ccna4期末考试题
- 格式:doc
- 大小:2.39 MB
- 文档页数:16
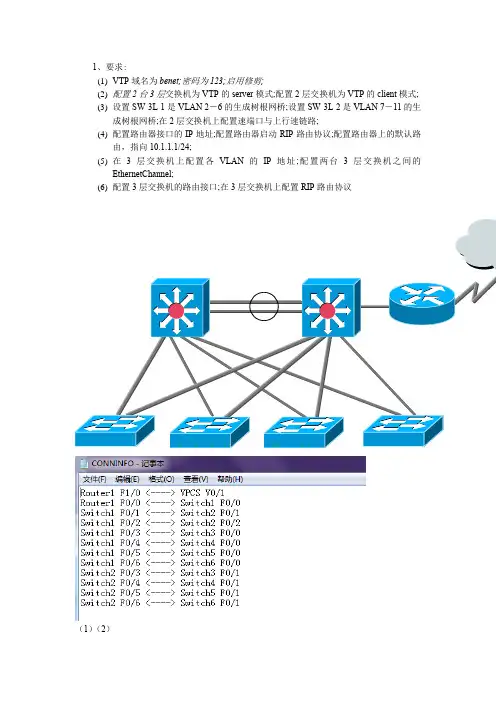
1、要求:(1)VTP域名为benet;密码为123;启用修剪;(2)配置2台3层交换机为VTP的server模式;配置2层交换机为VTP的client模式;(3)设置SW-3L-1是VLAN 2-6的生成树根网桥;设置SW-3L-2是VLAN 7-11的生成树根网桥;在2层交换机上配置速端口与上行速链路;(4)配置路由器接口的IP地址;配置路由器启动RIP路由协议;配置路由器上的默认路由,指向10.1.1.1/24;(5)在3层交换机上配置各VLAN的IP地址;配置两台3层交换机之间的EthernetChannel;(6)配置3层交换机的路由接口;在3层交换机上配置RIP路由协议(1)(2)○1SW1-3L 配置vtp域名benetpassword 123 Server模式SW2-3L同样配置○2SW1-3L启用修剪SW2-3L同样配置○3SW3-2L配置vtp的client模式、SW4-2L、SW5-3L、SW6-3L相同配置(3)设置SW-3L-1是VLAN 2-6的生成树根网桥;设置SW-3L-2是VLAN 7-11的生成树根网桥;在2层交换机上配置速端口与上行速链路;○1SW-3L-1是VLAN 2-6的生成树根网桥;;○2设置SW-3L-2是VLAN 7-11的生成树根网桥○3SW3-2L配置速端口与上行链路,SW4-2L、SW5-2L 、SW6-2L上同样配置(4)配置路由器接口的IP地址;配置路由器启动RIP路由协议;配置路由器上的默认路由,指向10.1.1.1/24○1路由器上配置ip地址○2路由器上配置默认路由和RIP○3SW1-3L各vlan的ip地址○4SW2-3L各vlan的ip地址(5)在3层交换机上配置各VLAN的IP地址;配置两台3层交换机之间的EthernetChannel ○1在SW1-3L配置EthernetChannel;○2在SW2-3L配置EthernetChannel;(6)配置3层交换机的路由接口;在3层交换机上配置RIP路由协议○1SW1-3L上配置路由接口○2SW2-3L上配置路由接口○3SW1-3L上的RIP配置○4SW2-3L上的RIP配置○5在SW1-3L验证RIP○6在SW2-3L验证RIP2、要求:如图所示,四台路由器R1,R2,R3以及R4运行OSPF协议(要求发布各路由器的loopback0地址),R1与R2属于Area1,R2与R3属于Area0,R3与R4属于Area2。
如果将命令如果将命令 ip dhcp excluded-address 10.10.4.1 10.10.4.5 添加到配置为添加到配置为 DHCP 服务器的本该路由器将丢弃发往该路由器将丢弃发往 10.10.4.1 和 10.10.4.5 的流量。
的流量。
不会路由地址处于不会路由地址处于 10.10.4.1 到 10.10.4.5 之间的客户端所发出的流量。
DHCP 服务器不会分配服务器不会分配 10.10.4.1 到 10.10.4.5 之间的地址。
之间的地址。
该路由器将忽略来自地址处于 10.10.4.1 到 10.10.4.5 之间的之间的 DHCP 服务器的流量。
服务器的流量。
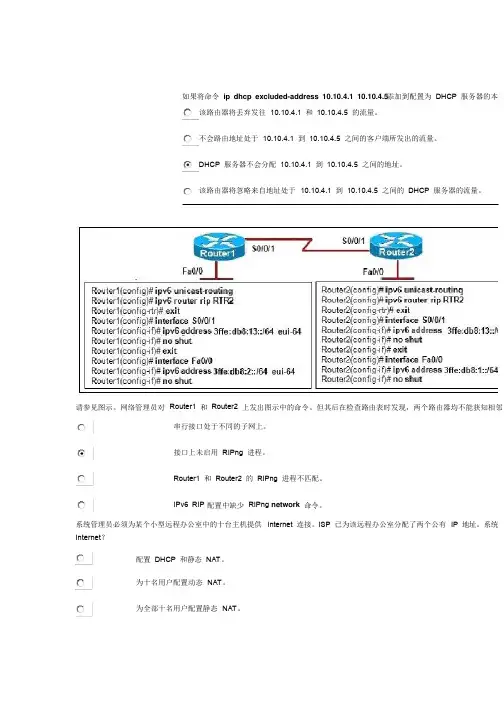
请参见图示。
网络管理员对请参见图示。
网络管理员对 Router1 和 Router2 上发出图示中的命令。
但其后在检查路由表时发现,两个路由器均不能获知相邻串行接口处于不同的子网上。
接口上未启用接口上未启用 RIPng 进程。
进程。
Router1 和 Router2 的 RIPng 进程不匹配。
进程不匹配。
IPv6 RIP 配置中缺少配置中缺少 RIPng network 命令。
命令。
系统管理员必须为某个小型远程办公室中的十台主机提供 Internet 连接。
ISP 已为该远程办公室分配了两个公有 IP 地址。
系统Internet配置配置 DHCP 和静态和静态 NAT 。
为十名用户配置动态为十名用户配置动态 NAT 。
为全部十名用户配置静态为全部十名用户配置静态 NAT 。
配置带过载的动态配置带过载的动态 NAT 。
网络管理员在上周更改了其网络交换机的 VLAN 配置。
管理员如何才能确定添加和更改的动作是否改善了公司内部网的性能和可进行性能测试,并与过去测得的基线进行比较。
与部门秘书交谈,询问他们是否感觉网页加载时间有所改善。
监控从远程站点加载公司网页的时间,以确定内部网的性能。
将公司将公司 Web 服务器上的本周点击次数与前几周记录的值相比较。

C C N A考试题(总9页) -CAL-FENGHAI.-(YICAI)-Company One1-CAL-本页仅作为文档封面,使用请直接删除第一部分:选择题1:提供可靠数据传输、流控的是OSI的第几层()A、表示层B、网络层C、传输层D、会话层E、链路层2:子网掩码产生在那一层()A、表示层B、网络层C、传输层D、会话层3:当路由器接收的IP报文的目的地址不是本路由器的接口IP地址,并且在路由表中未找到匹配的路由项,采取的策略是()A、丢掉该分组B、将该分组分片C、转发该分组D、以上答案均不对4:当一台主机从一个网络移到另一个网络时,以下说法正确的是()A、必须改变它的IP地址和MAC地址B、必须改变它的IP地址,但不需改动MAC地址C、必须改变它的MAC地址,但不需改动IP地址D、MAC地址、IP地址都不需改动5:ISO提出OSI的关键是()A、系统互联B、提高网络速度C、为计算机制定标准D、经济利益6:OSI参考模型按顺序有哪些层()A、应用层、传输层、网络层、物理层B、应用层、表示层、会话层、网络层、传输层、数据链路层、物理层C、应用层、表示层、会话层、传输层、网络层、数据链路层、物理层D、应用层、会话层、传输层、物理层7:LAN的拓扑形式一般以()为主。
A、总线型B、环型C、令牌环D、载波侦听与冲突检测CSMA/CD8:网段地址154.27.0.0的网络,若不做子网划分,能支持()台主机A、254B、1024C、65,534D、16,777,2069:路由器网络层的基本功能是()。
A、配置IP地址B、寻找路由和转发报文C、将MAC地址解释成IP地址10:选出基于TCP协议的应用程序()。
A、PINGB、TFTPC、TELNETD、OSPF11:某公司申请到一个C类IP地址,但要连接6个的子公司,最大的一个子公司有26台计算机,每个子公司在一个网段中,则子网掩码应设为()。
A、255.255.255.0B、255.255.255.128C、255.255.255.192D、255.255.255.22412:B类地址的缺省掩码是()。
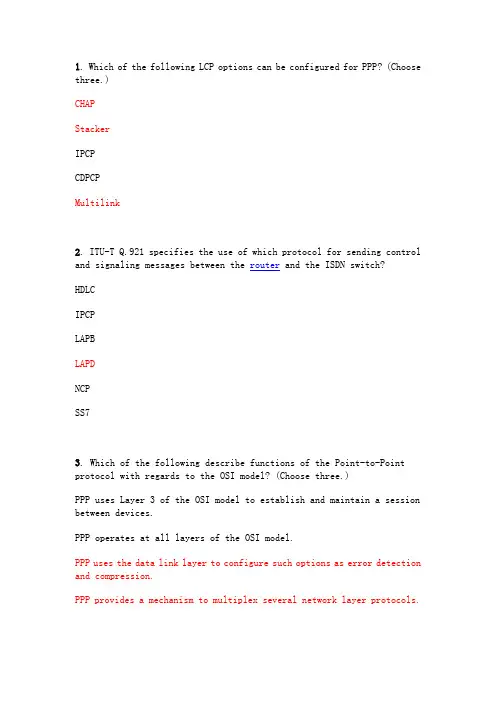
1. Which of the following LCP options can be configured for PPP? (Choose three.)CHAPStackerIPCPCDPCPMultilink2. ITU-T Q.921 specifies the use of which protocol for sending control and signaling messages between the router and the ISDN switch?HDLCIPCPLAPBLAPDNCPSS73. Which of the following describe functions of the Point-to-Point protocol with regards to the OSI model? (Choose three.)PPP uses Layer 3 of the OSI model to establish and maintain a session between devices.PPP operates at all layers of the OSI model.PPP uses the data link layer to configure such options as error detection and compression.PPP provides a mechanism to multiplex several network layer protocols.PPP uses Network Control Protocols (NCP) to test and maintain connectivity between devices.PPP can be configured on both synchronous and asynchronous serial interfaces.4. Which of the following statements regarding point-to-point subinterfaces are true? (Choose two.)A point-to-point subinterface on one router must be connected to a similar subinterface on a remote router.Each point-to-point subinterface connection is configured with its own subnet.The DLCIs configured on the remote and local routers must be the same for the PVC.LMI frames are not transmitted through a subinterface.Routing updates in point-to-point networks are not subject to thesplit-horizon rule.5.How will data be transmitted from the router to the ISP if the router has the two links shown in the graphic?Both links will transmit data at the same rate.1544 bits can be transmitted simultaneously from the router over the T1 line.Both links will transmit bits one by one.The 56K link will transmit a maximum of 53 bits at the same time.6. A network administrator is asked to design a system to allow simultaneous access to the Internet for 250 users. The ISP for this network can only supply five public IPs. What can be used to accomplish this task?routable translationdynamic translationstatic translationport address translation7. Which of the following statements are true about Frame Relay? (Choose three.)Frame Relay operation is defined by a series of ISO standards.Frame Relay is a packet switched, connection-oriented, wide area network service.Frame Relay only supports point-to-point connections.A router can be considered as data terminal equipment (DTE) in a frame relay system.Frame Relay is a cell switched, connection-oriented, wide area network service.Frame Relay networks use a subset of the HDLC protocol to carry information.8. Why would data frames be discarded in a Frame Relay network? (Choose two.)The frame contains an incorrect IP address.An error has been detected in computing the frame check sequence.There is not enough bandwidth dedicated for the data contained in the frame.Data is transmitted at a rate greater than the access speed.The frame contains an incorrect DLCI.9.Which of the following can be concluded from the router output displayed in the