CCNA2_7_english
- 格式:doc
- 大小:145.50 KB
- 文档页数:11

培训大讲堂官方YY 频道:3660mCCNA题库考试代号:640-802考试时间:英文110+30=140分钟通过分数:825题库版本:V104。
4鸿鹄论坛招募CCNA、CCNP答疑讲师答疑地点:鸿鹄官方YY频道3660鸿鹄大讲堂:http://bbs。
hh010。
com/thread—46172—1-1.htmlCCNA题库战报交流QQ群:144288127 (500人超级群)CCNA题库战报交流区:/forum—261-1.html1000 G视频教程免费下载:http://bbs.hh010。
com/forum-228—1。
htmlCCNA(640—802)题库V104.4CCNA(640—802)题库V104。
4(情人节版)CCNA 题库战报500人超级QQ群144288127V104系列是官方的终结版本,以后不会再出V105 V106 V108等等CCNA 最新题库/最新战报发布区:http://bbs.hh010。
com/forum—261-1。
html下载官方正版题库、看最新考试战报,请随时关注鸿鹄论坛http:// CCNA考试报名1900,详情请联系鸿鹄全国区十七名客服QQ 712023090-712023106========================================更新内容:V104。
1修正V104中错误题目,确定经典争议题目答案;V104。
2增加拖图题并可完美模拟考试,VCE题库增加中文注释;V104.3针对思科CCNA考试变题,更新考试新增题目93Q,更新V104。
2实验题;V104。
4增加全文中文注释,汇总V104.3九次更新,删除部分旧题目,为目前最新官方正版题库;2011。
8。
1 增加每日新题,修订部分错误。
2012。
2。
14 情人节版增加5道新题,分别是519、520、521、522、523题修改176题、375题、443题、482题答案错误修改59题、88题、453题、107题、270题注释错误增加个别疑难拖图题注释,优化实验题=============================================QUESTION 1When you are logged into a switch, which prompt indicates that you are in privileged mode? (当您登录到交换机,哪种提示表明你在特权模式?)A。

CCNA专业英文词汇全集CCNA为思科最基础的入门认证,其中,考试偏重网络概念和理论,对于初学者来说,不少专业英文术语难以理解,导致学员学习进度维难。
CISCO系列认证的原版教材,专业词汇出现频率积高,考生只要熟悉本文,相信学习起来一定事半功倍^-^10BaseT-----原始IEEE802.3标准的一部分,1OBaseT是1OMb/s基带以太网规范,它使用两对双绞电缆(3类、4类或5类),一对用于发送数据另一对用于接收数据。
1OBaseT每段的距离限制约为100米。
参见Ethernet和IEEE 802.3。
1OOBaseT-----基于IEEE 802.3U标准,1OOBaseT是使用UTP接线的基带快速以太网规范。
当没有通信量出现时。
1OOBaseT在网络上发送链接脉冲(比1OBaseT中使用的包含更多信息)。
参见10BaseT、Fast Ethernet和IEEE 802.3。
100BaseTX-----基于IEEE 802.3U标准,100BaseTX是使用两对UTP或STP 接线的10OMb/S基带快速以太网规范。
第一对线接收数据;第二对线发送数据。
为确保正确的信号定时,一个100BaseTX网段不能超过100米长。
A&B bit signaling (A和B比特信令)-----用于T-1传输设备,有时称为"第24信道信令"。
在这一方案中,每个T-1于信道使用每个第六帧的一个比特来发送监控信令信息。
AAA-----身份验证(Authentication)、授权(Authorization)和统计(Accounting)Cisco开发的一个提供网络安全的系统。
奏见authentication。
authorization和accountingAAL ATM适应层-----数据链路层的一个与服务有关的子层,数据链路层从其他应用程序接受数据并将其带人ATM层的48字节有效负载段中。

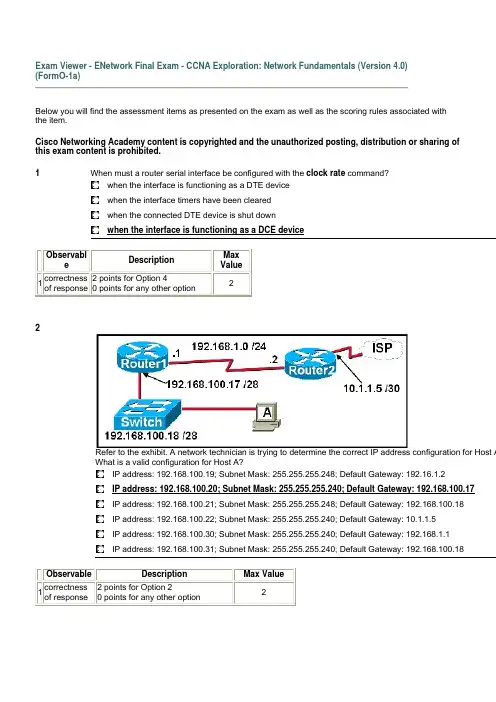
Exam Viewer - ENetwork Final Exam - CCNA Exploration: Network Fundamentals (Version 4.0)(FormO-1a)Below you will find the assessment items as presented on the exam as well as the scoring rules associated with the item.Cisco Networking Academy content is copyrighted and the unauthorized posting, distribution or sharing of this exam content is prohibited.1When must a router serial interface be configured with the clock rate command?when the interface is functioning as a DTE devicewhen the interface timers have been clearedwhen the connected DTE device is shut downwhen the interface is functioning as a DCE deviceObservable DescriptionMaxValue1correctnessof response2 points for Option 40 points for any other option22Refer to the exhibit. A network technician is trying to determine the correct IP address configuration for Host AWhat is a valid configuration for Host A?IP address: 192.168.100.19; Subnet Mask: 255.255.255.248; Default Gateway: 192.16.1.2IP address: 192.168.100.20; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.17IP address: 192.168.100.21; Subnet Mask: 255.255.255.248; Default Gateway: 192.168.100.18IP address: 192.168.100.22; Subnet Mask: 255.255.255.240; Default Gateway: 10.1.1.5IP address: 192.168.100.30; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.1.1IP address: 192.168.100.31; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.18 Observable Description Max Value1correctnessof response2 points for Option 20 points for any other option23Refer to the exhibit. What function does router RT_A need to provide to allow Internet access for hosts in thisnetwork?address translationDHCP servicesftpdweb serverObservable Description Max Value1correctnessof response2 points for Option 10 points for any other option24Refer to the exhibit. Host A attempts to establish a TCP/IP session with host C. During this attempt, a frame wa captured with the source MAC address 0050.7320.D632 and the destination MAC address 0030.8517.44C4. The packet inside the captured frame has an IP source address 192.168.7.5, and the destination IP address is 192.168.219.24. At which point in the network was this packet captured?leaving host Aleaving ATLleaving Dallasleaving NYCObservable Description MaxValue1correctnessof response2 points for Option 30 points for any other option25Which range of port numbers are reserved for services that are commonly used by applications that run on servers?0 to 2550 to 10231024 to 4915149152 to 65535Observable Description Max Value1correctness ofresponse2 points for Option 20 