On the relation between SAT and BDDs for equivalence checking
- 格式:pdf
- 大小:67.28 KB
- 文档页数:6

十月新SAT写作五个提分建议两分钟做个小测试,看看你的英语水平/test/liuxue.aspx?tid=16-73675-0一、五条小建议,让你的新写作获得高分1.Less is not more. More is more.写得多虽然无法确保高分,而且可能会给考官一种冗长啰嗦之感。
但是写得越少,你的观点、论述、分析就越无法有效展开。
所以,关键是要在写作数量和写作质量上做到平衡。
字数是基本的要求,下面的几条建议可以帮助小伙伴在写作质量上获得提升。
2.Pick one side.OG上虽然明确指出在分析中,考生既可以论证原文是如何说服读者,同时也可以论证原文不具备说服力。
但是,写作考试的文章来源都很权威,而且在考试有限的时间和紧张的氛围中,直接分析原文的说服力强是最明智的选择。
3.T ake notes在具体的新SAT写作过程中,考生需要经常的refer back,如果在阅读原文的过程中,对原文的feature(写作手法,如evidence, reasoning, language等)不做任何标注,写作时是不是会有一种手忙脚乱的感觉?所以清晰的笔记是完全有必要的。
例如,用“?”来标记原文中的rhetorical question修辞;用“≠”标注修辞contrast;用(WC)标注修辞Word choice。
e five-paragraph essay format.采用五段式写作结构,这一结构虽然有“八股文”之嫌,但是对于应试作文来说,可以省很多构思文章结构的时间。
一般来说,在文章第一段开门见山的提出正文中要分析的三个features,正文三段对首段的三个features一一展开分析,末尾段对首段进行restate,整个文章就大功告成了。
5.Pace yourself.相对于老SAT来说,虽然新SAT写作考试时间上延长至50分钟,但新SAT 写作是一种基于阅读的写作,要求考生在透彻理解原文的基础上,从原文本中找到相应的细节来分析原文作者的论证说理过程。

Symbolic Model Checking using SAT procedures instead of BDDsA.Biere12,A.Cimatti3,E.M.Clarke12,M.Fujita4,Y.Zhu121Computer Science Department,Carnegie Mellon University,5000Forbes Avenue,Pittsburgh,PA15213,U.S.A.2Verysys Design Automation,Inc.,42707Lawrence Place,Fremont,CA94538,U.S.A.3Istituto per la Ricerca Scientifica e Tecnolgica(IRST),via Sommarive18,38055Povo(TN),Italy4Fujitsu Laboratories of America,Inc.595Lawrence Expressway,Sunnyvale,CA94086-3922,U.S.A.armin+,emc+,zhu+@,cimatti@irst.itc.it,fujita@AbstractIn this paper,we study the application of propositional deci-sion procedures in hardware verification.In particular,we applybounded model checking,as introduced in[1],to equivalence andinvariant checking.We present several optimizations that reducethe size of generated propositional formulas.In many instances,our SAT-based approach can significantly outperform BDD-basedapproaches.We observe that SAT-based techniques are particularlyefficient in detecting errors in both combinational and sequentialdesigns.1IntroductionA complex hardware design can be error-prone and mistakes arecostly.Formal verification techniques such as symbolic modelchecking are gaining wide industrial pared to tra-ditional validation techniques based on simulation,they providemore extensive coverage and can detect subtle errors.Representingand manipulating boolean expressions is critical to many formalverification techniques.BDDs[3]have traditionally been used forthis purpose.In this paper,we investigate an alternative approachbased on propositional decision procedures.Model checking[5]is an important technique for verifying se-quential designs.In model checking,the specification of a design isexpressed in temporal logic and the implementation is described asafinite state machine.Symbolic model checking uses boolean rep-resentation for thefinite state machine.By replacing explicit staterepresentation with boolean encoding,symbolic model checking[4,10]can handle much larger designs than explicit state modelchecking.With the introduction of bounded model checking[1],we areable to use efficient propositional decision procedures for sym-bolic model checking.In bounded model checking,only paths ofbounded length k are considered.Bounded model checking is thusconcerned withfinding bugs(or counterexamples)of limited lengthk.Given a specification in temporal logic and afinite state machine,we construct a propositional formula which is satisfiable iff there isa counterexample of length k.In practice,we look for longer and00011011Figure1:A two-bit counter with an erroneous transition2Bounded model checkingWe now briefly describe our techniques for bounded model check-ing.First,we give some background and notational conventions. Then we illustrate our approach with a simple example.More de-tails can be found in[1].2.1BackgroundThe specification of a system is expressed in linear temporal logic (LTL).In this paper we only consider the eventuality operator‘F’, and the globally operator‘G’.The techniques can also be applied to a more general class of operators[1].To simplify our discus-sion,we consider only existential LTL formulas,i.e.formulas of type E f where E is the existential path quantifier and f is a tem-poral formula that contains no path quantifiers.Note that E is the dual of the universal path quantifier A.Finding a witness for E f is equivalent tofinding a counterexample for A f.The implementation of a system is described as a Kripke struc-ture.A Kripke structure is a tuple M S I T with afinite set of states S,the set of initial states I S,a transition relation between states T S S,and the labeling of the states:S P A with atomic propositions A.In symbolic model checking,we assume that S01n and each state can be represented by a vector of state variables ss1s n where s i for i1n are propositional vari-ables.The labeling function can be omitted if every atomic propo-sitions corresponds to a state variable.An infinite sequence of statesπs0s1is a path iff s i s i1T for all i N.An LTL formula E f is true in a Kripke structure M(M E f)iff there exists a pathπin M withπf andπ0I.Model checking is concerned with the problem of determining the truth value of an LTL formula in a given Kripke structure,or equivalently,the problem of determining the existence of a witness for the LTL formula.We now illustrate bounded model checking with a simple example.2.2ExampleLet’s consider a two-bit counter.The implementation of the counter is shown as a Kripke structure in Figure1.There are four states in the Kripke structure.Each state s is represented by two state vari-ables s1and s0,denoting the value of the high bit and the low bit respectively.Initially,the value of the counter is00.Thus the initial state predicate I s is defined as s1s0.The transition relation T s s describes the increment of the counter at each step.We define inc s s as s0s0s1s0s1,and we define T s s as inc s s s1s0 s1s0.We deliberately add an erroneous transition from state10to itself.Suppose we are interested in the fact that the counter should eventually reach state11.We can specify the property as AF q, where q s is defined as ly,for all possible exe-cution paths,there exists a state such that q s holds.Equivalently, we can check whether there exists a path in which the counter never reaches state11.The new property is expressed as EG p,wherep s is defined as s1s0.Note that EG p is the dual of AF q.In bounded model checking,we restrict our attention to pathsof length k,that is,paths with k1states.We start with k0,andincrement k until a witness is found.Let’s consider the case where kequals2.We name the k1states as s0,s1,s2.We now formulatea set of constraints on s0s1and s2in propositional logic.The constraints guarantee that a path consisting of s0s1s2is indeed a witness of EG p,or equivalently,a counterexample for AF q.First,we constrain s0s1s2to be a valid path starting from the initial state.Unrolling the transition relation for2steps,we de-rive the propositional formula M2defined as I s0T s0s1 T s1s2,where I and T are predicates for the initial state and the transition relation defined earlier.Second,in order to be a witness for G p,the path must containa loop.Therefore there is a transition from s2to the initial states0,s1or itself.We define L2:T s2s0T s2s1T s2s2. Additionally,property p must hold on every state of the path.We derive a corresponding propositional formula G p2defined as L2p s0p s1p s2.The combination of both constraints, M2G p2,is the result of the translation.In this example,the resulting propositional formula is indeedsatisfiable.The satisfying assignment corresponds to a counterex-ample that is a path from the initial state00over01to10followed by the self-loop at state10.If the erroneous transitionfrom state10to itself is removed then the propositional formulabecomes unsatisfiable.This idea can be generalized to arbitrary LTL formulae.Thedetails are described in[1]together with the following theorem.Theorem1M E f iff M k f k is satisfiable for some k N.3Conversion to Clause FormMany propositional decision procedures assume the input problem to be in conjunctive normal form,or equivalently clause form(CF). In this section,we focus on techniques for converting arbitrary boolean formulas to CF.In particular,we investigate optimization techniques that reduce the number of variables and clauses in the CF generated.Satisfiability test for propositional problems is NP-complete. All known propositional decision procedures are exponential in the worst case.However,they may use different heuristics in guid-ing their search and exhibit different complexity in subsets of the propositional problems.Precise characterization of the“hardness”of propositional problems is difficult and is likely to be dependent on specific propositional decision procedures used.Reducing the size of CF may not always reduce the complexity of the problem. Our optimization techniques are heuristics in nature as well.Ex-perimental results show that these optimization techniques reduce the size of the CF as well as the time for satisfiability test.A formula f in CF is represented as a set of clauses,each clause is a set of literals,and each literal is either a positive or negative propositional variable.In other words,a formula is a conjunction of clauses,and a clause is a disjunction of literals.For example, a b c d e is represented as a b c d e.Given a boolean formula f,one may replace boolean operators in f with and and apply distributivity rule and De Morgan’s law to convert f into CF.The size of the resulting CF can be expo-nential with respect to the size of f.For example,the worse case occurs when f is in disjunctive normal form.To avoid the expo-nential explosion,we use a structure preserving CF transformation [13].procedure bool-to-cf(f,v f) casecached(f,v):return clause(f v f);f==h g:SMV1SA TOsec MB sec MB52457027741370291722201211413702031384370213151********Table1:Counterexample for liveness in a buggy DME(sec=sec-onds,MB=Mega Bytes).CMU with improvements including support for conjunctive parti-tioning.We refer to them as SMV1and SMV2respectively.4.1Model CheckingIn[1]we reported the results of applying bounded model check-ing to some academic examples.We showed that model check-ing safety properties for a sequential shift and add multiplier and finding short counterexamples for liveness properties of an asyn-chronous circuit could be done much faster with SAT than with BDD based methods.In particular,we studied the design of an asynchronous circuit for distributed mutual exclusion[9].We in-troduced a bug by removing some fairness constraints.The buggy design violated the liveness property that a request for a resource will be eventually acknowledged,and there is a counterexample of length2.We applied model checkers tofind the counterexample. Table1shows the results of this experiment.4.2Invariant CheckingSafety properties can be verified by proving an inductive invariant that holds at the initial state,is preserved by the transition rela-tion and implies the safety property[7].These three conditions can all be formulated as propositional satisfiability problems and ver-ified by a propositional decision procedure.Of course,being an inductive invariant is a sufficient but not necessary condition for a safety property.We implemented this approach in the tool BMC as follows.The user formulates the model as usual and specifies the invariant as a safety property(with AG).Then BMC generates two instances of a satisfiability problem.One formula for checking that the invariant is preserved by the transition relation and another formula for checking that the invariant holds initially.The third condition has to be formulated by the user.As an example for this technique we verified that the equiva-lence between two different implementations of a queue of a par-ticular length.This example is taken from[11]and it is known that no variable ordering exists such that the(RO)BDDs for the set of reachable states remain small.In the experiments of Table2an invariant that relates the contents of the two queues was manually constructed.As discussed above,three conditions have to be ver-ified for each particular length of the queues.We compared the results of SAT-based and BDD-based techniques.4.3Equivalence CheckingRecently,there has been a lot of progress in boolean equivalence checking[8,12].State-of-the-art equivalence checkers can handle designs with more than1million gates.These tools utilize the cor-respondence between internal signals and partition large circuits into much smaller ones.If the two circuits to be compared have significantly different structures,equivalence checkers can performSMV2PROVERl sec MB sec MB8240102102076641165731191701161857223302145765430155120308098451377201GB40h#ins#gatesIndustry18233Industry22328790Industry332210Table3:Equivalence checking using SAT procedures(sec=sec-onds).poorly even on much smaller designs.Most equivalence check-ers are BDD-based.We have investigated how propositional deci-sion