graphic? (Choose two.)The local DLCI number of this PVC is 100.The interface has been configured for subinterfaces and this map is for subinterface 0.Inverse ARP has determined the remote ip address as 10.140.1.1.The LMI type is ANSI (0×64).There is currently no congestion on the link.10. When planning simple WAN connections for a small company, which feature of the three layer hierarchical model makes it a good choice for the WAN topology.It provides for redundancy.It allows for easy WAN expansion in case of company growth.It is less expensive.It provides faster connection time.It provides less latency and jitter.11.The command output shown in the graphic was taken from a Cisco 806 broadband router. Which kind of address translation is in effect on this router?staticdynamicoverloadprivatepublic12. A network administrator has been asked to provide the network in the United States with an ISDN WAN link. The router available to provide the WAN connection is a non-modular Cisco router with two serial connections. What must be done to adapt one of the serial interfaces of this router for the ISDN connection?Nothing. The router is already suitable.Purchase a BRI WAN interface card to install in the router.Purchase a U interface to install in the router.Purchase a TA/NT1 device to install on the router.13. How does Frame Relay technology process frames that contain errors? (Choose two.)Frame Relay services depend on the upper layer protocols to handle error recovery.It requires the receiving device to request that the sender retransmit erroneous frames.FECN, BECN, and DE bits are set in the frames to minimize errors.The receiving device drops any frames that contain errors without notifying the sender.The frame relay switch notifies the sender that errors were detected.14. Which statements about DHCP are true? (Choose three.)DHCP uses TCP.DHCP uses UDP.DHCP sends messages to the server on port 67.DHCP sends messages to the server on port 68.DHCP sends messages to the client on port 67.DHCP sends messages to the client on port 68.15. Which command configures the SPID on the first B channel of an ISDN interface?Router(config)# isdn spid0 spid-number [ldn]Router(config)# isdn spid1 spid-number [ldn]Router(config-if)# isdn spid0 spid-number [ldn]Router(config-if)# isdn spid1 spid-number [ldn]16.Which command would produce the output shown in the graphic?show ip dhcp server statisticsshow ip dhcp bindingdebug ip dhcp server eventsdebug ip dhcp binding17. Which commands can be used to identify which DLCIs are active? (Choose two.)show frame-relay mapshow frame-relay lmishow frame-relay pvcshow frame-relay interfaceshow interfacesshow ip route18. When PPP authentication is enabled, which of the following may be checked before establishing a PPP link between two devices? (Choose two.)the enable password on the remote devicethe ip host configuration on the remote devicethe security server database for the username and password of the remote devicethe hostname and enable password on the local devicethe local database for the username and password of the remote device19. Which of the following are supported by a BRI interface on a router? (Choose two.)Two independent channels that can carry analog data with a bandwidth of 64 KHz.A single 128 Kbps digital bearer channel.Two multiplexed channels carrying digital data.A single 64 Kbps signaling channel.A multiplexed data channel that can only handle SS7 information.A 16 Kbps delta channel used for signaling purposes.20.An administrator consoled into the Jelly router needs to telnet to the Butter router. What DLCI will the Jelly router place in the frame to perform this operation?11011522022521.What is placed in the address field of a frame that will travel from the DC office of ABC company to the Orlando office?MAC address of the Orlando routerMAC address of the DC router192.168.1.25192.168.1.26DLCI 100DLCI 20022. The WAN connection for a nationwide company with 250 offices must support constant connections to core layer services for file sharing, and occasional Internet access. Which combination of WAN technologies will meet these needs with minimum expense?Frame Relay PVC for Internet access and ATM for file server accessFrame Relay PVC for Internet access and ISDN for file server accessISDN for Internet access and X.25 for file server accessISDN for Internet access and Frame Relay PVC for file server access23. What does a DLCI of 0 indicate about a frame? (Choose two.)This is the first data frame sent by the router.This is a management frame.The encapsulation type is Cisco.The encapsulation type is IETF.The LMI type is Ansi or q933a.The LMI type is Cisco.24. A company needs a WAN connection that is capable of transferring voice, video, and data at a minimum data rate of 155 Mbps. Which WAN connection is the best choice?X.25DSLATMISDN BRIISDN PRI25. What are three features of the CHAP protocol? (Choose three.)exchanges a random challenge number during the session to verify identitysends authentication password to verify identityprevents transmission of login information in plain textdisconnects the PPP session if authentication failsinitiates a two-way handshake26. Which of the following devices is used to establish the communications link between the customer equipment and the local loop for digital lines?terminal adaptermodemCSU/DSUPBX switchISDN switchFrame Relay Switch27. Which command would be used to exclude the IP address 192.168.24.5 from the DHCP address pool on a router?Router(dhcp-config)# ip dhcp excluded-address 192.168.24.5Router# ip dhcp excluded-address 192.168.24.5Router(config-excluded)# ip dhcp excluded-address 192.168.24.5Router(config)# ip dhcp excluded-address 192.168.24.5Router(config)# excluded-address 192.168.24.5Router(dhcp-config)# excluded-address 192.168.24.528. A router needs to forward a message received from a host. How does the