Internet Engineering Task Force Sally Floyd INTERNET DRAFT Jamshid Mahdavi
- 格式:pdf
- 大小:21.36 KB
- 文档页数:14

IETFIETF是Internet工程任务组(Internet Engineering Task Force)的简写。
IETF又叫互联网工程任务组,成立于1985年底,是全球互联网最具权威的技术标准化组织,主要任务是负责互联网相关技术规范的研发和制定,当前绝大多数国际互联网技术标准出自IETF。
1.IETF概述IETF(互联网工程任务组—The Internet Engineering Task Force)是松散的、自律的、志愿的民间学术组织。
IETF是一个由为互联网技术发展做出贡献的专家自发参与和管理的国际民间机构。
它汇集了与互联网架构演化和互联网稳定运作等业务相关的网络设计者、运营者和研究人员,并向所有对该行业感兴趣的人士开放。
任何人都可以注册参加IETF的会议。
IETF大会每年举行三次,规模均在千人以上。
2.IETF体系结构IETF体系结构分为三类,一个是互联网架构委员会(IAB),第二个是互联网工程指导委员会(IESG),第三个是在八个领域里面的工作组(Working Group)。
标准制定工作具体由工作组承担,工作组分成八个领域,分别是Internet路由、传输、应用领域等等。
IAB成员由IETF参会人员选出,主要是监管各个工作组的工作状况,它必须非常认真的考虑Internet是什么,它正在发生什么变化以及我们需要它做些什么等问题。
互联网工程指导委员会(IESG)主要的职责是接收各个工作组的报告,对他们的工作进行审查,然后对他们提出的各种各样的标准、各种各样的建议提出指导性的意见,甚至从工作的方向上、质量上和程序上给予一定的指导。
IETF基本上不太涉及应用领域,但仍设立了一个应用领域。
另外凡是没有归到以上那些领域的研究课题,都把它归至此类。
IETF实际上有上百个工作组,这里是真正完成工作的地方。
IETF大量的技术性工作均由其内部的各类工作组协作完成。
这些工作组按不同类别,如路由、传输、安全等专项课题而分别组建。

Ipsec VPN调研总结一、Ipsec原理Ipsec vpn指采用IPSec协议来实现远程接入的一种VPN技术,IPSec全称为Internet Protocol Security,是由Internet Engineering Task Force (IETF) 定义的安全标准框架,用以提供公用和专用网络的端对端加密和验证服务。
Ipsec是一个协议集,包括AH协议、ESP协议、密钥管理协议(IKE协议)和用于网络验证及加密的一些算法。
1、IPSec支持的两种封装模式传输(transport)模式:只是传输层数据被用来计算AH或ESP头,AH或ESP头以及ESP加密的用户数据被放置在原IP包头后面。
隧道(tunnel)模式:用户的整个IP数据包被用来计算AH或ESP头,AH或ESP头以及ESP加密的用户数据被封装在一个新的IP数据包中。
2、数据包结构◆传输模式:不改变原有的IP包头,通常用于主机与主机之间。
◆隧道模式:增加新的IP头,通常用于私网与私网之间通过公网进行通信。
3、场景应用图4、网关到网关交互图5、Ipsec体系结构:6、ipsec中安全算法●源认证用于对对等体的身份确认,具体方法包含:PSK(pre-share key);PK3(public key infrustructure公钥基础设施)数字证书,RSA等,后两种为非对称加密算法。
●数据加密对传输的数据进行加密,确保数据私密性,具体对称加密算法包含:des(data encrypt standard)共有2种密钥长度40bits,56bits,3des密钥长度为56bits的3倍;aes(advanced encrypted standard)AES 加密共有三种形式,分为AES 128(128-bit 长度加密),AES 192(192-bit 长度加密)以及AES 256(256-bit 长度加密)。
●完整性校验对接收的数据进行检查,确保数据没有被篡改,主要使用hash算法(HMAC hashed message authentication code),包含MD5(message digest输出128bit校验结果);SHA-1(secure hash algorithm 1)输出160bits校验结果。

IETF 名词解释
IETF是指互联网工程任务组(Internet Engineering Task Force),是一个负责互联网标准制定的国际组织。
以下是一些与IETF 相关的名词解释:
•RFC: 请求评论(Request for Comments),是IETF 的一种文件类型,用于记录和传播标准、协议、过程和相关信息。
RFC 文档由IETF 社区
进行讨论、定义和发布。
•Internet-Draft: 互联网草案,是IETF 开发新标准的初步文档,用于征求社区反馈并最终进入标准化流程。
•Working Group: 工作组,是IETF 的一个组织单位,由感兴趣的成员组成,研究并开发特定的标准。
•IESG: 互联网工程指导组(Internet Engineering Steering Group),是IETF 的一个组织,负责管理IETF 的全球标准化进程。
•IRTF: 互联网研究任务组(Internet Research Task Force),是IETF 的研究分支,负责对互联网技术进行研究和探索。

计算机网络管理课程设计1.引言简单网络管理协议(SNMP)首先是由Internet工程任务组织(Internet Engineering Task Force)(IETF)的研究小组为了解决Internet上的路由器管理问题而提出的。
SNMP被设计成与协议无关,所以它可以在IP,IPX,AppleTalk,OSI以及其他用到的传输协议上被使用。
它具有简单性,易于扩展性的特点。
SNMP是一系列协议组和规范(见下表),它们提供了一种从网络上的设备中收集网络管理信息的方法。
SNMP也为设备向网络管理工作站报告问题和错误提供了一种方法。
名字说明MIB 管理信息库SMI 管理信息的结构和标识SNMP 简单网络管理协议从被管理设备中收集数据有两种方法:一种是只轮询(polling-only)的方法,另一种是基于中断(interrupt-based)的方法。
Snmp发展到现在共有三个版本,本课程设计是基于snmpv1版本。
2.设计任务及思想2.1任务:设计一个Manager。
Manager可以向华为网络设备发送get和set报文,并获得有效操作结果,实现版本为SNMPv1.开发工具:VC++(Win32)内容: Socket网络通信、 BER编码、BER解码、SNMP报文构造、SNMP报文解析、用户输入/输出。
2.2思想:根据snmp协议,分析抓包软件抓出的结果。
Manager在进行操作时,先对要发送的报文进行构造,然后对要发送的报文各数据类型依据asn.1进行编码再发送。
agent接收到报文后,进行报文解析,再解码。
看manager的要求是什么,然后回应一个报文,即response 报文,manager即对回应的报文进行解析解码,整个过程由socket通信完成,snmp报文封装在udp中发送。
3设计过程2.1 BER编码和解码Ber编码是整个设计过程中的极为重要的部分,一个报文有很多段组成,每段的数据类型都不尽相同。
AR路由器配置IKE方式的IPSec VPNIPSec(Internet Protocol Security)是IETF(Internet Engineering Task Force)制定的一组开放的网络安全协议,在IP层通过数据来源认证、数据加密、数据完整性和抗重放功能来保证通信双方Internet上传输数据的安全性。
在Internet的传输中,绝大部分数据的内容都是明文传输的,这样就会存在很多潜在的危险,比如:密码、银行帐户的信息被窃取、篡改,用户的身份被冒充,遭受网络恶意攻击等。
网络中部署IPSec后,可对传输的数据进行保护处理,降低信息泄漏的风险。
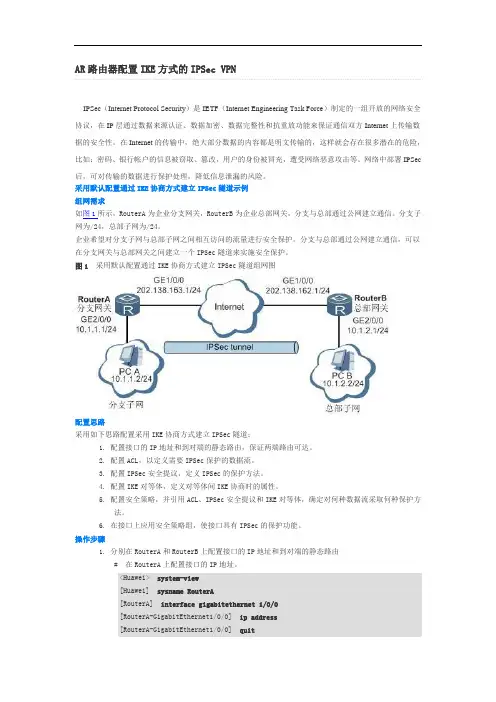
采用默认配置通过IKE协商方式建立IPSec隧道示例组网需求如图1所示,RouterA为企业分支网关,RouterB为企业总部网关,分支与总部通过公网建立通信。
分支子网为/24,总部子网为/24。
企业希望对分支子网与总部子网之间相互访问的流量进行安全保护。
分支与总部通过公网建立通信,可以在分支网关与总部网关之间建立一个IPSec隧道来实施安全保护。
图1 采用默认配置通过IKE协商方式建立IPSec隧道组网图配置思路采用如下思路配置采用IKE协商方式建立IPSec隧道:1.配置接口的IP地址和到对端的静态路由,保证两端路由可达。
2.配置ACL,以定义需要IPSec保护的数据流。
3.配置IPSec安全提议,定义IPSec的保护方法。
4.配置IKE对等体,定义对等体间IKE协商时的属性。
5.配置安全策略,并引用ACL、IPSec安全提议和IKE对等体,确定对何种数据流采取何种保护方法。
6.在接口上应用安全策略组,使接口具有IPSec的保护功能。
操作步骤1.分别在RouterA和RouterB上配置接口的IP地址和到对端的静态路由# 在RouterA上配置接口的IP地址。
<Huawei> system-view[Huawei] sysname RouterA[RouterA] interface gigabitethernet 1/0/0[RouterA-GigabitEthernet1/0/0] ip address[RouterA-GigabitEthernet1/0/0] quit[RouterA] interface gigabitethernet 2/0/0[RouterA-GigabitEthernet2/0/0] ip address[RouterA-GigabitEthernet2/0/0] quit# 在RouterA上配置到对端的静态路由,此处假设到对端的下一跳地址为。

通信行业英语中英对照手册(I)-OCU ISDN-Office Channel Unit ISDN的局内信道单元I/O Input / Output 输入/输出I2T Intelligent Interface Technology 智能接口技术IA Information Access 信息存取IA Intelligence Appliance 智能家电IA Internal Authentication 内部认证IA Internet Address 因特网地址IAB Internet Activities Board 因特网活动委员会IAB Internet Architecture Board 因特网体系委员会IAC Image Attenuation Coefficient 图像衰减系数IAC ISDN Access Control ISDN接入控制IAD Integrated Access Device 集成接入设备IAF Image Analysis Facility 图像分析设备IAM Initial Address Management 初始地址管理IAM Initial Address Messege 初始地址消息IAN Integrated Analog Network 综合模拟网IAN Irregularly Activated Network 不规则激活网络IANA Internet Assigned Number Authority 因特网分址机构IAP Internet Access Point 网际访问点IAP Internet Access Provider 因特网接入服务供应商IAR Intelligent Automatic Rerouting 智能型自动重选路由IAS Integrated Access Server 综合接入服务器IAS Interactive Application Server 交互应用服务器IB-DCA Interence-Based Dynamic Channel Allocation 基于干扰的信道动态分配IBC Information Bearer Channel 信息承载信道IBC Integrated Broadband Communication 综合宽带通信IBCN Integrated Broadband Communication Network 综合宽带通信网IBCN International Broadband Communication Network 国际宽带通信网络IBDN Integrated Building Distribution Network 楼宇综合布线网络IBGP Internal Border Gateway Protocol 内部边界网关协议IBI Intergrated Building Intelligent 综合大楼智能化IBMS Intelligent Building Management System 智能大厦管理系统IBN Integrated Broadband Network 综合宽带网IBS Intelligent Building System 智能大厦系统IBT Internet Browsing Terminal 因特网浏览终端IBWN Indoor Broadband Wireless Network 室内宽带无线网络IC Image Check 图像检验IC Image Compression 图像压缩IC Integrated Circuit 集成电路IC Interlock Code 互锁码ICB Incoming Call Barred 来话加锁ICBI Inter-Channel inter-Block Interference 信道间信息组间的干扰ICC Instantaneous Channel Characteristics 信道瞬态特性ICC Internet Call Center 因特网呼叫中心ICDN Integrated Communication Data Network 综合通信数据网络ICE In-Circuit Emulation 在线仿真ICE InterConnect Equipment 互连设备ICE Interface Configuration Environment 接口配置环境ICH Incoming CHannel 来话信道ICI Intelligent Communications Interface 智能通信接口ICI Inter-Carrier Interference 载波间干扰ICI Inter-Channel Interference 信道间干扰ICM Image Compression Manager 图像压缩管理器ICM Incoming Call Management 来话呼叫管理ICMP Inernal Control Message Protocol 内部控制信息协议ICMP Internet Control Message Protocol 因特网控制报文协议ICP Incoming Call Packet 呼入分组信息ICP Internal Connection Protocol 内部连接协议ICP Internet Content Provider 因特网内容服务供应商ICP Interworking Control Protocol 互通控制协议ICR Initial Cell Rate 初始信元率ICS ISDN Control Sublayer ISDN控制子层ICSA International Computer Security Associatiion 国际计算机安全协会ICT InComing Trunk 来话中继ICT Information and Communication Technology 信息和通信技术ICUG International Closed User Group 国际闭合用户群ICW Internet Call Waiting 因特网呼叫等待IDA Integrated Digital Access 综合数字接入IDA Interchange of Data between Administrations 机构间的数据交换IDA Internet Direct Access 因特网直接接入IDA Intrusion Detection Agent 入侵检测代理IDARA Improved Distributed Adaptive Routing Algorithm 改进的分布式自适应路由算法IDC Internet Data Center 因特网数据中心IDCC Integrated Data Communication Channel 综合数据通信信道IDCT Inverse Discrete Consine Transform 离散余弦逆变换IDD International Direct Dialing 国际直拨IDI Initial Domain Identifier 初始域标识符IDL Interactive Distance Learning 交互式远程学习IDL Interface Definition Language 接口定义语言IDL International Data Line 国际数据线路IDLC Integrated Digital Loop Carrier 综合数字环路载波IDMS Integrated Database Management System 综合数据库管理系统IDN Integrated Data Network 综合数据网络IDN Integrated Digital Network 综合数字网IDN Intelligent Data