Chapter22-digital vieo processing techniques and applications
- 格式:pdf
- 大小:6.63 MB
- 文档页数:29

AIOT-AIVD AI IoT Video Analysis GatewayUser’s Manual 1st EdCopyright NoticeThis document is copyrighted, 2019. All rights are reserved. The original manufacturer reserves the right to make improvements to the products described in this manual at any time without notice.No part of this manual may be reproduced, copied, translated, or transmitted in any form or by any means without the prior written permission of the original manufacturer. Information provided in this manual is intended to be accurate and reliable. However, the original manufacturer assumes no responsibility for its use, or for any infringements upon the rights of third parties that may result from its use.The material in this document is for product information only and is subject to change without notice. While reasonable efforts have been made in the preparation of this document to assure its accuracy, AAEON assumes no liabilities resulting from errors or omissions in this document, or from the use of the information contained herein. AAEON reserves the right to make changes in the product design without notice to its users.AcknowledgementAll other product s’ name or trademarks are properties of their respective owners.●Microsoft Windows is a registered trademark of Microsoft Corp.●Intel, Pentium, Celeron, and Xeon are registered trademarks of Intel Corporation ●Core, Atom are trademarks of Intel Corporation●ITE is a trademark of Integrated Technology Express, Inc.●IBM, PC/AT, PS/2, and VGA are trademarks of International Business MachinesCorporation.All other product names or trademarks are properties of their respective owners.Packing ListBefore setting up your product, please make sure the following items have been shipped:AIOT-AIVD 1If any of these items are missing or damaged, please contact your distributor or sales representative immediately.About this DocumentThis User’s Manual contains all the essential information, such as detailed descriptions and explanations on the product’s hardware and software features (if any), its specifications, dimensions, jumper/connector settings/definitions, and driver installation instructions (if any), to facilitate users in setting up their product.Users may refer to the product page on for the latest version of this document.Safety PrecautionsPlease read the following safety instructions carefully. It is advised that you keep this manual for future references1.All cautions and warnings on the device should be noted.2.Make sure the power source matches the power rating of the device.3.Position the power cord so that people cannot step on it. Do not place anythingover the power cord.4.Always completely disconnect the power before working on the system’shardware.5.No connections should be made when the system is powered as a sudden rushof power may damage sensitive electronic components.6.If the device is not to be used for a long time, disconnect it from the powersupply to avoid damage by transient over-voltage.7.Always disconnect this device from any AC supply before cleaning.8.While cleaning, use a damp cloth instead of liquid or spray detergents.9.Make sure the device is installed near a power outlet and is easily accessible.10.Keep this device away from humidity.11.Place the device on a solid surface during installation to prevent falls12.Do not cover the openings on the device to ensure optimal heat dissipation.13.Watch out for high temperatures when the system is running.14.Do not touch the heat sink or heat spreader when the system is running15.Never pour any liquid into the openings. This could cause fire or electric shock.16.As most electronic components are sensitive to static electrical charge, be sure toground yourself to prevent static charge when installing the internal components.Use a grounding wrist strap and contain all electronic components in anystatic-shielded containers.17.If any of the following situations arises, please the contact our service personnel:i.Damaged power cord or plugii.Liquid intrusion to the deviceiii.Exposure to moistureiv.Device is not working as expected or in a manner as described in this manualv.The device is dropped or damagedvi.Any obvious signs of damage displayed on the device18.DO NOT LEAVE THIS DEVICE IN AN UNCONTROLLED ENVIRONMENT WITHTEMPERATURES BEYOND THE DEVICE’S PERMITTED STORAGE TEMPERATURES (SEE CHAPTER 1) TO PREVENT DAMAGE.FCC Statementsubject to the following two conditions: (1) this device may notcause harmful interference, and (2) this device must accept anyinterference received including interference that may causeundesired operation.Caution:There is a danger of explosion if the battery is incorrectly replaced. Replace only with the same or equivalent type recommended by the manufacturer. Dispose of used batteries according to the manufacturer’s instructions and your local government’s recycling or disposal directives.Attention:Il y a un risque d’explosion si la batterie est remplacée de façon incorrecte.Ne la remplacer qu’avec le même modèle ou équivalent recommandé par le constructeur. Recycler les batteries usées en accord avec les instructions du fabricant et les directivesgouvernementales de recyclage.产品中有毒有害物质或元素名称及含量AAEON System QO4-381 Rev.A0Hazardous and T oxic Materials ListAAEON System QO4-381 Rev.A0T able of ContentsChapter 1 -Specifications (1)1.1Specifications (2)Chapter 2 – Hardware Information (5)2.1Dimensions (6)2.2I/O Location (7)2.3Jumpers and Connectors (8)2.4List of Switches and Connectors (10)2.4.1Power Button (UP-APL SW1) (11)2.4.2Switch (MINI-MYX SW1) (12)2.4.3RTC Battery Wafer (CN1) (12)2.4.4M.2 Key-E 2230 Connector (CN7) (13)2.4.5Mini Card Connector (CN8) (15)2.4.6SATA Connector (CN9) (16)2.4.7SATA Power Connector (CN10) (17)2.4.8Dual USB 3.0 Type-A Connector (CN14) (17)2.4.9USB 3.0 Type-A Connector (CN15) (18)2.4.10FAN Power Connector (CN17) (18)2.4.11Dual RJ45 LAN Connector (CN18) (19)2.4.12DC Jack (CN23) (20)2.4.13HDMI/DP Connector (CN24) (20)Chapter 3 - AMI BIOS Setup (22)3.1System T est and Initialization (23)3.2AMI BIOS Setup (24)3.3Setup submenu: Main (25)3.4Setup submenu: Advanced (26)3.4.1Advanced: ACPI Settings (27)3.4.2Advanced: SMART Settings (28)3.4.3Advanced: CPU Configuration (29)3.4.3.1CPU Power Management (30)3.4.4Advanced: Network Stack Configuration (31)3.4.5Advanced: USB Configuration (32)3.4.6Advanced: Hardware Monitor (33)3.4.7Advanced: Serial Port Console Redirection (34)3.4.8Advanced: T rusted Computing (35)3.4.9Advanced: Power Management (37)3.5Setup submenu: Chipset (38)3.5.1Chipset: North Bridge (39)3.5.2Chipset: South Bridge (42)3.5.2.1HD-Audio Configuration (43)3.5.2.2SATA Configuration (44)3.5.2.3SCC Configuration (46)3.6Setup submenu: Security (47)3.6.1Secure Boot (48)3.6.1.1Key Management (49)3.7Setup submenu: Boot (53)3.8Setup submenu: Save & Exit (54)Chapter 4 – Software and System Startup (55)4.1Drivers Download and Installation (56)4.2Quick Startup Guide (58)AI IoT Video Analysis GatewayAIOT-AIVD Chapter 1Specifications1.1 SpecificationsCPU Intel® Pentium N4200 Processor Chipset Intel® System on ChipMemory Onboard 8GB LPDDR4 memory Storage 64GB eMMC on board500GB HDD x 1 (Optional) Display HDMI x 1DP x 1Ethernet Realtek 8111G x 2USB USB 3.0 x 3COM —Digital I/O —Expansion Slot AI core X mini card module x 1M.2 2230 E-Key x 1Indicator —Wi-Fi 801.11ac (Optional)Bluetooth BT4.0 (Optional)LoRa —POE —OS Support Microsoft Windows 10, Linux Ubuntu,OpenVinoFront I/O RJ45 Connector x 2Power button x 1HDMI x 1DP x 1USB3.0 x 2Power input x 1Power button x 1Rear I/O USB 3.0 x 1Antenna connector x 1 (Optional) Right Side I/O Antenna connector x 1 (Optional) Left Side I/O Antenna connector x 1 (Optional)Power Requirement 5V DC InIP —Dimension 126 mm x 95 mm x 58 mm Mounting VESA MountGross Weight 2.4 lbs. (1.1 kg)Net Weight 1.5 lbs. (700 g)Operating T emperature 0°C ~ 60°CStorage T emperature -4°F ~ 158°F (-20°C ~ 70°C) Storage Humidity 5~95% @ 40°C, non-condensingAnti-Vibration 3 Grms/ 5 ~ 500Hz/ operation – eMMC1 Grms/ 5~ 500Hz/ operation – HDD Certification CE, FCC Class AAI IoT Video Analysis GatewayAIOT-AIVD Chapter 2 Hardware Information2.1 Dimensions2.2 I/O Location AI IoT Video Analysis Gateway AIOT-AIVD2.3 Jumpers and ConnectorsUP-APL Board T op Side AIOT-AIVDUP-APL Board Bottom SideMINI-MYX Connector T op Side AI IoT Video Analysis GatewayAIOT-AIVDAI IoT Video Analysis GatewayPosition FunctionAIOT-AIVD2.4.2Switch (MINI-MYX SW1)SW ValueBoard Value3 2 1Off Off Off 0Off Off On 1Off On Off 2Off On On 3On Off Off 4On Off On 5On On Off 6On On On 72.4.3 RTC Battery Wafer (CN1)Pin Signal1 +V_COIN_BAT2 GNDAI IoT Video Analysis GatewayAIOT-AIVD2.4.4M.2 Key-E 2230 Connector (CN7)1 GND2 3.3V 3USB_D+ 4 3.3V 5 USB_D- 6 NC 7 GND 8 NC 9 NC 10 NC 11 NC 12 NC 13 NC 14 NC 15 NC 16 NC 17 NC 18 GND 19 NC 20 NC 21 NC 22 UART0RXD 23 NC 24 N/A(Key-E) 25 N/A(Key-E) 26 N/A(Key-E) 27 N/A(Key-E) 28 N/A(Key-E) 29 N/A(Key-E) 30 N/A(Key-E) 31 N/A(Key-E) 32 UART0_TXD 33 GND 34 UART0_CTS 35PCIE_C_TXP336UART0_RTS37 PCIE_C_TXN3 38 NC39 GND 40 NC41 PCIE_RXP3 42 NC43 PCIE_RXN3 44 NC45 GND 46 NC47 CLK_PCIE_M2_P 48 NC49 CLK_PCIE_M2_N 50 Suspend Clock 51 GND 52 Reset#53 PCIE_M2_CLKREQ 54 Bluetooth Enable 55 Wake# 56 Wi-Fi Enable57 GND 58 SMBus_DAT59 NC 60 SMBus_CLK61 NC 62 SMBus_Alert63 GND 64 NC65 NC 66 NC67 NC 68 NC69 GND 70 NC71 NC 72 3.3V73 NC 74 3.3V75 GNDAIOT-AIVD 2.4.5 Mini Card Connector (CN8)Pin Signal Pin Signal1 Wake#2 3.3V3 NC4 GND5 INT_SERIRQ6 1.5V7 PCIE_MINI_CLKREQ 8 NC9 GND 10 NC11 CLK_PCIE_MINI_N 12 NC13 CLK_PCIE_MINI_P 14 NC15 GND 16 NC17 NC 18 GND19 NC 20 3G Enable21 GND 22 Reset#23 PERn0_mSATA_R+ 24 3.3V25 PERp0_mSATA_R- 26 GND27 GND 28 1.5V29 GND 30 NC31 PET n0_mSATA_T- 32 NC33 PET p0_mSATA_T+ 34 GND35 GND 36 USB_D-37 GND 38 USB_D+AIOT-AIVD39 3.3V 40 GND41 3.3V 42 NC43 mSATA_PCIe_SEL_C 44 NC45 NC 46 NC47 NC 48 1.5V49 NC 50 GND51 NC 52 3.3V 2.4.6 SATA Connector (CN9)Pin Signal Pin Signal1 GND 5 RX-2 TX+ 6 RX+3 TX- 7 GND4 GNDAIOT-AIVD 2.4.7 SATA Power Connector (CN10)Pin Signal1 5V2 GND2.4.8 Dual USB3.0 Type-A Connector (CN14)Pin Signal Pin Signal1 5V2 USB2_D1-3 USB2_D1+4 GND5 USB3_RX1-6 USB3_RX1+7 GND8 USB3_TX1-9 USB3_TX1+ 10 5V11 USB2_D2- 12 USB2_D2+ 13 GND 14 USB3_RX2- 15 USB3_RX2+ 16 GND17 USB3_TX2- 18 USB3_TX2+AIOT-AIVD 2.4.9 USB 3.0 Type-A Connector (CN15)Pin Signal Pin Signal1 5V2 USB2_D-3 USB2_D+4 GND5 USB3_RX-6 USB3_RX+7 GND 8 USB3_TX-9 USB3_TX+2.4.10FAN Power Connector (CN17)Pin Signal1 5V2 GNDAIOT-AIVD 2.4.11Dual RJ45 LAN Connector (CN18)Pin Signal Pin SignalR1A LAN1_MDI0+ R2A LAN1_MDI0-R3A LAN1_MDI1+ R4A LAN1_MDI1-R5A LAN1_MDI2+ R6A LAN1_MDI2-R7A LAN1_MDI3+ R8A LAN1_MDI3-R9A NC R10A GNDL1A LAN1_ACTL L2A LAN1_ACTLED+L3A LAN1_LINK1000# L4A LAN1_Link100#R1B LAN2_MDI0+ R2B LAN2_MDI0-R3B LAN2_MDI1+ R4B LAN2_MDI1-R5B LAN2_MDI2+ R6B LAN2_MDI2-R7B LAN2_MDI3+ R8B LAN2_MDI3-R9B NC R10B GNDL1B LAN2_ACTL L2B LAN2_ACTLED+L3B LAN2_LINK1000# L4B LAN2_Link100#AIOT-AIVD 2.4.12DC Jack (CN23)1 +5V2 GND3 GND2.4.13HDMI/DP Connector (CN24)Pin Signal Pin SignalP1 DDI0_TXP_DP_0 P2 GNDP3 DDI0_TXN_DP_0 P4 DDI0_TXP_DP_1 P5 GND P6 DDI0_TXN_DP_1 P7 DDI0_TXP_DP_2 P8 GNDP9 DDI0_TXN_DP_2 P10 Port0_CLK+P11 GND P12 Port0_CLK-Chapter 3 AMI BIOS Setup3.1 System T est and InitializationThe system uses certain routines to perform testing and initialization during the boot up sequence. If an error, fatal or non-fatal, is encountered, the system will output a few short beeps or an error message. The board can usually continue the boot up sequence with non-fatal errors.The system configuration verification routines check the current system configuration against the values stored in the CMOS memory. If they do not match, an error message will be output, and the BIOS setup program will need to be run to set the configuration information in memory.There are three situations in which the CMOS settings will need to be set or changed: - Starting the system for the first time- The system hardware has been changed- The CMOS memory has lost power and the configuration information is erasedThe system’s CMOS memory uses a backup battery for data retention. The battery must be replaced when it runs down.3.2 AMI BIOS SetupThe AMI BIOS ROM has a pre-installed Setup program that allows users to modify basic system configurations, which is stored in the battery-backed CMOS RAM and BIOS NVRAM so that the information is retained when the power is turned off.T o enter BIOS Setup, press <Del> or <ESC> immediately while your computer is powering up.The function for each interface can be found below.Main – Date and time can be set here. Press <T ab> to switch between date elementsAdvanced– Enable/ Disable boot option for legacy network devicesChipset– For hosting bridge parametersSecurity– The setup administrator password can be set hereBoot– Enable/ Disable quiet Boot OptionSave & Exit –Save your changes and exit the program3.3 Setup submenu: MainPress Delete to enter Setup AIOT-AIVD3.4 Setup submenu: Advanced AIOT-AIVDAI IoT Video Analysis Gateway AIOT-AIVD 3.4.1 Advanced: ACPI Settings3.4.2 Advanced: SMART Settings AIOT-AIVD3.4.3 Advanced: CPU Configuration AIOT-AIVD3.4.3.1 CPU Power Management AIOT-AIVD3.4.4 Advanced: Network Stack Configuration AIOT-AIVD3.4.5 Advanced: USB Configuration AIOT-AIVD3.4.6 Advanced: Hardware Monitor AIOT-AIVD3.4.7 Advanced: Serial Port Console Redirection AIOT-AIVD3.4.8 Advanced: T rusted Computing AIOT-AIVD3.4.9 Advanced: Power Management AIOT-AIVD3.5 Setup submenu: Chipset AIOT-AIVD。

英语单词mbs是什么中文意思英语单词mbs是什么中文意思由于mb这个单词在日常中并不常用,因此不少人都不理解它的中文意思。
以下是店铺为大家整理的英语单词mbs表达的中文意思的知识,一起来看看吧!英语单词mbs表达的中文意思Mutual Broadcasting System <美>相互广播公司;main bang suppressor 主冲击信号抑制器;megabits per second 每秒百万兆;网络解释1. 甲基丙烯酸甲酯-丁二烯-苯乙烯共聚物:试生产和批量生产表明,该材料具有良好的成型性,用此壳体装成电池,电池放电性能、密封性能、耐环境条件等均能符合相关标准,与原来的蓝色(甲基丙烯酸甲酯/丁二烯/苯乙烯)共聚物(MBS)壳体相比,具有尺寸稳定性高、表面光泽度好、透明度高、密度小、成本低等优点,2. 甲基丙烯酸丁二烯苯乙烯共聚物:丙烯腈-苯乙烯树脂(AS) 甲基丙烯酸-丁二烯-苯乙烯共聚物(MBS)丙烯腈-苯乙烯树脂(AS) 甲基丙烯酸-丁二烯-苯乙烯共聚物(MBS)丙烯腈-苯乙烯树脂(AS) 甲基丙烯酸-丁二烯-苯乙烯共聚物(MBS)3. 光幕触板:货梯从运货人员的安全和货物免受损伤的角度出发,象客梯一样把安全触板(SDE)或光幕安全触板(MBS)(二者选一)作为货梯必配的安全功能,这样既可保证运货人的安全,也可保证进出货梯的货物免受损伤.4. mbs:the mortgage-backed securities; 住房抵押贷款证券化5. mbs:models base system; 模型库系统6. mbs:multi-body systems dynamics; 多体系统动力学7. mbs:mortogage backed security; 住房抵押贷款证券英语单词mbs的单语例句1. All those enrolled at the Shanghai MBS center work as company consultants, and have the opportunity to collaboratewith Chinese business partners.2. The federal discount facility will enable banks to turn their quality ABCP into liquidity, while distressed MBS can be sold to the government.3. MBS Mt Eliza's open programs are rated by FT in the top 15 in the world for repeat business and growth.4. The MBS China center also offers a global careers service for its students.5. The ranking positions MBS Mt Eliza as the only Asia Pacific headquartered school in the global top 40 providers of executive education.6. Leaders in executive education from around the world joined with MBS Mt Eliza in April to discuss the future of executive education.7. The merged School maintains the name of Melbourne Business School across all programs and the MBS Mt Eliza name for executive education programs.英语单词mbs的'双语例句1. Then, the author analyses the main categories and the cash flows of the mortgage backed security. Two main factors, i.e. the term structure of interest rate model and the prepayment model, which influence the pricing models of the MBS are also researched.接着,本文对住房抵押贷款证券化的主要类型及其现金流问题进行了分析,并对影响住房抵押贷款证券化定价模型设定的两个主要因素,即利率期限结构模型和提前清偿预测模型进行了重点探讨。

售后服务监理服务内容及要求售后服务:监理服务内容及要求本文介绍了售后服务中的监理服务内容及要求,其中包括监理总体原则、监理范围、监理工期、监理团队要求以及监理工作的主要职责等方面。
监理总体原则是对监控系统实施监理,全程跟踪监理建设工程各子项目的工程采购、建设和施工的规范化,硬件的设备采购、验货等过程。
监理范围包括市委办公楼、市委大院、市委监控中心、市委壹宿舍、市委二宿舍、市委三宿舍监控系统的建设。
监理工期为25日,监理团队必须有常驻现场,且人员配备合理。
监理工作的主要职责包括工程质量控制、工程进度控制、投资控制、工程合同管理、信息、工程文档管理以及人员培训的质量控制等方面。
其中,工程质量控制方面,监理团队需协助审查且确认建设工程施工、设备供应承包商的合同和实施方案。
对采购的硬件设备和施工材料的合格证、质检方案和准用证进行审查,对采购的硬件设备的综合质量进行检验、测试和验收。
对施工项目施工质量进行把关。
工程进度控制方面,监理团队需审核工程的进度分解计划,确认分解计划能够保证总体计划目标的实现。
对项目工程实施进度进行实时跟踪,且要求各项目承建方对进度计划进行动态调整,以确保项目工程的阶段和总体进度目标的实现。
当工程目标出现偏离时,及时指出,且提出对策和建议,同时督促项目承建方尽快采取措施。
投资控制方面,监理团队需通过对工程实施中的方案及设计优化,对工程建设不可预见费的开支使用情况进行技术性审核且提出意见,确保投资控制于预算之内。
协助项目建设单位作好项目支付预算的现金流量表,将支付合同款项进度和工程质量进度相结合,促使履行合同。
工程合同管理方面,监理团队需跟踪检查合同的执行情况,确保项目承建方按时履约。
对合同的工期的延误和延期进行审核确认。
对合同变更、索赔等事宜进行审核确认。
根据合同约定,审核项目承建方的支付申请,签发付款凭证。
信息、工程文档管理方面,监理团队需于项目工程实施过程中作好工程监理日记及工程大事记。
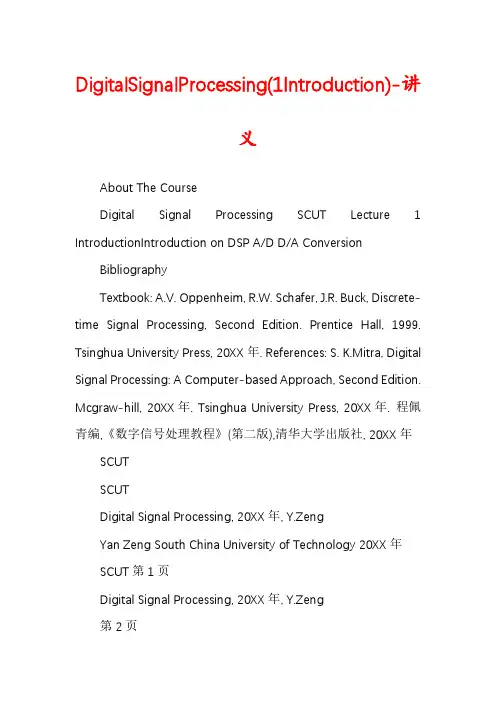
