播MP Multipoint Processor 多点处理器MP3 MPEG-1 layer 3 MPEG-1音频第三层标MPA Multichannel Protocol Analyser 多通道协议分析仪MPC Message Passing Coprocessor 信息传送协处理器MPC Minimum Performance Criterion 最低性能指标MPC MPOA Client MPOA客户机MPC Multimedia Personal Computer 多媒体个人计算机MPC Multimedia Product Council 多媒体产品协会MPC Multi-Processor Controller 多处理器控制器MPCI Mobile Protocol Capability Indicator 移动协议能力指示器MPCOS Multimedia Personal Computer Operating System 多媒体个人计算机*作系统MPD Mode Power Distribution 模功率分布MPDU Media Protocol Data Unit 媒体协议数据单元MPDU Message Protocol Data Unit 消息协议数据单元MPE Multimedia Processing Equipment 多媒体处理设备MPEG Motion Picture Experts Group 活动图像专家组(编码标准)MPF Mobile Packet processing Function 移动分组处理功能MPGA Mask Programmable Gate Array 掩模可编程门阵列MPI Message Passing Interface 消息传递接口MPI MultiPath Interference 多径干扰MPIC Message Processing Interrupt Count 信息处理中断计数MPICC Multimedia Personal Information Communication Center 多媒体个人信息通信中心MPIS MultiPurpose Information System 多用途信息系统MPL Message Processing Language 信息处理语言MPL Modular Part Library 模块化部件库MPL Multiple Parallel Loop 多平行环路MPLM Multiple PoLarization Modulation 多偏振(极化)调制MPLS Multi-Protocol Label Switching 多协议标记交换MPM Maintenance and Peripherals Module 维护和外围设备模块MPM Message Passing Model 报文传送模型MPM Message Processing Module 消息处理模块MPM Multi-Processor Mode 多处理机方式MPMP Microwave Point to MultiPoint 微波一点至多点MPNA MultiPort Network Adapter 多端口网络适配器MPOA MultiProtocol Over ATM ATM多协议运行MPOL MultiProblem Oriented Language 面向多种问题的语言MPP Massively Parallel Processor 大规模并行处理器MPP Message Passing Processing 报文传送处理MPP Message Processing Program 报文处理程序MPPF Multipoint Protocol Polling Function 多点协议*询功能MPR Multiple Protocol Router 多协议路由器MPS Message Processing System 信息处理系统MPS Mobile Phone Service 移动电话业务MPS Model Processing System 模型处理系统MPS MPOA Server MPOA服务器MPS MultiPriority System 多优先级系统MPSC MultiProtocol Serial Controller 多协议串行控制器MPSK Multiple Phase Shift Keying 多相移键控MPSR MultiPath Self-Routing 多通路自选路由MPTN Multi-Ptotocol Transport Network 多协议传输网络MPU Main Processor Unit 主处理器单元MPU Multimedia Processing Unit 多媒体处理单元MPVCS MultiPoint Video Conferencing System 多点视频会议系统MQ Message Queue 消息队列MR Modulation Rate 调制速率MR Multicast Repeater 多播复用器MRAS Multifame Remote Alarm Signal 多帧远程告警信号MRC Maximum Ratio Combining 最大比联合MRC Mobile Radio Communication 移动无线电通信MRCP Mobile Radio Control Post 移动无线电控制站MRCS Multiple Rate Circuit Switching 多速率电路交换MRM MultiResolution Modulation 多分辨率调制MRN Minimal Routing Number 最小路由选择数MRN Multiple Reflection Noise 多点反射噪声MRP Manufacturing Resource Planning 制造资源计划MRP Message Routing Process 信息路由选择过程MRRC Mobile Radio Resource Control 移动无线资源控制MRS Meeting Room System 会议室系统MRS Message Relay Service 消息转发业务MRSE Message Retrival Service Element 消息检索服务单元MRT Mean Repair Time 平均修复时间MRT Mean Response Time 平均响应时间MRT Message Routing Table 消息路由选择表MRTR Mobile Radio Transmit and Receive 移动无线电发射与接收MS Media Synchronization 媒体同步MS Message Storage 消息存储MS Message Store 消息存储器MS Mobile Service 移动业务MS Mobile Station 移动台MS Mobile Subscriber 移动用户MS Mode Scrambler 扰模器MS Multimedia System 多媒体系统MS Multiplex Section 复用段MS Multi-Stage 多级MS Mutual Synchronization 互同步MSA Multimedia Stream Adaptive 多媒体流量自调节器MSA Multiplex Section Adaptation 复用段适配MSAIS Multiplex Section Alarm Indication Signal 复用段告警指示信号MSAT Mobile SATellite 移动通信卫星MSB Maximum Spare Bandwidth 最大备用带宽MSB Most Significant Bit 最高有效位MSB Most Significant Byte 最高有效字节MSBP MultiService Billing Protocol 多业务计费协议MSB S MultiService Billing System 多业务计费系统MSC Main Switching Center 主交换中心MSC Master Supervision Center 主监控中心MSC Merge-Split Component 可组合分立式部件MSC Message Sequence Chart 信息序列图MSC Message Switching Center 信息交换中心MSC Mobile Switching Center 移动交换中心MSC Most Signification Character 最高有效字符MSC Multimedia Super Corridor (马来西亚)多媒体超级走廊MSCH Multiplex SubCHannel 复用子信道MSCM Multichannel SubCarrier Multiplexing 多信道副载波复用MSCP Mobility and Service Control Point 移动性和服务控制点MSCP Network Service Control Point 网络服务控制点MSCS Mass Storage Control System 大容量存储器控制系统MSCT Message Switching Concentration Technique 消息交换集中技术MSCU Multi Station Control Unit 多点控制单元MSD Medium Specific Decoder 中速专用译码器MSD Most Signification Digit 最高有效数字MSD SE Mobile Satellite Data Switching Exchange 移动卫星数据交换机MSD SL Multirate Single pair Digital Subscriber Line 多速率单对数字用户线MSE Maintenance SubEntity 维护子实体MSE Mean Squared Error 均方误差MSF Mass Storage Facility 大容量存储设备MSF Multichannel Selective Filter 多信道选择滤波器MSG S MeSseGe Switching 消息交换MSI Mobile Station Identification number 移动站识别号码MSIC Medium Scale Integrated Circuit 中规模集成电路MSID Mobile Station IDentifier 移动台识别码MSIN Mobile Subscriber Indentification Number 移动通信的用户识别号码MSIN MultiStage Interconnection Network 多级互连网络MSK Minimal Shift Keying 最小频移键控MSL MeSsege Length 消息长度MSL MicroStrip Laser 微带激光器MSL Mirrored Server Link 镜像服务器链接MSL Multimedia Software Layers 多媒体软件层MSL Multiplex Section Layer 复用段层MSL Multi-Satellite Link 多卫星链路MSLAN Middle Speed LAN 中速局域网MSLM Microchannel Spatial Light Modulator 微信道空间光调制器MSLR Main-to-Side Lobe Ratio 主/副瓣比MSM Matrix Stackable Module 矩阵式堆叠模块MSM Media Support Module 媒体支持模块MSM Message Switching Multiplexing 信息交换复用MSM Mobile Station Modem 移动站调制解调器MSM Multiwavelength Simultaneous Monitoring 多波长同步监视MSMC Multiwavelength Simultaneous Monitoring Circuit 多波长同步监视电路MSMR Multiple Service Multiple Resource 多业务多资源MSN Message Switching Network 消息交换网MSN Multi-Satellite Network 多卫星网络MSN Multi-Server Network 多服务器网络MSN Multi-System Networking 多系统联网MSN Mutual Synchronization Network 互同步网络MSNF Multi-System Networking Facility 多系统连网设备MSN S Multimedia Service Navigation System 多媒体业务导航系统MSO Multiple Service Operator 多业务运营商MSOH Multiplexing Section OverHead 复用段开销MSP Management Service Provider 管理服务提供商MSP Master Synchronization Pulse 主同步脉冲MSP Media Stream Protocol 媒体流协议MSP Mixed Signal Processing 混合信号处理MSP Multiplex Section Protection 复用段保护MSP Multi-Service Platform 多业务平台MSP MultiStream Processing 多数据流处理MSR Mobile Support Router 移动通信支持路由器MSRN Mobile Station Roaming Number 移动通信站漫游号码MSS MAN Switching System 城域网交换系统MSS Maritime Satellite Service 海事卫星业务MSS Mass Storage Subsystem 大容量存储器子系统MSS Master-Slave Synchronization 主-从同步MSS Metropolitan Switching System 城域交换系统MSS Mobile Satellite Service 移动卫星业务MSS Mobile Satellite System 移动卫星系统MSS Mobile Subscriber Station 移动用户站MSS Mobile Suporting Station 移动通信支持站MSS Multimedia System Service 多媒体系统业务MSS Maximum Segment Size 最大段宽MSSA Multi-Service Storage Architecture 多服务存储结构MSSC Maritime Satellite Switching Center 海事卫星交换中心MSSC Mobile Satellite Switching Center 移动通信卫星交换中心MSSC Mobile Service Switching Center 移动业务交换中心MSSCSG Modular Spread Spectrum Code-Sequence Generator 积木式扩频码序发生器MSSFU Mobile Satellite Store-and-Forward Unit 移动通信的卫星存储转发单元MSSR Multiple Service Single Resource 多业务单信源MST Minimum Spanning Tree 最小生成树吐血推荐:通信英语缩语手册(MST-MXU)MST Monolithic System Technology 单片系统技术MST Multi Service Terminal 多业务终端MST Multiplex Section Termination 复用段终接设备MSU Maintenance Signal Unit 维护信号单元MSU Mass Storage Unit 大容量存储单元MSU Message Signal Unit 消息信号单元MSU Multiple Signal Unit 多重信号单元MSU Multiple Subscriber Unit 多用户单元MSVC Meta Signaling Virtual Channel 元信令虚通道MSW Machine Status Word 机器状态字MSW MagnetoStatic Wave 静磁波MSW Message SWitch 消息交换器MT Machine Translation 机器翻译MT Magnetic Tape 磁带MT Maintenance Tree 维护树MT Master Terminal 主机终端MT Message Transfer 消息传送MT Message Type 消息类型MT Mobile Terminal 移动终端MT Multimedia Terminal 多媒体终端MT Multimedia Toolkits 多媒体工具包MT-CDMA MultiTone CDMA 多音CDMAMTA Message Transfer Agent 消息传送代理MTA Multimedia Titles and Application 多媒体节目及应用MTA Multimedia Transport API 多媒体运送应用编程接口MTA Multi-protocol Terminal Adaptor 多协议终端适配器MTAE Message Transfer Agent Entity 报文传送代理实体MTBC Mean Time Between Calls 平均呼叫间隔时间MTBC Mean Time Between Complaints 平均申告间隔时间MTBD Mean Time Between Defects 平均故障间隔时间MTBD Mean Time Between Degradation 平均衰变间隔时间MTBD Mean Time Between Detection 平均(故障)检测时间MTBE Mean Time Between Errors 平均错误间隔时间MTBF Maximal Time Between Faults 最大无故障工作时间MTBF Mean Time Between Failures 平均故障间隔时间MTBI Mean Time Between Interruption 平均中断间隔时间MTBM Mean Time Between Maintenance 平均维修间隔时间MTBM Mean Time Between Malfunction 平均误动作间隔时间MTBO Mean Time Between Overhauls 平均检修间隔时间MTBR Mean Time Between Removals 平均拆换间隔时间MTBR Mean Time Between Repairs 平均修理间隔时间MTBSE Mean Time Between Software Errors 平均软件错误间隔时间MTBSF Mean Time Between Service Failures 平均业务故障间隔时间MTBSF Mean Time Between System Failures 平均系统故障间隔时间MTBSO Mean Time Between Service Outage 平均业务中断间隔时间MTC Main Test Component 主测部件MTC Main Trunk Circuit 主干线电路MTC Message Transmission Control 信息传输控制MTC Multimedia Telephone Communication 多媒体电话通信MTCF Mean Time to Catastrophic Failure 平均出现严重故障的时间MTCM Message Transmission Control Module 消息传输控制模块MTCM Multiple Trellis-Coded Modulation 多格状编码调制MTCS Multimedia Telecommunication Conference System 多媒体电信会议系统MTD Maximum Transfer Delay 最大传送延迟MTDF Mean Time to Degradation Failure 平均出现衰变的时间MTDM Multimedia Time Division Modulator 多媒体时分调制器MTDTE Mobile Telephone Data Transfer Equipment 移动电话数据传送设备MTE Message Transfer Event 消息传送事件MTE Multisystem Test Equipment 多系统测试设备。

