数据结构2013春季A卷
- 格式:doc
- 大小:95.00 KB
- 文档页数:4

2014年山东春季高考集合部分习题解析
解析:集合M={1},集合N={1,2}则M,N的并集为{1,2}。
所以答案为:C
解析:命题P为:对于任意的x属于实数,都有x的平方大于0,则否P为存在x属于实数使得x的平方小于等于0。
所以答案为:B
解析:由a>0能推出a2 >0,但是a2 >0还有可能a是负数所以a2 >0不能推出a>0。
所以答案为:A
2013年山东春季高考集合部分习题解析
解析:由子集的概念得知N是M的子集,所以答案选C
解析:q是真命题,否q是假命题,所以A不正确;p是假命题,则否p是真命题,与上命题q后依然为真命题,所以B正确;p或上q为真,再否定为假,所以C不正确;p与上q为假命题,所以D不正确。
答案选B
解析:a+c=2b能推出a,b,c是等差数列,a,b,c是等差数列也能推出a+c=2b。
所以答案应该选择C
2012年山东春季高考集合部分习题解析
解析:M在集合U中的补集为{3},所以答案为B
解析:否p为真命题,则p为假命题,p与上q是真命题,说明p,q都是真命题,所以答案为D
咨询QQ:2777621658 YY视频课堂ID:95795536
更多考试要点,高考政策尽在——春季高考微信公众号:。

作业1. 线性表编程作业:1.将顺序表逆置,要求用最少的附加空间。
参考答案#include <stdio.h>#include <malloc.h>#include <process.h>#define LIST_INIT_SIZE 100#define LISTINCREMENT 10#define TRUE 1#define FALSE 0#define OK 1#define ERROR 0#define INFEASIBLE -1#define OVERFLOW -2typedef int Status;typedef int ElemType;typedef struct{ ElemType *elem;int length;int listsize;}SqList;//创建空顺序表Status InitList_Sq( SqList &L ){L.elem = (ElemType*) malloc (LIST_INIT_SIZE*sizeof(ElemType));if (!L.elem)exit(OVERFLOW);L.length = 0;L.listsize = LIST_INIT_SIZE;return OK;}//顺序表在第i个元素之前插入eStatus sxbcr(SqList &L, int i, ElemType e){ElemType *p,*q;if((i<1) || (i>L.length+1))return (ERROR);else{ q=&(L.elem[i-1]);for(p=&(L.elem[L.length-1]);p>=q;--p)*(p+1)=*p;*q=e;++L.length;return (OK);}}//顺序表显示void xsList(SqList L){int i=L.length,k;for(k=0;k<i;k++)printf("%d ",L.elem[k]);printf("\n");}//顺序表逆置void nizhi(SqList &L){int i=0,j=L.length-1;ElemType temp;for(;i<j;i++,j--){temp=L.elem[i];L.elem[i]=L.elem[j];L.elem[j]=temp;}}main(){SqList L;char flag1='y',flag2='n';int i;数据结构作业2013ElemType k;if(InitList_Sq(L)){printf("建立空顺序表成功!\n");do{printf("当前线性表长度为:%d\n",L.length);printf("请输入要插入元素的位置:");scanf("%d",&i);printf("请输入要插入的元素值:");scanf("%d",&k);if(sxbcr(L,i,k)){printf("插入成功,插入后顺序表长度为:%d\n",L.length);printf("插入后的顺序表为:");xsList(L);}elseprintf("插入失败");printf("\n继续插入元素?(y/n) ");fflush(stdin);scanf("%c",&flag1);}while(flag1=='y');nizhi(L);printf("顺序表逆置后为:\n");xsList(L);}}2.从键盘读入n个整数(升序),请编写算法实现:(1)CreateList():建立带表头结点的单链表;(2)PrintList():显示单链表,(形如:H->10->20->30->40);(3)InsertList():在有序单链表中插入元素x;(4)ReverseList():单链表就地逆置;(5)DelList():在有序单链表中删除所有值大于mink且小于maxk的元素。