DigitalSignalProcessing(1Introduction)-讲义About The CourseDigital Signal Processing SCUT Lecture 1 IntroductionIntroduction on DSP A/D D/A Conversion BibliographyTextbook: A.V. Oppenheim, R.W. Schafer, J.R. Buck, Discrete-time Signal Processing, Second Edition. Prentice Hall, 1999. Tsinghua University Press, 20XX年. References: S. K.Mitra, Digital Signal Processing: A Computer-based Approach, Second Edition. Mcgraw-hill, 20XX年. Tsinghua University Press, 20XX年. 程佩青编,《数字信号处理教程》(第二版),清华大学出版社, 20XX年SCUTSCUTDigital Signal Processing, 20XX年, Y.ZengYan Zeng South China University of Technology 20XX年SCUT第1页Digital Signal Processing, 20XX年, Y.Zeng第2页About The Course Instructor: Yan Zeng,C Phone: 8711 4480 (H), 189 **** ****C Office: Building#18 (412)C E-Mail: yzeng@, zengyan.gz@C E-Mail for submitting reports: scutoptics@ Grading PolicyCExercises and Reports: 20%CFinal exam: 80% Exercises and Reports: There are proper exercises, homeworks or reports every week, which must be delivered on every Wednesday.Digital Signal Processing, 20XX年, Y.Zeng第3页About The CourseSCUT眼界决定境界,视野决定胸怀,行动决定命运!广泛阅读,善于思考,勤于实践!仰望星空,脚踏实地!SCUTI will give you many careful and trenchant discussion on DSP theories, methods and a wild view to modern science and technoloty. Wish you have a great journey in the course!SCUTSCUTDigital Signal Processing, 20XX年, Y.Zeng第4页Chapter 1 Introduction Background Aim Motivation What is DSP Characteristics of DSP Basic Framework Main Application and Some Examples Sampling and Quantization( A/D D/A Conversion)1.1 BackgroundSCUT建安24年(公元219年)腊月,曹操与华佗。

Digital Signal Processing Digital Signal Processing (DSP) is a vital field that has revolutionized various aspects of our lives. From audio and video processing to telecommunications and medical imaging, DSP plays a crucial role in enhancing the quality of signals and extracting useful information from them. In this response, I will discuss the significance of DSP from multiple perspectives, highlightingits impact on different industries and the emotional elements associated with its advancements. From a technological perspective, DSP has opened up a world of possibilities. With the advent of high-speed processors and advanced algorithms, DSP techniques have become more powerful and versatile. This has enabled the development of sophisticated audio and video processing systems that can remove noise, enhance clarity, and even manipulate signals to create special effects. For example, in the entertainment industry, DSP is used to improve the audio quality of music recordings, making them more enjoyable for listeners. It also plays a crucial role in video editing, allowing professionals to enhance visual effects and create stunning visuals. In the field of telecommunications, DSP has revolutionized the way we communicate. From mobile phones to satellite communication systems, DSP algorithms are used to encode, transmit, and decode signals, ensuring reliable and high-quality communication. This has led to improved voice and video call quality, faster data transfer rates, and increased capacity in wireless networks. The emotional impact of these advancements is evident in our daily lives. We can now connect with our loved ones, no matter where they are in the world, with crystal-clear audio and video, bridging the distance and bringing us closer together. Another area where DSP has made significant contributions is medical imaging. Techniques like computed tomography (CT), magnetic resonance imaging (MRI), and ultrasound heavily rely on DSP algorithms to process and reconstruct images from raw data. This hasrevolutionized the diagnosis and treatment of various medical conditions, enabling doctors to visualize internal structures with unprecedented detail. The emotional impact of this cannot be overstated. DSP has saved countless lives by enabling early detection of diseases, guiding surgical procedures, and monitoring treatment progress. In addition to these industries, DSP has also found applications infields like radar and sonar systems, seismology, speech recognition, and even financial analysis. In radar and sonar systems, DSP algorithms are used to process the received signals and extract useful information about the surrounding environment. In seismology, DSP helps in detecting and analyzing earthquakes, providing valuable insights into the Earth's structure and predicting potential hazards. Speech recognition systems, like those used in virtual assistants, rely on DSP techniques to accurately interpret and respond to human speech. Infinancial analysis, DSP algorithms are used to analyze market data and make predictions, aiding in decision-making and risk management. The advancements in DSP have undoubtedly improved our lives in numerous ways, but it is essential to consider the ethical implications as well. With the increasing use of DSP in surveillance systems, privacy concerns have become more prominent. The ability to process and analyze vast amounts of audio and video data raises questions about the balance between security and individual privacy. It is crucial to develop regulations and guidelines to ensure that DSP technologies are used responsibly and ethically. In conclusion, Digital Signal Processing has had a profound impact on various industries, enhancing the quality of signals and extracting valuable information. From technological advancements to emotional impacts, DSP has revolutionized fields like entertainment, telecommunications, medical imaging, and more. However, it is important to consider the ethical implications and ensurethat DSP technologies are used responsibly. As we continue to push the boundaries of DSP, we must strive to strike a balance between technological advancements and the well-being of individuals and society as a whole.。

PrefaceNoticeProduct features and specifications described in this manual are subject to change without notice.The manufacturer shall not be liable for any damage, or for the loss of information resulting from the performance or use of the information contained herein.TrademarksAccusys and the names of Accusys products and logos referenced herein are trademarks and/or service marks or registered trademarks and/or service marks of Accusys, Inc. Microsoft, Windows, Windows NT, Windows 2000, Windows 2003, Windows XP, Windows Vista and MS-DOS are either trademarks or registered trademarks of Microsoft Corporation. Intel and Pentium are registered trademarks of Intel Corporation. Mac, Mac OS, and Macintosh are either registered trademarks or trademarks of Apple. Other product and company names mentioned herein may be trademarks and/or service marks of their respective owners.All contents of this manual are copyrighted by Accusys, Inc.The information contained herein is the exclusive property of Accusys, Inc. and shall not be copied, transferred, photocopied, translated on paper, film, electronic media, or computer-readable form, or otherwise reproduced in any way, without the express written permission of Accusys Inc.Manual version 1.3© Copyright 2007 Accusys, Inc.All rights reserved.ACS-61000/61010 User’s ManualAbout this manualCongratulations on your selection of the ACS-61000/61010. The card is monitored by a Java-based RAID GUI.INTENDED USERThis manual is designed and written for users installing and using RAID GUI. The intended user should have working knowledge of RAID planning and data storage. ORGANIZATION OF THE MANUALPART ONE:IntroductionChapter 1: Introduction provides an overview of the card and its features.PART TWO:Installing the cardChapter 2: Setting up RAID GUI provides details of how to setting up your card and connecting to the RAID GUI.PART THREE: Card ConfigurationsChapter 3: Card Connections provides details of the connectors on the RAID card. PART FOUR:Card BIOS and EFIChapter 4: The Card BIOS and EFI allows the user to configure a RAID array without using the RAIDGuard X GUI.PART FIVE: AppendicesAppendix A: Specifications lists the technical details of the ACS-61000/61010 RAID card.Appendix B: Contact Us lists contact details of Accusys business units around theworld.Guide to conventionsImportant information that users should be aware of is indicated with the following icons:This icon indicates the existence of a potential hazard that could result inpersonal injury, damage to your equipment or loss of data if the safetyinstruction is not observed.This icon indicates useful tips on getting the most from your RAID card. Important terms, commands and programs are put in Boldface font.2Table of ContentsPREFACE (1)N OTICE (1)T RADEMARKS (1)A BOUT THIS MANUAL (2)INTENDED USER (2)ORGANIZATION OF THE MANUAL (2)G UIDE TO CONVENTIONS (2)TABLE OF CONTENTS (3)CHAPTER 1 - INTRODUCTION (6)O VERVIEW (6)K EY F EATURES (7)SERIAL ATA (Serial advanced technology attachment) (8)PCI-EXPRESS X 8 (8)FIRMWARE (8)BIOS and EFI (8)B EFORE YOU BEGIN (9)WHAT’S IN THE BOX (9)OPTIONAL ITEMS (10)WHAT ELSE YOU NEED (10)F AMILIARIZING YOURSELF WITH THE RAID CARD (11)OVERVIEW (11)PIN SETTINGS (12)Serial Cable Connectors (1) (12)LCD Panel Connector (2) (12)Battery Module Connector (3) (12)ACS-61000/61010 User’s Manual4 CHAPTER 2 - INSTALLATION (14)I NSTALLATION FLOWCHART (14)P RE -INSTALLATION NOTICES (15)C ARD I NSTALLATION (16)H ARD D RIVE C ONNECTION (16)LCD P ANEL (OPTIONAL ) I NSTALLATION (17)B ATTERY B ACKUP M ODULE (O PTIONAL ) I NSTALLATION (17)CHAPTER 3 - CARD CONNECTIONS (19)MINI SAS CONNECTORS (1) (20)PCI-EXPRESS X 8 CONNECTOR (2) (20)SERIAL CONNECTOR PORT (3) (20)LCD PANEL CONNECTOR (4) (20)BATTERY CONNECTOR PORT (5) (20)CHAPTER 4 - BIOS (22)QUICK ARRAY CONFIGURATION (23)CUSTOM ARRAY CONFIGURATION (24)BIOS Menu Structure (25)BIOS Menu (27)APPENDIX A - SPECIFICATIONS (29)APPENDIX B - CONTACT US (30)T AIWAN - A CCUSYS , I NC (30)A MERICA - A CCUSYS U.S.A., I NC (30)K OREA - A CCUSYS K OREA , I NC (30)C HINA B EIJING - A CCUSYS C HINA , I NC (30)E UROPE - A CCUSYS EU B.V (30)ACS-61000/61010 User’s ManualChapter 1This chapter introduces the features and capabilities ofACS-61000/61010. You will find:Ö A full introduction to your RAID cardÖ Details of key featuresÖ A checklist of package contentsÖ A checklist of what else you need to start installationÖ An overview of the RAID cardOverviewThe ACS 61000/61010 PCI Express to SATA II RAID adaptors provide the latest functionality and performance for Windows, Linux and MAC operating systems. And with a Java based GUI the RAIDGuard X server and client software offers improved functionality and manageability. Using the latest Intel XScale ® 64-bit RISC processor the eXpeRAID family of adaptors supports up to 16 x SATA I/II disk drives making it ideal for applications that require high storage capacity and fast access such as video editing, digital surveillance, file servers and shared storage.Using intelligent I/O processing and elaborate algorithms the card bypasses slow disk drives and rebuilds the data by sustaining a stable throughput and streamlining the data transfer therefore enabling the smooth handling of heavy loaded and time critical applications.Data protection is one of the key features of the eXpeRAID adaptors. Not only do they protect against disk failure but also bad sectors using online recovery and reallocation. Disk scrubbing is available to fix the bad sectors and online data and parity refresh protects against data loss caused by media aging.The RAIDGuard X management software supports the online changing of RAID configurations; quick configuration on any Java enabled platform; and with the next generation BIOS and Windows Storport driver it’s future is guaranteed.6Chapter 1 – IntroductionKey FeaturesACS-61000/61010 features the following:z Multiple RAID levels: 0,1, 0+1, 5, 6, and JBODz Up to 4 independent disk arraysz Support 4~16 x SATA I/II drivesz RAID capacity partitioning: up to 16 slicesz Support up to 64 LUNsz Variable stripe sizes, up to 256KBz Selective initialization method with on-the-fly background initialization and performance evaluationz Support over-2TB volumesz Online RAID group expansionz Online RAID level migrationz On-the-fly RAID initializationz Snapshot for fast backup and restorez Support write-back and write-through cachingz Selective and adaptive read/write optimization policiesz Fast read response by intelligently bypass slow drivez Automatic drive insertion/removal detection and fast disk rebuildingz Online bad block data recovery and reallocationz Online disk scrubbing with data refresh and parity regenerationz Disk health monitoring by S.M.A.R.T.z NVRAM-based transaction log and auto parity resynchronizationz Array roaming and drive traveling with redundant on-disk meta dataz Array recovery to restore RAID configurationsz Dual firmware images for firmware recoveryz Support boot from RAIDz Enclosure components monitoring and controlz Optimized for multiple-stream video processingz Support for Windows Mac OS and Linuxz Java-based GUI for remote managementz Reliable multi-lane SATA connectorscompliantz RoHSACS-61000/61010 User’s Manual8 SERIAL ATA (Serial advanced technology attachment)The ACS-61000/61010 is designed for use with the latest Serial ATA II hard disk drives. Serial ATA (often abbreviated as SATA or S-ATA) allows data transfer up to 3 Gbps and is compatible with older Parallel ATA standards. It has an additional advantage parallel ATA in that cables are thinner, so airflow within computer cases is less impeded, and can extend to one meter in length (against only 40 cm for parallel ATA).PCI-EXPRESS X 8Developed by Intel in 2002 PCI-Express has been developed to match the speed of CPUs. It provides a serial communications channel that provides up to 2.5 Gbits/sec in each direction of a pair of wires. The 8 refers to the number of pairs of wires, therefore allowing a maximum of 20 Gbits/sec transfer.FIRMWAREAppropriate firmware must be loaded into the card for it to function. ACS-61000/61010 and are shipped with firmware preloaded. Check the installation disk that came with the package to find a backup firmware copy. You can also periodically check the vendor’s web site to find the latest firmware version for use with the card.BIOS and EFIThe ACS-61000/61010 contains an internal BIOS and EFI which can be used to configure a RAID Array instead of using the RAIDGuard X GUI. The BIOS and EFI are accessed as the card boots up and contains all the functionality of the RAIDGuard X GUI. The BIOS and EFI may be upgraded using the RAIDGuard X GUI, see for upgrades.Chapter 1 – IntroductionBefore you beginWHAT’S IN THE BOXSome vendors may ship certain components as standard, while other vendors treat the same component as optional. In its most basic configuration, your package should include the following:z 1 x ACS-61000/61010 PCI-Express toSATA RAID Cardz1~4 x Mini SAS x 4 multi-lane cable(50cm) by different modelz Quick Start Guidez Installation CD (includes ApplicationSoftware and Hardware user manuals)ACS-61000/61010 User’s Manual OPTIONAL ITEMSz Battery Backup Module (BBM) –theBBM stores the cached data in the eventof power supply failure.z LCD Control panel for seeing card statusand advanced configuration.WHAT ELSE YOU NEEDz LBA 48 bit Hard disk drives (HDDs) (different RAID levels requires different numbers of HDDs. See the RAIDGuard X User Manual to determine how many HDDs you require).z Disk enclosure / disk storage locations and power connection for each disk drive. z Host computer with spare PCI-e slot.z Static grounding strap or electrostatic discharge (ESD) safe work area.The hard drives in a RAID should match in size and speed. All drives in anyarray should be identical models with the same firmware versions. Arrayscan use a minimum of 1GB HDDs, however, the smallest drive will determinethe size of the array.The PCI-e slot on some motherboards is for graphics cards only. Check withthe motherboards vendor for compatibility.10Chapter 1 – IntroductionFamiliarizing yourself with the RAID card OVERVIEW1. Mini SAS connectors2. PCI-Express x 8 connector3. Serial cable connector4. LCD panel connector5. Battery module connector6. DDR memory connectorACS-61000/61010 User’s ManualPIN SETTINGSThe PIN settings on the card are as follows:Serial Cable Connectors (1)Connect the red strip of the serial connector cable to pin 1.LCD Panel Connector (2)Battery Module Connector (3)11012ACS-61000/61010 User’s ManualChapter 2This chapter presents:Ö Instructions on installing the card in the host system. Ö Instructions on installing hard drives.Installation flowchartInstallation of ACS-61000/61010 is simple. This chapter will lead you though the steps:14 zInstall the card in a host system.z Connect a Mini SAS cable from each hard disk drive in the intended array to one of the connectors on the card. zConnect power cables to each of the hard drives.zHardware installation complete.This manual provides full installation and setup instructions for the ACS-61000/61010 RAID card.Chapter 2 – InstallationPre-installation noticesBefore starting any kind of hardware installation, please ensure that allpower switches have been turned off and all power cords disconnected toprevent personal injury and damage to the hardware.To avoid overheating, ACS-61000/61010 should be installed in a well-ventilated area and in such a way that sufficient airflow is maintained acrossthe card chips.candamage electronic components. To guard against suchelectricityStaticdamage:Work in a static-free environmentWear a grounded anti-static wrist strapStore uninstalled components in anti-static bagsHandle PCBs by their edges and avoid touching chips and connectors.Environmental requirementsOperating Temperature: 0°C to 50°C (32°F to 122°F)Storage Temperature: -20°C to 70°C (-4°F to 158°F)Operating Humidity: 5-85%, non-condensingStorage Humidity:5-95%, non-condensingACS-61000/61010 User’s Manual Card InstallationRead the pre-installation notices earlier in this chapter before proceeding. 