Network 智能数据网络IDN Interactive Data Network 交互式数据网络IDN International Directory Network 国际目录网络IDNET IDentification NETwork 认证网IDP Internet Directory Provider 因特网目录服务供应商IDPR Inter-Domain Policy Routing 域间策略路由选择IDR Intermediate Data Rate 中等数据速率IDRP InterDomain Routing Protocol 域间路由选择协议IDS Intrusion Detection System 入侵检测系统IDS Isochronous Data Services 等时数据业务IDSE International Data Switching Exchange 国际数据交换机(局)IDSE Internetworking Data Switching Exchange 互连网数据交换机(局)IDSL ISDN DSL ISDN数字用户线IDSP Intelligent Dynamic Service Provisioning 智能型动态业务提供IDSS Intelligent Decision Support System 智能决策支持系统IDT Integrated Digital Terminal 综合数字终端IDT Intelligent Data Terminal 智能数据终端IDT Interactive Data Terminal 交互数据终端IDTC International Digital Transmission Center 国际数字传输中心IDU InDoor Unit 室内单元IDU Interface Data Unit 接口数据单元IEC Integrated Ethernet Chip 集成以太网电路芯片IEC InterExchange Carrier 局间载波IEC International Electrotechnical Commission 国际电工委员会IEE Institute of Electrical Engineers 电气工程师学会(英国)IEEE Institute of Electrical and Electronics Engineers 电气和电子工程师学会(美国) IEN Internet Experiment Note 因特网实验备忘录IEP Internet Equipment Provider 因特网设备供应商IEPG Internet Engineering and Planning Group 因特网工程和规划组IES ISDN Earth Station 综合业务数字网络地球站IESG Internet Engineering Steering Group 因特网工程指导组IETF Internet Engineering Task Force 因特网工程任务组IEW Intelligent and Electronic Warfare 智能和电子战IF Intermediate Frequency 中频IFD InterFace Device 接口设备IFH Intelligent Frequency Hopping 智能跳频IFIP International Federation for Information Processing 国际信息处理联合会IFITL Integrated Fiber In The Loop 综合光纤环路IFPH Inter-network FreePHone 网间被叫付费电话IFS Interactive Financial Services 交互式金融服务IFS InterFace Specification 接口规范IFS International Freephone Service 国际免费电话(被叫付费电话)IFU Interworking Functional Unit 互通功能单元IG Interactive Graphics 交互式图形IG International Gateway 国际网关IGD Interaction Graphics Display 交互式图形显示IGL Interactive Graphics Library 交互式图形库IGMP Internet Group Management Protocol 因特网组管理协议IGP Interior Gateway Protocol 内部网关协议IGRP Interior Gateway Routing Protocol 内部网关路由协议IGS Information Group Separator 信息组分隔符IHDL Input Hardware Des criptive Language 输入硬件描述语言IHL Internet Header Length 因特网报头长度IHV Independent Hardware Vendor 独立硬件商II Image Information 图像信息IIA Interactive Instructional Authoring 交互式教学写作IIA Internet Image Appliance 网络影像家电IIAS Interactive Instructional Authoring System 交互式教学写作系统IIC Incoming International Center 入局国际中心IID Image Intensifier Device 图像增强设备IIIN Intelligent Integrated Information Network 智能综合信息网络IIP Interface Information Processor 接口信息处理器IIS Internet Information Server 因特网信息服务器IIS Internet Information Service 因特网信息服务IISP Interim Inter-switch Signaling Protocol 临时的交换机间的信令协议IITA Information Infrastructure Technology and Application 信息基础设施技术及应用IITF Information Infrastructure Task Force 信息基础设施任务组IKBS Intelligent Knowledge Based System 基于知识的智能系统IKE Internet Key Exchange 因特网密钥交换IL Insertion Loss 插入损耗ILC Intelligent Line Card 智能线路卡ILD Insertion Loss Deviation 插入损耗偏差ILEC Incumbent Local Exchange Carrier 在业的本地交换运营公司ILI Idle Line Indicating 空闲线路指示ILMI Integrated Local Management Interface 综合本地管理接口ILMI Interim Local Management Interface 临时本地管理接口ILSLA Injection Locked Semiconductor Laser Amplifier 注入锁定半导体激光放大器IM Image Mixing 图像混合IM Instant Messaging 即时传信IM Integrated Modem 集成式调制解调器IM Interface Module 接口模块IM Inverse Multiplexing 反向复用IMA Interactive Multimedia Association 交互式多媒体协会IMAP Interactive Mail Access Protocol 交互邮件访问协议IMAP Internet Messaging Access Protocol 因特网消息存取协议IMAP4 Internet Message Access Protocol 4 因特网信息存取协议第4版IMC Inter-Module Connector 模块间连接器IMC International Maintenance Center 国际维护中心IMCC Inter-Module Communication Controller 模块间通信控制器IMEI International Mobile Equipment Identity 国际移动设备标识IMF InterMediate Fiber 中间光纤IMIS Integrated Management Information System 综合管理信息系统IMNI Internal Multimedia Network Infrastructure 多媒体网络内部基础设施IMP Interface Message Processor 接口报文处理器IMP Interface Module Processor 接口模块处理器IMS Information Management System 信息管理系统IMS Interactive Multimedia Service 交互式多媒体服务IMSI International Mobile Subscriber Identifier 国际移动用户标识符IMT Intelligent Multimode Terminal 智能多模式终端IMTC Internatinal Multimedia Television Committee 国际多媒体电视委员会IMTS Improved Mobile Telephone Service 改进的移动电话业务IMTV Interactive Multimedia TeleVision 交互式多媒体电视IMUX Input MUltipleX 输入复用IN Integrated Netowrk 综合网络IN Intelligent Network 智能网IN Interconnected Network 互连网络IN Internal Node 内节点IN-SL IN Service Logic 智能网业务逻辑IN-SM Intelligent Network Switching Manager 智能网交换管理器IN-SSM Intelligent Network Switching State Manager 智能网交换状态管理器IN-SSM Intelligent Network Switching Status Model 智能网交换状态模型INA Information Network Architecture 信息网体系结构INA Integral Network Arrangement 整体网络布局INA Integrated Network Architecture 综合网络体系结构INAP Intelligent Network Application Part 智能网应用部分INAP Intelligent Network Application Protocol 智能网应用协议INC Integrated Network Connection 综合网络连接INCC International Network Controlling Center 国际网络控制中心INCM Intelligent Network Conceptual Model 智能网概念模型INCS-1 Intelligent Network Capability Set-1 智能网能力组1INDB Intelligent Network DataBase 智能网数据库INDBMS Intelligent Network DataBase Management System 智能网数据库管理系统INE Intelligent Network Element 智能网元素INFM Intelligent Nework Functional Model 智能网功能模型INFO Integrated Network using Fiber Optics 采用光纤的综合网INI Intelligence Network Interface 智能网络接口INIC ISDN Network Identification Code ISDN网标识码INM Integrated Network Management 综合网络管理INM Integrated Network Monitoring 综合网监视INMARSAT INternational MARritime SAT ellite organization 国际海事卫星组织INMC International Network Management Center 国际网络管理中心INMOS IN service Management and Operation System 智能网业务管理及运行系统INMS Integrated Network Management System 综合网络管理系统INMS Intelligent Network Management System 智能网络管理系统INN Intermediate Network Node 中间网络节点INNO IN Network Operator 智能网运营商INP Intelligent Network Processor 智能网络处理器INS Information Network System 信息网络系统INS Intelligent Network Service 智能网络服务INSAT INternational SATellite 国际卫星INSES IN Services Emulation System 智能网业务仿真系统INSOS IN Service Operation System 智能网业务*作系统INSP Intelligent Network Service Provider 智能网服务供应商INSS Intelligent Network Service Subscriber 智能网业务用户INSTS IN Surveillance and Testing System 智能网监视和测试系统INT Interactive News Television 交互式电视新闻INTB IN TestBed 智能网试验台INTCO INT ernational COde of signal 国际信号码INTELSAT INternational TELecommunication SATellite 国际通信卫星(组织) INTIP INT egrated Information Processing 综合信息处理INTS Integrated National Telecommunication System 国家综合电信系统INTS INTernational Switch 国际交换INTS Inter-Network Time Slot 网络内部时隙INTSE INTelligent System Environment 智能系统环境IO Integrated Optics 集成光学IOAS Intelligence Office Automatic System 智能办公室自动化系统IOBB Input Output BroadBand 宽带输入输出IOC Input.Output Channel 输入/输出信道IOC Input / Output Controller 输入/输出控制器IOC Integrated Optical Circuit 集成光路IOC INTELSAT Operations Center 国际卫星组织*作中心IOC InterOffice Channel 局间信道IOCA Image Object Content Architecture 图像对象内容体系结构IOD Information On Demand 信息点播IODC International Operator Direct Calling 国际运营商直接呼叫IOLA Input / Output Link Adapter 输入/输出链路适配器IOLC Input / Output Link Control 输入/输出链路控制IOM Image-Oriented Memory 面向图像的存储器IOM Input / Output Multiplexer 输入/输出多路转换器IOM Integrated-Optic Modulator 集成光学调制器ION Integrated On-demand Network 综合按需服务网络IONI ISDN Optical Network Interface ISDN光网络接口IOP Input / Output Processor 输入输出处理器IOPDS Integrated-Optic Position / Displacement Sensor 集成光学位置/位移传感器IOS Integrated Office System 集成办公室系统IOS Intelligent Office System 智能办公室系统IOS Interactive Operating System 交互式*作系统IOS Internet Operating System 因特网*作系统IOS Internetwork Operating System 网间*作系统IOSB Input / Output Status Block 输入/输出状态块IOSC Input / Output Switching Channel 输入/输出交换通道IOSN Intelligent Optical Shuttle Node 智能光信息往返节点IOT Intra Office Trunk 局内中继IOTB Input / Output Transfer