points for any other2option6Which prompt represents the appropriate mode used for the copy running-config startup-config command ?Switch-6J>Switch-6J#Switch-6J(config)#Switch-6J(config-if)#Switch-6J(config-line)#Observable Description Max Value1correctness ofresponse2 points for Option 20 points for any otheroption27Refer to the exhibit. A technician is working on a network problem that requires verification of the router LANinterface. What address should be pinged from this host to confirm that the router interface is operational?127.0.0.1192.168.64.196192.168.254.1192.168.254.9192.168.254.254Observable Description Max Value1correctnessof response2 points for Option 30 points for any other option28Refer to the exhibit. Host A is unable to reach host B on the remote network. A technician attempted to pingthe local gateway and the ping was successful. To verify the host configuration, the technician issued theipconfig command. What is the likely cause of the problem?The local NIC is incorrectly configured.The subnet mask on host A is incorrectly configured.The IP address on host A is incorrectly configured.The default gateway on host A is incorrectly configured.Observable Description Max Value1correctnessof response2 points for Option 40 points for any other option29An organization has been assigned network ID 10.10.128.0 and subnet mask 255.255.224.0. Which IP address range can be used for this organization?10.10.128.0 to 10.10.160.25510.10.128.0 to 10.10.159.25510.10.128.0 to 10.10.192.25510.10.128.0 to 10.10.0.15910.10.128.0 to 10.10.159.0Observable Description Max Value1correctness ofresponse2 points for Option 20 points for any otheroption210Refer to the exhibit. An employee wants to access the organization intranet from home. Which intermediarydevice should be used to connect the organization intranet to the Internet to enable this access?hubswitchrouterwireless access pointObservable Description Max Value1correctnessof response2 points for Option 30 points for any other option211Which OSI layer manages data segments?application layerpresentation layersession layertransport layerObservable Description Max Value1correctness ofresponse2 points for Option 40 points for any otheroption212Which two types of media can provide bandwidth up to 1 Gb/s? (Choose two.)10 BASE-T100 BASE-T100 BASE-FX1000 BASE-TX1000 BASE-SXObservable DescriptionMaxValue1correctness ofresponseOption 4 and Option 5 are correct.1 point for each correct option.0 points if more options are selected thanrequired.213To enhance security in a network, the network administrator uses these commands:Router(config)# line console 0Router(config-line)# password j1mdi2Router(config-line)# loginWhat two conclusions are evident from these commands? (Choose two.)Users who attempt to connect to the console port of the router must enter a password.The entries permit access through the console by the use of j1mdi2 as the password.The entries eliminate the need for authentication.Access through the console will be denied because the console configuration is incomplete.The entries prevent passwords from being displayed as plain text.Observable DescriptionMaxValue1correctness ofresponseOption 1 and Option 2 are correct.1 point for each correct option.0 points if more options are selected thanrequired.214Refer to the exhibit. RouterB is configured properly. The Ethernet interface Fa0/0 of RouterA is configuredwith the use of the commands that are shown. However, a ping from the Fa0/0 interface of RouterA to theFa0/0 interface of RouterB is unsuccessful. What action should be taken on RouterA to solve this problem?Use the description command on the FastEthernet interface Fa0/0.Configure the clock rate of the FastEthernet interface Fa0/0.Use the no shutdown command on the FastEthernet interface Fa0/0.Reboot the router.Observable Description Max Value1correctness ofresponse2 points for Option 30 points for any other option215Refer to the exhibit. When host A sends a frame addressed for host D, which hosts will receive the frame?only host Donly hosts A and Donly hosts B, C, and Dall hostsObservable Description Max Value1correctnessof response2 points for Option 10 points for any other option216Refer to the exhibit. Communication for hosts X and Y is restricted to the local network. What is the reasonfor this?Host X is assigned a network address.Host Y is assigned a multicast address.Host X and host Y belong to different networks.The gateway addresses are broadcast addresses.Observable