procedures(SAT procedures)can be used instead of BDDs for equivalence checking.We use BMC to convert the equivalence checking problem to a propositional satisfiability problem.The output of BMC is a for-mula in CF which is fed into SATO.In Table3,we list some in-dustrial circuits that cannot be processed by some state-of-the-art equivalence checkers within24hours.In Industry1and Industry2,the logic of one circuit has been considerably optimized and the other is unoptimized.For both ex-amples,we applied logic optimization using SIS[14]on the circuits before submitting them for equivalence checking.This extra step of logic optimization greatly speeds up our verification.Without it,Industry1takes8246seconds and Industry2takes more than1 day.The use of logic transformation to speed up SAT procedures seems promising for future research.In Industry3,some outputs of the two circuits are not equivalent.However,only a small fraction of the input patterns can differentiate the two circuits(220out of 296).There is little hope that random simulation can identify the non-equality.SATO was able to identify counterexamples in a few seconds for every non-equivalent output!This example supports our belief that SA T-based approaches can detect errors efficiently.5ConclusionOur results demonstrate the potential of SAT-based techniques in various domains of hardware verification.We believe that SAT-based approaches complement the existing BDD-based approaches well.There are some promising directions of future research.Op-timization techniques in generating propositional formulas need to be further investigated.Previous work from otherfields such as ar-tificial intelligence may be relevant as well.Also,heuristics of SA T procedure need to be studied for the domain of hardware verifica-tion.For instance,in BDDs,interleaving the bits often provides a good variable ordering.Similar techniques may work well as split-ting heuristics for SA T procedures.References[1]B IERE,A.,C IMATTI,A.,C LARKE,E.M.,AND Z HU,Y.Symbolicmodel checking without BDDs.In TACAS’99(1999).to appear. [2]B OR¨ALV,A.The industrial success of verification tools based onSt˚a lmarck’s Method.In International Conference on Computer-Aided Verification(CAV’97)(1997),O.Grumberg,Ed.,no.1254in LNCS, Springer-V erlag.[3]B RYANT,R.E.Graph-based algorithms for boolean function manip-ulation.IEEE Transactions on Computers35,8(1986),677–691. [4]B URCH,J.R.,C LARKE,E.M.,AND M C M ILLAN,K.L.Symbolicmodel checking:1020states and rmation and Computa-tion98(1992),142–170.[5]C LARKE,E.,AND E MERSON,E.A.Design and synthesis of syn-chronization skeletons using branching time temporal logic.In Pro-ceedings of the IBM Workshop on Logics of Programs(1981),vol.131 of LNCS,Springer-V erlag,pp.52–71.[6]D AVIS,M.,AND P UTNAM,H.A computing procedure for quantifi-cation theory.Journal of the Association for Computing Machinery7 (1960),201–215.[7]D EHARBE,ing induction and BDDs to model check invariants.In CHARME’97(1997),D.Probst,Ed.,Chapman&Hall.[8]K UNZ,W.HANNIBAL:An efficient tool for logic verification basedon recursive learning.In ICCAD’93(1993),pp.538–543.[9]M ARTIN,A.J.The design of a self-timed circuit for distributed mu-tual exclusion.In Proceedings of the1985Chapel Hill Conference on Very Large Scale Integration(1985),H.Fuchs,Ed.[10]M C M ILLAN,K.L.Symbolic Model Checking:An Approach to theState Explosion Problem.Kluwer Academic Publishers,1993. [11]M C M ILLAN,K.L.A conjunctively decomposed boolean represen-tation for symbolic model checking.In CAV’96(1996),vol.1102of LNCS,Springer-V erlag,pp.13–25.[12]M UKHERJEE,R.,J AIN,J.,T AKAYAMA,K.,F UJITA,M.,A BRA-HAM,J.A.,AND F USSELL,D.S.FLOVER:Filtering oriented com-binational verification approach.In Proc.of International Workshop on Logic Synthesis(1995).[13]P LAISTED,D.,AND G REENBAUM,S.A structure-preserving clauseform translation.Journal of Symbolic Computation2(1986),293–304.[14]S ENTOVICH,E.M.,S INGH,K.J.,L AVAGNO,L.,M.,C.,M UR-GAI,R.,S ALDANHA,A.,S AVOJ,H.,S TEPHAN,P.R.,B RAYTON, R.K.,AND S ANGIOVANNI-V INCENTELLI,A.SIS:A System for Sequential Circuit Synthesis.Memorandum No.UCB/ERL M92/41, Electronics Research Laboratory,College of Engineering,University of California,Berkeley,1992.[15]S T˚ALMARCK,G.A system for determining propositional logic the-orems by applying values and rules to triplets that are generated froma formula,1989.Swedish patent no.467076(1992),U.S.patent no.5276897(1994),European patent no.0404454(1995).[16]Z HANG,H.SA TO:An efficient propositional prover.In InternationalConference on Automated Deduction(CADE’97)(1997),no.1249in LNAI,Springer-Verlag,pp.272–275.。


新SAT阅读中的“关系题”破解技巧两分钟做个小测试,看看你的英语水平/test/liuxue.aspx?tid=16-73675-0这里小编就带大家一起来看看如何理顺新SAT阅读文章中的关系,如何破解新SAT阅读中的“关系题”,技巧多多总有好处,Come on!走起来~Step 1Find the two parts of the passage mentioned in the question.在原文中找到题干所涉及的观点、事件或人物。
Step 2 Determine the relationship between the two situations or ideas (cause/effect, part/whole, comparison/contrast, claim/support)or people (parent/child, rival/rival, colleague/coworker).根据上述提供的关系,判断观点、事件、人物二者的关系。
Step 3Eliminate any answer choices that do not fit the relationship you have determined, or that simply do not make sense in the context of the passage.排除不符合原文所描述的关系的干扰项。
Step 4 Choose your answer from the remaining answer choices - whichever choice has more support from the passage.锁定最佳答案。
以上就是关于如何破解新SAT阅读中的“关系题”,供大家参考。
新SAT阅读中的“关系题”破解技巧/test/liuxue.aspx?tid=16-73675-0。

Efficient Verification of the PCI Local Bus usingBoolean SatisfiabilityFadi A. Aloul and Karem A. SakallahDepartment of Electrical Engineering and Computer ScienceUniversity of MichiganAnnArbor, MI 48109-2122{faloul, karem}@Abstract: The purpose of this paper is to study the application of Boolean Satisfiability to the verification of the PCI Local Bus. The novel feature of this approach is the generation of several propositional formulas that describe the specification of the bus system. The formulas are tested using a powerful SAT solver and the bus is verified for errors. The SAT-based approach has sev-eral important advantages over conventional BDD-based approaches such as achieving high speed testing. To demonstrate how our method works, we have modeled the PCI Local Bus and verified several properties.1 IntroductionRecent developments in semiconductor technology have made possible the integration of over 10 mil-lion transistors on a single chip. A related practice which is evolving to avoid designing systems from scratch is the use of predefined logic blocks referred to as Intellectual Property Components (IP cores) which are usually integrated using standard buses. While most components are usually pre-validated, stan-dard bus protocols still need to be tested and verified.Testing bus protocols is a major challenge. Most bus interface specifications are complex and infor-mally specified. Although a significant amount of work is devoted to the design and validation of bus inter-faces, errors produced by bus protocols can be very difficult to debug especially when system designers have restricted knowledge of the connected IP cores due to the protection of intellectual property.This paper examines the behavior of the PCI Local Bus [12]. It was developed by Intel to accommo-date the advance design of their pentium processors. The high performance bus is also used in DEC Alpha processors. We will model the PCI bus and verify several of its properties using SAT techniques.Several methods have been proposed to verify the PCI Local Bus [5, 6, 10, 11]. Formal verification techniques, such as model checking [8], have been used by several researchers to verify the complex hard-ware design. Chauhan et al. [6] specified the PCI bus using CTL [7] and model checked the state machine mentioned in the PCI specification document [12]. On the other hand, Shimizu et al. [10] specified the PCI bus with monitors and model checked various monitor properties. They present a simple specification style using monitor circuits. The style encourages readability and discourages errors. The English description of the PCI specification was translated into a collection of simple properties and a model checker was used to debug the monitor specifications.Recently, formal verification techniques, such as bounded model checking [1, 2], that uses satisfiabil-ity solvers instead of BDDs have been proposed. SAT-based approaches have several advantages over BDD-based approaches. BDDs [3] are based on canonical representations. A complete BDD has to be con-structed for every problem before testing it for 1-terminals. For large functions, however, the BDD sizes might be too large to fit into available computer memory. In any case, approaches that attempt to construct a complete representation of the function before checking its satisfiability end up doing more work than necessary. Therefore, SAT-based approaches that intelligently sample the variable space are often more effective. They are based on a polynomial representation and follow a depth-first search algorithm, looking for a satisfying assignment. They are less likely to fail due to exponential space blowup. Furthermore,BDD-based approaches require a good variable ordering to minimize the size of the BDD. However, these orderings usually need long periods of time. In contrast, SAT-based approaches can use different decision heuristics at different parts of the search tree to obtain an optimal solution in a short period of time.In this paper, we use Boolean satisfiability to verify the PCI Local Bus. Simple rules from the PCI specification document [12] are extracted and written into a set of logical expressions in conjunctive nor-mal form (CNF). The set of simple properties are based on the monitors introduced by Shimizu et al. [10].Several properties represented in CTL are converted into CNF and added into a CNF formula that contains the PCI specification expressions. A counter example of length K that violates a property can exist based on the solution of the CNF formula. Several formulas are created to verify each property. The formulas are tested using a powerful SAT-solver.The remainder of this paper is organized as follows. Section 2 presents a brief description of the CNF representation and the GRASP SAT solver. Section 3 discusses the modeling of the PCI Local Bus and Section 4 shows how it can be verified using our techniques. We also show some of the bugs found in the PCI protocol. Finally, Section 5 concludes the paper and provides some prospective on future work.2 Basic Definitions & NotationsA conjunctive normal form (CNF) formula on n binary variables is the conjunction (AND) of m clauses each of which is the disjunction (OR) of one or more literals, where a literal is the occurrence of a variable or its complement. The size of a clause is the number of its literals. A formula denotes a unique n -variable Boolean function and each of its clauses corre-sponds to an implicate (clause) of f . Clearly, a function f can be represented by many equivalent CNF for-mulas. We will refer to a CNF formula as a clause database and use “formula,” “CNF formula,” and “clause database” interchangeably. The satisfiability problem (SAT) is concerned with finding an assignment to the arguments of that makes the function equal to 1 or proving that the function is equal to the constant 0.In our experiment, we used the GRASP SAT solver [13] which can be classified as an enhancment to the basic Davis-Putnam backtrack search procedure [9]. The solver performs a depth-first search and can be viewed as consisting of 3 main engines: decision , deduction , and diagnosis . GRASP’s diagnosis engine analyzes the causes of conflicts and generates adequate information to prevent the conflicts from occurring at different parts of the search space. Furthermore, it enhances the diagnosis engine with a non-chronolog-ical backtracking scheme. A detailed description of the solver can be found in [13].3 PCI DescriptionThis section examines the PCI Local Bus, a high performance synchronous bus standard developed by Intel [12]. The bus has a data width of 32 or 64 bits. It is mainly used to connect processors, SCSI control-lers, LAN networks, motion video cards, and ISA bridge controllers.The bus supports two main phases: Arbitration and Address/Data . Both phases are fully synchronous.The arbitration phase involves a centralized algorithm. Each device on the bus has a unique pair of request (REQ) and grant (GNT) lines hardwired to a central arbiter. If a device desires the use of the bus it asserts the REQ line. The arbiter views the incoming requests and makes a decision on the next clock cycle. The decision is based on a Fixed-Priority or Round-Robin policy. The central arbiter is totally fair and serves every master. If the device is granted the bus, the arbiter will assert the device’s GNT line. The new bus master can’t control the bus until the old bus master has transferred all its data. The new master will have access