
外文原文
Based on infrared alarm technology security systems
1 the introduction
1.1 the research significance of this topic research situation at home and abroad .
With the development of society and science and technology unceasing development, people's living standards been improved greatly, and to the private property protection means in the unceasing enhancement, the intelligent facilities for anti-theft puts forward new requirements. This design is to meet the need of modern residential anti-theft designed family electronic alarm system. It in previous devices based on improved greatly, because use the single-chip processor signal, not only can used for single residential area, also can be used in a large-scale residential security systems. It's the job of the performance is good, do not appear to report and misstatement phenomenon, safe and reliable.
In our country, the present market condition alarm basically has triggered alarm system pressure switch electron and alarm system and pressure shading triggered alarm system, etc. Various kinds of alarm, but this several common alarm there are some shortcomings. This system USES a human pyroelectric infrared sensor in the human body detector in the flied, passive pyroelectric infrared detectors because of its low cost, easy fabrication, low cost, installation is more convenient, anti-theft performance is stable and high sensitivity, safe and reliable, has attracted broad family characteristics such as popular with the customers. And alarms installation concealment, not easily by rogue found.
1.2 infrared alarm technology introduction
1.2.1 nature objects of the infrared radiation
The nature of any object, as long as the temperature above absolute zero (273 ℃), constantly outward issued infrared radiation, and travel at the speed of light energy. Object radiate outward infrared radiation of energy and the object of temperature and infrared radiant wavelength. Assuming objects launching infrared radiation of peak wavelength for a few, its temperature for T, the radiation energy equals infrared radiation of peak wavelength gerben and object product temperature T. This product is a constant, namely:
The higher the temperature of the objects, emit infrared radiation of the smaller peak wavelength, send out infrared radiation energy is bigger also.
1.2.2.pyroelectric effect
Passive infrared detector also called pyroelectric infrared detector, its main working principle is pyroelectric effect. Pyroelectric effect means if make some strong dielectric material (such as qin batio3, qin wrong acid lead P (zT), etc.) of the surface temperature changes, then with the temperature rise or fall, material surface occurs polarization, namely on the surface of the charge will be produced change, and material surface charge lost balance and eventually charge will change withvoltage or current form output.
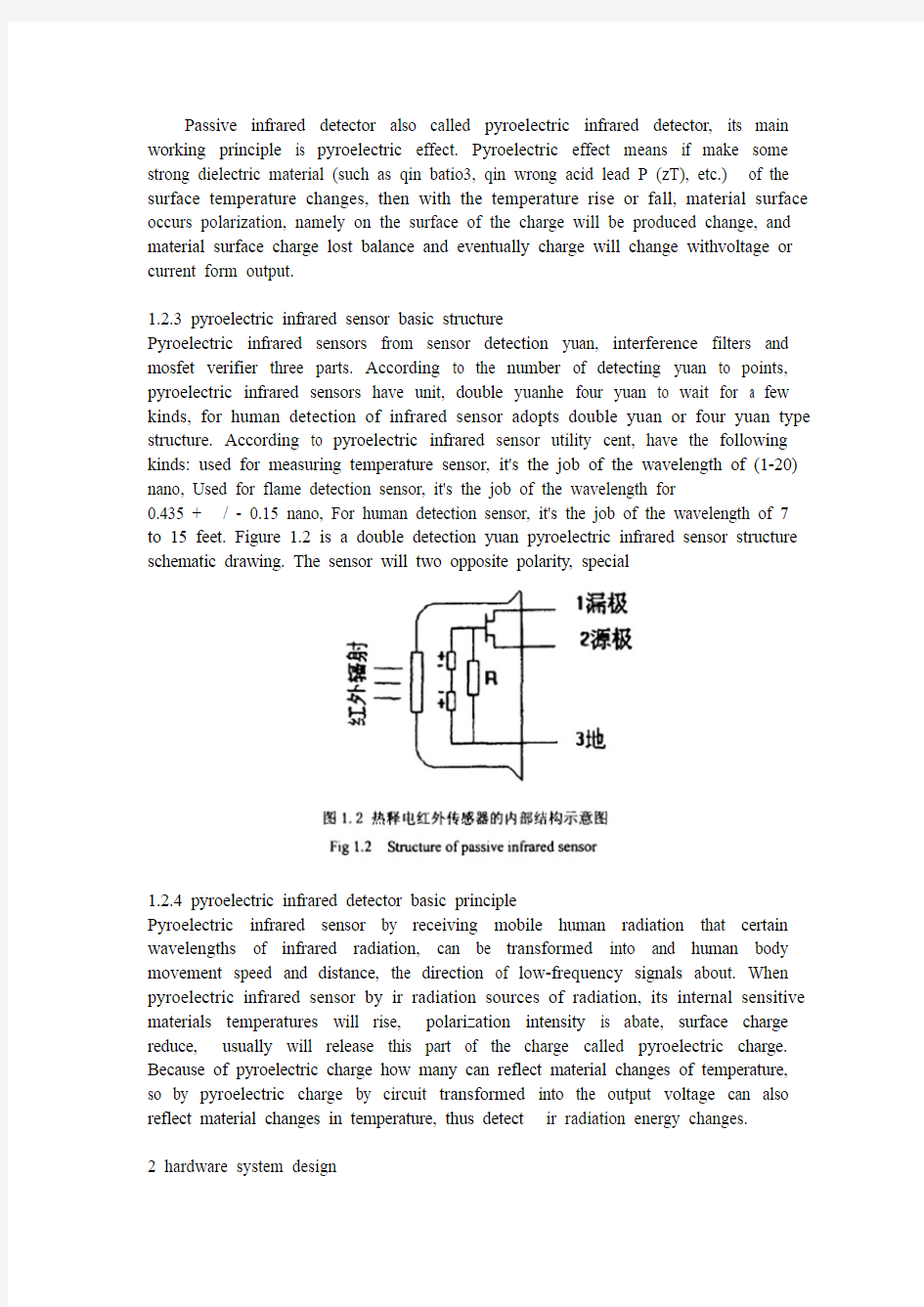
1.2.3 pyroelectric infrared sensor basic structure
Pyroelectric infrared sensors from sensor detection yuan, interference filters and mosfet verifier three parts. According to the number of detecting yuan to points, pyroelectric infrared sensors have unit, double yuanhe four yuan to wait for a few kinds, for human detection of infrared sensor adopts double yuan or four yuan type structure. According to pyroelectric infrared sensor utility cent, have the following kinds: used for measuring temperature sensor, it's the job of the wavelength of (1-20) nano, Used for flame detection sensor, it's the job of the wavelength for
0.435 + / - 0.15 nano, For human detection sensor, it's the job of the wavelength of 7 to 15 feet. Figure 1.2 is a double detection yuan pyroelectric infrared sensor structure schematic drawing. The sensor will two opposite polarity, special
