chi2011_refinding_email_camera_ready
- 格式:pdf
- 大小:417.99 KB
- 文档页数:10


R TO S -P X R O ST e c h n i c a l I n f o r m a t i o n13.03.19RTOS-PXROSRTOS Debugger forPXROS■Display of all PXROS System Resources ■Task Related Breakpoints■Dynamic Task Performance Measurement ■Download and Debug Tasks via Ethernet ■PXROS Specific Display of Real-Time Trace Listing■Statistic Evaluation and Graphic Display of Task Run Times■Statistic Evaluation and Graphic Display of Function Run Times■PRACTICE Functions for OS Data ■PXROS Related Pull-Down MenuThe TRACE32 system includes a configurable RTOS debugger to provide symbolic debugging in real time oper-ating systems. Our software package contains a ready-to-run configuration for the PXROS Real Time Operating System from HighTec.The PXROS awareness provides easy access to task lists and other kernel information, generates performance analysis data and enables you to do a most effective debugging with the TRACE32 systems on targets running PXROS.C166TriCoreR TOS Awareness on TR ACE32 with PXROSReal Time, Non-Intrusive Display of PXROS System ResourcesThe TRACE32 RTOS debugger for PXROS provides display functions to show the system resources of PXROS. All objects, such as tasks, mailboxes, messages etc. can be displayed and inspected. In addition, by using the pro-cessors capability of reading the targetmemory while the application is run-ning, or by using the emulators dual-port memory (if available), the display of all these regions can be viewed non-intrusively in real time. The tables are updated permanently (“On The Fly”), without affecting the application at all.Task Related BreakpointsAny breakpoint set in the TRACE32 debugger can be set dependent to a specific task. This means, that thebreakpoint will then only halt, if hit by the specified task. This allows taskrelated debugging even in shared code.Task list window, detailed task window andmailbox list windowBreakpoint list with task dependent breakpointsDynamic Task Performance MeasurementWhile PXROS is running, TRACE32 is capable of recurrently evaluating the current running task and collecting the results. The percentage, each task consumes of the system, is then dis-played graphically and updated perma-nently. The longer time you let the measurement run, the more exact are the results. This feature is available even without any hardware trace.Download and Debug Tasks via EthernetTRACE32 added a new functionality to its software, which allows connecting to the PXROS-HR target via Ethernet. Y ou can download tasks onto the run-ning target using TRACE32, and youcan debug those tasks individually over the Ethernet connections - which ena-bles you to debug your tasks even over the Internet.PXROS Specific Display of Real-Time Trace ListingThe data recorded in the real time trace buffer (if available) can be displayed and interpreted specific to the operat-ing system. The task switches are dis-played symbolically, either exclusively or in addition to other information.Statistic Evaluation and Graphic Display of Task Run TimesOut of the real time trace buffer (if avail-able), the analyzer can calculate statis-tic tables of task run times and task switches. A graphical diagram showswhich task was active at a specific time, giving a clear view of the behav-iour of the system.Statistics and flow of tasksTask Related Evaluation of Function Run TimesThe statistic and graphic evaluation of function calls and function run times (if available) can be done dependant to the actual running task. This is neces-sary, if different tasks call one single function at the same time, or if a task switch occurs in between the function.PRACTICE Functions for OS Data.The support includes extended PRAC-TICE functions for PXROS specific data, to be used in setup and test scripts. E.g. the function “task.con-fig(magic)” returns the address of the so called magic value, which corre-sponds to the id of the current execut-ing task.PXROS related pull-down menuBecause the menu bar of theTRACE32 user interface can be fully customized, you can create a new pull down menu, including operating sys-tem specific commands. We deliverPXROS support with an example for such specific menues, which provides fast access to the PXROS awareness features.Flow of functions, related to the calling tasksStatistics on function hierarchy, task relatedContactInternational RepresentativeArgentinaAnacom Eletronica Ltda.Mr. Rafael SoriceRua Nazareth, 807, BarcelonaBR-09551-200 São Caetano do Sul, SP Phone: +55 11 3422 4200FAX: +55 11 3422 4242EMAIL:******************.br AustraliaEmbedded Logic Solutions P/LMr. Ramzi KattanSuite 2, Level 3144 Marsden StreetParramatta NSW 2150Phone: +61 2 9687 1880FAX: +61 2 9687 1881EMAIL:*****************.au AustriaLauterbach GmbHAltlaufstr. 40D-85635 Höhenkirchen-Siegertsbrunn Phone: +49 8102 9876 190FAX: +49 8102 9876 187EMAIL:******************** BelgiumTritec Benelux B.V.Mr. Robbert de VoogtStationspark 550NL-3364 DA SliedrechtPhone: +31 184 41 41 31FAX: +31 184 42 36 11EMAIL:******************BrazilAnacom Eletronica Ltda.Mr. Rafael SoriceRua Nazareth, 807, BarcelonaBR-09551-200 São Caetano do Sul, SP Phone: +55 11 3422 4200FAX: +55 11 3422 4242EMAIL:******************.br CanadaLauterbach Inc.Mr. Udo Zoettler4 Mount Royal Ave.USA-Marlborough, MA 01752 Phone: +1 508 303 6812FAX: +1 508 303 6813EMAIL:********************** China BeijingLauterbach Technologies Co., LtdMr. Linglin HeBeijing OfficeA3,South Lishi Road, XiCheng District Beijing 100037, P.R. ChinaPhone: +86 10 68023502FAX: +86 10 68023523EMAIL:************************* China ShenzhenLauterbach Technologies Co., Ltd1406/E Xihaimingzhu BuildingNo.1 Taoyuan Road, Nanshan District Shenzhen 518052, P.R. China Phone: +86 755 8621 0671FAX: +86 755 8621 0675EMAIL:**************************China SuzhouLauterbach Technologies Co., Ltd Mr. Linglin HeHengyu Square, Rm 709No. 188, Xing Hai StreetSuzhou, 215021 P.R. of China Phone: +86 512 6265 8030FAX: +86 512 6265 8032EMAIL:********************** Czech. RepublicLauterbach GmbHAltlaufstr. 40D-85635 Höhenkirchen-Siegertsbrunn Phone: +49 8102 9876 130FAX: +49 8102 9876 187EMAIL:******************** DenmarkNohau Danmark A/SMr. Flemming JensenHørkær 26, Plan 4DK-2730 HerlevPhone: +45 44 52 16 50FAX: +45 44 52 26 55EMAIL:*************EgyptLauterbach GmbHAltlaufstr. 40D-85635 Höhenkirchen-Siegertsbrunn Phone: +49 8102 9876 130FAX: +49 8102 9876 187EMAIL:******************** FinlandNohau Solutions FinlandMr. Martti ViljainenTekniikantie 14FI-02150 EspooPhone: +358 40 546 0142FAX: +358 9 2517 8101EMAIL:**************FranceLauterbach S.A.R.L.Mr. Jean-Pierre ParadisoEuroparc - Le Hameau B135 Chemin Des BassinsF-94035 Créteil CedexPhone: +33 1 49 56 20 30FAX: +33 1 49 56 20 39EMAIL:********************** GermanyLauterbach GmbHSales Team GermanyAltlaufstr. 40D-85635 Höhenkirchen-Siegertsbrunn Phone: +49 8102 9876 190FAX: +49 8102 9876 187EMAIL:******************** GreeceLauterbach GmbHAltlaufstr. 40D-85635 Höhenkirchen-Siegertsbrunn Phone: +49 8102 9876 190FAX: +49 8102 9876 187EMAIL:******************** HungaryLauterbach GmbHAltlaufstr. 40D-85635 Höhenkirchen-Siegertsbrunn Phone: +49 8102 9876 190FAX: +49 8102 9876 187EMAIL:********************India-BangaloreElectro Systems Associates Pvt. Ltd. Mr. G. V. GurunathamS-606, World Trade CenterMalleswaram West, No.26/1, Dr. Rajkumar RoadIndia - Bangalore 560055Phone: +91 80 67648888FAX: +91 80 23475615EMAIL:************************* India-ChennaiElectro Systems Associates Pvt. Ltd. Mr. D. KannanNo.109 /59A , Ground FloorIV Avenue, Ashok NagarIndia - Chennai - 600 083 Tamilnadu Phone: +91 044-24715750FAX: ++91 44 24715750EMAIL:********************India-DelhiElectro Systems Associates Pvt. Ltd. Mr. R.K. BhandariNo. 705, 7th Floor, Laxmi Deep ShivajinagarIndia - Delhi - 110 092Phone: +91 11-22549351FAX:EMAIL:******************India-HyderabadElectro Systems Associates Pvt. Ltd. Mr. C.V.M. Sri Ram MurthyShop No. 14, "Global Enclave" Bhagyanagar Colony, Kukat pallyIndia - Hyderabad 500 072Phone: +91 40-23063346FAX: +91 40-23063346EMAIL:**********************India-KolkataElectro Systems Associates Pvt. Ltd. Mr. Arun RoyIndia - KolkataPhone: +91 98305 78843FAX:EMAIL:********************India-PuneElectro Systems Associates Pvt. Ltd. Mr. R K BhandariShriram Complex,1126/1, Model Colony ShivajinagarIndia - Pune - 411 016Phone: +91 20 - 30462035 / 25663FAX: +91 20-25677202EMAIL:*****************IrelandLauterbach Ltd.Mr. Richard Copeman11 Basepoint Enterprise Centre Stroudley RoadBasingstoke, Hants RG24 8UPPhone: 0044-118 328 3334FAX:EMAIL:**********************IsraelItec Ltd.Mr. Mauri GottliebP.O.Box 10002IL-Tel Aviv 61100Phone: +972 3 6491202FAX: +972 3 6497661EMAIL:***************.ilItalyLauterbach SrlMr. Maurizio MenegottoVia Enzo Ferrieri 12I-20153 MilanoPhone: +39 02 45490282FAX: +39 02 45490428EMAIL:**********************JapanLauterbach Japan, Ltd.Mr. Kenji Furukawa3-8-8 ShinyokohamaKouhoku-ku, Nisso 16th BuildingY okohama-shi, Japan 222-0033 Phone: +81 45 477 4511FAX: +81 45 477 4519EMAIL:******************.jp LuxembourgTritec Benelux B.V.Mr. Robbert de VoogtStationspark 550NL-3364 DA SliedrechtPhone: +31 184 41 41 31FAX: +31 184 42 36 11EMAIL:****************** MalaysiaFlash TechnologyMr. Teo Kian HockNo 61, # 04-15 Kaki Bukit Av 1Shun Li Industrial ParkSGP-Singapore 417943Phone: +65 6749 6168FAX: +65 6749 6138EMAIL:*******************.sg MexicoLauterbach Inc.Mr. Udo Zoettler4 Mount Royal Ave.USA-Marlborough, MA 01752 Phone: +1 508 303 6812FAX: +1 508 303 6813EMAIL:********************** NetherlandsTritec Benelux B.V.Mr. Robbert de VoogtStationspark 550NL-3364 DA SliedrechtPhone: +31 184 41 41 31FAX: +31 184 42 36 11EMAIL:******************New ZealandEmbedded Logic Solutions P/LMr. Ramzi KattanSuite 2, Level 3144 Marsden StreetParramatta NSW 2150Phone: +61 2 9687 1880FAX: +61 2 9687 1881EMAIL:*****************.au NorwayNohau Solutions ABMr. Jörgen NilssonDerbyvägen 6DSE-21235 MalmoePhone: +46 40 592 206FAX: +46-40 592 229EMAIL:*********************** PolandQUANTUM Sp. z o.o.Mr. Aleksander Bilul. Jeleniogorska 654-056 WroclawPhone: +48 71 362 6356FAX: +48 71 362 6357EMAIL:****************.pl PortugalCaptura Electronica,SCCLMr. Juan Martinezc/Duero, 40E-08031 BarcelonaPhone: +34 93 429 5730FAX: +34 93 407 0778EMAIL:******************* RomaniaLauterbach GmbHAltlaufstr. 40D-85635 Höhenkirchen-Siegertsbrunn Phone: +49 8102 9876 130FAX: +49 8102 9876 187EMAIL:********************RussiaRTSoftMr. Alexey IsaevNikitinskaya 3RUS-105037 MoscowPhone: +7 495 742 6828FAX: +7 495 742 6829EMAIL:****************.ruSingaporeFlash TechnologyMr. Teo Kian HockNo 61, # 04-15 Kaki Bukit Av 1Shun Li Industrial ParkSGP-Singapore 417943Phone: +65 6749 6168FAX: +65 6749 6138EMAIL:*******************.sgSouth Korea, PangyoHancom MDS Inc.Mr. Dongwook Jun3FL. Hancom Tower49, Daewangpangyo-ro 644, Bundang-gu Seongnam-si, Gyeonggi-do, 463-400, ROK Phone: +82-31-627-3000FAX: +82-31-627-3100EMAIL:*********************SpainCaptura Electronica,SCCLMr. Juan Martinezc/Duero, 40E-08031 BarcelonaPhone: +34 93 429 5730FAX: +34 93 407 0778EMAIL:*******************SwedenNohau Solutions ABMr. Jörgen NilssonDerbyvägen 6DSE-21235 MalmoePhone: +46 40 592 206FAX: +46 40 592 229EMAIL:*********************** SwitzerlandJDT Jberg DatenTechnikMr. Andreas JbergZimmereistrasse 2CH-5734 Reinach AGPhone: +41 62 7710 886FAX:EMAIL:********************TaiwanSuperlink Technology Corp.Mr. Sulin Huang3F-8,No.77,Sec.1,Xintaiwu Rd.,Xizhi District, New Taipei City 22101, Taiwan, R.O.C. Phone: +886 2 26983456FAX: +886 2 26983535EMAIL:**********************.tw TunisiaLauterbach Consulting S.A.R.L.Mr. Khaled JmalRoute El Ain Km 3.5TN-3062 SfaxPhone: +216-31361061FAX: +216-74611723EMAIL:********************** Turkey-1Tektronik Muh. ve Tic. A.S.Mr. Hakan Y avuzCyberPlaza B-Blok, 702BBilkent06800 AnkaraPhone: +90 312 437 3000FAX: +90 312 437 1616EMAIL:******************.tr Turkey-2G3TEK Embedded Technologies Ltd. Mr. Celal AygunIlkyerlesim Mah. 445.Sok. No: 4806370 Batikent/AnkaraPhone: +90 312 3324769FAX: +90 312 3324769EMAIL:**************UKLauterbach GmbHMr. Richard CopemanAltlaufstr. 40D-85635 Höhenkirchen-Siegertsbrunn Phone: +49 8102 9876 190FAX: +49 8102 9876 187EMAIL:******************** USA EastLauterbach Inc.Mr. Udo Zoettler4 Mount Royal Ave.USA-Marlborough, MA 01752 Phone: +1 508 303 6812FAX: +1 508 303 6813EMAIL:********************** USA WestLauterbach Inc.Mr. Bob Kupyn1111 Main Street, Suite 620USA-Vancouver, WA. 98660 Phone: +1 503 524 2222FAX: +1 503 524 2223EMAIL:************************Additional InformationLauterbach GmbHAltlaufstr. 40D-85635 Höhenkirchen-SiegertsbrunnTel. ++49 8102 9876-0 FAX -999*******************uterbach.deLauterbach Inc.4 Mount Royal Ave.Marlboro MA 01752Phone (508) 303 6812 FAX (508) 303 6813 ********************** Lauterbach Ltd.11 Basepoint Enterprise Ctre Stroudley Road Basingstoke, Hants RG24 8UPPhone ++44-1256-333-690 FAX -661**********************http:/Lauterbach S.A.R.L.135 Chemin Des BassinsF-94035 Créteil CedexPhone ++33-149-562-030FAX ++33-149-562-039**********************http:/uterbach.fr Lauterbach Japan, Ltd.3-9-5 Shinyokohama Kouhoku-kuY okohama-shi Japan 222-0033Phone ++81-45-477-4511 FAX -4519*********************uterbach.co.jp Lauterbach s.r.l.Lauterbach s.r.l.Via Enzo Ferrieri 12I-20153 MilanoPhone ++39 02 45490282FAX ++39 02 45490428*********************uterbach.itSuzhou Lauterbach Consulting Co.,Ltd.Room 1605, Xing Hai International Square No.200, Xing Hai StreetSuzhou, 215021 PR of ChinaPhone: 0086-512 6265 8030FAX: 0086-512 6265 8032*********************DisclaimerThe information presented is intended to give overview information only.Changes and technical enhancements or modifications can be made with-out notice.。

Radio ModulesRF-EMIP, RF-2400, RF-900 27th July 20212ImprintCopyright © 2021 Arnold & Richter Cine Technik GmbH & Co.Betriebs KG. All rights reserved. No parts of this documentmay be reproduced without prior written consent of Arnold &Richter Cine Technik GmbH & Co. Betriebs KG. Specificationsare subject to change without notice. Errors, omissions, andmodifications excepted.ARRI, ALEXA, AMIRA, Master Grip, LDS and LENS DATASYSTEM are trademarks or registered trademarks of Arnold& Richter Cine Technik GmbH & Co. Betriebs KG. All otherbrands or products are trademarks or registered trademarks oftheir respective holders and should be treated as such. Originalversion.For Further AssistanceARRI Cine + Video Geräte Gesellschaft m.b.H.Pottendorferstraße 23-25/3/1A-1120 Vienna AustriaE-mail: ****************Website: 3ScopeThis USER MANUAL applies to the following product:K2.0036599RF-900 Radio Module 900 MHz FHSSK2.0036598RF-2400 Radio Module 2400 MHz FHSSK2.0033702RF-EMIP Radio Module 2400 MHz DSSS4Revision historyVersion ID Order #Release Date0110005938K5.0040006F076402021-07-135DisclaimerBefore using the products described in this manual, be sure to read and understand all the respective instructions.The ARRI RF-EMIP, RF-2400, RF-900 Radio Modules is/are only available to commercial customers. By utilization, the customer agrees that the Radio Modules or other components of the system are deployed for commercial use only. Otherwise the customer must contact ARRI before utilization.While ARRI endeavors to enhance the quality, reliability and safety of their products, customers agree and acknowledge that the possibility of defects thereof cannot be eliminated entirely.To minimize the risk of damage to property or injury (including death) to persons arising from defects in the products, customers must incorporate sufficient safety measures in their work with the system and heed the stated canonic use.ARRI or its subsidiaries do not assume any responsibility for losses incurred due to improper handling or configuration of the Radio Modules or other system components.ARRI assumes no responsibility for any errors that may appearin this document. The information is subject to change without notice.For product specification changes after this manual was published, refer to the latest published ARRI data sheets or release notes, etc., for the most up-to-date specifications. Notall products and/or types are available in every country. Please check with an ARRI sales representative for availability and additional information.Neither ARRI nor its subsidiaries assume any liability for infringement of patents, copyrights or other intellectual property rights of third parties by or arising from the use of ARRI products or any other liability arising from the use of such products. No license, express, implied or otherwise, is granted under any patents, copyrights or other intellectual property right of ARRI or others.ARRI or its subsidiaries expressly exclude any liability, warranty, demand or other obligation for any claim, representation, cause, action, or whatsoever, express or implied, whether in contract or not, including negligence, or incorporated in terms and conditions, whether by statue, law or otherwise. In no event shall ARRI6or its subsidiaries be liable for or have a remedy for recoveryof any special, direct, indirect, incidental, or consequentialdamages, including, but not limited to lost profits, lost savings,lost revenues or