to the bus as soon as the bus becomes idle. The bus is idle whenever the signals (FRAME) and initi-ator ready (IRDY) are deasserted.A device can start transmitting data as soon as its granted the bus and the bus is idle. This is referred to as the Address/Data phase. The transaction begins by asserting the FRAME signal. The address and the transaction type are then placed on the address/data multiplexed lines and the command line respectively.All target devices listen to the address and assert their device select (DEVSEL) line if it maps to theirϕx 1…x n ,,ω1…ωm ,,ϕf x 1…x n ,,()f x 1…x n ,,()address space. This indicates to the master that the target is present on the bus. The master then asserts the signal IRDY, declaring to the target that it is ready to transfer data. Data transfer starts when both IRDY and TRDY are asserted. Wait signals can be inserted between the data transfer phases by deasserting the IRDY or TRDY signals. The FRAME signal is deasserted one clock cycle before the end of the data phase.On the next clock cycle, both TRDY and IRDY signals are deasserted indicating the end of the Address/Data phase and making the bus return to the idle state. Furthermore, transactions can be terminated by the master or target in various situations. These are discussed in more detail in the next section.4 PCI VerificationThe key issues in verifying the PCI Local Bus are the modeling and debugging of the PCI specifica-tion. The PCI specification document is written in English and contains an informal overview of how the protocol works. We start by modeling the PCI protocol in CNF. For example, the PCI specification docu-ment lists a set of rules describing the target termination procedures. A simple rule such as:“Once a target asserts STOP#, it must keep STOP# asserted until FRAME# is deasserted, where-upon it must deassert STOP#.” P.42 Sec 3.3.3.2.1can be easily translated into a set of logical expressions:Stop(t n ) (Stop(t n+1) + Frame(t n ))(Frame(t n ) & Frame(t n+1)) Stop(t n+2)The above logical expressions can be represented in CNF as follows:( Stop(t n ) + Stop(t n+1) + Frame(t n ) )( Frame(t n ) + Frame(t n+1) + Stop(t n+2) )The PCI specification document is completely translated to CNF. Note that variables declared in CNF cor-respond to signals at specific time instances. Therefore, testing up to K time stages requires defining K unique variables for each signal. This is very useful in obtaining an accurate value for each signal at any time instance. The PCI specification is modeled in CNF for a single time unit t 0 using the signal variables for t 0. The single model is then replicated up to K levels by replacing every variable by the variable corre-sponding to the given time unit. An example of that is shown in Fig. 1(b). Finally, in order to avoid invalid states, signal values are initialized at time unit t 0 to the idle state.The second key issue has to do with debugging the protocol. Properties have to be added to check that no device ever observes an illegal combination of bus signals or an unexpected transaction. CTL formulas[7] can be used for dead state (existing reachable states with no transitions to other states) and property checking (incorrect behavior). CTL formulas are built from three components: atomic propositions , Bool-ean connectives , and temporal operators . Atomic propositions represent values of individual state vari-Figure 1: (a) PCI Transaction Example (b) Example of the PCI specification modeCLKREQGNTFRAMEAdd/DataDEVSELCommandIRDYTRDYAddress Data-1Data-2Bus Cmd Byte EnableSpec:CNF-Spec:K = 10 levels:Stop t n ()Stop t n 1+()Frame t n ()¬+()→Stop t n ()¬Stop t n 1+()Frame t n ()¬++()f Stop t 0()¬Stop t 1()Frame t 0()¬++()⋅=Stop t 1()¬Stop t 2()Frame t 1()¬++()…Stop t k 1–()¬Stop t k ()Frame t k 1–()¬++()(a)(b)→¬¬→¬¬¬¬¬ables. Boolean connectives include the basic AND (), OR (), and NOT () operations. Finally,temporal operators include path quantifiers (A:all, E:some) and temporal modality (F:eventually, G:glo-bally, X:next, and U:until). Path quantifiers indicate whether a property has to hold for “all ” execution paths or for “some ” paths. Properties expressed in CTL can be easily converted to CNF according to Fig.2. For example, to check whether two signals are never valid together for all paths, we use the following:AG (signalA & signalB)Since SAT solvers return after identifying a single valid path, it would be impossible to test if a prop-erty holds for all paths. Therefore, the inverse of the property is tested. An unsatisfiable solution indicates that the inverse of the property doesn’t appear in any path, hence the original property is valid for all paths.On the other hand, a satisfiable solution indicates a correct path with a false property. Converting the CTL formula to CNF yields the following boolean function:Proving the function unsatisfiable indicates that the CTL property holds. Note that a separate CNF formula is tested for each time unit. The function is unsatisfiable if all K formulas are proven unsatisfiable.The PCI specification was modeled in CNF up to 10 levels. The CNF model consisted of 1500 vari-ables and 11,000 clauses. The model included a single target with two masters but can be expanded to sev-eral devices. In order to make the verification simple, we didn’t include bus bridges, 64-bit extensions,locks, or interrupts. Several properties were verified including bus arbitration, read/write transactions,back-to-back transactions, and master/target terminations. The CNF formulas were tested using GRASP.The experiments were conducted on a 333 MHz Pentium Pro running Linux and equipped with 512 MByte of RAM. In order to measure the performance difference between SAT-based and BDD-based approaches,we modeled the PCI specification in SMV [4] and tested the same properties using CTL model checking.We used Carnegie Mellon's SMV [4] as the model checker. The SAT-based approach was able to verify the protocol within 2 minutes using up to 3.5 MByte of memory. The BDD-based approach required 112minutes of CPU and up to 27MByte of RAM.The above experiment uncovered several errors in the PCI specification that were previously identified by Chauhan et al. [6] and Shimizu et al. [10]. Some of these errors were based on a misinterpretation of the English description in the PCI specification document. Others were actual errors in the PCI protocol. One of the main errors detected deal with target-initiated terminations. Three types of target-initiated termina-∧∨¬¬f ϕmodel ()signalA t 0()signalB t 0()⋅signalA t 1()signalB t 1()⋅…signalA t k 1–()signalB t k 1–()⋅+++()⋅=Figure 2: Converting CTL formulas to CNF := CTL property at time k AG AF EG EF CTL formula in CNF Valid property if f SAT=f UNS =ϕdebug ω0¬ω1¬…ωk 1–¬+++()=ϕdebug ω0¬ω1¬…ωk 1–¬⋅⋅⋅()=ϕdebug ω0ω1…ωk 1–⋅⋅⋅()=ϕdebug ω0ω1…ωk 1–+++()=f ϕmodel ϕdebug⋅=ωk t 0t 2t 1t 0t 2t 1t 0t 2t 1t 0t 2t 1f SAT =f UNS =。


新教材高中英语新人教版选择性必修第一册:课时作业(十二) Unit 4 Section ⅢUsing Language层级一课时跟踪检测维度1 单词拼写1.The twins are so alike. It's difficult to ________ (辨别) one from the other.2.As a teacher, you have to ________ (调整) your methods to the needs of different children.3.Sorry to ________ (打扰) you, but there's a call for you on line two.4.With his arms folded across his ________ (胸部), Robert looked at his friend with a smile on his face.5.Having ________ (澄清) his opinion of the incident, Mr. Smith sat down and listened to others'.6.China suggests settling the ________ (冲突) through peaceful means.7.We can thoroughly recommend the firm you ________ (询问) about.8.Try to ________ (分心) yourself by playing mind games, choosing new running routes, or running with other people.9.We can ________ (察觉) his sorrow by the looks on his face.10.Hearing the result of the competition, she couldn't help ________ (哭泣) aloud.维度2 单句语法填空1.There is a growing ________ (tend) for people to work at home instead of in offices.2.According to the research, many ________ (educate) strongly oppose protecting children too much.3.From this experience, you should learn how ________ (distinguish) right from wrong.4.In China, smiling is not only an expression of happiness, but also a way to avoid being ________ (embarrass).5.When learning his friend had moved to a ________ (slight) larger house, he wandered around, depressed and full of ________ (anxious).6.I really felt ________ (shame) of failing to lend a hand to my neighbour when he was in need.7.In the street, she found herself ________ (stare) at by a stranger, which made her a little nervous.8.Last Sunday Jack wanted to go to the cinema ________ his cousin would rather stay at home.维度3 完成句子/句型转换1.当我们和朋友发生冲突的时候,换位思考是十分重要的。

2012年大连外国语大学英语专业(语言学)真题试卷(总分:154.00,做题时间:90分钟)一、判断题(总题数:20,分数:40.00)nguage is a means of verbal communication which can only take place effectively if all the users share a broad understanding of human interaction including such associated factors as nonverbal cues,motivation,and socio-cultural roles.(分数:2.00)A.True √B.False解析:解析:考查语言的定义和影响语言交际的因素。
人们之间的有效沟通会受到语言、肢体语言、社会及文化等因素的影响。
2.Different words are used to describe the concept indifferent languages.This reflects the design feature of displacement concerning human languages.(分数:2.00)A.TrueB.False √解析:解析:考查语言的任意性。
任意性指语言符号的形式与意义之间没有自然的联系。
3.Adults enjoy reading poems for its sheer beauty and children take delight in repetitive rhythms. This reflects the informative function of language.(分数:2.00)A.TrueB.False √解析:解析:考查语言的娱乐性功能。
人们有时会因为纯粹的乐趣而使用语言。
4.Journalists keep writing about and reporting on important events. This better reflects the recreational function of language.(分数:2.00)A.TrueB.False √解析:解析:考查语言的信息功能。

SAT语法笔记解题方法:一看逗号找谓语二跳修饰(定语、状语)找主干看逻辑合理性:保持原文强烈的语气完成进行时保持原文合理的时态,尽量避免虚拟语气忠实原文情态动词不作为考查方向90%以上考察非谓一般式不要随便改变重点解题步骤:1、解题遵循先语法后逻辑2、先基本结构错误后修饰性错误3、比较选项寻找差异e.g. “;"相当于带有并列关系的“。
”SAT十条公理:1、选项中含有being的95%是错的2、在SAT语法中there be句型表示自然存在的,原文中有there be70%是错的3、平行形式A, B and C中一定是and连接,而不是as well as4、动词优于形容词优于抽象名词5、主动优于被动,连词优于介词6、介词加which优于where(which前是什么介词不考)7、宾语从句that不省8、after和being有明显的先后关系,如果原文没有选项中有是错的9、没有do it / them / that 只有do so10. 表示是否只能用whether , 不使用if和whether ~ or not11. because of 后只能加名词或名词短语,不能加doing, one’s doing12。
doing;one’s doing,by one's doing 一般应为doing出题要点:见到平行看结构,形式功能要对称。
见到代词找指代,指代通常不合理。
见到谓语看主语,主谓一致看状语。
见到比较看对象,对象通常不可比。
(比较比喻看首尾)一、常考语法体系(挑错题Identifying Sentence Errors)1.主谓一致(Subject verb agreement)。
尤其是用于倒装时,比如there be句型或地点状语至于句首的倒装情况,一定要找到真正的主语。
通常一套writing里总会有一个倒装句,并多为动词部分出错.有插入语时,要勇敢的抛弃非中心部分,找到中心的主语。
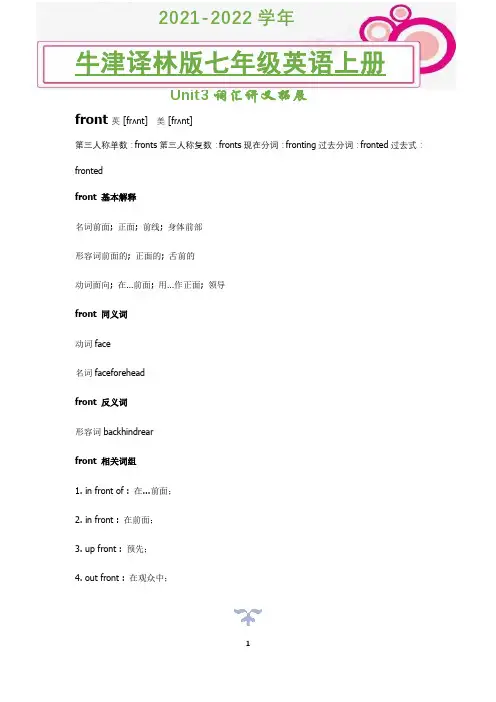
Unit3词汇讲义拓展front英 [frʌnt]美 [frʌnt]第三人称单数:fronts第三人称复数:fronts现在分词:fronting过去分词:fronted过去式:frontedfront 基本解释名词前面; 正面; 前线; 身体前部形容词前面的; 正面的; 舌前的动词面向; 在…前面; 用…作正面; 领导front 同义词动词face名词faceforeheadfront 反义词形容词backhindrearfront 相关词组1. in front of : 在...前面;2. in front : 在前面;3. up front : 预先;4. out front : 在观众中;Unit3词汇讲义拓展5. front to front : 面对面;6. get in front of oneself : 着慌, 被搞糊涂;7. come to the front : 变得引人注目, 出人头地;front 相关例句不及物动词1. Some claimed that the doctor's union fronted for the smuggling ring.有人说医师公会是走私集团的掩护机关。
名词1. That store was a front for foreign agent.那家商店是为外国间谍打掩护的。
2. She worked on the home front helping to produce weapons for the army.她在祖国帮助生产军队用的武器。
3. He has just returned from the front.他刚从前线回来。
front 情景对话退房A:Front Desk. Can I help you?前台,需要我为您服务吗?Unit3词汇讲义拓展B:Yes. I'm checking out now, and want to get a taxi to the cinema. Could you get one for me, please?我现在要退房,需要一部出租车到电影院。

2023年教师资格之中学英语学科知识与教学能力真题练习试卷B卷附答案单选题(共100题)1、 According to a recent research, the old are more than twice as likely to have a positive attitude to life __________ the young.A.asB.thanC.whileD.until【答案】 A2、Passage 1A.generally distorted valuesB.unfair wealth distributionC.a marginalized lifestyleD.a rigid moral code【答案】 A3、Skill-integrated activities allow teachers to build in more_________ into a lesson, for the rangeof activities will be wider.A.certaintyB.simplicityC.varietyD.accuracy【答案】 C4、For better classroom management, what should the teacher do while the students are doing activities?A.Participating in a groupB.Preparing for the next procedureC.Moving around to monitor, prompt and provide helpD.Standing in front of the class【答案】 C5、He pledged support for__________care", where youngsters werelooked after by close relatives like aunts or uncles, but not parents.A.familyB.kinshipC.siblingD.relative【答案】 B6、Which one does not belong to subjective questions in the following English tests?A.WritingB.Oral testC.TranslationD.Cloze【答案】 D7、Application of the transformational rules yields__________ structure.A.lexiconB.deepC.mexicalD.surface【答案】 D8、Y: Did you know that you were wearing odd socks?A.qualityB.quantityC.relationD.manner【答案】 C9、Passage 1A.measuring the level of messenger RNAB.calculating the number of more active gene typesC.instructing the production of certain proteinsparing less active genes with more active ones【答案】 A10、请阅读Passage 1。
中考英语科技创新的生态系统构建单选题40题1.The new technology can make our lives more convenient. “convenient” means _____.A.difficultB.easyfortableD.busy答案:C。