1.2.4 pyroelectric infrared detector basic principle
Pyroelectric infrared sensor by receiving mobile human radiation that certain wavelengths of infrared radiation, can be transformed into and human body movement speed and distance, the direction of low-frequency signals about. When pyroelectric infrared sensor by ir radiation sources of radiation, its internal sensitive materials temperatures will rise, polarization intensity is abate, surface charge reduce, usually will release this part of the charge called pyroelectric charge. Because of pyroelectric charge how many can reflect material changes of temperature, so by pyroelectric charge by circuit transformed into the output voltage can also reflect material changes in temperature, thus detect ir radiation energy changes.
2 hardware system design
2.1 infrared anti-theft alarm system hardware design
Because this design focuses on family guard against theft, real-time monitoring of a narrower range, so this design by simply using a passive infrared detector is enough. Therefore, infrared intelligent anti-theft alarm system, and the specific design requirements for:
(1)completes to high sensitive infrared sensor design, make its can warning of what happened real-time and accurate detection.
(2) automatic alarm (automatic dial-up alarm audible and visual alarm). We design the system must have the following function module:
1.passive infrared detector,
2.sound-light alarm,
3.telephone automatic dial-up function;
4.continued uninterrupted power supply,
According to the system to complete functions, we adopt single chip microcomputer as the core of the system unit, electronic detection, intelligent control and telephone tong
2.2 telephone automatic dial-up alarm circuit design
In order to simplify the whole system design process, we do not adopt MT880 chip dialing. Realization process is as follows:
First in telephone storage inside put on domestic host cell phone number
or alarm call 110. From MCU pins p2.0 and p2.1 drawn two wiring connect relays, a pick telephone keyboard MianDiJian, another connect telephone keyboard keys, automatic weighing dial because the phone keypad scanning is similar microcontroller keypad scanning, so can make SCM give fitst p2.0 a signal, lets telephone h-f, then give the p2.1 a signal, let relay connected, automatic weighing dial the key a potential, let telephone automatic dial-up, so they could finish the system alarm function.
2.3 system working principle
The whole system hardware part mainly includes six parts: MCU module; Infrared detector, Acousto-optic alarm circuit; Telephone automatic dial-up alarm circuit; Power supply circuit, Working state instructions circuit. Its system working principle for: the sensors will be detected signals to lead signal processor processing, microcontroller judgment to P1.0 mouth have pulse falling edge jumping signal immediately transferred to the acousto-optic alarm program, at this moment, the red light buzzer alarm rapid flashes, lasted 30s. In the 30s inside if someone press the switch, then eliminate alarm remove alarm. if this time no one remove alarm, the proof nobody at home in 30s system will automatically triggers telephone finish the whole system of police work project. Later, microcontroller will continue to cycle back ? sentenced
2.4 system total diagram
In proteus simulation system, the system circuit by crystals circuit, sound-light alarm circuit composed. Among them, we use connect the dedication of the P1.0 simulated infrared sensors, requirement when switch when pressed by the high jump, level is low, the equivalent of, sensor detects the state of man, the telephone line with P2.0 and P2.1 derivation, here without simulation telephone circuit diagram.
