Assignment
- 格式:doc
- 大小:62.50 KB
- 文档页数:6

在撰写一篇关于“assignment”词根词缀的文章之前,让我们先深入了解一下这个主题。
我们需要了解“assignment”是什么意思,以及它的词根和词缀分别代表什么含义。
接下来,我们将探讨“assignment”在不同领域和语境中的应用,以及它所涉及的深层含义和广泛影响。
我们会回顾和总结所学内容,以便全面和深刻地理解“assignment”这一主题。
1. “assignment”是什么意思?“assignment”这个词源自拉丁词根“assignare”,意为“指派”或“分派”。
在英文中,这个词通常表示指定特定的任务、工作或责任给某人,也可以指分配特定的任务或活动。
“assignment”还可以指代布置的作业、任务或项目。
2. 词根词缀含义解析在“assignment”这一词中,“assign-”是词根,代表指派或分派的意思。
而后缀“-ment”则表示名词形式,将动词转化为名词,表示行为、结果或状态。
我们可以理解“assignment”为指派的行为或状态,或指派所得到的任务、职责或作业。
3. “assignment”在不同领域和语境中的应用在教育领域,“assignment”通常指代老师布置给学生的作业或任务。
而在职场中,“assignment”可能指派给员工的特定责任或工作任务。
在法律上,“assignment”也具有特定的含义,指代将权利或债务转让给他人的行为。
在项目管理、军事领域等领域中,“assignment”也有着特定的应用和含义。
4. 个人观点和理解在我看来,“assignment”不仅仅是简单的任务分配,它背后蕴含着领导能力、责任担当和团队合作的重要意义。
在现代社会中,“assignment”更多地呈现为一种团队协作和角色分工的体现,是一种高效管理和资源配置的重要手段。
5. 总结和回顾通过本文的探讨,我们对“assignment”这一主题有了全面、深刻和灵活的理解。
我们了解了它的词根词缀含义、不同领域和语境中的应用,以及个人观点和理解。

英文Assignment的写作细节(别说留学生天天就是花天酒地的玩,我们比你们要辛苦)来源:王嘉煊Sylvia的日志我们的assignment通常分为两种形式,一是essay,一是report。
二者在形式上有所差别,但大体相同。
一篇assignment上面会对写成essay还是report格式作出明确要求。
在阅读题目时,请尽量仔细相同点:1、字体:Times New Roman,字号:小四,行距:1.5倍。
请有写作之前就把这些格式调好,以避免写好后再调会出现一些意想不到的情况。
2、段与段之间隔行。
每段不要求像中文写作那样空两格,而是直接顶格写。
下面还有一些相同点,我在两种文体分开讨论时,再涉及。
区别:Essay:Essay的写作相对report要简单一些。
通常只包括三个部分,Introduction, Main Body, Conclusion. Introduction 包括topic的背景介绍和文章要解决的主要问题。
一般占总字数的10%左右。
Main Body是主体部分,占总字数80%左右。
如果题目中作了具体要求,就根据题目提到的几个方面来逐一讨论就可以了。
有的题目没有作具体要求,就根据自己的构思来写。
但要求有逻辑性。
Conclusion也是占10%,在这一段里把文章中的主要观点用一到两句话概括出来。
Essay 可以不写题目,不要把小标题加粗。
Reference的写作是两种形式都要涉及的,我放在最后来详细说。
Report:它的写法大体上和essay差不多,但要求要严格一些。
第一:标题页:包括标题和executive summary. 在Executive summary中是对文章的摘要。
这个大家都知道怎么写我就不多说了。
这两个东西一般是单独占一页第二:主体部分。
Report的主体部分,前三个和essay差不多,只是在conclusion后还有一部分就是recommendations.是对提出的问题的建议。

Assignment(essay)和presentation(report)是每个留学生必须要经历的残酷生存赛...熬不过的assignmentAssignment一般都是会换算比例记入最后module的分数的。
首先是essay,report这类学术性的。
国外的论文要求那是相当严格,特别是引用的规则。
论文中提到的每一个观点都需要各种理论学说来支持。
而这些theory的来源要求也很高,如果你想要得高分,不能是随便一篇文章里的某一个所谓的expert说的,必须是相关领域相关专家发表在相关学术期刊上的,经过了Peer Review同行审查的最佳。
除了theory,必要的时候各种data以及report结果也需要引用,用于支撑你文章的观点。
所以,我们在写essay的时候,需要大量引用evidence来支撑文章,而每一个evidence都必须被标明作者以及年份,在文章中为citation,在文末为reference。
如果没有标明,则将被视为plagiarism抄袭,后果很严重,甚至导致直接挂科。
而即使你做了citation,也不能直接一字不动地照搬原文语句,需要通过quotation,paraphrase 或者summary来改写文章。
目前英国高校普遍要求通过数据库系统提交作业,自动在超过80亿的文献和网页中搜索和你的作业相似度高的文字,稍不注意就可能被电脑判断为相似度高的”伪剽窃“。
所以,想要写好一篇report和essay:1. 你要认真读懂并且理解老师给的题目2. 你要清楚这题目跟学过的那些知识点哪些理论可以联系得上3. 你要学会怎么规划整篇文章的结构以及每部分大致的字数,最后按顺序一部分一部分的去完成4. 你要学会规避“伪剽窃”这类系统性的写作风险这就是大部分中国留学生不能毕业的原因经常被坑/坑人的presentationpresentation分为个人和小组的,需要根据老师布置的主题来准备ppt和稿子。

DIRECTORATE OF LEARNING SYSTEMSDISTANCE EDUCATION COURSESStudent Number: ________________________________Name: _________________________________________Address: ______________________________________________________________________________________INTEGRATED HIV/AIDSTutor Marked AssignmentUnit 4: HIV Associated Conditions in Adults & Adolescents Instructions: Answer all the questions in this assignment.1. List the common neurological diseases seen in HIV positive patients_____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________2. Kasuku, who is known to be HIV positive, presents to hospital with a two week historyof weakness on one side of the body and difficulty with speech. The following are possible causes of his condition (indicate true or false).A. Candia albicansB. Cryptococcal meningitisC. MeningiomaD. LymphomaE. Toxoplasmosis3. Fatuma is a 38 year old woman who is HIV positive. She comes to the hospitalcomplaining of difficulty walking and leg weakness of sudden onset. What othersymptoms might she experience that are related to neuropathy?A. HeadacheB. IncontinenceC. SeizuresD. FeverE. Difficulty in breathing4. List the possible complications of peripheral neuropathy and outline how you willmanage them._____________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________5. Juma, who is 27 years old, complains of hearing voices and seeing people with swordschasing him. He tested HIV positive 3 years ago. The following statements are true of Juma’s condi tion.A. It is unrelated to his HIV statusB. HIV does not affect the brain directlyC. He should be given high doses of antipsychotic medicationD. The absence of fever makes infection unlikely6. a) What is delirium?_________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________b) List the possible causes of delirium in HIV positive patients_________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________7. List the common respiratory conditions seen in HIV/AIDS__________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________8. Which of the following drugs are used in the prevention of Tuberculosis?A. ClarithromycinB. CotrimoxazoleC. PyrazinamideD. IsoniazidE. Ketocnazole9. Which of the following statements are true regarding TB in HIV infection?A. HIV positive people with a negative Mantoux test should be offered prophylaxisagainst TB infectionB. Tuberculosis treatment is given for a longer timeC. It only occurs on those who are severely immunosuppressedD. It is difficulty to cure10. Outline the steps that should be taken to prevent tuberculosis in healthcare facilities.____________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________11. The following are useful in the management of pneumocystis carinii pneumoniaA. Penicillin VB. CotrimoxazoleC. ErythromycinD. DapsoneE. Prednisolone12. List the common causes of diarrhoea in HIV positive patients.____________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________13. Jama, who is HIV positive, is 22 years of age and works as a herds-boy. He spendsmost of the day in the fields and the only water available to him is from streams. He complains that he gets dizzy during the middle of the day. He has been having episodes of diarrhoea on and off for the last 4 weeks. What advise would you give Jama?____________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________14. Amina is a 37 year old housewife. She was found to be HIV positive during her lastpregnancy 2 years ago. She has noticed that she has been loosing weight over the last 3 months. She has mouth sores that are painful and occasionally has central chest pain when she swallows food.a. List the common causes of oral sores in HIV infection.____________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________b. On looking inside Amina’s mouth, you notice tha t she has white plaques (patches) atthe back of the mouth. What is the most likely cause of these patches?______________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________c. What are some of the effects of oral disease in HIV/AIDS?______________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________e. What treatment would you give Amina?_____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________15. List the possible causes of weight loss in HIV/AIDS:_____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________16. How do you assess a patient with weight loss in the HIV Clinic?_____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________17. List the common causes of skin disease in HIV/AIDS______________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________b. W hat are the common sites for Kaposi’s sarcoma lesions? How can these lesions bedescribed?________________________________________________________________________ ________________________________________________________________________ _________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________c. Why is it important to differentiate between lesions due to seborrheic dermatitis, andthose due to fungal infection? Mention some of the differences between these conditions. How would you treat them?________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ _______________________________________________________________________Congratulations! You have now come to the end of this unit. Remember to indicate your Student Number, names and address before sending this assignment. Once you complete this assignment, post or bring it in person to AMREF Training Centre.。

英文Assignment和Dissertation的写作细节(珍藏版)Dissertation一、Dissertation大体结构1.首先是Cover Page,即封面,包括论文的题目,作者姓名,所在学院,学校和上交时间等信息。
2.Declaration,也就是声明,“我声明,所有成果除了我已经注释的,其他均为我自己的研究成果,没有剽窃他人的”,之后是上交时间,指导导师,签名,学院等。