Block 输入/输出传送块IP Image Processing 图像处理IP Information Processing 信息处理IP Intelligent Peripheral 智能外设IP Internet Protocol 因特网协议IP Internetwork Protocol 网际协议IP Internetworking Protocol 组网协议IP Interworking Protocol 互通协议IPA Image Processing Algorithm 图像处理算法IPA Inerworking by Port Access 端口接入的互通IPBX International PBX 国际PBXIPC Integrated Peripheral Channel 集成外围通道IPC Intelligent Peripheral Controller 智能外设控制器IPC Inter-Personal Communications 人际通信IPC Inter-Process Communication 进程间通信IPC Inter-Processor Communication 处理器间通信IPCDN IP over Cable Data Network 电缆数据网传送IPIPCE International Path Core Element 国际通路核心单元IPCP IP Control Protocol IP控制协议IPCSM Input Port Controller SubModule 输入端口控制器的子模块IPDC IP Device Control IP设备控制IPE In-band Parameter Exchange 带内参数交换IPEI International Portable Equipment Identity 国际便携式设备标识IPF Image Processing Facility 图像处理设备IPG Interactive Program Guide 交互式节目指南IPG Inter-Packet Gap 分组信息间隙IPI Initial Protocol Identifier 初始协议标识符IPI Intelligent Peripheral Interface 智能外围接口IPL Initial Program Load 初始程序装入IPLB IP Load Balancing IP负载平衡IPLC International Public Leased Circuit 国际公用出租线路IPLI Internet Private Line Interface 因特网专用线接口IPLTC International Private Leased Telecommunication Circuit 国际专用租线通信电路IPM Inter-Personal Messeging 人际传信IPM-EOS Inter-Personal Message Element Of Service 人际报文业务单元IPM-UA Inter-Personal Messeging User Agent 人际传信用户代理IPME Inter-Personal Messaging Environment 人际传信环境IPMS Inter-Personal Messaging Service 人际传信业务IPMS Inter-Personal Messaging System 人际传信系统IPMS-MS Inter-Personal Messaging System Message Store 人际传信系统信息存储IPMS-UA Inter-Personal Messaging System User Agent 人际传信系统用户代理IPN Instant Private Network 瞬时专用网络IPN Inter-Personal Notification 人际通知IPng Internet Protocol next generation 下一代因特网协议IPOA IP Over ATM ATM网络承载IPIPP Internet Payment Provider 因特网支付业务提供商IPP Internet Platform Provider 因特网平台供应商IPPR Image Processing and Pattern Recognition 图像处理和模式识别IPR Intellectual Property Rights 知识产权IPS Image Processing System 图像处理系统IPS Information Processing System 信息处理系统IPS Information Protection System 信息保护系统IPS Intelligent Protection Switching 智能保护交换IPsec IP security protocol IP安全协议IPSF IP Service Function IP业务功能IPSS International Packet Switched Service 国际分组交换业务IPT Information Processing Technique 信息处理技术IPT Information Providing Terminal 信息提供终端IPUI International Portable User Identity 国际便携式用户标识IPv6 IP version 6 第六版IPIPX Internet Packet eXchange 因特网分组交换IPX Internetwork Packet eXchange 网际包(分组)交换IPX Interprocess Packet eXchange 进程间分组交换IQ Information Query 信息查询IQL Interactive Query Language 交互式查询语言IR Incoming Route 入路由IR Information Retrieval 信息检索IR InfraRed 红外IR Intelligent Robot 智能机器人IR Internal Router 内部路由器IRC Internet Relay Chat 因特网中继交谈IrDA Infra-red Data Association 红外数据协会IRFU Integrated Radio Frequency Unit 综合无线电频率单位IRI InfraRed Image 红外图像IRIM InfreRed Interface Module 远端接口模块IRIS Integrated platform for Regional Information System 地区信息系统用综合平台IRL Inter-Repeater Link 中继器间链路IRLAP InfraRed Link Access Protocol 红外链接存取协议IrLAP IrDA Link Access Protocol IrDA链路接入协议IRM Integrated Reference Model 综合参考模型IrMC Infrared Mobile Communication 红外移动通信IRN Information Resource Network 信息资源网络IRN Intermediate Routing Node 中间路由选择节点IRP Internal Reference Point 内部参考点IRP International Routing Plan 国际路由规划IRQ Information Repeat reQuest 信息重传请求IRSG Internet Research Steering Group 因特网研究指导组IRSU ISDN Remote Subscriber Unit ISDN远端用户单元IRTF Internet Research T ask Force 因特网研究任务工作组IS Imaging System 成像系统IS Information Science 信息科学IS Information System 信息系统IS Integrated Service 综合业务IS Intelligence System 智能系统IS Interactive Service 交互式业务IS Interactive Signal 交互信号IS Interface Specification 接口规范IS Interim Standard 临时标准IS-IS Intermediate System-to-Intermediate System 中间系统到中间系统ISA Industry Standard Architecture 工业标准体系结构ISA Information System Architecture 信息系统结构ISA Interim Standard Architecture 临时标准体系ISAN Integrated Service Analog Network 综合业务模拟网ISAP Interactive Speech Application Platform 交互语言应用平台ISAPI Internet Server Application Programming Interface 因特网服务器应用编程接口ISB Intelligent Signaling Bus 智能信令总线ISB Interface Schduling Block 接口调度块ISC International Switching Center 国际交换中心ISC Internet Software Consortium 因特网软件联盟ISC InterStellar Communications 星际通信ISCC International Service Coordination Center 国际业务协调中心ISCCI International Standard Commerical Code for Indexing 国际标准商用索引代码ISCII International Standard Code for Information Interchange 国际标准信息交换代码ISCP ISDN Signaling Control Part ISDN信令控制部分ISDCN Integrated Service Digital Center Network 综合业务数字中心网ISDN Integrated Service Digital Network 综合业务数字网ISDN-BA ISDN Basic rate Access ISDN基本速率接入ISDN-BRI ISDN Basid Rate Interface ISDN基本速率接口ISDN-PRA ISDN Primary Rate Access ISDN一次群速率接入ISDN-PRM ISDN Protocol Reference Model ISDN协议参考模型ISDN-SN ISDN Subscriber NumberISDN-UP ISDN User Part ISDN用户部分ISDS Integrated Switched Data Service 综合交换数据业务ISDT Integrated Service Digital Terminal 综合业务数字终端ISDX Integrated Service Digital eXchange 综合业务数字交换ISE Integrated Service Exchange 综合业务交换局ISE Integrated Switch Element 综合交换单元ISE Intelligent Synthesis Environment 智能综合环境ISEC Internet Service and Electronic Commerce 因特网服务和电子商务ISH Information Super Highway 信息高速公路ISIDE Interactive Satellite Integrated Data Exchange 交互式卫星综合数据交换ISL Inter-Satellite Link 卫星之间的链路ISLAN Integrated Services Local Area Network 综合业务局域网ISM Intelligent Synchronous Multiplexer 智能同步复用器ISM Interactive Storage Media 交互式存储媒体ISM Interface Subscriber Module 用户接口模块ISM Internet Server Manager 因特网服务器管理器ISM Internet Service Manager 因特网服务器管理程序ISMA Idle Signal Multiple Access 空闲信号多址ISMAN Integrated Services Metropolitan Area Network 综合业务城域网ISMC International Switching Maintenance Center 国际交换维护中心ISMS Image Store Management System 图像存储管理系统ISN Information System Network 信息系统网络ISN Integrated Services Network 综合业务网ISN Integrated Synchronous Network 综合同步网ISN International Signaling Network 国际信令网ISN Internet Shopping Network 因特网购物网络ISN Internet Support Node 因特网支持节点ISO International Standardization Organization 国际标准化组织ISOC Internet SOCiety 因特网学会ISODE ISO Development Environment ISO开发环境ISP Interactive Session Protocol 交互式会晤协议ISP Intermediate Service Part 中间业务部分ISP International Signaling Point 国际信令点ISP International Standardized Profile 国际标准化规格ISP Internet Service Provider 因特网服务供应商ISP Interoperable Systems Project 可互*作系统计划ISPBX Integrated Services PBX 综合业务PBXISPC International Signaling Point Code 国际信令点码ISR Initial Submission Rate 初始提供速率ISR International Simple Resell 国际简单转卖ISR Interrupt Service Routine 中断服务程序ISSLL Integrated Services over Specific Link Layer 专用链路层上的综合业务ISSS Interactive Subscriber Service Subsystem 交互式服务子系统ISTC International Satellite Transmission Center 国际卫星传输中心ISTC International Switching and Testing Center 国际交换和测试中心ISTV Integrated Service T eleVision 综合业务广播电视ISU Idle Signal Unit 空闲信号单元ISU Isochronous Slot Utilization 等时隙利用ISUP ISDN User Part ISDN用户部分ISV Independent Software Vendor 独立软件销售商ISVR Inter Smart Video Recorder 灵巧型视频录像机IT Information Technology 信息技术IT Information Theory 信息论IT International Transit 国际转接ITA International Telegraph Alphabet 国际电报字母表ITA2 International Telegraph Alphabet No.2 国际电报字母表第二版ITC Information Transfer Channel 信息传递信道ITC Intelligent Terminal Controller 智能终端控制器ITC International Telecommunication Center 国际电信中心ITC International Telephone Center 国际电话中心ITC International Television Center 国际电视中心ITC International Transit Center 国际转接中心ITC International Transmission Center 国际传输中心ITC InterToll Communication 长途局间通信ITCC International Telecommunication Control Center 国际电信控制中心ITD Interaural Time Difference 声源到达听者两耳的时间差ITDM Intelligent Time-Division Multiplexer 智能时分多路复用ITE Information Technology Equipment 信息技术设备ITE International Telephone Exchange 国际电话交换台ITF Information Transport Function 信息传送功能ITM ISDN