“convenient”意思是方便的,A 选项“difficult”是困难的;B 选项“easy”是容易的;C 选项“comfortable”是舒适的、方便的;D 选项“busy”是忙碌的。
所以答案是C。
2.In the field of technology innovation, we often use “smartphone”. What's the Chinese meaning of “smartphone”?A.电脑B.智能手机C.平板电脑D.电视答案:B。
“smartphone”的中文意思是智能手机。
A 选项是电脑;C 选项是平板电脑;D 选项是电视。
所以答案是B。
3.Technology innovation brings us many new _____.A.productsB.booksC.pens答案:A。
科技创新给我们带来很多新的产品。
B 选项是书;C 选项是钢笔;D 选项是铅笔。
所以答案是A。
4.We can use technology to solve many problems. “solve” means _____.A.createB.findC.answerD.make答案:C。
“solve”意思是解决,A 选项“create”是创造;B 选项“find”是找到;C 选项“answer”是回答、解决;D 选项“make”是制作。
所以答案是C。
5.The development of technology needs a lot of _____.A.moneyB.timeC.peopleD.effort答案:D。
语言学导论第11讲:⏹ENDOCENTRIC construction is one whose distribution is functionally equivalent to thatof one or more of irs constituents,i.e., a word or a group os words, which serves as a definable CENTRE or HEAD.⏹EXOCENTRIC construction is just the opposite of endocentric construction. It refers to agroup of syntactically related words where none of the words id functionally equivalent to the group as a whole.Endocentric constructions fall into two main types, depending on the relation between constituents: coordination and subordination.COORDINATION is a common syntactic pattern in English and other langauges formed by grouping together two or more categories of the same type with the help of a conjunction such as and, but, and or.SUBORDINATION refers to the process or result of linking linguistic units so that they have different syntactic status, one being dependent upon the other, and usually a constituent of the other.The three basic ytpes of subordinate clauses are: complement clauses, adjunct (or adverbial ) clauses, and relative clauses.(p.89-92)The term category is used for defining properties of units like noun and verb.⏹The noun is usually said to have the categories of number, gender, case; and the verb thecategories of tense, aspect, voice.⏹1) Number is mostly a category of the noun and pronoun.There are usually two terms of number: singular and plural.Classical Greek and Arabic have a third number: dual.Chinese has no numbers.⏹“们”can be used only with human nouns, but not with “things”. Even with human nouns,it cannot be used together with quantifiers.学生们, *椅子们, *三个学生们2) Gender is also mostly a category of the noun and pronoun.In English, the gender distinctions are natural, determined by the biological gender of the creature: actor, actress, hero, heroine, etc.In French,the gender distinctions are grammatical.⏹3) The category of case is prominent in the grammar of Latin, with six distinctions ofnominative(主格), vocative(呼格), accusative(宾格), genitive(属格),dative(与格) and ablative(离格).In English, pronouns have three cases of nominative主格, accusative宾格and genitive属格. Nouns have only two cases:general通格and genitive属格(John’s, boy’s)⏹Tense and AspectTense and Aspect are two important categories of the verb, and they were not separated in traditional grammar. Based on the tense system in Latin grammar, English used to have sixteen tenses.⏹Two Distinctions made by modern linguists:⏹1)The distinction between time and tense:Time is a universal concept, which every language is capable of expressing; tense is a linguistic concept, which varies from language to language.⏹2) The distinction between tense and aspect:⏹Tense is deictic(指示的), i.e.indicating time relative to the time of utterance; aspectindicates the time not relative to utterance, but relative to the time of another event described, or implied, in the narrative.As a result,⏹there are only two tenses recognized now: past and present⏹The so-called future tense is not expressed by morphology, not by the different forms ofthe verb, but by various other means, such as “will/shall”, “be going to”, “present progressive aspect”, “simple present tense”etc.⏹There are two aspects: perfective(完成体) and imperfective(未完成体).⏹The former refers to the completion of an action, and the later expresses durationwithout completion.⏹In English, the two aspects are known as “perfective” and “progressive”.⏹Quirk suggested that the perfective should be interpreted in the broadest possible way asindicating anterior time:(先前时间)i.e. “time preceding whatever time orientation is signalled by tense or by other elements of the sentence or its context.”(“由时、或句子的其它成分、或上下文表明的任何时间定位前的时间”)Concord and Government一致关系和支配关系Concord(agreement) is the requirement that the forms of two or more words in a syntactic relationship should agree with each other in terms of some categories.⏹He speaks English.⏹They spoke English.⏹Government means that the form of some words is controlled by other words in certainsyntactic constructions.⏹It differs from concord in that this is a relationship in which a word of a certain classdetermines the form of others in terms of certain category.⏹In English, the pronoun after a verb or a preposition should be in the object form as in“She gave him a book”.⏹Syntactic Functionit is the relationship between a linguistic form and other parts of the linguistic pattern in which it is used.There are 5 functional categories of clause constituents:Subject,verb,object,complement, and adverbialS—subjectV—verbO—object –direct object (Od)—indirect object(Oi)C—complement –subject complement (Cs)—object complement(Co)A—adverbial –subject-related(As)—object-related(Ao)A subordinate clause may function as subject, object, complement, or adverbial in a superordinate clause. For example:That we need a larger computer has become obvious. (subject)He doesn’t know when they will come. (direct object)You can tell them that I’ll be back in ten minutes.(indirect object)One result of the delay was that the cost became much higher.(subject complement)I found her reading in the dining room.(object complement)When you see Jack, give him my best wishes. (adverbial)Subject:Grammatical subject & logical subject:John was bitten by the dog.The core object noun (John)sits in the slot before the verb in the passive, it is called the GRAMMA TICAL SUBJECT, for the original object noun phrase occupies the grammatical space before a verb, the space that a subject normally occupies, the core subject (a dog), now the object of a preposition, is called the LOGICAL SUBJECT,since semanticallt the core subject still does what a subject normally does: it performs a action.The properties of subjects in English:a. Word order: Subject ordinarily precedes the verb in statements: Sally collects stamps.b. Pro-forms: the first and third person pronouns in English appear in a special form when the pronoun is a subject:He loves her.They threw stones at us.c. Agreement with verb:She angers him.They anger him.d.Content questions: if the subjects id replaced by a question word, the rest of the sentence remains unchanged, but when any other element of the sentence is replaced by a question word, an auxiliary verb must appear before the subject.John stole/would steal Mrs. Thatcher’s picture from the British Council.(ask questions with the above underlined words respectively.)e. Tag question: it always contains a pronoun which refers back to the subject,and never to any other elements in the sentence.John loves Mary, doesn’t he?John loves Mary, doesn’t she? ﹡Predicate: it refers to a major constituent of sentence structure in a binary analysis in which all obligatory constituents other than the subject were considered together. It usually expresses actions, processes, and states that relate to the subject.The new master soon put the class into good order.we can divide it first into subject,and predicate, then to divide the subject into nominative and its enlargement, and finally its predicate into finite verb, completion and extension, the completion being either object or commplement ot both.Subject: Nominative: masterenlargement: (1) the, (2) newPredicate: finite verb: putcompletion: object: the classcomplement:into good orderextension: soonThe predicator comprises what there is of the verbal group in addition to the finite element. Some claused, known as non-finite clauses, have only a predicator.Mary sat at the desk, reading a book.The predicator has four functions:(1) It specifies time reference other than reference to the time of the speech event,i.e.’secondary’tense: past, present or future.(2) It specifies various other aspects and phrases like seeming, trying,hoping, etc.(3) It specifies the voice: active or passive(4) It specifies the process (action, event, mental process, behavior, relation or existence.e.g.Has been trying to be heard(1) A complex secondary tense, been +ing;(2) A conative phase, try +to(3)Passive voice, be+ -d(4)The nmental process hear(5)Object:Grammar usually considers the object as the non-subject argument (中词)of a transitive verb. Object may refer to the “receiver”or “goal”of an action, and it is further classified into DIRECT OBJECT and INDIRECT OBJECT.Mother bought a dollMother gave my sister a doll.In some inflecting languages, object is marked by case labels: the accusative case for direct object, and the dative case for indirect object.In English, “object”is recognized by tracing its relation to word order and by inflections (of pronoun).Mother gave a doll to my sisterJohn kicked me.In some inflecting languages, object is marked by case labels: the accusative case for direct object, and the dative case for indirect object.In English, “object”is recognized by tracing its relation to word order and by inflections (of pronoun).Mother gave a doll to my sisterJohn kicked me.Modern grammar regards the object as an element which can become subject in a passive construction.Jim broke the window glass. (The window glass was brokenby Jim)Mike beat Mary. (Mary was beaten by Mike)。
Cut SweepingNiklas EenCadence Research Labs,Berkeley,USA.AbstractThis paper presents a light-weight sweeping method,sim-ilar to SAT-and BDD-sweeping.Performance are on the order of10x to100x faster than SAT-sweeping for large de-signs,while achieving about50-90%of the reductions.1IntroductionIn recent years,two methods for circuit minimization through detection of equivalent points,BDD-sweeping[4] and SAT-sweeping[3,8],have become prevalent in logic synthesis and verification[6,7].Both methods are in prin-ciple complete,i.e.theyfind all existing pairs of equiva-lent points in the circuit,but are for reasons of scalability often made incomplete by introducing multiple sweeping layers(for BDD-sweeping)or time-bounded SAT-runs(for SAT-sweeping).Even so,these methods do not scale well beyond a million gates,and few applications have the time-budget to sweep such large designs.For those cases,this paper proposes a new algorithm, cut-sweeping,that is inherently incomplete but scales to much larger designs than the previous methods.Experi-mental results show that for million-gate designs,runtime is on the order of seconds and minutes rather than hours and days,while still picking off50-90%of all equivalences present in the circuit.This allows for the method to be used in applications such as hardware accelerated emulation or FPGA synthesis.The cut-sweeping method is based on partially enumer-ating,and hashing,the k-feasible cuts of the circuit[5].If two nodes try to hash the same cut,they are found equiv-alent.On a high level,the procedure resembles BDD-sweeping,but with the BDDs kept very small(actually rep-resented as truth-tables),and the sweeping layers being de-termined individually for each node in a muchfiner grained fashion than for BDD-sweeping.is determined by the user and isfixed throughout the pro-cedure.For each cut,the functional relation between the inputs(leaves)and the output is computed and stored as a 2k-bit truth-table(FTB–“function table”)together with the cut.If the cut-sets for two nodes m and n have a common element,and the associated FTBs are the same,m and n are proven equivalent.The information is immediately used to rewrite the network by substituting either m for n or vice versa,after which the cut-enumeration is resumed.The rationale behind the procedure is that most of the equivalent points detected by existing sweeping methods are local,and if we use wide enough cuts,we should be able to capture a big part of them.3.1Cut normalizationIn a practical implementation of the procedure just outlined, an actual cut will be stored as a vector,i.e.an ordered se-quence.The bit-pattern comprising the FTB will depend on the order,so to facilitate comparison between cuts(includ-ing their FTBs)the cut-inputs are kept sorted according to a global order on the gates(any order will do).Moreover, it is desirable to identify functions f and¬f,because they can be used interchangeably in an AIG by adjusting the sign attributes on the arcs accordingly.As cuts are stored during the enumeration,we therefore enforce the lowest bit of the FTB to be zero by simply inverting the whole FTB if neces-sary,and remembering that the cut now represents¬f rather than f.3.2Cut mergingCombining