3.Acknowledgment,写要感谢的人,导师是必须要感谢的,当然还可以感谢其他人,这个随意。
4.Content,目录,这个要两端对其,整体格式一致,用Word中的目录索引功能自动生成。
一般三级目录就可以了。
比如3,3.1,3.1.2。
5.List of Figures,也就是所有图片的一个目录,包括所有在论文中出现的图片标题,不要把图片也贴上,只要标题。
比如:1.1 XXXX标题名称2.1 XXXX标题名称6.List of T ables,和上面类似,就是表格的目录。
(注:以上内容的页码为罗马数字,从下面的Abstract开始,为阿拉伯数字并从1重新开始,这个在word中可以设置。
目录第一条从Introduction开始,而不是Abstract,切记。
)7.Abstract,也就是摘要。
一般50-60页的论文摘要1页以内即可,最好控制在半页到3/4页,不要多。
8.Introduction,介绍部分。
9.Background 或者Literature Review,题目只要涉及这些方面即可,一般是这两个。
内容也是。
(具体写作我后面会具体说)。
10.Proposed Method也就是主体部分,题目自定或者问问导师,但是内容是你的研究成果的描述。
11.Analytical and T est Results,分析和测试结果,题目自定,内容主要就是测试结果。
12.Discussion,对结果产生的分析和解释,也有并入上面的一说。

第一讲练习试将下列句子译成汉语:1.The many colors of a rainbow range from red on the outside to violet on the inside.彩虹有多种颜色,外圈红,内圈紫。
2. He had a disconcerting habit of expressing contradictory ideas in rapid succession.他有一种令人难堪的习惯:一会儿一个看法,自相矛盾,变化无常。
3.This was an intelligently organized and fervent meeting in a packed Town Hall, with Mr. Strong in the chair.这是一次精心组织起来的会议。
市政厅里济济一堂,热情洋溢,主持会议的是斯特朗先生。
4.Power can be transmitted over a great distance withpractically negligible loss if it is carried by an electric current.电流可以把动力传送到很远的地方,其消耗几乎可以忽略不计。
5.The present onslaught of vehicles poses a serious threat to urban life and pedestrian peace of mind.当前,车辆横冲直闯,严重地威胁着城市生活,路上行人无不提心吊胆。
6.Change of information, if any, concerning the contents of this section will be found in the appendix at the end of this book.本节内容如有更改,均见本书末附录。
7.She said, with perfect truth, that “it must be delightful to have a brother,”and easily got the pity of tender-hearted Amelia, for being alone in the world, an orphan without friends or kindred.她说道,“有个哥哥该多好啊,”这话说得入情入理。

Chapter 1321.The document becomes a negotiable instrument wherein the title to themerchandise goes with possession of the bill of lading.此提单成为流通票据,其货物的所有权随着提单的持有者而转移。
2.We surrendered a clean on board bill of lading for the negotiation ofpayment.议付时,我们提交了清洁已装船提单。
3.You may draw a clean draft on us for the value of this sample shipment.你方可向我方开出光票索取这批货的价款。
4.The balance of USD 10,000 has been drawn at sight on you.我方已向你方开出USD10,000的即期汇票。
5.You can draw on us against this credit.你方可以凭此信用证向我方开立汇票。
6.Bill of lading should be made out to order and endorsed in blank.提单应当要有指示并且要有空白背书。
7.The customary letter of credit calls for “a full set on board ocean bills oflading to order of shipper, blank endorsed”.习惯上的信用证要求全套的已装船提单要有承运人指示,及空白背书。
8.If blank endorsement is made, the holder of the B/L has the right to takedelivery of the goods.如果已经空白背书,提单的所有者就有权提取货物。
Assignment/p/2474897921翻译/cn/help/simulink/slref/assignment.html赋值到指定元素的信号库Math OperationsAssignment块分配指定元素的值的信号。
您可以指定元素的索引被分配的值块的对话框中输入索引,或块通过连接一个外部索引的来源或来源。
块的数据端口处的信号,标记为U,指定值被分配到Y。
该块从数据信号中的元素替换指定Y的元素基于该值,您输入的Number of output dimensions参数,显示一个表的索引选项。
表中的每一行对应输出维度的一个在Number of output dimensions中.对于每个维度,可以定义的元素的信号来工作。
指定为一个1-D的信号和一个2-D信号的矩阵信号作为一个矢量信号。
当您设定的分配块的块图标变化,操作多维信号。
例如,假设一个5-D信号基于索引模式。
该表在分配块对话框中切换到包括一个行的每个维度。
如果你定义了每个维度的以下项:∙1Index Option, 选择Assign all∙2Index Option, 选择Index vector (dialog)Index, 输入[1 3 5]∙3Index Option, 选择Starting index (dialog)Index, 输入4∙4Index Option, 选择Starting index (port)∙5Index Option, 选择Index vector (port)分配的值将是Y(1:end,[1 3 5],4:3+size(U,3),Idx4:Idx4+size(U,4)-1,Idx5)=U, where Idx4和Idx5是输入端口4和5的维度.分配块的数据端口标记为U.本节的其余部分是指为了简化解释块的使用为数据端口U。
您可以使用块将值指派给向量,矩阵或多维信号。
您可以使用一个数组作为分配块的输入信号的总线。
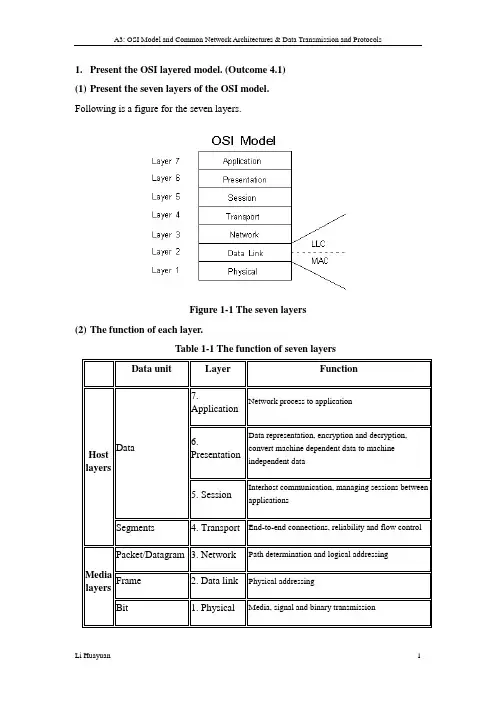
1.Present the OSI layered model. (Outcome 4.1)(1)Present the seven layers of the OSI model.Following is a figure for the seven layers.Figure 1-1 The seven layers(2)The function of each layer.Table 1-1 The function of seven layers(3)The relationship of layers.Moving from the top, down - messages get larger and larger. A message is passed down, and the lower layer adds a header to it. This is called encapsulation, because it is like placing an object into a capsule. The header is sometimes called a wrapper. Each successive lower layer encapsulates what it receives from the layer above it. Moving from the bottom, up - messages get smaller and smaller. A message is first stripped of it's header, and then the inner contents (the "data" portion) is passed up. This is "decapsulation" but no one uses that term. Each successive upper layer receives the data message from the layer below, and then strips off it's own header and passes the data up.2.Explain the role of drivers in a network, discussing their relationship to the NOS and OSI model. (Outcome 4.2)(1)The function of drivers in a network.LAN drivers direct the function of the hardware used to transfer data to and from computers in the LAN. These drivers come in many types, and they can be installed on a user's computer or on a shared server. Network hardware devices, which might need LAN drivers to function, include network routers, modems, network cards, or network card adapters.(2)Drivers’ relationship to the Windows server 2003.Drivers are one kinds of software help communication between Win 2003 and hardware. The connecting hardware can never work without the matching driver. In usually, Win 2003 owns the driver. It can update the driver by the “Windows Update”from the control platform. If it didn’t owns the driver, then it need the CD which as the additional with the hardware, or search and download from the internet.(3)Drivers’ relationship to the OSI model.Different driver works on different layer. The File system driver works on application layer, session and presentation layers. The gate way works on the Transport layer. The router works on the Network layer. The switch works on the Data link layer. The repeater works on Physical layer.3.Discuss how drivers are selected and implemented for various network components; install NIC driver and demonstrate how to remove and update. (Outcome4.3)(1)Discuss how drivers are selected and implemented for sound card, network interface card and video card.Every computer has its own drivers includes sound card, network interface card and video card and so on. When we buy the computer, a CD/DVD contain drivers will be give us. We can use the CD/DVDs to select and implement the drivers. And we can download some driver software to check out whether our computer lack of drivers, then select the driver and implement it.(2)Install Microsoft Loopback Adapter driver.Following are the figures for install steps:Figure 3-1 Installation1Figure 3-2 Installation2Figure 3-3 Installation3Figure 3-4 Installation4Figure 3-5 Installation5Figure 3-6 Installation6Figure 3-7 Installation7Figure 3-8 Installation8(3)Remove and update the Microsoft Loopback Adapter driver. Following are figures show the steps for remove and update:Figure 3-9 Step1Figure 3-10 Step2Figure 3-11 Remove and update4.Explain the detailed operation of different IEEE 802.N network configurations. (Outcome 4.4)Table 4-1 The detailed operation of different IEEE 802.N5.Refer the 802 protocols to the existing OSI layers. (Outcome 4.5)(1)The IEEE 802 model.IEEE 802 refers to a family of IEEE standards dealing with local area networks and metropolitan area networks.More specifically, the IEEE 802 standards are restricted to networks carrying variable-size packets. (By contrast, in cell relay networks data is transmitted in short, uniformly sized units called cells. Isochronous networks, where data is transmitted as a steady stream of octets, or groups of octets, at regular time intervals, are also out of the scope of this standard.) The number 802 was simply the next free number IEEE could assign,[1] though “802” is sometimes associated with the date the first me eting was held — February 1980.The services and protocols specified in IEEE 802 map to the lower two layers (Data Link and Physical) of the seven-layer OSI networking reference model. In fact, IEEE 802 splits the OSI Data Link Layer into two sub-layers named Logical Link Control (LLC) and Media Access Control (MAC), so that the layers can be listed like this:Data link layer⏹LLC Sublayer⏹MAC SublayerPhysical layerThe IEEE 802 family of standards is maintained by the IEEE 802 LAN/MAN Standards Committee (LMSC). The most widely used standards are for the Ethernet family, Token Ring, Wireless LAN, Bridging and Virtual Bridged LANs. An individual Working Group provides the focus for each area.