Anonymous Gossip Improving Multicast Reliability in Mobile Ad-Hoc Networks
- 格式:pdf
- 大小:77.54 KB
- 文档页数:9
![[转载]Gossip算法学习](https://uimg.taocdn.com/3c08ca35cdbff121dd36a32d7375a417866fc1ee.webp)
[转载]Gossip算法学习1. 概述gossip,顾名思义,类似于流⾔传播的概念,是⼀种可以按照⾃⼰的期望,⾃⾏选择与之交换信息的节点的通信⽅式gossip, or anto-entropy, is an attractive way of replicating state that does not have strong consistency requirements2. 算法描述假设有 {p, q, ...} 为协议参与者。
每个参与者都有关于⼀个⾃⼰信息的表。
⽤编程语⾔可以描述为:记 InfoMap = Map<Key, (Value, Version)>,那么每个参与者要维护⼀个 InfoMap 类型的变量 localInfo。
同时每⼀个参与者要知道所有其他参与者的信息, 即要维护⼀个全局的表,即 Map<participant, InfoMap> 类型的变量 globalMap。
每个参与者更新⾃⼰的 localInfo,⽽由Gossip 协议负责将更新的信息同步到整个⽹络上。
每个节点和系统中的某些节点成为 peer (如果系统的规模⽐较⼩,和系统中所有的其他节点成为 peer)。
有三种不同的同步信息的⽅法:1)push-gossip: 最简单的情况下,⼀个节点 p 向 q 发送整个 GlobalMap2)pull-gossip: p 向 q 发送 digest, q 根据 digest 向 p 发送 p 过期的 (key, (value, version)) 列表3)push-pull-gossip:与pull-gossip类似,只是多了⼀步,A再将本地⽐B新的数据推送给B,B更新本地3. 特点gossip不要求节点知道所有其他节点,因此具有去中⼼化的特点,节点之间完全对等,不需要任何的中⼼节点。
gossip算法⼜被称为反熵(Anti-Entropy),熵是物理学上的⼀个概念,代表杂乱⽆章,⽽反熵就是在杂乱⽆章中寻求⼀致,这充分说明了Gossip的特点:在⼀个有界⽹络中,每个节点都随机地与其他节点通信,经过⼀番杂乱⽆章的通信,最终所有节点的状态都会达成⼀致。

⽹络传输协议有哪些注明:以下内容复制于百度知道,本⼈⽤于学习。
TCP/IP,互联⽹传输协议。
以下为各种⽹络传输协议列表(后⾯数字表⽰应⽤层协议默认服务端⼝):AARP (ARP Address Resolution Protocol)BBGP (边缘⽹关协议 Border Gateway Protocol)蓝⽛(Blue Tooth)BOOTP (Bootstrap Protocol)DDHCP( Dynamic Host Configuration Protocol)DNS(域名服务 Domain Name Service)DVMRP (Distance-Vector Multicast Routing Protocol)EEGP (Exterior Gateway Protocol)FFTP (⽂件传输协议 File Transfer Protocol) 21HHDLC (⾼级数据链路控制协议 High-level Data Link Control)HELLO(routing protocol)HTTP 超⽂本传输协议 80HTTPS 安全超级⽂本传输协议IICMP (互联⽹控制报⽂协议 Internet Control Message Protocol)IDRP (InterDomain Routing Protocol)IEEE 802IGMP (Internet Group Management Protocol)IGP (内部⽹关协议 Interior Gateway Protocol )IMAPIP (互联⽹协议 Internet Protocol)IPXIS-IS(Intermediate System to Intermediate System Protocol)LLCP (链路控制协议 Link Control Protocol)LLC (逻辑链路控制协议 Logical Link Control)MMLD (多播监听发现协议 Multicast Listener Discovery)NNCP (⽹络控制协议 Network Control Protocol)NNTP (⽹络新闻传输协议 Network News Transfer Protocol) 119NTP (Network Time Protocol)PPPP (点对点协议 Protocol)POP (邮局协议 Post Office Protocol) 110RRARP (逆向地址解析协议 Reverse Address Resolution Protocol)RIP (路由信息协议 Routing Information Protocol)SSLIP (串⾏链路连接协议Serial Link Internet Protocol)SNMP (简单⽹络管理协议 Simple Network Management Protocol)SMTP (简单邮件传输协议 Simple Mail Transport Protocol) 25SCTP(流控制传输协议 Stream Control Transmission Protocol)TTCP (传输控制协议 Transmission Control Protocol)TFTP (Trivial File Transfer Protocol)Telnet (远程终端协议 remote terminal protocol) 23UUDP (⽤户数据报协议 User Datagram Protocol)常⽤的有以下⼏种:ARP(Address Resolution Protocol)地址解析协议 它是⽤于映射计算机的物理地址和临时指定的⽹络地址。

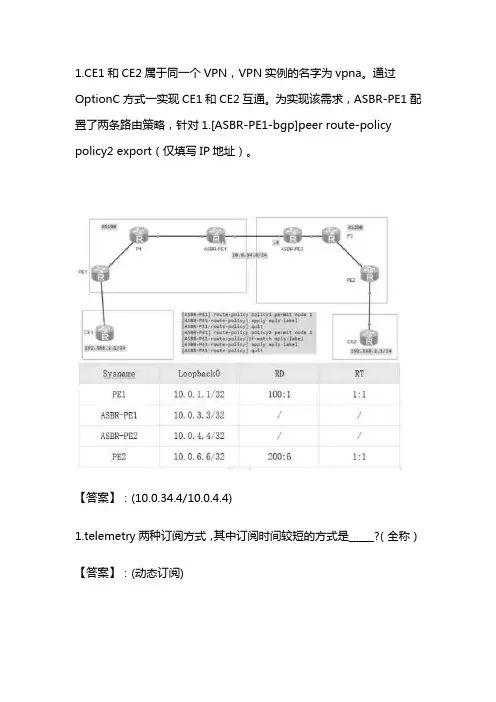
1.CE1和CE2属于同一个VPN,VPN实例的名字为vpna。
通过OptionC方式一实现CE1和CE2互通。
为实现该需求,ASBR-PE1配置了两条路由策略,针对1.[ASBR-PE1-bgp]peer route-policy policy2 export(仅填写IP地址)。
【答案】:(10.0.34.4/10.0.4.4)1.telemetry两种订阅方式,其中订阅时间较短的方式是_____?(全称)【答案】:(动态订阅)1.<rpc xm/ns ="xxxx"message-id="1024“属于netconf中的_____层(中文全称)【答案】:(消息)1.请将以下命令与其作用对应起来_______。
【答案】:(Arp br adcast-Suppress enable ---- ARP广播抑制Arp c llect h st enable ---- 主机信息搜集Arp-pr xy l cal enable ---- ARP本地代理Arp distribute-gateway enable ---- 分布式网关)1.Q S在执行时有一定的顺序,请将以下的几个Q S功能模块按照正确的顺序排序。
1-复杂流分类、2-拥塞避免、3-拥塞管理、4-简单流分类、5-流量整形1.CE1 和CE2 属于同一个WPN,VPN 实例的名字为vpna。
通过OptionC 方式一实现CE1 和CE2 互通。
为实现该需求,请将以下命令行与设备编号进行匹配。
1.HQoS 一共有三级队列: Leve1l, Level2, Level3。
请将以下队列名称与队列等级一一对应。
【答案】:1. NETC NE内容层为设备配置数据,针对以下NETC NEF信息,描述正确的有哪些项?A、该配置采用了Huawei-YANG方式B、该配置为在设备上创建VLAN 10C、该配置采用了NETC NF <edit-c nfig>操作,把配置数据加载到启动配置库D、<c nfig>中包含了“perati n”属性,为merge操作【答案】:ABCD1.SR-MPLS P licy可以借助BGP扩展来传递隧道信息,其信息如图所示。

An Overview of Recent Progress in the Study of Distributed Multi-agent CoordinationYongcan Cao,Member,IEEE,Wenwu Yu,Member,IEEE,Wei Ren,Member,IEEE,and Guanrong Chen,Fellow,IEEEAbstract—This article reviews some main results and progress in distributed multi-agent coordination,focusing on papers pub-lished in major control systems and robotics journals since 2006.Distributed coordination of multiple vehicles,including unmanned aerial vehicles,unmanned ground vehicles and un-manned underwater vehicles,has been a very active research subject studied extensively by the systems and control community. The recent results in this area are categorized into several directions,such as consensus,formation control,optimization, and estimation.After the review,a short discussion section is included to summarize the existing research and to propose several promising research directions along with some open problems that are deemed important for further investigations.Index Terms—Distributed coordination,formation control,sen-sor networks,multi-agent systemI.I NTRODUCTIONC ONTROL theory and practice may date back to thebeginning of the last century when Wright Brothers attempted theirfirst testflight in1903.Since then,control theory has gradually gained popularity,receiving more and wider attention especially during the World War II when it was developed and applied tofire-control systems,missile nav-igation and guidance,as well as various electronic automation devices.In the past several decades,modern control theory was further advanced due to the booming of aerospace technology based on large-scale engineering systems.During the rapid and sustained development of the modern control theory,technology for controlling a single vehicle, albeit higher-dimensional and complex,has become relatively mature and has produced many effective tools such as PID control,adaptive control,nonlinear control,intelligent control, This work was supported by the National Science Foundation under CAREER Award ECCS-1213291,the National Natural Science Foundation of China under Grant No.61104145and61120106010,the Natural Science Foundation of Jiangsu Province of China under Grant No.BK2011581,the Research Fund for the Doctoral Program of Higher Education of China under Grant No.20110092120024,the Fundamental Research Funds for the Central Universities of China,and the Hong Kong RGC under GRF Grant CityU1114/11E.The work of Yongcan Cao was supported by a National Research Council Research Associateship Award at AFRL.Y.Cao is with the Control Science Center of Excellence,Air Force Research Laboratory,Wright-Patterson AFB,OH45433,USA.W.Yu is with the Department of Mathematics,Southeast University,Nanjing210096,China and also with the School of Electrical and Computer Engineering,RMIT University,Melbourne VIC3001,Australia.W.Ren is with the Department of Electrical Engineering,University of California,Riverside,CA92521,USA.G.Chen is with the Department of Electronic Engineering,City University of Hong Kong,Hong Kong SAR,China.Copyright(c)2009IEEE.Personal use of this material is permitted. However,permission to use this material for any other purposes must be obtained from the IEEE by sending a request to pubs-permissions@.and robust control methodologies.In the past two decades in particular,control of multiple vehicles has received increas-ing demands spurred by the fact that many benefits can be obtained when a single complicated vehicle is equivalently replaced by multiple yet simpler vehicles.In this endeavor, two approaches are commonly adopted for controlling multiple vehicles:a centralized approach and a distributed approach. The centralized approach is based on the assumption that a central station is available and powerful enough to control a whole group of vehicles.Essentially,the centralized ap-proach is a direct extension of the traditional single-vehicle-based control philosophy and strategy.On the contrary,the distributed approach does not require a central station for control,at the cost of becoming far more complex in structure and organization.Although both approaches are considered practical depending on the situations and conditions of the real applications,the distributed approach is believed more promising due to many inevitable physical constraints such as limited resources and energy,short wireless communication ranges,narrow bandwidths,and large sizes of vehicles to manage and control.Therefore,the focus of this overview is placed on the distributed approach.In distributed control of a group of autonomous vehicles,the main objective typically is to have the whole group of vehicles working in a cooperative fashion throughout a distributed pro-tocol.Here,cooperative refers to a close relationship among all vehicles in the group where information sharing plays a central role.The distributed approach has many advantages in achieving cooperative group performances,especially with low operational costs,less system requirements,high robustness, strong adaptivity,andflexible scalability,therefore has been widely recognized and appreciated.The study of distributed control of multiple vehicles was perhapsfirst motivated by the work in distributed comput-ing[1],management science[2],and statistical physics[3]. In the control systems society,some pioneering works are generally referred to[4],[5],where an asynchronous agree-ment problem was studied for distributed decision-making problems.Thereafter,some consensus algorithms were studied under various information-flow constraints[6]–[10].There are several journal special issues on the related topics published af-ter2006,including the IEEE Transactions on Control Systems Technology(vol.15,no.4,2007),Proceedings of the IEEE (vol.94,no.4,2007),ASME Journal of Dynamic Systems, Measurement,and Control(vol.129,no.5,2007),SIAM Journal of Control and Optimization(vol.48,no.1,2009),and International Journal of Robust and Nonlinear Control(vol.21,no.12,2011).In addition,there are some recent reviewsand progress reports given in the surveys[11]–[15]and thebooks[16]–[23],among others.This article reviews some main results and recent progressin distributed multi-agent coordination,published in majorcontrol systems and robotics journals since2006.Due to space limitations,we refer the readers to[24]for a more completeversion of the same overview.For results before2006,thereaders are referred to[11]–[14].Specifically,this article reviews the recent research resultsin the following directions,which are not independent but actually may have overlapping to some extent:1.Consensus and the like(synchronization,rendezvous).Consensus refers to the group behavior that all theagents asymptotically reach a certain common agreementthrough a local distributed protocol,with or without predefined common speed and orientation.2.Distributed formation and the like(flocking).Distributedformation refers to the group behavior that all the agents form a pre-designed geometrical configuration throughlocal interactions with or without a common reference.3.Distributed optimization.This refers to algorithmic devel-opments for the analysis and optimization of large-scaledistributed systems.4.Distributed estimation and control.This refers to dis-tributed control design based on local estimation aboutthe needed global information.The rest of this article is organized as follows.In Section II,basic notations of graph theory and stochastic matrices are introduced.Sections III,IV,V,and VI describe the recentresearch results and progress in consensus,formation control, optimization,and estimation.Finally,the article is concludedby a short section of discussions with future perspectives.II.P RELIMINARIESA.Graph TheoryFor a system of n connected agents,its network topology can be modeled as a directed graph denoted by G=(V,W),where V={v1,v2,···,v n}and W⊆V×V are,respectively, the set of agents and the set of edges which directionallyconnect the agents together.Specifically,the directed edgedenoted by an ordered pair(v i,v j)means that agent j can access the state information of agent i.Accordingly,agent i is a neighbor of agent j.A directed path is a sequence of directed edges in the form of(v1,v2),(v2,v3),···,with all v i∈V.A directed graph has a directed spanning tree if there exists at least one agent that has a directed path to every other agent.The union of a set of directed graphs with the same setof agents,{G i1,···,G im},is a directed graph with the sameset of agents and its set of edges is given by the union of the edge sets of all the directed graphs G ij,j=1,···,m.A complete directed graph is a directed graph in which each pair of distinct agents is bidirectionally connected by an edge,thus there is a directed path from any agent to any other agent in the network.Two matrices are used to represent the network topology: the adjacency matrix A=[a ij]∈R n×n with a ij>0if (v j,v i)∈W and a ij=0otherwise,and the Laplacian matrix L=[ℓij]∈R n×n withℓii= n j=1a ij andℓij=−a ij,i=j, which is generally asymmetric for directed graphs.B.Stochastic MatricesA nonnegative square matrix is called(row)stochastic matrix if its every row is summed up to one.The product of two stochastic matrices is still a stochastic matrix.A row stochastic matrix P∈R n×n is called indecomposable and aperiodic if lim k→∞P k=1y T for some y∈R n[25],where 1is a vector with all elements being1.III.C ONSENSUSConsider a group of n agents,each with single-integrator kinematics described by˙x i(t)=u i(t),i=1,···,n,(1) where x i(t)and u i(t)are,respectively,the state and the control input of the i th agent.A typical consensus control algorithm is designed asu i(t)=nj=1a ij(t)[x j(t)−x i(t)],(2)where a ij(t)is the(i,j)th entry of the corresponding ad-jacency matrix at time t.The main idea behind(2)is that each agent moves towards the weighted average of the states of its neighbors.Given the switching network pattern due to the continuous motions of the dynamic agents,coupling coefficients a ij(t)in(2),hence the graph topologies,are generally time-varying.It is shown in[9],[10]that consensus is achieved