Taming numbers and durations in the model checking integrated planning system
- 格式:pdf
- 大小:649.91 KB
- 文档页数:44
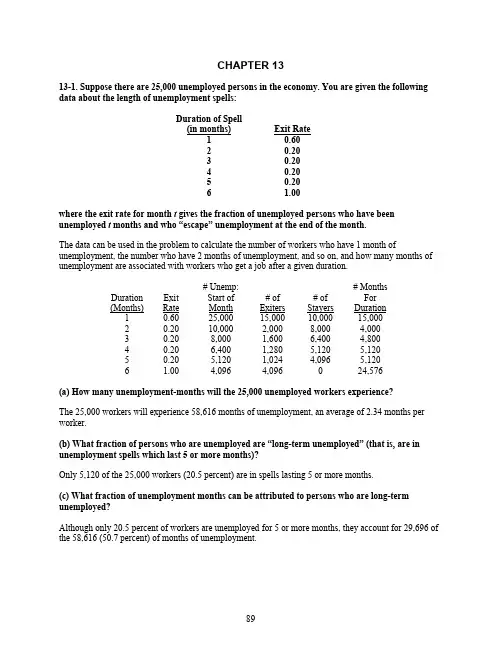
CHAPTER 1313-1. Suppose there are 25,000 unemployed persons in the economy. You are given the following data about the length of unemployment spells:Duration of Spell(in months) ExitRate1 0.602 0.203 0.204 0.205 0.206 1.00where the exit rate for month t gives the fraction of unemployed persons who have been unemployed t months and who “escape” unemployment at the end of the month.The data can be used in the problem to calculate the number of workers who have 1 month of unemployment, the number who have 2 months of unemployment, and so on, and how many months of unemployment are associated with workers who get a job after a given duration.Duration (Months) ExitRate# Unemp:Start ofMonth# ofExiters# ofStayers# MonthsForDuration1 0.60 25,000 15,00010,000 15,0002 0.20 10,000 2,000 8,000 4,0003 0.20 8,000 1,600 6,400 4,8004 0.20 6,400 1,280 5,120 5,1205 0.20 5,120 1,024 4,096 5,1206 1.00 4,096 4,096 0 24,576(a) How many unemployment-months will the 25,000 unemployed workers experience?The 25,000 workers will experience 58,616 months of unemployment, an average of 2.34 months per worker.(b) What fraction of persons who are unemployed are “long-term unemployed” (that is, are in unemployment spells which last 5 or more months)?Only 5,120 of the 25,000 workers (20.5 percent) are in spells lasting 5 or more months.(c) What fraction of unemployment months can be attributed to persons who are long-term unemployed?Although only 20.5 percent of workers are unemployed for 5 or more months, they account for 29,696 of the 58,616 (50.7 percent) of months of unemployment.(d) What is the nature of the unemployment problem in this example: too many workers losing their jobs or too many long spells?Most spells are short-lived, but workers in long spells account for most of the unemployment observed in this economy. Thus, the main problem is too many long spells.13-2. Consider Table 599 of the 2002 U.S. Statistical Abstract.(a) How many workers aged 20 or older were unemployed in the United States during 2001? How many of these were unemployed less than 5 weeks, 5 to 14 weeks, 15 to 26 weeks, and 27 or more weeks?In total, 5,554,000 workers aged 20 years or older were unemployed in the U.S. in 2001. Of these, 40 percent, or 2,221,600 workers, were unemployed for less than 5 weeks; 32.2 percent, or 1,788,388 workers, were unemployed between 5 and 14 weeks; 15.5 percent, or 860,870 workers, were unemployed15 to 26 weeks, and 12.9 percent, or 716,466 workers were unemployed for 27 or more weeks.(b) Assume that the average spell of unemployment is 2.5 weeks for anyone unemployed for less than 5 weeks. Similarly, assume the average spell is 10 weeks, 20 weeks, and 35 weeks for the remaining categories. How many weeks did the average unemployed worker remain unemployed? What percent of total months of unemployment are attributable to the workers that remained unemployed for at least 15 weeks?The total number of weeks of unemployment is calculated as:2,221,600(2.5) + 1,788,388(10) + 860,870(20) + 716,466(35) = 65,731,590months of unemployment spread over 5,554,000 unemployed workers, implies that the average unemployed worker remained unemployed for 11.835 weeks. The percent of total months of unemployment attributable to the workers that remained unemployed for at least 15 weeks is[ 860,870(20) + 716,466(35) ] / 65,731,590 = 64.34 percent.13-3. Suppose the marginal revenue from search isMR = 50 - 1.5w,where w is the wage offer at hand. The marginal cost of search isMC = 5 + w.(a) Why is the marginal revenue from search a negative function of the wage offer at hand?If the offer-at-hand is relatively low, it pays to keep on searching as the next offer is likely higher than the offer-at-hand. If the offer-at-hand is very high, however, it does not pay to keep on searching since it is unlikely that the next search will generate a higher wage offer.(b) Can you give an economic interpretation of the intercept in the marginal cost equation; in other words, what does it mean to say that the intercept equals $5? Similarly, what does it mean to say that the slope in the marginal cost equation equals one dollar?The $5 indicates the out-of-pocket search costs. Even if the offer-at-hand is zero (so that there is no opportunity cost to search), it still costs money to get to the firm and learn about the details of the potential job offer. The slope equals $1, because the costs of search also vary directly with the opportunity cost of search which is the wage offer at hand. If the wage offer at hand is $10, the opportunity cost from one more search equal $10; if the wage offer at hand is $11, the opportunity cost would be $11, and so on.(c) What is the worker’s asking wage? Will a worker accept a job offer of $15?The asking wage is obtained by equating the marginal revenue of search to the marginal cost of search, or 50 – 1.5w = 5 + w. Solving for w implies that the asking wage is $18. The worker, therefore, would not accept a job offer of $15.(d) Suppose UI benefits are reduced, causing the marginal cost of search to increase to MC = 20 + w. What is the new asking wage? Will the worker accept a job offer of $15?If we equate the new marginal cost equation to the marginal revenue equation we find that the asking wage drops to $12. The worker will now accept a wage offer of $15.13-4. (a) How does the exclusion of non-working welfare recipients affect the calculation of the unemployment rate? Use the 2002 U.S. Statistical Abstract to estimate what the 2000 unemployment rate would have been if welfare recipients had been included in the calculation.Excluding non-working welfare recipients from the unemployment rate biases the unemployment rate downward. Table 560 of the Statistical Abstract shows that the labor force in 2000 totaled 140,863,000, while the number employed totaled 135,208,000. Thus, the unemployment rate was 4.0 percent.Table 513 of the Statistical Abstract shows that 2,253,000 people received public assistance in 2000. Assuming all of these were non-working and out of the labor force, their inclusion in the calculation of the unemployment rate would increase the unemployment rate to(140,863,000 + 2,253,000 – 135,208,000) / (140,863,000 + 2,253,000) = 5.5%.(b) How does the exclusion of black market workers affect the calculation of the unemployment rate? Estimate, the best you can, what the 2000 unemployment rate would have been if workers in the underground economy had been included in the calculation.Excluding black market workers from the calculation of the unemployment rate keeps the unemployment rate artificially high. At the best, black market workers are not counted in the labor force, but at the worst, the black market workers claim to be in the labor force and without a job. The problem is that there is no (or very little) data on the black market by definition. Some researchers have estimated the underground economy to be on the order of 10 to 20 percent of activity in the U.S. Suppose half of underground economy workers have regular market jobs as well. Suppose further that of the remaining half, one half claim to be unemployed while the other half is out of the labor force. Thus, 10 percent of the unemployed workers are the number of underground economy workers in the labor force without a job: 10 percent of(140,863,000 – 135,208,000) = 565,500. An equal number say they are not in the labor force. (And twice this number is already reporting having a legitimate job.) Using these estimates, therefore, the labor force should be 140,863,000 + 565,500 = 141,428,500, while the number employed should be 135,208,000 + 565,500 + 565,500 = 136,339,000. Thus, the unemployment rate would be(141,428,500 – 136,339,000) / 141,428,500 = 3.6%.13-5. Compare two unemployed workers; the first is 25 years old and the second is 55 years old. Both workers have similar skills and face the same wage offer distribution. Suppose that both workers also incur similar search costs. Which worker will have a higher asking wage? Why? Can search theory explain why the unemployment rate of young workers differs from that of older workers?The marginal revenue of search depends on the length of the payoff period. Younger workers have the most to gain from obtaining higher paying jobs, since they can then collect the returns from their search investment over a longer expected work-life. As a result, it pays for younger workers to set their asking wage at a relatively high level. This implies that younger workers will tend to have higher unemployment rates and longer spells of unemployment than older workers.13-6. Suppose the government proposes to increase the level of UI benefits for unemployed workers.A particular industry is now paying efficiency wages to its workers in order to discourage them from shirking. What is the effect of the proposed legislation on the wage and on the unemployment rate for workers in that industry?The introduction of UI benefits shifts the no-shirking supply curve upwards (from NS to NS′), because a higher wage would have to be paid in order to attract the same number of workers who do not shirk. As a result, the new equilibrium (point Q′) entails a higher efficiency wage and leads to a larger number of unemployed workers.Dploym ent13-7. It is well known that more-educated workers are less likely to be unemployed and haveshorter unemployment spells than less-educated workers. Which theory(ies), the job search model, the sectoral shifts hypothesis, or the efficiency wage model, can explain this empirical correlation?Two of the theories in question can be formulated in such a way that they each predict that more-educated workers will have less unemployment and shorter spells of unemployment than less-educated workers.The job search model suggests that highly educated workers would have a lower unemployment rate either if they have relatively higher search costs or relatively lower gains from search. It could then be argued, for example, that search costs are (relatively) higher for highly-educated workers than for less-educated workers, perhaps because the nature of the job match between a highly educated worker and a firm is much more complex than the type of job match required between the firm and a worker who does repetitive tasks.Similarly, it is plausible to argue that it is easier to retool a highly-educated worker than a less-educated worker. The decline in demand in particular industries, then, leads to sectoral shift that can be better weathered by highly-educated workers.The efficiency wage model, however, has a harder time explaining the correlation. Presumably, the output of highly-educated workers is more difficult to measure than the output of less-educated workers. As a result, efficiency wages are more likely to arise in industries that employ highly-educated workers, and these industries (which pay above-market wages) would have to maintain a pool of unemployed workers in order to keep the employed workers in line.13-8. Suppose a country has 100 million inhabitants. The population can be divided into the employed, the unemployed, and the persons who are out of the labor force (OLF). In any given year, the transition probabilities among the various categories are given by:Moving Into:Employed Unemployed OLFEmployed 0.94 0.02 0.04 Unemployed 0.20 0.65 0.15 Moving From: OLF 0.05 0.03 0.92These transition probabilities are interpreted as follows. In any given year, 2 percent of the workers who are employed become unemployed; 20 percent of the workers who are unemployed find jobs, and so on. What will be the steady-state unemployment rate?Use E for the number of employed people, U for the number of unemployed, and N for the number not participating. The flows of people among the three categories can be found by multiplying these numbers with respective probabilities in the table. In the steady-state, the flows into each category must exactly balance the outflows. This produces the following equations:Employed: E = .94E + .20U + .05NUnemployed: U = .02E + .65U + .03NOLF: N = .04E + .15U + .92NOnly two of the three equations can be used, however, as E + U + N = 100 million. The steady-state solutions for E, U, and N can now be found with brute force algebra. The solution is that 54.273 million are employed, 6.466 million are unemployed, and 39.261 million are not in the labor force. The steady-state unemployment rate is then%646.10739.60466.6100100=×=×+=E U U u .13-9. Consider an economy with 250,000 adults, of which, 40,000 are retired senior citizens, 20,000 are college students, 120,000 are employed, 8,000 are looking for work, and 62,000 stay at home. What is the labor force participation rate? What is the unemployment rate?The labor force participation rate = ( 120,000 + 8,000 ) / 250,000 = 51.2 percent.The unemployment rate = 8,000 / ( 120,000 + 8,000 ) = 6.25 percent.13-10. Consider an economy with 3 types of jobs. The table below shows the jobs, the frequency with which vacancies open up on a yearly basis, and the income associated with each job. Searching for a job costs $C per year and generates at most 1 job offer. There is a 20 percent chance of not generating any offer in a year. (Note: the expected search duration for a job with probability p of appearing is 1/p years.)Job Type Frequency IncomeA 30 percent $60,000B 20 percent $100,000C 30 percent $80,000As a function of C , specify the optimal job search strategy if the worker maximizes her expected income net of search costs.There are four possible strategies for the worker: accept any job paying at least $100,000, accept any job paying at least $80,000, accept any job paying at least $60,000, or do not search for a job.Under the first strategy, the worker will only accept a B job. The expected search time for a B job is 5 years. Thus, the expected value of this strategy is $100,000 – 5C .Under the second strategy, the worker will accept a B or a C job. The expected search time, therefore, is 2 years (i.e., there is a 50 percent chance of receiving a B or a C job in a year, so the search time is 1/0.5 =2). Thus, the expected value of this strategy isC C 2000,88$2)000,80($3.02.03.0)000,100($3.02.02.0−=−+++.Under the third strategy, the worker will accept any of the three jobs. The expected search time, therefore, is 1.25 years, and the expected value of this strategy isC C 25.1500,77$25.1)000,60($8.03.0)000,80($8.03.0)000,100($8.02.0−=−++.Under the fourth strategy, the worker does not search, and therefore does not find a job or incur search costs, for an expected payoff of $0.One can now compare the four expected payoffs to determine that the optimal search strategy is:Accept the first B job if C < $4,000.Accept the first B or C job if $4,000 # C < $14,000.Accept the first job of any kind if $14,000 # C < $62,000.Don’t search if $62,000 # C .13-11. (a) A country is debating whether to fund a national database of job openings and giving all unemployed workers free access to it. What effect would this plan have on the long-rununemployment rate? What effect would this plan have on the average duration of unemployment? Why?Lower search costs would probably increase the unemployment rate. Lower search costs (similar to extended UI benefits) will cause workers to keep their asking wage higher for a longer time. Thus, unemployed workers will be more selective in the jobs they accept. The result is that workers remain unemployed for longer periods of time. It is also possible that lower search costs will entice workers to quit their jobs in order to look for a better job. This will also increase the unemployment rate.(b) A country is debating whether to impose a $10,000 tax on employers for every worker they lay-off. What effect would this plan have on the long-run unemployment rate? What effect would this plan have on the average duration of unemployment?This policy would cause firms, in the long-run, to be very cautious in hiring new workers. (This cautious behavior is evident in Japan and some countries in Europe. The UI system in the US may also cause firms to be a bit cautious in hiring new workers.) Thus, the unemployed will remain unemployed for longer durations. The effect on the unemployment rate is a little ambiguous. The unemployment rate wouldlikely increase in the long-run, but one could also argue that the end result will be less labor turnover and, therefore, a lower rate of unemployment, especially if unemployed workers under the proposed rules are more easily discouraged and exit the labor force all together.。

高二英语经济预测单选题50题1. The GDP of a country measures the total value of all final goods and services produced within a country's borders _.A. in a given yearB. for several yearsC. since its establishmentD. in a future year答案:A。
解析:GDP(国内生产总值)是衡量一个国家在特定的一年里,在其境内生产的所有最终商品和服务的总价值。
选项A“in a given year” 在给定的一年)符合GDP的定义中关于时间的界定。
选项B“for several years” 好几年)不是GDP计算的常规时间跨度。
选项C“since its establishment”(自从它建立以来)这种时间界定不符合GDP的计算方式。
选项D“in a future year”(在未来的一年),GDP 是对已经发生的生产成果的衡量,不是未来的。
2. Inflation refers to _.A. a decrease in the general price levelB. an increase in the general price levelC. a stable price levelD. a random change in price level答案:B。
解析:通货膨胀(Inflation)指的是总体物价水平的上升。
选项A“a decrease in the general price level” 总体物价水平下降)是通货紧缩的概念。
选项C“a stable price level”( 稳定的物价水平)与通货膨胀概念相悖。
选项D“a random change in price level”(物价水平随机变化)没有准确表达通货膨胀是物价上升这一概念。

阅读是工作和日常生活中获取信息的一项重要手段,也是语言获得的重要途径之一。
近年来,区域经济的发展带动了对商务英语阅读教学的关注。
本文以高职学生为研究对象,以能力为导向,在分析商务英语阅读中图式的特点和功能的基础上,探讨图式理论对提高商务英语专业学生阅读能力的促进作用。
一、图式的概念和分类图式是由英国心理学家巴特利特(Bartlett,F.)提出,图式是阅读者对世界知识的总和,是读者从不同经历中获取经验和知识,并按情景分门别类储存于大脑的知识结构的立体网络。
20世纪70年代后期,美国人工智能专家鲁美哈特在前人研究的基础上,将图式的概念发展成为一种系统、完整的理论——图式理论。
该理论指出:当读者在理解新事物时,需要将事物与已知的观念、过去的经历和已有知识联系起来。
Cook(1989)认为图式是指读者头脑中的“先存知识”和“背景知识”。
图式在阅读理解过程中起着重要作用。
根据Carrell and Eisterhold(1983)的图式理论,图式可分为语言、形式和内容三类。
读者理解语言材料的最有效的过程就是头脑中的图式与语言材料所提供的信息之间相互作用的过程。
在此过程中,读者根据已有的背景知识和经验在“自上而下”的过程中对阅读材料做出推测;在“自下而上”的过程中对文字、语法等进行解码,构成篇章意义。
在商务英语阅读中,三类图式具备了一定的特点,在交换的阅读过程中共同作用已达到有效的理解。
语言图式的特点主要体现在商务词汇的商务背景、一词多义和大量的术语及缩写词上;形式图式的特点则由商务阅读文本约定俗成的结构和格式来体现;内容图式的特点则表现为商务学科特点的内容和文化背景。
要达到顺利而有效的商务阅读理解,读者就必须具备一定的图式,并在交互阅读过程中有效地激活相关图式。
图式的缺失或未能激活都将导致阅读理解的失败。
二、语言图式“自下而上”(the bottom-up process )这种阅读方式的采用大多由语言图式产生。

Financial Markets and Institutions, 8e (Mishkin)Chapter 20 The Mutual Fund Industry20.1 Multiple Choice1) At the beginning of 2013, mutual funds held about ________ of the U.S. stock market was held by mutual funds.A) 30%B) 50%C) 10%D) 70%Answer: ATopic: Chapter 20.1 The Growth of Mutual FundsQuestion Status: Updated from Previous Edition2) The origins of mutual funds can be traced back to the mid to late 1800s in________.A) England and ScotlandB) New York CityC) BostonD) GermanyAnswer: ATopic: Chapter 20.1 The Growth of Mutual FundsQuestion Status: New Question3) ________ intermediation means that small investors can pool their funds with other investors to purchase high face value securities.A) LiquidityB) FinancialC) DenominationD) ShareAnswer: CTopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Previous Edition4) Mutual funds offer investors all of the following exceptA) greater-than-average returns.B) diversified portfolios.C) lower transaction costs.D) professional investment management.Answer: ATopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Previous Edition5) Mutual fundsA) pool the resources of many small investors by selling these investors shares and using the proceeds to buy securities.B) allow small investors to obtain the benefits of lower transaction costs in purchasing securities.C) provide small investors a diversified portfolio that reduces risk.D) do all of the above.E) do only A and B of the above.Answer: DTopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Previous Edition6) ________ enables mutual funds to consistently outperform a randomly selected group of stocks.A) Managerial expertiseB) DiversificationC) Denomination intermediationD) None of the aboveAnswer: DTopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Previous Edition7) At the end of 2012 there were over ________ separate mutual funds with total assets over ________.A) 800; $10 trillionB) 7,500; $13 trillionC) 10,000; $10 trillionD) 1,000; $7 trillionAnswer: BTopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Updated from Previous Edition8) Most mutual funds are structured in two ways. The most common structure is a(n) ________ fund, from which shares can be redeemed at any time at a price that is tied to the asset value of the fund. A(n) ________ fund has a fixed number of nonredeemable shares that are traded in the over-the-counter market.A) closed-end; open-endB) open-end; closed-endC) no-load; closed-endD) no-load; loadE) load; no-loadAnswer: BTopic: Chapter 20.3 Mutual Fund StructureQuestion Status: Previous Edition9) Which of the following is an advantage to investors of an open-end mutual fund?A) Once all the shares have been sold, the investor does not have to put in more money.B) The investors can sell their shares in the over-the-counter market with low transaction fees.C) The fund agrees to redeem shares at any time.D) The market value of the fund's shares may be higher than the value of the assets held by the fund.Answer: CTopic: Chapter 20.3 Mutual Fund StructureQuestion Status: Previous Edition10) The net asset value of a mutual fund isA) determined by subtracting the fund's liabilities from its assets and dividing by the number of shares outstanding.B) determined by calculating the net price of the assets owned by the fund.C) calculated every 15 minutes and used for transactions occurring during the next 15-minute interval.D) calculated as the difference between the fund's assets and its liabilities. Answer: ATopic: Chapter 20.3 Mutual Fund StructureQuestion Status: Previous Edition11) ________ funds are the simplest type of investment funds to manage.A) BalancedB) Global equityC) GrowthD) IndexAnswer: DTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition12) The majority of mutual fund assets are now owned byA) individual investors.B) institutional investors.C) fiduciaries.D) business organizations.E) retirees.Answer: ATopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Previous