A Mobile Agent-based System for Dynamic Task Allocation in Clusters of Embedded Smart Camer
- 格式:pdf
- 大小:391.17 KB
- 文档页数:10
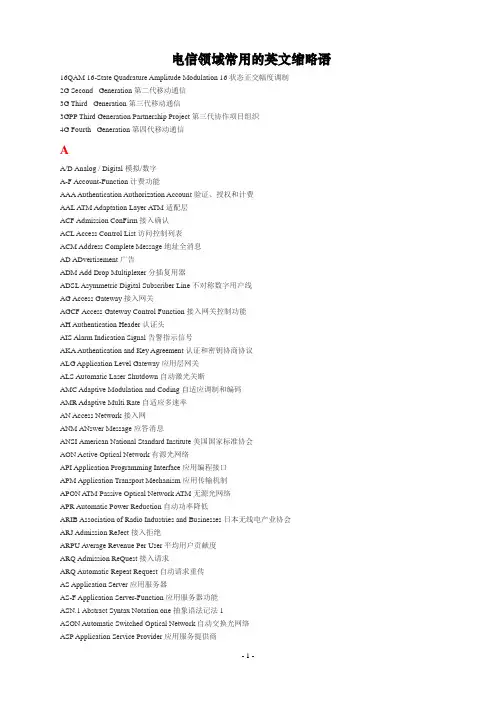
电信领域常用的英文缩略语16QAM 16-State Quadrature Amplitude Modulation 16状态正交幅度调制2G Second Generation 第二代移动通信3G Third Generation 第三代移动通信3GPP Third Generation Partnership Project 第三代协作项目组织4G Fourth Generation 第四代移动通信AA/D Analog / Digital 模拟/数字A-F Account-Function 计费功能AAA Authentication Authorization Account 验证、授权和计费AAL ATM Adaptation Layer ATM适配层ACF Admission ConFirm 接入确认ACL Access Control List 访问控制列表ACM Address Complete Message 地址全消息AD ADvertisement 广告ADM Add Drop Multiplexer 分插复用器ADSL Asymmetric Digital Subscriber Line 不对称数字用户线AG Access Gateway 接入网关AGCF Access Gateway Control Function 接入网关控制功能AH Authentication Header 认证头AIS Alarm Indication Signal 告警指示信号AKA Authentication and Key Agreement 认证和密钥协商协议ALG Application Level Gateway 应用层网关ALS Automatic Laser Shutdown 自动激光关断AMC Adaptive Modulation and Coding 自适应调制和编码AMR Adaptive Multi Rate 自适应多速率AN Access Network 接入网ANM ANswer Message 应答消息ANSI American National Standard Institute 美国国家标准协会AON Active Optical Network 有源光网络API Application Programming Interface 应用编程接口APM Application Transport Mechanism 应用传输机制APON A TM Passive Optical Network A TM无源光网络APR Automatic Power Reduction 自动功率降低ARIB Association of Radio Industries and Businesses 日本无线电产业协会ARJ Admission ReJect 接入拒绝ARPU Average Revenue Per User 平均用户贡献度ARQ Admission ReQuest 接入请求ARQ Automatic Repeat Request 自动请求重传AS Application Server 应用服务器AS-F Application Server-Function 应用服务器功能ASN.1 Abstract Syntax Notation one 抽象语法记法1ASON Automatic Switched Optical Network 自动交换光网络ASP Application Service Provider 应用服务提供商ASP Abstract Service Primitive 抽象业务原语ASTN Automatic Switched Transport Network 自动交换传输网A T Access Terminal 接入终端ATIS Alliance for Telecommunications Industry Solutions 电信业解决方案联盟ATM Asynchronous Transfer Mode 异步传输模式AUC AUthentication Center 鉴权中心BB-INAP Broadband-Intelligent Network Application Protocol 宽带智能网应用协议B-ISDN Broadband-Integrated Services Digital Network 宽带综合业务数字网B-ISUP Broadband-ISDN User Part 宽带ISDN用户部分B-SCE Broadband-Service Create Environment 宽带业务生成环境B-SCP Broadband-Service Control Point 宽带业务控制点B-SDP Broadband-Service Data Point 宽带业务数据点B-SMS Broadband-Service Manage System 宽带业务管理系统B-SSP Broadband-Service Switch Point 宽带业务交换点B-VPN Broadband Virtual Private Network 宽带虚拟专用网络B3G Beyond 3G 超3GBA Border Agent 边界代理BAS Broadband Access Server 宽带接入服务器BCF Bandwidth ConFirm 带宽确认BCF Bearer Control Function 承载控制功能BCMCS Broadcast and Multicast Service 广播和组播业务BCTP Bearer Control Tunneling Protocol 承载控制隧道协议BCU Bearer Control Unit 承载控制单元BcN Broadband Convergence Network 宽带融合网络BER Basic Encoding Rules 基本编码规则BG Border Gateway 边界网关BGCF Breakout Gateway Call Function 出口网关控制功能BGF Border Gateway Function 边界网关功能BGP Border Gateway Protocol 边界网关协议BHCA Busy Hour Call Attempts 忙时试呼次数BICC Bearer Independent Call Control 与承载无关的呼叫控制BICSCN Bearer Independent Circuit Switching Core Network 与承载无关的电路交换网络BIP Broadband Intelligent Peripheral 宽带智能外设BIS Bump In the Stack 栈内凸块BIWF Bearer InterWorking Function 承载互通功能BMAC Basic Media Access Control 基本媒体接入控制BMF Bearer Media Function 承载媒体功能BNC Backbone Network Connection 骨干网连接BNF Backus-Nayr Format Backus-Nayr形式BPON Broadband Passive Optical Network 宽带无源光网络BRAS Broadband Remote Access Server 宽带远程接入服务器BRJ Bandwidth ReJect 带宽拒绝BRQ Bandwidth Request 带宽请求BSC Base Station Controller 基站控制器BTS Base Transceiver Station 基站收发信台CC/S Client/Server 客户端/服务器CAC Connection Admission Control 连接允许控制CAMEL Customized Applications for Mobile Network 移动网增强逻辑的客户化应用CAP CAMEL Application Part CAMEL应用部分CAP Carrierless Amplitude and Phase Modulation 无载波幅相调制CATV CAble TeleVision 有线电视CBC Call Bearer Control 呼叫承载控制CBR Constant Bit Rate 固定比特率CCAMP Common Control and Measurement Plane 通用控制和测量平面CCI Connect Control Interface 连接控制接口CCM Call Control Management 呼叫控制管理CCNR Call Completion on No Reply 未应答的呼叫完成CCSA China Communications Standards Association 中国通信标准化协会CCU Call Control Unit 呼叫控制单元CCXML Call Control Extensible Markup Language 呼叫控制可扩展标识语言CDM Code Division Multiplexing 码分复用CDMA Code Division Multiple Access 码分多址接入CDR Call Detail Record 呼叫详细记录CDRS Call Detail Record Server 呼叫详细记录服务器CELP Code Excited Linear Prediction 码本激励线性预测CGI Common Gateway Interface 公共网关接口CIC Circuit Identification Code 电路识别码CIDR Classless Inter Domain Routing 无类域间路由选择CIF Common Intermediate Format 公共中间格式CIR Committed Information Rate 承诺信息速率CJK China Japan Korea 中日韩合作组织CLI Command Line Interface 命令行接口CLIP Calling Line Identification Presentation 主叫号码识别显示CLIR Calling Line Identification Restriction 主叫号码识别限制CLP Cell Loss Priority 信元丢失优先级CM Cable Modem 电缆调制解调器CMIP Common Management Information Protocol 通用管理信息协议CMISE Common Management Information Service Element 公用管理信息业务单元CMN Call Mediation Node 呼叫协调节点CN Core Network 核心网COPS Common Open Policy Service 公共开放策略业务CORBA Common Object Request Broker Architecture 公共对象请求代理结构CoS Class of Service 业务分类CPE Customer Premises Equipment 用户终端设备CPN Customer Premises Network 用户驻地网CPL Call Processing Language 呼叫处理语言CPS Character Per Second 每秒字符数CR-LDP Constraint-Based Routing Label Distribution Protocol 基于路由受限的标签分发协议CS Circuit Switched 电路交换CS-1 Capability Set 1 能力集1CSA Carrier Service Area 载波服务区CSCF Call Session Control Function 呼叫会话控制功能CSF Call Service Function 呼叫业务功能CSI Circuit Switched Interworking 电路交换域互通CSS Customer Service System 客户服务系统CSSNP Circuit-Switched Service Notification Protocol 电路交换业务通知协议CWDM Coarse Wave Division Multiplexer 稀疏波分复用CWTS China Wireless Telecommunication Standards 中国无线通信标准研究组DD/A Digital/Analog 数字/模拟DBA Dynamic Bandwidth Assignment 动态带宽分配DCF Disengage ConFirm 终止确认DCM Distributed Call and Connection Management 分布式呼叫和连接管理DCN Data Communication Network 数据通信网DCS Digital Cross-connect System 数字交叉连接DDN Digital Data Network 数字数据网DDoS Distributed Denial of Service 分布式拒绝服务DDRP Domain to Domain Routing Protocol 域到域路由协议DECT Digital Enhanced Cordless Telecommunication 数字增强型无绳通信DFE Decision Feedback Equalizer 判决反馈均衡器DFT Discrete Fourier Transform 离散傅里叶变换DHCP Dynamic Host Configuration Protocol 动态主机配置协议DiffServ Differentiated Service 区分服务DMT Discrete Multi-Tone 离散多音频DNS Domain Name Service 域名服务DNS-ALG DNS- Application Level Gateway 域名服务器-应用层代理网关DOPRA Distributed Object-oriented Programmable Real-time Architecture 分布式面向对象可编程实时构架DoS Denial of Service 拒绝服务DP Detection Point 检测点DRJ Disengage ReJect 终止拒绝DRQ Disengage ReQuest 终止请求DS-CDMA Direct Sequence-Code Division Multiple Access 直扩码分多址DSC Downlink Shared Channel 下行链路共享信道DSCP Differentiated Services Code Point DiffServ代码点DSL Digital Subscriber Line 数字用户线DSLAM Digital Subscriber Line Access Multiplexer 数字用户线接入复用器DSMP Data Service Management Platform 数据业务管理平台DSP Digital Signal Processor 数字信号处理器DSS1 Digital Subscriber Signaling No1 1号数字用户信令DSS2 Digital Subscriber Signaling No.2 2号数字用户信令DSTM Dual Stack Transition Mechanism 双协议栈过渡机制DTE Data Terminal Equipment 数据终端设备DTMF Dual Tone Multi Frequency 双音多频DU Distribution Unit 分配单元DVC Data V oice Conflux 数据语音合线DWDM Dense Wavelength Division Multiplexing 密集波分复用DXC Digital Cross Connection 数字交叉连接EE-NNI Exterior-Network Network Interface 外部网络-网络接口EAS Erisson Application Server 爱立信应用服务器ECC Embedded Control Channel 嵌入式控制信道EDFA Erbium Doped Fiber Amplifier 掺铒光纤放大器EDGE Enhanced Data rates for Global Evolution GSM演进增强数据速率EDSL Ethernet Digital Subscriber Line 以太网数字用户线EFM Ethernet in the First Mile 第一英里以太网EFMA Ethernet in the First Mile Alliance 第一英里以太网联盟EIR Equipment Identity Register 设备识别寄存器EIR Excessive Information Rate 额外信息速率EIRP Effective Isotropic Radiation Power 全向有效辐射功率EMF Element Management Function 单元管理功能EML Element Management Layer 网元管理层EMS Element Management System 网元管理系统ENUM E.164 NUMber and DNS E.164号码和域名系统EoVDSL Ethernet over VDSL 基于以太网技术的VDSLEPON Ethernet Passive Optical Network 以太网无源光网络ESCON Enterprise Systems Connection 企业系统互联ESE Expandable Switching Exchange 开放式可编程交换平台ESN Electric Sequence Number 电子序列号ESP Encapsulating Security Payload 封装安全载荷ETSI European Telecommunications Standards Institution 欧洲电信标准化委员会EUDCH Enhanced Uplink Dedicated Channel 增强的上行链路专用信道FF-SCH Forward-Supplemental Channel 前向辅助信道FCS Fast Cell Selection 快速蜂窝选择FCS Frame Check Sequence 帧检验序列FDD Frequency Division Duplex 频分双工FDDI Fiber Distributed Data Interface 光纤分布式数据接口FDM Frequency Division Multiplexing 频分复用FDMA Frequency Division Multiple Access 频分多址FE Fast Ethernet 快速以太网FFT Fast Fourier Transform 快速傅立叶变换FG NGN NGN Focus Group 下一代网络专题组FICON Fiber Connection 光纤互联FISU Fill-In Signal Unit 填充信号单元FITL Fiber In The Loop 环路光纤FMC Fixed Mobile Convergence 固定通信与移动通信融合FPBN Future Packet-Based Networks 未来分组网FPLMTS Future Public Land Mobile Telecommunication System 未来公众陆地移动通信系统FR Frame Relay 帧中继FSAN Full Service Access Networks 全业务接入网FSTP Fast Spanning Tree Protocol 快速生成树协议FTP File Transfer Protocol 文件传输协议FTTB Fiber To The Building 光纤到大楼FTTC Fiber To The Cabinet 光纤到接线柜FTTC Fiber To The Curb 光纤到路边FTTH Fiber To The Home 光纤到户FTTO Fiber To The Office 光纤到办公室GGE Gigabit Ethernet 千兆比特以太网GEM GPON Encapsulation Method GPON封装方法GEPON Gigabit Ethernet Passive Optical Network 千兆比特以太网无源光网络GERAN GSM/EDGE Radio Access Network GSM/EDGE无线接入网GFP Generic Framing Procedure 通用成帧规程GGSN Gateway GPRS Supporting Node GPRS网关支持节点GII Global Information Infrastructure 全球信息基础设施GMII Gigabit Media Independent Interface 千兆比特媒体无关接口GMSC Gateway Mobile Switching Center 网关移动交换中心GMPLS Generalized Multiple Protocol Label Switching 通用多协议标签交换GPON Gigabit Passive Optical Network 千兆比特无源光网络GPRS General Packet Radio Service 通用分组无线业务GRE Generic Routing Encapsulation 通用路由封装GSM Global System for Mobile Communication 全球移动通信系统GSN GPRS Supporting Nodes GPRS支持节点GSN Gateway Service Node 网关服务节点GSTN General Switched Telephone Network 普通电话交换网GTC GPON Transmission Convergence GPON传输汇聚层GTP GPRS Tunneling Protocol GPRS隧道协议GTT Globe Text Telephone 全球文本电话HHARQ Hybrid Automatic Repeat Request 混合自动请求重传HDLC High-level Data Link Control 高级数据链路控制HDR High Data Rate 高数据速率HDSL High Bit Rate Digital Subscriber Line 高比特率数字用户线HEC Header Error Check 帧头错误检验HFC Hybrid Fiber Coaxial 混合光纤同轴电缆网HLR Home Location Register 归属位置寄存器HS-DPCCH High Speed-Dedicated Physical Control CHannel 高速专用物理控制信道HS-DSCH High Speed-Downlink Shared CHannel 高速下行共享信道HS-SCCH High Speed-Shared Control CHannel 高速共享控制信道HSDPA High Speed Downlink Packet Access 高速下行链路数据分组接入HSPA High Speed Packet Access 高速数据分组接入HSS Home Subscriber Server 归属用户服务器HSUPA High Speed Uplink Packet Access 高速上行链路数据分组接入HTTP Hypertext Transfer Protocol 超文本传输协议II-CSCF Interrogating CSCF 查询CSCFI-NNI Inter-Network Network Interface 内部网络-网络接口IACK Information Request ACKnowledgement 信息请求确认IAD Integrated Access Device 综合接入设备IADMS Integrated Access Device Management System 综合接入设备管理系统IAM Initial Address Message 初始地址消息IANA Internet Assigned Numbers Authority 因特网编号分配部门IBCF Internet Border Control Function 因特网边界点控制功能ICMP Internet Control Message Protocol 因特网控制报文协议ICP Internet Content Provider 因特网内容提供商ICV Integrity Check Value 完整性校验值ICW Internet Call Waiting 因特网呼叫等待IDC Internet Data Center 因特网数据中心IEEE Institute of Electrical and Electronics Engineers 电子电气工程师协会IETF Internet Engineering Task Force 互联网工程任务组IKE Internet Key Exchange Internet密钥交换IM Instant Message 即时消息IM IP Multimedia IP多媒体IM-SSF IP Multimedia-Service Switching Function IP多媒体业务交换功能IMEI International Mobile Equipment Identifier 国际移动设备识别码IMS IP Multimedia Subsystem IP多媒体子系统IMTC International Multimedia Teleconferencing Consortium 国际多媒体电视会议联合会IN Intelligent Network 智能网INAP Intelligent Network Application Protocol 智能网应用协议INAK Information Request Negative AcKnowledgement 信息查询否认INES Intelligent Network Entrance System 智能网网关系统IntServ Integrated Service 综合服务ION Intelligent Optical Network 智能光网络IOS Interactive Operating System 交互式操作系统IP Internet Protocol 因特网协议IP Intelligent Peripheral 智能外设IP-CAN IP Connectivity Access Network IP接入网络IPBCP IP Bearer Control Protocol IP承载控制协议IPCC International PacketComm Consortium 国际分组通信论坛IPDC IP Device Control IP设备控制IPSec IP Security IP安全IPTV IP TeleVision IP电视IPX Internetwork Packet Exchange 网间分组交换IRQ Information ReQuest 信息请求IRR Information Request Response 信息请求响应IS-IS Intermediate System to Intermediate System Routing Protocol 中间系统到中间系统的路由选择协议ISC International Softswitch Consortium 国际软交换论坛ISC Internal Service Control 因特网业务控制ISCE Integrated Service Creation Environment 综合业务生成环境ISCP Integrated Service Control Point 综合业务控制点ISDN Integrated Services Digital Network 综合业务数字网ISDP Integrated Service Data Point 综合业务数据点ISIM IP Multimedia Service Identity Module IP多媒体业务身份模块ISMAP Integrated Service Management Access Point 综合业务管理接入点ISMP Integrated Service Management Point 综合业务管理点ISN Interface Service Node 接口服务节点ISO International Organization for Standardization 国际标准化组织ISP Internet Service Provider 因特网服务提供商ISSP Integrated Service Switching Point 综合业务交换点ISUP ISDN User Part 综合业务数字网用户部分IT Information Technology 信息技术ITU International Telecommunications Union 国际电信联盟ITU-T ITU Telecommunication Standardization Sector 国际电信联盟电信标准化组织IUA ISDN User Adaptation Layer ISDN用户适配层协议IVR Interactive V oice Response 交互式语音应答IWF InterWorking Function 互通功能JJ2EE Java 2 Platform Enterprise Edition Java 2平台企业版JAIN Java APIs for Integrated Networks 综合网络的Java APIsJRG Joint Rapporteur Group 课题报告联合起草小组LL2TP Layer2 Tunneling Protocol 第二层隧道协议LAC Link Access Control 链路接入控制LAN Local Area Network 局域网LAPS Link Access Protocol-SDH SDH链路接入协议LCAS Link Capacity Adjustment Scheme 链路容量调整机制LCR Low Chip Rate 低码片速率LDAP Lightweight Directory Access Protocol 轻量级目录访问协议LDP Label Distribution Protocol 标签分发协议LE Local Exchange 本地交换机LLID Logical Link Identification 逻辑链路标识LMDS Local Multipoint Distribution Services 本地多点分配业务LMP Link Management Protocol 链路管理协议LMT Local Maintenance Terminal 本地维护终端LRM Link Resource Manager 链路资源管理器LS Local Switch 本地交换局LSP Label Switch Path 标签交换路径LSSU Link Statues Signal Unit 链路状态信号单元LSW LAN SWitch 局域网交换机LT Line Terminal 线路终端MM2UA MTP 2 User Adaptation Layer MTP第二级用户适配层M3UA MTP 3 User Adaptation Layer MTP第三级用户适配层M2PA MTP 2 Peer-to-peer Adaptation Layer MTP第二级对等适配层MAC Medium Access Control 媒体接入控制MAI Multiple Access Interference 多址干扰MAN Metropolitan Area Network 城域网MAP Mobile Application Part 移动应用部分MBMS Multimedia Broadcast and Multicast Service 多媒体广播和组播MC Multi-point Controller 多点控制器MC-CDMA Multiple Carrier-Code Division Multiple Access 多载波码分多址MCF Media Control Function 媒体控制功能MCS Multimedia Communication Server 多媒体通信服务器MCS Multimedia Communication System 多媒体通信系统MCU Multi-point Control Unit 多点控制单元MDCP Media Device Control Protocol 媒体设备控制协议MEID Mobile Equipment Identifier 移动设备标识MFI Multiple Frame Indicator 复帧指示器MG Media Gateway 媒体网关MGC Media Gateway Controller 媒体网关控制器MGC-F Media Gateway Control-Function 媒体网关控制功能MGCF Media Gateway Control Function 媒体网关控制功能MGCP Media Gateway Control Protocol 媒体网关控制协议MG-F Media Gateway-Function 媒体网关功能MGU Media Gateway Unit 媒体网关单元MIME Multi-purpose Internet Mail Extension 多用途因特网邮件扩展MIMO Multiple Input Multiple Output 多输入多输出MIP Mobile IP 移动IPML-PPP Multi-Link Point to Point Protocol 多链路点对点协议MM Mobility Management 移动性管理MMDS Multi-channel Multi-point Distribution Services 多通道多点分配业务MML Man-Machine Language 人机语言MMS Multimedia Message Service 多媒体消息服务MMSF Media Mapping/Switching Function 媒体映射/交换功能MMUSIC Multiparty Multimedia Session Control 多方多媒体会话控制MP Multi-point Processor 多点处理器MPCP Multi-point Control Protocol 多点控制协议MPEG Moving Picture Expert Group 活动图象专家组MPLS Multi-Protocol Label Switching 多协议标签交换MRF Media Resource Function 媒体资源功能MRFC Media Resource Function Controller 媒体资源功能控制器MRFP Media Resource Function Processor 媒体资源功能处理器MRS Multimedia Resource Server 多媒体资源服务器MS Mobile Station 移动台MS Media Server 媒体服务器MS-F Media Server-Function 媒体服务器功能MSC Mobile Switching Center 移动交换中心MSID Mobile Station Identifier 移动台标识符MSP Multiplex Section Protection 复用段保护MSTP Multi-Service Transmission Platform 多业务传输平台MSU Message Signal Unit 消息信号单元MTA Message Transfer Agent 消息传输代理MTP Message Transport Part 消息传输部分MTU Maximum Transfer Unit 最大传输单元MUD Multiple User Detection 多用户检测NN-ISDN Narrowband-ISDN 窄带ISDNN-ISUP Narrowband-ISDN User Part 窄带ISDN用户部分NAPT Network Address Port Translation 网络地址端口转换NAS Network Access Server 网络接入服务器NASS Network Attachment Sub-System 网络附着子系统NA T Network Address Translation 网络地址转换NAT/PT Network Address Translation/Protocol Translation 网络地址转换/协议转换NE Network Element 网元NEL Network Element Layer 网元层NGI Next Generation Internet 下一代因特网NGN Next Generation Network 下一代网络NII National Information Infrastructure 国家信息基础设施NMI Network Management Interface 网络管理接口NMI-A Network Management Interface-A 网络管理接口ANMI-T Network Management Interface-T 网络管理接口TNMS Network Management System 网络管理系统NP Network Performance 网络性能NRT-VBR Non Real Time-Variable Bit Rate 非实时可变比特率NSAP Network Service Access Point 网络业务接入点NT Network Terminal 网络终端NTT Nippon Telegraph and Telephone Corporation 日本电话电报公司NU Network Unit 网络单元OOADM Optical Add Drop Multiplexer 光分插复用器OAM Operation Administration and Maintenance 运行、管理和维护OAM&P Operation Administration Maintenance and Provisioning 运行、管理、维护和配置OAN Optical Access Network 光接入网OBS On-line Billing System 在线计费系统ODN Optical Distribution Network 光配线网ODSI Optical Domain Service Interconnect 光域业务互连OEO Optical-Electrical-Optical Converter 光/电/光转换器OFC Optical Fiber Communications 光纤通信OFDM Orthogonal Frequency Division Multiplexing 正交频分复用OIF Optical Internetworking Forum 光因特网论坛OLS Optical Label Switching 光标签交换OLT Optical Line Terminal 光线路终端OMA Open Mobile Alliance 开放移动联盟OMC-R Operation and Maintenance Center-Radio 无线维护操作中心OMCI ONT Management and Control Interface 光网络终端管理与控制接口OMCI Operations Management Communications Interface 操作管理通信接口OMG Object Management Group 对象管理组ONLY One Number Links You 一号通ONNS Optical Network Navigation System 光网络导航系统ONU Optical Network Unit 光网络单元OPTIS Overlapped PAM Transmission with Interlocking