数据结构复习答案一、选择填空1.下面关于线性表的叙述中,错误的是哪一个?()A)线性表采用顺序存储,必须占用一片连续的存储单元。
√B)线性表采用顺序存储,便于进行插入和删除操作。
C)线性表采用链接存储,不必占用一片连续的存储单元。
D)线性表采用链接存储,便于插入和删除操作。
2.若某线性表最常用的操作是存取任一指定序号的元素和在最后进行插入和删除运算,则利用()存储方式最节省时间。
√A)顺序表B)双链表C)带头结点的双循环链表D)单循环链表3.链表不具有的特点是()。
A)插入、删除不需要移动元素√B)可随机访问任一元素C)不必事先估计存储空间D)所需空间与线性长度成正比4.若长度为n的线性表采用顺序存储结构,在其第i个位置插入一个新元素的算法的时间复杂度为()(1<=i<=n+1)。
A)O(0) B)O(1) √C)O(n) D)O(n2)5.线性表(a1,a2,…,an)以链接方式存储时,访问第i位置元素的时间复杂度为()。
A)O(i) B)O(1) √C)O(n) D)O(i-1)6.对于一个头指针为head的带头结点的单链表,判定该表为空表的条件是()A)head==NULL B)head→next==NULL√C)head→next==head D)head!=NULL7.在单链表指针为p的结点之后插入指针为s的结点,正确的操作是:()。
A)p->next=s;s->next=p->next; √B)s->next=p->next;p->next=s;C)p->next=s;p->next=s->next; D)p->next=s->next;p->next=s;8.设指针变量p指向单链表结点A,则删除结点A的后继结点B需要的操作为( )。
√A)p->next=p->next->next B)p=p->nextC)p=p->next->next D)p->next=p9.( )又称为FIFO表;( )又称为FILO表。

天津市高等院校春季招生统一考试计算机基础本试卷分为第Ⅰ卷(选择题)和第Ⅱ卷(非选择题)两部分,共150分。
考试用时120分钟。
第Ⅰ卷1至10页,第Ⅱ卷11至12页。
答卷前。
考生务必将自己的姓名、准考号填写在答题卡上,并在规定位置粘贴考试用条形码。
答卷时,考生务必将答案涂写在答题卡上指定位置的边框区域内,超出答题区域或直接答在试卷上的无效。
考试结束后,将本试卷和答题卡一并交回。
祝各位考生考试顺利!第Ⅰ卷注意事项:1.每小题选出答案后,用2B铅笔将答题卡上对应题目的答案标号涂黑。
如需改动,用橡皮擦干净后,再选涂其他答案标号。
2.本卷共2大题,共100分。
一、单项选择题:本大题共50小题,每小题1分,共50分。
每小题给出的四个选项中,只有一项是最符合题目要求的。
1.计算机的内存容量主要是指A.Cache的容量B.ROM的容量C.CMOS的容量D.RAM的容量2.计算机中存储1个英文字符占用的字节数是A.1 B.2C.3 D.43.汉字在计算机内部存储、处理的代码称为A.外码B.机内码C.ASCII码D.标准码4.应用计算机进行试卷评阅并统计分数,属于计算机应用领域的A.科学计算B.数据处理C.人工智能D.计算机辅助教学5.计算机指令的执行过程包括取出指令、分析指令和A.打印指令B.删除指令C.执行指令D.存储指令6.任何程序执行时都必须被加载到A.磁盘中B.硬盘中C.内存中D.显示器中7.字符“d”的ASCII码值是100,则字符“f”的ASCII码值是A.68 B.100C.70 D.1028.下列不属于...系统软件的是A.操作系统B.高级语言源程序C.编译程序D.数据库管理系统9.在WindowsXP中,文件系统的目录结构为A.网状结构B.树型结构C.层次结构D.线性结构10.咋WindowsXP中,将一个非活动窗口转变为活动窗口的过程称为A.打开B.切换C.移动D.运行11.在WindowsXP中,卸载“画图”程序,应使用控制面板中的A.系统B.管理工具C.任务计划D.添加或删除程序12.在WindowsXP中,下列文件名错误..的是A.a.c B.a_b.txtC.1.bat D.a\c.c13.在WindowsXP默认情况下,鼠标指针“ ”表示A.垂直调整B.水平调整C.精确定位D.沿对角线调整14.在WindowsXP中,下列关于快捷方式叙述错误..的是A.快捷方式可以被移动或复制B.同一个程序可以创建多个快捷方式C.快捷方式不能重命名,但可以删除D.可以为应用程序创建快捷方式,也可以为文档创建快捷方式15.