router identify the correct VC to forward the message? (Choose two.)The router forwards the frame to all ports in the network and learns the address from the reply frame.The destination host IP address is embedded in the DLCI.The router searches Inverse ARP tables for maps of DLCIs to IP addresses.A table of static mappings can be searched.The router broadcasts a request for the required IP address.29. Which of the following switching types will allow the communication devices in the provider’s network to be shared and only allocated to an individual subscriber during data transfer?circuit-switchedpacket-switchedframe-switcheddedicated-switched lineslease-switched30. Which of the following IP addresses are defined by RFC 1918 as private addresses? (Choose three.)192.168.146.0/22172.10.25.0/16172.31.0.0/1620.0.0.0/810.172.92.8/2931. Which of the following describes the PAP protocol? (Choose two.)sends unencrypted authentication passwordsperforms a three-way handshakeallows repeated login attemptsuses the remote router hostname to verify identitysends a random challenge throughout the session32. Which of the following protocols can be used to encapsulate data traffic sent from a router BRI interface? (Choose two.)Link Access Protocol – DataHigh-Level Data Link ControlLogical Link ControlSerial Data Link ControlPoint to Point protocolBinary Synchronous Control protocol33. Which statement explains why basic DSL is an unpopular WAN connectivity choice for enterprise computer departments that support home users?DSL offers insufficient bandwidth to home users.DSL requires the installation of new cables, which is not always possible for home users.DSL dialup connection time is too slow for business use.DSL has limited geographical availability.34. Which of the following are functions of the Local Management Interface used in Frame Relay networks? (Choose three.)exchange information about the status of virtual circuitsmap DLCIs to network addressesprovide flow controlprovide error notificationprovide congestion notificationsend keepalive packets to verify operation of the PVC35.An ISDN router is configured for DDR as shown in the graphic to provide Internet connectivity for the company. Immediately after a user in the company attempts opens a web browser to connect to the Internet, anotheruser in the company tries to download a file using FTP. What will happen? (Choose two.)The user that opened the browser will connect to the Internet because the DDR link will consider this traffic interesting.The Internet user will be disconnected because the FTP data will cause the DDR link to shut down.The DDR link will allow the FTP traffic because it is interesting.The DDR link will not allow the FTP traffic because it is not interesting.The FTP connection will fail because the DDR link is already in use for the Internet connection.The FTP connection will succeed because the web user already opened the DDR link.36. Which command will provide for CHAP authentication if the hostname on a challenging router is tampa with a password of florida?username tampa password floridausername tampa floridahostname tampa password floridahostname tampa florida37. Which of the following is a function of a DCE device?determines the next-hop address for a packetmultiplexes signals from several sourcesadapts information for use on a service provider’s networkused to directly connect two DTEs to simulate a WAN network38. Which operating systems support multiuser capability? (Choose three.) LinuxWindows 98Windows MEWindows XPWindows 200039. Why was NAT created? (Choose two.)to create firewalls on routersto conserve IP addressesto translate domain names into IP addressesto map network addresses to the corresponding data link addressto hide internal addresses from external devices40. Which of the following terms describes a device that will put data on the local loop?DLCICODCEDTEPRIBRI41. How many separate B channel circuits can be provisioned on a PRI interface that uses a T1 line for connectivity?21623243012842.The LAN attached to the Ethernet interface of the Raleigh router shown in the graphic is addressed with private IP addresses. If one public IP is assigned to the company, which commands could be used in a configuration that allows all devices with private IPs in this network to access the Internet? (Choose two.)ip nat inside source list 1 interface serial0 overloadip nat outside source list 1 interface serial0 overloadip nat inside serial0ip nat inside source list 1 pool Raleigh overloadip nat inside Raleigh overloadip inside nat source list 1 interface serial0 Raleigh43.Which of the following describes the WAN devices and cabling shown in the graphic? (Choose two.)A null-modem cable is used between RouterD and DeviceC for connectivity.A DB-25 or DB-9 serial cable is connected to interface S0/0 of RouterA.DeviceB and DeviceC are DCE devices.The same encoding scheme must be used by DeviceB and DeviceC.A synchronous serial connection exists between DeviceB and DeviceC.44. Which of the following are commonly used as Data Communications Equipment? (Choose two.)modemrouterCSU/DSUISDN SwitchFrame Relay Switch45. What does the command debug isdn q921 display?exchange of call setup and teardown messagesPAP and CHAP authentication trafficLayer 2 messages on the D channelprotocol errors and statisticsLayer 2 messages on the B channel46. A technician is testing the functionality of a recently installed router. The technician is unable to ping the serial interface of a remote router. The technician executes the show interface serial0/0command on the local router and sees the following line in the output:Serial0/0 is up, line protocol is downWhat are possible causes for this command output? (Choose three.) remote CSU/DSU failureserial cable missinginterface shutdownkeepalives not being sentclocking signal missing。

缩小范围
收集可疑设备的症状
分析现有症状