1. Remove the blanking plate from thePCI-e slot.2. Position the connector of the card overthe expansion slot.3. Press the connector of the card gentlybut firmly into the expansion slot until itis correctly and securely seated.4. Secure the metal bracket of the card tothe system case with a screw.5. Go to the Hard drive connection.Many mother boards only come with 1 PCI-Express interface, beforeinstallation ensure there is one free.Hard Drive Connection1. Attach Mini SAS cables to theconnectors on the card. One cable cancontrol a maximum of 4 HDDs.2. Install the disks in the desired locationeg within the system case or within anindependent disk rack.3. Connect the other end of each cable tothe connectors on each of the harddrives.4. Attach a power connector to each drive,either from the host system or from anindependent power source.16Chapter 2 – InstallationLCD Panel (optional ) InstallationRead the pre-installation notices earlier in this chapter before proceeding. 1. Remove or open the system case toallow access to the 51/4” drive bay youare going to use for the LCD panel.2. Remove the blanking plate from thisslot.3. With the cables connected to the backof the LCD panel, slide the panel intothe system case.4. Secure the LCD panel using screws oneither side.5. Connect the cables to the card.6. Go to the Card Installation.Battery Backup Module (Optional) Installation1. Open the case of the host computerand remove a blanking plate from therear.2. Connect the cables of the BBM to the61000/61010 card, as shown.3. Secure the BBM to the space left by theblanking plate.4. Close the case.The BBM is approximately 2cm high; ensure that your computer case hassufficient room.ACS-61000/61010 User’s Manual18Chapter 3 – Card ConnectionsChapter 3This chapter details the usage of the connectors on theACS-61000/61010 cards.In addition to the ports used for connecting to HDDs; the ACS-61000/61010 also includes connectors for external devices.1. Mini SAS connectors2. PCI-Express x 8 connector3. Serial cable connector4. LCD panel connector5. Battery backup module connector6. DDR memory connectorACS-61000/61010 User’s ManualMINI SAS CONNECTORS (1)Used for connecting the interface cables to Hard Disk Drives. See Part 2 Hard Drive Connection.PCI-EXPRESS X 8 CONNECTOR (2)Used for connecting the card into the server. See Part 2 Card Installation.SERIAL CONNECTOR PORT (3)The serial connectors (2 supplied) allow engineers to configure the card from a terminal connection. Since this requires specialized knowledge it is recommended that the included GUI is used.LCD PANEL CONNECTOR (4)The LCD Panel and connector (not supplied) enable you to configure the card without using the BIOS or RAIDGuard X GUI.Follow the instructions below to use the LCD panel:1. Use the up and down buttons to cycle through the menus.2. Press the ENT button to access the menus and confirm a command.3. Press the ESC button to return to the previous menu.BATTERY CONNECTOR PORT (5)The battery connector port is used to attach a ACS-1161 or ACS-1162 battery backup module (optional). In the event of the PSU failing on the server during saving and transmission of data the module will keep the data in the cache memory until the card resume its work. The BBM occupies 1 rear blanking slot and once charged the BBM will last for more than 72 hours (on board memory).20ACS-61000/61010 User’s Manual Chapter 4This chapter details the usage of the BIOS on the ACS-61000/61010.The BIOS functionality is similar to that of the RAIDGUARD X application. Below is a menu tree detailing the menu structure of the BIOS.1. Start the server and watch the screen. When it gets to the position shown below pressEnter.2. Enter the password (the default is 00000000 (8 zeros) and press Enter.22Chapter 4 – BIOSQUICK ARRAY CONFIGURATION1. For first time use go RAID Configuration > Create Array > Quick Array Configuration.The BIOS will recognize how many drives are installed and provide the best solution.Type Y to begin configuration.1. If there are only 2 disks installed the default RAID array is 0 (zero).2. If there are more than 2 disks the default RAID array is 5.ACS-61000/61010 User’s ManualCUSTOM ARRAY CONFIGURATION1. To change the details of an Array go to RAID Configuration > Create Array > CustomArray Configuration. See the screen below for configuration details.2. Use the Tab button to switch between windows.All other features are accessible through the RAIDGuard X application supplied with the card. See the supplied manual for details on how to use these functions.24Chapter 4 – BIOSBIOS Menu StructureThe BIOS menu structure details how the commands in the BIOS relate to each other. The BIOS manages the same information as the RAIDGuard X application, see it's user manual for further details on these functions.ACS-61000/61010 User’s Manual26Chapter 4 – BIOSBIOS MenuThe menu below gives brief information about the functions of the BIOS menu, for further details see the RAIDGuard X user manual.RAID ConfigCreate Array Quickly create and array, administer the details ofa current and array and configure a JBODSet Slice Add and delete slicesLUN and Map Display details and sets LUNs and Maps Locked Disk Unlock locked disksRefresh Array Refresh an array to improve performanceRAID Checking Check that the RAID is functioning correctly RAID Expansion Expand the disks of an arrayRAID Migration Migrate an array from one RAID type to anothereg from RAID 5 to RAID 1Disk Config UtilityAutomatic Detection Detects installed disksDisk Information Displays manufacturer and speed details of theinstalled disksController Config UtilityPassword Change Change the BIOS passwordSerial Number Display the serial number of the RAID card System Cache Activate and disable the system cacheDisk Cache Activate and disable disk cachingDisk Lag Proof Activate and disable disk lag proof modeNCQ Mode Activate and disable NCQ modeSynchronize Cache Mode Activate and disable synchronize cache mode Real Time Clock Display and set the BIOS clockS.M.A.R.T. Activate and disable S.M.A.R.T. warnings andpolling frequencyMax pre-fetch number Set the maximum number of stripes that can bepre-fetched by the arrayAbout Displays the BIOS version and companyinformationExit Exits the BIOSACS-61000/61010 User’s Manual28Appendix A – SpecificationsAppendix ACPU Intel 80333PCI Express One PCI-e x 8PCI64-bit PCIX-133R6 support YesDiskDisk Interface SATA II/SATADisk Channel 4~16 HDDs, 1~4 internal mini SAS connector Disk Interface Chip Marvell 6081 x 1~2HostHost Channel PCI-e x 4 or x 8 lane from PC.Memory (ACS-61000)Memory type On board DDR 2 memory chipMemory size 256MB with 64-bit DDR II 400 with ECC Memory (ACS-61010)Memory type DDR SODIMMMemory size 64MB ~ 2 GB (with or without ECC)SDRAM type 128/256/512 Mbit and 1Gbit chip densityUser Interface (option)LCD Interface One LCD panel - 2 lines by 16 characters, oneconnector on HBA card.Button Interface UP, Down, ESC, Enter, one connector on HBAcardYes, one on-board connector supportBattery backup interface(option)Fan support Yes, 1 fan connector, support +12V fan Terminal Port For users messages, out-band APIDisk status LED For disk fail and access LEDConnector Two 2x8 pin connector without housing Dimensions Board size 187.7mm(L) x 68.9mm(H)PCB thickness 1.6 mmOperating parametersOperating Temperature 0°C ~50°COperating Humidity 5%~85%, Non-condensingStorage Humidity 5%~95%Storage Temperature -20°C ~70°CACS-61000/61010 User’s Manual30 Appendix BTaiwan - Accusys, Inc.• 5F.,No.38, Taiyuan St., Jhubei City, Hsinchu County 302, Taiwan, R.O.C. • Tel : +886-3-560-0288 • Fax : +886-3-560-0299• / • e-mail:*****************.twAmerica - Accusys U.S.A., Inc.• 46710 Fremont Blvd. Fremont, CA 94538, U.S.A. • Tel :+1-510-661-0800 • FAX :+1-510-661-9800 • Toll-free number:+1-866-277-5888 • /• e-mail:**********************,********************Korea - Accusys Korea, Inc.• Baegang B/D 5F Shinsa-Dong 666-14 Kangnam-Gu, Seoul, Korea • Tel : (02)6245-9050 • Fax : (02)3443-9050• http://www.accusys.co.kr/ • e-mail:****************.krChina Beijing- Accusys China, Inc.• B1701, Horizon International Tower, No.6, ZhiChun Road, HaiDian District, Beijing • Tel: +86-10-82800080 • Fax: +86-10-82800784 • E-mail: *****************.cn • Europe - Accusys EU B.V• Columbusstraat 2-10, 3165 AD Rotterdam, Netherlands • Tel : +31-10-4284117 • Fax : +31-10-4284114• • ftp://• e-mail:*******************,*********************。

Taurus SeriesMultimedia PlayersT3 SpecificationsProduct Version: V1.3.0 Document Number:NS120100242XI 'AN NOVA ST A R TEC H C O .,L T D .Copyright © 2018 Xi’an NovaStar Tech Co., Ltd. All Rights Reserved.No part of this document may be copied, reproduced, extracted or transmitted in any form or by any means without the prior written consent of Xi’an Nova Star Tech Co., Ltd.Trademarkis a trademark of Xi’an NovaStar Tech Co., Ltd.StatementYou are welcome to use the product of Xi’an NovaStar Tech Co., Ltd. (hereinafter referred to as NovaStar). This document is intended to help you understand and use the product. For accuracy and reliability, NovaStar may make improvements and/or changes to this document at any time and without notice. If you experience any problems in use or have any suggestions, please contact us via contact info given in document. We will do our best to solve any issues, as well as evaluate and implement any suggestions.X I'A NN OV AS TA RT EC HC O.,L TD.Table of ContentsTable of Contents ............................................................................................................................ ii 1 Safety .. (1)1.1 Storage and Transport Safety ..................................................................................................................... 1 1.2 Installation and Use Safety .. (1)2 Overview (3)2.1 Introduction .................................................................................................................................................. 3 2.2 Application ................................................................................................................................................... 3 3 Features ........................................................................................................................................... 5 3.1 Synchronization mechanism for multi-screen playing ................................................................................. 5 3.2 Powerful Processing Capability ................................................................................................................... 5 3.3 Omnidirectional Control Plan .. (5)3.4 Dual-Wi-Fi Mode .......................................................................................................................................... 6 3.4.1 Wi-Fi AP Mode .......................................................................................................................................... 7 3.4.2 Wi-Fi Sta Mode .. (7)3.4.3 Wi-Fi AP+Sta Mode .................................................................................................................................. 7 3.5 Redundant Backup ...................................................................................................................................... 8 4 Hardware Structure....................................................................................................................... 9 4.1 Appearance . (9)4.2 Dimensions (11)5 Software Structure (12)5.1 System Software ........................................................................................................................................ 12 5.2 Related Configuration Software .. (12)6 Product Specifications ................................................................................................................ 13 7 Audio and Video Decoder Specifications (15)7.1 Image ......................................................................................................................................................... 15 7.1.1 Decoder .................................................................................................................................................. 15 7.1.2 Encoder .................................................................................................................................................. 15 7.2 Audio .......................................................................................................................................................... 16 7.2.1 Decoder .. (16)X I 'A N N O V A S T A R T E C H C O .,L T D.7.2.2 Encoder (16)7.3 Video (17)7.3.1 Decoder (17)7.3.2 Encoder (18)X I'A NN OV AS TA RT EC HC O.,L TD.1SafetyThis chapter illustrates Taurus series products safety to ensure storage, transportation, installation and usage safety of the products.Safety description is applicable to all personnel that contact or use the products. First, pay attention to following points:● Read throughout the description. ● Save the whole description.●Be complied with the whole description.1.1 Storage and Transport Safety ● Pay attention to dust and water prevention.● Avoid long-term direct sunlight. ● Do not place the products in the position near fire and heat.● Do not place the products in an area containing explosive materials. ● Do not place the products in strong electromagnetic environment. ● Place the products in a stable position to prevent damage or personal injury caused by dropping.●Save the packing box and materials which will come in handy if you ever have to ship your products. For maximum protection, repack your product as it wasoriginally packed at the factory.1.2 Installation and Use Safety● Only trained professionals may install the products.● Do not insert and unplug (power cord plug) when the power is on. ● Ensure the safe grounding of the device.● Be careful about electric shock risk. Built-in power supply. ● Always wear a wrist band and insulating gloves.● Do not place the products in an area having more or strong shake. ● Perform dust removing regularly.●Rather than having the product disassembled and maintained by non-certified professionals, please contact NovaStar for maintenance at any time.X I 'A N N O V A S T A R T E CHCO .,L T D.Replace faulty parts only with the spare parts supplied by NovaStar.X I'A NN OV AS TA RT EC HC O.,L TD.2Overview2.1 IntroductionTaurus series products are NovaStar's second generation of multimedia players dedicated to small and medium-sized full-color LED displays.T3 of the Taurus series products (herein after referred to as “T 3”) feature following advantages, better satisfying users’ requir ements:●Loading capacity up to 650,000 pixels●Synchronization mechanism for multi-screen playing● Powerful processing capability ● Omnidirectional control plan ● Dual-Wi-Fi mode ●Redundant backup Note: If the user has a high demand on synchronization, the time synchronization module isrecommended. For details, please consult our technical staff. In addition to solution publishing and screen control via PC, mobile phones and LAN, the omnidirectional control plan also supports remote centralized publishing and monitoring. 