在Windows XP中,将某文件的属性设置为“只读”,则A.该文件不能在文件列表中显示B.系统备份该文件后,将其删除C.该文件被修改后,不能以原文件名保存D.该文件可以被其他用户修改,但不能删除16.在Windows XP中,将“回收站”中的文件还原,文件将恢复到A.内存B.控制面板C.剪贴板D.被删除的位置17.在Windows XP中,要将系统显示的图标和文字都变小一些,可以调整A.颜色质量B.屏幕分辨率C.桌面背景D.显示对比度18.在Word 2003中,下列可以同时显示水平标尺和垂直标尺的视图是A.页面视图B.阅读版式C.大纲视图D.普通视图19.在Word 2003中,要显示“表格和边框”工具栏,可以使用A.“工具”菜单B.“插入”菜单C.“视图”菜单D.“格式”菜单20.在Word 2003中,窗口状态栏内不显示...A.当前页的页码B.文档的文件名C.当前文档的页数D.插入点所在的行列号21.在Word 2003中,下列任务可以通过“自动更正”完成的是A.使句首字母大写B.更改单元格底纹C.更正标点符号错误D.更改文字颜色22.在Word 2003中,要将所选文字的字形设置为“倾斜”,可以使用A.按钮B .按钮C.按钮D .按钮23.在Word 2003中,将插入点快速移动到文档最后一页的结尾处,可以按A.Alt+End键B.Alt+Page Down键C.Ctrl+End键D.Shift+Page Down键24.在Word 2003中,当前编辑状态为“改写”,若插入点在字符串“abcde”中的“a”与“b”之间,则输入“123”后字符串为A.a123e B.a123bcdeC.123de D.123abcde 25.在Word 2003中,下列关于表格叙述错误..的是A.单元格可以被拆分B.同一行中各单元格的宽度可以不同C.单元格中可以绘制斜线D.同一行中各单元格的高度可以不同26.咋Word 2003中,已打开两个文档sw.doc和sj.doc,执行“窗口”菜单“全部重排”命令后A.仅显示sj.doc的窗口B.两个窗口按上下平铺位置显示C.仅显示sw.doc的窗口D.两个窗口按左右平铺位置显示27.在Excel 2003中,单元格内输入“12-10”并确认后,系统默认此单元格显示内容为A.2 B.#NAME?C.12-10 D.12月10日28.在Excel 2003中,向多个选中的单元格中输入相同的内容,可以在一次输入后按A.Ctrl+Enter键B.Ctrl+Shift键C.Ctrl+Alt键D.Ctrl+Tab键29.在Excel 2003中,填充柄位于单元格或选中区域的A.中间B.左下角C.右上角D.右下角30.在Excel 2003中,名称框用于显示A.单元格或区域地址B.工作部名称C.单元格或区域内容D.工作表名称31.在Excel 2003中,将数字以文本方式显示,应在数字前输入A.单引号“'”B.分号“;”C.冒号“:”D.逗号“,”32.在Excel 2003中,下列属于单元格绝对引用的是A.D2 B.D$2C.$D$2 D.$D233.在Excel 2003中,下列叙述错误..的是A.可以设置页眉和页脚B.工作表中可以插入艺术字C.只能在同一个工作簿中复制工作表D.工作簿中默认包含3个工作表34.在Excel 2003中,若删除工作表中图表的某一数据系列,则A.工作表中对应的数据无变化B.清除工作表中对应的数据C.工作表中对应的数据变为零D.删除工作表中对应的单元格35.在Excel 2003中,某工作表中数据如下图所示。

2013年上海市普通高等学校春季招生考试数 学 试 卷考试注意: 1.答卷前,考生务必将姓名、高考座位号、校验码等填写清楚。
2.本试卷共有31道试题,满分150分。
考试时间120分钟。
3.请考生用钢笔或圆珠笔按要求在试卷相应位置上作答。
一. 填空题(本大题满分36分)本大题共有12题,要求直接填写结果,每题填对得3分,否则一律得0分。
1. 函数2log (2)y x =+的定义域是2. 方程28x=的解是 3. 抛物线28y x =的准线方程是 4. 函数2sin y x =的最小正周期是5. 已知向量(1 )a k =,,(9 6)b k =-,。
若//a b ,则实数 k = 6. 函数4sin 3cos y x x =+的最大值是 7. 复数23i +(i 是虚数单位)的模是8. 在ABC ∆中,角 A B C 、、所对边长分别为 a b c 、、,若5 8 60a b B ===,,,则b= 9. 在如图所示的正方体1111ABCD A B C D -中,异面直线1A B 与1B C 所成角的大小为 10. 从4名男同学和6名女同学中随机选取3人参加某社团活动,选出的3人中男女同学都有的 概率为 (结果用数值表示)。