Trunk Module 综合业务数字网中继模块ITMC International Transmission Maintenance Center 国际传输维护中心ITN Integrated Teleprocessing Network 综合远程处理网络ITN Intelligent Telecommunication Node 智能电信节点ITPC International Television Program Center 国际电视节目中心ITR Instantaneous Transmission Rate 瞬时传输速率ITR Internet Talk Radio 因特网无线对话ITS Independent Television Service 独立电视服务ITS Information Transfer System 信息转换系统ITS Information Transmission System 信息传输系统ITS Insertion Test Signal 插入测试信号ITS Intelligent Transport System 智能交通系统ITS International Telecommunication Service 国际电信业务ITSC International Telephone Service Center 国际电话业务中心ITSO International Telecommunications Satellite Organization 国际电信卫星组织ITSP Internet Telephony Service Provider IP电话业务提供商ITT InterToll Trunk 长途电话中继线ITTP Intelligent Terminal Transfer Protocol 智能终端转换协议ITTS Intelligent Target Tracking System 智能目标跟踪系统ITU International Telecommunication Union 国际电信联盟ITU-R ITU-Radio communications sector 国际电信联盟无线电通信组ITU-T ITU-Telecommunication standardization sector 国际电信联盟电信标准化组ITV Interactive TeleVision 交互式电视IU Interface Unit 接口单元IUI Intelligent User Interface 智能用户接口IUI Inter-User Interference 用户间干扰IUO Intelligent Underlay Overlay 智能双层网IUR Internet Usage Record 因特网使用记录IV Interactive Video 交互式视频IV Interface Vector 接口向量IVA Iitial Video Address 初始视频地址IVANS Insurance value Added Network Services 保险业增值网络服务IVAP Internal Videotex Application Provider 内部可视图文应用供应商IVBC International Videoconference Booking Center 国际电视会议登记中心IVC Independent Virtual Channel 独立虚拟信道IVC International Videoconference Center 国际会议电视中心IVD Interactive Video Disk 交互式视频盘IVD Interpolated Voice Data 内插语音数据IVDS Interactive Video Database Services 交互式视频数据库业务IVDT Integrated Voice Data Terminal 综合话音数据终端IVE International Videotex Equipment 国际可视图文设备IVG Interactive Video Game 交互式视频游戏IVHS Intelligent Vehicle and Highway System 智能车辆和公路系统IVIS Interactive Video Information System 交互视频信息系统IVMS Integrated Voice-Messaging System 综合语音信息系统IVN Interactive Video Network 交互式视频网络IVOD Interactive Video On Demand 交互式视频点播IVOT Inter-network teleVOTing 网间电子投票业务IVPN International Virtual Private Network 国际虚拟专用网IVR Integrated Voice Response 综合语音响应IVR Interactive Voice Response 交互式语音应答IVS Intelligent Video Smoother 智能视频平滑器IVS Interactive Video Service 交互式视频业务IVS Interactive Videodisc System 交互式视盘系统IW Information War 信息战IWAN Integrated services Wireless-Access Network 综合业务无线接入网络IWC Indoor Wireless Channel 室内无线信道IWC Interferometric all-optical Wavelength Converter 干涉全光波长变换器IWC Interferometric Wavelength Converter 干涉波长变换器IWCS Integrated Wideband Communication System 综合宽带通信系统IWF InterWorking Facility 互通设备IWF InterWorking Function 互通功能IWK Issuer Working Key 发行卡的工作密钥IWS Intelligent Work Station 智能工作站IWS Intelligent Workstation Support 智能工作站支持IWU InterWorking Unit 互通单元IXC Inter-eXchange Carrier 交互运营商IXP Internet eXchange Point 因特网交换点。
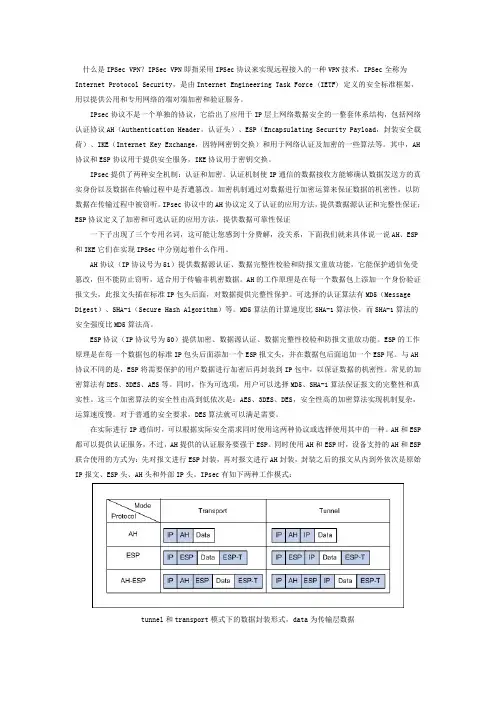
什么是IPSec VPN?IPSec VPN即指采用IPSec协议来实现远程接入的一种VPN技术,IPSec全称为Internet Protocol Security,是由Internet Engineering Task Force (IETF) 定义的安全标准框架,用以提供公用和专用网络的端对端加密和验证服务。
IPsec协议不是一个单独的协议,它给出了应用于IP层上网络数据安全的一整套体系结构,包括网络认证协议AH(Authentication Header,认证头)、ESP(Encapsulating Security Payload,封装安全载荷)、IKE(Internet Key Exchange,因特网密钥交换)和用于网络认证及加密的一些算法等。
其中,AH 协议和ESP协议用于提供安全服务,IKE协议用于密钥交换。
IPsec提供了两种安全机制:认证和加密。
认证机制使IP通信的数据接收方能够确认数据发送方的真实身份以及数据在传输过程中是否遭篡改。
加密机制通过对数据进行加密运算来保证数据的机密性,以防数据在传输过程中被窃听。
IPsec协议中的AH协议定义了认证的应用方法,提供数据源认证和完整性保证;ESP协议定义了加密和可选认证的应用方法,提供数据可靠性保证一下子出现了三个专用名词,这可能让您感到十分费解,没关系,下面我们就来具体说一说AH、ESP 和IKE它们在实现IPSec中分别起着什么作用。
AH协议(IP协议号为51)提供数据源认证、数据完整性校验和防报文重放功能,它能保护通信免受篡改,但不能防止窃听,适合用于传输非机密数据。
AH的工作原理是在每一个数据包上添加一个身份验证报文头,此报文头插在标准IP包头后面,对数据提供完整性保护。
可选择的认证算法有MD5(Message Digest)、SHA-1(Secure Hash Algorithm)等。
MD5算法的计算速度比SHA-1算法快,而SHA-1算法的安全强度比MD5算法高。


IEFT(Internet Engineering Task Force)标准是由IEFT组织制定和维护的一系列互联网技术标准。
IEFT是一个开放的组织,旨在推动互联网标准化工作,通过一系列工作组(Working Groups)的合作来开发和演进互联网协议。
以下是一些常见的IEFT标准的例子:
1. TCP/IP(Transmission Control Protocol/Internet Protocol):TCP/IP 是互联网数据传输的基本协议,它定义了互联网的网络层和传输层协议。
2. HTTP(Hypertext Transfer Protocol):HTTP是用于在Web浏览器和Web服务器之间传输超文本的协议,定义了客户端和服务器之间的通信规则。
3. DNS(Domain Name System):DNS是用于将域名转换为IP地址的分布式命名系统,它提供了域名解析服务。
4. TLS(Transport Layer Security):TLS是一种安全协议,用于保护网络通信的机密性和完整性,后续版本称为SSL(Secure Sockets Layer)。
5. IPv6(Internet Protocol version 6):IPv6是互联网协议的下一代版
本,旨在解决IPv4地址不足的问题,并提供更好的安全性和性能。
这些标准在互联网的各个方面起着重要的作用,如网络通信、安全、域名解析等。
IEFT通过合作的方式,不断推动互联网的发展和标准的演进。

对IETF的理解1、概述IETF(互联网工程任务组——The Internet Engineering Task Force)是松散的、自律的、志愿的民间学术组织——即一个由为互联网技术工程及发展做出贡献的专家自发参与和管理的国际民间组织机构。
它汇聚了与互联网架构演化和互联网稳定运作等业务相关的网络设计者、运营者和研究者,并向所有对该行业感兴趣的人开放。
任何人都可以注册参加IETF的会议。
它成立于1985年底,其主要任务是负责互联网相关技术规范的研发和制定,主要有八大研究领域如下:应用研究、通用研究、网际互联、操作与管理、实时应用与基础设施、路由、安全、传输这八大研究领域。
同时它有以下组织构成:ISOC 、IAB、IESG IANA 、RFCE等。
2、IETF的运作流程这个工作组主要负责互联网相关技术规范标准的研究与制定,其中标准的制定工作由各工作组承担,而标准的制定来源于对该行业感兴趣的人做的对某种标准的设想的RFC(request for comments——请求评议)。
第一,RFC作为一个Internet草案发布,当这文档有一个ID号后作者可以发邮件给RFCE告知你的RFC有价值,那么RFCE(RFC文档编辑者)向IESG(Internet工程指导组)请求查阅该文档并给其加上评论和注释,IESG会安排IETF(互联网工程任务组)的工作组对该文档进行研究,最终由IESG核准,一旦被通过则RFCE负责编辑文档并提交给体系委员会(IAB),然后又IAB安排IANA给该文档一固定编号,由Internet协会(ISOC)通过Internet向全世界颁布出版该文档。
综上所述,标准制定工作具体由工作组承担,互联网工程指导委员会(IESG)主要的职责是接收各个工作组的报告,对他们的工作进行审查并给出指导性建议,互联网架构委员会(IAB)主要负责监管八大工作组的工作状况。
2、IETF的工作情况IETF主要工作任务是:(1).鉴定互联网的运行和技术问题,并提出解决方案;(2).详细说明互联网协议的发展或用途,解决相应问题;(3).向IESG提出针对互联网协议标准及用途的建议;(4).促进互联网研究任务组(IRTF)的技术研究成果向互联网社区推广;(5).为包括互联网用户、研究人员、行销商、制造商及管理者等提供信息交流的论坛。

最新计算机网络术语大全:internet因特网ipinternet protocol,网际协议isdnintegrated service digital network,综合服务数字网络isoc: internet society,因特网协会ispinternet service provider,因特网服务提供商lanlocal area network,局域网ldap: lightweight directory access protocol,轻权目录访问协议iab: internet activities board,因特网工作委员会计算机网络术语ietf: internet engineering task force,因特网工程作业推动l2tplayer 2 tunneling protocol,二级通道协议lmds: local multipoint distributed system,局域多点分布式系统mime: multipurpose internet mail extension,多用途因特网邮件扩展协议 adsl: asymmetric digital subscriber line,不对称数字订阅线路ah: authentication header,鉴定文件头amraudio/modem riser,音效/数据主机板附加直立插卡arpaddress resolution protocol,地址解析协议atmasynchronous transfer mode,异步传输模式bodbandwidth on demand,弹性带宽运用cbrcommitted burst rate,约定突发速率ietfinternet engineering task framework,因特网工程任务组ike: internet key exchange,因特网密钥交换协议imap4: internet message access protocol version 4,第四版因特网信息存取协议mnp: microcom networking protocalmodemmodulator demodulator,调制解调器natnetwork address translation,网络地址转换ncnetwork computer,网络计算机nds: novell directory service,novell目录服务nntp: network news transfer protocol,网络新闻传输协议msn: microsoft network,微软网络ccirn: coordinating committee for intercontinental research networking,洲际研究网络协调委员会ccmcall control manager,拨号控制管理cdsl: consumer digital subscriber line消费者数字订阅线路cgicommon gateway interface,通用网关接口ciea: commercial internet exchange association,商业因特网交易协会circommitted infomation rate,约定信息速率ctsclear to send,清除发送dbs-pc: direct broadcast satellite pc人造卫星直接广播式pcdce: data circuit terminal equipment,数据通信设备des: data encryption standard,数据加密标准dmt: discrete multi - tone,不连续多基频模式dnsdomain name system,域名系统docsisdata over cable service interface specifications,线缆服务接口数据规格dte: data terminal equipment,数据终端设备ebrexcess burst rate,超额突发速率esp: encapsulating security payload,压缩安全有效载荷fdm: frequency division multi,频率分离flow-control流控制fricc: federal research internet coordinating committee,联邦调查因特网协调委员会ftpfile transfer protocol,文件传输协议hardware oriented system transfer,全面硬件导向系统转移hdsl: high bit rate dsl,高比特率数字订阅线路httphypertext transfer protocol,超文本传输协议icmpinternet control message protocol,因特网信息控制协议感谢您的阅读,祝您生活愉快。
IPSec基础IPsec简介IPSec,因特网协议安全,是由IETF(Internet Engineering Task Force)定义的一套在网络层提供IP安全性的协议。
基于Ipsec的VPN,如阿姆瑞特VPN,由两部分组成:∙Internet密钥交换协议(IKE)∙IPsec协议(AH/ESP/二者都有)第一部分,IKE是初始协商阶段,两个VPN端点在这个阶段协商使用哪种方法为下面的IP 数据流提供安全。
而且,通过定义一套安全联盟(SA),IKE用于管理连接;SA面向每个连接的。
SA是单向的,因此每个Ipsec连接至少有2个SA。
