Views Customizable abstractions for context-aware applications in MANETs
- 格式:pdf
- 大小:113.04 KB
- 文档页数:7

C#中abstract的⽤法详解abstract可以⽤来修饰类,⽅法,属性,索引器和时间,这⾥不包括字段. 使⽤abstrac修饰的类,该类只能作为其他类的基类,不能实例化,⽽且abstract修饰的成员在派⽣类中必须全部实现,不允许部分实现,否则编译异常. 如:using System;namespace ConsoleApplication8{class Program{static void Main(string[] args){BClass b = new BClass();b.m1();}}abstract class AClass{public abstract void m1();public abstract void m2();}class BClass : AClass{public override void m1(){throw new NotImplementedException();}//public override void m2()//{// throw new NotImplementedException();//}}}Abstract classes have the following features:抽象类拥有如下特征:1,抽象类不能被实例化, 但可以有实例构造函数, 类是否可以实例化取决于是否拥有实例化的权限 (对于抽象类的权限是abstract, 禁⽌实例化),即使不提供构造函数, 编译器也会提供默认构造函数;2,抽象类可以包含抽象⽅法和访问器;3,抽象类不能使⽤sealed修饰, sealed意为不能被继承;4,所有继承⾃抽象类的⾮抽象类必须实现所有的抽象成员,包括⽅法,属性,索引器,事件;abstract修饰的⽅法有如下特征:1,抽象⽅法即是虚拟⽅法(隐含);2,抽象⽅法只能在抽象类中声明;3,因为抽象⽅法只是声明, 不提供实现, 所以⽅法只以分号结束,没有⽅法体,即没有花括号部分;如public abstract void MyMethod();4,override修饰的覆盖⽅法提供实现,且只能作为⾮抽象类的成员;5,在抽象⽅法的声明上不能使⽤virtual或者是static修饰.即不能是静态的,⼜因为abstract已经是虚拟的,⽆需再⽤virtual强调.抽象属性尽管在⾏为上与抽象⽅法相似,但仍有有如下不同:1,不能在静态属性上应⽤abstract修饰符;2,抽象属性在⾮抽象的派⽣类中覆盖重写,使⽤override修饰符;抽象类与接⼝:1,抽象类必须提供所有接⼝成员的实现;2,继承接⼝的抽象类可以将接⼝的成员映射位抽象⽅法.如:interface I{void M();}abstract class C: I{public abstract void M();}抽象类实例:// abstract_keyword.cs// 抽象类using System;abstract class BaseClass // 抽象类{protected int _x = 100; //抽象类可以定义字段,但不可以是抽象字段,也没有这⼀说法.protected int _y = 150;public BaseClass(int i) //可以定义实例构造函数,仅供派⽣的⾮抽象类调⽤; 这⾥显式提供构造函数,编译器将不再提供默认构造函数. {fielda = i;}public BaseClass(){}private int fielda;public static int fieldsa = 0;public abstract void AbstractMethod(); // 抽象⽅法public abstract int X { get; } //抽象属性public abstract int Y { get; }public abstract string IdxString { get; set; } //抽象属性public abstract char this[int i] { get; } //抽象索引器}class DerivedClass : BaseClass{private string idxstring;private int fieldb;//如果基类中没有定义⽆参构造函数,但存在有参数的构造函数,//那么这⾥派⽣类得构造函数必须调⽤基类的有参数构造函数,否则编译出错public DerivedClass(int p): base(p) //这⾥的:base(p)可省略,因为基类定义了默认的⽆参构造函数{fieldb = p;}public override string IdxString //覆盖重新属性{get{return idxstring;}set{idxstring = value;}}public override char this[int i] //覆盖重写索引器{get { return IdxString[i]; }}public override void AbstractMethod(){_x++;_y++;}public override int X // 覆盖重写属性{get{return _x + 10;}}public override int Y // 覆盖重写属性{get{return _y + 10;}}static void Main(){DerivedClass o = new DerivedClass(1);o.AbstractMethod();Console.WriteLine("x = {0}, y = {1}", o.X, o.Y);}}以上所述是⼩编给⼤家介绍的C#中abstract的⽤法详解,希望对⼤家有所帮助,如果⼤家有任何疑问请给我留⾔,⼩编会及时回复⼤家的。


customize-cra override "customizecra override" refers to the process of personalizing or modifying a specific feature or element of an application or software. This article will provide a step-by-step guide on how to perform a "customizecra override" and the benefits it can bring.Introduction:Customization is an essential aspect of software development and user experience. It allows users to tailor an application or software according to their specific needs and preferences. The "customizecra override" process enables users to override default settings, functionalities, or styles of a particular feature within an application. By doing so, users can enjoy a more personalized and enhanced user experience. In this article, we will walk you through the steps required to perform a "customizecra override" effectively.Step 1: Identify the Feature to OverrideThe first step in the "customizecra override" process is to identify the feature or element within the application that you intend to modify. It could be anything from the appearance of a button to the behavior of a search function. Once you have identified the target feature, proceed to the next step.Step 2: Familiarize Yourself with the CodebaseTo perform a successful "customizecra override," it's crucial to have a good understanding of the application's underlying codebase. Familiarize yourself with the relevant components, modules, and stylesheets related to the feature you want to override. This step might require some technical knowledge or assistance from developers if you are not proficient in coding.Step 3: Create a Customization StrategyBefore making any changes, it's essential to have a clear plan or strategy about what you want to achieve with your customization. Determine the specific modifications or enhancements you wish to apply to the feature. Outline the goals, requirements, and desired outcome of your customization. This strategy will serve as a roadmap for the next steps.Step 4: Set Up a Development EnvironmentTo safely perform a "customizecra override," it's recommended to set up a separate development environment. This ensures that any changes you make won't affect the production version of the application. Clone the project repository or create a local copy towork on.Step 5: Modify the Target FeatureUsing your chosen code editor or integrated development environment (IDE), navigate to the relevant files associated with the feature you want to customize. Make the necessary modifications according to your customization plan. This might involve changing the existing code, adding new code, or modifying existing stylesheets.Step 6: Test and DebugAfter completing the customization, it's crucial to thoroughly test and debug your changes. Run the application in the development environment and verify if the modifications are working as intended. Test various scenarios and edge cases to ensure that the customization doesn't introduce any errors or conflicts.Step 7: Refine and IterateBased on the testing phase, you might discover areas that require further refinement or improvement. It's common to iterate on the customization process, making additional adjustments until the desired outcome is achieved. Pay attention to user feedback or anypotential issues that arise during testing.Step 8: Document and ShareOnce the customization is finalized and tested successfully, document the steps you followed, including any code changes, stylesheets modifications, or additional dependencies used. This documentation will be useful for future reference or sharing your customization with other users or developers.Conclusion:Performing a "customizecra override" allows users to tailor an application's features to their specific needs. By following thestep-by-step guide outlined in this article, you can effectively implement a customization process. Remember to have a clear plan, familiarize yourself with the codebase, and thoroughly test your changes to ensure a smooth and successful customization experience.。

1.面向对象的思想主要包括什么?答:个人认为一各程序语言要成为真正的面向对象的程序设计语言,它必须符合下列条件: 1抽象(abstraction)—抽象能够有效地管理一个问题的复杂性,其作法是划分出与该问题相关的一组对象.2 封装(Encapsulation)—封装是指将一个抽象的内部实现隐藏在特定的对象之内.3 多态(polymorphism)—多态会提供相同方法的多种操作方法的多种操作实作.例如,不同的对象都会拥有一个Save方法,但是每一个Save方法会执行不同的操作.4 继承(inheritance)—Visual C# 2005 最令人兴奋之处就是其继承特性.v c#2005则提供了真正的方法继承,因此您可以重复使用一个类的实例.2.什么是中的用户控件自己动手作自己的控件来取代.NET提供的控件。
这种控件就是用户控件。
后缀为.ascx3.什么叫应用程序域?什么是受管制的代码?什么是强类型系统?什么是装箱和拆箱?什么是重载?什么是多态? CTS、CLS和CLR分别作何解释?应用程序域:应用程序域(通常是AppDomain)是用于隔离应用程序的虚拟进程。
在同一个应用程序作用域中创建的所有对象(换句话说,从该应用程序的入口点开始沿着对象激活序列的任何地方)都在同一个应用程序域中创建。
多个应用程序域可以存在于一个操作系统进程中,使它们成为隔离应用程序的简便方式。
操作系统进程通过使用各不相同的内存地址空间来提供隔离。
尽管它是有效的,但也是代价昂贵的,并且不能达到大型Web 服务器所需要的数量。
与其相比,公共语言运行时通过管理在应用程序域中运行的代码的内存使用来强制进行应用程序隔离。
这样就确保它不会访问应用程序域以外的内存。
需要注意的是,只有类型安全的代码才能以这种方式管理(当在应用程序域中加载不安全代码时,运行时不能保证隔离)。
理解应用程序域:应用程序域是.NET 运行库的逻辑进程表示,操作系统进程可以包含多个应用程序域。

Visual Abstracts示例1. 什么是Visual Abstracts?Visual Abstracts是一种科学传播的新形式,它通过图形和简洁的文字呈现科学研究的关键信息,使复杂的研究内容更易于理解和传播。
Visual Abstracts通常用于学术期刊、学术会议或社交媒体上,以吸引读者的注意并概括研究的核心内容。
2. Visual Abstracts的优势2.1 提高可视化效果Visual Abstracts通过图形和图表的方式,将研究的关键结果和发现直观地展示给读者。
相比于传统的文字摘要,Visual Abstracts更容易引起读者的兴趣和注意,提高了信息的可视化效果。
2.2 简洁明了的信息传递Visual Abstracts通过简洁明了的文字和图形,将研究的要点和重要信息传达给读者。
它避免了繁琐的技术术语和复杂的研究方法的描述,使得读者更容易理解和记忆研究的关键内容。
2.3 提高科学传播的效率Visual Abstracts的简洁和可视化特点使得科学研究更易于传播。
读者可以通过浏览Visual Abstracts来了解研究的主要结果,从而决定是否深入阅读全文。
这种高效的科学传播方式有助于提高科学研究的影响力和可见度。
3. Visual Abstracts的制作步骤3.1 确定关键信息在制作Visual Abstracts之前,首先需要确定研究的关键信息。
这包括研究的背景、目的、方法、结果和结论等。
通过梳理和整理这些关键信息,可以为制作Visual Abstracts提供清晰的思路。
3.2 设计布局和图形在制作Visual Abstracts时,需要设计合适的布局和图形来展示关键信息。
合理的布局能够使信息有序地呈现,而图形的使用可以增加可视化效果。
常用的图形包括流程图、柱状图、折线图等,根据研究内容选择合适的图形进行呈现。
3.3 编写简洁的文字描述除了图形之外,Visual Abstracts还需要简洁明了的文字描述来补充图形的信息。

In the future,mobile phones are expected to undergo significant transformations, becoming more advanced and integrated into our daily lives.Heres a glimpse into what future mobile phones might look like:1.Advanced AI Integration:Future mobile phones will likely have more sophisticated artificial intelligence capabilities.They will be capable of understanding and predicting user behavior,offering personalized suggestions and assistance.2.Flexible and Foldable Displays:The technology for flexible screens will improve, allowing phones to be rolled up or folded when not in use.This will make them more portable and less prone to breakage.3.Extended Battery Life:With the advancement in battery technology,future mobile phones will have longerlasting batteries,possibly with wireless charging capabilities that can be charged from a distance.4.Augmented Reality AR Integration:Phones will have builtin AR capabilities,allowing users to overlay digital information onto the real world,enhancing gaming,navigation, and social interactions.5.Seamless Connectivity:Future mobile phones will connect effortlessly with other devices and networks,including5G and beyond,ensuring highspeed internet access and smooth data transfer.6.Enhanced Security Features:As cyber threats become more sophisticated,mobile phones will incorporate advanced security measures such as biometric authentication, secure data encryption,and intrusion detection systems.7.Health Monitoring:Future mobile phones may come with builtin health monitoring tools,such as heart rate monitors,blood pressure sensors,and even sleep tracking, providing users with valuable health data.8.Environmental Adaptability:Phones will be designed to withstand harsher conditions, with improved water and dust resistance,as well as the ability to operate in extreme temperatures.9.EcoFriendly Materials:There will be a shift towards using sustainable and recyclable materials in the construction of mobile phones,reducing their environmental impact.10.Customizable Interfaces:Users will have the ability to customize their phonesinterface to suit their preferences,including the layout,color scheme,and even the level of interaction with AI assistants.11.Voice and Gesture Control:Future mobile phones will likely have more advanced voice recognition and gesture control,reducing the need for physical buttons and improving user experience.12.Holographic Projection:Some models may feature holographic projection capabilities, allowing users to interact with3D images and videos.13.Integration with Wearable Tech:Mobile phones will work more closely with wearable technology,such as smartwatches and health bands,providing a seamless user experience across devices.14.Smart Home Control:Phones will serve as central hubs for controlling smart home devices,allowing users to manage their homes lighting,temperature,and security systems from their mobile device.15.Virtual Personal Assistants:AIpowered personal assistants will become more humanlike,offering emotional intelligence and the ability to learn from user interactions to provide better service.The future of mobile phones is exciting,with technology continually pushing the boundaries of what is possible.These devices will not only be tools for communication and entertainment but also integral parts of our lives,enhancing our experiences and making our daily tasks more efficient and enjoyable.。

Annotation实战【自定义AbstractProcessor】前言在使用Java的过程中,每个开发人员都接触过@Override, @Deprecated 等等各式各样的注解,这些东西是java最基础的一些原生定义好的annotation。
本文通过一个实例演示如果自定义自己的annotation,使得在编译源码代码阶段进行额外操作。
案例源码预热简单说一下annotation的基本知识,从java的官方技术文档可以直接找到annotation的技术点。
Annotations, a form of metadata, provide data about a program thatisnot part ofthe program itself. Annotations have no direct effect onthe operation ofthe code they annotate.Annotations是一种元数据,其作用在于提供程序本身以外的一些数据信息,也就是说Annotation他不会属于程序代码本身,不参与逻辑运算,故而不会对原程序代码的操作产生直接的影响。
一般来说Annotation有如下三种使用情形:Information for the compiler— Annotations can be used by the compiler to detect errors or suppress * warnings.∙Compile-time and deployment-time processing— Software tools can process annotation information to generate code, XML files, and so forth.∙Runtime processing— Some annotations are available to be examined at runtime.∙为编译器提供辅助信息— Annotations可以为编译器提供而外信息,以便于检测错误,抑制警告等.∙编译源代码时进行而外操作—软件工具可以通过处理Annotation信息来生成原代码,xml文件等等.∙运行时处理—有一些annotation甚至可以在程序运行时被检测,使用.具体annotation的详细知识点可以参考技术文档,本文案例针对的是编译源代码时进行而外操作。
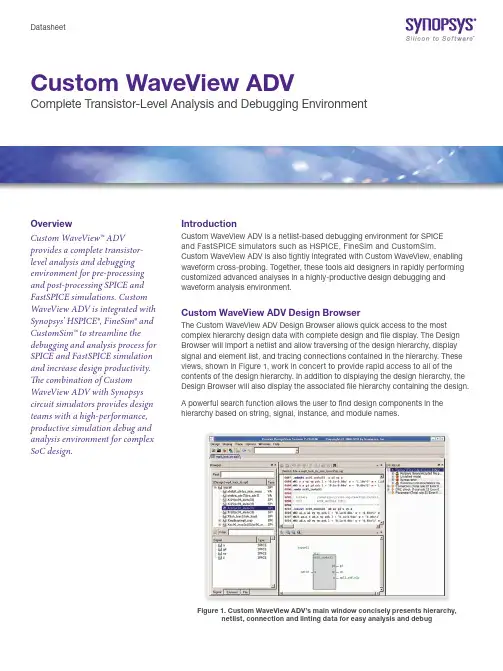