Figure 3.5
3 software system design
3.1 control module design program
Microcomputer in the initial plus electric, voltage is not steady state, causing instability, at this time the SCM in commonly after power up to system with a piece of delay. Time-lapse after detecting P1 mouth microcontroller state, detection level
signal whether mutations, if is then calls the police processing procedure, including automatic dialup audible and visual alarm procedures, if no changes, ChuXiang level detection continues to P1 mouth state.
Figure 4.1 main program flowchart
3.2 system development adopted by the programming and commissioning of the platform
This system language using assembly language preparation, so choose wave6000, he has the microcontroller program edit, compile and debugging, etc., and generate hexadecimal. Files, through: machine TOPWIN burning software writeable microcontroller program memory. The simulation software use Proteus, he is from Britain Labcenter electronics company EDA software. The circuit of the simulation is interactive, aiming at the microprocessor application, still can directly based on schematic diagram of the virtual prototype programming, and implementing software source code level of real-time debugging, if have display and output, still can see after the operation of input and output effect.
4 system debugging and test
4.1 software debugging
Adopt modularization program design thought, fitst debugging subroutines, then gradually superposition debugging, through Proteus simulation software debugging, proof program can realize its function.
4.2 system debugging
Through the circuit of welding, each module function commissioning. I put the hardware that occur errors adjusted, in addition, infrared that piece, because is employing redirected of pyroelectric switch modified, so in must be taping photoconductive resistance to rise, has arrived in the days and nights can alarm function. The total system commissioning, through, error meets the requirement.
5 closing
This system uses a pyroelectric infrared sensor, its make simple low cost and installation are more convenient and anti-theft performance is stable and strong anti-jamming capability, high sensitivity, safe and reliable.
外文翻译
基于红外报警技术的防盗系统
1 绪论
1.1 本课题的研究现状及研究意义
随着社会的不断进步和科学技术不断发展,人们生活水平得到很大的提高,对私有财产的保护手段在不断的增强,对防盗设施的智能化提出了新的要求。本设计就是为了满足现代住宅防盗的需要而设计的家庭式电子防盗系统。它在以前的防盗器基础上进行了很大的改进,由于使用了单片机做信号处理器,不但可以用于单一的住宅区,也可以用于较大规模住宅区的防盗系统。它的工作性能好,不易出现不报和误报现象,安全可靠。
在我国,目前市面上报警器主要有压力触发式防盗报警器开关电子防盗报警器和压力遮光触发式防盗报警器等各种报警器,但这几种比较常见的报警器都存在一些缺点。本系统采用了人体热释电红外传感器,在人体探测器领域中,被动式热释电红外探测器因其价格低廉、制作简单、成本低,安装比较方便,防盗性能比较稳定,灵敏度高、安全可靠等特点,备受广大家庭用户的欢迎。而且防盗器安装隐蔽,不易被盗贼发现。
1.2 红外报警技术简介
1.2.1自然界物体的红外辐射特性
自然界的任何物体,只要温度高于绝对零度(273℃),总是不断地向外发出红外辐射,并以光的速度传播能量。物体向外辐射红外辐射的能量与物体的温度和红外辐射的波长有关。假定物体发射红外辐射的峰值波长为几,,它的温度为T,则辐射能量等于红外辐射的峰值波长戈与物体温度T的乘积。这一乘积为一常数,即:
物体的温度越高,它所发射的红外辐射的峰值波长越小,发出红外辐射的能量也越大。
1.2.2热释电效应
被动式红外探测器又称为热释电红外探测器,其主要工作原理便是热释电效应。热释电效应是指如果使某些强介电质材料(如钦酸钡、钦错酸铅P(zT)等)的
表面温度发生变化,则随着温度的上升或下降,材料表面发生极化,即表面上就会产生电荷的变化,从而使物质表面电荷失去平衡,最终电荷变化将以电压或电流形式输出。
1.2.3热释电红外传感器的基本结构
热释电红外传感器由传感探测元、干涉滤光片和场效应管匹配器三部分组成。按照探测元的数目来分,热释电红外传感器有单元、双元和四元等几种,用于人体探测的红外传感器采用双元或四元式结构。按照热释电红外传感器的用途来分,有以下几种:用于测量温度的传感器,它的工作波长为(1-20)纳米;用于火焰探测的传感器,它的工作波长为0.435+/-0.15纳米;用于人体探测的传感器,它的工作波长为7-15脚。图1.2是一个双探测元的热释电红外传感器的结构示意图。该传感器将两个极性相反、特性一致的探测元串接在一起,目的在于消除因环境温度和自身变化引起的干扰。它利用两个极性相反、大小相等的干扰信号在内部相互抵消的原理,使传感器起到补偿作用。当人体处于静止状态时,两元件极化程度相同,相互抵消;当人体移动时,两元件极化程度不同,净输出电压不为0,从而达到探测移动人体的目的。
1.2.4热释电红外探测器的基本原理
热释电红外传感器通过接收移动人体辐射出的特定波长的红外线,可以将其转化为与人体运动速度,距离,方向有关的低频电信号。当防范区域内没有移动的人体时,由于所有的背景物体(如墙壁、家具等)在室温下红外辐射的能量比较小,而且基本上是稳定的,所以不能触发报警器。当有人体突然进入探测区域时,会造成红外辐射能量的突然变化,红外探测器将接收到的活动人体与背景物体之间的红外热辐射能量的变化转化为相应的电信号,电信号的大小,决定于敏感元
件温度变化的快慢,经过后级比较器与状态控制器产生相应的输出信号U。,送往报警器,发出报警信号。红外探测器的探测波长为8-14微米,人体的红外辐射波长正好处于这个范围之内,因此能较好的探测到活动的人体。
2 硬件系统设计
2.1 红外防盗报警系统的硬件设计
由于本设计侧重于家庭防盗,实时监控的范围比较狭窄,因此本设计只需使用一个被动式红外探测器就足够。为此,红外智能防盗报警系统的具体设计要求为:
(1) 完成对高灵敏度红外传感器的设计,使其能对所发生的警情进行实时、准确的探测。
(2)可进行自动报警(自动拨号报警和声光报警)。
我们设计此系统必须具有以下功能模块:
1. 被动式红外探测器;
2.声光报警;
3. 电话自动拨号功能;
4. 持续不间断供电;