确定所有权
2逻
接口标识符
连接器类型
操作系统版本
电缆类型
虚电路
记录仅在园区网络中发现的设备的相关信息。
记录在整个网络中(包括远程站点)发现的设备的相关信息。
将网络配置表中与拓扑图所示组件相关的任何设备信息记录下来。
仅将网络配置表中与拓扑图所示组件相关的第
将网络配置表中与拓扑图所示组件相关的在网络使用高峰期收集的的设备信息记录下来。
检查所有服务器的电缆连接。
检查每块网卡上的连接指示灯是否为绿色。
在每台服务器上使用应用程序控制台来确保应用程序正在运行。
检查应用程序服务器上的事件日志,看是否有特定应用程序的错误消息。
测试客户端与服务器之间的
如果
在服务器上重新安装受影响的应用程序。
如果应用程序仍然无法响应,则在其中一台用户
6下
封装不正确
STP
ARP
时钟频率不正确
8全
数据中心中的超时传输现象表明存在本地物理层问题。
序以及电缆是否损坏。
因为所有客户端都遇到了应用程序问题,管理员应该对数据中心内的应用程序服务器使用自上而下问题的范围表明可能存在路由问题或生成树问题。
通过对员工进行调查以确定最近是否进行过更改。
10广12
14
极端工作条件下的预期性能
基线工具
知识库
协议分析器
电缆测试仪
18下
TCP/IP
TCP/IP
使用
网络接入层负责在
Internet
TCP/IP
20网。

ccna试题一、单选题1. 下面哪个是OSI模型的物理层?A. TCPB. IPC. EthernetD. HTTP答案:C2. 以下哪个是IPv6的全球未经分配地址?A. FC00::/7B. 2000::/3C. 8000::/4D. FFFF::/8答案:A3. 以下哪个在OSI模型的会话层工作?A. HTTPB. IPC. TCPD. NetBIOS答案:D二、多选题4. 下面哪些是用于路由器接口配置的命令?(选择两个)A. ip addressB. mac addressC. interfaceD. enable答案:A, C5. 下面哪些是IP协议的特点?(选择三个)A. 可靠传输B. 无连接C. 不可靠传输D. 面向连接答案:B, C, D6. 下面哪些是TCP的特点?(选择三个)A. 面向连接B. 可靠传输C. 无连接D. 面向字节流答案:A, B, D三、填空题7. TCP/IP协议族中,网络接口层对应的是__________。
答案:网络接口8. 在IPv6地址中,一个冒号表示__________。
答案:前缀和后缀之间的分隔符9. 在TCP连接终止过程中,主动关闭连接的一方发送的最后一个ACK分组中ACK标志位的值是__________。
答案:1四、解答题10. 请简要解释TCP/IP协议族中IP协议的作用。
答案:IP(Internet Protocol)协议是TCP/IP协议族中的一种网络层协议,主要负责在网络之间传输数据包。
它使用IP地址来标识网络上的设备,并通过路由选择算法实现数据包的正确传递。
IP协议是一种无连接的协议,不提供数据包的可靠传输,也不保证数据包按顺序到达目的地。
它使用IP头部来存储必要的控制信息,如源IP地址、目的IP地址、数据包长度等。
11. 请简要描述TCP三次握手的过程。
答案:TCP三次握手用于建立一个TCP连接。
过程如下:1. 客户端向服务器发送一个SYN(同步)分组,其中设置SYN标志位为1,并选择一个初始序列号。

在讨论网络设计时,为什么根据大小划分网络非常有用?了解已连接设备的数量可以确定核心层上需要多少多层交换机。
了解已连接设备的数量可以确定多少个额外的层将添加到三层分层网络设计中。
1如果已连接设备的数量已知,则可以在接入层上更好地实施高级冗余。
网络基础设施的复杂性取决于已连接设备的数量。
最高分值说明答案Option 42correctness of response以建筑块的形式为大型公司设计网络的其中一个好处是什么?故障隔离增加网络访问时间2安全控制宽松所需物理资源更少答案说明最高分值Option 12correctness of response员工、合作伙伴和客户依靠哪个网络模块维护的资源进行高效的创造、协作和信息交互?访问分布3服务数据中心企业边缘最高分值答案说明Option 32correctness of response公司通过多个连接连接到一个 ISP。
此类连接称为什么?单宿主多宿主4双多宿主双宿主最高分值答案说明Option 42correctness of response哪种情形将使企业决定实施公司 WAN?当员工分布在许多分支机构中时当网络需要跨越多栋建筑物时5的容量时当员工人数超过 LAN当企业决定保护其公司 LAN 时答案说明最高分值Option 1correctness of response 26 与电路交换网络相比,数据包交换网络的缺点是什么?成本更高带宽固定灵活性更低延迟更高最高分值说明答案Option 42correctness of response(DWDM) 的特征?哪项陈述正确描述了密集波分复用 SDH 标准。
它支持SONET 标准,但不支持它通过一对铜缆支持双向通信。
7ISP 之间的连接。
它可用于远程通信,比如它将传入的电信号分配到特定频率。
说明答案最高分值Option 32correctness of response连接?(请选择两项。
)帧中继适合哪两类 WAN公共基础设施私有基础设施 8专用Internet分组交换最高分值答案说明Option 2 and Option 5 are correct.2correctness of response)技术可作为底层网络来传输多种类型的网络流量(例如 IP、、以太网和 DSLATM WAN 哪种ISDNMPLS9帧中继WAN 以太网最高分值答案说明Option 22correctness of response连接到企业网络来 VPN 公司的安全策略规定销售部门的员工在去会见客户的路途中必须使用据。

ccna测试题及答案CCNA测试题及答案一、选择题1. 在Cisco设备上,以下哪个命令用于查看当前的路由表?A. show ip routeB. show running-configC. show interface statusD. show version答案:A2. 以下哪个协议用于在网络中自动发现其他设备?A. ARPB. CDPC. ICMPD. TCP答案:B3. 以下哪个命令用于配置Cisco设备上的接口?A. configure terminalB. interfaceC. ip addressD. hostname答案:A二、填空题4. 在Cisco设备上,使用命令_________可以查看接口的配置信息。
答案:show interface5. 静态路由配置中,_________命令用于指定下一跳地址。
答案:ip route6. 动态路由协议可以自动适应网络变化,其中_________是最常见的一种。
答案:RIP(路由信息协议)三、简答题7. 请简述VLAN(虚拟局域网)的作用。
答案:VLAN是一种将局域网内不同物理位置的设备划分为同一逻辑网络的技术,主要用于隔离广播域,提高网络的安全性和效率。
8. 描述交换机和路由器在网络中的基本功能。
答案:交换机主要用于局域网内部,通过MAC地址表来转发数据帧,实现数据包在局域网内的快速交换。
路由器则工作在网络层,使用IP地址来转发数据包,连接不同的网络,并进行路径选择。
四、计算题9. 假设一个子网掩码为255.255.255.192,计算这个子网的可用IP地址范围。
答案:可用IP地址范围为192.168.1.0到192.168.1.62(包含两端)。
五、实验题10. 请根据以下配置文件,列出Router1的接口配置信息。
```Router1show running-configinterface FastEthernet0/0ip address 192.168.1.1 255.255.255.0duplex autospeed auto!interface FastEthernet0/1no ip addressshutdown!interface Serial0/0/0ip address 10.0.0.1 255.255.255.252clock rate 64000!router ospf 1network 192.168.1.0 0.0.0.255 area 0network 10.0.0.0 0.0.0.3 area 0!```答案:- FastEthernet0/0: IP地址为192.168.1.1,子网掩码为255.255.255.0,双工模式和速度均为自动。
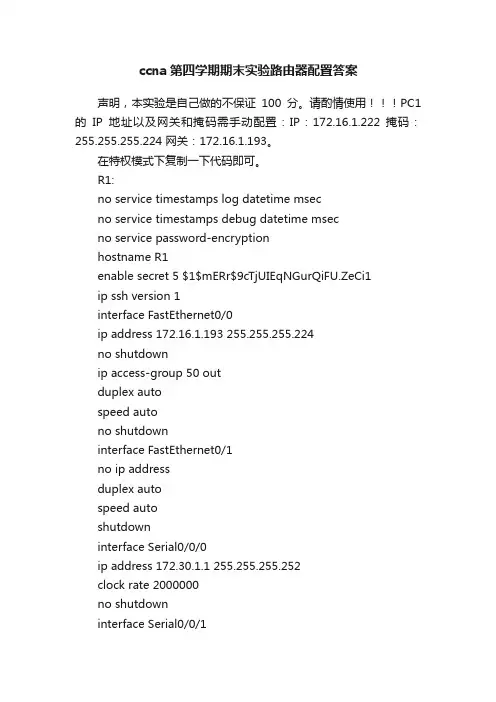
ccna第四学期期末实验路由器配置答案声明,本实验是自己做的不保证100分。
请酌情使用PC1的IP地址以及网关和掩码需手动配置:IP:172.16.1.222 掩码:255.255.255.224 网关:172.16.1.193。
在特权模式下复制一下代码即可。
R1:no service timestamps log datetime msecno service timestamps debug datetime msecno service password-encryptionhostname R1enable secret 5 $1$mERr$9cTjUIEqNGurQiFU.ZeCi1ip ssh version 1interface FastEthernet0/0ip address 172.16.1.193 255.255.255.224no shutdownip access-group 50 outduplex autospeed autono shutdowninterface FastEthernet0/1no ip addressduplex autospeed autoshutdowninterface Serial0/0/0ip address 172.30.1.1 255.255.255.252clock rate 2000000no shutdowninterface Serial0/0/1no ip addressno shutdownencapsulation frame-relayinterface Serial0/0/1.101 point-to-pointip address 10.10.10.1 255.255.255.252 frame-relay interface-dlci 101interface Vlan1no ip addressshutdownrouter eigrp 100network 172.16.0.0network 172.30.0.0network 10.0.0.0no auto-summaryip classlessaccess-list 50 deny 172.16.1.128 0.0.0.63 access-list 50 permit anybanner motd ^CAuthorized Access Only!^C logging trap debuggingline con 0exec-timeout 0 0password ciscologging synchronousloginline vty 0 4exec-timeout 0 0password ciscologging synchronousloginline vty 5 15exec-timeout 0 0password ciscologging synchronousloginntp update-calendarendR2:no service timestamps log datetime msecno service timestamps debug datetime msecno service password-encryptionhostname R2enable secret 5 $1$mERr$9cTjUIEqNGurQiFU.ZeCi1 username R3 password 0 ciscochapip ssh version 1ip name-server 0.0.0.0interface FastEthernet0/0no ip addressduplex autospeed autoshutdowninterface FastEthernet0/1no ip addressduplex autospeed autoshutdowninterface Serial0/0/0ip address 172.30.1.6 255.255.255.252 no shutdownencapsulation pppppp authentication chapip nat insideinterface Serial0/0/1no ip addressno shutdownencapsulation frame-relayinterface Serial0/0/1.201 point-to-point ip address 10.10.10.2 255.255.255.252 frame-relay interface-dlci 201ip nat insideinterface Serial0/1/0ip address 209.165.201.2 255.255.255.252 ip access-group FIREWALL inip nat outsideinterface Serial0/1/1no ip addressshutdowninterface Vlan1no ip addressshutdownrouter eigrp 100redistribute staticnetwork 10.0.0.0network 172.30.0.0no auto-summaryip nat inside source list 1 interface Serial0/1/0 overload ip classlessip route 0.0.0.0 0.0.0.0 Serial0/1/0access-list 1 permit 172.16.1.128 0.0.0.127ip access-list extended FIREWALLdeny icmp any any echodeny tcp any any eq telnetdeny tcp any any eq wwwpermit ip any anybanner motd ^CAuthorized Access Only!