(2)Compare the 802 protocols with the OSI layers.Figure 5-1 ComparisonThe main thing to note is that the original OSI model didn't include a "medium access" layer because the assumption was made that all networks would be made of point-to-point lines. Boy, were they wrong. They later hacked a medium access control sublayer into the data link layer.Basically, the OSI physical layer corresponds to the IEEE 802 physical layer. Then, the OSI data link layer corresponds to the 802 LLC and MAC layers.(3)Define and explain the data link layer in IEEE Project 802.The bottom two OSI layers, the physical layer and the data-link layer, define how multiple computers can use the network simultaneously without interfering with each other.The IEEE 802 project incorporated the specifications in those two layers to create standards that have defined the dominant LAN environments. Figure 5.8 shows the data-link layer and its two sublayers.After deciding that more detail was needed at the data-link layer, the 802 standards committee divided the data-link layer into two sublayers:Logical Link Control (LLC) Establishing and terminating links, controlling frametraffic, sequencing frames, and acknowledging frames●Media Access Control (MAC) Managing media access, delimiting frames,checking frame errors, and recognizing frame addressesLogical Link Control (LLC) SublayerThe LLC sublayer manages data-link communication and defines the use of logical interface points called service access points (SAP). Other computers can refer to and use SAPs to transfer information from the LLC sublayer to the upper OSI layers. Category 802.2 defines these standards.Media Access Control (MAC) SublayerAs Figure 5.9 indicates, the MAC sublayer is the lower of the two sublayers, providing shared access to the physical layer for the computers' NICs. The MAC layer communicates directly with the NIC and is responsible for delivering error-free data between two computers on the network.6.Relate how architecture influences access and control of the network and draw out merits of different architectures. (Outcome 4.6)(1)Explain CSMA/CD and Token Passing access and control method.a)CSMA/CDCarrier sense multiple access with collision detection (CSMA/CD) is a Media Access Control method in which:● A carrier sensing scheme is used.● A transmitting data station that detects another signal while transmitting a frame,stops transmitting that frame, transmits a jam signal, and then waits for a random time interval before trying to resend the frame.CSMA/CD is a modification of pure carrier senses multiple accesses (CSMA). CSMA/CD is used to improve CSMA performance by terminating transmission as soon as a collision is detected, thus shortening the time required before a retry can be attempted.b)Token PassingIn telecommunication, token passing is a channel access method where a signal called a token is passed between nodes that authorizes the node to communicate. The mostwell-known examples are token ring and ARCNET.Token passing schemes provide round-robin scheduling, and if the packets are equally sized, the scheduling is max-min fair. The advantage over contention based channel access is that collisions are eliminated, and that the channel bandwidth can be fully utilized without idle time when demand is heavy. The disadvantage is that even when demand is light, a station wishing to transmit must wait for the token, increasing latency.(2)Relate how architecture influences CSMA/CD and Token Passing.In the CSMA/CD media-access scheme, network devices contend for use of the physical network medium. CSMA/CD is therefore sometimes called contention access. Examples of LANs that use the CSMA/CD media-access scheme are Ethernet/IEEE 802.3 networks, including 100BaseT.In the token-passing media-access scheme, network devices access the physical medium based on possession of a token. Examples of LANs that use the token-passing media-access scheme are Token Ring/IEEE 802.5 and FDDI.(3)Draw out merits of Ethernet, Token Ring and ArcNet.a)Merits of EthernetConceptually Simple:Ethernet is simply daisy-chained together with coax cable and "T" adapters. There are usually no hubs, transceivers, or other devices used.Relatively Inexpensive:Due to the simplicity inherent in the design of Ethernet, it can be an inexpensive technology to implement.Noise Immunity:The coaxial cable used in a Ethernet network is very well shielded, and has a very high immunity from electrical noise caused by outside sources.b)Merits of Token RingToken Ring networks are deterministic in nature. In English, this means that the nodes may only transmit at certain, well defined times. This eliminates incidents of two or more nodes transmitting at the same time and corrupting each other's transmission(collisions). The elimination of collisions results in a network where data almost always gets to its destination on the first attempt, greatly reducing retransmissions which waste bandwidth. The end result is a higher effective bandwidth at the same wire speed.c)Merits of ArcNetARCNET added a small delay on an inactive network as a sending station waited to receive the token, but Ethernet's performance degraded drastically if too many peers attempted to broadcast at the same time, due to the time required for the slower processors of the day to process and recover from collisions.[citation needed] ARCNET had slightly lower best-case performance (viewed by a single stream), but was much more predictable. ARCNET also has the advantage that it achieved its best aggregate performance under the highest loading, approaching asymptotically its maximum throughput.7.Describe scenarios where one architecture might be favored over another. (Outcome 4.7)(1)Describe the features, cabling and components of Ethernet, Token Ring, Apple Talk and ArcNet.a)EthernetTable 7-1 The features of EthernetTable 7-2 The cablingComponentsIn an Ethernet LAN, the components include NIC, switch, hubs, router, and the cables.b)Token RingA Token Ring network includes the following features:•Star-wired ring topology•Token-passing access method•Shielded and unshielded twisted-pair (IBM Types 1, 2, and 3) cabling •Transfer rates of 4 and 16 Mbps•Baseband transmission•802.5 specificationsCablingThe STP or UTP cable to a hub connects computers on a Token Ring network. Figure 3.28 shows cable length limits for three types of cabling. Token Rings use IBM Type 1, 2, and 3 cabling. Most networks use IBM Cabling System Type 3 UTP cabling. ComponentsIn a Token Ring network, the components include Hub, Cabling, Connectors, Patch Cables, Media Filters, Patch Panels, Repeaters, Fiber-Optic Cable.c)Apple TalkFeatures•LocalTalk networks, which have a single network number and can have as many as 254 nodes. (They are actually limited to 32 or fewer nodes because of media capacity.)•EtherTalk and TokenTalk networks, which can be assigned a network range sothat the network can have more nodes. EtherTalk and TokenTalk networks can have as many as 253 nodes for every number in the network range, for a maximum of 16.5 million nodes.LocalTalk networks, which each must be in a single zone. Each EtherTalk and TokenTalk network can have multiple zones, and individual nodes on a network can be configured to be in any one of the network's associated zones.CablingSTP cabling is most often used in a bus or tree topology. A LocalTalk network supports a maximum of 32 devices.Because of LocalTalk's limitations, manufacturers other than Apple are often preferred for cabling. Farallon PhoneNet, for example, can handle 254 devices. PhoneNet uses telephone cable and connectors and can be implemented as a bus network or plugged into a central wiring hub to form a star topology.ComponentAppleTalk networks are arranged hierarchically. Four basic components form the basis of an AppleTalk network: sockets, nodes, networks, and zones.d)ArcNetFeaturesDeterministic Performance - Users Can Calculate the Worst Case Node to Node Message TimeLogical Ring - Nodes Automatically Find Their Neighbor to Create A Ring Automatic Reconfiguration - A New Node Joins the Ring Automatically Without Software InterventionBroadcast and Directed MessagesMulti-Master with Automatic Token GenerationCabling Options - Coaxial, Fiber, EIA-485 Twisted PairHigh Speed - Standard 2.5 Mbps, Optionally 19 kbps to 10 MbpsLow Cost ChipsLow Protocol Overhead - 3 or 4 Bytes—Good Usage of Available Bandwidth Variable Packet Size - 0 to 507 BytesBit Rate Scalable up to 10 Mbps—Grows with Your ApplicationHigh Noise ImmunityEasy/Simple Manageable Technology—No Special Development Tools Required CablingThe standard cabling used for ArcNet is 93-ohm RG-62 A/U, coaxial cable. ArcNet also supports twisted-pair and fiber-optic media. The distances between computers vary, depending on the cabling and the topology.