Description Max Value1correctness ofresponse2 points for Option 40 points for any other option217 A user enters /web1.htm in the address line of a browser. Which statement is trueabout this transaction?The "http" portion indicates the protocol that is being used.The "web1.htm" portion is the specific service name.The retrieved web page will be displayed in URL code.The "" is the name of the web page file that is called.Observable Description Max Value1correctness ofresponse2 points for Option 10 points for any other option218The tracert 10.1.3.2 command was issued on computer A. Computer A can ping other addresses on the local Computer A sent the first ICMP packet toward computer B with a TTL value of 1. A protocol analyzer that was on computer B showed that the packet never reached its destination. Why did the packet not reach the destinaThere is a TCP/IP problem on computer A.There is a routing loop between R1 and R2.R1 does not have a route for the destination network.The TTL for the packet was decreased to zero by R1.Observable Description MaxValue1correctnessof response2 points for Option 40 points for any other option219 A routing issue has occurred in your internetwork. Which of the following type of devices should beexamined to isolate this error?access pointhosthubrouterswitchObservable Description Max Value1correctness ofresponse2 points for Option 40 points for any otheroption220Which physical component is used to access and perform the initial configuration on a new unconfigured router?Observable DescriptionMax Value1correctness of response 2 points for Option 2 0 points for any other option221What can the user do from the command prompt, Router(config-line)# ?Configure one of the network interfaces.Configure one of the physical or virtual lines.Verify the running configuration on the device.Configure the parameters for one of the routing protocols.ObservableDescriptionMax Value1correctness of response2 points for Option 2 0 points for any other option222Which option shows the PDU that contains the Layer 3 source and destination addressing for a packet?Observable Description Max Value1correctness ofresponse2 points for Option 30 points for any other option223Refer to the exhibit. The ping 127.0.0.1 command is issued on the local host. What do the ping resultsindicate?The local host can send packets on the local network.The TCP/IP stack on the local host operates properly.The local host has full connectivity to the default gateway.The local host has full connectivity to the remote network. Observable Description Max Value1correctnessof response2 points for Option 20 points for any other option224Which topology divides the collision domain and provides full media bandwidth to the hosts in the network?Observable Description Max Value1 correctness of response2 points for Option 30 points for any other option225Refer to the exhibit. Which option correctly identifies the network address, range of host addresses, and thebroadcast address for the network that contains host A?Observable Description Max Value1correctness ofresponse2 points for Option 30 points for any other option226 A technician is setting up a workgroup for six users and wants to allow users to share files without settinup a server. Which application layer protocol will provide for peer-to-peer file sharing in a workgroup?DNSSMBHTTPDHCPObservable Description Max Value1correctness of 2 points for Option 2 2response 0 points for any otheroption27Which router component will have contents erased when the command erase startup-config is issued?flashRAMROMNVRAMObservable Description Max Value1correctness ofresponse2 points for Option 40 points for any otheroption228Refer to the exhibit. Host1 is in the process of setting up a TCP session with Host2. Host1 has sent a SYNmessage to begin session establishment. What happens next?Host1 sends a segment with the ACK flag = 0, SYN flag = 0 to Host2.Host1 sends a segment with the ACK flag = 1, SYN flag = 0 to Host2.Host1 sends a segment with the ACK flag = 1, SYN flag = 1 to Host2.Host2 sends a segment with the ACK flag = 0, SYN flag = 1 to Host1.Host2 sends a segment with the ACK flag = 1, SYN flag = 0 to Host1.Host2 sends a segment with the ACK flag = 1, SYN flag = 1 to Host1.Observable Description Max Value1correctnessof response2 points for Option 60 points for any other option229How many host addresses may be assigned when using the 128.107.0.0 network address with a subnet mask of 255.255.248.0?302562046204840944096Observable