^Clogging trap debuggingline con 0exec-timeout 0 0password ciscologging synchronousloginline vty 0 4exec-timeout 0 0password ciscologging synchronousloginline vty 5 15exec-timeout 0 0password ciscologging synchronousloginendR3:no service timestamps log datetime msecno service timestamps debug datetime msecno service password-encryptionhostname R3enable secret 5 $1$mERr$9cTjUIEqNGurQiFU.ZeCi1 username R2 password 0 ciscochapip ssh version 1ip name-server 0.0.0.0interface FastEthernet0/0ip address 172.16.1.129 255.255.255.192no shutdownduplex autospeed autointerface FastEthernet0/1no ip addressduplex autospeed autoshutdowninterface Serial0/0/0ip address 172.30.1.2 255.255.255.252no shutdowninterface Serial0/0/1ip address 172.30.1.5 255.255.255.252no shutdownencapsulation pppppp authentication chapclock rate 2000000interface Vlan1no ip addressshutdownrouter eigrp 100network 172.16.0.0network 172.30.0.0no auto-summaryip classlessip dhcp excluded-address 172.16.1.129 172.16.1.131 ip dhcp pool R3_LANnetwork 172.16.1.128 255.255.255.192default-router 172.16.1.129banner motd ^CAuthorized Access Only!^C logging trap debuggingline con 0exec-timeout 0 0password ciscologging synchronousloginline vty 0 4exec-timeout 0 0password ciscologging synchronousloginline vty 5 15exec-timeout 0 0password ciscologging synchronousloginntp update-calendar end。

1. What functionality do access control lists provide in the implementation of dynamic NAT on a Cisco router?define which addresses can be translateddefine which addresses are assigned to a NAT pooldefine which addresses are allowed out the routerdefine which addresses can be accessed from the inside network2. Which three guidelines would help contribute to creating a strong password policy? (Choose three.)Once a good password is created, do not change it.Deliberately misspell words when creating passwords.Create passwords that are at least 8 characters in length.Use combinations of upper case, lower case, and special characters.3.Refer to the exhibit. Every time the administrator reboots this router, the boot process ends in setup mode. What is a possible problem?There is insufficient RAM for the IOS to load on this router.A password recovery process should be done on this router.The bootstrap version and the version of the IOS are different.The IOS image is damaged and must be reloaded using tftpdnld.The configuration register is set to ignore the startup configuration.4. Which option correctly defines the capacity through the local loop guaranteed to a customer by the service provider?BEDECIRCBIR5.Refer to the exhibit. A host connected to Fa0/0 is unable to acquire an IP address from the DHCP server. The output of the debug ip dhcp server command shows "DHCPD: there is no address pool for 10.1.1.1". What is the problem?The 10.1.1.1 address is already configured on Fa0/0.The default router for the 10Network pool is incorrect.The ip helper-address must be added to Fa0/0 interface.The pool of addresses for the 10Network pool is incorrect.6. Which data link layer encapsulation protocol is used by default for serial connections between two Cisco routers?ATMFrame RelayHDLCPPPSDLCRefer to the exhibit. Which statement correctly describes how Router1 processes an FTP request that enters interface s0/0/0 and is destined for an FTP server at IP address 192.168.1.5?The router matches the incoming packet to the statement that was created by the access-list 201 deny icmp 192.168.1.0 0.0.0.255 any command, continues comparing the packet to the remaining statements in ACL 201 to ensure that no subsequent statements allow FTP, and then the router drops the packet.The router reaches the end of ACL 101 without matching a condition and drops the packet because there is no statement that was created by the access-list 101 permit ip any any command.The router matches the incoming packet to the statement that was created by the access-list 101 permit ip any 192.168.1.0 0.0.0.255 command and allows the packet into the router.It matches the incoming packet to the statement that was created by the access-list 201 permit ip any any command and allows the packet into the router.8. Compared with IDS systems, what can IPS systems do to provide further protection of computer systems?detect potential attacksstop the detected attack from executingupdate OS patches for computer systemsscan computer systems for viruses and spyware9. Which IEEE 802.16 broadband wireless technology allows users to connect to the ISP at speeds comparable to DSL and cable?Wi-FisatelliteWiMAXMetro Ethernet10. A network administrator has changed the VLAN configurations on his network switches over the past weekend. How can the administrator determine if the additions and changes improved performance and availability on the company intranet?Conduct a performance test and compare with the baseline that was established previously.Interview departmental secretaries and determine if they think load time for web pages has improved.Determine performance on the intranet by monitoring load times of company web pages from remote sites.Compare the hit counts on the company web server for the current week to the values that were recorded in previous weeks.11.Refer to the exhibit. What is the meaning of the term dynamic in the output of the command?The bandwidth capability of the interface increases and decreases automatically based on BECNs.The Serial0/0/1 interface acquired 172.16.3.1 from a DHCP server.The mapping between DLCI 100 and 172.16.3.1 was learned through Inverse ARP.DLCI 100 will automatically