if the underlying directed graph has a directed spanning tree in some jointly fashion in terms of a union of its time-varying graph topologies.The idea behind consensus serves as a fundamental principle for the design of distributed multi-agent coordination algo-rithms.Therefore,investigating consensus has been a main research direction in the study of distributed multi-agent co-ordination.To bridge the gap between the study of consensus algorithms and many physical properties inherited in practical systems,it is necessary and meaningful to study consensus by considering many practical factors,such as actuation,control, communication,computation,and vehicle dynamics,which characterize some important features of practical systems.This is the main motivation to study consensus.In the following part of the section,an overview of the research progress in the study of consensus is given,regarding stochastic network topologies and dynamics,complex dynamical systems,delay effects,and quantization,mainly after2006.Several milestone results prior to2006can be found in[2],[4]–[6],[8]–[10], [26].A.Stochastic Network Topologies and DynamicsIn multi-agent systems,the network topology among all vehicles plays a crucial role in determining consensus.The objective here is to explicitly identify necessary and/or suffi-cient conditions on the network topology such that consensus can be achieved under properly designed algorithms.It is often reasonable to consider the case when the network topology is deterministic under ideal communication chan-nels.Accordingly,main research on the consensus problem was conducted under a deterministicfixed/switching network topology.That is,the adjacency matrix A(t)is deterministic. Some other times,when considering random communication failures,random packet drops,and communication channel instabilities inherited in physical communication channels,it is necessary and important to study consensus problem in the stochastic setting where a network topology evolves according to some random distributions.That is,the adjacency matrix A(t)is stochastically evolving.In the deterministic setting,consensus is said to be achieved if all agents eventually reach agreement on a common state. In the stochastic setting,consensus is said to be achieved almost surely(respectively,in mean-square or in probability)if all agents reach agreement on a common state almost surely (respectively,in mean-square or with probability one).Note that the problem studied in the stochastic setting is slightly different from that studied in the deterministic setting due to the different assumptions in terms of the network topology. Consensus over a stochastic network topology was perhaps first studied in[27],where some sufficient conditions on the network topology were given to guarantee consensus with probability one for systems with single-integrator kinemat-ics(1),where the rate of convergence was also studied.Further results for consensus under a stochastic network topology were reported in[28]–[30],where research effort was conducted for systems with single-integrator kinematics[28],[29]or double-integrator dynamics[30].Consensus for single-integrator kine-matics under stochastic network topology has been exten-sively studied in particular,where some general conditions for almost-surely consensus was derived[29].Loosely speaking, almost-surely consensus for single-integrator kinematics can be achieved,i.e.,x i(t)−x j(t)→0almost surely,if and only if the expectation of the network topology,namely,the network topology associated with expectation E[A(t)],has a directed spanning tree.It is worth noting that the conditions are analogous to that in[9],[10],but in the stochastic setting. In view of the special structure of the closed-loop systems concerning consensus for single-integrator kinematics,basic properties of the stochastic matrices play a crucial role in the convergence analysis of the associated control algorithms. Consensus for double-integrator dynamics was studied in[30], where the switching network topology is assumed to be driven by a Bernoulli process,and it was shown that consensus can be achieved if the union of all the graphs has a directed spanning tree.Apparently,the requirement on the network topology for double-integrator dynamics is a special case of that for single-integrator kinematics due to the difference nature of thefinal states(constantfinal states for single-integrator kinematics and possible dynamicfinal states for double-integrator dynamics) caused by the substantial dynamical difference.It is still an open question as if some general conditions(corresponding to some specific algorithms)can be found for consensus with double-integrator dynamics.In addition to analyzing the conditions on the network topology such that consensus can be achieved,a special type of consensus algorithm,the so-called gossip algorithm[31],[32], has been used to achieve consensus in the stochastic setting. The gossip algorithm can always guarantee consensus almost surely if the available pairwise communication channels satisfy certain conditions(such as a connected graph).The way of network topology switching does not play any role in the consideration of consensus.The current study on consensus over stochastic network topologies has shown some interesting results regarding:(1) consensus algorithm design for various multi-agent systems,(2)conditions of the network topologies on consensus,and(3)effects of the stochastic network topologies on the con-vergence rate.Future research on this topic includes,but not limited to,the following two directions:(1)when the network topology itself is stochastic,how to determine the probability of reaching consensus almost surely?(2)compared with the deterministic network topology,what are the advantages and disadvantages of the stochastic network topology,regarding such as robustness and convergence rate?As is well known,disturbances and uncertainties often exist in networked systems,for example,channel noise,commu-nication noise,uncertainties in network parameters,etc.In addition to the stochastic network topologies discussed above, the effect of stochastic disturbances[33],[34]and uncertain-ties[35]on the consensus problem also needs investigation. Study has been mainly devoted to analyzing the performance of consensus algorithms subject to disturbances and to present-ing conditions on the uncertainties such that consensus can be achieved.In addition,another interesting direction in dealing with disturbances and uncertainties is to design distributed localfiltering algorithms so as to save energy and improve computational efficiency.Distributed localfiltering algorithms play an important role and are more effective than traditional centralizedfiltering algorithms for multi-agent systems.For example,in[36]–[38]some distributed Kalmanfilters are designed to implement data fusion.In[39],by analyzing consensus and pinning control in synchronization of complex networks,distributed consensusfiltering in sensor networks is addressed.Recently,Kalmanfiltering over a packet-dropping network is designed through a probabilistic approach[40]. Today,it remains a challenging problem to incorporate both dynamics of consensus and probabilistic(Kalman)filtering into a unified framework.plex Dynamical SystemsSince consensus is concerned with the behavior of a group of vehicles,it is natural to consider the system dynamics for practical vehicles in the study of the consensus problem. Although the study of consensus under various system dynam-ics is due to the existence of complex dynamics in practical systems,it is also interesting to observe that system dynamics play an important role in determining thefinal consensus state.For instance,the well-studied consensus of multi-agent systems with single-integrator kinematics often converges to a constantfinal value instead.However,consensus for double-integrator dynamics might admit a dynamicfinal value(i.e.,a time function).These important issues motivate the study of consensus under various system dynamics.As a direct extension of the study of the consensus prob-lem for systems with simple dynamics,for example,with single-integrator kinematics or double-integrator dynamics, consensus with general linear dynamics was also studied recently[41]–[43],where research is mainly devoted tofinding feedback control laws such that consensus(in terms of the output states)can be achieved for general linear systems˙x i=Ax i+Bu i,y i=Cx i,(3) where A,B,and C are constant matrices with compatible sizes.Apparently,the well-studied single-integrator kinematics and double-integrator dynamics are special cases of(3)for properly choosing A,B,and C.As a further extension,consensus for complex systems has also been extensively studied.Here,the term consensus for complex systems is used for the study of consensus problem when the system dynamics are nonlinear[44]–[48]or with nonlinear consensus algorithms[49],[50].Examples of the nonlinear system dynamics include:•Nonlinear oscillators[45].The dynamics are often as-sumed to be governed by the Kuramoto equation˙θi=ωi+Kstability.A well-studied consensus algorithm for(1)is given in(2),where it is now assumed that time delay exists.Two types of time delays,communication delay and input delay, have been considered in the munication delay accounts for the time for transmitting information from origin to destination.More precisely,if it takes time T ij for agent i to receive information from agent j,the closed-loop system of(1)using(2)under afixed network topology becomes˙x i(t)=nj=1a ij(t)[x j(t−T ij)−x i(t)].(7)An interpretation of(7)is that at time t,agent i receives information from agent j and uses data x j(t−T ij)instead of x j(t)due to the time delay.Note that agent i can get its own information instantly,therefore,input delay can be considered as the summation of computation time and execution time. More precisely,if the input delay for agent i is given by T p i, then the closed-loop system of(1)using(2)becomes˙x i(t)=nj=1a ij(t)[x j(t−T p i)−x i(t−T p i)].(8)Clearly,(7)refers to the case when only communication delay is considered while(8)refers to the case when only input delay is considered.It should be emphasized that both communication delay and input delay might be time-varying and they might co-exist at the same time.In addition to time delay,it is also important to consider packet drops in exchanging state information.Fortunately, consensus with packet drops can be considered as a special case of consensus with time delay,because re-sending packets after they were dropped can be easily done but just having time delay in the data transmission channels.Thus,the main problem involved in consensus with time delay is to study the effects of time delay on the convergence and performance of consensus,referred to as consensusabil-ity[52].Because time delay might affect the system stability,it is important to study under what conditions consensus can still be guaranteed even if time delay exists.In other words,can onefind conditions on the time delay such that consensus can be achieved?For this purpose,the effect of time delay on the consensusability of(1)using(2)was investigated.When there exists only(constant)input delay,a sufficient condition on the time delay to guarantee consensus under afixed undirected interaction graph is presented in[8].Specifically,an upper bound for the time delay is derived under which consensus can be achieved.This is a well-expected result because time delay normally degrades the system performance gradually but will not destroy the system stability unless the time delay is above a certain threshold.Further studies can be found in, e.g.,[53],[54],which demonstrate that for(1)using(2),the communication delay does not affect the consensusability but the input delay does.In a similar manner,consensus with time delay was studied for systems with different dynamics, where the dynamics(1)are replaced by other more complex ones,such as double-integrator dynamics[55],[56],complex networks[57],[58],rigid bodies[59],[60],and general nonlinear dynamics[61].In summary,the existing study of consensus with time delay mainly focuses on analyzing the stability of consensus algo-rithms with time delay for various types of system dynamics, including linear and nonlinear dynamics.Generally speaking, consensus with time delay for systems with nonlinear dynam-ics is more challenging.For most consensus algorithms with time delays,the main research question is to determine an upper bound of the time delay under which time delay does not affect the consensusability.For communication delay,it is possible to achieve consensus under a relatively large time delay threshold.A notable phenomenon in this case is that thefinal consensus state is constant.Considering both linear and nonlinear system dynamics in consensus,the main tools for stability analysis of the closed-loop systems include matrix theory[53],Lyapunov functions[57],frequency-domain ap-proach[54],passivity[58],and the contraction principle[62]. Although consensus with time delay has been studied extensively,it is often assumed that time delay is either constant or random.However,time delay itself might obey its own dynamics,which possibly depend on the communication distance,total computation load and computation capability, etc.Therefore,it is more suitable to represent the time delay as another system variable to be considered in the study of the consensus problem.In addition,it is also important to consider time delay and other physical constraints simultaneously in the study of the consensus problem.D.QuantizationQuantized consensus has been studied recently