Key to Exercises-Unit 1,3,4,5,9,10
- 格式:doc
- 大小:401.50 KB
- 文档页数:44

Key to the exercisesUnit OnePart One Reading TextⅠ. 1.Y 2. N 3.NG 4.Y 5. N 6.Y 7. N8. enjoy, relaxed educational9. creativity10. encourage students participationⅡ. BCBADⅢ. 1. D 2. I 3. J 4. O 5. G 6. N 7. C 8. L 9. M 10. EⅣ. 1. When permission was sought from senior management.2. They are skeptical that anything other than surface transformation is taking place.3. College entrance exam.4. The weight given to testing is regularly criticized.5. Memorization and rote learning.Ⅴ. 1. grow anxious2. taking the initiative3. a series of4. resulted in5. underlyingPart Two Reading Skills1. c-a-d-b2. b-a-d-c3.a-d-b-c4. a-d-e-b-c5. a-e-c-f-b-dPart Three Reading PracticePassage 1 CDBDAPassage 2 D ABBCPassage 3 A B CBDPart Four Home ReadingⅠ. 1. N 2. N 3. NG 4.Y 5.NG 6. N 7. Y8. originally expected9. attaining the same standards10. continuing professional educationⅡ. CDADCⅢ.1. has come to an end2. the knowledge and abilities of graduates applying for jobs3. bring about social reform4. learn best by rote5. our new opportunities for diversityIV. 1. 1. More than 93 percent of young people2. By adopting entrance examinations.3.The demand for education, especially the advanced professional education, is going up.4. Almost all children.5.This enables students and their parents to choose between alternative routes to learningoffered by competing schools.Unit TwoReading textⅠ. 1.Y 2. N 3. N 4. Y 5. NG 6. Y 7. N8. exhausted9. patterned after10. the experiences on the Morning NewsⅡ.DDCBBⅢ. 1.K 2. O 3. C 4. J 5. B 6. D 7. G 8. F 9. L 10. IⅣ. 1. Because she had just started a business successfully.2. He felt exhausted .3. The style of the show can’t draw the audience’s attention.4. Whoever gets Walter’s job, he will never devastated .5. Sometimes, a big promotion can’t bring happiness for family.Ⅴ. 1. was coming into my own2. occurred to me3. focusing on4.came over me5. stagger awayReading Skills1.A2.C3.C4.AReading PracticePassage 11.C2.D3.C4.A5.BPassage 21.D2.B3.C4.A5.CPassage 31.B2.D3.C4.A5.AHome ReadingⅠ. 1. N 2. Y 3. NG 4. Y 5. N 6. N 7. Y8. made my way out of9. successful10. valueⅡ. ABCDDⅢ.1.She was a school teacher.2.She decided to see her grandmother.3.In 1993.4.Because the fabric was full of memories, her grandma would turn into something new oneday.5.Because her husband could continue his education .IV.1. match my expectations of myself2. threaded its way3. faded away4. thought of5. meant toUnit ThreePart OneI. 1. N 2.N 3.N 4.Y 5.N 6.Y 7.NG8. puddling9. run out10. explanationsII. DABADIII 1.L 2.A 3.O 4.I 5.K 6.G 7.D 8.C 9.B 10.HIV. 1. She thought his father might like to play with them too.2. Because he threw away her affections towards him..3. You have things to play with, more important, you may associate them with your children4. He made them clean and tidy.5. The feelings and the fantastic world of Molly.V. 1.cram 2.unfolded 3.run out 4.hold 5.turned his attentionPart ThreeI. C B B D AII A D DA BIII A A DCDPart FourI. 1.N 2.N 3.Y 4.Y 5.NG 6.Y 7.N8. in trouble9. inner voice, mediate, pray10. actions, actions, wordsII. D A D D DIII.1.He used to lay around the tree, climb to the top of it, ate the apples, and take a nap under the shadow.2.Because he grew up and wanted to play toys.3.Because he did not have money to buy toys.4.He wanted to go sailing to relax himself. But he did not have a boat.5.(open answer)IV.1.from chopping off trees2. come and play with me3. show up4. leaned happily on5. come sit down with me and restUnit FourPart 1I. 1. Y 2. Y 3. Y 4. NG 5. N 6. N 7. Y8. full-time student; part-time worker9. critical need10. put a spot lightII. BACCAIII. 1. J; 2. D; 3. F ; 4. C ; 5. H ; 6. G; 7. A ; 8. N; 9. K ; 10. IIV.1.Social entertainment, cultural communication and positive social change.2. They share similar ethnic backgrounds.3. To dedicate the time and effort to the e-magazines.4. That there is more than one definition of success.5. Four.V 1. has been interesting to him2. Your idea will become reality.3. Even though / though / although they held different views / standpoints4. features / featured largely in her life5. aimed the camera at the picturePart 21. D;2.C;3.A;4.C5. TF6. FT7. FT8. FT9. T; 10. T; 11.T; 12. T; 13. F T T T T14. C; 15. BPart 3Passage 1 CADCDPassage 2 ADDBAPassage 3 DDDDDPart 4I. 1. N 2. Y 3. N 4. N 5. Y 6. NG 7. N8. fun and surprisingly addictive9. the latest Xbox 36010. bright and shinyII. DADBAIII.1. Two to three hours.2. Because she wanted to work through her grief.3. In websites that meld functions of the chat room, games and other services.4. By telephone.5. The Internet generation.IV.1.It was not until her third visit2. your future earnings will be considerable3. despite your achievements4. take advantage of all educational opportunities5. solving / working out the difficult questionTest OnePart I Vocabulary1-5 CDBDB 6-10 DACCD 11-15 CBBBA 16-20 DCBDC 21-25 ABCDD26-30 BAACD 31-35 CDBDA 36-40 ACCCDPart II Reading ComprehensionPassage One DCBAB Passage Two CACBAPassage Three CCCDA Passage Four DCBCAPart III Cloze1-5 C B A A D 6-10 B A A C D 11-15 A D A D C 16-20 D A B D BPart IV Translation1.master their tradition2.hold firm to his folksy habits3.divided loyalties4.their teeth to be ruined5.judge by appearances6.varies with supply and demand7.talk away in the background8.the strength of a body builder.9.sink into the chair10.a more moderate accommodation that balances economic against health concernsPart V WritingSelecting CoursesRecently, people in growing numbers show their concern about selecting courses. In some colleges, students are permitted to pick out their course’s professors freely. The reasons are listed as follows:In the first place, students can choose the teacher according to their interests, which will be helpful for their future careers. Besides, selecting courses can reduce the rate of students’ absence indirectly for students usually choose their favorite teachers.As far as I am concerned, every coin has two sides. On the one hand, students may learn the course better, because they may choose the professor they liked. On the other hand, if the professor who is very popular and a great number of students would like to attend his/her course, the classroom must be overcrowded. It will have a bad impact on the class.Unit FivePart II. 1. Y 2. NG 3. N 4. N 5. N, 6. Y, 7. Y 8. shocked 9. therapy 10. 24II. DCABDIII. 1. O; 2. I; 3. M ; 4. K ; 5. C ; 6. F; 7. E ; 8. G; 9. N ; 10. AIV.1. On the outside I was a healthy, athletic student, but on the inside I was just another statistic of aviolent crime.2. When the police arrived they immediately called the homicide division as they did not think Iwould survive and the paramedic reported that she had never seen a person so severely wounded survive.3. I am a very determined and stubborn person and he believes that someday he would return tocollege.4. Through Tom I learned: “Nothing is impossible and never, never give up or quit.”5. Living each day to the fullest, and doing the very best one can, then nothing is impossible.V. 1.fulfill their dream 2. wonder why 3. was awakened by4. for fear that5. look forward toPart Two1.Denotation: carry out a duty; act or showConnotation(s): work or operate2.Denotation: succeed in doing; run or take charge ofConnotation(s): control3.Denotation: points or facts about somethingConnotation(s): unimportant small points4.Denotation: break up by explosionsConnotation(s): rise into the air like a rocket that leaves the ground. The word give you a sense of quickness and forcefulness, for the plane is compared to a rocket leaving the ground or, as you read in the next part of the sentence, to a bullet shot out of a rifle.5.Denotation: beatingConnotation(s): violently rocking me from side to side and making me uncomfortable. It gives one sense of uneasiness and uncomfotableness.Part Three.CACCA BDBADPart FourI. 1.Y 2.N 3. N 4.NG 5.Y 6.N 7. Y 8. dismissed9. hostile 10. interferedII. ACDBBIII Answer:1.Because I was an inexperienced new comer.2.She took hostile action towards me.3.After reading the sentence, I knew that I had to take control of my life and stop blaming myprincipal. I couldn't control her behavior, but I could control my reactions to it.4.I learned that bullies are usually cowards who act upon their fears and insecurities. I alsolearned non-confrontational phrases to use in conversation,5.The author got a valuable lesson and learned that he would never again allow himself to be avictim.Unit SixPart One Reading TextI. 1. N 2. Y 3. N 4. Y 5.NY 6. N 7. Y8. different9. 30-5010. foodII. DBCCAIII. 1. C; 2. H; 3. M ; 4. F ; 5. N ; 6. L; 7. K ; 8. I; 9. E ; 10. BIV. 1. Because they lack employment opportunities.2. The level of education.3. Those are not born in Sweden.4. Marital status.5. Classical entrepreneurial incentives.V.1. share2. As mentioned/ indicated3. have an influence4. drew a conclusion5. survival ratePart Two Reading Skills1. A.Yes. The mother's reply is not very polite, even with the informal register. This is correct, because the mother is showing that she is annoyed by the child giving a request as an instruction.2. A.Yes. Here the guest might have been indirectly asking a drink, so the host offers some orange juice, but also does it rather indirectly, in case the guest was really just discussing the weather.3. B.No. Miss Wilson has given an order to a stranger, and this is not polite, even with "please" at the end. The reply should be more like "Could I have it back when you are finished, please?"4. A.Yes This is more common with children than adults. However, it is sometimes used as a joke when a person wants to beg for something unimportant (like a sweet) from a friend.5. A.Yes. Mrs Greene is not really giving an instruction, she is saying that she hopes Mr Cooper willl enjoy himself. In the same way, many people in the United States use "Have a nice day."6. A.Yes. Harry is being very polite, but he is saying that he will not do what the boss wants, because it is not possible to do it. He gives his refusal as a statement, so that it causes minimum offence. Harry should now explain why it is not possible .7. A.Yes. The mother has used the second part of a conditional sentence. The child understands that the first part (which was not spoken) is "Yes, you can play with Jenny ...."8. B.No. Joe's reply is too comprehensive, and it uses too many of Mikes words. All that is required is an a positive acknowledgement of the instruction/request; so use, "sure", or "ok", (for yes) or "hold on", "now now" (for no).9. A.Yes. The policeman does not really want to know if Jack can show him some identification,he wants to see the identification. So Jack gives him the identification, using "here you are" - an expression used when giving something.10. B.No. "Do you mind .." means "will you be upset..". Mr Bloggs' answer does not show whether he is answering Sally's question ("Will you be angry if I smoke?" - "Yes, I will") or the intention behind Sally's question. (That is: "Can I smoke?" - "Yes, of course")11. A.Yes. Karen is asking the question because she wants to read the William's paper. William uses a more informal register to show he is friendly ("Sure" is sometimes an informal way to say "yes"), and he adds "Go ahead" ("Go on and read it.")12. B.No Well, probably not. Joey's invitation is very casual (Notice the missing auxiliary "do"). Mary's answer is formal, and says "thank you" in three different ways. Joey will probably understand that Mary is being sarcastic.13. A.Yes. The instruction is really an informal invitation. "Ta" is a very informal way of saying "thank you" when you are given or offered something unimportant.14. B.No. It is not polite to refuse a formal request with a direct negative ("No".), even if you give the reason afterward. Instead, Mr Blake should say something like "Well, actually, it's very cold outside."15. A.Yes. Mr Williams is asking Tony to turn down his radio. Tony apologises for disturbing Mr Wilson, and says he (and his radio) will go away.16. B.No. The use of "Again?" shows he thinks he has heard enough. "Oh, all right then" is a way of indicating that the speaker will do as asked, but not enthusiastically.Part Three Reading PracticePassage 1DCBDAPassage 2CABCAPassage 3 DCACBPart Four Home ReadingI. 1. NG 2. N 3. N 4. Y 5. Y 6. N 7. N8. third9. social psychology10. motherhoodII.ABBBDIII. 1. Nearly 70 students.2. 2.Defining success.3. 3.After her mother lost a job.4. 4.She was stuck with terror.5. The notion of motherhood.IV. 1. double standard2. No stranger to success3. transition from one channel to anther4. Hosted by5. from cover to coverUnit SevernPart OneI. 1. NG 2. Y 3. N 4. Y 5. Y 6. N 7. Y8. turning nouns into verbs or verbs and nouns into adjectives9. the over-heated language of much of the media10. social status within societyII. ACADBIII. 1I 2 L 3 A 4C 5G 6K 7O 8E 9M 10BIV. 1. Yes, I did.2. I felt I could do better.3. They introduced new words into the American tongue.4. British speech is less general.5. American English casually uses one form of words for another.V. 1. participate in the discussion2. cope with the difficulties3. expose children to violence4. introduced into5. on both sides of the riverPart Two Reading SkillsddaefecfbcPart Three Reading PracticePassage 1 DBCDAPassage 2 BDDACPassage 3 CDBCDPart Four Home ReadingI. 1. Y 2Y 3 N 4 N 5 Y 6 Y 7 NG8. accustomed9.predicated10. encounterⅡ. DCBBAⅢ . 1. He wanted to find a public telephone to call his friend.2. The meaning of “wash up” is “to wash your hands”..3. Because people sound different in every part of the United States.4. By the end of the 14th century, about half of the English words were introduced by theFrench.5. Because they wanted to sound particularly well-educated.Unit EightPart One Reading TextI.1N 2. NG 3.N 4.N 5.Y 6.Y 7.N8. the sustainable development9 decreased noticeably in Tibet10. nature reservesⅡ. CDDABⅢ. 1. H 2.J 3. K 4. C 5. D 6. A 7. I 8. F 9. B 10. MIV. 1. The "Roof of the World”.2. The Tibet Autonomous Region is 1.22 million sq. km.3. Ecological improvement and environmental protection in Tibet.4. A project to restore farmland to forest is being undertaken.5. 70 nature reserves.V. 1. didn’t attach any importance to his statement2. taken a succession of measures3. in line with the principle of national independence.4. a weighty bearing on5. accounting for about 80% of the earth’s total number of black-necked cranes.Part Two Reading Skills1. Y2. N3. N4. Y5. N6. N7. Y8. N9. Y 10. NPart Three Reading PracticePassage 1 CABCAPassage 2 BDCBAPassage 3 DABDCPart Four Home ReadingI 1.N 2.N 3 .N 4.N 5.Y 6..NG 7.Y8. at ar m’s length distance9. exposure to10. check on its originII DADCDIII. 1. Because he had been inhaling unnecessarily high concentrations of radon.2. He ate some healthy” food for breakfast.3. He inclined his head at an unnatural angle when driving.4. He learned that both decaffeinated and ordinary coffee were harmful.5. He doubted about the origin of the fish for lunch.IV.1. occur to2. composed of3. at the risk of his own4. wanders through5. point outTest TwoPart I Vocabulary1-5 ACCDA 6-10 BCACA 11-15 ACDBB 16-20 CDABB 21-25 ADCCD26-30 AABBC 31-35 CACAA 36-40 BCBDBPart II Reading ComprehensionPassage 1 CCDAD Passage 2 CCCDA Passage 3 ABCDB Passage 4 CCDAC Part III Cloze1-5 CABBA 6-10 CDCDC 11-15 DDBBA 16-20 DCBACPart IV Translation1.in dilemma2.face up to the fact3.evolved from4.be exposed to air5.associated happiness with money6.gets accustom to7.take this opportunity to thank8.appeal to youmit suicidement on the election resultsPart V WritingSave the Wild AnimalsMany wild animals are facing the danger of extinction, because the environment that they are living in has changed greatly. For example, with the developmet of cities, the using of insecticide and serious pollution, their living areas have become narrowcr and narrower. Many of the wild animals, now are confronted with food crisis. At the same time, man is killing off species just for getting their fur, skin, horns, teeth and meat.In order to protect our resources of ecology, people should realize that the loss of any species is at least the loss of source of knowledge and a source of natural beauty. There fore, measures of the following should be taken: pollution standards are made to keepdown poisons; killing off certain rare species is prohibited; national parks should be set up as wild life, reserves.Only if we human beings take some drastic measures can wild animals be preserved.。
