Cluster Security with NVisionCC The Forseti Distributed File Integrity Checker
- 格式:pdf
- 大小:289.99 KB
- 文档页数:12

存储HCIP习题含答案一、单选题(共38题,每题1分,共38分)1.某容灾项目采用华为网络层完整空间快照方案,在9:00时开始对源卷创建快照,9:10时快照创建完成,在此过程中源卷有写操作,请问以下说法哪项是正确的?A、快照卷数据内容和源卷在9:00时数据内容相同。
B、快照卷是一份源卷在9:00时间点上的物理拷贝。
C、快照卷数据内容是源卷在9:00至3:10之间的增量数据。
D、快照卷数据内容和源卷在9:10时数据内容相同。
正确答案:A2.使用华为OceanStorBCManagereReplication配置主备容灾时,下列哪个操作不是必须的?A、添加存储设备和主机B、创建保护组C、配置站点D、配置主机组正确答案:D3.下面哪项属于oceanstor18000存储系列产品RAID2.0+技术支持的自动负载均衡技术?A、smartmotionB、smarttierC、smartqosD、smartpartition正确答案:A4.多路径软件的主要功能不包括以下那一项?A、负载均衡B、failover域failbackC、对数据加密D、屏蔽冗余磁盘正确答案:C5.在一个城市中,假如市公安局需要对各个派出所辖区内的视频监控进行定期归档,在这样的应用场景中,如果采用Oceanstor9000VIRC30提供的解决方案,应该推荐客户采用以下什么节点类型?A、P12节点B、P24节点C、P36节点D、P72节点E、C36节点正确答案:E6.大数据时代,也应该具有大数据思维,以下说法不正确的是哪一项?A、大数据时代,对数据的处理和分析不再依赖于随机的样本B、大数据时代,对大数据的处理分析更倾向于预测将会发生什么C、大数据时代,应该热衷追求数据的精确度正确答案:C7.在Oceanstor9000中,以下哪个组件的应用需要License支持。
A、NDMP备份B、同统一网管C、InfoReplicatorD、统一视图正确答案:C8.以下哪一项是华为混合闪存系列存储产品所支持的维护软件?A、SmartKitB、OceanStorUltraPathC、BCManagereReplicationD、OceanStoreSDK正确答案:A9.以下关于开箱验货说法不正确的是哪一项?A、开箱验货时出现错货、缺货,请填写《货物差错反馈表》反馈给当地办事处B、如果货物出现与装箱清单不符情况,应将已拆包装箱的设备转室内妥善存放C、开箱验货时,工程督导可以单独开箱清点货物正确答案:C10.以下关于华为OceanStor备份解决方案的描述,哪项是错误的,A、与容灾相比备份的恢复颗粒度较细,可以以文件为恢复级别,且可以做多个恢复版本。

2023 华为Datacom-HCIE 真题题库单项选择题1.[试题编号:190585] (单选题)华为SD-WAN解决方案中,当CPE位于NAT设备后的私网时,特别是两个站点的CPE同时位于NAT设备后的私网时,CPE之间需要使用NAT穿越技术。
华为SD-WAN解决方案中使用以下哪一项技术帮助CPE之间实现NAT穿越?A、NAT ALGB、NAT serverC、IPsec VPND、STUN答案:D解析:华为SD-WAN解决方案是一种通过网络控制器集中管理CPE设备、零配置开局的解决方案,可以帮助企业应对云服务带来的挑战,做到业务随需而变。
当CPE 位于NAT设备后的私网时,特别是两个站点的CPE同时位于NAT设备后的私网时,CPE之间需要使用NAT穿越技术,才能实现业务流量的互通。
华为SD-WAN 解决方案中使用STUN技术帮助CPE之间实现NAT穿越。
下面我来分析一下各个选项:A项:NAT ALG。
这个描述是错误的,因为NAT ALG是一种应用层网关技术,用于修改应用层报文中的IP地址和端口信息,以适应NAT转换后的地址变化,而不是用于实现NAT穿越。
B项:NAT server。
这个描述也是错误的,因为NAT server是一种NAT设备上的功能,用于将公网IP地址和端口映射到私网IP地址和端口,以提供对外服务,而不是用于实现NAT穿越。
C项:IPsec VPN。
这个描述同样是错误的,因为IPsec VPN是一种安全隧道技术,用于在不安全的网络中建立加密和认证的通道,以保护数据传输的安全性,而不是用于实现NAT穿越。
D项:STUN。
这个描述是正确的,因为STUN是一种NAT会话穿越应用程序,用于检测网络中是否存在NAT设备,并获取两个通信端点经NAT设备分配的IP 地址和端口号,在两个通信端点之间建立一条可穿越NAT的P2P链接2。
2.[试题编号:190584] (单选题)如图所示,在虚拟化园区网络中部署业务随行,其中PC1属于Sales安全组,PC2属于R&D安全组,PC3属于Market安全组。

四45五3六57十4十一34十二47没做“信息安全理论与技术"习题及答案教材:《信息安全概论》段云所,魏仕民,唐礼勇,陈钟,高等教育出版社第一章概述(习题一,p11)1.信息安全的目标是什么?答:信息安全的目标是保护信息的机密性、完整性、抗否认性和可用性;也有观点认为是机密性、完整性和可用性,即CIA(Confidentiality,Integrity,Availability)。
机密性(Confidentiality)是指保证信息不被非授权访问;即使非授权用户得到信息也无法知晓信息内容,因而不能使用完整性(Integrity)是指维护信息的一致性,即信息在生成、传输、存储和使用过程中不应发生人为或非人为的非授权簒改。
抗否认性(Non—repudiation)是指能保障用户无法在事后否认曾经对信息进行的生成、签发、接收等行为,是针对通信各方信息真实同一性的安全要求.可用性(Availability)是指保障信息资源随时可提供服务的特性.即授权用户根据需要可以随时访问所需信息。
2.简述信息安全的学科体系。
解:信息安全是一门交叉学科,涉及多方面的理论和应用知识.除了数学、通信、计算机等自然科学外,还涉及法律、心理学等社会科学.信息安全研究大致可以分为基础理论研究、应用技术研究、安全管理研究等。
信息安全研究包括密码研究、安全理论研究;应用技术研究包括安全实现技术、安全平台技术研究;安全管理研究包括安全标准、安全策略、安全测评等.3. 信息安全的理论、技术和应用是什么关系?如何体现?答:信息安全理论为信息安全技术和应用提供理论依据。
信息安全技术是信息安全理论的体现,并为信息安全应用提供技术依据。
信息安全应用是信息安全理论和技术的具体实践.它们之间的关系通过安全平台和安全管理来体现。
安全理论的研究成果为建设安全平台提供理论依据.安全技术的研究成果直接为平台安全防护和检测提供技术依据.平台安全不仅涉及物理安全、网络安全、系统安全、数据安全和边界安全,还包括用户行为的安全,安全管理包括安全标准、安全策略、安全测评等。
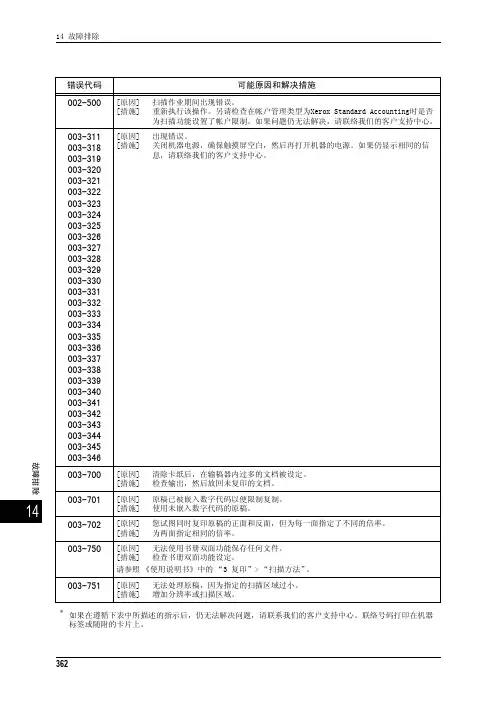

ict大数据复习题(含参考答案)一、单选题(共62题,每题1分,共62分)1.用户将证书上传到弹性负载均衡中,在创建()协议监听的时候绑定证书,提供HTTPS或TCP服务。
A、HTTPSB、HTTPC、TCPD、UDP正确答案:A2.LVS、Nginx节点服务正常时,每隔()秒会对ETCD节点连接,如果连续三次所有的ETCD节点都连接失败,产生集群健康检查告警。