DatasheetCustom WaveView ADVComplete Transistor-Level Analysis and Debugging EnvironmentOverviewCustom WaveView™ ADVprovides a complete transistor-level analysis and debuggingenvironment for pre-processingand post-processing SPICE andFastSPICE simulations. CustomWaveView ADV is integrated withSynopsys’ HSPICE®, FineSim® andCustomSim™ to streamline thedebugging and analysis process forSPICE and FastSPICE simulationand increase design productivity.The combination of CustomWaveView ADV with Synopsyscircuit simulators provides designteams with a high-performance,productive simulation debug andanalysis environment for complexSoC design.IntroductionCustom WaveView ADV is a netlist-based debugging environment for SPICEand FastSPICE simulators such as HSPICE, FineSim and CustomSim.Custom WaveView ADV is also tightly integrated with Custom WaveView, enablingwaveform cross-probing. Together, these tools aid designers in rapidly performingcustomized advanced analyses in a highly-productive design debugging andwaveform analysis environment.Custom WaveView ADV Design BrowserThe Custom WaveView ADV Design Browser allows quick access to the mostcomplex hierarchy design data with complete design and file display. The DesignBrowser will import a netlist and allow traversing of the design hierarchy, displaysignal and element list, and tracing connections contained in the hierarchy. Theseviews, shown in Figure 1, work in concert to provide rapid access to all of thecontents of the design hierarchy. In addition to displaying the design hierarchy, theDesign Browser will also display the associated file hierarchy containing the design.A powerful search function allows the user to find design components in thehierarchy based on string, signal, instance, and module names.Figure 1. Custom WaveView ADV’s main window concisely presents hierarchy,netlist, connection and linting data for easy analysis and debugDebuggingSourceView and ConnectionViewThe SourceView and ConnectionView shows the contents of the SPICE netlist and creates a visualization of the connections contained within the netlist (see Figure 1).SourceViewThe SourceView displays the hierarchical content of the SPICE netlist, allowing the designer to query the contents of a design or cell. Selecting a subcircuit in the SourceView displays the contents of that subcircuit as well as displaying the interface pins and netnames, and parameters in the ConnectionView. ConnectionViewThe ConnectionView creates design connectivity visualization of the object selected in the Hierarchy Browser. Included in the diagram are the name of the object, its terminal names and the nets that connect to it. In the case of subcircuits, the internal netnames are also displayed, making it easy to follow nets up and downthe hierarchy through subcircuit boundaries. CustomWaveView ADV’s Net Tracer can also be used to follow changing net names with ease through the design’s hierarchy.Signal TracingSignal flow can be traced in both SourceView and ConnectionView. In SourceView, the statements representing a selected net are highlighted and can be traced subsequently. In ConnectionView, devices or subcircuits connecting a selected signal are displayed and new connections can be displayed for pins/ports of the connected elements.SPICE Lint ViewCustom WaveView ADV’s SPICE Lint View performs user-selected compatibility checks that can be used to verify that the netlists being simulated conform to the proper syntax before wasting time on a long simulation before finding a problem. These checks are performed automatically as the netlist is read in with all errors or warnings being flagged in the SPICE Lint Window as well as the corresponding net and device being displayed in the SourceView and ConnectionView.SPICE Syntax RulesChecks for basic SPICE netlist syntax and structure errors such as: missing or redundant END statements, missing or mismatched model device names, missing ground nodes, invalid signal names, etc. Over 40 different syntax and structure checks are performed.Connection RulesFinds and flags problems with floating nodes or blocks, global nodes that are not driven by any source,DC-floating MOS gate and nodes, dangling element terminals, and floating transient sources. This helps the designer to deliver a quality netlist to the simulator of choice.Parameter Passing and Parameter Rule ChecksParameter passing rule checks verify that all passed parameters are properly defined before use and properly passed through the hierarchy. Parameters that are redefined or recursively defined are also found.The parameter rule checks also finds and flags parameter values that are set above user definable thresholds. This includes looking for element parameter Negative capacitance/resistance, out-of-range element values and sizes, non-positive subcircuit multiplier and PWL stimuli statements with sharp slews.Design Connectivity Rule ChecksLooks for static DC issues such as conducting device or path, leakage device or path, as well as pulse source errors and scale errors.Custom WaveView IncludedThe Waveform Window is Custom WaveView (included with a Custom WaveView ADV license), the industry standard for waveform analysis and measurement. Custom WaveView provides a host of capabilities for displaying, measuring, manipulating and saving simulation results. In addition to multiple panels containing waveforms, Custom WaveView also provides the ability to display more than one waveform tab allowing the designer to mix and match time and frequency domains in a single session. Custom WaveView is a full analog and mixed-signal display and analysis environment, reading simulation results from either analog or digital simulators and allowing complete conversion between views. For instance, Custom WaveView can read inthe analog results of an HSPICE simulation, convert those waveforms to digital (single or multi-bit with user selectable thresholds) and export those results for use in a digital simulation.Full cross-probing is supported between both Custom WaveView ADV and Custom WaveView.Other UtilitiesHierarchical Netlist Flatten and ExportHierarchical netlists can be flattened and exported to tools that require flat netlist views. The hierarchy information is preserved via net names in the flat netlist.Source Waveform PreviewStimuli statements (Pulse, PWL, Sine, Exp or SFFM) statements can be extracted from netlists and displayed prior to simulations to verify their correctness.Parameter ReportsA final report on all parameters in a netlist can be produced show their final values as passed to simulation.Total Device Area ReportsThe widths and lengths of transistors in netlists can be extracted and reported to help verify correct netlist construction. This capability helps eliminate errors like missing unit values that would result in one-meter transistors (rather than 1 micron) or 10-Farad capacitors (rather than 10 femtoFarads).HSPICE .Measure Statement Extraction and ReplayCustomExplorer contains the ability to scan a netlist and extract out all HSPICE .Measure statements and save them in a file. These statements retain their full design hierarchy and can be modified and replayed against existing simulation results. This capability eliminates lost simulation time when the designer determines, after a simulation, that additional .Measure needs to be performed, or when a given .Measure was incorrect during the simulation. In the latter case, the simulation does not need to be rerun as the incorrect .Measure can be fixed and replayed against the results, saving time and effort.Batch Waveform CompareA powerful capability in Custom WaveView ADV is the Batch Waveform Compare utility. This utility allows designers to compare two sets of simulation runs in batch and produce a text report of the differences. The Batch Waveform Compare system uses a simple rules file that controls the comparisons. Users can define what signals are to be compared and the tolerances of the comparisons. Using sample-based comparison techniques, the Batch Waveform Compare utility compares golden-to-target simulation results and supports both analog and digital waveforms. This capability helps eliminate the vast majority of manual “eyeballing”of analog or digital signals. Users have reported reducing as much as one full week of manual effort to 15 minutes for analyzing 100 analog waveforms.Extensible and OpenCustom WaveView ADV is open and extensible and can be controlled in both GUI or Batch mode with scripting. The GUI is also extensible, allowing CAD teams to craft custom measurements and provide them across their organizations through the regular menu system.Regression Scripting with the Analysis Command Environment (ACE)The Analysis Command Environment (ACE) is a Tcl-based extension language that provides near-complete control of Custom WaveView ADV. The ACE scripting environment contains hundreds of functions and can control the GUI, the waveform panels, the menu system or the measurement capabilities of either tool. Often used by CAD teams to extend the tools, the ACE scripting capability can also be used to perform Regression Scripting allowing designers to make changes to their design and then replay a wide variety of analyses in batch mode, freeing the designer to work on other aspects of the design. Encapsulating these analyses also means sharing best design practices across an organization improving quality and simplifying the collection of data for design reviews.Industry Standard Design Platform IntegrationsCustom WaveView ADV is also integrated into industry-standard design platforms to help maximize designer productivity during the design phase. A native integration of this tool into Synopsys’ Galaxy Custom Designer®system helps form a complete environment for analog block authoring in a single platform for both cell-based and custom design. Other design platform integrations include:`Cadence Design Systems: Virtuoso® Composer and ADE``JEDAT: Asca Circuit Design and Debugging Environment``Mentor Graphics: Design Architect® IC``Synopsys: Laker™ Custom Layout``Automation System`Supported File FormatsCustom WaveView ADV provides support for over 45 different file formats giving it the highest support of simulation file formats in the industry.`Supported Simulator Formats`–Synopsys• CustomSim and CustomSim FT (HSIM, XA and NanoSim — WDF, WDB, .Out and Vector)• HSPICE and HSPICE RF (.Tr0, .Ac0, .Sw0…— Binary and ASCII)• VCS (VCD and VPD)• Saber (AI/PL — Binary and ASCII)–Cadence Design Systems• Spectre (PSF, WSF — Binary and ASCII)• UltraSim (PSF, WSF — Binary and ASCII)• PSPICE (DAT)• Incisive (VCD)–Mentor Graphics• ModelSim (WLF)• Eldo (COU 4.3, 4.7 and Tr0)• ADMS (WDB and JWDB)• ADiT (Tr0 and Tb0)• HyperLynx (CSV)–Others• Agilent ADS (.ds — Binary and TouchStone S-Parameters — ASCII)• CSDF (ASCII)• Novas FSDB (Binary)• Legend (Tr0 Derivative)• SmartSPICE (Raw Derivative)• Five proprietary simulator formats are also available — please contact Synopsys–Data Formats• IBIS Models• Tektronix Agilent and Lecroy Scope Data• Text table data and Comma Separated Values (CSV)Synopsys, Inc. • 690 East Middlefield Road • Mountain View, CA 94043 • ©2016 Synopsys, Inc. All rights reserved. Synopsys is a trademark of Synopsys, Inc. in the United States and other countries. A list of Synopsys trademarks is available at /copyright.html . All other names mentioned herein are trademarks or registered trademarks of their respective owners.``Supported Netlist Formats–Synopsys HSPICE–DSPF–Cadence Spectre and CDL–Mentor Graphics Eldo–Standard SPICEPlatform Support``Microsoft Windows 64-bit``Red Hat Enterprise``SUSE Linux Enterprise (64)。

abstract 怎么读
“abstract”的发音为:英式英语[ˈæbstrækt],美式英语[ˈæbstrækt]。
在发音时,注意将重音放在第一个音节上,“æ”发类似“æb”的音,“strækt”部分要清晰发出“str”和“ækt”的音。
“abstract”是一个英语单词,可以用作形容词和名词。
作为形容词时,它的意思是“抽象的”,用来描述不具体、不实际、脱离实际的概念或思想。
作为名词时,它的意思是“摘要”,即对一篇文章、报告或研究的简短、概括性的总结。
此外,“abstract”还可以用作动词,意为“提取”、“抽取”,指从某物中提取出其本质或关键信息。
在计算机科学领域,“abstract”也常用来描述抽象类或抽象方法,这是一种编程概念,用于定义具有共同特性的类的方法,但不包含具体的实现。
总之,“abstract”是一个多功能的英语单词,在学术、商业和日常交流中都有广泛的应用。
正确掌握其发音和用法,有助于提高英语交流和理解能力。