Spectra 频谱互锁重叠的PAM传输OSA Open Service Architecture 开放的业务结构OSI Open Systems Interconnection 开放系统互连OSPF Open Shortest Path First 开放式最短路径优先OSS Operation Support Systems 运营支撑系统OSX Open Service Exchange 开放业务交换平台OTD Observation Time Difference 观察时间差OTN Optical Transport Network 光传输网络OVPN Optical Virtual Private Network 光虚拟专用网OXC Optical Cross Connect 光交叉连接PP-CSCF Proxy CSCF 代理CSCFP2MP Point to Multi-Point 点到多点PAM Pulse Amplitude Modulation 脉冲幅度调制PBN Packet Based Networks 分组网络PBS Polarization Beam Splitter 极化光束分离器PBX Private Branch eXchange 用户交换机PC Personal Computer 个人电脑PC Permanent Connection 永久性连接PCF Packet Control Function 分组控制功能实体PCM Pulse Code Modulation 脉冲编码调制PCS Physical Coding Sub-layer 物理编码子层PCS Personal Communication Service 个人通信业务PDF Policy Decision Function 策略判决功能PDN Packet Data Network 分组数据网PDP Policy Decision Point 策略决定点PDSN Packet Data Service Node 分组数据业务节点PDU Protocol Data Unit 协议数据单元PEP Policy Execution Point 策略执行点PER Packet Encoding Rules 分组编码规则PES PSTN Emulation Subsystem PSTN仿真子系统PHS Personal Hand-phone System 个人手持电话系统PI Physical Interface 物理接口PINT PSTN/Internet Internetworking PSTN与Internet的互通PLI PDU Length Indicator 协议数据单元长度指示符PLL Phase Locked Loop 锁相环PLMN Public Land Mobile Network 公用陆地移动网PLOAM Physical Layer OAM 物理层OAMPMA Physical Medium Attachment 物理媒体接入子层PMD Physical Medium Dependent 物理媒体相关子层PNNI Private Network-to-Network Interface 专用网间接口PoC Push to Talk over Cellular 无线一键通POH Path Overhead 通道开销PON Passive Optical Network 无源光网络POP Post Office Protocol 邮局协议PoS Packet over SDH SDH上的IP分组POS Passive Optical Splitter 无源光分路器POTS Plain Old Telephone Service 普通电话业务PPP Point to Point Protocol 点对点协议PPS Pre-Paid Service 预付费PR Packet Ring 分组环PRA Primary Rate Access 基群速率接入PRI Primary Rate Interface 基群速率接口PS Packet Switched 分组交换PSC Pre-paid Service Center 预付费业务中心PSE Personal Service Environment 个人业务环境PSTN Public Telephone Switched Network 公共交换电话网PTM Packet Transfer Mode 分组传输模式PTN Personal Telecommunications Number 个人通信号码PTT Push To Talk 一键通PVC Permanent Virtual Circuit 永久虚电路QQAM Quadrature Amplitude Modulation 正交幅度调制QCIF Quarter Common Intermediate Format 四分之一通用中间格式QIB Quality Indicator Bit 质量指示器位QoS Quality of Service 服务质量QPSK Quadrature Phase-Shift Keying 正交相移键控RR-SCH Reverse-Supplementary Channel 反向辅助信道R-SG Roaming Signaling Gateway 漫游信令网关RAB Reverse Activity Bit 反向激活比特RAC Resource Availability Confirm 资源可用确认RACS Resource and Admission Control Subsystem 资源与接入控制子系统RADIUS Remote Access Dial-In User Service 远程接入拨号用户业务RADSL Rate Adaptive Digital subscriber Line 速率自适应数字用户线路RAI Resource Availability Indication 资源可用指示RAN Radio Access Network 无线接入网RAS Registration Admission Status 注册、许可和状态RCF Registration ConFirm 注册确认REL Release 呼叫释放信息RFC Request For Comments 请求评论文档RG Residential Gateway 驻地网关RIP Request In Progress 请求进展RLP Radio Link Protocol 无线链路协议RLU Remote Line Unit 远端用户线单元RNC Radio Network Controller 无线网络控制器RNS Radio Network Subsystem 无线网络子系统RPR Resilient Packet Ring 弹性分组环RRJ Registration ReJect 注册拒绝RRQ Registration ReQuest 注册请求RSVP Resource Reservation Protocol 资源预留协议RSVP-TE Resource Reservation Protocol-Traffic Engineering 基于流量工程扩展的资源预留协议RTCP Real-time Transfer Control Protocol 实时传输控制协议RTP Real-time Transfer Protocol 实时传输协议RTSP Real-time Streaming Protocol 实时流媒体协议RTU Remote Terminal Unit 远方终端单元RT-VBR Real Time-Variable Bit Rate 实时可变比特率SS-CSCF Serving CSCF 服务CSCFSA Security Association 安全关联SA Smart Antenna 智能天线SACP Service Access Control Point 业务接入控制点SAD Security Association Database 安全关联数据库SAF Special Access Function 特定接入功能SAM Subscriber Application Management 用户应用管理系统SAM Subsequent Address Message 后续地址消息SC Switched Connection 交换式连接SC-F Signaling Conversion Function 信令转换功能SC-TDMA Single Carrier Time Division Multiple Access 单载波时分多址SCCP Signaling Connection control Part 信令连接控制部分SCE Service Creation Environment 业务生成环境SCEP Service Creation Environment Point 业务生成环境点SCF Service Control Function 业务控制功能SCM Sub-Carrier Multiplexing 副载波复用SCN Switched Circuit Network 电路交换网SCP Service Control Point 业务控制点SCS Service Capability Server 业务能力服务器SCTP Stream Control Transport Protocol 流控制传输协议SDF Service Data Function 业务数据功能SDH Synchronous Digital Hierarchy 同步数字系列SDL Simple Data Link 简单数据链路SDM Space Division Multiplexing 空分复用SDMA Space Division Multiple Access 空分多址SDP Service Data Point 业务数据点SDP Session Description Protocol 会话描述协议SDR Software Defined Radio 软件无线电SDSL Single Digital Subscriber Line 单线数字用户线SEP Signaling End Point 信令终结点SG Signaling Gateway 信令网关SGCP Simple Gateway Control Protocol 简单网关控制协议SGF Signaling Gateway Function 信令网关功能SGSN Serving GPRS Supporting Node GPRS服务支持节点SIB Service Independent Building Blocks 基于与业务无关的模块SIGTRAN Signaling Transport 信令传输协议SIIT Stateless IP/ICMP Translation 无状态IP/ICMP转换SIM Subscriber Identity Module 用户身份模块SIP Session Initiation Protocol 会话发起协议SIP-I SIP with Encapsulated ISUP 带有ISUP消息封装的SIP协议SIP-S SIP Servlet 应用于伺服系统的会话发起协议SIP-T Session Initiation Protocol for Telephone 应用于电话网的SIP协议SLA Service Level Agreement 服务等级协议SLF Subscriber Location Function 签约用户定位功能SLR Subscriber Location Router 用户位置路由器SMAP Service Management Access Point 业务管理接入点SMP Service Management Point 业务管理点SMS Service Management System 业务管理系统SMS Short Message Service 短消息业务SMTP Simple Mail Transfer Protocol 简单邮件传输协议SN Serving Node 服务节点SNC Sub-Network Connection 子网络连接SNCP Sub-Network Connection Protection 子网连接保护SNI Service Node Interface 业务节点接口SNMP Simple Network Management Protocol 简单网络管理协议SNR Signal to Noise Ratio 信噪比SOHO Small Office/Home Office 小办公室/家庭办公室SONET Synchronous Optical Network 光同步网SP Signaling Point 信令点SPAN Services and Protocols for Advanced Networks 高级网络的服务与协议SPC Soft Permanent Connection 软永久连接SPD Security Policy Database 安全策略数据库SPI Security Parameter Index 安全参数索引SPIRITS Service in the PSTN IN Requesting InTernet Service PSTN/IN请求因特网服务业务SPX Sequential Packet eXchange 序列分组交换SQ Sequence Indicator 序列指示器SRBP Signaling Radio Burst Protocol 信令无线突发协议SRF Specialized Resource Function 专用资源功能SRP Spatial Reuse Protocol 空间重用协议SS7 Signaling System 7 7号信令网SSF Service Switching Function 业务交换功能SSP Service Switching Point 业务交换点STC Space-Time Coding 空时编码STC Signaling Transport Converter 信令传输转换器STM Synchronous Transfer Mode 同步传输模式STM-N Synchronous Transport Module Level N 第N级同步传输模块STP Signaling Transfer Point 信令转接点STP Spanning Tree Protocol 生成树协议STS Synchronous Transport Signal 同步传输信号SUA SCCP User Adaptation Layer SCCP用户适配层TT-SG Transport Signaling Gateway 传输信令网关T2P Traffic-to-Pilot 业务到导航信道TACS Total Access Communication System 全接入通信系统TC Transmission Convergence 传输汇聚TCA Terminal Control Area 终端控制区TCAP Transaction Capabilities Application Part 事物处理应用部分TCP Transmission Control Protocol 传输控制协议TD-CDMA Time Division-Code Division Multiple Access 时分码分多址TD-SCDMA Time Division-Synchronization Code Division Multiple Access 时分同步码分多址TDD Time Division Duplex 时分双工TDM Time Division Multiplexing 时分复用TDMA Time Division Multiple Access 时分多址TE Terminal Equipment 终端设备TE Traffic Engineering 流量工程TeS Telephony Server 电话服务器TFTP Trivial File Transfer Protocol 普通文件传输协议TG Trunk Gateway 中继网关TIA Telecommunication Industry Association 电信工业协会TIPHON Telecommunications and Internet Protocol Harmonization Over Networks 透过网络的电信及网际网路通信协议TISPAN Telecommunications and Internet Converged Services and Protocols for Advanced Networking 电信和互联网融合业务及高级网络协议组TLS Transparent Local Area Network Service 透明局域网业务TML Telephone Markup Langue 电信标记语言TMN Telecommunications Management Network 电信管理网TMSC Trunk Mobile Switching Center 汇接移动交换中心TOS Type Of Service 服务类型TRAU Transcoder and Rate Adapter Unit 码型变换/速率适配器TRIP Telephony Routing over IP IP电话路由TSM TD-SCDMA System for Mobile TD-SCDMA移动通信系统TSN Trunk Service Node 中继服务节点TSP Terminal Supporting Processor 终端支持处理机TTC Telecommunication Technology Committee 日本情报通信技术委员会TTA Telecommunication Technology Association 韩国电气通信技术协会TTI Transmission Time Interval 传输时间间隔TTS Text To Speech 文本转换为语音TU Transaction User 事务用户TUP Telephone User Part 电话用户部分UUAS Universal Audio Server 通用语音服务器UBR Unspecified Bit Rate 未指定比特率UCF Unregistration ConFirm 注销确认UDP User Datagram Protocol 用户数据报协议UE User Equipment 用户设备UICC Universal Integrated Circuit Card 通用集成电路卡ULH Ultra Long Haul 超长距离传输UMS User Mobility Service 用户移动服务UMS Unified Messaging Service 统一消息业务UMTS Universal Mobile Telecommunications System 通用移动通信系统UNI User Network Interface 用户网络接口UPC Usage Parameter Control 使用参数控制UPT Universal Personal Telecommunication 通用个人通信URI Uniform Resource Identifier 统一资源标识URL Uniform Resource Locator 统一资源定位器URJ Unregistration ReJect 注销拒绝URQ Unregistration ReQuest 注销请求UBR Unspecified Bit Rate 未指定比特率USB Universal Serial Bus 通用串行总线USP Universal Signaling Point 通用信令网关UTRAN Universal Terrestrial Radio Access Network 通用地面无线接入网络VV5UA V5.2 User Adaptation Layer V5.2用户适配层VAD Voice Activity Detection 语音激活检测VC Virtual Container 虚容器VC Virtual Channel 虚拟通道VCG Virtual Concatenation Group 虚级联组VCI Virtual Channel Identifier 虚拟通道标识VCSEL Vertical Cavity Surface Emitting Lasers 垂直腔面发射激光器VDSL Very High Speed Digital Subscriber Line 甚高速数字用户线VHE Virtual Home Environment 虚拟归属环境VLAN Virtual LAN 虚拟局域网VLR Visited Location Register 拜访位置寄存器VoD Video on Demand 视频点播VoDSL Voice over DSL 在数字用户线上传输语音VoIP Voice over IP IP话音VP Virtual Path 虚拟路径VPG Virtual Path Group 虚拟路径组VPHS Virtual Private Hub Service 虚拟专用Hub业务VPI Virtual Path Identifier 虚拟路径标识VPLS Virtual Private LAN Service 虚拟专用局域网业务。

仿真算法知识点总结一、简介仿真算法是一种通过生成模型和运行模拟来研究系统或过程的方法。
它是一种用计算机模拟真实世界事件的技术,可以用来解决各种问题,包括工程、商业和科学领域的问题。
仿真算法可以帮助研究人员更好地理解系统的行为,并预测系统未来的发展趋势。
本文将对仿真算法的基本原理、常用技术和应用领域进行总结,以期帮助读者更好地了解和应用仿真算法。
二、基本原理1. 离散事件仿真(DES)离散事件仿真是一种基于离散时间系统的仿真技术。
在离散事件仿真中,系统中的事件和状态都是离散的,而时间是连续变化的。
离散事件仿真通常用于建模和分析复杂系统,例如生产线、通信网络和交通系统等。
离散事件仿真模型可以用于分析系统的性能、验证系统的设计和决策支持等方面。
2. 连续仿真(CS)连续仿真是一种基于连续时间系统的仿真技术。
在连续仿真中,系统中的状态和事件都是连续的,而时间也是连续的。
连续仿真通常用于建模和分析动态系统,例如电力系统、控制系统和生态系统等。
连续仿真模型可以用于分析系统的稳定性、动态特性和系统参数的设计等方面。
3. 混合仿真(HS)混合仿真是一种同时兼具离散事件仿真和连续仿真特点的仿真技术。
混合仿真可以用于建模和分析同时包含离散和连续过程的系统,例如混合生产系统、供应链系统和环境系统等。
混合仿真模型可以用于分析系统的整体性能、协调离散和连续过程以及系统的优化设计等方面。
4. 随机仿真随机仿真是一种基于概率分布的仿真技术。
在随机仿真中,系统的状态和事件都是随机的,而时间也是随机的。
随机仿真通常用于建模和分析具有随机性质的系统,例如金融系统、天气系统和生物系统等。
随机仿真模型可以用于分析系统的风险、概率特性和对策选择等方面。
5. Agent-Based ModelingAgent-based modeling (ABM) is a simulation technique that focuses on simulating the actions and interactions of autonomous agents within a system. This approach is often used for modeling complex and decentralized systems, such as social networks, biologicalecosystems, and market economies. In ABM, individual agents are modeled with their own sets of rules, behaviors, and decision-making processes, and their interactions with other agents and the environment are simulated over time. ABM can be used to study the emergent behavior and dynamics of complex systems, and to explore the effects of different agent behaviors and interactions on system-level outcomes.三、常用技术1. Monte Carlo方法蒙特卡洛方法是一种基于随机模拟的数值计算技术。

Ping LouÆZu-de ZhouÆYou-Ping ChenÆWu AiStudy on multi-agent-based agile supply chain management Received:23December2002/Accepted:23December2002/Published online:5December2003ÓSpringer-Verlag London Limited2003Abstract In a worldwide network of suppliers,factories, warehouses,distribution centres and retailers,the supply chain plays a very important role in the acquisition, transformation,and delivery of raw materials and products.One of the most important characteristics of agile supply chain is the ability to reconfigure dynami-cally and quickly according to demand changes in the market.In this paper,concepts and characteristics of an agile supply chain are discussed and the agile supply chain is regarded as one of the pivotal technologies of agile manufacture based on dynamic alliance.Also,the importance of coordination in supply chain is emphas-ised and a general architecture of agile supply chain management is presented based on a multi-agent theory, in which the supply chain is managed by a set of intelli-gent agents for one or more activities.The supply chain management system functions are to coordinate its agents.Agent functionalities and responsibilities are de-fined respectively,and a contract net protocol joint with case-based reasoning for coordination and an algorithm for task allocation is presented.Keywords Agile supply chainÆMulti-agent systemÆCoordinationÆCBRÆContract net protocol1IntroductionAdvanced technology and management are constantly being adopted to improve an enterpriseÕs strength and competitive ability in order to achieve predominance among hot global competition.In a report on21st century manufacturing strategy development,the author suggests that various production resources,including people,funds,technology and facilities should be inte-grated and managed as a whole;thus optimising the utilisation of resources and taking full advantage of advanced manufacturing technology,information tech-nology,network technology and computer[1].Agile manufacture based on dynamic alliance is coming into being so that enterprises can remain competitive in a constantly changing business environment and is becoming a main competitive paradigm in the interna-tional market.Agility,which has basically two mean-ings:flexibility and reconfigurability,has become a very important characteristic of a modern manufacturing enterprise.Flexibility is an enterpriseÕs ability to make adjustments according to customersÕneeds.Reconfigu-rability is the ability to meet changing demands[2,3].The ability to quickly respond to marketÕs changes, called agility,has been recognised as a key element in the success and survival of enterprises in todayÕs market.In order to keep up with rapid change,enterprises need to change traditional management in this hot competition. Through dynamic alliance,enterprises exert predomi-nance themselves,cooperate faithfully with each other, and compete jointly so as to meet the needs of the fluctuating market,andfinally achieve the goal of win-win[2,3].So how to improve agility in the supply chain, namelyflexibility and reconfigurability,is one of the important factors to win against the competition.Supply chain management(SCM)is an approach to satisfy the demands of customers for products and ser-vices via integrated management in the whole business process from raw material procurement to the product or service delivery to customers.In[4],M.S.Fox et al. describe the goals and architecture of integrated supply chain management system(ISCM).In this system,each agent performs one or more supply chain management functions,and coordinates its decisions with other rele-vant agents.ISCM provides an approach to the real timeInt J Adv Manuf Technol(2004)23:197–203 DOI10.1007/s00170-003-1626-xP.Lou(&)ÆZ.ZhouRoom107,D8Engineering Research Center of Numerical Control System,School of Mechanical Science&Engineering, Huazhong University of Science&Technology, 430074Wuhan,Hubei,P.R.ChinaE-mail:louping_98@Y.-P.ChenÆW.AiSchool of Mechanical Science and Engineering, Huazhong University of Science and Technology, 430074Wuhan,Hubei,P.R.Chinaperformance of supply chain function.The integration of multi-agent technology and constraint network for solving the supply chain management problem is pro-posed[6].In[7],Yan et al.develop a multi-agent-based negotiation support system for distributed electric power transmission cost allocation based on the networkflow model and knowledge query&manipulation language (KQML).A KQML based multi-agent coordination language was proposed in[8,9]for distributed and dy-namic supply chain management.However,the coordi-nation mechanisms have not been formally addressed in a multi-agent-based supply chain.In most industries, marketing is becoming more globalised,and the whole business process is being implemented into a complex network of supply chains.Each enterprise or business unit in the SCM represents an independent entity with conflicting and competing product requirements and may possess localised information relevant to their interests.Being aware of this independence,enterprises are regarded as autonomous agents that can decide how to deploy resources under their control to serve their interests.This paperfirst introduces concepts and characteris-tics of agile supply chains and emphasises the impor-tance of coordination in supply chain.Then,it presents an architecture of agile supply chain based on a multi-agent theory and states the agentsÕfunctions and responsibilities.Finally,it presents a CBR contract net protocol for coordination and the correlative algorithm for task allocation in multi-agent-based agile supply chains.2Agile supply chainA supply chain is a network from the topologic structure which is composed of autonomous or semi-autonomous enterprises.The enterprises all work together for pro-curement,production,delivery,and so on[10].There is a main enterprise in the supply chain that is responsible for configuring the supply chain according to the de-mand information and for achieving supply chain value using fundflow,materialflow and informationflow as mediums.There are three discontinuous buffers to make the materialflowfluently and satisfy the change in the demand.On the one hand,as every enterprise manages inventory independently,plenty of funds are wasted.As the demand information moves up-stream,the forecast is inaccurate and the respond to the change in demand is slow[11].Accordingly,the key method for competi-tiveness is improving and optimising supply chain management to achieve integrated,automated,and agile supply chain management and to cut costs in the supply chain.To optimise supply chain management and coordi-nate the processes for materialflow,fundflow and informationflow,it is necessary to make materialflow fluent,quickly fund turnover and keep information integrated.Prompt reconfiguration and coordination is an important