A、1B、2C、3D、5正确答案:D3.ELB七层基于()实现。
A、LVSB、NginxC、HaproxyD、Apache正确答案:B4.常用的数据收集工具不包括?A、LoaderB、SparkC、KettleD、Sqoop正确答案:B5.为了提高Kafka的容错性,Kafka支持Partition的复制策略,以下关于Leader Partition和Follower Partition的描述错误的是:()。
A、Kafka针对Partition的复制需要选出一个Leader。
由该Leader负责Partition的读写操作。
其他的副本节点只是负责数据同步B、由于Leader Server承载了全部的请求压力。
因此从集群的整体考虑,Kafka会将Leader均衡的分散在每个实例上,来确保数据均衡C、一个Kafka集群各个节点间不可能互为Leader和FlowerD、如果Leader失效。
那么将会有其他follower来接管(成为新的Leader)正确答案:C6.Numpy包中创建数组的函数为(____)。
A、arrayB、ndimC、reshapeD、shape正确答案:A7.以下不属于CN自动剔除约束的是:()。
A、设置CN心跳超时时间的值大于0B、集群中的CN 总数必须大于等于3C、多CN故障时只能剔除一个CND、CN剔除以后,逻辑集群的创建、删除、扩容、缩容、回滚、显示操作可以执行正确答案:D8.以下不属于数据科学家主要职责的是(____) 。
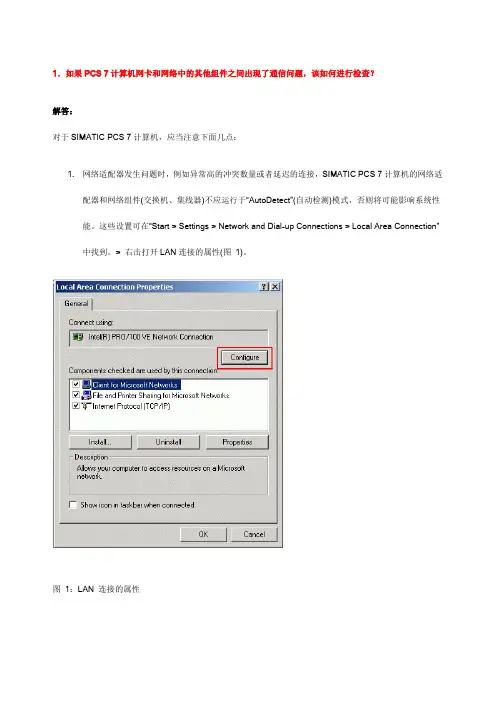
1.如果PCS 7计算机网卡和网络中的其他组件之间出现了通信问题,该如何进行检查?解答:对于SIMATIC PCS 7计算机,应当注意下面几点:1.网络适配器发生问题时,例如异常高的冲突数量或者延迟的连接,SIMATIC PCS 7计算机的网络适配器和网络组件(交换机、集线器)不应运行于“AutoDetect”(自动检测)模式,否则将可能影响系统性能。
这些设置可在“Start > Settings > Network and Dial-up Connections > Local Area Conn ection”中找到。
> 右击打开LAN连接的属性(图1)。
图1:LAN 连接的属性选择“Configure”并点击“Advanced”选项卡(图2)。
在项目“Link Speed & Duplex”中更改数值。
如有可能,100Mbps和Full Duplex(全双工)应当选为永久设置。
图2:网络适配器的高级设置注意事项:该设置的位置取决于使用的网络适配器的驱动程序。
对于OSM和ESM的组态设置,可在“SIMATIC Net Manual Collection”中找到。
< /p>2.检查SIMATIC PCS 7计算机,查看网络适配器是否组态为使用Microsoft Windows2000 中的电源管理。
如果是,则将其禁用。
这些设置可在“Start > Settings > Network and Dial-up Connection > Lan Area Connection”下找到。
右击打开LAN连接的属性(图1)。
选择“Configure”并点击“Power management”选项卡(图3)。
禁用“Allow the computer to turn off this device to save power”选项。
图3:网络适配器的电源管理2.同时运行Symantec的“GHOST Corporate Edition”软件和SIMATIC STEP 7 / PCS 7 / WinCC时,应当注意那些问题?解答:安装Symantec的“GHOST Corporate Edition”软件时有多种选择。

第一章课后练习1. 选择题(1)在5G移动通信系统网络架构中, 无线接入网的设备是( C )。
A. BTSB. BSCC. gNodeBD. eNodeB(2)从物理层次划分时, 5G承载网被分为( ABD )。
A. 前传网B. 中传网C. 后传网D. 回传网(3)为了满足低时延业务需要, 核心网的部分网络需要下沉到( D )中。
A. 核心DCB. 中心DCC. 区域DCD. 边缘DC(4)全球3G标准包含(ABCD )。
A. WCDMAB. CDMA2000C. TD-SCDMAD. WiMAX(5)4G使用的多址接入技术是(D)。
A. FDMAB. CDMAC. TDMAD. OFDMA2. 简答题(1)请写出ITU定义的5G的八大能力目标。
(2)请描述5G的三大应用场景。
5G的应用场景分为三大类: 增强移动带宽(enhanced Mobile Broadband, eMBB)、超高可靠低时延通信(Ultra Reliable and Low Latency Communication, URLLC)、海量物联网通信(massive Machine Type of Communication, mMTC), 不同应用场景有着不同的关键能力要求。
其中, 峰值速率、时延、连接数密度是关键能力。
eMBB场景下主要关注峰值速率和用户体验速率等, 其中, 5G的峰值速率相对于LTE的100Mbit/s提升了100倍, 达到了10Gbit/s;URLLC场景下主要关注时延和移动性, 其中, 5G的空口时延相对于LTE的50ms降低到了1ms;mMTC场景下主要关注连接数密度, 5G的每平方千米连接数相对于LTE 的104个提升到了106个。
第二章(1)以下可用于5G无线接入网部署的组网方式为( D )。
A. DRANB. CRANC. Cloud RAND. 以上都可以(2)以下不属于DRAN架构优势的是( D )。

大数据HCIA题库含参考答案一、单选题(共41题,每题1分,共41分)1.YARN调度器分配资源的顺序,下面哪一个描述是正确的?A、任意机器->同机架->本地资源B、任意机器->本地资源->同机架C、本地资源->同机架->任意机器D、同机架->任意机器->本地资源正确答案:C2.Flink中的()接口用于流数据处理,()接口用于批处理?A、DataStreamAPI,DataSetAPIB、DatabatchAPI,DataStreamAPIC、StreamAPI,BatchAPID、BatchAPI,StreamAPI正确答案:A3.关于Hive在FusionlnsightHD中的架构描述错误的是?A、只要有一个HiveServer不可用,整个Hive集群便不可用B、HiveServer负责接受客户端请求、解析、执行HQL命令并返回查询结果C、MetaStore用于提供原数据服务,依赖于DBServerD、在同一时间点HiveServeir只有一个处于Active状态,另一个则处于Standby状态正确答案:A4.FusionInsightHD系统中HDFS默认BlockSize是多少?A、32MBB、64MBC、128MBD、256MB正确答案:C5.FusionInsightHDHBase默认使用什么作为其底层文件存储系统?()A、HadoopB、MapReduceC、MemoryD、HDFS正确答案:D6.hbase的底层数据以()的形式存在的?A、行存储B、实时存储C、keyvalueD、列存储正确答案:C7.HDFS的副本存放策略中,同一机架不同服务器之间的距离是()A、2B、3C、1D、4正确答案:A8.下列选项中,关于Zookeeper可靠性含义说法正确的是?A、可靠性通过主备部署模式实现B、可靠性是指一条消息被一个server接收,它将被所有server接受C、可靠性是指无论哪个server,对外展示的均是同一个视图D、可靠性是指更新只能成功或者失败,没有中间状态正确答案:B9.以下关于FusionInsightCTBase的描述不正确的是?()A、CTBase的javaAPI提供一套Hbase连接池管理的接口,内部进行连接共享,减少客户端应用开发难度B、CTBase提供了一套WebUI进行元数据定义,提供了直观易用的表设计工具,降低表设计的难度。