2.2 ApplicationTaurus series products can be widely used in LED commercial display field, such asbar screen, chain store screen, advertising machine, mirror screen, retail store screen, door head screen, on board screen and the screen requiring no PC. Classification of Taurus’ application cases is shown in Table 2-1. Table 2-1 ApplicationXI 'A N N O V A S T A R T E C H C O .,L T D.X I'A NN OV AS TA RT EC HC O.,L T3Features3.1 Synchronization mechanism for multi-screen playingThe T3 support switching on/off function of synchronous display.When synchronous display is enabled, the same content can be played on different displays synchronously if the time of different T3 units are synchronous with one another and the same solution is being played.3.2 Powerful Processing CapabilityThe T3 feature powerful hardware processing capability: ● 1.5 GHz eight-core processor●Support for H.265 4K high-definition video hardware decoding playback ● Support for 1080P video hardware decoding ● 2 GB operating memory●8 GB on-board internal storage space with 4 GB available for users 3.3 Omnidirectional Control Plan Table 3-1 Control PlanXI 'A N N O V A S T A R T E C H CO .,L T D.Cluster control plan is a new internet control plan featuring following advantages:●More efficient: Use the cloud service mode to process services through a uniformplatform. For example, VNNOX is used to edit and publish solutions, and NovaiCare is used to centrally monitor display status.● More reliable: Ensure the reliability based on active and standby disaster recovery mechanism and data backup mechanism of the server. ● More safe: Ensure the system safety through channel encryption, data fingerprintand permission management. ● Easier to use: VNNOX and NovaiCare can be accessed through Web. As long asthere is internet, operation can be performed anytime and anywhere. ●More effective: This mode is more suitable for the commercial mode of advertising industry and digital signage industry, and makes information spreading more effective. 3.4 Dual-Wi-Fi Mode The T3 have permanent Wi-Fi AP and support the Wi-Fi Sta mode, carryingadvantages as shown below:●Completely cover Wi-Fi connection scene. The T3 can be connected to through self-carried Wi-Fi AP or the external router.●Completely cover client terminals. Mobile phone, Pad and PC can be used to log in T3 through wireless network.●Require no wiring. Display management can be managed at any time, having improvements in efficiency.T3’s Wi -Fi AP signal strength is related to the transmit distance and environment. Users can change the Wi-Fi antenna as required.XI 'A NN O V A S T A R T E C H C O .,L T D3.4.1 Wi-Fi AP ModeUsers connect the Wi-Fi AP of a T3 to directly access the T3. The SSID is “AP + the last 8 digits of the SN ”, for example, “AP10000033”, and the default password is “12345678”.3.4.2 Wi-Fi Sta Mode Configure an external router for a T3 and users can access the T3 by connecting the external router. If an external router is configured for multiple T3 units, a LAN can becreated. Users can access any of the T3 via the LAN.3.4.3 Wi-Fi AP+Sta ModeIn Wi-Fi AP+ Sta connection mode, users can either directly access the T3 or accessinternet through bridging connection. Upon the cluster solution, VNNOX andNovaiCare can realize remote solution publishing and remote monitoring respectively through the Internet.XI 'A N N O V A S T A R T E C HCO .,L T D.3.5 Redundant BackupT3 support network redundant backup and Ethernet port redundant backup.●Network redundant backup: The T3 automatically selects internet connectionmode among wired network or Wi-Fi Sta network according to the priority.●Ethernet port redundant backup: The T3 enhances connection reliability throughactive and standby redundant mechanism for the Ethernet port used to connectwith the receiving card.X I'A NN OV AS TA RT EC HC O.,L TD.4Hardware Structure4.1 AppearanceFigure 4-1 Appearance of T3Note: Product images provided in this file are for reference only, and the actualproducts shall prevail.Table 4-1 Connectors and buttons of the T3XI 'AN NOVA S TAR T E C HCO .,L T D.Note: Product images provided in this file are for reference only, and the actual products shall prevail.Table 4-2 Indicators of the T3 A R T E C HCO .,L T D.4.2 DimensionsThe total thickness (board thickness + thickness of the components on the front andback side) is no greater than 25.0mm.Unit of the dimension chart is “mm”. Ground connection is enabled for location hole(GND).X I'A NN OV AS TA RT EC HC O.,L TD.5Software Structure5.1 System Software● Android operating system software ● Android terminal application software ●FPGA programNote: The third-party applications are not supported.5.2 Related Configuration SoftwareTable 5-1 Related configuration softwareE C HCO .,L T D.6 Product Specifications SpecificationsAntennaAntenna extension mastX I'A NN OV AS TA RT EC HC O.,L TD.7Audio and Video DecoderSpecifications7.1 Image7.1.1 Decoder7.1.2 EncoderO .,L T D.7.2 Audio 7.2.1 Decoder7.2.2 Encoder7.3 Video 7.3.1 DecoderNote: Output data format is YUV420 semi-planar, and YUV400(monochrome) is also supported for H.264.7.3.2 EncoderXI 'AN NOVA S。

分数:仲恺农业工程学院信息工程专业英语题目:班级:通信工程091姓名:徐铭璐学号:200910324225Introduction to Digital Image Processing数字图像处理7.1 What Is Digital Image Processing?7.1什么事图像处理An image may be defined as a two-dimensional function, (,)f x y, where x and y are spatial (plane) coordinates, and the amplitude of f at any pair of coordinates (x, y) is called the intensity or gray level of the image at that point. When x, y, and the amplitude values of f are all finite, discrete quantities, we call the image a digital image. The field of digital image processing refers to processing digital images by means of a digital computer. Note that a digital image is composed of a finite number of elements, each of which has a particular location and value. These elements are referred to as picture elements, image elements, pels, and pixels. Pixel is the term most widely used to denote the elements of a digital image.一幅图像可定义为一个二维函数f(x, y),这里x和y是空间坐标,而在任何一对空间坐标f(x, y)上的幅值f称为该点图像的强度或灰度。


3LASERType Semiconductor laser InGaAlP (DVD) AIGaAs (CD)Wave length 658 nm (DVD) 790 nm (CD)Output Power 7.0 mW (DVD) 10.0 mW (VCD/CD)Beam divergence 60 degreesFor Customer Use:Read carefully the information located at the bottom or rear of your DVD Video player and enter below the Serial No. Retain this information for future reference.Model No. DVP 5166KSerial No. ___________________USB extension cablePress PREVí / NEXTë to display the other pictures on the previous / next page.Select this if you have aOthersSoftware upgradePeriodically Philips will issue softwareupgrade to enhance your userexperience.I MPORTANT!– Power supply must not beinterrupted during upgrade!To check the current software version of this DVD player;A Press OPEN/CLOSEç on the DVDplayer to open the disc tray.The disc tray will open.B Press numeric keypad ‘55’ on theremote control.The fi le name of the software installed in the DVD player appears on the TVscreen.To download and install the latestsoftware to the DVD player;A Visit the Philips website ‘www.philips.com/welcome’ to check the availability of the latest software upgrade.B Download the software to a CD-R.C Insert the CD-R to the disc slot.The menu appears on the TV screen.Upgrade File DetectedUpgrade?Press Play to startD Press PLAY/PAUSE u to downloadthe latest software in the DVD player.The DVD player will restartautomatically once the downloadcomplete.46Specifi cationsTV STANDARD (PAL/50Hz) (NTSC/60Hz) Number of lines 625 525Playback Multistandard(PAL/NTSC)VIDEO PERFORMANCEVideo DAC 12 bit, 108 MHzYPbPr 0.7 Vpp ~ 75 ohmVideo Output 1Vpp ~ 75 ohmVIDEO FORMATDigital MPEG 2 for DVD,SVCD Compression MPEG 1 for VCDDivX®DVD50Hz 60HzHoriz. resolution 720 pixels 720 pixelsVertical resolution 576 lines 480 linesVCD50Hz 60HzHoriz. resolution 352 pixels 352 pixelsVertical resolution 288 lines 240 linesAUDIO FORMATDigital MPEG/AC-3/compressedPCM Digital16, 20, 24 bitsfs, 44.1, 48, 96kHzMP3(ISO 9660) 96, 112, 128,256, 320 kbps &variablebitratefs, 32, 44.1, 48 kHz Analog Sound StereoDolby Surround compatible downmix from Dolby Digital multi-channel sound AUDIO PERFORMANCEDA Converter 24 bit, 192 kHzDVD fs 96 kHz 4Hz- 44kHzfs 48 kHz 4Hz- 22kHz SVCD fs 48 kHz 4Hz- 22kHzfs 44.1kHz 4Hz- 20kHzCD/VCD fs 44.1kHz 4Hz- 20kHz Signal-Noise (1kHz) > 90 dB Dynamic range(1kHz) > 80 dB Crosstalk (1kHz) > 70 dB Distortion/noise (1kHz) > 65 dBMPEG MP3 MPEG Audio L3 CONNECTIONSYPbPr Output Cinch 3xVideo Output Cinch (yellow)Audio Output(L+R)Cinch (white/red)Digital Output 1 coaxialIEC60958 for CDDA / LPCMIEC61937 for MPEG 1/2,DolbyDigital6 channal analog outputAudio Front L/R Clinch (white/red)Audio Rear L/R Clinch (white/red)Audio Center Clinch (blue)Audio Subwoofer Clinch (black)CABINETDimensions (w x h x d) 435 x 38 x 210 mm Weight Approximately 2 kgPOWER CONSUMPTIONPower Supply Rating 110V – 240V;50/60H z Power consumption < 10 WPower consumption in < 1 W Standby mode47Why does it take so long to display the contents on my USB device?– This could be due to the large numbers of fi les (>500 fi les/folders) or size of thefi les (>1MB.)– There could be other non-supported fi les in the device that the system is trying toread/display.What if un-supported devices (e.g. USB mouse, keyboards) are plugged into the player?– The device may cause the player to be unstable. Remove the unsupporteddevice and unplug the mains cord. Waitfor a few minutes before reconnectingthe mains cord and power on the playeragain.What happens when I plug in a USB HDD?– HDD is not supported as the large storage capacity makes navigation verydiffi cult. Transfer the music fi les (mp3)and photos (jpg) into a fl ash drive.Why does the system fail to detect my USB portable music player?– The portable music player may require propriety software that is bundled withour player in order to access thecontents (eg. playlist.)Why can’t some devices be playback from USB Port on my player?– USB Port only offer 500mA current, could not power up HDD players whichrequire more current.– Device which shows USB Mass Storage Device might actually be USB Hub whendetect in USB analyser.– Devices in NTFS format can’t besupported.– Devices require drivers to be installed will not supported by this player. Theyare not UMS or MTP devices, which does not require any driver installation or start up disc. When in UMS or MTP mode, the device is treated as an external HDD orportable device.What types of fi le does the player support?– We support only FAT16 and FAT32, not NTFS.Why does the fi le name appear to be different from what was displayed on my computer (e.g. from “Good Bye. jpg” to “Good_B~1.jpg”)?– The length of the fi le name is restricted by the fi le system of the device (FAT16),which only supports eight (8) characters.– The computer may be able to display the full fi le name as the operating system can convert the fi le system.Is simultaneous USB and Disc playback possible?– This is not possible due to memory limitation. In addition, a different userinterface will be needed in order tofunction and in order to be simpleenough to use.Why can’t I rotate the pictures in my device?– In order to rotate the pictures in the USB device, the picture must containEXIF information, stored by most digitalcameras. This EXIF information mayhave been removed when you edit orcopy the picture from other devices using editing programs.Why can’t the player play some of my music fi les, photos or movies?– The music fi les may not be playable because of different formats and encoding bit-rates. Similarly, the photos may be of low resolution or too high resolution for the player to support.Frequently Asked Questions (USB)50。

Digital Image Processing, 3rd ed(数字图像处理(第3版)内附图片)数据摘要:DIGITAL IMAGE PROCESSING has been the world's leading textbook in its field for more than 30 years. As in the 1977 and 1987 editions by Gonzalez and Wintz, and the 1992 and 2002 editions by Gonzalez and Woods, this fifth-generation book was prepared with students and instructors in mind. The principal objectives of the book continue to be to provide an introduction to basic concepts and methodologies for digital image processing, and to develop a foundation that can be used as the basis for further study and research in this field. The material is timely, highly readable, and illustrated with numerous examples of practical significance. All mainstream areas of image processing are covered, including image fundamentals, image enhancement in the spatial and frequency domains, restoration, color image processing, wavelets, image compression, morphology, segmentation, and image description. Coverage concludes with a discussion on the fundamentals of object recognition.Although the book is completely self-contained, this companion web site provides additional support in the form of review material, answers to selected problems, laboratory project suggestions, and a score of otherfeatures. A supplementary instructor's manual is available to instructors who have adopted the book for classroom use. See also a partial list of institutions that use the book.One of the principal reasons this book has been the world leader in its field for more than 30 years is the level of attention we pay to the changing educational needs of our readers. The present edition is based on the most extensive survey we have ever conducted. The survey involved faculty, students, and independent readers of the book in 134 institutions from 32 countries. Many of the following new features are based on the results of that survey.中文关键词:数字图像处理,图像基础,图像在空间和频率域的增强,图像压缩,图像描述,英文关键词:digital image processing,image fundamentals,image compression,image description,数据格式:IMAGE数据用途:数字图像处理数据详细介绍:Digital Image Processing, 3rd editionBasic Information:ISBN number 9780131687288.Publisher: Prentice Hall12 chapters.954 pages.© 2008.DIGITAL IMAGE PROCESSING has been the world's leading textbook in its field for more than 30 years. As in the 1977 and 1987 editions by Gonzalez and Wintz, and the 1992 and 2002 editions by Gonzalez and Woods, this fifth-generation book was prepared with students and instructors in mind. The principal objectives of the book continue to be to provide an introduction to basic concepts and methodologies for digital image processing, and to develop a foundation that can be used as the basis for further study and research in this field. The material is timely, highly readable, and illustrated with numerous examples of practical significance. All mainstream areas of image processing are covered, including image fundamentals, imageenhancement in the spatial and frequency domains, restoration, color image processing, wavelets, image compression, morphology, segmentation, and image description. Coverage concludes with a discussion on the fundamentals of object recognition.Although the book is completely self-contained, this companion web site provides additional support in the form of review material, answers to selected problems, laboratory project suggestions, and a score of other features. A supplementary instructor's manual is available to instructors who have adopted the book for classroom use. See also a partial list of institutions that use the book.One of the principal reasons this book has been the world leader in its field for more than 30 years is the level of attention we pay to the changing educational needs of our readers. The present edition is based on the most extensive survey we have ever conducted. The survey involved faculty, students, and independent readers of the book in 134 institutions from 32 countries. Many of the following new features are based on the results of that survey.NEW FEATURESA revision of introductory concepts that provides readers with foundation material much earlier in the book than before.A revised and updated discussion of intensity transformation, spatialcorrelation, convolution, and their application to spatial filtering.New discussion of fuzzy sets and their application to image processing.A new chapter on the discrete Fourier transform and frequency domain processing.New coverage of computerized tomography.A revision of the wavelets chapter.A new chapter on data compression, including new compression techniques, digital video compression, standards, and watermarking.New coverage of morphological reconstruction, gray-scale morphology, and advanced morphological algorithms.New coverage of the Marr-Hildreth and Canny edge detection algorithms.Expanded coverage of image thresholding.New examples and illustrations involving over 400 new images and more than 200 new drawings and tables.Expanded homework sets, including over 80 new problems.Updated bibliography.Differences Between the DIP and DIPUM BooksDigital Image Processing is a book on fundamentals.Digital Image Processing Using MATLAB is a book on the software implementation of those fundamentals.The key difference between the books is that Digital Image Processing (DIP) deals primarily with the theoretical foundation of digital image processing, while Digital Image Processing Using MATLAB (DIPUM) is a book whose main focus is the use of MATLAB for image processing. The DIPUM book covers essentially the same topics as DIP, but the theoretical treatment is not as detailed. Some instructors prefer to fill in the theoretical details in class in favor of having available a book with a strong emphasis on implementation.© 2008 by Pearson Education, Inc.Pearson Prentice HallPearson Education, Inc.Upper Saddle River, New Jersey 07458All rights reserved. No part of this book may be reproduced, in any form, or by any means, without permission in writing from the publisher. Pearson Prentice Hall ® is a trademark of Pearson Education, Inc. The authors and publisher of this book have used their best efforts in preparing this book.These efforts include the development, research, and testing of the theories and programs to determine their effectiveness.The authors and publisher make no warranty of any kind, expressed or implied,with regard to these programs or the documentation contained in this book.The authors and publisher shall not be liable in any event for incidental or consequential damages with, or arising outof, the furnishing, performance, or use of these programs. 数据预览:点此下载完整数据集。