two cuts C1and C2with their associated FTBs requires the following steps:1.The inputs(stored as vectors)are merged and sorted.If the new input vector is larger than the cut-width k, the merge operation is aborted.2.The FTBs of C1and C2are manipulated to reflect thenew input order and the extra inputs from the other cut.3.The two FTBs are bitwise-ANDed(there are onlyAND-nodes in an AIG)to produce the FTB for the new cut.Additionally,a fourth step can be carried out:scanning the new FTB for redundant inputs.Although the cut struc-turally depends on all inputs of C1∪C2,due to reconver-gence it often happens that inputs are semantically masked (i.e.the input does not affect the output).In the experiments (section5),this step is performed.3.3Prioritizing cutsGiven the procedure for merging two cuts,implementing the⊗k operation is straight-forward.To make the procedure feasible for larger cut-widths,however,some cuts have to be discarded.If two nodes are equivalent,it is enough to detect just one common cut,which motivates keeping only a few“good”cuts for each node.These“priority cuts”[1] should be chosen to maximize the likelihood of capturing equivalent nodes in the local transitive fanout.We make two observations:1.Nodes with a single fanout need not be used as input toa cut.If two nodes m and n have a common cut,theremust be a common cut where every node has fanout degree≥2.2.Nodes with a high fanout degree will occur in morecuts,and thus,cuts where all inputs have a high fanout degree should have a higher chance of occurring in multiple cut-sets.From the second bullet we propose the following sorting criteria for cuts:cutQuality(C)= n∈C1design1678,396502,871—2154s541,767(78%)—74s572,050(61%)—8s design21,378,8821,184,646—4021s1,209,155(87%)—110s1,223,025(80%)—14s design32,174,1881,871,434—7379s1,906,063(89%)—171s1,931,225(80%)—23s design42,403,3222,097,401—15,003s2,240,949(53%)—109s2,255,588(48%)—20s design53,160,0672,744,998—22,422s2,832,021(79%)—311s2,886,273(66%)—40s design617,409,623[>24h]17,130,262—1824s17,176,208—273scutEnum(Wire w,Map Wire,Cuts cutset,Map Cut,Wire unique,int k,int N){Cuts cuts–Empty array;elements added by’push()’Cuts∆0=cutset.lookup(w in0)Cuts∆1=cutset.lookup(w in1)–E NUMERATE CUTS:cuts.push({w})–Add singleton cutforEach(c0,c1)∈∆0×∆1do{if(|c0|==1&&nFanouts(w in0)<2)continue–Use only singleton cuts fromif(|c1|==1&&nFanouts(w in1)<2)continue nodes with multiple fanoutsCut c=merge(c0,sign(w in0),c1,sign(w in1),k)if(c.null())continue–Resulting cut is wider than kif(c.size()==0)–Node is constantstrashedReplace(w,(c.ftb==0)?W IRE T RUE)returnelse if(c.size()==1)–Node is equal to an inputstrashedReplace(w,(c.ftb==F TBN ULL&¬Deleted(v))–Found the same cut in hash-tableWire w in0=(c.ftb&1)?¬w:w–Normalization for negationstrashedReplace(w in0,v)return}–S TORE CUTS:if(cuts.size()>N) keep the N best cuts according to“cutQuality()”cutset.set(w,cuts)forEach c∈cuts do{Wire v=(c.ftb&1)?¬w:w–Normalization for negationunique.set(c,v)}}Figure1.Cut-enumeration for one gate.Wire’w’points to an AND-gate with inputs w in0and w in1,for which sets of cuts has already been computed.The above procedure combines these sets to a cut-set for’w’,and at the same time looks for equivalences to use for rewriting.cutEnum(Network network,int k,int N){Map Wire,Cuts cutset–default value is the empty setMap Cut,Wire unique–Uniqueness table for cutstopologicallyForEach w∈network do–bottom-up traversal from PIs to POsif(type(w)==G ATE T YPE。
2024-2025学年外研版英语小学六年级上学期期中复习试卷及答案指导一、听力部分(本大题有12小题,每小题2分,共24分)1、What is the weather like today in the dialogue?A. It’s sunny.B. It’s cloudy.C. It’s rainy.Answer: CExplanation: In the dialogue, one of the speakers mentions, “Look outside! It’s raining cats and dogs,” which indicates that it is rainy.2、Where does the conversation take place?A. At a library.B. At a park.C. At a school.Answer: AExplanation: The conversation includes references to “borrowing a book” and “the library rules,” which suggests that it is taking place at a library.3、Listen to the conversation between a student and a teacher. Choose the correct answer to the following question.Question: What does the teacher ask the student to do?A. To read the passage again.B. To summarize the main idea of the passage.C. To explain the difficult words in the passage.Answer: BExplanation: In the conversation, the teacher asks the student to summarize the main idea of the passage, which means the student needs to provide a brief overview of the passage’s content.4、Listen to the dialogue between two friends discussing their favorite sports. Answer the following question.Question: What sport does the second friend like?A. BasketballB. SoccerC. TennisAnswer: BExplanation: In the dialogue, the first friend asks the second friend about their favorite sport, and the second friend responds by saying they like soccer. Therefore, the correct answer is B.5、Listen to the dialogue and choose the best answer for each question.A. What is the weather like today?B. What time is it?C. How are the students feeling today?Answer: AExplanation: In the dialogue, one of the speakers mentions, “The weather is sunny today,” which indicates that the weather is the topic being discussed.6、Listen to the passage and complete the following sentence.The student is going to the library because ______.A. he needs to borrow some books for his projectB. he wants to read a new novelC. he wants to meet his friendsAnswer: AExplanation: The passage clearly states that the student needs to borrow some books for his school project, which is why he is going to the library.7.A: What is the weather like today?B: It’s sunny, but it’s a b it cold.Q: How is the weather today?A: It’s sunny, but a bit cold.Answer: It’s sunny, but a bit cold.Explanation: This question asks about the weather today. In the dialogue, the answer is given directly: “It’s sunny, but it’s a bit cold.”8.A: How do you usually go to school?B: I usually go to school by bus, but sometimes I walk.Q: How does the student usually go to school?A: The student usually goes to school by bus, but sometimes walks.Answer: The student usually goes to school by bus, but sometimes walks. Explanation: This question asks about the student’s usual mode of transportation to school. The answer is provided in the dialogue: “I usually go to school by bus, but sometimes I walk.”9.Listen to the conversation and answer the question.W: Hello, John. How was your science fair project?M: It was great, thank you! I built a model of a solar-powered car.W: That sounds interesting. How long did it take you to complete it?M: It took me about two months, including researching and building the car.Question: How long did it take John to complete his science fair project?A. One monthB. Two monthsC. Three monthsD. Four monthsAnswer: B. Two monthsExplanation: The answer is found in the dialogue where John says, “It took me about two months, including researching and building the car.”10.Listen to the passage and complete the sentence.The teacher asked the students to write a short story. The story should be about a day at the beach. Sarah started her story with, “On a sunny Saturday morning, my family and I decided to go to the beach.”Question: What did Sarah and her family decide to do on a sunny Saturdaymorning?A. Go to the parkB. Go to the beachC. Go to a movieD. Go to the zooAnswer: B. Go to the beachExplanation: The answer is directly stated in the first sentence of Sarah’s story, “On a sunny Saturday morning, my family and I decided to go to the beach.”11.Listen to the dialogue between two students, Xiao Ming and Xiao Li, and answer the question.Question: What subject do they prefer?A)MathB)EnglishC)ScienceD)HistoryAnswer: B) EnglishExplanation: In the dialogue, Xiao Ming says, “I think English is the most interesting subject.” Therefore, they both prefer English.12.Listen to a short passage about a famous place in China and answer the question.Question: What is the passage mainly about?A)The history of the placeB)The food in the placeC)The attractions in the placeD)The culture in the placeAnswer: C) The attractions in the placeExplanation: The passage talks about the famous attractions in the place, such as the Great Wall, the Forbidden City, and the Summer Palace. It mentions the beauty and significance of these attractions, making it clear that the passage is mainly about the attractions in the place.二、选择题(本大题有12小题,每小题2分,共24分)1、Choose the correct word to complete the sentence.The cat is very_______and always keeps its fur clean.A. lazyB. activeC. cleverD. tidyAnswer: DExplanation: The correct answer is “tidy” because it describes the cat’s habit of keeping its fur clean. The other options do not fit the context of the sentence.2、Select the word that is different from the others in terms of meaning.A. jumpB. flyC. swimD. eatAnswer: DExplanation: The word “eat” is different from the others as it refers to the act of consuming food. “Jump,” “fly,” and “swim” are all related to forms of movement.3、Choose the correct word to complete the sentence.The cat is sitting___________the tree, watching the birds.A)inB)onC)atD)underAnswer: B) onExplanation: The correct preposition to use with “the tree” is “on,” indicating that the cat is sitting on top of the tree.4、Select the sentence that is grammatically correct.A)She has went to the store.B)He is going to the movies, isn’t?C)They are going to the park, aren’t they?D)I have been to the museum, hasn’t I?Answer: C) They are going to the park, aren’t they?Explanation: Option C is the correct sentence because it uses the correctsubject-verb agreement and question formation. Options A, B, and D contain grammatical errors.5.Choose the correct word to complete the sentence:The cat___________on the mat.A. sitB. sitsC. satD. sittingAnswer: BExplanation: The correct form of the verb to use with “the cat” as the subject and “on the mat” as the location is the present simple tense. Therefore, “sits” is the correct choice.6.Select the word that is spelled correctly:Which of the following words is spelled correctly?A. thereB. theirC. they’reD. there’sAnswer: BExplanation: “Their” is the correct spelling for the possessive adjective used to describe something owned by them. The other options are incorrect spellings or are different words with different meanings. “There” means at that place;“they’re” is a contraction for “they are”; “there’s” is a contraction for “there is” or “there are.”7.Choose the correct word to complete the sentence:The cat is sleeping in the _.A. boxB. treeC. riverAnswer: AExplanation: The correct answer is “box” because it is the most suitable place for a cat to sleep. The other options, “tree” and “river,” are not appropriate places for a cat to sleep.8.Choose the correct word to complete the sentence:The teacher asked the students to write a_about their summer vacation.A. storyB. poemC. essayAnswer: CExplanation: The correct answer is “essay” because it is the most suitable type of writing for describing a personal experience, such as a summer vacation. “Story” and “poem” are also forms of writing but ar e less appropriate for this context.9.Choose the correct word to complete the sentence.The cat is sleeping on the _.A. tableB. chairC. bedAnswer: CExplanation: The correct answer is “bed” because it is the most typical place for a cat to sleep. The other options, “table” and “chair,” are less common for a cat’s resting place.10.Select the word that does not belong in the following list.a)appleb)bananac)oranged)tomatoAnswer: DExplanation: The word that does not belong is “tomato.” Apples, bananas, and oranges are all fruits, while tomatoes are technically a vegetable. They are often used as fruits in cooking, but botanically, they are classified as vegetables.11.The cat sat on the_(A) mat B) table C) floor D) chair.Answer: AExpla nation: The correct answer is “mat” because the phrase “The cat sat on the mat” is a common expression, meaning the cat was sitting on a small rug or mat. The other options do not fit the context of the sentence.12.Where is the school (A) near B) far from C) beside D) in.Answer: BExplanation: The correct answer is “far from” because it indicates a distance from the school. The phrase “Where is the school” is asking for the location of the school in relation to something else. “Near” and “beside” would im ply proximity, while “in” would imply the school is located inside something. “Far from” is the only option that suggests a distance.