在IKE(因特网密钥交换)部分对此有更详细的描述。
另一部分是IKE协商后,用加密和认证方法实际传输的IP数据。
有几种方法,如IPsec协议ESP, AH或两者结合在一起都可以做到这一点。
IPsec协议(ESP/AH)部分对此进行了解释。
建立VPN事件的流程可做如下简要描述:∙IKE协商如何保护IKE∙IKE协商如何保护Ipsec∙Ipsec在VPN中传输数据后面的部分将具体描述每一个步骤。
Internet密钥交换协议(IKE)这部分描述IKE,因特网密钥交换协议,及其使用的参数。
加密和认证数据比较直接,唯一需要的是加密和认证算法,及其使用的密钥。
因特网密钥交换协议(IKE),用作分配这些对话用密钥的一种方法,而且在VPN端点间,规定了如何保护数据的方法。
IKE主要有三项任务:∙为端点间的认证提供方法∙建立新的IPsec连接(创建一对SA)∙管理现有连接IKE跟踪连接的方法是给每个连接分配一组安全联盟(SA)。
SA描述与特殊连接相关的所有参数,包括使用的Ipsec协议(ESP/AH/二者兼有),加密/解密和认证/确认传输数据使用的对话密钥。
SA本身是单向的,每个连接需要一个以上的SA。
大多数情况下,只使用ESP或AH,每个连接要创建2个SA,一个描述入站数据流,另一个描述出站数据流。
sdp rfc 标准SDP (Session Description Protocol) RFC 标准是一种用于描述实时通信会话的协议。
它是由IETF(Internet Engineering Task Force)组织开发和维护的,并被广泛应用于各种应用中,如VoIP(Voice over IP)、视频会议、实时聊天等。
本篇文章将逐步介绍SDP RFC 标准,包括其作用、结构和原则,以及如何使用SDP建立和管理通信会话。
SDP的作用是为会话提供细节描述和控制信息。
通过SDP,参与会话的各方可以交换会话相关的参数和特性,以便彼此理解和协调会话的细节。
SDP不仅可以用于建立新的会话,还可以用于修改已经存在的会话。
SDP消息的结构按照一定的规范组织,以便参与者可以方便地解析和理解消息的内容。
一个典型的SDP消息由多个字段组成,每个字段包含一个标签和对应的值。
常见的字段包括会话名称、会话ID、会话版本、媒体描述、网络地址等。
通过这些字段,SDP消息可以描述会话的各个方面,包括会话的会议信息、媒体流参数、媒体流的编码格式和传输方式等。
SDP采用文本形式的消息格式,方便阅读和交换。
消息采用行的形式组织,每一行包含一个字段。
其中以大写字母开头的行为标签行,而其余的行为数值行。
标签行指示了该行的数值行的含义,而数值行则包含了对应标签行所描述的值。
SDP的使用原则根据RFC标准规定,使用时应遵循一定的规则和约定。
例如,SDP消息应使用有效的编码格式,如ASCII或UTF-8,以确保消息能够正确传输和解析。
另外,SDP消息应包含足够的信息以便各方能够正确理解和处理会话,而且应尽量减少不必要的冗余信息。
使用SDP建立和管理通信会话的过程可以分为以下几个步骤:1. 建立会话:在SDP消息中,首先定义会话名称、ID和版本等基本信息。
这些信息用于唯一标识会话,并确保参与者可以准确地识别和区分不同的会话。
例如:v=0o=- 1234567890 1 IN IP4 192.0.2.1s=My Session2. 定义媒体流:接下来,定义会话中的媒体流信息。
ie开头的英文单词1. 介绍在英语单词中,以ie开头的词汇有许多不同的含义和用法。
这些词汇可以用于描述不同的主题,包括技术、学术、商业等方面。
本文将对其中几个常见的ie开头的英文单词进行介绍和探讨。
2. Internet Explorer (IE)Internet Explorer是微软开发的一款网页浏览器,也是早期互联网上最常用的浏览器之一。
IE在1995年发布,并在接下来的几十年中成为最受欢迎和广泛使用的浏览器之一。
然而,随着时间的推移,其他浏览器的兴起以及安全性和性能问题的出现,IE的市场份额逐渐下降。
微软在2015年宣布停止继续开发和支持IE,并推出了新的Edge浏览器来取代IE。
2.1 IE的特点和功能•IE具有简单易用的用户界面,使得初学者和非技术人士可以轻松上手。
•它提供了多标签浏览、书签管理、搜索引擎集成等基本功能。
•IE支持活动记录和缓存,以提供更快的浏览速度和更好的用户体验。
•它还支持Internet Explorer兼容模式,以确保旧版本网站的正确显示。
2.2 IE的影响和衰落IE在互联网早期扮演着重要的角色,但随着技术的发展和用户需求的变化,它的市场份额逐渐下滑。
以下是导致IE衰落的一些主要原因:1.安全性问题:IE在过去的几年中一直被认为是最不安全的浏览器之一。
它容易受到恶意软件和黑客攻击,给用户的信息安全带来风险。
2.性能问题:与其他现代浏览器相比,IE的性能较差。
它的加载速度慢,对新的Web标准支持不足,导致用户体验差。
3.竞争对手的崛起:随着Chrome、Firefox和Safari等新一代浏览器的崛起,IE的市场份额逐渐被分散。
这些浏览器在性能、安全性和功能方面都提供了更好的体验。
4.微软的战略转变:微软决定停止继续开发和支持IE,转而推出新的Edge浏览器。
这标志着IE的结束和一个新时代的开始。
3. Internet Engineering Task Force (IETF)Internet Engineering Task Force是一个技术组织,致力于互联网标准的发展和推广。
ospf协议
OSPF协议(Open Shortest Path First Protocol)是一种面向链路状态的内部网关协议(IGP),它是一种开放式协议,由IETF(Internet Engineering Task Force)定义。
OSPF协议广泛应用于大型企业和ISP互联网的路由器之间的通信。
它可以与其他IP路由协议(如RIP、BGP和EIGRP等)结合使用,但通常情况下仅与其自身配套的OSPF协议结合使用。
OSPF协议是一种动态路由协议,能够通过计算网络中各个节点的最短路径,自适应地选择网络中最优的路径。
它使用“链路状态”信息来计算路由表,并交换信息以使所有路由器都维护相同的链路状态数据库(LSDB)。
OSPF协议使用“区域”定义实现路由器自治域之间更平滑的划分。
OSPF网络可以分成许多区域,每个区域可以配置自己的路由器。
在一个区域内,较少的LSA会减少大量的网络负载和Cpu利用率。
当路由器A需要向路由器B发送一个数据包,但是路由器A没有直接和B相连,它会查找LSDB来找到最短路径。
当它找到该路径时,OSPF协议将在LSDB上的路由器中查找它需要经过的路由器并转发该数据包。
OSPF协议的主要优点是:1.可以通过控制各个区域之间的出口点,实现路由器自治域之间的更平滑的划分;2.良好的扩展性,可支持上千个路由器的网络;3.可以支持多种路由协议,例如IPv4、IPv6等等;4.通过路由器间交换网络拓扑信息,快速适应网络拓扑的变化。
OSPF协议的主要缺点是:1.相对于RIP等协议,实现和运维成本更高;2.设计复杂性较高,对设备要求多。
Internet 工程任务组工作动态IETF网址1、概述IETF(互联网工程任务组—The Internet Engineering Task Force)是松散的、自律的、志愿的民间学术组织,成立于1985年底, 其主要任务是负责互联网相关技术规范的研发和制定。
IETF是一个由为互联网技术工程及发展做出贡献的专家自发参与和管理的国际民间机构。
它汇集了与互联网架构演化和互联网稳定运作等业务相关的网络设计者、运营者和研究人员,并向所有对该行业感兴趣的人士开放。
任何人都可以注册参加IETF的会议。
IETF大会每年举行三次,规模均在千人以上。
IETF大量的技术性工作均由其内部的各类工作组协作完成。
这些工作组按不同类别,如路由、传输、安全等专项课题而分别组建。
IETF的交流工作主要是在各个工作组所设立的邮件组中进行,这也是IETF的主要工作方式。
目前,IETF已成为全球互联网界最具权威的大型技术研究组织。
但是它有别于像国际电联(ITU-International Telecommunication Union)这样的传统意义上的标准制定组织。
IETF的参与者都是志愿人员,他们大多是通过IETF每年召开的三次会议来完成该组织的如下使命:1.鉴定互联网的运行和技术问题,并提出解决方案;2.详细说明互联网协议的发展或用途,解决相应问题;3.向IESG提出针对互联网协议标准及用途的建议;4.促进互联网研究任务组(IRTF)的技术研究成果向互联网社区推广;5.为包括互联网用户、研究人员、行销商、制造商及管理者等提供信息交流的论坛。
2、IETF相关组织机构(1)互联网协会(ISCO -Internet Society)ISCO是一个国际的,非盈利性的会员制组织,其作用是促进互联网在全球范围的应用。
实现方式之一便是对各类互联网组织提供财政和法律支持,特别是对IAB管理下的IETF提供资助。
(2)互联网架构委员会(IAB-Internet Architecture Board)IAB是ISOC的技术咨询团体,承担ISCO技术顾问组的角色;IAB负责定义整个互联网的架构和长期发展规划,通过IESG向IETF提供指导并协调各个IETF工作组的活动,在新的IETF工作组设立之前IAB负责审查此工作组的章程,从而保证其设置的合理性,因此可以认为IAB是IETF的最高技术决策机构。
ietf 草案IETF草案是什么?IETF草案,全称是Internet Engineering Task Force草案,是一种被广泛应用于互联网发展的技术标准。
IETF草案起源于1986年,是由全球互联网技术专家组成的团队共同制定的。
IETF草案通过公开审查的方式,确保了互联网技术的开放性、透明性和自由性。
本文将对IETF草案的背景、特点及其在互联网发展中的应用进行探讨。
一、IETF草案的背景IETF草案的出现源于互联网技术的快速发展和全球性的需求,互联网的开放性和共享性使得团队合作和技术标准的制定成为必要。
IETF作为一个非营利性的组织,旨在促进互联网技术的发展和标准化,从而保障互联网的互通性和稳定性。
二、IETF草案的特点1. 开放性和透明性:IETF草案的制定过程公开透明,任何人都可以参与和贡献自己的意见和建议。
这有助于形成多元化、民主化的技术标准。
2. 社区参与:IETF草案是由互联网技术专家组成的社区共同制定的,每个成员都可以通过研究、讨论和实践来提出自己的建议。
这种社区参与的模式有助于增强技术标准的可靠性和实用性。
3. 快速迭代和更新:互联网发展的速度非常快,为了适应新技术的需求和变化,IETF草案采用了快速迭代的方式来更新和修订技术标准。
这有助于提高互联网技术的灵活性和时效性。
三、IETF草案在互联网发展中的应用1. 规范互联网协议:IETF草案制定了许多互联网协议,如TCP/IP协议、HTTP协议等。
这些协议对于保障互联网的正常运行和通信的顺畅性起着至关重要的作用。
2. 提升互联网安全性:IETF草案不仅制定了安全性相关的协议,如TLS协议、IPsec协议等,还关注于互联网安全的发展趋势和挑战。
通过不断更新和改进安全协议,提升互联网的安全性。
3. 促进新技术创新:IETF草案对新兴技术的发展和应用具有重要的引导作用。
例如,IPv6的实施、WebRTC的推广等,都得益于IETF草案的推动和标准化。
Internet Engineering Task Force Sally Floyd INTERNET DRAFT Jamshid Mahdavi draft-floyd-sack-00.txt Matt Mathis Matthew Podolsky Allyn Romanow August 1999 Expires: February 2000An Extension to the Selective Acknowledgement (SACK) Option for TCPStatus of this MemoThis document is an Internet-Draft and is in full conformance withall provisions of Section 10 of RFC2026.Internet-Drafts are working documents of the Internet EngineeringTask Force (IETF), its areas, and its working groups. Note thatother groups may also distribute working documents as Internet-Drafts.Internet-Drafts are draft documents valid for a maximum of six months and may be updated, replaced, or obsoleted by other documents at any time. It is inappropriate to use Internet- Drafts as referencematerial or to cite them other than as "work in progress."The list of current Internet-Drafts can be accessed at/ietf/1id-abstracts.txtThe list of Internet-Draft Shadow Directories can be accessed at/shadow.html.AbstractThis note defines an extension of the Selective Acknowledgement(SACK) Option [RFC2018] for TCP. RFC 2018 specified the use of theSACK option for acknowledging out-of-sequence data not covered byTCP’s cumulative acknowledgement field. This note extends RFC 2018by specifying the use of the SACK option for acknowledging duplicate packets. This note suggests that when duplicate packets arereceived, the first block of the SACK option field can be used toreport the sequence numbers of the packet that triggered theacknowledgement. This extension to the SACK option allows the TCPsender to infer the order of packets received at the receiver,allowing the sender to infer when it has unnecessarily retransmitted a packet. A TCP sender could then use this information for morerobust operation in an environment of reordered packets, ACK loss,packet replication, and/or early retransmit timeouts.1. Conventions and AcronymsThe keywords MUST, MUST NOT, REQUIRED, SHALL, SHALL NOT, SHOULD,SHOULD NOT, RECOMMENDED, MAY, and OPTIONAL, when they appear in this document, are to be interpreted as described in [B97].2. IntroductionThe Selective Acknowledgement (SACK) option defined in RFC 2018 isused by the TCP data receiver to acknowledge non-contiguous blocks of data not covered by the Cumulative Acknowledgement field. However,RFC 2018 does not specify the use of the SACK option when duplicatesegments are received. This note specifies the use of the SACKoption when acknowledging the receipt of a duplicate packet [F99].We use the term D-SACK (for duplicate-SACK) to refer to a SACK block that reports a duplicate segment.This document does not make any changes to TCP’s use of thecumulative acknowledgement field, or to the TCP receiver’s decisionof *when* to send an acknowledgement packet. This document