with motiva-tion from digital signal processing.Here,quantized consensus refers to consensus when the measurements are digital rather than analog therefore the information received by each agent is not continuous and might have been truncated due to digital finite precision constraints.Roughly speaking,for an analog signal s,a typical quantizer with an accuracy parameterδ, also referred to as quantization step size,is described by Q(s)=q(s,δ),where Q(s)is the quantized signal and q(·,·) is the associated quantization function.For instance[63],a quantizer rounding a signal s to its nearest integer can be expressed as Q(s)=n,if s∈[(n−1/2)δ,(n+1/2)δ],n∈Z, where Z denotes the integer set.Note that the types of quantizers might be different for different systems,hence Q(s) may differ for different systems.Due to the truncation of the signals received,consensus is now considered achieved if the maximal state difference is not larger than the accuracy level associated with the whole system.A notable feature for consensus with quantization is that the time to reach consensus is usuallyfinite.That is,it often takes afinite period of time for all agents’states to converge to an accuracy interval.Accordingly,the main research is to investigate the convergence time associated with the proposed consensus algorithm.Quantized consensus was probablyfirst studied in[63], where a quantized gossip algorithm was proposed and its convergence was analyzed.In particular,the bound of theconvergence time for a complete graph was shown to be poly-nomial in the network size.In[64],coding/decoding strate-gies were introduced to the quantized consensus algorithms, where it was shown that the convergence rate depends on the accuracy of the quantization but not the coding/decoding schemes.In[65],quantized consensus was studied via the gossip algorithm,with both lower and upper bounds of the expected convergence time in the worst case derived in terms of the principle submatrices of the Laplacian matrix.Further results regarding quantized consensus were reported in[66]–[68],where the main research was also on the convergence time for various proposed quantized consensus algorithms as well as the quantization effects on the convergence time.It is intuitively reasonable that the convergence time depends on both the quantization level and the network topology.It is then natural to ask if and how the quantization methods affect the convergence time.This is an important measure of the robustness of a quantized consensus algorithm(with respect to the quantization method).Note that it is interesting but also more challenging to study consensus for general linear/nonlinear systems with quantiza-tion.Because the difference between the truncated signal and the original signal is bounded,consensus with quantization can be considered as a special case of one without quantization when there exist bounded disturbances.Therefore,if consensus can be achieved for a group of vehicles in the absence of quantization,it might be intuitively correct to say that the differences among the states of all vehicles will be bounded if the quantization precision is small enough.However,it is still an open question to rigorously describe the quantization effects on consensus with general linear/nonlinear systems.E.RemarksIn summary,the existing research on the consensus problem has covered a number of physical properties for practical systems and control performance analysis.However,the study of the consensus problem covering multiple physical properties and/or control performance analysis has been largely ignored. In other words,two or more problems discussed in the above subsections might need to be taken into consideration simul-taneously when studying the consensus problem.In addition, consensus algorithms normally guarantee the agreement of a team of agents on some common states without taking group formation into consideration.To reflect many practical applications where a group of agents are normally required to form some preferred geometric structure,it is desirable to consider a task-oriented formation control problem for a group of mobile agents,which motivates the study of formation control presented in the next section.IV.F ORMATION C ONTROLCompared with the consensus problem where thefinal states of all agents typically reach a singleton,thefinal states of all agents can be more diversified under the formation control scenario.Indeed,formation control is more desirable in many practical applications such as formationflying,co-operative transportation,sensor networks,as well as combat intelligence,surveillance,and reconnaissance.In addition,theperformance of a team of agents working cooperatively oftenexceeds the simple integration of the performances of all individual agents.For its broad applications and advantages,formation control has been a very active research subject inthe control systems community,where a certain geometric pattern is aimed to form with or without a group reference.More precisely,the main objective of formation control is to coordinate a group of agents such that they can achievesome desired formation so that some tasks can befinished bythe collaboration of the agents.Generally speaking,formation control can be categorized according to the group reference.Formation control without a group reference,called formationproducing,refers to the algorithm design for a group of agents to reach some pre-desired geometric pattern in the absenceof a group reference,which can also be considered as the control objective.Formation control with a group reference,called formation tracking,refers to the same task but followingthe predesignated group reference.Due to the existence of the group reference,formation tracking is usually much morechallenging than formation producing and control algorithmsfor the latter might not be useful for the former.As of today, there are still many open questions in solving the formationtracking problem.The following part of the section reviews and discussesrecent research results and progress in formation control, including formation producing and formation tracking,mainlyaccomplished after2006.Several milestone results prior to 2006can be found in[69]–[71].A.Formation ProducingThe existing work in formation control aims at analyzingthe formation behavior under certain control laws,along with stability analysis.1)Matrix Theory Approach:Due to the nature of multi-agent systems,matrix theory has been frequently used in thestability analysis of their distributed coordination.Note that consensus input to each agent(see e.g.,(2))isessentially a weighted average of the differences between the states of the agent’s neighbors and its own.As an extensionof the consensus algorithms,some coupling matrices wereintroduced here to offset the corresponding control inputs by some angles[72],[73].For example,given(1),the controlinput(2)is revised as u i(t)= n j=1a ij(t)C[x j(t)−x i(t)], where C is a coupling matrix with compatible size.If x i∈R3, then C can be viewed as the3-D rotational matrix.The mainidea behind the revised algorithm is that the original controlinput for reaching consensus is now rotated by some angles. The closed-loop system can be expressed in a vector form, whose stability can be determined by studying the distribution of the eigenvalues of a certain transfer matrix.Main research work was conducted in[72],[73]to analyze the collective motions for systems with single-integrator kinematics and double-integrator dynamics,where the network topology,the damping gain,and C were shown to affect the collective motions.Analogously,the collective motions for a team of nonlinear self-propelling agents were shown to be affected by。

高中英语作文博客必须尽快实名制(Bloggers must soongive real names)hu qiheng, chairman of the board of directors of the isc, was reported to have said on tuesday at info china 2010 in beijing that china is making attempts to strike a balance between individual privacy and public interests.”the past understanding of privacy is too absolute. not only china, but also the whole world, should realize the necessity of balancing individual privacy and public and national interests,” he said.a new system is likely to be adopted, requiring chinese netizens to submit information like real names and id card numbers when they register a blog or a bbs (bulletin board service) izens will be able to continue choosing their own online name, and as long as they do not violate laws their personal information will remain private and safe.the first area for real name application will be blogs, a popular form of internet-based diary.blogs have been used by somepeople to infringe upon other people’s privacy and rights.for example an infamous tv host had thousands of netizens visit her blog just because she wrote an article about a well-known tv anchor’s marriage history, which included some allegedly false information.as a blogger’s real name is unknown, it is very difficult to safeguard privacy and rights.the society, affiliated to the ministry of information industry, was entrusted by the ministry to form a blog research panel to provide solutions for the development of china’s blog industry.the real name system is said to be able to protect law-abiding netizens’privacy.yang junzuo, secretary-general of isc’s self-discipline working commission, was quoted by beijing-based china times a month ago saying that the real name system is the solution.”free speech on the internet does not include talking nonsense and not taking responsibility. bad symptoms will be curbed,” he was quoted as saying.however, not many netizens support the system.an online poll at yesterday showed that only one quarter of surveyed netizens agreed that the system would crack down on online CRImes while not interfering with internet use.more than 70 per cent of people were against it, believingit was “absurd” to enforce a real name system just because of a minority of people who committed online CRImes.xinhua news agency reported that hu stressed at the meeting that the society would adopt multiple ways to improve the internet environment.hu was quoted as saying that the direct purpose of improving the internet environment is to enable the young generation to grow up in an internet-friendly environment like youth in developed countries.。


分布式原理:一文了解Gossip 协议gossip 协议(gossip protocol)又称epidemic 协议(epidemic protocol),是基于流行病传播方式的节点或者进程之间信息交换的协议,在分布式系统中被广泛使用,比如我们可以使用gossip 协议来确保网络中所有节点的数据一样。
从gossip 单词就可以看到,其中文意思是八卦、流言等意思,我们可以想象下绯闻的传播(或者流行病的传播);gossip 协议的工作原理就类似于这个。
gossip 协议利用一种随机的方式将信息传播到整个网络中,并在一定时间内使得系统内的所有节点数据一致。
Gossip 其实是一种去中心化思路的分布式协议,解决状态在集群中的传播和状态一致性的保证两个问题。
gossip 优势可扩展性(Scalable)gossip 协议是可扩展的,一般需要O(logN)轮就可以将信息传播到所有的节点,其中N 代表节点的个数。
每个节点仅发送固定数量的消息,并且与网络中节点数目无法。
在数据传送的时候,节点并不会等待消息的ack,所以消息传送失败也没有关系,因为可以通过其他节点将消息传递给之前传送失败的节点。
系统可以轻松扩展到数百万个进程。
容错(Fault-tolerance)网络中任何节点的重启或者宕机都不会影响gossip 协议的运行。
健壮性(Robust)gossip 协议是去中心化的协议,所以集群中的所有节点都是对等的,没有特殊的节点,所以任何节点出现问题都不会阻止其他节点继续发送消息。
任何节点都可以随时加入或离开,而不会影响系统的整体服务质量(QOS)最终一致性(Convergent consistency)Gossip 协议实现信息指数级的快速传播,因此在有新信息需要传播时,消息可以快速地发送到全局节点,在有限的时间内能够做到所有节点都拥有最新的数据。
gossip 协议的类型。

异质信息网络的互信息最大化社区搜索异质信息网络的互信息最大化社区搜索随着信息技术的不断发展,人们对于社交网络的研究也越来越深入。
在社交网络中,人们通过互相交流分享信息,形成了一个庞大而复杂的信息网络。
然而,传统的社区搜索算法在处理这种异质信息网络时面临一些挑战,例如节点类型多样性和节点之间边的异构性。
因此,研究人员提出了基于互信息最大化的社区搜索方法,可以有效地发现异质信息网络中的社区结构。
互信息最大化是一种用于发现社区结构的无监督学习方法,它通过计算节点对之间的互信息来衡量它们之间的相关性。
在异质信息网络中,节点之间可能存在多种类型的关系,例如用户之间的社交关系、物品与用户之间的交互关系等。
传统的社区搜索算法往往忽视了这些节点类型的差异,导致无法准确地发现社区结构。
而互信息最大化的方法能够利用节点之间的关系和节点的属性信息,有效地挖掘不同类型节点之间的关联性。
在互信息最大化的社区搜索方法中,首先需要构建节点之间的关系网络。
异质信息网络中的节点可以表示为多维向量,每个维度对应一个节点类型。
节点之间的关系可以表示为一个矩阵,其中每个元素表示两个节点之间的互信息。
然后,通过最大化节点对之间的互信息,可以找到具有相关性的节点对,进而聚类形成社区结构。
通过不断调整聚类的阈值,可以得到不同规模的社区。
与传统的社区搜索算法相比,互信息最大化的方法具有以下优势。
首先,它能够考虑节点之间的多样性,不仅仅局限于某一类型的节点。
这样可以更全面地发现社区结构。
其次,互信息最大化的方法可以充分利用节点的属性信息,例如节点的特征向量、标签等。
这样可以提供更具有解释性的社区结果。
此外,互信息最大化的方法还能够适应异质信息网络的动态变化,对于新增节点或者关系的处理更加灵活。
然而,互信息最大化的社区搜索方法也面临一些挑战。
首先,节点之间的关系网络构建需要耗费大量的计算资源和存储空间。
同时,由于异质信息网络的复杂性,目前还缺乏有效的算法来准确地计算节点对之间的互信息。

产业观察INDUSTRY OBSERVATIONS32信息安全与通信保密 SEPT2020阿伦·维什瓦纳特(Arun Vishwanath)博士毕业于哈佛大学,是网络安全研究和咨询公司Avant Research Group(ARG)的首席技术官、美国国家安全局安全与隐私科学理事会杰出专家小组成员,曾多次受邀出席美国参议院/众议院的全球安全会议,首次强调了用户责任的必要性,从发展网络卫生到更安全地使用网络,以避免受到网络攻击。
迄今为止,他发表近50篇关于技术用户和网络安全问题的文章,其中,关于提高网络抵御在线社交工程能力的研究得到了美国国家科学基金会的资助,研究成果已提交给世界各地的国家安全和执法机构的负责人。
来自社会工程角度的网络脆弱性思考——访网络安全和网络隐私领域的权威专家阿伦·维什瓦纳特博士阿伦·维什瓦纳特博士侧重于提高个人、组织和国家对网络攻击的抵御能力的研究,重点关注网络安全中最薄弱的环节,即我们所有的互联网用户。
他是第一个证明用户认知作用的研究者,特别是有关用户如何处理信息和网络风险,其研究首次强调社交媒体的危险性,而且还是第一个展示基于移动的社交工程攻击的威胁的研究人员。
阿伦·维什瓦纳特博士还扮演着技术专家的角色,出于对公共利益的考虑,他撰写和强调了网络安全方面的问题及其解决方案。
他的许多独创性想法导致了新产品、新工艺和新政策的产生,对网络安全科学的研究和观点也曾在《连线》杂志、《今日美国》、Politico、CNN、《华盛顿邮报》、《科学美国人》以及其他数百家国内外新闻机构上发表过专题报道。
安吉拉·斯科特·布里格斯:您是如何成为人类网络脆弱性和社会工程领域的世界顶级专家的?阿伦·维什瓦纳特:我是一名受过训练的社会科学家,我对网络安全的兴趣来自我在技术应用和心理学方面的研究工作。
我花了十年时间研究人们是如何安吉拉·斯科特·布里格斯■ 高端访谈栏目责编:李天婴33SEPT 2020 信息安全与通信保密产生创新的想法、技能、技术,以及人们如何接受、拒绝、利用或错误地利用它们。

网络很神秘吗英语作文Title: The Mystique of the Internet。