Edition13) Capital appreciation funds select stocks of ________ and tend to be ________ risky than total return funds.A) large, established companies that pay dividends regularly; moreB) large, established companies that pay dividends regularly; lessC) companies expected to grow rapidly; moreD) companies expected to grow rapidly; lessAnswer: CTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition14) From largest to smallest in terms of total assets, the four classes of mutual funds areA) equity funds, bond funds, hybrid funds, money market funds.B) equity funds, money market funds, bond funds, hybrid funds.C) money market funds, equity funds, hybrid funds, bond funds.D) bond funds, money market funds, equity funds, hybrid funds.Answer: BTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition15) Measured by assets, the most popular type of bond fund is the ________ bond fund.A) state municipalB) strategic incomeC) governmentD) high-yieldAnswer: BTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition16) People who take their money out of insured bank deposits to invest in uninsured money market mutual funds have ________ risk because money market funds invest in ________ assets.A) high; long-termB) low; short-termC) high; short-termD) low; long-termAnswer: BTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition17) The largest share of assets held by money market mutual funds isA) Treasury bills.B) certificates of deposit.C) commercial paper.D) repurchase agreements.Answer: CTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition18) Which of the following is a feature of index funds?A) They have lower fees.B) They select and hold stocks to match the performance of a stock index.C) They do not require managers to select stocks and decide when to buy and sell.D) All of the above.Answer: DTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition19) A deferred-load mutual fund charges a commissionA) when shares are purchased.B) when shares are sold.C) both when shares are purchased and when they are sold.D) when shares are redeemed.Answer: DTopic: Chapter 20.5 Fee Structure of Investment FundsQuestion Status: Previous Edition20) Over the past twenty years, mutual fund fees have ________, largely because________.A) fallen; SEC fee disclosure rules have led to greater competitionB) risen; investors have learned that funds with high fees provide better performanceC) risen; there has been collusion between large mutual fund companiesD) fallen; advances in information technology have lowered transaction costs Answer: ATopic: Chapter 20.5 Fee Structure of Investment FundsQuestion Status: Previous Edition21) Which of the following is most likely to be a no-load fund?A) Value fundsB) Hedge fundsC) Growth fundsD) Index fundsAnswer: DTopic: Chapter 20.5 Fee Structure of Investment FundsQuestion Status: Previous Edition22) When investors switch between funds within the same fund family, mutual funds may chargeA) a contingent deferred sales charge.B) a redemption fee.C) an exchange fee.D) 12b-1 fees.E) an account maintenance fee.Answer: CTopic: Chapter 20.5 Fee Structure of Investment FundsQuestion Status: Previous Edition23) The Securities Acts of 1933 and 1934 did notA) regulate the activities of investment funds.B) require funds to register with the SEC.C) include antifraud rules covering the purchase and sale of fund shares.D) apply to investment funds.Answer: BTopic: Chapter 20.6 Regulation of Mutual FundsQuestion Status: Previous Edition24) The largest share of total investment in mutual funds is inA) stock funds.B) hybrid funds.C) bond funds.D) money market funds.Answer: ATopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition25) Over ________ of the total daily volume in stocks is due to institutions initiating trades.A) 70%B) 50%C) 25%D) 90%Answer: ATopic: Chapter 20.6 Regulation of Mutual FundsQuestion Status: New Question26) Hedge funds areA) low risk because they are market-neutral.B) low risk if they buy Treasury bonds.C) low risk because they hedge their investments.D) high risk because they are market-neutral.E) high risk, even though they may be market-neutral.Answer: ETopic: Chapter 20.7 Hedge FundsQuestion Status: Previous Edition27) The near collapse of Long Term Capital Management was caused byA) the high management fees charged by the fund's two Nobel Prize winners.B) the fund's high leverage ratio of 20 to 1.C) a sharp decrease in the spread between corporate bonds and Treasury bonds.D) a sharp increase in the spread between corporate bonds and Treasury bonds.E) the fund's shift away from a market-neutral investment strategy.Answer: DTopic: Chapter 20.7 Hedge FundsQuestion Status: Previous Edition28) Conflicts arise in the mutual funds industry because ________ cannot effectively monitor ________.A) investment advisers; directorsB) directors; shareholdersC) shareholders; investment advisersD) investment advisers; stocks that will outperform the overall marketAnswer: CTopic: Chapter 20.8 Conflicts of Interest in the Mutual Fund IndustryQuestion Status: Previous Edition29) Late trading is the practice of allowing orders received ________ to trade at the ________ net asset value.A) before 4:00 PM; 4:00 PMB) after 4:00 PM; 4:00 PMC) after 4:00 PM; next day'sD) before 4:00 PM; previous day'sAnswer: BTopic: Chapter 20.8 Conflicts of Interest in the Mutual Fund IndustryQuestion Status: Previous Edition30) Market timingA) takes advantage of time differences between the east and west coasts of the United States.B) takes advantage of arbitrage opportunities in foreign stocks.C) takes advantage of the time lag between the receipt and execution of orders.D) is discouraged by the stiff fees mutual funds charge every investor for buying and then selling shares on the same day.Answer: BTopic: Chapter 20.8 Conflicts of Interest in the Mutual Fund IndustryQuestion Status: Previous Edition31) Late trading and market timingA) allow large, favored investors in a mutual fund to profit at the expense of other investors in the fund.B) hurt ordinary investors by increasing the number of fund shares and diluting the fund's net asset value.C) are both A and B of the above.D) are none of the above.Answer: CTopic: Chapter 20.8 Conflicts of Interest in the Mutual Fund Industry Question Status: Previous Edition32) Which of the following is not a proposal to deal with abuses in the mutual fund industry?A) Strictly enforce the 4:00 PM net asset value rule.B) Make redemption fees mandatory.C) Disclose compensation arrangements for investment advisers.D) Increase the number of dependent directors.Answer: DTopic: Chapter 20.8 Conflicts of Interest in the Mutual Fund IndustryQuestion Status: Previous Edition33) ________ means the investors can convert their investment into cash quickly at a low cost.A) Liquidity intermediationB) Denomination intermediationC) DiversificationD) Managerial expertiseAnswer: ATopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Previous Edition34) At the start of 2014, one share of Berkshire Hathaway's A-shares was trading at over $150,000. ________ in an mutual fund gives a small investor access to these shares.A) Liquidity intermediationB) Denomination intermediationC) DiversificationD) Managerial expertiseAnswer: BTopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Previous Edition35) Mutual fund companies frequently offer a number of separate mutual funds called ________.A) indexesB) complexesC) componentsD) actuariesAnswer: BTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition36) Equity funds can be placed in which class according to the Investment Company Institute?A) Capital appreciation fundsB) World fundsC) Total return fundsD) All of the aboveAnswer: DTopic: Chapter 20.4 Investment Objective Classes Question Status: Previous Edition37) Government bonds are essentially default risk-free, ________ returns.A) and will yield highB) and will yield the highestC) but will have relatively lowD) none of the aboveAnswer: CTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition38) ________ bonds combine stocks into one fund.A) HybridB) Money marketC) MunicipalD) EquityAnswer: ATopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition39) All ________ are open-end investment funds that invest only in money market securities.A) Stock fundsB) Bond fundsC) Money market mutual fundsD) all of the aboveAnswer: CTopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition20.2 True/False1) The larger the number of shares traded in a stock transaction, the lower the transaction costs per share.Answer: TRUETopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Previous Edition2) The increase in the number of defined contribution pension funds has slowed the growth of mutual funds.Answer: FALSETopic: Chapter 20.1 The Growth of Mutual FundsQuestion Status: Previous Edition3) Mutual funds accounted for $5.3 trillion, or 27%, of the $19.5 trillion U.S. retirement market at the beginning of 2013.Answer: TRUETopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Updated from Previous Edition4) Among the investors in mutual funds, only about 25% cite preparing for retirement as one of their main reasons for holding shares.Answer: FALSETopic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Updated from Previous Edition5) Open-end mutual funds are more common than closed-end funds.Answer: TRUETopic: Chapter 20.3 Mutual Fund StructureQuestion Status: Previous Edition6) The net asset value of a mutual fund is the average market price of the stocks, bonds, and other assets the fund owns.Answer: FALSETopic: Chapter 20.3 Mutual Fund StructureQuestion Status: Previous Edition7) A mutual fund's board of directors picks the securities that will be held and makes buy and sell decisions.Answer: FALSETopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition8) Money market mutual funds originated when the brokerage firm Merrill Lynch offered its customers an account from which funds could be taken to purchase securities and into which funds could be deposited when securities were sold. Answer: TRUETopic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition9) A deferred load is a fee charged when shares in a mutual fund are redeemed. Answer: TRUETopic: Chapter 20.5 Fee Structure of Investment FundsQuestion Status: Previous Edition10) Several academic research studies show that investors earn higher returns by investing in mutual funds that charge higher fees.Answer: FALSETopic: Chapter 20.5 Fee Structure of Investment FundsQuestion Status: Previous Edition11) Hedge funds have a minimum investment requirement of between $100,000 and$20 million, with the typical minimum investment being $1 million.Answer: TRUETopic: Chapter 20.7 Hedge FundsQuestion Status: New Question12) SEC research suggests that about three-fourths of mutual funds let privileged shareholders engage in market timing.Answer: TRUETopic: Chapter 20.8 Conflicts of Interest in the Mutual Fund IndustryQuestion Status: Previous Edition13) One factor explaining the rapid growth in mutual funds is that they are financial intermediaries that are not regulated by the federal government.Answer: FALSETopic: Chapter 20.1 The Growth of Mutual FundsQuestion Status: Previous Edition14) Whether a fund is organized as a closed- or an open-end fund, is will have the same basic organizational structure.Answer: TRUETopic: Chapter 20.3 Mutual Fund StructureQuestion Status: Previous Edition15) The primary purpose of loads is to provide compensation for sales brokers. Answer: TRUETopic: Chapter 20.5 Fee Structure of Investment FundsQuestion Status: Previous Edition16) Mutual funds are regulated under four federal laws designed to protect investors. Answer: TRUETopic: Chapter 20.6 Regulation of Mutual FundsQuestion Status: Previous Edition20.3 Essay1) What benefits do mutual funds offer investors?Topic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: Previous Edition2) How is a mutual fund's net asset value calculated?Topic: Chapter 20.3 Mutual Fund StructureQuestion Status: Previous Edition3) How did money market mutual funds originate and why did they become especially popular in the late 1970s and early 1980s?Topic: Chapter 20.1 The Growth of Mutual FundsQuestion Status: Previous Edition4) How does the governance structure of mutual funds lead to asymmetric information and conflicts of interest?Topic: Chapter 20.8 Conflicts of Interest in the Mutual Fund IndustryQuestion Status: Previous Edition5) Describe the practices of late trading and market timing and explain how these practices harm a mutual fund's shareholders.Topic: Chapter 20.8 Conflicts of Interest in the Mutual Fund IndustryQuestion Status: Previous Edition6) Discuss the proposals that have been made to reduce the conflict of interest abuses in the mutual funds industry.Topic: Chapter 20.8 Conflicts of Interest in the Mutual Fund IndustryQuestion Status: Previous Edition7) How is an index fund different from the other four primary investment objective classes for mutual funds?Topic: Chapter 20.4 Investment Objective ClassesQuestion Status: New Question8) Discuss the four primary classes of mutual funds available to investors.Topic: Chapter 20.4 Investment Objective ClassesQuestion Status: Previous Edition9) What are the five benefits of mutual funds?Topic: Chapter 20.2 Benefits of Mutual FundsQuestion Status: New Question10) What is the difference between an open-end and a closed-end mutual fund? Topic: Chapter 20.3 Mutual Fund StructureQuestion Status: New Question11) What are two key differences between a traditional mutual fund and a hedge fund?Topic: Chapter 20.7 Hedge FundsQuestion Status: New Question。

Duration Modeling Techniques for Continuous Speech RecognitionJanne Pylkk¨o nen and Mikko KurimoNeural Networks Research CentreHelsinki University of Technology,Finlandjanne.pylkkonen@hut.fi,mikko.kurimo@hut.fiAbstractPhone durations play a significant part in the com-prehension of speech.The duration information is still mostly disregarded in automatic speech recognizers due to the use of hidden Markov models(HMMs)which are deficient in modeling phone durations properly.Previous results have shown that using different approaches for ex-plicit duration modeling have improved the isolated word recognition in English.However,a unified comparison between the methods has not been reported.In this paper three techniques for explicit duration modeling are compared and evaluated in a large vocab-ulary continuous speech recognition task.The target lan-guage was Finnish,in which phone durations are espe-cially important for proper understanding.The results show that the choice of the duration modeling technique depends on the speed requirements of the recognizer.The best technique required a slightly longer running time than without an explicit duration model,but achieved an 8%relative improvement to the letter error rate.1.IntroductionThe modern automatic speech recognition(ASR)sys-tems are based on modeling the phones with hidden Markov models(HMM),using HMM states in a left-to-right topology for each phone.The transition probabili-ties of the HMMs represent the statistical duration infor-mation of the phones.It has been noted that these transi-tion probabilities have little effect to the recognition per-formance[1],and hence it is customary to ignore the use of more detailed durational information and rely more on the actual acoustic data.The durational information is still worth of further examination.Although phone durations do not have ac-tual discriminative role in English,they do help in distin-guishing several words from each other,such as sit and seat or ship and sheep.In some other languages,for ex-ample in Finnish,phone durations can be the only clue in discriminating between certain words.Good duration modeling can therefore be a major issue.It has been reported in several papers that using ex-plicit state duration models with hidden Markov mod-els improve the recognition accuracy[2,3,4].However,most of the evaluations in these papers have been isolated word recognition tests with connected word models,not continuous speech recognition tests with phoneme based models nowadays in use.Besides,no single method have been found which would completely satisfy the modeling needs,and the different approaches have varying implica-tions,for example,to the recognition efficiency.To gain more insight into this matter,this paper presents a com-parison between three different extensions to integrate ex-plicit duration models into the HMMs.The modeling techniques are evaluated using a modern phoneme based ASR[5]in a large vocabulary continuous speech recog-nition(LVCSR)task.2.HMM based duration modelingtechniquesIncorporating explicit state duration models into the HMMs introduces problems,as it breaks up some of the assumptions which are employed in the efficient HMM algorithms.A direct consequence of the Markov assump-tion is that state durations have a geometric distribution, defined by the probability of the self-transition.When this distribution is replaced with an explicitly defined one,the Markov assumption no longer holds.The Baum-Welch and Viterbi algorithms[6]used tofind the opti-mal paths through an HMM heavily depend on this as-sumption,so they are no longer applicable in their basic forms.Modifying them to properly deal with the loss of this simplifying assumption seriously degrades their effi-ciency.The solution is then tofind some other restrictive assumptions or to use sub-optimal algorithms.Before reviewing the different duration modeling techniques,the distributions of phone durations arefirst examined.2.1.Phone durations distribution modelsFor a phone model with three HMM states,the prior distribution of a phone duration is the convolution of three geometric distributions determined by the transition probabilities of the HMM.The properties of this prior distribution can be analyzed by considering the state du-rations as independent random variables.The mean andFigure2:Sub-HMM topology.The rightmost state illus-trates the next HMM or sub-HMM state,so that the mini-mum duration in the sub-HMM is one.imum duration of one normal HMM state.Expanding each HMM state to this kind of sub-HMM introduces a large number of free parameters to be es-timated.It may be therefore necessary to constrain the parameters in some way.In[10]the number of states in sub-HMMs were determined by the number of occur-rences in the HMM state in the training phase,and the transition probabilities of all the sub-HMM states of all the phone models were set to be the same.In this work, a heuristic rule for determining the number of sub-HMM states was used so that goodfits to the measured dura-tion distributions were achieved with low numbers of sub-HMM states.On average,the sub-HMMs had3.8states. The transition probabilities were constrained byfitting a gamma distribution to the measured duration distribution.2.4.Post-processor duration modelBoth HSMM and ESHMM degrade the efficiency of the recognition,the former by altering the algorithms and the latter by introducing additional states for the HMMs. Juang et al.[2]proposed a duration model which avoids this kind of loss of efficiency.Their method uses the out-put of the Viterbi algorithm and ranks the proposed paths using better models for the state durations.The method is therefore called the post-processor duration model.The augmentation of the log likelihood given by the Viterbi algorithm can be stated aslogˆf=log f+αNj=1log d j(τj).(1)f denotes the likelihood score given by the Viterbi search,αis an empirical scaling factor,N is the number of dis-tinct HMM states through which the best path traversed, d j are the duration probability distribution functions of those states,andτj are the durations spent in each state.3.Evaluation3.1.SetupThe utility of the duration modeling techniques was eval-uated with speaker dependent speech recognition tests. Finnish was used as the target language,as the proper un-derstanding of Finnish is more dependent on the correct durational information than,for example,with English. The speech material was a book spoken by a professional speaker,which was a reasonable choice for minimizing the unwanted variation of phone durations.An extract of 12hours was used to train the models,and independent parts of9and30minutes were used as development and evaluation sets,respectively.The development set was used to optimize the empirical scaling factors for the log likelihoods of the language model,the transition proba-bilities,and the duration distribution probabilities.The speech recognition system used for the evaluation has been presented in[5].The number of triphone mod-els was empirically adjusted to the available data.For the language model,a morph based trigram model was used. All the duration distributions were modeled with gamma distributions.As the different duration modeling tech-niques affect both the efficiency and the accuracy of the recognition,the recognition tests were run with different pruning settings(affecting the optimality of the Viterbi algorithm)to achieve different running times.The run-ning time is indicated by a real-time factor,which should be interpreted only as a relative value for the number of reasons affecting the actual speed of the recognition.The recognition accuracy was measured by a letter error rate (LER).As compared with the word error rate(WER),it is more suitable for a language such as Finnish where rather long words consisting of many morphemes are common.3.2.ResultsFigure3shows the recognition accuracy as a function of the real-time factor for different setups.The model la-beled as“HMM”is the baseline result without explicit duration modeling.Thefigure shows clearly that the in-tended running speed affects the choice of the best du-ration modeling technique.For moderate speeds(real-time factors10to30)the post-processor model functions best.But if the pruning level of the recognition is set to low enough,the HSMM outperforms the others.The ESHMM does not seem to produce good results,despite its intuitive approach.All the models suffer from randomfluctuation in the LER measurements after they have reached their optimal running speed.This is due to inherent noise in the mea-surements,along with the effects resulting from the gen-eral pruning strategy used in the Viterbi algorithm.Mea-sured from the points of the best performance,the let-ter error rate of the post-processor duration model was 2.73%,corresponding to the word error rate of15.3%. The HSMM achieved a LER of2.63%(WER15.2%). Compared to the baseline result with a LER of2.88% (WER16.2%),the post-processor duration model im-proved the LER about5%,while the HSMM achieved about8%relative improvement.。