社会公共安全防范协会安防考试以下关于NVR存储说法不正确的是()A.图片空间必须分配空间才能使用B.可以单独分配存储空间C、硬盘可以即插即用, 不必单独分配存储空间D.可以使用盘组功能更好的管理相机的存储空间参考答案: A关于NVR的智能检测, 下列说法不正确的是支持人脸检测、虚焦检测和声音检测支持区域入侵、越界检测和客流量支持场景变更、云台控制和图像调节支持智能运动跟踪、物品遗留和物品搬移参考答案: D智慧城市由()、传输网络和感应识别末梢等系统组成。
应急中心市民服务中心云计算中心指挥中心参考答案: C下列关于VMS-B200外置解码器上墙说法不正确的是。
如果出现上墙黑屏、卡顿问题, 可以排查IPC的码流是否符合解码器的解码标准卡顿的其中一个原因是网络丢包导致, 网络丢包通过增加交换机就能完全解决DC1801.DC2804/2808、DC104/108、DC4304均不支持265和Ucode, 所以黑屏的可能原因是265和Ucode开启导致操作上墙时提示无法上墙, 可能的原因是该通道离线了参考答案: B数字化综合网格建设是推进云改数转战略在最后()的落地。
1公里1级1步1米参考答案: DVMS-B200存储阵列重建时的硬盘指示灯状态是什么?绿灯常亮黄灯常亮绿灯闪烁黄灯闪烁参考答案: DNVR抓包定位国标跨域对接问题, NVR使用网卡二对接上级平台, 那么抓包时应选择哪个网卡进行抓包操作。
A.网卡一B.网卡二C.网卡三D.网卡四以下哪个系列安检机不需要单独配置操作台()。
A.5030系列B.6550系列C.100100系列参考答案: A关于无线网桥产品。
下列说法正确的有()。
A.通过无线方式回传数据, 需要接入点和客户端一起使用, 和无线AP一样B.PTP模式, 需要用一对产品去实现, 根据距离的远近选择对应的产品C.PTMP模式, 一个接入点可接入多个客户端, WLN-EB5F工作在接入点模式, WLN-EB5E工作在客户端模式D.中继模式, 为减少信号衰减, 不可视的两点之间推荐使用“间接传输”的模式, 根据距离的远近选择对应的产品参考答案: D下列关于一体机智能录像、回放说法错误的是?A.智能录像需要摄像机支持B、对于设备录像(录像存储在NVR上), 需将NVR升级至最新的软件版本以支持此功能C.以国标协议添加的设备不支持智能回放D.智能回放模式下支持回放上墙功能参考答案: C下列音频编码格式中, 宇视相机无法使用的是()。

数据传输⽤⼾指南·法律声明法律声明阿⾥云提醒您在阅读或使⽤本⽂档之前仔细阅读、充分理解本法律声明各条款的内容。
如果您阅读或使⽤本⽂档,您的阅读或使⽤⾏为将被视为对本声明全部内容的认可。
1. 您应当通过阿⾥云⽹站或阿⾥云提供的其他授权通道下载、获取本⽂档,且仅能⽤于⾃⾝的合法合规的业务活动。
本⽂档的内容视为阿⾥云的保密信息,您应当严格遵守保密义务;未经阿⾥云事先书⾯同意,您不得向任何第三⽅披露本⼿册内容或提供给任何第三⽅使⽤。
2. 未经阿⾥云事先书⾯许可,任何单位、公司或个⼈不得擅⾃摘抄、翻译、复制本⽂档内容的部分或全部,不得以任何⽅式或途径进⾏传播和宣传。
3. 由于产品版本升级、调整或其他原因,本⽂档内容有可能变更。
阿⾥云保留在没有任何通知或者提⽰下对本⽂档的内容进⾏修改的权利,并在阿⾥云授权通道中不时发布更新后的⽤⼾⽂档。
您应当实时关注⽤⼾⽂档的版本变更并通过阿⾥云授权渠道下载、获取最新版的⽤⼾⽂档。
4. 本⽂档仅作为⽤⼾使⽤阿⾥云产品及服务的参考性指引,阿⾥云以产品及服务的“现状”、“有缺陷”和“当前功能”的状态提供本⽂档。
阿⾥云在现有技术的基础上尽最⼤努⼒提供相应的介绍及操作指引,但阿⾥云在此明确声明对本⽂档内容的准确性、完整性、适⽤性、可靠性等不作任何明⽰或暗⽰的保证。
任何单位、公司或个⼈因为下载、使⽤或信赖本⽂档⽽发⽣任何差错或经济损失的,阿⾥云不承担任何法律责任。
在任何情况下,阿⾥云均不对任何间接性、后果性、惩戒性、偶然性、特殊性或刑罚性的损害,包括⽤⼾使⽤或信赖本⽂档⽽遭受的利润损失,承担责任(即使阿⾥云已被告知该等损失的可能性)。
5. 阿⾥云⽹站上所有内容,包括但不限于著作、产品、图⽚、档案、资讯、资料、⽹站架构、⽹站画⾯的安排、⽹⻚设计,均由阿⾥云和/或其关联公司依法拥有其知识产权,包括但不限于商标权、专利权、著作权、商业秘密等。
⾮经阿⾥云和/或其关联公司书⾯同意,任何⼈不得擅⾃使⽤、修改、复制、公开传播、改变、散布、发⾏或公开发表阿⾥云⽹站、产品程序或内容。

系统部署运维手册目录一、系统基本情况 (7)1.系统配置目标 (7)2.网络结构图 (8)3.服务器IP分配表 (8)二、安装作系统 (10)1.启动安装程序 (10)2.选择安装过程中使用的语言 (11)3.键盘设置 (12)4.本地磁盘分区 (12)5.安装引导装载程序 (13)6.网络设置 (13)7.设置时区 (14)8.设置根帐号口令 (15)9.选择安装类型 (15)10安装确认 (16)11系统安装 (17)12安装完成 (18)13第一次启动 (18)三、磁盘阵列安装 (24)1.配置NeoStor服务器 (25)2.RAID配置 (26)3.扫描物理设备 (28)4.创建逻辑资源 (29)5.创建SAN客户端336.为客户端创建Target (36)7.为客户端分配逻辑资源 (38)12.数据库服务器TurboHA配置 (126)九、应用服务(业务运行平台应用程序) (134)十、应用服务(服务) (136)十一、应用服务(运行监管应用程序) (137)十二、应用服务(运行监管服务) (139)十三(交易平台服务) (144)十四、应用服务(银行接口) (145)十五、数据库部署管理 (146)九、附1:卸载Weblogic中间件 (150)十、附2:卸载Oracle (150)十一、附3:Linux常用操作命令 (150)一、系统基本情况1.系统配置目标实现业务运行平台与运行监管系统各环节均保证系统能高可靠运行,具体配置要求如下:1)业务运行平台:A.代理服务器:两台服务器安装TurboLinux操作系统、Weblogic中间件,TurboLinux HA软件,配置成互为热备的工作模式;B.应用服务器:三台服务器安装TurboLinux操作系统、Weblogic中间件,配置成集群模式,响应代理服务器分发过来的HTTP请求,图片文件统一写到磁盘阵列上;部署业务运行平台应用软件,由集群系统统一分发到各集群服务器上;部署业务运行交易服务通信服务程序。
存储HCIP习题库(附答案)一、单选题(共38题,每题1分,共38分)1.下面关于eReplication的描述不正确的是:A、eReplication是一款华为技术有限公司开发的备份业务管理软件套件。
B、eReplication支持可视化管理,保护组和恢复计划的执行状态一目了然。
C、eReplication是一款华为技术有限公司开发的容灾业务管理软件套件。