The internet, a vast network connecting billions of people worldwide, is undeniably shrouded in mystique. Its complexities, capabilities, and implications have fascinated scholars, technologists, and the general public alike. In this essay, we delve into the enigmatic nature of the internet, exploring its multifaceted aspects and the impact it has on society.One of the primary reasons behind the mystique of the internet lies in its sheer scale and scope. With billions of websites, terabytes of data, and countless interconnected devices, the internet represents an unfathomable expanse of information and connectivity. Its seemingly infinite nature captivates the imagination, evoking a sense of wonder and curiosity about what lies beyond the surface.Furthermore, the internet's decentralized structure adds to its mystique. Unlike traditional forms of communication and information dissemination, which are often centralized and hierarchical, the internet operates on a distributed network model. This decentralized architecture fosters resilience, flexibility, and innovation but also introduces complexities that can be difficult to comprehend fully.Moreover, the rapid pace of technological advancement contributes to the mystique of the internet. New technologies, protocols, and applications emerge regularly, reshaping the digital landscape and challenging our understanding of what is possible. From artificial intelligence to blockchain to virtual reality, the internet continually pushes the boundaries of innovation, leaving us in awe of its transformative potential.The internet's role as a catalyst for social and cultural change further adds to its mystique. It has revolutionized how we communicate, collaborate, and consume information, fundamentally altering the fabric of society.Social media platforms, online communities, and digital activism have empowered individuals to connect, express themselves, and effect change on a global scale. Yet, the internet's influence is not without controversy, as concerns about privacy, misinformation, and digital divide persist.Additionally, the anonymity and pseudonymity afforded by the internet contribute to its mystique. Users can interact and engage with others without revealing their true identities, creating virtual personas and online personas that may differ from their offline selves. This anonymity can foster creativity, experimentation, and freedom of expression but also raises questions about authenticity and trust in online interactions.Furthermore, the internet's role as a gateway to knowledge and information fuels its mystique. With a few clicks, we can access a wealth of resources on virtually any topic imaginable, from academic research papers to DIY tutorials to obscure subcultures. The democratization of information has empowered individuals to learn, explore,and discover new interests and passions, transcending geographical and cultural boundaries in the process.In conclusion, the internet's mystique stems from its vastness, complexity, and transformative power. As we navigate the digital age, it is essential to approach the internet with a critical eye, acknowledging both its potential and its pitfalls. By embracing curiosity, inquiry, and open dialogue, we can unravel the mysteries of the internet and harness its power for the betterment of society.。
Diss.ETH No.16653User-Centric Dependability Concepts for Ubiquitous ComputingA dissertation submitted to theSWISS FEDERAL INSTITUTE OF TECHNOLOGYZURICH(ETH ZURICH)for the degree ofDoctor of Technical Sciencespresented byJürgen BohnDiplom-Informatiker,University of Karlsruhe(TH),Germanyborn October16,1973citizen of Germanyaccepted on the recommendation ofProf.Dr.Friedemann Mattern,examinerDr.Albrecht Schmidt,co-examiner2006Bibliography[AAA97]Ward Andy,Jones Alan,and Hopper Andy.A New Location Technique for the Active Office.IEEE Personal Communications,4(5):42–47,1997. [AAC+00]Harold Abelson,Don Allen,Daniel Coore,Chris Hanson,George Homsy,Thomas F.Knight,Jr.,Radhika Nagpal,Erik Rauch,Gerald JaySussman,and Ron Weiss.Amorphous munications ofthe ACM,43(5):74–82,March2000.[ABL04]Giuseppe Anastasi,Alberto Bartoli,and Flaminia L.Luccio.Fault-tolerant support for reliable multicast in mobile wireless systems:designand evaluation.Wireless Networks,10(3):259–269,2004.[ABO02]Gregory D.Abowd,Agathe Battestini,and Thomas O’Connell.The Lo-cation Service:A framework for handling multiple location sensing tech-nologies,2002.Available online at /fce/ahri/publications/location_service.pdf.[ACDP05]Matthieu Anne,James L.Crowley,Vincent Devin,and Gilles Privat.Localisation intra-batiment multi-technologies:RFID,wifiet vision.InUbiMob’05:Proceedings of the2nd French-speaking conference on Mo-bility and ubiquity computing,pages29–35,New York,NY,USA,2005.ACM Press.[ACH+01]Mike Addlesee,Rupert Curwen,Steve Hodges,Joe Newman,Pete Steggles,Andy Ward,and Andy Hopper.Implementing a Sentient Com-puting puter,34(8):50–56,2001.[ACT00]Marcos Kawazoe Aguilera,Wei Chen,and Sam Toueg.Failure Detection and Consensus in the Crash Recovery Model.Distributed Computing,13(2):99–125,April2000.[Ada00]Natascha Adamowsky.Kulturelle denburger Diskurs“Ubiq-uitous Computing”,February2000.Available online at http://www.inf.ethz.ch/vs/events/slides/adamowldbg.pdf.[ADS02]James Aspnes,ZoëDiamadi,and Gauri Shah.Fault-tolerant routing in peer-to-peer systems.In Twenty-First ACM Symposium on Principles ofDistributed Computing,pages223–232,July2002.[AJLS97]M.D.Addlesee,A.Jones,F.Livesey,and F.Samaria.The ORL Active Floor.IEEE Personal Communications,4(5):35–41,October1997. [AKS04]Ankur Agiwal,Parakram Khandpur,and Huzur Saran.LOCATOR:loca-tion estimation system For wireless LANs.In WMASH’04:Proceedingsof the2nd ACM international workshop on Wireless mobile applications311Bibliographyand services on WLAN hotspots,pages102–109,New York,NY,USA,2004.ACM Press.[AL86] A.Avizienis and prie.Dependable computing:From concepts to design diversity.Proceedings of the IEEE,74(5):629–638,May1986. [AM00]Gregory D.Abowd and Elizabeth D.Mynatt.Charting Past,Present and Future Research in Ubiquitous Computing.ACM Transactions onComputer-Human Interaction,Special issue on HCI in the new Mille-nium,7(1):29–58,March2000.[Ana05]Analysys Research.The Western European Mobile Market:trends and forecasts2005-2010.6th Edition,April2005.Available on-line at /default.asp?Mode=article\&iLeftArticle=1876.[Ano01]Anonymous.Workshop on Embedded Computing.Report,Sponsored by NSF and ACM SIGDA,November2001.[Ara95]Agustin A.Araya.Questioning Ubiquitous Computing.In Proceedings of the1995ACM23rd Annual Conference on Computer Science.ACMPress,1995.Available online at /10.1145/259526.259560.[ART05]O.Amft,J.Randall,and G.Tröster.Towards LuxTrace:Using solar cells to support human position tracking.In Proceedings of2nd Inter-national Forum on Applied Wearable Computing,Zürich,Switzerland,March2005.[AS85]Bowen Alpern and Fred B.Schneider.Defining rmation Processing Letters,21:181–185,1985.[ASRPZ03]Stefan Arbanowski,Stephan Steglich,Ilja Radusch,and Radu Popescu-Zeletin.Super Distributed Objects:An Execution Environmentfor I-Centric Services.In Proceedings9th IEEE International Workshopon Object-Oriented Real-Time Dependable Systems(WORDS’03),pages201–208.IEEE Computer Society,October2003.[ASSC02a]I.F.Akyildiz,W.Su,Y.Sankarasubramaniam,and E.Cayirci.A survey on sensor networks.IEEE Communications Magazine,40(8):102–114,August2002.[ASSC02b]I.F.Akyildiz,W.Su,Y.Sankarasubramaniam,and E.Cayirci.Wire-less Sensor Networks:A Survey.IEEE Computer Networks,38(4):393–422,March2002.[ATS04]Stephanos Androutsellis-Theotokis and Diomidis Spinellis.A survey of peer-to-peer content distribution technologies.ACM Computing Surveys,36(4):335–371,2004.[Bak04]Bonnie C.Baker.Wireless Communication Using the IrDA Standard Pro-tocol.Analog Design Note ADN006,Microchip Technology Inc,January2004.312Bibliography [Bal96]T.R.Balch.Grid-based navigation for mobile robots.The Robotics Practitioner,2(1),1996.[Bar02]David Barkai.Peer-to-Peer Computing.Technologies for Sharing and Collaborating on the Net.Rich Bowles,2002.[Bär04]Marco Bär.Collaborative Map-Making in an Area of Randomly Dis-tributed RFID-Tags using a LEGO Mindstorms Robot Vehicle.Semesterthesis,Institute for Pervasive Computing,Department of Computer Sci-ence,ETH Zurich,Switzerland,July2004.[BBH+04]Gaetano Borriello,Waylon Brunette,Matthew Hall,Carl Hartung, and Cameron Tangney.Reminding About Tagged Objects Using Pas-sive RFIDs.In Proceedings of6th International Conference on Ubiq-uitous Computing(UbiComp2004),Nottingham,UK,September7-10,2004,number3205in Lecture Notes in Computer Science,pages36–53.Springer,2004.[BC06]Bluetooth –The Official Bluetooth Wireless Info ,February2006.[BCL+03a]Jürgen Bohn,Vlad Coroama,Marc Langheinrich,Friedemann Mat-tern,and Michael Rohs.Allgegenwart und Verschwinden des Computers–Leben in einer Welt smarter Alltagsdinge.In Ralf Grötker,editor,Privat!Kontrollierte Freiheit in einer vernetzten Welt,pages195–245.Heise-Verlag,March2003.[BCL+03b]Jürgen Bohn,Vlad Coroama,Marc Langheinrich,Friedemann Mat-tern,and Michael Rohs.Disappearing Computers Everywhere–Livingin a World of Smart Everyday Objects.In New Media,Technology andEveryday Life in Europe Conference(EMTEL2003),London,UK,April2003.Available online at /.[BCL+04a]Jürgen Bohn,Vlad Coroama,Marc Langheinrich,Friedemann Mat-tern,and Michael Rohs.Living in a World of Smart Everyday Objects–Social,Economic,and Ethical Implications.Journal of Human andEcological Risk Assessment,10(5),October2004.[BCL+04b]Jürgen Bohn,Vlad Coroama,Marc Langheinrich,Friedemann Mat-tern,and Michael Rohs.Social,Economic,and Ethical Implicationsof Ambient Intelligence and Ubiquitous Computing.In W.Weber,J.Rabaey,and E.Aarts,editors,Ambient Intelligence.Springer,2004. [BDM93]Michael Barborak,Anton Dahbura,and Miroslaw Malek.The con-sensus problem in fault-tolerant computing.ACM Computing Surveys,25(2):171–220,June1993.[BEGH01]Nirupama Bulusu,Deborah Estrin,Lewis Girod,and John Heidemann.Scalable coordination for wireless sensor networks:Self-configuring local-ization systems.In Proceedings6th International Symposium on Commu-nication Theory and Applications(ISCTA’01).University of California,Los Angeles,July15-20th2001.313Bibliography[BFA05]Azzedine Boukerche,Xin Fei,and Regina B.Araujo.An energy aware coverage-preserving scheme for wireless sensor networks.In PE-WASUN’05:Proceedings of the2nd ACM international workshop on Performanceevaluation of wireless ad hoc,sensor,and ubiquitous networks,pages205–213,New York,NY,USA,2005.ACM Press.[BFH97]W.Burgard,D.Fox,and D.Hennig.Fast Grid-based Position Tracking for Mobile Robots.In Proceedings of the21th German Conference onArtificial Intelligence,volume1303of Lecture Notes in Computer Science.Springer,1997.[BG95]Kenneth P.Birman and Bradford B.Glade.Reliability through consis-tency.IEEE Software,pages29–41,May1995.[BGS01]M.Beigl,H.-W.Gellersen,and A.Schmidt.Mediacups:Experience with Design and Use of Computer-Augmented Everyday puterNetworks,Special Issue on Pervasive Computing,Elsevier,35(4):401–409,March2001.[BGV02]Jürgen Bohn,Felix Gärtner,and Harald Vogt.Dependability Issues of Pervasive Computing in a Healthcare Environment.In Dieter Hutter,Günter Müller,Werner Stephan,and Markus Ullmann,editors,Proceed-ings of the1st International Conference on Security in Pervasive Com-puting,number2082in Lecture Notes in Computer Science,Boppard,Germany,March2002.Springer.[BH00]Levente Buttyan and Jean-Pierre Hubaux.Enforcing Service Availability in Mobile Ad-Hoc WANs.In IEEE/ACM Workshop on Mobile Ad HocNetworking and Computing(MobiHOC),2000.[BH01]Levente Buttyan and Jean-Pierre Hubaux.Nuglets:a Virtual Currency to Stimulate Cooperation in Self-Organized Mobile Ad Hoc Networks.Technical report,EPFL Lausanne,Switzerland,2001.[BH03]Levente Buttyán and Jean-Pierre Hubaux.Stimulating cooperation in self-organizing mobile ad hoc networks.Mobile Networks and Applica-tions,8(5):579–592,2003.[Bha97]Vaduvur Bharghavan.Challenges and solutions to adaptive computing and seamless mobility over heterogeneous wireless networks.WirelessPersonal Communications,4(2):217–256,1997.[BHE00]Nirupama Bulusu,John Heidemann,and Deborah Estrin.GPS-less low cost outdoor localization for very small devices.IEEE Personal Commu-nications Magazine,7(5):28–34,October2000.[Bir93]Kenneth P.Birman.The process group approach to reliable distributed munications of the ACM,36(12):37–53,1993.[Bit05].Domain names disputes,2005.Available online at http: ///internet/domain.html#disputes.314Bibliography [BJ87]K.P.Birman and T.A.Joseph.Reliable Communication in the Pres-ence of Failures.ACM Transactions on Computer Systems,5(1):47–76,February1987.[BJM+91]M.Banâtre,Ph.Joubert,Ch.Morin,G.Muller, B.Rochat,and P.Sanchez.Stable transactional memories and fault tolerant architec-tures.SIGOPS Operating Systems Review,25(1):68–72,1991.[BK02]H.-B.Bludau and A.Koop,editors.Proceedings2nd Conf.on Mo-bile Computing in Medicine,Workshop of the Project Group MoCoMed,rmatik&GI-Fachausschuss4.7,Heidelberg,vol-ume15of LNI.GI,2002.[BKM+04]Jan Beutel,Oliver Kasten,Friedemann Mattern,Kay Römer,Frank Siegemund,and Lothar Thiele.Prototyping Wireless Sensor NetworkApplications with BTnodes.In1st European Workshop on Wireless Sen-sor Networks(EWSN),pages323–338,Berlin,Germany,January2004.Springer.[BKW02]J.Baus,A.Krüger,and W.Wahlster.A Resource-Adaptive Mobile Nav-igation System.In Proceedings of International Conference on IntelligentUser Interfaces IUI2002.ACM Press,2002.[BM04]Jürgen Bohn and Friedemann Mattern.Super-Distributed RFID Tag Infrastructures.In Panos Markopoulos,Berry Eggen,Emile Aarts,andJames Crowley,editors,Proceedings of the2nd European Symposium onAmbient Intelligence(EUSAI2004),Eindhoven,The Netherlands,num-ber3295in Lecture Notes in Computer Science,pages1–12.Springer,November2004.[BMF+00]Wolfram Burgard,Mark Moors,Dieter Fox,Reid Simmons,and Sebas-tian Thrun.Collaborative Multi-Robot Exploration.In Proceedings ofthe IEEE International Conference on Robotics and Automation(ICRA),2000.[Boh03]Jürgen Bohn.Exploiting Heterogeneity in Ubiquitous Computing En-vironments for Robust Positioning and Localization.Workshop onLocation-Aware Computing at Ubicomp2003,October2003.[Boh04a]Jürgen Bohn.Instant Personalization and Temporary Ownership of Handheld Devices.In Proceedings of the6th IEEE Workshop on Mo-bile Computing Systems&Applications(WMCSA2004),pages134–143,Windermere,Cumbria,UK,December2004.IEEE Computer SocietyPress,Los Alamitos,California.