F U S I O N E D I T I O NR E L E A S E11.1.2C ONTENTS I N B RIEFOverview (2)Smart View Panel (2)Context-Sensitive Ribbons (2)Integration with Outlook (3)Redesigned Options Dialog Box (3)Planning Features (4)Financial Management Features (5)Smart View and Disclosure Management Integration (5)New VBA Functions (5)EPM System New Features (6)OverviewThis document describes the new features introduced in Oracle Hyperion Smart View for Office, Fusion Edition Release 11.1.2.It is our goal to make Oracle products, services, and supporting documentation accessible to the disabled community. Smart View Release 11.1.2 supports accessibility features, which are described in Appendix A of the Smart View for Office User's Guide.Smart View PanelFrom the Smart View Panel, you can manage data source connections, access data and task lists, create reports, and open Oracle Crystal Ball Enterprise Performance Management, Fusion Edition workbooks if you are licensed for Crystal Ball EPM.The Smart View Panel, opened from the Smart View ribbon, is displayed by default on the right side of the Microsoft Office application. You can move, re-size, or close the Smart View Panel from the down arrow in the title bar.The Smart View Panel contains the following panes:l Home: A panel that displays links to shared connections and private connections as well asa list of recently used items - ad hoc grids, data forms, and tasks - which you can click toestablish a connection.l Shared Connections: A drop-down menu of available connections from Oracle's Hyperion®Shared Services and a tree view of the contents of the currently selected connection.l Private Connections: A drop-down menu of available connections saved on the local computer and a tree view of the contents of the currently selected connection. You can also enter a URL to connect directly to a data source here.l Task Lists: A tree list of tasks from which you can manage your tasks. This pane opens only when you select a task list from shared connections or private connections.l Simulation Workbook: (only if you are licensed for Crystal Ball EPM) A tree list of available Oracle Crystal Ball Enterprise Performance Management, Fusion Edition workbooks that you can open in Smart View.l Action Panel: A list of operations available based on the selection in the shared connection.private connection, or task list tree list.Context-Sensitive RibbonsSmart View operations in Microsoft Office applications are available through ribbon commands. The Smart View ribbon, which contains commands for common Smart View operations, is always present. When you connect to a data source (other than Oracle's Hyperion Reporting and Analysis), the corresponding data source ribbon is also displayed. For Oracle Hyperion Planning, Fusion Edition, Oracle Hyperion Financial Management, Fusion Edition, and Oracle's Hyperion® Enterprise®, when you enter ad hoc analysis, the data source ribbon is automatically 2New Featuresreplaced by its ad hoc version. Each ribbon displays only the commands permitted for that datasource, mode, and Office application.These are the new ribbons:l Smart Viewl Essbasel Planningl Planning Ad Hocl HFM (Financial Management )l HFM Ad Hocl Enterprise (Oracle's Hyperion® Enterprise®)l Enterprise Ad Hocl OBIEE (Oracle Business Intelligence Enterprise Edition)Note:Microsoft Office 2003 users can still access Smart View operations via menus.Integration with OutlookPlanning and Financial Management task lists are now integrated into Outlook, so users canintegrate their tasks into Outlook tasks and perform these tasks from within Outlook. Data formtasks are seamlessly launched from Outlook into the familiar Excel interface.Redesigned Options Dialog BoxThe Smart View Options dialog box has been redesigned to make options more easily accessible.Options are organized into categories to provide better user experience and accommodateprovider-specific options. Like other components of Smart View in this release, options areavailable to users only if they are supported by the currently connected data source.The following new options are available from the Options dialog box:l Change the language in which Smart View is displayed without having to re-install Smart Viewl In shortcut menus, choose whether to display Smart View and Microsoft items or only Smart View itemsl Reset all options to default setting with a click of the Reset buttonNew Features3Figure 1 Options Dialog BoxPlanning FeaturesThis release of Smart View supports a greatly expanded set of Planning functionality.l Planning task lists are now integrated into Outlook, so planners can integrate their tasks into Outlook tasks, and can perform these tasks from within Outlook. Planning data form tasks are seamlessly launched from Outlook into the familiar Excel interfacel Planning task lists are available in Office, including task status and task reports; users can perform tasks in Excel, and have them automatically synchronized with the Webl All process management end-user functionality can be accessed from Outlook and Excel l Data validation, including validation indicators and messagesl The ability to monitor the status of Planning jobs in the Job Consolel Composite data forms in Microsoft Office with shared dimensions that are automatically synchronized across multiple data formsl Mass Allocate and Grid Spread for spreading valuesl Copy data across versions for scenario-entity combinationsl Dynamic user variables that allow end users to select and change user variable values directly in data formsl Custom right-click menus for data and metadatal Member formula display4New Featuresl Setting Planning user preferences within Smart Viewl Data forms enabled for ad hoc allow users to slice data and save a slice to create reports or share with other usersFor information about Planning, see the Oracle Hyperion Planning New Features and OracleHyperion Planning User's Guide.Financial Management FeaturesIn this release, Smart Slices are available toFinancial Management users who connect to SmartView. Using Smart Slices, Financial Management users can create and save reports from theReport Designer and cascade reports across a selected dimension.Smart View and Disclosure Management IntegrationCustomers who use Smart View in Excel or Word to assemble financial reports can also useOracle Hyperion Disclosure Management, which allows you to assemble a reporting packagefor submission to a regulatory agency that includes financial statements, as well as supportingschedules and commentary which may exist in Excel, Word, or an Oracle Hyperion FinancialReporting, Fusion Edition report.The first release of Oracle Hyperion Disclosure Management offers a complete XBRL creationand management solution with Enterprise level XBRL mapping; XBRL Taxonomy management,editing and viewing; and Instance document creation, validation and viewing. While viewingSmart View queries in Word or Excel, users can perform data source level mapping with theXBRL Taxonomy Mapping Tool, that allows for re-usable taxonomy element mapping withinOracle Hyperion Financial Management, Fusion Edition, Oracle Hyperion Planning, FusionEdition, and Oracle Essbase.New VBA FunctionsThis release features the following new VBA functions.l HypFindMemberEx retrieves member information like dimension, alias, generation and level names.l HypSetAsDefault creates a connection default.l HypOpenForm opens a data form.l HypSetPages sets page members for the selected sheet.l HypGetPagePOVChoices returns the available member names and member description fora given dimension.l HypDeleteMetaData deletes Oracle Hyperion Smart View for Office, Fusion Edition metadata from the workbook.New Features5l HypGetSharedConnectionsURL returns the Shared Connections URL to be used (also shown in the Options dialog box).l HypSetSharedConnectionsURL sets the Shared Connections URL in the config file and Options dialog box.l HypIsConnectedToSharedConnections checks whether SmartView is connected to Shared Connections.EPM System New Featuresl Most Oracle Hyperion Enterprise Performance Management System products have adopted Oracle Diagnostic Logging (ODL) as the logging mechanism. The ODL framework provides uniform support for managing log files, including log file rotation, maximum log file size, and the maximum log directory size. For more information, see the “Using EPM System Logs” chapter of the Oracle Hyperion Enterprise Performance Management System Installation and Configuration Troubleshooting Guide.l Oracle Configuration Manager (OCM) integrates with My Oracle Support and provides configuration information for Oracle software. It assists in the troubleshooting,maintenance, and diagnostics of your EPM System deployment. For more information about Oracle Configuration Manager see the Oracle Hyperion Enterprise PerformanceManagement System Installation and Configuration Guide.l With this release, many EPM System products support hostnames that resolve to IPv6 addresses. See the Oracle Hyperion Enterprise Performance Management System Certification Matrix. IPv4 support (both hostname and IP address) remains unchanged from earlier releases.l Oracle Hyperion Enterprise Performance Management System supports the following types of SSL configurations:m Full SSL Deployment (including data access)m SSL Terminating at the Web Serverm SSL Accelerators (Off-loading)m Two-way SSLFor more information on the SSL configurations, see the Oracle Hyperion EnterprisePerformance Management System Security Administration Guide.6New FeaturesNew Features7COPYRIGHT NOTICESmart View New Features, 11.1.2Copyright © 2004, 2010, Oracle and/or its affiliates. All rights reserved.Authors: EPM Information Development TeamThis software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing.If this software or related documentation is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable:U.S. GOVERNMENT RIGHTS:Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). Oracle USA, Inc., 500 Oracle Parkway, Redwood City, CA 94065.This software is developed for general use in a variety of information management applications. It is not developed or intended for use in any inherently dangerous applications, including applications which may create a risk of personal injury. If you use this software in dangerous applications, then you shall be responsible to take all appropriate fail-safe, backup, redundancy, and other measures to ensure the safe use of this software. Oracle Corporation and its affiliates disclaim any liability for any damages caused by use of this software in dangerous applications.Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners.This software and documentation may provide access to or information on content, products, and services from third parties. Oracle Corporation and its affiliates are not responsible for and expressly disclaim all warranties of any kind with respect to third-party content, products, and services. Oracle Corporation and its affiliates will not be responsible for any loss, costs, or damages incurred due to your access to or use of third-party content, products, or services.。

C++中abstract修饰类的用法1. 概述在C++中,我们经常会听到关于abstract类的概念。
那么,abstract 类到底是什么?它又有什么作用呢?2. 什么是abstract类在C++中,我们可以使用关键字“abstract”来修饰一个类,使其成为一个“abstract类”。
一个abstract类是一种不能被实例化的类,即不能创建它的对象。
abstract类通常用于定义接口和抽象的行为,它的目的是为了让其他类继承并实现它的纯虚函数。
3. abstract类的定义要定义一个abstract类,我们可以在类中声明纯虚函数。
纯虚函数是指在类中声明但没有实现的虚函数。
通过在函数声明后面加上“= 0”来将一个虚函数声明为纯虚函数。
例如:```C++class AbstractClass {public:virtual void pureVirtualFunction() = 0;};```4. abstract类的作用abstract类的作用主要有以下几点:- 定义接口:abstract类定义了一组接口,表示了一种抽象的行为。
其他类可以继承并实现这些接口。
这样一来,我们就可以通过基类指针来调用派生类的函数。
- 特定行为的约束:abstract类可以约束其派生类必须实现某些特定的行为。
这样一来,我们就可以确保派生类都具有相同的接口,从而提高代码的一致性和可维护性。
- 防止实例化:abstract类的对象不能被创建,这可以防止程序员错误地使用该类,从而避免一些潜在的错误。
5. 如何使用abstract类在C++中,我们可以通过继承abstract类并实现其中定义的纯虚函数来使用abstract类。
例如:```C++class ConcreteClass : public AbstractClass {public:void pureVirtualFunction() override {// 实现纯虚函数的具体逻辑}};```在上面的例子中,ConcreteClass继承了AbstractClass,并实现了其中定义的纯虚函数pureVirtualFunction。
CAsCaDE:C Assertion Checker andDeductive EngineNikhil Sethi and Clark BarrettNew York University,New York,NY-10012{nsethi,barrett}@Abstract.We present a tool,called CAsCaDE,to check assertions inC programs as part of a multi-stage verification strategy.CAsCaDEtakes as input a C program and a controlfile(the output of an earlierstage)that specifies one or more assertions to be checked together with(optionally)some restrictions on program behaviors.For each assertion,CAsCaDE produces either a concrete trace violating the assertion or aproof that the assertion cannot be violated.1IntroductionSoftware verification is an active area of research[2,3,5–8,11,12].A number of tools have been developed which canfind bugs in real applications with large code bases.However,in order to analyze large programs,these tools typically must abstract the state of the program.As a result,at least some of the errors reported by such tools are often false.To reduce the number of false errors,some tools sacrifice soundness and only report warnings that they deem to be most important[12].A promising alternative approach is the idea of two-stage verification[2,9,10].In two-stage verification,a light-weight analysis capable of scaling to large programs is run first to identify potential bugs.This is followed by a more detailed analysis of the error traces identified in thefirst stage to rule out false errors.CAsCaDE provides a generic back-end for two-stage verification of C programs which can be easily integrated with any initial stage.CAsCaDE can handle most C constructs including loops,functions(including recursive functions),structs,pointers,and dynamic memory allocation.2System DescriptionThe overall design of CAsCaDE is shown in Fig.1.The core module of CAs-CaDE takes as input an abstract syntax tree representing a C program and a controlfile that specifies one or more assertions to be checked together with(op-tionally)some restrictions on program behaviors.The core module uses symbolic simulation over the abstract syntax tree to build verification conditions corre-sponding to the assertions given in the controlfile.CAsCaDE uses a bounded model-checking approach to handle loops(and recursive functions).Loops areFig.1.CAsCaDE:System designunrolled afixed number of times(this number can be specified by the user). CAsCaDE models the heap exactly and can track alias relationships between pointers.2.1Abstract InterfacesCAsCaDE is designed to be easily customizable.Major components are hidden behind abstract interfaces.This makes it easy to provide and experiment with a variety of configurations based on the same basic architecture.The core module depends on implementations of three generic abstract interfaces:an abstract syntax tree,a memory module,and a theorem prover.Abstract Syntax Tree.CAsCaDE has a simple internal representation of programs as an abstract syntax tree.All operations are done on this internal representation,completely separating it