Are Supershells Powered by Multiple Supernovae Modeling the Radio Pulsar Population Produce
- 格式:pdf
- 大小:196.45 KB
- 文档页数:17

科技是把双刃英语作文高二Technology is a double-edged sword. On one hand, it has brought about tremendous advancements and convenience inour lives. From smartphones to artificial intelligence, technology has revolutionized the way we communicate, work, and live. It has made information readily accessible andhas connected people from all corners of the world. However, on the other hand, technology has also led to various negative consequences. It has created a sense of dependency and addiction, as people become glued to their screens and lose touch with the real world. Additionally, technologyhas raised concerns about privacy and security, as our personal information becomes vulnerable to cyber attacks.The rapid development of technology has undoubtedly changed the way we communicate. Social media platforms like Facebook and Instagram have made it easier for us toconnect with friends and family, no matter where they are. We can share our thoughts, photos, and videos with just a few taps on our screens. However, this constant need forvalidation and attention on social media has also led to a rise in mental health issues, such as anxiety and depression. People are constantly comparing themselves to others and seeking approval from strangers, which can be detrimental to their self-esteem and well-being.In the workplace, technology has greatly improved efficiency and productivity. With the help of computers and software programs, tasks that used to take hours can now be completed in a matter of minutes. This has allowed businesses to streamline their operations and achieve higher levels of profitability. However, the automation of jobs has also resulted in unemployment and job insecurity for many individuals. As machines become more advanced and capable of performing complex tasks, there is a growing concern that humans will be replaced by robots andartificial intelligence.Education has also been greatly impacted by technology. Online learning platforms and educational apps have made it possible for students to access educational resources anytime, anywhere. This has opened up opportunities forindividuals who may not have had access to quality education otherwise. However, the reliance on technology in the classroom has also raised concerns about the lack of face-to-face interaction and the potential for cheating. Students may become too reliant on technology and lose important social and problem-solving skills.In conclusion, technology has undoubtedly brought about numerous benefits and advancements in our lives. However, it is important to recognize the negative consequences that come with it. We must be mindful of our usage and ensure that technology does not control us. It is crucial tostrike a balance between embracing the convenience and opportunities that technology offers, while also being aware of its potential drawbacks. Only then can we truly harness the power of technology for the betterment of society.。
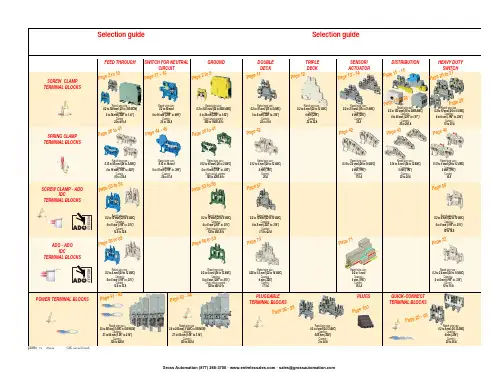
ABB EntrelecSommaireBU0402061SNC 160 003 C0205SummarySelection guide ....................................................................................page 1Screw clamp ........................................................................................page 2Feed through and ground terminal blocks .......................................................page 2 - 5 to 10Single pole, multiclamp terminal blocks..........................................................................page 4Feed through terminal blocks - Double-deck................................................................page 11Feed through terminal blocks - Triple-deck...................................................................page 12Three level sensor, terminal blocks without ground connection...................................page 13Three level sensor, terminal blocks with ground connection ........................................page 14Terminal blocks for distribution boxes, double deck + protection .......................page 15 - 16Interruptible terminal blocks for neutral circuit......................................................page 17 - 18Distribution : phase, ground terminal blocks .......................................................page 19 to 21Single pole or four pole distribution blocks..........................................................page 22 to 24Heavy duty switch terminal blocks with blade......................................................page 25 - 26Heavy duty switch terminal blocks with push-turn knob..............................................page 26Heavy duty switch terminal blocks with contact control pull lever...............................page 29Heavy duty switch terminal blocks with blade - Double-deck .....................................page 27Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.)or 6.35x25.4 mm (1/4x1 in.) and 6.35x32 mm (1/4x11/4 in.) fuse s.........................................page 28 - 29Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.) fuses -Double-dec k.....................................................................................................................page 27Terminal blocks for test circuits with sliding bridge ......................................................page 30Terminal blocks for metering circuits.............................................................................page 31ESSAILEC terminal blocks.............................................................................................page 32Safety connection terminal blocks ................................................................................page 33Miniblocks for EN 50045 (DIN 46277/2) rail ..........................................................page 34 - 35Spring clamp ......................................................................................page 36Angled terminal blocks - Feed through and ground .....................................................page 36Feed through and ground terminal blocks ...........................................................page 37 to 41Feed through terminal blocks - Double deck ................................................................page 42Terminal blocks for sensors / actuators ........................................................................page 42Terminal blocks for distribution boxes...........................................................................page 43Switch terminal blocks for neutral conductor........................................................page 44 - 45Heavy duty switch terminal blocks with blade..............................................................page 46Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.) fuse s....page 47Miniblocks Spring clamp ......................................................................................page 48 to 52ADO - Screw clamp ...........................................................................page 53Feed through and ground terminal blocks ...........................................................page 53 to 56Feed through and ground terminal blocks - Double-deck............................................page 57Heavy duty switch terminal blocks with blade..............................................................page 58Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.) fuse s ......page 59 - 60Miniblocks ADO - Screw clamp............................................................................page 61 to 65ADO - ADO .........................................................................................page 66Feed through and ground terminal blocks ...........................................................page 66 to 69Feed through and ground terminal blocks - Double-deck............................................page 70Terminal blocks for sensors / actuators ........................................................................page 71Heavy duty switch terminal blocks with blade..............................................................page 72Fuse holder terminal blocks for 5x20 mm (.197x.787 in.) and 5x25 mm (.197x.984 in.) fuse s ......page 73 - 74Miniblocks ADO - ADO .........................................................................................page 75 to 79Accessories ADO ...........................................................................................................page 80Power terminal blocks .............................................................page 81 to 84Quick-connect terminal blocks .................................................page 85 - 86Terminal blocks for railway applications ................................page 87 to 97Pluggable terminal blocks .....................................................page 98 to 100Accessories......................................................................................page 101Marking..................................................................................page 102 to 104GrossAutomation(877)268-3700··*************************PR30PR3.Z2PR3.G2PR5PR4PR1.Z2Rated wire size :Rated wire size :Rated wire size :Rated wire size :Mounting railsShield terminals forcollector barMarking tableHorizontal Rated wire size :0.5 to 16 mm² (22 to 8 AWG)Rated wire size :Rated wire size :Rated wire size :P a g e t o 29e30 t o 32ag e e3P a ge 8 t o 60a g e6t o 6574P a ge 7 t o 79P a ge 9P a g P a gGrossAutomation(877)268-3700··*************************2ABB Entrelecd010830402051SNC 160 003 C0205MA 2,5/5 - 2.5 mm² blocks - 5 mm .200" spacingAccessoriesGrossAutomation(877)268-3700··*************************3ABB Entrelec D010740402051SNC 160 003 C0205M 4/6 - 4 mm² blocks - 6 mm .238" spacingAccessoriesGrossAutomation(877)268-3700··*************************4ABB EntrelecD011030402051SNC 160 003 C0205M 4/6.3A - 4 mm² blocks - 6 mm .238" spacingM 4/6.4A - 4 mm² blocks - 6 mm .238" spacingGrossAutomation(877)268-3700··*************************5ABB Entrelec D010840402051SNC 160 003 C0205M 6/8 - 6 mm² blocks - 8 mm .315" spacingAccessoriesGrossAutomation(877)268-3700··*************************6ABB EntrelecD010850402051SNC 160 003 C0205M 10/10 - 10 mm² blocks - 10 mm .394" spacingAccessoriesGrossAutomation(877)268-3700··*************************7ABB Entrelec D010860402051SNC 160 003 C0205M 16/12 - 16 mm² blocks - 12 mm .473" spacingAccessoriesGrossAutomation(877)268-3700··*************************8ABB EntrelecD010870402051SNC 160 003 C0205M 35/16 - 35 mm² blocks - 16 mm .630" spacingGrossAutomation(877)268-3700··*************************M 95/26 - 95 mm² blocks - 26 mm 1.02" spacingM 70/22.P - 70 mm² ground block with rail contact - 22 mm .630" spacingSelection35 mm / 1.37"12 mm / 0.47"14-30 Nm / 124-260 Ib.in 1.2-1.4 Nm / 10.6-12.3 Ib.in1000600600415400400577070240 mm 2500 MCM 500 MCM 10 mm 2 6 AWG 6 AWG IEC UL CSANFC DIN0.5 - 160.5 - 100 AWG-600 MCM 2 AWG-500 MCM 50 - 30035 - 24018-6 AWGD 150/31.D10 - 150 mm² blocks - 31 mm 1.22" spacingCharacteristicsD 240/36.D10 - 240 mm² blocks - 36 mm 1.41" spacingSelectionWire size main circuit mm² / AWG VoltageV Current main circuit A Current outputARated wire size main circuit mm² / AWG Rated wire size outputmm² / AWG Wire stripping length main circuit mm / inches Wire stripping length output mm / inches Recommended torque main circuit Nm / Ib.in Recommended torque outputNm / Ib.inSolid Stranded Solid Stranded Wire size output mm² / AWG9.5 mm / .37"0.5-0.8 Nm / 4.4-7.1 Ib.in5003003003220204 mm 212 AWG12 AWG0.2 - 422-12 AWG 22-12 AWG 0.22 - 4IEC ULCSANFC DINCharacteristicsWire size mm² / AWGSolid Stranded D 4/6.T3 - 4 mm² blocks - 6 mm .238" spacingSelectionVoltage V CurrentARated wire sizemm² / AWG Wire stripping length mm / inches Recommended torqueNm / Ib.inM 4/6.T3.P - 4 mm² block - 6 mm .238" spacingD 2,5/6.D - 2.5 mm² blocks - 6 mm .238" spacingD 2,5/6.DL - 2.5 mm² blocks - 6 mm .238" spacingD 2,5/6.DPA1 - 2.5 mm² blocks - 6 mm .238" spacingD 2,5/6.DPAL1 - 2.5 mm² blocks - 6 mm .238" spacingD 4/6... - 4 mm² blocks - 6 mm .238" spacingD 4/6.LNTP - 4 mm² closed blocks - 17.8 mm .700" spacingMA 2,5/5.NT- 2.5 mm² block - 5 mm .200" spacingAccessories**SFB2 : 16 to 35 mm² 6 to 2 AWG H= 3 mm/.12"M 10/10.NT- 10 mm² block - 10 mm .394" spacingAccessories(1) Except for M 35/16 NT (closed block)*SFB1 : 0.5 to 35 mm² 18 to 2 AWG H= 7 mm/.28"**SFB2 : 16 to 35 mm² 6 to 2 AWG H= 3 mm/.12"MB 4/6... - 4 mm² blocks - 6 mm .238" spacingMB 6/8... - 6 mm² blocks - 8 mm .315" spacingMB 10/10... - 10 mm² blocks - 10 mm .394" spacingBRU 125 A - 35 mm² block - 27 mm 1.063" spacingBRU 160 A - 70 mm² block - 35.2 mm 1.388" spacingBRU 250 A - 120 mm² blocks - 44.5 mm 1.752" spacingBRU 400 A - 185 mm² block - 44.5 mm 1.752" spacingAccessoriesAccessoriesBRT 80 A - 16 mm² block - 48 mm 1.89" spacingBRT 125 A - 35 mm² block - 48 mm 1.89" spacingBRT 160 A - 50 mm² block - 50 mm 1.97" spacing9.5 mm / .37"0.5-0.6 Nm / 4.4-5.3 Ib.in4003003002010104 mm 210 AWG 12 AWG 0.5 - 422-10 AWG20-12 AWG0.5 - 2.5IEC ULCSANFC DINMA 2,5/5.SNB - 2.5 mm² blocks - 5 mm .200" spacingCharacteristicsM 4/6.SNB - 4 mm² blocks - 6 mm .238" spacingSelectionWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping length mm / inches Recommended torqueNm / Ib.inSolid StrandedM 6/8.SNB - 6 mm² blocks - 8 mm .315" spacing - blade switchingSelectionAccessoriesM 4/8.D2.SF - for fuses 5x20 mm .197x.787 in. and 5x25 mm .197x.984 in. -4 mm² blocks - 8 mm .315" spacingM 4/6.D2.SNBT - 4 mm² blocks - 6 mm .238" spacing - blade switchM 4/8.SF- 4 mm² blocks - 8 mm .315" spacingM 4/8.SFL - 4 mm² blocks - 8 mm .315" spacing12 mm / .472"1.2-1.4 Nm / 10.6-12.3 Ib.in800(1)60060016252510 mm 210 AWG8 AWG0.5 - 1622-10 AWG 22-8 AWG 0.5 - 10IEC ULCSANFC DINCBD2SML 10/13.SF - for fuses 6.35x25.4 mm 1/4x1 in. and 6.35x32 mm 1/4x11/4 in. -10 mm² blocks - 13 mm .512" spacingSelectionAccessoriesCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping length mm / inches Recommended torqueNm / Ib.inSolid Stranded (1) Insulation voltage of terminal block - operating voltage : according to fuse.M 4/6.D2.2S2... - 4 mm² blocks - 6 mm .238" spacing11 mm / .43"0.8-1 Nm / 7.1-8.9 Ib.in50060030306 mm 28 AWG0.5 - 1022-8 AWG0.5 - 6IECULCSANFC DINM 6/8.ST... - 6 mm² blocks - 8 mm .315" spacingCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping length mm / inches Recommended torqueNm / Ib.inSolid Stranded M 6/8.STA - 6 mm² blocks - 8 mm .315" spacing(3)Only for M 6/8.STAM 4/6.ST- 4 mm² blocks - 6 mm .236" spacingBNT...PC...(2) Only for M10/10.ST-SnThe PREM IUM solution for testing the secondary circuits of current or voltage transformers.ESSAILEC, approved by the major electricity utilities, remains the premium choice for the energy market.Implemented in the transformers secondary circuits, ESSAILEC thanks to its intelligent “make before break” design eases and secures any intervention. Cutting the energy supply is avoided with zero risk for the operator.The plug and socket connection cuts cost installation as well as in-situ wiring errors. ESSAILEC is ideal for the wiring of sub-assemblies in the secondary circuits.ESSAILEC terminal blocksProtection relays,Protection relays,Testing :The ESSAILEC socket supplies energy to the protection or counting devices. The insertion of the test plug, which is connected to the measurement equipment, allows the testing of the devices, without perturbing the circuit.ESSAILEC blocks are well adapted to current or voltage measurement :-Current sockets with make before break contacts and pre-wired test plug for current measures-Voltage sockets with open contacts and pre-wired test plug for voltage measures-Up to 4 ammeters or 4 voltmeters connected to the test plugDistributing :The ESSAILEC plug is continuously mounted on the socket to supply current or voltage to secondary circuits sub assemblies.ESSAILEC blocks extreme versatility allow :-Safe current distribution with current socket with mobile contacts since the secondary circuit is not cut when plug is removed-Voltage or polarity distribution with dedicated voltage or polarity socket with closed contactESSAILEC is designed to offer :Great flexibility :-Connection multi contacts « plug and play »-Panel, rail, rack fixed mounting or stand-alone connector -Two wiring technologies, up to 10 mm²Extreme reliability :-Non symmetric blocks -Coding accessories -IP20 design -Locking system -Sealed coverR S T NFor technical characteristics and complete part numbers list, please ask for the ESSAILEC catalog10005006003225254 mm 21.65 mm²12 AWG 13 mm / .51"IECB.SCSANFC DINTS 50-180.5 - 0.8 Nm /4.4 - 7.1 Ib.in0.2 - 422-12 AWG0.22 - 40.5 - 1.50.28 - 1.6580050060041252562.512 AWG 13 mm / .51"0.8 - 1 Nm / 7.1 - 8.9 Ib.inIECB.S CSANFC DINTS 50-180.5 - 1020-12 AWG0.5 - 60.28 - 2.590050060046406510 mm 26 mm² 6 AWG 14 mm / .55"IECB.S UL/CSANFC DINTS 50-181.2 - 1.4 Nm / 10.6 - 12.3 Ib.in0.5 - 1620 - 6 AWG0.5 - 100.28 - 6M 4/6.RS - 4 mm² blocks - 6 mm .238" spacingCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping lengthmm / inches Recommended torque (screw)Nm / Ib.inSolid wire Stranded wire Solid wire Stranded wire Screw clampLugsM 6/8.RS - 6 mm² blocks - 8 mm .315" spacingCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping lengthmm / inches Recommended torque (screw)Nm / Ib.inSolid wire Stranded wire Solid wire Stranded wire Screw clampLugspending M 10/10.RS - 10 mm² blocks - 10 mm .394" spacingCharacteristicsWire size mm² / AWGVoltage V CurrentARated wire sizemm² / AWG Wire stripping lengthmm / inches Recommended torque (screw)Nm / Ib.inSolid wire Stranded wire Solid wire Stranded wire Screw clampLugspending SelectionAccessories(1) Only for block M 4/6.RS (4) For blocks M 4/6.RS and M 6/8.RS(2) Only for block M 6/8.RS(3) Only for block M 10/10.RSDR 1,5/4 - 1.5 mm² blocks - 4 mm .157" spacingDR 1,5/5... - 1.5 mm² blocks - 5 mm .200" spacing。