AREA: Artificial Intelligence and Related SubjectsRank 1:AAAI: American Association for AI National ConferenceCVPR: IEEE Conf on Comp Vision and Pattern RecognitionECCV: European Conference on Computer VisionIJCAI: Intl Joint Conf on AIICCV: Intl Conf on Computer VisionICML: Intl Conf on Machine LearningKDD: Knowledge Discovery and Data MiningKR: Intl Conf on Principles of KR & ReasoningNIPS: Neural Information Processing SystemsUAI: Conference on Uncertainty in AIICAA: International Conference on Autonomous AgentsACL: Annual Meeting of the ACL (Association of Computational Linguistics) Rank 2:NAACL: North American Chapter of the ACLAID: Intl Conf on AI in DesignAI-ED: World Conference on AI in EducationCAIP: Inttl Conf on Comp. Analysis of Images and PatternsCSSAC: Cognitive Science Society Annual ConferenceEAI: European Conf on AIEML: European Conf on Machine LearningGP: Genetic Programming ConferenceIAAI: Innovative Applications in AIICIP: Intl Conf on Image ProcessingICNN/IJCNN: Intl (Joint) Conference on Neural NetworksICPR: Intl Conf on Pattern RecognitionICDAR: International Conference on Document Analysis and Recognition ICTAI: IEEE conference on Tools with AIAMAI: Artificial Intelligence and MathsDAS: International Workshop on Document Analysis SystemsWACV: IEEE Workshop on Apps of Computer VisionCOLING: International Conference on Computational LiguisticsEMNLP: Empirical Methods in Natural Language ProcessingEACL: Annual Meeting of European Association Computational Lingustics CoNLL: Conference on Natural Language LearningRank 3:PRICAI: Pacific Rim Intl Conf on AIAAI: Australian National Conf on AIACCV: Asian Conference on Computer VisionAI*IA: Congress of the Italian Assoc for AIANNIE: Artificial Neural Networks in EngineeringANZIIS: Australian/NZ Conf on Intelligent Inf. SystemsCAIA: Conf on AI for ApplicationsCAAI: Canadian Artificial Intelligence ConferenceASADM: Chicago ASA Data Mining Conf: A Hard Look at DMEPIA: Portuguese Conference on Artificial IntelligenceFCKAML: French Conf on Know. Acquisition & Machine LearningICANN: International Conf on Artificial Neural NetworksICCB: International Conference on Case-Based ReasoningICGA: International Conference on Genetic AlgorithmsICONIP: Intl Conf on Neural Information ProcessingIEA/AIE: Intl Conf on Ind. & Eng. Apps of AI & Expert SysICMS: International Conference on Multiagent SystemsICPS: International conference on Planning SystemsIWANN: Intl Work-Conf on Art & Natural Neural NetworksPACES: Pacific Asian Conference on Expert SystemsSCAI: Scandinavian Conference on Artifical IntelligenceSPICIS: Singapore Intl Conf on Intelligent SystemPAKDD: Pacific-Asia Conf on Know. Discovery & Data MiningSMC: IEEE Intl Conf on Systems, Man and CyberneticsPAKDDM: Practical App of Knowledge Discovery & Data MiningWCNN: The World Congress on Neural NetworksWCES: World Congress on Expert SystemsINBS: IEEE Intl Symp on Intell. in Neural \& Bio SystemsASC: Intl Conf on AI and Soft ComputingPACLIC: Pacific Asia Conference on Language, Information and Computation ICCC: International Conference on Chinese ComputingICADL: International Conference on Asian Digital LibrariesRANLP: Recent Advances in Natural Language ProcessingNLPRS: Natural Language Pacific Rim SymposiumOthers:ICRA: IEEE Intl Conf on Robotics and AutomationNNSP: Neural Networks for Signal ProcessingICASSP: IEEE Intl Conf on Acoustics, Speech and SPGCCCE: Global Chinese Conference on Computers in EducationICAI: Intl Conf on Artificial IntelligenceAEN: IASTED Intl Conf on AI, Exp Sys & Neural NetworksWMSCI: World Multiconfs on Sys, Cybernetics & InformaticsLREC: Language Resources and Evaluation ConferenceAREA: Hardware and ArchitectureRank 1:ASPLOS: Architectural Support for Prog Lang and OSISCA: ACM/IEEE Symp on Computer ArchitectureICCAD: Intl Conf on Computer-Aided DesignDAC: Design Automation ConfMICRO: Intl Symp on MicroarchitectureHPCA: IEEE Symp on High-Perf Comp ArchitectureRank 2:FCCM: IEEE Symposium on Field Programmable Custom Computing Machines SUPER: ACM/IEEE Supercomputing ConferenceICS: Intl Conf on SupercomputingISSCC: IEEE Intl Solid-State Circuits ConfHCS: Hot Chips SympVLSI: IEEE Symp VLSI CircuitsISSS: International Symposium on System SynthesisDATE: IEEE/ACM Design, Automation & Test in Europe ConferenceRank 3:ICA3PP: Algs and Archs for Parall ProcEuroMICRO: New Frontiers of Information TechnologyACS: Australian Supercomputing ConfUnranked:Advanced Research in VLSIInternational Symposium on System SynthesisInternational Symposium on Computer DesignInternational Symposium on Circuits and SystemsAsia Pacific Design Automation ConferenceInternational Symposium on Physical DesignInternational Conference on VLSI DesignAREA: ApplicationsRank 1:I3DG: ACM-SIGRAPH Interactive 3D GraphicsSIGGRAPH: ACM SIGGRAPH ConferenceACM-MM: ACM Multimedia ConferenceDCC: Data Compression ConfSIGMETRICS: ACM Conf on Meas. & Modelling of Comp SysSIGIR: ACM SIGIR Conf on Information RetrievalPECCS: IFIP Intl Conf on Perf Eval of Comp \& Comm SysWWW: World-Wide Web ConferenceRank 2:EUROGRAPH: European Graphics ConferenceCGI: Computer Graphics InternationalCANIM: Computer AnimationPG: Pacific GraphicsNOSSDAV: Network and OS Support for Digital A/VPADS: ACM/IEEE/SCS Workshop on Parallel \& Dist Simulation WSC: Winter Simulation ConferenceASS: IEEE Annual Simulation SymposiumMASCOTS: Symp Model Analysis \& Sim of Comp \& Telecom Sys PT: Perf Tools - Intl Conf on Model Tech \& Tools for CPENetStore: Network Storage SymposiumMMCN: ACM/SPIE Multimedia Computing and NetworkingJCDL: Joint Conference on Digital LibrariesRank 3:ACM-HPC: ACM Hypertext ConfMMM: Multimedia ModellingICME: Intl Conf on MMedia & ExpoDSS: Distributed Simulation SymposiumSCSC: Summer Computer Simulation ConferenceWCSS: World Congress on Systems SimulationESS: European Simulation SymposiumESM: European Simulation MulticonferenceHPCN: High-Performance Computing and NetworkingGeometry Modeling and ProcessingWISEDS-RT: Distributed Simulation and Real-time ApplicationsIEEE Intl Wshop on Dist Int Simul and Real-Time ApplicationsECIR: European Colloquium on Information RetrievalUn-ranked:DVAT: IS\&T/SPIE Conf on Dig Video Compression Alg \& Tech MME: IEEE Intl Conf. on Multimedia in EducationICMSO: Intl Conf on Modelling, Simulation and OptimisationICMS: IASTED Intl Conf on Modelling and SimulationAREA: System Technology (Including networking and security)Rank 1:SIGCOMM: ACM Conf on Comm Architectures, Protocols & Apps SPAA: Symp on Parallel Algms and ArchitecturePODC: ACM Symp on Principles of Distributed ComputingPPoPP: Principles and Practice of Parallel ProgrammingMassPar: Symp on Frontiers of Massively Parallel ProcRTSS: Real Time Systems SympSOSP: ACM SIGOPS Symp on OS PrinciplesOSDI: Usenix Symp on OS Design and ImplementationCCS: ACM Conf on Comp and Communications SecurityS&P (Oakland): IEEE Symposium on Security and PrivacyMOBICOM: ACM Intl Conf on Mobile Computing and NetworkingMOBIHOC: ACM International Symposium on Mobile Ad Hoc Networking and ComputingICNP: Intl Conf on Network ProtocolsOPENARCH: IEEE Conf on Open Arch and Network ProgPACT: Intl Conf on Parallel Arch and Compil TechINFOCOM: Annual Joint Conf IEEE Comp & Comm SocRank 2:USENIX Symp on Internet Tech and SysCC: Compiler ConstructionIPDPS: Intl Parallel and Dist Processing SympMOBISYS: International Conference on Mobile Systems, Applications, and Services SenSys: ACM Conference on Embedded Networked Sensor SystemsICPP: Intl Conf on Parallel ProcessingICDCS: IEEE Intl Conf on Distributed Comp SystemsSRDS: Symp on Reliable Distributed SystemsMPPOI: Massively Par Proc Using Opt InterconnsASAP: Intl Conf on Apps for Specific Array ProcessorsEuro-Par: European Conf. on Parallel ComputingUsenix Security SymposiumNDSS: ISOC Network and Distributed System Security SymposiumESORICS: European Symposium on Research in Computer SecurityRAID: International Symposium on Recent Advances in Intrusion DetectionDSN: The International Conference on Dependable Systems and NetworksACSAC: Annual Computer Security Applications ConferenceWCW: Web Caching WorkshopLCN: IEEE Annual Conference on Local Computer NetworksIPCCC: IEEE Intl Phoenix Conf on Comp & CommunicationsCCC: Cluster Computing ConferenceICC: Intl Conf on CommWCNC: IEEE Wireless Communications and Networking ConferenceIPSN: International Conference on Information Processing in Sensor NetworksIPTPS: Annual International Workshop on Peer-To-Peer SystemsCSFW: IEEE Computer Security Foundations WorkshopRank 3:MPCS: Intl. Conf. on Massively Parallel Computing SystemsGLOBECOM: Global CommIMC: Internet Measurement ConferenceIC3N: Intl Conf on Comp Comm and NetworksICCC: Intl Conf on Comp CommunicationNOMS: IEEE Network Operations and Management SympCONPAR: Intl Conf on Vector and Parallel ProcessingVAPP: Vector and Parallel ProcessingICPADS: Intl Conf. on Parallel and Distributed SystemsPublic Key CryptosystemsFast Software EncryptionSecureComm: Int. Conf on Security and Privacy for Emerging Areas in Communication NetworksAsiaCCS: ACM Symposium on Information, Computer and Communications Security ACNS: International Conference on Applied Cryptography and Network SecurityAnnual Workshop on Selected Areas in CryptographyAustralasia Conference on Information Security and PrivacyInt. Conf on Inofrm and Comm. SecurityFinancial CryptographyWorkshop on Information HidingSmart Card Research and Advanced Application ConferenceICON: Intl Conf on NetworksIMSA: Intl Conf on Internet and MMedia SysNCC: Nat Conf CommIN: IEEE Intell Network WorkshopSoftcomm: Conf on Software in Tcomms and Comp NetworksINET: Internet Society ConfWorkshop on Security and Privacy in E-commerceEEE: IEEE Conference on e-Technology, e-Commerce and e-Service (Suggested by Roy Grønmo. Thanks)Un-ranked:PARCO: Parallel ComputingSE: Intl Conf on Systems EngineeringAREA: Programming Languages and Software EngineeringRank 1:POPL: ACM-SIGACT Symp on Principles of Prog LangsPLDI: ACM-SIGPLAN Symp on Prog Lang Design & ImplOOPSLA: OO Prog Systems, Langs and ApplicationsICFP: Intl Conf on Function ProgrammingJICSLP/ICLP/ILPS: (Joint) Intl Conf/Symp on Logic ProgICSE: Intl Conf on Software EngineeringFSE: ACM Conference on the Foundations of Software Engineering (inc: ESEC-FSE when held jointly)FM/FME: Formal Methods, World Congress/EuropeCAV: Computer Aided VerificationRank 2:CP: Intl Conf on Principles & Practice of Constraint ProgTACAS: Tools and Algos for the Const and An of SystemsESOP: European Conf on ProgrammingICCL: IEEE Intl Conf on Computer LanguagesPEPM: Symp on Partial Evalutation and Prog ManipulationSAS: Static Analysis SymposiumRTA: Rewriting Techniques and ApplicationsESEC: European Software Engineering ConfIWSSD: Intl Workshop on S/W Spec & DesignCAiSE: Intl Conf on Advanced Info System EngineeringITC: IEEE Intl Test ConfIWCASE: Intl Workshop on Cumpter-Aided Software EngSSR: ACM SIGSOFT Working Conf on Software ReusabilitySEKE: Intl Conf on S/E and Knowledge EngineeringICSR: IEEE Intl Conf on Software ReuseASE: Automated Software Engineering ConferencePADL: Practical Aspects of Declarative LanguagesISRE: Requirements EngineeringICECCS: IEEE Intl Conf on Eng. of Complex Computer SystemsIEEE Intl Conf on Formal Engineering MethodsIntl Conf on Integrated Formal MethodsFOSSACS: Foundations of Software Science and Comp StructRank 3:FASE: Fund Appr to Soft EngAPSEC: Asia-Pacific S/E ConfPAP/PACT: Practical Aspects of PROLOG/Constraint TechALP: Intl Conf on Algebraic and Logic ProgrammingPLILP: Prog, Lang Implentation & Logic ProgrammingLOPSTR: Intl Workshop on Logic Prog Synthesis & TransfICCC: Intl Conf on Compiler ConstructionCOMPSAC: Intl. Computer S/W and Applications ConfCSM: Conf on Software MaintenanceTAPSOFT: Intl Joint Conf on Theory & Pract of S/W DevWCRE: SIGSOFT Working Conf on Reverse EngineeringAQSDT: Symp on Assessment of Quality S/W Dev ToolsIFIP Intl Conf on Open Distributed ProcessingIntl Conf of Z UsersIFIP Joint Int'l Conference on Formal Description Techniques and Protocol Specification,Testing, And VerificatiPSI (Ershov conference)UML: International Conference on the Unified Modeling LanguageEDOC: IEEE Conference on Enterprise Computing (Suggested by Roy Grønmo.)Un-ranked:Australian Software Engineering ConferenceIEEE Int. W'shop on Object-oriented Real-time Dependable Sys. (WORDS)IEEE International Symposium on High Assurance Systems EngineeringThe Northern Formal Methods WorkshopsFormal Methods PacificInt. Workshop on Formal Methods for Industrial Critical SystemsJFPLC - International French Speaking Conference on Logic and Constraint ProgrammingL&L - Workshop on Logic and LearningSFP - Scottish Functional Programming WorkshopHASKELL - Haskell WorkshopLCCS - International Workshop on Logic and Complexity in Computer ScienceVLFM - Visual Languages and Formal MethodsNASA LaRC Formal Methods Workshop(1) FATES - A Satellite workshop on Formal Approaches to Testing of Software(1) Workshop On Java For High-Performance Computing(1) DSLSE - Domain-Specific Languages for Software Engineering(1) FTJP - Workshop on Formal Techniques for Java Programs(*) WFLP - International Workshop on Functional and (Constraint) Logic Programming (*) FOOL - International Workshop on Foundations of Object-Oriented L anguages (*) SREIS - Symposium on Requirements Engineering for Information Sec urity(*) HLPP - International workshop on High-level parallel programming and applications (*) INAP - International Conference on Applications of Prolog(*) MPOOL - Workshop on Multiparadigm Programming with OO Languages(*) PADO - Symposium on Programs as Data Objects(*) TOOLS: Int'l Conf Technology of Object-Oriented Languages and Systems(*) Australasian Conference on Parallel And Real-Time SystemsAREA: Algorithms and TheoryRank 1:STOC: ACM Symp on Theory of ComputingFOCS: IEEE Symp on Foundations of Computer ScienceCOLT: Computational Learning TheoryLICS: IEEE Symp on Logic in Computer ScienceSCG: ACM Symp on Computational GeometrySODA: ACM/SIAM Symp on Discrete AlgorithmsSPAA: ACM Symp on Parallel Algorithms and ArchitecturesPODC: ACM Symp on Principles of Distributed ComputingISSAC: Intl. Symp on Symbolic and Algebraic ComputationCRYPTO: Advances in CryptologyEUROCRYPT: European Conf on CryptographyRank 2:CONCUR: International Conference on Concurrency TheoryICALP: Intl Colloquium on Automata, Languages and ProgSTACS: Symp on Theoretical Aspects of Computer ScienceCC: IEEE Symp on Computational ComplexityWADS: Workshop on Algorithms and Data StructuresMFCS: Mathematical Foundations of Computer ScienceSWAT: Scandinavian Workshop on Algorithm TheoryESA: European Symp on AlgorithmsIPCO: MPS Conf on integer programming & comb optimization LFCS: Logical Foundations of Computer ScienceALT: Algorithmic Learning TheoryEUROCOLT: European Conf on Learning TheoryWDAG: Workshop on Distributed AlgorithmsISTCS: Israel Symp