正确答案:A2.某企业需要对其重要业务的数据进行持续保护,且需要在不影响业务的情况下,对LUN的数据进行不同的操作,如:生成报表、数据测试、数据分析等。
以下哪种特性可以满足该企业要求()A、SmartVirtualizationB、HyperCDPC、SmartCacheD、HyperLock正确答案:B3.运维工程师A查询华为全闪存存储手册关于硬件可信安全启动的过程,下列顺序正确的是()①验证Grub的签名公钥②验证软件签名证书状态③验证并加载Grub④验证并加载OSA、④①③②B、①④②③C、①③②④D、①②③④正确答案:D4.关于目标端重删,以下描述不正确的是哪一项?A、不能节省传输带宽。
B、不占用源端的资源。
C、目标端重删等同于后处理重删(Post-processing)。
D、数据块从源端传输到目标端,在目标端进行去重操作。
正确答案:C5.经测试客户的两个数据中心带宽为155Mbit/s,某应用峰值写带宽为9.8MB/s,平均写带宽为300KB/s,平均写I/O大小4KB.,带宽利用率为70%,同事选用主备同步远程复制容灾方案,该方案:A、不可行,通过计算带宽需要200Mbit/s。
B、不可行,主备同步远程复制容灾方案要求带宽利用率必须>80%,C、不可行,主备同步远程复制容灾方案要求写I/O大小必须<2KB。
D、可行,因为条件满足主备同步远程复制容灾方案要求。
正确答案:D6.以下描述是哪种备份组网的特点1占用较大的现有网络带宽。
存储HCIP试题库一、单选题(共38题,每题1分,共38分)1.某多用户多媒体点播业务应用,用户使用码流各不相同。
此应用在做后台N8500集群IAS存储系统LUN规划时,应选择的预取策略为:A、不预取B、固定预取C、智能预取D、可变预取正确答案:D2.下列哪个选项不是云存储的典型应用场景:A、运营云B、私有云C、政务云D、警务云正确答案:B3.关于Oceanstor9000InfoStamper特性描述不正确的是以下哪一项?A、Oceanstor9000的元数据采用镜像的方式进行冗余,对元数据使用COW 技术B、InfoStamper特性提供基于文件级别的快照C、Oceanstor9000InfoStamper采用ROW技术D、采用ROW的方式优点在于对系统性能的影响较小正确答案:B4.RAID2.0+技术中,sas硬盘且分出的chunk大小默认为多少MB?A、256MBB、64KBC、512MBD、64MB正确答案:D5.在存储规划设计流程中,以下哪一项不属于业务规划流程()A、基础业务B、容量规划C、增值功能D、网络规划正确答案:A6.下面属于华为存储danger类型的高危命令的时哪个命令?A、rebootsystemB、changalarmclearsequencelist=3424C、importconfiguration_dataD、showalarm正确答案:A7.关于华为Oceanstorv3融合存储系统说法不正确的是哪一项?A、使用同一存储池技术B、通过并行双栈的方式同时支持san和nasC、文件系统可实现数据重删压缩功能D、san引擎和文件引擎拥有独立的架构正确答案:D8.华为oceanstorv3重删压缩功能可为客户节省存储空间,降低TCO,以下重删压缩功能说法错误的时哪一项?A、可对文件系统和thinlun进行数据重删B、对数据进行指纹计算的最小容量单位是extentC、可对重删厚度数据进行压缩,重删压缩结合使用,综合效果更好D、如系统配置了重删压缩加速卡,则指纹计算,压缩,解压等操作将会由该加速卡完成正确答案:B9.某应用的数据初始容量是500GB.,备份频率是每周1次全备,6次增备,全备和增备的数据保存周期均为4周,冗余比为20%。
存储HCIP习题一、单选题(共38题,每题1分,共38分)1.在华为OceanStor9000中,以下哪个不属于NFS共享支持的鉴权方式?A、NIS鉴权B、LDAP鉴权C、客户端IP地址/主机名鉴权D、本地用户鉴权正确答案:D2.华为端到端双活数据中心解决方案分为6层,这六层是:A、存储层、会话层、应用层、网络层、传输层和安全层B、存储层、会话层、应用层、网络层、传输层和物理层C、存储层、计算层、应用层、网络层、传输层和安全层D、存储层、计算层、应用层、网络层、传输层和物理层正确答案:C3.关于华为分布式存储多级缓存技术读缓存的过程,优先从下列哪项读取命中()A、MemoryWriteCacheB、SSDReadCacheC、MemoryReadCacheD、SSDWriteCache正确答案:C4.华为oceanstorv3重删压缩功能可为客户节省存储空间,降低TCO,以下重删压缩功能说法错误的时哪一项?A、可对文件系统和thinlun进行数据重删B、对数据进行指纹计算的最小容量单位是extentC、可对重删厚度数据进行压缩,重删压缩结合使用,综合效果更好D、如系统配置了重删压缩加速卡,则指纹计算,压缩,解压等操作将会由该加速卡完成正确答案:B5.某公司业务运行在华为分布式存储上,其中用户数据业务使用块服务,并开启重删功能。
在用户数据业务高峰期,需要优先确保前端业务性能,存储系统会使用哪种重方式()A、在线重删B、源端重删C、关闭重删D、后重删正确答案:D6.以下哪个不是NAS系统的体系结构中必须包含的组件?A、可访问的磁盘阵列B、文件系统C、访问文件系统的业务接口D、FC交换机正确答案:D7.当需要卸载华为UltraPath主机多路径软件时,以下操作正确的时哪一项?A、停止主机业务读写后,立即执行UltraPath卸载命令B、iscsi业务环境中,先删除主机上的磁盘映射,再断开主机iscsi启动器的所有连接,最后执行UltraPath卸载命令C、FC业务环境中,断开所有FC主机物理端口连接后,执行UltraPath 卸载命令正确答案:B8.更换存储设备控制器钱需要确认以下信息,其中描述错误的是那一项?A、针对后端组网,需检查sas链路是否物理冗余B、正对前端组网,需要保证主机到阵列双控物理链路均正常C、只需要确保巡检工具巡检结果通过即可D、需检查主机到阵列双控的逻辑链路是否正常正确答案:C9.下列选项中不属于DSS力能的是:A、告警管理B、SLA管理C、服务编排D、服务发布正确答案:B10.FTP协议中的ASCII传输模式不建议传输如下哪种类型的文件?A、*.txtB、*.batC、*.cfgD、*.bin正确答案:D11.华为oceanstorv3lun拷贝与lun克隆描述正确的时哪一项?A、lun克隆源lun和目标lun的工作控制器必须相同,lun拷贝源lun 和目标lun无此要求B、lun拷贝的源lun大小可以小于目标lun,lun克隆的lun和从lun的大小必须完全一致C、lun拷贝只可以进行异地数据备份,lun克隆只可以进行本地数据备份D、lun克隆同步数据时,需要停止主机业务,lun拷贝进行数据同步时不需要停止业务正确答案:B12.关于华为分布式存储多级缓存技术中小I0写缓存的场景,下列哪项顺序是正确的()①写入基于SSD缓盘的WAL日志区,返回主机写操作完成②当内存写缓存达到一定水位,数据开始往下刷盘③数据写入基于RAM的WriteCache④小IO会先写入本节点的SSD缓存等待聚合成大IO 后再写入HDDA、①②③④B、③①②④C、③②①④D、③④①②正确答案:C13.运维工程师A查询华为全闪存存储手册关于硬件可信安全启动的过程,下列顺序正确的是()①验证Grub的签名公钥②验证软件签名证书状态③验证并加载Grub④验证并加载OSA、④①③②B、①④②③C、①③②④D、①②③④正确答案:D14.站点A需要的存储容量为2543GB.,站点B需要的存储容量为3000GB.,站点B的备份数据远程复制到站点A保存。
