Senn_TIF_ch01_Answer
- 格式:pdf
- 大小:157.78 KB
- 文档页数:21
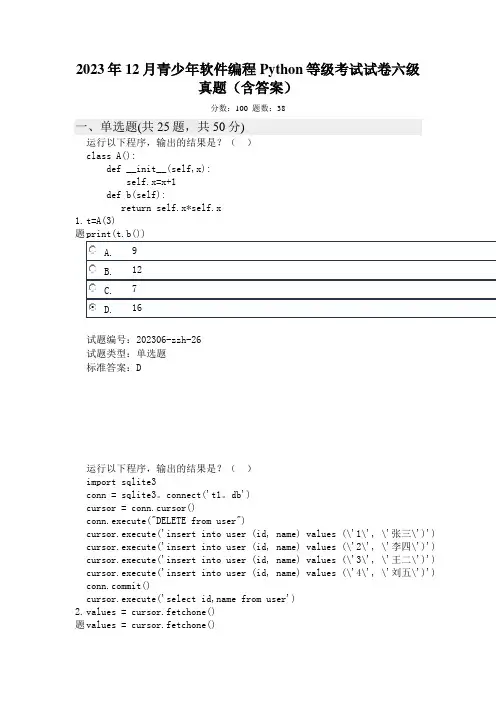
2023年12月青少年软件编程Python等级考试试卷六级真题(含答案)分数:100 题数:38一、单选题(共25题,共50分)1.题运行以下程序,输出的结果是?()class A():def __init__(self,x):self.x=x+1def b(self):return self.x*self.xt=A(3)print(t.b())试题编号:202306-zzh-26试题类型:单选题标准答案:D2.题运行以下程序,输出的结果是?()import sqlite3conn = sqlite3。
connect('t1。
db')cursor = conn.cursor()conn.execute("DELETE from user")cursor.execute('insert into user (id, name) values (\'1\', \'张三\')') cursor.execute('insert into user (id, name) values (\'2\', \'李四\')') cursor.execute('insert into user (id, name) values (\'3\', \'王二\')') cursor.execute('insert into user (id, name) values (\'4\', \'刘五\')') mit()cursor.execute('select id,name from user')values = cursor.fetchone()values = cursor.fetchone()print(values)cursor.close()conn.close()试题编号:202306-zzh-30试题类型:单选题标准答案:C3.题 以下SQLite 语句可以修改记录的是?( )试题编号:202306-zzh-31试题类型:单选题标准答案:B4.题 SQLite 函数中,以下语句的作用是?( )values = cursor.fetchmany(2)print(values)试题编号:202306-zzh-32试题类型:单选题标准答案:A5.题关于SQLite,说法错误的是?()试题编号:202306-zzh-33试题类型:单选题标准答案:D6.题有一个叫做Animal的类,请问下面哪个选项是正确的创建子类Cat的语法?()试题编号:20230614-ltj-023 试题类型:单选题标准答案:A7.题下面的代码定义了一个Circle类,用于表示圆形的信息。

densenet的python实现-回复DenseNet是一种深度卷积神经网络(CNN)架构,其主要优点是能够充分利用网络中的特征信息,并在不同层之间建立密集的连接。
这使得DenseNet能够在许多计算机视觉任务中取得出色的性能,在图像分类、目标检测和图像分割等领域都有广泛的应用。
在本文中,我们将深入探讨DenseNet的实现原理和关键技术,并使用Python进行详细的代码说明。
1. 密集连接(Dense Connectivity)DenseNet的核心思想是密集连接,它是在每个层之间创建了一个直接的连接,使得前一层的输出可以直接传递给后续层的每个卷积层。
这种密集连接的方式有助于特征的重用,并且可以更有效地传递梯度,从而提高网络的训练效果。
2. DenseNet的网络结构DenseNet主要由密集块(Dense Block)和过渡块(Transition Block)两部分组成。
密集块由多个卷积层组成,每个卷积层都接收来自前一层的所有特征图作为输入,并将自己的输出传递给后续所有层。
过渡块用于减小特征图的尺寸,同时通过降低特征图的数量来控制网络的复杂度。
3. 密集块的具体实现在实现密集块时,我们可以使用批量归一化(Batch Normalization)和ReLU激活函数来增强网络的表达能力。
每个卷积层的输入是包括前一层输出和其余层输出的连接,具体实现如下:pythonfrom yers import Conv2D, Concatenatedef dense_block(X, layers_num, growth_rate):concat_layers = [X]for i in range(layers_num):conv = Conv2D(filters=growth_rate, kernel_size=(3, 3), padding='same')(X)concat_layers.append(conv)X = Concatenate()(concat_layers)return X在上述代码中,`X`是输入特征图,`layers_num`是每个密集块的卷积层数量,`growth_rate`是指定每个卷积层输出的特征图数量。

HK32F0301M用户手册版本:2.2发布日期:2023-10-13深圳市航顺芯片技术研发有限公司前言编写目的本文档介绍了HK32F0301M系列芯片的功能框图、存储器映射、Flash、中断和事件等功能以及各功能模块的寄存器描述,旨在帮助用户快速开发HK32F0301M的应用及产品。
读者对象本文适用于以下读者:•开发工程师•芯片测试工程师版本说明本文档对应的产品系列为HK32F0301M系列芯片。
修订记录目录1 简介 (1)2 系统及存储器概述 (2)2.1 系统架构 (2)2.1.1 总线架构 (2)2.2 存储器映射及寄存器编址 (3)2.3 SRAM (3)2.4 启动配置 (4)3 Flash (5)3.1 Flash特性 (5)3.2 Flash功能 (5)3.2.1 Flash结构 (5)3.2.2 读操作 (6)3.2.3 读保护 (6)3.2.3.1 改变读保护级别 (7)3.2.4 写保护 (7)3.2.5 主Flash写和擦除操作 (8)3.2.5.1 主Flash空间的解锁 (8)3.2.5.2 主Flash擦除 (8)3.2.5.3 主Flash编程 (10)3.2.6 Flash中断 (11)3.3 Flash选项字节 (11)3.3.1 选项字节擦除 (13)3.3.2 选项字节编程 (14)3.4 EEPROM (14)3.4.1 EEPROM的擦除 (15)3.4.2 EEPROM的编程 (15)3.5 Flash寄存器 (15)3.5.1 Flash访问控制寄存器(FLASH_ACR) (15)3.5.2 Flash关键字寄存器(FLASH_KEYR) (16)3.5.4 Flash状态寄存器(FLASH_SR) (17)3.5.5 Flash控制寄存器(FLASH_CR) (18)3.5.6 Flash地址寄存器(FLASH_AR) (19)3.5.7 Flash选项字节寄存器(FLASH_OBR) (19)3.5.8 Flash写保护寄存器(FLASH_WRPR) (20)3.5.9 Flash控制寄存器2(FLASH_ECR) (21)3.5.10 中断向量表偏移寄存器(INT_VEC_OFFSET) (21)4 CRC计算单元(CRC) (23)4.1 CRC主要功能 (23)4.2 CRC功能描述 (23)4.3 CRC寄存器 (24)4.3.1 数据寄存器(CRC_DR) (24)4.3.2 独立数据寄存器(CRC_IDR) (24)4.3.3 控制寄存器(CRC_CR) (25)4.3.4 CRC初值寄存器(CRC_INIT) (25)5 电源控制(PWR) (27)5.1 电源 (27)5.1.1 独立的A/D转换器供电和参考电压 (27)5.1.2 电压调节器 (27)5.2 上电/掉电复位(POR/PDR) (28)5.3 低功耗模式 (28)5.3.1 降低系统时钟 (29)5.3.2 外部时钟的控制 (29)5.3.3 睡眠(Sleep)模式 (30)5.3.3.1 进入睡眠模式 (30)5.3.3.2 退出睡眠模式 (30)5.3.4 深度睡眠(DeepSleep)模式 (31)5.3.5 停机(Stop)模式 (31)5.3.5.1 进入停机模式 (31)5.3.5.2 退出停机模式 (31)5.3.6.1 进入待机模式 (31)5.3.6.2 退出待机模式 (32)5.3.6.3 待机模式下的输入/输出端口状态 (32)5.3.6.4 待机模式下的自动唤醒(STBAWU) (32)5.3.6.5 待机模式下的IO保持 (32)5.3.6.6 待机模式下的备份 (32)5.3.7 调试模式 (32)5.4 PWR寄存器 (32)5.4.1 电源控制寄存器(PWR_CR) (32)5.4.2 电源控制/状态寄存器(PWR_CSR) (33)5.4.3 WKUP引脚极性控制寄存器(PWR_WUP_POL) (34)5.4.4 待机模式下掉电检测控制寄存器(PWR_PORPDR_CFG) (35)5.4.5 内部参考电压输出选择寄存器(PWR_VREF_SEL) (36)5.4.6 待机模式下自动唤醒定时器(PWR_SAWUT) (36)5.4.7 待机模式下备份(PWR_SBKP0) (36)5.4.8 待机模式下备份(PWR_SBKP1) (37)6 复位和时钟控制(RCC) (38)6.1 复位 (38)6.1.1 系统复位 (38)6.1.2 电源复位 (39)6.2 时钟 (39)6.2.1 HSI时钟 (40)6.2.2 GPIO外部时钟输入 (40)6.2.3 LSI时钟 (40)6.2.4 系统时钟(SYSCLK)选择 (41)6.2.5 看门狗时钟 (41)6.2.6 时钟输出功能(MCO) (41)6.3 RCC寄存器 (41)6.3.1 时钟控制寄存器(RCC_CR) (41)6.3.2 时钟配置寄存器(RCC_CFGR) (43)6.3.4 APB2外设复位寄存器(RCC_APB2RSTR) (46)6.3.5 APB1外设复位寄存器(RCC_APB1RSTR) (47)6.3.6 AHB外部时钟使能寄存器(RCC_AHBENR) (49)6.3.7 APB外设时钟使能寄存器2(RCC_APB2ENR) (50)6.3.8 APB1外设时钟使能寄存器(RCC_APB1ENR) (52)6.3.9 控制/状态寄存器(RCC_CSR) (53)6.3.10 AHB外设复位寄存器(RCC_AHBRSTR) (55)6.3.11 时钟配置寄存器3(RCC_CFGR3) (56)6.3.12 控制寄存器(RCC_CSS) (57)6.3.13 时钟配置寄存器4(RCC_CFGR4) (57)7 系统配置控制器(SYSCFG) (59)7.1 SYSCFG寄存器 (59)7.1.1 SYSCFG配置寄存器1(SYSCFG_CFGR1) (59)7.1.2 SYSCFG外部中断配置寄存器1(SYSCFG_EXTICR1) (59)7.1.3 SYSCFG外部中断配置寄存器2(SYSCFG_EXTICR2) (60)8 通用I/O(GPIO) (61)8.1 GPIO的主要特性 (61)8.2 GPIO功能描述 (61)8.2.1 通用I/O(GPIO) (63)8.2.2 I/O引脚复用功能复用器和映射 (63)8.2.3 I/O端口控制寄存器 (64)8.2.4 I/O端口数据寄存器 (64)8.2.5 I/O数据位操作 (64)8.2.6 GPIO锁定机制 (64)8.2.7 I/O复用功能输入输出 (65)8.2.8 外部中断线/唤醒线 (65)8.2.9 输出配置 (65)8.2.10 复用功能配置 (65)8.2.11 模拟配置 (65)8.2.12 施密特功能配置 (66)8.3.1 GPIO端口模式寄存器(GPIOx_MODER)(x = A..D) (66)8.3.2 GPIO端口输出类型寄存器(GPIOx_OTYPER)(x = A..D) (66)8.3.3 GPIO口输出速度寄存器(GPIOx_OSPEEDR)(x = A..D) (67)8.3.4 GPIO口上拉/下拉寄存器(GPIOx_PUPDR)(x = A..D) (67)8.3.5 GPIO端口输入数据寄存器(GPIOx_IDR)(x = A..D) (67)8.3.6 GPIO端口输出数据寄存器(GPIOx_ODR)(x = A..D) (68)8.3.7 GPIO端口置位/复位寄存器(GPIOx_BSRR)(x = A..D) (68)8.3.8 GPIO端口配置锁定寄存器(GPIOx_LCKR)(x = A..B) (69)8.3.9 GPIO复用功能低位寄存器(GPIOx_AFRL)(x = A..D) (70)8.3.10 GPIO端口位复位寄存器(GPIOx_BRR)(x=A..D) (70)8.3.11 GPIO端口输入输出施密特寄存器(GPIOx_IOSR)(x=A..D) (71)9 引脚选择功能(IOMUX) (72)9.1 功能介绍 (72)9.2 IOMUX寄存器 (72)9.2.1 IOMUX引脚功能选择寄存器(PIN_FUNC_SEL) (72)9.2.2 IOMUX引脚选择寄存器(PKG_PIN_SEL) (73)9.2.3 IOMUX功能控制寄存器(NRST_PIN_KEY) (74)9.2.4 IOMUX引脚功能控制寄存器(NRST_PA0_SEL) (74)9.2.5 IOMUX引脚功能控制寄存器(TIM2_CH0_IN_SEL) (75)10 中断和事件(NVIC和EXTI) (76)10.1 嵌套向量中断控制器(NVIC) (76)10.1.1 NVIC主要特性 (76)10.1.2 系统嘀嗒校准值寄存器 (76)10.1.3中断和异常向量 (76)10.2 扩展中断和事件控制器(EXTI) (78)10.2.1 主要特性 (78)10.2.2 框图 (78)10.2.3 EXTI与周边模块关系 (79)10.2.4 唤醒事件管理 (79)10.2.5 功能说明 (80)10.2.5.2 硬件事件选择 (80)10.2.5.3 软件中断/事件的选择 (80)10.2.6 外部中断/事件线映射 (80)10.3 EXTI寄存器 (81)10.3.1 中断屏蔽寄存器(EXTI_IMR) (81)10.3.2 事件屏蔽寄存器(EXTI_EMR) (82)10.3.3 上升沿触发选择寄存器(EXTI_RTSR) (82)10.3.4 下降沿触发选择寄存器(EXTI_FTSR) (83)10.3.5 软件中断事件寄存器(EXTI_SWIER) (83)10.3.6 请求挂起寄存器(EXTI_PR) (84)11 模拟数字转换器(ADC) (85)11.1 ADC主要特性 (85)11.2 ADC功能描述 (85)11.2.1 ADC引脚和内部信号 (86)11.2.2 校准(ADCAL) (86)11.2.3 ADC开关控制(ADEN, ADDIS, ADRDY) (87)11.2.4 ADC时钟(CKMODE) (88)11.2.5 配置ADC (89)11.2.6 通道选择 (89)11.2.7 可编程采样时间(SMP) (89)11.2.8 单次转换模式(CONT=0) (90)11.2.9 连续转换模式(CONT=1) (90)11.2.10 开始转换(ADSTART) (91)11.2.11 时序 (91)11.2.12 停止正在进行的转换(ADSTP) (92)11.3 外部触发转换和触发极性(EXTSEL, EXTEN) (92)11.3.1 不连续模式(DISCEN) (93)11.3.2 转换结束、采样阶段结束(EOC, EOSMP标志) (94)11.3.3 转换序列结束(EOS标志) (94)11.3.4 时序图示例(单次/连续模式硬件/软件触发) (94)11.4.1 数据管理和数据对齐(ADC_DR, ALIGN) (95)11.4.2 ADC溢出(OVR, OVRMOD) (96)11.5 功耗特性 (97)11.5.1 等待模式转换 (97)11.5.2 自动关闭模式(AUTOFF) (97)11.6 模拟窗口看门狗(AWDEN, AWDSGL, AWDCH, HT/LT, AWD) (98)11.7 内部参考电压 (99)11.8 ADC中断 (100)11.9 ADC寄存器 (101)11.9.1 ADC中断和状态寄存器(ADC_ISR) (101)11.9.2 ADC中断使能寄存器(ADC_IER) (102)11.9.3 ADC控制寄存器(ADC_CR) (103)11.9.4 ADC配置寄存器1(ADC_CFGR1) (105)11.9.5 ADC配置寄存器2(ADC_CFGR2) (108)11.9.6 ADC采样时间寄存器(ADC_SMPR) (108)11.9.7 ADC看门狗阈值寄存器(ADC_TR) (109)11.9.8 ADC通道选择寄存器(ADC_CHSELR) (109)11.9.9 ADC数据寄存器(ADC_DR) (110)11.9.10 ADC通用配置寄存器(ADC_CCR) (110)11.9.11 ADC控制寄存器2(ADC_CR2) (111)12 高级控制定时器(TIM1) (112)12.1 TIM1主要功能 (112)12.2 TIM1功能描述 (113)12.2.1 时基单元 (113)12.2.2 计数器模式 (115)12.2.2.1 向上计数模式 (115)12.2.2.2 向下计数模式 (118)12.2.2.3 中央对齐模式(向上/向下计数) (119)12.2.3 重复计数器 (122)12.2.4 时钟选择 (123)12.2.6 输入捕获模式 (127)12.2.7 PWM输入模式 (128)12.2.8 强制输出模式 (128)12.2.9 输出比较模式 (129)12.2.10 PWM模式 (130)12.2.10.1 PWM边沿对齐模式 (130)12.2.10.2 PWM中央对齐模式 (131)12.2.11 互补输出和死区插入 (132)12.2.12 使用刹车功能 (134)12.2.13 在外部事件时清除OCxREF信号 (135)12.2.14 产生六步PWM输出 (136)12.2.15 单脉冲模式 (137)12.2.16 编码器接口模式 (138)12.2.17 定时器输入异或功能 (139)12.2.18 与霍尔传感器的接口 (140)12.2.19 TIM1定时器和外部触发的同步 (141)12.2.19.1 从模式:复位模式 (141)12.2.19.2 从模式:门控模式 (142)12.2.19.3 从模式:触发模式 (142)12.2.19.4 从模式:外部时钟模式2+触发模式 (143)12.2.20 定时器同步 (143)12.2.21 调试模式 (144)12.3 TIM1寄存器 (144)12.3.1 TIM1控制存器1(TIM1_CR1) (144)12.3.2 TIM1控制寄存器2(TIM1_CR2) (145)12.3.3 TIM1从模式控制寄存器(TIM1_SMCR) (147)12.3.4 TIM1中断使能寄存器(TIM1_DIER) (149)12.3.5 TIM1状态寄存器(TIM1_SR) (150)12.3.6 TIM1事件产生寄存器(TIM1_EGR) (152)12.3.7 TIM1捕捉/比较模式寄存器1(TIM1_CCMR1) (153)12.3.9 TIM1捕捉/比较使能寄存器(TIM1_CCER) (158)12.3.10 TIM1计数器(TIM1_CNT) (160)12.3.11 TIM1预分频器(TIM1_PSC) (161)12.3.12 TIM1自动重装载寄存器(TIM1_ARR) (161)12.3.13 TIM1重复计数寄存器(TIM1_RCR) (161)12.3.14 TIM1捕捉/比较寄存器1(TIM1_CCR1) (162)12.3.15 TIM1捕捉/比较寄存器2(TIM1_CCR2) (162)12.3.16 TIM1捕捉/比较寄存器3(TIM1_CCR3) (162)12.3.17 TIM1捕捉/比较寄存器4(TIM1_CCR4) (163)12.3.18 TIM1刹车和死区寄存器(TIM1_BDTR) (163)13 通用定时器(TIM2) (165)13.1 TIM2主要功能 (165)13.2 TIM2功能描述 (166)13.2.1 时基单元 (166)13.2.2 计数器模式 (168)13.2.2.1 向上计数模式 (168)13.2.2.2 向下计数模式 (171)13.2.2.3 中央对齐模式(向上/向下计数) (174)13.2.3 时钟选择 (177)13.2.4 捕获/比较通道 (179)13.2.5 输入捕获模式 (181)13.2.6 PWM输入模式 (181)13.2.7 强置输出模式 (182)13.2.8 输出比较模式 (182)13.2.9 PWM模式 (183)13.2.9.1 PWM边沿对齐模式 (184)13.2.9.2 PWM中央对齐模式 (184)13.2.10 单脉冲模式 (185)13.2.11 在外部事件时清除OCxREF信号 (187)13.2.12 编码器接口模式 (187)13.2.14 定时器和外部触发的同步 (189)13.2.14.1 从模式:复位模式 (189)13.2.14.2 从模式:门控模式 (190)13.2.14.3 从模式:触发模式 (190)13.2.14.4 从模式:外部时钟模式2+触发模式 (191)13.2.15 定时器同步 (191)13.2.15.1 使用一个定时器作为另一个定时器的预分频器 (192)13.2.15.2 使用一个定时器使能另一个定时器 (192)13.2.15.3 使用一个定时器去启动另一个定时器 (194)13.2.15.4 使用一个外部触发同步地启动2个定时器 (195)13.2.16 调试模式 (196)13.3 TIM2寄存器 (196)13.3.1 TIM2控制寄存器1(TIM2_CR1) (196)13.3.2 TIM2控制寄存器2(TIM2_CR2) (198)13.3.3 TIM2从模式控制寄存器(TIM2_SMCR) (199)13.3.4 TIM2中断允许寄存器(TIM2_DIER) (201)13.3.5 TIM2状态寄存器(TIM2_SR) (202)13.3.6 TIM2事件产生寄存器(TIM2_EGR) (203)13.3.7 TIM2捕捉/比较模式寄存器1(TIM2_CCMR1) (204)13.3.8 TIM2捕捉/比较模式寄存器2(TIM2_CCMR2) (207)13.3.9 TIM2捕捉/比较使能寄存器(TIM2_CCER) (209)13.3.10 TIM2计数器(TIM2_CNT) (210)13.3.11 TIM2预分频(TIM2_PSC) (210)13.3.12 TIM2自动重装寄存器(TIM2_ARR) (211)13.3.13 TIM2捕捉/比较寄存器1(TIM2_CCR1) (211)13.3.14 TIM2捕捉/比较寄存器2(TIM2_CCR2) (212)13.3.15 TIM2捕捉/比较寄存器3(TIM2_CCR3) (212)13.3.16 TIM2捕捉/比较寄存器4(TIM2_CCR4) (213)14 基本定时器(TIM6) (214)14.1 TIM6主要功能 (214)14.2.1 时基单元 (214)14.2.2 计数模式 (216)14.2.2.1 向上计数模式 (216)14.2.2.2 向下计数模式 (218)14.2.3 时钟源 (221)14.2.4 调试模式 (221)14.3 TIM6寄存器 (221)14.3.1 TIM6控制寄存器1(TIM6_CR1) (221)14.3.2 TIM6控制寄存器2(TIM6_CR2) (222)14.3.3 