根据系统所要完成的功能,我们采用单片机作为系统的核心单元,将电子探测、智能控制和电话通讯技术相结合,形成一个两级联网通讯的防盗报警系统。系统总体架构简图如图3.1所示。
2.2电话自动拨号报警电路的设计
为了简化整个系统的设计流程,我们不采用MT880芯片拨号。具体实现过程如下:
先在电话机的存储里面存上家庭主人的手机号码或报警电话110.从单片机
的引脚p2.0和p2.1引出两条接线接继电器,一条接电话机键盘的免提键,另外一条接电话机键盘的自动重拨键,由于电话键盘扫描是类似单片机键盘扫描,所以可以让单片机先给p2.0一个信号,让电话免提,然后再给p2.1一个信号,让继电器接通,给自动重拨键一个电位,让电话机自动拨号,这样就能完成系统报警功能。
2.3系统工作原理
整个系统的硬件部分主要包括六个部分:MCU模块;红外探测器;声光报警电路;电话自动拨号报警电路;电源电路;工作状态指示电路。其系统工作原理为:传感器将探测到的信号送到前置信号处理器处理,单片机判断到P1.0口有脉冲下降沿跳变信号时立刻转到声光报警程序,这时蜂鸣器报警,红灯快速闪烁,过程持续30s。在这30s内如果有人按下消除报警的开关,则解除报警。如果这段时间没有人解除报警,则证明家里没有人,系统会在30s后自动触发电话机报警,完成整个系统的工作工程。之后,单片机会继续循环回到判断P1.0口,等待下一次报警。
2.4 系统总的电路图
在用proteus模拟系统时,系统电路由晶振电路,声光报警电路组成。其中,我们用接P1.0的开光模拟红外线传感器,要求当开关按下时,电平由高跳到低,这相当于,传感器检测到人的状态,电话线用P2.0和P2.1引出,在这里不模拟电话线路图。
华北电力大学科技学院 毕业设计(论文)附件 外文文献翻译 学号:121912020115姓名:彭钰钊 所在系别:动力工程系专业班级:测控技术与仪器12K1指导教师:李冰 原文标题:Infrared Remote Control System Abstract 2016 年 4 月 19 日
红外遥控系统 摘要 红外数据通信技术是目前在世界范围内被广泛使用的一种无线连接技术,被众多的硬件和软件平台所支持。红外收发器产品具有成本低,小型化,传输速率快,点对点安全传输,不受电磁干扰等特点,可以实现信息在不同产品之间快速、方便、安全地交换与传送,在短距离无线传输方面拥有十分明显的优势。红外遥控收发系统的设计在具有很高的实用价值,目前红外收发器产品在可携式产品中的应用潜力很大。全世界约有1亿5千万台设备采用红外技术,在电子产品和工业设备、医疗设备等领域广泛使用。绝大多数笔记本电脑和手机都配置红外收发器接口。随着红外数据传输技术更加成熟、成本下降,红外收发器在短距离通讯领域必将得到更广泛的应用。 本系统的设计目的是用红外线作为传输媒质来传输用户的操作信息并由接收电路解调出原始信号,主要用到编码芯片和解码芯片对信号进行调制与解调,其中编码芯片用的是台湾生产的PT2262,解码芯片是PT2272。主要工作原理是:利用编码键盘可以为PT2262提供的输入信息,PT2262对输入的信息进行编码并加载到38KHZ的载波上并调制红外发射二极管并辐射到空间,然后再由接收系统接收到发射的信号并解调出原始信息,由PT2272对原信号进行解码以驱动相应的电路完成用户的操作要求。 关键字:红外线;编码;解码;LM386;红外收发器。 1 绪论
Statistical hypothesis testing Adriana Albu,Loredana Ungureanu Politehnica University Timisoara,adrianaa@aut.utt.ro Politehnica University Timisoara,loredanau@aut.utt.ro Abstract In this article,we present a Bayesian statistical hypothesis testing inspection, testing theory and the process Mentioned hypothesis testing in the real world and the importance of, and successful test of the Notes. Key words Bayesian hypothesis testing; Bayesian inference;Test of significance Introduction A statistical hypothesis test is a method of making decisions using data, whether from a controlled experiment or an observational study (not controlled). In statistics, a result is called statistically significant if it is unlikely to have occurred by chance alone, according to a pre-determined threshold probability, the significance level. The phrase "test of significance" was coined by Ronald Fisher: "Critical tests of this kind may be called tests of significance, and when such tests are available we may discover whether a second sample is or is not significantly different from the first."[1] Hypothesis testing is sometimes called confirmatory data analysis, in contrast to exploratory data analysis. In frequency probability,these decisions are almost always made using null-hypothesis tests. These are tests that answer the question Assuming that the null hypothesis is true, what is the probability of observing a value for the test statistic that is at [] least as extreme as the value that was actually observed?) 2 More formally, they represent answers to the question, posed before undertaking an experiment,of what outcomes of the experiment would lead to rejection of the null hypothesis for a pre-specified probability of an incorrect rejection. One use of hypothesis testing is deciding whether experimental results contain enough information to cast doubt on conventional wisdom. Statistical hypothesis testing is a key technique of frequentist statistical inference. The Bayesian approach to hypothesis testing is to base rejection of the hypothesis on the posterior probability.[3][4]Other approaches to reaching a decision based on data are available via decision theory and optimal decisions. The critical region of a hypothesis test is the set of all outcomes which cause the null hypothesis to be rejected in favor of the alternative hypothesis. The critical region is usually denoted by the letter C. One-sample tests are appropriate when a sample is being compared to the population from a hypothesis. The population characteristics are known from theory or are calculated from the population.