RN-08645-205_v01 | May 2017 Release NotesTABLE OF CONTENTS Chapter 1. NCCL Overview (1)Chapter 2. NCCL Release 2.0.5 (3)The NVIDIA Collective Communications Library (NCCL, pronounced “Nickel”) is a library of multi-GPU collective communication primitives that are topology-aware and can be easily integrated into applications.Collective communication algorithms employ many processors working in concert to aggregate data. NCCL is not a full-blown parallel programming framework; rather, itis a library focused on accelerating collective communication primitives. The following collective operations are currently supported:‣AllReduce‣Broadcast‣Reduce‣AllGather‣ReduceScatterTight synchronization between communicating processors is a key aspect of collective communication. CUDA based collectives would traditionally be realized through a combination of CUDA memory copy operations and CUDA kernels for local reductions. NCCL, on the other hand, implements each collective in a single kernel handling both communication and computation operations. This allows for fast synchronization and minimizes the resources needed to reach peak bandwidth.NCCL conveniently removes the need for developers to optimize their applicationsfor specific machines. NCCL provides fast collectives over multiple GPUs both within and across nodes. It supports a variety of interconnect technologies including PCIe, NVLINK, InfiniBand Verbs, and IP sockets. NCCL also automatically patterns its communication strategy to match the system’s underlying GPU interconnect topology. Next to performance, ease of programming was the primary consideration in the design of NCCL. NCCL uses a simple C API, which can be easily accessed from a variety of programming languages. NCCL closely follows the popular collectives API defined by MPI (Message Passing Interface). Anyone familiar with MPI will thus find NCCL’s API very natural to use. In a minor departure from MPI, NCCL collectives take a “stream”argument which provides direct integration with the CUDA programming model. Finally, NCCL is compatible with virtually any multi-GPU parallelization model, for example:NCCL Overview‣single-threaded‣multi-threaded, for example, using one thread per GPU‣multi-process, for example, MPI combined with multi-threaded operation on GPUs NCCL has found great application in Deep Learning Frameworks, where the AllReduce collective is heavily used for neural network training. Efficient scaling of neural network training is possible with the multi-GPU and multi node communication provided by NCCL.Key Features and EnhancementsThis NCCL release includes the following key features and enhancements.‣NCCL 2.0.5 provides support for intra-node and inter-node communication.‣NCCL optimizes intra-node communication using NVLink, PCI express, and shared memory.‣Between nodes, NCCL implements fast transfers over sockets or InfiniBand verbs.‣GPU-to-GPU and GPU-to-Network direct transfers, using the GPU Direct technology, are extensively used when the hardware topology permits it.Using NCCL 2.0.5Ensure you are familiar with the following notes when using this release.