流媒体传输协议及音视频编解码技术引言随着互联网的普及和带宽的提高,流媒体技术在现代通信领域得到了广泛的应用。
流媒体传输协议和音视频编解码技术是实现流媒体的关键技术,本文将介绍流媒体传输协议的分类和特点,以及常用的音视频编解码技术原理。
一、流媒体传输协议流媒体传输协议是指用于实现音视频流传输的协议,常见的流媒体传输协议有HTTP、RTSP、RTMP、HLS等。
这些协议各有其特点和适用场景。
1.1 HTTPHTTP(Hyper Text Transfer Protocol)是一种应用层协议,常用于在万维网上进行数据传输。
在流媒体领域,HTTP被广泛用于传输音视频流。
其具有跨平台、易于使用的特点,同时也能保证较好的兼容性和稳定性。
然而,由于HTTP协议本身的限制,其传输效率相对较低,对实时性要求较高的应用场景有一定局限性。
1.2 RTSPRTSP(Real-Time Streaming Protocol)是一种应用层协议,用于控制多媒体服务器之间的数据传输。
RTSP协议提供了对流媒体的完整控制,包括播放、暂停、停止、快进、快退等功能。
其支持实时流媒体传输,并具有较好的实时性。
但是,RTSP协议不直接传输音视频流数据,因此需要结合其他协议(如RTP/RTCP协议)来实现音视频数据的传输。
1.3 RTMPRTMP(Real-Time Messaging Protocol)是Adobe开发的协议,用于高性能流媒体传输。
RTMP协议通过发送音视频数据块来实现实时性较高的流媒体传输。
尤其在直播领域,RTMP被广泛应用。
然而,由于其是Adobe自有协议,导致其在移动设备和部分客户端上的兼容性有一定问题。
1.4 HLSHLS(HTTP Live Streaming)是苹果公司推出的流媒体传输协议,在移动设备和桌面浏览器上具有良好的兼容性。
HLS协议通过将音视频流切分成若干个小片段进行传输,并根据网络情况动态调整码率,以实现适应不同网络环境下的流媒体传输。
abbreviations0-93G3rd Generation Networks3PL3rd Party Logistics4PL4th Party Logistics4SC4-High Straddle Carrier5-S Seiri, Seiton, Seiso, Seiketsu, ShitsukeAABC ABC ClassificationAGVs Automated Guided VehiclesAI Artificial IntelligenceAMPS Administrative Monetary Penalty SystemAMS Automated Manifest SystemANERA Asia North America Eastbound Rate Agreement A.P.All purposesAPEC Asia-Pacific Economic CooperationAPI Application Programming InterfaceASME American Society of Mechanical Engineers ASN Advanced Shipping NoticeASP Active Sever PageAS/RS Automated Storage and Retrieval Systema.t.s.All time savedAWB Air WaybillBB2B Business to BusinessB2C Business to CustomerBAF Bunker Adjustment FactorB/B Break BulkBCC Blind Carbon CopyBCO Beneficial Cargo OwnerBIMCO The Baltic and International Maritime Council B/L Bill of LadingBPO Business Process OutsourcingBSC Balanced ScorecardBSP British Standard Pipe TreadCCAF Currency Adjustment FactorCBM Cubic MetreCBO Community Based OrganizationCC Carbon CopyCCR Commodity Classification RatesCDMA Code Division Multiple AddressCEP Courier, Express, ParcelCEPA Closer Economic Partnership Arrangement C&F Cost and FreightCF Collapsible Flat RackCFM Cubic Feet per MinuteCFR Cost and FreightCFS Container Freight StationCGI Common Gateway InterfaceCIF Cost, Insurance and FreightCILT The Chartered Institute of Logistics andTransportCIM The Chartered Institute of MarketingCIP Carriage and Insurance Paid ToCIS Commonwealth of Independent States CKD Completely Knocked DownCLM The Council of Logistics ManagementCLP Container Load PlanCNOOC China National Offshore Oil Corp.C/O Certificate of OriginCOA Contract of AffreightmentC.O.C.Carrier's Own ContainerC.O.D.Cash On DeliveryCOFC Container-on-flatcarCOGS Cost of Goods SoldCon-Ro Container-Roll ShipCOP Custom of the PortCOSCO China Ocean Shipping CompanyCOSL China Oilfield Services LimitedC/P Charter PartyCPFR Collaborative Planning Forecasting andReplenishmentCPT Carriage Paid ToCQD Customary Quick DispatchCRM Customer Relationship ManagementCRP Continuous Replenishment ProgramCSC International Convention for Safe ContainerCSF Critical Success FactorCSI Container Securtiy IntiativeCSP Commerce Service ProvidersCY Container YardDD/A Document Against Acceptance DAF Delivered at FrontierDC Distribution CentreD1/2D Demurrage Half DispatchDDC Destination Delivery ChargeDDF Documentation Fee – Destination DDP Delivered Duty PaidDDU Delivered Duty UnpaidDEQ Delivered Ex-QuayDES Delivered Ex-Shipd.f.Dead FreightDFZ Duty Free ZoneD.G.Dangerous GoodsDHC Handling Charge – Destination DNS Domain Name SystemD/O Delivery OrderD.O.P Dropping Outward PilotDOS Disk Operating SystemD/P Document Against PaymentDPA Transport Arbitrary – Destination DPP Damage Protection PlanD/R Dock ReceiptDRP Distribution Resources Planning DWCT Deadweight Cargo TonnageDWT Deadweight Tonnage (All Told)EECR Efficient Customer Response ECSI Export Cargo Shipping Instruction EDI Electronic Data InterchangeEH&S Environment Health & SafetyEIR Equipment Interchange Receipt E.I.U.Even If UsedE.&O.E.Errors and Omissions Excepted EOQ Economic Order QuantityEPQ Economic Production Quantity ERM Enterprise Resources Management ERP Enterprise Resources Planning ETA Estimated Time of ArrivalETD Estimated Time of DepartureETR Estimated Time of ReadinessETS Estimated Time of SailingEXW Ex-WorksFFAF Fuel Adjustment FactorFAK Freight All KindsFAQ Frequently Asked QuestionFAS Free Alongside ShipFB/L FIATA Combined Transport Bill of Lading FBO Faith Based OrganisationFCA Free CarrierFCL Full Container LoadFCR Forwarder's Cargo ReceiptFEFC Far East Freight ConferenceFEU Forty Feet Equivalent UnitF.H.E.X.Fridays and holidays excludedF.I.Free InFIATA International Federation of Forwarding Agent AssociationsFIBC Flexible Intermediate Bulk ContainerFIFO First-in, First-outF.I.O.Free In and OutFIOST Free In, Out, Stowed & TrimmedFIS Fixed-Interval SystemFMC Federal Maritime CommissionFMCG Fast Moving Consumer GoodsF.O.Free OutFOA Fire Defence Agency (Japanese)FOB Free On BoardF.O.R.Free On RailF.O.T.Free On TruckF.P.A.Free of Paticular AverageFQS Fixed-Quantity SystemFR Flat Rack ContainerFRC Fuel Recovery ChargeFSDC Full-Service Distribution CompanyFT Freight TonFTP File Transfer ProtocolFTZ Free Trade ZonesGGATT General Agreement on Tariffs and Trade GCC Gas Carrier CodeGCR General Cargo RatesGDP Gross Domestic ProductGIF Graphics Interchange FormatGMDSS Global Maritime Distree and Safety System GP General Purpose ContainerGPRS General Packet Radio ServiceGPS Global Positioning SystemGRI General Rate IncreaseGRT Gross Registered TonnageGSA General Sales AgentGSC Global Supply ChainGSM Global System for Mobile CommunicationsGVW Gross Vehicle WeightsGWT Gross WeightHHAFFA Hong Kong Association of Freight Forwarding and Logistics Ltd.HAWB House Air WaybillH.F.O.Heavy Fuel OilH/H Half Height ContainerHKIM Hong Kong Institute of MarketingHSCodesHarmonized System of CodesHTML Hypertext Mark-up LanguageHTTP Hypertext Transfer ProtocolII.A.Im AuftragIADA Intra Asia Discussion AgreementIAF Inflation Adjustment FactorI.A.RatesIndependent Action RatesIATA International Air Transport AssociationIBC Intermediate Bulk ContainerICAO International Civil Aviation OrganizationICC International Chamber of CommerceICD Inland Container DepotICP Internet Content ProviderICT Information and Communications TechnologyIEEE the Institute of Electronic and Electrical EngineeringIICL Institute of International Container Lessors IMDG International Maritime Dangerous Goods Code IMF International Monetary FundIMO International Maritime OrganizationIncotermsInternational Commercial TermsIP Internet ProtocolIPI Interior Point IntermodalIPO Initial Public OfferingIRA Informal Rate AgreementISAPI Internet Server Application ProgrammingInterfaceISDN Integrated Server Digital NetworkISO International Standard OrganizationISP Internet Service ProviderISPS International Ship and Port Facility Security ITF International Transport Workers' Federation IWL Institute Warranty LimitsJJIT Just In TimeKKbps Kilobits per secondKPI Key Performance IndicatorKSF Key Success FactorK/T Kilo TonsLLAN Local Area NetworkingLASH Ligther Aboard ShipLAYCAN Laydays/Cancelling (Dates)L/C Letter of CreditLCL Less than a Container LoadL/G Letter of GuaranteeL.I.Liner InwardLIFO Liner In Free OutLILO Last-In, Last-OutL.I.O.Liner In and OutL/L Loading ListL.L.M.C Limitation of Liability for Maritime Claims LMX Leader-Member ExchangeLNG Liquefied Natural GasL.O.A.Lenght OverallLo-Lo Lift-on Lift-off ShipLPG Liquefied Petroleum GasLSD Landing, Storage and DeliveryLT Lead TimeLTL Less-Than-TruckloadMMAWB Master Air WaybillMB MegabyteMBO Management By ObjectiveMbps Millions of Bits Per SecondMIS Management Information SystemMLB Mainland BridgeMLO Main Line OperatorsMMS Multimedia Messaging ServicesM/N Marks and NumbersMNC Multinational Corporationmol.More or LessMOLCHMore or Less in Character's OptionOPMOLOO More or Less in Owner's OptionMPEG Motion Picture Experts GroupMPS Master Production ScheduleMQC Minimum Quantity CommitmentM/R Mate RateMRP Material Requirements PlanningMRP II Manufacturing Resource PlanningM/S Motor ShipMSDS Material Safety Data SheetMT Metric TonMTO Multimode Transport OperatorNN/A Not Applicable/Not AvailableNAFTA North America Free Trade AgreementNAP Network Access PointNCV No Customs ValuationNEC Not Elsewhere ClassifiedNGO Non-Governmental OrganizationN.O.E.Not Otherwise EnumeratedNOI Not Otherwise IndexedNOIBN Not Otherwise Indexed by NameNOR