11. 若等差数列的前6项和为23,前9项和为57,则数列的前n 项和n =S 12. 36的所有正约数之和可按如下方法得到: 因为2236=23⨯,所以36的所有正约数之和为22222222(133)(22323)(22323)(122)133)91++++⨯+⨯++⨯+⨯=++++=(参照上述方法,可求得2000的所有正约数之和为D 1C 1B 1A 1D C AB二.选择题(本大题满分36分)本大题共有12题,每题都给出四个结论,其中有且只有一个结论是正确的。
考生必须把真确结论的代码写在题后的括号内,选对得3分,否则一律得0分。
13.展开式为ad-bc 的行列式是( )(A )a bd c (B)a cb d (C)a db c (D)b ad c14.设-1()f x为函数()f x =)(A) 1(2)2f-= (B) 1(2)4f -= (C) 1(4)2f-= (D) 1(4)4f -=15.直线2310x y -+=的一个方向向量是( )(A) (2 3)-, (B) (2 3), (C) (3 2)-, (D) (3 2), 16函数12()f x x-=的大致图像是( )17.如果0a b <<,那么下列不等式成立的是( ) (A)11a b < (B) 2ab b < (C) 2ab a -<- (D) 11a b-<- 18.若复数12 z z 、满足21z z =,则12 z z 、在复数平面上对应的点12 Z Z 、( ) (A) 关于x 轴对称 (B)关于y 轴对称(C) 关于原点对称 (D)关于直线y x =对称 19. 10(1)x +的二项展开式中的一项是( )(A )45x (B )290x (C ) 3120x (D )4252x20.既是偶函数又在区间(0 )π,上单调递减的函数是( ) (A )sin y x = (B )cos y x = (C )sin 2y x = (D )cos 2y x = 21.若两个球的表面积之比为1:4,则这两个球的体积之比为( )(A )1:2 (B )1:4 (C )1:8 (D )1:16 22.设全集U R =,下列集合运算结果为R 的是( ) (A )u ZN ð (B )u N N ð (C )()u u ∅痧 (D ){0}u ð23.已知 a b c R ∈、、,“240b ac -<”是“函数2()f x ax bx c =++的图像恒在x 轴上方”的( )(A )充分非必要条件 (B )必要非充分条件 (C )充要条件 (D )既非充分又非必要条件 24.已知 A B 、为平面内两定点,过该平面内动点M 作直线AB 的垂线,垂足为N .若2MN AN NB λ=⋅,其中λ为常数,则动点M 的轨迹不可能是( )(A )圆 (B ) 椭圆 (C ) 抛物线 (D )双曲线三、解答题(本大题满分78分)本大题共有7题,解答下列各题必须写出必要的步骤。
生答题不得过此线··密····························封·························线···························· 院系 专业年级 班级 姓名 学号··················装····························订·························线···························· 一、选择填空题(每题只有1个正确答案,每题1分,共20分)1.从逻辑上可以把数据结构分为( )两大类。


第一部分:数据结构——线性结构(顺序表、链表、栈、队列、数组、串)考点:1、时间复杂度2、数据的逻辑结构与存储结构相关知识——分类、与存储结构之间的关系3、顺序表的知识——特点4、链表的知识——编程求单链表中结点的个数、插入、删除。
5、栈与队列知识——特点、循环队列、基本术语、链队列6、数组与矩阵——求元素的地址、稀疏矩阵行优先存储:下标从1开始:Loc(A i,j) = Loc(A1,1)+[(i-1)*n+j-1]*b下标从0开始:Loc(A i,j) = Loc(A0,0)+(i*n+j)*b 列优先存储:下标从1开始:Loc(A i,j) = Loc(A1,1)+[(j-1)*m+i-1]*b下标从0开始:Loc(A i,j) = Loc(A0,0)+(j*m+i)*b1. 设顺序线性表中有n个数据元素,则第i个位置上插入一个数据元素需要移动表中___________个数据元素;删除第i个位置上的数据元素需要移动表中___________个元素。
2.数据的逻辑结构通常有集合、线性结构、_________ 和 _________ 四类结构。
3.若进栈序列为a、b、c ,且进栈和出栈可以穿插进行,则可能出现_________个不同的出栈序列。