[Boh04b]Jürgen Bohn.The Smart Jigsaw Puzzle Assistant:Using RFID Tech-nology for Building Augmented Real-World Games.Workshop on Gam-ing Applications in Pervasive Computing Environments at PERVASIVE2004,Vienna,Austria,April2004.Available online at http://www.ipsi.fraunhofer.de/ambiente/pervasivegaming/.315Bibliography[Boh06]Jürgen Bohn.Prototypical Implementation of Location-Aware Services based on Super-Distributed RFID Tags.In Proceedings19th InternationalConference on Architecture of Computing Systems(ARCS’06),number3894in Lecture Notes in Computer Science,pages69–83,Frankfurt amMain,Germany,March2006.Springer.[Boh07a]Jürgen Bohn.iPOS:A Fault-Tolerant and Adaptive Multi-Sensor Posi-tioning Architecture with QoS Guarantees.Sensor Review Journal,2007.Accepted for Publication.[Boh07b]Jürgen Bohn.Prototypical Implementation of Location-Aware Services based on a Middleware Architecture for Super-Distributed RFID Tag In-frastructures.Personal and Ubiquitous Computing,2007.In Press.Onlineversion available at /10.1007/s00779-006-0107-2. [BP00]P.Bahl and V.N.Padmanabhan.RADAR:An in-building RF-based user location and tracking system.In INFOCOM2000,pages775–784,2000.[BR01]Jürgen Bohn and Michael Rohs.Klicken in der realen Welt.In Konferenz Mensch und Computer2001.Workshop Mensch-Computer-Interaktionin allgegenwärtigen Informationssystemen.Michael Beigl,Hans-WernerGellersen,and Norbert Streitz,Bad Honnef,Bonn,March2001.Avail-able online at /mc2001/.[Bre03]Elizabeth A.Bretz.Precision navigation in European skies.IEEE Spec-trum,40(9):16,September2003.[BS06]Bluetooth –The Official Bluetooth Membership Site.,February2006.[Bur05]Martin Burri.LuxTraceRT:A Self-Calibrating Real-Time Positioning System using Solar Cells as Main Sensory Input.Semester thesis,Dis-tributed Systems Group,ETH Zürich,Switzerland,October2005. [BV03]Jürgen Bohn and Harald Vogt.Robust Probabilistic Positioning based on High-Level Sensor-Fusion and Map Knowledge.Technical Report421,Institute for Pervasive Computing,Department of Computer Science,ETH Zurich,Switzerland,April2003.[BWLW04]Bharat Bhargava,Xiaoxin Wu,Yi Lu,and Weichao Wang.Integrat-ing heterogeneous wireless technologies:a cellular aided mobile ad hocnetwork(cama).Mobile Networks and Applications,9(4):393–408,2004. [Cas02]Henri Casanova.Distributed computing research issues in grid comput-ing.SIGACT News,33(3):50–70,2002.[CBM04]Vlad Coroama,Jürgen Bohn,and Friedemann Mattern.Living in a Smart Environment–Scenarios and Implications of the Coming Ubiqui-tous Information Societyi.In Proceedings of the International Conferenceon Systems,Man and Cybernetics2004(IEEE SMC2004),volume6,pages5633–5638,The Hague,The Netherlands,October2004.316Bibliography [CCR+04]Y.Chen,X.Y.Chen,F.Y.Rao,X.L.Yu,Y.Li,and D.Liu.LORE: An infrastructure to support location-aware services.IBM Journal ofResearch and Development,48(5/6):601–616,2004.[CCS99]Dryer D.C.,Eisbach C.,and Ark W.S.At what cost pervasive?a social computing view of mobile computing systems.IBM Systems Journal,38(4):652–676,1999.[CDG+02]Miguel Castro,Peter Druschel,Ayalvadi Ganesh,Antony Rowstron, and Dan S.Wallach.Secure routing for structured peer-to-peer overlaynetworks.SIGOPS Operating Systems Review,36(SI):299–314,2002. [CDK00]G.Coulouris,J.Dollimore,and T.Kindberg.Distributed Systems-Con-cepts and Design.Addison-Wesley,3rd edition,2000.[CGN+05]Jason Campbell,Phillip B.Gibbons,Suman Nath,Padmanabhan Pillai, Srinivasan Seshan,and Rahul Sukthankar.IrisNet:an internet-scalearchitecture for multimedia sensors.In MULTIMEDIA’05:Proceedingsof the13th annual ACM international conference on Multimedia,pages81–88,New York,NY,USA,2005.ACM Press.[CH04]Vlad Coroama and Norbert Höckl.Pervasive Insurance Markets and their Consequences.In1st International Workshop on Sustainable PervasiveComputing at PERVASIVE2004,Vienna,Austria,April2004.[CJ02]P.Chandrasekaran and A.Joshi.MobileIQ:a framework for mobile in-formation access.In Proceedings3rd International Conference on MobileData Management,pages43–50,January2002.[CK00]G.Chen and D.Kotz.A Survey of Context-Aware Mobile Computing Re-search.Technical Report TR2000-381,Department of Computer Science,Dartmouth College,November2000.[CK03] C.-Y.Chong and S.P.Kumar.Sensor networks:evolution,opportunities, and challenges.Proceedings of the IEEE,91(8):1247–1256,August2003. [CKR04]Vlad Coroama,Tarik Kapic,and Felix Röthenbacher.Improving the reality perception of visually impaired through pervasive computing.InAlois Ferscha,Horst Hoertner,and Gabriele Kotsis,editors,Advancesin Pervasive Computing,pages369–376,Vienna,Austria,April2004.Austrian Computer Society(OCG).[CLMZ03]G.Cabri,L.Leonardi,M.Mamei,and F.Zambonelli.Location-dependent services for mobile users.IEEE Transactions on Systems,Man and Cybernetics,33(6):667–681,November2003.[CN02]M.D.Corner and B.D.Noble.Zero-interaction authentication.In Pro-ceedings8th Annual International Conference on Mobile computing andnetworking,pages1–11.ACM Press,2002.[Cor06]Vlad Coroama.The Smart Tachograph–Individual Accounting of Traffic Costs and its Implications.In Proceedings of PERVASIVE2006,pages135–152,Dublin,Ireland,May2006.317Bibliography[CR03]Vlad Coroama and Felix Röthenbacher.The Chatty Environment–Providing Everyday Independence to the Visually Impaired.Workshopon Ubiquitous Computing for Pervasive Healthcare Applications at Ubi-Comp2003,October2003.[CR04]Vlad Coroama and Felix Röthenbacher.The Chatty Environment.In Demo at the Second Conference on Pervasive Computing and Communi-cations(PerCom2004),Orlando,Florida,March2004.[CRC05]Shiva Chetan,Anand Ranganathan,and Roy Campbell.Towards Fault Tolerant Pervasive Computing.IEEE Technology and Society,24(1):38–44,2005.[CSG99] D.Chen,A.Schmidt,and H.-W.Gellesen.An Architecture for Multi-Sensor Fusion in Mobile Environments.In Proceedings of the Interna-tional Conference on Information Fusion,Sunnyvale,CA,USA,vol-ume II,pages861–868,July1999.[DA00]Anind K.Dey and Gregory D.Abowd.Towards a Better Understanding of Context and Context-Awareness.In Workshop on The What,Who,Where,When,and How of Context-Awareness,Part of the Conferenceon Human Factors in Computing Systems(CHI2000),The Hague,TheNetherlands,April2000.[DAS01] A.Dey,G.D.Abowd,and D.Salber.A conceptual framework and a toolkit for supporting the rapid prototyping of context-aware applica-tions.Human-Computer Interaction,16(2–4):97–166,2001.[DCME01]N.Davies,K.Cheverst,K.Mitchell,and ing and Deter-mining Location in a Context-Sensitive Tour Guide.IEEE Computer,34(8):35–41,August2001.[Der02]Michael L.Dertouzos.Human-centered systems.In The invisible future: the seamless integration of technology into everyday life,pages181–191.McGraw-Hill,Inc.,New York,NY,USA,2002.[Dev04]Device Independence Working Group(DIWG).Composite Capabil-ity/Preference Profiles(CC/PP):Structure and Vocabularies1.0.W3CRecommendation,January2004.[Dey01]Anind K.Dey.Understanding and Using Context.Personal and Ubiqui-tous Computing,5(1):4–7,2001.[DH98] F.Dawson and T.Howes.vCard MIME Directory Profile.Internet RFC2426,September1998.[dI01]Diego López de Ipiña.Video-Based Sensing for Wide Deployment of Sentient Spaces.In Proceedings of the2nd PACT2001Workshop onUbiquitous Computing and Communications,September2001.[Dic56]Philip K.Dick.Minority Report.Fantastic Universe,January1956. 318Bibliography [dLKWZ03]E.de Lara,R.Kumar,D.S.Wallach,and W.Zwaenepoel.Collab-oration and multimedia authoring on mobile devices.In Proceedings ofMobiSys2003,San Francisco,USA,May2003.[DM04] F.DePaoli and L.Mariani.Dependability in peer-to-peer systems.IEEE Internet Computing,8(4):54–61,2004.[DNH04]Domain Name Handbook.Domain Dispute Index,2004.Available online at /dd.html.[Dom04]Svetlana Domnitcheva.Smart Vacuum Cleaner–An Autonomous Location-Aware Cleaning Device.In Adjunct Proceedings of UbiComp2004,September2004.[DS98] F.Dawson and D.Stenerson.Internet Calendaring and Scheduling Core Object Specification(iCalendar).Internet RFC2445,November1998. [EC03]European Commission.The Galilei Project:GALILEO Design Consolidation.http://europa.eu.int/comm/dgs/energy_transport/galileo/doc/,August2003.[EC05]European Commission.Galileo project webpage.http://www.europa.eu.int/comm/dgs/energy_transport/galileo/index_en.htm,July2005.[ECPS02]Deborah Estrin,David Culler,Kris Pister,and Gaurav Sukhatme.Con-necting the Physical World with Pervasive Networks.IEEE PervasiveComputing–Mobile and Ubiquitous Systems,1(1):59–69,January2002. [EGHK99]Deborah Estrin,Ramesh Govindan,John Heidemann,and Satish Ku-mar.Next century challenges:scalable coordination in sensor networks.In MobiCom’99:Proceedings of the5th annual ACM/IEEE interna-tional conference on Mobile computing and networking,pages263–270.ACM Press,1999.[EKM04]Virantha Ekanayake,Kelly Clinton IV,and Rajit Manohar.An ultra low-power processor for sensor networks.In ASPLOS-XI:Proceedings of the11th international conference on Architectural support for programminglanguages and operating systems,pages27–36,New York,NY,USA,2004.ACM Press.[Ele06]Electronic Frontier Foundation.Blue Ribbon Campaign.Defending Free-dom in the Digital /br/,February2006.[Elf89]Alberto ing occupancy grids for mobile robot perception and navigation.IEEE Computer,22(6):46–57,June1989.[Eur06]Eurocontrol.World Geodetic System1984.Homepage at , 2006.[Fal02]M.A.C.Fallon.Handheld Devices:Toward a More Mobile Campus.Syllabus Magazine,November2002.319[FBDT99]D.Fox,W.Burgard,F.Dellaert,and S.Thrun.Monte Carlo Local-ization:Efficient Position Estimation for Mobile Robots.In Proceedingsof the National Conferenceon Artificial Intelligence.AAAI Press/TheMIT Press,1999.[FBKT00]D.Fox,W.Burgard,H.Kruppa,and S.Thrun.A Probabilistic Ap-proach to Collaborative Multi-Robot Localization.Autonomous Robots,8(3):325–344,2000.[FBT99] D.Fox,W.Burgard,and S.Thrun.Markov Localization for Mobile Robots in Dynamic Environments.Journal of Artificial Intelligence Re-search,11:391–427,November1999.[FHL+03]D.Fox,J.Hightower,L.Liao,D.Schulz,and G.Borriello.Bayesian filtering for location estimation.IEEE Pervasive Computing,2(3):24–33,July-September2003.[FIB95]George W.Fitzmaurice,Hiroshi Ishii,and William A.S.Buxton.Bricks: laying the foundations for graspable user interfaces.In CHI’95:Proceed-ings of the SIGCHI conference on Human factors in computing systems,pages442–449.ACM Press/Addison-Wesley Publishing Co.,1995. [Fin03]K.Finkenzeller.RFID Handbook:Fundamentals and Applications in Contactless Smart Cards and Identification.John Wiley&Sons,2ndedition edition,April2003.[Fit93]George W.Fitzmaurice.Situated Information Spaces and Spatially Aware Palmtop munications of the ACM,36(7):38–49,July1993.[FJB+04]Richard Fairhurst,Ben Jameson,Andrew Bolt,Robert Brown,and Matthew Slattery.Geowiki-a map which you can annotate.Home-page at ,2004.[FKSK02]M.Funabashi,K.Kawano,S.Sameshima,and H.Kato.Middle-ware technology for ubiquitous computing:Aya(context-aware and yetanother service)that permits autonomous collaboration on super dis-tributed objects.In Proceedings IEEE International Conference on Sys-tems,Man and Cybernetics,volume2,pages623–628,October2002. [FKT01]Ian Foster,C.Kesselman,and S.Tuecke.The Anatomy of the Grid: Enabling Scalable Virtual Organizations.Intl.Journal SupercomputerApplications(IJSA),15(3),2001.[FL04]Christian Flörkemeier and Matthias Lampe.Issues with RFID usage in ubiquitous computing applications.In Proceedings PERVASIVE2004,number3001in Lecture Notes in Computer Science,pages188–193,Linz/Vienna,Austria,April2004.Springer.[FL05a]Marco Feriencik and Matthias Leumann.iPOS:Ein adaptives System zur Selbst-Positionierung von mobilen ressourcenbeschränkten Geräten.Semester thesis,Institute for Pervasive Computing,Department of Com-puter Science,ETH Zurich,Switzerland,June2005.320[FL05b]Christian Flörkemeier and Matthias Lampe.RFID middleware design -addressing application requirements and RFID.In Proceedings sOc-EUSAI2005(Smart Objects Conference),Grenoble,France,October2005.[FLP85]Michael J.Fischer,Nancy A.Lynch,and Michael S.Paterson.Impos-sibility of distributed consensus with one faulty process.Journal of theACM,32(2):374–382,April1985.[FLSC04]Michal Feldman,Kevin Lai,Ion Stoica,and John Chuang.Robust in-centive techniques for peer-to-peer networks.In EC’04:Proceedings ofthe5th ACM conference on Electronic commerce,pages102–111,NewYork,NY,USA,2004.ACM Press.[Fos02]Ian Foster.The Grid:A New Infrastructure for21st Century Science.Physics Today,55(2):42,February2002.[FS99]Jason Flinn and Mahadev Satyanarayanan.Energy-aware adaptation for mobile applications.In SOSP’99:Proceedings of the seventeenth ACMsymposium on Operating systems principles,pages48–63,New York,NY,USA,1999.ACM Press.[FS04]Jason Flinn and Mahadev Satyanarayanan.Managing battery lifetime with energy-aware adaptation.ACM Transactions on Computer Systems,22(2):137–179,2004.[FZ94]G.H.Forman and J.Zahorjan.The challenges of mobile computing.IEEE Computer,27(4):38–47,April1994.[Gal04]RenéGallati.Anpassung eines probabilistischen Positionierungsdien-stes für die Verwendung mit mobilen ressourcenbeschränkten Geräten.Semester thesis,Institute for Pervasive Computing,Department of Com-puter Science,ETH Zurich,Switzerland,November2004.[Gär99] F.C.Gärtner.Fundamentals of fault-tolerant distributed computing in asynchronous environments.ACM Computing Surveys(CSUR),31(1):1–26,1999.[Gar05a]Gartner,Inc.Gartner Says Strong Fourth Quarter Sales Led Worldwide Mobile Phone Sales to30Percent Growth in2004.Gartner Press Release,2.March2005.Available online at /press_releases/asset_121402_11.html.[Gar05b]Gartner,Inc.Gartner Says Wireless E-Mail Applications Drive World-wide PDA Shipments Increase25Percent in First Quarter of2005.Gartner Press Release,4.May2005.Available online at http://www./press_releases/asset_126216_11.html.