ARK方舟生存进化代码大全方舟指令按~ 进入控制台**24号补丁以后进入控制台改按TAB黑色是命令,绿色是中英说明-------------------------------------------------------------------------------多人模式---------------------------------------------------------SetCheatPlayer True Enables Cheat Menu 开启作弊选单SetCheatPlayer False Disables Cheat Menu 关闭作弊选单AdminCheat AllowPlayerToJoinNoCheck Whitelists a player 将玩家设为白名单AdminCheat DisallowPlayerToJoinNoCheck Removes player from whitelist 将玩家从白名单移除AdminCheat Broadcast Broadcasts a message to the whole server. 送出信息给所有人AdminCheat SetMessageOfTheDay Sets the MOD 设定MOD AdminCheat God Unkillable, except you can drown. 无敌AdminCheat Fly Able to Fly 飞行模式AdminCheat Walk Deactivates Flying 取消飞行模式AdminCheat Teleport Teleports you in the direction you are facing. 传送至你当前看的点AdminCheat Slomo <#> Changes server speed. Values are 1-5. 1 = Normal Speed 设定时间速度<1-5> ,1=正常速度AdminCheat PlayersOnly Freezes all Dinos at their current position. Also freezes crafting. 冻结所有恐龙行动,制作中的工作也会受影响AdminCheat Ghost Noclip, walk through walls/objects. 穿墙模式AdminCheat ForceTame Instantly tames a Dino. Can ride without saddle. 强制驯化恐龙(看著要驯的恐龙打这指令)AdminCheat AddExperience 1000 0 0 1 Gives yourself 1000 XP 给自己经验值1000(可改其它值)-AddExperience (value for first number) (toggle option in relation to tribe) (Second toggle) (third toggle) so in total there should be 4 separate numbers. AdminCheat GiveResources Gives you 50 of all resources 给各种资源物件50份AdminCheat InfiniteStats Infinite Hunger, Stamina, Ammo, etc.. 状态/子弹不减(饥饿、耐力、免装弹....等)BanPlayer Bans user from server 后面加玩家ID,将玩家踢出UnBanPlayer Unbans user from server 后面加玩家ID, 将玩家取消踢出AdminCheat DamageTarget Damages a creature you are looking at for a set amount 伤害当前所看的目标AdminCheat DestroyAllEnemies Destroys all enemies. They respawn after a while. 杀死所有的恐龙,过一会会重生出来GiveEngrams unlocks all crafting recipes for your character -* Bugged - You can't craft these recipes 开启所有蓝图(目前此功能有问题) AdminCheat HurtMe Deals damage to yourself 伤害自己(自杀)ToggleGun Toggles visibility of current equipped item 当前装备物品隐形开/关AdminCheat SetTimeOfDay Changes time of day 设定时间(后面要加时间如settimeofday 04:00)AdminCheat SetPlayerPos 0 0 0 Allows you to teleport to coordinates. 传送到座标( 如setplayerpos 12,12,132)AdminCheat SaveWorld Saves current worldstate 手动储存AdminCheat Quit Exits the current world. Use after saving for a safe shutdown. 离开游戏AdminCheat ExecSetSleeping True/False Puts character to sleep/wakes them up 设定玩家为睡眠(true)/醒来(false)AdminCheat EnemyInvisible True/False Makes all creatures ignoreyou even if you attack them 玩家隐身,恐龙就算被打也看不到AdminCheat DestroyAll Destroys all Objects/Dinos of a classname 删除所有物件及恐龙AdminCheat Summon Summons a dino at your location. 召唤一只恐龙到当前位置AdminCheat GiveItemNum Gives you an item. 给指定的物品请参照下面的物品ID >>例1:giveitemnum 105 1 1 false 给储存箱1个Stat FPS Shows your FPS and latency, usable by anyone. 显示帧数--------------------------------------------------------------------------------------------------------单人模式-----------------------------------------------------SetCheatPlayer True Enables Cheat Menu 开启作弊选单SetCheatPlayer False Disables Cheat Menu 关闭作弊选单God Unkillable, except you can drown. 无敌Fly Able to Fly 飞行模式Walk Deactivates Flying 取消飞行模式Teleport Teleports you in the direction you are facing. 传送至你当前看的点Slomo <#> Changes server speed. Values are 1-5. 1 =Normal Speed 设定时间速度<1-5> ,1=正常速度PlayersOnly Freezes all Dinos at their current position. Also freezes crafting. 冻结所有恐龙行动,制作中的工作也会受影响Ghost Noclip, walk through walls/objects. 穿墙模式ForceTame Instantly tames a Dino. Can ride without saddle. 强制驯化恐龙(看著要驯的恐龙打这指令)AddExperience 1000 0 0 1 Gives yourself 1000 XP 给自己经验值1000(可改其它值)-AddExperience (value for first number) (toggle option in relation to tribe) (Second toggle) (third toggle) so in total there should be 4 separate numbers. GiveResources Gives you 50 of all resources 给各种资源物件50份InfiniteStats Infinite Hunger, Stamina, Ammo, etc.. 状态/子弹不减(饥饿、耐力、免装弹....等)DamageTarget Damages a creature you are looking at for a set amount 伤害当前所看的目标DestroyAllEnemies Destroys all enemies. They respawn after a while. 杀死所有的恐龙,过一会会重生出来GiveEngrams unlocks all crafting recipes for your character -* Bugged - You can't craft these recipes 开启所有蓝图(目前此功能有问题) HurtMe Deals damage to yourself 伤害自己(自杀)例hurtme 1000ToggleGun Toggles visibility of current equipped item 当前装备物品隐形开/关SetTimeOfDay Changes time of day 设定时间(后面要加时间如settimeofday 04:00)SetPlayerPos 0 0 0 Allows you to teleport to coordinates. 传送到座标( 如setplayerpos 12,12,132)SaveWorld Saves current worldstate 手动储存Quit Exits the current world. Use after saving for a safe shutdown. 离开游戏ExecSetSleeping True/False Puts character to sleep/wakes them up 设定玩家为睡眠(true)/醒来(false)EnemyInvisible True/False Makes all creatures ignore you even if you attack them 玩家隐身,恐龙就算被打也看不到DestroyAll Destroys all Objects/Dinos of a classname 删除所有物件及恐龙Summon Summons a dino at your location. 召唤一只恐龙到当前位置GiveItemNum Gives you an item. 给指定的物品请参照下面的物品ID >>例1:giveitemnum 105 1 1 false 给储存箱1个Stat FPS Shows your FPS and latency, usable by anyone. 显示帧数cheat engine(CE) 修改表(27号补丁测试有效) ARK.CT (50.08 KB, 下载次数: 953)Full Player Status 玩家状态全满Player Pointer 各项属性(手动修改)Unlimited Ammo (untested) 无限子弹Unlimited Inventory 物品不减Unlimited Durability 耐用度不减Ignore Engram Requirements 忽略技能点需求Ignore Crafting Requirements 忽略蓝图需求Instant Taming 秒驯Unlimited Engram 无限技能点Unlimited Buff Durations 无限状态加成时间Inventory Selection Pointer 选定物品修改全物品IDItem ID Item Description1 Simple Pistol2 Assault Rifle3 Rocket Launcher4 Simple Bullet5 Bow6 Genade7 Wood8 Stone9 Metal10 Hide11 Chitin12 Raw Meat13 Spoiled Meat14 Cooked Meat15 Water Jar16 Water Jar (Full)17 Cloth Pants18 Cloth Shirt19 Cloth Hat20 Cloth Boots21 Cloth Gloves22 Hide pants23 Hide Shirt24 Hide Hat25 Hide Boots26 Hide Gloves27 Chitin Leggings28 Chitin Chestpiece29 Chitin Helmet30 Chitin Boots31 Chitin Gauntlets32 Stone Arrow33 Stone Pick34 Stone Hatchet35 Metal Pick36 Metal Hatchet37 Torch38 Paintbrush39 Campfire40 Standing Torch41 Hide Sleeping Bag42 Remote Detonator43 C4 Charge44 Blood Extraction Syringe45 Blood Pack46 Improvised Explosive Device47 Waterskin48 Waterskin(Full)49 Berrybush Seeds50 Fertilizer51 Bingleberry Soup52 Medical Brew53 Energy Brew54 Dinosaur Feces55 Human Feces56 Stegosaurus Egg57Spear58 Red Coloring59 Green Coloring60 Blue Coloring61 Yellow Coloring62 Purple Coloring63 Orange Coloring64 Black Coloring65 White Coloring66 Brown Coloring67 Cyan Coloring68 Purple Coloring69 Rex Saddle70 Tranq Arrow71 Pistol Hat Skin72 GPS73 Flint74 Metal Ingot75 Thatch76 Fiber77 Charcoal78 Crystal79 Thatch Roof80 Thatch Door81 Thatch Foundation82 Thatch Wall83 Thatch Doorframe84 Wooden Catwalk85 Wooden Ceiling86 Wooden Hatchframe87 Wooden Door88 Wooden Foundation89 Wooden Ladder90 Wooden Pillar91 Wooden Ramp92 Wooden Trapdoor93 Wooden Wall94 Wooden Doorframe95 Wooden WindowFrame96 Wooden Window97 Wooden Sign98 Blueprint: Note99 Citronal100 Parasaur Saddle101 Raptor Saddle102 Stego Saddle103 Trike Saddle104 Pulmonoscorpius Saddle105 Storage Box106 Large Storage Box107 Mortar and Pestle108 Sparkpowder109 Gunpowder110 Stone Irrigation Pipe - Intake111 Stone Irrigation Pipe - Straight 112 Stone Irrigation Pipe - Incline113 Stone Irrigation Pipe - Intersection 114 Stone Irrigation Pipe - Vertical 115 Stone Irrigation Pipe - Tap116 Amarberry Seed117 Amarberry118 Azulberry119 Tintoberry120 Mejoberry121 Narcoberry122 Stimberry123 Narcotic124 Stimulant125 Refining Forge126 Smithy127 Compost Bin128 Cooking Pot129 Simple Bed130 Small Crop Plot131 Pteranodon Saddle132 Longneck Rifle133 Citronal Seed134 Specimen Implant135 Bronto Saddle136 Wooden Fence Foundation 137 Compass138 Scope Attachment139 Slingshot140 Pike141 Radio142 Obsidian143 Dinosaur Gateway144 Simple Rifle Ammo145 Summon Broodmother 146 Cementing Paste147 Dinosaur Gate148 Artifact of the Hunter149 Artifact of the Pack150 Artifact of the Massive 151 Artifact of the Devious 152 Artifact of the Clever153 Artifact of the Skylord154 Artifact of the Devourer 155 Artifact of the Queen156 Artifact of the Strong157 Artifact of the Flamekeeper 158 Argentavis Talon159 Megalodon Tooth160 Tyrannosaur Arm161 Saurpod Vertebra162 Oil163 Silica Pearls164 Gasoline165 Electronics166 Polymer167 Metal Catwalk168 Metal Ceiling169Metal Hatchframe 170 Metal Door171 Metal Fence Foundation172 Metal Foundation173 Behemoth Gate174 Behemoth Gateway175 Metal Ladder176 Metal Pillar177 Metal Ramp178 Metal Trapdoor179 Metal Wall180 Metal Doorframe181 Metal Windowframe182 metal Window183 Super Test meat184 Flare Gun185 Fabricator186 Water Tank187 Parachute188 Air Conditioner189 Electrical Generator190 Electrical Outlet191 Inclined Electrical Cable192 Electrical Cable Intersection193 Straight Electrical Cable194 Vertical Electrical Cable195 Lamppost196 Refrigerator197 Auto Turret198 Remote Keypad199 Metal Irrigation Pipe - Inclined 200 Metal Irrigation Pipe - Tap201 Metal Irrigation Pipe - Intersection 202 Metal irrigation Pipe - Straight 203 Metal Irrigation Pipe - Tap204 Metal Irrigation Pipe - Vertical 205 Flashlight Attachment206 Silencer Attachment 207 Carbonemys Saddle 208 Sarco Saddle209 Ankylo Saddle210 Mammoth Saddle211 Megalodon Saddle 212 Sabertooth Saddle 213 Carno Saddle214 Argentavis Saddle215 Plesiosaur Saddle216 Chitin/Keratin217 Keratin218 Metal Sign219 Holo-Scope Attachment 220 Laser Attachment221 Wooden Billboard222 Flak Leggings223 Flak Chestpiece224 Flak Helmet225 Flak Boots226 Flak Gauntlets227 Enduro Stew228 Lazarus Chowder229 Calien Soup230 Fria Curry231 Focal Chilli232 Savoroot233 Longgrass1234 Rockarrot235 Azulberry Seed236 Tintoberry Seed237 Mejoberry Seed238 Narcoberry Seed239 Stimberry Seed240 Savoroot Seed241 Longgrass Seed242 Rockarrot Seed243 Metal Billboard244 Fabricated Pistol245 Advanced Bullet246 Advanced Rifle Bullet 247 Rocket Propelled Grenade 248 Medium Crop Plot249 Large Crop Plot250 Rare Flower251 Rare Mushroom252 Raw Prime Meat253 Cooked Prime Meat254 Battle Tartare255 Shadow Steak Saute256 Rockwell Recipes: Enduro Stew257 Rockwell Recipes: Lazarus Chowder 258 Rockwell Recipes: Calien Soup259 Rockwell Recipes: Fria Curry260 Rockwell Recipes: Focal Chilli261 Rockwell Recipes: Battle Tartare262 Rockwell Recipes: Shadow Steak Saute 263 Notes on Rockwell Recipes264 Wall Sign265 Metal Dinosaur Gateway266 Metal Dinosaur Gate267 Shotgun268 Simple Shotgun Ammo269 Metal WallSign270 Amarberry Seed271 Azulberry Seed272 Tintoberry Seed273 Narcoberry Seed274 Stimberry Seed275 Mejoberry Seed276 Citronal Seed277 Savaroot Seed278 Longgrass Seed279 Rockarrot Seed280 Flag281 Hunter Skin Hat282 Rex Stomped Glasses Saddle 283 Spyglass284 Spider Flag285 Phiomia Saddle286 Medium Dinosaur Feces 287 Large Dinosaur Feces288 Brontosaurus Egg289 Parasaur Egg290 Raptor Egg291 T-Rex Egg292 Triceratops Egg293 Parasaur ARK Founder Saddle Skin294 Dodo Egg---------------------------------------------------------------------------------------------------------------------------------------------------------------------全召唤陆上型Ankylo summon Ankylo_Character_BP_CAraneo summon SpiderS_Character_BP_CCarno summon Carno_Character_BP_CDilo summon Dilo_Character_BP_CDodo summon Dodo_Character_BP_CMammoth summon Mammoth_Character_BP_CParasaur summon Para_Character_BP_CPhioma summon Phiomia_Character_BP_CRaptor summon Raptor_Character_BP_CSaber summon Saber_Character_BP_CSarco summon Sarco_Character_BP_CBrontosaurus summon Sauropod_Character_BP_C Scorpion summon Scorpion_Character_BP_C Stegosaurus summon Stego_Character_BP_C Titanoboa summon BoaFrill_Character_BP_CT-Rex summon Rex_Character_BP_CTrike summon Trike_Character_BP_CTurtle summon Turtle_Character_BP_C水中型Coel(Fish) summon Coel_Character_BP_C Megalodon summon Megalodon_Character_BP_C Piranha summon Piranha_Character_BP_C空中型Argentavis summon Argent_Character_BP_COnyc summon Bat_Character_BP_CPtero summon Ptero_Character_BP_CBOSS型Broodmother Lyrix summon SpiderL_Character_BP_C。

US president George W. Bush knows he’s unpopular. But he thinks he has done his best to solve the financial crisis, in which "… the excesses of the past have caused a lot of folks to hurt when it comes to their 401(k)’s or jobs," Bush said in an interview with Fox News Channel last week. What is a 401(k)? This is the name of a retirement savings plan initiated by the US federal government. Employees can choose to put a certain amount of their salary into an account and withdraw the money when they retire. The money is invested collectively. The financial crisis has shrunk many people’s 401k funds. The fund’s name comes from the section of US law that initiated it: the 401(k) section of the US Internal Revenue Code, passed into law in 1978. Here are some other numbers that carry special significance in American English: 101 Pronounced "one-oh-one", it refers to courses intended for beginners – "English 101" (英语⼊门课), for example. The university offers 101 courses for those freshmen and sophomores who have little knowledge of mathematics. 411 When someone says 411, they are referring to information about something; 411 is the number Americans dial to find people’s telephone numbers. The number 114 is used for this service in China. So what’s the 411 on your recent job interview? [What’s the news about your recent job interview?] 9 times out of 10 = most of the time Nine times out of 10, she will cook a delicious meal. put 2 and 2 together = think about something I think if you put two and two together you will make the right decision.。

Financial Markets and Institutions, 8e (Mishkin)Chapter 14 The Mortgage Markets14.1 Multiple Choice1) Which of the following are important ways in which mortgage markets differ from the stock and bond markets?A) The usual borrowers in the capital markets are government entities and businesses, whereas the usual borrowers in the mortgage markets are individuals.B) Most mortgages are secured by real estate, whereas the majority of capital market borrowing is unsecured.C) Because mortgages are made for different amounts and different maturities, developing a secondary market has been more difficult.D) All of the above are important differences.E) Only A and B of the above are important differences.Answer: DTopic: Chapter 14.1 What Are Mortgages?Question Status: Previous Edition2) Which of the following are important ways in which mortgage markets differ from stock and bond markets?A) The usual borrowers in capital markets are government entities, whereas the usual borrowers in mortgage markets are small businesses.B) The usual borrowers in capital markets are government entities and large businesses, whereas the usual borrowers in mortgage markets are small businesses.C) The usual borrowers in capital markets are government entities and large businesses, whereas the usual borrowers in mortgage markets are small businesses and individuals.D) The usual borrowers in capital markets are businesses and government entities, whereas the usual borrowers in mortgage markets are individuals.Answer: DTopic: Chapter 14.1 What Are Mortgages?Question Status: Previous Edition3) Which of the following are true of mortgages?A) A mortgage is a long-term loan secured by real estate.B) A borrower pays off a mortgage in a combination of principal and interest payments that result in full payment of the debt by maturity.C) Over 80 percent of mortgage loans finance residential home purchases.D) All of the above are true of mortgages.E) Only A and B of the above are true of mortgages.Answer: DTopic: Chapter 14.1 What Are Mortgages?Question Status: Previous Edition4) Which of the following are true of mortgages?A) A mortgage is a long-term loan secured by real estate.B) Borrowers pay off mortgages over time in some combination of principal and interest payments that result in full payment of the debt by maturity.C) Less than 65 percent of mortgage loans finance residential home purchases.D) All of the above are true of mortgages.E) Only A and B of the above are true of mortgages.Answer: ETopic: Chapter 14.1 What Are Mortgages?Question Status: Previous Edition5) Which of the following are true of mortgage interest rates?A) Interest rates on mortgage loans are determined by three factors: current long-term market rates, the term of the mortgage, and the number of discount points paid.B) Mortgage interest rates tend to track along with Treasury bond rates.C) The interest rate on 15-year mortgages is lower than the rate on 30-year mortgages, all else the same.D) All of the above are true.E) Only A and B of the above are true.Answer: DTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition6) Which of the following are true of mortgages?A) More than 80 percent of mortgage loans finance residential home purchases.B) The National Banking Act of 1863 rewarded banks that increased mortgage lending.C) Most mortgages during the 1920s and 1930s were balloon loans.D) All of the above are true.E) Only A and C of the above are true.Answer: ETopic: Chapter 14.1 What Are Mortgages?Question Status: Previous Edition7) Which of the following is true of mortgage interest rates?A) Longer-term mortgages have lower interest rates than shorter-term mortgages.B) Mortgage rates are lower than Treasury bond rates because of the tax deductibility of mortgage interest rates.C) In exchange for points, lenders reduce interest rates on mortgage loans.D) All of the above are true.E) Only A and B of the above are true.Answer: CTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition8) Typically, discount points should not be paid if the borrower will pay off the loan in ________ years or less.A) 5B) 10C) 15D) 20Answer: ATopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition9) Which of the following is true of mortgage interest rates?A) Longer-term mortgages have higher interest rates than shorter-term mortgages.B) In exchange for points, lenders reduce interest rates on mortgage loans.C) Mortgage rates are lower than Treasury bond rates because of the tax deductibility of mortgage interest payments.D) All of the above are true.E) Only A and B of the above are true.Answer: ETopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition10) Which of the following reduces moral hazard for the mortgage borrower?A) CollateralB) Down paymentsC) Private mortgage insuranceD) Borrower qualificationsAnswer: BTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition11) Which of the following protects the mortgage lender's right to sell property if the underlying loan defaults?A) A lienB) A down paymentC) Private mortgage insuranceD) Borrower qualificationE) AmortizationAnswer: ATopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition12) Which of the following is true of mortgage interest rates?A) Mortgage rates are closely tied to Treasury bond rates, but mortgage rates tend to stay below Treasury rates because mortgages are secured with collateral.B) Longer-term mortgages have higher interest rates than shorter-term mortgages.C) Interest rates are higher on mortgage loans on which lenders charge points.D) All of the above are true.E) Only A and B of the above are true.Answer: BTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition13) During the early years of an amortizing mortgage loan, the lender appliesA) most of the monthly payment to the outstanding principal balance.B) all of the monthly payment to the outstanding principal balance.C) most of the monthly payment to interest on the loan.D) all of the monthly payment to interest on the loan.E) the monthly payment equally to interest on the loan and the outstanding principal balance.Answer: CTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition14) During the last years of an amortizing mortgage loan, the lender appliesA) most of the monthly payment to the outstanding principal balance.B) all of the monthly payment to the outstanding principal balance.C) most of the monthly payment to interest on the loan.D) all of the monthly payment to interest on the loan.E) the monthly payment equally to interest on the loan and the outstanding principal balance.Answer: ATopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition15) During the last years of a balloon mortgage loan, the lender appliesA) most of the monthly payment to the outstanding principal balance.B) all of the monthly payment to the outstanding principal balance.C) most of the monthly payment to interest on the loan.D) all of the monthly payment to interest on the loan.E) the monthly payment equally to interest on the loan and the outstanding principal balance.Answer: DTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition16) During the early years of a balloon mortgage loan, the lender appliesA) most of the monthly payment to the outstanding principal balance.B) all of the monthly payment to the outstanding principal balance.C) most of the monthly payment to interest on the loan.D) all of the monthly payment to interest on the loan.E) the monthly payment equally to interest on the loan and the outstanding principal balance.Answer: DTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition17) A borrower who qualifies for an FHA or VA loan enjoys the advantage thatA) the mortgage payment is much lower.B) only a very low or zero down payment is required.C) the cost of private mortgage insurance is lower.D) the government holds the lien on the property.Answer: BTopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition18) (I) Conventional mortgages are originated by private lending institutions, and FHA or VA loans are originated by the government. (II) Conventional mortgages are insured by private companies, and FHA or VA loans are insured by the government.A) (I) is true, (II) false.B) (I) is false, (II) true.C) Both are true.D) Both are false.Answer: BTopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition19) Borrowers tend to prefer ________ to ________, whereas lenders prefer ________.A) fixed-rate loans; ARMs; fixed-rate loansB) ARMs; fixed-rate loans; fixed-rate loansC) fixed-rate loans; ARMs; ARMsD) ARMs; fixed-rate loans; ARMsAnswer: CTopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition20) (I) ARMs offer lower initial rates and the rate may fall during the life of the loan. (II) Conventional mortgages do not allow a borrower to take advantage of falling interest rates.A) (I) is true, (II) is false.B) (I) is false, (II) is true.C) Both are true.D) Both are false.Answer: ATopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition21) Growing-equity mortgages (GEMs)A) help the borrower pay off the loan in a shorter time.B) have such low payments in the first few years that the principal balance increases.C) offer borrowers payments that are initially lower than the payments on aconventional mortgage.D) do all of the above.E) do only A and B of the above.Answer: ATopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition22) A borrower with a 30-year loan can create a GEM byA) simply increasing the monthly payments beyond what is required and designating that the excess be applied entirely to the principal.B) converting his ARM into a conventional mortgage.C) converting his conventional mortgage into an ARM.D) converting his conventional mortgage into a GPM.Answer: ATopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition23) Which of the following are useful for home buyers who expect their income to rise in the future?A) GPMsB) RAMsC) GEMsD) Only A and B are useful.E) Only A and C are useful.Answer: ETopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition24) Which of the following are useful for home buyers who expect their income to fall in the future?A) GPMsB) RAMsC) GEMsD) Only A and B are useful.E) Only A and C are useful.Answer: BTopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition25) Retired people can live on the equity they have in their homes by using aA) GEM.B) GPM.C) SAM.D) RAM.Answer: DTopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition26) Second mortgages serve the following purposes:A) they give borrowers a way to use the equity they have in their homes as security for another loan.B) they allow borrowers to get a tax deduction on loans secured by their primary residence or vacation home.C) they allow borrowers to convert their conventional mortgages into GEMs.D) all of the above.E) only A and B of the above.Answer: ETopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition27) Which of the following is a disadvantage of a second mortgage compared to credit card debt?A) The loans are secured by the borrower's home.B) The borrower gives up the tax deduction on the primary mortgage.C) The borrower must pay points to get a second mortgage loan.D) The borrower will find it more difficult to qualify for a second mortgage loan.Answer: ATopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition28) The share of the mortgage market held by savings and loans isA) over 50 percent.B) approximately 40 percent.C) approximately 20 percent.D) less than 5 percent.Answer: DTopic: Chapter 14.4 Mortgage-Lending InstitutionsQuestion Status: Updated from Previous Edition29) The share of the mortgage market held by commercial banks is approximatelyA) 50 percent.B) 30 percent.C) 15 percent.D) 5 percent.Answer: BTopic: Chapter 14.4 Mortgage-Lending Institutions Question Status: Updated from Previous Edition30) A loan-servicing agent willA) package the loan for an investor.B) hold the loan in their investment portfolio.C) collect payments from the borrower.D) do both A and C of the above.E) do both B and C of the above.Answer: CTopic: Chapter 14.5 Loan ServicingQuestion Status: Previous Edition31) Distinct elements of a mortgage loan includeA) origination.B) investment.C) servicing.D) all of the above.E) only B and C of the above.Answer: DTopic: Chapter 14.6 Secondary Mortgage MarketQuestion Status: Previous Edition32) The Federal National Mortgage Association (Fannie Mae)A) was set up to buy mortgages from thrifts so that these institutions could make more loans.B) funds purchases of mortgages by selling bonds to the public.C) provides insurance for certain mortgage contracts.D) does all of the above.E) does only A and B of the above.Answer: ETopic: Chapter 14.6 Secondary Mortgage MarketQuestion Status: Previous Edition33) The Federal Housing Administration (FHA)A) was set up to buy mortgages from thrifts so that these institutions could make more loans.B) funds purchases of mortgages by selling bonds to the public.C) provides insurance for certain mortgage contracts.D) does all of the above.E) does only A and B of the above.Answer: CTopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition34) ________ issues participation certificates, and ________ provides federal insurance for participation certificates.A) Freddie Mac; Freddie MacB) Freddie Mac; Ginnie MaeC) Ginnie Mae; Freddie MacD) Ginnie Mae; Ginnie MaeE) Freddie Mac; no oneAnswer: ETopic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Previous Edition35) REMICs are most likeA) Freddie Mac pass-through securities.B) Ginnie Mae pass-through securities.C) participation certificates.D) collateralized mortgage obligations.Answer: DTopic: Chapter 14.8 What Is a Mortgage-Backed Security? Question Status: Previous Edition36) Ginnie MaeA) insures qualifying mortgages.B) insures pass-through certificates.C) insures collateralized mortgage obligations.D) does only A and B. of the above.E) does only B and C of the above.Answer: BTopic: Chapter 14.8 What Is a Mortgage-Backed Security? Question Status: Previous Edition37) Mortgage-backed securitiesA) have been growing in popularity in recent years as institutional investors look for attractive investment opportunities.B) are securities collateralized by a pool of mortgages.C) are securities collateralized by both insured and uninsured mortgages.D) are all of the above.E) are only A and B of the above.Answer: DTopic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Previous Edition38) The most common type of mortgage-backed security isA) the mortgage pass-through, a security that has the borrower's mortgage payments pass through the trustee before being disbursed to the investors.B) collateralized mortgage obligations, a security which reduces prepayment risk.C) the participation certificate, a security which passes the borrower's mortgage payments equally among all the owners of the certificates.D) the securitized mortgage, a security which increases the liquidity of otherwise illiquid mortgages.Answer: ATopic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Previous Edition39) The interest rate borrowers pay on their mortgages is determined byA) current long-term market rates.B) the term.C) the number of discount points.D) all of the above.Answer: DTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition40) A loan for borrowers who do not qualify for loans at the usual market rate of interest because of a poor credit rating or because the loan is larger than justified by their income isA) a subprime mortgage.B) a securitized mortgage.C) an insured mortgage.D) a graduated-payment mortgage.Answer: ATopic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Previous Edition41) The percentage of the total loan paid back immediately when a mortgage loan is obtained, which lowers the annual interest rate on the debt, is calledA) discount points.B) loan terms.C) collateral.D) down payment.Answer: ATopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition42) Which of the following terms are found in mortgage loan contracts to protect the lender from financial loss?A) CollateralB) Down paymentC) Private mortgage insuranceD) All of the aboveAnswer: DTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition43) What factors are used in determining a person's FICO score?A) Past payment historyB) Outstanding debtC) Length of credit historyD) All of the aboveAnswer: DTopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition44) Between 2000 and 2005, home prices increased an average of ________ per year.A) 2%B) 4%C) 8%D) 12%Answer: CTopic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: New Question45) From 2000 to 2005, housing prices increased, on average, by over 40%. This run up in prices was caused byA) speculators.B) an increase in subprime loans, which increased demand for new and existing houses.C) both A and B.D) None of the above are correct.Answer: CTopic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Updated from Previous Edition14.2 True/False1) In 2012, mortgage loans to farms represented the largest proportion of mortgage lending in the U.S.Answer: FALSETopic: Chapter 14.1 What Are Mortgages?Question Status: New Question2) Down payments are designed to reduce the likelihood of default on mortgage loans.Answer: TRUETopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition3) Discount points (or simply points) are interest payments made at the beginning of a loan.Answer: TRUETopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition4) A point on a mortgage loan refers to one monthly payment of principal and interest.Answer: FALSETopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition5) Closing for a mortgage loan refers to the moment the loan is paid off.Answer: FALSETopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition6) Private mortgage insurance is a policy that guarantees to make up any discrepancy between the value of the property and the loan amount, should a default occur.Answer: TRUETopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition7) During the early years of a mortgage loan, the lender applies most of the payment to the principal on the loan.Answer: FALSETopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition8) One important advantage to a borrower who qualifies for an FHA or VA loan is the very low interest rate on the mortgage.Answer: FALSETopic: Chapter 14.3 Types of Mortgages9) Adjustable-rate mortgages generally have lower initial interest rates than fixed-rate mortgages.Answer: TRUETopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition10) Mortgage interest rates loosely track interest rates on three-month Treasury bills.Answer: FALSETopic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition11) An advantage of a graduated-payment mortgage is that borrowers will qualify for a larger loan than if they requested a conventional mortgage.Answer: TRUETopic: Chapter 14.3 Types of Mortgages12) Nearly half the funds for mortgage lending comes from mortgage pools and trusts.Answer: FALSETopic: Chapter 14.4 Mortgage-Lending InstitutionsQuestion Status: Updated from Previous Edition13) Many institutions that make mortgage loans do not want to hold large portfolios of long-term securities, because it would subject them to unacceptably high interest-rate risk.Answer: TRUETopic: Chapter 14.4 Mortgage-Lending InstitutionsQuestion Status: Previous Edition14) A problem that initially hindered the marketability of mortgages in a secondary market was that they were not standardized.Answer: TRUETopic: Chapter 14.6 Secondary Mortgage MarketQuestion Status: Previous Edition15) Mortgage-backed securities have declined in popularity in recent years as institutional investors have sought higher returns in other markets.Answer: FALSETopic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Previous Edition16) Mortgage-backed securities are marketable securities collateralized by a pool of mortgages.Answer: TRUETopic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Previous Edition17) Fannie Mae and Freddie Mac together either own or insure the risk on nearly one-fourth of America's residential mortgages.Answer: FALSETopic: Chapter 14.4 Mortgage-Lending InstitutionsQuestion Status: Previous Edition18) A FICO score below 660 is considered good while a score above 720 is likely to cause problems in obtaining a loan.Answer: FALSETopic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition19) Subprime loans are those made to borrowers who do not qualify for loans at the usual market rate of interest because of a poor credit rating or because the loan is larger than justified by their income.Answer: TRUETopic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Previous Edition14.3 Essay1) How has the modern mortgage market changed over recent years?Topic: Chapter 14.1 What Are Mortgages?Question Status: Previous Edition2) Explain the features of mortgage loans that are designed to reduce the likelihood of default.Topic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition3) What are points? What is their purpose?Topic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition4) How does an amortizing mortgage loan differ from a balloon mortgage loan?Topic: Chapter 14.2 Characteristics of the Residential MortgageQuestion Status: Previous Edition5) Evaluate the advantages and disadvantages, from both the lender's and borrower's perspectives, of fixed-rate and adjustable-rate mortgages.Topic: Chapter 14.3 Types of MortgagesQuestion Status: Previous Edition6) Why has the online lending market developed in recent years and what are the advantages and disadvantages of this development?Topic: Chapter 14.4 Mortgage-Lending InstitutionsQuestion Status: Previous Edition7) Why may Fannie Mae and Freddie Mac pose a threat to the health of the financial system?Topic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Previous Edition8) What are mortgage-backed securities, why were they developed, whattypes of mortgage-backed securities are there, and how do they work?Topic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: Previous Edition9) What are the benefits and side effects of securitized mortgages?Topic: Chapter 14.7 Securitization of MortgagesQuestion Status: Previous Edition10) Discuss the pros and cons of a subprime market for residential mortgages in the U.S.Topic: Chapter 14.8 What Is a Mortgage-Backed Security?Question Status: New Question。


2000-2013年考研英语历年真题和答案(英语一)ui2013年考研英语(一)真题 (6)Section I Use of English (6)Section II Reading Comprehension (11)Part APart B (35)Part C (42)Section III Writing (48)Part A48Part B (49)2013考研英语(一)答案 (50)Section I Use of English (50)Section II Reading Comprehension (57)Section III Writing (79)2012年考研英语(一)试题 (83)Section I Use of English (83)Section II Reading Comprehension.Part A87Part B (110)Part C (115)Section III Writing (118)Part APart B (119)2012考研英语(一)答案 (121)Section I (121)Section II Reading Comprehension (132)作文 (167)2011考研英语(一)试题 (172)Section I Use of English (172)Section II Reading Comprehension (178)Part A (178)Part B (205)Part C (211)Section ⅢWriting (216)Part A (216)Part B (216)2011考研英语(一)答案 (219)Section I Use of English (219)Section II Reading Comprehension (226)Section III Writing (244)2010年考研英语(一)试题 (250)Section I Use of English (250)Section II Reading Comprehension (251)Part A (251)Part B (258)Part C (260)Section ⅢWriting (260)Part A (260)Part B (261)2009年考研英语(一)试题 (262)Section I Use of English (262)Section I I Reading comprehension (263)Part A (263)Part B (270)Part C (271)Section ⅢWriting (272)Part A (272)Part B (272)2009年考研英语(一)答案 (274)Section I: Use of English (10 points) (274)Section II: Reading Comprehension (60 points) (274)Section III: Writing (30 points) (274)2008年考研英语(一)试题 (276)Section I Use of English (276)Section II Reading Comprehension (277)Part A (277)Part B (284)Part C (286)Section III Writing (287)Part A (287)Part B (287)2008年考研英语(一)答案 (289)Section I: Use of English (10 points) (289)Section II: Reading Comprehension (60 points) (289)Section III: Writing (30 points) (289)2007年考研英语(一)试题 (291)Section I Use of English (291)Section II Reading Comprehension (295)Part A (295)Part B (303)Part C (304)Section III Writing (305)Part A (305)Part B (306)2007年考研英语(一)答案 (307)Section I: Use of English (10 points) (307)Section II: Reading Comprehension (60 points) (307)Section III: Writing (30 points) (307)2006年考研英语(一)试题 (309)Section I Use of English (309)Section II Reading Comprehension (313)Part A (313)2002年考研英语(一)试题 (381)Section I Listening Comprehension (381)Part A (381)Part B (382)Part C (382)Section II Use of English (385)Section III Reading Comprehension (390)Part A (390)Part B (398)Section IV Writing (399)2002年考研英语(一)答案 (400)Section I: Listening Comprehension (20 points) (400)Section II: Use of English (10 points) (400)Section III: Reading Comprehension (50 points) (400)Section IV: Writing (20 points) (401)2001年考研英语(一)试题 (402)Section I Structure and Vocabulary (402)Part A (402)Part B (405)Section II Cloze Test (410)Section III Reading Comprehension (414)Section IV English-Chinese Translation (423)Section V Writing (424)2001年考研英语(一)答案 (426)Section I: Structure and Vocabulary (15 points) (426)Section II: Cloze Text (10 points) (426)Section III: Reading Comprehension (40 points) (426)Section IV: English-Chinese Translation (15 points) (426)Section V: Writing (20 points) (427)2000年考研英语(一)试题 (428)Section I Structure and Vocabulary (428)Part A (428)Part B (431)Part C (432)Section II Cloze Test (437)Section III Reading Comprehension (440)Section IV English-Chinese Translation (448)Section V Writing (449)2000年考研英语(一)答案 (451)Section I: Structure and Vocabulary (20 points) (451)Section III: Reading Comprehension (40 points) (451)Section IV: English-Chinese Translation (15 points) (451)Section V: Writing (15 points) (452)2013年考研英语(一)真题Section I Use of EnglishDirections: Read the following text. Choose the best word(s) for each numbered blank and mark A, B, C or D on ANSWER SHEET 1. (10 points) People are, on the whole, poor at considering background information when making individual decisions. At first glance this might seem like a strength that ___1___ the ability to make judgments which are unbiased by ___2___ factors. But Dr Simonton speculated that an inability to consider the big ___3___ was leading decision-makers to be biased by the daily samples of information they were working with. ___4___, hetheorized that a judge ___5___ of appearing too soft ___6___crime might be more likely to send someone to prison ___7___he had already sentenced five or six other defendants only to forced community service on that day.To ___8___this idea, they turned their attention to the university-admissions process. In theory, the ___9___ of an applicant should not depend on the few others___10___ randomly for interview during the same day, but Dr Simonton suspected the truth was___11___.He studied the results of 9,323 MBA interviews ___12___ by 31 admissions officers. The interviewers had ___13___ applicants on a scale of one to five. This scale ___14___ numerous factorsinto consideration. The scores were ___15___ used in conjunction w ith an applicant’s score on the GMAT, a standardized exam which is ___16___out of 800 points, to make a decision on whether to accept him or her.Dr Simonton found if the score of the previous candidate in a daily series of interviewees was 0.75 points or more higher than that of the one ___17___ that, then the score for the next applicant would___18___ by an average of 0.075 points. This might sound small, but to___19___the effects of such a decrease a candidate would need 30 more GMAT points than would otherwise have been ___20___.1. A grants B submits C transmits Ddelivers2. A minor B external C crucial D objective3. A issue B vision C picture D moment4. A Above all B On average C In principleD For example5. A fond B fearful C capable D thoughtless6. A in B for C to D on7. A if B until C though D unless8. A. test B. emphasize C. share D. promote9. A. decision B. quality C. status D. success10. A. found B. studied C. chosen D.identified11. A. otherwise B. defensible C. replaceable D. exceptional12. A. inspired B. expressed C. conductedD. secured13. A. assigned B. rated C. matched D. arranged14. A. put B. got C. took D. gave15. A. instead B. then C. ever D. rather16. A. selected B. passed C. marked D. introduced17. A below B after C above D before18. A jump B float C fluctuate D drop19. A achieve B undo C maintain D disregard20. A necessary B possible C promising D helpfulSection II Reading ComprehensionPart ADirections: Read the following four texts. Answer the questions below each text by choosing A, B, C or D. Mark your answers on ANSWER SHEET 1. (40 points)Text 1In the 2006 film version of The Devil Wears Prada ,Miranda Priestly, played by Meryl Streep, scolds her unattractive assistant for imagining that high fashion doesn’t affect her, Priestly explains how the deep blue color of the assistant’s sweater descended over the years from fashion shows to departments stores and to the bargain bin in which the poor girl doubtless found her garment.This top-down conception of the fashion business couldn`t be more out of date or at odds with the feverish would described in Overdressed, Elizabeth Cline`s three-year indictment of “fast fashion”. In the last decade or so, advances in technology have allowed mass-market labels such as Zara, H&M, and Uniqlo to react to trends more quickly and anticipate demand more precisely. Quicker turnarounds mean less wasted inventory, more frequent release, and more profit. These labels encourage style-conscious consumers tosee clothes as disposable-meant to last only a wash or two, although they don’t advertise that –and to renew their wardrobe every few weeks. By offering on-trend items at dirt-cheap prices, Cline argues, these brands have hijacked fashion cycles, shaking an industry long accustomed to a seasonal pace.The victims of this revolution, of course, are not limited to designers. For H&M to offer a $5.95 knit miniskirt in all its 2,300-pius stores around the world, it must rely on low-wage overseas labor, order in volumes that strain natural resources, and use massive amounts of harmful chemicals.Overdressed is the fashion world`s answer toconsumer-activist bestsellers like Michael Pollan`s. The Omnivore`s Dilemma. “Mass-produced clothing ,like fast food, fills a hunger and need, yet is non-durable and wasteful,”Cline argues. Americans, she finds, buy roughly 20 billion garments a year – about 64 items per person – and no matter how much they give away, this excess leads to waste.Towards the end of Overdressed, Cline introduced her ideal, a Brooklyn woman named Sarah Kate Beaumont, who since 2008 has made all of her own clothes –and beautifully. But as Cline is the first to note, it took Beaumont decades to perfect her craft; he r example can’t be knocked off.Though several fast-fashion companies have made efforts to curb their impact on labor and the environment –including H&M, with its green Conscious Collection line –Cline believes lasting change can only be effected by the customer. She exhibits the idealism common to many advocates of sustainability, be it in food or in energy. Vanity is a constant; people will only start shopping more sustainably when they can’t afford not to.21. Priestly criticizes her assistant for her[A] poor bargaining skill.