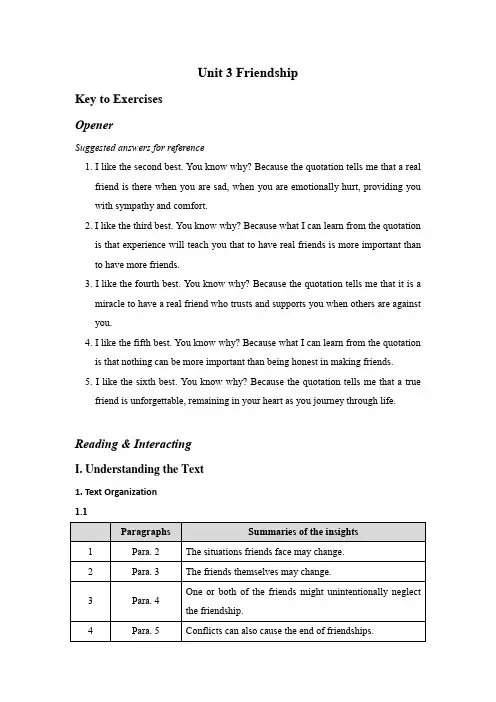
Unit 3 FriendshipKey to ExercisesOpenerSuggested answers for reference1. I like the second best. You know why? Because the quotation tells me that a realfriend is there when you are sad, when you are emotionally hurt, providing you with sympathy and comfort.2. I like the third best. You know why? Because what I can learn from the quotationis that experience will teach you that to have real friends is more important than to have more friends.3. I like the fourth best. You know why? Because the quotation tells me that it is amiracle to have a real friend who trusts and supports you when others are against you.4. I like the fifth best. You know why? Because what I can learn from the quotationis that nothing can be more important than being honest in making friends.5. I like the sixth best. You know why? Because the quotation tells me that a truefriend is unforgettable, remaining in your heart as you journey through life.Reading & InteractingI. Understanding the Text1. Text Organization1.11.2Para. 1 serves as an introduction to why friendships end.Para. 6 serves as a conclusion: Anyway, most friendships do enrich our lives no matter whether they are long or short.2. Comprehension Check2.1 Focusing on the main ideasWhy do friendships end? The author offers some insights into the question.Friendships end because the situations friends are in change. These changes can’t help but affect a friendship. Next, the friends themselves may change. The breakups can be mutual or one-sided. It hurts less when both friends change. What tends to hurt most is when just one friend changes. A third reason is that as much as two people might want a friendship to survive, one or both of them might unintentionally neglect it. Lastly, conflicts can cause the end of a friendship, since most friendships have breaking points under pressure.2.2 Digging into detail1. Why do some friendships end, no matter how much you want them to last?2. When you decide to relocate for a new school or job, this can’t help but affect afriendship. Likewise, if a friend of yours is in an accident, develops an illness, or loses someone close, these situations can’t help but affect a friendship. These events can end friendships if the necessary adjustments are not made.3. For example, when one or both friends start to date or get married, theirfriendship may come to an end. It hurts less when both friends want to do so. It tends to hurt most when just one friend changes.4. Friendship needs regular care. Taking a friendship for granted can cause it tobreak.5. A blow to a flower. If a flower gets repeatedly trampled on, it’ll eventuallybreak. So even those amazing close friendships need care when conflicts arise.2.3 Understanding difficult sentences1. B2. B3. A4. A5. BII. Focusing on Language in Context1.11. We set out to find the truth behind the mystery of the scientist’s disappearance.2. A good relationship is built on honesty, trust, and mutual respect.3. Kids may grow faster or slower but most of them still end up with an averageheight.4. In the joint venture, the Chinese party will hold a 51 percent controllinginterest.5. Although John has dated the girl for a year, he is still in two minds as towhether to marry her or not.6. Many people are unaware of just how much food and drink they consume eachday.7. In order not to hurt Mary’s feelings, please don’t refer to the incident again.8. He and Jeannie used to live together, but recently they have been apart for thefirst time.9. Adam has announced that he is to take an extended touring break in order tospend more time with his family.10. Jim survived the heart attack thanks to the prompt first aid treatment.11. His interview did not go well and his chance of getting the job slipped away.12. Kids exposed to an unhealthy environment tend to grow up with moreproblems.13. An occasional all-nighter is rough, but he is young enough to bounce back.14. Olivier turned it down flat and tried to persuade Vivien to do likewise.15. Nowadays when you buy a house in a big city, you have to invest lots of money.1.21. passion2. due to3. moreover4. cannot help but5. revive6. As much as7. neglected 8. on her own 9. injure1.31. While there are a couple of antibiotics that usually work, if they are overusedthey, too, may cease to be effective.2. I felt betrayed when he treated me like that.3. At least three people are reported to have been involved in the crime.4. The main reason that he developed liver cancer is because he had been exposedto high levels of radiation.5. Do not take on more responsibilities than you can handle.2. Word Formation2.1skilled →unskilledbalance →imbalancesufficient →insufficientagreeable →disagreeableunderstanding →misunderstanding2.21. As for the children of the unskilled workers, relatively few of them are able tosecure a place in college.2. Friendships are hard to survive in a disagreeable social environment.3. Some conflicts due to misunderstandings can cause the end of friendships.4. In recent years, we have invested more in basic science, but I think theinvestment ratio is still insufficient.5. The imbalance between consumption and investment must be corrected in orderto achieve sustained economic growth.3. Sentence Patterns3.11. There is no doubt he is impeccable when it comes to honesty.2. When it comes to diet and exercise, we all know what to do, but we seldom dowhat we know.3. I’m not good at English, but when it comes to math, I am the best in the class. 3.21. No matter how heavy the rain was, the soldiers kept marching on.2. Sam said, “No matter who becomes the President, I don’t care.”3. No matter whether she comes or not, it makes no difference to me.4. Comprehensive Practice4.1 ClozeWhen it comes to friendship, few of us deliberately want them to cease. On the contrary, we want our friendships not merely to survive, but to flourish. Yet, no matter how much we value friendship, sometimes we do drift apart from one another. Without noticing it we may fail to invest enough time and effort in maintaining our relationships. If we neglect them in this way they cannot help but be damaged. And once the damage is done, it is often hard to revive the friendship.4.2 Translation1. The article/essay helps us get a deep insight into the nature of the problem.2. Based on mutual respect, friendship will flourish.3. Like a plant, friendship will wither if neglected.4. No matter what may happen, we will do our best to overcome it.5. A friendship without constant care from both sides will end up with a breakup.6. This year cold weather has seriously affected the crops in the northern region.7. As much as I hate to do it, I must finish the task as planned.8. That means the new law also applies to private businesses.Reading & ComprehendingReading 11. Comprehension Check for Reading 11. F2. T3. F4. T5. T6. T7. T8. F9. T 10. T2. Translation1. 你的朋友被告上法庭受审,而你被传唤作证。


Key toexercisesUnit1Preview1.Listentothe recording of the text and then fill in the blanks in the following sentences.1.. aim/purpose; training;practical/professional skills; technical training;universities2..graduateschool;Shakespeare’s p lays; be apharmacist3. makingaliving;keephimself;hisfamily;expose;ideas4.waking;average;aliving;allabout5. in dang er; m echanized savages; push-buttonNeanderthals6. have left us; peculiar accom plishments;species7.. center;storehouse8.. sarcastic;humorous2.R ead the text for better comprehension a nd a nswerthequestions,paying special a ttention to the par ts in boldtype.1)It m e a ns a nnoyi n g experiences, t ou g h pro blems or failures.2)The y must have finishe d their graduat e s t udie s w i th a n advanc e d d e gr e eli keaPhD.3)Itsimplymeans?one of thestudents?.Theword?body?here meansthewholegroupofstudents.Becausethestudentisthinandtall.Itismeanttobe humorous rather thaninsulting.4)He t ea ches Englishliterature.5)Byus i ngt helike t h e c our s word?s t u f f?,h eshowshisdislikefor t he c ou r se ve r y clea r ly.Hedoesn’tebe c ausehethinksitis us e l ess forhisplanned career.6)Wecanassumethathedoesnotthinkitnecessarytowastemoneyonthe books since heintends to drop thecourse.7)The latter. It is a humorous way of referring to a certain type of people.8)He is talking about the Pharmacy School. He is being sarcasticwhenhecallsit?a DrugstoreMechanicsSchool?Itmeans?技工?.9)He is talking about the diploma for university orcollegegraduates.He has in mind people like what the student wants tobe:pharmacists.10)Itmeans?havingbeenintroduced to theideasdevelopedorproduced throughouthistory.11)It refers to his effort to convince thestudent.12)?Hold?hereisanintransitiveverbmeaning?remaintrue?.Itisoftenuseda sase t phrase?hol dtrue?.13)Itmeans?thingsofthesamekind?.诸如此类14)We call it the fut ure c on tinuou s t e ns e. It i s used for ongoin g future ac t ions.15)He is saying here that you will make sure that the medicineyou make will not be mixed with poison if you are trained as a pharmacist;thatthehousesyoubuildwillsuccessfullykeepoutbullsifyourchosenjobise ngineering;and t h at yo ur client w i l l not be sentenc ed to d eat h b e cause you a re inc om petent if you want to b e al a wyer.16)T he s e are a ll us eful things to d o… a nd raises/bri n g s up your c hildren.17)InformalEnglish,?may?is usedtoexpress ahopeorwish.Moreexamples:Mayourcountrybeprosperousandourpeoplehappy.May peacefina l lypr e vail.Note: suf fi ce (be s uff i cient) It is formal for hu m orouseffect.18)民主的思想家. Will you be heading a family that is familiar withthegreatdemocratic ideas in past history?19)He meansthetallstudent.?Pest?is oftenused to refer to anannoying person especially achild.20)No. H e means that he i s a i ming to m ak e m oney. T hat i s hispurpos e forcoming toschool.21)…you’regoi n gto ha vetroublefi n dingsometh i ngt od owhen you arenot spending money.22)…thenyoushouldn’tgotocollege.Youhavenoreasontogotocollege.23)Heissayingherethatyoungpeoplemaybecomesavagesliketheancientpe opl ew ho lived 35,000 t o 130,000 yea rs a go although t h ey c annowpushbut t onsa ndu semachi n e s,hence, a ?n ew s p ec i es?.24)Ourcoll e g e sareboundtoprod uc eso m estude nt softhi s ki nd.H e i sver ysarcasticabout these people and thinks that they are not truly educatedandcivilizedastheyshouldbetoday.Thereforeheusestheexpression:?such li feforms?. Note alsothattheword?graduate?is usedas a transitiveverbhere.25)We are talking about how ideas or concepts are developedandhowimportant they are in the evolution of the human species. Animalsliveby instinct. Only human beings are able to formulate ideas such aslove,freedom,democracy,andequality.Theseideasmakeusdifferentfromotherani mals. And we get these ideas from people in the past. That is why readingissoimportant.Manyscholarsmaintainthatwithoutreadingwe do n’tknowhow tothink.Thereare,however,peoplewhoemphasizetheimportanceofdirect experienceSometimestheyevengoas far as to maintain .Theysaythat‘Doing isalsolearning’.that reading may prevent us from creativethinking.26)The fact that we have the faculty means that…Vocabulary1.D o t he f ollowing exercises on wor d f or mation rules.1)Thefollowingwordsareadjectivesendingwiththesuffixes?-ent?a nd?-a nt,?andtheircorrespondingnounsusuallyendingwith?-ence?a nd?-a nce.?Decide which of the following should be the for mer, and which the latter.1.di f fe r ent2.i nd ependent3.extrava g a n tpetent5.arrogant6.important7.c o nfi de nt8.fra g ra n t9.signifi c ant10.convenient 11.e vident12.i nt e ll i g ent13.re levant14.present15.urgent16.violent17.c ur re n t18.fr e qu en t19.di stantNote: The following words are nouns, not adjectives: accountant;assistant;defendant; dependant;attendant2)Guess the cor r esponding nouns of the following, paying special a ttention totheirpronuncia t ion.1.qua l ifi c ati o n c l arifi c at i onunification notificationclassification identificationintensification justificationsimplif i cation c ert ifi c at i onglori f ication speci fi cat i on2.m o derniz a ti onmechani z ationrealization civilizationglobalization specializationAmericanization industrializationurbanization idealizationcentralization marketizationnationalization privatization3.permission discussionadmission professioncommission confessionremission impressionemission oppressionsubmission compressiontransmission expressionom i s s i on depre s sion3)Giveder i vative s of th e f oll o wi n gwords.1.se ns e: sensitive; s en sible; s en se l ess; sens i bility; ove rs ensitive; ins e ns i tive2.technique: technical; technically;technician;3.special: specially; specialty;specialize4.intellect: intellectual; intelligent;intelligence5.civil: c i vi l ize; c i vi l ization; ci v i l ized;u nc iviliz e d4)T r ans l ate the following i nt o C hi n e s e.1.Many people agree that the increased enrollment is a bigaccomplishment.2.The lack of availability of certified accountants who can meetsuchhighqualifications is still a bigproblem.3.Early specialization is not wise. Students should have a wide exposure toworldculturebe f ore t h eyspeci a lize.4.Strong as we might be some day we must never become a r rogant. We shouldcontinuetopur sue the policy of peaceful co-existence amongnations.powerrestsessentiallywithitsadvanced civilization.5.Itis a penetr a tingthoughtthat a nation’s6.Ourmemoryofpastdisastrousexperiencesisanextremelyimportantspiritualresource.2.Tr anslate the following v er b+noun c oll oc at i ons intoEn g li s h.1)f oldone’sarms2)fold theletter3)acquireknowledge4)generateideas5)g en e ratejobs6)gen e r ate p ow er7)g en e r at e i nte r e s t8)employworkers9)use/employtime10)rear/raiseone’schildren11)rearsheep12)raiseone’sfamily13)raiseone’svoice14)raisetax15)raise thequestion16)maintaincontact17)maintain law andorder18)maintainpeace3.Give the synonyms and antonyms of thefollowing.Synonyms1.re a sona bl y/r athe r/quite2.c l earl y/evi d ently3.tokeep4.toraise5.togain/obtain6.t opr oduce7.t opr ove8.de pa rtment(univers i ty)9.humanity10.drugstore /chemist (英)11.type/example/model/case Antonyms1.una v aila bl e2.m ode s t ly3.general4.unqualified5.uncivilized/savage6.t ounfol d7.unemployed8.incompetence9.insensitive 12.t oent e r/join13.how eve r/but14.sharp/thoughtful15.thinker/intellectual16.toshake/tremble/shiver17.una voidably/ce rt ainly/18.t o s uppos e/presume/thi nk/guess19.t ohel p/ass i st20.strange/odd/unusual/queer21.achievement/success/victory22.specialskillplete the sentences with the expressions listedbelow.1)to see to it; exposedto2)out for; succeedin3)a v e ra gesout4)specializein5)stuckfor6)presideover7)stuck for; see to itthat8)t r ue of9)out to; see to itthat10)have nobusiness5.Fill in the blanks with the r ight wor d or expression in the bracket.1)in making; tofind2)see3)out; of; of;for4)to5)by;for6)Poor as he w a s;put7)for8)in9)believed in;forcing10)physicist;sensitive6.Tr anslate the following sentences intoEnglish.1)It is wrong to raise our children the way we grow flowers in the greenhouse.Wemust exposethemtoallsocialproblemsbecauseverysoontheywillbedealingwiththemasresponsible citizens.2)As time goes on we a re inevit a bly g oing t o get more a nd m o re invol v edininte rna ti on alaffairs. And conflicts are sure to occur because there always exist different viewsandinterests betweennations.3)We are proud of our accomplishments, and we have reason to be. But we mustneverbecomearrogant. Otherwise we will lose ourfriends.4)Information is now easily available. An average computer can store the informationofasmalllibrary5)Thatconstructioncompanyisnotqualifiedtohandletheproject. Theydonothaveany legal documentto certify that they have the necessary expertise. We must find acompany that specializes in buildingtheatres.6)These think tanks do not make decisions. They are out to generate new ideasandpenetratinganalyses that will be extremely useful for decisionmakers.7)The growthofGDPisnoteverything.Ourcountrycannotbesaidtohavebeen modernizedunlessthequalityofour people’slivesisreallyimprove d.8)Poor as we were in many ways at that time, we were still quite happy as children,fortherewas clean air, clean water, a lot of fish, crabs and eels in the rivers, lakes, andponds; and alot of flowers, trees and birds in thefields.9)Giveabsolutepowertosomeindividualoranyparticulargroupofpeople,andthatperson orgrouparesure to abusethatpowerbecause,justasLordActonsays,?P o w ercorrupts,and abs olute pow erc orr u pt s absol u tely.?10)Traditionallyinourcountryschooleducationwasalwayssaidtobemore importantand usefulcompared with all otherpursuits.Gr ammar1.. Point out how future time is expressed and what concept each futureexpression conveys.Itisfarmorecomplicatedtotalkaboutthefuturethantotalkaboutthepresentandpast.Generally,future time is expressed in these ways.Future a tPresenta)) ?will?asin3):usedtosaysomethingisexpectedtohappen?w illbe doing?as in4):usedtosaythatyouaresurethatsomethingwillhappen becausearrangements have been madeb)?begoingto?:used2),5)tosaythatsomethingwillhappenquitesoonortotalkaboutsb’sintentionsorwhattheyhavedecidedtodoc)?the present progressive?as in10):used to talkaboutsomethingthatwillhappen be c aus eyou have p lann e d or arra n g e ditd)?the s impl e present?asin9):us e d to saythat s om et hi ngwil l de f initely happ en ata particulartime, especially because it has been officiallyarrangedFuture in thePasta)) ?would?asin7):usedtosaywhatyouintendedtodoorexpectedtohappenb)?was/weregoingto?asin1):usedtosaythatsomethingwasexpectedtohappenc)?w a s/were t o do?a s i n6),8):used to t alk a bout so m ething t hat w ouldha ppe nbecause it hadbeen planned orarranged.2.. Learntouse emphasizingcoordinatingconjunctions.1.Point out the gr a mmatical for m each pair of theconjunctionsconnects.Emphasizing coordinating conjunctions connect parts of thesentence that have thesame grammatical form.1)twonouns2)twoadjectives3)two prepositionalphrases4)two infinitivephrases5)two nounphrases6)two nounphrases7)two prepositionalphrases8)two prepositionalphrasesbine each pair of the sentences using the r ight emphasizing coordinatingconjunctions.1)) Theprovinceisstrongbothinindustryandinagriculture./Theprovinceisnot only strong inindustry, but a lso inagriculture.2)) Relief agencies say the immediate problem is not a lack of food, but transportation.3)) Generally, after working for the company for five years, young employees eitherareprom ot ed orleav e.4)) TV programs for children should not only entertain but a lsoteach.5)) Obviously, these children are motivated not by a desire to achieve, but byfearoffailure6)) At present, it would be neither practical nor desirable toeliminateexaminations altogether.7))AsianAmericansareplayingamoreactiveroleinpoliticsthaneverbefore,bothat localandnationallevel.8)) Myunclebelievesthatinourtownsightseeingisbestdoneeitherbytourbusorby bicyc l e.9)) Wood floori ng not on l y cleans e as il y, but is environmental ly frie ndl y.10)) Until I read the article I knew neither where she was brought up nor (whereshewas)educated.11)) I find the new manager neither easy to get along with nor delightful to talk to.12)) Contrary to what people had expected, not only did he attend the meeting,buthe als os pokefort w e nt ymi nut es.3.. Fill in each blank with ONE suita ble word.(1)other (2)best (3)reason (4)mental (5)next(6)As (7)take (8)cool (9)thinking (10)rest4.. Tr anslate the following sentences intoEnglish.1)) The premier is leaving for New York for a UN conferencetomorrow.2)) He is to meet the heads of state of several countries during his stay in New York.3))What a re you going to do during the National Day holidays? Are yougoinghomeor staying oncampus?4)) —Whatdoyouthinkschoolwillbelikeintwentyyears’time?— I think children will probably lear n at home with a mechanicalteacher.5)) Thirty years ago, my grandparents never thought they would be able to moveintoa two-storey house with all the modern facilities.6)) What they lack is not money butexperience.7)) They have come to China not only to learn Chinese, but to learnaboutChinese culture as well.8)) What children want most from their parents are not material things butloveand attention.9)) You may either write your essay in your regular exercise book or do it onyourcomputer.showup.Eitherhewasnotinterested,orhesimply forgot10))I’m notquitesurewhyhedidn’taboutit.11)) A society should respect both its scientists and its garbagecollectors.12)) He i s m i s e r ly b ot h with hi s money an d wit h hi s time.5.. Identify and cor rect the mistakes. Note there is no mistake in two of thesentences.1)) I will phone you as soon as I ar r ive inBeijing.2)) We can har dly imagine what life will be like in 50years.3)) WhatarewegoingtodoifEdithwon’thelpus?(Nomistakeinthissentence.Here?if…will?ispossiblewhenwillexpresses?willingness?.)4)) Pleasebeseated,everyone.Theshowisa b outtobegin.(Use?beabouttodosth?tosaythatsomethingwillhappenalmostimmediately.?Will?isnotused.)Chinawillbeabletosendmantothe Moon.(?Tobea5))Itispredictedthatinaboutten years’time,bletodo sth?is usedtosayitispossibleforsomeoneor something to dosomething.)6)) Dropinwheneveryouplease.You’ll alwaysbewelcome.(Adverbsof frequency, such as always, usua lly, often, sometimes, etc, usually go immediately infront of the m a inve r b.)7)) Nei t herhispa re nts,norhisbrot he r was ablet oc ometohispe r form a nce.(Th em ai n verbagrees with the noun phrase introduced bynor.)8)) Both her friends and her English teacher believe she will win the talentcontest.9)) My father regards creativity both as a gift and as a skill. (Normally, the twoitems c onne cte d by emphas i z i ng coordina t ing conj unc t i ons s houl d be expr e s s e di n the same grammatical form, here, two prepositionalphrases.)10))Wecaneitherdoitnoworafterclass—uptoyou.(Nomistake.Thoughthetwo items?now?and?afterclass?aren’tit’sthesamegra mmaticalform,thisisacceptablebecausewecanregardthemascondensedfrom?W ecaneitherdoit nowordoit a f terclass.?T he r e fore,thet w oitemscanalso b e d i fferentgramma t ical fo rms serving the same grammatical function, here, bothadverbials.)Unit2Preview1.L isten to the r ecor ding of the text and fill in the blanks in the followingsentences.1)racialequality2)civil rights; lingeron3)husband; qui t e a g ood hu s band/very conside r ate; li beral; ra c ia l4)considered;unprepared5)give his wife; hadadmitted6)found out;pressing7)look; argued about such seriousmatters8)perfectly nor m al;to l erate9)are differentculturally10)culturally and socially; racialsegregation11)white; married; a perfectstranger2.R ead the text for better comprehension and answer thequestions.1)?pi tchin?me a ns?t o joi n w i thotherpeopleindoinga j ob?.Intheex pre ssion?topit c habaseball?,theword?pitch?means?tothrow?.?topitchatent?means?toputupatent 支帐篷.?pitchdark?means?asdarkaspitch?漆黑—pitchmeans沥青?housework?meansthe workyoudotokeepyourhousecleanandtidy;?homework?means the work a teacher gives to a student to do out of class.2)Af t er th i nki n g of a l l as p ects of t he mat t er c a r e ful l y.We can assume that he would have considered the difficulties and problems he believeditwould bring to his life if he married a blackwife.3)Heknewtherewouldbeanunpleasantquarrel,andthatitwaswiserforhimjusttokeephis mouth shut.This shows that they have had previous serious disagreements. Thiswas notthefi r st t ime.It shows that the man has seldom taken his wifeseriously.4)?youcomingalong…andimplying…?isthecomplexobjectof?need?.a racist,hewouldnotsayno,sincehiswifeisexactly the samepersonexceptfor her Ifheweren’tskincolor.5)No. It is clear that the wife is using an ironicaltone.No.Themanisusingacommonexcuseofwhiteracistswhotrytojustifytheirprejudice based on different skin color by using a seemingly more neutral and respectableterm?culturaldifferences?.6)To show that he found the situation veryannoying.Normallyitmeans?w hat I sayisabsolutely true?,butherehemeans?I t istruenotbecauseI am saying it.I have statistics to prove this.?7)She saiditcontemptuously.She wasgettingangry.8)Because his wife keeps mimicking him, showing that she thinks what he saidwasridiculous andhypocritical.。

Key to ExercisesUnit 1Task 1A. Answer the following questions.1) What did Gretel want to see in the City of London?Key: She wanted to see St. Paul's Cathedral.2) Why was she so surprised?Key: She was so surprised because she saw so many Englishmen who looked alike.3) What did the Englishmen look like?Key: They were all wearing dark suits and bowler hats, carrying umbrellas and newspapers.4) Why did Gretel think they must be typical English gentlemen?Key: Because she had often read about them and seen photographs of them, who all looked as if they were wearing a uniform.5) Did Mr. Clark also think there is such thing as a "typical" Englishman?Key: No, he didn't.6) What English saying did Mr. Clark use to prove his opinion?Key: He used the English saying "It takes all kinds to make a world" to prove his opinion.B. Write down the poem "if All the Seas Were One Sea".If all the seas were one sea, what a great sea it would be! And if all the trees were one tree, what a great tree it would be! And if this tree were to fall in the sea, what a great splash there would be!Task 2KeyA. Complete the following sentences with what you hear on thetape.1) I found that living in Japan, people were much busier. They seem to work thewhole day.2) Where I was living in Japan, in the north, it was much colder than England,especially in winter, minus thirty degrees centigrade. Does the winter inOsaka last longer than the winter in England?3) I found Japan much more mountainous than Britain, especially in the north.The mountains are much higher and much more rocky. I found it morebeautiful than Britain.4) And therefore the towns and villages tend to be more crowded.5) So because the cities are more crowded, the houses tend to be smaller, don'tthey?B. Decide whether the following statements are true (T) or false (F) according tothe tape.1) People need to take three showers a day in the humid and hot summer inJapan. [ T ]2) Winter in Osaka is shorter than that in England. [ T ]3) Etsuko thinks the countryside in Japan is more beautiful than that inEngland. [ F ]4) Britain is mountainous and Japan is much flatter. [ F ]5) Houses in Britain tend to be smaller and compact. [ F ]Task 3A. Answer the following questions,1) What is the difference between the folk dances in the US and other countries?Key: In the US, people usually dance just to enjoy themselves; they don't inviteother people to watch them.2) How many dancers are there in a folk dance in the US according to the man?Key: Usually eight people dance together.3) Why is it called square dance?Key: Because people form a square in dancing with a man and a woman on each side of the square.4) How does the man tell the dancers what they should do?Key: He usually makes it into a song.5) What kind of clothes do people wear in folk dancing?Key: They wear old-fashioned clothes.B. Decide whether the following statements are true (T) or false (F) accordingto the tape.1) There is only one folk dancing group in each city in the United States. [ F ]2) Usually there are four men and four women in a folk dancing group. [ T ]3) In square dancing, there are four people on each side of the square. [ F ]4) A man usually speaks quickly to tell the dancers what they should do. [ F ]5) People dance fast, therefore there is not much time for them to think of theinstructions in the song. [ Y ]C. Complete the following sentences with what you hear on thetape,1) In square dancing, usually eight people form a square when they start, with aman and a woman on each side of the square.2) Then there's a man who tells the dancers what they should do. He usuallymakes it into a song, and sings it while they dance.3) Folk dancing in the Unites States is very fast; people don't have much time tothink.4) The dancers wear old-fashioned clothes. They makes the dances pretty towatch.Task 4Answer the following questions.1) What was known as "Setsubun"?Key: It was a time to celebrate the end of winter and the beginning of spring.2) What did many Chinese families burn to bring good luck before the Chinese Lunar New Year?Key: They burned the picture of their kitchen god to bring good luck.3) What was the old custom in choosing what to wear by brides in America?Key: The custom said the brides must wear "something old, something new, something borrowed, and something blue" to bring good luck.4) Why did the people of Ponti, Italy eat an omelet made with 1,000 eggs beforeLent?Key: Because they could not eat meat, eggs or dairy products during Lent, so they tried to use up these things before Lent began.5) What was a "Start"?Key: It was a straw man made by children in Czech; it was a figure of death.6) What did people do on St. Anthony's Day in Mexico?Key: People brought their animals to church. And before the animals went into the church, people dressed them up in flowers and ribbons.Task 5A, Decide whether the following statements are true (T) or false (F) according to the tape.1) The two speakers agree that Victorian life used to be much more fun than it is now.