from the front end which is responsible for building the abstract syntax tree.CAsCaDE currently has an implementa-tion using EDG[4],an industrial-strength parser for C programs,as a front end to create the abstract syntax tree.Abstract Theorem Prover.CAsCaDE uses an abstract theorem proving interface.The interface provides an abstract ExprNode object which corresponds to the implementation of logical expressions in the underlying theorem prover.It also specifies some standard operations on ExprNode like arithmetic operations, boolean operations and array operations.Any theorem prover which can support these operations can easily be used with CAsCaDE.An unsupported operation can be set to return unknown.CAsCaDE currently uses CVC Lite[1]as itstheorem prover.The advantage of using CVC Lite is that we have in-house expertise on using and modifying the theorem prover.Abstract Memory Module.All memory operations during simulation are handled by an abstract interface modeling heap memory.Memory is a mapping from addresses to values where both of them are ExprNode objects.Functions like allocate,deallocate,read and write are supported.The memory module also provides a check address function which checks if a given address is valid or not.This function can be used in assertions.The current implementation of the abstract memory module is the IntegerMemoryModule which uses an array of integers to model memory.We expect to provide a more precise memory module using bit-vectors(which are supported in the latest version of CVC Lite)in the near future.2.2Core ModuleThe core module of CAsCaDE consists of the simulator which is assisted by the AST Manipulator.The Simulator integrates the various modules.It symbolically simulates the program,building expressions using the abstract interface to the theorem prover, and then checking the expressions corresponding to the assertions specified in the controlfile.An interface to the simulator is also exported,enabling CAsCaDE to be used as a library that can be integrated with other tools.The AST Manipulator module has various functions which can modify the AST.For example,unrolling of the loops is handled by this module.This module also interfaces with the controlfile and integrates the restrictions on execution paths and variables with the AST.2.3The Control FileExecution of the tool is guided by a Control File.A controlfile specifies the assertion(s)to be checked.In addition,a controlfile can be used to constrain the search for a violating trace by restricting the program paths to be explored or giving constraints on program variables.This allows important information about feasible violations gathered by an earlier stage to be communicated to CAsCaDE.Controlfile has a simple XML format.It has multiple SourceFile sections which give the paths to C sourcefiles.It has one or more Run section.Each Run section specifies a single run of CAsCaDE.A run of cascade has a single StartPosition and EndPosition section which give the start and end point of simulation respectively.Further a Run may optionally have multiple WayPoint sections.A WayPoint specifies that CAsCaDE should consider only those pro-gram paths which pass through the WayPoint.Additionally CAsCaDE provides three meta-commands that can be inserted at any position in the Cfile.These are:–cascadeassume takes a boolean C expression as its argument and presents it as an axiom to the abstract theorem prover.–cascade valid<ControlFile><SourceFile><Name>~/example/ex1.c</Name><FileId>1</FileId></SourceFile><Section><StartPosition><Position><FileId>1</FileId><Function>f</Function><LineNum>1</LineNum></Position><Command><CascadeFunction>cascade_assume</CascadeFunction><Argument>a>0</Argument></Command></StartPosition><EndPosition><Position><FileId>1</FileId><Function>f</Function><LineNum>9</LineNum></Position><Command><CascadeFunction>cascade_check_valid_address</CascadeFunction><Argument>p</Argument></Command></EndPosition></Section></ControlFile>3ConclusionCAsCaDE is still in initial stages of development.We have tested this on some simple examples.We believe that two stage verification is a promising approach to attack the software verification problem.Having a separate tool to serve as the second stage is advantageous over having an integrated second stage.The theoretical tools used in the two stages are very different.Where thefirst stage,in order to scale up,emphasizes coarse abstractions of data and controlflow, the second stage,in order to correctly check deeper properties needs to model data and controlflow much more exactly.With a stand alone second stage new advances will immediately benefit allfirst stage tools.We hope that we will be able to reach a wider audience and researches will be encouraged to use CAsCaDE.We believe CAsCaDE has a great potential, but to be able to fully realize it we need collaborators that are working on tools that can act asfirst stage.For more information on CAsCaDE visit:/acsys/cascade References1. C.Barrett and S.Berezin.CVC Lite:A new implementation of the cooperatingvalidity checker.In R.Alur and D.A.Peled,editors,CAV,volume3114of Lecture Notes in Computer Science,pages515–518.Springer-Verlag,July2004.Boston, Massachusetts.2. D.Beyer,T.A.Henzinger,R.Jhala,and R.Majumdar.Checking memory safetywith blast.In FASE,pages2–18,2005.3. B.Blanchet,P.Cousot,R.Cousot,J.Feret,L.Mauborgne,A.Min´e,D.Monniaux,and X.Rival.A static analyzer for large safety-critical software.In PLDI,pages 196–207,New York,NY,USA,2003.ACM Press.4.Edison design group..5.V.Ganapathy,S.Jha,D.Chandler,D.Melski,and D.Vitek.Buffer overrun de-tection using linear programming and static analysis.In Conference on Computer and Communications Security,pages245–354,2003.6.S.Hallem,B.Chelf,Y.Xie,and D.Engler.A system and language for buildingsystem-specific,static analyses.In PLDI,pages69–82,New York,NY,USA,2002.ACM Press.7. D.Heine and m.A practicalflow-sensitive and context-sensitive c and c++memory leak detector.In PLDI,pages168–181,June2003.8.G.J.Holzmann.Static source code checking for user-defined properties.In Proc.IDPT2002,Pasadena,CA,USA,2002.9.Orion:static analysis of c and c++code./cm/cs/what/orion/index.html.10.X.Rival.Understanding the origin of alarms in astr´e e.In SAS,volume3672ofLNCS,pages303–319,London(UK),Sept.2005.Springer.11.Y.Xie and A.Aiken.Saturn:A sat-based tool for bug detection.In CAV,pages139–143,2005.12.Y.Xie,A.Chou,and D.Engler.Archer:using symbolic,path-sensitive analysis todetect memory access errors.In ESEC/FSE,pages327–336,New York,NY,USA, 2003.ACM Press.。
AutoCAD 2018.1 and AutoCAD LT 2018.1 Update Preview GuideThe AutoCAD 2018.1 Update offers new software enhancements and tools to simplify your workflows and improve productivity. To help you quickly identify new features in the user interface, make sure the Highlight New Features option in the Help menu is turned on.Views and ViewportsEnhancements in the AutoCAD 2018.1 Update make working with named views and layout viewports easier than ever!Named ViewsA new Named Views panel is added to the View ribbon tab with tools to easily create, restore, and edit named views.The View dropdown list in the panel allows you to easily restore named views by selecting it from the dropdown list:The New View tool offers a simplified version of the New View/Shot Properties dialog box with only the most basic controls for creating a new view. You can expand it to access the full set of View and Shot Properties.*The View Manager button displays the View Manager dialog box. From there, you can edit and manage named views.Inserting Named Views as ViewportsNow for the cool part: inserting named views onto a layout!The Layout ribbon tab is a contextual tab that is displayed when a layout is made active. If you click on the Layout ribbon tab, you will see that it now includes a new Insert View tool. The Insert View tool displays all the named model views in the drawing as either a gallery with thumbnail preview images, or a simple list (depending on whether you have GALLERYVIEW enabled).Simply select a view from the gallery and place it onto your layout. The result is the same as the multi-step process of creating a layout viewport, making it active, selecting a view, setting the scale, resizing the viewport, and locking it. Now, you can do it in a single step—enabling you to add many views very quickly!AutoCAD applies the annotation scale of the view to the viewport scale if it will fit on the sheet. If it doesn’t fit, AutoCAD estimates and applies a standard scale based on the size of the named view and the layout in order to fit on half the sheet. You can easily change the scale during insertion by selecting the desired scale from the right-click menu.Viewport Grip EnhancementsYou can easily change the scale of or move a paper space viewport at any time by selecting it and then using the move grip or the triangular scale grip. You can also use viewport grips at the corners to modify the viewport boundary—but you’re much less likely to need them as viewport boundaries automatically resize when you change the viewport scale!Inserting a New View as a ViewportYou can quickly create new model views—even while working on a layout—by selecting the New View tool from the Insert View gallery control.This allows you to specify the view area in model space and then immediately place the view on the layout. If the drawing contains no named views, selecting the Insert View tool from the Layout ribbon tab automatically launches the New View behavior.With these enhancements to views and viewports, we think you’ll be able to reduce clicks and save time!Layer Property overridesImprovements to the Layer Manager and other Layer controls make it easier to identify overrides and to restore them to their default values.Layer PropertiesThe Layer Properties Manager includes a new status icon to indicate when an Xref layer contains overrides. Passing the cursor over the icon displays a tooltip listing all of the applied the layer overrides.A new toggle in the Layer Properties Manager makes it even easier to identify Xref layer overrides by applying a background color to any and all layers and properties with overrides—including both Xref and viewport overrides.To further aide in identifying Xref layers with overrides, a new Xref Overrides layer filter is available. Simply select the Xref Overrides filter to see a list of all the Xref layers in the drawing with applied overrides. A right-click menu option enables you to easily reset any or all of the Xref layer properties to their original values.A similar option is available when you right-click on any layer in the layer list with Xref layer overrides. You can choose to reset Xref layer properties for just the selected layers or for all layers.Additionally, a new XREF option in the -LAYER command offers command line access to remove Xref overrides, and a previously hidden option in the VPLAYER command for removing Viewport Overrides [reMoveoverrides] has been exposed.Note: The order of the columns in the Layer Properties Manager has changed for Layouts and the Global and VP properties for each Layer property are now grouped together. To simplify the Layer Properties Manager, the Plot Style and VP Plot Style columns are no longer displayed for drawings in Color Dependent mode (PSTYLEMODE-1).Layer SettingsThe Layer Settings dialog box is updated to include new controls for managing Xref layer properties. Access it from the Settings icon in the upper righthand corner of the Layer Properties Manager. The option to Retain changes to Xref layers (VISRETAIN system variable) has moved from the Options dialog box (Open and Save tab) to the Layer Settings dialog box. With the option to retain overrides to Xref layer properties enabled (VISRETAIN = 1), you can now specify which, if any, Xref layer properties you want to reload, offering you more flexibility to control Xref overrides. The various layer property options are stored in the registry via the new VISRETAINMODE system variable.Another new control in the Layer Settings dialog box, Treat Xref object properties as ByLayer, offers easy access to the XREFOVERRIDE system variable (which enables you to force object properties of Xref objects to use ByLayer properties).Additional enhancements to layer behaviorA new system variable, XREFLAYER, allows you to specify a default layer on which to place attached Xref files regardless of which layer is set as current.When you rename or delete an Xref layer in the Xref drawing, it will automatically be renamed/deleted when you reload it in the host drawings.Improved 3D navigation performanceThe navigation speed of 3D models (when viewing with the most common visual styles) continues to improve with the AutoCAD 2018.1 Update. The 3D graphics performance for the Wireframe, Realistic, and Shaded visual styles has increased significantly, depending on the content of the DWG files tested. Measuring the frames-per-second performance in six large benchmark models, the median FPS performance increase in AutoCAD 2018 Update was 175% faster (2.75x) than the FPS in AutoCAD 2017, and 37% faster (1.37x) than in AutoCAD 2018 (pre-update). For best results, use these 3D visual styles in their default states on a 64-bit machine with a compatible graphics card. The commands offering the greatest benefit from theseperformance improvements include those that are most used: 3DORBIT, ZOOM, PAN, and VSCURRENT.High resolution (4K) monitor supportSupport for high resolution monitors continues to be improved in the AutoCAD 2018.1 Update. More than 200 dialog boxes and other User Interface elements have been updated to ensure the best possible viewing experience on 4K displays and higher. Just a few examples include the Edit Layer State and Insert Table dialog boxes as well as the Visual LISP editor.Performance EnhancementsPlot and Preview offer significant performance improvements for drawings with missing SHX fonts.Standards CheckingCustom line type properties are supported when checking STANDARDS with multiple custom line type definitions in drawing.Object SelectionCrossing window and Fence selections are supported when trimming or extending lines that are not on the current UCS plane.。