(2)Describe appropriate application scenarios of Ethernet, Token Ring, Apple Talk and ArcNet.a)EthernetNearly all scenarios can use the Ethernet, it is so popular in the world, but its limitation is that if many people want to connect the Ethernet in a area, the speed will be slow down.b)Token RingToken Ring networks give the benefit of a very fast. deterministic network, but require a major commitment to properly plan and maintain. Before choosing Token Ring as the technology for a particular project, it is very important to ensure that the organization has the ability to commit the time and resources necessary. Not doing so is basically a recipe for disaster.c)Apple talkAppleTalk is the Apple network architecture and is included in the Macintosh operating system software. Figure 7-1 shows a typical AppleTalk network configuration. This means that network capabilities are built into every Macintosh. It is used for sharing information and print etc.Figure 7-1 Apple talk networkd)ArcNetDatapoint Corporation developed the Attached Resource Computer Network (ArcNet) in 1977. Figure 7-2 shows a star-wired ArcNet. It is a simple, inexpensive, flexible network architecture designed for workgroup-size networks. The first ArcNet cards were shipped in 1983.Figure 7-2 Simple star-wired ArcNet8.Discuss the role of packets and how they are built up from their various components, giving an example where data packets are transmitted through different layers of the OSI model. (Outcome 5.1)(1)Discuss the role of the frame and how it is built up from its components.In computer networking, a frame is a data packet on the Layer 2 of the OSI model. A frame is "the unit of transmission in a link layer protocol, and consists of a link-layer header followed by a packet." Examples are Ethernet frames (maximum 1500 byte plus overhead), PPP frames and V.42 modem frames.The Ethernet II frame is a standard format for data transmitted via an Ethernet network. The frame refers to a collection of byte values in specified locations that identify the frame sender, the intended receiver, the data payload and an error-check value. Packaging data into frames such as this enables data to be sent via a packet-switching network rather than requiring a constant end-to-end connection. (2)Discuss the role of the packet and how it is built up from its components. Packets are constructed in such a way that layers for each protocol used for a particular connection are wrapped around the packets, like the layers of skin on an onion.At each layer (except perhaps at the application layer), a packet has two parts: theheader and the body. The header contains protocol information relevant to that layer, while the body contains the data for that layer, which often consists of a whole packet from the next layer in the stack. Each layer treats the information it gets from the layer above it as data, and applies its own header to this data. At each layer, the packet contains all of the information passed from the higher layer; nothing is lost. This process of preserving the data while attaching a new header is known as encapsulation.(3)Discuss the role of the segment and how it is built up from its components. Transmission Control Protocol accepts data from a data stream, segments it into chunks, and adds a TCP header creating a TCP segment. The TCP segment is then encapsulated into an Internet Protocol (IP) datagram. A TCP segment is "the packet of information that TCP uses to exchange data with its peers."A TCP segment consists of a segment header and a data section. The TCP header contains 10 mandatory fields, and an optional extension field (Options, pink background in table).The data section follows the header. Its contents are the payload data carried for the application. The length of the data section is not specified in the TCP segment header. It can be calculated by subtracting the combined length of the TCP header and the encapsulating IP header from the total IP datagram length (specified in the IP header).(4)Taking network layer for example, describe how data packets are transmitted through Transmission layer, Network layer and Data Link layer.a)Layer 4: Transport Layer•Manages end-to-end message delivery in network•Provides reliable and sequential packet delivery through error recovery and flow control mechanisms•Provides connectionless oriented packet deliveryb)Layer 3: Network Layer•Determines how data are transferred between network devices•Routes packets according to unique network device addresses•Provides flow and congestion control to prevent network resource depletionc)Layer 2: Data Link Layer•Defines procedures for operating the communication links•Frames packets•Detects and corrects packets transmit errors9.Discuss the role of protocols at different layers of the OSI model, describing the function of specific protocols. (Outcome 5.2)(1)Discuss the role of protocols at physical layer, data link layer, network layer, transport layer, session layer, presentation layer and application layer of the OSI model.Figure 9-1 The protocols at physical layera)Medium-access protocolsDefines the addressing that distinguishes each node an a NetWare network.b)Internetwork Packet Exchange (IPX)Defines the addressing schemes used on a NetWare network.c)Sequenced Packet Exchange (SPX)Provides security and reliability to the IPX protocol.d)Routing Information Protocol (RIP)Facilitates the exchange of routing information on a NetWare network.e)Service Advertising Protocol (SAP)Allows service-providing nodes to advertise their services and addresses.f)NetWare Core Protocol (NCP)Defines the connection control and service request encoding that make possible the interaction between clients and servers(2)Describe the function of FTP, HTTP, TELNET, SMPT, TCP, UDP, IP, ARP and ICMP.a)FTPFile Transfer Protocol (FTP) is a standard network protocol used to transfer files from one host to another host over a TCP-based network, such as the Internet. FTP is built on client-server architecture and uses separate control and data connections between the client and server. FTP users may authenticate themselves using a clear-text sign-in protocol but can connect anonymously if the server is configured to allow it.b)HTTPThe Hypertext Transfer Protocol (HTTP) is an application protocol for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web.c)TELNETTelnet is a network protocol used on the Internet or local area networks to provide a bidirectional interactive text-oriented communications facility using a virtual terminal connection. User data is interspersed in-band with Telnet control information in an 8-bit byte oriented data connection over the Transmission Control Protocol (TCP). d)SMTPSMTP is a standard electronic-mail protocol that handles the sending of mail from one SMTP to another SMTP server. To accomplish the transport, the SMTP server has its own MX (mail exchanger) record in the DNS database that corresponds to the domain for which it is configured to receive mail.e)TCPThe Transmission Control Protocol (TCP) is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol (IP), and therefore the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered delivery of a stream of bytes from a program on one computer to another program on another computer. TCP is the protocol that major Internet applications such as the World Wide Web, email, remote administration and file transfer rely on. Other applications, which do not requirereliable data stream service, may use the User Datagram Protocol (UDP), which provides a datagram service that emphasizes