[ F ]2) In Victorian England, people had to wear hats and long gloves even when theywere eating cakes and biscuits. [ T ]3) Life is much slower than it used to be in Victorian England, where people neverhad time to stop and enjoy themselves. [ F ]4) There were more illnesses in Victorian times, some of which do not exist today. [ T ]5) Children in Victorian England hardly ever saw their parents, because their parents were working hard. [ F ]6) Children nowadays do not wear tight, uncomfortable grown-up clothes, and theirlife is much better than before. [ T ]7) According to the woman, women today enjoy more freedom, though they may haveto work hard. [ T ]B. Write out a list of the advantages and disadvantages of life in the Victoriantimes.Task 6A. Choose the best answer to complete each of the following sentences.l) With the industrialization of American society, the family became more common.(-b)a) extended b) nuclear c) blended2) At present, nearly one out of every marriages in the United States ends indivorce. (-a)a) two b) three c) four3) Now one in Americans lives alone. ( c)a) three b) four c) five4) Currently, there is a(n) in the number of childless marriages. ( a )a) increase b) decrease c) don't knowB. Complete the following sentences with what you hear on the tape.l) The American family unit is in the process of chang_e_. There used to be mainly two types of families: the extended and the nuclear.2) Then as patterns changed and the economy progressed from agricultural toindustrial, people were forced to move to different parts of the country for "job opportunities. These moves split up the extended family.3) Now besides these two types of traditional groupings, the word "family" is beingexpanded. to include a variety of other liying arrangements.C. Complete the definitions below according to what you hear on the tape.1) The extended families most often include mother, father, children, and some other relatives, such as grandparents, living in the same house or nearby.2) The nuclear families usually consist of only the parents and the children.3) The blended families occur when previously married men and women marry again and combine the children from former marriages into a new family.Task 7A.Fill in the following chart with a "√" mark in corresponding columnsB. Choose the best answer to complete each of the following sentences.I) Japanese women often go to university to study- . ( c )a) medicine b) science c) arts2) There may be women in engineering classes of thirty or forty students. ( c )a) three or five b) two or four c) one or two3) Men do NOT want to work for a big company to . ( a )a) look for a wife b) earn a lot of money c) support a family4) Nowadays Japanese women begin to look for a job because they (b)a) want to compete with men b) like it c) hope to find a good husband5) A few years after Japanese women get married, they often ( c )a) work in the same companyb) find a better job in another companyc) stay at home and look after everything6) After Japanese men get married, they often . ( c )a) prepare the mealb) look after the childrenc) go out for a drink after work7) Japanese women can go back to work (--c)a) after their children are bornb) when their old company wants them backc) after their children have grown upTask 8A. Choose the best answer to complete each of the following sentences.1) "Taking their vows" means . ( a )a) getting married b) getting divorced c) getting engaged2) "We basically suit each other very well" means . ( c )a) we like each otherb) we're completely similiar to each otherc) we get along with each other3) When Sue says that she and her husband are "loath to lose their freedom justyet". She means ( b )a) they hate the idea of having childrenb) they want to enjoy their freedom for a few more years, but they mayconsider having some kids laterc) they are revolted by the idea of giving up their freedom4) If a person is frowned upon by society, he/she is . ( c )a) criticized severely by societyb) ridiculed by peoplec) disapproved of by society5) When asked about how people get married in England, Geth is talking about~ (c)a) people born in London onlyb) people whose family are all living in Londonc) people living in London with their parents and relatives living elsewherein Britain6) At a registry office you need a minimum of (b)a) the bride and bridegroom plus four other peopleb) the bride and bridegroom and two other peoplec) the bride and bridegroom only7) Geth thinks that young people in London often live together ~ ( c )a) because they are afraid of marriageb) with the intention to get married eventuallyc) without thinking of ever getting married8) Chris thinks divorce is . ( b )a) more difficult for menb) more difficult for womenc) now considered quite acceptable by societyB. Decide whether the following statements are true (T) or false (F) according tothe tape.1) In Geth's opinion, people usually go back to where their parents live to getmarried. [ T ]2) It is a tradition for all the relatives and friends to have a drink together after thewedding ceremony. [ T ]3) Marriage in a registry office takes longer than in a church. [ F ]4) Home ties are more restrictive in London than in the country. [ F ]5) In Geth's opinion, people who live in London can do more or less as they please.[ T ]6) Geth thinks divorce is more likely if people have been living together beforegetting married. [F]7) Sue's marriage is unsuccessful because she and her husband have little incommon. [ F ]8) Sue and her husband loathe the idea of having children. [ F ]9) Divorced women sometimes find it difficult to get morried again. [ T ]10) The technical difficulties are the only problems in getting a divorce. [ F ]Task 9ScriptSocial customs and ways of behaving change. But they do not necessarily always change for the better. Things which were considered impolite many years ago are now acceptable. Just a few years ago, it was considered impolite behaviour for a man tosmoke on the street. No man who thought of himself as being a gentleman would make a fool of himself by smoking when a lady was in the room.The important thing to remember about social customs is not to do anything that might make other people feel uncomfortable- especially if they are your guests. There is a story about a rich nobleman who had a very formal dinner party. When the food was served, one of the guests started to eat his peas with a knife. Other guests were amused or shocked, but the nobleman calmly picked up his knife and began eating in the same way. It would have been bad manners to make his guest feel foolish or uncomfortable.Unit 2Task 1Choose the best answer to each of the following questions,1) Which of the following statements is correct in describing the size of Texas? (b)a) Texas is the largest state in the US.b) Texas is the second largest state in the US.c) Texas ranks the forty-ninth in terms of the size.d) Texas is smaller than Alaska, but it is a little bigger than many other states inthe US.2) Which of the following statement is correct about the weather in Texas? ( a )a) Texas has different kinds of weather pattems as it is such a big state.b) The weather in Alaska must be more varied than that in Texas, since it coversa larger area.c) Texas has the coldest place in winter in the US.d) Texas has the warmest place in summer in the US.3) If you were going to travel in Texas, how would you plan your tour to enjoy niceweather everywhere you went? (d)a) Visit Laredo in summer and Amarillo in winter.b) Visit Laredo in winter and Amarillo in summer.c) Visit Laredo in spring and Amarillo in autumn.d) Visit Laredo in winter and Amarillo in autumn.Task 2A. Decide whether the following statements are true (T) or false (F) according tothe tape.1) The extreme weather in Britain never lasts long. [ T ]2) There is a huge amount of rain in Britain. [ F ]3) People coming to Britain should be prepared for the notorious fogs. [ F ]B. Choose the best answer to each of the following questions.1) What was Nick's explanation for the bad reputation of the British climate? (d)a) It is very cold.b) It rains heavily.c) The dense fog often frustrates people.d) The weather often changes quickly and unpredictably.2) What does NOT account for the fact that you could feel cold at almost any timeof the year in Britain? (c)a) Draughty British houses.b) Little sunshine.c) Fog.d) Humidity.3) Which of the following is NOT Nick's implication by saying, "to understand themeaning Of the splendid word 'drizzle'"? (c)a) He advised people coming to Britain to bring an umbrella.b) He realized that British weather is terrible.c) He thought learning English well could help foreigners to live inBritain.d) He thought it rains often but not always heavily in Britain.C. Fill in the blanks with what you hear on the tape.Why then, he asked, has the British climate such a bad reputation? He answered by saying it was because of the extraordinary, unreliable weather. There was no partof the year at which you could be certain the weather would be dry or wet, clear ordull, hot or cold. A bad day in July could be as cold as a mild day in January.Task 3Complete the following summary of the passage.I. Low temperature in the countryReason: Trees, grass, lakes and steams help to cool the area around them.II. High temperature in citiesA. Warm nightReasons: 1. Cities are built of asphalt, concrete, iron and steel.2. Streets and buildings take in the heat during the day and throw off heat into theair at night.B. Warmer wintersReason: The heat set off from car engines and electrical appliance warms cities even in winter.III. How cities influence global climateA. Global climate may get cooler, for air pollution may stop sunlight from reaching theearth.B. Global climate may get warmer, which may cause1. Ice near the North and South poles to melt.2. Cities near oceans to be slowly flooded and people living in these cities to moveto higher land.Task 4A. Choose the best answer to each of the following questions.l) Which of the following statements is true according to the article? (b)a) Red sky in the morning means that the weather is going to change.b) Red sky at dusk means that good weather is coming.c) Red sky in the morning means that the weather will be good.d) Red sky at dusk means that the weather is going to be bad at night.2) What is meant by a "weather predictor" here? ( c )a) A person who predicts weather.b) An apparatus by which people predict weather.c) A natural phenomenon which helps people to predict weather.d) A weather service station.B. Fill in the blanks with what you hear from the tape.Red sky at night, sailors' delight.Red sky at morning, sailors take warning.OrEvening red and morning gray,sends the traveler on his way.Evening gray, morning red,brings the rain down on his head.C. Decide whether the following statements are true (T) or false (F) according to the tape.l) A red sky is caused by dust particles. [ F ]2) A high pressure system brings in dry weather, while a low pressure system brings inmoisture. [ T]3) If there is a red sun in the morning, bad weather is on the way. [ F ]Task 5Choose the best answer to each of the following questions.l) Why does the man often find himself in a raft on the river during lightning storms? (c)a) He enjoys fishing in stormy weather.b) Probably he does not have the habit of listening to weather report.c) He goes fishing very often and sometimes gets caught in bad weather.d) He wants to test where is the safest place to stay when lightening occurs.2) What kind of debate does the man often have with his companion when lightningapproaches? (b)a) To stay in the raft or get into the water.b) To stay in the raft or get ashore.c) To stay in the raft or get into a car.d) To get into the water or get ashore.3) Why does the meteorologist suggest that he should not stay in the raft when a lightningstorm comes? (d)a) His raft is not insulated.b) Lightning travels at a very high speed.c) Lightning releases very strong electricity.d) The electricity released by the lightning travels in water and can penetrate theraft.4) How much electricity can a lightning flash deliver? ( c )a) 100 amps.b) 10,000 amps.c) 100,000 amps.d) 1,000,000 amps.5) What should a person do if lightning occurs when he or she is on a river? ( c )a) Abandon his or her raft.b) Swim to the shore.c) Seek shelter on land.d) Stay on the craft.Task 6A. Decide whether the following statements are true (T) or false (F) according to thetape.1) Tornados often occur in the summer. [ F ]2) A tornado forms when a layer of warm, dry air is on top of a layer of cool, moist air.[ T ]3) As the air rotates, the cloud develops upward. [ F ]4) A tornado does not form on the ground. [ T ]5) Air moves at a speed between 200 and 700 kilometers at the eye of a tornado. [ F ]6) A tornado develops from a dark rain cloud and gets darker when it draws in dirtfrom the ground. [ T ]B. Fill in the blanks with what you hear on the tape.When the tornado touches the ground, it does incredible damage. It usually touches the ground for only about one minute, and it usually travels along the ground for only about one kilometer, but during that one minute, buildings are destroyed, trees are lifted up out of the ground, small objects are carried away, and sometimes people are killed or injured.Task 7A. Choose the best answer to each of the following questions.1) When is the weather report broadcast? (b)a) 9 am.b) 9pm.c) 9 o'clock. But it's unclear whether it's 9 am or 9 pm.d) Not mentioned in the material.2) What day is this weather forecast on air? ( a )a) Thursday. b) Friday.c) Saturday. d) Sunday.3) If you are going on holiday during the weekend, which place should you avoid?(b)a) Greece. b) France.c) Spain. d) Southeast Italy.B. Summarize the weather conditions reported in the radio programme.l) For today: It has been nice weather during the day, but it is going to change atnight.2) For the weekend: Fine weather in southern Europe and not so nice in NorthernEurope.C. Match each place with the corresponding weather condition there.For todaySoutheast England Maximum temperatures of around 21 degreesSouthern Scotland 26 degrees Celsius by mid-afternoonBrightonMidlands Light showers around middayNorthwest of Scotland 15 hours of lovely sunshineFor the weekendSpain Cloudy but mainly dry with sunny periods, 23 degreesCelsiusGreece Heavy rain, 17 degrees CelsiusFranc Cloudy with rain, maximum temperatures of 22 degrees Northem Ireland 34 degrees CelsiusMost of England 32 degrees CelsiusTask 8Task 9A, Tick the statements "√" that correctly describe the tornado in Xenia in 1974.1) It was named "Super Outbreak". [ ]2) It hit 13 states. [ ]3) It killed 33 people. [√]4) It lasted for 16 hours and 10 minutes. [ ]5) It killed 330 people and injured nearly 5,550. [ ]6) It was one of the most destructive in US history. [√]7) It was of the most intense level. [√]B. Rearrange the following sentences describing the boy's experiences on theday when the tornado hit his town.a. I got back home just in time to answer Mom's telephone.b. I woke Dad up to watch.c. I thought I heard my father calling me.d. I watched TV.e. Dad and I went into the bathroom.f. I was playing with some neighborhood kids after school.[ f ]---[ c ]--[ a ]---[ d ]---[ b ]--[ e ]C. Decide whether the following statements are true (T) or false (F) according tothe tape.1) 5 people were killed in a parking lot in the tornado in Xenia in 1974. [ F ]2) 13 US states were struck by 148 storms within 2 days. [ T ]3) The Xenia tornado became a textbook case because it killed 33 people. [ F ]4) The witness said that he would not do business any more due to hisexperience in that tornado. [F]D. Choose the best answer to each of the following questions.1) Which of the following coincidences did NOT help the boy to survive thetornado? (d)a) The boy thought he heard his father calling him.b) The boy's father had a very bad case of tonsillitis and stayed at home on thatday.c) The boy got back home just in time to answer his mother's call.d) He was watching TV when the tornado arrived.2) Why do you think that the witness could still clearly remember theconversation between his father and him While they stayed in the bathroom to wait for the tornado to go by? (b)a) He had a very good memory.b) He was highly alert at that time.c) The tornado stayed on the ground for a reasonably long time.d) The conversation was interesting.Task 10ScriptUndoubtedly, Tibet is one of the harshest places for human existence. It is cool in summer but freezing cold in winter. In Lhasa, the mildest city in Tibet, temperatures may exceed 29 degrees Celsius in summer while plummeting to -16 degrees Celsius in winter! Sun radiation is extremely strong in Tibet. The sunlight in Lhasa is so intense that the city is called Sunlight City. The thin air can neither block off nor retain heat so that there are great temperature extremes on the same day! The average temperature in northern Tibet is subzero and winter arrives in October until thefollowing May or June. July and August are the best time to visit the area, enjoying warm temperatures, intense sunshine, beautiful scenery and festive events. May, June and September represent the tourist season in east Tibet. In winter, roads are all blocked by heavy snow. Landslides and rock falls frequently occur, which will make travel difficult.。