Description Max Value1correctness ofresponse2 points for Option 30 points for any otheroption230Refer to the exhibit. Host A is able to access resources on the local LAN but is unable to access anyresources on the Internet. What is the likely cause of this problem?The host subnet mask in incorrect.The network uses private addresses.The host address is a network address.The default gateway is on a different subnet from the host.Observable Description Max Value1correctness ofresponse2 points for Option 40 points for any other option231What is described by the network access layer of the TCP/IP model?rules for packet acknowledgment, error recovery, and sequencingrules for the handoff from the internet layer to the network access protocolsrules for how source and destination hosts exchange data between programsrules for determining which processes can be used to route messages through an internetwork Observable DescriptionMax Value1correctness ofresponse2 points for Option 20 points for any otheroption232Which two factors contribute to the increased throughput when all nodes of a LAN are connected to a switch instead of a hub? (Choose two.)full-duplex operationcollision-free environmentlogical bus media accessbroadcast-free environmentpoint-to-multipoint topologyObservable DescriptionMaxValue1correctness ofresponseOption 1 and Option 2 are correct.1 point for each correct option.0 points if more options are selected thanrequired.233Which application layer protocol allows administrators to log into a server from remote locations and control a server as though logged in locally?DNSFTPDHCPSMTPTelnetObservable DescriptionMax Value1correctness ofresponse2 points for Option 50 points for any otheroption234 A network technician has made a UTP cable that is terminated as T568A on one end and T568B on theopposite end. What type of cable has been constructed?patchconsolecrossoverstraight-throughObservable Description Max Value1correctness ofresponse2 points for Option 30 points for any otheroption235Which application belongs to the category of the client/server model?using Telnet to access a routerexchanging information via instant messagingprinting a document to a locally connected printerscanning a document with a directly connected scanner Observable Description Max Value1correctness ofresponse2 points for Option 10 points for any otheroption236Refer to the exhibit. Which two layers of the OSI model describe the same functions as the transport andinternet layers of the TCP/IP model? (Choose two.)application layerpresentation layersession layertransport layernetwork layerdata link layerphysical layerObservable DescriptionMaxValue 1correctness of responseOption 4 and Option 5 are correct. 1 point for each correct option.0 points if more options are selected than required.237What command can be used to troubleshoot domain name resolution issues?getarp -a tracertnslookupObservable DescriptionMax Value1correctness of response 2 points for Option 4 0 points for any other option238Refer to the exhibit. For connecting two routers with an Ethernet crossover cable, which interface should be used?AB C DObservableDescription Max Value1correctness of response 2 points for Option 30 points for any other option239A technician is asked to secure the privileged EXEC mode of a switch by requiring a password. Whichtype of password would require this login and be considered the most secure?consoleenable enable secret VTYObservableDescriptionMax Value1correctness of response 2 points for Option 3 0 points for any other option240Which three addresses belong to the category of public IP addresses? (Choose three.)127.0.0.1196.1.105.6 132.11.9.99 10.0.0.1 172.16.9.10 46.1.1.97ObservableDescriptionMaxValue1correctness of responseOption 2, Option 3, and Option 6 are correct.1 point for each correct option.0 points if more options are selected than required.341A network administrator is configuring several switches for a network. The switches have similar configurations and only minor differences. The administrator wants to save all commands that are issued on the first switch to a text file for editing. Which transfer option should be selected in HyperTerminal?Observable Description MaxValue1correctnessof response2 points for Option 30 points for any other option242Which option represents a point-to-point logical topology diagram?Observable DescriptionMax Value1correctness ofresponse2 points for Option 40 points for any other option243Refer to the exhibit. What two facts can be determined from the session information that is displayed?