Notice of ReadinessN.O.S.Not Otherwise SpecifiedNPO Non Profit OrganizationNRT Net Registered TonnageNVD No Value DeclaredNVOCC Non Vessel Operating Common Carrier NWT Net WeightOOCP Overland Common PointOD Organization DevelopmentODC Odd Dimension CargoesODF Documentaion Free - OriginOECD Organization for Economic Cooperation and DevelopmentOEM Original Equipment ManufacturerO/H Over HeightOHC Handling Charge - OriginOJT On-the-Job TrainingOMC Occupational Market ConditionOPM Other People's MoneyORC Origin Receiving ChargeO/S Open Side ContainerOS&D Over, Short and DamagedOSHA Occupational Safety & Health ActOT Open Top ContainerO/T Over TimeOTROff-the-Road TyresTyresO/W Over WidthOWS Overweight SurchargePP2P Path to ProfitP2P Peer-to-PeerPAI Peformance Appraisal InterviewPAQ Position Analysis QuestionairePCD Pitch Circle DiameterPCS Port Congestion SurchargePDA Personal Digital AssistantPDF Portable Document FormatPDPR Per Day Pro RataPENAVIChina Ocean Shipping CompanyCOP.F.T.Per Freight TonP. & I.Protection and Indemnity Club (Association) ClubPKI Public Key InfrastructurePOD Port of DischargePOL Port of LoadingPOP Point of PresencePOS Point of SaleP.P.Per ProeurationemPPP Point-to-Point ProtocolPRD Pearl River DeltaPS Port SurchargePSS Peak Season SurchargePSTN Public Switched Telephone NetworkPTO Please Turn OverleafPWS Personal Web ServerQQDII Qualified Domestic Institutional Investors QFII Qualified Foreign Institutional InvestorsQR Quick ResponseRRAM Random Access MemoryREIT Real Estate Investment TrustRF Reefer ContainerRFID Radio Frequency IdentificationRFP Request for ProposalRFQ Request for QuotationRFRC Rail Fuel Recovery ChargeRMB RenminbiRMG Rail Mounted GantryROA Return on AssetsR.O.B.Remaining on BoardROI Return on InvestmentRo-Ro Roll-on Roll-off ShipRRS Rate Restoration SurchargeR/T Revenue TonsR.T.W.Round the World ServiceRVNX Released Value Not ExceedingSS.A.Safe GroundSAN Storage Area NetworkS.B.Safe BerthSBT Segregated Ballast TankS/C Service ContractSCM Supply Chain ManagementSCQ Special Commodity QuotationSCR Specific Commodity RatesS.D.Single Deck ShipSED Shipper's Export DeclarationSER Carrier Security ChargeSET Secure Electronic TransactionS.G.Specific GravitySHEX Saturday and Holidays Excluded SHINC Saturday and Holidays Included SIM.SUSimilar SubstituteB.SKU Stock Keeping UnitSLA Services Level AgreementSME Small and Medium-size Enterprises SMS Short Message ServicesSMTP Simple Mail Transport Protocol SNMP Simple Network Management Protocol S/O Shipping OrderS.O.C.Shipper's Own ContainerS.P.Safe PortSPC Statistical Process ControlSPIM Single Period Inventory ModelsSQL Structure Query LanguageSS Safety StockS/S SteamshipS.S.H.E. X.Saturdays, Sundays and Holidays ExcludedS.S.H.I.N.C.Saturdays, Sundays and Holidays Included SSL Secure Socket LayerS.T.C.Said To ContainSTCC Standard Transportation Commodity CodeTTACA Transatlantic Conference AgreementTBN To Be NominatedTCP Transmission Control ProtocolTDW Total DeadweightTEU Twenty-foot Equivalent UnitT.H.C.Terminal Handling ChargeTMS Transportation Management SystemTOFC Trailer-On-FlatcarTPC Tones Per CentimeterTPD Tones Per DayTPI Tones Per InchTQC Total Quality ControlTQM Total Quality ManagementT.R.S.Terminal Receiving StationTSA Transpacific Stabilization AgreementTSR Trans Siberian RailwayTT Telegraphic TransferTVC Time Volume ContractTWRA Transpacific Westbound Rate AgreementUUBC Universal Bulk CarrierUCP Uniform Customs and Practice for Documentary CreditsUHF Ultra High frequencyULCC Ultra Large Crude CarrierULD Unit Load DeviceUNCTAD United Nations Conference of Trade andDevelopmentURL Uniform Resource LocatorUU Unless UsedVVAN Value-Added NetworksV.A.T.Value Added TaxVHF Very High Frequencyly (Used in Tariffs to Specify Commodities VLCC Very Large Crude CarrierVMI Vendor Managed InventoryVOC Vessel Operating CarrierV.O.W.Vehicle On WheelVPN Virtual Private NetworkV.S.A.Vessel Sharing AgreementVSL VesselWWAP Wireless Appreciation ProtocolWCS Wireless Communications ServiceWDEX Warehouse Withdrawal for Transportation Immediate ExportationWDT Warehouse Withdrawal for TransportationWDT&E Warehouse WithdrawalforTransportationExportationW.E.F.With Effect FromW.I.B.O. N.Whether In Berth Or NotW.I.F.P.O.N.Whether In Free Pratique Or NotWI-FI Wireless FidelityWIP Work in ProcessW.I.P.O.N.Whether In Port Or NotW/M Weight or MeasurementWMS Warehouse Management SystemWPA With Paticular AverageW.P.Weather PermittingW.R.War RisksWTO World Trade OrganizationW.T.S.Working Time SavedW.W.Warehouse WarrantWWD Weather Working DaysW.W.R.C.D.Whe n Wh ere Ready on Completion of Discharge WWW World Wide WebXXML Extensible Mark-up LanguageYYAS Yen Appreciate Surcharge第三代網路第三方物流第四方物流集裝箱高跨車吊具常組織、常整頓、常清潔、常規範、常自律ABC分類化自動導引車人工智能行政罰款制度海關自動艙單系統亞洲北美東向運協會全部裝卸時間亞太經濟合作組織程式設定介面機械工程師美洲協會事前出貨通知單動態伺服端網員自動化存儲和修復系統操作節省的全部時間空運提單企業與企業之間的交易企業與客戶之間的交易燃油附加費散件雜貨密件抄送貨物擁有者權益波羅的海國際海運公會海運提單企業外判程序平衡記分卡英國標準的管子踩踏幣值附加費立方米社區性組織抄送等價貨物運價分發(部門)若干位址編碼-更緊密經貿關系的安排成本和運費折疊式板架集裝箱每分鐘的立方尺成本和運費集裝箱貨物集散站共同閘道介面成本和運費兼付保險費英國特許物流運輸學會英國特許市務學會兼付指定運費及保險費獨立國家聯合體全拆裝物流管理學會集裝箱/裝載計劃表中國海洋石油總公司產地來源證包運合同船東提供集裝箱交貨付現集裝箱輸送銷貨成本集裝箱/滾裝兩用船港口慣例中國遠洋運輸公司中海油田服務股份有限公司租船合同(租約)預報和補充合作計劃兼付指定運費習慣快速裝運客戶關係管理連續補充庫存計劃對安全容器的國際規定-商業服務提供商集裝箱堆場承兌交單貨交邊境配送中心速遣費為滯期費的一半目的地提貨費目的地文件費貨交入口國家連稅貨交入口國家倉庫貨交指定港口倉庫貨交指定港口船上虧艙費貨交指定港口倉庫危險品貨物目的地操作費網絡領域名字系統出貨單引航員下船時磁盤作業系統付款交單目的地運輸附加費集裝箱損壤保險場站收據分發資源計劃淨載重吨位總載重吨位(量)有效回應顧客的準則-電子資訊傳遞職業環境健康安全集裝箱設備交接單即使使用錯誤和遺漏不在此限經濟訂購量經濟生產批量企業資源管理企業資源計劃預定扺港時間預定離港時間預計準備就緒時間到戶取貨燃料附加費同一費率常見問題船邊交貨國際運輸商協會聯運提單宗教組織貨交貨運商人整箱集裝貨運承運人領貨單遠東歐州運費公會40英呎標準雜裝箱計算單位星期五和節假日除外船方負責裝船費用國際運輸商協-貨物先進倉和先出倉的安排船方不負擔裝卸費船方不負責裝船卸船理艙及平艙費用定期訂貨方式美國聯邦海事委員會快速銷售消費品船方不負責卸船費用防禦代辦處離岸價格火車上交貨貨車上交貨-定量訂貨方式平板集裝箱恢復燃料費全方位物流服務公司運費吨檔案傳輸協定自由貿易區關與貿易總協定-普通貨物運價國民生產總值圖形學交換版式-多用途集裝箱全球衛星定位系統全部費率調高注冊(容積)總吨總推廣代理全球供應鏈全球系統之機動通信-毛重香港貨運物流業協會有限公司代理空運提單重油半高集裝箱香港市務學會-超文本記號超文本傳送-亞洲集裝箱運輸研討協定通貨膨脹調整系數獨立等級價格國際航空運輸協會中型液體集裝箱國際民用航空組織國際商會?陸集裝箱聯網內容供應商資訊和通訊技術電子和電的工程學院國際集裝箱出租商學會國際危險的商品代碼-國際海事組織國際貿易術語國際網路議定書經美國西岸入內陸運輸首次上市集資項目非正式運價協定國際網路伺服器應用式設計介面數位式多功能公眾通信網路國際標準化組織網絡供應商國際船舶與港口保安設施規則國際運輸工人聯合會(倫敦保險人)協會保証航行範圍運送及時千分之一秒關鍵績效指標成功因素公噸本區域網絡集裝箱子母船-信用證併箱散貨保函入口航線運費不包括卸貨費貨物後進倉和後出倉的安排船方負責裝卸費,但不包碼頭費裝貨清單海事索賠任限制領導-成員交換理論液化天然氣全長吊裝船液化石油汽卸貨、倉儲和送貨費訂貨到交貨的時間散貨拼車空運提單百萬位元目標管理數百萬位分之一秒管理資訊系統大陸橋運輸模式遠洋船公司多型通訊聯繫服務嘜頭-增减承租人有增選擇權船東有增選擇權活動圖片小組專家總生產日程表最小數量承諾-材料需要計劃-輪船材料安全資料表公吨聯運商不適用/無資料北美自由貿易協定網路途徑點無聲明價值-非政府組織除非另有列名--船舶準備就緒通知書除非另有指定非營利組織注冊(容積)淨吨不要求聲明價值無船舶公共承運商-內陸公共交貨點組織發展特殊尺寸貨物來源地文件費-原產商超出正常高度來源地操作費在職培訓-籌集資金始發港付加費開邊集裝箱超, 欠及破損 (指收貨與提單不一致的三種情況) -開頂集裝箱加班時間-超出正常闊度超重附加費對得益的路徑同儕網路運算---港口擠塞附加費電子手賬便攜式文件版式-中國外輸代理公司(外代)每運費吨船東保賠協會公開鑰匙基礎卸貨港裝貨港存在的點--點對點的草案泛珠三角州港口附加費季節附加費公開轉換電話網路請閱後頁私人伺服器國內機構投資者赴海外投資資格認定制度國外機構投資者到內地投資資格認定制度快速反應隨機途徑記憶(存儲器)領匯房地產投資信託基金冷藏集裝箱無線射頻識別技術書面建議要求書面報價要求軌道燃料恢復費用人民幣台軌道式龍門吊資產回報船上所有投資回報滾裝船比率修復附加費計費噸全球性服務-安全擱淺網路存儲安全泊位分隔壓載水艙貨量簽訂合同鏈鎖供給管理特種商品報價特種貨物運價單層甲板船-船東保安費用安全電子交易比重--相似替換船儲備保持的單位服務等級協議中、小型企業短訊服務簡單郵件運輸草案簡單網路管理草案裝船單付貨人所屬集箱安全港口統計製程管制單一週期的存貨模式架構疑問語安全庫存-星期六、日和節假日除外星期六、日和節假日包括在內付款加密法據報內裝-跨大西洋公會協定指定船舶傳輸控制草案總載重量20英呎標準集裝箱計算單位碼頭操作費運輸管理系統集裝箱車架輸送每厘米吃水吨數每天裝卸吨數每英寸吃水吨數全面品質控制全面品質管理碼頭收貨站跨太平洋穩定協議西伯利亞大鐵路電匯時間貨量合同泛太平洋西向運費協會通用散裝貨船跟單信用證統一慣例和實務特高頻50萬噸油輸成組器聯合國貿發會議網址-增值網增值稅甚高頻-20萬噸油輪供應商的存貨管理系統船舶承運商可駕駛的車輛虛疑網路船舶共用協議輪船無線應(運)用草案無線通信服務---自生效無論靠泊與否無論是否通過檢驗無線相容認證未完工的產品不論是否在港內重量/體積倉庫管理系統-天氣允許兵險-節省的裝卸時間--何時何處還船全球資訊網(發源地-歐洲量子物理實驗室)可延長的記號語言日圓調整費。
0引言屏幕映射属于一种新的显示方法,也就是说它能将完整的窗口界面通过网络,映射到另一台计算机的屏幕上,主要解决不同设备之间的互操作与资源共享问题。
苹果公司最早提出的图形用户界面GUI (Graphic User Interface)为屏幕映射技术的产生和发展奠定了基础[1]。
伴随着物联网的快速发展,车联网也呼之欲出,车机互联也逐步成为车联网研究的重要应用之一。
在车联网车载终端应用过程中,由于车载终端硬件设备更新换代较慢,部分功能不能满足发展的需要,迫切需要一种替代的功能更新方案,屏幕映射技术的出现解决了车载终端硬件功能不足的问题。
将移动终端屏幕内容镜像到车载大屏幕,让我们可以利用移动终端的硬件与软件的强大功能,解决车载终端的不足,同时,利用车载终端的大屏幕显示移动终端的内容,不用看着移动终端屏幕,只需要用车载上的物理按键或语音命令就能控制手机,给驾乘人员带来更多的便利与舒适。
目前屏幕映射主要有3种互联方案:(1)MirrorLink。
MirrorLink最大的优势是平台独立独立性和开放性,MirrorLink有更好的兼容性,除了iOS设备外,几乎所有的主流智能手机系统都能支持[2]。
MirrorLink支持无线和有线连接,能够实现屏幕双向控制等。
但是,MirrorLink也存在播放视频延时,不支持语音控制等缺陷。
(2)AirPlay。
AirPlay拥有流畅清晰的画面,美中不足的是没法实现双向控制,支持的视频格式有限,连接不方便等缺点。
(3)Miracast。
Miracast[2]的技术优势是其视频播放的流畅度,但是Miracast方案也有显著的缺点:无法双向控制、延迟明显、车机需要自带wifi、耗电现象严重等。
由于MirrorLink概念提出时间早且是唯一的行业内推出的统一标准,平台独立性与开放性,兼容性好等优点,目前大多数汽车厂商都采用此方案。
课题组针对MirrorLink的不足,融合了Miracast在视频传输的优点,设计出了一套新的车机互联方案。