三、完型填空(10分)Task 3: Cloze CompletionRead the following passage and choose the best word for each blank from the options given below.The school trip to the [1] was a great success. The children were excited to learn about the animals and plants there. As soon as they arrived, the guide [2] them to the entrance of the zoo. The animals were so [3] that the children couldn’t help but stop to take pictures. After visiting the big cats, they moved on to the [4] section. Here, they learned about the birds from all over the world. The most fascinating part was the [5], where they saw a penguin parade!1.A) museumB) parkC) zooD) beach2.A) invitedB) showedC) tookD) called3.A) beautifulB) loudC) shyD) wild4.A) mammalsB) reptilesC) birdsD) insects5.A) aquariumB) playgroundC) libraryD) observatoryAnswers:1.C) zoo2.C) took3.A) beautiful4.C) birds5.A) aquarium四、阅读理解(26分)Title: The Secret GardenOnce upon a time, in a small village, there lived a young girl named Mary. She was an orphan, living with her aunt and uncle in their cold, dark house. Mary was not happy with her life, and she often felt lonely and sad.One day, Mary’s uncle gave her a mysterious letter. The letter told her about a secret garden hidden behind an old wall in the village. The garden had been abandoned for many years, but it was said to be full of beauty and magic.Mary decided to explore the garden. She followed the directions in the letter and found the entrance. As she stepped inside, she was amazed by the colorful flowers, the tall trees, and the clear streams. She felt a sense of peace and happiness she had never known before.In the garden, Mary met a friendly robin named Robin. Robin showed her around the garden and told her stories about the magic that once lived there. Mary realized that the garden was a place of healing and joy, and she knew she had to protect it.One day, while exploring the garden, Mary found an old, broken garden gate. She decided to fix it, and with the help of Robin and other friends she made in the garden, she managed to restore the gate. As she pushed the gate open, she felt a warm, comforting breeze and heard a soft whisper.The whisper was from the garden itself, thanking Mary for her kindness and inviting her to continue caring for it. Mary promised to protect the garden,and she knew that her life would never be the same again.Questions:1.What was Mary’s feeling about her life before she found the secret garden?A. HappyB. SadC. NervousD. Excited2.Who showed Mary around the secret garden?A. Her auntB. Her uncleC. A friendly robinD. A mysterious old man3.What did Mary learn about the secret garden?A. It was a place of danger and fearB. It was a place of healing and joyC. It was a place where she could find her lost relativesD. It was a place where she could learn magicAnswers:1.B. Sad2.C. A friendly robin3.B. It was a place of healing and joy五、写作题(16分)Task:Write a short story about a school event that you recently experienced. Describe the event, your feelings about it, and what you learned from it. Your story should be at least 100 words long.Example:Last week, our school held a sports day. The atmosphere was electric as students from different classes participated in various games. I was part of the relay team and felt a mix of excitement and nervousness.The relay race was intense, and our team worked together to hand over the baton quickly. In the end, we came in third place. Although we didn’t win, the experience taught me the importance of teamwork and perseverance. I realized that even though I was nervous, my teammates believed in me, and that made me feel supported.This event also made me appreciate the efforts of the teachers who organized it. They put in a lot of hard work to make sure everything went smoothly. I am grateful for their dedication and the opportunity to take part in such a fun and challenging event.Analysis:The example story follows the task requirements by describing a recent school event (sports day) and the writer’s feelings and learnings from it. The story is structured with a clear beginning, middle, and end, and it includes sensorydetails to make the scene vivid. The writer shows personal reflection by discussing the importance of teamwork and perseverance, and also acknowledges the efforts of the organizers. The word count is above the minimum requirement, and the story is coherent and engaging.。
2024年高二英语数学建模方法单选题30题1.Mathematical modeling often involves collecting and analyzing data. In this process, we need to use some specific tools. What does "analyzing data" mean?A.collecting dataB.presenting dataC.examining dataD.predicting data答案:C。
“analyzing data”的意思是分析数据,也就是对数据进行检查、研究等,C 选项“examining data”( 检查数据)意思最为接近。
A 选项是收集数据;B 选项是呈现数据;D 选项是预测数据。
2.When we do mathematical modeling, we usually start with defining the problem. What's the synonym of "defining the problem"?A.solving the problemB.describing the problemC.ignoring the problemplicating the problem答案:B。
“defining the problem”是定义问题,B 选项“describing the problem” 描述问题)意思最为接近。
A 选项是解决问题;C 选项是忽略问题;D 选项是使问题复杂。
3.In mathematical modeling, we need to make assumptions. What does "make assumptions" mean?A.guess randomlyB.prove somethingC.make suppositionsD.do experiments答案:C。
人教版新课标初中英语单词八年级下册Unit1matter'mt n.问题;事情What'sthematter 怎么了出什么事了sore s:adj.疼痛的;酸痛的haveacold 感冒stomachache n.胃痛;腹痛haveastomachache 胃痛footf t n.脚;足neck nek n.颈;脖子stomach'stmkn.胃;腹部throatθr t n.咽喉;喉咙fever'fi:vn.发烧lielay躺;平躺liedown 躺下restrest v.&n.放松;休息coughkf n.&v.咳嗽X-rayeksre n.X射线;X光toothache'tu:θe k n.牙痛takeone'stemperature量体温headache'hede kn.头痛haveafever 发烧breakbre kn.间歇;休息takebreakstakeabreak休息hurt h:t v.hurt使疼痛;受伤passenger'psndn.乘客;旅客offfadv.&prep.离开某处;不工作;从……去掉getoff 下车toone'ssurprise 使……惊讶的;出乎……意料onto 'ntprep.向;朝trouble'tr bln.问题;苦恼hith tv.hit用手或器具击;打rightaway 立即;马上getinto 陷入;参与herselfh:'selfpron.she的反身代词她自己bandage'bnddn.绷带v.用绷带包扎sicks kadj.生病的;有病的kneeni:n.膝;膝盖nosebleed'no zbli:dn.鼻出血breathebri:ev.呼吸sunburnedsnb:nd adj.晒伤的ourselves 'a'selvzpron.we的反身代词我们自己climber'klam n.登山者;攀登者beusedto习惯于……;适应于……riskrsk n.&v.危险;风险;冒险takeriskstakearisk冒险accident'ksdntn.交通事故;意外遭遇situation'stj'en n.情况;状况kiloki:l =kilogramn.千克;公斤rockr kn.岩石runoutof 用尽;耗尽knifena fn.pl.knives刀cutoff 切除bloodbl dn.血meanmi:nv.meant意思是;打算;意欲getoutof 离开;从……出来importancem'p:tnsn.重要性;重要decisiond'snn.决定;抉择controlk ntr l v.限制;约束;管理;控制beincontrolof 掌管;管理spirit'sprtn.勇气;意志;精神;酒精death deθn.死;死亡giveup 放弃;投降nursen:sn.护士Judy 'du:d朱迪女名Nancy'nns南希女名Mandy'm nde曼迪女名Aron 'ern阿伦·罗尔斯顿Utah 'ju:tɑ:犹他州美国Unit2cleanup 打扫或清楚干净cheertv.欢呼;喝彩cheerup 使变得更高兴;振奋起来giveout 分发;散发volunteer'vln'tv.义务做;自愿做n.志愿者comeupwith 想出;提出主意、计划、回答等putoff 推迟sign sa nn.标志;信号notice'ntsn.通知;通告;注意v.注意到;意识到handout 分发callup 打电话给某人;征召usedto 曾经……;过去……lonely'lnladj.孤独的;寂寞的carefor 照顾;非常喜欢several'sevr lpron.几个;数个;一些strongstradj.强烈的;强壮的feeling'fi:ln.感觉;感触satisfaction'sts'fknn.满足;满意joydn.高兴;愉快owner'nn.物主;主人tryout 参加……选拔;试用journey'd:nn.尤指长途旅行;行程raise 're zv.募集;征集alone'lnadv.独自单独repairr'pev.修理修补fixf ksv.修理;安装fixup 修理;装饰giveaway 赠送;捐赠takeafter 外貌或行为像broken'brknadj.破损的;残缺的wheelwi:ln.车轮;轮子letter'letn.信;函Miss m sn.女士;小姐setup 建立;设立disabledds'ebldadj.丧失能力的;有残疾的makeadifference 影响;有作用blindbla ndadj.瞎的;失明的deaf defadj.聋的imagine'mdnv.想象;设想difficulty'dfkltn.困难;难题open'pnv.开;打开door d:n.门carry'krv.拿;提;扛train tre nv.训练;培训excitedk'satd adj.激动的;兴奋的training'trenn.训练;培训kindness'kandnsn.仁慈;善良clever'klevadj.聪明的;聪颖的understan'nd'stndv.understood理解;领会changetendv.&n.变化;改变interest'ntrstn.兴趣;关注;v.使感兴趣;使关注sirs:n.先生madam'mdmn.夫人;女士Mario'mereo马里奥男名Jimmy'dm吉米男名Unit3rubbish'rbn.垃圾;废弃物takeouttherubbish 倒垃圾foldf ldv.折叠;对折sweepswi:pv.swept扫;打扫floor fl:n.地板messmesn.杂乱;不整洁throwθrv.threw扔;掷allthetime 频繁;反复neither'nae,'ni:eadv.也不shirt:tn.衬衫assoonas 一……就……;尽快pass pɑ:sv.给;递;走过;通过borrow'brv.借;借用lend lendv.借给;借出finger'fgn.手指hate he tv.厌恶;讨厌choret:n.杂务;乏味无聊的工作whilewa lconj.与……同时;当……的时候;而;然而snacksn kn.点心;小吃;快餐stressstresn.精神压力;心理负担wastewe stn.浪费;垃圾v.浪费;滥用inorderto 目的是;为了providepr'vadv.提供;供应anyway'enweadv.而且;加之dependd'pendv.依靠;信赖dependon 依靠;信赖developd'velpv.发展;壮大independence 'nd'pendnsn.独立fairness'fensn.公正性;合理性sinces nsconj.因为;既然prep.conj.&adv.从……以后;自……以来neighbor=neighbour n.邻居takecareof 照顾;处理illladj.有病;不舒服drop dr pv.落下;掉下independent'nd'pendntadj.独立的;自主的fairfeadj.合理的;公平的unfair'n'feadj.不合理的;不公正的Sandy'snd桑迪女名Unit4allow'lav.允许;准许wrongradj.有毛病;错误的What'swrong 哪儿不舒服midnight'mdnatn.午夜;子夜lookthrough 快速查看;浏览guessgesv.猜测;估计deal di:ln.协议;交易bigdeal 重要的事workout 成功地发展;解决getonwith 和睦相处;关系良好relationr'lenn.关系;联系;交往communicationk'mju:nkenn.交流;沟通argue'ɑ:gju:v.争吵;争论cloudkla dn.云;云朵elder'eldadj.年级较长的insteadn'stedadv.代替;反而;却whatever wt'evpron.任何;每一nervous'n:vsadj.焦虑的;担忧的offer 'fv.主动提出;自愿给予proper'prpadj.正确的;恰当的secondly'sekndladv.第二;其次communicatek'mju:nketv.交流;沟通explainks'plenv.解释;说明clearkladj.清楚易懂的;晴朗的copy 'kpv.抄袭;模仿;复制;复印returnr't:nv.归还;回来;返回anymore'enm: adv.常用于否定句和疑问句末再也不;不再member'membn.成员;分子pressure'pren.压力competek m'pi:tv.竞争;对抗opinion'pnjnn.意见;想法;看法skillsk ln.技艺;技巧typical'tpkladj.典型的football'ftb:ln.美式橄榄球;足球cutout 删除;删去quickkw kadj.快的;迅速的;时间短暂的continuekn'tnj:v.持续;继续存在comparekm'pev.比较crazy'krezadj.不理智的;疯狂的pushpv.鞭策;督促;推动developmentd'velpmntn.发展;发育;成长causek:zv.造成;引起usual'ju:ladj.通常的;寻常的inone'sopinion 依……看perhapsp'hpsadv.可能;大概;也许Cathy 凯茜女名Taylor 泰勒姓Unit5rainstorm 'renst:rmn.暴风雨alarm'lɑ:mn.闹钟gooff闹钟发出响声beginb'gnv.began开始heavily'hevladv.在很大程度上;大量地suddenly'sdnladv.突然;忽然pickup=pickupthephone接电话strangestrendadj.奇特的;奇怪的stormst:mn.暴风雨wind wnd,wandn.风light la tn.光;光线;光亮report v.&n.报道;公布area 'ern.地域;地区woodw dn.木;木头window'wndn.窗;窗户flashlight'fllatn.手电筒;火炬matchmtn.火柴beat bi:tv.敲打;打败against'genst,'genstprep.倚;碰;撞asleep'sli:padj.睡着fallasleep 进入梦乡;睡着diedown 逐渐变弱;逐渐消失riseraz v.&n.升起;增加;提高fallen'f:lnadj.倒下的;落下的apart'pɑ:tadv.分离;分开havealook 看一看icy'asadj.覆盖着冰的;冰冷的kidk dv.开玩笑;欺骗n.小孩realize'rlazv.理解;领会;认识到makeone'sway 前往;费力地前进passage'psdn.章节;段落pupil'pju:pln.学生completelykm'pli:tladv.彻底地;完全地shockedktadj.惊愕的;受震惊的silence'salnsn.沉默;缄默;无声insilence 沉默;无声recently adv.不久前;最近takedown 拆除;往下拽;记录terrorist'terrstn.恐怖主义者;恐怖分子date 'de tn.日期;日子tower'tan.塔;塔楼atfirst 首先;最初truth tru:θ实情;事实Allen'ln艾伦姓MartinLutherKing 马丁·路德·金Alabama'l'bm阿拉巴马州美国AnimalHelpline 动物保护热线WorldTradeCenter 世贸大楼美国纽约Unit6shootu:tv.shot射击;发射stonest nn.石头weakwi:kadj.虚弱的;无力的godg dn.神;上帝remindr'mandv.提醒;使想起bitb tn.一点;小块alittlebit 有点儿;稍微silly 'sladj.愚蠢的;不明事理的insteadof 代替;反而object'bdkt'b'dektn.物体;物品hide ha dv.隐藏;隐蔽tailte ln.尾巴magic'mdkadj.有魔力的;有神奇力量的stick st kn.棍;条excitek'satv.使激动;使兴奋Western'west nadj.西方国家的;尤指欧美的;西方的w可以小写onceuponatime 从前stepsister'stepsstn.继姐妹prince'pr nsn.王子fallinlove 爱上;喜欢上fitf tv.适合;合身couple'k pln.尤指夫妻;两人;两件事物smilesmal v.&n.笑;微笑marry'mrvt.结婚getmarried 结婚gold g ldn.金子;金币adj.金色的emperor'emprn.国王silks lkn.丝绸;丝织物underwear'ndwen.内衣nobody'nbdpron.没有人n.小人物stupid'stju:p dadj.愚蠢的cheatt i:tv.欺骗;蒙骗n.骗子stepmother'step'men.继母wife wa fn.妻子;太太husband'hzbndn.丈夫wholeh ladj.全部的;整体的scenesi:nn.戏剧或歌剧的场;场景moonlight'mu:nla tn.月光shineanv.shone发光;照耀brightbra tadv.光两地;明亮地adj.明亮的;光线充足的groundgra ndn.地;地面leadli:dvled 带路;领路voicev sn.声音bravebre vadj.勇敢的;无畏的Claudia'kl:dj克劳迪娅女名JourneytotheWest 西游记theMonkeyKing 美猴王SleepingBeauty 睡美人Cinderella'snd'rel灰姑娘LittleredRidingHood 小红帽HanselandGretel 韩塞尔与葛雷特糖果屋Unit7squareskwen.平方;正方形meter=metre n.米;公尺deepdi:padj.深的;纵深的desert'dezt,d'z:tn.沙漠population'ppj'lenn.人口;人口数量Asia 'en.亚洲feelfree 可以随便做某事tour tn.旅行;旅游tourist'trstn.旅行者;观光者wall w:ln.墙amazing'mezadj.令人大为惊奇的;令人惊喜或惊叹的ancient'enntadj.古代的;古老的protectpr'tektv.保护;防护wide wa dadj.宽的;宽阔的asfarasIknow 就我所知achievement'ti:vmntn.成就;成绩southwestern adj.西南的;西南方向的thick θ kadj.厚的;浓的includen'klu:dv.包括;包含freezing'fri:zadj.极冷的;冰冻的conditionkn'dnn.条件;状况takein 吸入;吞入体内succeeds k'si:dv.实现目标;成功challenge v.&n.挑战;考验inthefaceof 面对问题、困难等achieve'ti:vv.达到;完成;成功forcef:sn.力;力量nature'netn.自然界;大自然eventhough=evenif 即使;虽然ocean'nn.大海;海洋thePacificOcean 太平洋cm=centimetercentimeter 厘米weighwev.重量是……;称……的重量birth b:θn.出生;诞生atbirth 出生时upto 到达某数量、程度等;至多有;不多于adult'dltadj.成年的;成人的n.成人;成年动物bamboo b m'bu:n.竹子endangeredn'dend d adj.濒危的researchrs:t n.&v.研究;调查用作名词时,重音可放在第一个音节keeper'ki:pn.饲养员;保管人awake'wekadj.醒着excitementk'satmntn.激动;兴奋walkinto 走路时撞着fallover 绊倒illness'lnsn.疾病;病remainingrmen adj.遗留的;剩余的orso 大约artworkɑ:tw:k n.图片;插图wildwa ldadj.野生的government'gvnmntn.政府;内阁whalewe ln.鲸oilln.油;食用油;石油protectionpr'teknn.保护;保卫hugehju:dadj.巨大的;极多的TenzingNorgay 丹增·诺尔盖EdmundHillary 埃德蒙希拉里JunkoTabei 田部井淳子Qomolangma 珠穆朗玛峰theNile 尼罗河theCaspianSea 里海世界最大的咸水湖theSahara 撒哈拉沙漠theYangtzeRiver 长江theYellowRiver 黄河theMingDynasty 明朝theMingGreatWall 明长城theHimalayas 喜马拉雅山脉theAmazonRiver 亚马逊河ChengduResearchBase 成都研究基地Unit8treasure'tren.珠宝;财富island'alndn.岛fullof 满是……的;有大量的;有丰富的classic'klskn.经典作品;名着pagepedn.书刊或纸张的页,面,张hurry'hrv.匆忙;赶快hurryup 赶快;急忙做某事duedju:adj.预期;预定shippn.船tooltu:ln.工具gung nn.枪;炮markmɑ:kn.迹象;记号;分数v.做记号;打分sand s ndn.沙滩;沙cannibal'knbln.食人肉者towardst'w:dzprep.朝;向;对着landl ndn.陆地;大地fiction'fknn.小说sciencefiction 科幻小说或影片等technologytek'nldn.科技;工艺Frenchfrent法语popp pn.流行音乐;流行乐曲rockr kn.摇滚乐bandb ndn.乐队countrymusiccountry 乡村音乐foreverf'revadv.永远abroad'br:dadv.在国外;到国外actually'ktjladv.真实地;事实上eversince 自从fanf nn.迷;狂热爱好者southern'senadj.南方的modern'mdnadj.现代的;当代的successs k'sesn.成功belongb'lv.属于;归属oneanother 互相laughterlɑ:ftn.笑;笑声beauty'bju:tn.美;美丽million'mljnnum.百万record'rek:d,r'k:dn.唱片;记录v.录制;录音introduce 'ntr'dju:sv.介绍;引荐linela nn.行;排Alex'lks亚历克斯男名GarthBrooks 加思·布鲁克斯theBeatles 披头士乐队英国TreasureIsland 金银岛AliceinWonderland 爱丽丝梦游仙境LittleWoman 小妇人OliveTwist 雾都孤儿RobinsonCrusoe 鲁滨逊漂流记TomSawyer 汤姆·索娅历险记HarryPotter 哈利·波特Nashville'nvl纳什维尔美国田纳西州府Tennesseeten'si:田纳西州美国CountryMusicHallofFameMu 乡村音乐名人堂博物馆Unit9Amusement'mju:zmntn.娱乐;游戏Amusement park 游乐场somewhere'smweadv.在某处;到某处camera'kmrn.照相机;摄影机;摄像机inventionn'vennn.发明物inventn'ventv.发明;创造unbelievablenb'li:vbladj.难以置信的;不真实的progress'prgres,pr'gresn.进步;进展rapid'rpdadj.迅速的;快速的unusualn'ju:ladj.特别的;不寻常的toilet'tltn.坐便器;厕所encouragen'krdv.鼓励social's ladj.社会的peaceful'pi:sf ladj.和平的;安宁的teaart 茶艺performancep'f:mnsn.表演;演出perfect'p:fkt,'p:fektadj.完美的;完全的teaset 茶具itselft'selfpron.it的反身代词它自己collectk'lektv.收集;采集acoupleof 两个;一对;几个German'd:mnadj.德国的;德语的;德国人的n.德语;德国人themeθi:mn.主题ridera dn.供乘骑的游乐设施;短途旅程province'prvnsn.省份thousand'θazndnum.一千thousandsof 数以千计的;许许多多的ontheonehand...ontheotherhand...一方面……另一方面……safese fadj.安全的;无危险的simply'smpladv.仅仅;只;不过fearfr v.&n.害怕;惧怕whether'weeconj.不管……;还是;或者……或者;是否Indian'ndnadj.印度的n.印度人Japanese'dp'ni:zadj.;日本的;日本人的;日语的n.日本人;日语foxf ksn.狐狸allyearround 全年equator'kwetn.赤道wheneverwen'evconj.在任何……时候;无论何时springsprn.春天mostly'mstladv.主要地;通常locationl'kenn.地点;位置NationalScienceMuseum 国家科学博物馆InternationalMuseumofToile 国际厕所博物馆HangzhouNationalTeaMuseum 杭州国家茶博物馆DonaldDuck 唐老鸭Disneyland'dznlnd迪斯尼乐园DisneyCruise 迪斯尼游轮theTerracottaArmy 兵马俑theBird'sNest 鸟巢Singapore'sg'p:新加坡SoutheastAsia 东南亚NightSafari 夜间动物园Unit10yard jɑ:dn.院子yardsale 庭院拍卖会sweetswi:tadj.甜蜜的;甜的;含糖的memory'memrn.记忆;回忆centsentn.分;分币toytn.玩具bear ben.熊maker'mekn.生产者;制订者breakmaker 面包机scarfskɑ:fn.围巾;披巾;头巾softs ftadj.软的;柔软的softtoy 软体玩具;布绒玩具checktek v.&n.检查;审查checkout 查看;观察boardb:dn.板;木板boardgame 棋类游戏junior'du:njadj.地位或职位、级别低下的juniorhighschool 初级中学clearklv.清理;清除clearout 清理;丢掉bedroom'bedr mn.卧室nolonger 不再;不复ownnv.拥有;有railway'relwen.铁路;铁道partpɑ:tv.离开;分开partwith 放弃;交出尤指不舍得的东西certain's:tnadj.某种;某事;某人asfor 至于;关于honest'nstadj.城市的;老实的tobehonest 说实在的whilewa ln.一段时间;一会儿truthful'tru:θf ladj.诚实的;真实的hometownhom'tann.家乡;故乡nowadays'nadezadv.现今;现在;目前searchs:t v.&n.搜索;搜查among'mprep.在其中;……之一crayon'kre nn.彩色铅笔或粉笔、蜡笔shameemn.羞耻;羞愧;惭愧regardr'gɑ:dv.将……认为;把……视为countka ntv.数数century'sentrn.百年;世纪accordingto 依据;按照opposite'pztprep.与……相对;在……对面adj.对面的;另一边的especiallys'peladv.尤其;特别;格外childhood'taldhdn.童年;幼年considerkn'sdv.注视;仔细考虑closeto 几乎;接近holdh ldv.held,held拥有;抓住。