Inventory management Inventory Control On the so-called "inventory control", many people will interpret it as a "storage management", which is actually a big distortion. The traditional narrow view, mainly for warehouse inventory control of materials for inventory, data processing, storage, distribution, etc., through the implementation of anti-corrosion, temperature and humidity control means, to make the custody of the physical inventory to maintain optimum purposes. This is just a form of inventory control, or can be defined as the physical inventory control. How, then, from a broad perspective to understand inventory control? Inventory control should be related to the company's financial and operational objectives, in particular operating cash flow by optimizing the entire demand and supply chain management processes (DSCM), a reasonable set of ERP control strategy, and supported by appropriate information processing tools, tools to achieved in ensuring the timely delivery of the premise, as far as possible to reduce inventory levels, reducing inventory and obsolescence, the risk of devaluation. In this sense, the physical inventory control to achieve financial goals is just a means to control the entire inventory or just a necessary part; from the perspective of organizational functions, physical inventory control, warehouse management is mainly the responsibility of The broad inventory control is the demand and supply chain management, and the whole company's responsibility. Why until now many people's understanding of inventory control, limited physical inventory control? The following two reasons can not be ignored: First, our enterprises do not attach importance to inventory control. Especially those who benefit relatively good business, as long as there is money on the few people to consider the problem of inventory turnover. Inventory control is simply interpreted as warehouse management, unless the time to spend money, it may have been to see the inventory problem, and see the results are often very simple procurement to buy more, or did not do warehouse departments . Second, ERP misleading. Invoicing software is simple audacity to call it ERP, companies on their so-called ERP can reduce the number of inventory, inventory control, seems to rely on their small software can get. Even as SAP, BAAN ERP world, the field of
文献信息: 文献标题:Challenges and opportunities affecting the future of human resource management(影响人力资源管理未来的挑战和机遇) 国外作者:Dianna L. Stone,Diana L. Deadrick 文献出处:《Human Resource Management Review》, 2015, 25(2):139-145 字数统计:英文3725单词,21193字符;中文6933汉字 外文文献: Challenges and opportunities affecting the future of human resource management Abstract Today, the field of Human Resource Management (HR) is experiencing numerous pressures for change. Shifts in the economy, globalization, domestic diversity, and technology have created new demands for organizations, and propelled the field in some completely new directions. However, we believe that these challenges also create numerous opportunities for HR and organizations as a whole. Thus, the primary purposes of this article are to examine some of the challenges and opportunities that should influence the future of HR. We also consider implications for future research and practice in the field. Keywords: Future of human resource management, Globalization, Knowledge economy Diversity, Technology 1.Change from a manufacturing to a service or knowledge economy One of the major challenges influencing the future of HR processes is the change from a manufacturing to a service or knowledgebased economy. This new economy is characterized by a decline in manufacturing and a growth in service or knowledge as the core of the economic base. A service economy can be defined as a system based on buying and selling of services or providing something for others (Oxford
吉林化工学院理学院 毕业论文外文翻译English Title(Times New Roman ,三号) 学生学号:08810219 学生姓名:袁庚文 专业班级:信息与计算科学0802 指导教师:赵瑛 职称副教授 起止日期:2012.2.27~2012.3.14 吉林化工学院 Jilin Institute of Chemical Technology