计算机方面的英文术语的英文缩写:3GIO(Third Generation InputOutput,第三代输入输出技术)ACR(Advanced Communications Riser,高级通讯升级卡)ADIMM(advanced Dual In-line Memory Modules,高级双重内嵌式内存模块)AGTL+(Assisted Gunning Transceiver Logic,援助发射接收逻辑电路)AHCI(Advanced Host Controller Interface,高级主机控制器接口)AIMM(AGP Inline Memory Module,AGP板上内存升级模块)AMR(Audio/Modem Riser;音效/调制解调器主机板附加直立插卡)AHA(Accelerated Hub Architecture,加速中心架构)AOI(Automatic Optical Inspection,自动光学检验)APU(Audio Processing Unit,音频处理单元)ARF(Asynchronous Receive FIFO,异步接收先入先出)ASF(Alert Standards Forum,警告标准讨论)ASK IR(Amplitude Shift Keyed Infra-Red,长波形可移动输入红外线)AT(Advanced Technology,先进技术)ATX(AT Extend,扩展型AT)BIOS(Basic InputOutput System,基本输入输出系统)CNR(Communication and Networking Riser,通讯和网络升级卡)CSA(Communication Streaming Architecture,通讯流架构)CSE(Configuration Space Enable,可分配空间)COAST(Cache-on-a-stick,条状缓存)DASP(Dynamic Adaptive Speculative Pre-Processor,动态适应预测预处理器)DB Device Bay,设备插架DMI(Desktop Management Interface,桌面管理接口)DOT(Dynamic Overclocking Technonlogy,动态超频技术)DPP(direct print Protocol,直接打印协议DRCG(Direct Rambus clock generator,直接RAMBUS时钟发生器)DVMT(Dynamic Video Memory Technology,动态视频内存技术)E(Economy,经济,或Entry-level,入门级)EB(Expansion Bus,扩展总线)EFI(Extensible Firmware Interface,扩展固件接口)EHCI(Enhanced Host Controller Interface,加强型主机端控制接口)EISA(Enhanced Industry Standard Architecture,增强形工业标准架构)EMI(Electromagnetic Interference,电磁干扰)ESCD(Extended System Configuration Data,可扩展系统配置数据)ESR(Equivalent Series Resistance,等价系列电阻)FBC(Frame Buffer Cache,帧缓冲缓存)FireWire(火线,即IEEE1394标准)FlexATX(Flexibility ATX,可扩展性ATX)FSB(Front Side Bus,前端总线)FWH(Firmware Hub,固件中心)GB(Garibaldi架构,Garibaldi基于ATX架构,但是也能够使用WTX构架的机箱)GMCH(Graphics & Memory Controller Hub,图形和内存控制中心)GPA(Graphics Performance Accelerator,图形性能加速卡)GPIs(General Purpose Inputs,普通操作输入)GTL+(Gunning Transceiver Logic,发射接收逻辑电路)HDIT(High Bandwidth Differential Interconnect Technology,高带宽微分互连技术)HSLB(High Speed Link Bus,高速链路总线)HT(HyperTransport,超级传输)I2C(Inter-IC)I2C(Inter-Integrated Circuit,内置集成电路)IA(Instantly Available,即时可用)IBASES(Intel Baseline AGP System Evaluation Suite,英特尔基线AGP系统评估套件)IC(integrate circuit,集成电路)ICH(InputOutput Controller Hub,输入输出控制中心)ICH-S(ICH-Hance Rapids,ICH高速型)ICP(Integrated Communications Processor,整合型通讯处理器)IHA(Intel Hub Architecture,英特尔Hub架构)IMB(Inter Module Bus,隐藏模块总线)INTIN(Interrupt Inputs,中断输入)IPMAT(Intel Power Management Analysis Tool,英特尔能源管理分析工具)IR(infrared ray,红外线)IrDA(infrared ray,红外线通信接口,可进行局域网存取和文件共享)ISA(Industry Standard Architecture,工业标准架构)ISA(instruction set architecture,工业设置架构)K8HTB(K8 HyperTransport Bridge,K8闪电传输桥)LSI(Large Scale Integration,大规模集成电路)LPC(Low Pin Count,少针脚型接口)MAC(Media Access Controller,媒体存储控制器)MBA(manage boot agent,管理启动代理)MC(Memory Controller,内存控制器)MCA(Micro Channel Architecture,微通道架构)MCC(Multilayer Ceramic Capacitor,积层陶瓷电容)MCH(Memory Controller Hub,内存控制中心)MDC(Mobile Daughter Card,移动式子卡)MII(Media Independent Interface,媒体独立接口)MIO(Media IO,媒体输入输出单元)MOSFET(metallic oxide semiconductor field effecttransistor,金属氧化物半导体场效应晶体管)MRH-R(Memory Repeater Hub,内存数据处理中心)MRH-S(SDRAM Repeater Hub,SDRAM数据处理中心)MRIMM(Media-RIMM,媒体RIMM扩展槽)MSI(Message Signaled Interrupt,信息信号中断)MSPCE(Multiple Streams with Pipelining and Concurrent Execution,多重数据流的流水线式传输与并发执行)MT=MegaTransfers(兆传输率)MTH(Memory Transfer Hub,内存转换中心)MuTIOL(Multi-Threaded IO link,多线程IO链路)NCQ(Native Command Qu,本地命令序列)NGIO(Next Generation InputOutput,新一代输入输出标准)NPPA(nForce Platform Processor Architecture,nForce平台处理架构)OHCI(Open Host Controller Interface,开放式主控制器接口)ORB(operation request block,操作请求块)ORS(Over Reflow Soldering,再流回焊接,SMT元件的焊接方式)P64H(64-bit PCI Controller Hub,64位PCI控制中心)PCB(printed circuit board,印刷电路板)PCBA(Printed Circuit Board Assembly,印刷电路板装配)PCI(Peripheral Component Interconnect,互连外围设备)PCI SIG(Peripheral Component Interconnect Special Interest Group,互连外围设备专业组)PDD(Performance Driven Design,性能驱动设计)PHY(Port Physical Layer,端口物理层)POST(Power On Self Test,加电自测试)PS2(Personal System 2,第二代个人系统)PTH(Plated-Through-Hole technology,镀通孔技术)RE(Read Enable,可读取)QP(Quad-Pumped,四倍泵)RBB(Rapid BIOS Boot,快速BIOS启动)RNG(Random number Generator,随机数字发生器)RTC(Real Time Clock,实时时钟)KBC(KeyBroad Control,键盘控制器)SAP(Sideband Address Port,边带寻址端口)SBA(Side Band Addressing,边带寻址)SBC(single board computer,单板计算机)SBP-2(serial bus protocol 2,第二代串行总线协协)SCI(Serial Communications Interface,串行通讯接口)SCK (CMOS clock,CMOS时钟)SDU(segment data unit,分段数据单元)SFF(Small Form Factor,小尺寸架构)SFS(Stepless Frequency Selection,步进频率选项)SMA(Share Memory Architecture,共享内存结构)SMT(Surface Mounted Technology,表面黏贴式封装)SPI(Serial Peripheral Interface,串行外围设备接口)SSLL(Single Stream with Low Latency,低延迟的单独数据流传输)STD(Suspend To Disk,磁盘唤醒)STR(Suspend To RAM,内存唤醒)SVR(Switching Voltage Regulator,交换式电压调节)THT(Through Hole Technology,插入式封装技术)UCHI(Universal Host Controller Interface,通用宿主控制器接口)UPA(Universal Platform Architecture,统一平台架构)UPDG(Universal Platform Design Guide,统一平台设计导刊)USART(Universal Synchronous Asynchronous Receiver Transmitter,通用同步非同步接收传送器)USB(Universal Serial Bus,通用串行总线)API(Application Programming Interfaces,应用程序接口)ASCII(American Standard Code for Information Interchange,美国国家标准信息交换代码)ATL ActiveX Template Library(ActiveX模板库)BASICBeginner's All-purpose Symbolic Instruction Code(初学者通用指令代码)COM Component Object Model(组件对象模式)DNA Distributed Internet Application(分布式因特网应用程序)HLL(high level language,高级语言)HLLCA(High-Level Language Computing Architecture,高级语言计算架构)MFC Microsoft Foundation Classes(微软基础类库)NVSDK(nVidia Software Development Kit,nvidia软件开发工具包)SDK(Software Development Kit,软件开发工具包)STL(Standard Template Library,标准模版库)AES(Attachment Execution Service,附件执行服务)ASF(Advanced Streaming Format,高级数据流格式)ASP(Active Server Pages,活动服务页)BRC(Beta Release Candidate,测试发布候选版0)CE(Consumer Electronics,消费电子)COA(Certificate of Authenticity,真品证明书)DCOM(Distributing Component Object Model,分布式组成物体模块)DCE(Desktop Composition Engine,桌面组成引擎)DEP(data execution prevention,数据执行预防)DHCP(Dynamic Host Configuration Protocol,动态主机分配协议)DID(Device ID,设备ID)dll(dynamic link library,动态链接库)DMF Distribution Media FormatDMT(Discreet Monitor Timing,智能型显示器调速)DOM(Document Object Model,文档目标模型)DUN(Dial-Up Networking,拨号网络)E-WDM(Enhanced Windows Driver Model,增强型视窗驱动程序模块)EULA(End-User License Agreement,最终用户释放协议)EPM(enterprise project manage)ERD(Emergency Repair Disk,应急修理磁盘)GDI(Graphics Device Interface,图形设备接口)GUI(Graphics User Interface,图形用户界面)GPF(General protect fault,一般保护性错误)GTF(General Timing Formula,普通调速方程式)HCL(Hardware Compatibility List,硬件兼容性列表)HCRP(Hardcopy Cable Replacement Profile,硬复制电缆复位协议子集)HE(Home Edition,家庭版)HTA HyperText Application,超文本应用程序IAS(Internet Authentication Service,因特网证明服务)ICF(Internet Connection Firewall,因特网连接防火墙)IIS(Internet Information Server,因特网信息服务器)INF File(Information File,信息文件)INI File(Initialization File,初始化文件)IOMON(Intel WDM IO Subsystem Performance Monitor,英特尔WDM输入输出子系统性能监视)LOB(Large Object,大型对象)MBSA(Microsoft Baseline Security Analyzer,微软基准安全分析器)ME(Millennium Edition,千年版)MMC(Microsoft Management Console,微软管理控制台)MMC(MultiMedia Controler,多媒体控制器)MTP(Microsoft Multimedia Transport Protocol,微软多媒体传输器协议)MUI(Multilingual User Interface,多语言用户接口)NDIS Network Driver Interface Specification,网络驱动程序接口规范NT(New Technology,新技术)OLE(Object Linking and Embedding,对象链接和嵌入)OPP(Object Push Profile,物体推拉传输协议)PAN(Personal Area Networking,个人区域网络)Qos(Quality of Service,服务质量)RC(Release Candidate,候补释放版)RDP(Remote Desktop Protocol,远程桌面协议)RMS(Rights Management Services,版权管理服务)RPC(remote procedure calls,远程程序呼叫)RRVP Resource ReserVation Protocol(资源保留协议)RsoP(Resultant Set of Policy,方针结果规定)RTM(release to manufacture,厂商版,公开发行批量生产)RTOS(Real Time Operating Systems,实时操作系统)SBFS Simple Boot Flag Specification,简单引导标记规范SDP(Service Discovery Protocol,服务发现协议)SHS(Shell Scrap Object,外壳剪贴对象)SID(Subsystem ID,子系统ID)SIP(Session Initiation Protocol,会议起始协议)SMS(Systems Management Server,系统管理服务器)SP(Service Pack,服务工具包)SVID(Subsystem Vendor ID,子系统销售者ID)VBA(Visual Basic for Applications,应用程序可视化Basic)VEFAT Virtual File Allocation Table(虚拟文件分配表)VSDS(Visual Studio development System ,虚拟工作室发展系统)VxD(Virtual device drivers,虚拟设备驱动程序)VID(Vendor ID,销售者ID)VLK(Volume License,大量授权企业版)WebDAV(Web-based Distributed Authoring and Versioning,基于网页的分布式创造和翻译)WDM(Windows Driver Model,视窗驱动程序模块)WGF(Windows Graphic Foundation,视窗图形基础)Winsock Windows Socket,视窗套接口WFP(Windows File Protection,视窗文件保护)WHQL Windows Hardware Quality Labs,Windows硬件质量实验室WHS Windows Scripting Host,视窗脚本程序WMA(Windows Media Audio,视窗媒体音频)WMP(Windows Media Player,视窗媒体播放器)WMS(Windows Media Services,视窗媒体服务)ZAM Zero Administration for Windows,零管理视窗系统CSS(Cascading Style Sheets,层叠格式表)DCD Document Content Description for XML XML文件内容描述DTD Document Type Definition,文件类型定义DTXS(Decryption Transform for XML Signature,XML签名解密转换)HTML(HyperText Markup Language,超文本标记语言)JVM(Java Virtual Machine, Java虚拟机)OJI Open Java VM Interface,开放JAVA虚拟机接口SDML(Small Device Markup Language,小型设备标示语言)SGML Standard Generalized Markup Language,标准通用标记语言SMIL Synchronous Multimedia Integrate Language(同步多媒体集成语言)VRML:Virtual Reality Makeup Language,虚拟现实结构化语言VXML(Voice eXtensible Markup Language,语音扩展标记语言)XML Extensible Markup Language(可扩展标记语言)XMLESP(XML Encryption Syntax and Processing,XML加密语法和处理)XSL(Extensible Style Sheet Language,可扩展设计语言)XSLT(Extensible Stylesheet Language Transformation,可扩展式表语言转换)ABB(Advanced Boot Block,高级启动块)ABP Address Bit Permuting,地址位序列改变ADT(Advanced DRAM Technology,先进DRAM技术联盟)AL(Additive