On the Relation between SAT and BDDs for Equivalence Checking Sherief Reda1 Rolf Drechsler2 Alex Orailoglu1 1Computer Science & Engineering Department 2Institute of Computer ScienceUniversity of California, San Diego University of BremenLa Jolla, CA, 92093 28359 Bremen, GermanyAbstractState-of-the-art verification tools are based on efficient operations on Boolean formulas. Traditional manipulation techniques are based on Binary Decision Diagrams (BDDs) and SAT solvers. In this paper, we study the relation between the two procedures and show how the number of backtracks obtained in the Davis-Putnam (DP) procedure is linked to the number of paths in the BDD. We utilize this relation to devise a method that uses BDD variable ordering techniques to run the DP procedure. Experimental results confirm that the proposed method results in a dramatic decrease in the number of backtracks and in the time needed to prove the Boolean satisfiability problem as well.1 IntroductionBoolean Satisfiability (SAT) has received increased attention as a promising technique for Automatic Test Pattern Generation (ATPG) and equivalence checking [1], [2]. Virtually all SAT techniques rely on the use of the Davis-Putnam procedure (DP) [3], [4] to explore the search tree. If there is a pattern that differentiates the circuits under verification, then DP will eventually find it or prove that the SAT formula is unsatisfiable. Numerous techniques have been proposed to reduce the search tree. Some of these techniques such as iterated global implications [2] and recursive learning [5] are applied as a preprocessing step, while others are applied during the course of the application of the DP procedure. For example, clause recording [6] and cache-based backtracking [7] are used to avoid conflicts. An alternative research trend focuses on identifying variable orderings techniques that minimize the number of backtracks executed by the DP procedure to find a satisfying assignment1. The effectiveness of these techniques is sharply limited though in case the formula is unsatisfiable. On the other hand, Binary Decision Diagrams (BDDs), as introduced in [9], have been traditionally used to solve the equivalence checking problem due to their canonical property. However, it is this requirement for canonicity that makes BDDs inefficient in representing certain classes of functions. For example, integer multipliers have displayed exponential memory requirements for any variable ordering [10].1 An excellent survey can be found in [8]. There has been increased interest in techniques that integrate SAT and BDDs to reduce the time and space needed to solve the equivalence checking problem [11], [12]. Though it has been noted that SAT and BDDs represent the same entity [7], there is little understanding of the relation between the two procedures and how the techniques of one domain can be utilized in the other.In this paper we attempt to provide an improved understanding of the relation between these two procedures. We view the equivalence checking problem as a search in the decision trees of the two circuits for a path that leads to the terminal 1(0) in one but leads to the 0(1) terminal in the other. From this perspective, it would be desirable to decrease the number of paths, thus reducing the number of backtracks and time needed to solve the problem. We propose a dynamic variable ordering technique to run the DP procedure. The technique is geared towards minimization of the number of backtracks needed to prove the unsatisfiability of the CNF formula that results from proving the equivalence of two circuits. We compare our method with the greedy variable ordering of TEGUS [2]. Experimental results verify that the proposed approach results in a dramatic decrease in the number of backtracks and time needed to solve the problem.The organization of the paper is as follows. Section 2 introduces the necessary preliminaries for the material in this paper. Section 3 presents the theoretical foundations for the relation between the DP procedure and BDDs. Section 4 proposes a dynamic BDD-based variable ordering technique for the DP procedure. Experimental results are given in Section 5, followed up by conclusions in Section 6.2 Preliminaries2.1 Binary Decision DiagramsA Binary Decision Diagram (BDD) is a rooted directed acyclic graph with two terminal nodes that are referred to as the 0-terminal and the 1-terminal. Every non-terminal node is associated with a primary input variable such that it has two outgoing edges called the 0-edge corresponding to assigning the variable a false truth value, and the 1-edge corresponding to assigning the variable a true truth value. An Ordered Binary Decision Diagram (OBDD) is a BDD such that the input variables appear in a fixed order on all the paths of the graph, and no variable appears more thanonce in the path. A Reduced Ordered BDD (ROBDD) is an OBDD that results from the repeated application of the following two rules:1. Eliminate all redundant nodes whose edges point to the same node.2. Share all equivalent sub-graphs.Figure 1 illustrates an example of an ROBDD where the solid edges denote the 1-edges and the dashed edges denote the 0-edges. In the following treatment, only reduced ordered BDDs are considered and for short we denote them as BDDs.2.2 The Davis-Putnam ProcedureA CNF formula ϕ is a set of clauses where each clause is the disjunction of a number of literals where a literal is a variable or its negation. Since each logic gate can be represented by a number of clauses [1], a CNF formula of a logic circuit is the conjunction of the CNF formulas of all the gates. A CNF formula is satisfiable if at least one set of assignments to the variables of the formula makes it evaluate to true.Virtually all SAT solvers use the Davis-Putnam (DP) procedure in their core [3], [4] in order to find a satisfying assignment for the formula or conversely to prove the formula unsatisfiable. The DP procedure performs a backtracking depth-first search in the space of all truth assignments to find a satisfying assignment for the CNF formula. The performance of backtracking is greatly improved by employing unit clause propagation: whenever a unit clause arises, the variable occurring in that clause is assigned the truth-value that satisfies the clause. The formula is thereupon simplified which may lead to new unit clauses. Figure 2 outlines the DP procedure. The procedure returns true in case the CNF formula is satisfiable, false otherwise.3 On the relation between the DP procedure and BDDsIn this section we study the relation between the DP procedure and the BDD representation of the same circuit. We first formalize the various properties of the CNF formulas generated from multi-level combinational logic circuits and show how these properties allow a measure of flexibility in the search for a satisfying assignment to the formula. Furthermore, we prove the relation between the number of backtracks obtained using the DP procedure and the number of paths in the corresponding BDD. This relation allows the calculation of optimal lower bounds for the number of backtracks needed to prove the equivalence of two equivalent circuits. We start by introducing some notation to provide a concise basis for the formalization of the derived results.Let ϕbe a CNF formula, and V(ϕ) denote the set of variables that ϕ depends on. A clause c i∈ϕ is satisfied if there is some assignment to its literals such that the disjunction of the literals evaluates to true. The CNF formula ϕ is satisfied if there is a truth assignment to V(ϕ) such that every clause c i∈ϕ is satisfied.Let C-CNF denote the set of CNF formulas generated from multi-level combinational logic circuits. Let C ∈ C-CNF be a multi-level combinational circuit, and let f be the underlying Boolean function of C. Since the logic value of all the internal and output signals of C can be derived from the values of the primary inputs, we consider the support of f to be the primary inputs only. We denote the set of primary inputs of ϕby P(ϕ). In addition, we introduce the variable χto reference the primary output of the circuit. The relation between ϕ, P(ϕ) and V(ϕ) is given by the next lemma.Lemma 1 If ϕ∈ C-CNF, then it is possible to find a set of variables P(ϕ)⊂V(ϕ) such that ϕ can be satisfied by only splitting on the variables of P(ϕ) in the DP procedure. Proof Since the internal nodes of a multi-level logic circuit are functions of the primary inputs, it is possible to determine their assignment given some assignment on the set of primary input variables, P(ϕ).the search of a satisfying assignment to the whole CNF formula. This subset of currently assigned primary inputs shall be denoted by S, and their truth assignments by A s. The restricted Boolean function that results from the application of A s to ϕ shall be denoted by f As.In order to avoid fruitless searches, the DP procedure should avoid assigning truth-values to variables that can make no contribution to the satisfiability of the formula.This notion is captured by the following definition. Definition 1 If A s is the truth assignment of a set S⊆P(ϕ) and v∈P(ϕ) but v∉S then v is said to be redundant under A s if ∂ f As /∂v = 0.Definition 1 simply states that if the restricted Boolean function f As is insensitive to the change in v, then there is no point in assigning v a truth value. This notion allows us to tailor down the satisfiability of C-CNF formulas as given by the following theorem.Theorem 1 A CNF formula ϕ∈ C-CNF is satisfied under a truth assignment A s of a set S⊆P(ϕ) if ∀v∈(P(ϕ)-S): ∂ f As /∂v = 0.Proof If ∀v∈(P(ϕ)-S): ∂f(A s)/∂v= 0, then no truth assignment to any element that belongs to (P(ϕ)-S) can change the function f(A s).Since all variables in S areassigned truth values under A s and (P(ϕ)-S) ∪S = P(ϕ), then it follows from Lemma 1 that ϕis satisfied.Theorem 2 defines our notion of satisfiability for CSAT. In addition, it opens the possibility for the primary output variable χto be assigned a truth-value while there exist clauses that are not evaluated to true and have some remaining unassigned literals. Example 1 illustrates such a case.Example 1 The CNF formula of the circuit in Figure 3 is ϕ= (¬a + d) ⋅ (¬b + d) ⋅ (a + b + ¬d) ⋅ (c + ¬z) ⋅ (d + ¬z) ⋅(¬d + ¬c + z). In this example, P(ϕ) = {a, b, c}, χ = z and under the partial assignment A s = {c = 0}, where S = {c}, z is assigned the truth value false and ϕ = (¬a + d) ⋅ (¬b + d) ⋅ (a + b + ¬d). We notice that under A s both ∂f As/∂a and ∂f As/∂b equal zero, since the function output value is already determined. Furthermore, there exists a truth assignment to the set of variables P(ϕ)-S that satisfies the remaining clauses. This truth assignment is however of no interest since the primary output has already been assigned a truth-value. As an illustration for Definition 1, if A s = {a = 1} where S= {a} then ϕ= (c+ ¬z) ⋅(¬c+ z) and ∂f As/∂b = 0, yet z is not assigned a truth value. Thus, ϕ is not satisfied but b is redundant