[B] insensitivity to fashion.[C] obsession with high fashion.[D] lack of imagination.22. According to Cline, mass-market labelsurge consumers to[A] combat unnecessary waste.[B] shut out the feverish fashion world.[C] resist the influence of advertisements.[D] shop for their garments more frequently.23. The word “indictment”(Line 3, Para.2) is closest in meaning to[A] accusation.[B] enthusiasm.[C] indifference.[D] tolerance.24. Which of the following can be inferred from the last paragraph?[A] Vanity has more often been found in idealists.[B] The fast-fashion industry ignores sustainability.[C] People are more interested in unaffordable garments.[D] Pricing is vital to environment-friendly purchasing.25. What is the subject of the text?[A] Satire on an extravagant lifestyle.[B] Challenge to a high-fashion myth.[C] Criticism of the fast-fashion industry.[D] Exposure of a mass-market secret.Text 2An old saying has it that half of all advertising budgets are wasted-the trouble is, no one knows which half. In the internet age, at least in theory,this fraction can be much reduced. By watching what people search for, click on and say online, companies can aim “behavioral” ads at those most likely to buy.In the past couple of weeks a quarrel has illustrated the value to advertisers of such fine-grained information: Should advertisers assume that people are happy to be tracked and sent behavioral ads? Or should they have explicit permission?In December 2010 America's Federal Trade Commission (FTC) proposed adding a "do not track "(DNT) option to internet browsers ,so that users could tell advertisers that they did not want to be followed .Microsoft's Internet Explorer andApple's Safari both offer DNT ;Google's Chrome is due to do so this year. In February the FTC and Digital Advertising Alliance (DAA) agreed that the industry would get cracking on responding to DNT requests.On May 31st Microsoft Set off the row: It said that Internet Explorer 10, the version due to appear windows 8, would have DNT as a default.It is not yet clear how advertisers will respond. Getting a DNT signal does not oblige anyone to stop tracking, although some companies have promised to do so. Unable to tell whether someone really objects to behavioral ads or whether they are sticking w ith Microsoft’s default, some may ignore a DNT signal and presson anyway.Also unclear is why Microsoft has gone it alone. After all, it has an ad business too, which it says will comply with DNT requests, though it is still working out how. If it is trying to upset Google, which relies almost wholly on default will become the norm. DNT does not seem an obviously huge selling point for windows 8-though the firm has compared some of its other products favorably with Google's on that count before. Brendon Lynch, MMicrosoft's chief privacy officer, blogged: "we believe consumers should have more control." Could it really be that simple?26. It is suggested in paragraph 1 that“behavioral”ads help advertisers to:[A] ease competition among themselves[B] lower their operational costs[C] avoid complaints from consumers[D] provide better online services27. “The industry”(Line 6,Para.3) refers to:[A] online advertisers[B] e-commerce conductors[C] digital information analysis[D] internet browser developers28. Bob Liodice holds that setting DNT as a default[A] many cut the number of junk ads[B] fails to affect the ad industry[C] will not benefit consumers[D] goes against human nature29. which of the following is true according to Paragraph.6?[A] DNT may not serve its intended purpose[B] Advertisers are willing to implement DNT[C] DNT is losing its popularity among consumers[D] Advertisers are obliged to offer behavioral ads30. The author's attitude towards what Brendon Lynch said in his blog is one of:[A] indulgence[B] understanding[C] appreciation[D] skepticismText 3Up until a few decades ago, our visions of the future were largely - though by no means uniformly - glowingly positive. Science and technology would cure all the ills of humanity, leading to lives of fulfillment and opportunity for all.Now utopia has grown unfashionable, as we have gained a deeper appreciation of the range of threats facing us, from asteroid strike to epidemic flu and to climate change. You might even be tempted to assume that humanity has little future to look forward to.But such gloominess is misplaced. The fossil record shows that many species have endured formillions of years - so why shouldn't we? Take a broader look at our species' place in the universe, and it becomes clear that we have an excellent chance of surviving for tens, if not hundreds, of thousands of years . Look up Homo sapiens in the "Red List" of threatened species of the International Union for the Conversation of Nature (IUCN) ,and you will read: "Listed as Least Concern as the species is very widely distributed, adaptable, currently increasing, and there are no major threats resulting in an overall population decline."So what does our deep future hold? A growing number of researchers and organizations are now thinking seriously about that question.For example, the Long Now Foundation has its flagship project a medical clock that is designed to still be marking time thousands of years hence.Perhaps willfully, it may be easier to think about such lengthy timescales than about the more immediate future. The potential evolution of today's technology, and its social consequences, is dazzlingly complicated, and it's perhaps best left to science fiction writers and futurologists to explore the many possibilities we can envisage. That's one reason why we have launched Arc, a new publication dedicated to the near future.But take a longer view and there is a surprising amount that we can say withconsiderable assurance. As so often, the past holds the key to the future: we have now identified enough of the long-term patterns shaping the history of the planet, and our species, to make evidence-based forecasts about the situations in which our descendants will find themselves.This long perspective makes the pessimistic view of our prospects seem more likely to be a passing fad. To be sure, the future is not all rosy. But we are now knowledgeable enough to reduce many of the risks that threatened the existence of earlier humans, and to improve the lot of those to come.31. Our vision of the future used to beinspired by[A] our desire for lives of fulfillment[B] our faith in science and technology[C] our awareness of potential risks[D] our belief in equal opportunity32. The IUCN`s “Red List”suggest that human being are[A] a sustained species[B] a threaten to the environment[C] the world`s dominant power[D] a misplaced race33. Which of the following is true according to Paragraph 5?[A] Arc helps limit the scope of futurological studies.[B] Technology offers solutions to social problem.[C] The interest in science fiction is on the rise.[D] Our Immediate future is hard to conceive.34. To ensure the future of mankind, it is crucial to[A] explore our planet`s abundant resources[B] adopt an optimistic view of the world[C] draw on our experience from the past[D] curb our ambition to reshape history35. Which of the following would be the best title for the text?[A] Uncertainty about Our Future[B] Evolution of the Human Species[C] The Ever-bright Prospects of Mankind[D] Science, Technology and HumanityText 4On a five to three vote, the Supreme Court knocked out much of Arizona's immigration law Monday-a modest policy victory for the Obama Administration. But on the more important matter of the Constitution, the decision was an 8-0 defeat for the federal government and the states.In Arizona, United States, the majority overturned three of the four contested provisions of Arizona's controversial plan to have state and local police enforce federal immigrations law. The Constitutional principles that Washington alone has the power to "establish a uniform Rule ofnaturalization" and that federal laws precede state laws are noncontroversial. Arizona had attempted to fashion state police that ran to the existing federal ones.Justice Anthony Kennedy, joined by Chief Justice John Roberts and the Court's liberals, ruled that the state flew too close to the federal sun. On the overturned provisions the majority held the congress had deliberately "occupied the field" and Arizona had thus intruded on the federal's privileged powersHowever, the Justices said that Arizona police would be allowed to verify the legal status of people who come in contact with law enforcement. That`s because Congress has alwaysenvisioned joint federal-state immigration enforcement and explicitly encourages state officers to share information and cooperate with federal colleagues.Two of the three objecting Justice-Samuel Alito and Clarence Thomas-agreed with this Constitutional logic but disagreed about which Arizona rules conflicted with the federal statute. The only major objection came from Justice Antonin Scalia, who offered an even more robust defense of state privileges going back to the alien and Sedition Acts.The 8-0 objection to President Obama turns on what Justice Samuel Alito describes in his objection as “a shocking assertion of federalexecutive power”. The White House argued the Arizona`s laws conflicted with its enforcement priorities, even if state laws complied with federal statutes to the letter. In effect, the White House claimed that it could invalidate any otherwise legitimate state law that it disagrees with.Some powers do belong exclusively to the federal government, and control of citizenship and the borders is among them. But if Congress wanted to prevent states from using their own resources to check immigration status. It never did so. The administration was in essence asserting that because it didn't want to carry out Congress's immigration wishes, no state should be allowed to do so either. Every Justice rightlyrejected this remarkable claim.36. Three provisions of Arizona`s plan were overturned because they[A] deprived the federal police of Constitutional powers.[B] disturbed the power balance between different states.[C] overstepped the authority of federal immigration law.[D] contradicted both the federal and state policies.37. On which of the following did the Justices agree, according to Paragraph4?[A] Federal officers` duty to withhold immigrants` information.[B] States` independence from federal immigration law.[C] States` legitimate role in immigration enforcement.[D] Congress`s intervention in immigration enforcement.38. It can be inferred from Paragraph 5 that the Alien and Sedition Acts[A] violated the Constitution.[B] undermined the states` interests.[C] supported the federal statute.[D] stood in favor of the states.39. The White House claims that its power of enforcement[A] Outweighs that held by the states.[B] is dependent on the states` support.[C] is established by federal statutes.[D] rarely goes against state laws.40. What can be learned from the last paragraph?[A] Immigration issues are usually decided by Congress.[B] Justices intended to check the power of the Administration.[C] Justices wanted to strengthen its coordination with Congress.[D] The Administration is dominant over immigration issues.Part BDirections:In the following text, some sentences have been removed. For Questions 41-45, choose the most suitable one from the list A-G to fit into each of the numbered blanks. There are two extra choices, which do not fit in any of the blanks. Mark your answers on ANSWER SHEET1.(10 points)The social sciences are flourishing. As of 2005, there were almost half a million professional social scientists from all fields in the world, working both inside and outside academia. According to the World Social Science Report 2010, the number of social-science students worldwide has swollen by about 11% every yearsince 2000.Yet this enormous resource in not contributing enough to today`s global challenges including climate change, security, sustainable development and health.(41)______Humanity has the necessary agro-technological tools to eradicate hunger , from genetically engineered crops to artificial fertilizers . Here, too, the problems are social: the organization and distribution of food, wealth and prosperity.(42)____This is a shame—the community should be grasping the opportunity to raise its influence in the real world. To paraphrase the great social scientist Joseph Schumpeter: there is no radical innovation without creativedestruction.Today, the social sciences are largely focused on disciplinary problems and internal scholarly debates, rather than on topics with external impact.Analyses reveal that the number of papers including the keywords “environmental changed”or “climate change”have increased rapidly since 2004,(43)____When social scientists do tackle practical issues, their scope is often local: Belgium is interested mainly in the effects of poverty on Belgium for example .And whether the community’s work contributes much to an overall accumulation of knowledge is doubtful.The problem is not necessarily the amount of available funding (44)____this is an adequate amount so long as it is aimed in the right direction. Social scientists who complain about a lack of funding should not expect more in today`s economic climate.The trick is to direct these funds better. The European Union Framework funding programs have long had a category specifically targeted at social scientists. This year, it was proposed that system be changed: Horizon 2020, a new program to be enacted in 2014, would not have such a category. This has resulted in protests from social scientists. But the intention is not to neglect social science; rather, the complete opposite.(45)____That should create more collaborative endeavors and help to develop projects aimed directly at solving global problems.[A] It could be that we are evolving two communities of social scientists: one that is discipline-oriented and publishing in highly specialized journals, and one that is problem-oriented and publishing elsewhere, such as policy briefs.[B] However, the numbers are still small: in 2010, about 1,600 of the100,000 social-sciences papers published globally included one of these keywords.[C] The idea is to force social to integrate their work with other categories, including health anddemographic change food security, marine research and the bio-economy, clear, efficient energy; and inclusive, innovative and secure societies.[D] The solution is to change the mindset of the academic community, and what it considers to be its main goal. Global challenges and social innovation ought to receive much more attention from scientists, especially the young ones.[E] These issues all have root causes in human behavior. All require behavioral change and social innovations, as well as technological development. Stemming climate change, for example, is as much about changing consumption patterns and promoting tax acceptance as it is aboutdeveloping clean energy.[F] Despite these factors, many social scientists seem reluctant to tackle such problems. And in Europe, some are up in arms over a proposal to drop a specific funding category for social-science research and to integrate it within cross-cutting topics of sustainable development.[G] During the late 1990s , national spending on social sciences and the humanities as a percentage of all research and development funds-including government, higher education, non-profit and corporate -varied from around 4% to 25%; in most European nations , it is about 15%.Part CDirections: Read the following text carefully and then translate the underlined segments into Chinese. Your translation should be written clearly on ANSWER SHEET 2. (10 points)It is speculated that gardens arise from a basic need in the individuals who made them: the need for creative expression. There is no doubt that gardens evidence an impossible urge to create, express, fashion, and beautify and that self-expression is a basic human urge; (46) Yet when one looks at the photographs of the garden created by the homeless, it strikes one that, for all their diversity of styles, these gardens speak of various other fundamental urges, beyond that of decoration and creative expression.One of these urges had to do with creating a state of peace in the midst of turbulence, a “still point of the turning world,”to borrow a phrase from T. S. Eliot. (47)A sacred place of peace, however crude it may be, is a distinctly human need, as opposed to shelter, which is a distinctly animal need. This distinction is so much so that where the latter is lacking, as it is for these unlikely gardens, the former becomes all the more urgent. Composure is a state of mind made possible by the structuring of one’s relation to one’s environment. (48) The gardens of the homeless which are in effect homeless gardens introduce from into an urban environment where it either didn’t exist or was not discernible assuch. In so doing they give composure to a segment of the inarticulate environment in which they take their stand.Another urge or need that these gardens appear to respond to, or to arise from is so intrinsic that we are barely ever conscious of its abiding claims on us. When we are deprived of green, of plants, of trees, (49) most of us give into a demoralization of spirit which we usually blame on some psychological conditions, until one day we find ourselves in garden and feel the expression vanish as if by magic. In most of the homeless gardens of New York City the actual cultivation of plants is unfeasible, yet even so the compositions often seem to represent attempts。
问题:1。
前提"If your premise is established, your conclusions are easily deducible.""如果你的前提成立,那么就很容易推断出你的结论了。
"·论断的前题是本市没有高尔夫场和假日饭店,或是有但不够吸引人。
但这一前提在论断中没有被保障成立。
因为论断没有提供任何有关本市目前旅游设施的资料,这样我们就无法评估建一个高尔夫场等是必要还是浪费。
前提不成立,论断也就不成立。
2。
经济繁荣:The flourish of economy?3。
通货膨胀和贬值:Inflation & devaluation4。
消费水平/购买力:purchasing power经济形势economic situation5。
本地的优势劣势superiority & inferiority6。
参与研究的人群的性别、年龄、职业等特征的分布The distribution of the gender, the age, and the career of the participants in the study.7。
另外论者也没有告诉我们他们是否在采访中采取了措施以保证结果准确,比如采访话题是否会引导孩子谈论父母。
But we are told nothing about the way the poll was conducted and how well it represented the public opinionsAnd whether it guarantees whether it will influence8。
师资情况,学生结构The overall level of the faculty and the students.9。
它涉及到新添设备、运作等环节,这些都会增加开销。
论者没有提供资料证明这部分开销的上涨会小于远程学位帮助降低的开支。
PartⅠ.Decide whether each of the following statements is true or false (10%)每题1分, 答错不扣分1.I.perfec.market.existed.resource.woul.b.mor.mobil.an.coul.therefor.b.transferre.t.thos.countrie.mor.willin.t.pa..hig.pric.fo.them.. .. .2.Th.forwar.contrac.ca.hedg.futur.receivable.o.payable.i.foreig.currencie.t.insulat.th.fir.agains.exchang.rat.risk ... . )3.Th.primar.objectiv.o.th.multinationa.corporatio.i.stil.th.sam.primar.objectiv.o.an.firm.i.e..t.maximiz.sharehol de.wealth.. .. )4..lo.inflatio.rat.tend.t.increas.import.an.decreas.exports.thereb.decreasin.th.curren.accoun.deficit.othe.thing.e qual......5..capita.accoun.defici.reflect..ne.sal.o.th.hom.currenc.i.exchang.fo.othe.currencies.Thi.place.upwar.pressur.o.tha.hom.currency’.value.. .. )parativ.advantag.implie.tha.countrie.shoul.specializ.i.production.thereb.relyin.o.othe.countrie .fo.som.products.. .. .7.Covere.interes.arbitrag.i.plausibl.whe.th.forwar.premiu.reflec.th.interes.rat.differentia.betwee.tw.countrie.sp ecifie.b.th.interes.rat.parit.formula. .. . )8.Th.tota.impac.o.transactio.exposur.i.o.th.overal.valu.o.th.firm.. .. .9. .pu.optio.i.a.optio.t.sell-b.th.buye.o.th.option-.state.numbe.o.unit.o.th.underlyin.instrumen.a..specifie.pric.pe.uni.durin..specifie.period... . )10.Future.mus.b.marked-to-market.Option.ar.not.....)PartⅡ:Cloze (20%)每题2分, 答错不扣分1.I.inflatio.i..foreig.countr.differ.fro.inflatio.i.th.hom.country.th.exchang.rat.wil.adjus.t.maintai.equal.. purchasin.powe... )2.Speculator.wh.expec..currenc.t..appreciat..... .coul.purchas.currenc.future.contract.fo.tha.currency.3.Covere.interes.arbitrag.involve.th.short-ter.investmen.i..foreig.currenc.tha.i.covere.b.....forwar.contrac...... .t. sel.tha.currenc.whe.th.investmen.matures.4.. Appreciation.Revalu....)petitio.i.increased.5.....PP... .suggest..relationshi.betwee.th.inflatio.differentia.o.tw.countrie.an.th.percentag.chang.i.th.spo.exchang.ra t.ove.time.6.IF.i.base.o.nomina.interes.rat....differential....).whic.ar.influence.b.expecte.inflation.7.Transactio.exposur.i..subse.o.economi.exposure.Economi.exposur.include.an.for.b.whic.th.firm’... valu... .wil.b.affected.modit.a..state.pric.i..... pu..optio..i.exercised9.Ther.ar.thre.type.o.long-ter.internationa.bonds.The.ar.Globa.bond. .. eurobond.....an....foreig.bond...).10.An.goo.secondar.marke.fo.financ.instrument.mus.hav.a.efficien.clearin.system.Mos.Eurobond.ar.cleare.thr oug.eithe...Euroclea... ..o.Cedel.PartⅢ:Questions and Calculations (60%)过程正确结果计算错误扣2分rmation:A BankB BankBid price of Canadian dollar $0.802 $0.796Ask price of Canadian dollar $0.808 $0.800rmation.i.locationa.arbitrag.possible?put.t h.profi.fro.thi.arbitrag.i.yo.ha.$1,000,e.(5%)ANSWER:Yes! One could purchase New Zealand dollars at Y Bank for $.80 and sell them to X Bank for $.802. With $1 million available, 1.25 million New Zealand dollars could be purchased at Y Bank. These New Zealand dollars could then be sold to X Bank for $1,002,500, thereby generating a profit of $2,500.2.Assum.tha.th.spo.exchang.rat.o.th.Britis.poun.i.$1.90..Ho.wil.thi.spo.rat.adjus.i.tw.year.i.th.Unite.Kingdo.experience.a.inflatio.rat.o..percen.pe.yea.whil.th.Unite.State.experience.a.inflatio.rat.o..perc en. pe.year?(10%)ANSWER:According to PPP, forward rate/spot=indexdom/indexforth.exchang.rat.o.th.poun.wil.depreciat.b.4..percent.Therefore.th.spo.rat.woul.adjus.t.$1.9..[..(–.047)..$1.81073.Assum.tha.th.spo.exchang.rat.o.th.Singapor.dolla.i.$0.70..Th.one-yea.interes.rat.i.1.percen.i.th.Unite.State.a n..percen.i.Singapore..Wha.wil.th.spo.rat.b.i.on.yea.accordin.t.th.IFE?.(5%)ANSWER: according to the IFE,St+1/St=(1+Rh)/(1+Rf)$.70 × (1 + .04) = $0.7284.Assum.tha.XY.Co.ha.ne.receivable.o.100,00.Singapor.dollar.i.9.days..Th.spo.rat.o.th.S.i.$0.50.an.th.Singap or.interes.rat.i.2.ove.9.days..Sugges.ho.th.U.S.fir.coul.implemen..mone.marke.hedge..B.precis. .(10%)ANSWER: The firm could borrow the amount of Singapore dollars so that the 100,000 Singapore dollars to be received could be used to pay off the loan. This amounts to (100,000/1.02) = about S$98,039, which could be converted to about $49,020 and invested. The borrowing of Singapore dollars has offset the transaction exposure due to the future receivables in Singapore dollars.pan.ordere..Jagua.sedan.I..month..i.wil.pa.£30,00.fo.th.car.I.worrie.tha.poun.ster1in.migh.ris.sharpl.fro.th.curren.rate($1.90)pan.bough...mont.poun.cal.(suppose.contrac.siz..£35,000.wit..strik.pric.o.$1.9.fo..premiu.o.2..cents/£.(1)Is hedging in the options market better if the £ rose to $1.92 in 6 months?(2)what did the exchange rate have to be for the company to break even?(15%)Solution:(1)I.th..ros.t.$pan.woul. exercis.th.poun.cal.option.Th.su.o.th.strik.pric.an.premiu..i.$1.90 + $0.023 = $1.9230/£Thi.i.bigge.tha.$1.92.So hedging in the options market is not better.(2.whe.w.sa.th. compan.ca.brea.even.w.mea.tha.hedgin.o.no.hedgin.doesn’. matter.An.onl.whe.(strik.pric..premiu.).th.exchang.rat.,hedging or not doesn’t matter.So, the exchange rate =$1.923/£.6.Discus.th.advantage.an.disadvantage.o.fixe.exchang.rat.system.(15%)textbook page50 答案以教材第50 页为准PART Ⅳ: Diagram(10%)Th.strik.pric.fo..cal.i.$1.67/£.Th.premiu.quote.a.th.Exchang.i.$0.022.pe.Britis.pound.Diagram the profit and loss potential, and the break-even price for this call optionSolution:Following diagram shows the profit and loss potential, and the break-even price of this put option:PART Ⅴa) b) Calculate the expected value of the hedge.c) How could you replicate this hedge in the money market?Yo.ar.expectin.revenue.o.Y100,00.i.on.mont.tha.yo.wil.nee.t.cover.t.dollars.Yo.coul.hedg.thi.i.forwar.market.b.takin.lon.position.i.U.dollar.(shor.position.i.Japanes.Yen).B.lockin.i.you.pric.a.$..Y105.you.dolla.revenue.ar.guarantee.t.b.Y100,000/ 105 = $952You could replicate this hedge by using the following:a) Borrow in Japanb) Convert the Yen to dollarsc) Invest the dollars in the USd) Pay back the loan when you receive the Y100,000。