Latency,附加反应时间)ALDC(Adaptive Lossless Data Compression,适应无损数据压缩)APM(Automated Precision Manufacturing,自动化精确生产)ATC(Access Time from Clock,时钟存取时间)ATP(Active to Precharge,激活到预充电)BEDO(Burst Enhanced Data-Out RAM,突发型数据增强输出内存)BPA(Bit Packing Architecture,位封包架构)AFC media(antiferromagnetically coupled media,反铁磁性耦合介质)BLP(Bottom Leaded Package,底部导向封装)BSRAM(Burst pipelined synchronous static RAM,突发式管道同步静态存储器)CAS(Column Address Strobe,列地址控制器)CCT(Clock Cycle Time,时钟周期)CDRAM(Cache DRAM,附加缓存型DRAM)CL(CAS Latency,CAS反应时间)CMR(Colossal Magnetoresistive,巨磁阻抗)CPA(Close Page Autoprecharge,接近页自动预充电)CSP(Chip Size Package,芯片尺寸封装)CTR(CAS to RAS,列地址到行地址延迟时间)DB Deep Buffer(深度缓冲)DD(Double Side,双面内存)DDBGA(Die Dimension Ball Grid Array,内核密度球状矩阵排列)DDR(Double Date Rate,上下行双数据率)DDR SDRAM(Double Date Rate,上下行双数据率SDRAM)DRCG(Direct Rambus Clock Generator,直接RAMBUS时钟发生器)DIL(dual-in-line)DIVA(Data IntensiVe Architecture,数据加强架构)DIMM(Dual In-line Memory Modules,双重内嵌式内存模块)DLL(Delay-Locked Loop,延时锁定循环电路)DQS(Bidirectional data strobe,双向数据滤波)DRAM(Dynamic Random Access Memory,动态随机存储器)DRDRAM(Direct RAMBUS DRAM,直接内存总线DRAM)DRSL(Direct RAMBUS Signaling Level,直接RAMBUS信号级)DRSL(Differential Rambus Signaling Levels,微分RAMBUS信号级)DSM(Distributed shared memory,分布式共享内存)ECC(Error Checking and Correction,错误检查修正)ED(Execution driven,执行驱动)EDO(Enhanced Data-Out RAM,数据增强输出内存)EHSDRAM(Enhanced High Speed DRAM,增强型超高速内存)EL DDR(Enhanced Latency DDR,增强反应周期DDR内存)EMS(Enhanced Memory System,增强内存系统)EMS(Expanded Memory Specification,扩充内存规格)EOL(End of Life,最终完成产品)EPROM(erasable, programmable ROM,可擦写可编程ROM)EPOC(Elevated Package Over CSP,CSP架空封装)EPV(Extended Voltage Proteciton,扩展电压保护)ESDRAM(Enhanced SDRAM,增强型SDRAM)ESRAM(Enhanced SRAM,增强型SRAM)EEPROM(Electrically Erasable Programmable ROM,电擦写可编程只读存储器)FCRAM(Fast Cycle RAM,快周期随机存储器)FEMMA(Foldable Electronic Memory Module Assembly,折叠电子内存模块装配)FM(Flash Memory,快闪存储器)FMD ROM (Fluorescent Material Read Only Memory,荧光质只读存储器)FPM(Fast Page Mode,快页模式内存)HDSS(Holographic Data Storage System,全息数据存储系统)HMC(holographic media card,全息媒体卡)HMD(holographic media disk,全息媒体磁盘)HSDRAM(High Speed DRAM,超高速内存)LRU(least recently used,最少最近使用)MADP(Memory Address Data Path,内存地址数据路径)MDRAM(Multi Bank Random Access Memory,多储蓄库随机存储器)MRAM(Magnetic Random Access Memory,磁性随机存取存储器)ns(nanosecond,纳秒,毫微秒,10亿分之一秒)NVRAM(Non-Volatile RAM,非可变性RAM)NWX(no write transfer,非写转换)ODR(Octal Data Rate,八倍数据率)ODT(on-die termination,片内终结器)OP(Open Page,开放页)PIROM:Processor Information ROM,处理器信息ROMPLEDM Phase-state Low Electron(hole)-number Drive MemoryPLL(Phase Lock Loop,相位锁定环)PRISM(Photorefractive Information Storage Material,摄影折射信息存储原料)PROM(Programmable Read Only Memory,可编程只读存储器)PTA(Precharge to Active,预充电到激活)QBM(Quad Band Memory,四倍边带内存)QRSL(Quad Rambus Signaling Levels,四倍RAMBUS信号级)RAC(Rambus Asic Cell,Rambus集成电路单元)RAC(Row Access Time,行存取时间)RAM(Random Access Memory,随机存储器)RAS(Row Address Strobe,行地址控制器)RAT(Precharge to Active Trp,预充电到激活时间)RCD(Row to Cas Delay,行地址到列地址控制器延迟时间)RDF(Rambus Developer Forum,RAMBUS发展商论坛)RDRAM(Rambus Direct RAM,直接型RambusRAM)RIMM(RAMBUS In-line Memory Modules,RAMBUS内嵌式内存模块)ROM(read-only memory,只读存储器)RRAM(Resistance RAM,非挥发性阻抗存储器)RP(RAS Pre-charge Times,行地址预充电时间)RL(Read Latency,读取反应时间)SCP(CHIP SCALE PACKGE,芯片比例封装)SD(Single Side,单面内存)SDRAM(Synchronous Dynamic RAM,同步动态内存)SDR(Single Date Rate,单数据率)SDR SDRAM(Single Date Rate,单数据率SDRAM)SGRAM(synchronous graphics RAM,同步图形随机储存器)SIMM(Single Inline Memory Module,单边直线内存模块)SLM(Spatial Light Modulator,空间光线调节器)SM(Smart Media,智能存储卡)SMRAM(System Management RAM,系统管理内存)SODIMM(Small Outline Dual In-line Memory Modules,小型双重内嵌式内存模块)SPD(Serial Presence Detect,串行存在检查)SRAM(Static Random Access Memory,静态随机存储器)SRAM(single-transistor DRAM,单晶体管DRAM)SSFDC(Solid State Floppy Disk Card,固态软盘卡,通常指Smart Media)SSTL(Stub Series Terminated Logic,残余连续终结逻辑电路)TCP(Tape Carrier Packaging,带载封装)TCSR(temperature compensated self refresh,温度补偿自刷新)TD(Trace driven,追踪驱动)TOM(Top of main memory,主内存顶端)TSOPs(thin small outline packages,小型薄型封装)UMA(Upper Memory Area,上部内存区)ULVS(ultra low voltage signal,超低电压信号)USWV(Uncacheable, Speculative, Write-Combining非缓冲随机混合写入)VCRAM(Virtual Channel Memory,虚拟通道内存)VCMA(Virtual Channel Memory architecture,虚拟通道内存结构)VCSDRAM(Virtual Channel SDRAM,虚拟通道内存)VM(Virtual Memory,虚拟存储器)VR(Virtual Register,虚拟寄存器)WBGA(Windows-BGA,WBGA的面积尺寸为传统TSOP封装的36.52%,重量为传统TSOP的23.37%,整个WBGA的面积与内核的比例为128%,也就是说,封装的面积仅比管芯大28%。
交互式多媒体通信标准Interactive multimedia communication standards play a crucial rolein the development of various communication technologies and platforms. It serves as a set of guidelines and protocols that ensure seamless interaction and exchange of multimedia data over different networks and devices. 交互式多媒体通信标准在各种通信技术和平台的发展中起着至关重要的作用。
它作为一套指导方针和协议,确保在不同网络和设备上实现多媒体数据的无缝互动和交换。
The development of interactive multimedia communication standards has revolutionized the way we communicate and share information. With the advent of these standards, users can now seamlessly engage in video calls, share high-quality audio and video content, and collaborate in real-time across different devices and platforms. 交互式多媒体通信标准的发展改变了我们交流和共享信息的方式。
有了这些标准的出现,用户现在可以轻松进行视频通话,分享高质量的音频和视频内容,并在不同设备和平台上实时进行协作。
These standards provide the foundation for the development of various multimedia applications and services, such as videoconferencing, live streaming, online gaming, and virtual classrooms. They ensure that multimedia data is transmitted and received in a consistent and reliable manner, regardless of the type of network or device being used. 这些标准为各种多媒体应用和服务的开发提供了基础,如视频会议、直播、在线游戏和虚拟课堂。
流媒体基础知识(上)一、前言随着越来越多的朋友开始选择ADSL、Cable Modem或FTTB+ LAN作为首要的上网方式,宽频时代即将到来,这使我们“宽频 KTV、影音聊天室、线上电影院、远程教育”的梦想即将成为现实,而与其密切相关的“流媒体(Streaming Media)”也成了许多人谈论的热门话题,因为“流媒体”正是实现这些宽频应用的技术动力。
宽频时代的到来还使得网民们不再满足于仅仅作为一项服务的受众,他们需要更大规模的交流,从中体现个体的价值,因此,许多朋友开始用自己的计算机,搭建网络广播和点播站点。
他们充满着满腔的热情,但不可否认的是,中国网民先天技术上的不足,让他们在建设这样的站点时遇到重重险阻,以至于放弃。
如何将这种热情在技术的引导下成为动力,这正是我们家用电脑所要做的,所以,在今天,在这里,我就将给大家介绍如何打造属于自己的流媒体服务器。
不过,在开始正式的流媒体服务器架设之前,请让我们先了解一下流媒体服务器的基础知识。
二、流媒体基础知识什么是流媒体?目前,在网络上传输音/视频等多媒体信息有两种解决方案,即http或ftp下载以及流式传输。
http或ftp下载使用标准的http和ftp协议,但由于多媒体信息个头巨大,下载一个多媒体文件一般需要几分钟或几小时的时间,这就造成为了看一个并不知道内容的视频,首先需要耗费可能比整个视频都要长的时间来完成下载。
这些被下载的文件还必须在下载前制作完成,放在网络服务器上,这样造成的直接后果就是:网络带宽不断提高,人们下载的等待时间越来越少,但最终还是不能观看网上现场直播。
流式传输时,声音、影像或动画等多媒体信息由流媒体服务器向用户计算机连续、实时传送,它首先在使用者端的电脑上创建一个缓冲区,于播放前预先下载一段资料作为缓冲,用户不必等到整个文件全部下载完毕,而只需经过几秒或十数秒的启动延时即可进行观看。
当多媒体信息在客户机上播放时,文件的剩余部分将在后台从服务器内继续下载。
1MULTIMEDIA TRANSPORT PROTOCOL ANDMULTICAST COMMUNICATIONSerge Fdida Laboratoire MASI-CNRS, Université Pierre et Marie Curie4 place Jussieu, 75005 Paris, FranceTel. +33-1-44-27-30-58, Fax. +33-1-44-27-62-86E-mail: Serge.Fdida@masi.ibp.frABSTRACTThe emerging of high speed networks provides the infrastructure for handling a wide set of new applications, covering distributed multimedia cooperative features. In this framework, multipeer communication is a major service/protocol issue because most of these applications exhibit the need for such a functionality. Besides many functions and mechanisms, the semantics of transport layer multicast conversation has to be defined. We show that a new service semantic called statistical-reliable, in which the reliability is enforced when desired by applications, is of major interest for the high-performance networking paradigm. This new reliability semantic can be implemented using a protocol akin to the XTP bucket algorithm. The interest of the developed protocol is that 1) it can perform efficiently on top of wide area (for instance ATM-based) networks as well as LANs, 2) it provides a continuous reliability service from best-effort to all-reliable as a function of the application requirements, 3) it is able to handle group size from small to very large with only a slight increase of overhead, 4) it works for unicast communication. These functionalities provide an interesting and efficient protocol for covering the need of distributed multimedia applications.1. INTRODUCTIONMultipeer communication defines the transfer of information units between several users, organized within a group structure. Multicasting or peer-to-multipeer exchange is designed for transferring information from a single source to a set of receivers known as the group. The multicast service is undoubtedly useful for distributed systems of the future. This service is currently under study in many standard protocols (ATM, Internet, Transport, Application). Multicasting offers significant performance advantages over multiple sequential unicastings in terms of efficient use of the network bandwidth, decreasing the elapsed time and increasing concurrency. It will thus rapidly become a preferred paradigm for many applications [Ngo91] such as resource finding [Aha88], replicated