adapt to changes in the Frame Relay cloud.12. Which type of ACL will permit traffic inbound into a private network only if an outbound session has already been established between the source and destination?extendedreflexivestandardtime-based13. Which two statements are true about IPv6 link local addresses? (Choose two.)They begin with the 2000::/3 prefix.They begin with the FE80::/10 prefix.They are assigned by IANA to an organization.They must be manually configured by the administrator.They are assigned to a host by a stateless autoconfiguration process.14. A company is looking for a WAN solution to connect its headquarters site to four remote sites. What are two advantages that dedicated leased lines provide compared to a shared Frame Relay solution? (Choose two.)reduced jitterreduced costsreduced latencythe ability to burst above guaranteed bandwidththe ability to borrow unused bandwidth from the leased lines of other customers15.Refer to the exhibit. A network administrator is trying to connect R1 remotely to make configuration changes. Based on the exhibited command output, what will be the result when attempting to connect to R1?failure to connect due to Telnet not being enabledfailure to connect due to incomplete configuration for Telneta successful connection and ability to make configuration changesa successful connection but inability to make configuration changes because of the absence of an enable secret password16. What are two effective measures for securing routers? (Choose two.)Protect all active router interfaces by configuring them as passive interfaces.Configure remote administration through VTY lines for Telnet access. Use quotes or phrases to create pass phrases.Disable the HTTP server service.Enable SNMP traps.17. An issue of response time has recently arisen on an application server. The new release of a software package has also been installed on the server. The configuration of the network has changed recently. To identify the problem, individuals from both teams responsible for the recent changes begin to investigate the source of the problem. Which statement applies to this situation?Scheduling will be easy if the network and software teams work independently.It will be difficult to isolate the problem if two teams are implementing changes independently.Results from changes will be easier to reconcile and document if each team works in isolation.Only results from the software package should be tested as the network is designed to accommodate the proposed software platform.Refer to the exhibit. From the output of the show interfaces and ping commands, at which layer of the OSI model is a fault indicated?applicationtransportnetworkdata linkphysical19. Which technology is used to dynamically map next hop, network layer addresses to virtual circuits in a Frame Relay network?Inverse ARPLMIDLCI20. An administrator learns of an e-mail that has been received by a number of users in the company. This e-mail appears to come from the office of the administrator. The e-mail asks the users to confirm their account and password information. Which type of security threat does this e-mail represent?crackingphishingphreakingspamming21.Refer to the exhibit. Which data transmission technology is being represented?TDMPPPHDLCSLIP22.Refer to the exhibit. Results of the show vlan and show vtp status commands for switches S1 and S2 are displayed in the exhibit. VLAN 11 was created on S1. Why is VLAN 11 missing from S2?There is a Layer 2 loop.The VTP domain names do not match.Only one switch can be in server mode.S2 has a higher spanning-tree priority for VLAN 11 than S1 does.23. What is the result of adding the global command servicepassword-encryption to the configuration of a router?Line passwords are encrypted with type 7 encryption.Enable passwords are encrypted with type 5 encryption.All services must provide an encrypted password to function.Only encrypted messages are allowed for router communication.24. While troubleshooting a problem with an e-mail server, an administrator observes that the switch port used by the server shows "up, line protocol up". The administrator cannot ping the server. At which layer of the OSI model is the problem most likely to be found?application layernetwork layerdata link layerphysical layer25. Where does a service provider assume responsibility from a customer for a WAN connection?local loopDTE cable on routerdemarcation pointdemilitarized zone26. What will be the result of adding the command ip dhcp excluded-address 192.168.24.1 192.168.24.5to the configuration of a local router that has been configured as a DHCP server?Traffic that is destined for 192.168.24.1 and 192.168.24.5 will be dropped by the router.Traffic will not be routed from clients with addresses between192.168.24.1 and 192.168.24.5.The DHCP server will not issue the addresses ranging from 192.168.24.1 to 192.168.24.5.The router will ignore all traffic that comes from the DHCP servers with addresses 192.168.24.1 and 192.168.24.5.27.Refer to the exhibit. Partial results of the show access-lists and show ip interface FastEthernet 0/1 commands for router Router1 are shown. There are no other ACLs in effect. Host A is unable to telnet to host B. Which action will correct the problem but still restrict other traffic between the two networks?Apply the ACL in the inbound direction.Apply the ACL on the FastEthernet 0/0 interface.Reverse the order of the TCP protocol statements in the ACL.Modify the second entry in the list to permit tcp host 172.16.10.10 any eq telnet .28.Refer to the exhibit. The corporate network that is shown has been assigned network 172.16.128.0/19 for use at branch office LANs. If VLSM is used, what mask should be used for addressing hosts at Branch4 with minimal waste from unused addresses?