characteristic of agile supply chain according to dynamic alliance compositing and de-compositing(enterprise reconfiguration).Agile supply chain management can improve enterprise reconfiguring agility.The agile supply chain breaks through the tra-ditional line-style organizational structure.With net-work technology an enterprise group is formed by a cooperative relationship which includes an enterprise business centre,a production design centre,a supplier,a distribution centre,a bank,a decision-making centre, etc.It reduces the lead time to the market to satisfy customer demand.Agile supply chain without temporal and spatial limits promptly expands the enterprise scale,marketing share and resource by allied enterprise.So,a key factor of the agile supply chain is to integrate heterogeneous information systems adopted in various enterprises.The integration information system can provide marketing information and supplier details.Feasible inventory, quantity and cycle of replenished stock,delivery,etc.is designed using the shared information.It is evident that agile supply chain is a typical distributed system.A multi-agent system(MAS)which is characterised byflexibility and adaptability is suit-able for an open and dynamic environment.Thus MAS is a good method for agile supply chain man-agement.3The concept of agents and MASSome people define an agent as any piece of software or object which can perform a specific given task.Presently the prevailing opinion is that an agent must exhibit three important general characteristics:autonomy,adapta-tion,and cooperation[8,12,13].Autonomy means that agents have their own agenda of goals and exhibit goal-directed behaviour.Agents are not simply reactive,but can be pro-active and take initiatives as they deem appropriate.Adaptation implies that agents are capable of adapting to the environment,which includes other agents and human users,and can learn from the expe-rience in order to improve themselves in a changing environment.Cooperation and coordination between agents are probably the most important feature of MAS. Unlike those stand-alone agents,agents in a MAS col-laborate with each other to achieve common goals.In other words,these agents share information,knowledge, and tasks among themselves.The intelligence of MAS is not only reflected by the expertise of individual agents but also exhibited by the emerged collective behaviour beyond individual agents.Of course various agents have different functions,but some functions are needed for each agent.A generic structure of agents that includes two parts is presented:agent kernel and function mod-ule.Figure1exhibits the generic structure of agents which is a plug-in model.In Fig.1,the generic agent includes the following components:198The mailbox handles communication between one agent and the other agents.The message handler processes incoming message from the mailbox,orders them according to priority level,and dispatches them to the relevant components of the agent.The coordination engine makes decisions concerning the agent Õs goals,e.g.how they should be pursued,when to abandon them,etc.,and sends the accepted tasks to the planner/scheduler.It is also responsible for coordi-nating the agents Õinteractions with other agents using coordination protocols and strategies.The planner and scheduler plans the agent Õs tasks on the basis of decisions made by the coordination engine and on resources and task specifications available to the agent.If not,a message is sent to the coordination en-gine for finding extra resources.The blackboard provides a shared work area for exchanging information,data,and knowledge among function modules.Every function module is an inde-pendent entity.These function modules execute con-currently by the control of planner/scheduler and collaborate through the blackboard.The acquaintance database describes one agent Õs relationships with other agents in the society,and its beliefs about the capabilities of those agents.The coor-dination engine uses information contained in this database when making collaborative arrangements with other agents.The resource database reserves a list of resources (referred to in this paper as facts)that are owned by and available to the agent.The resource database also sup-ports a direct interface to external systems,which allows the interface to dynamically link and utilise a proprie-tary database.The ontology database stores the logical definition of each fact type—its legal attributes,the range of legal values for each attribute,any constraints betweenattribute values,and any relationship between the attributes of that fact and other facts.The task/plan database provides logical descriptions of planning operators (or tasks)known to the agent.4Multi-agent-based agile supply chain management Multi-agent-based agile supply chain management per-forms many functions in a tightly coordinated manner.Agents organise supply chain networks dynamically by coordination according to a changing environment,e.g.exchange rates go up and down unpredictably,customers change or cancel orders,materials do not arrive on time,production facilities fail,etc.[2,14].Each agent performs one or more supply chain functions independently,and each coordinates his action with other agents.Figure 2provides the architecture of multi-agent-based agile supply chains.There are two types of agents:functional agents and mediator agents.Functional agents plan and/or control activities in the supply chain.Mediator agents play a system coordinator role s by promoting coopera-tion among agents and providing message services.Mediator agents dispatch the tasks to the functional agents or other mediator agents,and then those func-tional or mediator agents complete the tasks by coordi-nation.All functional agents coordinate with each other to achieve the goals assigned by mediator agents.The mediator-mediator and mediator-agent communication is asynchronous,and the communication mode can be point-to-point (between two agents),broadcast (one to all agents),or multicast (to a selected group of agents).Messages are formatted in an extended KQML format.The architecture is characterised by organizational hier-archy and team spirit,simplifying the organisational architecture and reducing the time needed to fulfil the task.The rest of this section briefly describes each of the mediator agents underdevelopment.Fig.1Generic structures of agents199–Customer mediator agent:This agent is responsible for acquiring orders from customers,negotiating with customers about prices,due dates,technical advisory,etc.,and handling customer requests for modifying or cancelling respective orders,then sending the order information to a scheduling mediator agent.If a customer request needs to be re-designed,the infor-mation is sent to a design mediator agent,then to a scheduling mediator agent.–Scheduling mediator agent:This agent is responsible for scheduling and re-scheduling activities in the fac-tory,exploring hypothetical ‘‘what-if’’scenarios for potential new orders,and generating schedules that are sent to the production mediator agent and logis-tics mediator agent.The scheduling agent also acts as a coordinator when infeasible situations arise.It has the capability to explore tradeoffs among the various constraints and goals that exit in the plant.–Logistics mediator agent:This agent is responsible for coordinating multi-plans,multiple-supplier,and the multiple-distribution centre domain of the enterprise to achieve the best possible results in terms of supply chain goals,which include on-time delivery,cost minimisation,etc.It manages the movement of products or materials across the supply chain from the supplier of raw materials to the finished product customer.–Production mediator agent:This agent performs the order release and real-time floor control functions as directed by the scheduling mediator agent.It monitors production operation and facilities.If the production operation is abnormal or a machine breaks down,this agent re-arranges the task or re-schedules with the scheduling mediator agent.–Transportation mediator agent:This agent is responsible for the assignment and scheduling of transportation resources in order to satisfy inter-plant movement specified by the logistics mediator agent.It is able to take into account a variety oftransportation assets and transportation routes in the construction of its schedules.The goal is to send the right materials on time to the right location as assigned by the logistics mediator agent.–Inventory mediator agent:There are three invento-ries at the manufacturing site:raw product inven-tory,work-in-process inventory,and finished product inventory.This agent is responsible for managing these inventories to satisfy production requirements.–Supplier mediator agent:This agent is responsible for managing supplier information and choosing suppli-ers based on requests in the production process.–Design mediator agent:This agent is responsible for developing new goods and for sending the relevant information to the scheduling mediator agent for scheduling,as well as to the customer mediator agent for providing technological advice.5Coordination in a multi-agent-based agile supply chainCoordination has been defined as the process of man-aging dependencies between activities [15].One impor-tant characteristic of an agile supply chain is the ability to reconfigure quickly according to change in the envi-ronment.In order to operate efficiently,functional entities in the supply chain must work in a tightly coordinated manner.The supply chain works as a net-work of cooperating agents,in which each performs one or more supply chain functions,and each coordinates its action with that of other agents [5].Correspondingly,a SCMS transforms to a MAS.In this MAS,agents may join the system and leave it according to coordinating processes.With coordination among agents,this MAS achieves the goal of ‘‘the right products in the right quantities (at the right location)at the right moment at minimalcost’’.Fig.2An architecture of multi-agent based agile supply chain management2005.1Contract net protocol combined withcase-based reasoningThe contract net is a negotiation protocol(CNP)pro-posed by Smith[15].In the CNP,every agent is regarded as a node,such as a manager or a contractor.The manager agent(MA)is responsible for decomposing, announcing,and allocating the task and contractor agent(CA)is responsible for performing the task.This protocol has been widely used for multi-agent negotia-tion,but it is inefficient.For this reason,contract net protocol is combined with case-based reasoning(CBR).In case-based reasoning(CBR),the target case is defined as problem or instance which is currently being faced,and the base case is problem or instance in the database.CBR searches the base case in the database under the direction of the target case,and then the base case instructs the target case to solve the problem.This method is efficient.But at the very beginning,it is very difficult to set up a database which includes all problems solving cases.The cases may be depicted as follows:C¼\task;MA;taskÀconstraint;agentÀset> Here,MA is task manager.Task-constraint repre-sents various constraint conditions for performing the task,depicted as a vector{c1,c2,c3,...,c m}.Agent-set is a set of performing the task as defined below:Agent set¼\sub task i;agent id;cost;time;resource>f gtask¼[ni¼1sub task iIn the supply chain,the same process in which a certain product moves from the manufacturer to the customer is performed iteratively.So,case-based rea-soning is very efficient.Consequently,combining con-tract net protocol with CBR could avoid high communicating on load,thus promoting efficiency.The process can be depicted as follows(Fig.3).5.2The algorithm for task allocation baseon CBR contract net protocolThere are two types of agents in the supply chain, cooperative and self-interested agents.Cooperative agents attempt to maximise social welfare,which is the sum of the agents utilities.They are willing to take individual losses in service of the good of the society of agents.For example,function agents come from the same enterprise.In truth,the task allocation among cooperative agents is combinational optimisation prob-lem.Self-interested agents seek to maximise their own profit without caring about the others.In such a case,an agent is willing to do other agentsÕtasks only for com-pensation[16].Function agents,for example,come from different enterprises.In the following section the algorithm for task allo-cation among self-interested agents based on CBR contract net protocol will be addressed.Before describ-ing the algorithm,there are some definitions that must be clarified:Task—A task which is performed by one agent or several agents together:T=<task,reward,con-straints>,where task is the set of tasks(task={t1,t2,..., t m}),reward is the payoffto the agents that perform the task(reward={r1,r2,...,r m}),and constraints refer to the bounded condition for performing the task(con-straints={c1,c2,...,c n}).Agent coalition(AC)—A group of agents that per-form task T,described as a set AC={agent i,i=1,2,...,n}.Efficiency of agent—Efficiency of an agent i is de-scribed as follows:E i¼rewardÀcostðÞ=costð1Þwhere reward is the payoffto the agent performing task T,and cost refers to that spend on performing the task. If agent i is not awarded the task,then E i=0.Efficiency of agent coalition—E coalition¼rewardÀX micost iÀh!,X micost iþh!ð2Þwhere reward is the payoffof the agent coalition per-forming task T;cost i refers to that spend on performing task t i;and h is the expense on forming coalition,which is shared by the members of the coalition.If the coalition is not awarded task T,then E coalition<=0.6Algorithm:1.After MA accepts the task T=<task,reward,constraint>(task is decomposable),then it searches the database.2.If itfinds a corresponding case,it assigns the task orsubtask to the related agents according to the case, and the process is over3.If no case is found,then the task T is announced toall relevant agents(agent i,i=1,2,...n).4.The relevant agents make bids for the task accord-ing to their own states and capabilities.Thebid Fig.3CBR contract net process201from agent i can be described as follows:Bid i =<agentid i ,T i ,price i ,condition i >,where i ex-presses the bidding agent (i =1,2,...,h );agentid i is the exclusive agent identifier;T i is the task set of agent i Õs fulfilment;price i is the recompense of agent i fulfilling the task T i ;and condition i is the constraint conditions for agent i to fulfil the task T i .5.If [1 i h&T i then the task T can not be performed.Otherwise MA makes a complete combination of the agents,namely to form a number of agent coalitions (or agent sets,amounting to N =2h )1).6.First MA deletes those agent coalitions where no agents are able to satisfy the constraint condition.Next the rest of the coalitions are grouped by the number of agents in coalitions and put into set P (P ={P 1,P 2,...,P h })in order of the minimum re-compense increase of the coalitions,where P i is the set of agent coalitions,including i agents.7.MA puts the first coalition from each group P i(i =1,2,...,h )into set L ,and if L is null then it returns to (10),otherwise it calculates the minimum re-compense of each coalition as follows:Min Pm iprice i ÃT is :t :P h i ¼1T i TP m icondition i constraitThen it searches for the minimal agent coalition AC min from the set L .8.MA sends the AC min to the relevant agents,namely MA requests that these agent fulfil the task to-gether.The relevant agents calculate the E coalition and E i according to Eqs.1and 2.IfE coalition !max miE i ,then all agents in the AC minaccept the proposal to form a coalition to perform the task T together.MA assigns the task to the AC min ,and the process is over.Otherwise it deletes the AC min from P i and returns to (7).9.If the relevant agents accept the task or subtask,then MA assigns the task to them.The process is over.If some agents cannot accept the subtask and the stated time is not attained,then it returns to (3),otherwise it returns to (10).10.The process is terminated (namely the task cannotbe performed).After all processes have been completed,case-based maintenance is required to improve the CBR.Thus efficiency is continuously promoted.6.1An example–A simple instantiation of a supply chain simulation is presented here and the negotiating process among agents is shown.In this supply chain instantiation,thetransportation mediator agent (TMA)has a transporttask T ,in which it has to deliver the finished product to the customer within 15units of time and must pay 1500monetary units for it,that is T =<t ,1500,15>.Four transport companies can perform task T .Each company is an autonomous agent,that is four agents,agent A,agent B,agent C and agent D.So the TMA announces the task T to the four agents.Then the four agents make a bid for the task T as shown in Table 1.