Abstract封装,继承,多态封装:把⼀些数据(字段,属性) 和⾏为(⽅法) 包裹在⼀个单元---Class⾥;对外屏蔽细节(private...);对内公开⼀些属性和⽅法,具体是怎么做的不需要告诉⽤户。
访问修饰符:public 公开访问protected ⼦类访问internal 当前类库访问protected internal ⼦类且是当前类库访问private 私有访问继承:通过继承,⼦类可以拥有⽗类⼀切的属性和⽅法,任何⽗类出现的地⽅都可以⽤⼦类代替。
英⽂原话其实说的是:The Liskov Substitution Principle :(LSP, lsp) is a concept in Object Oriented Programming that states: Functions that use pointers or references to base classes must be able to use objects of derived classes without knowing it.使⽤任何⽗类指针或者引⽤的地⽅都可以⽤⼦类来替换⽽不⽤知道⼦类是什么。
还可以增加⼀些⽗类没有的属性和⽅法。
好处:代码的重⽤多态:多态是⾯向对象的重要特性,简单点说:“⼀个接⼝,多种实现”,就是同⼀种事物表现出的多种形态。
⾮虚⽅法的调⽤,由编译时决定虚⽅法的调⽤,由运⾏时决定ParentClass instance = new ChildClass();monMethod(); 普通⽅法的调⽤(⾮虚⽅法),调⽤⽗类的,由⽗类指针决定。
instance.VirtualMethod(); 虚⽅法的调⽤,调⽤⼦类的,运⾏时决定。
instance.AbstractMethod(); 抽象⽅法的调⽤,⽗类未实现,调⽤⼦类的。
1using MyAbstract.Abstract;2using System;3using System.Collections.Generic;4using System.Linq;5using System.Text;6using System.Threading.Tasks;78namespace MyAbstract9 {10///<summary>11///封装12///</summary>13public class People14 {15public int Id { get; set; }16public string Name { get; set; }17protected int Salary { get; set; }1819///<summary>20///呼吸:其实是⾝体多个部位协同⼯作的21///</summary>22public void Breath()23 {24 Console.WriteLine("Breath");25 }2627// 呼吸28//public29//protected ⼦类访问30//internal 当前类库访问31//protected internal32//private33 }34///<summary>35///学⽣36///</summary>37public class Student : People38 {39public new void Breath()40 {41 Console.WriteLine("Breath");42 }4344private int Tall { get; set; }4546public void Study()47 {48//base.Salary49 Console.WriteLine("学习.Net⾼级开发");50 }51public void PlayLumia(Lumia phone)52 {53 Console.WriteLine("This is {0} play {1}", , phone.GetType());54 phone.Call();55 phone.Photo();56 }57public void PlayiPhone(iPhone phone)58 {59 Console.WriteLine("This is {0} play {1}", , phone.GetType());60 phone.Call();61 phone.Photo();62 }6364public void PlayiPhone(Oppo phone)65 {66 Console.WriteLine("This is {0} play {1}", , phone.GetType());67 phone.Call();68 phone.Photo();69 }7071///<summary>72///⾯向基类73///</summary>74///<param name="phone"></param>75public void PlayPhone(AbstractPhone phone)76 {77 Console.WriteLine("This is {0} play {1}", , phone.GetType());78 phone.Call();79 phone.Photo();80 }8182public void PlayPhone<T>(T t) where T : AbstractPhone//基类83 {84 Console.WriteLine("This is {0} play {1}", , t.GetType());85 t.Call();86 t.Photo();87 }8889 }9091///<summary>92///⽼师93///</summary>94public class Teacher : People95 {96private int Tall { get; set; }9798public void Teach()99 {100 Console.WriteLine("教授.Net⾼级开发");101 }102103public void PlayiPhone(iPhone phone)104 {105 Console.WriteLine("This is {0} play {1}", , phone.GetType());106 phone.Call();107 phone.Photo();108 }109 }110 }View Code-----------------------------------------------------⽅法类型:void,int...普通⽅法----⼤家都是⼀样的virtual 虚⽅法(可以⽤override重写)---⼤家都有,但个别⼦类不⼀样,需要重写。
TRIOS Software OverviewTRIOS is TA Instruments’ state-of-the-art software package that uses cutting-edge technology for instrument control, data collection, and data analysis for thermal analysis and rheology instruments. The intuitive user interface allows you to simply and effectively program experiments and move easily between processing experiments and viewing and analyzing data. TRIOS software delivers a whole new experiment experience.•Easy organization and data fi le management •A unique fi le-naming system allows for effortless organization of data fi les •The History View and File Manager offer simple data fi le location •Compatibility with the latest Windows Operating System platforms •M aximum fl exibility •Instrument control and data analysis via any networked computer •Confi gurable for multiple monitors •Ability to control multiple instruments at once •Remote data analysis•Seamless integration between instrument control and data analysis•Easy data export in a variety of output formats, including XML, Word, Excel, and PDF •Simple graph formatting using The Ribbon •Customization of the displayThe TRIOS software is supported by a full range of services, including onsite training, customer service that is only a phone call away, and easy-to-use, easy-to-understand online help. All of these items refl ect TA Instruments’ commitment to providing thermal analysis and rheology products and related services that deliver maximum value for your investment.TA InstrumentsWhat’s New in TRIOS SoftwareWhat’s New in TRIOS Software V3.1TRIOS software is now better than ever with increased stabilization and key fi xes and enhancements, including User Interface changes that will make your TRIOS experience exceptional. The next generation of instrument control and data collection and analysis, TRIOS V3.1 is more effi cient and intuitive, allowing you to work faster and easier.General TRIOS EnhancementsLimited-Bandwidth Download OptionYou can now download TRIOS faster than ever by installing a version of TRIOS that does not include TRIOS Online Help.Ribbon ChangesThe Ribbon has been simplifi ed with the Home and View tabs consolidated into a single Experiment tab, removing redundancy and unused functionality.Previous Home tab:The File Manager button no longer exists. The ability to close the File Manager was removed, and overlay and analysis document creation is now only available from the File M anager right-click menu. New analysis is available from the Analysis tab. The Geometry information is now available from the Experiment tab. When a geometry is attached to the instrument, you can select the installed geometry from the list of geometry fi les previously created on the system. If your geometry does not appear in the list, clicking Add New Geometry will launch the New Geometry wizard. Editing a geometry can now only be done from the File Manager’s Geometries pane or on the geometry Experiment node.Previous View tab:Document Views functionality (creating a new spreadsheet and graph) as well as Layout functionality (saving and loading fi les) is now located solely in the File Manager. Switch Documents and Views functionality was removed. Access to the Properties panel now only exists from the right-click menu.New Legend User InterfaceUse the Legend menu to make your Legend customizations in one place. With one click of the mouse, you can select the desired Entry Type, choose what items you want to appear in the legend, modify text color and title justifi cation, and turn on/off the Legend title.Additionally, when editing the Legend directly from the graph, use the Quick Format option for editing text that automatically displays when you select an item in the Legend. From the Quick Format box, you canchange the font face, size, and style.Previous Home tabPrevious View tabNew Legend User InterfaceQuick Format optionQuick Format optionNew Curves User InterfaceFormatting curves on a graph is now easier and more intuitive with the introduction of the Curves Format dialog box.•Choose to format your curves Automatically or Manually. Use the Automatic Formatting option to apply your customizations based on the fi le, step, and/or variable, or use the Manual Formatting option to apply your customizations per curve. •Use the palette to specify the order of the colors, symbols, line styles, and extra symbols used on your curves. •Additional formatting options include setting the line thickness, symbol size, and symbol density, and adding extra symbols to the curve •Set the style selection with the use of Quick Styles so that you can easily and quickly apply previously defi ned formatting to your curvesRHEOLOGYARES-G2 EnhancementsOrthogonal Superposition (OSP) FeatureThe Orthogonal Superposition (OSP) feature was added for the ARES-G2. In the OSP mode, the normal force transducer operates as an actuator applying a small sinusoidal linear deformation to the sample while recording the force at the same time. Instead of holding the transducer shaft at a fi xed position, the shaft can now be periodically oscillated in the vertical direction at small amplitudes.The major applications of the OSP mode include: •The superposition of a small strain oscillatory deformation normal to the direction of steady shear fl ow (Orthogonal Superposition) •Oscillation testing in the two orthogonal directions at the same frequency (2D-SAOS)A new group of test modes has been created for Orthogonal oscillation. These test modes are only available for the Orthogonal double wall concentric cylinder, Parallel plate, and Orthogonal torsion fi xture. This feature requires an ARES-G2 with Serial Number 4010-0383 or higher or an earlier version that has been upgraded together with appropriate geometries.DMA ModeThe ARES-G2 DM A feature is designed to allow geometries such as tension/compression and bending to be used with the instrument. DM A testing uses the standard oscillation test modes; when one of these geometries (Three point bending, Mixed bending, Clamped bending, or Linear tension) is selected, the mode of deformation is changed from shear to linear, with the appropriate set of variables. This feature is limited to oscillation tests only since that is the only motor mode available.This feature requires an ARES-G2 with Serial Number 4010-0383 or higher or an earlier version that has been upgraded together withappropriate geometries.Curves User InterfaceOrthogonal Superposition (OSP) FeatureProportional Axial Force ControlAxial force control on an ARES-G2 now has the ability to adjust the commanded force level to follow changes in sample stiffness. Typically this is used to decrease the axial force on a sample as it softens to avoid issues with samples being squashed or stretched too much as they soften. This is done by taking a reference value for the sample stiffness at the start of the test, and using the ratio of the reference stiffness and the current sample stiffness to adjust the commanded axial force.This option is enabled by selecting Compensate for stiffness changes. The compensation scaling factor is a value between 0.0 and 1.0 which controls the relationship between the changes in stiffness and the axial force changes. A value of 0.0 results in a constant force, and a value of 1.0 result in the axial force being a linear function of the stiffness ratio.Motor Control PanelThe ARES-G2 motor control panel and Real time variable signal list were updated to allow for better control of sample displacement and strain by using relative rather than absolute positioning.There are now separate signals for motor position (angular offset relative to encoder home position), and displacement (a running change in displacement since a tare in the DSP). The reported strain signal is now based on the geometry strain constant and the measured displacement.Button changes:•Zerodisplacement: Used to zero the displacement signal •Go to home position: Goes to the encoder zero position•Move to orientation angle: M oves to the geometry alignment angle. Enabled only if the active geometry has an alignment angle (i.e. ARES-G2 DMA fi xture)NOTE: The Move to orientation angle has been added to allow thecorrect positioning of the bending and the tension fi xtures for DM A testing after installing the geometry. The orientation angle is calibrated for every geometry and stored with the geometry parameters.ARES-G2 Phase CalibrationThe phase angle calibration code has been updated to use a hermite spline rather than a polynomial fi t to the phase error. This new phase angle correction provides a better fi t at lower frequencies than the polynomial fi t.When the analysis code is invoked, it checks the instrument fi rmware to see if the hermite spline correction is supported. If supported, it uses the new analysis. If this correction is not supported, it reverts back to the older polynomial implementation.The new form shows the user-adjustable number of terms used in the spline, as well as the correction coeffi cients between the measured data and the corrected data for both the phase and amplitude corrections. It also shows the agreement between the calibration data and the spline coeffi cients that are currently loaded in the instrument. An overlay can be created to show this graphically, if desired, by looking at the “Source data” and “Interpolated data” zones.Motor Control PanelARES-G2 Phase Calibration Compensate for stiffness changesARES-G2 Procedure ChangeIn order to repeat the same step