‣The NCCL 2.0 API is different from NCCL 1.x. Some porting may be needed for NCCL 1.x applications to work correctly. Refer to the documentation regardingmigrating from NCCL 1.x to NCCL 2.0 in the NCCL Developer Guide.‣NCCL 2.0.5 has the new configuration file support. The NCCL environment variables can now be set in ~/.nccl.conf and /etc/nccl.conf.‣Values defined in ~/.nccl.conf take precedence over ones in /etc/nccl.conf.‣The syntax for each line of the NCCL configuration file is<NCCL_VAR_NAME>=<VALUE>.Known Issues‣If NCCL returns any error code, set the environment variable NCCL_DEBUG to WARN to receive an explicit error message.‣RoCE support is experimental.‣Using multiple processes in conjunction with multiple threads to manage the different GPUs may in some cases cause ncclCommInitRank to fail whileNCCL Release 2.0.5 establishing IPCs (cudaIpcOpenMemHandle). This problem does not appear when using only processes or only threads.NoticeTHE INFORMATION IN THIS GUIDE AND ALL OTHER INFORMATION CONTAINED IN NVIDIA DOCUMENTATION REFERENCED IN THIS GUIDE IS PROVIDED “AS IS.” NVIDIA MAKES NO WARRANTIES, EXPRESSED, IMPLIED, STATUTORY, OR OTHERWISE WITH RESPECT TO THE INFORMATION FOR THE PRODUCT, AND EXPRESSL Y DISCLAIMS ALL IMPLIED WARRANTIES OF NONINFRINGEMENT, MERCHANTABILITY, AND FITNESS FOR A PARTICULAR PURPOSE. Notwithstanding any damages that customer might incur for any reason whatsoever, NVIDIA’s aggregate and cumulative liability towards customer for the product described in this guide shall be limited in accordance with the NVIDIA terms and conditions of sale for the product.THE NVIDIA PRODUCT DESCRIBED IN THIS GUIDE IS NOT FAULT TOLERANT AND IS NOT DESIGNED, MANUFACTURED OR INTENDED FOR USE IN CONNECTION WITH THE DESIGN, CONSTRUCTION, MAINTENANCE, AND/OR OPERATION OF ANY SYSTEM WHERE THE USE OR A FAILURE OF SUCH SYSTEM COULD RESULT IN A SITUATION THAT THREATENS THE SAFETY OF HUMAN LIFE OR SEVERE PHYSICAL HARM OR PROPERTY DAMAGE (INCLUDING, FOR EXAMPLE, USE IN CONNECTION WITH ANY NUCLEAR, AVIONICS, LIFE SUPPORT OR OTHER LIFE CRITICAL APPLICATION). NVIDIA EXPRESSL Y DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY OF FITNESS FOR SUCH HIGH RISK USES. NVIDIA SHALL NOT BE LIABLE TO CUSTOMER OR ANY THIRD PARTY, IN WHOLE OR IN PART, FOR ANY CLAIMS OR DAMAGES ARISING FROM SUCH HIGH RISK USES.NVIDIA makes no representation or warranty that the product described in this guide will be suitable for any specified use without further testing or modification. T esting of all parameters of each product is not necessarily performed by NVIDIA. It is customer’s sole responsibility to ensure the product is suitable and fit for the application planned by customer and to do the necessary testing for the application in order to avoid a default of the application or the product. Weaknesses in customer’s product designs may affect the quality and reliability of the NVIDIA product and may result in additional or different conditions and/ or requirements beyond those contained in this guide. NVIDIA does not accept any liability related to any default, damage, costs or problem which may be based on or attributable to: (i) the use of the NVIDIA product in any manner that is contrary to this guide, or (ii) customer product designs.Other than the right for customer to use the information in this guide with the product, no other license, either expressed or implied, is hereby granted by NVIDIA under this guide. Reproduction of information in this guide is permissible only if reproduction is approved by NVIDIA in writing, is reproduced without alteration, and is accompanied by all associated conditions, limitations, and notices.TrademarksNVIDIA, the NVIDIA logo, and cuBLAS, CUDA, cuDNN, cuFFT, cuSPARSE, DIGITS, DGX, DGX-1, Jetson, Kepler, NVIDIA Maxwell, NCCL, NVLink, Pascal, T egra, T ensorRT, and T esla are trademarks and/or registered trademarks of NVIDIA Corporation in the Unites States and other countries. Other company and product names may be trademarks of the respective companies with which they are associated.Copyright© 2018 NVIDIA Corporation. All rights reserved.。
GHOST客户端参数:GHOST参数/?或/H:查看帮助。
-CLONE:克隆。
-IA:对所有分区中的扇区进行映象。
-ID:对整个磁盘(包括未分区空间)进行复制。
-IR:和ID一样,但不将分区调整为扇区界限。
-IB:只复制磁盘的启动扇区。
-IAL:对LINUX分区进行整个复制,对其它分区则用正常方法。
-OR:覆盖空间并进行完整性检查。
-NOLILO:复制后不要试图去修正LILO启动调入器。
-BOOTCD:当使用-SURE直接制作CD-R映象时,期望找到可启动软盘。
-FDSZ:清除目标磁盘上的标志性字节。
-FDSP:保留目标磁盘上的标志性字节。
(优先级高于-FSSZ)-LPM:LPT主并行连接模式。
-LPS:LPT从并行连接模式。
-TCPM:TCP/IP主连接模式。
-TCPS:TCP/IP从连接模式。
-USBM:自动进入USB主模式。
-USBS:自动进入USB从模式。
-JL:记录多点传送会话诊断消息到文件。
-JS:设置最大的多点传送值。
-JA:设置多点传送会话的名称。
-AUTO:不要提示输入文件名,使用默认值。
-CHKIMG:检查映象文件的完整性。
-PWD:指定密码。
-SKIP:指定需要跳过的FAT文件系统中的文件或目录。
-PMBR:当进行任何磁盘复制操作时,保留目标磁盘中的主引导记录。
-SPAN:允许存取多个卷。
-SPLIT:当创建映象时将映象分成数块。
-Z:压缩映象文件。
-F64:当调入旧映象文件时允许64K的簇大小。
-FATLIMIT:防止FAT分区大小超过2兆。
-F32:将FAT16转换为FAT32。
-NTD:允许NTFS内部诊断检查。
-NTC-:禁止NTFS连续簇分配。
-NTCHKDSK:强制CHKDSK在下一个NTFS卷启动。
-NTIC:忽略NTFS卷上的CHKDSK位。
-NTIL:忽略非空的NTFS日志文件检查位。
-NTIID:忽略分区系统标识符的复制。
-TAPEBUFFERED:默认的磁带模式。
ClusterSecuritywithNVisionCC:TheForsetiDistributedFileIntegrityChecker
AdamJ.Lee†‡,GregoryA.Koenig†‡,andWilliamYurcik††NationalCenterforSupercomputingApplications
‡DepartmentofComputerScience
UniversityofIllinoisatUrbana-Champaign{adamlee,koenig,byurcik}@ncsa.uiuc.edu
AbstractAttackerswhoareabletocompromiseasinglenodeinahighperformancecomputingclustercanusethatnodeasalaunchpointforanumberofmaliciousac-tions.Inmanycases,thepasswordusedtologintoasinglenodecanbeusedtoaccessalargenumberofnodesinthesystem,allowingtheattackertoutilizethevastcomputingandstoragecapabilitiesofthecompro-misedclustertosniffnetworktraffic,carryoutbrute-forcepasswordcracking,launchdistributeddenialofserviceattacks,orserveillegaldigitalcontent.Often,thesetypesofattackersmodifyimportantsystemfilestocollectpasswordstootheraccounts,disablecertainloggingfacilities,orcreateback-doorsintothesystem.Inthispaper,wepresentForseti,adistributedfileintegritycheckerdesignedspecificallyforthehighper-formancecomputingclusterenvironment.Forsetiwasdesignedtoaddresstheshortcomingsexhibitedbyex-istinghost-basedintrusiondetectionsystemswhenusedintheclusterenvironmentandtoprovideameansofdetectingchangestocriticalsystemfilesmadebyroot-leveladversaries.Wediscussthedesignandimplemen-tationoftheForsetisystem,presentasecurityanalysisofForseti,examinetheperformanceofthesystem,andexplorehowForseticanbeusedinconcertwithothersecuritymonitoringtechniquestoenhancethesecurityoftheHPCclusterenvironment.