–So the four agents can form 24)1coalitions (see Fig.4),which are put into set P .Cooperation between agents in the coalition requires expense and the ex-pense for forming the coalition increases with the growth of in coalition size.This means that expanding the coalition may be non-beneficial.The expense of each agent in forming a coalition h is 100.First,the coalitions in which no agents can satisfy the constraint conditions are deleted from the set P .The rest of the coalitions are grouped by the number of agents in the coalition and ordered according to the recompense of each group that was increased due to the coalition,namely P 1={B},P 2={{A,B},{A,C},{B,C},{A,D},{B,D}},P 3={{A,B,C},{A,B,D},{B,C,D}},P 4={{A,B,C,D}}.Then the cost and efficiency of coalition {B},{A,C}and {A,B,C}are calculated as follows:Price f A ;B g ¼Min ð800x 1þ1200x 2Þs :t :20x 1þ12x 2 15x 1þx 2!1x 1!0:x 2!0Price f A ;B ;C g ¼Min ð800y 1þ1200y 2þ2000y 3Þs :t :20y 1þ12y 2þ5y 3 15y 1þy 2þy 3!1y 1!0:y 2!0;y 3!Fig.4Agent coalition graphTable 1The bids of four agents Agent Id Price Conditions Agent A 80020Agent B 120012Agent C 20005AgentD25003202the following result can be obtained:Price{B}=1200; x1=0.3750,x2=0.6250,Price{A,B}=1050;and y1= 0.3750,y2=0.6250,y3=0.The above result shows that agent B does not attend the coalition{A,B,C},that is both agent B and coalition{A,B}can fulfill the task and satisfy the constraint conditions.According to Eqs.1 and2,E A,E B,E{A,B}:E A=0(because TMA does not assign the task to A.),E B=(1500)1200)/1200=0.25, E{A,B}=(1500)1050)2*100)/(1050+2*100)=0.2can be obtained.Because of E{A,B}<max{E A,E B},agent B does not agree to form a coalition.Therefore,the TMA se-lects agent B to fulfil the task.7ConclusionsIn this paper,the concept and characteristics of agile supply chain management are introduced.Dynamic and quick reconfiguration is one of important characteristics of an agile supply chain and agile supply chain man-agement is one of the key technologies of agile manu-facturing based on dynamic alliances.As agile supply chain is a typical distributed system,and MAS is effi-cient for this task.In the architecture of agile supply chain management, the supply chain is managed by a set of intelligent agents that are responsible for one or more activities.In order to realise the agility of supply chains,coordination amongst agents is very important.Therefore,it can be suggested that contract net protocol should be combined with case-based reasoning to coordinate among agents. Acknowledgement The authors would like to acknowledge the funding support from the National Science Fund Committee (NSFC)of China(Grant No.5991076861).References1.Goldman S,Nagel R,Preiss K(1995)Agile competitors andvirtual organization.Van Nostrsand Reinhold,New York, pp23–32,pp158–1662.Yusuf YY,Sarhadi M,Gunasekaran A(1999)Agile manu-facturing:the drivers,concepts and attributes.Int J Prod Eng 62:33–433.Gunasekaran A(1999)Agile manufacturing:A framework forresearch and development.Int J Prod Eng62:87–1054.Fox MS,Chionglo JF,Barbuceanu M(1992)Integrated chainmanagement system.Technical report,Enterprise Integration Laboratory,University of Toronto5.Shen W,Ulieru M,Norrie DH,Kremer R(1999)Implementingthe internet enabled supply chain through a collaborative agent system.In:Proceedings of agentsÔ99workshop on agent-based decision support for managing the internet-enabled supply-chain,Seattle,pp55–626.Sandholm TW,Lesser VR(1995)On automated contracting inmulti-enterprise manufacturing.Advanced Systems and Tools, Edinburgh,Scotland,pp33–427.Beck JC,Fox MS(1994)Supply chain coordination via medi-ated constraint relaxation.In:Proceedings of thefirst Canadian workshop on distributed artificial intelligence,Banff,Alberta, 15May19948.Chen Y,Peng Y,Finin T,Labrou Y,Cost R,Chu B,Sun R,Willhelm R(1999)A negotiation-based multi-agent system for supply chain management.In:Working notes of the ACM autonomous agents workshop on agent-based decision-support for managing the internet-enabled supply-chain,4:1–79.Wooldridge M,Jennings NR(1995)Intelligent agents:theoryand practice.Knowl Eng Rev10(2):115–15210.Barbuceanu M,Fox MS(1997)The design of a coordinationlanguage for multi-agent systems.In:Muller JP,Wooldridge MJ,Jennings NR(eds)Intelligent agent III:agents theories, architecture and languanges(Lecture notes in artificial intelligence),Springer,Berlin Heidelberg New York,pp341–35711.Hal L,Padmanabhan V,Whang S(1997)The Bullwhip effect insupply chains.Sloan Manag Rev38(4):93–10212.Yung S,Yang C(1999)A new approach to solve supply chainmanagement problem by integrating multi-agent technology and constraint network.HICASS-3213.Yan Y,Yen J,Bui T(2000)A multi-agent based negotiationsupport system for distributed transmission cost allocation.HICASS-3314.Nwana H(1996)Software agents:an overview.Knowl Eng Rev11(3):1–4015.Smith RG(1980)Contract net protocol:high-level communi-cation and control in a distributed problem solver.IEEE Trans Comput29(12):1104–111316.Barbuceanu M,Fox MS(1996)Coordinating multiple agentsin the supply chain.In:Proceedings of thefifth workshop on enabling technology for collaborative enterprises(WET ICEÕ96).IEEE Computer Society Press,pp134–14117.Jennings NR,Faratin P,Norman TJ,OÕBrien P,Odgers B(2000)Autonomous agents for business process management.Int J Appl Artif Intell14(2):145–1818.Malone TW,Crowston K(1991)Toward an interdisciplinarytheory of coordination.Center for coordination science tech-nical report120,MIT Sloan School203。

Akamai各产品线介绍Akamai各产品线产品简介[作者]本⽂主要列举了Akamai各⼤产品线的各类产品,并且做了简要介绍,从Akamai的产品线可以⼤致看出Akamai战略发展⽅向以及⽬前已有解决⽅案的市场深⼊度。
Akamai⼤致分为五⼤产品线:⽹络性能解决⽅案媒体分发解决⽅案云安全解决⽅案云⽹络解决⽅案⽹络运营商解决⽅案◆⽹络性能产品线:主要web为主,静态⽹页类与动态加速,还有基于IP应⽤的加速(TCP层的优化加速,与APPA⼀样的产品),还有源站负载均衡等⼀些服务;◆媒体分发产品线:主要以直播和点播加速为主,还有云平台的流媒体服务器,以及播放器,最后还带个云存储产品,从这⾥看出Akamai产品解决⽅案是很强⼤很深⼊的,真正的端到端的媒体解决⽅案,从源站到⽤户端,也可以说从第⼀公⾥到最后⼀公⾥的这样⼀套整体解决⽅案,从根本上可以看出Akamai是⼀家技术导向型的公司,研发实⼒的确很强;并且Akamai还有客户端软件Akamai NetSession Interface,这个虽说主要⽤于媒体分发或下载,但可以看出这就是最后⼀公⾥加速了,这也算是将CDN打⼊了⼤众群体。
◆云安全产品线:主要以web⽹站类的安全,防攻击再加上WAF等,这个主要看经验积累了;但是通过收购Prolexic公司,拓展了⾃⼰产品线的市场范围,可以对基于IP的应⽤进⾏防护,并且有对整个数据中⼼的防护⽅案,这样就从最底层设备到最上层应⽤都能覆盖,真正的基于云的安全防护能⼒。
◆云⽹络产品线:主要与Cisco和Steelhead合作的两个产品。
◆⽹络运营商产品线:主要是卖软件了,授权license,其他的产品可以说是卖服务,这个可以说就是纯粹卖技术了。
经常会看见业界介绍Akamai五⼤解决⽅案如下:Akamai平台⼀共包括五⼤产品解决⽅案。
分别是AQUA(针对⽹站类型的应⽤业务)、SOLA(针对媒体视频传播及软件下载业务)、TERRA、KONA(提供客户防护⽹络攻击及⽹络监控功能,如DDos)、AURA(与运营商合作的⼀款产品)。

3GPP Third Generation Partnership Project3GPP2 Third Generation Partnership Project 2AA Anchor AuthenticationAAA Authorization, Authentication and Accounting 授权、鉴权、计费AAA Proxy An intermediary for transparently routing and/or processing AAA messages sent between a AAA client and a AAA serverAAA Server Computer system performing AAA services (authentication, authorization, accounting)AAA-V AAA proxy server located within the visited networkAAS Adaptive Antenna System 自适应天线系统AC Admission ControlACID ARQ channel IDAES Advanced Encryption Standard 高级加密算法AF Application FunctionAI Antenna indexAI_SN ARQ identifier sequence numberAK Authentication KeyAMC Adaptive modulation and coding 自适应调制编码AP Access point 接入点API Application Program InterfaceARQ Automatic Repeat Request 自动重复请求ASA Authentication and service authorization 鉴权和服务授权ASCA Adjacent subcarrier allocationASN Access Service NetworkASP Application Service ProviderASR Anchor switch reportingATDD Adaptive time-division duplexing 自适应时分复用ATM Asynchronous Transfer mode 异步传输模式AWGN Additive white Gaussian noise 加性高斯白噪声BE Best effort 尽力而为BER Bit error rate 误码率BPRI Burst profile ranking indicatorBPSK Binary Phase Shift Keying 二相相移键控BR Bandwidth RequestBS Base Station 基站BSC Base station control 基站控制器BSN Back sequence numberBSN Block sequence numberBTC Block turbo code 块Turbo码BTS Base transceiver station 基站收发信机BU Binding UpdateBW Bandwidth 带宽BWA Broadband Wireless Access 宽带无线接入BW AA Bandwidth allocation / access 带宽分配/接入CBC Cipher block chaining 密码块链CBC-MAC Cipher block chaining message authentication code 密码块链消息鉴权码CBR Constant bit rate 常数比特率CCH Control subchannel 控制子信道CCM CTR mode with CBC-MACCCoA Collocated Care of AddressCDMA Code division multiple access 码分多址CDMA2000 3rd Generation Code Division Multiple Access Radio TechnologyCID Connection IDentifier 连接标识CII CID inclusion indicationCINR Carrier to interference-plus-noise ratio 载干比CIR Carrier to interference ratio 载干比CIOQ Combined input-output queued 输入输出排队CLP Cell loss priority 信元丢失优先级CLR Cell loss ratio 蜂窝丢失比CMAC Cipher-based message authentication code 基于加密的消息鉴权码CMIP Client Mobile IPCN Core network 核心网COA Care of AddressCOA Change of authorizationCOS Class of ServiceCP Cyclic prefix 循环前缀CPE Customer premise equipment 客户端设备CPLT CompleteCPS Common Part Sublayer 公共部分子层CQI Channel quality information 信道质量信息CQICH Channel quality information channel 信道质量信息信道CRC Cyclic Redundency Check 循环冗余校验CS Convergence Sublayer 汇聚子层CSDPS Channel state dependent packet scheduling 依赖信道状态的分组调度CSIT Channel state information at the transmitter 发送侧信道状态信息CSMA/CA Carrier sense multiple access with collision avoidance 载波侦听多点接入/冲突避免CSN Connectivity Service NetworkCT CQI typeCTC Convolutional turbo codes 卷积turbo码CTD Cell transfer delay 蜂窝转移时延CTI Coherent time indexCTR Counter mode encryptionCTS Clear to sendDAD Duplicate Address DetectionDAMA Demand Assigned Multiple Accese 按需分配多址接入DA VIC Digital audio visual council 数字音频可视委员会dBi Decibels of gain relative to the zero dB gain of a free-space isotropic radiatordBm Decibels relative to one milliwattDBPC Downlink burst profile changeDCDCA Dynamic channel allocation 动态信道分配DCD Downlink channel descriptor 下行信道描述符DCF Distributed coordination function 分布式协调功能DECT Digital enhanced cordless telecommunications 数字增强型无绳通信DES Data encryption standard 数据加密标准DFS Dynamic Frequency Selection 动态频率选择DHCP Dynamic host configuration protocol 动态主机配置协议DIUC Downlink interval usage code 下行间隔使用码DL Downlink 下行DLFP Downlink frame. prefixDNS Domain Name ServiceDOCSIS Data over cable system interface specification 有线电缆数据服务接口规范DoS Denial of ServiceDP Data pathDP Decision pointDPF Data path functionDSA Dynamic service addition 动态服务流添加DSC Dynamci service change 动态服务流更改DS-CDMA Direct spread CDMA 直扩码分多址DSCP Differentiated services code point 区分服务编码DSD Dynamic service delete 动态服务流删除DSL Digital Subscriber LineDTDMA 分布式时分多址DVB Digital video broadcastE2E End-to-EndE911 US Emergency ServicesEAP Extensible authentication protocol 扩展鉴权协议EAP-AKA EAP Authentication and Key Agreement to be used with USIMEAP-SIM EAP Subscriber Identity Module to be used with SIMEAP-TLS EAP with TLSEAPMSCHAPv2 Microsoft* Challenge Handshake Authentication Protocol version 2 EC Encryption codeECB Electronic code bookECRTP Enhanced compressed real time protocolEDE Electronic data exchangeEDF Earliest deadline first 最早到期优先EIK EAP integrity keyEIRP Equivalent Isotropic Radiated Power 等效全向辐射功率EP Encoded packetEP Enforcement pointERT Extended Real-TimeertPS Extended Real-Time Polling SystemESF Extended subheader fieldETE End to end 端到端ETSI European telecommunication standards institute 欧洲电信标准协会EVM Error vector magnitude 误差矢量幅度FA Foreign Agent 外部代理FA Frequency assignment 频率分配FBSS Fast base station switching 快速基站转换FCA Fixed channel header 固定信道分配FCAPS Fault Configuration Accounting Performance and SecurityFCC Federal communications commisstion 联邦通信委员会FCH Frame. control header 帧控制头FDD Frequency division duplexing 频分双工FDMA Frequency division multiple access 频分多址FEC Forward error correction 前向纠错FFT Fast Fourier transform. 快速傅立叶变换FHDC Frequency hopping diversity codingFIFO First in first out 先入先出FL Frame. latencyFLI Frame. latency indicationFPC Fast power controlFQDN Fully Qualified Domain NameFSN Forward sequence numberFUSC Full usage of subchannels 完全利用子信道FWA Fixed Wireless Access 固定无线接入GKEK Group key encryption keyGMH Generic MAC headerGPC Grant per connection 每连接授予GPRS General Packet Radio ServicesGPSS Grant per subscriber station 每站点授予GRE Generic Routing EncapsulationGRF Gain reduce factor 增益减少因之GSA Group Security AssociationGSM Global system for mobile communications 全球移动通信系统GTEK Group traffic encryption keyGW GatewayH-ARQ Hybrid automatic repeat request 混合自动请求重传HA Home AgentHAO Home address optionHCS Header check sequenceHFDD Half FDDHLHLA Hotline applicationHLD Hotline deviceHMAC Hashed message authentication code 哈希消息鉴权码HNSP Home network service providerHO Handover 切换HO ID Handoff IdentifierHoA MS Home AddressHOL Head of line 队列顶端Hotspot Public location such as an airport or hotel where WLAN services have been deployedHSDPA High speed downlink packet access 高速分组下行链路接入HT Header type 报头类型HTTP HyperText Transfer ProtocolICI Inter channel interference 信道间干扰IE Information element 信息单元IEEE Institute of Electrical and Electronics EngineersIEEE 802.3 IEEE standard specification for EthernetIETF Internet engineering task force 互联网工程任务组IFFT Inverse fast Fourier transform. 反快速傅立叶变换IID Interface IdentifierIK Integrity KeyIMS IP Multimedia sybsytem IP多媒体子系统IPsec IP Security –A network-layer security standard providing data privacy, integrity, and replay protection.IPv4 Internet Protocol Version 4IPv6 Internet Protocol Version 6IR Incremental redundancyIQ Input queued 输入排队ISF Initial service flowISI Inter symbol interference 符号间干扰ITU International telecommunication union 国际电信联盟IWF Internetworking FunctionIWFQ Ideal wireless fair queue 理想无线公平队列IWG Inter-working GatewayIWU Internetworking UnitKDFKEK Key encrypt keysLAN Local area network 局域网LBS Location Based ServicesLDPC Low-density parity-check 低密度校验码LLC Logical Link Control 逻辑链路控制LMDS Local multipoint Distribute service 本地多点分配业务LSB Least Significant Bit 最低比特位LoS Line of Sight 视距LPF Local Policy FunctionLR Location registerLRS Latency rate server 时延速率服务器LSB Least signification bit 最不重要的比特LSP Label switched path 标签交换路径LSR Label switched router 标签交换路由器LU Location updateMAC Medium Access Control 媒质接入控制MAC Message authentication codeMAK MBS authentication keyMAN Metropolitan area network 城域网MASCARA Mobile Access Scheme based on Contention And Reservation for ATIV1 MBMS Multimedia Broadcast/Multicast ServiceMBRA Multicast and broadcast rekeying algorithmMBS Multicast and broadcast servicesMBSGSA MBS GSAMC-CDMA Multicarrie CDMA 多载波CDMAMCS Modulation coding schemeMDHO Macro diversity handover 宏分集切换MGTEK MBS GTEKMI Matrix indicatorMIB Management information base 管理信息库MIMO Multi Input Multi Output 多入多出MIP Mobile IP (Refers to both Mobile Ipv4 and Mobile Ipv6)ML Maxium likelihood 最大似然MMDS Multi-channel microwave distribution system 多路微波分配系统MMS Multimedia Messaging ServiceMOB MobilityMPEG Motion picture experts group 活动图像专家组MPLS Multiple protocol label switch 多协议标签交换MS Mobile station 移动站MSB Most Significant Bit 最高比特位MSK Master Session KeyMSS Mobile Subscriber Station 移动用户站MTK MBS traffic keyMU Multiple user ?NAI Network Access IdentifierNAP Network Access ProviderNAPT Network Address Port TranslationNAT Network Address TranslationNIST National istitute of standards and technologyNLOS Non Line Of Sight 非视距NMS Network Management SystemNNI Network to network interfaceNONCE 当前使用的一次性随机数识别符NRM Network Reference ModelnrtPS Non-real-time polling service 非实时查询服务NSP Network Service ProviderOAM Operations and MaintenanceOFDM Orthogonal Frequency Division Multiplexing 正交频分复用OFDMA Orthogonal Frequency Division Multiple Access 正交频分多址OQ Output queued 输出队列OTA Over-The-AirP-CSCF Proxy-Call Session Control FunctionPA Paging agentPAK Primary authorization keyPAPR Peak to average power ratioPAR Peak average ratio 峰值平均功率比PBWI Preferred bandwidth indexPC Power control 功率控制PC Paging controllerPCF Point coordination function 点协调功能PDF Policy decision functionsPDG Packet Data GatewayPDU Protocol Data Unit 协议数据单元PEAP Protected EAP, IETF draft protocol for using TLS to protect EAP PEP Policy enforcement pointPF Policy FunctionPG Paging groupPG ID Paging Group IdentifierPHB Per-hop behavior. 