in a procedure, the step has to be entered multiple times. With the new repeat function, a single step can be repeated multiple times. In addition some key test parameters can be changed during the repeat runs; for example the temperature can be incremented by a certain value at each repeat run.ARES-G2 Motor BoostTRIOS V3.1 now supports a second power amplifi er to double the motor power output. T his feature allows applying larger strains on high viscosity materials such as rubber compounds. No user interface changes are associated with this feature. TRIOS automatically recognizes when a second power amplifi er is connected and confi gures itself.Electro Rheology Conditioning BlockThe electro rheology conditioning block was updated to allow for voltage ramps and disconnection of the power amplifi er for a better “zero voltage” point.Three different types of voltage ramps are available: •A simple ramp from an initial voltage from a fi nal voltage •A ramp and hold profi le where the voltage is ramped from an initial value to a fi nal value, and the fi nal value is maintained for specifi ed period of time •A double ramp where the voltage is ramped from an initial value to a fi nal value, then back to the initial value The zero voltage mode sets what happens when a zero voltage level is commanded: Command zero volts uses the function generator to commanded a zero volt level into the power amplifi er, Disable amplifi er uses the ARES-G2 enable relay to open the HV circuit.ARES-G2 and RSA-G2 Enhancements Geometry CalibrationsARES-G2/RSA-G2 geometry calibrations were updated to match the method used by DHR/AR rheometers. Previously, geometry-specifi c calibrations where performed by using the Calibration pane in the TRIOS File M anager, and then applying the resulting calibration parameters to the active geometry. The update includes a Calibrations tab that was added to the geometry document, which shows the current calibration value and the date the calibration was performed, as well as hosts a control panel that can be used to run the geometry calibration in place.The Calibration panels displayed depend on the specifi cs of thegeometry.ARES-G2 Procedure ChangeGeometry CalibrationsARES-G2 Procedure ChangeARES-G2 and DHR EnhancementsTribo-Rheometry Accessory for ARES-G2 and DHRThe Tribo-rheometry option for the ARES-G2 and DHR is now available. Tribology test procedures are used to measure the friction coeffi cient, CoF, as a function of the sliding speed under dry and lubricated conditions between any two substrates in contact. Applications range from biological, personal products like creams and lotions, to automotive components and lubrication in machinery design.Tribology tests can only be used with the special Tribo-rheometry geometries. The tribo-rheometry geometry is supported in the following test modes:•Flow Sweep, which is converted to a “Tribology Sweep” when executed.•Transient fl ow steps (Step Rate, Flow Rate, Flow Temperature ramp), which are converted to Tribology Steps when executing.Procedure templates for common Tribology tests can be loaded from the template folder.The modular Tribo-Rheometry Accessory can be confi gured with 4 different geometries (Ring on Plate, Ball on Three Plates, Three Balls on Plate, and Ball on Three Balls), offering a range of contact profi les that are compatible with ARES-G2 FCO and APS or the DHR ETC and Stepped Disposable Peltier Plate.DHR/AR Enhancements•Support for DHR Optics Plate Accessory, Building M aterial Cell, and Bayonet Peltier Plate•DHR Pressure Cell•Support for vane and starch rotor added•Calibration page correctly refl ects mapping status•Resetting of geometry gap fi xed•M ap only applied during test to avoid over speed error when magnetic coupling not engaged•DHR Gap Compensation Calibration: Now allows calibrations to be performed from high to low temperatures•DHR zero gap: Deceleration added to existing standard and axial force modes•DHR Flow Sweep: Scaled time average option fi xed•Concentric cylinder•The end effect fi eld can be changed in a results fi le which will force a recalculation of the data•Rheology Advantage fi les now load with the end effect set to 1•Rheology Advantage fi les measured with ver.1 Double Gap load with the correct immersed heightRheology Analysis•Spriggs and Oldroyd models for oscillation data that were previously available in Rheology Advantage are now available in TRIOSV3.1•Carreau-Yasuda model for fl ow data added•Arrhenius model improved with better starting conditionsTemplate folderNew geometryRheology AnalysisProcedure templateTHERMAL ANALYSISDiscovery TGA EnhancementsModulated TGA (MTGA) SupportM odulated TGA (M TGA) is now supported by TRIOS software V3.1. This option, used with the Discovery TGA, is used to study the same decomposition or volatilization transitions as conventional TGA, plus provides new information that permits unique insights into the behavior of the weight loss reaction — specifi cally, obtaining kinetic information about one or more weight losses, in a shorter period of time than the multiple heating rate approach. M TGA also provides continuous measured values for activation energy throughout the weight loss reaction, not just at specifi c reaction levels.M odulated TGA experiments can be run as either Standard or High Resolution procedures.Discovery DSC Enhancements•To ensure the safety of the user, the Gas 1 selection for the Discovery DSC can now be used for Nitrogen only.INSTALLING TRIOS SOFTW AREFor instructions on installing TRIOS software, refer to the Installing TRIOS Software instructions.ADDITIONAL RESOURCESA number of additional resources are available to you. For assistance with the TRIOS software, fi rst consult the Online Help.For immediate assistance contact the TA Instruments Hotline at +1 302-427-4000 from 8:00 am to 4:30 pm EST.For email support, please send your question to one of the following:t*********************************************************************************************************PREVIOUS WHAT’S NEW DOCUMENTSFor Previous What’s New in TRIOS Software documents, click here.TA INSTRUMENTS OFFICESFor information on our latest products, contact information, and more, see our web site at:TA Instruments — Waters LLCCorporate Headquarters159 Lukens DriveNew Castle, DE 19720USATelephone: 302-427-4000Fax: 302-427-4001Email: **********************。
Views:Customizable Abstractions for Context-AwareApplications in MANETsKurt Schelfthout Distrinet-K.U.LeuvenCelestijnenlaan200A 3001Leuven,Belgium kurts@cs.kuleuven.beTom HolvoetDistrinet-K.U.LeuvenCelestijnenlaan200A3001Leuven,Belgiumtom@cs.kuleuven.beY olande BerbersDistrinet-K.U.LeuvenCelestijnenlaan200A3001Leuven,Belgiumyolande@cs.kuleuven.beABSTRACTProgramming applications for highly dynamic environments such as mobile ad hoc networks(MANETs)is complex,since the work-ing context of applications changes continuously.This paper presents “views”as abstractions for representing and maintaining context information,tailored to applications in MANETs.An application agent can define a view by declaratively describing the context in-formation it is interested in.A supporting middleware platform, called ObjectPlaces,ensures that the information represented by a view continuously reflects the agent’s context information,de-spite the dynamic situation in a MANET.We elaborate on the dis-tributed protocol that ObjectPlaces uses to maintain the information of views,and give a thorough evaluation.1.INTRODUCTIONGiven the increasing pervasiveness of networks due to the ad-vent of wireless communication,the next generation of distributed systems presumes little network infrastructure,and is comprised of computing devices(nodes)that can be carried around,or are placed on moving vehicles.Mobile computing nodes connected in such an ad hoc way form a mobile ad hoc network(MANET).An application developed for MANETs necessarily consists of distributed agents that need to communicate among each other to achieve a common goal.Given the dynamics of a MANET,this communication between application agents is complex:the nodes on which these agents live are mobile,and can disappear from a conversation at any time.Dealing with this complexity at the ap-plication level is hard,so an application developer benefits greatly from a coordination middleware that offers high level mechanisms to manage communication among agents.ObjectPlaces is a coordination middleware that supports afirst order abstraction of an agent’s context.For our purposes,an agent’s context is the aggregate of all available information on currently reachable nodes in the MANET.An agent’s context thus changes because(1)information on a reachable node is changed,or(2) the set of reachable nodes changes.In ObjectPlaces,an agent can gather context by defining a view.A view is built by the middleware Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on thefirst page.To copy otherwise,to republish,to post on servers or to redistribute to lists,requires prior specific permission and/or a fee.SELMAS’05at ICSE’05May15-16,2005,St.Louis,Missouri,USA. Copyright2005ACM1-59593-116-3/00/0004...$5.00.based on a declarative specification that describes“how far”over the network the view reaches,and in what information the viewing agent is interested in.The most important property of a view is that it is an actively maintained structure,that changes as the agent’s context changes. The agent can listen for new context events,e.g.the arrival of a new node carrying interesting information.A motivating example for such an active notion of context occurred in a real world ap-plication,wherein we are currently applying the ObjectPlaces mid-dleware.In this application,automatic guided vehicles(AGVs)in a warehouse coordinate to transport goods.AGVs communicate to avoid collisions(among other things);an AGV thus needs to be notified actively when another vehicle enters in a possible col-lision range.Other examples are rescue workers that want to be notified of incoming and leaving ambulances,battlefield scenarios where soldiers want to be notified of incoming transports,etc.If the middleware does not support an active context representation,the application programmer is forced to program such a representation using polling.In the following section,we describe the ObjectPlaces middle-ware in more detail,as well its relation to existing coordination middleware.In Sect.3we describe a protocol to maintain a view in a MANET.Then,the ObjectPlaces middleware and specifically the notion of a view is evaluated analytically and empirically in Sect.4.Finally,we conclude.2.VIEWS ON OBJECTPLACESIn ObjectPlaces,each agent can maintain”viewable data”in a local collection of objects called an objectplace1.The objects in an objectplace represent information that is of interest to other agents, and so contribute to the overall context information available.Other agents can gather copies of objects from objectplaces on nodes in their neighborhood using a view.In other words,context informa-tion is made available by putting it in a local objectplace,and can be gathered by building a view.Agents can coordinate by influencing each other’s context,much like what happens in everyday traffic: when a car driver is going to take a right turn,he or she turns on the turning indicator.Other drivers can see this”context change”,and react appropriately.First we describe how an agent can manipulate its local object-place,then views are described in more detail.The section is con-cluded with a discussion of ObjectPlaces in relation to existing work.1”ObjectPlaces”-the middleware-is written in plural and with two capitals,”objectplace”-the software entity-is written without capitals.2.1Manipulating an objectplaceAn objectplace by itself is basically a tuplespace variant:an ob-jectplace is a set of objects that can be manipulated by operations such as put,read and take.Contrary to existing tuplespace ap-proaches however,an objectplace has a fundamentally asynchronous interface:operations return control to the client immediately(an agent that uses the middleware is called a client of the middleware), and results are returned as they are available via a callback.This is important in order to allow views to be built efficiently and conve-niently,see Sect.2.3.For clarity,we have made two simplifications.First,although an objectplace can be manipulated remotely,for this paper the reader can assume that an objectplace is only locally accessible.Views, discussed in the next section,provide a way for clients to observe the contents of remote objectplaces.Second,although a client can create objectplaces at will,we assume that the middleware offers exactly one objectplace on each node.Similar to tuplespaces,in order to read or take objects from an objectplace,clients indicate what objects they want to read by means of a template.A template is a function from the set of objects to a boolean value.Every object for which the template function returns true matches with the template.The operations on an objectplace are the following:put(Set,Callback)puts the given set of objects in the objectplace.Returns true to the callback if all objects were successfullyadded.take(ObjectTmplt,Callback)removes the objects matching