economic loss of any kind or for any claim bya third party, downtime, good-will, damage to or replacement ofequipment or property, any cost or recovery of any material orgoods associated with the assembly or use of our products, orany other damages or injury of the persons and so on or underany other legal theory.In the event that one or all of the foregoing clauses are notallowed by applicable law, the fullest extent permissible clausesby applicable law are validated.How to Use this Manual 71How to Use this ManualThis manual describes the necessary information for using theproduct.For further details, refer tothe ARRI website at /radio-modules For Tech Tips, please visit the ARRI Youtube Channel at https:///user/ar-richannel:The appendix at the back of the manual contains useful reference material including technical data, connector pin-out diagrams and dimensional drawings.Additional InformationFor useful information in addition to this user manual please have a look at the ARRI Learn & Help section on the ARRI website.Strengthen Your Knowledge and Get TrainedThe ARRI Academy courses provide unrivalled insights into the full possibilities of working with ARRI camera systems, lenses,lights and accessories.To learn more, please visit /academy .8Table of ContentsTable of Contents1How to Use this Manual (7)2For Your Safety (9)3Audience and intended use (11)4Scope of Delivery and Warranty (12)5Introduction (13)6Layout (15)7Radio types (18)8Compatibility (20)9Appendix (23)9.1Antenna connector (23)9.2Specifications (23)9.3Dimensions and weight (25)9.4Part numbers (27)9.5Glossary (28)9.6Service Contacts (29)9.7International declarations (31)2For Your SafetyBefore use, please ensure that all users read, understand, andfollow the instructions comprehensively in this document.Risk levels and alert symbolsSafety warnings, safety alert symbols, and signal words in theseinstructions indicate different risk levels:Note: Provides additional information to clarify or simplify aprocedure.Vital PrecautionsGeneral precautionsUse only the tools, materials and procedures recommended in this document. Unplug all cables during transport.Do not store the Radio Modules in places where it/they may be subject to temperature extremes, direct sunlight, high humidity, severe vibration, or strong magnetic fields.Audience and intended use11 3Audience and intended useThe Radio Modules is solely and exclusively for use onprofessional camera setups.12Scope of Delivery and Warranty 4Scope of Delivery and WarrantyDeliveryOn delivery, please check that the package and content areintact. Never accept a damaged or incomplete delivery. Acomplete delivery includes:Radio ModuleInstruction manualOriginal packagingWarrantyFor scope of warranty, please ask your local ARRI ServicePartner. ARRI is not liable for consequences from inadequateshipment, improper use, or third-party products.5IntroductionWith the introduction of the Hi-5 Hand Unit ARRI offers threedifferent exchangeable radio modules for various shootingconditions and regions:RF-EMIP Radio Module 2400 MHz DSSSRF-2400 Radio Module 2400 MHz FHSSRF-900 Radio Module 900 MHz FHSSMain featuresRF-EMIP Radio Module:White-coded radio moduleCertified regions: worldwideFixed radio channels (14 channels)Compatible with existing ARRI hand units, cameras, motorcontrollers and the cforce mini RF motor containing ARRI'swhite-coded radio moduleNetwork mode: can pair with up to three hand units forsplit focus, iris and zoom operations to one camera/motorcontrollerRF-2400 Radio Module:Certified regions: worldwide100 channels (= defined hopping schemes)Its frequency hopping transmission method ensures astrong radio link with exceptionally good interferenceimmunity.RF-900 Radio Module:Long-Range SolutionCertified regions: USA and Canada100 channels (= defined hopping schemes)Its frequency hopping transmission method ensures astrong radio link with exceptionally good interferenceimmunity.Network mode: can pair with up to three hand units for splitfocus, iris and zoom operations6LayoutRF-900 Radio Module 900 MHz FHSSRF-2400 Radio Module 2400 MHz FHSSRF-EMIP Radio Module 2400 MHz DSSS7Radio typesRF-EMIP Radio ModuleA white-colored ring at the base of the antenna socket identifiesthe white-coded radio module. There are 14 channels to choosefrom:Channel Frequency ZigBee IEEE802.15.4 Channel0 2.410 GHz121 2.415 GHz132 2.430 GHz163 2.435 GHz174 2.450 GHz205 2.455 GHz216 2.470 GHz247 2.475 GHz258 2.420 GHz149 2.425 GHz1510 2.440 GHz1811 2.445 GHz1912 2.460 GHz2213 2.465 GHz23RF-2400 Radio ModuleA or orange-colored ring at the base of the antenna socketidentifies the RF-2400 radio module.RF-900 Radio ModuleAn grey-colored ring at the base of the antenna socket identifies the RF-900 radio module.ATTENTIONPlease ensure that the region is configured correctly, as it may be illegal to use the RF-EMIP, RF-2400, RF-900 in a region other than specified in the setting. All settings are compliant to FCC and IC regulations.20Compatibility8CompatibilityThe RF-EMIP, RF-2400 and RF-900 Radio Modules interface withthe Hi-5 Hand Unit and the Radio Interface Adapter RIA-1.ATTENTIONWhen removing the radio modules from the hosting units (Hi-5Hand Unit, Radio Interface Adapter RIA-1), please check thetemperature of the radio modules first. If they are hot, pleasewait until they have cooled down.Radio CompatibilityThe RF-EMIP is compatible with all devices which have a built-in EMIP100, EMIP200, EMIP300, EMIP400 or EMIP400s white-coded radio module as follows:Sample Configuration:Compatibilities with White-coded Radio-integrated DevicesCompatibilityto cameras–ALEXA Mini–ALEXA Mini LF–ALEXA Plus cameras (ALEXA LF, Plus,XT, SXT, 65)Compatibility to hand units(in Network Mode)–WCU-4–SXU-1Compatibility tomotor controller–UMC-4–AMC-1–SMC-1–EMC-1 Compatibility tolens motor–cforce mini RF9Appendix9.1Antenna connectorThe radio connection is established via the antenna mountedto the antenna connector. The radio module inside could bedamaged by electrostatic discharge via the open connector. Werecommend using the originally supplied antenna only.9.2SpecificationsElectrical/General DataRF-EMIP Radio ModuleSupported Frequency 2.400 - 2.4835 GHzChannel Spacing 5 MHzBand ISM 2400 MHzModulation Type Direct Sequence Spread SpectrumOperating Mode Point-to-MultipointTransmit Power Dep. on regions between 8.9 - 70.8 mWRF-2400 Radio ModuleSupported Frequency 2.400 - 2.4835 GHzBand ISM 2400 MHzModulation Type Frequency Hopping Spread SpectrumOperating Mode Point-to-pointTransmit Power100mWRF-900 Radio ModuleSupported Frequency902 - 928 MHzBand ISM 900 MHzModulation Type Frequency Hopping Spread Spectrum Operating Mode Point-to-MultipointTransmit Power Standard Mode: 100 mWHi-Power Mode: 1 W ConnectorInterface10pin IRISOEnvironmental-20 to +50°C (-4° to +122° F) Operating temperaturerangePower ConsumptionPower consumption depends on the different radio modules that are used. Using the Hi-5 hand unit with one of the modules results in different power requirements:RF-EMIP**************RF-2400**************RF-900@100mW:**************RF-900@1W:**********9.3Dimensions and weightRF-EMIP Radio ModuleWeight of the RF-EMIP Radio Module: 52g/1,83oz (includingantenna)RF-2400 Radio ModuleWeight of the RF-2400 Radio Module: 52g/1,83oz (includingantenna)RF-900 Radio ModuleDimensions:Weight of the RF-900 Radio Module: 55g/1,94oz (including antenna)9.4Part numbersRF-900 Radio ModuleK2.0036599RF-900 Radio Module 900 MHz FHSSIncludes:K2.00414372db 900Mhz Antenna RPSMARF-2400 Radio ModuleK2.0036598RF-2400 Radio Module 2400 MHz FHSSIncludes:K2.0002007Outdoor Antenna (straight)RF-EMIP Radio ModuleK2.0033702RF-EMIP Radio Module 2400 MHz DSSSIncludes:K2.0002007Outdoor Antenna (straight)Radio Module SetsKK.0039986RF-900 Radio Module 900 MHz FHSS SetKK.0039984RF-2400 Radio Module 2400 MHz FHSS SetKK.0039985RF-EMIP Module 2400 MHz DSSS Radio Set9.5GlossaryDSSS Direct Sequence Spread SpectrumFHSS Frequency Hopping Spread SpectrumISM Industrial Scientific MedicalPoint-to-Multi-point In point-to-multipoint networks one device can connect with multiple devices at the same time. Also known as Network mode where multiple devices can operate in the same radio connec-tion for splitting focus, iris and zoom control.Point-to-Point In point-to-point networks one device can con-nect with another single device at the sametime.ZigBEE ZigBee is a wireless communication technologydesigned based on IEEE 802.15.4. It is one ofthe most economical, low-power consuming da-ta transfer technology that operates with a sim-ple networking protocol.IEEE Institute of Electrical and Electronics Engineers9.6Service ContactsArnold & Richter Cine Technik GmbH & Co. Betriebs KG Herbert-Bayer-Str. 1080807 MunichGermany+49 89 3809 2121Business hours:Mo. - Fr. 09:00 - 17:00 (CET)***************ARRI CT Limited / London 2 Highbridge, Oxford Road UB8 1LX UxbridgeUnited Kingdom+44 1895 457 000 Business hours:Mo. - Thu. 09:00 - 17:30 Fr. 09:00 - 17:00 (GMT)*******************ARRI Inc. / West Coast3700 Vanowen StreetCA 91505 BurbankUSA+1 818 841 7070Business hours:Mo. - Fr. 09:00 am- 05:00 pm (PT) ****************ARRI Inc. / East Coast617 Route 303NY 10913 BlauveltUSA+1 845 353 1400Business hours:Mo. - Fr. 08:00 am - 05:30 pm (EST) ****************ARRI Canada Limited1200 Aerowood Drive, Unit 29ON L4W 2S7 Mississauga Canada+1 416 255 3335Business hours:Mo. - Fr. 08:30 am - 05:00 pm (EDT) ****************ARRI Australia Pty LtdLevel 1, Unit 1, 706 Mowbray Road Lane CoveNSW 2066 SydneyAustralia+61 2 9855 43050Business hours:Mo. - Fr. 08:00 am - 05:00 pm (AEST)****************.auARRI China (Beijing) Co. Ltd. Chaowai SOHO Tower C, 6/F, 0628/0656Chaowai Dajie Yi 6BeijingChina+86 10 5900 9680Business hours:Mo. - Fr. 09:00 am - 06:00 pm (CST) ***************ARRI ASIA Limited41/F One Kowloon, 1 WangYuen Street Kowloon BayHong KongP. R. China+852 2537 4266Business hours:Mo. - Fr. 10:00 am - 06:30 pm (HKT) ***************ARRI Brasil LtdaAvenida Ibirapuera 2907 – Cj. 421, Indianópolis04029-200 São PauloBrazil+55 1150419450Bars-Pro Ltd.Distributor4-Ya Magistralnaya Ulitsa, 11/2 123007 MoscowRussia+7 4995860299Business hours:Mo. - Fr. 09:00 am - 05:30 pm (BRT) *******************Business hours:Mo. - Sat. 10:00 - 18:00 (MSK) ****************CINEOM Broadcast DMCC.Unit No. 2109, Jumeirah Bay Tower X2 Cluster XJumeirah Lakes TowersP.O Box 414659Dubai, UAE+971 (0) 45570477Business hours:Sa. - Th. 10:00 am- 06:00 pm*************************CINEOM Broadcast India Pvt. Ltd. C-4, Goldline Business CentreLink Rd. Malad West400 064 MumbaiIndia+91 (0)22 42 10 9000Business hours:Mo. - Sat. 10:00 am - 06:00 pm (IST) ***************************LINKA Ithalat Ihracat ve Diş Tic. DistributorHalide Edip Adıvar Mah. Darülaceze Cad.No:3 Akın Plaza Kat:5 95-96 34381 Şişli, IstanbulTurkey+90 2123584520Business hours:Mo. - Fr. 09:00 - 18:00 (EET)*********************.tr9.7International declarationsEU-Declaration of ConformityProduct Description: RF module 2.4 GHz: RF-EMIP / RF-2400The designated product conforms with the specifications of thefollowing European directives:1Directive 2014/53/EU of the European Parliament and the Council of 16 April 2014 on the harmonization of the lawsof the Member States relating to the making available onthe market of radio equipment and repealing Directive - OJL 153, 22.5.2014, S. 62–106.2Directive 2011/65/EU of the European Parliament andthe Council of 8 June 2011 on the restriction of the use ofcertain hazardous substances in electrical and electronicequipment - OJ L 174, 1.7.2011, S. 88–110.The compliance with the requirements of the European Directiveswas proved by the application of the following standards:Essential requirements regarding No 1Art. 3.1 a following 2014/35/EU: EN 62479:2010; EN IEC62368-1:2020 + A11:2020Art. 3.1 b following 2014/30/EU: EN 301 489-1 V2.2.3; EN301 489-17 V3.2.2Art. 3.2: EN 300 328 V2.1.1; EN 300 328 V2.2.2Essential requirements regarding No 2EN 50581:2012;To evaluate the respective information we used:http://ec.europa.eu/growth/single-market/european-standards/harmonised-standards/index_en.htmFCC Class A StatementNote: This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipmentis operated in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference in which case the user will be required to correct the interference at his own expense.Caution: changes or modifications to the product not expressly approved by the party responsible for compliance could void the user's authority to operate the equipment.Industry Canada Compliance StatementThis device complies with RSS-210 of Industry Canada. Operation is subject to the following two conditions:(1) This device may not cause interference.(2) This device must accept any interference, including interference that may cause undesired operation of this device. Cet appareil est conforme à CNR-210 d'Industrie Canada.L’exploitation est autorisée aux deux conditions suivantes:(1) L’appareil ne doit pas produire de brouillage.(2) L’appareil doit accepter tout brouillage radioélectrique subi,même si le brouillage est susceptible d’en compromettre le fonctionnement.Japan MIC StatementComplies with Ministry of Internal Affairs and Communications notification Article 88, Annex 43.Radio ModulesThe RF-EMIP Radio Module contains the following radio module: FCC ID: Y7N-EMIP400IC ID: 9482A-EMIP400CMIT ID: 2017DJ7863C(M)MIC ID: 020-180030NCC: CCAH18LP0660T0KC: R-CRM-ARg-EMIP400EMIP400s: ETA:1385/2018/ERLOThe RF-2400 Radio Module contains the following radio module: FCC ID: NS9P2400IC ID: 3143A-P2400R210-114971 (Japan)The RF-900 Radio Module contains the following radio module: IC ID: 3143A-13P900FCC ID: NS913P900The RF-900 Radio Module has been tested and complies with the applicable limit values for protection against high-frequency energy (RF energy)。

FANTASTIC COLORFUL UNDERWATER PICTURESSeaLife high definition cameras: All models can be used above and below water comfortably and deliver great images.newMICRO 2.0 (64GB & 32GB) MICRO HD 1.0 (16GB)Image Sensor 16-Megapixel SONY CMOS 14-Megapixel CMOS Movie Resolution HD/1080p @ 60 fps or 1296p @ 30 fps HD/1080p @ 30fps or 720p @ 60 fps Memory 64GB (25000 images/12hrs video) 16GB (4000+ images/3hrs+ video) 32GB (12000+ images/6hrs+ vidéo) Focus Range 30 cm to infinity 30 cm to infinity Download/share WIFI via Sealife Micro Cam App or via cable Cable LCD 2.4“ TFT LCD color display 2.4“ TFT LCD color display Field of View 130° Super Wide, 100° Wide, and 80° Standard 140° Super Wide, 130° Wide, and 90° Standard Depth Individually depth tested to 60 m Individually depth tested to 60 m Dimensions: 279g & 10.7 x 5.3 x 7.4cm 266g & 10.7 x 5.3 x 7.4cm Battery Lithium rechargeable (3.7V, 2350 mAh) Lithium rechargeable (3.7V, 2400 mAh) Battery life 3+ hours (Approximately 1000+ images/ 3+ hours video)TECHNICAL CHARACTERISTICSMICRO HD 1.0 - 16GBMICRO 2.0 - 32GB WIFI & 64GB - WIFIThe MICRO HD range of cameras are permanently sealed and absolutely flood-proof. Easy to use, with nothing to maintain.With rich, colourful still images, full 1080p HD video, instant focusing, and a built-in 130-degree Fisheye Lens, the Micro 2.0 has everything needed to capture and share your underwater encounters down to 60 meters.The Micro 2.0 includes two shooting modes: time lapse shooting and upside-down shooting and is available in two capacities: 32GB with WiFi, or 64GB with WiFi, connecting wirelessly to smartphones and tablets with the SeaLife Micro Cam app.UNDERWATER CAMERA SETSMICRO 2.0 1500 PROThe SeaLife Micro 2.0 1500 Pro set includes thepermanently sealed Micro 2.0 32GB WiFi camera,Flex-Connect Micro Tray, Grip, Flex Arm, SeaDragon 1500 Lumen Light and travel case.MICRO 2.0 2500 PROThe SeaLife Micro 2.0 2500 Pro set includes thepermanently sealed Micro 2.0 64GB WiFi camera,Flex-Connect Micro Tray, Grip, Flex Arm, SeaDragon 2500 Lumen Light and travel case.SEA DRAGON PHOTO-VIDEO LIGHTS 2500, 2100, 2000 & 1500• One button control for easy operation - one button to power light on/off, select brightness and switch beam angle • Depth rated to 60 meters - Guaranteed• Easy to expand with Flex-Connect™ trays, grips and Flex Arms, handle, Y-S, ball joint, cold shoe and other accessories • Quick-release button to detach light and aim in crevices and hard to reach areas • Corrosion-proof metal light head for heat dispersion and durability• Waterproof battery compartment - even if the O-ring seal fails, the battery compartment is isolated so water cannot reach the internal electronics • Universal mounting screw fits SeaLife and other brands of underwater cameras w/ standard ¼-20 tripod mountSEA DRAGON 2000Shown with DC1400SEA DRAGON 2100Shown with MICRO HD 1.0SEA DRAGON 2500Shown with MICRO HD 1.0Brightness (lumens) 2500 2100 2000 1500Beam angle 120° 100 ° or 15 ° (spot) 100° 120°Effective Range 1.2m 1.2m 1.2m 1.0m Color Rendering Index 90 72 72 80Bulb COB LED 7 x 3W LED (CREE XML2 LEDs) 6 x 3W LED (CREE XML LED) COB LED Bulb Life: 35 000 hours 35 000 hours 35 000 hours 35 000 hours Battery (included) L-Ion 7.4V, 3400 mAh, 25Wh L-Ion 7.4V, 3400 mAh, 25Wh L-Ion 7.4V, 3100 mAh, 23Wh L-Ion 7.4V, 3400 mAh, 25Wh Battery Run Time: 60 minutes at full power/120 minutes at half