/19/20/21/22/23/2429.Refer to the exhibit. RIPv2 has been configured on all routers in the network. Routers R1 and R3 have not received any RIP routing updates. What will fix the issue?Enable RIP authentication on R2.Issue the ip directed-broadcast command on R2.Change the subnet masks to 10.11.12.0/8 and 172.16.40.0/16 on R2.Enable CDP on R2 so that the other routers will receive routing updates.30.Refer to the exhibit. This serial interface is not functioning correctly. Based on the output shown, what is the most likely cause?improper LMI typeinterface resetPPP negotiation failureunplugged cable31. Which statement is true about PAP in the authentication of a PPP session?PAP uses a two-way handshake.The password is unique and random.PAP conducts periodic password challenges.PAP uses MD5 hashing to keep the password secure.32. An administrator is configuring a dual stack router with IPv6 and IPv4 using RIPng. The administrator receives an error message when trying to enter the IPv4 routes into RIPng. What is the cause of the problem?When IPv4 and IPv6 are configured on the same interface, all IPv4 addresses are over-written in favor of the newer technology.Incorrect IPv4 addresses are entered on the router interfaces.RIPng is incompatible with dual-stack technology.IPv4 is incompatible with RIPng.33. What is tunneling?using digital certificates to ensure that data endpoints are authentic creating a hash to ensure the integrity of data as it traverses a networkusing alternate paths to avoid access control lists and bypass security measuresencapsulating an entire packet within another packet for transmission over a network34. Which statement is true about NCP?Link termination is the responsibility of NCP.Each network protocol has a corresponding NCP.NCP establishes the initial link between PPP devices.NCP tests the link to ensure that the link quality is sufficient. 35.Refer to the exhibit. A network administrator is creating a prototype to verify the new WAN design. However, the communication between the two routers cannot be established. Based on the output of the commands, what can be done to solve the problem?Replace the serial cable .Replace the WIC on RA.Configure RA with a clock rate command.Issue a no shutdown interface command on RB.36.Refer to the exhibit. Based on the output as shown, which two statements correctly define how the router will treat Telnet traffic that comes into interface FastEthernet 0/1? (Choose two).Telnet to 172.16.10.0/24 is denied.Telnet to 172.16.20.0/24 is denied.Telnet to 172.16.0.0/24 is permitted.Telnet to 172.16.10.0/24 is permitted.Telnet to 172.16.20.0/24 is permitted.37. Which Frame Relay flow control mechanism is used to signal routers that they should reduce the flow rate of frames?DEBECIRFECNCBIR38.Refer to the exhibit. A network administrator configures a standard access control list on Router1 to prohibit traffic from the 192.168.0.0/24 network from reaching the Internet. The access control list also permits traffic from the 192.168.0.0/24 network to reach the 192.168.1.0/24 network. On which interface and in which direction should the access control list be applied?interface Fa0/0, inboundinterface Fa0/0, outboundinterface S0/0/0, inboundinterface S0/0/0, outbound39. Which configuration on the vty lines provides the best security measure for network administrators to remotely access the core routers at headquarters?Answer: 3nd option 40.Refer to the exhibit. What can be concluded from the exhibited output of the debug ip nat command?The 10.1.1.225 host is exchanging packets with the 192.168.0.10 host.The native 10.1.200.254 address is being translated to 192.168.0.10.The 192.168.0.0/24 network is the inside network.Port address translation is in effect.41. A network administrator is instructing a technician on best practices for applying ACLs. Which suggestion should the administrator provide?Named ACLs are less efficient than numbered ACLs.Standard ACLs should be applied closest to the core layer.ACLs applied to outbound interfaces are the most efficient.Extended ACLs should be applied closest to the source that is specified by the ACL.42.Refer to the exhibit. Headquarters is connected through the Internet to branch office A and branch office B. Which WAN technology would be best suited to provide secure connectivity between headquarters and both branch offices?ATMVPNISDNFrame Relaybroadband DSL43. Which three physical network problems should be checked when a bottom-up troubleshooting approach has been chosen to troubleshoot network performance? (Choose three.)cable connectivityhigh collision countsSTP failures and loopsaddress mapping errorshigh CPU utilization ratesexcess packets that are filtered by the firewall44.Refer to the exhibit. A network administrator is attempting to configure a Frame Relay network. The administrator enters the commands as shown in the exhibit on R2, but the Frame Relay PVCs are inactive. What is the problem?The incorrect DLCI numbers are being configured on R2.The S0/0/0 interface on R2 needs to be point-to-point.The frame-relay map commands are missing the cisco keyword at the end.A single router interface cannot connect to more than one Frame Relay peer at a time.45. Which IP address and wildcard mask would be used in an ACL to block traffic from all hosts on the same subnet as host 192.168.16.43/28?access-list 10 deny 192.168.16.0 0.0.0.31access-list 10 deny 192.168.16.16 0.0.0.31access-list 10 deny 192.168.16.32 0.0.0.16access-list 10 deny 192.168.16.32 0.0.0.15access-list 10 deny 192.168.16.43 0.0.0.1646. Which combination of Layer 2 protocol and authentication should be used to establish a link without sending authentication information in plain text between a Cisco and a non-Cisco router?PPP with PAPPPP with CHAPHDLC with PAPHDLC with CHAP47. When would the multipoint keyword be used in Frame Relay PVCs configuration?when global DLCIs are in usewhen using physical interfaceswhen