用英语写一篇80字的网络安全作文全文共6篇示例,供读者参考篇1Cybersecurity: Keeping the Internet Safe for EveryoneHi there! My name is Jamie, and I'm 10 years old. Today, I want to talk to you about something super important called cybersecurity. It's a big word, I know, but it's really important for keeping the internet safe for all of us.You see, the internet is like this massive playground where we can learn, play games, watch videos, and talk to our friends and family. It's so much fun! But just like in a real playground, there are some not-so-nice people who might try to cause trouble or hurt others. That's where cybersecurity comes in.Cybersecurity is all about protecting our computers, phones, tablets, and other devices from bad guys who want to steal our information or mess things up. These bad guys are called hackers, and they use all sorts of sneaky tricks to try and get into our devices.One of the biggest threats is something called malware. Malware is like a computer virus that can infect your device and cause all sorts of problems. It can steal your personal information, slow down your computer, or even delete all your files! Scary, right?But don't worry, there are ways to protect ourselves from malware and other cyber threats. First and foremost, we need to have strong passwords for all our accounts. A strong password is one that's long, has a mix of letters, numbers, and special characters, and isn't something easy to guess like your name or birthday.Another important thing is to be careful about what links we click on and what files we download. Sometimes, hackers will try to trick us into clicking on a bad link or downloading a file that contains malware. That's why it's always best to only click on links or download files from sources you trust, like your parents, teachers, or reputable websites.We also need to be extra careful when we're using public Wi-Fi networks, like at a coffee shop or the library. These networks aren't as secure as the one we have at home, so it's best to avoid doing anything too sensitive, like online banking or shopping, while connected to them.One of the coolest things about cybersecurity is that there are special people called cybersecurity professionals whose job is to keep the internet safe for everyone. They're like the superheroes of the digital world! They use all sorts of high-tech tools and techniques to fight off hackers and protect our devices and information.Cybersecurity professionals work for companies, governments, and even video game companies to make sure their systems are secure and their customers' information is protected. They're always on the lookout for new threats and vulnerabilities, and they're constantly coming up with new ways to stay one step ahead of the bad guys.But cybersecurity isn't just about the professionals – we all have a role to play in keeping the internet safe. By being smart about our online habits, using strong passwords, and being cautious about what we click on or download, we can help make the internet a safer place for everyone.So, the next time you're surfing the web or playing your favorite online game, remember the importance of cybersecurity. It's like having a super-strong force field around your devices, protecting you from all the bad stuff out there.And who knows, maybe one day you'll grow up to be a cybersecurity superhero yourself! Imagine fighting off hackers and protecting the world from cyber threats – how cool would that be?For now, keep being smart and safe online, my friends. The internet is an amazing place, and with cybersecurity on our side, we can all enjoy it without worrying about the bad guys. Let's keep the internet safe and fun for everyone!篇2My Big Sister Teaches Me About CybersecurityMy big sister Julia is so smart! She's in middle school and knows all about computers and the internet. I'm just in 4th grade, so a lot of that stuff is still pretty confusing to me. But Julia is really patient and helps explain things in a way I can understand.The other day, I was playing an online game on my tablet when Julia came into my room. "Whatcha doing, squirt?" she asked, ruffling my hair. I made a face - I hate when she calls me that! "I'm playing Quarriors. It's this really cool game where you build up armies and battle other players online," I explained.Julia nodded slowly. "That's cool. Just be careful when you're playing games like that or browsing online. There are some bad people out there who might try to hack into your device or steal your personal information."I looked at her blankly. "What do you mean? Like a computer virus?""Exactly," Julia said. "Viruses, malware, spyware - those are all types of malicious code that cybercriminals use to attack devices and networks. They can get onto your computer or phone in lots of sneaky ways, like through spam emails, infected websites, or even disguising themselves as safe files or programs."I shuddered at the thought. "That's really scary! What would happen if I got a virus?""Well, it depends on the type of malware. Some viruses just corrupt your data or cause your device to crash. But others can give the hacker remote access, letting them spy on you through your webcam, log your keystrokes to steal passwords, or lock you out of your device entirely and hold it for ransom," Julia explained."That's terrible!" I exclaimed. "How can I protect myself?"Julia smiled. "I'm glad you asked! There are some simple cybersecurity best practices everyone should follow. First, be really careful what you click on or download - never open any files or attachments unless you know exactly what they are and where they came from. Install good anti-virus and anti-malware software to scan for threats."She continued, "Creating strong, unique passwords for every account is crucial too. And never share personal information like your name, address, phone number, or birthday online unless you're absolutely sure the website is safe and legit."I nodded along slowly, trying to absorb all the advice. "This cybersecurity stuff is complicated! Is there anything else I need to know?""Using public WiFi networks can be really risky, since it's easy for hackers to intercept your data traffic over an unsecured connection. It's best to avoid doing anything private like online banking when you're on public WiFi," Julia warned. "Oh, and be careful about the devices and technology you bring into our home too. Some cheap gadgets from sketchy manufacturers could potentially be lined with malware or backdoors for cybercrooks to exploit."My eyes were as wide as saucers. "The internet sounds so dangerous! Maybe I shouldn't even go online at all..."Julia laughed and put a hand on my shoulder. "Don't be scared, little bro. As long as you stay vigilant and follow cybersecurity best practices, you'll be just fine. The internet is an amazing resource when you know how to navigate it safely."I thought for a moment, then nodded firmly. "You're right. Thanks for explaining all this to me, Julia. I'm going to be way more careful about stuff like passwords, downloads, and sketchy links from now on. The internet is awesome - I don't want some meanie hackers ruining it for me!"Julia grinned and ruffled my hair again. "That's the spirit! Now get back to your game, kid. Just remember - if anything seems fishy, log off and come find me. Looking out for cyber threats is all part of being a responsible digital citizen these days.""Will do!" I gave her a cheesy thumbs-up, then turned my attention back to the game, feeling a little wiser about the big wide web and the importance of cybersecurity. With Julia's advice, I was ready to safely explore all the amazing things the online world had to offer!篇3My Big Book About Staying Safe OnlineHey kids! It's me, Cyber Buddy the cyber safety mascot. Today I want to teach you all about staying safe when you're online. The internet is an amazing place where you can learn new things, talk to your friends, watch videos, and play games. But just like in the real world, there are some bad people out there who might try to take advantage of you or get your private information. That's why it's super important to follow some basic rules about cybersecurity.First things first - what even is cybersecurity? It's all about protecting your devices like phones, tablets, and computers from bad people trying to break in or mess with your stuff. Just like you lock your house to keep burglars out, cybersecurity is about putting locks on your virtual spaces too!One of the biggest cybersecurity risks is from malware. Malware is bad software that nasty hackers make to mess up your devices and steal your info. It can come from downloading apps from sketchy websites, opening unsafe email attachments, or even just clicking on virus links. Malware is like a stickycomputer booger that gets all over your device and causes all kinds of problems!To avoid malware, only download apps and programs from legit stores you know and trust. Never open email attachments from people you don't know. And of course, never ever click on suspicious links, even if they look funny or silly. Those could just be traps to infect your device with malware!Another big cybersecurity danger is from phishing scams. That's when a bad person sends you a message pretending to be someone else, like your bank, a company you buy stuff from, or even a friend or family member. They'll make the message look really real and then try to trick you into giving out your passwords, credit card numbers, or other private info. Phishing is just a big fat lie to steal your secrets!The best way to spot a phishing scam is to always double check who the message is really from. If it's asking for your passwords or personal details, that's a huge red flag because legit companies will never ask for that stuff over email or text. When in doubt, ask a trusted adult before responding to any suspicious messages.Speaking of trusted adults, it's really important to have open conversations with your parents, teachers, and other trustedgrown-ups about being safe online. They can help you understand what's safe and what's not, and make sure you aren't doing anything risky without even realizing it. Having that guidance is key to great cyber safety!You should also make sure to keep your device's security software like antivirus programs and firewalls up-to-date. That's like keeping your device's force field strong to deflect any nasty malware trying to break through. Your parents can help make sure all that security stuff stays current.Another cybersecurity basic is using strong passwords that are really hard for bad guys to guess. Never use easy passwords like "password" or "123456". Instead, mix together some wacky words with numbers and symbols to create super passwords that only you know. And definitely don't share your passwords with anyone except your parents!While it's fun to chat with friends online, you have to be really careful about what personal information you share and who you're sharing it with. Never give out sensitive details like your address, phone number, birthdate, or where you go to school to anyone you don't know in real life and trust completely. There could be creepy adults pretending to be other kids trying to coax those secrets out of you.If you ever get a message or see something online that makes you uncomfortable or seems creepy, trust your instincts! Don't engage with that person anymore and tell a parent or trusted adult right away so they can look into it. Some people have really bad intentions online, so you always need to be on guard.Speaking of being on guard, you also need to protect your privacy by being smart about what you post and share online too. Never share passwords or other sensitive details. Be careful about posting your location, since that could let people know where you live or go to school. And simply avoid sharing anything too personal that could be embarrassing or used against you later.Overall, just use common sense and don't be shy about asking parents or teachers for help if you're ever unsure about something online. We all need to work together to build a safer, more secure internet for everyone!Well, that's about all the cybersecurity tips I can fit into one book! Just remember - think before you click, keep your personal info locked, tell a trusted adult about any cyber sketchiness, and we can all explore the internet while keeping the bad guys at bay.Stay cyber smart out there, and I'll see you again soon for more security fun!Your friend,Cyber Buddy篇4Title: Being Safe Online is Important!Hi there! My name is Tommy, and I'm here to talk to you about something really important – staying safe online! These days, we spend a lot of time on the internet, whether it's for schoolwork, playing games, or just having fun. But you know what? There are also some not-so-nice people out there who might try to cause trouble or even hurt us.That's why it's super duper important to be careful when we're online. Let me tell you a little story about what happened to my friend Lily last week.Lily was playing her favorite game online when a pop-up appeared, asking her to enter her parents' credit card information to get a special prize. Now, Lily is a smart cookie, but she got a little too excited about the prize and typed in thenumbers without thinking twice. Big mistake! The next day, her mom got a huge bill for stuff they didn't even buy!That's called a scam, and it's one of the ways thosenot-so-nice people try to trick us into giving them our personal information or money. Lily felt really bad about it, and her parents had to cancel their credit card and go through a whole lot of trouble.But you know what? That's not the only danger lurking online. Sometimes, strangers might try to chat with us and say mean things or ask us for pictures or information we shouldn't share. That's called cyberbullying, and it's not okay at all!So, what can we do to stay safe? Here are some super important tips:Never, ever share personal information like your name, address, phone number, or school with someone you don't know online. That's private stuff!Don't open any links or attachments from people you don't know or trust. They could have viruses that mess up your computer or steal your info.If someone is being mean or making you feel uncomfortable online, tell a trusted adult right away. You don't have to deal with that alone.Use strong passwords that are hard to guess, and don't share them with anyone except your parents or guardians.Be careful about what you post online. Once it's out there, it's really hard to take it back!Always ask your parents or guardians before giving out any personal information or downloading something new.Following these tips might seem like a lot of work, but it's so important to keep ourselves safe. The internet is an amazing place, but we have to be smart and careful explorers!Remember, if something ever feels wrong or makes you uncomfortable online, trust your instincts and tell a trusted adult right away. We're all in this together, and by looking out for each other, we can have tons of fun online without any worries.Stay safe, stay smart, and keep being awesome! Until next time, this is Tommy signing off!篇5Computer Safety is Really Important!Hi friends! Today I want to talk to you about something super important called cybersecurity. Cybersecurity is all about keeping computers, phones, tablets and the internet safe from bad guys trying to cause trouble. It's a big word, but it's really important for all of us to understand, even kids like you and me!The internet is amazing - it lets us learn new things, watch fun videos, play games and talk to our friends and family online. But there are some not-so-nice people out there who try to mess things up and cause problems. That's where cybersecurity comes in篇6Cybersecurity: Keeping Safe in the Digital WorldHi there! My name is Emma and I'm going to tell you all about cybersecurity today. Cybersecurity is really important, especially for kids like us who spend a lot of time online these days. It's all about keeping safe when we use computers, tablets, smartphones and the internet.The internet is an awesome place - we can learn new things, watch fun videos, play games and chat with our friends online. But there are also some bad people out there who try to cause trouble. These troublemakers are called hackers or cybercriminals. Their mean tricks and digital traps are called cyber threats.One common cyber threat is a computer virus. Viruses are programs that can sneak into your device without you knowing. Once inside, they can do all sorts of nasty stuff like delete your files, steal your info or even let the hacker control your device remotely! Scary, right? That's why we need good cybersecurity habits to block viruses.Another threat is called malware, which is short for "malicious software". Malware programs are designed to damage devices or steal data. Some malware locks your computer and holds it for ransom until you pay money to。

顾家北0813精品班作文大作文Many people think it is very important to protect the environment but they make no effort to do it themselves. Why do you think it is the case? What actions can be done to ensure that individuals protect the environment?顾家北Environmental problems have threatened the world but few people have chosen to take any action to deal with these problems, although they realise the impact of these environmental woes on their lives. We should implement some changes to improve the situation.Many people spend money wisely, so they are not willing to purchase environmentally friendly products, de spite the fact that these products can help preserve the environment. These products are normally more expensive than conventionalcounterparts. For example, LED lighting devices are energy efficient, but normally charge consumers a higher price than traditional light bulbs. Electriccarsarenormallylikelyto cost more money than those vehiclespoweredbypetrol. As consumers do not optfor these green products, it is not easy to conserveresources and reducepollution.Another reason is that many people are not willing to change their ways of life, even though these lifestyles can be harmful to the environment. The use of electrical equipment has led to a sharp rise in electricity consumption, which means that the powergenerationsector has a higher demand for fossilfuels. People also prefer to travel by car, but car emissions can cause global warming, which is a threat to the environment. The reliance on different electronic products including mobile phones is another issue, since many of these products end up in landfill sites.These problems can be tackled by two policies. Governments can enact laws to forbid those behaviours which can cause damage to the environment, such as disposing of waste carelessly. Those who drop litter should be fined, so the environmental impact of this behaviour can be reduced. Another solution is to offer subsidies to encourage people to go green. For example, those consumers who buy fuel efficient cars can be subsidised, so car emissions can be reduced significantly.Currently, more and more people are aware of the importance of environmentalprotection but the public never give priority to protect environment during their daily life.One reason accounts for the phenomenon is that people live carefully without spending their money on environmental products. Households live with a tight budget are not willing to spend their money these products, whose prices are higher than other similar goods. For instance, LED lights are energy saving, but they are more expensive than incandescent bulbs. Similarly, prices of electric vehicles are higherthan those of traditional vehicles averagely. For the sake of money, people quit buying green products and this is contrary to our purpose of environmental protection.Another reason can be that people are not willing to change their living styles, which need to consume various kinds of energy. For example, electronic appliances consume electricity while driving consumes petrol. Especially those who are fond of plenty of materials consume more.Personally, the government are supposed to establish relevant laws to ban citizens from doing detrimental behaviours to environment. Punishments are imperative for those who littered. On the other hand, it is also imperative for the government to give subsidies to encourage environmental protection. Some countries, such as China, provide subsidies for those who purchasing vehicles under 1.6L.All in all, only through the joint efforts of government and individuals can we live in a sustainable environment.Currently, a large proportion of children are exposed to an ocean of commercial advertisements day to day. I am on the side that the ads, which purposely incite kids to buy snacks, toys and electronic games, should be limited or even, banned.Suppose that ads aim to kids were rectified, children will not request their parents to buy what they want day in and day out. Kids lack sensitivity to price, nevertheless,parents tend to satisfy their material needs. For instance, some children like expensive toys and girls are in favor of clothes. This will bring a heavy burden for the middle-class families. Only by minimize the impact of ads on kids can the problem be avoided.Children may have eccentric behaviours and bad living habits due to the ads. Some kids are fans of fast food, since they see ads of it every day. Others are in bad temper, due to the violent games they play daily. The predominance of games is also resulted from merchants’ propaganda. All these problems will influence the healthy growth process of kids both physically and mentally.However, we cannot deny that some ads do have their advantages to kids. Some advertisements promote nutrient food, such as milk, wheat, etc. Meanwhile, some advertise books, games and educational toys. Parents, who are not familiar with these products, can have a comprehensive verdict according to advertisements.In a nutshell, I strongly suggest the government ban ads whose target consumers are kids, especially if their products are harmful to children. But if the products the advertisements focus on are beneficial, then the ads should be allowed.