key-to-exercises(U1)Unit 1Active reading 1 (P5)3. 34. b, c, c, d, c, a5. 1 productive, 2 attendance, 3 resistance, 4 ambitious, 5 acceptance, 6 script, 7 impressive6. (1) attendance, (2) ambitious, (3) productive, (4) impressive, (5) resistance, (6) script,(7) acceptance7. 1 mortgage, 2 deck, 3 surf, 4 coastal, defy, 5 lengthy8. b, a, b, b, b, a, b, b9. 1 The use of the time expression, together with the past tense, is a signal that this isa narrative with a sequence of events. The word our indicates that this is a storyof personal experience.2 This indicates that studying for the final exams was not the only concern of thestudents. So it is a transition from studying for final exams to the next topic –getting a job after graduation.3 Because this changes the focus onto the writer as an individual. The we paragraphsare general background to the main narrative about the individual, which is coming.4 This change to direct speech opens a moment-by-moment dialogue. This slows downthe narrative of events but gives a good impression of how the writer found it difficult to say what he wanted to do and how the father made few comments.5 The topic shifts to crabs. The sentence also arouses the readers’ interest – we expectsome fascinating new information about crabs here. Later, we realize how the topic of crabs is connected with the son finding a job, and the crabs’ behaviour leads the father to give memorable advice.6 Yes, we don’t know what happens next, but the implication is fairly clear that thefather would support the son’s idea of travel and of being a writer. It makes a better conclusion not to say it explicitly, as it leaves a lot of room for personalinterpretation.Active reading 2 (P8)2. c, d, b3. 34. 1 triple, 2 cemetery, 3 rear, 4 biography, 5 cram, 6 budding, 7 finite, 8 elapse5. 1 elapsed, cemetery, 2 crammed, 3 triple, 4 budding, biography, 5 finite6. a, b, a, a, b, b, a, a7. a, b, b, a, a, b, b, b, a8. We may not even last that long.(“life is short”)It could be sooner than we’d like. (“life is short”)… go out and do them now before it’s too late. (“act now”)It needs to be brought forward and done now ...(“act now”)• The novel … the trip … your mind’s-eye dream-job … the West End play … – you have to do them now.• Tomorrow is just another version of now, an empty field that will remain so unless we start plantingsome seeds.• Fill your bowl. We come this way but once so let’s make the best of the short stay.• Fit as much into the short time there as yo u can.• And now is the time, not tomorrow. There is no time like the present.• … if we are dying and our allotted time is finite, why the hell aren’t we doing all the things we want to do NOW?• So I say stop waiting and meet providence halfway. Start fi lling your life with the riches on offer …• Act now or your time will elapse and you’ll end up as a sepia-coloured relative …9. 1 The image is of the reaper of death. We never know when death will come to us. Thereaper wears a black hood so you can’t se e his face, and he carries a scythe which represents cutting people down like corn; he brings our last breath.2 This refers to the main body of the story, and the main part of our life, like the meatin a sandwich. The meat is between two pieces of bread; the main content of the story is between the prologue and epilogue.3 This means plans which you have postponed or kept waiting as a low priority, as ifthey are simmering gently but not really cooking on the back part of the cooker.4 This means tomorrow is like a note which has promised a payment of money but bywhich we can’t actually get the cash. It never really comes unless we act now.5 The image is of someone driving a car and looking in the rear-view mirror. They arelooking at their past with lots of regrets about what they could have, should have, or would have done but did not in fact do.6 This means take as much as you can in your life within the limits of what is possible.The image is of filling a salad bowl with as much salad as possible because you only have one chance to serve yourself.7 This image is of a man waiting for a girl who has said she will come but who isn’t5 It wasn’t just that the Grim Reaper was intended to frighten people, but it wasalso a figure of fun.5. 1 settle(a) On the surfaces that aren’t used very often or aren’t cleaned.(b) Yes, it is, because the disagreement i s solved and each p arty is satisied with theoutcome.(c) Nothing, because you have paid everything that is owed.(d) We relax in a comfortable chair and enjoy it.2 smooth(a) No, because the sea is calm. We will feel seasick if it is rough.(b) No, because the changeover has gone well, without dificulties.(c) Not necessarily, because some people whotalk confidently like that do so to trick you,like a conidence trickster or conman.3 offer(a) We say “no”, because we are refusing it.(b) We should say, “I apologize”or “I’msorry”.(c) In a shop, because the shop is offering aspecial price or reduction for something. (d) They are intelligent, talented, gifted orcreative and they will bring these kinds ofqualities to their work.4 bear(a) No, we will remember it and consider it fora particular occasion in future.(b) We look similar in certain physicalfeatures.(c) I can’t bear to think too much about someof the problems in the world, famine, war, poverty etc. In the modern world, why don’t we just solve them?5 resistance(a) No, not easily. They refuse to accept theidea maybe because it’s j ust a bad idea, or they may change their mind if they understand it better.(b) The soldiers met opposition from thosethey were fighting against.(c) Yes, we can keep ourselves as healthy aspossible with a good diet and getting enough exercise so that we are less likely to catch a cold, or if we do get one, we won’t suffer so badly.6. Translate the paras into Chinese.1 注:and guys wore the bags under their eyesand their pale, sleepy faces with pride …这句的动词wear 后面带两个宾语,中文找不到能带这两个宾语的动词,故处理成四个中文短句;翻译like medals provingtheir diligence 时,采用“增词法”增加“这些”来概括前面所描写的“眼袋”,“脸色苍白”,“睡眼惺忪”等,使译文含义更加清晰流畅。

Key to ExercisesPreview第一大题1.This article was written in praise of the heroes and the heroism demonstrated during an air crash which took place in WashingtonD.C. in the year 1982.2.The terrible crash occurred in cold winter when a jet plane from Washington National Airport hit the bridge over the Potomac river. The plane dropped into the river and soon sank/ went under, bring many passengers down with it. Those who managed to get out of the plane found themselves in icy-cold water.3.Disasters are always terrible because they mean great damage and loss of life. As disasters go, this air crash was nothing very special. But because of the four heroes, it brought millions to tears or attention. Three of them formed a police helicopter team, andthey risked their lives again and again as they tried to pick up survivors. But the greatest hero was a man known as “the man in the water”because his name was never found. He was seen clinging to the tail of the plane with five other passengers. But every time a lifeline or flotation ring was dropped to him, he passed it on to another of the passengers. Those passengers survived. But the man did not.4.The emotional impact of this display of courage and noble character was tremendous, because it showed human nature at its best. This man in the water must have been an ordinary person. Before the air crash, he would never have guessed what a heroic deed he was going to perform that day, but when the great test came, he rose to the occasion.5.The author believes that this disaster filled people with a sense of pride rather than sadness, because in the contest between indifferent natural forces and the moral power of human beings, human beings have won.The man went down in the river, but he actually rose to immortality.第二大题1.The unusual element is the bridge, because normally, air crashes do not involve a bridge. Note: The word “element” means a factor or a basic part of something complicated.2.“A city of form and rules” means a city that is shapely or beautiful and orderly, but it suddenly turned into its opposite and became chaotic, turning into a state of complete disorder and confusion.The two metals here refers to the bridge and the plane, both of which are made of metal, or more specifically, iron and steel钢铁.3.From the point of view of artistic beauty, there was also a clash or conflict, because the plane was painted into blue and green, the river and black, and the chunks of ice were grey. Mixture of different types of color would make the viewers uncomfortable, so they wou ld regard this scene as “aesthetic clash”.4.Perhaps people did not regard this air clash as a failure at all. They all saw the triumph of human nature over the elements.5.Here human nature and natural powers are in conflict/clash.“Groping and struggling” re fers to the fact that normally it is human instinct本能;天性to grope for something to hang on to (=to hold on; to survive) and to struggle for life.6.Rise to the occasion: to deal successfully with a problem or situation that is especially difficult.7.The sente nce means “Three out of the four acknowledged heroes...are able to account for their behavior”.Account for: to give a satisfactory explanation.8.In the line of duty: while working; while on duty9.Skutnic added that somebody had to go in the water saying what every hero would say under the circumstances, but although the remark has been repeated by many heroes, it isstill admirable.10.It means the main reason for the emotional impact, or the person who caused the great emotional impact.11.Mass casualty: a great number of people injured and killed in an accident or battle. The word “mass” here is an adjective, meaning affecting a lot of people. Cf: mass murder; mass killing; mass destruction; mass hysteria; mass protest; mass movement; mass unemployment; the mass media; the mass market; mass-produce v; mass-produced adj.; mass production. Derivation: massacre; massiveCommitment: a sense of duty and responsibility and a determination to work hard at it.12.As his name remained unknown, it made him a sort of symbol, a symbol of what human beings can do when they are at their best. 13.“listening to...” is a participle phrase used as an adverbial of manner, modifying thepredicate of the main clause “sitting”; “tell...” and “saying...” are both part of the complex object of “listening to”; and “to fasten...” is part of the complex object of “tell”.14.In the essential, classic circumstance: in the most significant/crucial/decisive and typical circumstance15.The age-old battle between human beings and nature16.Go at each other: to fight each other violentlyAct on principles: to act according to the distinction between good and evil; to act according to moral principles17.It means that when the man in the water gave a lifeline to the people gasping for survival, in the same way he seemed to be also saving the lives of those who watched him, making them understand life’s true meaning. 18.Hold it to a standoff: make nature unable to win the battle immediately (迫使自然接受在和人的斗争中的僵持局面,使它不能马上得逞)Vocabulary第一大题第一小题1.Incompetence2.Immoral3.Impossible4.Incomplete5.Impersonal6.Incredible7.Indirect8.Immovable9.Immortal10.Impolitermal12.Improper13.Impartial14.Impatient15.Incorrect16.Incapable17.Insignificant18.Impractical19.Imperfect20.Insensitive21.Impermissible22.Impenetrable23.Indifferent24.Immovable25.Invisible26.Immodest27.Immature28.Invaluable29.Invariable30.immeasurable第二小题(1)-ee: noun. One who receives(2)-eer: noun. Doer; device for(3)-ess: noun. female第三小题1.经济起飞2.欢送会3.梦想复辟4.可耻的出卖5.后续讨论6.产品用后就扔的现代经济7.使用过多的化妆品8.严重的精神崩溃9.给了个表示许可的信号10.怀疑这是有意掩盖真相11.我们叫个外卖吧12.在军事接管之后13.给学生一些讲义14.改革的好处、红利15.联盟最后的破裂16.中途退学的人17.第二天清晨仍能感觉到的酒后头昏18.出来参加投票的人不多vote第二大题1.Employer2.Unfasten3.Bad/evil4.Unidentified5.Concerned/caring/considerate/interested/sy mpathetic6.Immovable7.Impersonal8.Irresponsible9.Selfishness10.Individual/personal/specific/private/unique One and only11.Shallow12.Undress13.Slightly/somewhat/in part/partially impartial14.Deny denial15.(bride)Groom第三大题1.Air crashes/air collision and other natural disasters2.Human nature and character3.The tail section of a jet plane4.Huge chunks of ice; a huge chunk of ice5.A flotation ring6.Fasten the seat belt7.Culture/Culturalconflict/clash/collision/shock8.Flight 9119.Mechanical failure10.Human tragedy11.Harsh remarks12.Make a distinction between good and evil13.Presidential monuments14.Typical/classic/representative circumstance15.Universal character/characteristic/feature16.A public hero17.Emotional impact18.A moment of high/heavy traffic; rush hour; traffic peak19.Enduring/lasting wonder20.Air Florida21.Congressional Budget Office/Bureau/22.Mass casualties第四大题1.Refer to; known as2.In reality; as ever; responsible forNote:A small, isolated group or area:there were pockets of disaffection 不满;背叛in parts of the countryMORE EXAMPLE SENTENCESIt is calling for a new approach to nature conservation, focusing on whole landscapes rather than isolated pockets.偏远区域Famine is biting deep in isolated pockets all over the country.There are coalitions, but they're in separate pockets around the country, it is not a national coalition.ADJECTIVE [ATTRIBUTIVE]Of a suitable size for carrying in a pocket:a pocket German dictionaryPick sb’s pocketPickpocket n. thief/theft/thieve3.Brought; to tears; sticksIf you do something single-handed(ly), you do it on your own, without help from anyone else. 单独地I brought up my seven childrensingle-handed.我独自带大了7个孩子。