TIM6中断使能寄存器(TIM6_DIER) (223)14.3.4 TIM6状态寄存器(TIM6_SR) (223)14.3.5 TIM6事件产生寄存器(TIM6_EGR) (224)14.3.6 TIM6定时器(TIM6_CNT) (224)14.3.7 TIM6预分频器(TIM6_PSC) (224)14.3.8 TIM6自动重装寄存器(TIM6_ARR) (225)15 自动唤醒定时器(AWU) (226)15.1 AWU寄存器 (226)15.1.1 控制寄存器(AWU_CR) (226)15.1.2 控制寄存器(AWU_SR) (226)16 独立看门狗(IWDG) (228)16.1 IWDG主要功能 (228)16.2 IWDG功能描述 (228)16.2.1 窗口选项 (229)16.2.2 硬件看门狗 (230)16.2.3 寄存器访问保护 (230)16.2.4 调试模式 (230)16.3 IWDG寄存器 (230)16.3.1 关键字寄存器(IWDG_KR) (230)16.3.2 预分频寄存器(IWDG_PR) (231)16.3.3 重加载寄存器(IWDG_RLR) (231)16.3.5 窗口寄存器(IWDG_WINR) (232)17 系统窗口看门狗(WWDG) (234)17.1 WWDG主要特性 (234)17.2 WWDG功能描述 (234)17.2.1 启动看门狗 (234)17.2.2 控制递减计数器 (235)17.2.3 看门狗中断高级特性 (235)17.2.4 如何编写看门狗超时程序 (235)17.2.5 调试模式 (236)17.3 WWDG寄存器 (236)17.3.1 控制寄存器(WWDG_CR) (236)17.3.2 配置寄存器(WWDG_CFR) (237)17.3.3 状态寄存器(WWDG_SR) (237)18 内部集成电路接口(I2C) (238)18.1 I2C主要特性 (238)18.2 I2C功能说明 (238)18.2.1 I2C框图 (239)18.2.2 I2C时钟要求 (239)18.2.3 模式选择 (240)18.2.4 I2C初始化 (240)18.2.5 软件复位 (244)18.2.6 数据传输 (244)18.2.7 从模式 (247)18.2.8 主模式 (253)18.2.9 I2C_TIMINGR寄存器配置示例 (262)18.2.10 SMBus I2C特性 (263)18.2.11 SMBus初始化 (265)18.2.12 SMBus:I2C_TIMEOUTR寄存器配置示例 (267)18.2.13 SMBus模式 (267)18.2.14 地址匹配时从停机模式唤醒 (272)18.2.16 调试模式 (274)18.3 I2C低功耗模式 (274)18.4 I2C中断 (274)18.5 I2C寄存器 (275)18.5.1 控制寄存器1(I2C_CR1) (275)18.5.2 控制寄存器2(I2C_CR2) (278)18.5.3 本机地址1寄存器(I2C_OAR1) (280)18.5.4 本机地址2寄存器(I2C_OAR2) (281)18.5.5 时序寄存器(I2C_TIMINGR) (282)18.5.6 超时寄存器(I2C_TIMEOUTR) (282)18.5.7 中断和状态寄存器(I2C_ISR) (283)18.5.8 中断清除寄存器(I2C_ICR) (285)18.5.9 PEC寄存器(I2C_PECR) (286)18.5.10 接收数据寄存器(I2C_RXDR) (287)18.5.11 发送数据寄存器(I2C_TXDR) (287)19 通用同步异步收发器(USART) (288)19.1 USART主要特性 (288)19.2 USART扩展特性 (288)19.3 USART实现 (289)19.4 USART功能说明 (289)19.4.1 USART字符说明 (290)19.4.2 USART发送器 (291)19.4.3 USART接收器 (293)19.4.4 USART波特率生成 (296)19.4.5 USART接收器对时钟偏差的容差 (298)19.4.6 USART自动波特率检测 (299)19.4.7 使用USART进行多处理器通信 (300)19.4.8 使用USART进行Modbus通信 (301)19.4.9 USART奇偶校验 (301)19.4.10 USART LIN(局域互连网络)模式 (302)19.4.12 USART单线半双工通信 (306)19.4.13 USART智能卡模式 (306)19.4.14 USART IrDA SIR ENDEC模块 (309)19.4.15 RS485驱动器使能 (310)19.4.16 从停机模式唤醒 (310)19.5 USART低功耗模式 (311)19.6 USART中断 (311)19.7 USART寄存器 (312)19.7.1 控制寄存器1(USART_CR1) (312)19.7.2 控制寄存器2(USART_CR2) (315)19.7.3 控制寄存器3(USART_CR3) (319)19.7.4 波特率寄存器(USART_BRR) (322)19.7.5 保护时间和预分频器寄存器(USART_GTPR) (322)19.7.6 接收超时寄存器(USART_RTOR) (323)19.7.7 请求寄存器(USART_RQR) (324)19.7.8 中断和状态寄存器(USART_ISR) (324)19.7.9 中断标志清除寄存器(USART_ICR) (328)19.7.10 数据接收寄存器(USART_RDR) (330)19.7.11 数据发送寄存器(USART_TDR) (330)20 串行外设接口(SPI/I2S) (331)20.1 SPI和I2S主要特征 (331)20.2 SPI主要特征 (331)20.2.1 I2S主要特征 (331)20.3 SPI/I2S实现 (332)20.4 SPI功能说明 (332)20.4.1 一个主器件和一个从器件之间的通信 (333)20.4.1.1 全双工通信 (333)20.4.1.2 半双工通信 (333)20.4.1.3 单工通信 (334)20.4.2 标准多从器件通信 (335)20.4.5 通信格式 (337)20.4.5.1 时钟相位和极性控制 (337)20.4.5.2 数据帧格式 (338)20.4.6 SPI配置 (338)20.4.7 使能SPI步骤 (339)20.4.8 数据发送和接收过程 (339)20.4.9 禁用SPI步骤 (341)20.4.10 SPI状态标志 (342)20.4.11 SPI错误标志 (342)20.4.12 NSS脉冲模式 (343)20.4.13 TI模式 (344)20.4.14 CRC计算 (344)20.5 SPI中断 (345)20.6 SPI接口特性 (345)20.7 I2S功能说明 (347)20.7.1 I2S概述 (347)20.7.2 I2S全双工 (349)20.7.3 支持的音频协议 (349)20.7.4 启动描述 (355)20.7.5 时钟发生器 (356)20.7.6 I2S主模式 (357)20.7.7 I2S从模式 (359)20.7.8 I2S状态标志 (360)20.7.9 I2S错误标志 (361)20.8 I2S中断 (361)20.9 I2S接口特性 (362)20.10 SPI寄存器 (363)20.10.1 SPI控制寄存器1(SPI_CR1) (363)20.10.2 SPI控制寄存器2(SPI_CR2) (365)20.10.5 SPI的CRC多项式寄存器(SPI_CRCPR) (368)20.10.6 SPI接收CRC寄存器(SPI_RXCRCR) (369)20.10.7 SPI发送CRC寄存器(SPI_TXCRCR) (369)20.10.8 SPI_I2S配置寄存器(SPI_I2SCFGR) (369)20.10.9 SPI_I2S预分频寄存器(SPI_I2SPR) (371)21 蜂鸣器(Beeper) (372)21.1 蜂鸣器主要特性 (372)21.2 蜂鸣器功能说明 (372)21.2.1 蜂鸣器框图 (372)21.2.2 定时触发 (372)21.3 Beeper寄存器 (372)21.3.1 配置寄存器(BEEP_CFGR) (372)21.3.2 控制寄存器(BEEP_CR) (373)22 设备电子签名(UID) (375)22.1 唯一设备ID寄存器(64位) (375)22.1.1 UID寄存器0(U_ID0) (375)22.1.2 UID寄存器1(U_ID1) (375)23 调试支持(DBG) (377)23.1 概述 (377)23.2 ARM®参考文档 (378)23.3 引脚排列和调试端口引脚 (378)23.3.1 SWD端口引脚 (378)23.3.2 SW-DP引脚分配 (378)23.3.3 SWD引脚上的内部上拉和下拉 (378)23.4 SWD端口 (378)23.4.1 SWD协议简介 (378)23.4.2 SWD协议序列 (379)23.4.3 SW-DP状态机(复位、空闲状态、ID代码) (380)23.4.4 DP和AP读/写访问 (380)23.5 内核调试 (381)23.6 BPU(断点单元) (382)23.6.1 BPU功能 (382)23.7 DWT(数据观察点) (382)23.7.1 DWT功能 (382)23.7.2 DWT程序计数器采样寄存器 (382)23.8 MCU调试组件(DBG) (382)23.8.1 对低功耗模式的调试支持 (382)23.8.2 对定时器、看门狗和I2C的调试支持 (383)23.9 DBGMCU寄存器 (383)23.9.1 MCU器件ID代码寄存器(DBGMCU_IDCODE) (383)23.9.2 调试MCU配置寄存器(DBGMCU_CR) (383)23.9.3 调试MCU APB1冻结寄存器(DBGMCU_APB1_FZ) (384)24 缩略语与术语 (386)24.1 寄存器描述中的缩略语 (386)24.2 缩略语 (386)24.3 术语 (387)25 重要提示 (388)简介1简介本文档为HK32F0301M系列芯片的用户手册。

python编写答题程序好的,以下是一个简单的Python答题程序的示例代码:python复制代码:# 定义题目和答案questions = [{"question": "1 + 1 = ?", "answer": 2},{"question": "2 * 2 = ?", "answer": 4},{"question": "What is the capital of France?", "answer": "Paris"},{"question": "What color are apples?", "answer": "Red or green"}]# 循环遍历题目,询问用户答案并判断是否正确for i, question in enumerate(questions):print(f"{i+1}. {question['question']}")answer = input("Your answer: ")if answer == question['answer']:print("Correct!")else:print(f"Wrong! The correct answer is{question['answer']}")这个程序定义了一个包含四个问题的列表,然后循环遍历问题并询问用户答案。
如果用户回答正确,则输出“Correct!”;否则输出“Wrong!”和正确答案。
注意,这个程序使用了Python内置的input()函数来获取用户输入。

python一级模拟试题您的姓名: [填空题] *_________________________________1.已知a="161",b="16",c="8",执行语句d=a>b and a>c,变量d的值为是?()[单选题] *A.0B.1C.TrueD.False(正确答案)答案解析:本题考查的是字符串+运算。
字符串+表示将后面的字符串拼接在前面的字符串中。
2.执行语句flag="3456">"36",变量flag的值?() [单选题] *A."3456"B."36"C.TrueD.False(正确答案)3.执行语句y=123%100后,变量y的值为?() [单选题] *A.1B.3C.12D.23(正确答案)4.Python是一种计算机( )语言? [单选题] *A.低级B.高级(正确答案)C.机器D.汇编5.以下哪种输入不可以得到以下反馈:重要的事情说三遍:戴口罩!戴口罩!戴口罩!?() [单选题] *A.print("重要的事情说三遍:戴口罩!戴口罩!戴口罩!")B.print("重要的事情说三遍:"+"戴口罩!"*3)C.print('重要的事情说三遍:'+'戴口罩!'*3)D.print('重要的事情说三遍:戴口罩!'*3)(正确答案)6.在Python函数中,用于获取用户输入的是?() [单选题] *A.str()B.eval()C.print()D.input()(正确答案)7.关于Python赋值语句,以下选项中不合法的是?() [单选题] *A.a,b=b,aB.a=b=1C.a=(b=1)(正确答案)D.a=1;b=18.在Python中输入 2+7/2 ,输出结果为哪一种数据类型?() [单选题] *A.整数型B.浮点型(正确答案)C.字符型D.文字型9.在Python中,a=2,b="3.5",如果想进行2+3.5的加法运算,我们应该如何编写代码?() [单选题] *A.a+bB.str(a)+bC.a+ int(b)D.a+eval(b)(正确答案)10.算数运算符、比较运算符和逻辑运算符,在Python的运算中的优先关系是?() [单选题] *A.算数运算符>比较运算符>逻辑运算符(正确答案)B.比较运算符>逻辑运算符>算术运算符C.算数运算符>逻辑运算符>比较运算符D.逻辑运算符>比较运算符>算数运算符11.下面图形最有可能是哪个选项的代码执行后的效果?()[单选题] *A.B.(正确答案)C.D.12.print(1024//10**2)的结果是?() [单选题] *A.100B.24C.10(正确答案)D.10.2413.turtle.reset() 命令的含义是下列哪一种? [单选题] *A.不清空turtle窗口,重置turtle的位置和状态B.清空turtle窗口,重置turtle状态为初始状态(正确答案)C.清空turtle窗口,但是turtle的位置和状态不会改变D.撤销上一个动作14.假设我们设定turtle库中画笔粗细为5,我们调用turtle.dot(None,"red")函数画圆点时,圆点的直径是多少?() [单选题] *A.5(正确答案)B.10C.18D.2015.函数turtle.circle(50,steps=4),画的是什么图形?() [单选题] *A.直径是50的圆B.对角线为50的正方形C.对角线为100的正方形(正确答案)D.边长是50的正方形16.使用下面选项中的代码组合成一个turtle文件中的一部分,来绘制一个空心五角星的脚本中,最不可能用到下面哪条代码?() [单选题] *A.t.left(144)B.import turtleC.t.circle(36)(正确答案)D.t=turtle.Pen()17.以下不属于Python常见编程环境的是?() [单选题] *A.IDLEB.Visual Studio CodeC.JAVA(正确答案)D.JupyterNotebook18.在turtle库中的指令,执行以下代码指令后,画笔为哪种颜色?()[单选题] *A.粉色B.黄色C.绿色(正确答案)D.程序报错19.假设x = 14,y = 6,那么执行x>y and 5,的结果为?() [单选题] *A.x>yB.5(正确答案)C.FalseD.True答案解析:当and左边条件为真时,则返回and右边的值20.以下哪个变量名是符合Python变量命名规范的?() [单选题] *A.123B.my varC.my_variable(正确答案)D.&var21.已知:a = 7,b = 5,c = 12 执行以下哪个语句结果为True?() [单选题] *A.a > c or a < bB.a < c(正确答案)C.a < c and a < bD.c < b22.执行7 * 8 – 6 > 10 输出的结果是?() [单选题] *A.56B.50C.FalseD.True(正确答案)23.关于Python以下说法正确的是?() [单选题] *A.Python安装好后,IDLE也需要提前安装才可以用。

初中生学习python试题库及答案一、选择题1. Python中,哪个关键字用于定义函数?A. functionB. defC. classD. return答案:B2. 在Python中,以下哪个是正确的字符串?A. 'Hello, World!'B. "Hello, World!"C. Both A and BD. None of the above答案:C3. Python中,以下哪个是正确的列表?A. [1, 2, 3, 4]B. (1, 2, 3, 4)C. {1, 2, 3, 4}D. A and B答案:D4. 在Python中,哪个模块用于数学运算?A. mathB. mathsC. calculatorD. numbers答案:A5. Python中,以下哪个是正确的字典?A. {'name': 'Alice', 'age': 25}B. [name: 'Alice', age: 25]C. {name: 'Alice', age: 25}D. (name: 'Alice', age: 25)答案:A二、填空题1. Python是一种______语言,它强调代码的可读性和简洁性。
答案:高级2. 在Python中,使用______运算符可以连接字符串。
答案:+3. Python中的______函数可以计算列表中所有元素的和。
答案:sum4. Python中,______关键字用于创建循环,直到满足某个条件。
答案:while5. Python中,______函数用于生成指定范围内的数字序列。
答案:range三、简答题1. 请简述Python中列表和元组的区别。
答案:列表是可变的,可以添加、删除或更改其元素,而元组是不可变的,一旦创建就不能修改其元素。
2. 什么是Python中的异常处理,它有什么作用?答案:异常处理是Python中用于处理程序运行时可能出现的错误的机制。

infilter函数-回复Infilter函数:单行代码实现Python列表过滤器的神奇函数引言:在Python编程中,列表是常用的数据结构之一。
我们经常会遇到需要根据一定条件对列表进行过滤的需求,从而提取出符合特定条件的元素。
过去,这种操作通常需要编写循环或使用内置函数,但现在,一个名为"infilter"的函数横空出世,它能以极简的方式实现对列表的过滤操作。
本文将逐步介绍infilter函数的使用方法和原理。
第一步:简介infilter函数infilter函数是Python编程中的一个实用函数,它的功能是根据指定的条件将列表中的元素进行过滤,返回符合条件的元素列表。
它以单行代码的方式实现了列表的过滤操作,让代码变得简洁高效。
第二步:infilter函数的语法在使用infilter函数之前,我们先来了解一下它的语法。
infilter函数的语法如下:pythonnew_list = infilter(condition, old_list)其中,condition是一个lambda表达式,用于指定过滤条件;old_list 是待过滤的列表;new_list是符合条件的元素组成的新列表。
第三步:使用示例为了更好地理解infilter函数的用法,我们来看一个具体的使用示例。
假设我们有一个存储学生成绩的列表,我们想要从中挑选出不及格的成绩,可以使用infilter函数来实现。
pythongrades = [80, 75, 90, 60, 65, 95]failed_grades = infilter(lambda x: x < 60, grades)在上述示例中,lambda表达式`lambda x: x < 60`用于指定过滤条件,即成绩小于60分;grades是待过滤的列表,其中存储了学生成绩;failed_grades是过滤后的结果列表,存储了不及格的成绩。
第四步:infilter函数的原理了解了infilter函数的用法,我们再来看一下其实现的原理。


Question-Answer Dataset(试题答案数据集)数据摘要:This page provides a link to a corpus of Wikipedia articles, manually-generated factoid questions from them, and manually-generated answers to these questions, for use in academic research. These data were collected by Noah Smith, Michael Heilman, Rebecca Hwa, Shay Cohen, Kevin Gimpel, and many students at Carnegie Mellon University and the University of Pittsburgh between 2008 and 2010.中文关键词:问题,答案,数据集,语料库,手工生成,英文关键词:questions,answers,Dataset,corpus,questions,manually-generated,数据格式:TEXT数据用途:Information Processing,Academic Research数据详细介绍:Question-Answer DatasetThis page provides a link to a corpus of Wikipedia articles, manually-generated factoid questions from them, and manually-generated answers to these questions, for use in academic research. These data were collected by Noah Smith, Michael Heilman, Rebecca Hwa, Shay Cohen, Kevin Gimpel, and many students at Carnegie Mellon University and the University of Pittsburgh between 2008 and 2010.DownloadManually-generated factoid question/answer pairs with difficulty ratings from Wikipedia articles. Dataset includes articles, questions, and answers.Version 1.1 released August 6, 2010README.v1.1; Question_Answer_Dataset_v1.1.tar.gzArchived ReleasesVersion 1.0 released February 18, 2010README.v1.0; Question_Answer_Dataset_v1.0.tar.gzFurther ReadingPlease cite this paper if you write any papers involving the use of the data above: Question Generation as a Competitive Undergraduate Course ProjectNoah A. Smith, Michael Heilman, and Rebecca HwaIn Proceedings of the NSF Workshop on the Question Generation Shared Task and Evaluation Challenge, Arlington, VA, September 2008.AcknowledgmentsThis research project was supported by NSF IIS-0713265 (to Smith), an NSF Graduate Research Fellowship (to Heilman), NSF IIS-0712810 and IIS-0745914 (to Hwa), and Institute of Education Sciences, U.S. Department of Education R305B040063 (to Carnegie Mellon).数据预览:点此下载完整数据集。