file system [Che85], distributed games [Ber85], distributed databases [Sto79], email distribution list [Sak85], routing table dissemination [Qui80] and computer conferencing [Agu86], etc.The concept of multicast communications has received much recent attention. One can cite work carried out in standardization committees (ANSI, ISO, etc. [Coh91, Coc92, Mou92, ISO93, MPC95] and projects CIO [Mat93, Mil93], Berkom [Del93] for the definition of a multicast taxonomy, service and protocol. Although, most of the existing multicast algorithms are focused on the MAC or IP [Dee89], [Top90] layer. Some work already started on point-to-multipoint communications in ATM-based systems [Rob95]. Little attention was devoted to the development of multicast protocols at the transport layer [ISO88, Che88, PEI92, San92].A transport layer multicast shall provide a simultaneous transfer of the same TPDU to a number of peer transport layer entities. In providing such a multicast service, the transport layer relies on the multicast capabilities provided by the underlying network. Multicasting can be achieved at different levels. It is natural at the MAC layer, also provided at the AAL layer (without error recovery), and can be made available at the network layer [Dee89] if required mechanisms are provided (connection set up, routing, resource management, etc.). When applied at the transport layer, functionalities to be used rely on the multicasting facilities provided at the lower layers, namely, either MAC, AAL or IP layer. Transport layer multicasting will be more easy to design if the underlying service provide an efficient multicasting facility; otherwise, some problems have to be solved such as packet replication, error recovery and routing. Other aspects needs definitely to be studied such as addressing and group management.We focus in this paper on the design issues of a multicast transport protocol able to perform efficiently on top of networks with various characteristics. This study is based on the XTP3.6 multicast approach [PEI92] and some other protocols [Cla87, Che88, Min89, Wat89]. See [Doe90] for a survey of lightweight transport protocols.In a modern transport protocol there are at least six procedures: connection management, data transfer, state/time synchronization, flowcontrol, rate control, and error control. Incorporating such procedures in a multicast transport layer imposes significant challenges and a new multicast protocol must be designed and integrated into the transport layer. One of the central issues associated with the development of the multicast transport protocol is error detection and recovery. The reliability semantic has a significant impact on the protocol complexity as well as the group size that increases overhead. We introduce a statistical-reliable multicast semantic that is able to cope with a wide set of application requirements and group size with a limited overhead. We then describe the basic design features of the associated protocol.The paper is structured as follows. Section 2 introduces briefly the transport layer multicast taxonomy, semantic and model. The motivation for a Statistical-reliable semantic is presented in section 3, as well as the salient features of the proposed protocol for ensuring efficient reliable communication. Other important issues related to multicasting are discussed in section 4. The concluding remarks and future work is contained in section 5.2. TRANSPORT LAYER MULTICASTIn this section, we briefly introduced some important issues of the multipeer/multicast environment that will be used in the remainder of the paper. Some key elements of the on-going multicast taxonomy definition are introduced. Then, we present the associated multicast service semantics that are used today as well as a model for the transport layer multicast.2.1 TaxonomyThe taxonomy is of most importance because it defines a common vocabulary and framework to name and address multipeer communication. Works on that topic started a few years ago and are mainly discussed within the OSI standardization body [Mou92, ISO93, Mat93, MPC95]. We briefly introduce in the sequel some important elements of the taxonomy.The group concept allows to define a set of entities as a single entity identified by a single group-name and group-address and whose membership in the group is defined by a rule, a set of rules or a list. A (N)-Multicast group is a set of (N)-entities that abide by the rule(s) for belonging to a group able to utilize multicast services. An (N)-enrolled-group is a set of entities, called members, which have completed the registration and activation procedures and therefore are in the position to be rached by the means of at least one (N)-group-name and (N)-group-address. A group can be static or dynamic depending on the fact that the criteria defining the group membership can evolve. A group has a known population when it is possible to identify the individual name or addressof every other member of the group. There are two sub-categories of known population: complete known population where every member of the group is able to determine the identity of every other member of the group and partial-known population where only a subset of the group is able to do so. A group has an unknown population where it is not possible to determine the identity of every member of the group. A (N)-group-association is an association established between members of an (N)-enrolled-group, and possibly (N)-entities not belonging to the enrolled-group, for the purpose of transfering data. The establishement of a (N)-group-association leads to the creation of a (N-1)-group-connection (connection-oriented-mode) or exists only during the instance of communication (connectionless mode). Within the (N)-enrolled-group membership, the members that have accepted to participate in a group-association are called participants and this set is called the Active-group. The Active-Group-Integrity (AGI) specifies the set of conditions concerning the active group which must be true in order for the group connection to be in the data transfer phase. When the AGI is no more satisfied, the group-association is either released or suspended until all conditions are satisfied again. For instance, a Quorum specifies that a minimum number of participants is required to consider that the AGI is satisfied.2.2 SemanticWithin the transport layer, multicast association needs to support a wide variety of Transport Service (TS) user requirements. Thus, the semantics of transport layer multicast association needs to be defined. We present four categories for this purpose.Best Effort Multicast provides a "best effort" sequential transport of a single variable length TSDU to a set of TS users. The service is best effort in that missing or corrupted TSDUs are not delivered or recovered. All-reliable Multicast ensures that the lost or damaged T P D U is retransmitted until the transmitter knows with absolute certainty that all receivers have correctly received it. k-Reliable Multicast defines that a successful transmission is achieved if at least a number of k (k<group size) receivers have correctly received the TSDUs.We propose another reliable semantic stronger than best-effort multicast but weaker than all-reliable multicast called statistical-reliable in which the reliability is enforced when desired by applications. The point at which the reliability becomes unacceptable would be application dependent. The Statistical-reliable Multicast does not enforce absolute reliability and the multicast sender does eliminate the need for maintaining state of individual multicast receivers. Using this semantic, the multicast transmission is considered successful if none, some or all TS users receive the multicast data. As the transmitter is relieved of any concern with the states of receivers, there is no way to know whether or not all receivers have successfully received the multicast TPDU s. However, if a more stringent requirements on the reliability is needed, it can be implemented on top of this statistical-reliable multicast transport protocol, i.e. protocol that deals with reliability in an application dependentmanner. Note also that this concept can be efficiently used in other environments with different requirements and objectives (for instance multipoint ABR).2.3 Model of the Transport Layer MulticastTransport layer multicast is defined as the transfer of a transport service data unit (TSDU) which is received from the sending transport service user (TS-user) to a set of receiving TS-users. The data transfer is simplex and begins after