U n i t1练习答案-全新版大学进阶英语-CAL-FENGHAI.-(YICAI)-Company One1Unit 1 Key to ExercisesOpener1. Mr. Qian Xuesen was a distinguished and world-renowned rocket scientist. Steve Jobs was a famous American entrepreneur, the co-founder, chairman, and CEO of Apple Inc.2. Both of them were dream pursuers and hard workers who finally succeeded in fulfilling their dreams in their own specialized domains. Qian Xuesen became universally acknowledged as the father of China’s space programs, and Steve Jobs came to fame as a creative entrepreneur who revolutionized many products, including personal computers and smartphones.3. In the early 1950s, Qian, a scientist working in the United States, suffered serious persecution by the US government just because he sympathized with China. However, he remained firm and overcame lots of difficulties and returned to his motherland in the end. Following that, he devoted himself whole-heartedly to the development of China’s nuclear weapons program. As to Jobs, he also had to overcome a lot of obstacles on his way to success. Once he was forced out of Apple, the company he had co-founded. But years later he came back and became its CEO, and led the world in tablet computing and smartphones.Reading & InteractingI. Understanding the Text1. Text OrganizationThe D evelopment of the Writer’s Skills as a DJ2. Comprehension Check2.1 Focusing on the main ideasRobbie Wilde has been enjoying his life as a DJ. He was born withperfect hearing, but is now completely deaf in his right ear and can hardly hear in his left. He grew up in a musical home environment and started deejaying at age 18. With a strong desire to perfect his skills, he asked a well-known DJ for tutoring. He has been working hard and does not want his skills recognized simply because people have sympathy for his disability. In this way, he sets a good example for other young people in chasing their dreams.2.2 Digging into detail1. He was born with perfect hearing in both ears, but severe ear infections that started when he was five left him deaf in his right ear and 50% deaf in his left. Over time, his remaining hearing dropped to 20%.2. They were always surprised.3. He places one speaker facing his good left ear, and makes it louder all the way up. The speakers that play the bass are put on the floor behind him, so he can hear some of the lower frequencies and feels the beat in his feet.4. It most probably means “with the eyes”.5. He loves its creativity, and what he can do with a machine, two turntables, and a mixer.2.3 Understanding difficult sentences•1) A•2) B•3) B•4) A•5) BII. Focusing on Language in Context1. Key Words & Expressions1.114.The art exhibition is great; it’s a pity you don’t have time to go there but you cansee it on your computer screen.15. The researchers are concerned about the increasing frequency of the illness in thevillage.1.2•1) big on•2) all the way•3) motivation•4) predicting•5) hooked•6) pursuit of•7) elementary•8) folk•9) taken over1.32. Word Formation3. Sentence Patterns2. When one door closes, another opens for you. How about looking for other opportunities3. It is not enough to learn from textbooks. Why not take a part-time job to gain some practical experiences?4. The school doesn’t have a student society that provides community services.How about starting one with your classmates?5. If we agree that college life is a new experience for growing up, why not take a more active part in various activities on campus?4. Comprehensive Practice1. A: Our government encourages college students to be creative and start career planning early. What does this mean for your dream of a future job?2. A: My problem is that I have dreams but they always seem so far away and hard to achieve. What’s your advice?B: First, you need to look inside yourself and know what you really want to do. In other words, you need to build up your confidence and believe in yourself/your dream. Second, create a concrete plan and take action in pursuit of your dream. By so doing, you will, I’m sure, make your dream come true over time.3. A: Do you have a dream job in mind already If so, what is it Would you mind sharing it with usB: My dream job is a corporate position such as a manager leading a team to help the company reach its goals. What I like most about the job is to overcome challenges and make decisions with creativity. I’ve got hooked on reading books on team leadership now!4. A: In chasing my dream, obstacles come my way from time to time. I sometimes think of giving up. As a successful CEO, can you share your experience with me about how to deal with them?B: Yes, I’d be more than happy to do so. To deal with things holding me back, I’ll look closely at them first, and then make a list, instead of saying to myself “Whynot just give up”. For some obstacles, I will not let excuses take over. For example, it actually doesn’t help if my blame goes all the way to life not treating me well. By finding the right kind of help, I can grow stronger no matter what and do well.Reading & ComprehendingReading 11. Comprehension Check for Reading 1•1) T•2) F•3) T•4) F•5) F•6) T•7) T•8) F•9) T•10) T2. Translation1.我喜欢读塞涅卡的作品,因为这些书中弘扬的正是我的家庭教育所推崇的精神——不追名逐利,过简单、诚实、体面的生活。

Keys to the exercises of the Unit 1III. Vocabulary & Structure1.1) rough 2)exceeding 3)stand out 4)Witnesses5) rejected 6)adopted 7)flowed in 8)emerged9)To seek out 10)(should)resolve2.1)The tiny nun in the cotton habit founded in the slums of Calcutta an order that grew into an international movement.2) By the age of 12 she was already resolved to become a nun.3) She heard what she said was without doubt a call from God to serve the poorest of the poor.4) The vow of poverty was more strict than in other orders because,in Mother Teresa’s view,“to be able to love the poor and know the poor we must be poor ourselves.”5) By the 1980s Mother Teresa had become a familiar figure at scenes of disaster..IV. Banked Cloze1. J 2.C 3. F 4.B 5.O6. M 7.G 8.A 9.N 10.IV. Translation1.1) to reject a human soul in need2) the love and cheerfulness that permeatedthe wards3) forced her to announce her retirement4) giving cause for concern5) adopted the religious nameV. Translation2.1)身着修女袍的她证明了“信仰诚,大山移”这一真理。

Unit 1 Fairy TaleA Glimpse at Words and ExpressionsPlease read the following sentences. Pay attention to the underlined part in each sentence and see how these expressions are used in the context, and then write down its meaning in the blanks provided.1.They gave themselves ridiculous airs, and wouldnot keep company with any but persons of quality. (associate with; make friends with)2.This news had liked to have turned the heads ofthe two eldest daughters, who immediatelyflattered themselves with the hopes of returningto town.(make sb. conceited )a3.…they went to law with him about themerchandise. (went to legal preceedings against )4.If your daughter refuse to die in your stead, youwill return within three months. ( in stead of you; in yourplace )5.The beast responded, “You are very good, and Iam greatly obliged to you.”(am grateful to you)6.Will you give me leave to see you sup? (give me permission)7.…her newly found happiness and materialcomfort with the Beast(give comfort to)A Sip of Word FormationBuild Your VocabularyDecide which form of the negative prefix to use to make each word. Add the prefix and write the whole word.A Smart Word PlayerThe word in capitals at the end of each of the following sentences can be used to form a word that fits suitably in the blank space. Fill each blank this way.Example : He said “Good morning ” in a most friendly way. (FRIEND)1. There is no doubt that cannabis will remain an _illegal drug for the foreseeable future. (LEGAL)2. It was quite impossible for us to drive all the way from Paris to Madrid in one day.(POSSIBLE)3. He made a (n) unsuccessful attempt to climb the highest mountain in the range.(SUCCESSFUL)4. To take the boat out with four children under the age of ten and with no life jackets on board was quite irresponsible of him. (RESPONSIBLE)5. The dress she was wearing was quite ___________ for the occasion. (APPROPRIATE)6. It was very impolite of him to insult his mother in front of his aunt. (POLITE)7. They were a completely _________ family and I never thought that one day I would marry one of the daughters. (RELIGIOUS)8. As a politician he was dishonest and it was not long before nobody trusted him.(HONEST)9. The goods were imperfect and had to be returned to the store we bought them from.(PERFECT)10. She was ________ with her life and decided that things had to change. (CONTENTED)共有六个部分组成。

Unit Nine Move to ChinaVII. Key to ExercisesTask-based Teaching Procedure One1.C2. A3. BTask-based Teaching Procedure Two1, 2, 4, 5, 6, 8Task-based Teaching Procedure Three1-5 B I C D A 6-10 E F G H JPersonal ChallengePart I Reading for understanding●Section A Information Recognition 略●Section B Reading for Deep understanding1-6 C A C D B DPart II Vocabulary Exercise●Section A Blank Filling1 with2. in3. to4. in5. for6. into7. between8. to9.around/round10. into●Section B Multiple choice1-5 A C B A B 6-10 D B A C B 11-15 A D A C BPart III Sentence StructureSection A Sentence Formation1.The librarians were faced with the huge task of listing all the books.2.The government has taken control of all the newspapers.3.Dealers were paying unbelievable prices for her painting.4.For my part, I prefer leaving the country.5.The man was suspected of committing murder.Section B Paragraph Coherence1-5 D C N L J 6-10 B A H O MExercise to Empower Yourself Part I Word formation1.considerate;2.management;3.disillusioned4.assumptionplaint6.additional7.explosion8.imaginative9.reference10.courageous11.proposal12.preparationPart II Speed-up translatione back to2.make preparations for/prepare (oneself) for…3.dream of4.be on holiday5. a fleeting idea6.as time goes7.turn out to be8.pursue one’s dream9.as well10.be under construction11.in addition12.realize/fulfill one’s dream13.be sick of14.be confident15.to have deep impression of/be impressed withPart III Word AcquisitionSection B Look through the following phrases and try to memorize them as quickly as possible and fill in the blanks with proper words.1.at2.for3.on/upon4.up5.down6.on7.off8.on9.up with10.togetherPart IV Chinese-English TranslationOver the next four days, the lunar exploration of Apollo taught us the quality of human being: in a word, restless. Human curiosity was never to be satisfied with; it would only constantly look for new targets. As the third moon landing human (and the first to fall on the moon), Conrad knew well that the target of people would change frequently. Since Armstrong and Aldrin took the first moon landing the award, there was no more concern about Apollo 12. Conrad later appeared in an advertisement for American Express. All those who showed up are some forgotten American celebrities, including cartoon rabbit elder brother's voice MEL Blanc. However, from many aspects, the lunar flight in which Conrad involved was the most interesting among Apollo lunar exploration plans. For example, Bean, with whom Conrad landing on the moon, was the most talented among astronauts, but he worked hard and maked up intelligence by diligence. When Bean finally ascended the surface of the moon, he threw away the silver NASA wearing badges, because he knew that walking on the moon would mean he had won a gold medal. However, when they flew back to the earth, Bean directly told Conrad how disappointed he was about the moon. He said,” I feel a little bit like songs ‘aren't just expressed’ in the feeling’”. Here we haveconcluded a timeless truth, that is: achievement itself is not important, the important thing is for you to pay efforts.Part V English-Chinese Translation1.“移居中国吧!”我北京的新朋友黛西曾在MSN(微软即时通讯软件)对话中打出了这样一句话。
Unit 5 Pioneers of Flight Key to ExercisesOpenerReading & InteractingI. Understanding the Text1. Text Organization2. Comprehension CheckFocusing on the main ideasThe article consists of three stories about pioneers of flight. The first story is about a Chinese named Wan Hu, who made an unsuccessful attempt at spaceflight in He built a spaceship powered by 47 rockets using gunpowder. His idea was crazy, but his dream of flight came true 500 years later when China successfully launched its first manned Shenzhou V spaceship. The second one is about the Spruce Goose, a flying boat designed to meet the need of transporting troops and materials during World War II. It was made entirely of wood and still holds the record for the greatest wingspan. Although it was never put to use, many of its design features have been incorporated into today’s cargo planes. The last is about Leonardo da Vinci, the most famous artist of the Renaissance. Apart from his great artistic work, he also drew sketches of flying devices with flapping wings controlled and steered by human pilots. Five hundred years later, a professional parachutist made a successful jump using a wood and canvas parachute based on one of da Vinci’s designs/sketches.Digging into detail1. Because it was powered by rockets.2. It was the biggest airplane ever built up to that time, and still holds the recordfor the greatest wingspan. Besides, it was made entirely of wood.3. No, because it was behind schedule and was not completed until well after thewar.4. Da Vinci’s flying machines have wings that flap like birds in flight.5. Because it is difficult for ordinary people to understand their passion for flight,their spirit of innovation, and their courage to try and make their dream come true.Understanding difficult sentences1. A2. B3. A4. B5. BII. Focusing on Language in Context1. Key Words & Expressions1. He regards learning as a daily experience as well as a lifetime mission.2. His plan is to design a new model, into which some features of previousmodels will be incorporated.3. The ship, with 1,000 passengers aboard, was bound for New York.4. It’s one thing to learn the rules of politics from books. It is quite another to getinto the complex world of real-life politics.5. At yesterday’s sports meet, my roommate Brian broke the record of our schoolin the men’s 100-meter race.6. Jack had a hard time grasping the basic concepts of mathematics.7. They are working on a new project, which calls for a(n) enormous amount oftime and energy.8. After I bought this iPad, I put into storage my old computer.9. The new law tries to maintain a balance between national interests andindividual rights.10. The teacher drew a(n) analogy between the human heart and a pump to helpstudents understand how it works.11. If we teachers believe in education and focus on students’ growth, our laborwill eventually pay off.12. On display in the exhibition room is a new device to harness wind power.13. His newly published book, which has made waves in literary circles, is based onevents that the writer himself has witnessed.14. At the meeting, he tried to steer the discussion