(Choose two.)The protocol is a connection-oriented protocol.This exchange is part of the three-way handshake.The SYN flag is representing the initial establishment of a session.The destination port indicates that an FTP session has been initiated.The source port does not support communication with the destination port that is listed.Observable DescriptionMax Value1correctness ofresponseOption 1 and Option 2 are correct.1 point for each correct option.0 points if more options are selected thanrequired.244Which communication tool allows real-time collaboration?wikie-mailwebloginstant messagingObservable Description Max Value1correctness ofresponse2 points for Option 40 points for any otheroption245Which prompt is associated with the privileged exec mode?R1>R1#R1(config)#R1(config-router)#Observable Description Max Value1correctness ofresponse2 points for Option 20 points for any otheroption246What is the effect of the command copy running-config tftp?copies the configuration from a remote machine into RAMcopies the configuration from a remote machine into NVRAMcopies the configuration currently in RAM to a remote machinecopies the configuration currently in NVRAM to a remote machine Observable Description Max Value1correctness ofresponse2 points for Option 30 points for any otheroption247Refer to the exhibit. Which type of network design is shown?client/serverwide areadedicated serverpeer-to-peerObservable Description Max Value1correctnessof response2 points for Option 40 points for any other option248Refer to the exhibit. A network administrator remotely accesses the CLI of RouterB from PC1 using Telnet.Which statement is true about this connection?The data is automatically encrypted.A Telnet server process is running on PC1.The connection is made through a VTY session on the router.A GET request was sent to RouterB to retrieve data during this session.Observable Description Max Value1correctnessof response2 points for Option 30 points for any other option249Refer to the exhibit. A network technician wants to connect host A to the console of a Cisco switch to initializethe configuration. What type of cable is required for this connection?straight-through cablecrossover cablerollover cableserial cableObservable Description Max Value1correctness 2 points for Option 3 2of response 0 points for any other option50 A technician makes several changes to the running configuration on a router, but the desired results arenot achieved. The technician issues the reload command. What action will be taken by the router?All changes will be lost and the router will restart immediately.Changes will be saved automatically and the router will restart.The user will be prompted to save changes before the router restarts.The router will detect changes to the running configuration and will reload using the configurationstored in RAM.Observable Description Max Value1correctness ofresponse2 points for Option 30 points for any otheroption2。


思科认证英文全名及中文职称对照Testpassport ccna 题库我想多多少少应该有部分或者大部分人都是说不全思科认证英文全名的,今天就了解到的和日常收集整理的认证资料写进我的博客的时候顺带发一份给大家,主要是思科的部分认证的中英文全称,供大家温习温习。
思科认证英文全名及中文职称对照【思科认证网络工程师】(英文全名Cisco Certified Network Associate,简称CCNA)表示具备基本的和初步的网络知识。
拥有CCNA认证的人士可以为小型网络(不超过100个节点)安装、配置和操作LAN、WAN和拨号接入服务,其中包括但不仅限于下列协议:IP、IGRP、串行、帧中继、IP RIP、VLAN、RIP、以太网和访问列表。
【思科认证设计工程师】(英文全名Cisco Certified Design Associate,简称CCDA)表示在设计思科网络基础设施方面具备基本的或者初步的知识。
拥有CCDA 认证的人士可以为企业和机构设计包含LAN、WAN和拨号接入服务的路由和交换网络基础设施【思科认证高级网络工程师】(英文全名Cisco Certified Network Professional,简称CC NP)表示网络人士具有对从100个节点到超过500 个节点的融合式局域网和广域网进行安装、配置和排障的能力。
获得CCNP认证资格的网络人士拥有丰富的知识和技能,能够管理构成网络核心的路由器和交换机,以及将语音、无线和安全集成到网络之中的边缘应用。
必备条件:有效的CCNA认证资格。
【思科认证语音专家】(英文全名Cisco Certified Voice Professional,简称CCVP)CCVP 认证表示非常精通融合式IP网络的实施、运行、配置和排障。
认证内容侧重于Cis co Systems CallManager、服务质量(QoS)、网关、关守、IP电话、语音应用和思科路由器及Cisco Catalyst交换机上的应用等主题。


ccna考试题库最新版CCNA(Cisco Certified Network Associate)认证是全球范围内最受欢迎的网络工程师认证之一,具备CCNA认证可以证明一个人在建立、规划、运行、安装和配置中等规模的局域网和广域网方面的专业知识。
为了帮助广大考生顺利通过CCNA考试,不断更新的CCNA考试题库至关重要。
以下是最新版本的CCNA考试题库,希望对考生们有所帮助。
第一部分:网络基础知识1. 什么是OSI七层模型?简要介绍每一层的功能。
2. TCP和UDP之间有哪些区别?请分别举例说明。
3. 什么是IP地址?IP地址的类型有哪些?请列举并简要介绍各自的特点。
4. 什么是子网掩码?为什么在网络中使用子网掩码?5. 简述常见的网络设备有哪些,以及各自的功能与作用。
第二部分:路由和交换技术1. 路由器和交换机之间有何区别?请进行比较并指出各自的优势和劣势。
2. 什么是VLAN?VLAN的作用及在网络中的应用场景是什么?3. OSPF和EIGRP是两种常见的路由协议,请比较它们的特点并举例说明。
4. 请解释静态路由和动态路由的概念以及在网络中的应用。
5. 交换机在网络中扮演什么角色?交换机的MAC地址表是如何工作的?第三部分:网络安全和管理1. 网络安全的重要性是什么?请列举几种常见的网络安全威胁并介绍应对策略。
2. 什么是ACL(访问控制列表)?ACL的作用是什么?请给出一个ACL的配置示例。