onlyconcerns the contents of the SACK option when an acknowledgement issent.This extension is compatible with current implementations of the SACK option in TCP. That is, if one of the TCP end-nodes does notimplement this D-SACK extension and the other TCP end-node does, webelieve that this use of the D-SACK extension by one of the end nodes will not introduce problems.The use of D-SACK does not require separate negotiation between a TCP sender and receiver that have already negotiated SACK capability.The absence of separate negotiation for D-SACK means that the TCPreceiver could send D-SACK blocks when the TCP sender does notunderstand this extension to SACK. In this case, the TCP sender will simply discard any D-SACK blocks, and process the other SACK blocksin the SACK option field as it normally would.3. The Sack Option Format as defined in RFC 2018The SACK option as defined in RFC 2018 is as follows:+--------+--------+| Kind=5 | Length |+--------+--------+--------+--------+| Left Edge of 1st Block |+--------+--------+--------+--------+| Right Edge of 1st Block |+--------+--------+--------+--------+| |/ . . . /| |+--------+--------+--------+--------+| Left Edge of nth Block |+--------+--------+--------+--------+| Right Edge of nth Block |+--------+--------+--------+--------+The Selective Acknowledgement (SACK) option in the TCP headercontains a number of SACK blocks, where each block specifies the left and right edge of a block of data received at the TCP receiver. Inparticular, a block represents a contiguous sequence space of datareceived and queued at the receiver, where the ‘‘left edge’’ of theblock is the first sequence number of the block, and the ‘‘rightedge’’ is the sequence number immediately following the last sequence number of the block.RFC 2018 implies that the first SACK block specify the segment thattriggered the acknowledgement. From RFC 2018, when the data receiver chooses to send a SACK option, ‘‘the first SACK block ... MUSTspecify the contiguous block of data containing the segment whichtriggered this ACK, unless that segment advanced the AcknowledgmentNumber field in the header.’’However, RFC 2018 does not address the use of the SACK option whenacknowledging a duplicate segment. For example, RFC 2018 specifiesthat ‘‘each block represents received bytes of data that arecontiguous and isolated’’. RFC 2018 further specifies that ‘‘if sent at all, SACK options SHOULD be included in all ACKs which do not ACK the highest sequence number in the data receiver’s queue.’’ RFC 2018 does not specify the use of the SACK option when a duplicate segment is received, and the cumulative acknowledgement field in the ACKacknowledges all of the data in the data receiver’s queue.4. Use of the SACK option for reporting a duplicate segmentThis section specifies the use of SACK blocks when the SACK option is used in reporting a duplicate segment. When D-SACK is used, thefirst block of the SACK option should be a D-SACK block specifyingthe sequence numbers for the duplicate segment that triggers theacknowledgement. If the duplicate segment is part of a larger block of non-contiguous data in the receiver’s data queue, then thefollowing SACK block should be used to specify this larger block.Additional SACK blocks can be used to specify additional non-contiguous blocks of data, as specified in RFC 2018.The guidelines for reporting duplicate segments are summarized below: (1) A D-SACK block is only used to report a duplicate contiguoussequence of data received by the receiver in the most recent packet.(2) Each duplicate contiguous sequence of data received is reportedin at most one D-SACK block. (I.e., the receiver sends two identical D-SACK blocks in subsequent packets only if the receiver receives two duplicate segments.)(3) The left edge of the D-SACK block specifies the first sequencenumber of the duplicate contiguous sequence, and the right edge ofthe D-SACK block specifies the sequence number immediately following the last sequence in the duplicate contiguous sequence.(4) If the D-SACK block reports a duplicate contiguous sequence froma (possibly larger) block of data in the receiver’s data queue above the cumulative acknowledgement, then the second SACK block in thatSACK option should specify that (possibly larger) block of data.(5) Following the SACK blocks described above for reporting duplicate segments, additional SACK blocks can be used for reporting additional blocks of data, as specified in RFC 2018.Note that because each duplicate segment is reported in only one ACK packet, information about that duplicate segment will be lost if that ACK packet is dropped in the network.4.1 Reporting Full Duplicate SegmentsWe illustrate these guidelines with three examples. In each example, we assume that the data receiver has first received eight segments of 500 bytes each, and has sent an acknowledgement with the cumulativeacknowledgement field set to 4000 (assuming the first sequence number is zero). The D-SACK block is underlined in each example.4.1.1: Example 1: Reporting a duplicate segment.Because several ACK packets are lost, the data sender retransmitspacket 3000-3499, and the data receiver subsequently receives aduplicate segment with sequence numbers 3000-3499. The receiversends an acknowledgement with the cumulative acknowledgement fieldset to 4000, and the first, D-SACK block specifying sequence numbers 3000-3500.Transmitted Received ACK SentSegment Segment (Including SACK Blocks)3000-3499 3000-3499 3500 (ACK dropped)3500-3999 3500-3999 4000 (ACK dropped)3000-3499 3000-3499 4000, SACK=3000-3500---------4.1.2. Example 2: Reporting an out-of-order segment and a duplicate segment.Following a lost data packet, the receiver receives an out-of-orderdata segment, which triggers the SACK option as specified in RFC2018. Because of several lost ACK packets, the sender thenretransmits a data packet. The receiver receives the duplicatepacket, and reports it in the first, D-SACK block:Transmitted Received ACK SentSegment Segment (Including SACK Blocks)3000-3499 3000-3499 3500 (ACK dropped)3500-3999 3500-3999 4000 (ACK dropped)4000-4499 (data packet dropped)4500-4999 4500-4999 4000, SACK=4500-5000 (ACK dropped)3000-3499 3000-3499 4000, SACK=3000-3500, 4500-5000---------4.1.3. Example 3: Reporting a duplicate of an out-of-order segment.Because of a lost data packet, the receiver receives two out-of-order segments. The receiver next receives a duplicate segment for one of these out-of-order segments:Transmitted Received ACK SentSegment Segment (Including SACK Blocks)3500-3999 3500-3999 40004000-4499 (data packet dropped)4500-4999 4500-4999 4000, SACK=4500-50005000-5499 5000-5499 4000, SACK=4500-5500(duplicated packet)5000-5499 4000, SACK=5000-5500, 4500-5500---------4.2. Reporting Partial Duplicate SegmentsIt may be possible that a sender transmits a packet that includes one or more duplicate sub-segments--that is, only part but not all of the transmitted packet has already arrived at the receiver. This canoccur when the size of the sender’s transmitted segments increases,which can occur when the PMTU increases in the middle of a TCPsession, for example. The guidelines in Section 4 above apply toreporting partial as well as full duplicate segments. This sectiongives examples of these guidelines when reporting partial duplicatesegments.When the SACK option is used for reporting partial duplicatesegments, the first D-SACK block reports the first duplicate sub-segment. If the data packet being acknowledged contains multiplepartial duplicate sub-segments, then only the first such duplicatesub-segment is reported in the SACK option. We illustrate this with the