away from criticizing theeducational experiment.15. The money was given to Ann as a scholarship, with no conditions attached.1. steer2. behind schedule3. ahead of his time4. Transportation of5. confirmed6. put on display7. harnessing8. had its roots in1. The artist drew a sketch of the young lady before going into a more detailedpainting.2. Brown currently is focusing on devising/designing a new type of washingmachine that does not use water.3. We need to adopt a different approach to music in education.4. Usually a label with your name and address is attached to your suitcase beforeyou check in at the airport.5. A new system should be devised because the old system simply doesn’t work.2. Collocation1. We rejected the proposal as a matter of principle.2. Although I am not an American football fan, it doesn’t mean I have no interestin it.3. Demand for coal is down and so are the prices.4. Biking is a green alternative to driving.5. Our research on climate change focuses on its effect on the environment.3. Sentence Patterns1. Our reading room has many interesting books as well as the latest magazines.2. The 300-page book contains many pictures of the artist as well as some of hisfamous paintings.3. For character building, one needs to succeed as well as fail sometimes.4. The latest model of the Huawei mobile phone is very popular at home as wellas abroad.1. Legend has it that the guy invented chess to please his King.2. Word has it that the CEO of my company will retire next year.3. Rumor has it that he has spent all his money on this crazy and risky plan.4. Legend has it that those who step onto this stone will have good luck.4. Comprehensive PracticeClozeLong, long ago Greek legend has it that Daedalus, a brilliant inventor, was imprisoned together with his son Icarus on an island in the Mediterranean. In order to escape, Daedalus devised a clever plan and sketched out his idea to his son. They would both fly away from the island like birds. It was risky, but both thought it worth a try. Using feathers attached together with wax and string, Daedalus made them both a pair of wonderful wings. Harnessed to these they were able to take to the air, leaving those on the ground who witnessed their flight amazed at their strange device. As they flew off over the sea their escape seemed certain. But Icarus, ignoring the warnings of his father, came too close to the sun. The wax holding his wings together melted and he plunged to his death in the ocean below.Translation1. How to harness the power of the rockets is the key to the successful launch ofa spaceship.2. The 20th century witnessed the growth of the aviation industry.3. During World War II, the United States needed giant cargo planes fortransportation of war materials.4. The film The Aviator is based on the life of Howard Hughes.5. The professor thinks that more money should be invested in/put into researchin the field of energy efficiency.6. They are carrying out a secret mission.7. “Focus on the content of the article. Don’t worry about individual words,” saidthe teacher to the students.8. Wan Hu’s plan was too risky and too primitive to be successful.Reading & ComprehendingReading 11. Comprehension Check for Reading 11. F2. F3. T4. F5. T6. T7. F8. T9. T 10. T2. Translation1. 他俩合起来的履历看上去令所有真正的飞行冒险家都羡慕不已。
Unit 1 Key to ExercisesOpener1.Mr. Qian Xuesen was a distinguished and world-renowned rocket scientist. Steve Jobs was a famous American entrepreneur, the co-founder, chairman, and CEO of Apple Inc.2.Both of them were dream pursuers and hard workers who finally succeeded in fulfillingtheir dreams in their own specialized domains. Qian Xuesen became universally acknowledged as the father of China ' s space programs, and Steve Jobs came to fame as a creative entrepreneur whorevolutionized many products, including personal computers and smartphones.3.In the early 1950s, Qian, a scientist working in the United States, suffered serious persecution by the US government just because he sympathized with China. However, he remained firm and overcame lots of difficulties and returned to his motherland in the end. Following that, he devoted himself whole- heartedly to the development of China ' s nuclear weapons program. As toJobs, he also had to overcome a lot of obstacles on his way to success. Once he was forced out of Apple, the company he had co-founded. But years later he came back and became its CEO, and led the world in tablet computing and smartphones.Reading & InteractingI.Understanding the TextThe Development of the Writer lls' a s SakDiJ1.Text OrganizationThe Development of the Writer lls' a s Sa kDiJprehension CheckFocusing on the main ideasRobbie Wilde has been enjoying his life as a DJ. He was born with perfect hearing , but is now completely deaf in his right ear and can hardly hear in his left. He grew up in amusical home environment and started deejaying at age 18. With a strong desire to perfect his skills, he asked a well-known DJ for tutoring . He has been working hard and does not want his skills recognized simply because people havesympathyfor his disability. In this way, he sets a good example for other young people in chasing their dreams.Digging into detail1.He was born with perfect hearing in both ears, but severe ear infections that started when he was five left him deaf in his right ear and 50% deaf in his left. Over time, his remaining hearing dropped to 20%.2.They were always surprised.3.He places one speaker facing his good left ear, and makes it louder all the way up. The speakers that play the bass are put on the floor behind him, so he can hear some of the lower frequencies and feels the beat in his feet.4.It most probably means “ with the eyes ”.5.He loves its creativity, and what he can do with a machine, two turntables, and a mixer. Understanding difficult sentencesII. Focusing on Language in Context1.Key Words & Expressions1.Good teachers should encourage students to use their creativity to express themselves andmake them feel proud of what they can achieve.2.I ' ve made new friends and admoing well at college. I think I enjoyin'g bme ing a college student.3.People with disabilities want to be treated like everyone else and given equalopportunities. They do not want sympathy .4.Life is full of challenges. We should be strong enough to face up to them.5.A great pianist does not succeed overnight. His skills are developed over time .6.It is reported that millions of people in the US are not covered by health insurance.7.The party really came to life once again when the huge birthday cake was served.8.The train must be running late; we should have got to Beijing by now.9.How determined one is to achieve one' sd ream is clearly a sign that can be used topredictsuccess.10.Setting a goal and goingall the wayto achieve it can be a great test of one' sw ill andperseverance.11.The doctor tried to prevent the infection spreading to other parts of the body. was toldthat my computer wasn ' t powerful enough to rsuonft wth a rte .13. Corporate executives usually have high salaries.art exhibition is great; it 'sp aity you don 'hta ve time to go there but you can see it on your computer screen.15. The researchers are concerned about the increasing frequency of the illness in thevillage.1)big on2)all the way3)motivation4)predicting5)hooked6)pursuit of7)elementary8)folk9)taken over1.We waited for Phil for two hours, but he didn 't show u. pWe had to cancel the appointment.2.Nowadays the price of hiring a tutor is very high. So many parents choose to tutor their kids/children themselves .3.Be positive about your life and see amazing things you have achieved. In other words,believe in yourself !4.When we' rey oung, we take risks and may fail. However, we should keepchasing our dreamsandnever give up.5.I ' ll find a job and become a skilled worker after graduating from co llege. Ihave nomotivation for going to graduate school.2.Word Formation1.When you email me, don ' t forget to attach a copy of the document.2.Sea level rise can increase the height of storm waves, making more areas vulnerable to stormdamage.3.The letter must have sat in the drawer for such a long time that it has yellowed .4.Bob lives not far from the school he attends. So he bicycles to school.5.Greenmeans they 're doing wreelld; means they might fail.3.Sentence Patterns1.I know you ' ve set youar l.gWo hy not make a plan2.When one door closes, another opens for you. How about looking for other opportunities3.It is not enough to learn from textbooks. Why not take a part-time job to gain some practical experiences4.The school doesn 'ht ave a student society that provides community services.How about starting one with your classmates5.If we agree that college life is a new experience for growing up, why not take a more active part invarious activities on campusprehensive Practice1.A: Our government encourages college students to be creative and start career planning early. What does this mean for your dream of a future jobB: As a college student, I am big on learning and applying skills our future job needs instead of book knowledge only. I would like to take onchallengesduring college. And I have strongmotivation to go abroad to learn more someday.2.A: My problem is that I have dreams but they always seem so far away and hard to achieve.What ' s your adviceB: First, you need to look inside yourself and know what you really want to do. In other words, you need to build up your confidence and believe in yourself/your dream. Second, create a concrete plan and take action in pursuit of your dream . By so doing, you will, I ' m sure, make your dream come true over time .3.A: Do you have a dream job in mind already If so, what is it Would you mind sharing it with us B: My dream job is a corporate position such as a manager leading a team to help the company reach its goals. What I like most about the job is to overcome challenges and make decisions with creativity . I ' veh go o tked on reading books on team leadership now!4.A: In chasing my dream, obstacles come my way from time to time. I sometimes think of giving up. As a successful CEO, can you share your experience with me about how to deal with them B: Yes, I ' d be more than happy to do so. To deal with things holding me back, I them first,and then make a list, instead of saying to myself “Why not just give up”F. or someobstacles, I will not let excuses take over. For example, it actually doesn 't help if mya blthe wayto life not treating me well. By finding the right kind of help, I can grow stronger no matter what and do well.Reading & ComprehendingReading 11. Comprehension Check for Reading 12.Translation1.我喜欢读塞涅卡的作品,因为这些书中弘扬的正是我的家庭教育所推崇的精神——不追名逐利,过简单、诚实、体面的生活。
大学英语综合教程1-Unit-3习题答案Key to Exercises (Unit 3)Text comprehension:I. AII.F, T, T, T, FIII.1. Refer to Para 1 for the four examples.2. Refer to Para 4. It could not only set anexample for your children and grandchildren but it adds priceless panache to your image.3. Refer to Para 5. The fact that the guesthad included a recipe for a dish the author had complimented her on at an earlier gathering made the author feel all the more appreciative.4. Refer to Para 7. It is the simple phrase"Excuse me".5. Refer to Para 9. It is because to use goodmanners with our own families counts the most, for those are the people we love the most.6. As good manners are infectious, shewishes that everyone would catch them sothat they would spread..IV. 1. a gracious manner adds great splendor to your image.2. I dare say the note my guest sent me didn't take long to write.3. The simple phrase "excuse me" made most of your irritation disappear.4. Being punctual has always beenconsidered a virtue, both in the past andat present; it has not becomeoutdated.VocabularyI. 1. become different from what it should belike2. displaying gratitude by waving a hand ornodding the head; move out onto the main road3. be of great significance4. who receives the thank-you note remark5. produce a far-reaching effect6. practice good mannersII. Punctuality, routine, infectious, bet,terrific, board, valued, count,cherishes, irritationsIII. D, A, B, B, C, A, D, AIV. 1 praised, compliment, praise, complimented2. appreciated, enjoyed, enjoying, appreciated3. priceless, priceless, precious, precious4. see, Notice, see, noticedV. 1. thanks (recognition)2. activeness (liveliness, briskness,eagerness)3. fashionable ( graceful, elegant)4. selfish (mean, ungenerous)5. nice (courteous, polite, friendly)6. leisurely (relaxed, idle, unoccupied,lazy)7. annoyance (displeasure,dissatisfaction)8.promptness ( timekeeping, reliability) VI. unfriendly, boyhood, understanding, reception,disappearance, decision, differing,elevatedGrammarII. 1. older than2.more interested3. as crowded as4. As pale as5. More exciting than6. As complicated7.easier than8.nicer9. more selective10.nicer11.as unlucky as12. more difficultIII.1. stronger2. more noisy3. more expensive4. more difficult5. happier6. younger7. more often8. further9. more exciting10. louderIV.1. more comfortable2. the funniest3. the worst4. more serious5. the most popular6. quieter7. the most beautiful8. healthier9. the least honorable10. less challenging; least challenging V. 1. Older 2. Oldest 3. True 4. True 5. Further 6. A more 7. Better 8.trueVI. e.g. But even worse was the fact that the headmaster had found out the boys' secret plan.Translation exercisesI.1. 譬如,我在纽约就看到这样的差别,与我20多年前刚搬来时大不相同了:人们蜂拥走进电梯,却没有让电梯里的人先出来;别人为他们开门时,从来不说“谢谢”;需要同事给他们递东西时,从来不说“请”;当其他开车人为他们让道时,也从不挥手或点头表示谢意。