[GBPK02]J.Glas,M.Banu,V.Prodanov,and P.Kiss.Wireless LANs.In Pro-ceedings of the Workshop on Advances in Analog Circuit Design,March2002.321[GDL+04]Robert Grimm,Janet Davis,Eric Lemar,Adam Macbeth,Steven Swan-son,Thomas Anderson,Brian Bershad,Gaetano Borriello,Steven Grib-ble,and David Wetherall.System support for pervasive applications.ACM Transactions on Computer Systems,22(4):421–486,2004.[Geg04]Christian Gegenschatz.Zuverlässige Patientenüberwachung in einer Ubiquitous-Computing-Umgebung.Diplomarbeit,Institute for PervasiveComputing,Department of Computer Science,ETH Zurich,Switzerland,June2004.[Gel98]Hans-Werner Gellersen.Environment-Mediated Communication.In-ternational Workshop on Interactive Applications of Mobile Computing(IMC’98),1998.[Ger98]Lou Gerstner.Keynote Speech at CeBIT’98in Hanover,Germany,18.March1998.[Get93]I.Getting.The Global Positioning System.IEEE Spectrum30,12:36–47, December1993.[GGE+05]Deepak Ganesan,Ben Greenstein,Deborah Estrin,John Heidemann, and Ramesh Govindan.Multiresolution storage and search in sensornetworks.ACM Transactions on Storage,1(3):277–315,2005.[GHM99]K.Goto,Matsubara H.,and S.Myojo.A mobile guide system for vi-sually disabled persons.In Proceedings4th International Symposium onAutonomous Decentralized Systems,pages12–17,March1999.[GK00]P.Gupta and P.R.Kumar.The capacity of wireless networks.IEEE Transactions on Information Theory,46(2):388–404,March2000. [GKK+03]Phillip B.Gibbons,Brad Karp,Yan Ke,Suman Nath,and Srinivasan Seshan.IrisNet:An Architecture for a World-Wide Sensor Web.IEEEPervasive Computing,October–November:22–33,2003.[GLHB03]David Graumann,Walter Lara,Jeffrey Hightower,and Gaetano Bor-riello.Real-world implementation of the Location Stack:The UniversalLocation Framework.In Proceedings5th IEEE Workshop on Mobile Com-puting Systems&Applications(WMCSA2003),pages122–128.IEEEComputer Society Press,October2003.[GM02]Jean-Claude Geffroy and Gilles Motet.Design of Dependable Computing Systems.Kluwer Academic Publishers,2002.[Gon01]Daniel Jorge Viegas Gonçalves.Ubiquitous computing and AI towards an inclusive society.In WUAUC’01:Proceedings of the2001EC/NSFWorkshop on Universal Accessibility of Ubiquitous Computing,pages37–40.ACM Press,2001.[GS97]Rachid Guerraoui and AndréSchiper.Genuine atomic multicast.In Proceedings of the11th International Workshop on Distributed Algorithms(WDAG97),number1320in Lecture Notes in Computer Science,pages141–154.Springer-Verlag,September1997.322。
gossip 协议Gossip协议是一种用于在分布式系统中进行信息交换的协议。
它通过不断地将信息从一个节点传播到另一个节点,以达到保持节点状态一致性的目的。
该协议具有高度的容错性和可扩展性,因此在许多分布式系统中被广泛应用。
Gossip协议的基本思想是每个节点周期性地选择一些其他节点,随机地将自己的最新状态发送给这些节点,并接收来自这些节点的最新状态。
通过反复进行这种信息交换,每个节点都会逐渐了解到整个系统的最新状态。
在Gossip协议中,每个节点都有一个本地的状态信息,该信息可以是节点本身的状态,或者是它所维护的某个数据结构的状态。
节点周期性地选择一些与之通信的节点,并将自己的状态信息发送给它们。
同时,节点也会接收来自这些节点的状态信息,并与自己本地的状态信息进行比较。
如果接收到的状态信息比自己的新,则更新本地的状态信息。
Gossip协议的传播机制非常简单,每个节点都会随机地选择一些其他节点进行通信。
这种随机性使得Gossip协议具有较好的容错性和可扩展性。
即使系统中存在部分节点宕机或网络故障,也不会对整个系统的运行产生太大影响。
另外,Gossip协议还可以通过一些优化策略来提高性能。
例如,节点可以选择离自己较近的节点进行信息交换,从而减少网络延迟。
节点还可以动态地调整自己的邻居节点,以适应系统的变化。
Gossip协议的一个重要应用是在分布式数据库中,用于保持副本之间的一致性。
每个节点都维护一份数据的副本,并通过Gossip协议来传播修改操作。
通过不断地进行信息交换,所有节点最终会达到一致的状态。
总之,Gossip协议是一种高度容错和可扩展的分布式系统协议。
它通过随机选择节点进行信息交换,从而实现了节点状态的一致性。
在实际应用中,Gossip协议被广泛应用于分布式数据库、分布式存储系统和数据中心网络等领域。
随着分布式系统的不断发展,Gossip协议将在未来的分布式系统中扮演更重要的角色。
社交网络上的虚假信息传播和应对策略英语作文范文Title: The Spread of Misinformation on Social Networks and CountermeasuresIntroduction:In today's digital era, the rise of social networks has revolutionized the way we communicate, share information, and interact with one another. While social networks provide numerous advantages, they also serve as breeding grounds for the proliferation of misinformation. This essay will explore the various strategies employed to tackle the dissemination of false information on social networks.Body:1. Enhancing Media Literacy and Critical Thinking Skills:One of the most effective long-term strategies to combat the spread of misinformation is by empowering individuals with robust media literacy and critical thinking skills. Educational programs and campaigns aimed at teaching users how to identify reputable sources, fact-check information, and critically analyze content can play a crucial role in minimizing the impact of false information.2. Strengthening Fact-Checking Mechanisms:Collaboration between social media platforms, independent fact-checkers, and credible news organizations is essential to establish reliable fact-checking mechanisms. By actively identifying and debunking misinformation, these entities can prevent false narratives from gaining momentum on social networks. Social media platforms should also invest in automated tools that can detect and flag potential instances of misinformation for review.3. Promoting Algorithmic Transparency and Responsibility:Social media platforms employ complex algorithms that determine the content users see on their feeds. Ensuring algorithmic transparency and accountability is crucial to tackle the spread of misinformation. Platforms should provide clear explanations of how their algorithms work and how they prioritize content, while also disclosing any potential biases. Users should have more control over the content they are exposed to, allowing them to make informed decisions about the trustworthiness of the information.4. Encouraging User Responsibility and Digital Citizenship:To combat the spread of misinformation, social network users must also take responsibility for their own actions. Encouraging digital citizenship and promoting responsible online behavior are essential. Users should be educated on the potential consequences of sharing unverified information and understand their role in being part of the solution.Emphasizing the importance of verifying information before sharing it can significantly reduce the spread of false narratives.5. Collaboration with Governments and Legislation:Governments play a vital role in addressing the spread of misinformation. Collaboration between social media platforms and lawmakers can lead to the establishment of effective legislation to combat online misinformation. By implementing regulations that hold platforms accountable for the content shared on their networks, governments can ensure that social media giants actively work to prevent and counter the dissemination of false information.Conclusion:Countering the spread of misinformation on social networks is a complex and multifaceted challenge. It requires a collaborative effort between social media platforms, fact-checking organizations, governments, and individualsthemselves. By promoting media literacy, strengthening fact-checking mechanisms, enhancing algorithmic transparency, fostering user responsibility, and implementing responsible legislation, we can build a more trustworthy and reliable online environment. Together, we can minimize the impact of misinformation and foster an informed society.。
gossip阅读理解Gossip,即流言蜚语,是人们在日常生活中经常会遇到的一种现象。
它指的是人们在没有确凿证据的情况下,通过传言或者口耳相传的方式,传播一些关于他人的私人事务或者隐私。
尽管有些人认为流言蜚语只是一种无害的娱乐方式,但实际上,它对个人和社会都可能带来负面影响。
首先,流言蜚语可能会对个人造成伤害。
当一个人成为流言的对象时,他们可能会受到他人的误解和指责。
这种误解和指责可能会导致个人形象的受损,甚至对其心理健康产生负面影响。
此外,流言蜚语还可能导致人际关系的破裂,因为它会破坏人们之间的信任和友谊。
当一个人发现自己被朋友或亲人背后议论时,他们可能会感到失望和伤心,从而导致关系的疏远。
其次,流言蜚语对社会也会带来一系列问题。
首先,它可能会导致社会的不稳定。
当流言蜚语传播得越来越广泛时,人们可能会对他人产生误解和偏见,从而导致社会的分裂和冲突。
其次,流言蜚语可能会对个人和组织的声誉造成损害。
一旦有关某个人或组织的流言蜚语传播开来,即使事实最终被证明是错误的,也很难恢复受损的声誉。
最后,流言蜚语还可能对个人的隐私权产生侵犯。
每个人都有权利保护自己的隐私,但流言蜚语的传播可能会泄露他人的私人信息,从而侵犯他们的隐私权。
然而,要解决流言蜚语问题并不容易。
首先,个人应该保持谨慎和理性。
在听到流言蜚语时,我们应该保持冷静,不要轻易相信。
我们应该学会辨别真假信息,不要盲目传播。
其次,媒体和社交平台也应该承担起责任。
他们应该加强对信息的审核和管理,避免传播虚假信息。
此外,教育也起着重要的作用。
学校和家庭应该教育孩子们要尊重他人的隐私,不要参与流言蜚语的传播。
总之,流言蜚语是一种普遍存在的现象,它对个人和社会都可能带来负面影响。
我们应该保持谨慎和理性,不要轻易相信和传播流言蜚语。
媒体和社交平台也应该加强信息审核和管理,避免传播虚假信息。
通过教育,我们可以培养出一个尊重他人隐私的社会氛围,减少流言蜚语的发生。
信息泛滥,如何管理注意力作者:卡斯滕·伦·彼泽森来源:《商业评论》2021年第03期在你阅读本文的这段时间里,你可能会下意识地查看一下自己的手机。
也许你注意到锁屏界面上跳出了邮件或短信通知,于是忍不住想知道是谁发来的消息。
一旦你开始浏览手机应用程序,就会自然而然地关注推特(Twitter)。
如果你将推特作为自己主要的媒体信息源,你也许会点击浏览有关区块链(block chain)或者巴巴多斯(Barbados)度假攻略的文章。
此时的你要是还能将注意力拉回到本文,我会感到很幸运。
尼古拉斯·卡尔(Nicholas Carr)在《浅薄:你是互联网的奴隶还是主宰者》(The Shallows: What the Internet Is Doing to Our Brains)一书中指出,瞬息万变的互联网正在劫持我们的专注力和思考力,让我们的行为出现了严重偏差。
这一观点我很难苟同。
更确切地说,我认为在当今职场上,人们无法阻挡喧嚣网络带来的诱惑,这是一个不能回避的现实。
在大数据迅猛发展和处理器日益强大的时代,我们必须以更快的速度吸收更多的信息。
无论你是思想家、管理人员抑或是创新者,都需要兼具两个看似相反的特质,如此方能在这个干扰不断、纷繁芜杂的世界中立于不败之地。
一方面,你必须从海量资源中获取各类信息,学会一心多用;另一方面,你又必须培养自己的专注力,做到一心一意。
我把这种看似二元对立实则高度统一的行为称作“分散集中悖论”(distraction-focus paradox)。
这两种特质看似水火不容,但它们组合而成的技能,却可以在高度互联时代管理你最宝贵的个人资源(即专注力)。
的确,这两种能力一直都很重要,而随着社交媒体和移动计算的不断发展,未来几年里这两种能力的组合将变得更加重要(副栏“互联世界的技能组合”介绍了这些基本技能的不同组合所产生的净效应)。
知识工作者需要多种多样的信息。
Share Anonymous Statistics IdeaIntroductionIn today’s data-driven world, collecting statistics plays a vital role in making informed decisions and analyzing trends. However, privacy concerns often arise when it comes to sharing data. One potential solution to this is the concept of sharing anonymous statistics. This article explores the benefits, challenges, and implementation strategies for sharing statistics while preserving anonymity.Why Share Anonymous Statistics?1.Benefit 1: Promoting Transparency–Sharing anonymous statistics allows organizations to be transparent about their data without compromising individualprivacy.–Publicly sharing statistics fosters trust and accountability by enabling others to verify claims and make data-drivendecisions.2.Benefit 2: Facilitating Research–Academics, researchers, and policymakers often require access to large-scale anonymized data to study trends,patterns, and make informed policy decisions.–Sharing anonymous statistics facilitates this research without exposing personal details or violating privacyregulations.3.Benefit 3: Empowering Individuals–Shared anonymous statistics enable individuals to compare their experiences and behaviors with broader populations,leading to self-improvement and behavioral changes.–For example, sharing anonymous statistics on energyconsumption helps individuals understand their consumptionpatterns in comparison to others and make necessaryadjustments.Challenges in Sharing Anonymous Statistics1.Challenge 1: Preserving Anonymity–Anonymizing data is crucial to protect individual identities, but it can be challenging to achieve complete anonymity.–Methods such as removing direct identifiers, aggregation, and noise addition can help minimize the risk of re-identification.2.Challenge 2: Data Quality and Accuracy–When sharing statistics, ensuring data quality and accuracy is essential for making reliable inferences.–Proper data cleaning, validation, and implementingstatistical standards are necessary to enhance data quality. 3.Challenge 3: Balancing Granularity–Striking a balance between providing detailed statistics and preserving anonymity is critical.–Aggregating data at an appropriate level ensures individual privacy while still providing meaningful insights.4.Challenge 4: Data Security–Safeguarding the shared anonymous statistics fromunauthorized access, breaches, or misuse is a significantconcern.–Implementing robust security measures, including encryption, access controls, and periodic monitoring, is vital toprotect the data.Strategies for Sharing Anonymous Statistics1.Strategy 1: Rigorous de-identification–Before sharing statistics, organizations must conduct a comprehensive de-identification process to reduce thepossibility of re-identification.–This involves removing or encrypting specific identifiers while maintaining data utility and preserving privacy.2.Strategy 2: Data Sharing Agreements–Establishing formal data sharing agreements with defined purposes and restrictions is crucial.–These agreements should outline the permitted use, access control mechanisms, and responsibilities of the entitiesinvolved.3.Strategy 3: Data Perturbation Techniques–Applying noise or perturbation techniques to the original data before sharing can further enhance privacy protection.–Differential privacy methods and k-anonymity techniques are commonly used to achieve a balance between privacy and datautility.4.Strategy 4: Transparency and Auditability–Organizations should provide transparency about theiranonymization processes to instill trust among data users.–Regular audits and third-party validation can ensurecompliance with privacy regulations and maintain theintegrity of shared statistics.5.Strategy 5: User Consent and Education–Obtaining informed consent from individuals before sharing their anonymized data is essential.–Educating data subjects about the purpose and benefits of sharing anonymous statistics helps build a consent-drivenframework.ConclusionSharing anonymous statistics offers numerous benefits, including increased transparency, facilitating research, and empowering individuals. However, challenges related to preserving anonymity, ensuring data quality, maintaining security, and balancing granularity need to be addressed. Implementing rigorous de-identification processes, establishing data sharing agreements, utilizing perturbation techniques, ensuring transparency, and obtaining user consent are key strategies for successful implementation. By overcoming these challenges and adopting appropriate strategies, organizations and individuals can harness the power of shared statistics while protecting individual privacy.。