on Theory of Computing and SystemsISAAC: Intl Symp on Algorithms and ComputationFST&TCS: Foundations of S/W Tech & Theoretical CSLATIN: Intl Symp on Latin American Theoretical Informatics RECOMB: Annual Intl Conf on Comp Molecular BiologyCADE: Conf on Automated DeductionIEEEIT: IEEE Symposium on Information TheoryAsiacryptRank 3:MEGA: Methods Effectives en Geometrie AlgebriqueASIAN: Asian Computing Science ConfCCCG: Canadian Conf on Computational GeometryFCT: Fundamentals of Computation TheoryWG: Workshop on Graph TheoryCIAC: Italian Conf on Algorithms and ComplexityICCI: Advances in Computing and InformationAWTI: Argentine Workshop on Theoretical InformaticsCATS: The Australian Theory SympCOCOON: Annual Intl Computing and Combinatorics ConfUMC: Unconventional Models of ComputationMCU: Universal Machines and ComputationsGD: Graph DrawingSIROCCO: Structural Info & Communication ComplexityALEX: Algorithms and ExperimentsALG: ENGG Workshop on Algorithm EngineeringLPMA: Intl Workshop on Logic Programming and Multi-AgentsEWLR: European Workshop on Learning RobotsCITB: Complexity & info-theoretic approaches to biologyFTP: Intl Workshop on First-Order Theorem Proving (FTP)CSL: Annual Conf on Computer Science Logic (CSL)AAAAECC: Conf On Applied Algebra, Algebraic Algms & ECCDMTCS: Intl Conf on Disc Math and TCSUn-ranked:Information Theory WorkshopAREA: Data BasesRank 1:SIGMOD: ACM SIGMOD Conf on Management of DataPODS: ACM SIGMOD Conf on Principles of DB SystemsVLDB: Very Large Data BasesICDE: Intl Conf on Data EngineeringICDT: Intl Conf on Database TheoryRank 2:SSD: Intl Symp on Large Spatial DatabasesDEXA: Database and Expert System ApplicationsFODO: Intl Conf on Foundation on Data OrganizationEDBT: Extending DB TechnologyDOOD: Deductive and Object-Oriented DatabasesDASFAA: Database Systems for Advanced ApplicationsCIKM: Intl. Conf on Information and Knowledge ManagementSSDBM: Intl Conf on Scientific and Statistical DB MgmtCoopIS - Conference on Cooperative Information SystemsER - Intl Conf on Conceptual Modeling (ER)Rank 3:COMAD: Intl Conf on Management of DataBNCOD: British National Conference on DatabasesADC: Australasian Database ConferenceADBIS: Symposium on Advances in DB and Information Systems DaWaK - Data Warehousing and Knowledge DiscoveryRIDE WorkshopIFIP-DS: IFIP-DS ConferenceIFIP-DBSEC - IFIP Workshop on Database SecurityNGDB: Intl Symp on Next Generation DB Systems and AppsADTI: Intl Symp on Advanced DB Technologies and IntegrationFEWFDB: Far East Workshop on Future DB SystemsMDM - Int. Conf. on Mobile Data Access/Management (MDA/MDM) ICDM - IEEE International Conference on Data MiningVDB - Visual Database SystemsIDEAS - International Database Engineering and Application SymposiumOthers:ARTDB - Active and Real-Time Database SystemsCODAS: Intl Symp on Cooperative DB Systems for Adv AppsDBPL - Workshop on Database Programming LanguagesEFIS/EFDBS - Engineering Federated Information (Database) SystemsKRDB - Knowledge Representation Meets DatabasesNDB - National Database Conference (China)NLDB - Applications of Natural Language to Data BasesKDDMBD - Knowledge Discovery and Data Mining in Biological Databases Meeting FQAS - Flexible Query-Answering SystemsIDC(W) - International Database Conference (HK CS)RTDB - Workshop on Real-Time DatabasesSBBD: Brazilian Symposium on DatabasesWebDB - International Workshop on the Web and DatabasesWAIM: Interational Conference on Web Age Information Management(1) DASWIS - Data Semantics in Web Information Systems(1) DMDW - Design and Management of Data Warehouses(1) DOLAP - International Workshop on Data Warehousing and OLAP(1) DMKD - Workshop on Research Issues in Data Mining and Knowledge Discovery(1) KDEX - Knowledge and Data Engineering Exchange Workshop(1) NRDM - Workshop on Network-Related Data Management(1) MobiDE - Workshop on Data Engineering for Wireless and Mobile Access(1) MDDS - Mobility in Databases and Distributed Systems(1) MEWS - Mining for Enhanced Web Search(1) TAKMA - Theory and Applications of Knowledge MAnagement(1) WIDM: International Workshop on Web Information and Data Management(1) W2GIS - International Workshop on Web and Wireless Geographical Information Systems* CDB - Constraint Databases and Applications* DTVE - Workshop on Database Technology for Virtual Enterprises* IWDOM - International Workshop on Distributed Object Management* IW-MMDBMS - Int. Workshop on Multi-Media Data Base Management Systems* OODBS - Workshop on Object-Oriented Database Systems* PDIS: Parallel and Distributed Information SystemsAREA: MiscellaneousRank 1:Rank 2:AMIA: American Medical Informatics Annual Fall SymposiumDNA: Meeting on DNA Based ComputersRank 3:MEDINFO: World Congress on Medical InformaticsInternational Conference on Sequences and their ApplicationsECAIM: European Conf on AI in MedicineAPAMI: Asia Pacific Assoc for Medical Informatics ConfSAC: ACM/SIGAPP Symposium on Applied ComputingICSC: Internal Computer Science ConferenceISCIS: Intl Symp on Computer and Information SciencesICSC2: International Computer Symposium ConferenceICCE: Intl Conf on Comps in EduEd-MediaWCC: World Computing CongressPATAT: Practice and Theory of Automated TimetablingNot Encouraged (NO INTENTION TO OFFEND THESE ORGANIZERS):International Multiconferences in Computer ScienceSCI: World Multi confs on systemics, sybernetics and informaticsSSGRR: International conf on Advances in Infrastructure for e-B, e-Edu and e-Science and e-MedicineIASTED conferences。
高等美术教育048 / INDUSTRIAL DESIGN 工业设计基于OBE 教育理念的《数字媒体视觉设计》课程教学改革探究RESEARCH ON TEACHING REFORM OF "DIGITAL MEDIA VISUAL DESIGN" COURSE BASED ON OBE EDUCATIONAL CONCEPT桂林电子科技大学 李润润业后一段时间内应达到的能力及其发展水平有明确的预估,然后设计出适宜的教育课程体系和实践环节来保障学生达到这些预期的能力目标。
成果导向教育主要重视的是学生在学习过程中的自主学习能力,不是让学生进行被动听课,要在课程中养成独立思考的能力。
因此,为了适应成果导向教育的要求,至少要实现如图1所示的五个转变。
2《数字媒体视觉设计》课程的存在问题《数字媒体视觉设计》课程融合了数字媒体的理论知识以及视觉传达的设计方法,涉及知识面较广,而现有的教学模式难以帮助学生掌握本课程的知识以及获得较强的专业技能。
《数字媒体视觉设计》在教学过程中凸显出来的问题主要为以下几方面。
2.1教学目标不明确教学目标包括课程培养目标、课堂教学目标以及教育成才目标。
目前《数字媒体视觉设计》课程教学目标没有以学生为中心,并缺乏对学生德育方面的培养教育。
在实际的教学过程中学生在学习课程前对课程没有整体了解,学习目标不明确,学生在课堂学习的过程中常常处于被听课的状态,不清楚自己掌握了哪些有效的知识点,更不清楚自己有哪些欠缺,导致上课注意力不能集中,学习独立性差。
2.2课程实践实用性不强《数字媒体视觉设计》课程在授课过程中的实践环节,学生往往还是停留在表面理解部分,没有将实际调研分析的结果具体与设计相结合,对于设计的具体内容也还是停留在表面的视觉设计上,没有深入的探究用户的使用心理,站在用户的角度考虑问题,这将导致学生未来在工作岗位上也无法胜任实际的设计工作。
2.3考核方式单一在考核方式上,《数字媒体视觉设计》课程对于学生的评价标准以结果为主要依据,学生能力参差不齐,采用单一的考核标在高校的课程体系建设过程中,为适应社会对于应用型人才的需求,高校开始更加注重学生在本科阶段实践应用能力的培养,也开始重视对OBE 工程教育模式的研究和应用[1]。
TMX-xxxxSDI2 Series High Definition Digital Video Tracking Matrix SwitcherInstallation and Operation ManualV 1.1Remark:⏹All rights reserved for translation, reprint or reproduction⏹Contents may change without prior announcement⏹All technical specifications are guideline data and not guaranteed features⏹Taiden Co., Ltd. is not responsible for any damage caused by improper use of this manual⏹The equipment must be connected to earth!⏹This product conforms to the rules of the European directive 2014/30/EU.⏹If any detailed information needed, please contact your local agent or TAIDEN service center in your region.Any feedback, advice and suggestion about the products is appreciated⏹TAIDEN is the registered trademark of TAIDEN Co., Ltd.1. Read and keep these instructions.2. Heed all warnings and follow all instructions.3. The apparatus shall not be exposed to dripping orsplashing and that no objects filled with liquids, suchas vases, shall be placed on the apparatus.4. The MAINS plug serving as a disconnection device,should be easy to operate.5. The apparatus should be connected to the MAINSsocket-outlet with protective earth.6. Clean only with dry cloth.7. Do not block any ventilation openings. Install inaccordance with the manufacturer’s instructions.8. Do not install near any heat sources such as radiators,heat registers, stoves, or other apparatus (includingamplifiers) that produce heat.9. Do not defeat the safety purpose of the polarized orgrounding-type plug. A polarized plug has two bladeswith one wider than the other. A grounding type plughas two blades and a third grounding prong. The wideblade and the third prong are provided for your safety.If the provided plug does not fit into your outlet,consult an electrician for replacement of the obsoleteoutlet.10. Protect the power cord from being walked on orpinched particularly at plugs, convenience receptacles, and the point where they exit from theapparatus.11. Only use attachments/accessories specified by themanufacturer.12. Use only with the cart, stand, tripod, bracket, or tablespecified by the manufacturer, or sold with theapparatus. When a cart is used, use caution whenmoving the cart/apparatus combination to avoid injuryfrom tip-over.13. Unplug this apparatus during lightning storms orwhen unused for long periods of time.14. Refer all servicing to qualified service personnel.Servicing is required when the apparatus has beendamaged in any way, such as power-supply cord orplug is damaged, liquid has been spilled or objectshave fallen into the apparatus, the apparatus hasbeen exposed to rain or moisture, does not operatenormally, or has been dropped. 15. Do not place the equipment on any uneven orunstable stand; original product package or appropriate package should be used to avoid damagecaused by strong impacts during transportation.16. Power supply cords:AC 100 V-240 V 50 Hz/ 60 Hz17. The quantity of connected units in one system shouldnot exceed prescribed quantity. For service, pleasecontact the nearest TAIDEN Service Center.18. Use ONLY specified connection cable to connect thesystem equipment.19. All TAIDEN products are guaranteed for definite time(see the WARRANTY CARD for details) excluding thefollowing cases:A. All damage or malfunction caused by humannegligence;B. Damage or malfunction caused by improperoperating by operator;C. Parts damage or loss caused by disassemblingthe product by non-authorized personnel.20. Upon receipt of the product, please fill out theWarranty Card enclosed and post it to TAIDENService Center nearby in your region.The lightning flash with an arrowhead symbol, withan equilateral triangle, is intended to alert the userto the presence of uninsulated ‘dangerous voltage’within the products enclosure that may be ofsufficient magnitude to constitute a risk of electricshock to persons.The exclamation mark within an equilateral triangle is intended to alert the user to the presence of important operating and maintenance (servicing) instructions in the literature accompanying the appliance.Attention: Installation should be performed by qualified service personnel only in accordance with the National Electrical or applicable local codes.Power Disconnect: Units with or without ON – OFF switch have power supplied to the unit whenever the power cord is inserted into the power source; however, the unit is operational only when the ON – OFF switch is in the ON position. The power cord is the main power disconnect for all unitsContentsInstallation & User Guide (V)Chapter 1. High Definition Digital Video Tracking Matrix Switchers (1)1.1 Functions and indications (1)1.2 Installation and connection (2)1.2.1 Installation (2)1.2.2 Connection with control devices (2)1.2.3 Connection with input, output devices (2)1.3 Setup and Operation (4)1.3.1 Menu setup (4)1.3.2 Switch operation (7)Chapter 2. IR Remote Control (10)Chapter 3. Communication protocol and control code (11)Chapter 4. Technical data (13)Installation & User GuideAbout this manualThis manual is a comprehensive guide to the installation and operation of TAIDEN SDI Series High Definition Digital Video Tracking Matrix Switchers. It includes: connection and operation, protocol and control code, etc.The manual is divided into the following chapters:Chapter 1: High Definition Digital Video TrackingMatrix SwitchersDescriptions in detail of the functions and indications, installation and connection, configuration and operation of High Definition Digital Video Tracking Matrix Switchers.Chapter 2: IR Remote ControlIntroduction into the operation of IR remote control.Chapter 3: Communication protocol and control codeDetailed description of codes and their function.Chapter 4: Technical dataMechanical and electrical details of the High Definition Digital Video Tracking Matrix Switchers. This manual is applicable to:TMX-1608SDI216×8 High Definition Digital Video Tracking Matrix Switcher (SD/HD/3G)TMX-1604SDI216×4 High Definition Digital Video Tracking Matrix Switcher (SD/HD/3G)TMX-0808SDI28×8 High Definition Digital Video Tracking Matrix Switcher (SD/HD/3G)TMX-0804SDI28×4 High Definition Digital Video Tracking Matrix Switcher (SD/HD/3G)TMX-0404SDI24×4 High Definition Digital Video Tracking Matrix Switcher (SD/HD/3G)Chapter 1. High Definition Digital Video Tracking Matrix SwitchersFigure 1.1 Panels of SDI Matrix SwitcherFront panel:1. “MENU” buttona) If in current state, press “MENU” go to main menu;b) If in menu state, press “MENU” go to sub menu;c) Select/Deselect in network configuration. 2. “⇦” (Left) button 3. “⇨” (Right) button 4. “Exit” buttonReturn to previous directory or root. 5. IR receiving windowReceives the IR signals from remote control; make sure the remote control aims at the window.6. “NETWORK” indicatorIndicator flashes if Matrix Switcher is communicating with conference main unit. 7. “ACTIVE” indicatorIndicator will be turned on if Matrix Switcher executes switch instructions. 8. “POWER” indicator 9. LCDRear panel:10. RJ45 interface11. RS-422/TAINET interfaceRS-422 for connecting to dome camera; TAINET for connecting to VIDEO SWITCH of main unit.12. USB interface for upgrade 13. Video inputs 14. Video outputs15. Grounding point 16. Power cable interface 17. RS-422/232 interfaceRS-422 for connecting to dome camera; RS-232 for connecting to keyboard (Baud rate:9600).18. Control interface COM11.2.1 Installation1U High Definition Digital Video Tracking Matrix Switcher just needs to put it into the cabinet, and fix itby screws. As figure 1.2.Figure 1.2 Installation1.2.2 Connection with control devicesHigh Definition Digital Video Tracking Matrix Switcher can be can be controlled by Central Control System via RS-232 interface COM1. It also offers a USB interface used for software upgrade. As figure 1.3.1.2.3 Connection with input, output devices High Definition Digital Video Tracking Matrix Switcher supports various digital video signal sources, including: full HD (3G), HD and SD. As figure 1.3.Please use good quality Twisted Pair cable to connect input and output device, i.e. RG59 and RG60.Control Interface:Control TypeCOM (RS-232)9 pin female D connector COM1 Baud rate: 115200, data: 8 bits,stop: 1 bit, no parity check bitRJ45TCP/IPTAINETBaud rate: 19200, to TO VIDEOSWITCHER of main unit RS-422 Baud rate: 9600, to domecamera RS-232Baud rate: 9600, to keyboardFigure 1.3 Connection for input and output devices1.3.1 Menu setup 1.3.1.1 Menu setupTo explain menu setup of SDI series Matrix Switcher, TMX-1608SDI2 serves as example.TMX-1608SDI2 main interface:Press“MENU” to enter main menu and press “⇦/⇨” until “Setting” prompts; Press “MENU” again to enter setup menu, including: 1. Ring 2. Video Track 3. Video Track Type 4. Video Track DelayPress “EXIT” to exit menu.Menu 1 to menu 4 are explained explicitly: 1. RingBuzzer ring on-off of this unit. If buzzer ring is setup “on”, the buzzer will ring when front panel operation or IR remote control. The buzzer ring can be setup “off”. ✷ ON: buzzer is on ; ✷OFF: buzzer is off.to enter setup menu andpress “⇦/⇨” until “Setting” prompts;2. Press “MENU” and press “⇦/⇨” until “Ring”3. Press “MENU” to enter setup;4. Press “⇦/⇨” to select parameter;5. Press “MENU” to confirm.2. Video TrackSelect the function of video track on or off.3、Video Track TypeWhen Video Track is on, camera protocol can be selected from HCS-3316RS232/ HCS-3316RS485/ HUAWEI VPC620/ SONY HD1/ PELCO D/ PELCO P1/ PELCO P2/ SONY D70/ SONY D100/ SONY BRC-Z330/ SONY BRC300/ SONY BRC700. Please select correct protocol according to actual device type.The maximal number of cameras that can be connected to the HD Digital Video Tracking MatrixSwitcher is shown in follow:Protocol predefined position Camera No. TotalTMX-16xxSDI2 PELCO-D 64 161024PELCO-P 64161024 VISCA 6414896TMX-08xxSDI2PELCO-D 64 8512PELCO-P 648512 VISCA 647448TMX-04xxSDI2 PELCO-D 64 4 256 PELCO-P 64 4 256 VISCA 6442561. Press “MENU” and press “⇦/⇨” until “Setting” prompts;2. Press “MENU” and press “⇦/⇨” until “Video Track Type” prompts;3. Press “MENU” to enter setup;4. Press “⇦/⇨” to select parameter;5. Press “MENU” to confirm.1. Press “MENU” and press “⇦/⇨” until“Setting” prompts;and press “⇦/⇨” until“Video Track” prompts;3. Press “MENU” to enter setup;/⇨” to adjust parameter;5. Press “MENU” to confirm.4. Video Track DelayThe interval ranges from 0 second to 8 seconds by steps of 0.5 seconds.1. Press “MENU” and press “⇦/⇨” until“Setting” prompts;2. Press “MENU”and press “⇦/⇨” until3. Press “MENU” to enter setup;4. Press “⇦/⇨” to adjust parameter;5. Press “MENU” to confirm.1.3.2 Switch operationTo explain menu operation of SDI series Matrix Switcher, TMX-1608SDI2 type serves as example. All SDI series Matrix Switcher can refer to it.TMX-1608SDI2 main interface:Press “MENU” to enter switch menu, including: 1. Switch Video 2. Switch Through* Switch through one channel or all channels. 