reduced latency over reliability.f)UDPUDP uses a best-effort delivery system, similar to how first class and lower postal services of the Indian Postal Service work. With a first class letter (post card), you place the destination address and put it in your mailbox, and hope that it arrives at the destination.g)IPThe Internet Protocol (IP) is the principal communications protocol used for relaying datagrams (packets) across an internetwork using the Internet Protocol Suite. Responsible for routing packets across network boundaries, it is the primary protocol that establishes the Internet.IP is the primary protocol in the Internet Layer of the Internet Protocol Suite and has the task of delivering datagrams from the source host to the destination host solely based on their addresses. For this purpose, IP defines addressing methods and structures for datagram encapsulation.h)ARPThe Address Resolution Protocol (ARP) is an Internet layer protocol that helps TCP/IP network components find other devices in the same broadcast domain.ARP resolves an IP address of a destination to the MAC address of the destination on the same data link layer medium, such as Ethernet. Remember that for two devices to talk to each other in Ethernet (as with most layer 2 technologies), the data link layer uses a physical address (MAC) to differentiate the machines on the segment. When Ethernet devices talk to each other at the data link layer, they need to know each other MAC addressesi)ICMPICMP provides network diagnostic functions and error reporting. One of the most used IP commands is the Packet Internet Grouper (PING) command. When a host PINGS another client, it sends an ICMP ECHO request, and the receiving host responds with an ICMP ECHO REPLY. PING checks network connectivity on clientsand routers. ICMP also provides a little network help for routers. When a router is being overloaded with route requests, the router sends a source quench message to all clients on the network, instructing them to slow their data requests to the router.10.Explain examples of transmission between different network layers. (Outcome 5.3)(1)Explain the process of data transmission how host A sends the data via different layers.Figure 10-1 The process of data transmission1When host A sends a message to host B, the message moves down the successive layers of host A, from the application layer to the presentation layer, to the session layer, etc., until it reaches the physical layer. It is then transmitted across the communication line between host A and node X, and moves up the three layers of node X and down again. Then it is transmitted to node Y where it goes through the same procedure, and finally is transmitted to host B, where it moves up its seven layers, until it arrives at the application layer of host B.(2)Explain the process of data transmission how host B receives the data via different layers.Figure 10-2 The process of data transmission2System B receives the request on Layer 1, and begins the decapsulation process, stripping the Layer 1 headers and footers off to reveal the Layer 2 information, and so forth, all the way up to the 7th layer.ConclusionAfter finished this assignment, I know the OSI layered model, the role of drivers in a network, and their relationship to the NOS and OSI model function of drivers in a network. I know how drivers are selected and implemented for various network components. I learn how to install, remove and update NIC driver. I know the detailed operation of different IEEE 802.N network configurations, the 802 protocols to the existing OSI layers, how architecture influences access and control of the network and merits of different architectures. I understand some scenarios where architecture might be favored over another, the role of packets and how they are built up from their various components. I also know the example where data packets are transmitted through different layers of the OSI model, the role of protocols at different layers of the OSI model, the function of specific protocols examples of transmission between different network layers.Through this assignment, I learn a lot.Reference/wiki/OSI_model#Cross-layer_functions [Accessed on June 25, 2011]/wiki/IEEE_802 [Accessed on June 25, 2011]/ccna/internetworking/lanprotocols.html [Accessed on June 25, 2011]/wiki/Token_passing [Accessed on June 25, 2011]/wiki/Carrier_sense_multiple_access_with_collision_detection /wiki/ARCnet [Accessed on June 25, 2011]/~cyh/cis370/ebook/ch03f.htm [Accessed on June 25, 2011] http://docstore.mik.ua/orelly/networking_2ndEd/fire/ch04_01.htm [Accessed on June 25, 2011]/wiki/Transmission_Control_Protocol#TCP_segment_structure [Accessed on June 25, 2011]/n_plus_certifications/protocol_tcp_ip_udp_ftp_t ftp_smtp.htm [Accessed on June 25, 2011]。


Assignment 6 辞格翻译练习Render the following into Chinese or English by using free or literal translation.1.The fury of the crowd erupted like a volcano.暴动的人群像火山喷发一般蜂拥而出。
2.I can’t save myself any more than a clay idol can save itself while swimmingacross a river.我自己都泥菩萨过河,自身难保了。
3.If we attack quickly, we can nip the enemy’s plans in the bud.如果我们攻击迅速,就可以把敌人的计划消灭在萌芽状态。
4.When my ship comes in, I will take a trip to Africa.等我发了财,我要去非洲旅行。
5.Men are April when they woo, December when they wed, maids are Ma y whenthey maids, but the sky changes when they are wives.男人求婚时像四月一样温和,结婚后如腊月一般冷漠;少女恋爱时像五月一样柔和,结婚后如天气一般阴晴不定。
6.He was born with a silver spoon in his mouth.他是嘴里含着银汤匙出生的。
(他天生富贵命)7.It can’t be defined by the span of a single journey from diaper to shroud.人从出生到死亡,这不能被定义为一个单一的旅程的跨度。
8.His cruel kindness is simply beyond words.他这该死的仁慈根本无法用语言来表达。
assignment作业摘要:一、作业的定义和意义1.作业的定义2.作业的意义二、作业的分类1.课堂作业2.课后作业3.家庭作业三、作业的作用1.巩固课堂所学知识2.培养学生的自主学习能力3.提高学生的综合素质四、如何合理安排作业1.合理安排作业时间2.注重作业质量3.家长和老师的配合与监督五、我国对学生作业的管理政策1.减负政策2.作业管理的规定3.对作业质量的要求六、结论正文:一、作业的定义和意义作业是指学生在课堂之外,为完成学习任务而进行的学习活动。
作业有助于巩固课堂所学知识,培养学生的自主学习能力,提高学生的综合素质。
二、作业的分类1.课堂作业:学生在课堂上完成的练习或任务。
2.课后作业:学生在课后完成的练习或任务。
3.家庭作业:学生在家庭环境中完成的练习或任务。
三、作业的作用1.巩固课堂所学知识:通过作业,学生可以加深对课堂知识的理解和记忆,为今后的学习打下基础。
2.培养学生的自主学习能力:作业要求学生独立完成,有助于培养学生自主学习的能力和习惯。
3.提高学生的综合素质:通过完成不同类型的作业,学生可以提高自己的思维能力、动手能力、协作能力等。
四、如何合理安排作业1.合理安排作业时间:学生应合理安排作业时间,避免过度拖延或临时抱佛脚。
2.注重作业质量:学生应注重作业的质量,力求做到准确、规范、有创意。
3.家长和老师的配合与监督:家长和老师应共同关注学生的作业完成情况,及时给予指导和鼓励。
五、我国对学生作业的管理政策1.减负政策:我国政府出台了一系列减负政策,以减轻学生的课业负担,让学生有更多的时间参与课外活动和锻炼身体。
2.作业管理的规定:教育部门对学生的作业量、作业时间、作业内容等作出了明确的规定。
3.对作业质量的要求:教育部门要求教师提高作业质量,注重培养学生的创新能力和综合素质。
综上所述,作业是学生学习过程中不可或缺的一部分,它能帮助学生巩固知识、培养能力、提高素质。
出国留学的学生在递交申请材料时一般都要向学校提供2-3篇的推荐信,因其重要性,学生对自己认识不到位,或是不能进行很好的挖掘,再加上英文水平一般,那么要想给录取官留下一个很好的印象就相当难了。
很多学生会求助于留学文书机构,但是很多机构因为不专业出现了大的问题,导致申请被拒的现象是屡屡发生。
出现大的问题的原因主要有:第一,套用模板。
很多学生自己写的时候在网上参考了很多推荐信的写作范文,甚至很多不专业也不负责任的机构为了省事,在网上直接下载模板,稍作修改就上交了。
结果就是推荐信上所有的中国申请者都是学习刻苦、善于钻研、乐于助人,是教过的最好的学生,而没有任何学生的特质。
第二,客服人员即是写作者。
有的写作机构规模太小,客服人员在快速催单之后,对于学生的自身情况,优缺点都不太了解,就自己动手写了起来,英文水平也不专业,仅仅是去过国外就声称自己在国外进修过,最后的结果就是惨败而归,学生有问题时却找不到对方机构!找一些质量很次的论文机构,不仅浪费了钱财,还耽误了申请的机会,对于以后再申请这个学校也有一些不好的影响。
这两个主要的问题,在优越论文网这里就全然不是问题了。
因为:第一,优越论文网可保证能随时联系。
优越论文网有着独特的优势,写手团队完备并且不断扩大,为了随时服务客户,客服人员不辞劳苦,一天24小时都在线,随时解答任何疑问。
第二,优越论文网能保证绝对地负责任。
客服人员能够随时在线接待客户,还能够耐心听取,并认真全面地记下学生提供的所有信息,在写作过程中也参考学生及时补充的信息和要求。
推荐信写好后,跟客户联系,进行文章要点核对以及再次交流,做到让客户绝对满意。
第三,优越论文网能保证写手专业。
优越论文网的文案老师都是在国外深造回国的,有着扎实的英语写作技能,根据申请者的资料进行原创写作,坚决排斥使用模板修改信息,保证每一位申请者的文书都是独一无二的。
并且能根据学生的实际情况就某一角度进行最大限度地深挖,切实地达到推荐效果。
海外留学对于assignment的要求assignment在我们以前学习英语的时候,只知道它是作业的意思。
而随着我们的长大,甚至出国留了学,却发现我们不会写assignment了,为什么?在欧美,一些大学的assignment其实有两种,一种是报告形式,另一种则是文章、短文的形式。
它们需要各专业的专业性知识,用这两种形式来完成导师布置的相关任务。
那么从国内去海外留学的留学生们怎么去适应欧美的这些assignment呢?本站可为您提供专业的指导服务,接下来先让我们来参详一下某海外assignment 要求,供大家参考。