4.在栈结构中,允许插入的一端称为 _________;在队列结构中,允许删除的一端称为 _________。
5. 下列程序段的时间复杂度为_____________s=0;for(i=1;i<n;i++)for(j=1;j<n;j++)s+=i*j;6. 假设某个带头结点的单链表的头指针为head,则判定该表为空表的条件()A、head= =NULLB、head->next= =NULLC、head!=NULLD、head->next= =head7. 栈是一种操作受限的线性结构,其操作的主要特点是()A、先进先出B、后进先出C、进优于出D、出优于进8. 假设以数组A[n]存放循环队列的元素,其头、尾指针分别为front和rear。
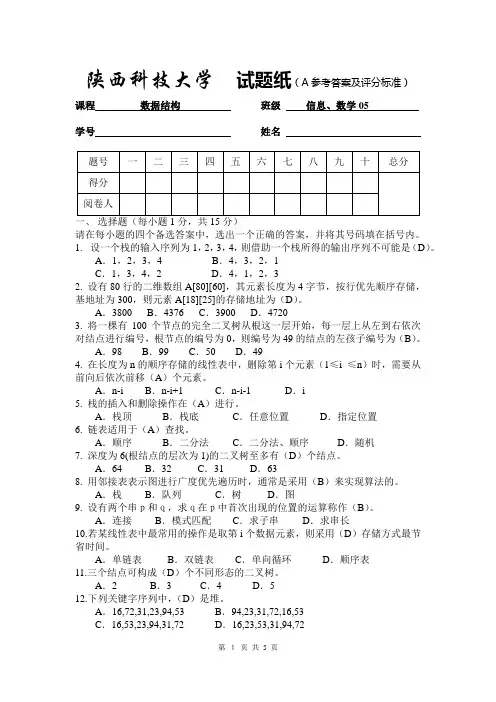
陕西科技大学试题纸(A参考答案及评分标准)课程数据结构班级信息、数学05学号姓名请在每小题的四个备选答案中,选出一个正确的答案,并将其号码填在括号内。
1.设一个栈的输入序列为1,2,3,4,则借助一个栈所得的输出序列不可能是(D)。
A.1,2,3,4 B.4,3,2,1C.1,3,4,2 D.4,1,2,32. 设有80行的二维数组A[80][60],其元素长度为4字节,按行优先顺序存储,基地址为300,则元素A[18][25]的存储地址为(D)。
A.3800 B.4376 C.3900 D.47203. 将一棵有100个节点的完全二叉树从根这一层开始,每一层上从左到右依次对结点进行编号,根节点的编号为0,则编号为49的结点的左孩子编号为(B)。
A.98 B.99 C.50 D.494. 在长度为n的顺序存储的线性表中,删除第i个元素(1≤i ≤n)时,需要从前向后依次前移(A)个元素。
A.n-i B.n-i+1 C.n-i-1 D.i5. 栈的插入和删除操作在(A)进行。
A.栈顶B.栈底C.任意位置D.指定位置6. 链表适用于(A)查找。
A.顺序B.二分法C.二分法、顺序D.随机7. 深度为6(根结点的层次为1)的二叉树至多有(D)个结点。
A.64 B.32 C.31 D.638. 用邻接表表示图进行广度优先遍历时,通常是采用(B)来实现算法的。
A.栈B.队列C.树D.图9. 设有两个串p和q,求q在p中首次出现的位置的运算称作(B)。
A.连接B.模式匹配C.求子串D.求串长10.若某线性表中最常用的操作是取第i个数据元素,则采用(D)存储方式最节省时间。
A.单链表B.双链表C.单向循环D.顺序表11.三个结点可构成(D)个不同形态的二叉树。
A.2 B.3 C.4 D.512.下列关键字序列中,(D)是堆。
A.16,72,31,23,94,53 B.94,23,31,72,16,53C.16,53,23,94,31,72 D.16,23,53,31,94,7213.把一棵树转换为二叉树后,这棵二叉树的形态是(A)。

2013山东春考数学试题一、选择题1. 若集合{}{}1,2,3,4,1,2,3M N ==,则下列关系式正确的是( ) A 。
MN M = B 。
M N N = C.N M ≠⊂ D.N M ≠⊃2.若p 是假命题,q 是真命题,则下列命题为真的是( ) A 。
q ⌝ B.p q ⌝∧ C.()p q ⌝∨ D 。
p q ∧ 3。
过点()1,2P ,且与直线310x y +-=平行的直线方程是( )A 。
350x y +-= B.370x y +-= C.350x y -+= D. 350x y --= 4.“2a c b +=”是“,,a b c 成等差数列”的( )A 。
充分不必要条件 B.必要不充分条件 C 。
充要条件 D.既不充分也不必要条件5.函数y =)A 。
[]1,5- B.[]5,1-- C.(][),15,-∞-+∞ D. (][),51,-∞-+∞6.已知点()()1,2,3,4M N ,则12MN 的坐标是( ) A.()1,1 B 。
()1,2 C.()2,2 D.()2,3 7。
若函数2sin 3y x πω⎛⎫=+ ⎪⎝⎭的最小正周期为π,则ω的值为( ) A.1 B.2 C 。
12D.4 8.已知点()()1,6,3,2M N -,则线段MN 的垂直平分线方程为( )A 。
40x y --=B 。
30x y -+= C.50x y +-= D 。
4170x y +-= 9.五边形ABCDE 为正五边形,以,,,,A BCDE 为顶点的三角形的个数是( ) A.5 B 。
10 C.15 D.2010.二次函数()()31y x x =--的对称轴是直线( ) A 。
1x =- B.1x = C 。
2x =- D.2x = 11。
已知点()9,2P m m -+在第一象限,则m 的取值范围是( ) A 。
29m -<< B 。