python中insect的用法-回复题目:Python中insect的用法及实例解析引言:Python作为一种高级编程语言,拥有丰富的内置函数和运算符,涵盖了众多的功能以及方便的语法特性。
其中一个很有用的内置运算符就是insect(in)运算符,它允许我们在列表、字符串、元组、集合等数据结构中检查特定值是否存在。
本文将深入探讨Python中insect运算符的用法,提供各种实例来帮助读者更好地理解。
一、insect运算符的概述insect(in)运算符是Python中的一个成员测试运算符。
通过insect运算符,我们可以在一个可迭代对象(如列表、字符串、元组、集合等)中判断某个值是否存在。
如果存在,将返回True;否则返回False。
insect 运算符通常与条件语句一起使用,帮助我们根据特定的条件来执行相关的操作。
二、insect运算符的语法使用insect运算符非常简单,其语法如下:value in iterable其中,value为我们要检查的特定值,iterable则是一个可迭代的对象。
三、insect运算符的使用示例下面通过一些实例来详细解释insect运算符的用法。
3.1 检查列表中的元素列表是Python中最常用的数据结构之一。
我们可以使用insect运算符来检查特定的元素是否在列表中存在。
pythonfruits = ['apple', 'banana', 'orange', 'grape']if 'apple' in fruits:print("Yes, apple is in the fruits list.")else:print("No, apple is not in the fruits list.")以上代码会输出结果:Yes, apple is in the fruits list.3.2 检查字符串中的字符Python中的字符串也是可以使用insect运算符进行成员测试的。

现在大多人使用互联网搜索答案英语作文精选英文现在大多人使用互联网搜索答案英语作文:The Prevalence of Internet Search for Answers in Modern SocietyIn today's digital age, the internet has become an integral part of our daily lives, revolutionizing the way we access and disseminate information. One of the most notable aspects of this transformation is the widespread reliance on the internet for searching and finding answers to various questions and inquiries.The convenience and efficiency of internet search engines have made them the go-to tool for most people when they encounter a problem or a question. Whether it's a simple query about a definition, a complex scientific query, or a practical issue like finding a nearby restaurant, the internet provides instant and comprehensive results. Search engines such as Google, Bing, and Yahoo have become household names, synonymous with finding answers online.The popularity of internet search can be attributed to several factors. Firstly, the vast amount of information available on the internet makes it a virtual library of knowledge. From academic articles to personal blogs, the internet hosts a diverse range of perspectives and opinions, allowing users to explore different angles of a topic. Secondly, the ease of use and accessibility of search engines have made them extremely user-friendly. Even those with minimal technical skills can navigate search engines and find relevant results with ease.However, while internet search has numerous benefits, it also poses some challenges. The sheer volume of information can be overwhelming, and it's often difficult to separatereliable sources from unreliable ones. Additionally, the personalized search results based on algorithms and user data can sometimes limit exposure to diverse perspectives.Despite these challenges, the internet remains a valuable resource for finding answers. Many people rely on it to stay informed, solve problems, and make decisions. As technology continues to advance, the role of internet search in our lives is likely to become even more prominent.In conclusion, the internet has become the primary source of information and answers for most people. Its convenience, efficiency, and vast amount of information make it a powerful tool for knowledge acquisition and problem-solving. While we must remain vigilant about the reliability of the information we find, the internet remains an indispensable part of modern life.中文对照翻译:网络搜索在现代社会的普及在今天的数字时代,互联网已经成为我们日常生活中不可或缺的一部分,彻底改变了我们获取和传播信息的方式。
现在大多人使用互联网搜索答案英语作文Searching for Answers on the InternetHi there! My name is Emma and I'm 10 years old. Today I want to tell you all about how people use the internet to search for answers.The internet is this huge thing with websites and apps and all sorts of information. It's kind of like a really big library, but instead of books it has websites. And instead of being in a building, it's just out there in cyberspace!Whenever I have a question about something, the first thing I do is ask my parents or teachers. But sometimes they don't know the answer. That's when we go on the internet to search for it!There are special websites called "search engines" that let you type in what you're looking for. The biggest ones are Google, Yahoo, and Bing. My favorite is Google because it's really easy to use and gives good results.Let me give you an example of how it works. Let's say I'm wondering what the biggest ocean in the world is. I'd go to Google and type that into the search box. Then Google looksthrough basically the entire internet to find websites with that information.In just a few seconds, it shows me a bunch of results - website links that might have what I'm looking for. The first result says that the Pacific Ocean is the biggest. That seems right since I've heard of the Pacific before.But to make sure, I'll click on a few more of the results to see some other websites and information about ocean sizes. By looking at a few different sites, I can piece together a pretty good answer.It's amazing how quickly I can find that kind of fact and information on the internet. Can you imagine if I had to go to the library and look through book after book to try and find those couple sentences about ocean sizes? It would take hours instead of seconds!The internet is really useful for lots of other things too beyond just looking up facts. Let's say I'm working on a school project about Ancient Rome. I can search for things like:• "Ancient Rome facts for kids"• "Ancient Roman lifestyle"• "Ancient Roman leaders"• "Ancient Roman architecture"And I'll get websites, videos, photos, and more all about those topics related to my project. No more having to rely just on that one old book about Rome my library happens to have!Or let's say I need to find instructions for something hands-on like tying a knot or doing an arts and crafts project. I can search for a how-to video that will walk me through each step clearly. Way easier than trying to follow confusing written steps!The internet is also great if I get stuck on a math problem or don't understand something I'm learning in class. There are step-by-step explanations, videos, practice quizzes, and more to help me out. My dad says he wishes they had that stuff when he was a kid!Obviously not everything online is true though. That's why it's important to use trustworthy, factual websites like encyclopedias, educational sites, government sites, and so on. My teachers have given me tips like checking when the website was last updated and who created the information.It's also smart not to just go with the very first result, but to look at a few different sources before deciding if the informationseems accurate and reliable. I always triple check important facts before putting them in a school paper!So as you can see, the internet has become the go-to place for finding all kinds of information and answers in a fast, modern, and easy way. Pretty much anytime I or my friends or family have a question, checking online is the first step.Whether it's looking up quick facts, doing in-depth research, finding instructions, getting explanations, or anything else - the internet has a wealth of knowledge that's available literally at our fingertips!It makes learning about the world, staying curious, and getting smarter so much more accessible. Imagine how hard it would be without the internet to find answers to every random question that pops into our heads? We'd have to lug around endless encyclopedias everywhere we go!Some adults say they spent hours as kids looking for basic facts and information in libraries and books. But my generation is really lucky to have the internet. We can get answers in an instant with just a few taps or clicks.I know the internet didn't exist when my grandparents were young. In fact, my grandpa likes to brag that he survived collegewithout being able to search anything online. But I honestly don't know how he did it! Having the world's information at my fingertips through search engines seems totally normal and necessary to me.So that's the story on how most of us use the mighty internet to search for answers these days. Pretty cool, right? Let me know if you have any other questions! I'll be sure to look up the answers online.。
精选文档Python 练习题库By 郑红波2017-12-19一、填空题1. Python 标准库 math 顶用来计算平方根的函数是__________ 。
( sqrt)2.在 Python 中 __________表示空种类。
( None)3.列表、元组、字符串是 Python 的_________(有序?无序 ) 序列。
(有序)4.查察变量种类的 Python 内置函数是 ________________ 。
( type() )5.查察变量内存地点的 Python 内置函数是 _________________。
( id() )6. 表达式 [1, 2, 3]*3 的履行结果为______________________ 。
( [1, 2, 3, 1, 2, 3, 1, 2, 3] )7.list(map(str, [1, 2, 3])) 的履行结果为 _____________________ 。
([ ‘1’,‘2’,‘3’])8. 已知 x = 3,而且 id(x) 的返回值为 496103280 ,那么履行语句x += 6 以后,表达式id(x) ==496103280 的值为 ___________。
( False)9. 已知 x = 3 ,那么履行语句x *= 6 以后, x 的值为 ________________ 。
( 18)10. 表达式“ [3] in [1, 2, 3, 4] ”的值为 ________________ 。
( False)11. 假定列表对象 aList 的值为 [3, 4, 5, 6, 7, 9, 11, 13, 15, 17],那么切片 aList[3:7] 获取的值是______________________ 。
([6, 7, 9, 11] )12. 使用列表推导式生成包括10 个数字 5 的列表,语句能够写为_______________ 。
( [5 for i inrange(10)] )13. 假定有列表 a = ['name', 'age', 'sex'] 和 b = ['Dong', 38, 'Male'] ,请使用一个语句将这两个列表的内容变换为词典,而且以列表 a 中的元素为“键” ,以列表 b 中的元素为“值” ,这个语句能够写为 _____________________ 。
每个设备只能答题一次的代码 python.import hashlib.def check_answer(device_id, question_id):# 生成设备ID的唯一标识符。
device_hash =hashlib.sha256(device_id.encode()).hexdigest()。
# 检查设备ID是否已经答过该题目。
if check_answer_in_database(device_hash, question_id):return "该设备已经答过该题目"else:# 将设备ID和题目ID添加到数据库中。
add_answer_to_database(device_hash,question_id)。
return "可以答题"def check_answer_in_database(device_hash, question_id):# 在数据库中检查设备ID和题目ID是否存在。