小作文第一篇The table illustrates the proportion of people who are laid off in Poland, Denmark, Germany, Italy and Hungary. The two colons are the figures of young people (aged from 15-24) and all citizens respectively.The highest unemployment rate for young goes to Poland, which reaches 37% and is twice more than the rate of its overall rate 15%. Coming next is Italy. The proportionof its young citizens who are out of work is 23% and its unemployment of whole country comes to top at 18%. Hungary shows mediocre rates of 21% and 17%. And German figures are 4% and 3% lower than Denmark respectively. Denmark keepsboth figures lowest, with the unemployment rate for 15-24 age group 8% and for overall only 3%.All of the five countries show 3~5% rates lower of overall unemployment than thoseof the young, except Poland which has the largest gap between the two figures.第二篇The bar charts provide us information about how families in an Asian country spent their money in 1998 and 2008.A glance at the charts tells that expenditure on different goods in 2008 overweighed that in 1998 except that spent on clothes. People gave much more priority to spiritual enjoyment which lead to a huge increase of expenditure on holiday, eating out, reading (newspapers and magazines) and going to cinema, rising from 8% to 15%, 6% to 15%,3% to 8% and 3%to 5% respectively. The costs for electronic goods also increased from 12% to14% during the decade.The only difference is expenditure on clothes which was totally opposite to the mainstream. The proportion of it was 10% in 1998; however it dropped to half of its original rates in 2008.All in all, the past 10 years witnessed a huge change of the expenditure on various of aspects for households.第三篇The charts tell the proportion of different categories of house people live in three parts of Australia in 2001 and 2006.In 2001, Victoria had 76% residents in house, 12% in semi-detached house, 11%in apartments and the rest in other types. In NSW, house also accounted for the largest part of 66%, with 10% and 13% in duplex and flat respectively. And more peoplelived in other kinds. Tasmania had largest proportion of house living population,which reaches 88%.Five years later, the rates for house all dropped 2% in the three regions. As forsemi-detached house, Victoria, NSW and Tasmania saw 1% increase, 1percent decrease and stability respectively. The figures of flat all had a slightly increase. And for the rest unmentioned types, they remained the same at 1% except NSW rose from 11% to 12%.The table compares five European countries in terms of the proportions of unemployed people as well as the figures for those young people out of work. Poland had the highest youth unemployment rate at 37%, nearly five times the level in Denmark. The levels of unemployment for young people were similar in other countries, with the highest seen in Italy 23% and the lowest in Germany at 17%.It is clear from the table that in all these countries, the unemployment rate for the younger generation was higher than the overall unemployment figures. Interestingly, Poland, Germany, Italy and Hungary had similar unemployment rates, ranging between 15% and 18%. The figure for Denmark was significantly lower at 3%. Overall, youth unemployment was more serious in Poland than in other countries. Denmark had the lowest figures for both youth unemployment and overall unemployment, while other countries had similar figures for these problems.流程图写作The chart illustrates how to use cocoa beans to produce several food items for customers.Firstly, whole beans are carefully picking before drying in the shell. Then they are pressed into cocoa liquor, which is the main material of the second stage. Then cocoa liquor is further pressed untilit becomes a coca cake, which is directly sent to industry to make cakes and drinks or is sold to the consumer after grinded into cocoa powder. The cocoa liquor can also convert into cocoa and then be sent to relevantindustry.Cocoa liquor, after further refining, mix with cocoa and sugar turns to industry chocolate. Finished chocolate products will be put on the shell, before the final process.All in all, cocoa beans can be used to produce cocoa powder, chocolate products and ingredients for relevant industry through three simple stages starting frompre-processing raw material to final packaging for sell.顾家北The whole beans are picked at the first stage with shells removed, and then dried and pressed until cocoa liquor is created. This marks the start of the second stage, which involves three processes. The cocoa liquor can be used to make coca cakes in the first option. Another choice is the manufacture of cocoa, while cocoa liquor is refined in the third process to produce industrial chocolate.In the final stage, these materials are processed further to create different end products for either corporate clients or ordinary consumers. Coca cakes are ground into cocoapowder for individual consumers, or directly delivered to catering businesses which provide drinks and cakes. Cocoa in the second procedure mentioned earlier is also transported to these businesses. In contrast, the industrial chocolate is flavored with sugar, and finished chocolate products are subsequently available for consumers.第一篇The table provides us with data of the percentage of consumer expenditure on different items in five countries in 2002.The biggest number existed in Turkey, where people spent 32.14% of their income on food, drink and tobacco, almost five times the number of percentage spent on clothing (6.63%) and eight times the figure of percentage spent on spiritualenjoyment. Coming next is Ireland, whose percentage of national consumer expenditure of eating was28.91%. Costs for clothing and footwear accounted for only 6.43%, three times the expenditure of leisure and education. Spain took the third place though the proportionof its national consumer expenditure was the lowest (1.98%). Expenditure of food items in Spain accounted for 18.8%, threefold the figure of its clothing spending. Italy and Sweden citizenshad small percentages of income spent on food(16.36%,15.77%),only about half the figure of Turkey. However, their clothing costs (9%, 5.4%) and spiritualpay-outs (3.2%, 3.22%) were relatively high.In a nutshell, the percentages of national consumer expenditure by category in 2001 varied a lot among the five countries. But all shared some similarities, namely, largest proportion of expenditure on food, drink and tobacco and smallest percentage of leisure and education costs.第二篇The bar charts show the number of marriages and divorces in USA and marital statusof American adults during the period of 1970 to 2000.The number of marriages remained at 2.5 million in 1970 and 1980, after which it had a slightly decrease to 2 million in 2000. The divorces number started form 1 million in 1970 and suddenly increased to almost 1.5 million during that decade. Then it dropped to nearly 1 million in 1980 and finally reached to its start(1 million).The percentage of never married adults was 15% in 1970 and the figure inclined to 20% thirty years later. The proportions of both married and widowedadults saw drops during the three decades. Married adults accounted for 70% in 1970 while the figure was less than 60% in 2000. As for divorce rate, it had a significant rise form nearly 0% to almost 10%.All in all, the period from 1970 to 2000 witnessed a huge change of marriages and divorces in America. Both the total number and percentage of marriage decreased while the proportions of never married and divorced people saw an upward trend.流程图The two diagrams illustrate how to produce cement and how to use cement to produce concrete.Cement production is relatively complex and uses two materials. Firstly, limestone and clay are placed in the crusher, where these materials are crushed by the crusher. Then powder is mixed by the mixer, before being heated by the rotating heater. At the next stage, heated powder is sent to the grind, where it is grounded into cement. And finally cement is packed in the bags.Concrete production is relatively simple. 15% of cement, 10% of water, 25% of sand and 50% of gravel, namely small stones are mix in the concrete mixer, where they turned out to be concrete.All in all, cement production includes 5 stages and the outcome cement is one of the four raw materials of the concrete production.地图The maps show how an area changed during the period of 1780 to 2000.In 1780, there were 100 homes located on the north-eastern corner with woods to the south. A river crossed the area from south to north with four farms in the middle of the region.80 years later, the number of dwelling places doubled to 200, while the number of farms dropped by half and woods also shrank in size. A road was built in the north area, connecting the living place to the river. Another major change is that a bridge was constructed over the river.In 2000, the number of homes suddenly increased to 500 and a newly built road, heading towards south replaced farm and woods area, which linked the dwelling places to the school and sports field in the south. Several shops opened to the right side of the downstream river with a wetland for birds to their south.Overall, this area saw an increase in constructions such as dwelling places, schools and facilities, although farmland and forests were removed for new buildings and transportinfrastructure.大作文We live in cities or towns which have museums displaying historical and cultural importance, but people do not visit them. Why do you think people do not visit museums in their local areas?What is the importance of museums to society?顾家北Visiting museums is hardly a rewarding experience for many people, so they will not consider this option when they can spend leisure time on other activities. These museums do not organize new exhibitions that can keep up with the trends, or provide any form of entertainment like interactive games to attract the young audience. This is why a trip to a museum can hardly compete for attention with sports, picnics and parties. Another reason is that people can gather information about those artefacts on display on the Internet. They will increase knowledge about the stories behind and the cultural value of each item, without having to visiting the museum in person.Museums can encourage visitors’ interest in their c ultural heritage and disseminate knowledge about a city or a county’s cultural assets. Some exhibitions may show ancient utensils used by previous generations, so people who attend these exhibitions may have a good idea of how traditional food was cooked. Some historical documents and paintings might show the architectural style which used to predominate, and many visitors might be impressed by the architectural achievements of their ancestors. With such knowledge, these visitors may make an effort to preserve some traditions and keep some old-fashioned cooking skills or building techniques alive.Museums have also been operating as a center of learning, where young people can keep up to date with the cutting-edge technology in different fields. The aviation museums, for example, give children a glimpse of the airline industry and even space travel, including spaceships and equipment supporting astronauts who explored the outer space. The museum of archeology can show them how some species have died out, and possibly inspire them to do research in biology and extend our knowledge of how to preserve our ecosystem. They could not make contributions to social progress, if they did not have access to such knowledge.Recently, an increasing number of people refused to pay a visit to museums in their local places. Personally, following reasons may account for the phenomenon.Some people reckon museums as boring places so that they are never willing to visit. For example, the historical and cultural importance displayed there has never changed and there is no entertainment, such as interactive games. All these tend to left people a boring feeling. In contrast, people prefer to join some interesting activities such as ball games, picnic and dining out. Another reason is that nowadays people learn history and acquire science knowledge through internet rather than go to library in person. Information of the exhibition's the historical value and story can be easily accessed on line.However, visiting museums play an important role in tradition inheriting. Ancient vessels provide us with traditional cooking methods while murals enable us to comprehend style of ancient architecture to some degree. It is advantageous for young people to pass on the culture if they have a good acknowledge of their own tradition by visiting museums.Additionally, museums offer us the most advanced science and technology, which is beneficial to the development of the society. The latest development of space and universe in our country can be acquired in space museums and the young can understand the reason of creature extinction through visiting archaeology museums. Museums can motivate the interests of the adolescents and the young will accelerates the development of society in the future.Overall, visiting museums is of great significance for both the individuals’ comprehending of culture and the development of our society.顾家北Visiting museums is hardly a rewarding experience for many people, so they will not consider this option when they can spend leisure time on other activities. These museums do not organise new exhibitions that can keep up with the trends, or provide any form of entertainment like interactive games to attract the young audience. This is why a trip to a museum can hardly compete for attention with sports, picnics and parties. Another reason is that people can gather information about those artefacts on display on the Internet. They will increase knowledge about the stories behind and the cultural value of each item, without having to visiting the museum in person.Museums can encourage visitors’ interest in their cultural heritage and disseminate knowledge about a city or a county’s cultural assets. Some exhibitions may show ancient utensils used by previous generations, so people who attend these exhibitions may have a good idea of how traditional food was cooked. Some historical documents and paintings might show the architectural style which used to predominate, and many visitors might be impressed by the architectural achievements of their ancestors. With such knowledge, these visitors may make an effort to preserve some traditions and keep some old-fashioned cooking skills or building techniques alive.Museums can also provide us with the latest technological advances, which is beneficial to the development of the society. For example, the aviation museums offer us latest knowledge of aeronautics while the archaeology museums help us comprehend the reason of extinction. This is why museums can not only motivate the interests of teenagers but also encourage them to study hard in a long run, which will accelerate the improvement of the society in the future. (Self-written paragraph)The aviation museums spaceships, shuttles, astronauts, explore the outer space,Some people think university education should provide students with skills of employment in the future while others believe that people should focus on academic study only. Discuss both views and give your own opinion.Some people think the increasing business and cultural contact between countries brings many positive effects. Others say it causes the loss of national identities. Discuss on both sides and give your opinion.People rely more on foreign products and imitate traditions and culture of other countries, which lead to a hard way to pass on their own culture. For instance, too much reliance on the foreign cosmetics will surely shrink the demand of domestic market, which requires the local industry to downsize work force and thus traditional ways of making up will be abandoned. Additionally, those who are in favor of celebrating others’ festivals tend to give less priority to their own traditions. This will put the intangible culture heritage form our ancestors in a dangerous situation.Many countries spend a lot of money in art. Some people think investment in art is necessary, but others say money is better spent on public services and facilities. Discuss both views and give your own opinion.翻译练习1. 人们对政府赞助艺术(government sponsorship)有不同的看法,特别在国家遇到预算问题的时候。