power/240 minutes at quarter power 70 mins (full power) Dimensions 12.2 x 5.6 x 9.7 cm (head only) 13 x 5.6 x 9.7 cm (head only) 22 x 24 x 6 cm (Set) 12.2 x 5.6 x 9.7 cm (head only) Weight 371g (head only) 450g (head only) 652g (Set) 371g (head only)SEA DRAGON 1500Shown with MICRO 2.0TECHNICAL CHARACTERISTICSDIGITAL SEA DRAGON FLASHR educes backscatter and produces bright, deep colors in underwater photos. Adjustable or Auto Mode brightness for optimal exposure. Underwater range: up to 2,5m. Includes snap-on diffuser, standard tray, grip and case. Not compatible with the MICRO range.SEA DRAGON MINI 600Apowerful 600 lumen LED using the new CREE XM-L@ LED for multiple applications down to 100m, 75° wide beam angle, delivered with two CR123 lithium batteries giving 150 minutes burn time at 40% power and 60 minutes at 100% power, also compatible with 18650 Li 3.7v battery giving 250 minutes burn time at 40% power and 100 minutes at 100% power, easy on/off light head twist control, includes GoPro° camera mount, universal Y-S adapter and lanyard clip. The Mini 600 is now equipped with an over-pressure valve to release battery off-gassing.Dimensions : 96.5g (without batteries) & 3.4cm (diameter) x 13.5 cmSEA DRAGON MINI 650The compact and ergonomic Sea Dragon Mini 650 Flood provides 650 lumens across a wide 120-degree beam that is ideal for brightening your photo or video subject, or illuminating a large area on your dive. The Sea Dragon Mini 650 Spot has a concentrated 15-degree beam (10-degrees underwater) that is ideal for pointing out sea creatures and covering long distances to illuminate your dive.The light features single button operation and is powered by two CR123 batteries (included) or an optional rechargeable lithium ion battery (Tenergy 18650 2600mAh 3.7v) delivering up to 100 minutes of burn time at full power. Depth tested to 100 meters. Dimensions : 189g (without batteries) & 4.1cm (diameter) x 15.9 cm.Guide Number20m full power/1.5m low powerCoverage Angle 80° horizontal x 60° vertical (100° with included diffuser)Color Temperature 5700 degrees KelvinPower Source 4 AA batteries (NiMH recommended)Battery Life 150 flashesDimensions509g (with batteries) & 12.7 x 11.4 x 6.4 cmQuickly and easily expand your camera set with flex-connect accessories - add grips, Flex Arms, trays and more with just a “click!” flex-connect allows you to transform your camera set from compact to full-featured in just seconds, providing a quick way to adjust to any diving environment. To assemble and disassemble just in seconds.MICRO/DUAL TRAYSChoose between two tray sizes and build your ideal system. For maximum illumination and stability.Sea Dragon 2000flex-connect Flex Armflex-connect GripFisheye Wide Angle Lensflex-connect Dual TrayDC1400 Cameraflex-connect Flex ArmSea Dragon Flash‘Flex-Connect’ is a range of Sealife Accessories. The trays, mounts and flex arms allow you to easily expand your camera set. Modular for travel and they quickly and easily lock into place.Flex Arms extend lights with 100° of silent bending motion. Cold Shoe Mount and Micro Tray provide an incredibly compact set-up. Dual Tray enables you to connect multiple lights to your camera.BEGIN BY CHOOSING YOUR TRAY .....FLEX ARMThe Flex Arm can be bent up to 100° and adds 7” of length, so you can aim the light exactly where you need it.COLD SHOE MOUNTUse the Cold Shoe Mount to mount a light directly to your camera for an ultra compact system. You can also use the GoPro® Adapter to mount a GoPro® directly above your camera in order to simultaneously capture underwater photos and video.GOPRO® ADAPTEREasily and safely connect the GoPro® camera to Flex-Connect accessories.YS ADAPTERThe YS Adapter makes the SeaLife system compatible with any underwater light or flash using a YS mount.HANDLEUse the Sea Dragon 1200 or 2000 lumen light as a handy dive light. Just click the light onto the Handle and you are ready to go. Of course, the H andle in combination with the GoPro® Adapter can also be used for the GoPro®, creating an extremely comfortable grip for comfortable GoPro® images.BALL JOINT ADAPTERThe adapter connects Sea Dragon Lights and Flex-Connect accessories to any underwater camera using the 1”/25mm ball joint mounting system.MICRO HD ADAPTERAdapter to connect your Micro HD to GoPro® accessoriesTRAY HANDLEThe Flex-Connect Grip provides a comfortable grip and improved handling for your light, flash or underwater camera set.THEN ADD HANDLES AND ARMS....35.5X27.9X12.7cmThe illustrations in this catalog may not exactly represent the products described and are intended as a guide only. We reserve the right to alter product descriptions or specifications as necessary.© Copyright 2015 SCUBAPRO. Johnson Outdoors Diving, LLC.FISHEYE LENSThe fisheye lens has an effective focal length of 16mm and increases the field of vision of the DC1400 by 80%. This allows for incredible perspective shots under water.10X CLOSE UP LENSThe 10x close-up lens allows you to get even closer to your subject.AQUA PODThe 135cm Aqua Pod allows you to take photos and videos from creative perspectives and to take selfies, close-ups, and videos while maintaining enough distance between you and your subject. The Aqua Pod Mini extends to 95cm and is comfortably light.GoPro® with Aqua Pod and Mini 600W IDE ANGLE LENSY ou want to fit everything into the shot and stay within the shooting range of your flash. The wide-angle lens takes a full-frame picture of a 5’ shark within 5’shooting distance.Not compatible with DC1400 or MICRO range.OBJECTIVE GRAND ANGLE MINIAmust-have lens for divers. Get closer to the subject and still fit everything in the picture. Not compatible with DC1400 or MICRO range.Absorbs moisture to prevent fogging and corrosion of your SeaLife camera.M OIST URE MUNCHER S OFT PRO CASEB UOYANCY WEIGHT AND FLOAT STRAPL-ION BATTERIEFor SeaDragon Photo-Video lights.BATTERIES & CHARGERFor SeaDragon Mini 650 & Mini 600OTHER ACCESSORIES。

浙江省金砖联盟2024-2025学年高二上学期11月期中英语试题一、阅读理解It’s widely acknowledged that effective communication counts at work. That’s why our communication workshops, where multiple forms of presentations are offered, are so popular. Welcome to join us and here are the resumes (简历) of two potential presenters recommended for this year’s summer communication workshops.1.Who will probably be the target audience of the workshop’s presentations?A.Those desiring to improve interactions at work.B.Those longing to give public speeches to others.C.Those looking forward to having a job interview.D.Those aiming to upgrade their English writing skills.2.What do Martin and Sandra have in common in their resumes?A.A strong background on PR activities.B.Being fluent in Cantonese and Putonghua.C.Having been employed in a university.D.Working experience for more than 10 years. 3.What can be expected from the presentation of Sandra Wong?A.Corporate training in business English.B.One-to-one training in business writing.C.Tips on a good relationship with clients.D.Beneficial videos and technical support.O. Henry(1862-1910) was an American short story author whose real name was William Sydney Porter. Henry’s works reflected his wide-range of experiences and are distinctive for its witticism(俏皮话), clever wordplay, and unexpected twist endings.Like many other writers, O. Henry’s early career aims were unfocused and he wandered across different activities and professions before he finally found his calling as a short story writer. He started working in his uncle’s drugstore in 1879. Later, he moved to Texas where he lived on a farm and learned sheep shepherding, cooking, babysitting, and bits of Spanish and German fromthe many migrant farmhands.Over the next several years, he took a number of different jobs, from drafting to journalism, and banking, but he was careless with accounting, thus fired by the bank and charged with a crime in 1894. He fled the day before the trial in 1896, first to New Orleans, then to Honduras, where he learned his wife was dying and could not join him, so he returned to Austin and turned himself in to the court. His father-in-law helped him out so he could remain with his wife until her death in 1897. Later he was sentenced and served in Federal prison in Ohio from 1989-1902.The many twists and turns of O. Henry’s own life, including his travels in Latin America and time spent in prison, clearly inspired his stories’ twists and wordplay. His prolific writing period began in 1902 in New York City, where he wrote 381 short stories which show his obvious affection for this City and its diversity of people and places. O. Henry’s trademark is his witty, plot-twisting endings, and his warm characterization of the awkward and difficult situations and the creative ways people find to deal with them, which typically features in his work like The Last Leaf,The Gift of the Magi, etc. All of his stories are highly entertaining, whether read for pleasure or studied in classrooms around the world.Unfortunately, O. Henry’s personal tragedy was heavy drinking. He died in 1910 of several diseases. He was a gifted short story writer and left us a rich legacy of great stories to enjoy. 4.What happened to O. Henry in his early life?A.He took up writing as his lifelong profession early on.B.He had a pretty good command of Spanish and German.C.He engaged himself with numerous jobs to experience life.D.He failed to live a stable life and switched jobs for a living.5.What does the underlined word “prolific” in paragraph 4 mean?A.relevant B.productive C.profitable D.original 6.Which of the following words can best describe O. Henry’s works?A.Educational and tragic.B.Unpredictable and serious.C.Fascinating and twisty.D.Extraordinary and formal.7.What does O. Henry’s life story convey?A.More haste, less speed.B.Time and tide wait for no man.C.He who laughs last laughs best.D.Suffering is a stepping stone to genius.A recent study on New Scientist reveals that police can access a collection of data from smart speakers found at crime scenes that could be invaluable in solving murders or robberies. Data on recently recognised faces, internet searches and voice commands could be extracted even without the owner’s permission or assistance from the manufacturer.Jona Crasselt and Gaston Pugliese at the University of Erlangen-Nuremberg in Germany tested how much information can be pulled from such a device after seeing news report of Amazon refusing police access to smart speaker data in a murder case. “We not only obtained access to the local data, but also were able to access the data stored in the cloud,” says Crasselt. “The investigators would be able to access the data themselves without relying on Amazon to provide it to them.”The researchers focused on Amazon’s Echo Show 15, a smart assistant with a display screen, a camera, six microphones and a light sensor. They explored inside the Echo Show with a device designed to test what signals or data are flowing at various points on a circuit board. The pair were able to gain access to the unencypted (未加密的) file system. “Records of detected movement and faces recognized by the built-in camera and artificial intelligence are accessible,” says Pugliese, “as well as details of voice requests, calendars, contacts, conversations, photos and videos.” He added that it required some technical knowledge to obtain the local data, but it was surprising that the file system was not encrypted.An Amazon spokesperson told New Scientist: “The security of our devices and customer data is a top priority. In this case, the researcher’s findings required direct physical access to the Echo device and specialised expertise to extract data from internal device components. We appreciate the work the security research community does to help us further improve our devices.”Criminologist David Wilson at Birmingham City University, UK, says it’s a simple human reality that you’re most likely to be victims to someone you know. “We already have access to information from those domestic settings through mobile phones, Facebook, Instagram posts. In spite of the fact that smart speaker evidence may be useful, it is controversial,” he says. “because there are privacy issues.”8.What might be helpful in solving crimes according to the study?A.The smart speaker on the spot.B.The manufacturer’s assistance.C.The user’s or owner’s permission.D.The artificial intelligence system.9.What did Gaston Pugliese imply in paragraph 3?A.The file system is incredibly difficult to access.B.Sufficient information is stored in the speaker.C.Echo Show is equipped with various functions.D.Advanced techniques are needed to obtain data.10.What measures may Amazon take as a consequence of the researchers’ findings?A.To advocate the indirect physical access.B.To provide the files for the investigators.C.To better the security of the customer data.D.To extract the details of the users’privacy.11.What’s David Wilson attitude towards smart speaker evidence?A.Doubtful.B.Objective.C.Resistant.D.Optimistic.On Aug 20, the highly anticipated Black Myth: Wukong — A Chinese self-developed AAA game — made its first public appearance at home and abroad, immediately becoming a hit in the industry.Notably, the game has also sparked interest in Chinese culture, as it is greatly grounded in Chinese mythology and inspired by the legends of the Monkey King — or Sun Wukong — in Journey to the West, a Chinese classic novel that has been represented in numerous films, TV shows and cartoons. Another distinguishing characteristic of the game is that its art design has taken inspiration from ancient Chinese architecture and other traditional cultural heritages.This cultural feature of the game has resulted in additional benefits outside the game industry, arousing passionate enthusiasm from netizens to experience the Chinese cultural heritage displayed in the game. Thus, according to Chinese media reports, it has generated a new touring option — following in the footsteps of Wukong to see the Chinese cultural attractions.Shanxi is no doubt one of the biggest beneficiaries of this cultural tourism boom as the North China province boasts the largest number of locations where the game takes place. Of the 36 scenic spots featured in the game, 27 are located in Shanxi, according to Shanxi’s cultural and tourism officials. “Shanxi was selected by the game’s development team as the major destination for filming,” added the officials, “because it boasts some 28,000 sites of ancient buildings — thelargest number in China’s provincial-level regions.”The cooperation between Shanxi and Game Science has achieved a win-win result. As Black Myth: Wukong becomes a hit domestically and globally, Shanxi has seen an immediate rise in popularity in its tourism industry. Over the past two weeks after the game’s release, Huayan Temple in Datong, for instance, reported a 50 percent increase in tourist visits compared with the same period of last year, according to local officials.Latest media reports predicted that Shanxi will be among the hottest destinations during the coming National Day holiday in early October thanks to the game. On popular online travel platform Qunar, the number of searches of Shanxi soared by 1.2 times in August compared with the previous month.12.Why did the game immediately become a hit according to the passage?A.It appeals much to young game players.B.It is independently developed in China.C.It features varieties of cultural elements.D.It comes from an ancient classic novel. 13.What has the popular game brought about?A.A great enthusiasm about a Chinese novel.B.A keen interest in Chinese cultural heritage.C.A well-developed tourism industry in China.D.A deep exploration of the Chineselegends.14.What can be inferred from the statements of the officials of Shanxi?A.There was a rise of 50 percent in the tourist visits of Shanxi.B.Shanxi benefited the most from this phenomenal game craze.C.Shanxi owns the most ancient architectures in China’s regions.D.More than half of the scenic spots involved are located in Shanxi.15.What can be the best title of the text?A.Video Games Boost Local Tourism.B.Shanxi Tourism Sees Surprising Increase.C.Video Games Bring Digital Revival.D.Cultural Tourism Improves Video Games.The pros and cons of opening more drop-in centers for young night drifters(漂泊者)The issue of what to do with young night drifters has been much discussed. Many people think that the government ought to open more drop-in centers. 16 Following are the advantages and disadvantages of opening more drop-in centers for young night drifters.One advantage of opening more drop-in centers is that it would keep young night drifters safe. 17 For example, they may fall victim to gangs and drug dealers. Some young night drifters are also bullied. This is probably due to the fact that they are young and vulnerable.Another argument that is commonly heard is that having more drop-in centers would decrease night drifting. Drop-in centers provide an easy way to offer young night drifters professional advice. Counsellors can give young drifters advice about how to solve problems with their families. 18In addition to these advantages of opening more drop-in centers for young night drifters, however, there are also a number of disadvantages. 