9m -<<2 C.2m -> D.9m <12.在同一坐标系中,二次函数()21y a x a =-+与指数函数xy a =的图象可能是( )13。

南京工业大学2013年硕士研究生入学考试初试试题(A 卷)科目代码:828科目名称:数据结构与操作系统满分:150分注意:①认真阅读答题纸上的注意事项;②所有答案必须写在答题纸上,写在本试题纸或草稿纸上均无效;③本试题纸须随答题纸一起装入试题袋中交回!第一部分:数据结构(共75分)一、选择题(每小题2分,共10分)1.数据结构是一门研究非数值计算的程序设计问题中计算机的操作对象以及它们之间的()和运算的学科。
A.结构 B.关系 C.算法 D.操作2、指出下列时间复杂度最坏的级别是。
A.对数阶O(log 2n) B.指数阶O(2n ) C.线性阶O(n) D.平方阶O(n 2)3、设S 和队列Q 的初始状态均为空,元素abcdefg 依次进入栈S 。
若每个元出栈后立即进入队列Q,且七个元素出队的顺序bdcfeag ,则栈S 的容量至少是()。
A.1 B.2 C.3 D.44、已知模式串P=’ABAAB’,其next 函数值是()。
A.01112 B.01222 C.01122D.011235、对基本有序表(21,36,40,54,28,64,69,73)进行排序,使用下列哪种方法最好()。
A.简单选择排序 B.直接插入排序 C.冒泡排序 D.归并排序二、填空题(每小题2分,共10分)1、线性结构中元素之间存在一对一的关系,图形结构中元素之间存在关系。
2、评价一个算法一般从4个方面进行:正确性、可读性、和。
3、找是具有特点的运算受限的线性表,队列是具有特点的运算变限的线性表。
4、动态查我表与静态查找表的区别是。
5、一组记录的关键字为(45,79,56,38,40,84)则利用堆排序方法建立的初始大根堆为。
三、计算应用题(共35分)1、某电文中使用5个字符:a,b,c,d,e 出现的频率依次:为2、4、5、9、10,试构造一棵对应的哈夫树及哈夫曼编码,并计算其带权路径长度WPL 。
(7分)2、由下列网络的邻接矩阵,画出此带权的图(v1~v6)及BFS 序列,并用Prim 法画出它的最小生成树(从v1出发)(6分)⎥⎥⎥⎥⎥⎥⎥⎥⎦⎤⎢⎢⎢⎢⎢⎢⎢⎢⎣⎡03415012223401900201519011700011060120760172220001703、设关键字序列(10,6,4,10,15,12),插入生成平衡二叉排序树(画出平衡调整的过程并指出每次调整所属的类型)。
重庆大学试卷 教务处07版 第 1 页 共 4 页 重庆大学 数据结构 课程试卷 A卷 B卷 2012 ~2013 学年 第 2 学期
开课学院: 计算机学院 课程号: 18013840 考试日期: 2013-7-02 考试方式:开卷闭卷 其他 考试时间: 120 分钟
题 号 一 二 三 四 五 六 七 八 九 十 总 分 得 分 一、Single Choice(30 points) 1. Here is a series of C++ statements using the list ADT in the book. L1.append(10); L1.append(20); L1.append(15); If these statements are applied to an empty list, the result will look like:( ) a) < 10 20 15 | > b) < | 10 20 15 > c) < 15 20 10 | > d) < | 15 20 10 >
2. When comparing the array-based and linked implementations, the array-based implementation has: ( ) a) faster direct access to elements by position,but slower insert/delete from the current position. b) slower direct access to elements by position,but faster insert/delete from the current position. c) both faster direct access to elements by position, and faster insert/delete from the current position. d) both slower direct access to elements by position, and slower insert/delete from the current position.