multicasts must be supportedwhen participating routers are in the same subnet48. A network technician analyzes the network and notices late collisions. The collisions occur accompanied by jabber that originates from the server. What is the likely cause of the problem?faulty switch portweb server CPU overloadfaulty NIC in the web servermisconfiguration of web server services49.Refer to the exhibit. R1 is performing NAT overload for the 10.1.1.0/24 inside network. Host A has sent a packet to the web server. What is the destination IP address of the return packet from the web server?10.1.1.2:1234172.30.20.1:1234172.30.20.1:3333192.168.1.2:8050.Refer to the exhibit. All devices are configured as shown in the exhibit. PC1 is unable to ping the default gateway. What is the cause of the problem?The default gateway is in the wrong subnet.STP has blocked the port that PC1 is connected to.Port Fa0/2 on S2 is assigned to the wrong VLAN.S2 has the wrong IP address assigned to the VLAN30 interface.51. When Frame Relay encapsulation is used, what feature provides flow control and exchanges information about the status of virtual circuits?LCPLMIDLCIInverse ARP52. A network administrator is tasked with maintaining two remote locations in the same city. Both locations use the same service provider and have the same service plan for DSL service. When comparing download rates, it is noticed that the location on the East side of town has a faster download rate than the location on the West side of town. How can this be explained?The West side has a high volume of POTS traffic.The West side of town is downloading larger packets.The service provider is closer to the location on the East side.More clients share a connection to the DSLAM on the West side.。
Which combination of Layer 2 protocol and authentication should be used to establish a link without sending authentication information in plain text between a Cisco and a non-Cisco router?
PPP with PAP
PPP with CHAP HDLC with PAP HDLC with CHAP
2At what physical location does the responsibilty for a WAN connection change from the user to the service provider? demilitarized zone (DMZ)
demarcation point local loop cloud
3
Refer to the exhibit. A network administrator has issued the commands that are shown on Router1 and Router2. A later review of the routing tables reveals that neither router is learning the LAN network of the neighbor router. What is most likely the problem with the RIPng configuration?
The serial interfaces are in different subnets.
The RIPng process is not enabled on interfaces. The RIPng network command is not configured. The RIPng processes do not match between Router1 and Router2.
4What effect would the Router1(config-ext-nacl)# permit tcp 172.16.4.0 0.0.0.255 any eq www command have when implemented inbound on the f0/0 interface?
All TCP traffic is permitted, and all other traffic is denied.
The command is rejected by the router because it is incomplete. All traffic from 172.16.4.0/24 is permitted anywhere on any port. Traffic originating from 172.16.4.0/24 is permitted to all TCP port 80 destinations.
5Which three statements accurately describe a security policy? (Choose three.) It creates a basis for legal action if necessary. It defines a process for managing security violations. It defines acceptable and unacceptable use of network resources. The remote access policy is a component of the security policy that governs acceptable use of e-mail systems. It is kept private from users to prevent the possibility of circumventing security measures. It provides step-by-step procedures to harden routers and other network devices.
6
Refer to the exhibit. What can be concluded from the exhibited output of the debug ip nat command? The 10.1.1.225 host is exchanging packets with the 192.168.0.10 host.
The native 10.1.200.254 address is being translated to 192.168.0.10. The 192.168.0.0/24 network is the inside network. Port address translation is in effect.
7Which statement about a VPN is true? VPN link establishment and maintenance is provided by LCP.
DLCI addresses are used to identify each end of the VPN tunnel. VPNs use virtual Layer 3 connections that are routed through the Internet. Only IP packets can be encapsulated by a VPN for tunneling through the Internet.
8
Refer to the exhibit. From the output of the show interface commands, at which OSI layer is a fault indicated? application
transport network data link physical
9
Refer to the exhibit. You are a network administrator who has been tasked with completing the Frame Relay topology that interconnects two remote sites. How should the point-to-point subinterfaces be configured on HQ to complete the topology? HQ(config-subif)#frame-relay interface-dlci 103 on Serial 0/0/0.1 HQ(config-subif)#frame-relay interface-dlci 203 on Serial 0/0/0.2 HQ(config-subif)#frame-relay interface-dlci 301 on Serial 0/0/0.1 HQ(config-subif)# frame-relay interface-dlci 302 on Serial 0/0/0.2 HQ(config-subif)#frame-relay map ip 172.16.1.1 103 broadcast on Serial 0/0/0.1 HQ(config-subif)#frame-relay map ip 172.16.2.2 203 broadcast on Serial 0/0/0.2 HQ(config-subif)#frame-relay map ip 172.16.1.1 301 broadcast on Serial 0/0/0.1 HQ(config-subif)#frame-relay map ip 172.16.2.2 302 broadcast on Serial 0/0/0.2
10
Refer to the exhibit. Which statement correctly describes how Router1 processes an FTP request entering interface s0/0/0, destined for an FTP server at IP address 192.168.1.5? It matches the incoming packet to the access-list 201 permit any any statement and allows the packet into the router. It reaches the end of ACL 101 without matching a condition and drops the packet because there is no access-list 101 permit any any statement. It matches the incoming packet to the access-list 101 permit ip any 192.168.1.0 0.0.0.255 statement, ignores the remaining statements in ACL 101, and allows the packet into the router.