每跳行为PHS Payload Header Suppression 净荷报头压缩PHSF Payload header suppression fieldPHSI Payload Header Suppression identifier 净荷报头压缩索引PHSM Payload header suppression maskPHY PHYsical Layer 物理层PKM Privacy key management 密钥管理PMC Power control mode changePMIP Proxy-Mobile IPPMK Pairwise master keyPMP Point to multipoint 点队多点PN Packet numberPoA Point of AttachmentPPAC Prepaid accounting capabilityPPAQ Prepaid accounting quotaPPC Prepaid clientPPS Prepaid serverPPTP Point-to-point tunneling protocolPRBS Pseudo-random binary pulse sequence 伪随机二进制序列PRMA Packet Reservation Multiple Access 分组预约多址PS Physical slot 物理时隙PSD Power spectrum density 功率普密度PSL Physical service levelPSK Pre-shared keyPSTN Public switched telephone network 公用电话交换网PTI Payload type indicator 净荷种类指示PtP Peer to PeerPUSC Partial usage of subchannels 部分利用子信道PUSC-ASCA PUSC adjacent subcarrier allocationQAM Quadrature Amplitude Modulation 正交幅度调制QoS Quality of Service 服务质量QPSK Quadrature Phase Shift Keying 四相相移键控RADIUS Remote Access Dial In User Service, a network protocol for AAA services RAN Radio access network 无线接入网RCID Reduced CIDREP ReportREQ Request 请求RES ResetRK Root keyRLC Radio Link Control 无线链路控制RMS Root mean square 均方根PN Pseudo-noiseRNG Ranging 调整ROC Rollover counterROHC Robust header compressionRP Reference PointRRA Radio Resource AgentRRC Radio Resource ControllerRRM Radio Resource ManagementRSA Rivest shamir adlemen 一种加密算法RSP Response 响应RSSI Receive signal strength indicator 接收信号强度指示RST Rate speed timestamp scheduler 速率分隔时签调度器RSVP Resource reservation protocol 资源预留协议RTD Round trip delayRTS Request to sendrtPS Real-time polling service 实时查询服务RUIM Removable User Identity ModuleS-CSCF Serving-Call Session Control FunctionSA Security Association 安全联系SAP Service Access Point 服务接入点SBC SS basic capabilitySBCH Shared broadcast control channelSBSSC 单载波调制模式,WirelessMAN-SC, 10~66 GHz, TDD、FDDSca 单载波调制模式,WirelessMAN-Sca, 2~11 GHz授权频率, AAS、ARQ、STC, TDD、FDDSCI Spare capacity indicatorSDMA Spatial division multiple accessSDU Service Data Unit 服务数据单元SDU Service data unit 服务数据单元SFA Service Flow AuthorizationSFI Service Flow Index 服务公平指数SFID Service Flow Identifier 业务流标识SFM Service Flow ManagementSHO Soft handover 软切换SIM Subscriber Identity Module. Smart cards used by GSM operators.SLA Service level agreement 服务水平协定SLAAC Stateless address autoconfigurationSLP Service level predictionSLPB Starting location of preferred bandwidthSM Spatial multiplexingSMS Short message service 短消息服务SMTP Simple Mail Transport ProtocolSN Sequence numberSNR Signal to noise ratio 信噪比SNMP Simple network management protocol 简单网络管理协议SPID Sub-packet identifier 子数据包标志SS Subscriber Station 用户站SS7 Signaling System 7SSID Subscriber station identification (MAC address)SSL Secure Sockets LayerSSRTG SS Rx/Tx gap 终端收/ 发切换间隔SSTG Subscriber station transition gap 终端发送间隔SSTTG SS Tx/Rx gap终端发/ 收切换间隔Standard Deviation 标准差STC Space Time Coding 空时编码STC Session termination capabilitySTTD Space time transmit diversitySWAP Share wireless access protocol 共享无线接入协议TCM Trellis coded modulation 格形编码调制TCP Transmisstion control protocol 传输控制协议TDD Time division duplexing 时分双工TDMA Time division multiple access 时分多址TEK Traffic encryption keyTFTP Trivial file transfer protocol 简单文件传输协议TLS Transport Layer Security, a variant of SSLTLV Type/length/value 类型/长度/值TO Transmission opportunityTOS Type of service 服务类型TSI Tariff switch intervalTTLS Tunneled TLSTITSU Time interval after tariff switch update timerTUSC Tile usage of subchannelsTuple In mathematics, a tuple is a finite sequence(also known as an “ordered list”) of objects, each of a specified type. A tuple containing n objects is known as an “n-tuple”. Names for tuples of specific length: Empty tuple(0), Single/signleton/sole/only(1), Double/pair/twice(2), Triple/triplet/treble/thrice/threesome/troika/trio(3), Quadruple(4), Quintuple/pentuple(5), Sextuple/hextuple(6), Septuple(7), Octuple(8), Nonuple(9), Decuple(10).UCD Uplink channel dscriptor 上行信道描述器UDP User Datagram ProtocolUE User equipment 用户设备UEP Unequal error protectionUGS Unsolicited grant service 主动授予服务UICC Universal Integrated Circuit CardUIUC Uplink interval usage code 上行间隔使用码UL Uplink 上行UMTS Universal mobile telecommunication system 通用移动通信系统UNI User ot network interfaceUPS Uplink packet scheduler 上行分组调度器USIM Universal Subscriber Identity Module. Smart cards used by UMTS operatorsUW Unique word 独特字VBR Variable bit rate 可变比特速率VC Virtual channel 虚拟信道VCI Virtual channel identifier 虚拟信道标志VLAN Virtual Local Area Network 虚拟局域网VNSP Visited network service providerVOD Video on demand 视频点播V oIP Voice over IPVP Virtual path 虚拟通道VPI Virtual path identifier 虚拟通道标志VPN Virtual Private NetworkVSA Vendor-Specific AttributeVSIF Vendor Specific Information FieldWCDMA Wideband Code-Division Multiple AccessWEP Wired Equivalent Privacy, the initial (fatally flawed) security solution for the 802.11 link layer.WFI Worst-case fairness index 最坏公平指数WFQ Weight fair queue 加权公平队列Wi-Fi Wireless Fidelity, refers to 802.11 standards, including 802.11b, 802.11a, and 802.11gWiMAX World Interoperability for microwave access 世界微波接入互操作性WirelessHUMAN 高速非授权城域网, 2~11 GHz非授权频率, AAS、ARQ、Mesh、STC、DFS, TDDWirelessMAN-OFDM OFDMA正交频分复用, 2~11 GHz授权频率, AAS、ARQ、Mesh、STC, TDD、FDDWirelessMAN-OFDMA OFDMA正交频分多址, 2~11 GHz授权频率, AAS、ARQ、STC, TDD、FDDWirelessMAN-SC 单载波调制模式, 10~66 GHz, TDD、FDDWirelessMAN-Sca 单载波调制模式,2~11 GHz授权频率, AAS、ARQ、STC, TDD、FDDWLAN Wireless local area network 无线局域网WMAN Wireless metropolitan area network 无线城域网WPA Wi-Fi Protected Access, a subset of the 802.11i security standard compatible with existing WLAN hardware. Wi-Fi Protected Access* includes per-packet Message Integrity Check (MIC), per-user dynamic WEP keys (TKIP), and 802.1X authentication. Wi-Fi保护接入WPAN Wireless personal area network 无线个人域网WWAN Wireless Wide Area NetworkX.509 ITU standard for digital public-key certificate issued by a CAZT-CC Termination or zero-tailing encoded,where the encoder is forced to return to the all-zerostate feeding a sufficient number of zeros into theencoder。


A MOBILE AGENT-BASED COMMUNICATIONSMIDDLEWAREFOR DATA STREAMING IN THE BATTLEFIELDABSTRACTIn this paper we introduce the FlexFeed framework in the context of military combat operations. FlexFeed realizesthe notion of Agile Computing for streaming data communicationsand implements a flexible, robust and efficient]publish/subscribe infrastructure for dynamic ad hoc environmentunder resource and policy constraints. Theframework uses mobile software agents for underlyingconfiguration and policy enforcement. The paper illustratesthe effectiveness of the framework with quantitativeexperiments over simulated scenarios.INTRODUCTIONDependable communication capabilities are amongst the most important technical requirements for mission successin military operations. Complex missions involving coalitionforces, robotic support units, remote sensor beds andautonomous vehicles will require underlying communicationinfrastructures that are more flexible, efficient, androbust in order successfully operate in the face of enemyattacks.Most communications between peers in the battlefield areeither to exchange state and environmental information orto relay command and control messages. State informationincludes, for instance, relative position of troops and vehicles(enemy and friendly), sensor data from unmanned vehiclesor sensor beds, situation data, etc. This type of datais often transmitted as streams of arbitrary durations, suchas video-feeds from a camera sensor or continuous GPSposition data from moving vehicles or troops.Furthermore, the communications infrastructure must adjustto changes in overall mission goals and operationstempo. During monitoring and recognition missions, conservingpower might be the primary objective function toextend the life of network resources. However, as engagementtakes place, the communications infrastructure mayneed to quickly shift into a high performance mode to effectivelysupport and optimize the kill chain as the primaryobjective.In this paper we present FlexFeed, a mobile-agent basedcommunications framework, applied to the battlefield scenario.Our proposal leverages from years of research in thefields of mobile ad hoc networks and intelligent softwareagents to build an efficient, self-configurable, and selfhealingcommunications network for these types of environments.After an introductory description of the environment andsystem requirements, we will discuss the related work inthis area and the concepts proposed in FlexFeed. A briefdescription of the implementation details of frameworkwill be then followed by case studies, presented and experimentallyevaluated on a simulated network to illustrateFlexFeed capabilities.COMMUNICATIONS IN THE BATTLEFIELDAs part of the Army’s Objective Force to be deployedwithin the next decade, Future Combat Systems (FCS) isenvisioned as a system of systems that will integrate severallightweight, highly mobile components including newgenerations of manned and unmanned military vehicles, hese light vehicleswill partially replace heavy armored slower vehiclesin order to bring unprecedented levels of dynamism andagility to the combat theater.Furthermore, FCS operations will heavily rely on informationsuperiority to quickly take control of the battlefield and react to enemy movements and changesof strategy. This capability depends on the notion of universaltasking, where resources and information are directlyavailable at any timeto the edge warriors and commandersin the field.An enabling key-capability for this vision is an efficientand adaptive communications infrastructure to support andextend edge warrior capabilities and provide access tocritical information at any time, while at the same timeensuring optimal resource utilization and security both atthe infrastructure and information levels. Figure 1 shows aschematic view of some of the elements involved in theseeypes of operations.In general, a communications model capable of supportingFCS requirements is an ad-hoc publish/subscribe model.Soldiers and systems in the network will subscribe to sen2of 8 data and state information to plan and coordinate localtasks in response to high level instructions from the commandand control center.Figure 1 –Communications infrastructure in the battlefieldBased on FCS requirements, an appropriate data communicationsframework must be capable of satisfying the followingrequirements:a) Ad hoc: In most cases, as illustrated in figure 1, networksbetween nodes will be ad hoc, formed by proximityduring the operation itself. The communications infrastructuremust not depend on pre-established infrastructuralcomponents or centralized management stations. This capabilityis important both from a scalability and robustnessperspective, eliminating (or mitigating) single points offailure in the network.b) Efficiency: Communications and computational resourcesin the battlefield are expected to be limited andoften times, battery operated. Ad hoc sensor beds andsmall autonomous vehicles deployed during the operationwill have a life-span strictly limited by their battery life. Inmost cases, it is imperative that the communications infrastructure operate efficiently across different types of applicationsand scenarios to extend the life of network resources.c) Heterogeneity: Systems in the battlefield tend varygreatly in terms of computation and communications capabilities.Lightweight attack vehicles, small robotic units,and unmanned aerial vehicles will all have different degreesof computation and sensing capabilities andaccess tothe wireless environment.d) Application-aware Capabilities: A common limitation inmost communications frameworks currently available isthe lack of interaction between applications and theunderlyingdata transmission protocols. This limitation is oftenaccepted in lieu of the benefit of layer isolation and inmaking protocols interchangeable. For improved efficiencyhowever, the communications infrastructure canand should benefit from data-aware protocols at all levels.d) Robustness to External Attacks: The communicationsinfrastructure must be able to resist to both physical andnetwork attacks. Degradation with loss of communicationresources must be graceful and most importantly, must beselective. Special types of operations and tasks that arecritical to the overall operation must have precedence overless relevant tasks. This requirement goes beyond theconventionalnotion of quality of service in data networks.Ideally, the framework must be aware of the importance ofdata transmission not only in terms of data-type, source,and destination, but also in terms of high level goals andmission OPTEMPO in order to makeprioritization decisions.c) Robustness to Environmental Changes: The environmentalconditions, topology, and size of the network willvary significantly. In the battlefield, nodes can arbitrarilyjoin and leave the network. Nodes can be physically destroyedor made unavailable at any time. Anappropriatecommunications infrastructure must be able to cope withthese changes quickly and efficiently.e) Reactive and Proactive OPTEMPO Adaptability: Theframework must also be able to properly adapt to changein overall mission goals or situation in the battlefield. Forinstance, changes in operational tempo can be eitherpushed to or autonomously detected by framework nodes,which should automatically result in changes in the communicationsbehavior. Forinstance, when precursors ofengagement are identified, the framework, in accordancewith global policies, must autonomously switch from apower efficient mode a low latency, high performancemode to support combat systems.f) Proactive Resource Manipulation for Survivability andImproved Efficiency: This notion was initially proposedwithin the context of Agile Computing (Suri, 2002). It refersto the notion of granting the framework with the abilityto proactively manipulate physical (or logical) resourcesin the framework in order to recover criticalconnectivity segments or to significantly improve performance.g) High Level Policies for Monitoring and Control: From ahuman perspective, monitoring and control of such complexsystems is a very difficult task. An appropriate frameworkfor these types of systems must support interfaces topolicy infrastructures that would allow humans to easilydefine and establish constraints and obligations to regulatethe overalloperation of the framework. From an optimizationperspective, most policies would ultimately result inlow level constraints taken into account by the frameworkwhen deciding about resource allocation.In the last few years, a number of research proposals havebeen introduced to address some of these mon to most of them is the notion of a customizablepublish/subscribe communications mechanism capable toefficiently support messaging and data streaming.RELATED WORKConventional topic-based publish/subscribe systems suchas such as Vitria (Skeen, 1998), TPS (Eugster et al., 2001)3 of 8and JORAM (Maistre, 2003) leveraged form multicast protocolsand the assumption of a clear hierarchy on data andevents to build efficient multicast groups for topic-baseddata distribution. Multicast based protocols often providean efficient solution to the problem but they assume thatonly nodes participating in the multicast group wouldshare the data for distribution (at the level of the multicasttree). Furthermore, most multicast protocols assume data(or events) to be strictly hierarchical and processing capabilitiesfor data transformation within the hierarchy mustbe available a priori at all nodes.A number of gossip-based (or epidemic) protocols werealso proposed in the same context (Lin and Marzullo,1999; Ganesh et al., 2001; Eugster et al., 2003). In general, these are efficient and scalable protocols but assume nodata hierarchy and often make no attempt for cost or constraintoptimization based on data stream aggregationandfiltering.Multicast protocols specifically designed for peer-to-peernetworks such Scribe (Rowstron et al., 2001) and HiCan(Ratnasamy et al., 2001) came to solve scalability issues inaddressing and group coordination. They too, however,assumed that only nodes subscribedto the multicast groupwould participate in the multicast tree and that data processingcapabilities are available at all nodes a priori.Alternatives to the multicast option were also proposed atthe level of unicast routing in the form of data-aware customizedad hoc routing protocols. An important exampleof these types of data-centric routing protocols is DirectedDiffusion (Intanagonwiwat et al. 2000). The Directed Diffusionprotocol proposes a highly scalable data-aware decentralizedrouting algorithm. The protocol supports thecreation of data distribution trees including nodes that arenot directly subscribing for the data. The protocol, however,also assumes that data transformation capabilities areavailable a priori at each node, which is not a realistic assumptionfor the types of environments envisioned in FCS.More recently, Baehni et al. (2004) proposed a data-awaremulticast protocol (daMulticast) for peer-to-peer networks.The approach leveraged from some of thedata-centrictechniques for data description and group membership,significantly improving reliability and at the same timereducing the memory complexity involved in maintaininggroup membership at each node.In the most part, the approaches share the notion of usingdata-aware techniques for resource or performance optimization.The problem, however, is that data-aware frameworksare usually highly customized to a set of applicationsor data types, often requiring significant time andeffort to support new scenarios or capabilities. In manycases, such changes are not even possible, as hardwaremight have been already deployed or might be under externaladministrative control, like in the case of combat orMilitary Operations Other than War (MOOTW) coalitionoperations.THE FLEXFEED FRAMEWORKIn this paper we propose FlexFeed, a mobile-agent basedcommunications framework designed to support highlycustomized data streams in mobile ad-hoc network environmentsunder policy and resource constraints.The concepts implemented in FlexFeed were first introducedby Carvalho et al. (2002). The fundamental ideas ofthe framework are based on the concepts of Agile Computing(Suri, 2002) where network and system resources areopportunistically exploited to transparently support applicationrequests in a manner that is efficient, robust, andadaptable to changes in the environment.The FlexFeed framework is essentially based on three coreconcepts: a) Opportunistic resource exploitation; b) Flexibilityand run time self-configuration via on-demand codeand process migration; and c) In-stream data processing.Inthe framework, these capabilities are combined and extendedto address the requirements identified in the typesof environments expected in FCS.The framework uses data-aware mobile agents to bettercustomize multicast trees and to provide in-stream dataprocessing (i.e. to take advantage of the multi-hop natureof the communications path in these types of environmentsto distribute computation data processing loads). Specializedagents can be injected in the framework by authorizedparties at run-time, allowing for great flexibility and supportof highly specialized data streams. The overall behaviorof the framework is regulated by high level policiesdefined, verified, and distributed by an integrated policyinfrastructure designed for multi-agent systems. A proof-concept version of the FlexFeed framework was developedand tested both in simulated and physical environments.The framework was also demonstrated in actuallive exercises conducted by theArmy (ARL QL2, 2004)and the demonstrations for the Navy (ONR NAIMT,2004). In the subsequent items, we will briefly discuss theimplementation details of the framework, followed by experimentalsimulation results of illustrative case studies.THE FRAMEWORK COMPONENTSThe FlexFeed framework is a distributed application-leveliddleware that is installed in all participating systems.te middleware