examples below.4.2.1. Example 4: Reporting a single duplicate subsegment.The sender increases the packet size from 500 bytes to 1000 bytes.The receiver subsequently receives a 1000-byte packet containing one 500-byte subsegment that has already been received and one which has not. The receiver reports only the already received subsegment using a single D-SACK block.Transmitted Received ACK SentSegment Segment (Including SACK Blocks)500-999 500-999 10001000-1499 (delayed)1500-1999 (data packet dropped)2000-2499 2000-2499 1000, SACK=2000-25001000-2000 1000-1499 1500, SACK=2000-25001000-2000 2500, SACK=1000-1500---------4.2.2. Example 5: Two non-contiguous duplicate subsegments covered by the cumulative acknowledgement.After the sender increases its packet size from 500 bytes to 1500bytes, the receiver receives a packet containing two non-contiguousduplicate 500-byte subsegments which are less than the cumulativeacknowledgement field. The receiver reports the first such duplicate segment in a single D-SACK block.Transmitted Received ACK SentSegment Segment (Including SACK Blocks)500-999 500-999 10001000-1499 (delayed)1500-1999 (data packet dropped)2000-2499 (delayed)2500-2999 (data packet dropped)3000-3499 3000-3499 1000, SACK=3000-35001000-2499 1000-1499 1500, SACK=3000-35002000-2499 1500, SACK=2000-2500, 3000-35001000-2499 2500, SACK=1000-1500, 3000-3500---------4.2.3. Example 6: Two non-contiguous duplicate subsegments not covered by the cumulative acknowledgement.This example is similar to Example 5, except that after the senderincreases the packet size, the receiver receives a packet containing two non-contiguous duplicate subsegments which are above thecumulative acknowledgement field, rather than below. The first, D-SACK block reports the first duplicate subsegment, and the second,SACK block reports the larger block of non-contiguous data that itbelongs to.Transmitted Received ACK SentSegment Segment (Including SACK Blocks)500-999 500-999 10001000-1499 (data packet dropped)1500-1999 (delayed)2000-2499 (data packet dropped)2500-2999 (delayed)3000-3499 (data packet dropped)3500-3999 3500-3999 1000, SACK=3500-40001000-1499 (data packet dropped)1500-2999 1500-1999 1000, SACK=1500-2000, 3500-40002000-2499 1000, SACK=2000-2500, 1500-2000,3500-40001500-2999 1000, SACK=1500-2000, 1500-3000,---------3500-40004.3. Interaction Between D-SACK and PAWSRFC 1323 [RFC1323] specifies an algorithm for Protection AgainstWrapped Sequence Numbers (PAWS). PAWS gives a method fordistinguishing between sequence numbers for new data, and sequencenumbers from a previous cycle through the sequence number space.Duplicate segments might be detected by PAWS as belonging to aprevious cycle through the sequence number space.RFC 1323 specifies that for such packets, the receiver should do the following:Send an acknowledgement in reply as specified in RFC 793 page 69, and drop the segment.Since PAWS still requires sending an ACK, there is no harmfulinteraction between PAWS and the use of D-SACK. The D-SACK block can be included in the SACK option of the ACK, as outlined in Section 4, independently of the use of PAWS by the TCP receiver, andindependently of the determination by PAWS of the validity orinvalidity of the data segment.TCP senders receiving D-SACK blocks should be aware that a segmentreported as a duplicate segment could possibly have been from a prior cycle through the sequence number space. This is independent of the use of PAWS by the TCP data receiver. We do not anticipate that this will present significant problems for senders using D-SACKinformation.5. Detection of Duplicate PacketsThis extension to the SACK option enables the receiver to accurately report the reception of duplicate data. Because each receipt of aduplicate packet is reported in only one ACK packet, the loss of asingle ACK can prevent this information from reaching the sender. In addition, we note that the sender can not necessarily trust thereceiver to send it accurate information [SCWA99].In order for the sender to check that the first (D)SACK block of anacknowledgement in fact acknowledges duplicate data, the sendershould compare the sequence space in the first SACK block to thecumulative ACK which is carried IN THE SAME PACKET. If the SACKsequence space is less than this cumulative ACK, it is an indication that the segment identified by the SACK block has been received more than once by the receiver. An implementation MUST NOT compare thesequence space in the SACK block to the TCP state variable snd.una(which carries the total cumulative ACK), as this may result in thewrong conclusion if ACK packets are reordered.If the sequence space in the first SACK block is greater than thecumulative ACK, then the sender next compares the sequence space inthe first SACK block with the sequence space in the second SACKblock, if there is one. This comparison can determine if the firstSACK block is reporting duplicate data that lies above the cumulative ACK.TCP implementations which follow RFC 2581 [RFC2581] could seeduplicate packets in each of the following four situations. Thisdocument does not specify what action a TCP implementation shouldtake in these cases. The extension to the SACK option simply enables the sender to detect each of these cases. Note that these fourconditions are not an exhaustive list of possible cases for duplicate packets, but are representative of the most common/likely cases.Subsequent documents will describe experimental proposals for sender responses to the detection of unnecessary retransmits due toreordering, lost ACKS, or early retransmit timeouts.5.1. Replication by the networkIf a packet is replicated in the network, this extension to the SACK option can identify this. For example:Transmitted Received ACK SentSegment Segment (Including SACK Blocks)500-999 500-999 10001000-1499 1000-1499 1500(replicated)1000-1499 1500, SACK=1000-1500---------In this case, the second packet was replicated in the network. AnACK containing a D-SACK block which is lower than its ACK field andis not identical to a previously retransmitted segment is indicative of a replication by the network.WITHOUT D-SACK:If D-SACK was not used and the last ACK was piggybacked on a datapacket, the sender would not know that a packet had been replicatedin the network. If D-SACK was not used and neither of the last twoACKs was piggybacked on a data packet, then the sender couldreasonably infer that either some data packet *or* the final ACKpacket had been replicated in the network. The receipt of the D-SACK packet gives the sender positive knowledge that this data packet was replicated in the network (assuming that the receiver is not lying).RESEARCH ISSUES:The current SACK option already allows the sender to identifyduplicate ACKs that do not acknowledge new data, but the D-SACKoption gives the sender a stronger basis for inferring that aduplicate ACK does not acknowledge new data. The knowledge that aduplicate ACK does not acknowledge new data allows the sender torefrain from using that duplicate ACKs to infer packet loss (e.g.,Fast Retransmit) or to send more data (e.g., Fast Recovery).5.2. False retransmit due to reorderingIf packets are reordered in the network such that a segment arrivesmore than 3 packets out of order, TCP’s Fast Retransmit algorithmwill retransmit the out-of-order packet. An example of this is shown below:Transmitted Received ACK SentSegment Segment (Including SACK Blocks)500-999 500-999 10001000-1499 (delayed)1500-1999 1500-1999 1000, SACK=1500-20002000-2499 2000-2499 1000, SACK=1500-25002500-2999 2500-2999 1000, SACK=1500-30001000-1499 1000-1499 30001000-1499 3000, SACK=1000-1500---------In this case, an ACK containing a SACK block which is lower than its ACK field and identical to a previously retransmitted segment isindicative of a significant reordering followed by a false(unnecessary) retransmission.WITHOUT D-SACK:With the use of D-SACK illustrated above, the sender knows thateither the first transmission of segment 1000-1499 was delayed in the network, or the first transmission of segment 1000-1499 was droppedand the second transmission of segment 1000-1499 was duplicated.Given that no other segments have been duplicated in the network,this second option can be considered unlikely.Without the use of D-SACK, the sender would only know that either the first transmission of segment 1000-1499 was delayed in the network,or that either one of the data segments or the final ACK wasduplicated in the network. Thus, the use of D-SACK allows the senderto more reliably infer that the first transmission of segment1000-1499 was not dropped.