with the template from the objectplace and returns them to thecallback.watch(ObjectTmplt,EventTmplt,Lease,Callback)observes the content of the objectplace.Returns copies of objects match-ing the object template to the callback(the objectplace is notchanged).The event template is used to indicate in whatevents on the matching object the client is interested in.Eventtemplate and lease are described in detail shortly.A watch operation’s event template can match with three pos-sible events:isPresent,isPut or isTaken.If the event tem-plate matches with isPresent,the objectplace returns copies of all matching objects it currently contains to the callback,and re-turns the empty set if there are no matches(this is important for so-called test-for-absence operations,where the client needs to know there are no matching objects).If isPresent is the only event with which the event template matches,the watch operation isfin-ished.However,when the event template also matches with isPut or isTaken,the objectplace must return copies of matching ob-jects that are either put in or taken from the objectplace.In order to do so,the operation is registered by the objectplace,and when an appropriate event occurs on an object matched by the object tem-plate,the client is notified.An event template that matches with isPresent and isPut for example,first returns copies of ob-jects currently contained in the objectplace.When new matching objects are put in the objectplace,copies of these are returned in a subsequent call to the callback.Objects returned to the callback are also annotated with the event that occurred on the object,so the client can distinguish between events.To unregister watch operations that are waiting for an event,a watch can be provided with a Lease object.A client calls the discard operation on the Lease to unregister the corresponding watch operation.The same lease can be given as an argument to more than one watch;in that case,upon discard all these opera-tions are unregistered atomically.2.2ViewsA view is a local collection of objects,reflecting the contents of multiple objectplaces on reachable nodes in the network based on a declarative specification.This collection is continuously updated by the middleware,both with respect to changing contents of the objectplaces in the view,as with respect to changes in the network topology.A view thus represents the context of the viewing agent. To build a view,a client specifies:A distance metric and a bound determines“how far”over the net-work the client’s view will reach.An example is a hop count-metric with a bound of three:the view will span objectplacesreachable in a maximum of three hops from the node wherethe view is issued.An object template constrains what objects will be included in the view.Given these parameters,the ObjectPlaces middleware searches the network for nodes satisfying the constraints(using the protocol described in Sect.3).On these nodes’objectplaces,a watch op-eration with the given object template is executed.The watch’s event template matches with all possible events.The results of all these watch operations,which are events indicating the presence, arrival or removal of objects in an objectplace,are sent to the node issuing the view.This allows the viewing node to keep the view up to date with respect to changes in the content of the participating objectplaces.Changes in the network are handled by managing the watch registrations on the nodes in the view.When it is detected that a node moves out of the view,the view’s watch on the object-place of that node is unregistered,and the viewing node is notified; when a node moves into the view,a watch on its objectplace is reg-istered and consequently the viewing node is notified as well.How this detection is done is discussed in Sect. 3.A view is actively maintained in this way until it is released by the client.Any client on any node can build a view,and clients can specify as many views as they want.Each client can have its own set of views to observe the context that it is interested in.A client can not only specify constraints on the content of the view based on its interests,the content can also be represented in a client specific way(e.g.as a sorted collection).In its raw form, a view is built out of the events generated by the watch operations on the participating nodes,as well as events generated by the mid-dleware when a node leaves or joins the ers of the middle-ware can program their own representation using these raw events. For example,we have provided an implementation of a view as a collection,supporting a collection interface common in object-oriented API’s(i.e.java.util.Collection in Java).This allows sorting and iterating over the collection for example.The collection is updated as watch events are generated,e.g.when an isPut is received,the corresponding objects are added to the ually,a view is described as such a collection in this paper,since it is the most common usage pattern.Other represen-tations of a view can be an accumulation to a single value,e.g. the average of an attribute of the objects in the view,or translating objects in the view to objects the agent understands,to deal with heterogeneous agents.Both the contents and the representation of a view can thus be customized.As an example,suppose a car arriving at an intersection wants to know the positions of other cars,since the car has to give way from the right.It builds a view on all cars within50meters(distance metric and bound),containing position and car id objects(object template).The car chooses a sorted list as representation,closest carfirst.A traffic monitor nearby also builds a view on nearbycars,and car id objects,but accumulates the car id’s in a counter for traffic information purposes.In both cases,the content of the view is partly the same(car id’s),but the representation is different (a sorted list,vs.a count of the unique id’s).In conclusion,a view is a powerful abstraction that can be put to good use for coordination,since it is an active representation of a agent’s context.A view takes the heterogeneous nature of a MANET into account,because both the contents and the represen-tation of a view can be tailored to each client’s wishes.2.3Discussion and Related WorkThe ObjectPlaces middleware can be seen as a hybrid between two well known approaches for coordination:publish/subscribe systems and tuplespaces.In a publish/subscribe(P/S)system(e.g.[3,14]),publishers send notifications of state changes to a list of subscribers.Sub-scribers are not known in advance but let the P/S middleware know of their interest in certain events through the use of subscriptions. The P/S middleware handles the delivery of notifications to the right subscribers.ObjectPlaces can be seen as a P/S variant:a view is a subscrip-tion to events on objectplaces in the vicinity of a client.Clients ”publish events”by manipulating objects in their local objectplace, which triggers watch operations of views that are observing that ob-jectplace.The resulting events are then delivered to viewing clients. ObjectPlaces solves a problem when applying P/S middleware in MANETS:in[4]it is described that,due to the appearance and reappearance of nodes in a MANET,there is a phase immediately after reconnection in which a mobile subscriber needs to wait until events are published so that the subscriber can assess the current state of publishers.For example in STEAM[9],a P/S middleware for MANETs,publishers are burdened with sending events period-ically to account for possible newly arrived subscribers.Generally, this problem is handled by buffering previous events on reliable andfixed infrastructure,e.g.[5][15].Such afixed infrastructure is however not available in MANETs.In ObjectPlaces this problem is handled naturally.Objects are put in a local objectplace;newly arrived clients can be brought up to date immediately by querying neighboring objectplaces using a view.At the same time,the view subscribes to events on the objectplace,and so keeps the viewing client up to date in the future as well.The objectplaces thus act as a buffer in which clients can store observable state. Tuplespaces(TS)systems,with Linda[2]as afirst incarnation, provide a shared collection of data,called tuples,and a set of op-erations(read,write,take)on the collection to manipulate the data. Throughout the years,Linda has spawned many variants,e.g.[1] [16].Directly applying tuplespace systems in MANETs is difficult since clients need to know the location of a tuplespace to interact in beforehand,or a shared tuplespace must be discovered and agreed upon at runtime.Since there is no reliable infrastructure available in a MANET,solving this problem is not trivial.In ObjectPlaces, the solution is to let agents manipulate a local objectplace,com-bined with the use of a view to gather the contents of objectplaces on reachable nodes.From this viewpoint,a view is the necessary ”discovery mechanism”that detects reachable objectplaces accord-ing to client-specific constraints.As another point,objectplace operations are specifically designed to support views efficiently.Existing tuplespace approaches lack the event-based,asynchronous interface an objectplace provides. An event-based interface is necessary since a view requires active maintenance,so the viewing agent needs to be notified whenever an objectplace in its view changes.Since a tuplespace provides mostly synchronous operations(e.g.rd,rdp),a tuplespace would have to be polled regularly to keep the view up to date,which is an inefficient solution.With a watch operation,the client can query both the current contents(isPresent)and subscribe to events on the objectplace(isPut and isTaken).This ensures that the ob-jectplace notifies the client when appropriate,thus eliminating the need for polling.Although existing models do support event-like operations(e.g. JavaSpaces’notify[16]or LIME’s reactions[10]),these are not sufficient.For example,JavaSpaces notify can”only”send notifi-cations of incoming tuples,while a view also needs to react to ob-jects that are removed from an objectplace in order to be up to date. Another issue is that an objectplace supports both querying the cur-rent contents and subscribing to events atomically:otherwise,a view may miss some objects.JavaSpaces can support this by pro-viding a transaction mechanism,but we feel this is too heavyweight for application in a MANET.Also in programmable or extensible tuplespaces like TuCSoN[11]and MARS[1],extending the in-terface with asynchronous operation is possible,but these mecha-nisms are too heavyweight for application in MANETs.The ob-jectplace’s watch operation solves the problem by allowing clients to specify an appropriate event template.Finally,we discuss the relation of ObjectPlaces to a number of coordination middleware approaches specifically for MANETs. LIME[10]is a middleware for mobile agents and mobile nodes that attaches a personal tuplespace to each agent in the applica-tion,and shares these tuplespaces transparently when two agents are on the same or connected node.The LIME middleware was extended recently in EgoSpaces[12].In EgoSpaces,clients can build a view over the locally available network,similarly based on a distance metric.EgoSpaces’view is always represented as a tu-plespace(supporting primitives like in,inp,...).In ObjectPlaces, the representation of the view can be tailored to the client’s wishes (e.g.a sorted collection),thus supporting heterogeneous agents bet-ter.Furthermore,while it is possible to register reactions on a view in EgoSpaces,these can react”only”to incoming tuples[7].It is unclear how an agent can be notified of a tuple leaving it’s view (except by polling),a necessary precondition for building an up to date client-side representation such as in ObjectPlaces.TOTA[8](Tuples On The Air)is a middleware that provides ap-plications with the notion of a self-maintaining distributed tuple. Each node in the network hosts a tuplespace.A distributed tuple is propagated to nearby nodes,and can be changed with each propa-gation according to an application-specific rule(e.g.counting the number of hops from the root).This tuple is then maintained by the middleware as the network changes.An important difference with ObjectPlaces is that a view is specific for every client,while a dis-tributed tuple is the same for all observers.In other words,while in TOTA the”sender”of a message(the agent that adds a distributed tuple)determines both who it reaches and what the content is,in ObjectPlaces the”receivers”of a message(the clients that build a view)can determine both content and representation.3.VIEW PROTOCOLThe construction of a view in a MANET requires a distributed protocol that is able tofind and maintain a set of reachable nodes in the network given a bound on a distance metric.This means that the protocol should be able to:(1)notify the viewing node when a node enters or leaves the view(2)register and deregister watch operations on nodes entering and leaving the view respec-tively;(3)route the events generated by the watch operations to the node where the view was defined.Existing ad hoc routing pro-tocols(for an overview,we refer to[13])are not adequate becausethey can only provide afixed”distance