Anonymous Gossip:Improving Multicast Reliability in Mobile Ad-Hoc Networks∗Ranveer Chandra Venugopalan Ramasubramanian Kenneth P.BirmanDepartment of Computer ScienceCornell University,Ithaca,NY14853,USA{ranveer,ramasv,ken}@AbstractIn recent years,a number of applications of ad-hoc net-works have been proposed.Many of them are based on the availability of a robust and reliable multicast protocol.In this paper,we address the issue of reliability and propose a scalable method to improve packet delivery of multicast routing protocols and decrease the variation in the number of packets received by different nodes.The proposed pro-tocol works in two phases.In thefirst phase,any suitable protocol is used to multicast a message to the group,while in the second concurrent phase,the gossip protocol tries to recover lost messages.Our proposed gossip protocol is called Anonymous Gossip(AG)since nodes need not know the other group members for gossip to be successful.This is extremely desirable for mobile nodes,that have limited resources,and where the knowledge of group membership is difficult to obtain.As afirst step,anonymous gossip is implemented over MAODV without much overhead and its performance is studied.Simulations show that the packet delivery of MAODV is significantly improved and the varia-tion in number of packets delivered is decreased.1.IntroductionAd-hoc networks are mobile networks that operate in the absence of anyfixed infrastructure,employing peer-to-peer communication to establish network connectivity.These networks have a wide range of applications such as disaster relief andfield operations,war front activities,and commu-nication between automobiles on highways.Group com-munication or multicast is a natural requirement for many of these applications and the reliability of the multicast pro-tocol could affect their performance significantly.Ad-hoc networks function under severe constraints such as mobility of nodes,insufficient power and memory on mobile devices, and bandwidth restriction of the wireless medium.These ∗The authors were supported in part by DARPA/AFRL-IFGA grant F30602-99-1-0532and in part by NSF-CISE grant9703470,with addi-tional support from the AFRL-IFGA Information Assurance Institute,from Microsoft Research and from the Intel Corporation.restrictions make the existing multicast routing protocols such as MAODV very unreliable even in moderately sized networks.This paper discusses our protocol,Anonymous Gossip,a scalable method for providing probabilistic guar-antees to multicast reliability in mobile ad-hoc networks.2.Multicast Reliability in Ad-Hoc NetworksSeveral protocols have been designed in recent years to address the issues of multicast routing in ad-hoc net-works.Approaches range from simple ideas such as se-lectiveflooding[13]to more complex protocols that main-tain knowledge of the network connectivity or dynamically gather route information.Many multicast protocols ap-proach the problem of multicast in ad-hoc networks by building and maintaining multicast trees or meshes to estab-lish connectivity among group members.MAODV[2]and AMRIS[8]are protocols that maintain multicast trees while ODMRP[10]and MCEDAR[6]are mesh-based.The mesh-based protocol,ODMRP[10]provides better packet deliv-ery than tree-based protocols but pays an extra cost for mesh maintenance.However,these protocols do not attempt to ensure packet delivery and packet loss is a problem during mesh/tree reconfiguration,a frequent repair activity.Fur-ther,the number of packets received by different members of a group is highly variable,with some members receiving very few packets while others receive almost all the packets even though the network may not be partitioned at that time.Multicast reliability in wired networks has received a lot of attention in the past years.Protocols such as SRM[3], RMTP[4]and PGM[5]focus on best effort reliability but are very scalable and easy to implement.These protocols, which are NACK-based(meaning that the receiver has the onus for initiating recovery)depend on the multicast rout-ing tree constructed by the Internet group multicast proto-col,IGMP.In ad-hoc networks,routes changes very rapidly and the methods used by these protocols are consequently not available to us.Bimodal Multicast[1]is another scal-able system,which uses gossip to provide probabilistic re-liability in wired networks.Our premise is that gossip is well matched to the needs of ad-hoc networks because it is a controlled form offlooding-messages are slowly prop-agated through the network without congesting the wire-less medium-and is independent of topology.This paper proposes a new method of gossip called anonymous gos-sip(AG),which does not require a group member to have any knowledge of the other group members.A multicast protocol based on anonymous gossip would proceed in two phases.In thefirst phase,packets are mul-ticast to the group using any unreliable multicast protocol. In the second phase,periodic anonymous gossip takes place in the background and ensures that most of the reachable members receive the packets.This method can be imple-mented on top of any of the tree-based and mesh-based pro-tocols with little or no overhead,and without affecting the scalability of the underlying protocol.In this paper,we dis-cuss our implementation of AG using MAODV as the un-derlying protocol.Simulation results show that using gos-sip over MAODV significantly increases the packet deliv-ery,while the variation in the number of packets received by different nodes decreases.3.Overview of AODV MulticastMAODV is a reactive protocol that dynamically creates and maintains a multicast tree for each group.It is an adap-tation of AODV,a unicast routing protocol.Due to con-straints of space,we present in this section a brief overview of only those aspects of MAODV relevant to our implemen-tation.A detailed description of MAODV can be found in [2][11].Each node running MAODV maintains two routing ta-bles:Route Table(RT)and Multicast Route Table(MRT). The Route Table is used for recording the next hop for routes to other nodes in the network.Each entry in RT con-tains a destination IP address,a destination sequence num-ber,hop count to the destination,IP address of next hop,and the lifetime of this entry.The destination sequence number tracks the freshness of the route to that destination.A source node S trying to send a message to a node B,first looks for a route to B in its RT.If a valid route is not found,S broad-casts a route request message called RREQ.A node receiv-ing this RREQ message can unicast a route reply RREP to S if it is the destination node or if it has a fresh enough route to B.Otherwise the node broadcasts the RREQ to its neighbors.The source node S selects the shortest among the freshest routes from the received RREPs and adds the entry in the Route Table.Nodes relaying the RREQs and the RREPS add the reverse and forward route entries into their Route Table respectively.The Multicast Route Table contains entries for multicast groups of which the node is a router(i.e.,a node in the mul-ticast tree).Each entry in this table contains the multicast group IP address,the group leader IP address,the group sequence number,hop count to the group leader,the next hops,and the lifetime.The next hops are the nodes in the multicast tree to which this node is connected.Each next hop entry has an enabledflag to indicate a potential but not yet activated entry.The next hop that is closer to the group leader is called the upstream node.A node S that is not a part of the multicast tree can join the multicast group by broadcasting a RREQ message with the joinflag set.Any node in the multicast tree can respond to a Join RREQ by unicasting an RREP back to S.These RREQs and RREPs are processed similar to unicast routing. In addition,nodes receiving Join RREQs also add entries with enabledflag false in their MRT.The node S selects a suitable route from the RREPs and sends an activation message called MACT along this route.All nodes receiving the MACT message change the enabledflag to true in their entries.Any group member,which is a leaf node in the multi-cast tree can leave the group by sending a MACT message to its upstream node with the pruneflag set.A node re-ceiving a Prune MACT deletes the sender from its next hop table.If it is a non-group member that has now become a leaf node,it leaves the group by sending a Prune MACT to its upstream node.Non-leaf nodes can leave a multicast group but must continue to function as routers in the multi-cast tree.When a link breakage occurs between two nodes U and D of a multicast tree,only the downstream node D attempts to repair this link.This restriction is necessary to prevent formation of loops.D sends an RREQ with an ex-tension containing the hop count to the group leader.Any multicast tree member closer to the group leader than D can reply to this RREQ.In case D receives no replies within a certain time even after a few rebroadcast of the RREQ,the network is assumed to be partitioned and a new group leader is selected in the downstream sub-tree.The details of how the new group leader is selected and how two partitioned trees can rejoin are described in[2][11].4.Anonymous Gossip ProtocolGossip as a general technique has been used to solve a number of problems such as network news dissemina-tion(NNTP),replicated data management[14]and failure detection[15].Bimodal multicast[1]uses gossip as a technique to achieve probabilistic reliability of multicast in wired networks.This protocol achieves a bimodal guaran-tee i.e.,all or no delivery with very high probability and partial delivery with very low probability,without sacrific-ing scalability and stable throughput(low jitter).We also use gossip to address the problem of reliable multicast in mobile ad-hoc networks and provide all or no delivery with very high probability and partial delivery with very low prob-ability.However,we use a different method of gossip to provide the same guarantees.A gossip based reliable multicast protocol involves two phases.In thefirst phase,any suitable unreliable protocol is used to multicast the message m,to be sent to the group. In the second phase,gossip is used to recover lost mes-sages from other members of the group that might have re-ceived it.This phase consists of periodically repeated gos-sip rounds in the background as more and more messages are multicast.A single gossip round can potentially recover many lost messages.A single round of gossip consists of the following steps,1.Node A randomly chooses another member of thegroup,say B.2.A sends B the information about messages it has re-ceived or not received.3.B checks to see if it has received any of the messageslisted by A.4.Then A and B could exchange messages which are nota part of each other’s message history.Posing such a broad algorithm in the form of a proto-col has to be done with meticulous care.The constraints of the environment have to be taken into account.As we have mentioned earlier,one of our primary goals is to pro-vide reliability without increasing the message overhead of the already congested mobile wireless environment.The following issues have to be answered keeping in mind the above constraints.1.How does node A know who the other members of thegroup are?2.How does A select which member to gossip with?3.What should be the direction of information exchange?4.How is the message history maintained?The following subsections describe these design issues in detail.4.1.Anonymous GossipIn our opinion,thefirst of the above questions is the most crucial issue.Bimodal multicast requires each participating node to have partial or total knowledge of group member-ship.This usually involves each node sending periodic heart beat messages to other nodes to keep the membership infor-mation current.In wired networks,where the nodes are in a domain sub-domain hierarchy,group membership can be maintained with limited overhead.However,in the wire-less environment maintaining even partial group member-ship is extremely expensive and would significantly reduce the throughput of the network.We propose a method called anonymous gossip(AG)to overcome this problem.AG does not require any member to know the other members of the multicast group.The node attempting to send a gossip mes-sage does not even know the identity of the node with which it will gossip until the other node sends back a gossip reply.We add a new type of message called gossip message. This message has the followingfivefields:/ Router Figure1.Local Anonymous Gossip in MAODV•Group Address:the address of the multicast group •Source Address:the address of the node sending thegossip message•Lost Buffer:an array offixed size,that carries se-quence numbers of messages that the source node be-lieves it has lost•Number Lost:the size of the Lost Array.