红警发现核聚变打击的英语作文The world has always been a complex and ever-changing place, where the pursuit of power and dominance is a constant driving force. In this ever-evolving landscape, the emergence of advanced military technologies has become a crucial factor in the global power dynamics. One such technology that has captured the attention of military strategists and the public alike is the concept of nuclear fusion as a weapon of mass destruction.The Red Alert, a highly classified military intelligence organization, has long been at the forefront of studying and understanding the implications of this devastating technology. Through their tireless efforts, they have uncovered a startling revelation – the existence of a nuclear fusion-based strike capability that could potentially reshape the balance of power on a global scale.The principles behind nuclear fusion are well-known – the process of fusing light atomic nuclei to create heavier ones, releasing an immense amount of energy in the process. This energy can be harnessed for peaceful purposes, such as the generation of clean andsustainable electricity. However, in the hands of those with malicious intent, this same process can be weaponized, leading to the development of fusion-based warheads that dwarf the destructive power of traditional nuclear weapons.The Red Alert's investigations have revealed that certain rogue nations and terrorist organizations have been actively pursuing the development of these fusion-based strike capabilities. The implications are staggering – a single fusion-based warhead could level an entire city, leaving behind a trail of devastation and destruction that would echo through the ages. The sheer scale of the potential damage is enough to send shockwaves through the international community.What makes the fusion-based strike capability even more alarming is the relative ease with which it can be developed, compared to the complex and resource-intensive process of building traditional nuclear weapons. The required materials and technological expertise are more readily available, making it a more accessible option for those seeking to acquire weapons of mass destruction.The Red Alert's findings have sparked a flurry of activity within the global intelligence community. Governments around the world have scrambled to bolster their defenses, seeking to develop countermeasures and early warning systems that could potentiallythwart such a devastating attack. The race to stay ahead of the curve has become a high-stakes game, with the future of entire nations hanging in the balance.Yet, the challenge lies not only in the development of effective deterrents but also in the delicate diplomatic balancing act required to prevent the proliferation of this technology. The Red Alert has recognized that a collaborative, international approach is essential in addressing this threat, as no single nation can shoulder the burden alone.Efforts are underway to establish robust international frameworks and treaties that would strictly regulate the research, development, and use of fusion-based weapons. The goal is to create a global consensus that would effectively curb the ambitions of those seeking to harness this power for nefarious purposes.However, the path forward is fraught with obstacles. Geopolitical tensions, conflicting national interests, and the ever-present risk of espionage and sabotage threaten to undermine these efforts. The Red Alert's operatives have been working tirelessly to navigate these treacherous waters, forging alliances and gathering intelligence that could prove crucial in the fight to prevent a global catastrophe.As the world holds its collective breath, the Red Alert continues itsvigilant watch, ever-alert to the slightest hint of a fusion-based strike capability emerging from the shadows. The stakes have never been higher, and the consequences of failure are unthinkable. The future of humanity hangs in the balance, and the Red Alert is the last line of defense against the looming threat of nuclear fusion as a weapon of mass destruction.。

核按钮英语作文Title: The Nuclear Button: Power, Responsibility, and Global Security。
In the realm of geopolitics, few symbols hold as much weight and significance as the nuclear button. It represents the ultimate power wielded by a select few individuals, capable of unleashing devastation on a scale never before seen in human history. The mere existence of this button underscores the importance of responsible governance and the imperative of maintaining global security.The concept of the nuclear button traces its origins back to the development of nuclear weapons during World War II. With the culmination of the Manhattan Project, humanity gained access to a form of destructive power previously unimaginable. Since then, the possession of nuclear weapons has become synonymous with geopolitical influence and deterrence.At the heart of the nuclear button dilemma lies the balance between power and responsibility. The ability to initiate a nuclear strike with the push of a button confers immense authority upon those entrusted with this capability. However, this power comes with an equally immense burden of responsibility. The consequences of a nuclear exchange are catastrophic, with the potential to inflict untoldsuffering and irreparable harm to both present and future generations.Furthermore, the existence of the nuclear button introduces a precarious dynamic into international relations. The concept of mutually assured destruction (MAD) has long served as a deterrent against nuclear conflict,with the understanding that any use of nuclear weaponswould result in catastrophic retaliation. However, the proliferation of nuclear weapons to additional states and the emergence of non-state actors have complicated this delicate balance.In recent years, advancements in technology have addeda new layer of complexity to the nuclear button dilemma. The rise of cyber warfare and the potential for hackers to infiltrate command and control systems raise concerns about the security and integrity of nuclear arsenals. The vulnerability of these systems underscores the need for robust safeguards and protocols to prevent unauthorized access or malicious interference.Moreover, the nuclear button dilemma extends beyond the realm of geopolitics to encompass ethical considerations as well. The very existence of nuclear weapons raises profound questions about the morality of their use and the ethical responsibilities of those who possess them. The indiscriminate nature of nuclear weapons makes them incompatible with principles of proportionality andcivilian immunity, casting doubt on their legitimacy as instruments of warfare.In light of these challenges, it is imperative for the international community to address the nuclear button dilemma with urgency and resolve. This requires a concerted effort to strengthen arms control agreements, promotedisarmament initiatives, and enhance transparency and confidence-building measures among nuclear-armed states. Additionally, investments in diplomatic dialogue and conflict resolution mechanisms can help mitigate tensions and reduce the risk of nuclear confrontation.Ultimately, the nuclear button serves as a sobering reminder of the awesome power of human ingenuity and the fragility of global security. Its existence demands vigilance, accountability, and a steadfast commitment to the pursuit of peace. Only through collective action and cooperation can we hope to navigate the complexities of the nuclear age and safeguard the future of humanity.。

支持正版拒绝盗版英语作文As the world becomes more and more digital, the issueof piracy has become increasingly prevalent. Piracy is the act of illegally copying and distributing someone else's work, whether it be music, movies, or software. This is a serious problem that affects not only the creators of the works, but also the consumers who purchase them. In this essay, I will argue that we should support the use of legitimate products and reject piracy.Firstly, piracy is a form of theft. When people pirate music, movies, or software, they are essentially stealing from the creators of those works. This is not only illegal, but it is also morally wrong. Creators invest a lot of time, effort, and money into producing their works, and they deserve to be compensated for their efforts. Piracy robs them of that compensation, and it discourages them from creating future works.Secondly, piracy harms consumers. Pirated products areoften of lower quality than legitimate products. For example, pirated movies may have poor video and audio quality, and they may be missing important scenes or subtitles. Pirated software may contain viruses or other malware that can harm your computer. Legitimate products, on the other hand, are guaranteed to be of high quality and safe to use.Furthermore, piracy also harms the economy. When people pirate works, they are not only stealing from the creators, but they are also taking money away from legitimate businesses. This can lead to job losses and a decrease in economic growth. In addition, piracy can also lead to an increase in prices for legitimate products, as companiestry to recoup their losses.In conclusion, we should support the use of legitimate products and reject piracy. Piracy is a form of theft that harms both creators and consumers. It also harms the economy and can lead to job losses. By choosing to use legitimate products, we can support the creators of thoseworks and ensure that we are getting high-quality products that are safe to use.。

八年级英语信息安全保护方法单选题30题1.We need to install a good _____ to protect our computer from viruses.A.softwareB.firewallC.hardwareD.program答案:B。
本题考查信息安全相关名词。
选项A“software”是软件,不能直接保护电脑免受病毒侵害。
选项B“firewall”防火墙,可以阻止病毒和恶意软件的入侵,符合题意。
选项C“hardware”是硬件,与防病毒关系不大。
选项D“program”程序,比较宽泛,不一定能起到保护电脑免受病毒侵害的作用。
2.Which one is an important tool for information security?A.keyboardB.mouseC.antivirus softwareD.monitor答案:C。
选项A“keyboard”键盘是输入设备,与信息安全关系不大。
选项B“mouse”鼠标也是输入设备,与信息安全无直接关系。
选项C“antivirus software”杀毒软件是信息安全的重要工具,正确。
选项D“monitor”显示器只是输出设备,不能保障信息安全。
3.A _____ can prevent unauthorized access to a network.A.routerB.switchC.gatewayD.server答案:C。
选项A“router”路由器主要用于网络连接和路由选择。
选项B“switch”交换机用于连接多台设备。
选项C“gateway”网关可以防止未经授权的访问网络,符合题意。
选项D“server”服务器主要提供服务,不能防止未经授权的访问。
4.The _____ is used to store important data securely.A.diskB driveC.cloud storageD.hard drive答案:C。

Chinese CultureChinese CharactersCang jie who created the Chinese characters which means the beginning of the Chinese culture in about 26th century BC.Chinese characters constitute the oldest continuously used system of writing in the world. By nature of widespread use in China and Japan, Chinese characters are among the most widely adopted writing systems in the world.Hakka cultureHakka are a subgroup of the Han Chinese that originated in northern China. It is the aboriginal people of the north of China.The Hakka , sometimes Hakka Han, are Han Chinese who speak the Hakka language and have links to the provincial areas of Guangdong, Jiangxi, Guangxi, Sichuan, Hunan and Fujian in China.The Hakka's ancestors were often said to have arrived from what is today's central China centuries ago. In a series of migrations, the Hakkas moved, settled in their present locations in southern China, and then often migrated overseas to various countries throughout the world. The worldwide population of Hakkas is about 80 million, though the number of Hakka-language speakers is fewer. Hakka people have had a significant influence on the course of Chinese and world history: in particular, they have been a source of many revolutionary, government, and military leaders.Yangshao cultureThe Yangshao culture was a Neolithic culture that existed extensively along the central Yellow River in China.It is dated from around 5000 BC to 3000 BC.They kept such animals as pigs, chickens and dogs, as well as sheep, goats, and cattle, but much of their meat came from hunting and fishing. Their stone tools were polished and highly specialized. The Yangshao people may also have practiced an early form of silkworm cultivation.Longshan cultureThe Longshan culture was a late Neolithic culture in China, centered on the central and lower Yellow River and dated from about 3000 BC to 2000 BC.The Longshan culture was a late Neolithic culture in China, centered on the central and lower Yellow River and dated from about 3000 BC to 2000 BC. The Longshan culture is named after thetown of Longshan in the east of the area under the administration of the city of Jinan, Shandong Province, where the first archaeological find (in 1928) and excavation (in 1930 and 1931) of this culture took place at the Chengziya Archaeological Site.The distinctive feature of the Longshan culture was the high level of skill in pottery making, including the use of pottery wheels.Xia DynastyThe Xia Dynasty (c. 2070 –c. 1600 BC) is the first dynasty in China to be described in ancient historical chronicles such as Bamboo Annals, Classic of History and Records of the Grand Historian. But there is not direct evidence to support that the Xia Dynasty has existed.According to the traditional chronology based upon calculations by Liu Xin, the Xia ruled between 2205 and 1766 BCE; according to the chronology based upon the Bamboo Annals, it ruled between 1989 and 1558 BC. The Xia–Shang–Zhou Chronology Project concluded that the Xia existed between 2070 and 1600 BCE. The tradition of tracing Chinese political history from heroic early emperors to the Xia to succeeding dynasties comes from the idea of the Mandate of Heaven, in which only one legitimate dynasty can exist at any given time, and was promoted by the Confucian school in the Eastern Zhou period, later becoming the basic position of imperial historiography and ideology.Shang DynastyShang is the first dynasty which has the direct and significantly records of the same period of the dynasty.most direct information comes from oracle bones –turtle shells, cattle scapulae, or other bones. There are remnants of advanced, stratified societies dating back to the Shang period have been found in the Yellow River Valley. (1600 BC–1046 BC)Archaeological work at the Ruins of Yin (near modern day Anyang), which has been identified as the last Shang capital, uncovered eleven major Yin royal tombs and the foundations of palaces and ritual sites, containing weapons of war and remains from both animal and human sacrifices. Tens of thousands of bronze, jade, stone, bone, and ceramic artifacts have been obtained. The workmanship on the bronzes attests to a high level of civilization.The inscriptions on the oracle bones are divinations, and they provide critical insight into many topics from the politics, economy, and religious practices to the art and medicine of this early stage of Chinese civilization.Zhou DynastyThe Zhou Dynasty was a Chinese dynasty that followed the Shang Dynasty and preceded the Qin Dynasty. In addition, Shang is the longest dynasty of China.(1046–256 BC) During the Zhou Dynasty, the use of iron was introduced to China, though this period of Chinese history produced what many consider the zenith of Chinese bronze-ware making. The dynasty also spans the period in which the written script evolved into its modern form with the useof an archaic clerical script that emerged during the late Warring States period.Spring and Autumn period & Warring States periodWarring States period about 476 BC–221 BCSpring and Autumn period about 770 BC –476 BCAt the same time, the constant conflict and need for innovative social and political models led to the development of many philosophical doctrines, later known as the Hundred Schools of Thought. The most notable schools of thought include Mohism, expounded by Mozi; Confucianism, represented by Mencius and Xunzi; Taoism, represented by Zhuangzi, and Legalism, represented by Shang Yang and Han Feizi.This period is most famous for the establishment of complex bureaucracies and centralized governments, as well as a clearly established legal system. The developments in political and military organization were the basis of the power of the Qin state, which conquered the other states and unified them under the Qin Empire in 221 BC.Qin DynastyThe Qin Dynasty was the first imperial dynasty of China, lasting from 221 to 206 BC.Qin Dynasty has a strong bow and arrow shooter force and the arrow was advanced at that time. Qin army has a strong bow and arrow shooter ForceThe Terracotta army is famous all over the worldDuring its reign over China, the Qin Dynasty achieved increased trade, improved agriculture, and military security. This was due to the abolition of landowning lords, to whom peasants had formerly held allegiance.The central government now had direct control of the masses, giving it access to a much larger workforce. This allowed for the construction of ambitious projects, such as a wall on the northern border, now known as the Great Wall of China.The Great Wall has 8851.8 kmChina's first imperial dynasty was the Qin Dynasty (221–206 BCE). The Qin unified the Chinese Warring States by conquest, but their empire became unstable after the death of the first emperor Qin Shi Huangdi. Within four years, the dynasty's authority had collapsed in the face of rebellion.Han DynastyThe Han Dynasty (206 BC –220 AD) was an imperial dynasty of ChinaScience and technology during the Han period saw significant advances, including papermaking, the use of negative numbers in mathematics, the raised-relief map, the hydraulic-powered armillary sphere for astronomy, and a seismometer employing an inverted pendulum.From the reign of Emperor Wu onward, the Chinese court officially sponsoredConfucianism in education and court politics, synthesized with the cosmology of later scholars such as Dong Zhongshu.Southern and Northern DynastiesThe Southern and Northern Dynasties was a period in the history of China that lasted from 420 to 589. Though an age of civil war and political chaos, it was also a time of flourishing arts and culture, advancement in technology, and the spreading of Mahayana Buddhism and Daoism. The period saw large-scale migration of Han Chinese people to the lands south of the Yangtze River.During this period the process of Sinicization accelerated among the non-Chinese arrivals in the north and among the aboriginal people in the south. This process was also accompanied by the increasing popularity of Buddhism (introduced into China in the 1st century) in both north and south China, along with Daoism gaining influence from the outline of Buddhist scriptures (with two essential Daoist canons written during this period). Although multiple story towers such as guard towers and residential apartments existed in previous periods, during this period the distinct Chinese pagoda tower (for storing Buddhist scriptures) evolved from the stupa, the latter originating from Buddhist traditions of protecting sutras in ancient India.There were notable technological advances during this period. With the invention of the stirrup during the earlier Western Jin Dynasty, heavy cavalry became standard in combat. Advances in medicine, astronomy, mathematics, and cartography are also noted by historians. The famous Chinese mathematician and astronomer Zu Chongzhi (429–500) belonged to this age, an intellectual and social product of the elite culture shaped and developed in southern China during this period of time.Sui DynastyThe Sui Dynasty (589–618 CE)was a short-lived Imperial Chinese dynasty. Preceded by the Southern and Northern Dynasties, it unified China for the first time after over a century of north-south division. It was followed by the Tang Dynasty.Founded by Emperor Wen of Sui, the Sui Dynasty capital was at Chang'an. His reign saw