Written Assignment and Guidelines for SubmissionAssignment Question:Discuss the effects of ageing under each of the following headings:1. Psychosocial2. Behavioural3. BiologicalDue Date:A hard copy of the 1000 to 1250 word assignment is due no later than 17:00 hours on Friday 15th April (end of week 7).Late submissions will not be accepted unless an Assignment Extension has been granted by the Course Coordinator Dr Tony Bush.Extension forms are available from the School of Health Sciences office on Level 4 of Building 201 (for Bundoora students) or from the School website on the RMIT internet. Students must follow School policy when applying for an extension; and must not assume that it will be granted automatically.Guidelines for submissionThese guidelines are intended to assist students in formulating a comprehensive and appropriate response to the question. The purpose of this assignment is for students togain an understanding of the biological, behavioural and psychosocial changes that occur with ageing. Throughout this process students can apply knowledge gained though lecture material.Format:Students must use these guidelines to format their assignment. This requires the student to write a brief introduction which should include introducing the topic, and stating what their intentions are in their response to the question.A conclusion is also required, in which the student is required to summarise the major points covered in their submission.The use of headings is mandatory to provide clearly structured signposts for both the student and the examiner. Adherence to the marking guide will ensure that students present their submission in a professional and academic style.Students are not to submit additional information as an Appendix. Headings related to specific content should be used to organise your information, and table of contents must be included.Word limit:An overall word limit of 1000-1250 words is required for this assessment. Students are not to go over the word limit by more than 250 words. If students are under the minimum word limit, it may mean that they have not answered the question in enough detail.References & Referencing:Students are to show evidence of research into the topic; in addition to the required textbook for this course. A minimum number of three (3) references used must be relevant to the topics, and must be contemporary (not older than 5 years generally) and relevant to the context of Ageing. The types of references used should include the textbook & journal articles (minimum of 2).Students should research the topic through the RMIT Library databases and e-journals.Students must reference all information from other sources, using appropriate intext referencing according to the American Psychological Association (APA) style of referencing. This includes intext referencing, and page numbers for direct and indirect quotes. Students must also include a reference list at the end of their assignment written exercise, formatted according to APA referencing style. Students can access information on formatting according to APA through the RMIT Library webpage (under the subject guide – Nursing –referencing – APA), on the Study and Learning Centre webpage or the Style Guide: Strategies for Effective Academic Writing on the DLS. . Students are advised to maintain an ongoing list of all references used during the writing of assignment; including details of web addresses, dates that sites were accessed, page numbers, etc.; to help them collate their final list.Spelling, Grammar & Presentation:Students must ensure that their spelling and grammar, including punctuation, meets academic standards. Spell checks on the computer are useful; but students need to also do a final read-through of their submission to check for errors. It is expected that students will also use professional language and terminology. This should include using and defining medical terms, in keeping with the expectations of registered nurses within the health care setting. The use of abbreviations should be limited to those commonly used, and should be written in full the first time used in the submission. Students are not to use their own shorthand or SMS type. The font used should be a clear typeface, and size 12. Normal size margins apply and double spacing, with students ensuring pages are numbered clearly.Submission Details:Students are to submit only a hard copy of their Assignment by or on the due date, following the instructions on the course DLS. Electronic submission may be asked for, when incidence of plagiarism is suspected so the assignment can be put through Turnitin©. Assignments are not to be emailed to the Course Coordinator. Students are also reminded to retain a hard and/or electronic copy of their submission; until afterthe final course marks have been collated, finalised and released to students.The assignment will be available for collection from the course coordinator after the official release of results.。
RMIT UniversitySchool of Health SciencesDiscipline of Nursing and MidwiferyNURS 1134 Aged Care Nursing 2011Written Assignment and Guidelines for SubmissionAssignment Question:Discuss the effects of ageing under each of the following headings:1. Psychosocial2. Behavioural3. BiologicalDue Date:A hard copy of the 1000 to 1250 word assignment is due no later than 17:00 hours on Friday 15th April (end of week 7).Late submissions will not be accepted unless an Assignment Extension has been granted by the Course Coordinator Dr Tony Bush.Extension forms are available from the School of Health Sciences office on Level 4 of Building 201 (for Bundoora students) or from the School website on the RMIT internet. Students must follow School policy when applying for an extension; and must not assume that it will be granted automatically.Guidelines for submissionThese guidelines are intended to assist students in formulating a comprehensive and appropriate response to the question. The purpose of this assignment is for students to gain an understanding of the biological, behavioural and psychosocial changes that occur with ageing. Throughout this process students can apply knowledge gained though lecture material.Format:Students must use these guidelines to format their assignment. This requires the student to write a brief introduction which should include introducing the topic, and stating what their intentions are in their response to the question.A conclusion is also required, in which the student is required to summarise the major points covered in their submission.The use of headings is mandatory to provide clearly structured signposts for both the student and the examiner. Adherence to the marking guide will ensure that students present their submission in a professional and academic style.Students are not to submit additional information as an Appendix. Headings related to specific content should be used to organise your information, and table of contents must be included.Word limit:An overall word limit of 1000-1250 words is required for this assessment. Students are not to go over the word limit by more than 250 words. If students are under the minimum word limit, it may mean that they have not answered the question in enough detail.References & Referencing:Students are to show evidence of research into the topic; in addition to the required textbook for this course. A minimum number of three (3) references used must be relevant to the topics, and must be contemporary (not older than 5 years generally) and relevant to the context of Ageing. The types of references used should include the textbook & journal articles (minimum of 2).Students should research the topic through the RMIT Library databases and e-journals.Students must reference all information from other sources, using appropriate intext referencing according to the American Psychological Association (APA) style of referencing. This includes intext referencing, and page numbers for direct and indirect quotes. Students must also include a reference list at the end of their assignment written exercise, formatted according to APA referencing style. Students can access information on formatting according to APA through the RMIT Library webpage (under the subject guide – Nursing –referencing – APA), on the Study and Learning Centre webpage or the Style Guide: Strategies for Effective Academic Writing on the DLS. . Students are advised to maintain an ongoing list of all references used during the writing of assignment; including details of web addresses, dates that sites were accessed, page numbers, etc.; to help them collate their final list.Spelling, Grammar & Presentation:Students must ensure that their spelling and grammar, including punctuation, meets academic standards. Spell checks on the computer are useful; but students need to also do a final read-through of their submission to check for errors. It is expected that students will also use professional language and terminology. This should include using and defining medical terms, in keeping with the expectations of registered nurses within the health care setting. The use of abbreviations should be limited to those commonly used, and should be written in full the first time used in the submission. Students are not to use their own shorthand or SMS type. The font used should be a clear typeface, and size 12. Normal size margins apply and double spacing, with students ensuring pages are numbered clearly. Submission Details:Students are to submit only a hard copy of their Assignment by or on the due date, following the instructions on the course DLS. Electronic submission may be asked for, when incidence of plagiarism is suspected so the assignment can be put through Turnitin©. Assignments are not to be emailed to the Course Coordinator. Students are also reminded to retain a hard and/or electronic copy of their submission; until after the final course marks have been collated, finalised and released to students. The assignment will be available for collection from the course coordinator after the official release of results.。