1 外文翻译的基本内容 应选择与本课题密切相关的外文文献(学术期刊网上的),译成中文,与原文装订在一起并独立成册。在毕业答辩前,同论文一起上交。译文字数不应少于3000个汉字。 2 书写规范 2.1 外文翻译的正文格式 正文版心设置为:上边距:3.5厘米,下边距:2.5厘米,左边距:3.5厘米,右边距:2厘米,页眉:2.5厘米,页脚:2厘米。 中文部分正文选用模板中的样式所定义的“正文”,每段落首行缩进2字;或者手动设置成每段落首行缩进2字,字体:宋体,字号:小四,行距:多倍行距1.3,间距:前段、后段均为0行。 这部分工作模板中已经自动设置为缺省值。 2.2标题格式 特别注意:各级标题的具体形式可参照外文原文确定。 1.第一级标题(如:第1章绪论)选用模板中的样式所定义的“标题1”,居左;或者手动设置成字体:黑体,居左,字号:三号,1.5倍行距,段后11磅,段前为11磅。 2.第二级标题(如:1.2 摘要与关键词)选用模板中的样式所定义的“标题2”,居左;或者手动设置成字体:黑体,居左,字号:四号,1.5倍行距,段后为0,段前0.5行。 3.第三级标题(如:1.2.1 摘要)选用模板中的样式所定义的“标题3”,居左;或者手动设置成字体:黑体,居左,字号:小四,1.5倍行距,段后为0,段前0.5行。 标题和后面文字之间空一格(半角)。 3 图表及公式等的格式说明 图表、公式、参考文献等的格式详见《吉林化工学院本科学生毕业设计说明书(论文)撰写规范及标准模版》中相关的说明。
文献翻译 原文 Combining JSP and Servlets The technology of JSP and Servlet is the most important technology which use Java technology to exploit request of server, and it is also the standard which exploit business application .Java developers prefer to use it for a variety of reasons, one of which is already familiar with the Java language for the development of this technology are easy to learn Java to the other is "a preparation, run everywhere" to bring the concept of Web applications, To achieve a "one-prepared everywhere realized." And more importantly, if followed some of the principles of good design, it can be said of separating and content to create high-quality, reusable, easy to maintain and modify the application. For example, if the document in HTML embedded Java code too much (script), will lead the developed application is extremely complex, difficult to read, it is not easy reuse, but also for future maintenance and modification will also cause difficulties. In fact, CSDN the JSP / Servlet forum, can often see some questions, the code is very long, can logic is not very clear, a large number of HTML and Java code mixed together. This is the random development of the defects. Early dynamic pages mainly CGI (Common Gateway Interface, public Gateway Interface) technology, you can use different languages of the CGI programs, such as VB, C / C + + or Delphi, and so on. Though the technology of CGI is developed and powerful, because of difficulties in programming, and low efficiency, modify complex shortcomings, it is gradually being replaced by the trend. Of all the new technology, JSP / Servlet with more efficient and easy to program, more powerful, more secure and has a good portability, they have been many people believe that the future is the most dynamic site of the future development of technology. Similar to CGI, Servlet support request / response model. When a customer submit a request to the server, the server presented the request Servlet, Servlet responsible for handling requests and generate a response, and then gave the server, and then from the server sent to
软件专业毕业论文外文文献中英文翻译 Object landscapes and lifetimes Tech nically, OOP is just about abstract data typing, in herita nee, and polymorphism, but other issues can be at least as importa nt. The rema in der of this sect ion will cover these issues. One of the most importa nt factors is the way objects are created and destroyed. Where is the data for an object and how is the lifetime of the object con trolled? There are differe nt philosophies at work here. C++ takes the approach that con trol of efficie ncy is the most importa nt issue, so it gives the programmer a choice. For maximum run-time speed, the storage and lifetime can be determined while the program is being written, by placing the objects on the stack (these are sometimes called automatic or scoped variables) or in the static storage area. This places a priority on the speed of storage allocatio n and release, and con trol of these can be very valuable in some situati ons. However, you sacrifice flexibility because you must know the exact qua ntity, lifetime, and type of objects while you're writing the program. If you are trying to solve a more general problem such as computer-aided desig