Chapter 3Adjusting Accounts and Preparing1. The cash basis of accounting reports revenues when cash is received while theaccrual basis reports revenues when they are earned. The cash basis reports expenses when cash is paid while the accrual basis reports expenses when they are incurred and matched with revenues they generated.2. The accrual basis of accounting generally provides a better indication of companyperformance and financial condition than does the cash basis. Also, the accrual basis increases the comparability of financial statements from one period to the next.Thus, business decision makers generally prefer the accrual basis.3. Businesses that have major seasonal variations in sales are most likely to select thenatural business year as the fiscal year.4. A prepaid expense is an item paid for in advance of receiving its benefits. As such, itis reported as an asset on the balance sheet.5. Long-term tangible plant assets such as equipment, buildings, and machinery leadto adjustments for depreciation. Generally, land is the only long-term tangible plant asset that does not require depreciation.6. The Accumulated Depreciation contra account is used for depreciation. It providesfinancial statement users with additional information about the relative age of the assets. Without the contra account information, the reader would not be able to tell whether the assets are new or in need of replacement.7. Unearned revenue refers to cash received in advance of providing products andservices. Another name for unearned revenue is deferred revenue. It is reported asa liability on the balance sheet.8. Accrued revenue is revenue that is earned but is not yet received in cash (and/orother assets) and the customer has not been billed prior to the end of the period.Therefore, end-of-period adjustments are made to record accrued revenue.Examples are interest income that has been earned but not collected and revenues from services performed that are neither collected nor billed.9.A If prepaid expenses are initially recorded with debits to expense accounts, then theprepaid expenses asset accounts are debited in the adjusting entries.10. For Best Buy, all of the accounts under the category of Property and Equipment(except for Land), require adjusting entries. The expense related to the depreciation expense account would be understated on the income statement if Best Buy fails to adjust these asset accounts. If the adjusting entries are not made, net income would be overstated. Note: Students might also correctly identify accounts receivable, goodwill, and tradenames as needing adjustment.11. Circuit City must make adjusting entries to Prepaid expenses and other currentassets; Deferred income taxes; Accrued expenses and other current liabilities;Accrued income taxes; and possibly other assets and liabilities such as Receivables for bad debts. (It is also possible that Circuit City would need to adjust Goodwill and Other intangible assets.)12. RadioShack would need to debit interest receivable and credit interest revenue.13. The Accrued Wages Expense would be reported as part of “Accrued Expenses” onCash AccountingRevenues (cash receipts) ...................................................... $52,000Expenses (cash payments: $37,500 - $6,000 + $3,250) ...... 34,750Net income ............................................................................. $17,250 Accrual AccountingRevenues (earned) ................................................................ $60,000Expenses (incurred) .............................................................. 37,500Net income .............................................................................. $22,500 Quick Study 3-2 (10 minutes)a. AE Accrued expensesb. PE Prepaid expensesc. UR Unearned revenuesd. PE Prepaid expenses (Depreciation)e. AR Accrued revenuesa. Debit Unearned Revenue Balance SheetCredit Revenue Earned Income Statementb. Debit Wages Expense Income StatementCredit Wages Payable Balance Sheetc. Debit Accounts Receivable Balance SheetCredit Revenue Earned Income Statementd. Debit Insurance Expense Income StatementCredit Prepaid Insurance Balance Sheete. Debit Depreciation Expense Income StatementCredit Accumulated Depreciation Balance SheetQuick Study 3-4 (15 minutes)a. Insurance Expense ....................................................... 3,000Prepaid Insurance ................................................. 3,000 To record 6-month insurance coverage expired.b. Supplies Expense ......................................................... 4,150Supplies .................................................................. 4,150 To record supplies used during the year.($900 + $4,000 – [?] = $750)Quick Study 3-5 (15 minutes)a. Depreciation Expense—Equipment ............................ 8,400Accumulated Depreciation—Equipment ............. 8,400 To record depreciation expense for the year.($45,000 - $3,000) / 5 years = $8,400b. No depreciation adjustments are made for land asit is expected to last indefinitely.Salaries Expense (400)Salaries Payable (400)To record salaries incurred but not yet paid.[One student earns $100 x 4 days, Mondaythrough Thursday]Quick Study 3-7 (15 minutes)a. Unearned Revenue ........................................................ 22,500Legal Revenue ....................................................... 22,500 To recognize legal revenue earned (30,000 x 3/4).b. Unearned Subscription Revenue ................................ 1,200Subscription Revenue ........................................... 1,200 To recognize subscription revenue earned.[100 x ($24 / 12 months) x 6 months]1. Accrue salaries expense e ga f2. Adjust the Unearned Services Revenue accountto recognize earned revenueb f3. Record the earning of services revenue for whichcash will be received the following periodQuick Study 3-9 (10 minutes)The answer is a.ExplanationThe debit balance in Prepaid Insurance was reduced by $400, implying a $400 debit to Insurance Expense. The credit balance in Interest Payable increased by $800, implying an $800 debit to Interest Expense.The answer is 2.ExplanationInsurance premium errorUnderstates expenses (and overstates assets) by .......... $1,600 Accrued salaries errorUnderstates expenses (and understates liabilities) by .... 1,000The collective effects from this company’s errors follow:Understates expenses by ..................................................... $2,600Overstates assets by ............................................................. $1,600Understates liabilities by ...................................................... $1,000 Quick Study 3-11 (10 minutes)Profit margin = $78,750 / $630,000 = 12.5%Interpretation: For each dollar that records as revenue, it earns 12.5 cents in net income. Miller’s 12.5% is markedly lower than competitors’ average profit margin of 15%—it must improve performance.Quick Study 3-12A (5 minutes)1. B 4. A2. F 5. D3. C 6. EExercise 3-2 (25 minutes)a. Depreciation Expense—Equipment ................................ 16,000Accumulated Depreciation—Equipment..................... 16,000 To record depreciation expense for the year.b. Insurance Expense ........................................................... 5,360Prepaid Insurance* ....................................................... 5,360 To record insurance coverage that expired($6,000 - $640).c. Office Supplies Expense .................................................. 3,422Office Supplies**............................................................ 3,422 To record office supplies used ($325 + $3,480 - $383).d. Unearned Fee Revenue .................................................... 3,000Fee Revenue .................................................................. 3,000 To record earned portion of fee received in advance($15,000 x 1/5).e. Insurance Expense ........................................................... 6,160Prepaid Insurance ......................................................... 6,160 To record insurance coverage that expired.f. Wages Expense ................................................................. 2,700Wages Payable .............................................................. 2,700 To record wages accrued but not yet paid.a. Unearned Fee Revenue .................................................... 5,000Fee Revenue .................................................................. 5,000 To record earned portion of fee received in advance($15,000 x 1/3).b. Wages Expense ................................................................. 7,500Wages Payable .............................................................. 7,500 To record wages accrued but not yet paid.c. Depreciation Expense—Equipment ................................ 17,251Accumulated Depreciation—Equipment..................... 17,251 To record depreciation expense for the year.d. Office Supplies Expense .................................................. 5,682Office Supplies*............................................................. 5,682 To record office supplies used ($240 + $6,102 - $660).e. Insurance Expense ........................................................... 2,700Prepaid Insurance†........................................................ 2,700 To record insurance coverage expired ($4,000 - $1,300).f. Interest Receivable ......................................................... 1,400Interest Revenue ........................................................ 1,400 To record interest earned but not yet received.g. Interest Expense ............................................................. 2,000Interest Payable........................................................... 2,000 To record interest incurred but not yet paid.a. Adjusting entry2009Dec. 31 Wages Expense (825)Wages Payable (825)To record accrued wages for one day.(5 workers x $165)b. Payday entry2010Jan. 4 Wages Expense.......................................................2,475Wages Payable (825)Cash .....................................................................3,300To record accrued and current wages.Wages expense = 5 workers x 3 days x $165Cash = 5 workers x 4 days x $165Exercise 3-5 (15 minutes)a. $ 2,000b. $ 6,607c. $11,987d. $ 1,375Proof: (a) (b) (c) (d) Supplies available – prior year-end ......... $ 350 $1,855 $ 1,576 $1,375 Supplies purchased in current year ........ 2,450 6,307 11,987 6,907 Total supplies available ............................ 2,800 8,162 13,563 8,282 Supplies available – current year-end ..... (800) (6,607) (2,056) (800) Supplies expense for current year........... $2,000 $1,555 $11,507 $7,482a.Apr. 30 Legal Fees Expense ........................................... 4,500Legal Fees Payable ..................................... 4,500 To record accrued legal fees.May 12 Legal Fees Payable ............................................ 4,500Cash ............................................................. 4,500 To pay accrued legal fees.b.Apr. 30 Interest Expense ................................................. 1,900Interest Payable .......................................... 1,900 To record accrued interest expense($5,700 x 10/30).May 20 Interest Payable .................................................. 1,900Interest Expense ................................................. 3,800Cash ............................................................. 5,700 To record payment of accrued and currentinterest expense ($5,700 x 20/30).c.Apr. 30 Salaries Expense ................................................ 4,800Salaries Payable.......................................... 4,800 To record accrued salaries($12,000 x 2/5 week).May 3 Salaries Payable ................................................. 4,800Salaries Expense ................................................ 7,200Cash ............................................................. 12,000 To record payment of accrued andcurrent salaries ($12,000 x 3/5 week).Basis*Basis Basis**Basis Dec. 31, 2007 ........$14,450 $0 2007 ..........$ 850 $15,300 Dec. 31, 2008 ........9,350 0 2008 ..........5,100 0 Dec. 31, 2009 ........4,250 0 2009 .......... 5,100 0 Dec. 31, 2010 ........0 0 2010 .......... 4,250 0$15,300 $15,300 Explanations:*Accrual asset balance equals months left in the policy x $425 per month (monthly cost is computed as $15,300 / 36 months).Months Left Balance12/31/2007 .. 34 $14,45012/31/2008 .. 22 9,35012/31/2009 .. 10 4,25012/31/2010 .. 0 0**Accrual insurance expense equals months covered in the year x $425 per month.Months Covered Expense2007 ............ 2 $ 8502008 ............12 5,1002009 ............12 5,1002010 ............10 4,250$15,300Dec. 31 Accounts Receivable ............................................. 1,980Fees Earned ..................................................... 1,980 To record earned but unbilled fees (30% x $6,600).31 Unearned Fees ........................................................ 4,620Fees Earned ..................................................... 4,620 To record earned fees collected in advance(70% x $6,600).31 Depreciation Expense—Computers ..................... 1,650Accumulated Depreciation-Computers ........ 1,650 To record depreciation on computers.31 Depreciation Expense—Office Furniture ............. . 1,925A ccumulated Depreciation—Office Furniture ... 1,925To record depreciation on office furniture.31 Salaries Expense .................................................... 2,695Salaries Payable.............................................. 2,695 To record accrued salaries.31 Insurance Expense.................................................. 1,430Prepaid Insurance ........................................... 1,430 To record expired prepaid insurance.31 Rent Expense (700)Rent Payable (700)To record accrued rent expense.31 Office Supplies Expense (528)Office Supplies (528)To record use of office supplies.31 Advertising Expense (500)Advertising Payable (500)To record accrued advertising expense.31 Utilities Expense (77)Utilities Payable (77)To record incurred and unpaid utility costs.a. $ 6,039 / $ 52,970 = 11.4%b. $100,890 / $ 471,430 = 21.4%c. $106,880 / $ 301,920 = 35.4%d. $ 67,140 / $1,721,520 = 3.9%e. $ 84,780 / $ 513,800 = 16.5%Analysis and Interpretation: Company c has the highest profitability according to the profit margin ratio. Company c earns 35.4 cents in net income for every one dollar of net sales earned.Exercise 3-10A (30 minutes)a.Dec. 1 Supplies Expense ................................................... 2,000Cash ................................................................. 2,000 Purchased supplies.b.Dec. 2 Insurance Expense ................................................. 1,540Cash ................................................................. 1,540 Paid insurance premiums.c.Dec. 15 Cash ......................................................................... 13,000Remodeling Fees Earned ............................... 13,000 Received fees for work to be done.d.Dec. 28 Cash ......................................................................... 3,700Remodeling Fees Earned ............................... 3,700 Received fees for work to be done.e.Dec. 31 Supplies .................................................................. 1,840Supplies Expense ........................................... 1,840 Adjust expenses for unused supplies.f.Dec. 31 Prepaid Insurance .................................................. 1,200Insurance Expense ......................................... 1,200 Adjust expenses for unexpired coverage($1,540 - $340).g.Dec. 31 Remodeling Fees Earned ..................................... 11,130Unearned Remodeling Fees .......................... 11,130 Adjusted revenues for unfinished projects($13,000 + 3,700 - $5,570).a. Initial credit recorded in the Unearned Fees accountJuly 1 Cash ....................................................................... 2,800Unearned Fees .............................................. 2,800 Received fees for work to be done for Solana.6 Cash ....................................................................... 8,100Unearned Fees .............................................. 8,100 Received fees for work to be done for Haru.12 Unearned Fees ...................................................... 2,800Fees Earned ................................................... 2,800 Completed work for Solana.18 Cash ....................................................................... 7,300Unearned Fees .............................................. 7,300 Received fees for work to be done for Jordan.27 Unearned Fees ...................................................... 8,100Fees Earned ................................................... 8,100 Completed work for customer Haru.31 No adjusting entries required.b. Initial credit recorded in the Fees Earned accountJuly 1 Cash ....................................................................... 2,800Fees Earned ................................................... 2,800 Received fees for work to be done for Solana.6 Cash ....................................................................... 8,100Fees Earned ................................................... 8,100 Received fees for work to be done for Haru.12 No entry required.18 Cash ....................................................................... 7,300Fees Earned ................................................... 7,300 Received fees for work to be done for Jordan.27 No entry required.31 Fees Earned .......................................................... 7,300Unearned Fees .............................................. 7,300 Adjusted to reflect unearned fees for unfinishedjob for Jordan.c. Under the first method (and using entries from a)Unearned Fees = $2,800 + $8,100 - $2,800 + $7,300 - $8,100 = $7,300 Fees Earned = $2,800 + $8,100 = $10,900Unearned Fees = $7,300Fees Earned = $2,800 + $8,100 + $7,300 - $7,300 = $10,9001. I 5. G 9. H2. D 6. C 10. E3. F 7. I 11. H4. B 8. A 12. BProblem 3-2A (35 minutes)Part 1Adjustment (a)Dec. 31 Office Supplies Expense ................................ 12,325Office Supplies ......................................... 12,325 To record cost of supplies used($2,900 + $11,977 - $2,552).Adjustment (b)31 Insurance Expense .......................................... 12,280Prepaid Insurance .................................... 12,280B 290 ($10,440/36 mo.) 9 2,610C 770 ($ 9,240 /12 mo.) 5 3,850Total $12,280Adjustment (c)31 Salaries Expense ............................................. 3,660Salaries Payable....................................... 3,660 To record accrued but unpaid wages(2 days x $1,830).Adjustment (d)Dec. 31 Depreciation Expense—Building ................... 18,875Accumulated Depreciation—Building ... 18,875 To record annual depreciation expense[($800,000 -$45,000) / 40 years = $18,875]Adjustment (e)31 Rent Receivable ............................................ 3,000Rent Earned ........................................... 3,000 To record earned but unpaid Dec. rent.Adjustment (f)31 Unearned Rent .............................................. 5,436Rent Earned ........................................... 5,436 To record the amount of rent earned forNovember and December (2 x $2,718).Part 2Cash Payment for (c)Jan. 6 Salaries Payable ........................................... 3,660Salaries Expense* ........................................ 5,490Cash ....................................................... 9,150 To record payment of accrued andcurrent salaries. *(3 days x $1,830)Cash Payment for (e)15Cash ............................................................... 6,000Rent Receivable .................................... 3,000Rent Earned ........................................... 