provides an API that allows applications specify services or requests for data streaming.At heimplementation , the framework combines amobile agent system with resource coordination and allo4of 8cation mechanism and a policy infrastructure to determined configure, at runtime, efficient data distribution treesbetween applications.The mobile agent system gives the framework the abilityto move code and computation between nodes to enable,on demand, new data-specific capabilities in nodes thatwill participate in the data distribution tree. Process migrationis used to improve survivability and system performance.AlthoughFlexFeed can be easily configured to workwith different agent systems, our proof of concept implementationwas developed on top of the NOMADS agentsystem (Suri et al., 2000; Groth and Suri, 2000).NOMADS is a mobile agent system for Java-based agents.It provides two implementations: Oasis and Spring. Oasisincorporates a custom Java-compatible Virtual Machine(named Aroma) whereas Spring is a pure Java implementation.The Aroma VM is a clean-room VM designed toprovide the enhanced capabilities of execution state captureand resource control.The resource coordination component (referred to in thispaper as the ‘coordinator’) is the intelligent part of theframework. It is responsible for realizing the notion of agilecomputing in the context of data streaming. The ‘coordinator’can be implemented as a distributed process or asa centralized component operating in one of the nodes ofthe framework. All experiments and examples shown inthis paper are based on one specific implementation of acentralized coordination algorithm (ULM) but decentralizedalternatives are also available.The policy infrastructure is independent of the framework.The goal of the policy framework is to provide a high levelinterface to the system in order to allow both human operatorsand applications to establish, query and modify highlevel requirements and constraints that will regulate howthe framework should operate. Furthermore, the policyinfrastructure is also responsible for validation, verification,disambiguation, and distribution of policies throughoutthe system. Policies can also be used to regulate andconstrain the autonomous behavior of the framework, providingbounds for self-adjustments to operation tempo andto the proactive manipulation of resources. Currently,FlexFeed uses KAoS (Bradshaw et al., 1997; Bradshaw etal. 2002; Bradshaw et al., 2003) as its policy framework.Access to these components is available at each nodethrough a common API. In order to participate in theframework, applications at each node can obtain an instanceof the FlexFeedManager Component (Figure 2).The FlexFeedManager provides the access API to the framework and allows applications to register, advertisecapabilities, and request data streams from other resources.Transparent to the applications, FlexFeedManagers at communicate in a peer-to-peer fashion to exchangestate and plan resource utilization. When a client places arequest for a data stream from a sensor as illustrated infigure 2, it specifies the source of the data and the requirementsfor the data stream (for example, resolutionand frame rate in the case of a video stream).That information, along with resource availability informationfrom local nodes, is used to build the data distributiontree from source to client. If using a centralized coordinator,the planning is done at one single location using globalstate data. Decentralized coordination algorithms rely onpeer to peer negotiation between FlexFeedManagers anduse only local state for planning.The client is allowed to specify any type of data, grantedthat it provides to the framework the necessary informationfor cost calculation and the code (in the form of mobileagents) necessary to manipulate (e.g. aggregation and filtering)the data for optimization. Because FlexFeed supportson-demand code deployment, trusted applicationscan provide new components to the framework at run time,enabling the support of previously unknown data types.The client can also provide complex data processing requestssuch as the one illustrated in figure 3. In that example,the client is specifying (through a graph structure) twodistinct data sources that should be merged with a specific(client-provided) processing element (FS) and then, discriminativelydelivered to two sink nodes. Details aboutthe data types and processing elements are embedded inthe graph node and edge components, using a pre-defineddata structure provided by the framework.The FlexFeed framework will load the appropriate softwarecomponents specified by the client (either from theclient host of from a common codebase) and will identifythe network resources necessary to support the request.The location of the logical fusion element (FS) can be atany intermediate node between the source and sink elements,based on resource availability, policies, and overallcosts for computation and data transmission.After mapping the request to the physical network, theframework will monitor environmental changes (such assignificant variations in resource availability or link failure)to transparently recalculate and adjust the data treeuntil the request is terminated by the client.CASE STUDIES AND EXPERIMENTAL RESULTSThe framework was tested in a simulated network wherepacket drops and bandwidthconstraints could be carefullycontrolled. The goal of these tests was to demonstrate theeffectiveness of on demand configuration of data-awarestreaming in the improvement of data quality and reductionof jitter. These metrics are highly relevant to applicationssuch as the remote control of unmanned vehicles.The overhead of the framework was also measure in termsof induced latency in the stream. The computational overheadfor running intermediate processing elements andfilters was disregarded and the coordination mechanismused in the experiments was the centralized ULM (Carvalho,2005) algorithm, based on an iterative version ofDijkstra’s shortest path algorithm applied in localized partsof the graph.The experiments were conducted on a 100baseT networkwith full connectivity. Bandwidth limitations betweenUA V and other nodes were simulated on a fixed wirednetwork. Figure 4 provides a schematic view of the testnetworks.Figure 4 – Schematic illustration of the environment consideredfor experiments In this configuration, nodes ‘S1’ and ‘S2’ represent two dismounted soldiers in direct communications range witheach other and with a tank nearby ‘T2’. All nodes are incommunications range with an unmanned aerial vehicle‘UA V’ on a fixed flying pattern over enemy territory.The bandwidth available from the UA V to the remainingnodes is variable and can be severely constrained at differenttimes. Our experimental procedure explores differentoperational scenarios on top of this configuration. The goalis to quantitatively illustrate how the FlexFeed frameworkimproves data communications by reducing delays betweenimage updates and the variance between packet arrivaltimes (jitter). In our experimental setup, each node isrepresented by a separate laptop. The bandwidth limitationson the UAV are simulated by a gateway runningNISTNet (Carson, 2002). Figure 5 shows the experimentalsetup designed to simulate the environment illustrated infigure 1.The centralized coordination node (not shown in figure 5)receives state information such as CPU and bandwidthavailability from each of the 4 nodes involved in the test.The frequency of updates is proportional to the rate ofchange in these metrics. When a client makes a request fora data stream, it specifies the source node (UA V), framerate, and resolution. The coordinator nodewill receive therequest and will handle it appropriately, building a datadistribution tree from the source, based on current globalsystem state.Optimizing Bandwidth UtilizationIn the first scenario, soldier ‘S1’ temporarily assumes controlof the UA V, taking it o ut of the flying pattern andcloser to enemy positions. Unaware of the fact that the vehicleis now under remote control, soldier ‘S2’ also requestsa video stream from the UA V’s camera. In this example,both video streams were requested at a 320x240resolution with 3 frames per second.Under unconstrained conditions, the combined streamsrequire the UA V to send approximately 50 KBps of data.In the initial condition the bandwidth limitation is 100KBps (equivalent to unconstrained bandwidth in this example)so there are no packet drops and the average delaybetween images is 271 milliseconds, which represents astream of approximately 2.69 frames per second. Note thatthe resulting frame-rate, even under unconstrained bandwidthconditions, only approximates the requested framerate.This is due to the delays involved in actual imagecapture (which is camera dependent), compression, andserialization.The bandwidth available from the UA V is then progressivelyreduced to a maximum of 40 KBps, 30 KBps, and6 of 8then 24 KBps. At each step, the average delay betweenimages is measure at each client ‘S1’ and ‘S2’.When the coordinator is inactive, that is, when the frameworkis not making any attempt to optimize data streams,the sensor (UA V) sends a unicast stream to each of theclients. Both streams will compete for the limited bandwidthand the delays at each client increase significantlywith the reduction in bandwidth availability. These resultsare shown in figure 6, with their 95% confidence errormargins.Figure 6 – Effects of bandwidth reduction without datastream coordination.In this example, as the bandwidth availability decreases,the delays quickly increase to the point where criticaltasks, such as the remote control of the UA V, are completelycompromised. A minimum frame-rate of 2 fps isrequired1, in this example, to safely navigate the UA V so itis clear that even small constraints in bandwidth availabilitycan compromise this task. Furthermore, we can verifythe well known bandwidth stealing behavior between clients,where bandwidth is not equally shared betweenstreams. This behavior has been previously reported in IPnetworks (Tschudin and Ossipov, 2004) and could compromisecritical tasks such as the control of the UA V.Figure 4 – Data distribution tree created by FlexFeedWhen the FlexFeed coordinator is enabled, the frameworkidentifies the stream requests and attempts to globally optimizedata distribution. In this specific case, the coordinator(which, is a centralized process) determines that bothstreams are similar (in fact, equal) and the overall bandwidthutilization can be reduced with a multicast-like datadistribution tree. The framework opportunistically identi-1 Although it is commonly accepted that a minimum of four frames persecond is necessary to remotely operate robotic vehicles, for illustrationpurposes in this example, the minimum requirement for teleoperationis assumed to be two frames per second.fies node ‘T2’ as a potential intermediate processing elementand builds the distribution tree illustrated in figure 4.Under the same bandwidth constraints, the framework ensuresthat the lowest capacity link (from the UA V) is notsaturated and delays between images are kept within reasonablebounds.Furthermore, the variance in delay (jitter) is significantlysmaller, ensuring that critical processes maintain minimum levels of throughput and quality of service.FlexFeed OverheadThe overhead of framework basically falls into two maincategories: a) the number of additional control messagesinvolved on sharing state between nodes (or betweennodes and the centralized coordinator) and b) the time requiredto determine, locate, and configure the nodes thatwill participate in the data stream. Both factors are highlydependent on the type of coordination mechanism used inthe framework (centralized, zone-based, or local), the complexityof the data, the scale of the network, its level ofconnectivity, and the frequency of state updates.In our example, the network topology is static and variationsin resource availability are small so our attention isfocused primarily on the delays (latency) caused by thecentralized coordination algorithm. Table 1 shows the averagedelays and their 95% confidence error margins observedin each test, both with and without the coordinator.The delays were measured as the average between the timeof the second client ‘S2’ request and the time when thefirst image is delivered to that client.When the coordinator is present (second column), there isan up-front cost in terms of latency that is due to the timespend in identifying and configuring network resources fordata distribution. When the coordinator is not present, theresponse to the data request is relatively fast at first but thedelays increase as the bandwidth is reduced. This is basicallydue to the fact that initial images are being lost on thesaturated channel when the coordinator is not present.FlexFeed versus MulticastThe data distribution tree presented in this example resemblesa data multicast tree, often obtained with conventionaldata multicast algorithms. As previously noted, FlexFeed7 of 8goes beyond conventional and data-aware multicast approachesby building a tree that include nodesthat are notnecessarily part of the multicast group (node T2 in thiscase). These nodes are opportunistically discovered andconfigured, at runtime by the framework, based on its currentresource availability, role in the network, and systempolicies.Furthermore, the configuration of node T2 can be highlydata-dependent and arbitrarily complex. In these examples,the intermediate node was use merely as a splitting pointfor the data distribution tree. It could also have receivedcustomized code to perform in-stream data transformationor specialized filtering.Consider the case where the request place by soldier ‘S2’was for a lower res olution video stream from the samesource. Multicast algorithms would often regard this as anindependent request or would have assumed that one of thenodes in the multicast group would be able to reduce theresolution of the stream to include the new request in thedata hierarchy. Data-centric protocol like Directed Diffusionwould also depend on an intermediate node’s a prioricapabilities to construct the low resolution data from thehigh resolution stream.In FlexFeed, the request placed by soldier ‘S2’ can sp ecifyreferences to data-specific code that will be installed, ondemand, on node ‘T2’ to act as a processing element. Thecode would be installed only in the necessary nodes (asdetermined by the coordination algorithms) and would beremoved when no longer necessary.Another extension of the same capability is the transparentenforcement of information release policies. In this case,upon S2’s data request, FlexFeed would query the policyframework for constraints or obligations involving the request.Consider, for example, that policies were previouslydefined to constrain unrestricted access from S2 to thatspecific data source. In that case the framework will,transparent to node ‘S2’, identify an intermediate node forpolicy enforcement and will deploy the customized datafilters (specified as part of the policy) to ensure compliancewith the specified requirements. This feature of Flex-Fleed has been extensively demonstrated by (Suri, Bradshawet al, 2003; Suri, Carvalho et al, 2003) in multiplesimulations and real life exercises.CONCLUSIONS AND FUTURE WORKIn this paper we have introduced the FlexFeed frameworkin the context of military combat operations. The conceptproposed in FlexFeed goes beyond current data-centricrouting approaches and data-aware multicast. It realizesthe notion of agile computing in the context of data communicationsand offers the basis for a truly customizablemiddleware for data communications in extreme environments.The framework is currently implemented and has beentested in several small scale exercises including soldiersoperating in conjunction with robotic units and remote systems.The framework currently relies on a centralized coordinationalgorithm for resource allocation. We are currentlydeveloping fully decentralized (and zone-based)algorithms to improve scalability, robustness, and performance.。

第44卷 第1期系统工程与电子技术Vol.44 No.12022年1月SystemsEngineeringandElectronicsJanuary 2022文章编号:1001 506X(2022)01 0279 06 网址:www.sys ele.com收稿日期:20210129;修回日期:20210516;网络优先出版日期:20210712。
网络优先出版地址:https:∥kns.cnki.net/kcms/detail/11.2422.TN.20210712.1620.018.html基金项目:国家自然科学基金(61867005,61806209,61773387)资助课题 通讯作者.引用格式:罗哲,权婉珍,张朴睿,等.单边Lipschitz非线性多智能体系统一致性追踪控制[J].系统工程与电子技术,2022,44(1):279 284.犚犲犳犲狉犲狀犮犲犳狅狉犿犪狋:LUOZ,QUANWZ,ZHANGPR,etal.Consensustrackingcontrolforone sideLipschitznonlinearmulti agentsystems[J].SystemsEngineeringandElectronics,2022,44(1):279 284.单边犔犻狆狊犮犺犻狋狕非线性多智能体系统一致性追踪控制罗 哲1,权婉珍1, ,张朴睿2,杨小冈1(1.火箭军工程大学导弹工程学院,陕西西安710025;2.国防科技大学航天科学与工程学院,湖南长沙410073) 摘 要:针对单边Lipschitz非线性多智能体系统,提出了一种分布式一致性控制方法。
首先,构建了领导跟随者动力学结构,用于实现单边Lipschitz多智能体系统的追踪控制。
然后,设计了单边Lipschitz非线性多智能体系统的一致性控制协议,可根据智能体之间局部交互信息构建分布式反馈控制,并将系统的一致性追踪问题转化为系统的稳定性问题。