# 返回True表示已经答过该题目,返回False表示未答过该题目。
# 这里只是示例,具体实现需要根据实际情况来。
return False.def add_answer_to_database(device_hash, question_id):# 将设备ID和题目ID添加到数据库中。
# 这里只是示例,具体实现需要根据实际情况来。
pass.在上述示例代码中,`check_answer`函数用于检查设备是否可以答题。
它接受设备ID和题目ID作为参数,并通过生成设备ID的唯一标识符来识别设备。
然后,它调用`check_answer_in_database`函数来检查设备ID和题目ID是否存在于数据库中。
如果已经答过该题目,则返回相应的提示信息;否则,调用`add_answer_to_database`函数将设备ID和题目ID添加到数据库中,并返回允许答题的提示信息。
python二级考试试题及答案1. 题目:以下哪个选项是Python中定义类的关键字?A. classB. functionC. structD. interface答案:A2. 题目:在Python中,以下哪个选项是正确的字符串格式化方法?A. "Hello, %s" % "world"B. "Hello, {0}".format("world")C. "Hello, {1}".format("world")D. "Hello, " + "world"答案:B3. 题目:Python中,以下哪个选项是正确的列表推导式?A. [x for x in range(10)]B. (x for x in range(10))C. [x if x % 2 == 0 for x in range(10)]D. [x for x in range(10) if x % 2 == 0]答案:D4. 题目:在Python中,以下哪个选项是正确的字典推导式?A. {x: x2 for x in range(5)}B. {x: x2 for x in range(5) if x % 2 == 0}C. {x: x2 for x in range(5) if x % 2 != 0}D. All of the above答案:D5. 题目:Python中,以下哪个选项是正确的文件操作方式?A. with open('file.txt', 'r') as file: file.read()B. file = open('file.txt', 'r')C. file = open('file.txt', 'w')D. file = open('file.txt', 'a')答案:A6. 题目:在Python中,以下哪个选项是正确的异常处理语句?A. try: pass except: passB. try: pass except Exception: passC. try: pass finally: passD. All of the above答案:D7. 题目:Python中,以下哪个选项是正确的装饰器定义方式?A. def decorator(func): return funcB. def decorator(func): def wrapper(): return func() return wrapperC. def decorator(func): def wrapper(*args, kwargs): return func(*args, kwargs) return wrapperD. All of the above答案:C8. 题目:在Python中,以下哪个选项是正确的生成器定义方式?A. def gen_func(): yield 1; yield 2B. def gen_func(): return (yield 1) + (yield 2)C. def gen_func(): yield from range(5)D. All of the above答案:D结束语:以上是Python二级考试的部分试题及答案,希望对您的学习和复习有所帮助。
2024年上海市英语初二上学期复习试卷与参考答案一、听力部分(本大题有20小题,每小题1分,共20分)1、What are the speakers mainly talking about?A. A school trip to the museumB. A new science projectC. An upcoming sports competitionAnswer: AExplanation: The conversation revolves around planning a school trip to the local museum, indicating that the primary topic of discussion is about a school trip, making option A the correct answer.2、How does the teacher suggest improving the student’s rea ding skills?A. By reading more fiction booksB. By practicing reading aloudC. By attending a reading clubAnswer: BExplanation: The teacher advises the student to read aloud more often to improve reading skills, as this practice can enhance fluency and comprehension, making option B the correct answer.3.You are listening to a conversation between two friends at a bookstore. The girl is looking for a book.Girl: Hey, do you think I should get this novel or the biography?Boy: Well, if you’re interested in contemporary literature, I’d say the novel is a must-read. But if you’re looking for something more informative, the biography might be a better choice.Question: What is the girl considering buying?A) A novelB) A biographyC) A contemporary literature collectionD) A non-fiction bookAnswer: B) A biographyExplanation: The girl is asking the boy if she should get a novel or a biography, indicating that she is considering these two options.4.You are listening to a weather report for the city of London.Weatherman: Good morning, everyone. The forecast for London today is partly cloudy with a high of 18 degrees Celsius. There is a 30% chance of scattered showers in the afternoon. The wind is expected to be light, coming from the north at 5 to 10 miles per hour.Question: What is the expected high temperature in London today?A) 15 degrees CelsiusB) 18 degrees CelsiusC) 20 degrees CelsiusD) 22 degrees CelsiusAnswer: B) 18 degrees CelsiusExplanation: The weatherman explicitly states that the expected high temperature in London today is 18 degrees Celsius.5.Listen to the dialogue and choose the best answer to complete the sentence.A. The boy is playing the guitar.B. The girl is singing a song.C. They are listening to the music together.Answer: BExpl anation: In the dialogue, the girl says, “Let’s sing a song together, Tom.” This indicates that the girl is singing a song, so the correct answer is B.6.Listen to the passage and answer the question.Question: What is the main topic of the passage?A. The importance of exercise.B. The benefits of reading books.C. The history of the Internet.Answer: AExplanation: The passage discusses how regular exercise can improve physical and mental health. It provides examples of different types of exercises and their benefits. Therefore, the main topic of the passage is the importance of exercise, making A the correct answer.7.You are listening to a conversation between a student and a teacher ina school office.Student: Excuse me, Mrs. Smith. I was wondering if I could have a makeup test for Math.Teacher: Sure, but you’ll need to provide a valid excuse and attend the makeup session next Wednesday after school.Question: What does the student need to do to take the makeup test?A) Provide a valid excuse and attend the makeup session.B) Pay a fee for the test.C) Study more for the next test.D) Miss the next class.Answer: A) Provide a valid excuse and attend the makeup session.解析:The teacher explicitly states that the student needs to provide a valid excuse and attend the makeup session to take the test, making option A the correct answer.8.Listen to a short dialogue between two friends at a bookstore.Person A: I can’t decide between this mystery novel and the fantasy book. What do you think?Person B: Well, if you like a fast-paced plot, the mystery novel is your choice. But if you enjoy a more imaginative story, the fantasy book would be better.Question: What advice does Person B give to Person A?A) To buy both books.B) To choose the mystery novel.C) To choose the fantasy book.D) To read both genres before deciding.Answer: C) To choose the fantasy book.解析:Person B recommends the fantasy book for someone who enjoys a more imaginative story, which corresponds to option C.9.Listen to the conversation and choose the best answer.A. The man is going to buy a new book.B. The woman is helping the man find a book.C. The man is looking for a map in the library.D. The woman is suggesting going to the bookstore.Answer: BExplanation: The woman says, “I think you should check out the reference section. There might be some helpful books there.” This indicates that she is helping the man find a book.10.Listen to the dialogue and answer the question.What is the main topic of the conversation?A. The weatherB. A school eventC. A family gatheringD. A book club meetingAnswer: BExplanation: The conversation discusses a school event, specifically asports game that is happening later in the day. The participants are planning to attend together.11.Listen to the dialogue and answer the question.A. What is the weather like today?B. Who is the man talking to?C. What is the woman going to do this afternoon?Answer: AExplanation: The woman says, “It’s sunny today, isn’t it?” This indicates that the weather is nice. Therefore, the correct answer is A.12.Listen to the conversation and complete the sentence.The man says, “I’m going to the library to study. Do you want to join me?”The woman replies, “__________.”A. I’m sorry, I can’t.B. That’s a g reat idea!C. I’m busy right now.Answer: BExplanation: The woman agrees to join the man by saying, “That’s a great idea!” This means she is interested in going to the library with him. Therefore, the correct answer is B.13.You are listening to a conversation between a student and a teacher ina school.Student: “Miss Green, when is the science fair this year?”Teacher: “The science fair is scheduled for October 15th, but the exact time hasn’t been finalized yet.”Question: When is the science fair scheduled for this year?A) October 15thB) October 16thC) October 14thD) October 17thAnswer: A) October 15thExplanation: The teacher explicitly mentions that the science fair is scheduled for October 15th.14.You are listening to a radio show about environmental issues.Host: “Today, we’re discussing the impact of single-use plastics on our oceans. According to our guest, Dr. Smith, what is the main concern regarding the pollution caused by single-use plastics?”Guest: “The main concern is the toxic substanc es that leach into the water when these plastics decompose, which can then be ingested by marine life.”Question: What is the main concern regarding the pollution caused by single-use plastics?A) The visual pollution they createB) The amount of plastic waste in landfillsC) The toxic substances leaching into the waterD) The damage to marine ecosystemsAnswer: C) The toxic substances leaching into the waterExplanation: The guest on the radio show specifically mentions that the concern is the toxic substances that leach into the water when single-use plastics decompose.15.You are listening to a conversation between two students, Alice and Bob, discussing their weekend plans.Alice: Hey Bob, what are you doing this weekend?Bob: Oh, I’m planning to go hiki ng with some friends. How about you? Alice: That sounds fun! I think I’ll just stay in and read a book.Bob: What kind of book are you reading?Alice: It’s a mystery novel. I love solving the clues and guessing the ending.Question: What is Alice planning to do this weekend?A) Go hikingB) Read a bookC) Go to a movieD) Visit a friendAnswer: B) Read a bookExplanation: In the conversation, Alice explicitly states, “I think I’ll just stay in and read a book,” which indicates her weekend plan.16.You are listening to a weather forecast for the upcoming week.Weatherman: Good morning, this is your weekly weather update. Here’s what we can expect for the next few days:Monday: Partly cloudy with a chance of rain in the afternoon. Tuesday: Rainy with a high of 60 degrees Fahrenheit.Wednesday: Clear and sunny with a high of 70 degrees Fahrenheit. Thursday: Increasing clouds with a chance of rain in the evening.Friday: Overcast with a high of 65 degrees Fahrenheit.Saturday: Rainy with a high of 58 degrees Fahrenheit.Sunday: Improving weather with a high of 68 degrees Fahrenheit.Question: Which day of the week is expected to have the highest temperature?A) MondayB) WednesdayC) ThursdayD) SundayAnswer: B) WednesdayExplanation: The weather forecast indicates that Wednesday