1.Re-examine Exhibit 1-1 which describes the outsourcing process for HP’s production of Proliant ML150. For each leg of the production chain, indentify the various accounting and related issues that might arise.The might issues:Different Socio-economic environments. step by 1,2,3,4,5. it is involved Singapore, America, Taiwan, CHINA and so on.Different National financial reporting principles. (step by 2,4,5)Special disclosures for nondomestic financial statement readers(1,2,3).The exchange rate.(4,5) changing rate ¥,$...Kinds of financial statement analysis.(1,2)The Changing prices .in the 5 step, machines produced in different countries and sold in local markets.The level of each area’s education.The rate of the inflation.2. Do you feel that efforts to harmonize global accounting standards are good thing? Why or why not?Yes. with the rapid development in the global economy, Globalization is an unstoppable trend for every countries. so, making efforts to harmonize global accounting standards conductive to economic globalization. It will reduce the transaction cost and analysis the financial statements in different countries before they making better decisions.A common financial language, applied consistently, will enable investors to compare the financial results of companies operating in different jurisdictions more easily and provide more opportunity for investment and diversification.3. If you had a nontrivial sum of money to invest and decided to invest it in country index fund, in which country or countries identified in Exhibit 1-6 would you invest your money? What accounting issues would play a role in your decision?I will choose America invest my money, especially NASDAQ OMX and NYSE Euronext(U.S.). There are so many domestic companies and foreign companies and the number of the company as the change of time is very smooth. At the same time, there is a perfect finance environment to be worth of investing my money.4. Consider the following countries: China, France, U.K. and Sweden.Where would they be classified based on leagal system? Where would they be classified based on accounting practice systems?Code law: France ,China, SwedenCommon law: U.KChina: uniform approach.I think Accounting is standardized by central government and used as a tool for administrative control.France: Uniform approachU.K: independent discipline approachSweden: macroeconomic approach5. Refer to lesson 3 and lesson3(2), which country’s GAAP appears to be the most oriented toward equity investors? Whic h country’s GAAP appears to be the least oriented toward equity investors? Why do you say that?Most oriented:U.K.U.K’s GAAP is the most closest to IFRS from the countries. Whose GPPA is clearly aimed at equity investors. Under U.K. GAAP, Goodwill is capitalized and amortized less than 20 years (annual impairment except). in some degree, IFRS can instead of U.K. GAAP.Least oriented:France.In France,Research and development cost is expensed as incurred, but capitalized in restriced. And Leased assets are not capitalized,Legal reserves must be created by 5% of income each year until the reserve equals 10% of legal capital.what’s more,Goodwill is not required to be impairments tested.6. What’s the significant difference between IFRS and China’s Account ing Standards for Business Enterprises?A.Allocation of fixed production overheads to costs of conversionIFRS requires that allocation of fixed production overheads to the costs of conversion is based on the normal capacity of the production facility. In periods of abnormally low production or idle plant, the amount of fixed production overheads allocated to each unit of production is not increased, with the unallocated overheads recognized as an expense in the period in which they are incurred. However, in periods of abnormally high production, the amount of fixed production overheads allocated to each unit of production is decreased so that inventories are not measured above cost.China’s accounting has no such requirement.B.Reversal of Inventory Write downIFRS requires write downs to be reversed, when the circumstances that previously caused inventories to be written down below cost no longer exist or when there is clear evidence of an increase in net realizable value because of changed economic circumstances.China’s accounting only permits reversal when the circumstances that previously caused inventories to be written down below cost no longer exist.IFRS requires the reversal to be recognized as a reduction in the amount of inventories recognized as an expense in the period in which the reversal occurs. China’s Accounting requires the reversal to be recognized under asset impairment loss.C. Compared to China’s Accounting , the amount of inventories recognized as an expense during the period.7. On April 1, A.C. Corporation, a calendar-year U.S. electronics manufacturer, buys 32.5 million yen worth of computer chips from a Japanese company paying 10% in the time, the balance to be paid in 3 months. Interest at 8% per annum is payable on the unpaid foreign currency balance. The U.S. dollar/Japanese yen exchange rate on April 1 was 1:93; on July 1 was 1:98. Required: prepare dated journal entries in U.S. dollars to record the incurrence and settlement of this foreign currency transaction assuming:①A.C. corporation adopts a single-transaction perspective, and②Two-tran sactions perspective.Under the single-transaction perspective1.on april 1. Transaction datedr. equipment $349462.37cr. s-t payable $34946.237l-t debt $314516.133total $349462.37yen 32500000/932.(1)on July 1.settlement daydr. accounts payable 17330.48cr. Equipment $17330.48yen 32.5*1000000*90%*(1/93-1/98)(2) dr.accounts payable $322346.94cr. Cash $322346.94Under the two-transaction perspective1. on april 1. Transaction datedr. equipment $349462.37cr. s-t payable $34946.237l-t debt $314516.133total $349462.37yen 32500000/932.