n, warehouse man ageme nt, or air-traffic con trol, this is too restrictive. The sec ond approach is to create objects dyn amically in a pool of memory called the heap. In this approach, you don't know un til run-time how many objects you n eed, what their lifetime is, or what their exact type is. Those are determined at the spur of the moment while the program is runnin g. If you n eed a new object, you simply make it on the heap at the point that you n eed it. Because the storage is man aged dyn amically, at run-time, the amount of time required to allocate storage on the heap is sig ni fica ntly Ion ger tha n the time to create storage on the stack. (Creat ing storage on the stack is ofte n a si ngle assembly in structio n to move the stack poin ter dow n, and ano ther to move it back up.) The dyn amic approach makes the gen erally logical assumpti on that objects tend to be complicated, so the extra overhead of finding storage and releas ing that storage will not have an importa nt impact on the creati on of an object .In additi on, the greater flexibility is esse ntial to solve the gen eral program ming problem. Java uses the sec ond approach, exclusive". Every time you want to create an object, you use the new keyword to build a dyn amic in sta nee of that object. There's ano ther issue, however, and that's the lifetime of an object. With Ian guages that allow objects to be created on the stack, the compiler determines how long the object lasts and can automatically destroy it. However, if you create it on the heap the compiler has no kno wledge of its lifetime. In a Ianguage like C++, you must determine programmatically when to destroy the
XXX学院 毕业设计(论文)外文资料翻译 学院:计算机与软件工程学院 专业:计算机科学技术(软件工程方向) 姓名: 学号: 外文出处:GoyKakus.THE RESEARCH OFCUSTOMER RELATIONSHIP MANAGEMENT STRATEGY [J]. International Journal of Management Research & Review, 2017, 1(9): 624-635. 附件: 1.外文资料翻译译文;2.外文原文。 注:请将该封面与附件装订成册。
附件1:外文资料翻译译文 客户关系管理战略研究 Goy Kakus 摘要 客户关系管理解决方案,通过为你提供客户业务数据来帮助你提供客户想要的服务或产品,提供更好的客户服务、交叉销售和更有效的销售,达成交易,保留现有客户并更好地理解你的客户是谁。本文探讨了客户关系管理模型在获得、保持与发展策略方面的优势。然而,我们对其定义和意义还存在一些困惑。本文通过考察关系营销和其他学科方面的相关文献,解释了客户关系管理的概念基础,从而对客户关系管理的知识作出了贡献。 关键词:客户关系管理模型, 客户关系管理的博弈改变者与关键策略 引言 CRM 是客户关系管理的简称。它的特征在于公司与客户的沟通,无论是销售还是服务相关的。客户关系管理这一术语经常用来解释企业客户关系,客户关系管理系统也以同样的方式被用来处理商业联系, 赢得客户,达成合同和赢得销售。 客户关系管理通常被考虑作为一个业务策略,从而使企业能够: *了解客户 *通过更好的客户体验留住客户 *吸引新客户 *赢得新客户和达成合同 *提高盈利 *减少客户管理成本 *通过服务台等工具软件,电子邮件组织者和不同类型的企业应用程序,企业业务经常寻求个性化的在线体验。 设计精良的客户关系管理包括以下特征: 1.客户关系管理是一种以顾客为中心并以客户投入为基础的服务响应,一对一的解决客户的必需品, 买家和卖家服务中心直接在线互动,帮助客户解决他
https://www.doczj.com/doc/b812898928.html,/finance/company/consumer.html Consumer finance company The consumer finance division of the SG group of France has become highly active within India. They plan to offer finance for vehicles and two-wheelers to consumers, aiming to provide close to Rs. 400 billion in India in the next few years of its operations. The SG group is also dealing in stock broking, asset management, investment banking, private banking, information technology and business processing. SG group has ventured into the rapidly growing consumer credit market in India, and have plans to construct a headquarters at Kolkata. The AIG Group has been approved by the RBI to set up a non-banking finance company (NBFC). AIG seeks to introduce its consumer finance and asset management businesses in India. AIG Capital India plans to emphasize credit cards, mortgage financing, consumer durable financing and personal loans. Leading Indian and international concerns like the HSBC, Deutsche Bank, Goldman Sachs, Barclays and HDFC Bank are also waiting to be approved by the Reserve Bank of India to initiate similar operations. AIG is presently involved in insurance and financial services in more than one hundred countries. The affiliates of the AIG Group also provide retirement and asset management services all over the world. Many international companies have been looking at NBFC business because of the growing consumer finance market. Unlike foreign banks, there are no strictures on branch openings for the NBFCs. GE Consumer Finance is a section of General Electric. It is responsible for looking after the retail finance operations. GE Consumer Finance also governs the GE Capital Asia. Outside the United States, GE Consumer Finance performs its operations under the GE Money brand. GE Consumer Finance currently offers financial services in more than fifty countries. The company deals in credit cards, personal finance, mortgages and automobile solutions. It has a client base of more than 118 million customers throughout the world