under A s.We notice that Rule 1 in Section 2.1 for BDD reduction is equivalent to Definition 1 in the CSAT context and thus tracing a path from the root to the 1-terminal or 0-terminal in the BDD of circuit C is equivalent to finding a satisfying assignment to the CNF formula ϕof C using the same variable ordering of the path in the BDD. This notion is captured in the following lemma.Lemma 2Given a BDD βand a CSAT formula ϕfor some logic circuit C, then under a variable ordering π and a truth assignment Aπon a certain path of βto the terminal, ϕ is satisfiable using the same variable ordering and truth assignment.Proof Assume the set of primary inputs is P. Then we can partition P into two sets, S and T, such that S contains all the variables that appear in πand T contains all the remaining variables. By Rule 1 of section 2.1, T is the set of all redundant nodes. But due to the equivalence of Rule 1 and Definition 1, it follows from Theorem 1 that ϕissatisfied.for splitting in the DP procedure is the same as in the corresponding BDD, then considering an alternative path in the BDD leads to a backtrack in the DP procedure. Thus, the number of paths exceeds the total number ofbacktracks exactly by 1.The importance of Theorem 4 is that it allows benchmarking any variable ordering strategy for the DP procedure against an optimal lower bound. We now develop a variable ordering heuristic for the DP procedure that tries to trace the same variable ordering for every path in the corresponding minimal path BDD of the circuit.4 Dynamic variable ordering strategy for the DP procedureFrom the previous section, we conclude that the variable ordering strategy should differ for every path of the decision tree, and furthermore result in no splitting on a redundant variable under the current partial assignment. In this section, we propose a structural method that avoids redundant splitting and tries to make the fewest possible splittings to satisfy ϕ. The method is based on the following theorem.Theorem 5 If a bounded gate lies on every path from the primary output χ to the unassigned primary input v∈(P(ϕ)-S) under a current partial assignment A s for a set S⊂P(ϕ), then ∂f As/∂v= 0.Proof The existence of a bounded gate (a gate with a specified output) in every path to χ implies that no value assigned to v can affect the function of the circuit since these bounded gates will suppress the propagation of the logic value. Thus, since f(A s) remains unchanged under any assignment to v, ∂f As/∂v=0.Table 1: Comparing Greedy search to BDD-based variable ordering for the DP procedure.procedure, we have to check that every path results in the same output assignment in both circuits. Applying the previous procedure of weight calculations to minimize the number of paths being compared, we trace the different paths of the BDD of the circuit in figure 4.a in the manner shown below.From the initial weights given in figure 4.a, we split on x3 since it has the highest weight. Suppose x3 is assigned the true value. Then by unit clause propagation, gate h becomes bounded to the truth value false. The weight calculation procedure is executed again but this time by setting the weights of bounded gates to zero. Figure 4.b illustrates the new weights. Next, x1, x2 or x3 can be chosen to split on; the resultant search tree will always produce identical number of backtracks. Notice that bounded gates are marked with a ‘*’ in the corresponding figure. After finishing this half of the decision tree, x3is flipped and assigned to false. The new calculated weights are shown in Figure 4.c. Since x4 has the highest weight, we split on x4 thus reaching the terminals.We now construct the minimum path BDD corresponding to this circuit as shown in Figure 4.d. We notice in the BDD that the splitting choices made by the previous procedure traverse this BDD in exact ordering for each path, thus producing the minimal number of backtracks, 5, corresponding to the minimal number of paths, 6.As was just illustrated, the proposed method has produced optimal results for the proposed example; however, the method is not in general optimal since it depends on the structure of the circuit. As shall be demonstrated in the next section, the proposed method is capable of achieving near optimal results.5 Experimental ResultsIn this section, we present experimental results for our proposed approach. The experiments have been carried out on a PC with an Intel Pentium 233 Mhz processor and 64MB of physical memory. We have used TEGUS [2] as a SAT solver and the CUDD [14] decision diagram package. In our experiments we consider the performance of the proposed approach to verify the equivalence of the ISCAS’85 benchmark circuits [15] against their non-redundant version. We benchmark our approach against the greedy search approach of TEGUS. Table 1 gives the results of such a comparison. Column 1 lists the circuit name. Column 2 provides the name of the output under verification. Columns 3 & 4 give the number of backtracks and time needed to prove the output using the TEGUS approach. Columns 5 & 6 give the number of backtracks and time needed to prove the output using the proposed approach. The possible “Abort” notation in columns 3 & 5 denotes reaching the 20 million backtrack threshold without reaching a successful resolution; the subsequent time columns in that case denote the time needed to reach this limit. Columns 7 & 8 report the percentage decrease in the number of backtracks and time, respectively. Column 9 provides the near minimal number of paths in the corresponding BDD. In obtaining the number of paths, we only consider a subspace of the possible variable orderings. We compare the number of paths that result from sifting [16] the corresponding BDD to a minimum size and picking the minimal path. For space considerations, we consider only three outputs from each circuit.Comparing the greedy approach to the proposed variable ordering strategy, we observe that the proposed approachTEGUS Greedy Search Proposed Approach Difference Minimal Path BDD Circuit OutputNameBacktracks Time(seconds) Backtracks Time(seconds)Backtracks Time #Paths370gat Abort 771.00 943200 185.00 95.3% 76.01% 894606 432gat Abort 770.00 816012 235.00 95.9% 69.48% 798906 c0432329gat 1646605 22.50 81912 5.94 95.0% 73.60% 57513 od1 Abort 1686.00 Abort 10351.00 - - 20000000 od18 Abort 1685.00 Abort 10245.00 - - 23000000 c0499od31 Abort 1691.00 Abort 10627.00 - - 23000000 864 649741 12.30 164656 27.50 74.7% -123.58% 89937 850 37225 0.60 24171 3.45 35.1% -475.00% 21981 c0880874 Abort 498.00 1083156 278.00 94.6% 44.18% 532793 1353 Abort 1921.00 Abort 8501.00 - - 21000000 1354 Abort 1892.00 Abort 8427.00 - - 23000000 c13551355 Abort 1984.00 Abort 8602.00 - - 2300000057 Abort 718.00 147457 11.90 99.3% 98.34% 13422160 Abort 1708.00 28161 20.10 99.9% 98.82% 26638 c190866 Abort 2058.00 14249 10.40 99.9% 99.49% 12638399 24550 0.73 4528 1.34 81.6% -83.56% 1636 384 6107715 652.00 70997 57.20 98.8% 91.23% 65535 c3540387 1582929 213.00 17312 17.00 98.9% 92.02% 16456 688 Abort 300.00 23974 13.00 99.9% 95.67% 13919843 Abort 3383.00 211181 162.0098.9% 95.21% 103569C5315818 85989 3.50 6537 2.18 92.4% 37.71% 2489 373 16 0.01 10 0.01 37.5% 0.00% 10 376 40952 1.30 15416 4.93 62.4% -279.23% 7152 C7522359 2474096 114.00 585584 285.00 76.3% -150.00% 196592 2223 157 0.01 102 0.01 35.0% 0.00% 102 3895 174315 12.20 106423 108.00 38.9% -785.25% 109668 c62884591 2794411 255.00 1705027 2689.00 39.0% -954.51% 1793496results on the average in 90% decrease in the number of backtracks. The time needed to complete the backtracks varies from reduction in 13 cases with an average of 70% decrease to increases in about 7 cases with an average increase of about 4 times. While at first glance the time results look inconclusive, it can be easily noted that the increases are essentially associated with low-backtrack, provable outputs, since in these cases the recurring weight assignment costs cannot be amortized across the small number of backtracks. Our approach greatly improves the performance of large search tree cases, the main focus of practical interest. We also notice that within the limit of 20 million backtracks, TEGUS fails to complete on 7 outputs while the proposed approach proves them in a relatively low number of backtracks.As proved in Section 3, the minimum number of paths that can be obtained from the corresponding BDD is a lower bound on the number of backtracks that can be obtained in the DP procedure. The number of paths provides an ability to benchmark various ordering techniques and also provides an insight on the performance of the DP procedure. For example, the huge number of paths in case of the c0499 & c1355 circuits (they are functionally equivalent) suggests that they are hard-to-prove outputs using the DP procedure. In addition, in circuits, like the c6288, where the variation of the number of paths with respect to the variable ordering is small, the dynamic weight assignment technique constitutes a time consuming step with respect to the overall time, as the number of backtracks varies slightly with respect to the variable splitting strategy2.6 ConclusionsIn this paper we have studied the relation between the search tree of the DP procedure and the BDD of the corresponding function, establishing that the number of paths from the root node to the terminals of the BDD is directly related to the number of backtracks needed to prove the equivalence of two functionally equivalent circuits. This relation introduces the ability to calculate an optimal lower bound on the number of backtracks needed to prove the equivalence checking problem. In addition, this relation has led to the conclusion that the capture of the variable ordering of the minimal path BDD in the DP procedure implies a reduction in the number of backtracks needed to prove the problem. In order to exploit this relation, we have devised a variable ordering technique for the DP procedure that through experimental results has exhibited superior performance in terms of the number of backtracks and time needed to prove the equivalence problem. The relation between the two procedures offers novel ways of tight integration of different prover approaches in a verification tool.2 After numerous experiments, we concluded that there is no apparent relation between the number of nodes and paths in a given BDD. References[1] T. Larrabee, “Test Pattern Generation using Boolean Satisfiability,” IEEE Trans. on Computer Aided Design, Vol. 11, No. 1, pp. 4-15, January 1992.[2] P. R. Stephan, R. K. Brayton, and A. Sangiovanni-Vincentelli, “Combinational Test Generation Using Satisfiability,” Technical Report UCB/ERL M92/112, Dept. of EECS, Univ. of California, Berkeley, Oct., 1992.[3] M. Davis, G, Logemann, and D. Loveland, “A Machine Program for Theorem Proving,” Communications of the ACM, (5):394-397, July 1962. [4] M. Davis, and H. Putnam, “A Computing Procedure for Quantifier Theory,” Communications of the ACM, (7):201-215, 1960.[5] J. Silva, T. Glass, “Combinational Equivalence Checking Using Boolean Satisfiability and Recursive Learning,” In Proc. of Design Automation, Test in Europe Conference, pp. 145-149, 1999.[6] J. Silva, “An Overview of Backtrack Search Satisfiability Algorithms,” in Fifth International Symposium on AI and Mathematics, January 1998. [7] M. Prasad, P. Chong, K. Keutzer, “Why is ATPG easy?” In Proceedings of the 36th Design Automation Conference, pp. 22-28, 1999.[8] J. Gu, P. W. Purdom, J. Franco, and B. W. Wah, in "Satisfiability Problem: Theory and Applications," DIMACS Series in Discrete Mathematics and Theoretical Computer Science, American Mathematical Society, pp. 19-152, 1997.[9] R. E. Bryant, “Graph Based Algorithms for Boolean Function Manipulation,” IEEE Trans, in Computers, Vol. C-35, No. 8, pp. 677-691, August 1986.[10] R. E. Bryant, “On the Complexity of VLSI Implementations and Graph Representations of Boolean Functions with Application to Integer Multiplication,” IEEE Transactions on Computers, Vol. 40, No. 2, pp. 205-213, Feb. 1991.[11] J. Burch, V. Singhal, “Tight Integration of Combinational Verification Methods,” ACM/IEEE Int. Conference on Computer-aided Design 1998, pp. 570-576, San Jose, CA, USA.[12] S. Reda, A. Salem, “Combinational Equivalence Checking using Binary Decision Diagrams and Boolean Satisfiability,” In Proc. of Design Automation, Test in Europe Conference, pp. 122-126, 2001.[13] S. Minato, Binary Decision Diagrams and applications for VLSI CAD, Kluwer Academic Publishers, 1996.[14] F. Somenzi, CUDD: Colorado University Decision Diagram Package. ftp:///pub.[15] F. Brglez and H. Fujiwara, “A Neural Netlist of 10 Combinational Benchmark Circuits and a Target Translator in Fortran,” In Intl. Symp. on Circuits and Systems, 663-698, June 1985.[16] R. Rudell, “Dynamic Variable Ordering for Ordered Binary Decision Diagrams,” In Proc. of Int. Conf. On Computer Aided Design, pp. 42-47, 1993。