19 According to these people, if there are more safe places for night drifters to hang out in, there is no motive for these young people to give up their nocturnal(夜间的) habits. Moreover, the attraction of having a special place to go to may encourage others to become night drifters as well.It is also argued that resources should be focused on providing services for all young people rather than just a small proportion of them. In other words, it may not be fair to support only night drifters.20 However, personally, I believe that ensuring the safety of young people and giving night drifters counselling are both necessary. I therefore believe that more drop-in centers should be provided for young night drifters in the city.A.They can also help them to handle negative peer pressure.B.People believe that disadvantages outweigh advantages.C.It is clear that the issue is not black and white.D.However, it is an issue that still divides many people.E.Hence, more drop-in centers are of vital significance to them.F.Young people who walk the streets at night often fall into bad ways.G.Some people argue it actually fails to discourage night drifting.二、完形填空The day before we boarded the ship to London, father said goodbye to his five-year-old dog, Spider, who was 21 by us all. Father’s friend was to look after him while we were overseas.Three weeks later, news came that Spider had run away. I will always remember my father’s tears in eyes. My mom and I tried to 22 him, knowing in our hearts how useless this was. Our excitement at finally arriving in England quickly 23 . The whole family fell into deep sorrow. 24 advertised constantly on the radio and in the newspaper, Spider was never found.We came back to our home five months later. My father immediately began his own 25 for Spider, only to get some false calls. Disappointment 26 our household. We all thought the dog was gone — possibly shot or dead from hunger and exhaustion.One cold Saturday morning, my father had another 27 from Gin Gin, 375 kilometres from our home. An elderly lady told him there was a dog like Spider in her disused tennis court. That was 28 for us to drive there. Five and a half hours later, we found the lady. My father was 29 to see the dog, so we followed her to the tennis court.30 , it seemed that the dog wasn’t around. Where could he be? My father had a strange look in his eye. He put two fingers to his lips and did his special 31 for Spider. All of a sudden, Spider 32 over the tennis court fence with great force and certainty, flying right into my father’s arms. My father’s eyes shone. For so long, my father never lost 33 that he would find his dog.Spider 34 the rest of his days with us, content and satisfied. He always waited for me coming home from school. He then waited for my father by the garage door. We never left him anywhere 35 again.21.A.adopted B.named C.trained D.loved 22.A.support B.comfort C.persuade D.bless 23.A.switched B.released C.disappeared D.approached 24.A.Since B.While C.When D.Unless 25.A.search B.appeal C.travel D.desire26.A.took up B.went through C.hung over D.pulled in 27.A.letter B.mail C.poster D.call 28.A.remote B.enough C.difficult D.possible 29.A.anxious B.nervous C.worried D.excited 30.A.Luckily B.Apparently C.Hopelessly D.Sadly 31.A.gesture B.signal C.whistle D.expression 32.A.climbed B.leapt C.fell D.rolled 33.A.hope B.effort C.patience D.trust 34.A.stayed B.spared C.saved D.spent 35.A.disused B.upset C.alone D.dirty三、语法填空阅读下面短文,在空白处填入1个适当的单词或括号内单词的正确形式。

寻物启事相机英语作文Missing Camera.英文回答:I lost my camera last week and I am desperately looking for it. It is a black Canon DSLR camera with a 50mm lens. I remember using it during a family gathering at the park, but I must have left it behind when we packed up. I have searched everywhere, but I cannot find it. I am really upset because that camera holds so many precious memories.I have asked around the park, but no one seems to have seen it. I even went to the park office to check if someone had turned it in, but they said no. I am starting to lose hope of ever finding it. It is not just the camera itself that I miss, but also the photos inside. They cannot be replaced.I am offering a reward to anyone who finds and returnsmy camera. It is not about the money; it is about the sentimental value attached to it. I am willing to pay whatever it takes to have it back. I have put up posterswith my contact information all over the neighborhood, hoping that someone will come forward with information.I have also reported the loss to the police. They took down all the details and said they would keep an eye outfor it. I hope that they can help me recover my camera. I cannot bear the thought of losing all those memories captured in the photos.If anyone has any information about the whereabouts of my camera, please contact me immediately. I am desperate to have it back. Thank you for your help.中文回答:我上周丢了我的相机,我正在拼命寻找它。
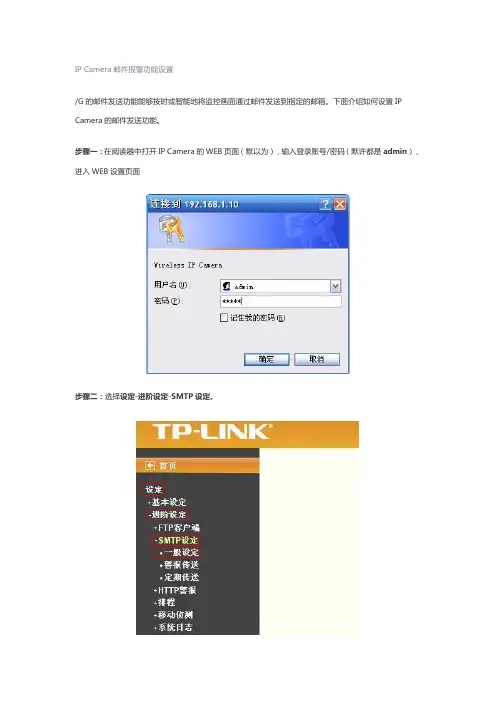
IP Camera邮件报警功能设置/G的邮件发送功能能够按时或智能地将监控画面通过邮件发送到指定的邮箱。
下面介绍如何设置IP Camera的邮件发送功能。
步骤一:在阅读器中打开IP Camera的WEB页面(默以为),输入登录账号/密码(默许都是admin),进入WEB设置页面步骤二:选择设定-进阶设定-SMTP设定。
步骤三:选择一样设定1.SMTP效劳器名称:设置登入邮箱的SMTP效劳器域名或IP,如网易163邮箱的SMTP效劳器:smtp.163;也能够直接填写SMTP效劳器的IP地址。
假设填写是域名,设备需设置DNS效劳器;2.SMTP效劳器端口:默许25,国内邮箱绝大多数利用25端口;3.认证:一样需要开启,用来设置您的邮箱账号和密码;4.利用者名称:登入邮箱的账号,能够填写完整邮箱如:12345@163,也能够直接填写12345;5.密码:登入邮箱的密码;6.收件者电子邮件地址:监控端邮箱地址,此邮箱将收到摄像头发送的邮件内容;7.治理员电子邮件地址:与登入邮箱相同,不然无法测试成功,本例:12345@163;8.主旨:发送邮件的题目;9.本文:发送邮件的文本内容,不支持中文,输入中文以后会显现乱码。
设置完成,点击确信保留配置。
点击测试,测试可否成功发送。
测试成功,会弹出如下界面,提示:SMTP Test Success,表示邮箱设定成功。
现在指定的收件人邮箱会收到这封测试邮件(只有题目和文本内容)。
步骤四:若是设置智能发送方式,请选择警报传送。
1,附加档案:默许关闭,为发送的报警图片概念名称信息的格式。
影像档案名称:发送画面的名称首字符;字尾:影像档案名称后所加的字符,能够选择日期时刻、序号或是空。
2,警报:移动侦测,需勾选。
移动侦测:支持同时对画面三个部份进行侦测,能够自行设定区域数量及大小1)移动侦测1:如上图所示默以为整个画面的侦测,大红色框覆盖区域,能够手动调整位置及覆盖区域大小;临界值:触发警报设置的阈值,当超过该阈值触发警报;感应度:移动侦测检测的频率设置。

中选中设备,点击 ,在弹出的界面中设置235)登录成功后,下载并安装视频插件。
【说明】如果直接通过Web 端首次登录未激活的设备,可在登录界面设置管理员的密码激活设备 ( 如图5 )。
登录前需要先将PC 机设置为与设备在同一网段。
4. 图像调节和镜头调整进入客户端后可以直接浏览图像,界面如图。
【说明】不同型号浏览界面略有差异,请以设备实际界面为主。
更多客户端说明参见客户端帮助文档。
调整设备方向,在Web 客户端上进行参数调整,直到浏览画面达到预定要求。
图 4图53 ) 点击 ,在弹出的界面中配置网络参数 。
静态分配IP 地址时,请选择自定义地址,填写以太网参数。
修改参数配置,需要填写管理员用户用户名(admin )及激活设备时所设置的密码。
完成IP 配置后,设备将自动重启,重启时间约为60秒。
4 ) 在IPCSearch 中双击设备或点击 ,输入用户名和密码 ( 如图4 ),登录Web 客户端。
线缆识别线序1 2 3 4 5 6 7 8 9 10RS485_ARS485_BAUDIO_IN 1AUDIO_IN 2AUDIO_OUTAUDIO_GNDALARM_INALARM_IN_GNDALARM_OUT 1AALARM_OUT 1BRS485串口ARS485串口B音频输入1音频输入2音频输出音频接地告警输入告警输入接地告警输出1,两个端子不分正负黄绿粉红白黑/白浅绿灰红蓝紫标签标示颜色组别 注释一组一组一组附 线缆识别图 61) When use the device for the first time, run the IPCSearch in the attached CD and set camera IP address and gateway. If the network provides DHCP service, DHCP server will assign IP for the camera automatically.2) Select the device and click “Batch processing”. In the popup interface, set admin user’s password and the claim e-mail address to find back the password. Click “Active” and wait for rebooting.Picture 33. L ogin client[Note]:Some models support PoE (Power on Ethernet). Only have to connect RJ45 connector to PoE switch and no other power supply is needed.The tail connector is subject to the actual model. Picture 2 shows the model with most complete connections.Please refer to the appendix for wire connection.System for client installation:Processor: 3.3 GHz CORE®i3 series or other equivalent processorsRAM Memory: 4GB or aboveOperating System: Windows XP or newer versionBrowser: IE7.0 and newer version, Firefox, Google Chrome (41 and lower)DirectX :9.0c[Note]: This Guide will take Windows XP as example to explain client login steps.4. Live view and lens adjustmentAfter login, user can view live video directly, as the picture shows.[Note]: Interface of different models may differ. Please refer to the help file for detailed explanation.Adjust camera direction, configure camera parameters in web client until the live view meets requirement.Picture 4Picture 53) Click “Modify Params” and set the network parameters. When configure a static IP for the camera, please check “Custom device address (Close DHCP)” and fill the Ethernet parameter. During the modification, the user name (admin) and the password set before activation should be entered. After configuration, the camera will reboot automatically and this takes 60s.4) Double click the device in IPCSearch or click “Login”. Enter user name and password (as Picture 4 shows) to login the web client.5) After login, download and install the plug-in.[Note]: If login the nonactivated camera by web client, you can set admin user’s password on the logininterface to activate the device (as in Picture 5). Before setting, set the PC and the device in the same LAN.Picture 6Kedacom Two (2) Year Limited Hardware WarrantyWHAT IS COVERED BY THIS WARRANTY?Kedacom warrants the Kedacom-branded hardware product and accessories contained in the original packaging (hereinafter referred to as "Kedacom Product") against defects in materials and workmanship when used normally in accordance with Kedacom's published guidelines for a period of TWO (2) YEARS from the date of original retail purchase in areas other than mainland China by the end-user purchaser (hereinafter referred to as "Warranty Period"). For the Kedacom Product purchased in mainland China, see the simplified Chinese version of this warranty for details. Kedacom's published guidelines include but are not limited to information contained in technical specifications, user guides, and service communications.The preceding applies unless otherwise agreed in the contract.WHAT IS NOT COVERED BY THIS WARRANTY?This warranty does not apply to any non-Kedacom branded hardware products or any software, even if packaged or sold with Kedacom hardware. Manufacturers, suppliers, or publishers, other than Kedacom, may provide their own warranties to you but Kedacom, in so far as permitted by law, provides their products "AS IS". Software distributed by Kedacom with or without the Kedacom brand (including, but not limited to system software) is not covered by this warranty. Please refer to the licensing agreement accompanying the software for details of your rights with respect to its use. Kedacom does not warrant that the operation of the Kedacom Product will be uninterrupted or error-free. Kedacom is not responsible for damage arising from failures to follow instructions relating to the Kedacom Product's use.This warranty does not apply: (a) to consumable parts, such as batteries, unless failure has occurred due to a defect in materials or workmanship; (b) to cosmetic damage, including but not limited to scratches, dents, and broken plastic on ports; (c) to damage caused by use with another product; (d) to damage caused by acts outside the control of Kedacom, including without limitation acts of God, accidents, abuse, misuse, fire, storms, earthquakes, flood, or other external cause; (e) to damage caused by exposure of the product to heat, bright light, sun, liquids, sand, or other contaminants; (f) to damage caused by operating the Kedacom Product outside Kedacom's published guidelines; (g) to damage caused by service (including upgrades and expansions) performed by anyone other than a representative of Kedacom, Kedacom employee, or authorized Kedacom agent; (h) to an Kedacom Product that has been modified to alter functionality or capability without the written permission of Kedacom; (i) to defects caused by normal wear and tear or otherwise due to the normal aging of the Kedacom Product, or (j) if any serial number has been removed or defaced from the Kedacom Product.YOUR RESPONSIBILITIESIf your Kedacom product is capable of storing data and other information, you should make periodic backup copies of the information contained on the storage media to protect the contents and as a precaution against possible operational failures.Before receiving warranty service, Kedacom or its authorized agents may require that you furnish proof of purchase details, respond to questions designed to assist with diagnosing potential issues, and follow Kedacom's procedures for obtaining warranty service. Before submitting your Kedacom Product for warranty service, you should maintain a separate backup copy of the contents of its storage media, remove all personal information that you want to protect, and disable all security passwords.During warranty service, it is possible that the contents of the Kedacom product's storage media will be lost, replaced or reformatted. In such an event, Kedacom and its authorized agents are not responsible for any loss of data or other information contained on the storage media or any other part of the Kedacom product serviced.Following warranty service, your Kedacom Product or a replacement product will be returned to you as your Kedacom Product was configured when originally purchased, subject to applicable updates. You will be responsible for reinstalling all other data and information. Recovery and reinstallation of other data and information are not covered under this warranty.WHAT WILL KEDACOM DO IF THE WARRANTY IS BREACHED?If during the Warranty Period, you submit a valid claim to Kedacom or an authorized Kedacom agent, Kedacom will, at its option, (i) repair the Kedacom Product using new or previously used parts that are equivalent to new in performance and reliability, or (ii) exchange the Kedacom Product for a refund of your purchase price.A Kedacom replacement part or product, including a user-installable Kedacom part that has been installed in accordance with instructions provided by Kedacom, assumes the remaining warranty of the Kedacom Product or ninety (90) days from the date of replacement or repair, whichever provides longer coverage for you. When a product or part is replaced or a refund provided, any replacement item becomes your property and the replaced or refunded item becomes Kedacom's property.Kedacom reserves the right to refund the purchase price as its exclusive warranty remedy.HOW TO OBTAIN WARRANTY SERVICE?To seek warranty service, please contact a local authorized Kedacom agent. When contacting the agent via telephone, other charges may apply depending on your location.User InformationComplete the form below and keep for ready reference.User Name:Address:Postal Code:Tel:Mobile:Fax:E-Mail:Product Name:Product Model:Date of Purchase:。

DatasheetAXIS P3245-VE Network CameraStreamlined outdoor-ready HDTV1080p fixed domeAXIS P3245-VE offers excellent image quality in HDTV1080p under any light conditions.This outdoor-ready,IK10-rated camera features Forensic WDR to provide clarity when there’s both dark and light areas in the scene.And, Lightfinder2.0delivers images with more life-like colors and sharp images of moving objects.Including a varifocal lens with remote zoom and focus capabilities,it eliminates the need for hands-on fine tuning.This camera features enhanced security functionality to ensure the integrity and authenticity of the camera’s firmware.Furthermore,it offers Axis Zipstream with support for H.264/H.265,which significantly reduces bandwidth and storage requirements.