[AP99] and [L99] both note that the sender could unambiguously detect an unnecessary retransmit with the use of the timestamp option. Inaddition, [AP99] proposes a heuristic for detecting an unnecessaryretransmit in an environment with neither timestamps nor SACK. [L99] also proposes a two-bit field as an alternate to the timestamp option for unambiguously marking the first three retransmissions of apacket. A similar idea was proposed in [ISO8073].RESEARCH ISSUES:The use of D-SACK allows the sender to detect some cases (e.g., when no ACK packets have been lost) when a a Fast Retransmit was due topacket reordering instead of packet loss. This allows the TCP sender to adjust the duplicate acknowledment threshold, to prevent suchunnecessary Fast Retransmits in the future. Coupled with this, when the sender determines, after the fact, that it has made anunnecessary window reduction, the sender has the option of‘‘undoing’’ that reduction in the congestion window by resettingssthresh to the value of the old congestion window, and slow-starting until the congestion window has reached that point.Any proposal for ‘‘undoing’’ a reduction in the congestion windowwould have to address the possibility that the TCP receiver could be lying in its reports of received packets [SCWA99].5.3. Retransmit Timeout Due to ACK LossIf an entire window of ACKs is lost, a timeout will result. Anexample of this is given below:Transmitted Received ACK SentSegment Segment (Including SACK Blocks)500-999 500-999 1000 (ACK dropped)1000-1499 1000-1499 1500 (ACK dropped)1500-1999 1500-1999 2000 (ACK dropped)2000-2499 2000-2499 2500 (ACK dropped)(timeout)500-999 500-999 2500, SACK=500-1000--------In this case, all of the ACKs are dropped, resulting in a timeout.This condition can be identified because the first ACK receivedfollowing the timeout carries a D-SACK block indicating duplicatedata was received.WITHOUT D-SACK:Without the use of D-SACK, the sender in this case would be unable to decide that no data packets has been dropped.RESEARCH ISSUES:For a TCP that implements some form of ACK congestion control[BPK97], this ability to distinguish between dropped data packets and dropped ACK packets would be particularly useful. In this case, the connection could implement congestion control for the return (ACK)path independently from the congestion control on the forward (data) path.5.4. Early Retransmit TimeoutIf the sender’s RTO is too short, an early retransmission timeout can occur when no packets have in fact been dropped in the network. Anexample of this is given below:Transmitted Received ACK SentSegment Segment (Including SACK Blocks)500-999 (delayed)1000-1499 (delayed)1500-1999 (delayed)2000-2499 (delayed)(timeout)500-999 (delayed)500-999 10001000-1499 (delayed)1000-1499 1500...1500-1999 20002000-2499 2500500-999 2500, SACK=500-1000--------1000-1499 2500, SACK=1000-1500---------...In this case, the first packet is retransmitted following thetimeout. Subsequently, the original window of packets arrives at the receiver, resulting in ACKs for these segments. Following this, the retransmissions of these segments arrive, resulting in ACKs carrying SACK blocks which identify the duplicate segments.This can be identified as an early retransmission timeout because the ACK for byte 1000 is received after the timeout with no SACKinformation, followed by an ACK which carries SACK information(500-999) indicating that the retransmitted segment had already been received.WITHOUT D-SACK:If D-SACK was not used and one of the duplicate ACKs was piggybacked on a data packet, the sender would not know how many duplicatepackets had been received. If D-SACK was not used and none of theduplicate ACKs were piggybacked on a data packet, then the senderwould have sent N duplicate packets, for some N, and received Nduplicate ACKs. In this case, the sender could reasonably infer that some data or ACK packet had been replicated in the network, or thatan early retransmission timeout had occurred (or that the receiver is lying).RESEARCH ISSUES:After the sender determines that an unnecessary (i.e., early)retransmit timeout has occurred, the sender could adjust parametersfor setting the RTO, to prevent more unnecessary retransmit timeouts. Coupled with this, when the sender determines, after the fact, thatit has made an unnecessary window reduction, the sender has theoption of ‘‘undoing’’ that reduction in the congestion window.6. Security ConsiderationsThis document neither strengthens nor weakens TCP’s current security properties.7. AcknowledgementsWe would like to thank Mark Handley, Reiner Ludwig, and VenkatPadmanabhan for conversations on these issues, and to thank MarkAllman for helpful feedback on this document.8. References[AP99] Mark Allman and Vern Paxson, On Estimating End-to-End Network Path Properties, SIGCOMM 99, August 1999. URL‘‘/sigcomm/sigcomm99/papers/session7-3.html’’.[BPK97] Hari Balakrishnan, Venkata Padmanabhan, and Randy H. Katz,The Effects of Asymmetry on TCP Performance, Third ACM/IEEE MobicomConference, Budapest, Hungary, Sep 1997. URL‘‘/˜padmanab/index.html#Publications’’.[F99] Floyd, S., Re: TCP and out-of-order delivery, Message ID<199902030027.QAA06775@> to the end-to-end-interestmailing list, February 1999. URL‘‘/floyd/notes/TCP_Feb99.email’’.[ISO8073] ISO/IEC, Information-processing systems - Open SystemsInterconnection - Connection Oriented Transport ProtocolSpecification, Internation Standard ISO/IEC 8073, December 1988.[L99] Reiner Ludwig, A Case for Flow Adaptive Wireless links,Technical Report UCB//CSD-99-1053, May 1999. URL‘‘/papers/Ludwig-FlowAdaptive/’’.[RFC1323] V. Jacobson, R. Braden, and D. Borman, TCP Extensions forHigh Performance, RFC 1323, May 1992. URL‘‘/rfc/rfc1323.txt’’.[RFC2018] Mathis, M., Mahdavi, J., Floyd, S., and Romanow, A., TCPSelective Acknowledgement Options. RFC 2018, Proposed Standard, April 1996. URL ‘‘ftp:///in-notes/rfc2018.txt’’.[RFC2581] M. Allman, V. Paxson, W. Stevens, TCP Congestion Control,RFC 2581, Proposed Standard, April 1999. URL ‘‘ftp:///in- notes/rfc2581.txt’’.[SCWA99] Stefan Savage, Neal Cardwell, David Wetherall, Tom Anderson, TCP Congestion Control with a Misbehaving Receiver, draft paper,April 1999.AUTHORS’ ADDRESSESSally FloydAT&T Center for Internet Research at ICSI (ACIRI)Phone: +1 510-642-4274 x189EMail: floyd@URL: /floyd/Jamshid MahdaviNovellPhone: 1-408-967-3806Email: mahdavi@Matt MathisPittsburgh Supercomputing CenterPhone: 412 268-3319Email: mathis@URL: /˜mathis/Matthew PodolskyUC Berkeley Computer Science Dept.Phone: 510-649-8914Email: podolsky@URL: /˜podolsky Allyn RomanowCisco SystemsPhone: 408-525-8836Email: allyn@This draft was created in August 1999.It expires February 2000.。