3. VPN是什么?VPN的工作原理及在企业网络中的应用。
4. SNMP是网络管理中常用的协议,它的作用是什么?请解释SNMP中的几个重要概念。
5. 如何保护无线网络的安全?请列举几种方法。
第四部分:WAN技术1. 什么是WAN?WAN的主要特点是什么?2. PPP协议和HDLC协议分别是什么?请比较它们的异同。
3. 什么是Frame Relay?Frame Relay的工作原理及在WAN中的应用。
4. 请解释T1和E1的概念,以及它们在传输速率和应用方面的差异。

chapter 1L1:物理层PDU:bits 比特流作用:传输比特流(01000100101010...)介质:同轴电缆: coaxial cable 传输距离 500米双绞线(TP):twisted-pair cable 传输距离 100米非屏蔽双绞线(UTP):室内屏蔽双绞线(STP):室外(环境干扰强)直通线:AA BB 链接异性端口:pc-hub pc-sw sw-router交叉线:AB 链接同性端口:pc-pc router-router pc-router sw-sw反线:1-8 8-1 用于本地连接的console 控制线网线的两种制作方式:568A:白绿绿白橙篮白蓝橙白棕棕568B:白橙橙白绿篮白蓝绿白棕棕 1236 网线使用DCE:数据终端设备,需要配置clock rate DTE:数据终结设备对应传输介质的支持传输距离:1)1000base-cx 使用的是铜缆。
最大传输距离25米2)100Base-Tx/Fx100Base-Tx以5类非屏蔽双绞线为传输介质(最大传输距离是100米)100Base-Fx以光纤为传输介质(2000米)。
3)1000base-SX(MMF多模):最长传输距离是550米4)1000base-LX:可以使用单模光纤也可以使用多模光纤使用多模光纤的最大传输距离为550m,使用单模光纤的最大传输距离为3千米5)1000base-zx(单模):最长传输距离是70KM以太网 Ethernent传输模式:单工:只能发或者收半双工:即可以收也可以发,但是同一时间只能收或者发列如对讲机全双工:同一时间既可以收也可以发列如手机Auto:中继器(Repeater):对信号放大,双绞线的传输距离只有100M,使用中继器可以延长传输距离。
hub :多口中继,一个数据帧从一个入口进,会发送到HUB的所有其他端口而不进行过滤。
L2:数据链路层PDU:frame 帧作用:成帧,差错控制设备:网桥(bridge):基于MAC地址转发,根据mac-port表,数据包只发到和MAC地址相对应的port端口交换机(switch):多口网桥,独享带宽L2层编制:MAC地址MAC地址构成:48bit,12位十六进制数可以通过ipconfig/all 查询电脑的mac地址L2表:MAC-port表(mac地址表)冲突域:不可避免的数据冲突范围,由中继、hub链接构成并扩大,见到L2层端口截止,每一个交换机端口形成一个冲突域HUB:所有端口都在一个冲突域,是增加了冲突域的范围交换机:没一个端口都是一个冲突域,是增加了冲突域的数量,减少了冲突域的范围HUB:是共享带宽 10M 所有端口共享10M交换机:独享带宽 10M 每个端口同时有10ML3:网络层 PDU:packet 包作用:逻辑编制:ip地址、路由(路径的选择)IP地址与mac地址的区别?Mac地址通信:同一个网络,mac通信跨网络通信:ip地址IP地址:版本v4;32bit;点分是进制法 192.168.0.1IP=网络位+主机位掩码:mask:连续的1+连续的0,来确定IP地址的网络位+主机位,1位对应网络位,0位对应主机位。

CCNA学习指南中文第七版第一章(1)集线器:1个冲突域。
1个广播域。
(2)网桥:2个冲突域。
1个广播域。
(3)交换机:4个冲突域。
1个广播域。
(4)路由器:3个冲突域。
个广播域。
(1) D.作为接收方的主机可使用流量控制(默认情况下,TCP 使用窗口技术)控制发送方。
通过缩小窗口,作为接收方的主机可降低发送方的传输速度,从而避免缓冲区溢出。
(2)D.发送给MAC地址ff:ff:ff:ff:ff:ff的数据是给所有工作站的广播。
(3) C 、D.你并非真的想增大冲突域,但集线器(多端口转发器)可提供这种功能。
(4) D.传输层从上层接收大型数据,将其分割成较小的片段,这些片段称为数据段。
(5) A 、C 、E 、G.路由器提供分组交换、分组过滤、互联网络通信以及路径选择功能。
虽然路由器确实分割或终止冲突域,但这不是路由器的主要功能,因此选项B不正确。
(6) B.路由器运行在第3层,LAN交换机运行在第2 层,以太网集线器运行在第1层。
字处理程序与应用层接口通信,但并非运行在第7层,因此答案为"无"。
(7) C.封装顺序为数据、数据段、分组、帧、比特。
(8) A 、D.分层模型的主要优点是,让应用程序开发人员能够只在分层模型的某一层修改程序的部分功能。
使用OSI 分层模型的优点包括但不限于:将网络通信过程划分成更小、更简单的组件,这有助于组件的开发、设计和故障排除;通过标准化网络组件,让多家厂商能够协作开发。
定义了模型每层执行的功能,从而鼓励了行业标准化。
让不同类型的网络硬件和软件能够彼此通信。
避免对一层的修改影响其他层。
从而避免妨碍开发工作。
(9)A 、D.不同于全双工,半双工以太网运行在一个共享的冲突域中,其有效吞吐量低于全双工模式。
(10)B.在网络中为建立连接添加交换机可缓解LAN拥案,而不会导致LAN拥塞。
(11)C.如果1 台交换机连接了3台计算机,且没有配置VLAN,它将创建1个广播域和3个冲突域。

CCNA思科考试答案(全)第 1 章考试1一家拥有10 名员工的小型公司使用单个LAN 在计算机之间共享信息。
哪种类型连接适合此公司?由当地电话服务提供商提供的拨号连接能够使公司方便且安全地连接员工的虚拟专用网络通过当地服务提供商建立的私有专用线路通过当地服务提供商提供的宽带服务(如DSL)答案:4解析:对于这种小型办公室,比较适合通过被称为数字用户线路(DSL) 的常见宽带服务实现Internet 连接,这种服务由当地的电话服务提供商提供。
由于员工人数很少,带宽的问题并不突出。
如果公司较大,在远程站点有分支机构,则专用线路会更加适合。
如果公司员工需要通过Internet 与公司联系,则采用虚拟专用网。
2哪种网络情况需要使用WAN?员工工作站需要获取动态分配的IP 地址。
员工在出差时需要通过VPN 连接到公司电子邮件服务器。
分支机构的员工需要与同一园区网络上的另一座建筑物内的公司总部共享文件。
员工需要访问托管在其建筑物内DMZ 中的公司Web 服务器上的网页。
答案:2解析:当出差的员工需要通过WAN 连接到公司电子邮件服务器时,VPN 将通过WAN 连接在员工笔记本电脑与公司网络之间创建一个安全隧道。
通过DHCP 获取动态IP 地址是LAN 通信的功能。
在企业园区的不同建筑物之间共享文件可通过LAN 基础设施来实现。
DMZ 是企业LAN 基础设施内一个受保护的网络。
3以下哪项描述了WAN 的特征?WAN 和LAN 在同一地理范围内运行,但有串行链路。
WAN 网络归运营商所有。
所有串行链路均被视为WAN 连接。
WAN 可提供到园区主干网的终端用户网络连接。
答案:2解析:WAN 可用于将企业LAN 互连到远程分支机构站点LAN 和远程工作人员站点。
WAN 归运营商所有。
虽然WAN 连接一般通过串行接口实现,但并不是所有串行链路均连接至WAN。
LAN(而非WAN)可在组织中提供终端用户网络连接。
4电路交换WAN 技术的两个常见类型是什么?(请选择两项。
CCNA详解:CCNA认证(CCNA-思科网络安装和支持认证助理)是整个Cisco认证体系中最初级的认证,同时它也是获得CCNP认证、CCDP认证和CCSP认证的必要条件(CCIP认证、CCIE认证不强制要求),而且许多Cisco 专业认证(Cisco Qualified Specialist)也要求考生首先得具备的CCNA认证。
CCNA认证属于Cisco售后工程师认证体系的入门认证,通过CCNA可以证明你已掌握网络的基本知识,并能初步安装、配置和操作Cisco路由器、交换机及简单的LAN和WAN。
CCNA认证表示经过认证的人员具有为小型办公室/家庭办公室(SOHO)市场联网的基本技术和相关知识。
通过CCNA认证的专业人员可以在小型网络 (100或100以下个节点)中安装、配置和运行LAN、WAN和拔号访问业务。
他们可以使用的协议包括(但不限于):IP, IGRP, IPX, Serial, AppleTalk, Frame Relay, IP RIP, VLAN, RIP, Ethernet, Access Lists.获得CCNA认证的先决条件不需要考生持有任何证书即可报考CCNA,同时对考生的年龄、学历、外语水平均没有硬性规定;CCNA认证的考试现在参加考试有2条途径:一、参加640-801 CCNA这一门考试;二、参加640-821 INTRO和640-811 ICND 这两门考试;CCNA认证的有效期CCNA证书的有效期为3年,3年之后需要参加再认证(Recertification)的考试,如果你在这2年时间内考取了更高级别的Cisco认证,则CCNA认证的有效期自动更新。
CCNA的再认证考试有效期满之后必须参加640-811 ICND的考试,或者参加任何一科CCNP、CCDP、CCIP、CCSP的考试,再或者参加Cisco专业认证(Cisco Qualified Specialist)中任何一科前缀为642-XXX的考试。