metric”(usually hop count). Since the distance metric used for building the view is application specific and determined at runtime,we need a protocol that doesfit our requirements.This protocol can be viewed as an alternative to the one proposed in[12].We assume from the underlying network layer that:(1)a single-hop broadcast is available that broadcasts a message to all nodes within communication reach,represented by the function broadcast (message);(2)a reliable single-hop unicast that sends a messageto a designated node within communication reach,represented by the function unicast(message,id receiver).We can reasonably expect these functions to be built based on data link standards such as IEEE802.11[6].Algorithm1The view protocol.on timeout t br1:removeOutdated(participants,f p.t br)2:broadcast(dist msg(id view,0,id root))on receive content message c3:updateT ime(participants,timestamp(c),c.id sender)4:updateV iew(participants,c.events)5:Process Participant:on timeout t br6:removeOutdated(neighbors,f n.t br)7:id parent=findP arent(neighbors)8:d current=calculateDistance(neighbors,id parent)9:if d current≤bound then10:broadcast(dist msg(id view,d current,id participant))11:events=objplace.watch(object template,allEvents,cb) 12:unicast(cont msg(id view,events,id participant),id parent) 13:else14:alive=false15:stop timeron receive distance message d16:updateT ime(neighbors,timestamp(d),d.id sender)17:updateDistance(neighbors,d.distance,d.id sender)18:alive=true19:start timeron receive content message c20:if alive then21:unicast(c,id parent)The data structures necessary for the protocol are depicted in Ta-ble1,while the protocol is depicted as Algorithm1.The protocol builds and maintains a shortest path spanning tree,starting on the node with the client issuing the view,called the root.This tree de-termines which nodes are included in the view-these are called the participants in the view.In the text and in algorithm1the protocolis described as if there is only one view-this is only for exposi-tory purposes.In reality this protocol is executed for every viewin which a node participates.That is why with each message a unique view id,id view is transmitted.The data structures in table1are also for one single view,and are duplicated for every view in which a node participates.The length of a path is determined by the distance metric,whichis a parameter of the protocol.This allows building a shortest path based on hop count,but also on any other distance metric such as physical distance,or bandwidth.The only constraint on the dis-tance metric is that it increases monotonically the further it gets propagated from the root,to ensure that the distance does not grow out of bounds as it gets propagated in a loop.Such a metric can always be chosen,by including a hop count with any other metric the client chooses(e.g.physical distance)[12].The view building process starts when a client issues a view.The node on which this client is located is responsible for building and maintaining it,and is the root for that view.The rootfirst builds a unique id for the view,consisting of its own id and a sequence number that is unique on each node.Two activities now occur in parallel:the building and maintaining of the shortest path spanning tree,and the building and maintaining of the contents of the view. The contents of the view is maintained at the root and consists of a list of participants and the objects their objectplaces currently con-tain.The spanning tree.To build and maintain the spanning tree, the root and all participants regularly broadcast distance messages. This allows participants to determine what their distance is from the root(d current),given the view’s distance metric.The root starts the tree-building process by broadcasting a distance message with the id of the new view,its own id and a distance of zero(line2). Nodes that receive a distance message check whether they are par-ticipants in the view.To this end,each participant maintains a list of its neighbors-nodes from which it has recently received a dis-tance message.Upon receipt of a distance message,the participant records the time the distance message was received from that neigh-bor(function updateT ime,l.16),and the distance that neighbor broadcasted(function updateDistance,l.17).The participant sets the alive variable to indicate it should check whether it is in a view, and starts a timer(if the participant already was in the view,these have no effect).After every broadcast period,given by t br,a participant recalcu-lates its distance from the root based on its list of neighbors.First, neighbors for which the timestamp of the distance message that was last received is older than a given timeout,are removed(us-ing removeOutdated,l.6).This timeout is given as a neighbor freshness factor f n that is multiplied with t br to determine the ac-tual timeout.The participant then determines the neighbor that is closest to the root using findP arent(l.7).Based on its parent’s distance,it calculates its own distance from the root d current us-ing the distance metric(l.8).If it is within the bound,it broadcasts a distance message itself(l.10),and repeats the process every t br time to account for changes in the tree.Otherwise,it goes to sleep, waiting for new distance messages to come in that might change the situation(l.14-15).The end result of this protocol is that each node regularly checks whether or not is in the view,and knows a parent in the tree which is the closest to the root of all its neighbors. The contents of the view.Each node that is in the view,deter-mines the objects it contributes to the view by executing a watch operation on its local objectplace.The resulting events of this watch are transported to the root using content messages.The events variable is the set of buffered events at the participant that have not been sent to the root yet(we are stretching notation in line 11,since these events are actually sent to callback cb).A node that receives such a content message from one of its children forwards it to its parent,so that it reaches the root(l.21).The root main-tains a list of participants of the view.For each content message it receives,it updates the objects that participant contributes to the view(using updateV iew,l.4).It also records the reception times-tamp of each content message(l.3),and removes those participants it hasn’t heard from for f p.t br time,where f p is the freshness of the participants(l.1).This means that participants must periodi-cally send a content message to the root,even when there are no events to be returned(events={})to ensure that the root does not consider them out of the view(l.12).This protocol tolerates mobility of any node and disappearanceRoot Participant Distance msg Content msg id view id view id view id view participants=neighbors=id sender id sender {(id participant,timestamp,{object})}{(id neighbor,timestamp,distance)}distance{event} distance metric,bound id parent,d currentobject template distance metric,boundobject templateTable1:Contents of data structures and communication messages.of participants.New nodes are discovered by the periodic broad-casting of the distance messages.Nodes that should be removed from view are detected because they discover for themselves that they don’t have any more neighbors,or their distance has gone out of bounds.Changes in the spanning tree are similarly detected through exchange of distance messages.Using the spanning tree to deliver events.When sending con-tent messages,the spanning tree is actually used as a multi-hop routing tree to the root.Although the shortest path from partici-pant to root may not always be known,at least some path exists (possibly temporarily containing cycles)and events are delivered as long as every node on the path forwards the content message to its parent.However,in the case where a node that received an event goes down before forwarding the event,the event is lost.To compensate for this loss,one can choose to use a reliable link protocol from node to root,such as the alternating1-bit protocol.Each event re-ceived by the root would then have to be acknowledged before the node can send another event.Although this makes the protocol re-liable,it also induces additional overhead.One possible solution is to use unreliable best-effort event delivery,which may be tolerable for some applications where the view may be slightly incorrect or out of date.Regularly,the view may be“flushed”and current state from all nodes is sent again.Propagation of other parameters.The parameters of the view, such as the distance metric,also need to be sent from the root to the participants.This was not discussed,but is done in a straight-forward way:whenever a node receives a distance message with an id view it does not know,it requests the relevant view parame-ters from the sender of the distance message.When the node deter-mines it is not in the view,it may delete this information-or decide to keep it for a while longer because it might become a participant in the view later.We do not elaborate further.4.EV ALUATIONThe following parameters influence the correctness and the per-formance of the view:(1)the broadcast period t br,(2)the freshness for neighbors f n,and(3)the freshness for participants f p.Instead of letting the application designer choose these experimentally,we mathematically derive bounds on these parameters,supporting the designer in making the right trade-offs.The view protocol is influenced by uncontrollable factors con-cerning the dynamics of MANETs.In order to keep the presenta-tion clear,we focus on the dynamics of the network only-in other words we assume for the rest of this section that the contents of the objectplaces stays the same.We focus on this problem because this is where any problems and bad assumptions will be revealed. Specifically,we take into account the number of nodes on a given area and the speed of these nodes.The speed influences how busy the protocol will be updating changes,and the concentration deter-mines connectivity,or the number of nodes in the view.We study how accurately the protocol can represent the perfect view,which is obtained by“stopping time”and comparing the view the protocol built at that time with how the view should look,given the current position and connectivity of the nodes.There are two kinds of errors:false exclusions,objects that are not in the view but should be;and false inclusions,objects that should not be in the view but are.4.1False exclusionsAfirst way how false exclusions occur is when a node enters the view,while the view didn’t notice the new arrival yet.The critical parameter to minimize this kind of false exclusion is the broadcast period.When this period is short enough,a new node entering the view receives a distance message from a neighbor early,and the view updates fast.Suppose nodes have communication range r, and relative speed v r,and we want to detect a node when it has traveled at most distance l into communication range of any par-ticipant.The worst case scenario occurs when an undetected node moves straight at another in the view.In this case,the maximum broadcast period to ensure that a node is detected is:t br≤r−lv r, with no transmission delay and no message loss.Supposing a message can get lost with probability p loss,then the minimum broadcast period to ensure that a node is detected at a distance l with minimum probability p detect is:t br≤r−ln.v r,with n the number of resends until a probability of receiving a message p detect is reached.From the inequality p detect≥1−p n loss,it follows that n≥log(1−p detect)loss.To incorporate message delays,these bounds should be tighter: one should subtract the message delay from a node to its neighbor and subtract the delay to send the contents from the new participant to the root.The second way a false exclusion occurs is when the root re-moves a participant while it should not,because a content message did not reach it in time.We write the time it takes to send a message i as t d,i(from the start of sending to the end of receiving),the time of reception of message i as t rec,i and the freshness of a participant as f p.For each two consecutive content messages1and2it should be true at the root that t rec,2≤t rec,1+f p.t br,otherwise a par-ticipant is removed in error.After some calculation,this becomes: t d,2−t d,1≤(f p−1).t br.This inequality gives a lower bound for both the freshness and the broadcast period.The inequality shows that the bound is dependent on the difference between two delays only.This means that if the delay increases fairly slowly,the proto-col adapts to this increase.Only when the delay suddenly increases with a value of(f p−1).t br does a false exclusion result.In other words,the broadcast period and the freshness determine the robust-ness of the protocol to message delays and congestion.The upper and lower bound described above show the tradeoff between accuracy and performance.The smaller the broadcast pe-riod,the more accurate and responsive the view becomes.How-ever,sending more messages affects the performance,and causes congestion.Choosing a small broadcast period and freshness also causes errors in the view by decreasing the protocol’s tolerance for。