(1)on July 1.settlement daydr. accounts payable 17330.48cr. Foreign exchange gain $17330.48(2) dr.accounts payable $322346.94cr. Cash $322346.948.Final assignmentTo develop a stock market in an emerging economy, there would be some necessary conditions. They are as follows:Perfect Laws, regulations; market supervision and management measures.In general, there would be little laws and regulatons in an emerging economy. When we have established the perfect laws and regulations, built our market supervision with measured managements, so the market maybe a good, an effecial market for every kind of subjects with normal transaction. In contrary, it promte government built the related laws.The state intervention policy of the economyIn some situations, the state intervention makes a huge effect on stock market. The policy offers a forward to the economy. If the stock market fits in well with the country’s policy, it can be developed much well and faster than not fitting in.The accounting environment and audit environmentThe requirements of the accounting and audit affect the reality of the listing company’s financial disclosure information, the influrence is obviously to be seen to the stock market.The level of the finance, intermediary agencyIf one country’s finance institu tions contain all sides of the economy, it is convenient for company financing during its growing. At the same time, the more information about the company, the little risk will the investor face.The quality of the investor and invest ways in the marketWhen investors are all reasonal to invest every transaction and there are so many invest ways we can choose to invest, the result is that the scene of the stock market will be much better than past.The quality of the listing conpanyWhen t he listing company’s development is more stable, its managements are more effecial, the stock market will be more healthy and then its investors will face little risk in the futuremarket.How do these conditions compare to the situation in china?Although china’s stock market has achieved a great development from the 90s in 20th century. However, there exists some issues.Laws regulations and market supervision ,management measuresAlthough china has estahlished some related laws, the basic law of the security is still not built. With the absence of the corrlation law system, there is no laws can be relyed in some special situations.what’s worse. Because of the Inadequate enforcement of the law,there exists some illegal behavior and criminal in the security transaction.Problem of the state intervention policy of the economyAs with main state’s policy, it leads tocapital market lost the main part of the economy. In the conditions of market economy,compang is the main body of the capital market.even,it is very weak for our company’s main parts. The feature of company are prolems existing in the government and company , unclear Property right and unclear responsibility, weak controlling, shortage of dynamic…these characters are bad for they growing well and make them lost its host position.The accounting environment and audit environmentOn one hand, there exist some not real accounting information in some listing cimpany. As a result of this, what will happens? The result is that invetor will face much more risk than ever. On the other hand, because of the phenomenon of controlling profit is widely spead, the investor especially those small investor will suff great loss.some questions about the audit ars also the importance factors for the loss.The level of the finance, intermediary agencyAs we all know, there are some shortcomings in the intermediary agency. At present, the agency contains security company, trust and investment companies, accounting institus, laws institus, assets valuation institus, Securities investment consulting company and so on. Although these companies involved in many related tasks such as transaction, finance consulting, running, publishing and so on, there are some shortcomings compared with foreion investing banks tasks. so, it is bad for Enterprise reorganization.The quality of the investorAs personality is the main body of the capital invest market, the quality and quantity are much more lower. It is clear to see that some typical of invest institus ,such as invest found, occupies a lower proportion. With the lag of capital investor development, severval big agencies and large numbers of personnal investor support the stock developing. Based on the rolses, it can not stop the stock market suddenly higher and suddenly lower in a short time. All of this is not good for stock market with a healthy growing.Invest ways in the marketThere are little kinds of transaction tools in the capital market and the capital market’s structure is absence in some degrees. In the developed capital market, it fills many kinds of tools. For example, 80 percent of the world’s fi nance tools are used in Hong Kong capital market. Moreover, Not only are there some kinds of investment such as option, index, but also it is a trend that these money will pass spot transaction. Compared with others, the number of the tools almost keep a little level in more than 5 years except stock in the capital market of our mainland. What’s worse, these tools are even limited from 1 to 5 years. These indicate thatthose invest ways is bad for resources optimization deployment.The quality of the listing conpanySo far, many of the listing company in our country are State-owned enterprises. With its special position, it takes some perposes such as political is the first part, second is economical, leading a lower level of company management. These issues bring some pentencial disasters to the stock market when it comes to personnal benefits.How likely is china to develop a stock market with fair trading? In the next text, I will tell some views about my personal opinion.There still exists some issues in china’s stock market at present. However, I'm optimistic about our stock market’s future. The reasons are as follows:Every thing has a progress to develop well. During the growing time, we will experience some issues. What it is same to our stock market, so we do not have to disappoint to our stock market. We believe that it woud be better in one day sooner or later.Our government is not stop fixing stock market. Our leaders have taken effecial measures to promote the market to get a healthy development. With the timegoes out, we have changed our old management models step by step. At the same time, we are studing the good managements from foreion countries. In the laws, we continue to improve laws and regulations. In the markets, contining broaden our finance market from demotic to intenantional.The development of economy. Since the reform and opening up from 1978, great changes have taken place in China’s every aspects, especially in the economy area. When our economy goes to a new stage, Stock market must be get a huge development.The speed of our education is also very fast. Today, we have a number of people who get the high degrees in the colleges. In the future, there are more people have the high level certificate related to the area of economics. Based on these people, the stock market will have a new blood during its steps when we look forward.New communication tools to used widely in people’s daily life. Internet, cell phones are the main part tools used to get the transaction informaton. Investors can get more details from the stock market, get more knowledge related to the company’s accounting. For some sides of the market, people will have a good opinion to the pertencial meaning of the policy.Our stock market is getting more and more better from the reality. Shanghai and Shenzhen, the two largest security in demotic market, have play an inportant role in our daily life.With the economic globalization, world economy are related more and more frequent. From the international environment, it is good for our stock market’s growing. Moerover, increasing economy is the trend of globalization. World is that, we also even growth.Form all above,we have reasons to believe that china’s stock market will be more and more better than past times.At the end of the paper, there will outline a plan of reforms to achieve stock market development in china.We should build more professional laws and regulations, especially the stock laws. Everyone must implement stick laws, forcing the rules. Fight against all kinds of illegal and criminal activities, such as the not real accouting, cheating transaction, in accordance with the law, enhance people's insurrence. To make the strong find to the company if it cheats its investor and related finance apartments.Increasing the ways of investing, we can bring in new finance tools and protect some tools ifthey appears strongly life during the economy.Requiring higher standards for accounting and audit institus qualitity. Supporting those institus from policy and punishing these institus if they broke the low.To the State-owned enterprise, we should take measures to reform the structure if they belongs to the listing companies and make them more efficient.Built some professional finance apartment , such as invest bank, found. These institus make the invest more professional. From the investors relationship, it will reduce investor’s blindness and risk when they enter the stock market.。