3. Close* Close one output or all outputs. 4. Setting * Setup menu. 5. Status* Request channel state. 6. Net SettingMenu 1 to menu 6 are explained explicitly:1. Switch VideoVideo switch key, switches one input video signal to any or all output channels.Example: Switch Video signal of input channel 1 tooutput channel 82. Switch ThroughSwitch through one input channel or all input channels to corresponding output channel(s).Example: Switch through channel 2. 1. Press “⇦/⇨” to select “Switch Video”;2. Press “MENU” to select input channel;3. Press “⇦/⇨” to adjust input channel as “1” and press “MENU” to confirm;4. Press “⇨” and press “⇦/⇨” to adjust output5. Press “MENU” to confirm and press “EXIT” to switch;3. CloseClose one output channel or all output channels.Example: Close output channel 2.4. SettingSetup menu (refer to section 1.3.1 for details).5. StatusRequest corresponding state of input and output channels.1. Press “MENU” and press “⇦/⇨” until “Setting” prompts;2. Press “MENU” to enter setup status.1. Press “MENU” and press “⇦/⇨” until2. Press “MENU” to request correspondingstatus;3. Press “⇦/⇨” to request next status.⇦/⇨” until 2. Press “MENU” to enter “Close ”menu; 3. Press “⇦/⇨” to select channel “2”; to switch;/⇨” to select “Switch through” prompts;⇦/⇨” to select channel “2”;6. Net SettingSet up the IP address, Subnet mask, Gateway and Host IP .Example: set the IP address as 192.168.2.219.1. Press “MENU” and press “⇦/⇨” until “NetSetting”;2. Press “MENU” to enter and press “⇦/⇨” to3. Press “⇦/⇨” to select the parameter andpress “MENU” to enter;/⇨” to adjust the parameter andChapter 2. IR Remote ControlChapter 3. Communication protocol and control codeThis code system is used for controlling and operating TAIDEN professional Matrix Switchers by central control system or user programming software.Protocol: Baud Rate: 115200; Data: 8 bits; Stop: 1 bit; Parity Check Bit: No. UDP port: 1600.TypeCodeDescriptionOperation Code [x1]All. Input channel [x1] switch to all output channelsAll#. Setup all channels one-to-one correspondence: 1->1, 2->2, 3->3… All$. Close all channels (Audio & Video)[x1]#. Input channel [x1] switch to output channel [x1] (Audio & Video) [x1]$. Close output channel [x1] (Audio & Video)[x1]V[x2]. Video of input channel [x1] switch to output channel [x2] (Video) [x1]A[x2]. Audio of input channel [x1] switch to output channel [x2] (Audio)[x1]B[x2]. Video and audio of input channel [x1] switch to output channel [x2] (Audio & Video)Save[X]. Save current status to scene [X] (X: 0 ~ 9) Recall[X]. Recall scene [X] (X: 0 ~ 9)Clear[X]. Clear scene [X], status of all output channel are closed (X: 0 ~ 9) Type*. Query the matrix type Version. Query the matrix versionStatus[x]. Query the input status of the output channel [x] Status. Query the input status of all output channels Default. Factory reset Demo. Work in demo modeUndo.Cancel the current operation and return to the last switch statusCamera%2d%2d%2d.Camera control%2d: camera ID (01 to 16)%2d: type (00 stop, 01 right, 02 left, 03 up, 04 down, 05 far, 06 near) %2d: speed control (01 slow, 02 fast)SetPreset%2d%2d.Predefine position settings%2d: camera ID (01 to 16) %2d: predefine position (01 to 64)CallPreset%2d%2d.Predefine position recall%2d: camera ID (01 to 16) %2d: predefine position (01 to 64)Command examples:1. [x1]All.For example: Input channel 3 switch to all output channels, code is “3All.”.2. All#.Setup all channels one-to-one correspondence: 1->1, 2->2, 3->3…8->8.3. All$.Close all output channels.4. [x]#.For example: Input channel 5 switch to output channel 5, code is “5#.”.5. [x]$.For example: Close output channel 5, code is “5$.”.6. [x1]V[x2].For example: Video of input channel 3 switch to output channel 5, code is “3V5.”. Video of input channel 3 switch to output channel 8, 9, 12, code is “3V8,9,12.”.7. [x1]B[x2].For example: Video and audio of input channel 1 switch to output channel 2, 3, 5, code is “1B2,3,5.”.8. Save[x].For example: Save current status to scene 7, code is “Save7.”.9. Recall[x].For example: Recall scene 5, code is “Recall5.”.Chapter 4. Technical dataCopyright by TAIDEN Last Revision: 07/2019 TAIDEN INDUSTRIAL CO., LTD.6/F, Block B, Future Plaza, 6060 Qiaoxiang Rd, Nanshan District, Shenzhen,China P .C.: 518053Website: Rhox Áudio e Vídeo Profissional - SIBS Quadra 2 conjunto C Lote 12Brasília - DF - 71736.203 - Tel (61) 3051-5800 https://.br。
CHAPTER22DIGITAL VIDEO PROCESSING TECHNIQUES AND APPLICA TIONSWHAT WILL WE LEARN?•What is motion estimation(ME)and why is it relevant?•Which techniques and algorithms can be used to estimate motion within a video sequence?•Which techniques can be used tofilter a video sequence?•What is the role of motion compensation(MC)in videofiltering?22.1FUNDAMENTALS OF MOTION ESTIMATION AND MOTION COMPENSATIONMotion is an essential aspect of video sequences.The ability to estimate,analyze,and compensate for relative motion is a common requirement of many video processing, analysis and compression algorithms and techniques.In this section,we present the fundamental concepts associated with motion estimation and compensation.Motion estimation is the process of analyzing successive frames in a video sequence to identify objects that are in motion.The motion of an object is usually described by a two-dimensional(2D)motion vector(MV),which encodes the length and direction of motion.Practical Image and Video Processing Using MATLAB®.By Oge Marques.©2011John Wiley&Sons,Inc.Published2011by John Wiley&Sons,Inc.561562DIGIT AL VIDEO PROCESSING TECHNIQUES AND APPLICATIONSFIGURE22.1Two frames at different time instants(t1and t1+ t)and the resulting optical flow.Redrawn from[SHB08].Many two-dimensional motion estimation algorithms are based on the concept of opticalflow,which can be defined as the pattern of apparent motion of objects, surfaces,and edges in a visual scene.The opticalflow—and consequently the apparent motion—can be computed by measuring variations(i.e.,gradients)of intensity values over time.The resulting pattern is a vectorfield—known as the opticalflowfield—containing the motion vectors for each support region(e.g.,pixel,block,or region) in the frame,representing the best approximation of the3D motion of object points across the2D frame.Figure22.1shows a schematic example of two consecutive frames and the resulting opticalflow.Opticalflow computations1are based on two assumptions[SHB08]:1.The observed brightness of an object is constant over time.This is referred toas the constant intensity assumption.2.Points that are spatially close to one another in the image plane tend to movein a similar manner(the velocity smoothness constraint).The two-dimensional motion estimation techniques aim at encoding motion infor-mation from intensity and color values obtained from the frames in a video sequence. This is a complex problem for many reasons,such as the following:•The actual scene is three dimensional(and so are the objects in it),but2D motion estimation algorithms have access only to a2D representation of it.Consequently,these algorithms must rely on the apparent motion of the objects relative to the frame,which does not always correspond to true motion in the original scene.There are many cases in which actual object motion would go undetected or—conversely—a2D motion estimation algorithm would estimate motion where none existed.An example of the former would be a sphere rotating on its own1The complete mathematical formulation of opticalflow methods is beyond the scope of this text.Refer to“Learn More About It”section at the end of the chapter for references.FUNDAMENT ALS OF MOTION ESTIMA TION AND MOTION COMPENSA TION563 axis.The latter problem can arise as a result of lighting variations,distractingobjects,or many other scenarios.•We can speak of motion only in relative terms,that is,by measuring how camera (or observer),objects of interest,and background move relatively to one another.There are six general cases to consider:1.Still camera,single moving object,constant background.2.Still camera,several moving objects,constant background.3.Still camera,single moving object,moving(cluttered)background.4.Still camera,several moving objects,moving(cluttered)background.5.Moving camera,fixed object(s),constant background.6.Moving camera,several moving objects,moving(cluttered)back-ground.Most motion estimation algorithms in use today can handle thefirst two cases rather easily.There is a significant amount of ongoing work on cases where the background is complex and contains motion(e.g.,wavering tree branches, light reflected on the ocean,etc.).Thefifth case is usually treated as a separate problem,for which the goal is to determine the type and amount of camera movement.Finally,the sixth category is beyond the reach of contemporary computer vision solutions.•There is an inherent ambiguity in the process of estimating motion based on edges of objects within the frame,which is known in the vision literature as the aperture problem,illustrated in Figure22.2.If we view the image through a small circular aperture,we cannot tell exactly where a point(x i,y i)on an edge moves to.Opticalflow-based ME algorithms usually rely on the motion vector perpendicular to the edge(indicated as u n),suggesting that the edge has moved up and to the right in this case.Clearly,it is possible that the actual motion wasFIGURE22.2The aperture problem.564DIGIT AL VIDEO PROCESSING TECHNIQUES AND APPLICATIONS different—from purely up(indicated as u)to purely to the right—but there is noway to know it for sure.•ME algorithms must work at a level of granularity that is appropriate to the task at hand.Representing a MV for each pixel is usually not a good idea,and neither is using a single MV for the entire frame.Many algorithmsfind a compromise between these two extreme cases,by working with nonoverlapping blocks.•In many cases(e.g.,object tracking applications),we might be interested in computing the motion of objects in the scene,which presupposes that they can be accessed as individual entities.This increases the complexity of the overall solution,since it would require(accurate)object segmentation before the ME calculations.•ME methods strongly depend on the intended application.For example,in video compression applications,the main goal of ME algorithms is to generate mo-tion vectors that allow a decoder to re-create a frame based on the motion-compensated differences between the current frame and a previously decoded frame,while saving bits in the process.In motion-compensated standards conver-sion,on the other hand,the goal is to align the interpolation axis to the direction of motion of objects across multiple frames,and therefore reduce artifacts such as judder.Motion compensation is the process by which the results of the motion estimation algorithms(usually encoded in the form of motion vectors)are employed to improve the performance of video processing algorithms.In its simplest case(e.g.,a linear camera motion such as panning),motion compensation computes where an object of interest will be in an intermediate targetfield/frame and then shifts the object to that position in each of the sourcefields/frames.In more general cases,the results of the motion estimation algorithm(i.e.,the motion vectors)are used to create the equivalent of interpolation axes,aligned with the trajectory of each moving object(Figure22.3).This causes a significant reduc-tion in motion and temporal aliasing and has a dramatic positive effect on the output of motion-compensated algorithms for tasks such as interframefiltering(see Sec-tion22.4.2),de-interlacing(see Section21.3.1),and standards conversion(see Sec-tion21.3),among many others.The overall performance of the motion-compensated video processing algorithms is determined primarily by the accuracy of the motion vectors,which underscores the importance of the motion estimation stage,which is described in more detail in the following sections.22.2GENERAL METHODOLOGIES IN MOTION ESTIMATIONThe2D motion estimation techniques described in this chapter address the problem of estimating the motion between two frames:f(x,y,t1),which will be called the anchor frame,and f(x,y,t2),which will be referred to as the target frame.The anchor frame may be either before or after the target frame in time.We will call it forwardGENERAL METHODOLOGIES IN MOTION ESTIMA TION565FIGURE22.3Motion compensation:interpolation axes are aligned with each moving object. Redrawn from[Wat94b].FIGURE22.4Anchor and target frames in forward and backward motion estimation. motion estimation the case where t2>t1and backward motion estimation the case where t1>t2.A motion vector d(x)=[d x d y]T will represent the displacement of a particular point x=(x i,y i)between time t1and t2.Figure22.4illustrates these concepts and associated notation.There are two main categories of ME approaches:•Feature-Based Methods:Establish a correspondence between pairs of selected feature points in the two frames and attempt tofit them into a motion model using methods such as least-squaresfitting.Feature-based methods are more often used in applications such as object tracking and3D reconstruction from 2D video.566DIGIT AL VIDEO PROCESSING TECHNIQUES AND APPLICATIONS •Intensity-Based Methods:Rely on the constant intensity assumption described earlier and approach the motion estimation problem from the perspective of an optimization problem,for which three key questions must be answered:–How to represent the motionfield?–Which criteria to use to estimate motion parameters?–How to search for optimal motion parameters?This section focuses exclusively on intensity-based methods.The answers to the three questions above will appear in Sections22.2.1–22.2.3,respectively.22.2.1Motion RepresentationMotion representation methods vary in terms of the size(and shape)of the region of support,which can vary among the following four types(illustrated in Figure22.5):1.Global:In this case,the region of support is the entire frame and a single mo-tion model applies to all points within the frame.This is the most constrained motion model,but it is also the one that requires fewest parameters to estimate.Global motion representation is often used to estimate camera-induced mo-tion,that is,apparent motion caused by camera operations such as pan,zoom, or tilt.FIGURE22.5Motion estimation methods:(a)global;(b)pixel-based;(c)block-based;(d)object-based.GENERAL METHODOLOGIES IN MOTION ESTIMA TION5672.Pixel-Based:This model produces the densest possible motionfield,with oneMV per pixel,representing the2D displacement of that point across successive frames.A smoothness constraint between adjacent MVs is often employed to ensure a more coherent motion representation.The computational complexity of pixel-based methods is high,due to the enormous number of values(twice the number of pixels in the frame)that need to be estimated.3.Block-Based:In this case,the entire frame is divided into nonoverlappingblocks,and the problem is reduced tofinding the MV that best represent the motion associated with each block.This model is widely used in video com-pression standards such as H.261,H.263,MPEG-1,and MPEG-2.4.Region-Based:In this model,the entire frame is divided into irregularly shapedregions,with each region corresponding to an object or subobject with consis-tent motion,which can be represented by a few parameters.It is used in the MPEG-4standard.22.2.2Motion Estimation CriteriaOnce a model and region of support have been chosen,the problem shifts to the esti-mation of the model parameters.One of the most popular motion estimation criteria—and the only one described in this book—is based on the displaced frame difference (DFD).It consists in computing the differences in intensity between every point in the anchor frame and the corresponding point in the target frame.Mathematically, the objective function can be written asE DFD(d)=(f2(x+d)−f1(x))p(22.1)x∈Rwhere f1(x)is the pixel value at x in time t1,f2(x+d)is the pixel value at(x+d) in time t2,d is the estimated displacement,and R is the region of support.When p=1,the error E DFD(d)is called the mean absolute difference(MAD), and when p=2,it is called the mean squared error(MSE).22.2.3Optimization MethodsThe error functions described by equation(22.1)can be minimized using different methods.The three most common optimization methods are as follows:•Exhaustive Search:As the name suggests,this method searches through all pos-sible parameter value combinations and is guaranteed to reach the global optimal at the expense of significant computational cost.It is typically used in conjunc-tion with the MAD criterion described earlier.