药剂学词汇英文缩写(English abbreviation)AAA 丙烯酸ABZ 阿苯达唑钠ACA 氰基丙烯酸烷基酯ACY 无环鸟苷ADEPT 抗体介导的酶-前药治疗系统ADR 阿霉素AIBN 偶氮二异丁腈AMA n-烷基甲基烯酸酯类ANN 人工智能网络ASGP-R 无唾液酸糖蛋白受体AUQ 药量-时间曲线下面积BBBB 血脑屏障BDNF 脑衍生神经营养因子BHA 叔丁基对羟基茴香醚BHT 二丁基羟基甲苯BNA 二甲基丙烯酸丁酯B.P 英国药典BPS 脑磷脂酰丝氨酸BSA 白蛋白BSM 脑神经磷脂CCA 醋酸纤维素CAP 醋酸纤维素酞酸酯CCNa 交联羧甲基纤维素钠CD 环糊精CD 圆二色谱CF 羧基荧光索CFCs 氟氯烷烃类化合物Ch 胆固醇CHP 出芽短梗孢糖CM-β-CD 羧基甲基-β-环糊精CMC 临界胶束浓度CMC-Na 羧甲基纤维素钠CME-β-CD 羧基甲基-乙基-β-环糊精CMS-Na 羧甲基淀粉钠CNS 中枢神经系统ConA 伴刀豆球蛋白ACPE 细胞致病效应CRH 临界相对湿度CSBDDS 结肠靶向生物粘附释药系统CSF 集落刺激因子DDAD 植入泵DBP 苯二甲酸二丁酯DBS 癸二酸二丁酯DCP 双鲸蜡磷脂酸DDS 药物输送系统DE-β-CD 二乙基-β-环糊精DEP 苯二甲酸二乙酯DLPC 二月桂酰磷脂酰胆碱DLPG 二月桂酰磷脂酰甘油DLS 激光散射DMA N,N-二甲基胺乙酯共聚物DM-β-CD 二甲基-β-环糊精DMF N,N-二甲基甲酰胺DMPA 二肉豆蔻酰磷脂酸DMPC 二肉豆蔻酰磷脂酰胆碱DMPE 二肉豆蔻酰磷脂酰乙醇胺DMPG 二肉豆蔻酰磷脂酰甘油DMPS 二肉豆蔻酰磷脂酰丝氨酸DMSO 二甲基亚砜DOPC 二油酰磷脂酰胆碱DOPE 双油酸磷酯乙醇胺DOPG 二油酰磷脂酰甘油DOSPA 2,3-二油酰氧-N-[2(精胺酸基酰胺)乙基]-N, N-二甲基-1-丙基-三氟乙酸胺DOTAP 1,2—二油酰氧丙基-N,N,N-三甲基溴化铵DOTMA N—[1-(2,3—二油酰基)丙基-]-N,N,N—三乙胺氯DPI 干粉吸入装置DPPA 二棕榈酰磷脂酸DPPE 二棕榈酰磷脂酰乙醇胺DPPC 二棕榈酰磷脂酰胆碱DPPG 二棕榈酰磷脂酰甘油DPPS 二棕榈酰磷脂酰丝氨酸DPSM 二棕榈酰鞘磷脂DSC 差示扫描量热分析DSPC 二硬脂酰磷脂酰胆碱DSPG 二硬脂酰磷脂酰甘油DSPE 二硬脂酸磷脂酰乙醇胺DSSM 二硬脂酰鞘磷脂DTA 差热分析DTS 皮肤治疗系统DV 置换价DVB 二乙烯苯E EC 乙基纤维素EDN 神经毒素Egg PC 卵磷脂EPO 促红细胞生成素ER 增渗比ESR 电子自旋共振光谱EV A 乙烯-醋酸乙烯共聚物F F 沉降容积比FITC 异硫氰酸荧光素FPLC 快速蛋白液相色谱FR 叶酸受体FSDA 国家食品药品监督管理局FSQ 荧光自我淬灭FTIR 傅立叶红外光谱G G1-β-CD 葡糖基-β-环糊精G2-β-CD 麦芽糖基-β-环糊精GCP 药品临床质量管理规定GH 生长激素GHRH 生长激素释放激素GHRHR 生长激素释放激素受体GLP 药品安全试验规范GM1 神经节苷酯GMP 药品生产质量管理规范GOD 葡萄糖氧化酶GPC 凝胶透过色谱法H HDL 高密度脂蛋白HE-β-CD 羟乙基-β-环糊精HIV 人体免疫缺乏病毒HLB 亲水亲油平衡值HP-β-CD 羟丙基-β-环糊精HPC 羟丙基纤维素HPCE 高效毛细管电泳HPH 高压匀化法HPMA 羟丙基甲基丙烯酰胺HPMC 羟丙甲纤维素HPMCAS 醋酸羟丙甲纤维素琥珀酸酯HPMCP 羟丙甲纤维素酞酸酯HPS 羟丙基淀粉HAS 人血清白蛋白IIC50 半数有效浓度IDDS 埋植给药系统IEF 等电聚焦法IFN 干扰素LHRH 促黄体生成素释放激素IL 免疫脂质体IOP 眼内压IUD 宫内埋植系统IVGTT 静注葡萄糖耐受性试验IVR 阴道内埋植系统JJ. P. 日本药局方KKS 卡巴氏瘤LLCST 低临界溶解温度LDL 低密度脂蛋白L-HPC 低取代羟丙基纤维素LMWP 低分子量蛋白LNG 左炔诺孕酮LS 脂质体LUV 大单层脂质体MMAC 最大增溶浓度MALDI-TOF-MS 基质辅助激光解吸/电离飞行时间质谱MBA 亚甲基双丙烯酰胺M-β-CD 甲基-β-环糊精MC 微囊McAb,MAB 单克隆抗体MCC 微晶纤维素MCF-7 人乳腺癌细胞MDI 定量吸入装置MGDF 巨核细胞生长发育因子MLD 药物淋巴结清扫术MLV 多层脂质体MMA 甲基丙烯酸甲酯mOsm 毫渗量MPPC 肉豆蔻酰磷脂酰胆碱MPS 单核细胞MRA 磁共振血管成像MS 微球MS质谱MVL 多囊脂质体Nnano-ESI-MS-MS 纳升电喷雾串联质谱技术Nano-ST 纳米科技NDGA 去甲双氢愈疮木酸NC 纳米囊NE 纳米乳剂NL 纳米脂质体NLS 核定位信号NM 纳米胶束NP 纳米粒NS 纳米球O OLVs 寡层脂质体Osm 渗量OTC 非处方药O/W 水包油PP 分配系数PA 磷脂酸PACA 聚氰基丙烯酸烷基酯PAGE 聚丙烯酰胺凝胶电泳PBCA 聚氰基丙烯酸正丁酯PC 磷脂酰胆碱PCDC 肠压控制型结肠释药胶囊PCL 聚已内酯PCS 激光散射PE 磷脂酰乙醇胺PEAA 聚乙基丙烯酸PEG 聚乙二醇PEO 聚氧乙烯PEO-PBLG 聚乙二醇-聚谷氨酸苄酯羧酸酐共聚物PG 磷脂酰甘油PG 聚谷氨酸PHB 聚3 羟基丁酸酯Ph. Int. 国际药典PI 磷脂酰肌醇PIB 聚异丁烯PLA 聚乳酸PLGA 聚乙交酯丙交酯PMF 肽质量指纹谱法PMMA 聚甲基丙烯酸甲酯PMPC 棕榈酰肉豆蔻酰磷脂酰胆碱PNAC 对硝基乙酰苯胺PNIPAM 聚异丙基丙烯酰胺PPA 聚丙烯酰胺PS 磷脂酰丝氨酸PS 药质体PSA 压敏胶PSPC 棕榈酰硬脂酰磷脂酰胆碱PV A 聚乙烯醇PVP 聚维酮PVPP 交联聚维酮RRES 网状内皮系统RESS 超临界溶液快速膨胀REV 逆相蒸发法RH 相对湿度SSA 硬脂酰胺SAV 单次接种疫苗SBE-β-CD 磺丁基醚-β-环糊精SCF 超临界溶液SDPC 水溶性大分子结合物SDS 十二烷基硫酸钠SFE 超临界萃取技术SLN 固体脂质纳米粒SLS 月桂醇硫酸钠SM 鞘磷脂SMANC 新抑癌菌素-苯乙烯马来酸SOD 超氧化物歧化酶SOM 生长介素SPIO 超顺磁性氧化铁SPPC 硬脂酰棕榈酰磷脂酰胆碱SSL 空间稳定脂质体SST 生长激素释放抑制激素SSTR 生长激素释放抑制激素受体SUV 小单层脂质体TTBAC 乙酰枸橼酸三丁酯TBC 枸橼酸三丁酯Tc 相变温度TCI 经皮免疫TDDS 靶向给药系统TDDS 透皮药物传递系统TDS 透皮贴剂TEC 枸橼酸三乙酯TFR 转铁蛋白受体TFV 干膜法Tg 玻璃化温度TGA 热重分析TOF-MS 飞行时间质谱TPN 全营养输液TPD 微粉超音速经皮给药法TRH 促甲状腺素释放激素TTS 透皮治疗系统UUK 尿激酶U. S. P. 美国药典USPIOs 超微型SPIO(超微型超顺磁性氧化铁)VVLDL 极低密度脂蛋白VME 乙烯基甲基醚VP 乙烯吡咯烷酮WWHO 世界卫生组织W/O 油包水。
2011年思科(CCNA CCNP CCIE)网络工程师认证考试网上报名流程图文详解2011-03-05 15:13首先注明几点:1、鉴于网上很多朋友想要提升自己的技术能力,想参加cisco 考试而不晓得如何报名以及参加考试的要求,本人根据经历为大家介绍一下!2下文本人所介绍的都是报名费,而如果你想知道培训费的价格请参照相关培训网站!3可以不用培训也可以直接参加考试,那就是你自己学习,成败在于自身的努力和实验条件(ccna可以,ccnp也差不多,但是建议ccie考试要参加正式培训)4、报考的人员学历不限,去考试中心参加考试时必须带好两类证件:第一类是身份证等证件;第二类是驾驶证、信用卡之类的证件。
5、需要有一张双币的信用卡(可以向朋友借都行),在官网上报名只需要250美元,在培训班报名是比较贵的!---------------------------------------------------------------------------------------------------------------------------------------------------------------------------网上报名流程:1.先上思科的官网上去注册一个账户,网址。
(这是全英文界面,点击主页右上角的register,进入注册页面,可以选择语言为中文,之后填写带星号的信息,最后填写验证码提交。
(这个账户名和密码保管好,这个账户是很有用的)2.接着上思科考试中心注册账户,网址思科全球唯一指定考试网站,点这个连接直接进入注册界面:https:///Dispatcher?application=Logi n&action=actStartApp&v=W2L&clientCode=CISCOTESTING(这个注册你只是提供你的个人信息和一个常用的邮箱地址,考试中心验证之后会在7天内发送一个属于你的账户和密码,之后你可以更改密码。
CCNA学习大纲CCNA学习大纲一、前言CCNA是Cisco公司推出的入门级网络认证中的新手村(入门级认证),是Cisco认证体系中最广泛接受的认证之一。
本文旨在为初学者提供学习CCNA所需的大纲和指导。
随着网络技术的发展,CCNA也在逐步升级优化,本文基于最新的CCNA 200-301考试大纲制定。
二、CCNA认证指南1. CCNA认证介绍CCNA即Cisco Certified Network Associate,是Cisco 路由交换和数据通信知识的基本测试,是证明个人在Cisco路由器和交换机网络设计和安装方面有一定的基础技能和运营经验。
2. CCNA认证类型CCNA认证已逐渐适应网络和IT行业的变化,并出现了不同的认证类型。
前后换了几代,下面是目前主流的CCNA认证类型。
(1) CCNA Routing and Switching:考生需要通过底层设备、网络标准、协议以及技术如何集成到业务网络中等方面的测试。
(2) CCNA Cloud:考生需要通过基于云平台的IT安全管理、设计、支持和解决故障方面的测试。
(3) CCNA Collaboration:考生需要通过实现CiscoCollaboration和Unified Communications应用方面的测试。
(4) CCNA Cyber Ops:考生需要通过基于网络安全操作的受攻击、威胁情报、事件分析等方面的测试,为网络安全分析员做好准备。
(5) CCNA Data Center:考生需要通过设计、配置和维护数据中心网络的测试。
(6) CCNA Industrial:考生需要了解和理解机器人控制、PLC和其他自动化控件以及工业网络。
(7) CCNA Security:考生需要通过为网络安全实现Core Security Technologies和下一代的网络技术提供适当的手段方面的测试。
(8) CCNA Service Provider:要求考生了解路由和Switch因特网服务提供商网络中的技术。