the reunification of Southern and Northern China and the construction of the Grand Canal. Emperors Wen and Yang undertook various reforms including the Equal-field system, which was initiated to reduce the rich-poor social gap that resulted in enhanced agricultural productivity, as well as government centralization and reforms, creating a new model of governance after centuries of division. The Three Departments and Six Ministries system was officially instituted, coinage was standardized and re-unified, defense was improved and the Great Wall expanded. Buddhism was also spread and encouraged throughout the empire, uniting the varied peoples and cultures of China. Weakened by costly and disastrous military campaigns against Goguryeo (in modern day Korea) which ended with the defeat of Sui in the early seventh century, the dynasty disintegrated through a combination of popular revolts, disloyalty, and assassination.Tang DynastyThe Tang Dynasty(June 18, 618 –June 1, 907) was an imperial dynasty of China preceded by the Sui Dynasty and followed by the Five Dynasties and Ten Kingdoms Period. It was founded by the Li family, who seized power during the decline and collapse of the Sui Empire. The dynasty was interrupted briefly by the Second Zhou Dynasty (October 8, 690 –March 3, 705) when Empress Wu Zetian seized the throne, becoming the only Chinese empress regnant, ruling in her own right.The Tang Dynasty, with its capital at Chang'an (present-day Xi'an), which at the time was the most populous city in the world, is generally regarded as a high point in Chinese civilization—equal to, or surpassing that of, the earlier Han Dynasty—a golden age of cosmopolitan culture. Its territory, acquired through the military campaigns of its early rulers, rivalled that of the Han Dynasty. In two censuses of the 7th and 8th centuries, the Tang records estimated the population by number of registered households at about 50 million people.Yet, even when the central government was breaking down and unable to compile an accurate census of the population in the 9th century, it is estimated that the population had grown by then to about 80 million people. With its large population base, the dynasty was able to raise professional and conscripted armies of hundreds of thousands of troops to contend with nomadic powers in dominating Inner Asia and the lucrative trade routes along the Silk Road. Various kingdoms and states paid tribute to the Tang court, while the Tang also conquered or subdued several regions which it indirectly controlled through a protectorate system. Besides political hegemony, the Tang also exerted a powerful cultural influence over neighboring states such as those in Korea, Japan, and Vietnam.Song DynastyThe Song Dynasty was a ruling dynasty in China between 960 and 1279; it succeeded the Five Dynasties and Ten Kingdoms Period, and was followed by the Yuan Dynasty. It was the first government in world history to issue banknotes or paper money, and the first Chinese government to establish a permanent standing navy. This dynasty also saw the first known use of gunpowder, as well as first discernment of true north using a compass.The Song Dynasty is divided into two distinct periods: the Northern Song and Southern Song. During the Northern Song (960–1127), the Song capital was in the northern city of Bianjing (now Kaifeng) and the dynasty controlled most of inner China. The Southern Song (Chinese: 1127–1279) refers to the period after the Song lost control of northern China to the Jin Dynasty. During this time, the Song court retreated south of the Yangtze River and established their capital at Lin'an (Hangzhou). Although the Song Dynasty had lost control of the traditional birthplace of Chinese civilization along the Yellow River, the Song economy was not in ruins, as the Southern Song Empire contained 60 percent of China's population and a majority of the most productive agricultural land. The Southern Song Dynasty considerably bolstered its naval strength to defend its waters and land borders and to conduct maritime missions abroad.To repel the Jin, and later the Mongols, the Song developed revolutionary new military technology augmented by the use of gunpowder.The porcelain of Song was very famous. No earthenware could stand up to boiling waterwithout dissolving and nowhere in Europe was it understood how to heat a kiln to the fourteen hundred degrees or so required to vitrify clay and make it impervious to liquids, boiling or not. Even so wise a man as Sir Francis Bacon could only view porcelain as a kind of plaster which, after a long lapse of time buried in the earth, "congealed and glazed itself into that fine substance." Other writers speculated it was made from lobster shell or eggs pounded into dust.Song RenzongHe was a emperor of Song Dynasty. Despite his long reign of over 40 years, Renzong is not widely known. His reign marked the high point of Song influences and powers but was also the beginning of its slow disintegration that would persist over the next century and a half.Renzong died in 1063 without an heir. His temple name means "Benevolent Ancestor".Ming DynastyThe Ming Dynasty, also Empire of the Great Ming, was the ruling dynasty of China for 276 years (1368–1644) following the collapse of the Mongol-led Yuan Dynasty. The Ming, described by some as "one of the greatest eras of orderly government and social stability in human history", was the last dynasty in China ruled by ethnic Han Chinese. Although the primary capital of Beijing fell in 1644 to a rebellion led by Li Zicheng (who established the Shun Dynasty, soon replaced by the Manchurian Qing Dynasty), regimes loyal to the Ming throne –collectively called the Southern Ming –survived until 1662.The Hongwu Emperor (ruled 1368–98) attempted to create a society of self-sufficient rural communities ordered in a rigid, immobile system that would guarantee and support a permanent class of soldiers for his dynasty: the empire's standing army exceeded one million troops and the navy's dockyards in Nanjing were the largest in the world. He also took great care breaking the power of the court eunuchs and unrelated magnates.Zheng He, led seven enormous voyages of exploration into the Indian Ocean as far as Arabia and the coast of Africa.Chinese invention1. Papermaking skill2. Compass3. Gunpowder4. TypographyThe Chinese Feudal SocietyIn China, there were approximately 559 ruler which means China had experienced more than 2,500 years of feudal society.Chiese FoodDough FigurineDough Figurine, a traditional Chinese art craft, used to be popular among children all over China.The dough figurine is a mixture of flour, glutinous rice flour and various colors, pinched into various figurines of people and animals.In the past, the dough figurine masters often carried a small box and walked around Hutong. But now, one can only see this traditional art craft on temple fair.Sugar paintingThe sugar painting is just paintings made of sugar, which can not only be eaten but also appreciated. The history of this handicraft, with the local characters of Sichuan Province, is more than 400 years.Mie Craftsmana craftsman who makes articles from bamboo stripsChinese Kung FuCustom“Lian”can be translate into “face”in English which is one of the most important cultural traits of Chinese people. Giving face (giving due respect) is a very important concept in China. You must give the appropriate respect according to rank and seniority.“Lian”can be translate into “face”in English which is one of the most important cultural traits of Chinese people. Giving face (giving due respect) is a very important concept in China. You must give the appropriate respect according to rank and seniority.。
长大以后成为科学家的英语作文小学二年级全文共3篇示例,供读者参考篇1My Dream of Becoming a ScientistEver since I was a little kid, I've been really curious about how things work. I'm always asking "Why?" and trying to figure out the reasons behind everything. That's why I want to be a scientist when I grow up - so I can discover new things and find explanations for all the mysteries of the world!I got really interested in science from watching TV shows and reading books about dinosaurs, outer space, animals, and nature. Learning about gigantic dinosaurs that roamed the Earth millions of years ago just blows my mind. How did they get so enormously big? Why did they go extinct? I want to be a paleontologist and dig up dinosaur bones to study them.Outer space is another huge interest of mine. I'm fascinated by all the planets, stars, galaxies, black holes, and everything else out in the universe. It's incredible that there are billions of other galaxies besides our Milky Way, each with millions or billions of stars! I'd love to be an astronomer and look through powerfultelescopes to study faraway planets, stars, and galaxies. Maybe I could even be an astronaut and travel into space myself one day.Animals are another passion of mine. I've always loved pets and going to the zoo to see all the cool creatures. I'm amazed at how all the different animals have adapted with specialised bodies and abilities to survive in their environments. Like how giraffes have long necks to eat leaves high up, or how chameleons can change colors. If I became a zoologist, I could travel to rainforests and other habitats to observe animals in the wild.I'm endlessly awed by the natural world and phenomena like volcanic eruptions, tsunamis, hurricanes, the water cycle, photosynthesis, and more. As a scientist, I could study these things and make new discoveries to help us better understand our planet. Maybe I could find ways to predict and protect against natural disasters, or discover cures for diseases by studying plants and other organisms.Every day when I wake up, my mind is buzzing with new questions about how things work. Like how does electricity actually work and let us turn on lights and TVs? What makes the sky blue during the day, then black at night? Why do some materials like wood burn, while others like metal don't? How doairplanes manage to stay up in the sky? Questions like these drive my curiosity to want to become a scientist and find the answers.Being a scientist seems like the best job ever because you get to run experiments, make new inventions, explore unknown frontiers, and unlock the secrets of the universe. I can't wait to use the scientific method of asking questions, forming hypotheses, testing them out, recording observations, and analyzing data to make new breakthroughs. I really enjoy hands-on projects too, so being able to build things and use special scientific tools and equipment in a lab sounds awesome.Of course, I know becoming a scientist takes a lot of hard work and studying. I'll need to do very well in all my science, math, and other classes through elementary, middle, and high school. Then I'll probably have to go to college for many more years to get an advanced degree like a Ph.D. But I'm willing to put in the effort because science is my biggest passion and I can't imagine doing anything else.My parents have been really supportive of my dreams too. We go to the science museum all the time, where I get to interact with cool exhibits and watch science shows. They let me borrow tons of science books from the library and buy me science kits todo experiments at home. For my last birthday, I got a microscope and telescope which have been so fun to use. My parents always encourage me to keep asking questions and learning.I've been so lucky to have amazing science teachers who have helped spark my curiosity from a young age. Last year, my first grade teacher, Mrs. Graham, would do weekly hands-on science projects with us like making volcanoes with baking soda and vinegar, building circuits, and dissecting owl pellets. We also went on a field trip to a nature center where we went hiking and exploring. That's when I decided I definitely want to be a scientist.This year in second grade, my teacher Mr. Lopez is continuing to fuel my interest in science. We've learned about weather, the water cycle, plants, matter, energy, and more through reading books, watching videos, and doing experiments. Just last week, we got to grow bacteria for a project on microorganisms. We also meet with high school student mentors who are doing science fair projects. Seeing their experiments makes me excited to do science fair projects myself soon.I know being a scientist won't always be easy. You have to work really hard, be patient, and don't always get the results you want right away. Experiments can fail and you have to stick withit. Making mistakes and learning from them is a huge part of the process. You have to think creatively and come up with new ways to test your ideas. Paying close attention to details and recording data carefully is crucial too.But for me, the rewards of being a scientist and making new discoveries would make all the hard work worth it. I'd get to travel to work in different environments like labs, forests, oceans, and even other planets! Finding something completely new that changes how we understand the world would be so fulfilling. Like Isaac Newton with gravity, Marie Curie with radioactivity, or Jane Goodall with chimpanzee behavior.I'm sure there will be times of frustration and failure when experiments don't go right. But scientists also get to experience the thrill of those "Eureka!" moments when they finally crack the code and make a game-changing breakthrough. Even just understanding a difficult concept you've been struggling with can feel like an accomplishment. As a scientist, I'd have the opportunity to continually learn new things and constantly expand my knowledge.Some kids want to be firefighters, police officers, athletes, or movie stars when they grow up. And those are all good careers that help people. But for me, being a scientist and exploring theunknown to increase human knowledge is the most exciting path.I can't wait to someday lead a team of other scientists doing important research in a lab, in the field, or even in outer space!I know it won't be easy and there's still so much for me to learn over the next decade-plus of education ahead of me. But my dream of becoming a scientist and uncovering the secrets of our world and beyond is what drives my passion every day. When I put my mind to something, I don't give up easily. After all, it was the curiosity, creativity, determination, and hard work of past scientists that led to inventions like computers, vaccines, space travel, and so many other world-changing innovations. As a future scientist myself, who knows what mind-blowing discoveries I could contribute next?篇2My Big Dream of Becoming a ScientistHave you ever wondered how things work? Like how a tiny seed can grow into a huge tree? Or how a teeny tiny egg can turn into a big fluffy chick? I think about stuff like that all the time! The world is full of so many amazing things, and I want to learn all about them. That's why when I grow up, I'm going to be a scientist!Being a scientist means getting to explore the coolest mysteries of the universe. Scientists are like super smart detectives who use their powerful brains to figure out how everything works. They get to perform all sorts of experiments and make new discoveries that help make the world a better place. How awesome is that?I already love learning about science and doing little experiments. Last year in 1st grade, we learned about plants and how they grow from seeds. We each got to plant our own bean seed in a cup of soil and watch it sprout up out of the dirt over a few weeks. It was so much fun checking on my plant every day and seeing the tiny stem and leaves poke through. I even made little drawings tracking how tall it grew. By the end, my bean plant was over a foot high! It's amazing something so huge came from that one tiny seed.Another time, we had a special visitor bring in chicken eggs that were just about to hatch. We got to watch the little chicks peck their way out of their shells right in front of our eyes. It was hard to believe those cute, fuzzy chicks were once inside those smooth hard eggs. I got to gently hold one of the chicks - its little heart was beating so fast in my hand! I couldn't stop smilingear to ear. The whole experience made me feel like a scientist discovering something new.In 2nd grade this year, we've been learning about the human body and how it works. Our teacher brought in an actual real skeleton to show us what our bones look like. It was both really cool and a little bit creepy at the same time! We learned all the bone names like the femur, fibula, and phalanges. We even got to put together a life-size model of the human body, placing each bone and organ in the right spot. I want to be a scientist who studies the body when I grow up so I can help figure out cures for diseases and make people healthier.My favorite thing we've done so far though is the simple machine projects. We learned about the six simple machines - the lever, wheel and axle, pulley, inclined plane, wedge, and screw. Then we got to build our own using everyday objects like rulers, paperclips, rubber bands, and pencils. I made an amazing laser-guided mousetrap powered by a pulley to drop the hammer. It was so fun figuring out how to get it to work just right. I'd love to be an inventor scientist someday too and create new awesome machines to help people.Science is everywhere in the world around us which is why I think it's the coolest subject ever. I mean, just look at howiciclesform with their millions of tiny ice crystals. Or how a rainbow appears in the sky when the sun hits raindrops at just the right angle. Our teacher showed us pictures of fractals, which are these infinitely complex patterns that keep repeating smaller and smaller portions of themselves. You can zoom in on them forever and they still look the same! The deeper you look into science, the weirder and more fascinating it gets.When I become a scientist, I hope I get to travel to do my research too. Can you imagine getting to go on expeditions to remote jungles or deep in the ocean to study animals and plants most people have never seen before? Or even traveling to outer space someday to walk on other planets or moons? How cool would it be to make a new discovery that changes everything we thought we knew!Of course, being a scientist isn't all fun and games. It takes a ton of hard work and studying to become an expert on your topic. You have to go to college for like a million years to get your Ph.D. You have to be really dedicated and never give up, even when your experiments fail over and over again. It can probably be pretty frustrating at times.But in the end, it's all worth it to me because scientists get to unlock the secrets of the universe. They get to stand on the verycutting edge of human knowledge and understand things nobody else does. Maybe I'll even get my picture in a science book someday if I make an important breakthrough!So yeah, that's why my big dream is to be a scientist when I grow up. I can't wait to start asking questions, doing experiments, and making new discoveries. Who knows what amazing mysteries are waiting to be solved? I'll keep studying hard and learning as much as I can. The whole world is my laboratory! Let the adventures of science begin!