•Gradient-Based Search:Uses numerical methods for gradient calculation and reaches the local optimal point closest to the initial solution.It is typically used in conjunction with the MSE criterion described earlier.568DIGIT AL VIDEO PROCESSING TECHNIQUES AND APPLICATIONS •Multiresolution Search:This method searches the motion parameters starting at a coarse resolution and propagating the partial solutions tofiner resolutions, which can then be successively refined.It is a good trade-off between speed(i.e., it is faster than exhaustive search)and does not suffer from the problem of being trapped into a local minimum(as the gradient-based method does).22.3MOTION ESTIMATION ALGORITHMSIn this section,we present a selected subset of block-based ME algorithms.These algorithms assume that a frame has been divided into M nonoverlapping blocks that together cover the entire frame.Moreover,the motion in each block is assumed to be constant,that is,it is assumed that the entire block undergoes a translation that can be encoded in the associated motion vector.The problem of block-based ME algorithms is tofind the best MV for each block.These algorithms are also called block matching algorithms(BMA).22.3.1Exhaustive Search Block Matching AlgorithmThe exhaustive search block matching algorithm(EBMA)(Figure22.6)works as follows:for each block B m in the anchor frame,it searches all candidate blocks (within a certain range)B m in the target frame,and selects the one with the minimum error,that is,the one that optimizes a cost function such as MAD.The search range is indicated in Figure22.6by R x and R y.The estimation accuracy of the EBMA method is determined by the step size for the block displacements.In the simplest case,the step size is one pixel,and the process is known as integer-pixel accuracy search.For more accurate motionFIGURE22.6Exhaustive search block matching algorithm(EBMA).MOTION ESTIMA TION ALGORITHMS569FIGURE22.7Block matching with half-pixel accuracy.The MV in this case is(1,1.5). Redrawn from[WOZ02].representation,half-pixel accuracy search is often used.In order to achieve subpixel accuracy,the target frame must be up-sampled(with the proper interpolation method, usually bilinear interpolation)by the proper factor.Figure22.7illustrates the process of block matching using half-pixel accuracy.In thisfigure,solid circles correspond to samples that exist in the original target frame,whereas hollow circles correspond to interpolated samples.In Tutorial22.1(page579),you will learn how to perform motion estimation using the EBMA method(using both full-pixel and half-pixel accuracy)in MATLAB.The EBMA algorithm has several weaknesses:•It causes a blocking artifact(noticeable discontinuity across block boundaries) in the predicted frame.•The resulting motionfield can be somewhat chaotic because MVs are indepen-dently estimated from block to block.•Flat regions are more likely to produce wrong MVs because motion is inde-terminate when spatial gradient is near zero(a problem shared by all optical flow-based methods).EXAMPLE22.1Figure22.8shows the full-pixel EBMA algorithm at work.Parts(a)and(b)show the target and anchor frame,respectively.Part(c)shows the motionfield,which exemplifies the last two limitations described earlier.Finally,part(d)shows a recon-structed frame,that is,a frame obtained by computing the estimated motion applied to the target frame.Ideally,part(d)should result in a frame identical to the one in570DIGIT AL VIDEO PROCESSING TECHNIQUES AND APPLICATIONSFIGURE22.8EBMA example:(a)target frame;(b)anchor frame;(c)motionfield over-lapped on anchor frame;(d)reconstructed frame.part(b),but this is clearly not the case:the presence of blocking artifacts(besides other imperfections)in the reconstructed frame is clearly visible.22.3.2Fast AlgorithmsThe EBMA algorithm is computationally expensive(and significantly more so if fractional pixel accuracy is used),which motivated the development of several fast algorithms for block matching.The two most popular fast search algorithms are the 2D log and the three-step search methods.They are briefly described next.2D Log Search Method The2D log search method(Figure22.9)starts from the position corresponding to zero displacement and testsfive search points,arranged in a diamond shape.It selects the block that yields minimum error(usually MAD is the chosenfigure of merit)and uses it to form a new search region around it.If the best matching point is the center point,it proceeds with a new search region that has an offset of half the amount of the previous offset;otherwise,the offset remainsMOTION ESTIMA TION ALGORITHMS571FIGURE22.92D log search.In this case,thefinal MV is(−6,2).Redrawn from[MPG85]. the same.The process is repeated for successively smaller ranges,until the offset is equal to1.Three-Step Search Method The three-step search method(Figure22.10)starts from the position corresponding to zero displacement and tests nine search points, with offset p/2,where p is half of the search range in each direction(horizontal or vertical).It selects the block that yields minimum error and uses it to form a new search region around it.The new search region has an offset of half the amount of the previous offset.The process is repeated for successively smaller ranges,until the offset is equal to1.22.3.3Hierarchical Block Matching AlgorithmThe hierarchical block matching algorithm(HBMA)is a multiresolution ME algo-rithm.It works byfirst estimating the motion vectors in a coarse resolution using a low-passfiltered,down-sampled frame pair.It then proceeds to modify and refine the initial solution using successivelyfiner resolutions and proportionally smaller search ranges.The most common approach uses a pyramid structure(Figure22.11) in which the resolution is reduced by half in both dimensions between successive lev-els.The HBMA algorithm strikes a compromise between execution time and quality of results:it has lower computational cost than the EBMA counterpart and produces better quality motion vectors than the fast algorithms described earlier.In Tutorial22.1572DIGIT AL VIDEO PROCESSING TECHNIQUES AND APPLICATIONSFIGURE22.10Three-step search.In this case,thefinal MV is(−6,2).Redrawn from [MPG85].FIGURE22.11Hierarchical block matching algorithm(HBMA)using three levels.Redrawn from[WOZ02].VIDEO ENHANCEMENT AND NOISE REDUCTION573 (page579),you will learn how to perform motion estimation using the HBMA method in MATLAB.22.3.4Phase Correlation MethodThe phase correlation method is a frequency-domain motion estimation technique that uses a normalized cross-correlation function computed in the frequency domain to estimate the relative shift between two blocks(one in the anchor frame,another in the target frame).The basic idea consists in performing spectral analysis on two successivefields and computing the phase differences.These differences undergo a reverse transform,which reveals peaks whose positions correspond to motions betweenfields.pute the discrete Fourier transform(DFT)of each block in the target andanchor frames(which we will denote frames k and k+1).2.Calculate the normalized cross-power spectrum between the resulting DFTsaccording to equation(22.2):C k,k+1=F k+1F∗k|F k+1F∗k|(22.2)where F k and F k+1are the DFT of two blocks at the same spatial location in frames k and k+1and∗denotes the complex conjugate.pute the phase correlation function,PCF(x),defined as the inverse DFTof C k,k+1,as follows:PCF(x)=F−1(C k,k+1)=δ(x+d)(22.3)where d is the displacement vector.4.Locate the peaks of the PCF.The basic algorithm described above,however,has a major limitation.It lacks the ability to tell which peak corresponds to which moving object in the frames. This problem can be resolved by adding a(selective)block matching stage, used to distinguish between valid motion vectors and false alarms.The modi-fied phase correlation method has the following strengths:it is fast,subpixel ac-curate,and amplitude(brightness)independent.In Tutorial22.1(page579),you will learn how to perform motion estimation using the phase correlation method in MATLAB.22.4VIDEO ENHANCEMENT AND NOISE REDUCTIONIn this section,we provide a brief overview of how video sequences can be pro-cessed usingfiltering techniques aimed at enhancing the image quality or reducing noise and other artifacts.The simplest approach consists of applying(spatial-or574DIGIT AL VIDEO PROCESSING TECHNIQUES AND APPLICATIONS frequency-domain)image processing algorithms to each individual frame:this will be called intraframefiltering.Many techniques described in Part I can be used to implement intraframefiltering,such as averagingfilter and its variants,median and weighted medianfilters,or Wienerfilters,to mention but a few.Better results,however,can be obtained by exploiting the contents of adjacent frames with significant redundant information,using video-specific(spatiotempo-ral)algorithms,which will be referred to as interframefiltering(Section22.4.2).In Tutorial22.2(page585),you will experiment with inter-and intraframe videofiltering techniques in MATLAB.22.4.1Noise Reduction in VideoVideo acquisition,transmission,and recording systems are not perfect.Consequently, video sequences may be subject to different types of noise and distortion.For analog video,the most common types are as follows:•Thermal(snow)Noise:Caused by temperature-dependent random signal-level fluctuations in amplifiers or signal attenuation due to rain.The visible effect on the screen resembles a snowstorm.•Composite Triple Beats(CTB):Caused by cumulative effect of third-order inter-modulation products and overdriven amplifiers.Produces graininess and tearing in the horizontal lines of the screen.•Composite Second-Order Beat(CSO):Caused by nonlinearities in the electron-ics.Appears on the screen as graininess texture or diagonal lines over the entire picture.•Single-Frequency Modulation Distortion:Caused by intermodulation products.Its visible effect on the screen consists of horizontal or diagonal bands,broad bands of color variation across the screen.•Impulse Noise(Short Duration and High Energy):Caused by lightning,car starters,industrial machines,and other sources.Produces spots on the screen and sharp click sounds in the audio.•Cochannel Interference:Caused when two pictures are received at the same time from two different TV transmitters at different locations,but which share the same TV channel.The visible effect occurs on the overlap of the unwanted service and is often accompanied by a“venetian blind”effect and distorted sound.•Ghosting:Caused by multiple transmission paths,resulting from signal reflec-tions.The visible effect consists in the appearance of a delayed version of the picture on the screen.For digital video,most of the unwanted artifacts result from side effects of the lossy compression techniques used to store or transmit the video using fewerVIDEO ENHANCEMENT AND NOISE REDUCTION575 bits.These are the main types of artifacts that may be present in digital video sequences:•Block Edge Effect(or Simply Blockiness):Caused by coarse quantization of DCT coefficients in block-based compression schemes(e.g.,M-JPEG and MPEG-1),which result in noticeable intensity discontinuities at the boundaries of adjacent blocks in the decoded frame.•False Edges(or False Contouring):Caused by coarse quantization of amplitude levels.Its visible effect in the frame is the appearance of edges at places wherea smooth intensity transition should occur.•Ringing:Caused by the use of idealfilters.Produces a rippling along high-contrast edges.•Blurring and Color Bleeding:Caused by imperfections in compression algo-rithms.Results in loss of spatial details,running or smearing of color in areas with complex textures or edges.•Mosquito Noise:Caused by imperfections in compression algorithms.Produces fluctuation of luminance/chrominance levels around high-contrast edges or mov-ing video objects.Video sequences,particularly old movies,can also be subject to other types of artifacts,such as the following:•Blotches:Large,uncorrelated,bright or dark spots,typically present infilm material,due to mishandling or aging.•Intensity Flicker:Unnatural temporalfluctuation of frame intensities that do not originate from the original scene.22.4.2Interframe Filtering TechniquesInterframefiltering techniques employ a spatiotemporal support region of size m×n×k,where m and n correspond to the size of a neighborhood in a frame and k denotes the number of frames taken into account.For the special case where m=n=1,the resultingfilter is called a temporalfilter,whereas the case where k=1corresponds to intraframefiltering.Interframefiltering techniques can be motion compensated, motion adaptive,or neither.The simplest interframefiltering technique is the spatiotemporal averagingfilter that consists of an extension of the basic averagingfilter to the spatiotemporal domain.A purely temporal version of the algorithm is known as frame averaging.Frame averaging is based on the fact that averaging multiple observations of essentially the same pixel in different frames eliminates noise while resulting in no loss of spatial image resolution.The amount of noise reduction is proportional to the number of frames used,but so is the amount of blurring.In other words,besides the spatial576DIGIT AL VIDEO PROCESSING TECHNIQUES AND APPLICATIONS blurring of2D averagingfilters,we now have a potential motion blur,due to movement of objects between consecutive frames.There are two solutions to the blurring problem:•Motion-adaptive,edge-preservingfilters,where frame-to-frame motion is treated as“temporal edges.”•Motion-compensatedfilters,involving:low-passfilters that are applied along the motion trajectory of each pixel,as determined by a motion estimation algorithm.Motion-compensatedfilters work under the assumption that the variation of pixel gray levels over any motion trajectory is mainly due to noise.Consequently,noise can be reduced by low-passfiltering over the respective motion trajectory at each pixel.Several motion-compensatedfiltering techniques have been proposed in the literature.They differ according to the following factors:•The motion estimation method.•The support of thefilter,where support is defined as the union of predetermined spatial neighborhoods centered about the pixel(subpixel)locations along the motion trajectory.•Thefilter structure(adaptive versus nonadaptive).The effectiveness of motion-compensatedfilters is strongly related to the accu-racy of the motion estimates.In the ideal case(perfect motion estimation),direct averaging of image intensities along a motion trajectory provides effective noise reduction.In practice,however,motion estimation is hardly ever perfect due to noise and sudden scene changes,as well as changes in illumination and camera views.22.5CASE STUDY:OBJECT SEGMENTATION AND TRACKING IN THE PRESENCE OF COMPLEX BACKGROUNDIn this section,we present an example of object segmentation and tracking using MATLAB and the Image Processing Toolbox(IPT).2Object detection and tracking are essential steps in many practical applications,for example,video surveillance systems.The solution presented in Figure22.12uses an object segmentation algorithm for video sequences with complex background,originally proposed by Socek et al. [SCM+05]and further refined and redesigned by´Culibrk et al.[CMS+06,CMS+07]. The output of the segmentation algorithm is a series of binary images(frames),where background pixels are labeled as0and any foreground objects are labeled as1.The 2The MATLAB code for this example was developed by Jeremy Jacob and can be downloaded from the book web site.。