>HDTV1080p video quality>Remote focus and zoom>Lightfinder2.0and Forensic WDR>Zipstream supporting H.264and H.265>Signed firmware and secure bootAXIS P3245-VE Network Camera CameraImage sensor1/2.8”progressive scan RGB CMOSLens Varifocal,3.4–8.9mm,F1.8Horizontal field of view:100°-36°Vertical field of view:53°-20°Remote zoom and focus,P-Iris control,IR correctedDay and night Automatically removable infrared-cut filterMinimum illumination With Forensic WDR and Lightfinder2.0: Color:0.1lux at50IRE,F1.8B/W:0.02lux at50IRE,F1.8Shutter speed1/66500s to2sCamera angleadjustmentPan±180°,tilt±75°,rotation±175°System on chip(SoC)Model ARTPEC-7Memory1024MB RAM,512MB Flash ComputecapabilitiesMachine learning processing unit(MLPU) VideoVideo compression H.264(MPEG-4Part10/AVC)Baseline,Main and High Profiles H.265(MPEG-H Part2/HEVC)Main ProfileMotion JPEGResolution1920x1080to160x90Frame rate With WDR:25/30fps with power line frequency50/60HzWithout WDR:50/60fps with power line frequency50/60Hz Video streaming Multiple,individually configurable streams in H.264,H.265,and Motion JPEGAxis Zipstream technology for H.264and H.265Controllable frame rate and bandwidthVBR/ABR/MBR H.264/H.265Multi-viewstreamingUp to2individually cropped out view areas in full frame rateImage settings Compression,color saturation,brightness,sharpness,contrast,local contrast,white balance,day/night threshold,tone mapping,exposure control(including automatic gain control),exposurezones,defogging,Forensic WDR:up to120dB depending onscene,barrel distortion correction,fine tuning of low-lightbehavior,dynamic text and image overlay,privacy masks,mirroring,rotation:0°,90°,180°,270°,including CorridorFormatPan/Tilt/Zoom Digital PTZ,preset positionsAudioAudio input/output Two-way audio connectivity via optional AXIS T61Audio and I/O Interfaces with portcast technologyNetworkSecurity Password protection,IP address filtering,HTTPS a encryption, IEEE802.1X(EAP-TLS)a network access control,digestauthentication,user access log,centralized certificatemanagement,brute force delay protection,signed firmware,secure bootSupported protocols IPv4,IPv6USGv6,ICMPv4/ICMPv6,HTTP,HTTP/2,HTTPS a,SSL/TLS a,QoS Layer3DiffServ,FTP,SFTP,CIFS/SMB,SMTP, mDNS(Bonjour),UPnP®,SNMP v1/v2c/v3(MIB-II),DNS/DNSv6, DDNS,NTP,RTSP,RTP,SRTP,TCP,UDP,IGMPv1/v2/v3,RTCP, ICMP,DHCPv4/v6,ARP,SOCKS,SSH,SIP,LLDP,CDP,MQTT v3.1.1, Syslog,Link-Local address(ZeroConf)System integrationApplication Programming Interface Open API for software integration,including VAPIX®and AXIS Camera Application Platform;specifications at One-click cloud connectionONVIF®Profile G,ONVIF®Profile M,ONVIF®Profile S,and ONVIF®Profile T,specification at Support for Session Initiation Protocol(SIP)for integration with Voice over IP(VoIP)systems,peer to peer or integrated with SIP/PBXEvent conditions Analytics,edge storage events,virtual inputs through APIMQTT subscribeEvent actions Record video:SD card and network shareUpload of images or video clips:FTP,SFTP,HTTP,HTTPS,networkshare,and emailPre-and post-alarm video or image buffering for recording oruploadNotification:email,HTTP,HTTPS,TCP,and SNMP trapMQTT publishOverlay text,make callData streaming Event dataBuilt-ininstallation aidsPixel counter,remote focus,remote zoomAnalyticsAXIS ObjectAnalyticsObject classes:humans,vehiclesTrigger conditions:line crossing,object in areaUp to10scenariosMetadata visualized with color-coded bounding boxesPolygon include/exclude areasPerspective configurationONVIF Motion Alarm eventApplications IncludedAXIS Object AnalyticsAXIS Motion Guard,AXIS Fence Guard,AXIS Loitering GuardAXIS Video Motion Detection,active tampering alarmSupportedSupport for AXIS Camera Application Platform enablinginstallation of third-party applications,see /acap GeneralCasing IP66-and NEMA4X-rated,IK10impact-resistant polycarbonate casing with hard-coated dome and dehumidifying membraneEncapsulated electronics and captive screwsColor:white NCS S1002-BFor repainting instructions and impact on warranty,contactyour Axis partner.Mounting Mounting bracket with holes for junction box(double-gang,single-gang,and4”octagon)and for wall or ceiling mount¼”-20UNC tripod screw threadSustainability PVC freePower Power over Ethernet(PoE)IEEE802.3af/802.3at Type1Class3Typical3.5W,max8WConnectors RJ4510BASE-T/100BASE-TX PoEAudio and I/O connectivity via AXIS T61Audio and I/O Interfaceswith portcast technologyStorage Support for microSD/microSDHC/microSDXC cardSupport for SD card encryption(AES-XTS-Plain64256bit)Recording to network-attached storage(NAS)For SD card and NAS recommendations see Operatingconditions-40°C to50°C(-40°F to122°F)Maximum temperature(intermittent):55°C(131°F)Absolute maximum temperature:74°C(165°F)according toNEMA TS22016,2.2.7Start-up temperature:-30°C to50°C(-22°F to122°F)Humidity10–100%RH(condensing)Storageconditions-40°C to65°C(-40°F to149°F)Humidity5–95%RH(non-condensing)Approvals EMCEN55032Class A,EN50121-4,IEC62236-4,EN55024,EN61000-6-1,EN61000-6-2,FCC Part15Subpart B Class A,ICES-3(A)/NMB-3(A),VCCI Class A,RCM AS/NZS CISPR32Class A,KC KN32Class A,KC KN35SafetyIEC/EN/UL62368-1,IEC/EN/UL60950-22,IS13252EnvironmentIEC60068-2-1,IEC60068-2-14,IEC60068-2-2,IEC60068-2-27,IEC60068-2-6,IEC60068-2-78IEC/EN60529IP66,IEC/EN62262IK10,NEMA250Type4X,NEMA TS2(2.2.7-2.2.9)NetworkNIST SP500-267Dimensions Without weathershield:Height:104mm(4.09in)ø149mm(5.87in) Weight With weathershield:800g(1.8lb)Included accessories Installation guide,Windows®decoder1-user license,drill template,Resistorx®T20L-key,cable gaskets,connector guard WeathershieldOptional accessories AXIS T94M02L Recessed Mount,AXIS T94T01D Pendant Kit, AXIS T6101Audio and I/O Interface,AXIS T6112Audio and I/O Interface,AXIS ACI Conduit Adapters,Axis mounts,smoked dome,black casingFor more accessories,see Video management software AXIS Companion,AXIS Camera Station,video managementsoftware from Axis Application Development Partners availableat /vmsLanguages English,German,French,Spanish,Italian,Russian,SimplifiedChinese,Japanese,Korean,Portuguese,Traditional ChineseWarranty5-year warranty,see /warrantya.This product includes software developed by the OpenSSL Project for use in theOpenSSL Toolkit.(),and cryptographic software written by Eric Young(*****************).Environmental responsibility:/environmental-responsibility©2019-2021Axis Communications AB.AXIS COMMUNICATIONS,AXIS,ARTPEC and VAPIX are registered trademarks ofAxis AB in various jurisdictions.All other trademarks are the property of their respective owners.We reserve the right tointroduce modifications without notice.T10130287/EN/M13.2/2110。

Thank you for choosing an Irix lens. You hold in your hand the fruit of the dedication and experien-ce of the combined forces of engineers and photo-graphers.Using the finest available materials, state-of-the--art technologies and cooperation, our team has created an excellent tool for both professional and amateur photographers.The Irix 11 mm f/4 is an ultra-wide-angle, rectilinear, manual focus lens, designed for full-frame DSLR cameras. It is also com-patible with many crop-sensor models.TABLE OF CONTENTSFRONT LENS CAP4FOCUS SCALE CALIBRATION5FOCUS LOCK RING6FOCUS RING7DEPTH OF FIELD SCALE11HYPERFOCAL SCALE12REAR GELATIN FILTER SLOT15HOW TO ATTACH THE LENS TO THE CAMERA16REAR LENS CAP17APERTURE CONTROL18HARD LENS CASE19MAINTENANCE20SAFETY PRECAUTIONS21TECHNICAL SPECIFICATION22TEMPLATE FOR CUTTING GELATIN FILTERS23FRONT LENS CAPThe front lens cap protects the front lens elementfrom possible contamination and impact damage.The cap should always be attached when the lensis not in use.To attach or remove the front cap, hold the lensbody firmly in one hand and grasp the cap withyour thumb and finger by the recesses in the frontof the cap. Squeeze gently toward the center of thecap to release the latches.Spare lens caps may be purchased through the Irixonline store .FOCUS SCALE CALIBRATION You Irix lens has been engineered to exacting stan-dards. The focus scale is factory calibrated andshould be accurate. In some cases, however, youmay find that the infinity mark on your lens doesnot correspond to the optimum focus setting fordistant objects. While the focus ring will rotate pastthe infinity setting to allow you to compensate forthis, it may be more convenient to re-calibrate theinfinity setting on your lens. You can make this ad-justment yourself or contact the Irix support teamfor help.To calibrate the focus ring:1. Remove the calibration window cover by unscrewing the T6Torx screw and sliding the cover outward.2. Set the focusing ring at the infinity position and then rotatethe focus lock ring to the locked position. The internal calibra-tion ring and small flat head locking screw should be visible.Note: The position of the calibration ring is maintained thanksto the screws with a large flat head. These screws must stayscrewed all the time.3. Using a flat head screwdriver, loosen the smaller screw onthe calibration ring. Be careful not to allow the screw to fall intothe lens housing. A screwdriver with a magnetic tip is recommen-ded. Turn on the live view on the camera and then use a thin tipscrewdriver to turn the calibration ring clockwise or counterc-lockwise until the correct focus on the plan is at least 15 meters(49 feet) away.FOCUS LOCK RINGThe focus lock ring allows you to fix the focusingring in a selected position. This innovative featurehelps prevent accidental movement, resulting infocus shift.You may want to use the focus lock during longexposures, time-lapse imaging, or whenever re-petitive shots are called for. You can also use it toavoid changing the focus setting while mountingor removing the lens or to retain the focus settingwhen storing it in a bag, case or backpack.Landscape photographers, street photographersand journalists can utilize the focus lock to keepthe lens at the infinity setting or hyperfocal distan-ce for a given aperture.To use the focus lock ring, turn the ring clockwiseuntil you feel a mechanical resistance which mayvary depending on the ambient temperature.CAUTION: Do not turn the focus lock ring out of the center mar-ker or use excessive force. This may damage the locking mecha-nism of the focus ring as well as make it more difficult to releasethe focus ring lock.FOCUS RINGThe focusing ring moves the internal focusingelements of the lens to achieve the desired focalpoint. You can focus visually while looking at yoursubject in the viewfinder or LCD screen or by usingthe distance, depth of field or hyperfocal scales onthe lens barrel.Your Irix lens allows you to set the focus at infinity without theneed to look at the scale. While rotating the focus ring, infinity isindicated by a click and a definitive stop in the rotation.The depth of field scale provides a visual reference for the range of maximum sharpness in your pho-tos at a given aperture and focus setting. It allows you to determine the plane of focus, within which objects in your image will be at their sharpest.Using the scale correctly takes practice. The following examples will demonstrate how to use it for creative control of depth of field (DoF).DoF control is achieved with the lens aperture, so you will needto set your camera to Aperture Priority or Manual mode.EXAMPLE NO 1In this example, the lens is focused on the seventh key from the font of the image. The lens aperture is at its maximum setting of 4.0You can see in the image that only the neighboring keys are in sharp focus at this aperture setting. Theterm for this effect is “shallow depth of field”.EXAMPLE NO 2In this image, the focus setting remains the same as the first example, while the aperture setting is changed to f/8.Consulting the DoF scale, we can now use the two numerals “8” on the scale to determine the distan-ces where sharpness will drop. Simply look for the distances in feet or meters that align with the “8”s on the scale to determine the closest (left “8”) and farthest (right “8”) points that will be in focus.You can verify the change in depth of field in the image. Noticethat the number of keys in focus has increased.DEPTH OF FIELD SCALEEXAMPLE NO 3Next, the aperture setting is decreased to f/16,without changing the focus setting. This smalleraperture will increase the DoF.You can see the increased plane of focus in theimage. Consulting the DoF scale at “16” will showa corresponding change in the indicated distances.The DoF scale can be used in this manner to esti-mate the plane of focus in your images at aperturesettings of f/8 and smaller.The DoF scale on your lens indicates the results with a full-fra-me camera. Using your lens with a camera with a smaller sen-sor and different pixel pitch will noticeably affect the depth offield and the accuracy of the scale. Practice will help you deter-mine and compensate for the difference.In landscape, travel and similar types of photo-graphy, it’s often beneficial to maximize the depth of field in your images. This is best accomplished by setting your focus at the closest point of sharp focus for the chosen aperture setting. That point is known as the hyperfocal distance. Even when using the DoF scale, this distance can be difficult todetermine in the actual scene.Your Irix lens includes an innovative feature that allows you to quickly focus your lens at the hyper-focal distance for apertures of f/4 to f/16. The hy-perfocal scale is located above the distance scale on the lens barrel.After selecting your aperture setting with your camera in aperture Priority or Manual mode, sim-ply align the corresponding f/number on the hy-perfocal sale with the center of focus indicator (thecenter mark on the DoF scale). Your focus is now set to the hyperfocal distance and there’s no need to focus visually!The landscape image to the left was taken using the hyperfocal scale at f/16. Notice the overall sharpness in the image.Notes:1. When using the hyperfocal scale for several consecutive pho-tos, consider using the focus ring lock.2. The hyperfocal scale is calibrated for use with a full frame camera. Using a camera with a smaller sensor will cause a shi-ft in DoF and a corresponding shift in the hyperfocal distance. With practice, you can learn to determine and compensate for the difference.The hyperfocal scale consists of four positions: 4, 8, 11 and 16. When working with the hyperfocalscale, the focus ring sets itself in aforementioned position and you should set this aperture number in your camera. Depending on a chosen position, your photo will be in focus according to the below scheme:position 4 – plans between 2 m (6.56 ft) and infinityposition 8 – plans between 0.95 m (3.12 ft) and infinity position 11 – plans between 0.65 m (2.13 ft) and infinity position 16 – plans between 0.45 m (1.48 ft) and infinityThis aperture value was set for the example photo, and the focus area covers all the plans.If you work with the hyperfocal scale for a longer time, consider using the focus ring lock.Your Irix lens is equipped with a 30mm x 30mm slot behind the rear element to accommodate ge-latin filters. A template for pre-cutting filters is inc -luded on the last page of this document.Exercise caution when inserting filters to avoid touching the rear lens element and electrical contacts on the mount.Filter dimensions that do not match the template in this manual should not be used.REAR GELATIN FILTER SLOTHOW TO ATTACH THE LENSTO THE CAMERAExact mounting methods vary from camera tocamera. Consult the user’s manual for your came-ra for instructions on mounting your Irix lens. Thedot on the case bevel closest to the camera indica-tes the alignment mark for mounting.Exercise caution when attaching and detaching your lens. Donot force the lens. Be sure to press the lock release on thecamera body when detaching the lens. Consult your cameramanual for the exact location of the release. Failure to followthese steps may cause permanent damage to your lens and/or camera.REAR LENS CAPThe rear lens cap protects the mount and rear ele-ments when the lens is detached from the camera.It should be attached immediately when the lensis removed.Your Irix lens comes with a spare rear cap, whichyou can find inside the lens box. Additional lenscaps can be purchased from ifneeded.To avoid damage, never place the rear of the lens on any surfa-ce with the rear lens cap removed.APERTURE CONTROLYour Irix lens is equipped to function with yourcamera’s electronic aperture controls. It also com-municates the aperture information to the came-ra’s software for display and EXIF data.This feature allows you to fully utilize the creativeaspects of lens aperture in conjunction with yourcamera’s metering system and autoexposure set-tings.There are a few important points to know aboutyour lens and its aperture settings:1. Using an aperture setting higher than f/16 may cause somelack of sharpness due to an optical phenomenon known asdiffraction. This is not a defect, but a natural occurrence in alloptics.HARD LENS CASETo protect your lens against damage from theenvironment, always store it in the included hardcase (Blackstone version) or soft lens pouch (Fireflyversion).While the case helps protect your lens, it is NOT waterproof andwill not prevent damage due to severe impacts.MAINTENANCEAll Irix lens elements are coated with an-ti-reflective compounds, which also in-crease their resistance to contamination.Periodic cleaning should consist of dust removalwith a bulb-type air blower or soft brush*, follo-wed by the use of cleaning products specificallymade for coated lenses to remove smudges, oilyfilms and fingerprints.* High-pressure air may cause damage to lens surfaces andseals.SAFETY PRECAUTIONSYour Irix lens is equipped with seals to prevent the infiltration ofdust, moisture and water splashes. This sealing does not makeyour lens completely waterproof. Do not allow your lens to be-come submerged, come into contact with liquids under pressu-re,or be stored in humid locations. Store your lens with silica gelpacks to help prevent moisture.Do not leave the lens exposed to strong sunlight or high tem-peratures.Do not look directly at the sun through the lens, as permanenteyesight damage may occur. Do not allow the lens to pointdirectly at the sun for prolonged periods, to avoid the risk offire or camera sensor damage.Keep the lens and all associated accessories out of the reachof children.Disassembly and/or modification of your Irix lens beyond theprocedures documented herein may permanently damageyour lens and/or void the warranty.Your satisfaction with your Irix lens is our first priority. Shouldyou find any irregularities or inconsistencies in the operationand performance of your lens, please contact the seller or anauthorized Irix service center.TECHNICAL SPECIFICATIONFocal Length 11 mmMaximum aperture value f/4.0Minimum aperture value f/22Number of aperture blades 9Image size 36 x 24 mmAngle of view 126°Minimal focusing distance 27,5 cm (0.91 ft)Number of lenses 16 (10 groups)Rear gelatin filter slot 30x30 mmDimensions 118 x 100 mm (4.49” x 4.05”)Weight 730-790 g (1.61 – 1.74 lbs)TEMPLATE FOR CUTTING GELATINE FILTERS。