篇3My Dream of Becoming a Great ScientistEver since I was a little kid, I've always been really curious about how the world works. I love learning new things and trying to figure out the reasons behind everything. That's why I want to become a scientist when I grow up!Scientists get to explore the most fascinating mysteries of the universe. They study topics like outer space, the human body, animals, plants, the environment, and so many other amazing subjects. By using their powerful minds and clever experiments, scientists gradually unlock the secrets of nature. I can't think of a more exciting way to spend your life!One area of science that really sparks my interest is space exploration. The thought of blasting off in a rocket ship and journeying to other planets seems unbelievably cool. I've read books about the planets in our solar system and learned their names - Mercury, Venus, Earth, Mars, Jupiter, Saturn, Uranus, and Neptune. The astronauts who traveled to the moon were true heroes and pioneers. I dream of one day walking on Mars or even farther out in the galaxy!There is still so much we have yet to discover about the depths of space. Scientists aren't even sure if there is other intelligent life elsewhere in the universe. I'd love to be part of a team that makes groundbreaking discoveries about extraterrestrial civilizations or strange new realms. Maybe I could be the first person to set foot on an alien world! How amazing would that be?Another field I find endlessly intriguing is the study of animals. The diversity of wildlife on our planet is justmind-blowing. From the graceful lions prowling the African savannah to the tiny, colorful fish darting around coral reefs, the animal kingdom is overflowing with curiously adapted creatures. As a zoologist, I could get up close and personal with some of nature's most magnificent beasts.Can you imagine tracking a family of wild elephants through dense jungles? Or diving deep into the ocean blue to swim alongside dolphins and whales? Getting to observe animals in their natural habitats would be a dream come true for me. I'd relish the chance to learn about their behaviors, traits, and roles within the environment first-hand.I'm also captivated by the idea of studying strange, new species that haven't even been discovered yet. All over the planet's rainforests, deserts, mountains, and other remote regions, there are probably plants and animals still unknown to science just waiting to be found and examined. How cool would it be if I got to be the first scientist to document an entirely new life form? I could get to pick its scientific name and everything!Of course, I'm pretty interested in understanding the human body and ways to keep people healthy too. By unlocking the mysteries of anatomy, biology, and medicine, scientist doctors have figured out how to treat awful diseases and developed amazing surgical techniques that save countless lives. It would be incredibly rewarding to dedicate my career towards improving people's well-being.Maybe I could invent a new cure for a terrible sickness like cancer or dementia that impacts millions around the world. Ormaybe I'll develop an innovative technology like artificial organs or bionic body parts that allow people with disabilities to overcome their physical challenges. Becoming a medical researcher would let me work on overcoming the biggest threats to human health and push the boundaries of what modern science can accomplish.No matter which specific branch of science I ultimately pursue, I know the life of a scientist would be a non-stop, fascinating adventure filled with epic discoveries andmind-blowing revelations. At the same time, I recognize that studying science takes a ton of hard work, patience, and commitment.I'll need to do really well in all my school subjects, especially the STEM fields like math, technology, engineering, biology, chemistry, and physics. Becoming an expert in the sciences requires years and years of difficult training and education. But I don't mind the hard work because I know it will pay off by allowing me to investigate the most thrilling frontiers of human knowledge.I feel like I was born with an insatiable curiosity to learn everything I possibly can about this amazing universe we live in. Whether I'm out exploring nature or studying from books, I'mconstantly asking "Why?" and searching for deeper truths about natural world. The scientist's job of unlocking those truths through research and experimentation is basically my dream career.Every day, there are tantalizing new riddles and puzzles about the cosmos, life on earth, and the rules of reality for scientists to untangle and decipher. I'm determined to keep my mind open and use my talents towards adding to humanity's profound understanding of the world around us. The thrill of suddenly grasping an important new scientific principle or unveiling a groundbreaking discovery would be immensely gratifying.Just imagining all of the wonders that have yet to be uncovered about the mysteries of existence gets me excited to start my eventual career as a scientist. I can't wait to one day trade in my school books and toys for real microscopes, lab coats, and cutting-edge equipment. The quest to expand the boundaries of human knowledge is a lofty but rewarding goal that I'm eager to dedicate my life's work towards.I hope that through my relentless studying, critical thinking, and spirit of intellectual curiosity, I'll be able to make my own important contributions to science. Who knows - maybe I'll evenbecome one of the great scientific minds that changes the world! For now though, I've got to focus on being a good student and learning as much as I possibly can. With hard work and perseverance, I'm confident that no feat of science will be too difficult for me to tackle when I grow up.。
英语动物特征介绍作文Title: Introduction to Animal Characteristics。
Animals are an incredibly diverse group of organisms, exhibiting a wide range of characteristics that allow them to adapt and thrive in various environments. From the soaring eagles to the slithering snakes, each species possesses unique traits that define its behavior, habitat, and ecological role. In this essay, we will explore some of the fascinating features and adaptations found in the animal kingdom.Firstly, let's delve into the realm of mammals. Mammals are distinguished by several key characteristics, including the presence of hair or fur, mammary glands for nursing their young, and a warm-blooded metabolism. These features enable mammals to regulate their body temperature and sustain energy levels, making them well-suited to diverse habitats ranging from icy tundras to scorching deserts. Moreover, mammals exhibit a remarkable diversity in size,from the tiny bumblebee bat to the colossal blue whale, showcasing the breadth of evolutionary innovation withinthis class.Moving on to the avian realm, birds are renowned for their feathers, which serve multiple functions beyondflight. Feathers provide insulation, aid in communication through colorful displays, and facilitate courtship rituals. Additionally, birds possess lightweight bones and efficient respiratory systems, allowing for powered flight—a remarkable adaptation that has enabled birds to colonize virtually every terrestrial habitat on Earth. From the acrobatic maneuvers of hummingbirds to the migratory featsof arctic terns, birds exemplify the wonders of aerial adaptation.Meanwhile, reptiles boast an array of features that set them apart from other vertebrates. One notablecharacteristic is their scaly skin, which helps prevent water loss and provides protection from predators. Reptiles are also ectothermic, relying on external sources of heatto regulate their body temperature. This reliance onenvironmental conditions influences their behavior and activity patterns, with many reptiles basking in the sun to warm their bodies before engaging in activities such as foraging or reproduction. Furthermore, reptiles exhibit diverse reproductive strategies, from egg-laying to live-bearing, reflecting the varied evolutionary pathways within this ancient lineage.In contrast, amphibians straddle the boundary between aquatic and terrestrial environments, displaying a unique set of adaptations suited to both realms. Amphibians typically undergo metamorphosis, transitioning from aquatic larvae to terrestrial adults—a process facilitated by specialized respiratory structures such as gills and lungs. Additionally, many amphibians have permeable skin that allows for gas exchange and water absorption, although this feature also renders them susceptible to environmental pollutants. Despite facing numerous threats, amphibians play vital roles in ecosystems as both predators and prey, contributing to nutrient cycling and maintaining ecological balance.Finally, let's consider the fascinating world of invertebrates, encompassing a vast array of organisms ranging from insects to mollusks. Invertebrates lack a backbone but exhibit astonishing diversity in form, function, and behavior. Insects, the most abundant group of animals on Earth, are characterized by their segmented bodies, compound eyes, and specialized mouthparts adaptedfor feeding on a variety of resources. Meanwhile, mollusks display a remarkable array of body plans, from the streamlined shells of snails to the tentacled appendages of octopuses, underscoring the adaptability and resilience of invertebrate life.In conclusion, the animal kingdom is a tapestry of diversity, with each species contributing its own uniqueset of characteristics to the rich fabric of life on Earth. Whether soaring through the skies, slithering through the undergrowth, or scuttling along the ocean floor, animals exemplify the beauty and complexity of biological evolution. By studying and appreciating the myriad adaptations foundin animals, we gain valuable insights into the processes shaping life on our planet.。
A centrifugal bambara groundnut sheller was designed,constructed and evaluated.The sheller consists of a feed hopper with a flow rate control device,shelling unit,separating unit and power system.Nine different impellers were used for the investigation at three different pod moisture contents.Results of the performance tests were examined using a3x3x3factorial design with moisture content,impeller slot angulations and number of impeller slots as variables.Results showed that moisture content,impeller slot angulations,number of impeller slots and interaction between these variables statistically affected the per-formance indicators(shelling efficiency,percentage of breakage, percentage of partially shelled pods,percentage of unshelled pods and winnowing efficiency)at the significance level of5%.The forward facing impeller with eight slots gave the best performance of96%shelling efficiency,3.4%breakage,0.6%partially shelled pods.No unshelled pods were recorded,and winnowing efficiency of97.3%was recorded at an average feed rate of215.8kg h-1.K e y w o r d s:bambara groundnut,centrifugal impeller,pods, winnowingINTRODUCTIONBambara groundnut(Vigna subterranean L.Verdc)is an indigenous African crop grown across the continent from Senegal to Kenya and from the Sahara to South Africa (Atiku et al.,2004).Bambara groundnut is the third most important grain after groundnut and cowpea(Ezeaku,1994). In separate reports by Ezue(1977)and Atiku(2000)it was noted that in Nigeria bambara groundnut is widely produced in Borno,Anambra,Plateau,Taraba,Sokoto,Bauchi, Benue,Kano,Yobe,Adamawa and Gombe states.Goli(1997)reported that bambara groundnut contains about63%carbohydrate,19%protein,and6.5%oil and is consumed in different forms.Other reports,by Akani et al. (2000),Atiku et al.(2004)and Linnemann(1988),stated that the seed of bambara groundnut can be used for baby food,human consumption,industrial products and for animal feed.Linnemann(1990)reported that bambara groundnut flour has been used in making bread in Zambia, and Brough et al.(1993)noted that the milk prepared from bambara groundnut gave a flavour preferred to that of milks from cowpea,pigeon pea and soybean.According to Atiku (2000)the fresh bambara groundnut seed is cooked before eating.It is used as main food,snacks,relish and medicine, and has a high ceremonial value.Kay(1979)recommended that after harvesting bambara groundnut is dried in the sun to about8to12%moisture content(w.b.).The dried seed could be taken as snacks after roasting or milled to flour for other food.Despite these economic importances,no commercial production and no industrial use of the crop take place in Nigeria.According to Akani et al.(2000)research is con-centrated only on the agronomic aspect,while the proces-sing aspects have been neglected.The pod of bambara groundnut is very hard and the cracking methods are still traditional.These cracking methods vary from locality to locality depending on the quantity produced.Some com-munities use mortar and pestle to crush dry pods.Some beat them with sticks on flat ground,others use stones to crush the pods on flat ground.These methods have the disadvan-tages of damaging the seeds,and are slow and tiresome.Atiku et al.(2004)evaluated the performance of a bam-bara groundnut sheller working on the principle of rollers and pneumatically separating the shells from the seeds. They got the maximum shelling and winnowing efficiencies of80and79.5%,respectively,at pod moisture content of5% (w.b.)and feed rate of93.6kg h-1.The percentage of dama-ged seed was about20%,the percentage of partially shelled (broken and unbroken seeds)and percentage of unshelled pods were10and7%,respectively,while the machine loss accounted for3%.Int.Agrophysics,2007,21,269-274Development and performance evaluation of impact bambara groundnut sheller©2007Institute of Agrophysics,Polish Academy of Sciences *Corresponding author’s e-mail:engrfasiu@Adigun and Oje (1993)reported that nuts whose shells/pods cannot be easily broken by the roller cracker are commonly cracked using a centrifugal cracker.Makanjuola (1975)evaluated some centrifugal impaction devices for shelling melon (egusi)seeds (Citrullus vulgaris )and found that a centrifugal impact method is a good technique for shelling melon seeds.He evaluated three types of impellers (A,B and C)with four slots,eight slots,and two parallel plates,respectively.He concluded that impeller type A was the most effective of all the three types tested.Odigboh (1979)developed and tested a prototype impact melon (Citrullus vulgaris )shelling machine that gave about 96%shelling efficiency and 100%winnowing efficiency.He also evaluated three types of impellers at different vane angulations with four vanes each.Impeller type A had radially positioned vanes,type B vanes positioned at 45°to the radius,while type C vanes at 90°to the radius of the circle.He concluded that impeller type B gave the best combination of higher shelling and low percentage of damage.Oluwole et al .(2004)developed and tested a sheanut cracker working on the principle of impaction and pneuma-tically separating the shells from the kernel.They got crack-ing efficiency of 100%and winnowing efficiency of 97%.They evaluated three types of impeller,similar to those of Odigboh (1979)but with slight differences in the vanes angulations.Impeller type A had radially positioned vanes;type B and type C had their vanes positioned at 45and 30°to the radius respectively.They concluded that the radially positioned vanes impeller gave 100%effective cracking efficiency.Akani et al .(2000)determined the optimum impact energy for shelling bambara groundnut at pod moisture content range of 5-8%(w.b.)and found that the impact energy ranged from 0.24to 0.59J.DESCRIPTION OF THE IMPACT SHELLERThe machine,similar in principle to Odigboh’s impact melon (Citrullus vulgaris )sheller (Fig.1),consists of a feed hopper,pod shelling unit separation unit and power unit.Figure 2shows the assembly details of the machine.The conical shaped hopper is mounted on the tool frame and is held in place by a hopper support frame.The base is connected directly to the shelling unit.A nut flow control device is located between the hopper and the shelling chamber.The shelling unit consists of a 410mm diameter by 150mm height cylindrical shell made from 5mm steel sheet,whose inner surface serves as the cracking surface,and an impeller of 370mm diameter made of 25by 50mmrectangular steel pipe similar to that described by Dicken (1961)as shown in Fig.3.These impellers were divided into three groups:A –impeller slots positioned at 45°to the tangent at the slots outlet (forward facing)represented with subscript F;B –radially positioned impeller slots (at 90°to tangent at the slots outlet)repre-sented with subscript R;and C –impeller slots positioned at 135°to the tangent at the slots outle (backward facing)represented with subscript B.270 F.A.OLUWOLE et al.Fig.1.Bambara groundnutsheller.Fig.2.Centrifugal impaction device:1–hopper,2–hopper sup-port frame,3–cracking chamber,4–impeller,5–transition chan-nel,6–shaft,7–pulley,8–bearing,9–belt,10–frame,11–seed collection chute,12–electric motor,13–chaff-outlet,14–inner funnel,15–separation compartment,16–axial fan.Each group has impellers with eight,four and two slots.The cylindrical shell is covered with a transparent plastic cover 400mm diameter of 4mm thickness with a concentric open-ing (80mm diameter)at the center (pods inlet).The impeller is concentrically positioned within the cylindrical shell and horizontally mounted on a vertical shaft to give a clearance that is greater than the size of the seed with cracking surface.Figure 4shows the impeller mounted in operational position.This impeller is driven by a vertical shaft powered by a 0.5hPa 1920r.p.m.electric motor through a system of belt and pulley.The separation unit comprises the transition channel (through which the mixture of seed and broken pods from the shelling chamber flows into the separation compartment),the separating chamber (where the seed and pods are separated by air current),the inner funnel shapped wire mesh for seeds collection,and the axial fan mounted directly on the electric motor,which is powered by the elec-tric motor to supply the air stream required for winnowing.At the upper part of the separating unit is the shells outlet.Inbetween the separating compartment and the shells outlet is a transparent cylindrical plastic column to observe the shells upward movement.These components are assembled and mounted on a rectangular tool frame that gives the machine a compact design and a sturdy outlook.PRINCIPLE OF OPERATIONTo operate the device,the nut flow control device is closed completely.The hopper is then filled with a known number and mass of nuts.The main switch is then switched on to actuate the electric motor which runs the impeller in the cracking chamber.As the impeller reaches its