3,000 To record past due rent for two months.Part 2Adjustment (a)Dec. 31 Insurance Expense ...............................................3,000Prepaid Insurance ...........................................3,000 To record the insurance expired.Adjustment (b)31 Teaching Supplies Expense ................................9,000Teaching Supplies ..........................................9,000 To record supplies used ($11,000 - $2,000).Adjustment (c)31 Depreciation Expense—Equipment ....................10,000Accumulated Depreciation—Equipment ............10,000 To record equipment depreciation.Adjustment (d)31 Depreciation Expense—Profess. Library ...........5,000A ccumul. Depreciation—Profess. Library.........5,000To record professional library depreciation.Adjustment (e)31 Unearned Training Fees .......................................5,000Training Fees Earned .....................................5,000 To record 2 months’ training fees earnedthat were collected in advance.Adjustment (f)31 Accounts Receivable ............................................4,000Tuition Fees Earned........................................4,000 To record tuition earned($1,600 x 2 1/2 months).Adjustment (g)31 Salaries Expense (480)Salaries Payable (480)To record accrued salaries(2 days x $120 x 2 employees).Adjustment (h)31 Rent Expense ........................................................2,178Prepaid Rent ....................................................2,178 To record expiration of prepaid rent.Part 3WELLS TEACHING INSTITUTEAdjusted Trial BalanceDecember 31, 2009Debit Credit Cash .......................................................................... $ 28,064Accounts receivable ................................................ 4,000Teaching supplies ................................................... 2,000Prepaid insurance .................................................... 13,000Prepaid rent 0Professional library ................................................. 33,000 Accumulated depreciation—Professional library ... $ 15,000 Equipment ................................................................ 75,800 Accumulated depreciation—Equipment ................ 25,000 Accounts payable .................................................... 39,500 Salaries payable . (480)Unearned training fees ............................................ 7,500 T. Wells, Capital ....................................................... 71,000 T. Wells, Withdrawals .............................................. 44,000Tuition fees earned .................................................. 115,000 Training fees earned ................................................ 46,000 Depreciation expense—Professional library ........ 5,000 Depreciation expense—Equipment ....................... 10,000Salaries expense ..................................................... 52,480Insurance expense................................................... 3,000Rent expense ............................................................ 26,136Teaching supplies expense .................................... 9,000 Advertising expense ................................................ 8,000Utilities expense....................................................... 6,000 _______ Totals ........................................................................ $319,480 $319,480Part 4WELLS TEACHING INSTITUTEIncome StatementFor Year Ended December 31, 2009RevenuesTuition fees earned ............................................ $115,000Training fees earned .......................................... 46,000Total revenues .................................................... $161,000 ExpensesDepreciation expense—Professional library ... 5,000Depreciation expense—Equipment .................. 10,000Salaries expense ................................................ 52,480Insurance expense ............................................. 3,000Rent expense ...................................................... 26,136Teaching supplies expense ............................... 9,000Advertising expense .......................................... 8,000Utilities expense ................................................. 6,000Total expenses ................................................... 119,616 Net income ............................................................ $ 41,384WELLS TEACHING INSTITUTEStatement of Owner’s EquityFor Year Ended December 31, 2009T. Wells, Capital, December 31, 2008 ................................. $ 71,000 Plus: Net income .................................................................. 41,384112,384 Less: Withdrawals by owner ............................................... 44,000 T. Wells, Capital, December 31, 2009 ................................. $ 68,384Problem 3-3A (Concluded)WELLS TEACHING INSTITUTEBalance SheetDecember 31, 2009AssetsCash ................................................................................. $ 28,064 Accounts receivable ...................................................... 4,000 Teaching supplies .......................................................... 2,000 Prepaid insurance .......................................................... 13,000 Professional library ........................................................ $33,000 Accumulated depreciation—Professional library ....... (15,000) 18,000 Equipment ....................................................................... 75,800 Accumulated depreciation—Equipment ...................... (25,000) 50,800 Total assets ..................................................................... $115,864LiabilitiesAccounts payable ........................................................... $ 39,500 Salaries payable . (480)Unearned training fees .................................................. 7,500 Total liabilities ................................................................ 47,480EquityT. Wells, Capital .............................................................. 68,384 Total liabilities and equity ............................................. $115,864Problem 3-4A (45 minutes) —Part 1Cash ......................................... $ 86,000 $ 86,000 Accounts receivable ........... 15,000 (a) 4,000 19,000Office supplies ...................... 17,800 (b) 8,800 9,000Prepaid insurance ................ 6,040 (c) 2,080 3,960Office equipment .................. 87,000 87,000 Accumulated depreciation—Office equipment ........... $ 24,000 (d) 2,000 $ 26,000 Accounts payable ................ 9,100 (e) 14,900 24,000 Interest payable ..................... (f) 2,500 2,500 Salaries payable ................... (g) 15,000 15,000 Unearned consulting fees .20,000 (h) 7,000 13,000 Long-term notes payable .. 54,000 54,000 K. Jenkins, Capital ............... 46,000 46,000 K. Jenkins, Withdrawals .... 10,000 10,000Consulting feesearned .................................... 165,000 (a)(h)4,0007,000 176,000Depreciation expense—Office equipment ................ (d) 2,000 2,000Salaries expense .................. 67,990 (g) 15,000 82,990Interest expense ................... 1,270 (f) 2,500 3,770 Insurance expense .............. (c) 2,080 2,080Rent expense ........................ 14,540 14,540Office supplies expense .... (b) 8,800 8,800 Advertising expense ........... 12,460 _______ (e) 14,900 ______ 27,360 _______ Totals ........................................ $318,100 $318,100 $56,280 $56,280 $356,500 $356,500 Adjustment description(a) Earned but uncollected revenues.(b) Cost of office supplies used.(c) Cost of expired insurance coverage.(d) Depreciation expense on office equipment.(e) Incurred but unpaid advertising expense.(f) Incurred but unpaid interest expense.(g) Incurred but unpaid salaries expense.(h) Earned revenues previously received in advance.。
annualized arithmetic average returnAnnualized arithmetic average return, also known as the average annual return or the arithmetic mean return, is a commonly used measure to evaluate the performance of an investment or a portfolio over a certain period of time. It represents the average rate of return achieved per year over the specified time frame.To calculate the annualized arithmetic average return, the following steps can be followed:1. Collect the historical return data: Gather the returns achieved for the investment or portfolio for each period within the chosen time frame. These returns can be daily, monthly, quarterly, or any other frequency.2. Calculate the arithmetic mean return: Add up all the individual returns and divide the sum by the total number of periods. Thiswill give the average return achieved over the specified time frame.3. Adjust for the measurement period: If the returns are reported ona periodic basis that is different from a yearly basis, adjustments need to be made to reflect the annualized return. For example, if the returns are reported on a monthly basis, the average return needs to be multiplied by 12 to obtain an annualized figure.The annualized arithmetic average return is widely used in the finance industry and plays a crucial role in investment management and performance evaluation. Here are some reasons why this measure is important:1. Comparable performance evaluation: By using the annualized arithmetic average return, investors can compare the performance of different investments or portfolios over the same time frame. This allows them to make informed decisions and allocate their capital efficiently.2. Risk assessment: The average return alone does not provide a complete picture of an investment's performance. However, when used in conjunction with other risk measures, such as standard deviation or beta, the annualized arithmetic average return helps investors understand the level of risk associated with a particular investment or portfolio.3. Future projections: The annualized arithmetic average return can also be used to estimate future returns. While this does not guarantee the actual returns, it provides a reasonable expectation based on historical performance.4. Benchmarking: Investors often compare the performance of their investments or portfolios with a benchmark index. The annualized arithmetic average return serves as a reference point to assess whether the investment outperformed or underperformed the benchmark.5. Investment fund evaluation: For mutual funds and other investment vehicles, the annualized arithmetic average return is a key metric for comparing different funds. Investors can evaluate the fund's historical performance and make informed decisions about investing in the fund.6. Performance measurement for managers: Fund managers and investment professionals often use the annualized arithmetic average return as a performance metric to evaluate their skill and ability to generate returns for investors.However, it is important to note that the annualized arithmetic average return has limitations and should not be the sole basis for investment decisions. It does not account for the compounding effect and assumes a constant rate of return over the entire time frame. Investors should consider other factors, such as volatility, risk, and underlying market conditions, to make informed investment choices.In conclusion, the annualized arithmetic average return is a widely used measure to evaluate investment performance. It provides investors with a standardized way to compare different investments and assess historical performance. By understanding this measure and its limitations, investors can make more informed decisions and manage their portfolios effectively.。
达人保证金阈值变动英语The Threshold Change of Expert Margin in EnglishIntroduction:In the field of trading and investment, the concept of margin is widely discussed and understood. Margin is the collateral that traders or investors need to deposit in order to participate in certain financial markets. This article aims to discuss the specific topic of the threshold change of expert margin in English.Expert Margin Explained:Before delving into the threshold change, it is essential to understand the concept of expert margin. Expert margin is the minimum amount of collateral that experienced traders or investors are required to deposit in order to participate in trading activities. This threshold is set by the trading platform or financial institution.The Importance of Expert Margin Threshold:The expert margin threshold plays a crucial role in maintaining the integrity and stability of the financial markets. It ensures that only qualified and experienced traders are allowed to engage in high-risk trading activities. By setting a higher threshold, it helps filter out less experienced or less competent individuals who may pose a higher risk to the market.Dynamic Nature of Expert Margin:In the trading world, expert margin thresholds are not fixed and can be subject to change. This dynamic nature enables trading platforms and financial institutions to adapt to the changing market conditions and regulate the participation of traders accordingly. Expert margin thresholds can be adjusted based on factors such as market volatility, risk levels, and regulatory requirements.Reasons for Threshold Change:Several factors can lead to a change in the expert margin threshold. The primary reason is market volatility. During periods of high volatility, the risk of making substantial losses increases. As a result, the threshold may be raised to limit the participation of traders who may not be able to withstand such volatility adequately.Another reason for the threshold change can be regulatory requirements. In the financial industry, regulatory bodies may impose new rules or guidelines that necessitate an adjustment in the expert margin threshold. These regulations are put in place to ensure the stability of the market and protect traders' interests.Impact on Traders:Changes in the expert margin threshold can have significant implications for traders. Traders who are already participating in the market may need to deposit additional collateral to meet the new threshold. This can directly impact their trading strategy and the amount of capital they can allocate to various trades.For potential traders, a higher expert margin threshold may deter their entry into the market, particularly if they do not have the required funds to meet the new threshold. This may limit the pool of participants and potentially contribute to a less vibrant market.How Traders Adapt:Traders need to adapt their strategies and financial planning when facing a change in the expert margin threshold. Firstly, they need to assess their financial capabilities and determine if they can meet the new threshold requirements. If necessary, they may need to allocate additional capital to meet the increased collateral demands.Moreover, traders should closely monitor the market conditions and regulatory updates to anticipate any potential changes in the expert margin threshold. Being proactive and staying informed can help them make well-informed decisions and adjust their trading activities accordingly.Conclusion:The threshold change of expert margin in English is a significant topic in the trading and investment industry. It highlights the importance of maintaining a balance between market participation and risk management. Traders should understand the dynamic nature of expert margin thresholds and be prepared to adapt their strategies when facing a change. By doing so, they can navigate the market effectively and protect their interests.。
Journal of Artificial Intelligence Research20(2003)195-238Submitted6/03;published12/03 Taming Numbers and Durations in the Model CheckingIntegrated Planning SystemStefan Edelkamp stefan.edelkamp@cs.uni-dortmund.de Baroper Straße301Fachbereich Informatik,GB IVUniversit¨a t Dortmund44221DortmundGermanyAbstractThe Model Checking Integrated Planning System(MIPS)is a temporal least commit-ment heuristic search planner based on aflexible object-oriented workbench architecture.Its design clearly separates explicit and symbolic directed exploration algorithms from the set of on-line and off-line computed estimates and associated data structures.MIPS has shown distinguished performance in the last two international planning com-petitions.In the last event the description language was extended from pure propositional planning to include numerical state variables,action durations,and plan quality objective functions.Plans were no longer sequences of actions but time-stamped schedules.As a participant of the fully automated track of the competition,MIPS has proven to bea general system;in each track and every benchmark domain it efficiently computed plansof remarkable quality.This article introduces and analyzes the most important algorithmic novelties that were necessary to tackle the new layers of expressiveness in the benchmark problems and to achieve a high level of performance.The extensions include critical path analysis of sequentially generated plans to generate corresponding optimal parallel plans.The linear time algorithm to compute the parallel plan bypasses known NP hardness results for partial ordering by scheduling plans with respect to the set of actions and the imposed precedence relations.The efficiency of this algorithm also allows us to improve the exploration guidance:for each encountered planning state the corresponding approximate sequential plan is scheduled.One major strength of MIPS is its static analysis phase that grounds and simplifies parameterized predicates,functions and operators,that infers knowledge to minimize the state description length,and that detects domain object symmetries.The latter aspect is analyzed in detail.MIPS has been developed to serve as a complete and optimal state space planner, with admissible estimates,exploration engines and branching cuts.In the competition version,however,certain performance compromises had to be made,includingfloating point arithmetic,weighted heuristic search exploration according to an inadmissible estimate and parameterized optimization.1.IntroductionPractical action planning and model checking appear to be closely related.The MIPS project targets the integration of model checking techniques into a domain-independent action planner.With the HSF-Spin experimental model checker(Edelkamp,Leue,&Lluch-Lafuente,2003)we are looking towards the integration of planning technology into anEdelkampexisting model checker.Additional synergies are exploited in the automated compilation of protocol software model checking problems into planner inputs(Edelkamp,2003).Model checking(Clarke,Grumberg,&Peled,1999)is the automated process to verify if a formal model of a system satisfies a specified temporal property or not.As an illustrative example,take an elevator control system together with a correctness property that requires an elevator to eventually stop on every call of a passenger or that guarantees that the door is closed,while the elevator is moving.Although the success in checking correctness is limited, model checkers have found many errors in current hardware and software designs.Models often consist of many concurrent sub-systems.Their combination is either synchronous,as often seen in hardware design verification,or asynchronous,as frequently given in commu-nication and security protocols,or in multi-threaded programming languages like Java.Model checking requires the exploration of very large state spaces containing all reach-able system states.This problem is known as the state explosion problem and occurs even when the sets of generated states is much smaller than the set of all reachable states.An error that shows a safety property violation,like a deadlock or a failed assertion, corresponds to one of a set of target nodes in the state space graph.Roughly speaking, something bad has occured.A liveness property violation refers to a(seeded)cycle in the graph.Roughly speaking,something good will never occur.For the case of the elevator example,eventually reaching a target state where a request button was pressed is a liveness property,while certifying closed doors refers to a safety property.The two main validation processes in model checking are explicit and symbolic search. In explicit-state model checking each state refers to afixed memory location and the state space graph is implicitly generated by successive expansions of state.In symbolic model checking(McMillan,1993;Clarke,McMillan,Dill,&Hwang,1992), (fixed-length)binary encodings of system states are used,so that each state can be rep-resented by its characteristic function representation.This function evaluates to true if and only if all Boolean state variables are assigned to bit values with respect to the binary encoding of the system state.Subsequently,the characteristic function is a conjunction of literals with a plain variable for a1in the encoding and a negated variable for a0.Sets of states are expressed as the disjunction of all individual characteristic functions.The unique symbolic representation of sets of states as Boolean formulae through binary decision diagrams(BDDs)(Bryant,1992)is often much smaller than the explicit one.BDDs are(ordered)read-once branching programs with nodes corresponding to variables,edges corresponding to variable outcomes,and each path corresponding to an assignment to the variables with the resulting evaluation at the leaves.One reason for the succinctness of BDDs is that directed acyclic graphs may express exponentially many paths.The transition relation is defined on two state variable sets.It evaluates to true,if and only if an operator exists that transforms a state into a valid successor.In some sense,BDDs exploit regularities of the state set and often appear well suited to regular hardware systems.In contrast,many software systems inherit a highly asynchronous and irregular structure,so that the use of BDDs with afixed variable ordering is generally notflexible enough.For symbolic exploration,a set of states is combined with the transition relation to compute the set of all possible successor states,i.e.the image.Starting with the initial state,iteration of image computations eventually explores the entire reachable state space.Taming Numbers and Durations in MIPSTo improve the efficiency of image computations,transition relations are often provided in partitioned form.The correspondence between action and model checking(Giunchiglia&Traverso,1999) can be roughly characterized as