the establishment of the transport layer multicast connection. The sender's transport layer entity prepares only a single copy of the transport protocol data unit (TPDU) that is designated as a multicast TPDU. This TPDU is then transferred to the sender network/link layer entity which is responsible for sending the incoming TPDU to the receivers of the group.Associated with a multicast association, the S-TSAP identifier is utilized to identify the sending TS-user and the G-TSAP is used to identify a set of destination TSAP s. The pair of S-TSAP/G-TSAP is mapped into a list of addresses at the network/link layer. We note that this mapping procedure is not however part of the transport layer functionality. According to this addressing scheme, a multicast connection is set up and maintained between a sender and a group of receivers such that the transfer of any data-bearing or status-request TPDU is multicast from the sender to the group. On the other hand, the transfer of any response TPDU is unicast back to the sender along an established connection between the individual receiver and the sender. The receivers should only generate response TPDU s when either:-specifically requested by the sender transport entity via status-request or data-bearing TPDU, or-explicitly announcing the request for retransmission.Clearly, the response TPDU contains only the announcement of the correctly received TPDU or the lost TPDU, and should not in any case contains the data-bearing TPDU.Figure 1 illustrates the model of the multicast transport layer connection described above. For the purpose of this paper, we assume that there is no transport connections established between any two receivers. It is worth noting that any design of a transport layer multicast should take as much advantage as possible of the facilities provided by the underlying network. The distribution of multicast services over point-to-point networks can be potentially costly if the participants must establish connections to any other participants, thus there is no coordination amongst receivers.Sender Receiver 1Receiver N3. STATISTICAL RELIABLE MULTICAST3.1 Motivation for a statistical-reliable serviceApplications have different reliability requirements that varies from all-reliable to best-effort type. On the other hand, they also exhibit other constraints or needs such as group communication in cooperative work. In multicast communication, reliability has a cost that depends heavily on the group size and dynamic. It is quite straightforward to design an efficient all-reliable multicast protocol as long as the group size remains manageable; otherwise, the overhead will increase dramatically as a function of the group size. The main reason is the need to monitor each single receiver to collect the state information of the multicast association. The purpose of the statistical-reliable semantic is to provide a continuous reliability service and to scale with group size (Figure 2). The statistical-reliable multicast does not enforce absolute reliability and the multicast sender does eliminate the need for maintaining state of individual multicast receivers. Using this semantic, the multicast transmission is considered successful if none, some or all TS users receive the multicast data. An important issue of such a service is to be able to assess the quality-of-service that it provides depending on the networking environment and protocol parameters. The idea for supporting this solution is not to provide to the service user a reliability of say x%, but to provide him with the highest reliability available. Performance studies of the designed algorithm [Fdi93], [Bra95], show that the quality-of-service provided by the protocol is either very good, or so poor that it can not work (due to buffer overflow). Statistical-reliable protocol appears in fact to be either unreliable (this should not appear!) or all-reliable with the benefit of a much lower cost and overhead than an all-reliable protocol. This behavior is due to the fact that there exists some communicationsituations where the application requirements (in throughput for instance)can not be sustained with the amount of available resources (mainly buffer and processing resources). A careful design and selection of protocol mechanisms will contribute to alleviate the communication overhead and increase the reliability level. Also, for some multimedia type of traffic, reliability is not required and the protocol can provide a best-effort service while disabling the heuristic.ReliabilityFigure 2: Reliability Semantic for MulticastingAs a conclusion of this section, we claim that a well-designed multicast protocol with the statistical-reliable semantic can be efficiently used for multimedia cooperative applications and scale properly with group size. For this purpose, we design new mechanisms for error control in the next section.3.2. Error Control in Statistical Reliable MulticastIn an earlier paper [San92], the authors presented the problem of design of error control protocol for X T P -based reliable multicast communication. This paper describes a more efficient multicast transport protocol designed for tackling issues such as reliability, scalability and AGI management. Other consideration in this study were to operate the protocol over non natural broadcast networks.The basic control framework of the protocol is akin the bucket heuristic proposed in XTP3.6. The main features of the bucket protocol are summarized below [PEI92], [San92].Figure 3 shows that a sender multicasts the data-bearing and control packets (in XTP parlance, DATA or CNTL packets) to a set of M receivers using a single group address . XTP assumes that the multicast sender has neither knowledge of all the receivers nor the individual addresses of all receivers.RECEIVERSMNetworkFigure 3: Multicast Operation in XTPThe XTP 's multicast error control is based upon the concept that the sender periodically multicasts a CNTL [sync=k ] packet to the receiver set to which each receiver immediately responds by multicasting a CNTL [echo=k ] packet to all member of the group. Each receiver must copy the sync value from incoming CNTL [sync=k ] packet into the echo field of outgoing CNTL [echo=k ] packet returned to the sender. Sync-echo pair is used to correlate a request CNTL [sync=k ] and its associated response CNTL [echo=k ], this procedure is known as synchronizing handshake . Of course, in order to uniquely identify the buckets, the sync value must be incremented by one for each (re)transmission of DATA or CNTL [sync ] packet. This will keep sender and receivers synchronized with respect to state information. The CNTL [sync ] is used to solicit the status of the receivers and CNTL [echo ] is used to transfer "status information"about the receiver. Each "status information" may contain reception status, flow control, rate control, and round-trip time estimate , etc . Here,we focus only on the reception status which is represented by two variables rseq (received sequence number) and dseq (delivered sequence number). The dseq and rseq represent two kinds of acknowledgement in XTP3.6. The dseq value is used by the receiver to indicate one larger than the sequence number of the received DATA packet last delivered to the XTP user. The dseq value is the only information required to release the sender's input buffers. The rseq contains a value one larger than the largest monotonic sequence number of the received D A T A packet received without error. The rseq provides the retransmission information to the sender which is necessary to trigger retransmission, starting with the byte identified by rseq . Note that dseq is not a mandatory parameter and has been removed in XTP4.0.Since the sender is not aware of the individual addresses of thereceiver set, it can not know from which receivers a burst of CNTL[echo] packet is received. A mechanism is required to efficiently interpret thisburst of CNTL[echo] packets and to determine the time period that thesender should wait for collecting CNTL[echo] packets before updating itsstate. To accomplish these objectives, XTP specifies a heuristic known as the Bucket Algorithm kept at the sender. The buckets can effectively accumulate the CNTL[echo] packets coming from multiple receivers and then forward the summary of CNTL[echo] packets to the sender's state machine. In other word, a multicast sender that executes a bucket algorithm considers all the receivers as a single entity thus many receiver's retransmission requests are transformed into a single retransmission.We give in this section a specification of XTP's