3. For a list of length n, the linked-list implementation's prev function requires worst-case time: ( )
a) O(1) b) O(log n). c) O(n). d) O(n^2). 4. Finding the element in an array-based list with a given key value requires worst case time: ( ) a) O(1). b) O(log n). c) O(n). d) O(n^2).
5. The Full Binary Tree Theorem states that: ( ) a) The number of leaves in a non-empty full binary tree is one more than the number of internal nodes. b) The number of leaves in a non-empty full binary tree is one less than the number of internal nodes. c) The number of leaves in a non-empty full binary tree is one half of the number of internal nodes. d) The number of internal nodes in a non-empty full binary tree is one half of the number of leaves.
6. If a node is at position r in the array implementation for a complete binary tree, then its parent is at: ( ) a) (r - 1)/2 if r > 0 b) 2r + 1 if (2r + 1) < n c) 2r + 2 if (2r + 2) < n d) r - 1 if r is even
7. Dijkstra's algorithm requires that vertices be visited in: ( ) a) Depth-first order. b) Breadth-first order. c) Order of distance from the source vertex. d) No particular order.
8. Which is a good example of a greedy algorithm? ( ) a) Floyd's all-pairs shortest path algorithm. b) Prim's minimal-cost spanning tree algorithm. c) Depth-first search. d) Topological sorting.
9. Which of the following is a true statement: ( ) a) In a BST, the left child of any node is less than the right child, and in a heap, the left child of any node is less than the right child. b) In a BST, the left child of any node is less than the right child,but in a heap, the left child of any node could be less than or greater than the right
命题人:石锐
组题人:
审题人:王茜
命题时间:2013.6.16
教务处制
学院
专业、班 年级 学号 姓名 公平竞争、诚实守信、严肃考纪、拒绝作弊
封 线
密 重庆大学试卷 教务处07版 第 2 页 共 4 页 child. c) In a BST, the left child of any node could be less or greater than the right child, but in a heap, the left child of any node must be less than the right child. d) In both a BST and a heap, the left child of any node could be either less than or greater than the right child. 10. The primary ADT access functions used to traverse a general tree are: ( ) a) left child and right sibling b) left child and right child c) leftmost child and right sibling d) leftmost child and next child 11. Huffman coding provides the optimal coding when: a) The messages are in English. b) The messages are binary numbers. c) The frequency of occurrence for a letter is independent of its context within the message. d) Never. 12. Shellsort takes advantage of the best-case behavior of which sort? ( ) a) Insertion sort b) Bubble sort c) Selection sort d) Radix sort 13.Given an unordered array containing N elements, how many comparisons will need to be performed (WORST CASE) to find a specific value? ( ) a. N/2 b. N c. 1 d. log(N) 14. A good hash function will: ( ) a) Use the high-order bits of the key value. b) Use the middle bits of the key value. c) Use the low-order bits of the key value. d) Make use of all bits in the key value. 15. A collision resolution technique that places all records directly into the hash table is called: ( ) a) Open hashing. b) Separate chaining. c) Closed hashing. d) Probe function.
16. Searching for all those records in a database with key value between 10 and 100 is known as: ( ) a) An exact match query. b) A range query. c) A sequential search. d) A binary search.
17.Ordered arrays, compared to unordered arrays, are ( ) a) Much quicker at deletion b) Quicker at searching c) Quicker at insertion d.)Quicker to create