follows.Similar to model checkers,action planners im-plicitly generate large state spaces,and both exploration approaches are based on applying operators to the current state.States spaces in model checking and in planning problems are often modelled as Kripke structures,i.e.state space graphs with states labelled by propo-sitional predicates.The satisfaction of a specified property on the one side corresponds to a complete exploration,and an unsolvable problem on the other side.In this respect,the goal in action planning can be cast as an error with the corresponding trail interpreted as a plan.In the elevator example,the goal of a planning task is to reach a state,in which the doors are open and the elevator is moving.Action planning refers to safety properties only, since goal achievement in traditional and competition planning problems have not yet been extended with temporal properties.However,temporally extended goals are of increasing research interest(Kabanza,Barbeau,&St-Denis,1997;Pistore&Traverso,2001;Lago, Pistore,&Traverso,2002).In contrast to model checkers that perform either symbolic or explicit exploration,MIPS features both.Moreover,it combines symbolic and explicit search planning in the form of symbolic pattern databases(Edelkamp,2002b).The planner MIPS implements heuristic search algorithms like A*(Pearl,1985)and IDA*(Korf,1985)for exploration,which include state-to-goal approximation into the search process to rank the states to be expanded next. Heuristic search has brought considerable gains to both planning(Bonet&Geffner,2001; Refanidis&Vlahavas,2000;Hoffmann&Nebel,2001;Bertoli,Cimatti,&Roveri,2001a; Jensen,Bryant,&Veloso,2002;Feng&Hansen,2002)and model checking(Yang&Dill, 1998;Edelkamp et al.,2003;Groce&Visser,2002;Bloem,Ravi,&Somenzi,2000;Ruys, 2003).Including resource variables,like the fuel level of a vehicle or the distance between two different locations,as well as action duration are relatively new aspects for competitive planning(Fox&Long,2003).The input format PDDL2.1is not restricted to variables of finite domain,but also includes rational(floating-point)variables in both precondition and effects.Similar to a set of atoms described by a propositional predicate,a set of numerical quantities can be described by a set of parameters.Through the notation of PDDL2.1,we refer to parameterized numerical quantities as functions.For example,the fuel level might be parameterized by the vehicle that is present in the problem instancefile description.In the competition,domains were provided in different tracks according to different lay-ers of language expressiveness:i)pure propositional planning,ii)planning with numerical resources,iii)planning with numerical resources and constant action duration,iv)planning with numerical resources and variable action duration,and,in some cases,v)complex prob-lems usually combining time and numbers in more interesting ways.MIPS competed as a fully automated system and performed remarkably well in allfive tracks;it solved a large number of problems and was the only fully automated planner that produced solutions in each track of every benchmark domain.In this paper the main algorithmic techniques for taming rational numbers,objective functions,and action duration are described.The article is structured as follows.First, we review the development of the MIPS system and assert its main contributions.ThenEdelkampwe address the object-oriented heuristic search framework of the system.Subsequently,we introduce some terminology that allows us to give a formal definition of the syntax and the semantics of a grounded mixed numerical and propositional planning problem instance. We then introduce the core contributions:critical path scheduling for concurrent plans, and efficient methods for detecting and using symmetry cuts.PERT scheduling produces optimal parallel plans in linear time given a sequence of operators and a precedence relation among them.The paper discusses pruning anomalies and the effect of different optimization criteria.We analyze the correctness and efficiency of symmetry detection in detail.The article closes with related work and concluding remarks.2.The Development of MIPSThe competition version of MIPS refers to initial work(Edelkamp&Reffel,1999a)in heuristic symbolic exploration of planning domains with theµcke model checker(Biere, 1997).This approach was effective in sample puzzle solving(Edelkamp&Reffel,1998)and in hardware verification problems(Reffel&Edelkamp,1999).For implementing a propositional planner,wefirst used our own BDD library called StaticBdd,in which large node tables are allocated prior to their use.During the imple-mentation process we changed the BDD representation mainly to improve performance for small planning problems.We selected the public domain c++BDD package Buddy(Lind-Nielsen,1999),which is moreflexible.The planning process was semi-automated(Edelkamp &Reffel,1999b);variable encodings were provided by hand,while the representations of all operators were established by enumerating all possible parameter instances.Once the state space encoding and action transition relation werefixed,exploration in the form of a symbolic breadth-first search of the state-space could be executed.At that time,we were not aware of any other work in BDD-based planning such as the work of Cimatti et al. (1997),which is likely thefirst link to planning via symbolic model checking.The team used the model checker(nu)SMV as the basis with an atom-to-variable planning state encoding scheme on top of it.Later on,we developed a parser and a static analyzer to automate the inference of state encodings,the generation of the transition relations,and the extraction of solution paths. In order to minimize the length of the state encoding,the new analyzer clustered atoms into groups(Edelkamp&Helmert,1999).As confirmed by other attempts(Weism¨u ller,1998), who started experimenting with PDDL specification inµcke,state minimization is in fact crucial.The simple encoding using one variable for each atom appears not to be competitive with respect to Graphplan-based(Blum&Furst,1995)and SAT-plan based planners(Kautz &Selman,1996).Subsequently,MIPS was thefirst fully automated planning system based on symbolic model checking technology that could deal with large domain descriptions.In the second international planning competition MIPS(Edelkamp&Helmert,2001) could handle the STRIPS(Fikes&Nilsson,1971)subset of the PDDL language(McDer-mott,2000)and some additional features from ADL(Pednault,1989),namely negative preconditions and(universal)conditional effects.MIPS was one offive planning systems to be awarded for“Distinguished Performance”in the fully automated track.The competition version(Edelkamp&Helmert,2000)already included explicit heuristic search algorithms based on a bit-vector state representation and the relaxed planning heuristic(RPH)(Hoff-Taming Numbers and Durations in MIPSmann&Nebel,2001)as well as symbolic heuristic search based on the HSP heuristic(Bonet &Geffner,2001)and a one-to-one atom derivative of RPH.In the competition,we used breadth-first bi-directional symbolic search whenever the single state heuristic search engine got stuck in its exploration.In between the planning competitions,explicit(Edelkamp,2001c)and symbolic pattern databases(Edelkamp,2002b)were proposed as off-line estimators for completely explored problem abstractions.Roughly speaking,pattern database abstractions slice the state vec-tor offluents into pieces and adjust the operators accordingly.The completely explored subspaces then serve as admissible estimates for the overall search and are competitive with the relaxed planning heuristic in several benchmark domains.For the third planning competition new levels of the planning domain description lan-guage(PDDL)were designed.Level1considers pure propositional planning.Level2also includes numerical resources and objective functions to be minimized.Level3additionally allows the specification of actions with durations.Consequently,MIPS has been extended to cope with these new forms of expressiveness.First results of MIPS in planning PDDL2.1problems are presented in(Edelkamp, 2001b).The preliminary treatment illustrates the parsing process in two simple bench-mark domains.Moreover,propositional heuristics and manual branching cuts were applied to accelerate sequential plan generation.This work was extended in(Edelkamp,2002a), where we presented two approximate exploration techniques to bound and tofix numerical domains,first results on symmetry detection based on fact groups,critical path scheduling, an any-time wrapper to produce optimal plans,and a numerical extension to RPH.3.Architecture of MIPSFigure1shows the main components of MIPS and the dataflow from the input definition of the domain and the problem instance to the resulting temporal plan in the output.As shown shaded in light gray,MIPS is divided into four parts:pre-compilation,heuristics, search algorithms,and post-compilation(scheduling).Henceforth,the planning process will be coarsely grouped into three stages,pre-compilation,heuristic search planning,and the construction of temporal plans.The problem and domain descriptionfiles are fed into the system,analyzed and grounded.Thisfixes the state space problem to be solved.The intermediate result is implicit,but can be saved in afile for use by other planners and model checkers.The basics of pre-compilation are covered in Section3.2.The next stage defines the planning process.The object-oriented workbench design of the planner allows different heuristic estimates to be combined with different search strategies and access data structures.Possible choices are listed in Sections3.3and 3.4. Temporal planning is based on(PERT)scheduling.This issue of rearranging sequential (relaxed)plans is addressed in detail in Section4.3.The planning system was developed in the spirit of the heuristic search framework, HSF for short(Edelkamp,1999),which allows attachment of newly implemented problem (puzzle)domains to an already compiled system.Similar to the approach that we took in model checking within HSF-Spin,we kept the extensible and general design.In fact we characterized both action planning and protocol validation as single-agent challenges. In contrast to the model checking approach,for planning we devised a hierarchy of systemEdelkampFigure1:Architecture of MIPS.states:the implementation for numerical states is a derived class of the one for propositional states.Similarily,the heuristic search algorithms are all based on an abstract search class.The main procedures that have to be provided to the search algorithm are a state expansion procedure,and a heuristic search evaluation function,both located in one of the hierarchi-cally organized heuristic estimator classes.In this sense,algorithms in MIPS are general node expanding schemes that can be adapted to very different problems.Additional data structures for the horizon list Open and the visited list Closed are constructed as parame-ters of the appropriate search algorithms.As a result,the implementations of the heuristic search algorithms and the associated data structures in the planner MIPS almost match those in our model checker.3.1Example ProblemThe running example for the paper is an instance of a rather simple PDDL2.1problem in Zeno-Travel.It is illustrated in Figure2.The initial configuration is drawn to the left ofTaming Numbers and Durations in MIPSFigure2:An instance for the Zeno-Travel domain with initial state(left)and goal state(s) (right).thefigure and the goal configuration to its right.Some global and local numeric variable assignments are not shown.Figures3and4provide the domain and problem specifications1.The instance asks for a temporal plan tofly passengers(dan,scott,and ernie)located somewhere on a small map(including the cities city-a,city-b,city-c,and city-d)with an aircraft(plane) to their respective target destinations.Boarding and debarking take a constant amount of time.The plane has afixed fuel capacity.Fuel and time are consumed according to the distances between the cities and the travel speed.Fuel can be restored by refueling the aircraft.As a result,the total amount of fuel is also maintained as a numerical quantity.3.2PrecompilerThe static analyzer takes the domain and problem instance as an input,grounds its proposi-tional state information and infers different forms of planner independent static information. Parsing Our simple Lisp parser generates a tree of Lisp entities.It reads the inputfiles and recognizes the domain and problem name.To cope with variable typing,we tem-porarily assert constant typed predicates to be removed together with other constant predicates in a further pre-compilation step.Thereby,we infer a type hierarchy and an associated mapping of objects to types.Indexing Based on the number of counted objects,indices for the grounded predicates, functions and actions are devised.Since in our example problem we have eight ob-jects and the predicates at and in have two parameters,we reserve2·8·8=128 index positions.Similarly,the function distance consumes64indices,while fuel,Edelkamp(define(domain zeno-travel)(:requirements:durative-actions:typing:fluents)(:types aircraft person city)(:predicates(at?x-(either person aircraft)?c-city)(in?p-person?a-aircraft))(:functions(fuel?a-aircraft)(distance?c1-city?c2-city)(slow-speed?a-aircraft)(fast-speed?a-aircraft)(slow-burn?a-aircraft)(fast-burn?a-aircraft)(capacity?a-aircraft)(refuel-rate?a-aircraft)(total-fuel-used)(boarding-time)(debarking-time))(:durative-action board:parameters(?p-person?a-aircraft?c-city):duration(=?duration boarding-time):condition(and(at start(at?p?c))(over all(at?a?c))):effect(and(at start(not(at?p?c)))(at end(in?p?a))))[...](:durative-action zoom:parameters(?a-aircraft?c1?c2-city):duration(=?duration(/(distance?c1?c2)(fast-speed?a))):condition(and(at start(at?a?c1))(at start(>=(fuel?a)(*(distance?c1?c2)(fast-burn?a))))) :effect(and(at start(not(at?a?c1)))(at end(at?a?c2))(at end(increase total-fuel-used(*(distance?c1?c2)(fast-burn?a))))(at end(decrease(fuel?a)(*(distance?c1?c2)(fast-burn?a))))))(:durative-action refuel:parameters(?a-aircraft?c-city):duration(=?duration(/(-(capacity?a)(fuel?a))(refuel-rate?a))):condition(and(at start(<(fuel?a)(capacity?a)))(over all(at?a?c))):effect(at end(assign(fuel?a)(capacity?a)))))Figure3:Zeno-Travel domain description in PDDL2.1.slow-speed,fast-speed,slow-burn,fast-burn,capacity,and refuel-rate each reserve eight index positions.For the quantities total-fuel-used,boarding-time, debarking-time only a single fact identifier is st but not least we model duration as an additional quantity total-time.This special variable is the only one that is overwritten in the least commitment planning approach when scheduling plans as described in Section4.Taming Numbers and Durations in MIPS(define(problem zeno-travel-1)(:domain zeno-travel)(:objects plane-aircrafternie scott dan-personcity-a city-b city-c city-d-city)(:init(=total-fuel-used0)(=debarking-time20)(=boarding-time30) (=(distance city-a city-b)600)(=(distance city-b city-a)600)(=(distance city-b city-c)800)(=(distance city-c city-b)800)(=(distance city-a city-c)1000)(=(distance city-c city-a)1000)(=(distance city-c city-d)1000)(=(distance city-d city-c)1000)(=(fast-speed plane)(/60060))(=(slow-speed plane)(/40060))(=(fuel plane)750)(=(capacity plane)750)(=(fast-burn plane)(/12))(=(slow-burn plane)(/13))(=(refuel-rate plane)(/75060))(at plane city-a)(at scott city-a)(at dan city-c)(at ernie city-c)) (:goal(and(at dan city-a)(at ernie city-d)(at scott city-d)))(:metric minimize total-time))Figure4:Zeno-Travel problem instance.Flattening Temporal Identifiers We interpret each action as an integral entity,so that all timed propositional and numerical preconditions can be merged.Similarly,all effects are merged,independent of time at which they happen.Invariant conditions like(over all(at?a?c))in the action board are added into the precondition set.We discuss the rationale for this step in Section4.1.Grounding Propositions Fact-space exploration is a relaxed enumeration of the planning problem to determine a superset of all reachable facts.Algorithmically,a FIFO fact queue is compiled.Successively extracted facts at the front of the queue are matched to the operators.Each time all preconditions of an operator are fulfilled,the resulting atoms according to the positive effect(add)list are determined and enqueued.This allows us to separate offconstant facts fromfluents,since only the latter are reached by exploration.Clustering Atoms For a concise encoding of the propositional part we separatefluents into groups,so that each state in the planning space can be expressed as a conjunc-tion of(possibly trivial)facts drawn from each fact group(Edelkamp&Helmert, 1999).More precisely,let#p i(o1,...,o i−1,o i+1,...,o n)be the number of objects o i for which the fact(p o1...o n)is true.We establish a single-valued invariant at i if#p i(o1,...,o i−1,o i+1,...,o n)=1.To allow for a better encoding,some predicates like at and in are merged.In the example,three groups determine the unique position of the persons(one offive)and one group determines the position of the plane(one of four).Therefore,3·⌈log5⌉+1·⌈log4⌉=11bits suffice to encode the total of19fluents.EdelkampGrounding Actions Fact-space exploration also determines all grounded operators.Once all preconditions are met and grounded,the symbolic effect lists are instantiated.In our case we determine98instantiated operators,which,by some further simplifications that eliminate duplicates and trivial operators(no-ops),are reduced to43. Grounding Functions Simultanous to fact space exploration of the propositional part of the problem,all heads of the numerical formulae in the effect lists are grounded.In the example case only three instantiated formulae arefluent(vary with time):(fuel plane)with initial value750as well as total-fuel-used and total-time both ini-tialized with zero.All other numerical predicates are in fact constants that can be substituted in the formula-bodies.In the example,the effect in(board dan city-a) reduces to(increase(total-time)30),while(zoom plane city-a city-b)has the numerical effects(increase(total-time)150),(increase(total-fuel-used) 300)),and(decrease(fuel plane)300).Refuelling,however,does not reduce toa single rational number,for example the effects in(refuel plane city-a)onlysimplify to(increase(total-time)(/(-(750(fuel plane))/12.5)))and (assign(fuel plane)750).To evaluate the former assignment especially for a for-ward chaining planner,the variable(total-time)has to be instantiated on-the-fly.This is due to the fact that the value of the quantity(fuel plane)is not constant and itself changes over time.Symmetry Detection Regularities of the planning problem with respect to the transpo-sition of domain objects is partially determined in the static analyzer and is addressed in detail in Section5.The intermediate textual format of the static analyzer in annotated grounded PDDL-like representation serves as an interface for other planners or model checkers,and as an additional resource for plan visualization.Figures5and6show parts of the intermediate representation as inferred in the Zeno-Travel example.3.3HeuristicsMIPS incorporates the following heuristic estimates.Relaxed planning heuristic(RPH)Approximation of the number of planning steps needed to solve the propositional planning problem with all delete effects removed(Hoff-mann&Nebel,2001).The heuristic is constructive,that is it returns the set of operators that appear in the relaxed plan.Numerical relaxed planning heuristic(numerical RPH)Our extension to RPH to deal with with numbers is a combined propositional and numerical approximation scheme allowing multiple operator application.Pattern database heuristic(explicit PDB)Different planning space abstractions are found in a greedy manner,yielding a selection of pattern databases thatfit into main memory.In contrast to RPH,pattern database can be designed to be disjoint yielding an admissible estimate as needed for optimal planning in A*(Edelkamp,2001c).(define(grounded zeno-travel-zeno-travel-1)(:fluents(at dan city-a)(at dan city-b)(at dan city-c)(at dan city-d)(at ernie city-a)(at ernie city-b)(at ernie city-c)(at ernie city-d)(at plane city-a)(at plane city-b)(at plane city-c)(at plane city-d)(at scott city-a)(at scott city-b)(at scott city-c)(at scott city-d)(in dan plane)(in ernie plane)(in scott plane))(:variables(fuel plane)(total-fuel-used)(total-time))(:init(at dan city-c)(at ernie city-c)(at plane city-a)(at scott city-a)(=(fuel plane)750)(=(total-fuel-used)0)(=(total-time)0))(:goal(at dan city-a)(at ernie city-d)(at scott city-d))(:metric minimize(total-time))(:group dan(at dan city-a)(at dan city-b)(at dan city-c)(at dan city-d)(in dan plane))(:group ernie(at ernie city-a)(at ernie city-b)(at ernie city-c)(at ernie city-d)(in ernie plane))(:group plane(at plane city-a)(at plane city-b)(at plane city-c)(at plane city-d))(:group scott(at scott city-a)(at scott city-b)(at scott city-c)(at scott city-d)(in scott plane))Figure5:Grounded representation of Zeno-Travel domain.Symbolic pattern database heuristic(symbolic PDB)Symbolic PDBs apply to ex-plicit and symbolic heuristic search engines(Edelkamp,2002b).Due to the succinct BDD-representation of sets of states,symbolic PDBs are often orders of magnitudes larger than explicit ones.Scheduling relaxed plan heuristic(scheduling RPH)Critical-path analysis through scheduling guide the planfinding phase.Like RPH,which computes the length of the greedily extracted sequential plan,scheduling RPH also takes the relaxed sequence of operators into account,but searches for a suitable parallel arrangement,which in turn defines the estimator function.3.4Exploration AlgorithmsThe algorithm portfolio includes three main explicit heuristic search algorithms.A*The A*algorithm(Hart,Nilsson,&Raphael,1968)is a variant of Dijkstra’s single-source shortest path exploration scheme executed on a re-weighted state space graph.For lower bound heuristics,A*can be shown to generate optimal plans(Pearl,1985).Weighting the influence of the heuristic estimate may accelerate solutionfinding,but also affects optimality(Pohl,1977).。