通信行业英语中英对照手册(I)-OCU ISDN-Office Channel Unit ISDN的局内信道单元I/O Input / Output 输入/输出I2T Intelligent Interface Technology 智能接口技术IA Information Access 信息存取IA Intelligence Appliance 智能家电IA Internal Authentication 内部认证IA Internet Address 因特网地址IAB Internet Activities Board 因特网活动委员会IAB Internet Architecture Board 因特网体系委员会IAC Image Attenuation Coefficient 图像衰减系数IAC ISDN Access Control ISDN接入控制IAD Integrated Access Device 集成接入设备IAF Image Analysis Facility 图像分析设备IAM Initial Address Management 初始地址管理IAM Initial Address Messege 初始地址消息IAN Integrated Analog Network 综合模拟网IAN Irregularly Activated Network 不规则激活网络IANA Internet Assigned Number Authority 因特网分址机构IAP Internet Access Point 网际访问点IAP Internet Access Provider 因特网接入服务供应商IAR Intelligent Automatic Rerouting 智能型自动重选路由IAS Integrated Access Server 综合接入服务器IAS Interactive Application Server 交互应用服务器IB-DCA Interence-Based Dynamic Channel Allocation 基于干扰的信道动态分配IBC Information Bearer Channel 信息承载信道IBC Integrated Broadband Communication 综合宽带通信IBCN Integrated Broadband Communication Network 综合宽带通信网IBCN International Broadband Communication Network 国际宽带通信网络IBDN Integrated Building Distribution Network 楼宇综合布线网络IBGP Internal Border Gateway Protocol 内部边界网关协议IBI Intergrated Building Intelligent 综合大楼智能化IBMS Intelligent Building Management System 智能大厦管理系统IBN Integrated Broadband Network 综合宽带网IBS Intelligent Building System 智能大厦系统IBT Internet Browsing Terminal 因特网浏览终端IBWN Indoor Broadband Wireless Network 室内宽带无线网络IC Image Check 图像检验IC Image Compression 图像压缩IC Integrated Circuit 集成电路IC Interlock Code 互锁码ICB Incoming Call Barred 来话加锁ICBI Inter-Channel inter-Block Interference 信道间信息组间的干扰ICC Instantaneous Channel Characteristics 信道瞬态特性ICC Internet Call Center 因特网呼叫中心ICDN Integrated Communication Data Network 综合通信数据网络ICE In-Circuit Emulation 在线仿真ICE InterConnect Equipment 互连设备ICE Interface Configuration Environment 接口配置环境ICH Incoming CHannel 来话信道ICI Intelligent Communications Interface 智能通信接口ICI Inter-Carrier Interference 载波间干扰ICI Inter-Channel Interference 信道间干扰ICM Image Compression Manager 图像压缩管理器ICM Incoming Call Management 来话呼叫管理ICMP Inernal Control Message Protocol 内部控制信息协议ICMP Internet Control Message Protocol 因特网控制报文协议ICP Incoming Call Packet 呼入分组信息ICP Internal Connection Protocol 内部连接协议ICP Internet Content Provider 因特网内容服务供应商ICP Interworking Control Protocol 互通控制协议ICR Initial Cell Rate 初始信元率ICS ISDN Control Sublayer ISDN控制子层ICSA International Computer Security Associatiion 国际计算机安全协会ICT InComing Trunk 来话中继ICT Information and Communication Technology 信息和通信技术ICUG International Closed User Group 国际闭合用户群ICW Internet Call Waiting 因特网呼叫等待IDA Integrated Digital Access 综合数字接入IDA Interchange of Data between Administrations 机构间的数据交换IDA Internet Direct Access 因特网直接接入IDA Intrusion Detection Agent 入侵检测代理IDARA Improved Distributed Adaptive Routing Algorithm 改进的分布式自适应路由算法IDC Internet Data Center 因特网数据中心IDCC Integrated Data Communication Channel 综合数据通信信道IDCT Inverse Discrete Consine Transform 离散余弦逆变换IDD International Direct Dialing 国际直拨IDI Initial Domain Identifier 初始域标识符IDL Interactive Distance Learning 交互式远程学习IDL Interface Definition Language 接口定义语言IDL International Data Line 国际数据线路IDLC Integrated Digital Loop Carrier 综合数字环路载波IDMS Integrated Database Management System 综合数据库管理系统IDN Integrated Data Network 综合数据网络IDN Integrated Digital Network 综合数字网IDN Intelligent Data Network 智能数据网络IDN Interactive Data Network 交互式数据网络IDN International Directory Network 国际目录网络IDNET IDentification NETwork 认证网IDP Internet Directory Provider 因特网目录服务供应商IDPR Inter-Domain Policy Routing 域间策略路由选择IDR Intermediate Data Rate 中等数据速率IDRP InterDomain Routing Protocol 域间路由选择协议IDS Intrusion Detection System 入侵检测系统IDS Isochronous Data Services 等时数据业务IDSE International Data Switching Exchange 国际数据交换机(局)IDSE Internetworking Data Switching Exchange 互连网数据交换机(局)IDSL ISDN DSL ISDN数字用户线IDSP Intelligent Dynamic Service Provisioning 智能型动态业务提供IDSS Intelligent Decision Support System 智能决策支持系统IDT Integrated Digital Terminal 综合数字终端IDT Intelligent Data Terminal 智能数据终端IDT Interactive Data Terminal 交互数据终端IDTC International Digital Transmission Center 国际数字传输中心IDU InDoor Unit 室内单元IDU Interface Data Unit 接口数据单元IEC Integrated Ethernet Chip 集成以太网电路芯片IEC InterExchange Carrier 局间载波IEC International Electrotechnical Commission 国际电工委员会IEE Institute of Electrical Engineers 电气工程师学会(英国)IEEE Institute of Electrical and Electronics Engineers 电气和电子工程师学会(美国) IEN Internet Experiment Note 因特网实验备忘录IEP Internet Equipment Provider 因特网设备供应商IEPG Internet Engineering and Planning Group 因特网工程和规划组IES ISDN Earth Station 综合业务数字网络地球站IESG Internet Engineering Steering Group 因特网工程指导组IETF Internet Engineering Task Force 因特网工程任务组IEW Intelligent and Electronic Warfare 智能和电子战IF Intermediate Frequency 中频IFD InterFace Device 接口设备IFH Intelligent Frequency Hopping 智能跳频IFIP International Federation for Information Processing 国际信息处理联合会IFITL Integrated Fiber In The Loop 综合光纤环路IFPH Inter-network FreePHone 网间被叫付费电话IFS Interactive Financial Services 交互式金融服务IFS InterFace Specification 接口规范IFS International Freephone Service 国际免费电话(被叫付费电话)IFU Interworking Functional Unit 互通功能单元IG Interactive Graphics 交互式图形IG International Gateway 国际网关IGD Interaction Graphics Display 交互式图形显示IGL Interactive Graphics Library 交互式图形库IGMP Internet Group Management Protocol 因特网组管理协议IGP Interior Gateway Protocol 内部网关协议IGRP Interior Gateway Routing Protocol 内部网关路由协议IGS Information Group Separator 信息组分隔符IHDL Input Hardware Des criptive Language 输入硬件描述语言IHL Internet Header Length 因特网报头长度IHV Independent Hardware Vendor 独立硬件商II Image Information 图像信息IIA Interactive Instructional Authoring 交互式教学写作IIA Internet Image Appliance 网络影像家电IIAS Interactive Instructional Authoring System 交互式教学写作系统IIC Incoming International Center 入局国际中心IID Image Intensifier Device 图像增强设备IIIN Intelligent Integrated Information Network 智能综合信息网络IIP Interface Information Processor 接口信息处理器IIS Internet Information Server 因特网信息服务器IIS Internet Information Service 因特网信息服务IISP Interim Inter-switch Signaling Protocol 临时的交换机间的信令协议IITA Information Infrastructure Technology and Application 信息基础设施技术及应用IITF Information Infrastructure Task Force 信息基础设施任务组IKBS Intelligent Knowledge Based System 基于知识的智能系统IKE Internet Key Exchange 因特网密钥交换IL Insertion Loss 插入损耗ILC Intelligent Line Card 智能线路卡ILD Insertion Loss Deviation 插入损耗偏差ILEC Incumbent Local Exchange Carrier 在业的本地交换运营公司ILI Idle Line Indicating 空闲线路指示ILMI Integrated Local Management Interface 综合本地管理接口ILMI Interim Local Management Interface 临时本地管理接口ILSLA Injection Locked Semiconductor Laser Amplifier 注入锁定半导体激光放大器IM Image Mixing 图像混合IM Instant Messaging 即时传信IM Integrated Modem 集成式调制解调器IM Interface Module 接口模块IM Inverse Multiplexing 反向复用IMA Interactive Multimedia Association 交互式多媒体协会IMAP Interactive Mail Access Protocol 交互邮件访问协议IMAP Internet Messaging Access Protocol 因特网消息存取协议IMAP4 Internet Message Access Protocol 4 因特网信息存取协议第4版IMC Inter-Module Connector 模块间连接器IMC International Maintenance Center 国际维护中心IMCC Inter-Module Communication Controller 模块间通信控制器IMEI International Mobile Equipment Identity 国际移动设备标识IMF InterMediate Fiber 中间光纤IMIS Integrated Management Information System 综合管理信息系统IMNI Internal Multimedia Network Infrastructure 多媒体网络内部基础设施IMP Interface Message Processor 接口报文处理器IMP Interface Module Processor 接口模块处理器IMS Information Management System 信息管理系统IMS Interactive Multimedia Service 交互式多媒体服务IMSI International Mobile Subscriber Identifier 国际移动用户标识符IMT Intelligent Multimode Terminal 智能多模式终端IMTC Internatinal Multimedia Television Committee 国际多媒体电视委员会IMTS Improved Mobile Telephone Service 改进的移动电话业务IMTV Interactive Multimedia TeleVision 交互式多媒体电视IMUX Input MUltipleX 输入复用IN Integrated Netowrk 综合网络IN Intelligent Network 智能网IN Interconnected Network 互连网络IN Internal Node 内节点IN-SL IN Service Logic 智能网业务逻辑IN-SM Intelligent Network Switching Manager 智能网交换管理器IN-SSM Intelligent Network Switching State Manager 智能网交换状态管理器IN-SSM Intelligent Network Switching Status Model 智能网交换状态模型INA Information Network Architecture 信息网体系结构INA Integral Network Arrangement 整体网络布局INA Integrated Network Architecture 综合网络体系结构INAP Intelligent Network Application Part 智能网应用部分INAP Intelligent Network Application Protocol 智能网应用协议INC Integrated Network Connection 综合网络连接INCC International Network Controlling Center 国际网络控制中心INCM Intelligent Network Conceptual Model 智能网概念模型INCS-1 Intelligent Network Capability Set-1 智能网能力组1INDB Intelligent Network DataBase 智能网数据库INDBMS Intelligent Network DataBase Management System 智能网数据库管理系统INE Intelligent Network Element 智能网元素INFM Intelligent Nework Functional Model 智能网功能模型INFO Integrated Network using Fiber Optics 采用光纤的综合网INI Intelligence Network Interface 智能网络接口INIC ISDN Network Identification Code ISDN网标识码INM Integrated Network Management 综合网络管理INM Integrated Network Monitoring 综合网监视INMARSAT INternational MARritime SAT ellite organization 国际海事卫星组织INMC International Network Management Center 国际网络管理中心INMOS IN service Management and Operation System 智能网业务管理及运行系统INMS Integrated Network Management System 综合网络管理系统INMS Intelligent Network Management System 智能网络管理系统INN Intermediate Network Node 中间网络节点INNO IN Network Operator 智能网运营商INP Intelligent Network Processor 智能网络处理器INS Information Network System 信息网络系统INS Intelligent Network Service 智能网络服务INSAT INternational SATellite 国际卫星INSES IN Services Emulation System 智能网业务仿真系统INSOS IN Service Operation System 智能网业务*作系统INSP Intelligent Network Service Provider 智能网服务供应商INSS Intelligent Network Service Subscriber 智能网业务用户INSTS IN Surveillance and Testing System 智能网监视和测试系统INT Interactive News Television 交互式电视新闻INTB IN TestBed 智能网试验台INTCO INT ernational COde of signal 国际信号码INTELSAT INternational TELecommunication SATellite 国际通信卫星(组织) INTIP INT egrated Information Processing 综合信息处理INTS Integrated National Telecommunication System 国家综合电信系统INTS INTernational Switch 国际交换INTS Inter-Network Time Slot 网络内部时隙INTSE INTelligent System Environment 智能系统环境IO Integrated Optics 集成光学IOAS Intelligence Office Automatic System 智能办公室自动化系统IOBB Input Output BroadBand 宽带输入输出IOC Input.Output Channel 输入/输出信道IOC Input / Output Controller 输入/输出控制器IOC Integrated Optical Circuit 集成光路IOC INTELSAT Operations Center 国际卫星组织*作中心IOC InterOffice Channel 局间信道IOCA Image Object Content Architecture 图像对象内容体系结构IOD Information On Demand 信息点播IODC International Operator Direct Calling 国际运营商直接呼叫IOLA Input / Output Link Adapter 输入/输出链路适配器IOLC Input / Output Link Control 输入/输出链路控制IOM Image-Oriented Memory 面向图像的存储器IOM Input / Output Multiplexer 输入/输出多路转换器IOM Integrated-Optic Modulator 集成光学调制器ION Integrated On-demand Network 综合按需服务网络IONI ISDN Optical Network Interface ISDN光网络接口IOP Input / Output Processor 输入输出处理器IOPDS Integrated-Optic Position / Displacement Sensor 集成光学位置/位移传感器IOS Integrated Office System 集成办公室系统IOS Intelligent Office System 智能办公室系统IOS Interactive Operating System 交互式*作系统IOS Internet Operating System 因特网*作系统IOS Internetwork Operating System 网间*作系统IOSB Input / Output Status Block 输入/输出状态块IOSC Input / Output Switching Channel 输入/输出交换通道IOSN Intelligent Optical Shuttle Node 智能光信息往返节点IOT Intra Office Trunk 局内中继IOTB Input / Output Transfer Block 输入/输出传送块IP Image Processing 图像处理IP Information Processing 信息处理IP Intelligent Peripheral 智能外设IP Internet Protocol 因特网协议IP Internetwork Protocol 网际协议IP Internetworking Protocol 组网协议IP Interworking Protocol 互通协议IPA Image Processing Algorithm 图像处理算法IPA Inerworking by Port Access 端口接入的互通IPBX International PBX 国际PBXIPC Integrated Peripheral Channel 集成外围通道IPC Intelligent Peripheral Controller 智能外设控制器IPC Inter-Personal Communications 人际通信IPC Inter-Process Communication 进程间通信IPC Inter-Processor Communication 处理器间通信IPCDN IP over Cable Data Network 电缆数据网传送IPIPCE International Path Core Element 国际通路核心单元IPCP IP Control Protocol IP控制协议IPCSM Input Port Controller SubModule 输入端口控制器的子模块IPDC IP Device Control IP设备控制IPE In-band Parameter Exchange 带内参数交换IPEI International Portable Equipment Identity 国际便携式设备标识IPF Image Processing Facility 图像处理设备IPG Interactive Program Guide 交互式节目指南IPG Inter-Packet Gap 分组信息间隙IPI Initial Protocol Identifier 初始协议标识符IPI Intelligent Peripheral Interface 智能外围接口IPL Initial Program Load 初始程序装入IPLB IP Load Balancing IP负载平衡IPLC International Public Leased Circuit 国际公用出租线路IPLI Internet Private Line Interface 因特网专用线接口IPLTC International Private Leased Telecommunication Circuit 国际专用租线通信电路IPM Inter-Personal Messeging 人际传信IPM-EOS Inter-Personal Message Element Of Service 人际报文业务单元IPM-UA Inter-Personal Messeging User Agent 人际传信用户代理IPME Inter-Personal Messaging Environment 人际传信环境IPMS Inter-Personal Messaging Service 人际传信业务IPMS Inter-Personal Messaging System 人际传信系统IPMS-MS Inter-Personal Messaging System Message Store 人际传信系统信息存储IPMS-UA Inter-Personal Messaging System User Agent 人际传信系统用户代理IPN Instant Private Network 瞬时专用网络IPN Inter-Personal Notification 人际通知IPng Internet Protocol next generation 下一代因特网协议IPOA IP Over ATM ATM网络承载IPIPP Internet Payment Provider 因特网支付业务提供商IPP Internet Platform Provider 因特网平台供应商IPPR Image Processing and Pattern Recognition 图像处理和模式识别IPR Intellectual Property Rights 知识产权IPS Image Processing System 图像处理系统IPS Information Processing System 信息处理系统IPS Information Protection System 信息保护系统IPS Intelligent Protection Switching 智能保护交换IPsec IP security protocol IP安全协议IPSF IP Service Function IP业务功能IPSS International Packet Switched Service 国际分组交换业务IPT Information Processing Technique 信息处理技术IPT Information Providing Terminal 信息提供终端IPUI International Portable User Identity 国际便携式用户标识IPv6 IP version 6 第六版IPIPX Internet Packet eXchange 因特网分组交换IPX Internetwork Packet eXchange 网际包(分组)交换IPX Interprocess Packet eXchange 进程间分组交换IQ Information Query 信息查询IQL Interactive Query Language 交互式查询语言IR Incoming Route 入路由IR Information Retrieval 信息检索IR InfraRed 红外IR Intelligent Robot 智能机器人IR Internal Router 内部路由器IRC Internet Relay Chat 因特网中继交谈IrDA Infra-red Data Association 红外数据协会IRFU Integrated Radio Frequency Unit 综合无线电频率单位IRI InfraRed Image 红外图像IRIM InfreRed Interface Module 远端接口模块IRIS Integrated platform for Regional Information System 地区信息系统用综合平台IRL Inter-Repeater Link 中继器间链路IRLAP InfraRed Link Access Protocol 红外链接存取协议IrLAP IrDA Link Access Protocol IrDA链路接入协议IRM Integrated Reference Model 综合参考模型IrMC Infrared Mobile Communication 红外移动通信IRN Information Resource Network 信息资源网络IRN Intermediate Routing Node 中间路由选择节点IRP Internal Reference Point 内部参考点IRP International Routing Plan 国际路由规划IRQ Information Repeat reQuest 信息重传请求IRSG Internet Research Steering Group 因特网研究指导组IRSU ISDN Remote Subscriber Unit ISDN远端用户单元IRTF Internet Research T ask Force 因特网研究任务工作组IS Imaging System 成像系统IS Information Science 信息科学IS Information System 信息系统IS Integrated Service 综合业务IS Intelligence System 智能系统IS Interactive Service 交互式业务IS Interactive Signal 交互信号IS Interface Specification 接口规范IS Interim Standard 临时标准IS-IS Intermediate System-to-Intermediate System 中间系统到中间系统ISA Industry Standard Architecture 工业标准体系结构ISA Information System Architecture 信息系统结构ISA Interim Standard Architecture 临时标准体系ISAN Integrated Service Analog Network 综合业务模拟网ISAP Interactive Speech Application Platform 交互语言应用平台ISAPI Internet Server Application Programming Interface 因特网服务器应用编程接口ISB Intelligent Signaling Bus 智能信令总线ISB Interface Schduling Block 接口调度块ISC International Switching Center 国际交换中心ISC Internet Software Consortium 因特网软件联盟ISC InterStellar Communications 星际通信ISCC International Service Coordination Center 国际业务协调中心ISCCI International Standard Commerical Code for Indexing 国际标准商用索引代码ISCII International Standard Code for Information Interchange 国际标准信息交换代码ISCP ISDN Signaling Control Part ISDN信令控制部分ISDCN Integrated Service Digital Center Network 综合业务数字中心网ISDN Integrated Service Digital Network 综合业务数字网ISDN-BA ISDN Basic rate Access ISDN基本速率接入ISDN-BRI ISDN Basid Rate Interface ISDN基本速率接口ISDN-PRA ISDN Primary Rate Access ISDN一次群速率接入ISDN-PRM ISDN Protocol Reference Model ISDN协议参考模型ISDN-SN ISDN Subscriber NumberISDN-UP ISDN User Part ISDN用户部分ISDS Integrated Switched Data Service 综合交换数据业务ISDT Integrated Service Digital Terminal 综合业务数字终端ISDX Integrated Service Digital eXchange 综合业务数字交换ISE Integrated Service Exchange 综合业务交换局ISE Integrated Switch Element 综合交换单元ISE Intelligent Synthesis Environment 智能综合环境ISEC Internet Service and Electronic Commerce 因特网服务和电子商务ISH Information Super Highway 信息高速公路ISIDE Interactive Satellite Integrated Data Exchange 交互式卫星综合数据交换ISL Inter-Satellite Link 卫星之间的链路ISLAN Integrated Services Local Area Network 综合业务局域网ISM Intelligent Synchronous Multiplexer 智能同步复用器ISM Interactive Storage Media 交互式存储媒体ISM Interface Subscriber Module 用户接口模块ISM Internet Server Manager 因特网服务器管理器ISM Internet Service Manager 因特网服务器管理程序ISMA Idle Signal Multiple Access 空闲信号多址ISMAN Integrated Services Metropolitan Area Network 综合业务城域网ISMC International Switching Maintenance Center 国际交换维护中心ISMS Image Store Management System 图像存储管理系统ISN Information System Network 信息系统网络ISN Integrated Services Network 综合业务网ISN Integrated Synchronous Network 综合同步网ISN International Signaling Network 国际信令网ISN Internet Shopping Network 因特网购物网络ISN Internet Support Node 因特网支持节点ISO International Standardization Organization 国际标准化组织ISOC Internet SOCiety 因特网学会ISODE ISO Development Environment ISO开发环境ISP Interactive Session Protocol 交互式会晤协议ISP Intermediate Service Part 中间业务部分ISP International Signaling Point 国际信令点ISP International Standardized Profile 国际标准化规格ISP Internet Service Provider 因特网服务供应商ISP Interoperable Systems Project 可互*作系统计划ISPBX Integrated Services PBX 综合业务PBXISPC International Signaling Point Code 国际信令点码ISR Initial Submission Rate 初始提供速率ISR International Simple Resell 国际简单转卖ISR Interrupt Service Routine 中断服务程序ISSLL Integrated Services over Specific Link Layer 专用链路层上的综合业务ISSS Interactive Subscriber Service Subsystem 交互式服务子系统ISTC International Satellite Transmission Center 国际卫星传输中心ISTC International Switching and Testing Center 国际交换和测试中心ISTV Integrated Service T eleVision 综合业务广播电视ISU Idle Signal Unit 空闲信号单元ISU Isochronous Slot Utilization 等时隙利用ISUP ISDN User Part ISDN用户部分ISV Independent Software Vendor 独立软件销售商ISVR Inter Smart Video Recorder 灵巧型视频录像机IT Information Technology 信息技术IT Information Theory 信息论IT International Transit 国际转接ITA International Telegraph Alphabet 国际电报字母表ITA2 International Telegraph Alphabet No.2 国际电报字母表第二版ITC Information Transfer Channel 信息传递信道ITC Intelligent Terminal Controller 智能终端控制器ITC International Telecommunication Center 国际电信中心ITC International Telephone Center 国际电话中心ITC