u Stylish indoor network camera u 720p resolution for sharp imagesuIntelligent noise reduction reduces bandwidth and storage requirements by up to 30%u SD card slot for local recording uFTP, Dropbox and e-mail alarmsThe 720p HD indoor camera is a ready-to-use,complete network video surveillance system inside a compact and stylish housing. This camera bringsBosch’s high-performance technology into the realm of homes, small office and retail businesses by offering a cost-effective solution for a broad range of applications.System overviewThe elegant, compact box design is ideal for homes,offices, businesses or shops where camera size and appearance is important. The camera has a 1/2.7-inch CMOS HD sensor and is a true day/night camera offering excellent performance day or night.FunctionsContent-Based Imaging TechnologyContent-Based Imaging Technology (C-BIT) is used to radically improve image quality in all lighting conditions and to identify areas for enhancedprocessing. The camera examines the scene usingintelligent video analytics and provides feedback to re-tune the image processing. This provides better detail in the areas that matter and better all-round performance.iDNR reduces bandwidth and storage requirements The camera uses intelligent Dynamic Noise Reduction (iDNR) which actively analyzes the contents of a scene and reduces noise artifacts accordingly.The low-noise image and the efficient H.264compression technology provide clear images while reducing bandwidth and storage by up to 30%compared to other H.264 cameras. This results in reduced-bandwidth streams that still retain a high image quality and smooth motion. The cameraprovides the most usable image possible by cleverly optimizing the detail-to-bandwidth ratio.The average typical optimized bandwidth in kbits/s for various image rates is shown in the table:Multiple streamsThe innovative multi-streaming feature delivers various H.264 streams together with an M‑JPEG stream. These streams facilitate bandwidth-efficient viewing and recording as well as integration with third-party video management systems.An upright mode can be selected for the second stream. In this mode an image of 400 x 720 (9:16 aspect ratio) is cropped from the full sensor image. When the scene to be monitored is suitable to this mode, the bandwidth and storage requirements are reduced.Simultaneous analog and IP video outputsA surge-protected analog video output ensures that high resolution IP video streaming and an analog video output are available simultaneously. This means, for example, that a confrontation monitor can easily be connected directly to the camera while still maintaining full IP functionality.Regions of interest and E-PTZRegions of Interest (ROI) can be user defined. The remote E-PTZ (Electronic Pan, Tilt and Zoom) controls allow you to select specific areas of the parent image. These regions produce separate streams for remote viewing and recording. These streams, together with the main stream, allow the operator to separately monitor the most interesting part of a scene while still retaining situational awareness.Built-in microphone, two-way audio and audio alarm The camera has a built-in microphone to allow operators to listen in on the monitored area. Two-way audio allows the operator to communicate with visitors or intruders via an external audio line input and output. Audio detection can be used to generate an alarm if needed.Tamper and motion detectionA wide range of configuration options is available for alarms signaling camera tampering. A built-in algorithm for detecting movement in the video can also be used for alarm signaling.Edge recordingThe SD card slot supports up to 2 TB of storage capacity. An SD card can be used for local alarm recording. Pre-alarm recording in RAM reduces recording bandwidth on the network, or — if SD card recording is used — extends the effective life of the storage medium.Storage managementRecording management can be controlled by the Bosch Video Recording Manager (VRM) or the camera can use iSCSI targets directly without any recording software.Cloud-based servicesThe camera supports time-based or alarm-based JPEG posting to four different accounts. These accounts can address FTP servers or cloud-based storage facilities (for example, Dropbox). Video clips or JPEG images can also be exported to these accounts.Alarms can be set up to trigger an e-mail or SMS notification so you are always aware of abnormal events.Easy installationPower for the camera can be supplied via a Power-over-Ethernet compliant network cable connection. With this configuration, only a single cable connection is required to view, power, and control the camera. Using PoE makes installation easier and more cost-effective, as cameras do not require a local power source.The camera can also be supplied with power from+12 VDC power supplies. To increase system reliability, the camera can be simultaneously connected to both PoE and +12 VDC supplies. Additionally, uninterruptible power supplies (UPS) can be used, which will allow continuous operation, even during a power failure. For trouble free network cabling, the cameras support Auto-MDIX.Simple set-upThe camera has a very intuitive user interface that allows fast and easy configuration. Six configurable user modes are provided with the best settings for a variety of applications:•Indoor – general day-to-night changes without sunhighlights and street lighting•Outdoor – general day-to-night changes with sunhighlights and street lighting•Motion – monitoring traffic or fast moving objects;motion artifacts are minimized•Lowlight – optimized for sufficient details at low light.•BLC – for people moving in front of a brightbackground•Vibrant – enhanced contrast, sharpness andsaturationTrue day/night switchingThe camera incorporates mechanical filter technology for vivid daytime color and exceptional night-time imaging while maintaining sharp focus under all lighting conditions.Access securityPassword protection with three levels and 802.1x authentication is supported. To secure Web browser access, use HTTPS with a SSL certificate stored in the camera. The video and audio communication channels can be independently AES encrypted with 128-bit keys by installing the optional encryption site license.Complete viewing softwareThere are many ways to access the camera’s features: using a web browser, with the Bosch Video Management System, with the Bosch Recording System, with the free-of-charge Bosch Video Client, or with the video security mobile App.The Bosch Video Client PC surveillance software offers a user-friendly interface to support easy installation and configuration. It also provides easy live viewing of multiple cameras, playback, forensic search and export.Video security AppThe Bosch video security mobile App has been developed to enable Anywhere access to HD surveillance images allowing you to view live images from any location. The App is designed to give you complete control of all your cameras, from panning and tilting to zoom and focus functions. It’s like taking your control room with you.This App, together with the separately available Bosch transcoder, will allow you to fully utilize our dynamic transcoding features so you can play back images even over low-bandwidth connections.System integrationThe camera conforms to the ONVIF (Open Network Video Interface Forum) Profile S specification. This guarantees interoperability between network video products regardless of manufacturer. For trouble-free network cabling, the camera supports Auto-MDIX which allows the use of straight or cross-over cables. Third-party integrators can easily access the internal feature set of the camera for integration into large projects. Visit the Bosch Integration Partner Program (IPP) website () for more information.Installation/configuration notes DimensionsSensitivity – (3200K, reflectivity 89%, F1.4, 30IRE)Resolutions (H x V)Ordering informationDINION IP 4000 HDIndoor 720p IP box design camera, iDNR; day/night; H. 264 quad-streaming; cloud services; ROI; motion/ tamper/audio detection; 720pOrder number NBN-40012-CDINION IP 4000 HDIndoor 720p IP box design camera, iDNR; day/night; H. 264 quad-streaming; cloud services; ROI; motion/ tamper/audio detection; 720p; varifocal 3.3 to 12 mm, DC Iris, F1.4 lensOrder number NBN-40012-V3AccessoriesVarifocal SR Megapixel LensRugged varifocal SR megapixel IR corrected lens.1/2.5" sensor; CS-mount; 4-pin SR-iris; 5 MP; 9 to40 mm; F1.5 to F8Order number LVF-5005C-S0940Varifocal SR Megapixel LensRugged varifocal SR megapixel IR corrected lens.1/2.5" sensor; CS-mount; 4-pin SR-iris; 5 MP; 1.8 to3 mm; F1.8 to F8Order number LVF-5005C-S1803S1460 Service/Monitor Cable2.5 mm jack to BNC video connector cable. 1 m Order number S1460EX12LED‑3BD‑8M Infrared IlluminatorMini IR 850 nm illuminator. LED array; 3D Diffuser; black; 17 m HFOV; 30º beam patternOrder number EX12LED-3BD-8MEX12LED‑3BD‑8W Infrared IlluminatorMini IR 850 nm illuminator. LED array; 3D Diffuser; black; 16 m HFOV; 60º beam patternOrder number EX12LED-3BD-8WEX12LED‑3BD‑9M Infrared IlluminatorMini IR 940 nm illuminator. LED array; 3D Diffuser; black; 17 m HFOV; 30º beam patternOrder number EX12LED-3BD-9MEX12LED‑3BD‑9W Infrared IlluminatorMini IR 940 nm illuminator. LED array; 3D Diffuser; black; 16 m HFOV; 60º beam patternOrder number EX12LED-3BD-9WSoftware OptionsBVIP AES 128 Bit EncryptionSingle installation licence for BVIP AES 128‑bit encryption site. Enables encrypted communication between BVIP devices and management stations. Order number MVS-FENC-AESRepresented by:Americas:Europe, Middle East, Africa:Asia-Pacific:China:America Latina:Bosch Security Systems, Inc. 130 Perinton Parkway Fairport, New York, 14450, USA Phone: +1 800 289 0096 Fax: +1 585 223 9180***********************.com Bosch Security Systems B.V.P.O. Box 800025617 BA Eindhoven, The NetherlandsPhone: + 31 40 2577 284Fax: +31 40 2577 330******************************Robert Bosch (SEA) Pte Ltd, SecuritySystems11 Bishan Street 21Singapore 573943Phone: +65 6571 2808Fax: +65 6571 2699*****************************Bosch (Shanghai) Security Systems Ltd.201 Building, No. 333 Fuquan RoadNorth IBPChangning District, Shanghai200335 ChinaPhone +86 21 22181111Fax: +86 21 22182398Robert Bosch Ltda Security Systems DivisionVia Anhanguera, Km 98CEP 13065-900Campinas, Sao Paulo, BrazilPhone: +55 19 2103 2860Fax: +55 19 2103 2862*****************************© Bosch Security Systems 2014 | Data subject to change without notice 136****5115|en,V4,24.Jan2014。
英语作文找到丢失的相机Title: Finding the Lost Camera。
Losing a camera can be a devastating experience, especially if it holds cherished memories captured in photographs. However, with determination and resourcefulness, it's possible to turn the tide and recover what was lost. Here's a narrative of such an experience, combining personal anecdotes with practical tips forfinding a lost camera.---。
It was a beautiful summer day when my family and I embarked on a hiking adventure in the picturesque mountains. Armed with our trusty camera, we eagerly captured every moment of our journey – from the lush greenery to the breathtaking vistas. Little did we know that this camera, which held the essence of our unforgettable day, would soon go missing.As we reached the summit and paused to admire the panoramic view, I reached into my backpack to retrieve the camera, only to find it missing. Panic surged through me as I frantically rummaged through every pocket and compartment, hoping it had simply been misplaced. But as minutes turned into hours, the sinking realization set in – our camerawas lost.Desperate to recover our precious memories, we immediately sprang into action. The first step was toretrace our steps, meticulously combing through the trails we had traversed. It was a painstaking process, each step tinged with anxiety and uncertainty. Yet, with each passing moment, our determination grew stronger.As we retraced our path, we also reached out to fellow hikers and park officials, spreading the word about ourlost camera. We shared descriptions and photos, hoping that someone might have come across it. Social media became our ally, as we posted appeals for help and shared our storyfar and wide. The power of community, we realized, could bea potent force in our quest.Days turned into weeks, and still, there was no sign of our camera. Doubt crept in, whispering that perhaps it was gone forever. Yet, we refused to succumb to despair. Instead, we expanded our search radius, exploring areas beyond the hiking trails where our camera might have wandered. We visited nearby towns and shops, plastering posters with details of our lost camera, clinging to the hope that someone would recognize it.And then, just when we least expected it, a breakthrough occurred. A kind-hearted stranger reached out to us, having stumbled upon our camera in a remote corner of the park. It was a moment of elation and disbelief, as we rushed to reclaim what was rightfully ours. Holding the camera in my hands once again, I felt a wave of gratitude wash over me – gratitude for the kindness of strangers,for the power of perseverance, and for the resilience of hope.Reflecting on this experience, I realized that findinga lost camera was about more than just recovering material possessions. It was a journey of resilience, resourcefulness, and human connection. It taught me the importance of staying determined in the face of adversity, of reaching out for help when needed, and of never losing faith in the possibility of a happy ending.In conclusion, losing a camera may seem like a daunting setback, but with perseverance and ingenuity, it's possible to turn the tide and find what was lost. Whether through retracing steps, leveraging community support, or expanding the search horizon, every effort counts. And in the end, the journey to find a lost camera may just lead to discoveries that go beyond the tangible – discoveries of strength, kindness, and the enduring power of hope.--。
寻物启事相机英语作文English Answer:I'm so sorry to hear about your lost camera. I know how much those things can mean to us. I would be happy to help you write a lost and found notice in English and Chinese. Here is what I came up with:Lost: Black Nikon D3500 DSLR camera with a Nikkor 18-55mm lens. The camera has a black leather case and a strap with a red stripe. It was last seen on the park bench near the playground.Reward: $100 reward for the safe return of the camera.Contact: If you have any information about the camera, please contact [Your Name] at [Your Phone Number] or [Your Email Address].中文回答:得知你丢失了相机,我深感遗憾。
我知道那些东西对我们有多么重要。
我愿意帮助你用英语和汉语写一份失物招领启事。
我想到的是:丢失物品,黑色尼康D3500数码单反相机,配尼克尔18-55mm镜头。
相机配有黑色皮套和一条带有红色条纹的背带。
最后一次出现在游乐场附近的公园长椅上。
报酬,相机安全归还者将获得100美元的报酬。
联系方式,如果你有关于相机的任何信息,请联系[你的姓名],电话,[你的电话号码],电子邮件地址,[你的电子邮件地址]。
英语作文找回丢失的照相机Title: The Quest for the Lost Camera。
Losing something valuable can be distressing,especially when it holds precious memories captured in photographs. Recently, I found myself in such a predicament when I misplaced my camera during a trip. The following narrative recounts my journey to recover the lost camera.It was a sunny afternoon when I embarked on a leisurely stroll through the picturesque streets of a quaint town.The camera slung over my shoulder was my faithful companion, capturing the charm and beauty of every moment. However, amidst the hustle and bustle of exploring, I suddenly realized that my cherished camera was no longer by my side.Panic surged through me as I retraced my steps, desperately scouring every nook and cranny in search of the lost camera. But alas, my efforts proved futile, anddespair threatened to engulf me. Nevertheless, fueled bydetermination and hope, I resolved to leave no stone unturned in my quest to retrieve what was lost.My first course of action was to retrace my steps meticulously, revisiting each place I had visited in the hopes of stumbling upon the elusive camera. As I wandered through the winding alleys and bustling markets, I engaged with locals, hoping that someone might have spotted the missing camera. Despite their kindness and willingness to assist, my search yielded no results.Undeterred, I turned to technology as my next ally in the quest for the lost camera. Armed with social media platforms and online forums, I posted detailed descriptions and photographs of the camera, appealing to the online community for assistance. The power of social media provedto be invaluable as my plea for help resonated with individuals far and wide, who shared my post and offered words of encouragement.Days turned into weeks, and still, there was no sign of the lost camera. Frustration threatened to erode my resolve,but I refused to succumb to despair. Instead, I intensified my efforts, reaching out to local authorities and businesses, inquiring if anyone had turned in a lost camera matching the description.Just when it seemed like all hope was lost, a glimmer of light emerged on the horizon. A kind-hearted individual contacted me, claiming to have found a camera matching the description I had provided. Elation surged through me as I arranged to meet the Good Samaritan, who graciously returned the lost camera to its rightful owner.Tears of joy welled up in my eyes as I held the recovered camera in my hands, grateful for the kindness and generosity of strangers. The journey to retrieve the lost camera had been fraught with challenges and setbacks, but in the end, perseverance triumphed, and the precious memories stored within the camera were restored.In conclusion, the quest for the lost camera was a testament to the power of determination, resilience, and the kindness of strangers. Though the journey was arduous,the joy of reclaiming what was lost made every trial worthwhile. As I reflect on this experience, I am reminded that even in the face of adversity, hope shines brightest, illuminating the path towards resolution and redemption.。