第二期七章1、A client is communicating with a server on a different segment of the network. How does the server determine确定what service is being requested by the client?确定提供的网络applies the default service configured in directory servicesuses ARP to discover the appropriate service from the local routersends a request to the client asking for the appropriate serviceidentifies the appropriate service from the destination port field目的端口号2、What is the function of the TCP three-way handshake?It enables the synchronization of port numbers between source and destination hosts.It immediately triggers the retransmission of lost data.It synchronizes同步both ends of a connection by allowing both sides to agree upon initial sequence numbers. 双方议定/协商初始序列号It identifies the destination application on the receiving host.3、What are three unique characteristics of UDP? (Choose three.) connection orientedfull-duplex operationlow overhead 低开销no flow control 无流量控制no error-recovery function 错误不重传reliable transmission4、Within TCP, what combination 组件makes up a socket pair对? 套接对source port with destination portsource IP address with destination portsource IP address and destination IP addresssource IP address and port with a destination IP address and port5、What type of update allows client computers to register注册and update their resource records 原纪录with a DNS server whenever changes occur? dynamiczone transferlocal recursive queryroot domain querytop-level domain query6、Which DNS zone resolves 解析an IP address to a qualified domain name 一个合格的域名?dynamic lookupforward lookupresolution lookupreverse lookup 反向查找7、Which two tasks are the responsibility of the local DNS server? (Choose two.)maintaining a large number of cached DNS entriesmaintaining the ISP servermapping name-to-IP addresses for internal hosts 内部主机的域名-IP映射forwarding name resolution解析requests to a caching-only server 将域名解析请求转发至只有缓存功能的服务器forwarding all name resolution requests to root servers on the Internet8、Which protocol is used to send e-mail, either from a client to a server or from a server to another server?SNMPFTPSMTPHTTPS9、A manufacturing company subscribes to certain hosted services from their ISP. The services required include hosted world wide web, file transfer, and e-mail. Which protocols represent these three key applications?(Choose three.)FTPHTTPDNSSNMPDHCPSMTP10、To meet customer expectations满足客户期望, an ISP must guarantee确保a level of service that is based on what two factors? (Choose two.)accessibilityadaptabilityavailability 可用性reliability 可靠性scalability11、Which two statements are true about the OSI and TCP/IP models? (Choose two.)The two bottom layers of the TCP/IP model make up the bottom layer of the OSI model.The TCP/IP model is a theoretical model and the OSI model is based on actual protocols.The OSI network layer is comparable相当于to the Internet layer of the TCP/IP model.The TCP/IP model specifies protocols for the physical network interconnection.The TCP/IP model is based on four layers and the OSI model is based on seven layers.12、What type of DNS server is typically maintained by an ISP?caching-only 缓存rootsecond-leveltop-level13、Which two options correctly match protocol and well-known port number协议和端口的匹配? (Choose two.)DNS - 25FTP - 110HTTP - 80POP3 - 25SMTP - 2514、What are three characteristics of HTTPS? (Choose three.)It uses a different client request-server response process than HTTP uses. It specifies additional rules for passing data between the application and data link layers.It supports authentication.It allows more simultaneous connections than HTTP allows.It encrypts packets with SSL.It requires additional server processing time.额外的服务器处理时间15、User1 is sending an e-mail to User2@. What are two characteristics of the process of sending this data? (Choose two.)It utilizes TCP port 110.A TCP connection is established directly between the User1 and User2 client computers in order to send the e-mail message.It utilizes利用a store and forward process. 使用存储转发The same application layer protocol is used to send the e-mail and retrieve it from the destination server.SMTP is used to send the e-mail message to the mail servers.16、Which three fields do a TCP header and a UDP header have in common? (Choose three.)source portwindowchecksum 校验和destination portacknowledgment numbersequence number17、When a host is communicating with multiple applications on the same server at the same time, which two values will likely be the same in all packets for each session? 那个保持一致的(Choose two.)IP addressMAC addresssession numbersequence number18、What are three characteristics of network reliability可用性? (Choose three.)Redundant冗余hardware provides enhanced reliability. 硬件冗余提供提高可靠性。