•Expected Sequence Number:the sequence number of the next message that the source expects.Each node randomly selects one of its neighbors and sends a gossip message to it.Any node receiving a gossip message randomly selects one of its neighbors(excluding the neigh-bor which sent the message)and propagates the message to it.If the receiving node is itself a member of the multicast group then it randomly decides to either accept the gossip or propagate it.The accepting node then unicasts a gossip reply to the initiator of this gossip request.The reply is de-scribed in section4.4.In a general multicast protocol of an ad-hoc network,the nodes themselves participate as routers. Also,only a subset of these nodes/routers would participate in routing any messages meant for a given multicast group. In such cases,only participating routers are to be consid-ered while propagating the gossip message.For example, in the implementation of this protocol on MAODV,only the routers in the multicast tree participate in propagating the gossip.As have seen in section3,each router maintains a multicast route table which constitutes the nexthops for this router.While propagating the gossip message,one of these nexthops is randomly selected.Propagation along the mul-ticast tree prevents gossip messages from reaching the same node twice.4.2.Locality of GossipPeriodic propagation of gossip messages generates con-tinuous traffic on the network.Choosing nearer membersto gossip with will reduce the network traffic,howevergossiping with a distant node is extremely important be-cause sometimes message loss could affect an entire local-ity.Hence we need a scheme that would gossip locally witha very high probability and with distant nodes occasion-ally.Our AG protocol is augmented to achieve this opti-mization.Here,we assume some familiarity with MAODV, because the constraint of brevity prevents us from explain-ing MAODV in detail,and yet our algorithm builds uponit.We require each node participating as a router in the multicast tree to maintain one additionalfield called near-est member.In the implementation over MAODV,the mul-ticast route table is augmented to have this extrafield asso-ciated with each nexthop entry.The nearest memberfieldassociated with a nexthop contains the distance to the near-est group member from this node by taking the link throughthis nexthop node.This adds very little overhead to the ex-isting multicast route table.Whenever a gossip message is received,a nexthop node is chosen so that a nexthop with asmaller nearest member value is chosen with higher prob-ability than a nexthop with a larger nearest member value. Thus with higher probability the gossip message is propa-gated to a closer node than to a distant node.Figure1illus-trates an AODV Multicast Tree,where{A,C,D,H,I,J}are the group members and{B,E,F,G}are the other par-ticipating routers.The numbers shown on their edges give the values of the nearest memberfield.As an example,forthe router E,the nearest group member through D is at adistance1and through F is at a distance3.Maintaining the validity of the nearest memberfield in each router can be done with limited overhead.This valueneeds to be modified when one of the following events oc-curs-a new member joins the group,an existing mem-ber leaves the group,or the mobility of nodes creates atopology change.Whenever a new member joins the group or an existing member leaves the group,the routers near-est to this node realize the eventfirst.For example inMAODV a member sends a MACT message to establish itself while joining(see section3for details).A mem-ber leaving the group sends a prune message to its nearest routers.The nearest router adds this new nexthop to its mul-ticast route table with value of nearest memberfield set toone or deletes this entry from its list of nexthops.Then for each of the nexthops present in its table,it recomputes thevalue of nearest member and sends this modified value tothat nexthop.For example,if{B,C,E}are the next hop entries for node D,and{b,c,e}are the associated near-est member values for these nexthop entries,then D sends 1+min(c,e)to B,1+min(b,e)to C and1+min(b,c) to E.This value needs to be sent only if it is different fromits previous value.Also,this value can be piggy backed on any other messages bound for the same router.Whena router receives this new value,it updates this entry in its table.It then sends a modify message to its nexthops in the same way as described above.Since we are propagat-ing the minimum of a set of values,any change in topology or group membership will only affect the routers in its lo-cality.These modify messages will not propagate far and hence will not increase congestion significantly.4.3.Cached GossipAG is done only using the routers participating in the multicast tree.If these routers are not well distributed in the topology of the network,there is a possibility that a gos-sip message reaches a node along a route longer than the shortest existing route between these two nodes.For ex-ample,when using AG over MAODV,the gossip message propagates only along the multicast tree,although other, potentially shorter,routes may exist between the gossiping members(note that the return path is unaffected by this phe-nomenon,because gossip replies are unicast).It is efficient to use the unicast routes to gossip with those nodes whose membership is already known.Further,these unicast routes may be available for gossip even when the multicast tree is being repaired.We incorporate this by introducing a member cache in all the member nodes of each multicast group.The mem-ber cache is a bounded buffer containing entries which are3-tuples(node addr,numhops,last gossip).The node addrfield contains the address of a group member, the numhopsfield contains the shortest distance between the nodes and the last gossip contains the time at which last gossip occured between these two nodes.This information itself is collected at no extra cost.The member cache table is updated each time a message is received from a group member.This message could be a data packet meant for this group,a gossip reply,or any other maintenance packet. For example,in MAODV,each route request(RREQ)for a group join generates replies from a number of nodes,many of which are members of the group(see[11][2]for details). Whenever such a message is received,we add the member information to the member cache.If this table is full and a new member has to be added,a member with a greater numhops is deleted from this table.If there are no members with greater numhops then the member with most recent last gossip is replaced with the new entry.This is done to avoid frequent gossips with the same members.In each gossip round,the node chooses to do anonymous gossip with probability p anon.If AG is chosen,then a gos-sip message is constructed with the address of this node as the initiator and this message is propagated as described in section4.1and4.2.If cached gossip is chosen,then a mem-ber is selected randomly from the member cache and a gos-sip message is unicast to this member.When a gossip reply is received from a member,the member information is up-dated in the member cache.If this member already exists in this table,then the numhops and last gossipfields areupdated.Otherwise,the member is added to the table as described above.4.4.Push vs PullThe importance of direction of information exchange is explained in[14].Our protocol implements a pull mode of message exchange that may be described as follows.Each node maintains a table called lost table,for every multicast group that it belongs to.This contains the sequence num-bers of all the messages this node believes itself to be lack-ing.An entry in this table will be made whenever a mes-sage is received with a sequence number greater than the ex-pected sequence number.Note that the sequence number is a2tuple including the sender address and a sequence num-ber,because different senders send messages to the mul-ticast group.Each node also maintains a bounded FIFO buffer,called history table containing the most recent mes-sages received.The most recent entries of the lost table are placed in a lost buffer.Whenever a node prepares a gos-sip message,the lost buffer and a list of expected sequence numbers is added to the gossip message.When a node re-ceives a gossip message,it compares the lost buffer and the expected sequence number list to see if its history table has a copy of any message sought by the gossip initiator.It then unicasts any message found back to the gossip initiator as the gossip reply.5.Simulation and PerformanceWe simulated our protocol on GloMoSim[17],which uses a parallel,event-driven simulation language called PARSEC[18].MAODV was implemented as described in version5of the IETF draft[11]and was adapted to imple-ment our gossip protocol.We understand that more recent drafts of MAODV are available,but we believe that the ex-tensions would not impact performance for the scenarios investigated.5.1.Simulation EnvironmentAfixed area of200m×200m was used in the simulation, and all the nodes were initially placed randomly within this area.The simulations were performed using the Random-Waypoint scheme to model the mobility of the nodes in the network.In this model,each node has a predefined mini-mum and maximum speed.It then travels towards a ran-dom spot at a speed chosen randomly from this interval. After reaching the destination,it rests for a period chosen from a uniform distribution between0and80seconds,be-fore continuing this mobility pattern.Each simulation was set to run for10minutes.The MAC layer protocol used was IEEE802.11and the bandwidth of the wireless medium was assumed to be2Mbps.The network consisted of a single multicast group with one-third of the nodes being group members.All the nodes joined the group at the beginning of the simulation and re-mained in it throughout the run period.One of the members was selected as the source of data packets.The source node generated packets of length64bytes at regular intervals of 200ms with the destination as the multicast group.In the 600second simulation time,the source node continued to send packets starting at120seconds and ending at560sec-onds.The initial delay of120sec was allowed for MAODV to build the initial multicast tree.The source node generated 2201data packets during the period of interest.Every group member sends one gossip message per sec-ond.Each gossip message could request for at most10lost messages.The size of the membership cache was also set to10.Each member could keep track of at most200lost messages,in the lost table,and remember the most recent 100messages received in the history table.For MAODV, the hello interval was set to600ms,the allowed hello loss to4,and the group hello interval to5sec.We studied the performance of our protocol while vary-ing three parameters:the transmission range,the maximum speed and the number of nodes.The transmission range is the distance from a node within which another node can re-ceive packets from it.All the nodes are assumed to have the same transmission range.The minimum speed was set to0for all the runs.We varied each parameter over a wide range,for differentfixed values of the other two parame-ters.For each set of parameters,we measured the number of packets received by each node in the multicast group. Each simulation was carried out10times with different val-ues for the random-seed.The performance graphs measure the number of packets received by the group members during each run.Each data point in the graph corresponds to the average of the number of packets received by each group member.The range of measured data values obtained for the full set of receivers is shown in the form of error bars,while a line connects the average across receivers.Notice that reception rates can vary widely for different receivers because of differences in network connectivity.Perfect reception rates would be graphed as2201:the number of packets multicast by the source.5.2.Packet Delivery vs.Transmission RangeThe transmission range was varied from45m to85m in steps of5m,keeping the total number of nodes constant at 40.This experiment was carried out for6values of the maximum speed.Fig.2and Fig.3show the variation of packet delivery for maximum speeds0.2m/sec and2m/sec respectively for both MAODV and our gossip protocol.It is interesting to note that the gossip protocol consis-tently performs better than the underlying multicast pro-tocol.Not only is the average packet delivery higher but the variation in the number of packets received by different group members is also significantly lower.As the transmis-sion range increases,the connectivity of the network im-proves leading to fewer link failures.Further,the lengthFigure 2.Packet Delivery vs Transmission Range when the max speed=0.2m/secFigure 3.Packet Delivery vs Transmission Range when the max speed=2m/secof the network routes becomes shorter,decreasing the route discovery and setup time.The effect of this is reflected by the steady improvement in packet delivery of both gossip and MAODV with increase in the transmission range.How-ever,this runs a risk of increasing the congestion in the net-work,which could affect the performance of the protocols.5.3.Packet Delivery vs.Maximum SpeedThe maximum speed of the nodes was varied in two phases,from0.1m/sec to1m/sec in steps of0.1m/sec and from1m/sec to10m/sec in steps of1m/sec.The transmis-sion range was set constant at75m and the number of nodes wasfixed at40.Fig.4and Fig.5show variation of packet delivery with speed for both the phases.These graphs con-tinue to illustrate that our protocol achieves better packet delivery with a decreased variation in the number of pack-ets received by the group members.At very low values of maximum speed,upto0.3m/sec,our protocol gives near 100%packet delivery.At higher speeds,the data deliveryFigure4.Packet Delivery vs Maximum Speed when the transmission range is75mFigure5.Packet Delivery vs Maximum Speed when the transmission range is75mvaries from90%to80%.We can see a gradual decrease in data delivery as the maximum speed increases in this range. Increase in the maximum speed causes the nodes to move faster and more frequently in the random waypoint model. This causes an increase in the frequency of link breakages, affecting the overall performance of the system.5.4.Packet Delivery vs.Number of NodesThe number of nodes was varied from40to100.In one experiment,the transmission range was adjusted in such a way that the average number of neighbors of a node re-mained approximately the same.As the number of nodes in the network increases,the routing distance between the nodes goes up,and hence the frequency of link failures in the network also increases.Fig.6shows the variation of packet delivery with the increase in the number of nodes. As the number of nodes increases,the packet delivery rate tends to decrease gradually because of the above mentioned reasons.In another experiment,the transmission range was。