will have a high of 70 degrees Fahrenheit, which is higher than any other day mentioned in the forecast.17.You are listening to a conversation between two friends, Sarah and Mike. They are talking about their weekend plans.Sarah: Hi, Mike! How are you doing?Mike: I’m doing well, Sarah. How about you?Sarah: I’m good, thanks. We’re thinking of going hiking this weekend. Do you want to join us?Mike: That sounds fun! When are you planning to go?Sarah: We’re thinking of leavin g on Saturday morning and returning on Sunday afternoon.Mike: That’s a great idea! I’ll be free on both days. How about meeting at the park at 8:00 a.m. on Saturday?Sarah: Sure, that works for me. We can bring some snacks and drinks too.Mike: Great! I’ll see you at the park on Saturday morning.Question: What are Sarah and Mike planning to do this weekend?Answer: They are planning to go hiking.Explanation: The conversation between Sarah and Mike indicates that they are discussing their weekend plans, specifically going hiking. They mention leaving on Saturday morning and returning on Sunday afternoon, confirming their plans to go hiking.18.Listen to a short dialogue between a teacher, Mr. Johnson, and a student, Emma.Mr. Johnson: Emma, how was your science project?Emma: It was really fun, Mr. Johnson. I learned a lot about the solar system.Mr. Johnson: That’s great to hear! Can you tell me what you found most interesting?Emma: Well, I was amazed by the fact that there are eight planets in our solar system, and each one has its own unique characteristics.Mr. Johnson: I see. Did you do any experiments to support your findings?Emma: Yes, I did. I conducted a small experiment to observe the effects of gravity on different objects.Mr. Johnson: That sounds interesting. What were your results?Emma: The experiment showed that heavier objects fell faster than lighter ones, which supports Newton’s law of universal gravitation.Mr. Johnson: Excellent! I’m glad to hear that you enjoyed the pro ject and learned something new.Question: What did Emma find most interesting about her science project? Answer: Emma found the fact that there are eight planets in our solar system and each one has its own unique characteristics most interesting.Explanation: In the dialogue, Emma mentions that she was amazed by the fact that there are eight planets in our solar system and each one has its own unique characteristics. This indicates that this aspect of the project was most interesting to her.19.Listen to the conversation between two friends at the school library and answer the question.Question: What book is the boy looking for?A. A science bookB. A history bookC. A mystery bookD. A fantasy bookAnswer: CExplanation: In the conversation, the boy mentions that he needs a book to help him with his homework on mysteries, so the correct answer is a mystery book.20.Listen to the short passage about the advantages of exercise and answer the question.Question: Which of the following is NOT mentioned as an advantage of exercise?A. Reduces stressB. Improves memoryC. Enhances sleep qualityD. Increases appetiteAnswer: DExplanation: In the passage, the advantages of exercise are discussed, including reducing stress, improving memory, and enhancing sleep quality. However, an increase in appetite is not mentioned as an advantage of exercise, making it the correct answer.二、阅读理解(30分)Reading ComprehensionPassage:In the small town of Willow Creek, there was once a bustling market every Saturday. The market was a hub of activity, where people from all over the townwould gather to buy fresh produce, homemade crafts, and enjoy the local food stalls. Among the vendors was a young girl named Lily, who sold handcrafted jewelry. Lily’s jewelry was uniqu e, often adorned with gemstones and beads she had found near the stream that ran through Willow Creek.One day, a famous fashion designer, Mr. Thompson, visited the market. He was captivated by Lily’s jewelry and decided to take a closer look. He approached Lily and complimented her on her craftsmanship. Impressed,Mr. Thompson asked if he could take some pictures of her jewelry to show his colleagues back in the city. Lily agreed, and soon after, she received a call from Mr. Thompson’s office offering her a contract to supply her jewelry to his fashion line.Lily’s business took off like a rocket. Her jewelry was featured in high-end fashion magazines and became a favorite among celebrities. The market in Willow Creek became even more popular, attracting tourists from far and wide. However, with her newfound success, Lily faced a new challenge: maintaining the quality of her products while keeping up with the high demand.Questions:1.What was the main reason Mr.Thompson was interested in Lily’s jewelry?A) It was mass-produced.B) It was sold in large quantities.C) It was unique and crafted with care.D) It was inexpensive and easily accessible.2.How did Lily’s business change after she started supplying jewelry toMr. Thompson’s fashion line?A) She had to close her stall at the market.B) She couldn’t keep up with the demand for her jewelry.C) She became a local celebrity and stopped making jewelry.D) She expanded her business but maintained the same quality.3.What was the challenge Lily faced with her increased success?A) She couldn’t find enough gemstones and beads.B) She had to decide whether to expand her business or not.C) She struggled to maintain the quality of her products.D) She had to find a new location for her market stall.Answers:1.C2.B3.C三、完型填空(15分)Section 3: Cloze TestRead the following passage and choose the best word for each blank from the options given.The world of technology has been 1 by incredible advancements in recent years. One of the most significant 2 has been the 3 of smartphones and tablets. These devices have revolutionized the way we 4 and access information. Here are someof the key 5 that have emerged as a result of this technological shift:1.A) affectedB) influencedC) transformedD) dominated2.A) innovationsB) discoveriesC) breakthroughsD) experiments3.A) inventionB) releaseC) usageD) popularity4.A) communicateB) travelC) liveD) learn5.A) benefitsB) challengesC) trendsD) discussionsAnswers:1.C) transformed2.A) innovations3.A) invention4.A) communicate5.A) benefits四、语法填空题(本大题有10小题,每小题1分,共10分)1、The cat is sitting in the 1 (sunshine) room.A. sunshineB. sunnyC. sunshinyD. sunshinyAnswer: B. sunnyExplanation: The correct answer is “sunny” because it is an adjective that describes the room as filled with sunlight. “Sunshine” is a noun and does not fit in the adjective slot required by the sentence structure.2、If it 2 (rain) tomorrow, we will have to cancel the picnic.A. rainsB. will rainC. rainedD. is rainedAnswer: A. rainsExplanation: The correct answer is “rains” because the sentence is in theconditional present tense, which is used to talk about future possibilities based on present conditions. The structure is “if + subject + verb in present simple, subject + will + verb in present simple.” “Will rain” is the correct form of the verb in this context.3.The students in our class,___________we have known for two years, are very friendly and helpful.A. whoB. thatC. whomD. whichAnswer: CExplanation: The correct answer is “whom” because it is used as the object of the preposition “in.” The relative pronoun “whom” refers back to “The students” and is used to connect the two clauses.4.If I___________more time, I would finish the project by tomorrow.A. hadB. haveC. have hadD. will haveAnswer: AExplanation: The correct answer is “had” because the se ntence is expressing a hypothetical situation in the past. The structure “If I had + past participle” is used to talk about a past situation that is not true.5.In the 5 morning, we 6 to the park for a walk.A. beautifulB. beautifullyC. beautyD. beautifullyAnswer: AExplanation: The correct answer is “beautiful” because it is an adjective that describes the morning. The sentence is talking about the quality of the morning, not about the way it is described or done, so “beautifully” (an adverb) and “beauty” (a noun) are not appropriate. “Beautifully” would be used if the sentence were talking about how the morning was described or the way it was done, which is not the case here.6.They 7 to the concert last night, but unfortunately, they 8 the tickets.A. were goingB. wentC. had goneD. have goneAnswer: BExplanation: The correct answer is “went” because the sentence is referring to a specific past event that occurred last night. “Went” is the simple past tense of the verb “go,” which is appropriate for describing a completed action in the past. The other options (“were going,” “had gone,” “have gone”) suggest actions in progress, past perfect, or present perfect respectively, which do not fit the context of the sentence.7.I have never seen a movie that is_______________interesting.A. soB. suchC. muchD. manyAnswer: AExplanation: The sentence is using the structure “so + adjective + a(n) + noun,” which is used to emphasize the degree of the adjective. The correct answer is “so” because it fits the structure perfectly.8.My sister’s birthday is coming up, and I think it would_______________a good idea to give her a surprise party.A. beB. isC. wasD. wereAnswer: AExplanation: The sentence is in the present tense, and the phrase “would + be” is used to express a suggestion or an opinion. Therefore, the correct answer is “be,” which is the base form of the verb “to be.”9.I have been to the Great Wall twice, but I still want to visit it again next year. ______, it’s such an amazing place.A. BesidesB. ThereforeC. HoweverD. OtherwiseAnswer: A. BesidesExplanation: The correct answer is “Besides” because it indicates an additional reason or point. “Therefore” is used to show a result, “However”is used to introduce a contrast, and “Otherwise” is used to suggest an alternative.10.She was_______in her exams this year, which was a big improvement from last year.A. failedB. passedC. successfulD. failed againAnswer: C. successfulExplanation: The correct answer is “successful” because it indicates a positive outcome. “Failed” and “failed again” suggest a negative outcome, while “passed” is a neutral term that does not convey the improvement mentioned in the sentence.