英语作文找回照相机Title: Finding My Lost Camera。
Losing my camera was a distressing experience, fraught with anxiety and frustration. It wasn't merely a device; it held memories captured in fleeting moments, each snapshot a fragment of time frozen in pixels. Losing it meant losing a part of my past, a part of myself. However, in the face of adversity, I embarked on a quest to reclaim what was lost.The first step in my endeavor was to retrace my steps.I mentally revisited the places I had been to, hoping to jog my memory and unearth clues that might lead me to my missing camera. Each location became a waypoint in my search, a potential site for discovery.Next, I reached out to establishments I had visited during the day of the loss. I called restaurants, cafes, and stores, inquiring if anyone had found or turned in a camera matching the description of mine. This step requiredpatience and persistence as I made numerous calls, hoping for a stroke of luck.Simultaneously, I utilized social media platforms to widen the reach of my search. I posted detailed descriptions of the lost camera along with my contact information, appealing to the online community for assistance. The power of social media in mobilizing collective efforts became evident as shares and retweets amplified the visibility of my plea.Moreover, I tapped into the network of acquaintances and friends, enlisting their support in spreading the word. Each share, each repost, served as a beacon of hope in the vast sea of the internet, illuminating the path toward recovery.As the days passed without any promising leads, frustration threatened to overshadow my determination. However, I refused to succumb to despair. Instead, I intensified my efforts, exploring unconventional avenues in pursuit of my lost camera.One such unconventional approach involved creatingflyers adorned with images of the camera and contact details. I distributed these flyers in the vicinity wherethe loss occurred, hoping to catch the attention of passersby who might have seen or heard something relevantto my search.Additionally, I leveraged technology to aid in my quest.I scoured online marketplaces and auction websites, monitoring listings for any signs of my missing camerabeing put up for sale. This digital vigilance required vigilance and meticulous attention to detail, but the potential payoff justified the effort.Despite my exhaustive efforts, days turned into weeks, and hope began to dwindle. It seemed as though my lost camera had vanished into the ether, forever beyond my reach. Nevertheless, I refused to concede defeat, clinging to the belief that persistence would eventually yield results.Then, just when I least expected it, a breakthroughemerged. A kind-hearted individual reached out, claiming to have found a camera matching the description I had provided. Elation surged through me as I arranged to meet the person and retrieve my long-lost possession.The reunion with my camera was an emotional moment, marked by relief and gratitude. Holding it in my hands once again, I realized the true value of perseverance and resilience in the face of adversity. The journey to find my lost camera had been arduous, but it had also been a testament to the power of determination and community support.In conclusion, the experience of losing andsubsequently finding my camera was a poignant reminder of the importance of never giving up hope, even in the face of seemingly insurmountable obstacles. Through a combinationof traditional detective work, modern technology, and the support of others, I was able to reclaim what was lost and rediscover a sense of optimism amidst adversity.。
Am I wasting my time organizing email?A study of email refindingSteve Whittaker, Tara Matthews, Julian Cerruti, Hernan Badenes, John TangIBM Research - AlmadenSan Jose, California, USA{sjwhitta, tlmatthe}@, {jcerruti, hbadenes}@, johntang@ABSTRACTWe all spend time every day looking for information in our email, yet we know little about this refinding process. Some users expend considerable preparatory effort creating complex folder structures to promote effective refinding. However modern email clients provide alternative opportunistic methods for access, such as search and threading, that promise to reduce the need to manually prepare. To compare these different refinding strategies, we instrumented a modern email client that supports search, folders, tagging and threading. We carried out a field study of 345 long-term users who conducted over 85,000 refinding actions. Our data support opportunistic access. People who create complex folders indeed rely on these for retrieval, but these preparatory behaviors are inefficient and do not improve retrieval success. In contrast, both search and threading promote more effective finding. We present design implications: current search-based clients ignore scrolling, the most prevalent refinding behavior, and threading approaches need to be extended.AUTHOR KEYWORDSEmail, refinding, management strategy, search, conversation threading, folders, usage logging, field study, PIM.ACM Classification KeywordsH5.3 Group and Organization Interfaces: Asynchronous interaction, Web-based interaction.INTRODUCTIONThe last few years have seen the emergence of many new communication tools and media, including IM, status updates, and twitter. Nevertheless, in work settings email is still the most commonly used communication application with reported estimates of 2.8 million emails sent per second [15]. Despite people’s reliance on email, fundamental aspects of its usage are still poorly understood. This is especially surprising because email critically affects productivity. People use email to manage everyday work tasks, using the inbox as a task manager and their archives for finding contacts and reference materials [2,7,23]. This paper looks at an important, under-examined aspect of task management, namely how people refind messages in email. Refinding is important for task management because people often defer acting on email. Dabbish et al. [7] show that people defer responding to 37% of messages that need a reply. Deferral occurs because people have insufficient time to respond at once, or they need to gather input from colleagues [2,23]. Refinding also occurs when people return to older emails to access important contact details or reference materials.Prior work identifies two main types of email management strategies that relate to different types of refinding behaviors [13,23]. The first management strategy is preparatory organization. Here the user deliberately creates manual folder structures or tags that anticipate the context of retrieval. Such preparation contrasts with opportunistic management that shifts the burden to the time of retrieval. Opportunistic refinding behaviors such as scrolling, sorting or searching do not require preparatory efforts. Previous research has noted the trade-offs between these management strategies. Preparation requires effort, which may not pay off, for example if folders do not match retrieval requirements. But relying on opportunistic methods can also compromise productivity. Active foldering reduces the complexity of the inbox. Without folders, important messages may be overlooked when huge numbers of unorganized messages accumulate in an overloaded inbox [2,7,23].Choice of management strategy has important productivity implications since preparatory strategies are costly to enact. Other work has shown that people spend an average of 10% of their total email time filing messages [3]. On average, they create a new email folder every 5 days [5]. People assume that such preparatory actions will expedite future retrieval. However, we currently lack systematic data about the extent to which these folders are actually used, because none of these prior studies examined actual access behaviors. Such access data would allow us to determine whether time spent filing is time well spent. This is important because prior work suggests that organization can be maladaptive, with people creating many tiny ‘failed folders’ or duplicate folders concerning the same topic [23].Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, or republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee.CHI 2011, May 7–12, 2011, Vancouver, BC, Canada.Copyright 2011 ACM 978-1-4503-0267-8/11/05....$10.00.Another important reason for reexamining how people manage and access email is the emergence of new search-oriented clients such as Gmail [12]. Such clients assume the benefits of the opportunistic approach as they do not directly support folders. A second novel characteristic is that they are thread-based. Building on much prior work on email visualization [2,19,20], Gmail offers intrinsic organization, where messages are automatically structured into threaded conversations.Threads potentially help people more easily access related messages. A thread-based inbox view is also more compact, enabling users to see more messages without scrolling, helping people who rely on leaving messages in the inbox to serve as ‘todo’ reminders. We therefore examine the utility of these new email client features by determining whether search and threads are useful for retrieval.We extend approaches used in prior work that tried to identify email management strategies by analyzing single snapshots of email mailboxes for their structural properties, such as mailbox size, number of folders, and inbox size, [2,11,13,23]. We also know that users are highly invested in their management strategies [2,23] so it is important to collect objective data about their efficacy. We therefore logged actual daily access behaviors for 345 users enacting over 85,000 refinding operations, and looked at how access behavior relates to management strategy. Our method has the benefit of capturing systematic, large-scale data about refinding behaviors ‘in the wild’. It complements smaller-scale observational studies of email organization [1,2,23], and lab experiments that attempt to simulate refinding (‘find the following emails from your mailbox’) [10]. Finally our study also extends the set of users studied. Unlike prior work, only 2% of our users are researchers.To apply this logging approach we needed to implement and instrument a fully featured modern email client. Later, we describe the client used to collect this data, which supports efficient search, tags, and threading.This paper looks at the main ways that people re-access email information, comparing the success of preparatory vs. opportunistic retrieval. We explore how two aspects of refinding interrelate. On one level we wish to characterize basic refinding behaviors to determine whether people typically search, scroll, access messages from folders, or sort when accessing emails. We also want to determine the efficiency and success of these different behaviors, as well as how behaviors interrelate. At the next level, we want to examine the relationship between refinding behaviors and people’s prior email management strategies, to determine for example, whether people who have constructed complex folder organizations are indeed more reliant on these at retrieval. We therefore ask the following specific questions: Access behaviors: What are people’s most common email refinding behaviors, when provided with a modern client that supports search, tagging, and threads, as well as folders? Do people opportunistically refind emails by scanning their inbox, searching, or sorting via header data? Or instead do they use preparatory behaviors that exploit pre-constructed organization in the form of folders or tags? Also, what are the interrelations between behaviors? For example, are there people who rely exclusively on search and never use folders for access?Relations between management strategy and access behaviors: Does prior organizational strategy influence actual retrieval? Are people who prepare for retrieval by actively filing, more likely to use these folders for access? In contrast, are people who make less effort to prepare for retrieval more reliant on search, scanning, and sorting? Impact of threads on access: Do threads affect people’s access behaviors? Are people with heavily threaded emails less reliant on folders for access?Efficiency and success of management strategies and access behaviors: We also wanted to know whether access behaviors affect finding outcome. Which behaviors are more efficient and which lead to more successful finding? We might expect folder-access to be more successful than search, as people have made deliberate efforts to organize messages into specific memorable categories. On the other hand, search may be more efficient as it might take users longer to access complex folder hierarchies. Finally, are people who create many folders more successful and efficient at retrieval?RELATED WORKStudies of email use have documented how people use email in diverse ways, including for task management and personal archiving [2,13,23]. Foldering behaviors are the most commonly studied email management practice. Whittaker and Sidner [23] characterized three common management strategies: no filers (forego using email folders, relying on browsing and search), frequent filers (minimize the number of messages in their email inbox by frequently filing into many folders and relying on folders for access), and spring cleaners (periodically clean their inbox into many folders). Fisher et al. [11] also added a fourth management strategy: users who kept their inboxes trim by filing into a small set of folders. Other studies [1,2] discovered similar management strategies, but also found that users did not exclusively fall into one category. Rather, users employ a combination of strategies over time [1,11]. Grouping messages together according to conversational threads (i.e., a reply chain of messages on a common topic) has been explored in prior research [2,3,19,20]. Gmail [12] uses threads (rather than individual messages) as the basic organizing unit for email management, although a more recent version also combines the functionality of folders and labels [16]. A thread-based inbox view is more compact, enabling users to see more messages without scrolling, helping those who rely on leaving messages in the inbox to serve as ‘todo’ reminders. Collecting messages into threads also gives users the context for interpreting an individual message [19]. While Venolia and NeustaedterFigure 1. User interface design for Bluemail, showing panes for foldering (A) and tagging (B), on the left, a message list area in the top center showing a threaded message (C) and a selected thread (D) which is displayed in the message preview below showing an interface to add tags to a message (E) and display tags already added to a message (F).