Key to Exercises of College English Book 3Unit 1★Text AVocabularyI.1.1) On balance 2) resist 3) haul 4) wicked 5) illustrated 6) budget7)lowering 8) boundary 9) involved 10) economic 11) blasting 12) just about2. 1) cut back/ down 2)pick up 3) get by 4) get through 5) face up to 6)turn in 7)makingup for 8)think up3. 1)…pursued his mathematical studies and taught himself astronomy.2) …often generate misleading thoughts.3) …attach great importance to combining theory with practice in our work.4)…be suspected of doing everything for money.5)…before he gets through life.4. 1)their indoor; a profit; to invest in2) device; the improvement; on a global scale3)stacked; temptation; never dined outII.1. 1)house 2)Home 3)home; family 4) household2. 1) doubt 2) suspected 3)doubted 4) suspected 5)suspectIII.1. rise2.final3. regular4. cash5. hows; whys6. upped7. yellowed8. bottled 9. lower 10. searchComprehensive ExerciseI. Cloze1. 1)gets by 2)temptation 3)get through 4) improvement 5)aside from6) suspect 7) supplement 8) profit 9)stacking2. 1) replaced 2) consider 3) quit 4) world 5) tough6) fuels 7) provide 8)luxuries 9)balance 10)idealII. Translation1.1) We have a problem with the computer system, but I think it’s pretty minor.2) My father died when I was too young to live on my own. The people of my hometown tookover ( responsibility for ) my upbringing at that point.3) The toys have to meet strict/tough safety requirements before they can be sold to children.4) Radio and television have supplemented rather than replaced the newspaper as carriers ofnews and opinion.5) When it comes to this magazine, it is/ carries a digest of articles from many newspapersand magazines around the world.2. A decade ago, Nancy did what so many Americans dream about. She quit an executiveposition and opened/ set up a household device store in her neighborhood. People like Nancy made the decision primarily for the improvement in the quality of their lives.But, to run a business on a small scale is by no means an easy job. Without her steady income, Nancy had to cut back on her daily expenses. Sometimes she did not even have the money to pay the premiums for the various kinds of insurance she needed.Fortunately, through her own hard work, she has now got through the most difficult time. She is determined to continue pursuing her vision of a better life.Unit 2★Text AVocabularyI. 1. 1)decades 2)historic 3)imposed 4)religious 5)slender 6)web 7)bade 8)site 9) on the side 10)authorized 11) terminal 12) make the best of2. 1) went through 2)stood up for 3) laid down 4) take on 5) let ( us ) down6) draw on 7) fall into 8) pass for3. 1) … are fully confident that the Americans will not be able to justify their measures to protect the struggling American steel industry.2) … in the eyes of Joe Klein, staff writer of the New Yorker and author of The Natural, the most talented politician of his generation and the most compelling.3) …people are really intent on destroying themselves with drugs.4)…could forge a completely different approach to life.5) It is our conviction that cloning of human beings is bound to cause many ethical and social problems in the long run.4. 1) As for; do not compel; capture of; have forged 2) At huge risk; the mission; shelter 3)who abolished; In the eyes of; racialII.1.I’ll tell you in a minute how I have attained the genuine sense of belonging inAmerica, but first let me hear about your French trip.2.Most McDonald’s look almost the same on the outside, but actually there areabout 16 different basic designs.3.Loaning money from the banks is but one of the methods we can use to getthrough a financial crisis.4.This second-hand car has been nothing but trouble; it is always breaking down.5.In your resume you’ve mentioned everything but one vital point.6.Our technicians have discovered a simple but effective solution to the problem.7.I am sorry, but I think you shouldn’t have lingered on over coffee and missed thelast bus.8.The bankruptcy of the company was not caused by evil, but by simple ignorance. III.1.lonely2. friendly3. weekly; monthly4. lovely5. cowardly6. kindly/saintly7. lively8. motherlyComprehensive ExerciseI.1. 1)forged 2) stand up 3) compelled 4) convictions 5) mission6) abolish 7) intent on 8) risk 9) In the eye of 10)threats2. 1) assistance 2) involved 3) estimated 4) coincidence 5) emerged 6) referred7)numerous 8) stationed 9)concern 10) captureII. Translation1.1) Though greatly affected by the consequences of the global financial crisis, we are stillconfident that we can face up to the challenge and overcome the crisis.2) Under threat of constant sand storms, we were compelled to leave our cherished villageand move to the new settlement.3)According to a recent online survey, a lot of consumers say they may be motivated toconsider buying products shown in TV commercials.4) Having spotted a truck driver dumping contaminated waste alongside the river, the oldman reported to the police at once.5) Some scientists hold to the firm conviction that people will come to like geneticallymodified crops someday since they can increase yields and help combat hunger and disease in the developing world.2. Shortly after he achieved freedom Henson became intent on assisting fugitive slaves.He secretly returned to the US from Canada several times to help others to travel the Underground Railroad to freedom. Once some slave catchers closed in on the escaping slaves and Henson when they were on the run. He disguised them and successfully avoided capture. Later he built a small settlement in Dresden, Canada for escaped slaves, setting up a chapel and a school. He held to the conviction that slavery would be abolished, and the day was bound to come when racial discrimination no longer existed.Unit 3★Text AVocabularyI.1.1) threatens 2)by a small margin 3) civilize 4)closed up 5) wandered 6) paste7) without so much as 8)sideways 9) hook up to 10) universal 11)chart 12)Bathed in2. 1) narrowed down2) looked back on3)cut off4)fit into5)wear ( the other ) down6) lies in7) put up8) stand for3. 1) … which is likely to make people vulnerable to asthma has been found by researchers at theDepartment of Clinical Medicine in Oxford.2)…with mirrored doors had to be built in so as to make their small bedroom look larger.3) …feature the space shuttle Challenger blowing up in January 1986---killing all seven crew.4) … threatened to keep the pupils in after school they were quieted at once.5) … are a major barrier to the country’s economic growth due to the fact that imported oil hasabsorbed 40% of its foreign exchange / because imported oil has absorbed 40% of its foreign exchange.4. 1)looked back on ; atmosphere ; urban life 2) era ; hooked up to the ; the electronic 3)thesuburb ; a sophisticated ; system ; analyze ; make errorsII.1.away2. inside/ in3.forward / through4. back5. off6. home7.back down8.in; outIII.1.Internet is not such an unusual word as it used to be2. Most men do not look unattractivein them 3. Wealthy as she is, she is not unconcerned by her sudden unemployment 4.This claim is not unrealistic in view of a sharp decrease in the city’s violent crimes 5. His poor health is not unrelated to his unhealthy way of life.Comprehensive ExerciseI. 1. 1)Statistics 2)rural 3)era 4) stood for 5)on the latch 6) vulnerable7) barriers 8)electronic 9) reflection 10) civilized2. 1) tougher 2) liable 3) shift 4) electric 5) cautious 6) sophisticated7) thieves 8) break 9)chances 10)signsII. Translation1. 1) The Internet is changing the way people live, no matter whether they are in urban or rural areas.2) Medium-sized and small companies are more vulnerable to the threat of the globaleconomic crisis than large ones.3) With regard to our term papers, the professor asked us to analyze the chart of unemployment first, and then provide critical reflections on the nation’s economic development.4) It never occurred to him that their team would win the basketball match by a large margin.5) Looking back on my twenty years’ teaching in high school, I attributed my success to patience, talent, and the constant pursuit of knowledge2. It is almost impossible to keep a determined burglar out. All you can do is discourage himfor a few minutes, thus exposing him to police patrols. Common sense tells us that lighting isa barrier to criminal activity. A light should be fixed in the doorway and switched on at night.Make sure / Assure yourself that you don’t leave the door on the latch if you happen to be the last to come in. if you decide to buy a sophisticated electronic alarm system, be sure to ask for its signs and put them up on both windows and doors. In addition you may have it hooked up to a police station.Unit 4★Text AVocabularyI.1. 1)accordingly 2)loose 3) concentration 4) stimulating 5) fabric 6) if anything7)reality 8)intuition 9) trifle 10)at the turn of the century 11) mess 12) undermine2. 1) approve of 2)slow down 3) taken in 4) sucked into 5) set…apart 6) dozed off7) call forth 8)stretch into 9) keep up with 10) believe in3. 1) provided inspiration for many artists and musicians over the decades.2) is credited to his powers of imagination3) on the foundations of an agricultural revolution4) not to make any complaints in the presence of the nurse.5) the outbreak of the Second World War.4. 1) flaw; came to the conclusion; would get nowhere2) in a row; dozed off; a mess of3) outbreak of; has undermined; has strainedII. Collocation1. With Christmas only a week away2. With his physical condition improving day by day3. With our GDP growing steadily4. With all the shops closed5. With her eyes closed6. With the fog lifting during the nightIII. Usage1. like/as2. as3. like4. like/as5.as/like6. as7. kike8.asComprehensive ExerciseI. Cloze1. 1)caution 2) came to the conclusion 3)never get anywhere 4) undermining 5) notgive/care a fig 6) flaw 7) beyond any doubt 8) foundation 9)remarkable/ impressive10)imagination2. 1) extent 2) inventions 3) bet 4) manages 5) vision 6) eventually 7) achievement 8)poverty 9) utilized 10) breakthroughII. Translation1. 1)The volunteers sent/assigned by the Red Cross disinfected, with great caution, the drinking water in the village so as to avoid an outbreak of plague.2) Einstein spent many years trying to unify the theories of electromagnetism and gravity but failed.3) Professor Wang won/ received the Presidential Award for his excellence in stimulating students’ creative imagination.4) As there were some major design flaws, the board of directors didn’t approve of the economic stimulus package.5) Having realized that nobody could help him, Jordan finally came to the conclusion that he had to face reality and take up/ meet the challenge by himself.2. What was remarkable about year 2005 was perhaps that the United Nations declared it“The World Year of Physics”. It was the 100th anniversary of Einstein’s theory of relativity and the 50th anniversary of his death. In 1905 Einstein published five highly important essays in the history of science, thus revolutionizing physics. His great achievements can be credited to his impressive powers of imagination, constant questioning, and not giving a fig for authority. It is beyond doubt that Einstein was the greatest scientist in the 20th century.。
Key to ExercisesUnit 1Text AII. VocabularyA.1. bear2. haunt3. bespeak4. approach5. trivial6. self-assertionB.1. A2. B3. B4. A5. C6. D7. B8. C9. D 10. CC.1. is afflicted with2. bearing3. press4. elusive5. abandon themselves6. trivial7. descend8. at lengthIII. Grammar & StructureA.1.don’t leave; will be; get2.was drowning; dived; rescued3.exploded; climbed4.reached; realized; didn’t know5.will be; opens6.will start; return7.makes; has found8.was raining; played/were playing; was trying; didn’t get on/wasn’t getting on; keptB.1. A2. B3. D4. A5. C6. A7. D8. B9. D 10. AIV. Translation1.Research revealed that the bird was on the brink of extincti on. It’s every citizen’sobligation to protect them.2.I felt approaching footsteps. Someone took my hand and I was caught up and heldclose in the arms of him.3.She had abandoned herself to grief since she heard the news that her husband waskilled in the car accident. Her sister strived to comfort her but in vain.4.According to laws, no one has the right to impose a private will upon others. As longas you follow the laws, you can do whatever you want.5.He opened the door to his parents’ importunities and desc ended the stairs slowly.Holding up his head high, he carried himself like an arrogant knight.Text BA.1. B.2. C.3. A.4. D.5. B.6. A.B.1. 天气晴朗时,总有一位画家带着他的画架呆在那儿。
1 Unit 1 Mathematics Reading 1 Section C Post-reading Task
Reading Comprehension 1. Directions: Work on your own and fill in the blanks with the main idea. Part 1 (Para. 1): Brief introduction to Russell‘s paradox Part 2 (Paras. 2-5): The effect of Russell‘s paradox on Gottlob Frege‘s system. Para. 2: Russell‘s paradox dealt a heavy blow to Frege‘s attempts to develop a foundation for all of mathematics using symbolic logic.
Para. 3: An illustration of Russell‘s paradox in terms of sets Para. 4: Contradiction found in the set. Para. 5: Frege noticed the devastating effect of Russell‘s paradox on his system and inability to solve it. Part 3 (Paras. 6-8): Solutions offered by mathematicians to Russel‘s paradox Para. 6: Russell‘s own response to the paradox with his "theory of types." Para. 7: Zermelo's solution to Russell's paradox Para. 8: What became of the effort to develop a logical foundation for all of mathematics? Part 4 (Para. 9): Correspondence between Russell and Frege on the paradox 3. Directions: Read the following passage carefully and fill in the blanks with the words you‘ve learned in the text. Russell's own response to the paradox came with the development of his theory of types in 1903. It was clear to Russell that some restrictions needed to be placed upon the original comprehension (or abstraction) axiom of naive set theory, the axiom that formalizes the intuition that any coherent condition may be used to determine a set (or class). Russell's basic idea was that reference to sets such as the set of all sets that are not members of themselves could be avoided by arranging all sentences into a hierarchy, beginning with sentences about individuals at the lowest level, sentences about sets of individuals at the next lowest level, sentences about sets of sets of individuals at the next lowest level, and so on. Using a vicious circle principle similar to that adopted by the mathematician Henri Poincaré, and his own so-called "no class" theory of classes, Russell was able to explain why the unrestricted comprehension axiom fails: propositional functions, such as the function "x is a set," may not be applied to themselves since self-application would involve a vicious circle. On Russell's view, all objects for which a given condition (or predicate) holds must be at the same level or of the same "type."
Vocabulary and Structure 1. Word-building 2
Directions: Give the correct form of the word according to the indication in the brackets. Then complete the sentences using the right form for each word. Use each word once.
discover— (suffix) symbol—(suffix) logic— (suffix) form—(suffix) correspond—(suffix) develop—(suffix) describe—(suffix) able—(prefix) contradict—(suffix) equal—(suffix) 1) The math may not have been new, but Duchin enjoyed the process of_________, and she got to work collaboratively with half a dozen other math whizzes.( discovery)
2) Packages can be sealed and can contain personal _________if it relates to the contents of the package.( correspondence)
3) New research indicates that the brain region may prefer_________ notation to other numeric representations .( symbolic)
4) To do this, an ideal model based on the _________ paradigm was constructed and then compared with a neutral model reflecting the further education system as it existed before the Act took effect.( equality)
5) Is this not in flagrant _________to Einstein's rule that signals do not travel faster than the velocity of light?( contradiction)
6) Sequential organization has the major advantage that the records are stored in a _________ order, presumably that sequence to which the records are normally required for printing and for soft copy reports.( logical)
7) The mathematical _________ of a zero-sum two-person game is not difficult to construct, and determining the optimal strategies and the value of the game is computationally straightforward.( description)
8) The proof we now know required the _________ of an entire field of mathematics that was unknown in Fermat's time.( development)
9) Williams adds that many courses in geometry, ―the one high school class that demands _________ reasoning,‖ have already been ―gutted‖ and are no longer proof-based.( formal)
10) The concept of total aircraft ownership will become increasingly important should the traditional trade structure be _________to cover the expanse of technologies economically.( unable)