五、简答题(本大题有5小题,每小题2分,共10分)1、What are the main differences between present simple and present continuous tenses?Answer:1.The present simple tense is used to describe habitual actions or general truths, while the present continuous tense is used to describe actions that are currently happening or in progress.2.The present simple tense does not use the auxiliary verb “be,” whereas the present continuous tense uses “am” for I/you/it, “is” for he/she/it, and “are” for we/you/they.3.The present simple tense does not use the word “now,” whereas the presentcontinuous tense often includes the adverb “now” to indicate the action isin the present moment.Explanation:The present simple tense is a regular tense used to express actions or states that are not limited to the present moment. It is also used for describing permanent situations, habits, general truths, and schedules. The present continuous tense, on the other hand, is used to talk about actions that are happening at the moment of speaking or are in the process of occurring. It often implies a temporary or ongoing nature of the action.2、How can you form negative and interrogative sentences in the past simple tense?Answer:1.To form a negative sentence in the past simple tense, you use the structure “didn’t + base form of the verb.”2.To form an interrogative sentence in the past simple tense, you place the auxiliary verb “did” before the subject, and then use the base form of the verb after the subject.Explanation:The past simple tense is used to describe actions or states that occurred ata specific time in the past. To form a negative sentence, you simply add “didn’t” before the subject, followed by the base form of the verb. For example, “She didn’t go to the party.” In an interrogative sentence, the auxiliary verb “did” is placed before the subject, which makes the sentence a yes/no question. Forexample, “Did she go to the party?” This structure is used to ask about past actions or events.3、What are the main differences between present simple and present continuous tenses in English?答案:The main differences between present simple and present continuous tenses are as follows:1.Present simple is used to describe habits, general truths, and repeated actions, while present continuous is used to describe actions that are currently happening or ongoing.2.Present simple does not indicate duration, whereas present continuous often implies a temporary or ongoing action with a specific time frame.3.Present simple is used for permanent situations, such as “I live in New York,” while present continuous can be used for temporary situations, like “I am living in a hotel while my house is being renovated.”解析:此题考查学生对现在简单时和现在进行时的区别的理解。
质数判断python代码-回复质数是指只能被1和自身整除的正整数。
在计算机编程中,判断一个数是否为质数是一个常见的问题。
本文将使用Python编程语言编写一个函数来判断质数,并解释其中的原理和步骤。
代码实现如下:pythondef is_prime(number):if number < 2:return Falsefor i in range(2, int(number 0.5) + 1):if number i == 0:return Falsereturn True这个函数接受一个整数作为参数,并返回一个布尔值,表示该数是否为质数。
现在我们一步一步来解释这个代码的工作原理。
首先,我们进行了一个简单的边界条件检查。
如果输入的数小于2,那么它不能被定义为质数,因为质数定义是大于1的整数。
因此,我们返回False来表示这个数不是质数。
接下来,我们开始使用循环迭代来检查该数是否可以被其他数整除。
我们从2开始,并一直迭代到输入数的平方根取整数部分加1为止。
为什么是平方根取整数部分加1?这是因为如果一个数可以被大于它平方根的数整除,那么必然也可以被小于等于它平方根的数整除。
在循环中,我们使用模运算来判断当前数是否能够整除输入的数。
如果能够整除,那么输入的数不是质数,我们返回False。
否则,我们继续迭代。
如果循环结束后都没有找到能整除的数,那么说明输入的数是质数,我们返回True来表示这个数是质数。
这样,我们就完成了一个用于判断质数的Python函数的编写。
质数判断的这个问题是一个经典的数论问题,利用循环和模运算可以高效解决。
本文中的Python代码可以用于判断任意给定的整数是否为质数,并在常规情况下快速给出答案。
然而,对于特别大的数,这个算法也会变得比较低效。
在实际应用中,可能需要使用更高效的质数判断算法。
但是对于一般的数值范围,本文中的代码已经足够满足需求。
另外,对于这个函数的优化还可以从多个角度进行。
Chapter 1Information Technology: Principles, Practices,and OpportunitiesTrue-False Questions1.Today, knowledge workers outnumber those employed in agriculture and manufacturingthroughout the developed world.Answer: True Difficulty: Easy Reference: p. 72.Effectiveness is a measure of the amount of work that can be accomplished with a certainlevel of effort.Answer: False Difficulty: Easy Reference: p. 83.Reengineering involves rethinking business practices, focusing on business processes, andintroducing incremental improvements to benefit both a business and its customers.Answer: False Difficulty: Medium Reference: p. 94.In the Information Age, work is accomplished through teamwork, interconnection, andshared information.Answer: True Difficulty: Easy Reference: pp. 9-105.To be successful in the Information Age, an organization must understand what IT can do toimprove its employees’ performance and how IT can enhance its products and services.Answer: True Difficulty: Medium Reference: p. 106. A customer’s order that consists of the name of the customer, the item(s) the customerpurchased, the quantity, and the price, is an example of information.Answer: False Difficulty: Hard Reference: p. 137. A program consists of a set of instructions that directs a computer to perform certain tasksand produce certain results.Answer: True Difficulty: Easy Reference: p. 178.MIS is a business information system designed to produce the information needed forsuccessful management of an unstructured problem, process, department, or business.Answer: False Difficulty: Hard Reference: p. 189. A typical business system includes not only people and departments but also procedures forconducting the business efficiently.Answer: True Difficulty: Medium Reference: p. 1910.America Online (AOL), Earthlink, Minitel, and the Internet, are all examples of publicnetworks.Answer: True Difficulty: Medium Reference: p. 1911.Data processing is the process of compiling detailed records of activities.Answer: False Difficulty: Easy Reference: p. 2312.The six functions of information technology are capturing, processing, generating,compiling, retrieving, and transmitting.Answer: False Difficulty: Easy Reference: p. 21rmation processing is a general term for the computer activity that entails processing anytype of information and transforming it into a different type of information.Answer: True Difficulty: Medium Reference: p. 2314.Word processing, image processing, and voice processing are all types of informationprocessing.Answer: True Difficulty: Medium Reference: p. 2415.The benefits of information technology include speed, consistency, effectiveness, andreliability.Answer: False Difficulty: Medium Reference: p. 2616.In general, computers are not very reliable.Answer: False Difficulty: Medium Reference: p. 2817.The process of recognizing a problem, identifying alternatives for solving it, and successfullyimplementing the chosen solution is called information management.Answer: False Difficulty: Medium Reference: p. 30rmation technology can be found in education, entertainment, manufacturing, journalism,and even agriculture.Answer: True Difficulty: Medium Reference: pp. 32-3319.One of the fundamental responsibilities of IT users, to be informed, states that users musttake responsibility for protecting data and information that are in a computer or transmittedover a network against intentional or accidental damage or loss.Answer: False Difficulty: Medium Reference: p. 3420.Knowing how IT is used in organizations, acquiring demonstrable IT skills, and being able tolist your IT accomplishments on your resume will give you a solid advantage when you arecompeting for a job.Answer: True Difficulty: Medium Reference: p. 34Multiple Choice Questions21. The __________________ is characterized by the simplification of work processes throughmechanization and automation.a.Agricultural Ageb.Industrial Agermation Aged.Machine Agee.None of the aboveAnswer: b Difficulty: Easy Reference: p. 722. Workers involved in the creation, distribution, and application of information are:a.data workers.rmation workers.c.knowledge workers.puter workers.e.technology workers.Answer: c Difficulty: Easy Reference: p. 723. The characteristics that distinguish the Information Age from previous ages include:a.an information-based society has arisen.b.businesses dependent on information technology to get their work done.c.Success in business is largely determined by the effectiveness with which informationtechnology is used.d.All of the above.e.Both a and b.Answer: d Difficulty: Medium Reference: p. 724. ______________ is the extent to which desirable results are achieved.a.Productivityb.Effectivenessc.Efficiencyd.Valuee.None of the aboveAnswer: b Difficulty: Medium Reference: p. 825. The activities that workers perform, the way they perform them, and the tools they use are:a.business processes.b.work processes.c.productivity.d.efficacy.e.effectiveness.Answer: b Difficulty: Easy Reference: p. 826. Separation of a work process into component tasks, with different workers specializing ineach of the tasks is called:a.teamwork.b.division of labor.c.reengineering.d.shared information.e.virtual team.Answer: b Difficulty: Medium Reference: p. 927. Interconnection means that:a.people work together to accomplish a team outcome rather than an individual job.b.individuals communicate regardless of distance to exchange ideas, experiences, andinsights.munication networks make information available to several people simultaneously,instantaneously, or whenever they need it.d.all of the above.e.none of the above.Answer: b Difficulty: Medium Reference: pp. 9-1028. In the Information Age, greater productivity is achieved through:a.teamwork.b.interconnection.c.division of labor.d.shared information.e.a, b, and d.Answer: e Difficulty: Easy Reference: pp. 9-1029. Products and services with embedded technology are sometimes called:a.technology-based.b.intelligence-based.c.knowledge-based.rmation-based.e.data-based.Answer: c Difficulty: Hard Reference: p. 1130. The pervasiveness of knowledge-based products, services, and activities in today’s societyhas:a.reshaped business processes to remove barriers that prohibit an organization fromproviding better products and services.b.separated a work process into component tasks, with different workers specializing ineach of the tasks.c.so thoroughly changed the way we act that we often take this technology for granted.d.Both a and b.e.Both a and c.Answer: c Difficulty: Hard Reference: p. 1231. ______________ refers to an organized, meaningful, and useful interpretation of data.a.Datarmationc.Knowledged.Databasee.None of the aboveAnswer: b Difficulty: Easy Reference: p. 1332. An awareness and understanding of a set of information and how that information can be putto the best use is:a.data.rmation.c.knowledge.d.intelligence.e.strategy.Answer: c Difficulty: Medium Reference: p. 1333. Which of the following is NOT a type of microcomputer?a.Notebook computerb.Tablet PCc.Personal digital assistantsd.Minicomputere.All of the above are microcomputers.Answer: d Difficulty: Medium Reference: p. 1434. An electronic system that can be instructed to accept, process, store, and present data andinformation is a(n):a.personal computer.b.notebook computer.c.tablet PC.d.personal digital assistant.e.All of the above.Answer: e Difficulty: Hard Reference: pp. 14-1535. ________________ are smaller versions of microcomputers that are designed for portability.a.Personal digital assistantsb.Minicomputersc.Notebook computersd.Palm PCse.Handheld computersAnswer: c Difficulty: Easy Reference: pp. 1536. PDAs and Palm PCs are often collectively referred to as:a.small computers.b.microcomputers.c.tablet PCs.d.handheld computers.e.portable computers.Answer: d Difficulty: Medium Reference: p. 1637. Software refers to:a.the instructions that manage the hardware.b.the computer and its associated equipment.c. a set of components that interact to accomplish a purpose.d.an interface between the computer and the network.e.None of the above.Answer: a Difficulty: Medium Reference: p. 1738. _________________ are generally larger, more expensive, and faster than midrangecomputers and permit the interconnection of a greater number of people.a.Microcomputersb.Minicomputersc.Mainframe computersd.Handheld computerse.Powerful computersAnswer: c Difficulty: Medium Reference: p. 1739. Which of the following statements about information system/management informationsystems (MIS) is NOT true?a.MIS is a business information system designed to produce the information needed forsuccessful management of a structured problem, process, department, or business.b.Data and information flow from one person or department to another via informationsystems.rmation systems serve all of the systems of a business by linking the differentcomponents together so that they work effectively toward the same goal.d.All of the above are true statements.e.Both a and c.Answer: d Difficulty: Hard Reference: p. 1940. _______________refers to the sending and receiving of data and information over a communications network.a.Hardwareb.Softwaremunicationd.Systeme.ProgramAnswer: c Difficulty: Easy Reference: p. 1941. A communications network consists of:a. a set of stations at different locations that are interconnected through a medium thatenables people to send and receive data and information.b.telephone wires and cables.c.hardware, programs, and information.d.all of the above.e.Both a and b.Answer: d Difficulty: Medium Reference: p. 1942. The transmission of data and information through a communications medium is:working.b.data communication.munications network.d.data retrieval.e.None of the above.Answer: b Difficulty: Medium Reference: p. 1943. Which of the following is NOT a public network?a.America Online (AOL)b.Earthlinkc.The Internetd.The World Wide Webe.All of the aboveAnswer: e Difficulty: Medium Reference: p. 19know-how consists of:technology44. Informationa.familiarity with the tools of IT, including the Internet.b.possession of the skills needed to use these tools.c.an understanding of when to use IT to solve a problem or create an opportunity.d.All of the above.e.Both a and c.Answer: d Difficulty: Medium Reference: pp. 19-2145. Which of the following is NOT a function of information technology?a.Captureb.Calculatec.Generationd.Storagee.All of the above are functions of information technology.Answer: b Difficulty: Medium Reference: p. 2146. Which of the following statements about information technology is NOT true?rmation technology’s great usefulness is as an aid in solving problems, unlockingcreativity, and making people more effective than they would be if they did not apply ITto their activities.b.The more “high-tech” the information technology you are considering, the moreimportant it is to consider the “high-touch” aspects of the matter—that is, “the peopleside.”c.Always fit people to information rather than fitting information to people.rmation technology performs six information-handling functions: capture,processing, generation, storage, retrieval, and transmission.e.The benefits of information technology are speed, consistency, precision, and reliability.Answer: c Difficulty: Hard Reference: p. 2147. According to the first principle of information technology, information technology’s greatusefulness is as an aid in:a.solving problems.b.unlocking creativity.c.making people more effective.d.All of the above.e.Both a and c.Answer: d Difficulty: Medium Reference: p. 2148. Which function of information technology is the process of compiling detailed records ofactivities?a.Capturingb.Retrievingc.Storingd.Processinge.GeneratingAnswer: a Difficulty: Easy Reference: p. 2149. Which function of information technology is the process of converting, analyzing,computing, and synthesizing all forms of data or information?a.Capturingb.Processingc.Retrievingd.Generatinge.TransmittingAnswer: b Difficulty: Easy Reference: p. 2350. Which function of information technology is the process of retaining information for futureuse?a.Capturingb.Processingc.Retrievingd.Generatinge.StoringAnswer: e Difficulty: Easy Reference: p. 2451. Data processing refers to:a.the process of retaining information for future use.b.the process of distributing information over a communications network.c.the process of handling data and its transformation into information.d.the process of compiling detailed records of activities.e.None of the above.Answer: c Difficulty: Easy Reference: p. 2352. Which of the following is NOT a type of information processing?a.Word processingb.Image processingc.Voice processingd.Video processinge.All of the above are types of information processing.Answer: e Difficulty: Medium Reference: p. 24refers to the creation of text-based documents, including reports, 53. _________________newsletters, and correspondence.a.Test processingb.Word processingc.Image processingd.Report processinge.Voice processingAnswer: b Difficulty: Medium Reference: p. 2454. Stored data and information are placed on a storage medium such as a(n):a.magnetic disk.b.magnetic tape.c.optical disk.d.All of the above.e.Both a and c.Answer: d Difficulty: Hard Reference: p. 2455. The benefits of information technology include:a.speed.b.consistency.c.effectiveness.d.All of the above.e.Both a and b.Answer: c Difficulty: Medium Reference: p. 2656. Which of the following is NOT a benefit of information technology?a.Speedb.Consistencyc.Effectivenessd.Precisione.ReliabilityAnswer: c Difficulty: Medium Reference: p. 2657. Which of the following is NOT a true statement?puters do everything in fractions of seconds.puters can detect minute differences that people cannot see.c.In general, computers are very reliable.puters excel at repeating actions consistently.e.All of the above are true statements.Answer: e Difficulty: Medium Reference: pp. 27-2858. Computers excel at:a.repeating actions consistently.b.managing the smallest differences, that is, in being precise.c.improving management skills of managersd.doing everything in fractions of seconds.e.a, b, and c.Answer: e Difficulty: Medium Reference: p. 2759. The illusion of reality created by a computer is called:a.super reality.b.pseudo reality.c.virtual reality.d.simulated reality.e.fake reality.Answer: c Difficulty: Medium Reference: p. 2860. The perceived difference between an existing condition and a desired condition is a(n):a.reality.b.situation.c.problem.d.solution.e.none of the above.Answer: c Difficulty: Medium Reference: p. 3061. The process of recognizing a problem, identifying alternatives, and successfullyimplementing the chosen solution is called:rmation management.b.knowledge management.c.problem solving.d.decision making.e.None of the above.Answer: c Difficulty: Medium Reference: p. 3062. Onlineeducation:a.eliminates the need to travel.b.is more cost-effective.c.makes learning more fun.d.Both a and c.e.None of the above.Answer: a Difficulty: Medium Reference: p. 3163. As companies seek to reduce the burden of travel for both customers and their ownemployees, a growing number are:a.developing information systems for customer relationship management.b.creating online learning systems to deliver product and service training.c.investing heavily in disaster recovery.d.Both a and b.e.Both b and c.Answer: b Difficulty: Hard Reference: p. 3164. At New York’s NASDAQ Exchange, stockbrokers:a.trade on the trading floor.b.do all their trading electronically.e information technology on the trading floor.d.Both a and c.e.None of the above.Answer: b Difficulty: Hard Reference: p. 3365. Information technology allows companies to reduce:a.workload.b.investments.c.paperwork.munication.e.Both b and c.Answer: c Difficulty: Medium Reference: p. 3266. Information technology cannot be found in:a.agriculture.b.shipping.c.manufacturing.cation.e.None of the above.Answer: e Difficulty: Medium Reference: p. 3367. Information technology can be found in:a.health and medicine.b.manufacturing.c.agriculture.d.All of the above.e.Both a and b.Answer: d Difficulty: Medium Reference: p. 3368. Electronic filing service allows the customers at H&R Block to:a.pay less taxes.b.receive refunds the same day they file their return.c.prepare tax returns without the help of the accountant.d.Both a and c.e.Both b and c.Answer: b Difficulty: Hard Reference: p. 3369. H&R Block was the first to:bine the IRS electronic filling process with its own Rapid Refund program.b.allow customers to file return electronically.c.allow customers to receive a refund the same day they file their return.d.Both a and b.e.Both a and c.Answer: e Difficulty: Hard Reference: p. 3370. Which of the following is NOT a fundamental