我国第三方物流中存在的问题、原因及战略选择 熊卫 【摘要】我国物流业发展刚刚起步,第三方物流的理论和实践等方面都比较薄弱。本文指出我国第三方物流存在的问题在于国内外第三方物流企业差距、物流效率不高、缺乏系统性管理、物流平台构筑滞后、物流管理观念落后等。分析了产生上述问题的原因,并提出了精益物流、中小型第三方物流企业价值链联盟、大型第三方物流企业虚拟化战略等三种可供选择的第三方物流企业发展战略。 【关键词】第三方物流;精益物流战略;价值链联盟;虚拟化战略 1引言 长期以来,我国国内企业对采购、运输、仓储、代理、包装、加工、配送等环节控制能力不强,在“采购黑洞”、“物流陷井”中造成的损失浪费难以计算。因此,对第三方物流的研究,对于促进我国经济整体效益的提高有着非常重要的理论和实践意义。本文试图对我国策三方物流存在的问题及原因进行分析探讨,并提出第三方物流几种可行的战略选择。 2我国第三方物流业存在的主要问题 (一)我国策三方物流企业与国外第三方物流企业的差距较大,具体表现在以下几个方面: 1、规模经济及资本差距明显。由于国外的大型第三方物流企业从全球经营的战略出发,其规模和资本优势是毫无疑问的,尤其初创时期的我国策三方物流业,本身的规模就很小,国外巨头雄厚的资本令国内企业相形见绌。 2、我国策三方物流业企业提供的物流服务水准及质量控制远不如国外同行。当国内一些企业还在把物流理解成“卡车加仓库“的时候,国外的物流企业早已完成了一系列标准化的改造。同时,国外的物流组织能力非常强大,例如德国一家第三方物流公司,公司各方面的物流专家遍布欧洲各地。如果有客户的货物需要经达不同的国家,那么欧洲各地的这些专家就在网上设计出一个最佳的物流解决方案。这种提供解决方案的能力就是这第三方物流公司的核心能力,而不像国内公司号称拥有多少条船,多少辆车。 3、我国加入WTO后物流产业的门槛降低。在物流服务业方面:我国承诺所有的服务行业,在经过合理过渡期后,取消大部分外国股权限制,不限制外国服务供应商进入
毕业论文(设计)外文翻译 题目:中国上市公司偏好股权融资:非制度性因素 系部名称:经济管理系专业班级:会计082班 学生姓名:任民学号: 200880444228 指导教师:冯银波教师职称:讲师 年月日
译文: 中国上市公司偏好股权融资:非制度性因素 国际商业管理杂志 2009.10 摘要:本文把重点集中于中国上市公司的融资活动,运用西方融资理论,从非制度性因素方面,如融资成本、企业资产类型和质量、盈利能力、行业因素、股权结构因素、财务管理水平和社会文化,分析了中国上市公司倾向于股权融资的原因,并得出结论,股权融资偏好是上市公司根据中国融资环境的一种合理的选择。最后,针对公司的股权融资偏好提出了一些简明的建议。 关键词:股权融资,非制度性因素,融资成本 一、前言 中国上市公司偏好于股权融资,根据中国证券报的数据显示,1997年上市公司在资本市场的融资金额为95.87亿美元,其中股票融资的比例是72.5%,,在1998年和1999年比例分别为72.6%和72.3%,另一方面,债券融资的比例分别是17.8%,24.9%和25.1%。在这三年,股票融资的比例,在比中国发达的资本市场中却在下跌。以美国为例,当美国企业需要的资金在资本市场上,于股权融资相比他们宁愿选择债券融资。统计数据显示,从1970年到1985年,美日企业债券融资占了境外融资的91.7%,比股权融资高很多。阎达五等发现,大约中国3/4的上市公司偏好于股权融资。许多研究的学者认为,上市公司按以下顺序进行外部融资:第一个是股票基金,第二个是可转换债券,三是短期债务,最后一个是长期负债。许多研究人员通常分析我国上市公司偏好股权是由于我们国家的经济改革所带来的制度性因素。他们认为,上市公司的融资活动违背了西方古典融资理论只是因为那些制度性原因。例如,优序融资理论认为,当企业需要资金时,他们首先应该转向内部资金(折旧和留存收益),然后再进行债权融资,最后的选择是股票融资。在这篇文章中,笔者认为,这是因为具体的金融环境激活了企业的这种偏好,并结合了非制度性因素和西方金融理论,尝试解释股权融资偏好的原因。
Advantages of Managed Code Microsoft intermediate language shares with Java byte code the idea that it is a low-level language witha simple syntax , which can be very quickly translated intonative machine code. Having this well-defined universal syntax for code has significant advantages. Platform independence First, it means that the same file containing byte code instructions can be placed on any platform; atruntime the final stage of compilation can then be easily accomplished so that the code will run on thatparticular platform. In other words, by compiling to IL we obtain platform independence for .NET, inmuch the same way as compiling to Java byte code gives Java platform independence. Performance improvement IL is actually a bit more ambitious than Java bytecode. IL is always Just-In-Time compiled (known as JIT), whereas Java byte code was ofteninterpreted. One of the disadvantages of Java was that, on execution, the process of translating from Javabyte code to native executable resulted in a loss of performance. Instead of compiling the entire application in one go (which could lead to a slow start-up time), the JITcompiler simply compiles each portion of code as it is called (just-in-time). When code has been compiled.once, the resultant native executable is stored until the application exits, so that it does not need to berecompiled the next time that portion of code is run. Microsoft argues that this process is more efficientthan compiling the entire application code at the start, because of the likelihood that large portions of anyapplication code will not actually be executed in any given run. Using the JIT compiler, such code willnever be compiled.