[19] and Bellotti et al. [2] conducted studies of threading with small groups of users, there has not been a large-scale study of thread usage.One might think that the emergence of effective search would lead users to reduce preparatory foldering. Yet Teevan et al. [18] observed for web access that even a perfect search engine could not fully satisfy users’ needs for managing their information. Instead, their users employed a mix of preparatory and opportunistic refinding behaviors. We explore if this result holds for email refinding as well. Other work has examined how people refind personal files on their personal computers, showing that people are more reliant on folder access than search. In addition, search and navigation are used in different situations: search is only used where users have forgotten where they stored a file, otherwise they rely on folders [4]. Dumais et al. [9] found that refinding emails was more prevalent than files or web documents, and that refinding tended to focus on recent emails. However, that study focused on search and did not compare it to other access methods, e.g. folders or scrolling. Elsweiler, et al. [10] looked at memory for email messages. Participants were usually able to remember whether a particular message was in their mailbox. Also, memory for specific information about each message was generally good; people remembered content, purpose, or task related information best, correctly recalling over 80% of this type of information, even when items were months old. However, frequent filers tended to remember less about their email messages. Filing information too quickly sometimes led to the creation of archives containing spurious information; premature filing also meant that users were not exposed to the information frequently in the inbox, making it hard to remember its properties or even its existence.THE BLUEMAIL SYSTEMBluemail is the email client used for this study. It is a web-based client that includes both traditional email management features such as folders, and modern attributes such as efficient search, tagging, and threads. This combination of features allowed us to directly compare the benefits of preparatory retrieval behaviors that rely on folders/tags, with opportunistic search and threading. We could not have made this direct comparison if we had used a client such as Gmail that does not directly support folders separately from tags. Also, Bluemail could be used to access existing Lotus Notes emails, making the transition to Bluemail very straightforward. For a full description of the design see [17].Figure 1 shows the main Bluemail interface. The layout follows a common email pattern with navigation panes onthe left for views and foldering (to which Bluemail adds an interface for tagging), a central content area with a message list on top, and a message preview panel at the bottom. Messages are filed into folders by drag and drop from the message list into a folder in the left pane. One novel feature of Bluemail that enhances scrolling is the Scroll Hint. As the user engages in sustained scrolling (> 1 second) the interface overlays currently visible messages with metadata such as date/author of the message currently in view. This hint provides orienteering information about visible messages without interrupting scrolling.Bluemail also supports efficient search (shown in the upper right of Figure 1) based on a full content index of all emails, with the search index being incrementally updated as new messages arrive. As in standard email clients, and unlike Gmail, messages can also be sorted by metadata fields such as sender (‘who’), or date (‘when’). The default view is by thread, which we now describe.Message ThreadsA message thread is defined as the set of messages that result from the natural reply-to chain in email. In Bluemail, threads are calculated against all the messages in a user’s email database, i.e., threads include messages even if they have been filed into different folders. This design contrasts with clients that do not have true folders (like Gmail). Bluemail uses the thread, not the individual message, as the fundamental organizing unit. Deleting, foldering, or tagging a thread acts on all the messages in the thread, even messages already foldered out of view. Figure 1C shows how threads are represented in the message list view. Each thread is gathered and collapsed into a single entry in the list. Users can toggle the view in the interface between the default threaded view and the traditional flat list of messages by clicking on the icon in the thread column header. The ‘what’ column for a thread shows the subject field corresponding to the most recently received message. After the subject text, we show in gray text as much of the message that space allows. User-applied tags are also shown pre-pended to the subject in a smaller blue font, as will be described in the tagging section below.Tagging MessagesThe interface for message tagging comprises four elements: a tag entry and display panel in the message, pre-pended tags in the list view’s ‘what’ column, a tag cloud, and a view of the message list filtered by tag. As a user tags messages, the tags are aggregated into a tag cloud as shown in Figure 1B. Clicking on a tag (anywhere a tag appears) filters the message list to show only messages across a user’s email (including other folders) with that tag. If any of those messages are part of a thread, the whole thread is shown in threaded view. Toggling to the unthreaded view shows only the individual messages marked with the tag. METHODUsersThe Bluemail prototype was released in our organization and used long term by many people. For our analyses, we focused on frequent users, i.e., people who used our system for at least a month, with an average of 64 days usage. As our main focus was on access behaviors, a criterion for inclusion was that a user had to have used each retrieval feature (folder-access, scroll, search, sort, tag-access) at least once. This assured us that users were aware of that feature’s existence. Overall 345 people satisfied these criteria. Users included people from many different job roles (marketing, executives, assistants, sales, engineers, communications) and organizational levels (managers and non-managers). Unlike many prior email studies there were few researchers (just 2% of our frequent users).MeasuresMany prior studies of email have taken a snapshot of a user at a single point in time. This approach has the disadvantage that it may capture the email system in an atypical state. To prevent this, we therefore recorded longitudinal daily system use, averaging measures across the entire period that each person used the system.General usage statisticsFor each user, we collected and averaged the following usage statistics over each day they used the system: •Days of system usage. We only included people withmore than 30 days of usage.•Total messages stored - number of messages included in all folders and the inbox.•Inbox size - number of inbox messages.•Number of folders.•Messages per thread -number of messages in each thread, excluding messages without replies.•Daily change in mailbox size. Other work notes that it is hard to determine the exact numbers of received messages because users delete messages [11]. We therefore recorded the daily change in mailbox size, i.e., the number of additional messages added or, in some cases, removed from the total archive each day. From a refinding perspective this is a better measure as it represents the set of messages users potentially access longer term.Access behaviorsWe also recorded various daily access behaviors. We logged each instance when the behavior was invoked. •Sort - whenever the user clicked the various header fields such as sender, subject, date, time, attachments, etc. •Folder-access - whenever a user opened a folder. •Scroll - whenever users scrolled for more than one second (a conservative criterion adopted to identify when scrolling is used for refinding).Table 1: Overall Usage Statistics.Mean Std. Deviation Days Used 63.97 42.61 Total Messages Stored 2568.79 3107.77 Inbox Size 870.28 1422.96 Number Folders 46.89 91.65Messages/Thread 3.61 1.54Daily Change in Size 24.24 58.07•Tag-access - whenever a user clicked on a tag. •Search - whenever the user conducted a search. •Open Message - whenever the user opened a message. •Operation duration- measured by subtracting thetimestamp of each operation from the timestamp of the subsequent operation.To preserve user privacy we did not record search terms or the names of folders and tags. We initially recorded other access operations, e.g., filter by flag (filtering for messages users had marked as important), or filter by unread messages (selecting the interface view which showed only unread messages). However, these behaviors accounted for less than 1% of all access behaviors and were only ever used by 8% and 17% of our users respectively. We therefore do not discuss them further.We also recorded the success and duration of finding sequences. We define a finding sequence as a set of access behaviors containing one or more sort, scroll, search, tag-access, or folder-access. Each finding operation was treated separately, so that opening a folder followed by a sort was treated as two separate operations. Searching followed by sorting was treated the same way. Our analysis is quantitative and relied on parsing large numbers of logfiles, so we aimed to define an automatically implementable definition of success and duration.Success: People usually want to find a target message to process the information it contains. We began by defining as successful an unbroken sequence of finding operations that terminated in a message being opened. Opening a message did not always indicate success, however. Observations of finding sequences revealed that users sometimes opened a message briefly, discovered that it was not the target, and then immediately resumed their finding operations. To determine the upper bound for this unsuccessful message opening interval, we timed 12 pilot users opening and reading two standard paragraphs from an email message that we felt would be sufficient for message identification. We found this took 29s. Any ‘open message’ operation lasting less than 29s and followed by subsequent finding operations was therefore treated as a non-terminal part of the finding sequence. 23% of sequences contained such unsuccessful opening of messages. Note that a user briefly opening a message and hitting ‘reply’ would be classified as a ‘success’ because the operation after ‘open message’ is not a finding operation.Failure: We classified as failures, sequences of finding operations that did not terminate in a message being opened, e.g., when the sequence was followed by the user closing their browser, or composing a new message.We acknowledge that finding success may also be influenced by subjective factors such as urgency or message importance. However our large-scale quantitative approach requires clearly definable success criteria, and it is hard to see how to operationalize these contextual factors in a working logfile parser.Duration: The finding sequence duration was the sum of the finding operation durations it comprised. For one specific case, we excluded final operation time: when people abandoned an unsuccessful finding sequence, there were sometimes long intervals, lasting tens of minutes before the subsequent operation. We could not assume that the user was actively engaged in that operation for the entire interval, so we excluded it.One potential limitation of this study is that we observed behavior for people who have been using our system for an average of two months. This may not be sufficient time for people to modify long-term email behaviors. To qualitatively profile our population however, we interviewed 32 users. We found that 60% regularly used Gmail, indicating that features such as tagging and search were highly familiar. Furthermore, we ensured that all users had used all access features at least once and found that certain features such as threading were immediately used ubiquitously—suggesting that people will readily change access strategy if they see the value of new technology. RESULTSOverall StatisticsTable 1 shows overall usage statistics, derived from daily samples. These are consistent with prior work (see Whittaker et al. [21] for a review), showing that users tend to build up large archives. However, the proportion (33%) of messages we observed being kept in the inbox is smaller than that reported in prior work. This may be due to different sampling methods, i.e., that we were sampling daily rather than relying on a single snapshot. Also, there may be over-representation of researchers in prior samples, and others [11] have speculated that researchers tend to hoard more than other types of workers. Finally threads did not tend to have a complex structure, with an average of 3.61 messages per thread, after we exclude singleton messages (i.e., messages without replies). As with all prior email research, there is high variability in most aspects of usage, as shown by the large standard deviations.Access BehaviorsWe next examined people’s access behaviors, which have not been systematically studied before.Table 2. Daily Usage, Distributions and Durations for Each Access Behavior. (Opportunistic behaviors are shaded.)Mean (SD) Accesses/day % of AllAccessesMean (SD)Duration insecondsFolder-accesses 0.21 (0.42)12 58.82 (30.22) Tag-accesses 0.02 (0.09) 1 not recordedSearches 0.71 (1.82)18 17.15 (36.86)Sorts 0.17 (0.33)7 13.96 (17.99)Scrolls 1.49 (1.76)62 25.77 (30.22) Overall, each person had an average of 61.75 (SD 110.7) finding sequences, lasting a mean of 69.59s (SD 33.48). Overall 88% of finding sequences were successful, and the average number of finding operations per sequence was 3.85 (SD 3.57). As expected, successful sequences contained fewer operations than unsuccessful ones (M = 3.67, SD 1.83 and M = 5.03, SD 5.26), paired t-test t(344) = 9.41, p <0.001, presumably because on encountering failure people persist in trying to find the target message.Opportunistic behaviors dominate retrievalOur first question concerned the overall frequencies of different access behaviors. We can distinguish between: (a) accesses based on preparatory activity, i.e., using folders and tags that users deliberately create in anticipation of retrieval, and (b) opportunistic accesses that do not rely on preparatory activity, i.e. sorting, scrolling and searching. Table 2 shows that opportunistic behaviors dominate. These account for 87% of accesses. This is mainly explained by the predominance of scrolling which accounts for 62% of all accesses. Of course, scrolling might be used in preparatory contexts, e.g. scrolling through a large folder. However scrolling and folder-access are highly negatively correlated (r(343)=-0.52, p<0.001). Overall then, preparatory activities (folder- and tag-accesses combined) are not prevalent. They account for just 13% of all access operations overall.A within sequence analysis indicated that specific behaviors tended to perseverate, with people relying on one or two strategies to find a specific message. Note too that there is enormous variability in individual usage for each of these behaviors (as indicated by their large standard deviations). The use of tagging was minimal, accounting for just 1% of all accesses. We therefore excluded it from subsequent analyses, removing finding sequences that included tags and relaxing the criterion that each user in the sample had to have used tag-access at least once. This added 13 users to our original user population.Efficiency of Different Access BehaviorsTable 2 also indicates large differences in duration for the different access behaviors. Each individual folder-access took approximately one minute, more than twice as long as scrolls, with both searches and sorts being relatively short (around 15s). Paired t-tests show that folder-access operations are significantly longer than scrolls (t(357) = 6.71, p<0.001). Scrolls in turn are significantly longer than searches (t(357) = 2.87, p<0.01). However, there is no difference between the durations of searches and sorts (t(357) = 0.51, p>0.05).Interrelations between Access BehaviorsWe next explored the interrelations between access behaviors, where we anticipated specific patterns. Users who have made the effort to create folders should be more reliant on a preparatory behavior like folder-access, and avoid opportunistic behaviors like search, sort, and scroll. Others we expected to rely exclusively on these opportunistic behaviors, eschewing folder-access.We found these expected combinations of access patterns. When we correlated behaviors per user, preparatory behavior, i.e. folder-access, was negatively correlated with search (r(356) = -0.25, p<0.001), and with scrolling (r(356) = -0.52, p<0.001). Thus, scrolling does not co-occur with folder-access, e.g. scrolling through large folders. As we expected, the various opportunistic behaviors positively intercorrelate, with searches correlating with sorts: r(356) = 0.23, p<0.001), and with scrolls r(356) = 0.61, p<0.001). This indicates that people tend to rely exclusively on either preparatory or opportunistic behaviors, but not a mixture of the two. This is an important result because it suggests that email clients, that mainly support search, like Gmail, are unlikely to be optimal for all users.The Relationship between Email Management Strategy, Threads and Access BehaviorsSo far our analysis has only examined access behaviors. In this section, we examine the relationship between access behaviors, threads, and email management strategy. Are people who engage in preparatory activity by making folders more likely to rely on these for retrieval? We also explore the effects of the intrinsic organization afforded by threads. Do threads make people less likely to use folders for access?People who create folders use them more often for access To analyze access behaviors with respect to management strategy, we must first operationalize management strategy. Prior work [1,13,23] proposed strategy differences, based on a combination of inbox size, number of folders as well as ‘large scale changes’ in inbox size over time. However, recent work [11] critiques these definitions arguing that they are ad hoc and do not reliably identify distinct user types. To avoid both of these problems, we used a simple propensity to organize metric based on the percentage of the user’s total mailbox that is stored in folders. People who are more committed to foldering should have a higher percentage of their information in folders, as opposed to the inbox. We conducted a median split on this percentage to divide users into high and low filers.Table 3 shows the frequency of different access behaviors (folder-access, scroll, sort, search), depending on whether a user is a high or low filer. To control for the large variance。