operating speed,the nut flow control device is opened to allow nuts to flow into the impeller eye.The incoming nuts slide and roll on the inner surface of the rectangular pipe,the centrifugal force developed as a result of the rotation of impeller throws the nuts against the cracking surface and causes the nuts to crack.The seeds and the shelled pods flow down through the clearance between the impeller and the cylindrical shell and fall on an inclined transition channel that leads to the separating compartment.Here the shells,which are lower in density than the seeds,are lifted up by the air stream from the axial fan and blown out through the shells outlet.The denser seeds fall through the air stream into the inner wire mesh funnel to the seed collection chute.Figure 4shows the impeller mounted in the operational position.PERFORMANCE TESTSTo carry out the performance tests,nine types of impellers were evaluated.Each of these impellers was used to shell bambara groundnut at three different moisture levels in the range of 5.3-12.2%(d.b.).Some quantity of bambara groundnut pods (N T )were randomly selected and weighed.These pods were poured into the hopper while the pods flow control was completely closed.The main control switch was switched on;as the impeller attained the operating speed,the pod flow control was opened to allow the pods to flow intoDEVELOPMENT AND PERFORMANCE EVALUATION OF IMPACT BAMBARA GROUNDNUT SHELLER 271Fig.3.Groups of impellers:A,B,andC.ACB8slots 4slots 2slotsFig.4.Impeller mounted in the operational position.the eye of the impeller at an average feed rate of215.8kg h-1. These pods were carefully collected after going through the impeller,and the number of pods fully shelled without broken seeds(N1),number of pods fully shelled with broken seeds(N2),number of pods partially shelled(N3)and number of unshelled pods(N4)were determined at the end of each run.The quantities of shells winnowed out(M SW)and of those collected with the seeds(M UW)were determined and recorded.Each of these tests was replicated five times at each of the moisture level and for each of the evaluated impellers. The performance was evaluated on the basis of the following indices(Oluwole et al,2007b):shelling efficiency,h S TN N=(/)1100,(1) percentage of broken seeds,h b TN N=(/)2100,(2) percentage of partially shelled pods,h p TN N=(/)3100,(3) percentage of unshelled pods,h u TN N=(/)4100,(4) winnowing efficiency,h w SW TSM M=(/)100,(5) where:N T–number of pods fed into the impeller:M TS=M SW+M UW.These results were statistically analysed using factorial design.RESULTS AND DISCUSSIONTables1and2show the results of the performance tests analyses.Table1shows that moisture content(M),number of impeller slots(f)and impeller slot angulations(S)signi-ficantly affect the shelling efficiency(h S),percentage of broken seeds(h b),percentage of partially shelled pods(h p), percentage of unshelled pods(h u)and winnowing effi-ciency(h w)at the significance level of5%.The interaction between moisture content and number of impeller slots(M x f) has a significant effect on the shelling efficiency and the per-centage of partially shelled pods at the significance level of 5%,while the interaction between moisture content and im-peller slots angulations(M x S)significantly affects the shel-ling efficiency,the percentage of partially shelled pods and the winnowing efficiency at the significance level of5%.Table2shows that the forward facing impeller con-sistently gave the best performance.Similar findings were reported by Oluwole et al.(2004)and Oluwole et al.(2007a) in performance evaluation of a sheanut cracker and effect of moisture content on crackability of bambara groundnut using a centrifugal cracker,respectively.Table2also reveals that the impellers with eight slots consistently gave the best performance.Similar findings were reported by Oluwole et al.(2007b)in an evaluation of some centrifugal impaction devices for shelling bambara groundnut.At all the moisture contents employed and for each of the impeller groups the shelling efficiency,percentage of broken seeds and the winnowing efficiency increased with increase in number of impeller slots,while the percentage of partially shelled pods and the percentage of unshelled pods decreased with increase in the number of impeller slots.This is because the higher the number of impeller slots the higher the number of pods that will emerge from the impeller and272 F.A.OLUWOLE et al.hit the cracking surface.。
Supercomputers: The Backbone of ModernComputingIn the rapidly evolving world of technology, supercomputers stand as the epitome of human ingenuity and technological advancement. These machines, with their incredible processing speeds and immense computational powers, have revolutionized various fields, including science, medicine, engineering, and even entertainment.Supercomputers are defined by their ability to perform billions of calculations per second, making them the fastest and most powerful computers in the world. They are equipped with the latest processors, large memory capacities, and state-of-the-art cooling systems to handle the immense heat generated during intense computing sessions.The importance of supercomputers cannot be overstated. In the field of science, they have enabled researchers to model complex systems, simulate natural phenomena, and analyze vast amounts of data. In medicine, supercomputers have aided in the development of new drugs and treatments, as well as in the advancement of diagnostic techniques. Inengineering, they have facilitated the design of complex structures and systems, ensuring their safety and efficiency. Even in entertainment, supercomputers have played a crucial role in creating realistic graphics and animations for movies, games, and other visual media.Despite their incredible capabilities, supercomputers are not without their challenges. The cost of building and maintaining these machines is astronomical, making them accessible only to a select few institutions and organizations. Additionally, the energy consumption of supercomputers is immense, posing a significant challenge to sustainable computing.However, despite these challenges, the future of supercomputers looks bright. With the advent of new technologies like quantum computing and the continuous improvement of hardware and software, we can expect supercomputers to become even more powerful and efficient in the coming years.In conclusion, supercomputers are a crucial component of modern computing, playing a pivotal role in various fields. Their capabilities and potential are limitless, andas technology continues to evolve, we can expect them to make even greater contributions to human progress and development.**超级计算机:现代计算的支柱**在科技飞速发展的世界中,超级计算机是人类智慧和科技进步的典范。
Elon Musk and others urge AI pause, citing 'risks to society' 马斯克等人联名呼吁暂停推出更强大的AI系统英文新闻:Elon Musk and others urge AI pause, citing 'risks to society' Elon Musk and a group of artificial intelligence experts and industry executives are calling for a six-month pause in developing systems more powerful than OpenAI's newly launched GPT-4, in an open letter citing potential risks to society."Powerful AI systems should be developed only once we are confident that their effects will be positive and their risks will be manageable," said the letter issued by the Future of Life Institute.AI systems with human-competitive intelligence can pose profound risks to society and humanity, as shown by extensive research and acknowledged by top AI labs.It said ChatGPT's ability to churn out authentic sounding text at speed and scale also makes it an ideal tool for propaganda and disinformation. "It allows users to generate and spread messages reflecting a specific narrative with relatively little effort."中文新闻:马斯克等人联名呼吁暂停推出更强大的AI系统马斯克和人工智能专家以及行业高管在一封公开信中呼吁暂停开发比OpenAI新推出的GPT-4更强大的人工智能系统,至少暂停6个月,并指出对社会存在潜在风险。
Data sheetHP USB Keyboard(QY776AA)The new HP USB Keyboard features an impressivelydurable design built for ease of use and everyday businesscomputingBuilt for durabilityLifecycle are up to 20 million keystrokes for heavy usage.Minimize damage from minor spills with the integrated spill-drain feature.Easy to connectGet fast data entry and quick USB connectivity for use with multiple operation systems.Sign up for updates/go/getupdatedRate this documentShare with colleagues Data sheet | HP USB Keyboard© Copyright © 2020 HP Development Company, L.P. The information contained herein is subject to change without notice. The only warranties for HP products are set forth in the express limited warranty statements accompanying such products. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.Part numberQY776AA Dimensions18.12 x 6.47 x 1.09 in (46.02 x 16.43 x 2.78 cm)Weight1.98 lb (0.9 kg)Keys104, 105, 106, 107, 109 layout (depending upon country)Operating voltage4.40 ~5.25 VAC Power consumption100 mA Max with 3 LEDs on InterfaceUSB Switch life20 million keystrokes Switch typeContamination-resistant switch membrane Operating temperature0°C to 40°C Non-operating temperature-40°C to 65°C Operating humidity20% to 80%Non-operating humidity10% to 90%System requiredWindows Vista, Windows 7, Windows 8, Windows 8.1, Windows 10, Available USB port Approvals FCCCEVCCITUV GScULICES-003 Class BBSMIKCCc-TickErgonomic compliance ISO-321 and TUV GSKit contentsKeyboard, Installation Guide, Warranty Card, Safety and Comfort Guide.HP USB Keyboard4AA7-6750ENW, January 2020Specifications。
a rXiv:as tr o-ph/41253v113Jan24Are Supershells Powered by Multiple Supernovae?Modeling the Radio Pulsar Population Produced by OB Associations Rosalba Perna 1,2and Bryan M.Gaensler 31.Department of Astrophysical Sciences,Princeton University,Princeton,NJ,085443.Harvard-Smithsonian Center for Astrophysics,60Garden Street,Cambridge,MA 02138ABSTRACT Traditional searches for radio pulsars have targeted individual small regions such as supernova remnants or globular clusters,or have covered large contiguous regions of the sky.None of these searches has been specifically directed towards giant supershells,some of which are likely to have been produced by multiple supernova (SN)explosions from an OB association.Here we perform a Monte-carlo simulation of the pulsar population associated with supershells powered by multiple SNe.We predict that several tens of radio pulsars could be detected with current instruments associated with the largest Galactic supershells (with kinetic energies 1053ergs),and a few pulsars with the smaller ones.We test these predictions for some of the supershells which lie in regions covered by past pulsar surveys.For the smaller supershells,our results are consistent with the few detected pulsars per bubble.For the giant supershell GSH 242–03+37,we find the multiple SN hypothesis inconsistent with current data at the ∼95%level.We stress the importance of undertaking deep pulsar surveys in correlation with supershells.Failure to detect any pulsar enhancement in the largest of them would put serious constraints on the multiple SN origin for them.Conversely,the discovery of the pulsar population associated with a supershell would allow a different/independent approach to the study of pulsar properties.Subject headings:Galaxy:structure —ISM:bubbles —pulsars:general —supernovae:general1.IntroductionSurveys for radio pulsars form the foundation for the considerable contribution which studies of neutron stars(NS)have made to astrophysics.Not only have such surveys identi-fied a variety of unique or unusual pulsars,but the large samples of objects thus accumulated have provided vital information on the velocity distribution,luminosity function,beaming fraction and magneticfield evolution of rotation powered NS(e.g.Ostriker&Gunn1969; Narayan&Ostriker1990;Lorimer et al.1993).Surveys for pulsars have usually either targeted specific regions such as supernova rem-nants,globular clusters,unidentified gamma-ray sources or steep-spectrum radio sources (e.g.Biggs&Lyne1996;Lorimer,Lyne&Camilo1998),or have carried out unbiased,but usually shallower,surveys over large regions of the sky(e.g.Manchester et al.1996,2001). The former set of surveys are aimed at discovering particulary interesting pulsars but cover only a small fraction of the sky;the latter usuallyfind large number of pulsars,and al-low statistical studies of pulsar birth parameters to be performed.However,these studies generally require apriori assumptions regarding the pulsar birth rate and the initial spatial distribution of pulsars in the Galaxy.In this paper,we perform thefirst study(to the best of our knowledge)of pulsars correlated to supershells in our Galaxy.Expanding giant H i supershells(see e.g.Tenorio-Tagle&Bodenheimer1988for a review)have been observed for several decades in21cm surveys of spiral galaxies.These nearly spherical structures have very low density in their interiors and high H i density at their boundaries,and expand at velocities of several tens of km s−1.Their radii are much larger than those of ordinary supernova remnants,often exceeding∼1kpc;their ages are typically in the range of106to a few×107years.The Milky Way contains several tens of them(Heiles1979,1984;McClure-Griffiths et al.2002), and in one case the estimated kinetic energy of expansion is as high as∼1054ergs(Heiles 1979).Similar supershells are also observed in other nearby galaxies(Rand&van der Hulst 1993;Kim et al.1999).Whereas it is clear that these H i supershells result from deposition of an enormous amount of energy into the interstellar medium,the energy source is still a subject of debate. Collisions with high-velocity clouds(Tenorio-Tagle1981)could account for those cases where only one hemisphere is present,and where the required input energy is not too large.How-ever,it is unclear how such collisions could produce the near-complete ringlike appearance observed in some cases(Rand&van der Hulst1993).Loeb&Perna(1998)and Efremov et al.(1998)suggested that Gamma-Ray Bursts might be responsible for powering the largest supershells.Whereas it is likely that a fraction of the smaller Galactic shells is indeed pow-ered by GRBs given estimates of their rates(e.g.Schmidt1999;Perna,Sari&Frail2003),however GRBs might not be able to power the largest supershells if they are beamed(and therefore their energies reduced compared to their isotropic values∼1053−1054ergs).The most discussed interpretation in the literature is that supershells are a consequence of the collective action of stellar winds and supernova(SN)explosions originating from OB star associations(e.g.McCray&Kafatos1987;Shull&Saken1995).Several hundreds of stars exploding within a relatively short time are necessary to power the most energetic supershells.The motivation for simulating and studying the population of pulsars associated with supershells is therefore twofold:first,it would provide an independent test of the multiple SN origin for them;second,if the pulsar population associated with a supershell is indeed identified,it would possibly provide an independent way to constrain pulsar birth param-eters.This is because both the birth rate and the birth location of the pulsars would be independently constrained rather than assumed a priori.The paper is organized as follows:§2.1discusses the model for the superbubble growth and the corresponding pulsar birth rates;the distributions of the pulsar characteristics and the Montecarlo simulation of the observable population are discussed in§2.2.In§3,the results of our simulations are compared to the data for the supershells which lie in regions of sky covered by past,sensitive pulsar surveys,and predictions are made for some of the other supershells for which current data are not sufficient to make a comparison at this time.Our work isfinally summarized in§4.2.Simulating a population of pulsars from an OB association2.1.OB associations and supershell growthThe evolution of a superbubble powered by a continuous energy source4has been cal-culated by Weaver et al.(1977;see also MacLow&McCray1988;Shull&Saken1995). Weaver et al.derived a similarity solution in terms of the equivalent mechanical luminosity of supernovae,L SN,ambient densityρ0and time t.This yields the time-evolution of thesuperbubble radiusR= 125n0 1/5,(1) and velocityV≈(15.7kms−1)L1/538n−1/50t−2/57.(2)Here n0is the atomic number density(in cm−3),t7=t/(107yr)and L38=L SN/(1038ergs s−1) is the equivalent of one SN of energy E SN=1051ergs occurring every∆t SN=E SN/L38= 3.2×105yr.5For a given superbubble,from the observed values of R,v and n0,we derive the corresponding age t7and the equivalent mechanical luminosity L SN.The number N SN of stars that become supernovae(SN)over the time scale t is given by N SN=L SN t/E SN. Although stellar winds from the OB association will produce a hot bubble before thefirst SN goes off,these winds are not important compared to SNe for the later dynamics of the supershell(McCray&Kafatos1987;Mac Low&McCray1988).Also,while the early times of the bubble evolution are sensitive to the details of the rate of energy injection(which is assumed constant in the Weaver et al.model),the late phase of the bubble is not6(Shull& Saken1995).We should point out that the factor N SN estimated using the equations above is typically a factor of a few smaller than the equivalent number estimated using the energy E E=5.3×1043n1.12R3.12V1.4ergs which would be required to produce the shell by a sudden explosion(Chevalier1974).The latter,larger,number has been the one often used in the literature to estimate superbubble energies(Heiles1979;Rhode et al.1999;McClure-Griffith et al.2002).The initial mass function for massive stars can be written as(Garmany,Conti&Chiosi 1982)f IMF(M∗)≡dN∗/dM∗∝M−β∗,(3) whereβ∼2.6.We assume M min=3M⊙and M max=140M⊙for the minimum and maximum mass of the distribution,respectively.The main-sequence lifetimes of massive stars are given approximately by(Stothers1972; Chiosi,Nasi&Sreenivasan1978)t∗∼ 3×107(M∗/10M⊙)−1.6yr if7 M∗ 30M⊙9×106(M∗/10M⊙)−0.5yr if M∗ 30M⊙.