responsibility of IT users?a.To be informedb.To produce knowledgec.To make proper use of ITd.To store informatione.Both b and dAnswer: e Difficulty: Medium Reference: p. 3471. The fundamental responsibilities of IT users are:a.to be informed.b.to make proper use of IT.c.to safeguard.d.All of the above.e.Both b and c.Answer: d Difficulty: Easy Reference: p. 3472. The fundamental assumption that states that users need to take responsibility for employingIT in desirable and ethical ways that help people and do not infringe on their privacy, rights, or well-being is:a.to be informed.b.to make proper use of IT.c.to be productive.d.to safeguard.e.to minimize damage.Answer: b Difficulty: Medium Reference: p. 3473. Which of the following statements about the responsibilities of IT users is NOT true?ers need to know how computers and networks can be applied in different situations.ers need to know the capabilities and limitations of IT.ers need to take responsibility for employing IT in desirable and ethical ways.d.It’s database administrator’s responsibility is to protect data and information that are in acomputer or transmitted over a network against intentional or accidental damage or loss.e.All of the above are true statements.Answer: d Difficulty: Medium Reference: p. 3474. In order to gain a solid advantage when you are competing for a job, you need to:a.know how IT is used in organizations.b.learn how to program a computer system.c.acquire demonstrable IT skills.d.Both a and c.e.Both b and c.Answer: d Difficulty: Medium Reference: p. 34emphasizes:75. Reengineeringa.rethinking of business activities.b.introducing incremental changes that benefit both a company’s customer and itsemployees.c.introducing radical changes that benefit both a company’s customer and its employees.d.Both a and b.e.Both a and c.Answer: e Difficulty: Medium Reference: p. 36Fill In the Blanks76. Knowledge workers are involved in the creation, distribution, and application of information.Difficulty: Easy Reference: p. 7information society, more people work at handling information than in the agriculture77. Ina(n)and manufacturing sectors combined.Difficulty: Easy Reference: p. 778. Business processes are collections of activities, often spanning several departments, that takeone or more kinds of input and create a result that is of value to a company’s customers.Difficulty: Medium Reference: p. 979. During the Industrial Age, greater productivity was attained by separating a work processinto component tasks, with different workers specializing in each of the tasks. This is calleddivision of labor.Difficulty: Easy Reference: p. 980. Embedded information technology means that IT is integrated with the other components ofproducts and services.Difficulty: Hard Reference: p. 1081. Information refers to an organized, meaningful, and useful interpretation of data.Difficulty: Easy Reference: p. 1382. Knowledge is the awareness and understanding of a set of information and how thatinformation can be put to the best use.Difficulty: Easy Reference: p. 1383. Small enough to be carried anywhere, and weighing less than a pound, personal digitalassistants (PDAs) are portable computers generally used as personal aids.Difficulty: Medium Reference: p. 1584. Hardware refers to the computer and its associated equipment.Difficulty: Easy Reference: p. 1785. A(n)system is a set of components that interact to accomplish a purpose.Difficulty: Easy Reference: p. 1886. One of the earliest business applications, data processing, focuses on taking data andtransforming them into information.Difficulty: Hard Reference: p. 2387. Generation refers to the process of organizing information into a useful form, whether asnumbers, text, sound, or visual image.Difficulty: Easy Reference: p. 2388. Transmission refers to the process of distributing information over a communicationsnetwork.Difficulty: Easy Reference: p. 2489. A computer system that can process multiple types of information simultaneously is amultimedia system.Difficulty: Medium Reference: p. 2490. The benefits of information technology include speed, consistency, precision, and reliability.Difficulty: Medium Reference: p. 2791. You can count on computers and communications networks to be available and properlyfunctioning when you need them—which is another kind of reliability, reliability of use.Difficulty: Hard Reference: p. 28problem is the perceived difference between an existing condition and a desired92. A(n)condition.Difficulty: Medium Reference: p. 3093. Problem solving is recognizing a problem, identifying alternatives for solving it, andsuccessfully implementing the chosen solution.Difficulty: Medium Reference: p. 3094. Today, Caterpillar Inc. test-drives its machines before it builds them—an advantage madepossible by virtual reality.Difficulty: Medium Reference: p. 2895. The three fundamental assumptions in using IT are to be informed, to make proper use ofIT, and to safeguard.Difficulty: Medium Reference: p. 34Essay Questions96. In the last 30 to 40 years, information and knowledge have been recognized as assets that asociety needs to develop and manage. With that realization, the Information Age began.Briefly discuss the six characteristics of the Information Age.The six characteristics of the Information Age are:1)An information-based society in which more people work at handling informationthan at agriculture and manufacturing combined has arisen.2)Businesses depend on information technology to get their work done.3)Work processes are being transformed to increase productivity.4)Information technology provides the means of rethink—that is, recreate orreengineer—conventional business processes.5)Success in business is largely determined by the effectiveness with whichinformation technology is used.6)Information technology is embedded in many products and services.97. How does use information technology to benefit both consumers and the U.S.Postal Service? Internet postage takes the hassle out of buying stamps and preparing your mail.With Internet postage, you can buy and print your own postage stamp right from yourdesktop computer. All that is required is software and a small, highly secure device (calledthe electronic vault), about the size of a 1-inch roll of traditional postage stamps that isconnected at the back of the desktop computer. Consumers can buy postage via a credit cardor use electronic funds transfer from their bank account, and then the postage is downloadedinto the electronic vault.The U.S. Postal Service benefits, too. The greater the number of individuals buying andusing electronic stamps, the shorter the lines at post-office stamp windows.98. Define data, information, and knowledge.Data are raw facts, figures, and details. Information refers to an organized, meaningful, anduseful interpretation of data, while knowledge is the awareness and understanding of a set ofinformation and how that information can be put to the best use.99. What are the three primary components of information technology?The three primary components of information technology are:1)Computers—electronic systems that can be instructed to accept, process, store, andpresent data and information.2)Communications networks—the interconnection of different locations through amedium that enables people to send and receive information.3)Know-how—the familiarity with the tools of IT, the skills needed to use these tools,and the understanding of when to use the.100. What is a computer? What are the different types of computers?A computer is an electronic system that can be instructed to accept, process, store, andpresent data and information. There are four types of computers:1)Microcomputers – a relatively compact type of computer, the most common of all,easily outsells all other types of computers annually for use in business and at home.2)Midrange computers – a type of computer used to interconnect people and large setsof information. More powerful than a microcomputer, the minicomputer is usuallydedicated to performing specific functions.3)Mainframes – a type of computer that is generally larger, more expensive, and fasterthan midrange computers and permits the interconnection of a greater number ofpeople.4)Supercomputers – a type of computer that is designed to solve problems consistingof long and difficult calculations. Supercomputer is the most powerful of allcomputers.101. What is a system? Is a business a system?A system is a set of components – people, computers, other businesses, government agencies– that interact to accomplish a purpose. A business is also a system. Its components –marketing, manufacturing, sales, research, shipping, accounting, and human resources – allwork together to create a product or service that benefits customers and therefore theemployees and shareholders of the organization.102. Discuss the six functions of information technology.The six functions of information technology are:1)Capture – the process of compiling detailed records of activities.2)Processing – the process of converting, analyzing, computing, and synthesizing allforms of data or information.3)Generation – the process of organizing information into a useful form, whether asnumbers, text, sound, or visual image.4)Storage – the computer process of retaining information for future use.5)Retrieval – the process by which a computer locates and copies stored data orinformation for further processing or for transmission to another user.6)Transmission – the computer process of distributing information over acommunications network.103. What is information processing? Discuss at least two types of information processing.Information processing is the transformation of any type of information into a different type of information. Types of information processing include the following:1)Word processing – The creation of text-based documents, including reports,newsletters, and correspondence.2)Image processing – Converting visual information into a format that can bemanaged within a computer system or transmitted between people and othercomputers.3)Voice processing – the transformation and transmission of spoken information.。