1IntroductionOverthecourseofthelasttwoyears,thesecurityoflarge-scalecommodityclustershasbecomeatopicofincreasingresearchandpracticalinterest.Attack-erswhoareabletocompromiseasinglenodeinoneoftheseclusterscanusethatnodeasalaunchpointforanumberofmaliciousactions.Inmanycases,thepasswordusedtologintoasinglenodecanbeusedtoaccessalargenumberofnodesinthesystem,al-lowingtheattackertoutilizethevastcomputingandstoragecapabilitiesofthecompromisedclustertocarryoutbrute-forcepasswordcracking,launchdistributeddenialofserviceattacks,orserveillegaldigitalcontent.Additionally,anattackercanlistentonetworktrafficforotheruserstologintotheircompromisednodesinhopesoflearningpasswordsforotheraccountsonthesesystems.Therecentriseinpopularityofgridcomputinghasexacerbatedthisproblembyincreasingtheamountofdamagethatcanbecausedwithasinglecompro-misedaccount.Oftentimes,apasswordusedtologintooneclusternodecanbeusednotonlytologintoothernodesinthesamecluster,butalsotologintootherclusterslocatedthroughoutthecomputationalgrid.Thisimpliesthatthecompromiseofasingleac-countonasingleclusternodecouldgiveanattackertheabilitytoaccessmanythousandsofgeographicallydis-tributedclusternodes.Thehighutilizationofclustersparticipatingingridcomputingsystemsallowsanat-tackersniffingforpasswordsonacompromisednodetogainaccesstoanextremelyhighnumberofotheruseraccounts.Thistechniqueisnotconjectureandwas,infact,usedduringtheTeraGridcompromisesthataf-fectedalargenumberofclustersworld-wideduringtheSpringof2004[11].Duringthistimeperiod,attackersinstalledTrojan-horsesshdprocessesdesignedtocap-turethepasswordsofusersloggingintocompromisednodessothatthesepasswordscouldthenbeusedtocompromiseothernodesthroughoutthegrid.Host-basedfileintegritycheckers(e.g.,[2,4,6,10,12,15,18,24])havebeenusedtohelpdetectthesetypesofattacksonhostsinenterprisecomputingsys-temsforanumberofyears.Thesetoolsareactivatedperiodically(usuallybymeansofaschedulersuchascron),tocheckvariouspropertiesofcriticalsystemfiles,includingaccesspermissions,timestamps,andcontenthashes.Thesepropertiesarecomparedtoref-erencevaluesstoredinaread-onlydatabase;fileswhosevaluesdifferfromthereferencecauseanalerttoberaised,suchasanentryinthesystemlogoranemailbeingsenttothesystemadministrator.Thoughthesesystemshaveworkedwellinenterprisecomputing,theysufferseveralshortcomingswhenusedinlarge-scalecommodityclusters.Installingandmanagingthesetoolsonthehundredsorthousandsofnodesinalargeclusterisatime-consumingprocessinvolvingchangestoeachnodewhensystemsoftwareisupgraded.Ad-ditionally,ifthesignaturedatabaseisstoredoneachnode,attackerscanrelativelyeasilychangethetheref-erencecopyofthefileinformation.Lastly,effectivelyloggingtheaccessviolationscanposeaproblemifanattackerhasgainedrootaccesstothemachine,astheycoulddisrupttheloggingmechanismandeasilycovertheirtracks.Toaddresstheshortcomingsofhost-basedfilein-tegritycheckerswhileretainingtheirstrengths,wehavedesignedForseti,adistributedfileintegritycheckerthatmeetstheuniqueneedsoftheHPCclusteren-vironment.Inourtool,thefileintegritydatabaseisseparatedfromthenodestobemonitoredandbylever-agingtheemergentpropertiesoftheHPCclustercom-putingenvironment[25],wecansignificantlyreducethesizeofthisdatabase.Clusternodescannotaccessthedatabase,meaningthatanattackerwhohascom-promisedsomenumberofnodesinthesystemcannotalterthestoredfilesignatures.Oursystemreliesonacollectornode(notnecessarilypartofthecluster)tocarryouttheintegrityscansbymakingremoteconnec-tionstothenodesinthesystem,pushingthenecessarysoftwaretothesystem,andcarryingoutthescan.Inthisway,Forsetihasnosoftwarefootprintonthenodestobemonitoredandaddinganewnodetobescannedisassimpleasupdatingthedatabasetoinformthecollectornodeofthischange.Thissystemisrobusttoindividualnodecompromisesand,thoughnotfool-proof,issignificantlyhardertodefeatthanotherhost-basedsystemsperformingsimilarfunction;hadForsetibeendeployedduringtheSpringof2004,theTeraGridattackscouldhavebeendetectedandstoppedmuchearlierthantheywere.Therestofthispaperisorganizedasfollows.InSection2wedescribeourthreatmodelanddiscusstheconditionsinwhichintegritymonitoringcanaidinthesecuritymonitoringoflarge-scalecommodityclusters.Section3brieflydiscussesthedesignofNVisionCC,theclustermonitoringtoolwithwhichForsetiinter-acts.InSection4,wediscusstheimplementationofourdistributedintegritycheckeranddetailitsinter-actionswithclusternodesandNVisionCC.WerevisitourthreatmodelanddiscusstheperformanceofthisscannerinSection5,andaddressrelatedworkinSec-tion6.WethenpresentourconclusionsanddirectionsforfutureworkinSection7.