(4)The least massive star that is expected to terminate as a Type II SN has initial mass M min,SN=7M⊙(Trimble1982).We take M max∼140M⊙as the mass of the most massive star of the association.Our results are rather insensitive to the precise value of the minimum star mass,M min,in the distribution,as stars with M<M min,SN would not contribute to the energetics of the shell.Similarly,our results are also rather insensitive to the precise value of the upper mass cutoffdue to both the steep decline in dN∗/dM∗at large M∗,as well as to the fact that low metallicity stars with mass in the range40−140M⊙collapse directly to a black hole(BH)without any significant explosion energy7(Heger et al.2003). The maximum mass of the star that will leave behind a NS is rather uncertain.However, estimates of rates of heavy element production require stars as massive as25M⊙to form supernovae(e.g.,Hillebrandt1982).Numerical simulations(e.g.,Heger et al.2003)find that for low-metallicity,non-rotating isolated stars,M=25M⊙is the maximum initial star mass that would leave behind a NS star remnant,while stars in the range25−40M⊙form a BH by fallback while releasing a small amount of energy into the medium.Following these results,here we assume that only stars in the range7−25M⊙leave behind a NS,while those with M>M SN,max=25M⊙(but M<40M⊙)contribute to power the supershell, but do not leave behind a pulsar.For stars with mass below7M⊙we assume that their energy contribution is negligible compared to that of the SNe.Note that,if stars had solar metallicity,they would be expected to form NS remnants for a much larger range of initial masses(Heger et al.2003),and therefore there would be many more pulsars than what we predict here8.Finally,we consider a model of an OB association with coeval star formation; that is all stars are assumed to be formed at once with no age spread.Once again,note that this is a conservative assumption for our predictions,because if stars were formed with an age spread,the pulsars in the bubble would be generally younger than in the coeval case, and hence would be more likely to be detectable(as younger pulsars have typically larger luminosities and beaming fractions).Also,they would have had less time to travel far from their birthplaces,and therefore a larger fraction of them would be closer to the supershell at the present time.2.2.Properties of the pulsar populationModelling the intrinsic properties of the Galactic population of pulsars,especially with respect to the luminosity function and initial spin period,has been the subject of extensive investigation in the past few decades(e.g.Gunn&Ostriker1970;Vivekanand&Narayan 1981;Phinney&Blandford1981;Narayan&Ostriker1990;Lyne et al.1985;Narayan1987; Stollman1987;Emmering&Chevalier1989;Lorimer et al.1993;Johnston1994;Cordes &Chernoff1998).Despite all these efforts,no consensus has been reached on what the intrinsic and birth properties of the pulsars are.The most recent,comprehensive analysis, based on large-scale0.4GHz pulsar surveys,has been made by Arzoumanian,Cordes& Chernoff(2002;ACC in the following).Here,as afirst step in estimating the expected number of pulsars for a supershell of given age and energy,we use their inferred parameters under the assumption that spin-down is only caused by dipole radiation losses.Theyfind that pulsars are likely to be born with velocities distributed according to a two-component gaussian distribution,with40%of them having a characteristic speed(i.e.magnitude of the3-D velocity)of90km s−1and the remaining of500km s−1.The initial birth period distribution(taken as a gaussian in log),has a mean log P0(s) =−2.3with a spread greater than0.29,while the initial magneticfield strength(also a log-gaussian),is found to have a mean log B0[G] =12.35and a variance of0.4.These distributions of initial parameters have been derived under the assumption of no magneticfield decay.The spin evolution of the pulsars is then simply given by:P(t)= P20+ 16π2R6B29Here we adopt the value0.3,after verifying that variations in the range0.3-0.6do not give statistically different results.spread in luminosity by considering a log-gaussian probability distribution with mean L given by Equation(6)and spreadσL.As pointed out by ACC,this is a way to parameterize the fact that the pulsar luminosity has an angle dependence with respect to the magnetic axis,and the particular value that is observed by a given observer depends on its orientation with respect to that axis.Wefind that,with a mean given by Equation(6),a spread∼0.8 (in the log)appears to give results consistent with the current data.For the evolution of the beaming fraction f with period we adopt the relation derived by Tauris&Manchester(1998)f=0.09 log P2 tanh ˙P315/P3−10DL /σDL +1 ,(8)where˙P15≡˙P/(10−15s s−1).DL=0.5andσDL=1.4represent the position and lateral extent of the death band,respectively.For the pulsar velocity distribution at birth,we adopt the double-gaussian model of ACC described above.The orientation of the pulsar kick at birth is assumed to be random, and the Galactic rotational velocity(220km s−1)is added vectorially to the initial kick velocity.Finally,we compute the detector sensitivity using the standard detector equation(e.g. Dewey et al.1984):S lim=σβ(T sys+T sky)BN pτobsWis the dispersion smearing across one frequency channel,andτscatt is the broadening of the pulse due to interstellar scattering.The dispersion measure and scattering measure of each pulsar(needed to calculate the above quantities)are computed using the public code10by Cordes&Lazio(2003),while the all-sky data are from the408MHz compilation of Haslam et al(1982),scaled to other frequencies assuming a spectral index of–2.6for the brightness temperature of the diffuse Galactic synchrotron background.We neglect the effects of cut-offs in harmonic summing andfiltering of the data(see e.g.Manchester et al.2001),which has a small effect on the sensitivity for periods which are not very short and for large DMs(F.Crawford2003,private communication).3.Simulating a survey of pulsars in a supershellThe simulation of the pulsar population produced by the OB association that gave rise to a supershell is of the Montecarlo-type.First,the mass of a star is generated from the distribution in Equation(3);only stars whose lifetime is shorter than the present age of the supershell,t shell,are followed.The birthtime t birth of a given pulsar is taken as the time that the progenitor star explodes.For each pulsar,the birth properties(Bfield,initial velocity, initial period)are computed according to the ACC distribution described above.The period of each pulsar is then evolved for a time t puls=t shell−t birth according to Equation(5);if the pulsar is still above the death band,a luminosity is assigned(based on the probability distribution described in§3).To determine whether the pulsar is beamed towards our line of sight,a random number x in the interval{0,1}is generated.If x≤f(defined in Eq:(7), then the pulsar is considered beamed towards us.The birth place of the pulsars is assumed to coincide with the center of the supershell;however,because of the relative motion of the supershell with respect to the sun(due to Galactic differential rotation),the coordinates of the supershell on the sky are a function of time.We account for this effect for a pulsar of age t puls by extrapolating backwards by a time t puls to determine the coordinates of the supershell on the sky(and hence of the pulsar birth place)at that specific time in the past.Thefinal position of the pulsar(i.e.,at its current age)is determined by integrating its equations of motion in the Galactic potential(Kuijken&Gilmore1989)for a time t puls.Finally,the flux of each pulsar is compared to the detector threshold after computing the dispersion and scattering measure for its position.The simulation is stopped when the number of supernovae reaches what is needed to power the supershell.Galactic shells and supershells have been studied for several decades since the pioneeringwork of Heiles(1979,1984).Pulsar surveys,on the other hand,have never been specifically directed at sampling supershell regions at high sensitivity.Therefore,for the purpose of our analysis in this paper,we use the results of existing surveys,while emphasizing the importance of future,deeper surveys of the supershell regions.A Montecarlo realization of the1.4-GHz pulsar population expected to be associated with the two Galactic supershells GSH242–03+37and GSH088+02–103(which are among the biggest in the Galaxy)is shown in Figure1and2.In both cases,the left panel shows the expected luminosity versus age distribution of pulsars beamed towards us(independently of whether still inside the shell or not).The oldest pulsars have an age comparable to the age of the supershell.The right panel shows the current position on the sky of the pulsars with respect to that of the supershell.Note that some of the pulsars have moved very far from the supershell and therefore they do not appear in the right panels of thefigures(which shows the region in the sky around the supershell).Our simulations show that there is a significant probability offinding an enhancement of pulsars in the innermost regions of the bubble.These pulsars are a combination of the youngest sources in the sample,those on the low-velocity tail of the distribution,and those whose velocity vector happens to be almost parallel to the line of sight.The region where GSH088+02–103lies has been searched in the Green Bank survey at370MHz(Sayer,Nice&Taylor1997),while GSH242–03+37has been searched at436MHz by the Parkes Southern Pulsar survey(Manchester et al.1996),and also had a few pointings at1.4GHz in the Parkes Multibeam Pulsar survey(Manchester et al.2001;A.J.Faulkner,2003,private communication).The predicted number of detected pulsars for the survey parameters corresponding to the region around each supershell are listed in Table1.In Figures1and2,as an example,we show the pulsars which would be visible with survey parameters corresponding to those of the current Parkes Multibeam Pulsar survey(filled symbols),as well as those which could not be detected by Parkes but would be visible to the planned Square Kilometer Array(SKA),which will have a sensitivity of about1.4µJy for one minute of integration time(Kramer2003).For a quantitative comparison with current data,we selected the most energetic super-shells among those at low Galactic latitude(Heiles1979;McClure-Griffiths et al.2002), where most of the pulsar surveys have been focused.Our results are summarized in Table1. For each supershell,we ran1000Montecarlo realizations of the pulsar population associated with it,and determined the mean and variance of the distribution for the number of pulsars that are expected to be found within the supershell region on the sky at the current time. To be more specific,if l0,b0are the Galactic coordinates of the supershell,and∆l and∆b its total extent(i.e.diameter)on the sky,then the pulsars associated with the supershells are those whose coordinates l,b satisfy the condition|l−l0|<∆l/2and|b−b0|<∆b/2,and are within a distance D±R,where D is the distance to the shell and R its mean radius.Theseare only a fraction of the ones produced within the association and potentially observable,as shown in Fig.1and2.For each supershell,we computed the distribution of pulsars whose flux is above the threshold of the deepest survey which has covered that particular region of sky in which the shell lies,as well as the distribution of pulsars which would be detectable with SKA.The pulsars in the current catalogue11which are candidate associations are also reported.These are selected on the basis of their coordinates l,b which have to satisfy the condition|l−l0|<∆l/2and|b−b0|<∆b/2,as well as on their distance,which has to be within D±R.However,both the pulsars and the shell distances are known with some uncertainty.For pulsars,the distance as inferred from dispersion measure has some25% uncertainty on a statistical average12(see e.g.Cordes&Lazio2003),while the errors on the supershell distances are specifically indicated in the McClure-Griffiths et al.sample,and most of them are in the range10-20%.Unfortunately no distance errors are provided in the Heiles(1979)sample,and for those we assume a more conservative25%uncertainty.We then consider a pulsar a possible association with the supershell if it falls within D±R after accounting for the distance uncertainties in both the pulsar and the supershell.As Table1shows,in a few cases,due to a combination of the large distances of the su-pershells and the comparatively poor sensitivity level at which the corresponding region was surveyed,no pulsars are expected to have been detected in association with the supershell, and therefore no meaningful constraints can be derived.For the two supershells which lie in the region covered by the Parkes Multibeam survey(GSH285–02+86and GSH292–01+55; McClure-Griffiths et al.2002),the predictions of the multiple SN scenario at the detection level of that survey are consistent with the number of candidate associations,although they do not rule out other interpretations,such as GRBs or collisions with high-velocity clouds, as in both these scenarios one would not expect any pulsar enhancement correlated with the supershell.Deeper surveys of those regions are needed to test the multiple SN scenario. However,an interesting constraint can already be derived for GSH242–03+37(Heiles1979). Our results(see Table1)show that there is a95%probability that the supershell was not the result of multiple SNe.Deeper surveys are necessary to set much tighter constraints. Our current results,in fact,are rather dependent on the luminosity function(Lorimer et al. 1993)that we have adopted here;however,recent new discoveries of low-luminosity radio pulsars(Camilo et al.2002a,2002b)might indicate that young pulsars might be fainter than previously realized,and this could be an alternate explanation for the lack of pulsars in the supershell at the current sensitivity threshold.However,when the sensitivity is sufficientlyhigh that even the faintest pulsars can be detected(as it will be with the planned SKA instrument),then the particular details of the luminosity function will be irrelevant for the proposed experiment.Also note that,while current pulsar surveys are able to probe mostly the pulsars within our Galaxy,the SKA survey will be able to detect a large fraction of pulsars also in the LMC,which has several giant supershells(Kim et al.1999).The analysis that we are proposing here can therefore be made also for the LMC supershells in the SKA era.Before concluding we should note that,besides depending on the total energetics13of the supershells(which determine the total number of SN explosions needed),our results also rely on the pulsar birth parameters,and in particular on their velocity distribution,magnetic field,and periods.Here we have adopted the ACC results for the case with braking index n=3,which corresponds to pure dipole losses.In reality,braking indices are often found to be different than3(e.g.Lyne et al.1996),possibly due to a variety of causes(e.g. Menou et al.2001and references therein),and this affects the pulsar evolution.ACC determined the initial birth parameters also for the case n=4.5,and found that they were not significantly different.In particular,the velocity distributions for the two cases are consistent within the error bars.Given that both sets of initial parameters are determined so that they yield the same pulsar distribution today,different initial conditions should not affect much our predictions for the observability of pulsars in the bubbles today.At any event,future population studies resulting from the analysis of the Parkes Multibeam Survey will be very important for further constraining the underlying pulsar distributions(Lorimer 2003;Vranesenic et al.2003)and,as a matter of fact,the study of the pulsar population associated with the largest supershells can be potentially used as an independent way to constrain pulsar birth parameters.Finally,we note that,if the giant supershells are indeed powered by multiple SN explo-sions,then besides the several tens of NS visible as radio pulsars,there should be hundreds of other NSs(all the pulsars not beamed towards us and all the ones that have passed the death line),plus a smaller number of BHs,in the region delimited by the superbubble.The only hope to possibly detect such large concentrations of compact objects would be through accretion from the interstellar medium on a Bondi-type mode(see Blaes&Madau1993 for NSs and Agol&Kamionkowski2002for BHs).However,current limits for detection of isolated,accreting NSs,may suggest that accretion occurs at a rate which is likely wellbelow the Bondi value(Perna et al.2003;Toropina et al.2003),and therefore this large concentration of isolated NSs and BHs in supershells might have to await more sensitive X-ray instruments to be possibly detected in X-rays.4.SummaryPulsar searches so far have mostly focused either on specifc regions such as supernova remnants and globular clusters or on a large contiguous region of sky.In this paper we have, for thefirst time,simulated the pulsar population that should be associated with the giant supershells observed in our Galaxy and in nearby galaxies,if their interpretation as due to multiple SN explosions is correct.We have found that,for the largest supershells,several tens of pulsars should be present within the supershell region.Failure to detect any pulsar enhancement in the largest superbubbles would put serious constraints on the multiple SN origin for them.Conversely,the discovery of the pulsar population associated with a superbubble would provide new insights into the distribution and birth properties of pulsars.We thank Andy Faulkner and Froney Crawford for information on the Parkes Multibeam Pulsar Survey,and Mordecai-Mark MacLow for a very useful discussion on estimates of supershell energetics.We also thank the referee,Fernando Camilo,for a careful reading of our manuscript and helpful comments.REFERENCESAgol,E.&Kamionkowski,M.2002,MNRAS,334,553Arzoumanian,Z,Cordes,J.M.&Chernoff,D.F.2002,ApJ,568,289(ACC)Biggs,J.D.&Lyne,A.G.1996,MNRAS,282,691Blaes,O.&Madau,P.1993,ApJ,403,690Camilo,F.,Manchester,R.N.,Gaensler,B.M.,Lorimer,D.R.2002a,ApJ,579L,25 Camilo,F.,Manchester,R.N.,Gaensler,B.M.;Lorimer,D.R.,Sarkissian,J.2002b,ApJ, 567L,71Chen,K,&Ruderman,M.1993,ApJ,402,564Chevalier,R.A.1974,ApJ,188,501Chiosi,C.,Nasi,E.,&Sreenivasan,S.P.1978,A&A,63,103Cordes,J.M.&Chernoff,D.F.1998,ApJ,505,315Cordes,J.M.&Lazio,T.J.2003,astro-ph/0207156Dewey,R.,Stokes,G.,Segelstein,D.,Taylor,J.,Weisberg,J.1984,in Birth and Evolution of Neutron Stars:Issues Raised by Millisecond Pulsars.Proceedings of the NRAO Workshop,Green Bank,West Virginia,June6-8,1984.Eds S.P.Reynolds and D.R.Stinebring.Green Bank:National Radio Astronomy Observatory,p.234 Efremov,Y.N.,Elmegreen,B.&Hodge,P.W.1998,ApJ,501,L163Emmering,R.T.&Chevalier,R.A.1989,ApJ,345,931Garmany,C.D.,Conti,P.S.,&Chiosi,C.1982,ApJ,263,777Gunn,J.E.&Ostriker,J.P.1970,ApJ,160,979Haslam,C.G.T.,Stoffel,H.,Salter,C.J.,Wilson,W.E.1982,et al,A&A Sup,47,1 Heiles,C.1979,ApJ,229,533Heiles,C.1984,ApJS,55,585Heger,A.,Fryer,C.L.,Woosley,S.E.,Langer,N.,Hartmann,D.H.2003,ApJ,591,288 Johnston,S.1994,MNRAS,268,595Hillebrandt,W.,1982,in“Supernovae:A survey of current research”,eds,M.J.Rees&R.J.Stoneham,(Reidel:Dordrecht),p.123Kim,S.,Dopita,M.A.,Staveley-Smith,L.,Bessell,M.S.1999,AJ,118,2797Kramer,M.2003,in“The Scientific Promise of the Square Kilometre Array”,eds.M.Kramer&S.Rawlings,(Oxford),in press(astro-ph/0306456)Kuijken,K.&Gilmore,G.1989,MNRAS,239,571Loeb,A.&Perna,R.1998,ApJ,503,L35Lorimer,D.R.,Bailes,M.,Dewey,R.J.,Harrison,P.A.1993,MNRAS,263,403 Lorimer,D.R.,Lyne,A.G.,Camilo,F.1998,A&A,331,1002Lorimer,D.R.,astro-ph/0308501,to appear in”Young Neutron Stars and Their Environ-ments”(IAU Symposium218,ASP Conference Proceedings),eds F.Camilo and B.M.GaenslerLyne,A.G.,Manchester,R.N.&Taylor,J.H.1985,MNRAS,213,613Lyne,A.G.,Pritchard,R.S.,Graham-Smith,F.&Camilo,F.1996,Nature,381,497 MacLow,M.&McCray,R.1988,ApJ,324,776。