bucket error control mechanism. Once a multicast transfer is initiated, a sender is imposed to maintain a bucket list consisting of a series of buckets which correspond to a finite time period T p(T p might be assigned with the worst case estimate of network-roundtrip-time or greater as suggested in [9]). A bucket may correspond to a time window T w where its length will determine the interval between the generation of two consecutive CNTL[sync] packets initiated by the sender. The bucket k is created when the sender submits a CNTL[sync=k] packet. The bucket k will be used to store all response CNTL[echo=k] packets associated with CNTL[sync=k]. For a given sender, the total number of buckets n should be (T p/T w) buckets. It is clear that T p and T w are two design parameters to be tuned. At the moment when a new bucket is created and if all the bucket list is full, the oldest bucket (i.e. the one labeled with the lowest value of sync) must be released in order to create a new one. Note that at this point in time, the sender's state should also be updated by applying the minimum values of dseq and rseq over all the buckets in the bucket list. Then the sender begins retransmitting with the byte identified by rseq and releases all input buffers containing data whose sequence numbers are less than the dseq value. The same action will take place each time the bucket is recycled.A performance analysis of the bucket algorithm was done in [Fdi93], [Bra95] and discusses the influence of the above parameters on the protocol efficiency and reliability.In the following, we extend the basic features of the error control protocol in the following directions: i) scalability issues, ii) protection against slow receivers and AGI management, iii) efficient processing of the bucket list. Other aspects such as filtering are also briefly addressed.e of NACK StrategyIn Negative A CK nowledgement (NACK) protocol, it is the receivers' responsibility to detect data packet losses and recover from them. This scheme is more appropriate for a high performance with low error rate broadband environment, therefore for multicast communications. The main reasons for this: (i) the NACK protocol detects faulty/lost packets and performs retransmission requests as quickly as possible therebykeeping the average packet delay low, (ii) the NACK strategy reduces the amount of control packet exchanged between systems, only data that is lost need to be acknowledged, and (iii) due to the fewer packet exchanges, the NACK based approach should result in lower processing overhead. There are, however, some inherent drawbacks of this scheme: (i) lack of efficient buffer management. The sender cannot release the packets from its buffers even if they have been received correctly by all receivers, (ii) it cannot detect receivers' failures, (iii) the receivers may have to wait for an unbounded time to detect the loss of the last data packet(s), and (iv) it works well only if the environment does not reorder packets. The first three issues can be overcome by introducing the sender based acknowledgement strategy discussed in the next subsection. The last issue will not appear in an ATM-based environment [Onv94] that is our target underlying network.At any receivers, a gap in sequence number implies a missing packet. Then, the corrupted receivers should immediately generate the NACK messages. The NACK messages need not be repeatedly transmitted by these corrupted receivers. If the NACK messages are lost, this will not violate the protocol. The succeeding sender based acknowledgement messages (described in the next subsection) will eventually update the record correctly. Note that in this study the number of receivers simultaneously missing their data is assumed to be very rare, thus the arrival of the back-to-back NACK messages at the source would be negligible. If this assumption is not verified, then the application requirements can not be met according to the network resources availability.It is worth to mention that the utilization of Forward-Error-Correction (FEC) techniques is very attractive in high-bandwidth networking environment because it avoids retransmissions while increasing bandwidth requirements. However, the main cause for errors is buffer overflow that might render FEC inefficient, especially if successive packets from the same connection get lost.2.Sender based Acknowledgement PolicyIn conjunction with the N A C K scheme, the sender based acknowledgement strategy may be used to efficiently signal the sender to release the buffers and to probe the status of the group when the protocol operates under normal conditions. The sender periodically issues status-request packets to the receiver group to solicit receivers' state information. Upon receipt of the status-request packets, the receivers generate the acknowledgement reply-messages returned to the original sender. The multicast sender uses these reply-messages to release its buffers.Generally speaking, multicast by its very nature is self synchronizing. This means that all multicast receivers get the status-request packets at roughly the same time, and thus respond at almost the same time. This can lead to congestion at the multicast source (implosion problem), with many of the replies being lost. It is very important to note that the replies that are dropped may be from the receivers who are missing the data. In this case the multicast sender will not be aware, andtherefore source congestion can make the statistical reliable multicast unreliable. To avoid this, a multicast transport protocol should have some sort of mechanism for minimizing the number of receiver responses and distributing such responses in time to cope with scalability issues. Damping and slotting where proposed in XTP but are not adapted to non-broadcast networks. One method for reducing the reply messages requires that the recipients only respond intermittently if they do not detect any packet loss. The common method for increasing the minimum spacing between replies is simply to have each response be returned at some random time by recipients using an exponential back-off algorithm. Hence, a receiver will only reply to a control packet every n requests, n following the exponential back-off value, which is bounded by a maximum value and reset on an error condition (NACK transmission).It is expected that the intermittent response and back-off schemes would effectively eliminate the source congestion and the peak processing demand at the multicast sender.3.Protection against slow receiversIn unicast, the association is useless if the packets cannot be delivered to the receiver, thus sender buffers should not be released until the receiver acknowledges the packets. However in multicast, the slowly responding receivers that miss data may not keep requesting retransmissions according to the AGI. If some protection is not built into the protocol, this can degrade the performance of all other recipients. Thus after a certain number of retries that allows the slow receivers to ensure reliable delivery, the sender buffers should be released. This scenario of a slow receiver within a group association is the one that is most likely to occur due to different receiver capabilities and resources. In this situation, the decision to drop the misbehaving user depends on the AGI that can lead either to disconnect this receiver or to release or suspend the association if this receiver is a key element of the application.In dealing with the problem of slow receiver(s), a method should be provided to inform receivers that the missing data is no longer available and thus can not be recovered. The slow receiver(s) may then leave the multicast association when it get too far behind. The proposed method consist in monitoring the connection throughput at the sender site. If the throughput gets under some QoS thresholds, a specific control packet (Monitoring packet) with the minimum accepted rseq value is sent to the multicast group. Each receiver reacts to the Monitoring packet according to their status as defined in the AGI condition. If a receiver can not sustain the minimum rate then it will disconnect itself from the connection if it is compliant with the AGI condition, otherwise, if the minimum rate can not be achieved then a disconnection request will be issued by the sender because the QoS requirements can not be guaranteed. Other scenarios might be envisaged to manage the AGI.4.Bucket AlgorithmThe provision of a statistical reliable multicast facility involves the following functionalities at the sender: (i) to collect the incoming。