International Television Center 国际电视中心ITC International Transit Center 国际转接中心ITC International Transmission Center 国际传输中心ITC InterToll Communication 长途局间通信ITCC International Telecommunication Control Center 国际电信控制中心ITD Interaural Time Difference 声源到达听者两耳的时间差ITDM Intelligent Time-Division Multiplexer 智能时分多路复用ITE Information Technology Equipment 信息技术设备ITE International Telephone Exchange 国际电话交换台ITF Information Transport Function 信息传送功能ITM ISDN Trunk Module 综合业务数字网中继模块ITMC International Transmission Maintenance Center 国际传输维护中心ITN Integrated Teleprocessing Network 综合远程处理网络ITN Intelligent Telecommunication Node 智能电信节点ITPC International Television Program Center 国际电视节目中心ITR Instantaneous Transmission Rate 瞬时传输速率ITR Internet Talk Radio 因特网无线对话ITS Independent Television Service 独立电视服务ITS Information Transfer System 信息转换系统ITS Information Transmission System 信息传输系统ITS Insertion Test Signal 插入测试信号ITS Intelligent Transport System 智能交通系统ITS International Telecommunication Service 国际电信业务ITSC International Telephone Service Center 国际电话业务中心ITSO International Telecommunications Satellite Organization 国际电信卫星组织ITSP Internet Telephony Service Provider IP电话业务提供商ITT InterToll Trunk 长途电话中继线ITTP Intelligent Terminal Transfer Protocol 智能终端转换协议ITTS Intelligent Target Tracking System 智能目标跟踪系统ITU International Telecommunication Union 国际电信联盟ITU-R ITU-Radio communications sector 国际电信联盟无线电通信组ITU-T ITU-Telecommunication standardization sector 国际电信联盟电信标准化组ITV Interactive TeleVision 交互式电视IU Interface Unit 接口单元IUI Intelligent User Interface 智能用户接口IUI Inter-User Interference 用户间干扰IUO Intelligent Underlay Overlay 智能双层网IUR Internet Usage Record 因特网使用记录IV Interactive Video 交互式视频IV Interface Vector 接口向量IVA Iitial Video Address 初始视频地址IVANS Insurance value Added Network Services 保险业增值网络服务IVAP Internal Videotex Application Provider 内部可视图文应用供应商IVBC International Videoconference Booking Center 国际电视会议登记中心IVC Independent Virtual Channel 独立虚拟信道IVC International Videoconference Center 国际会议电视中心IVD Interactive Video Disk 交互式视频盘IVD Interpolated Voice Data 内插语音数据IVDS Interactive Video Database Services 交互式视频数据库业务IVDT Integrated Voice Data Terminal 综合话音数据终端IVE International Videotex Equipment 国际可视图文设备IVG Interactive Video Game 交互式视频游戏IVHS Intelligent Vehicle and Highway System 智能车辆和公路系统IVIS Interactive Video Information System 交互视频信息系统IVMS Integrated Voice-Messaging System 综合语音信息系统IVN Interactive Video Network 交互式视频网络IVOD Interactive Video On Demand 交互式视频点播IVOT Inter-network teleVOTing 网间电子投票业务IVPN International Virtual Private Network 国际虚拟专用网IVR Integrated Voice Response 综合语音响应IVR Interactive Voice Response 交互式语音应答IVS Intelligent Video Smoother 智能视频平滑器IVS Interactive Video Service 交互式视频业务IVS Interactive Videodisc System 交互式视盘系统IW Information War 信息战IWAN Integrated services Wireless-Access Network 综合业务无线接入网络IWC Indoor Wireless Channel 室内无线信道IWC Interferometric all-optical Wavelength Converter 干涉全光波长变换器IWC Interferometric Wavelength Converter 干涉波长变换器IWCS Integrated Wideband Communication System 综合宽带通信系统IWF InterWorking Facility 互通设备IWF InterWorking Function 互通功能IWK Issuer Working Key 发行卡的工作密钥IWS Intelligent Work Station 智能工作站IWS Intelligent Workstation Support 智能工作站支持IWU InterWorking Unit 互通单元IXC Inter-eXchange Carrier 交互运营商IXP Internet eXchange Point 因特网交换点。

A Mobile Agent-Based Active Network ArchitectureChih-Lin Hu Department of Electrical Engineering National Taiwan UniversityTaipei,Taiwan,R.O.C.e-mail:clhu@.twWen-Shyen E.Chen Institute of Computer Science National Chung-Hsing University Taichung,Taiwan,R.O.C.e-mail:echen@.twAbstractActive networks enable customization of network func-tionality without the lengthy standard-mediated commit-tee processes.Most of the works in the literature uti-lize the capsules or active packets as the means to trans-fer code information across active networks.In this pa-per,we propose an active network infrastructure based on mobile agents technologies.In our prototype implemen-tation,mobile agents are the building blocks of carrying functional customizations,and the active nodes offer soft-ware application layers,the Agent Servers,to process mo-bile agent-specific customizations to facilitate network func-tionality.Both integrated and discrete operational models of network customizations are supported.In addition,for the application-specific protocol development and deploy-ment,an abstract protocol structure and a protocol loading mechanism are presented.Furthermore,we provide an agent management/control mechanism and devise a protocol man-agement/control mechanism.As a result,improved network functionality can be achieved.1IntroductionWith the rapid Internet proliferation and prevalence,the use of networks and the behaviors of network users are changing and diverse.A dominant TCP/IP network architec-ture can not keep up with the quick emergence of new net-work services and technologies which improve network per-formance and functionality.Without architectural support, current network environments impede the revolution of net-work communication technologies and prevalent extension of the Internet services.Several crucial problems within to-day’s Internet infrastructure can be identified.For example, difficulty of integrating new technologies and standards into the shared network infrastructure,difficulty in accommodat-ing new services with the existing architectural model,poor performance due to redundant operations at several proto-col layers,etc.However,due to being a general architecture and the existing hung investment,the networks can not be replaced rather preserved.A“matter-of-fact”premised way is upgrading and backward-compatible.Despite the strong demands to facilitate the network evolution,the employment of new network technologies and services is still confined by concerns of the lengthy standardization implementation,and widespread incremental deployment.Active networks[19]have been shown to address these issues through a fundamental change in the nature of the interoperability pared with the traditional net-work protocol,an active network aims to offer a software programmable paradigm where allows intermediate network nodes to perform dynamic network customization.Hence, active networks can fulfill rapid evolution of network tech-nologies and introduction of service applications without the lengthy process on standardizing the packet format and pro-tocols.In an active network,network messages can carry specific programs to customize services or configure network elements,and network elements can perform specific com-putation on the passing messages based on the agreement of program encoding and execution environment.For the net-work elements that do not support this agreement,they take these messages as legacy network packets and process them in ordinary way.In this way,new services can be brought in rapidly without the requirement for incremental deploy-ment or the need to construct an overlay.As a result,active networks can ameliorate network computation capability and functionality.Two main different approaches[19],discrete,and inte-grated approaches,have been introduced to create active net-works.With the discrete approach,e.g.,ANTS[20],CANES [4],DAN[10],the programs are injected into the nodes from the actual data packets traversing through network nodes. With integrated approach,e.g.,IP Option[22],ANEP[1], Smart Packet[17],every message can be treated as a“pro-gram.”A message(so-called capsule)contains a program fragment that may include embedded data to traverse net-work nodes.In addition,a mixed approach of these two,e.g.,SwitchWare[2],NetScript[9],has also been proposed. However,capsules or active packets are merely suitable to transferring miniature programs and the discrete pre-loading approach is not the ultimate goal of active networks to estab-lish aflexible architecture.To exploit programmable archi-tecture in“service introduction[21]”,in this paper,we pro-pose to use mobile agents[15]to establish an active network which elegantly support both two approaches.Mobile agents are characterized by their ability of roam-ing through wide area networks,autonomy of operating asynchronously with foreign hosts,and performing tasks on behalf of end-users.The methodology of mobile agent tech-nology supports encapsulation,program interposition,and execution,which makes a mobile agent as a suitable building block for the construction of active networks[11].Compared to capsules or active packets which are mainly for code trans-fer between network elements,mobile agents not only sup-port code transfer mechanism but also inherit the crucial fea-tures of the mobile agent technology.Summarily,the bene-fits[14]to use mobile agents includes reducing network traf-fic,protocol encapsulation,asynchronous and autonomous execution,dynamical adaptation,integrating heterogeneous systems,and achieve robustness and fault-tolerance.Over the past two years,we have developed an open mo-bile agent infrastructure,Pathfinder[7][6],to demonstrate agent distributed computation capacity.In this paper,we further exploit the capability of mobile agents to construct a mobile agent based active network architecture.Our pro-totype basically supports weak mobility,which is the ability of allowing code transfer across different active network el-ement,rather that the proactive or reactive migration,and remote cloning of strong mobility.Initially,we apply mo-bile agents common with capsule approach that provides a code transfer across network elements.However,essentially the scheme of a mobile agent is more adaptable than other approaches.Our experiment has shown mobile agents being effective in deploying specific customization.In addition, for the demand of monitoring mechanisms at mobile agents, we have devised an agent management mechanism,either absent or incomplete in the other architectures,which makes the mobile agent approach more viable in an active network construction.Our active network architecture isflexible enough to pro-vide rapid service introduction.For the application-specific protocol development and deployment,we integrate the de-screte(out-of-band)and integrated(in-band)transfer models by which a mobile agent can utilize to introduce network ap-plications and services.A mobile agent can be a“all-in-one”mobile agent which carries the main specific code objects along with the dependencies across an active network,or be a compact mobile agent which contacts with some service agent to indirectly perform customization.Basically,the in-stallation and configuration of a service agent is similar to other discrete approaches in an out-of-band way.Note that, furthermore,we employ a“third party”,which serves a ser-vice provider with trusty authentication to promote the ser-vice deployment.Although some degree of the effectiveness and performance will be compromised,this mechanism of service propagation can be simplified.The rest of the paper is organized as follows.Section2 presents some background and related work.Section3first describes a high-level abstraction of our proposed active net-work architecture and then the design of individual archi-tecture components,network communication protocols,and service deployment.Section4discusses the implementation of the architecture prototype.Finally,Section5gives some concluding remarks and future research topics.2Background and Related WorkThis sectionfirst describes the active network computa-tion model and the relationship between mobile agent tech-nology and active networks.The current active network re-search works are then introduced.2.1Active Network Computation ModelAn active network is a programmable network that allows intermediate nodes to perform computations up to the appli-cation layer;in addition,“end-users”can program the net-work by injecting their programs into it[16].By that reason, the nature of the network service is defined by the behavior of the individual nodes of the network,and how users can con-trol that behavior through coded information placed in their packet[5].Within an active network the network elements can have the functionality of dynamical control and network behavior.Furthermore,a message can consist of both pro-grams and data.The embedded programs can provide the control functions,and the data can replace the payload of the traditional packet,but in a form of a customizable structure used by the programs.Messages can inject the carried pro-grams into the network elements to customize the specific services or even to configure the network elements them-selves.Therefore,the network elements can perform cus-tomized computation upon subsequent messages following the path according to a prior specification by messages.In this way,more and more specific functions can be deployed into the networks in an effort to better service the users. 2.2Relationship between Mobile Agent Technol-ogy and Active NetworkMany active network architectures currently use code mo-bility paradigm[11]that is very close to mobile software agent technology.However,the idea of active network is much more general in terms of protocol encapsulation,and service customization,deployment and maintenance.A fun-damental difference is that active networks use the concept of network layer processing,whereas mobile agent systems run as application programs.General mobile agent systems are designed to support“agent migratory computation”to construct a ubiquitous Internet computing environment.In contrast,the primary purpose within active networks is to enable communication facilitation,and eventually to offer a flexible,dynamically customization,and programmable net-work infrastructure.The mobile agent paradigm proposes to treat the network as multiple agent-friendly environments, and mobile agents as programmatic entities migrating from one location to another to perform user-specific tasks.How-ever,active network conceptualizes the network as a collec-tion of active nodes that can perform any computations,and a collection of active packets that carry programs.From this point of view,a mobile agent may be regarded as a specific type of an active packet,and a mobile-agent-compatible node of traditional networks could be regarded as a specific type of an active node[16].2.3Active Network ResearchCurrently,some researchers are defining a general archi-tecture[18]for active network elements that contains mul-tiple execution environments to achieve component interop-erability.The Active Network Backbone(ABONE)is being used to test execution environments and implemented appli-cations.The major challenge in implementing this general architecture is to determine trade-off among usability,flexi-bility,security,and performance concerns.Due to the space limitation,we list just some related work in the literature as follows.MIT’s ANTS[20]features the capsule,a packet of Java byte-coded program,to carry spe-cific customization along with data payload.An ANTS’s node with Java Virtual Machine(JVM)exports API for a capsule interpretation and execution.In ANTS,capsule can install states and invoke preloaded classes.The granularity of control is at theflow/packet level[5].SwitchWare[2] at the University of Pennsylvania is based on the layered SANE and uses the scripting language called PLAN[12]to enable strong resource management and security guarantees. In SwitchWare,the packet is not allowed to install states in a network Script[9]at the Columbia University es-tablishes an agent-based middleware for programming func-tions of intermediate network nodes.It explores alternative models of active networks in which new services are intro-duced for control,rather than data transfer purposes,or by network management agents,rather than all users.BBN’s SmartPacket[17]applies active networks to assist the prob-lems of managing networks through the use of language de-sign techniques,with the Sprocket and Spanner languages. The Sprocket program is complied into Spanner code to yield very small(smaller than1Kbyte)encoded program. CANES[4]and Liane[3]at the Georgia Institute of Tech-Figure1.A Mobile Agent Based Active Network nology attempts to construct dynamic,trustworthy services by utilizing a reduced programming model that gives a set of reliable,pre-defined base services through control infor-mation in packet header.The advantage is that designers can limit the required security analysis.DAN[10]at Washing-ton University,similar to the approach of CANES,devises a DAN network packet,which contains afinite sequence of identifiers for functions and parameters.DAN aims to set up a topology of code servers in a large scale to simplify code distribution.Our work is complementary to several other active net-work efforts.We utilize the Java-based mobile agents as the building blocks of our active network architecture,to ex-plore the potential of mobile agent technologies.Although the standard of JVM does not allow access to low-level transmission resources and the implementations are limited to the basic network capabilities of Java,similar to ANTS and NetScript,the use of general-purpose Java bytecode and JVM can speed up the development process of our architec-ture.3A Mobile Agent Based Architecture This section describes the architecture design and consid-erations of our active network environment.Both agent mi-gratory computation models and enhanced network function-ality can be simultaneously provided in this active network architecture3.1Architecture OverviewAs illustrated in Figure1,our active network architecture consists of a group of active nodes which are interconnected across the local or wide area and by point-to-point or shared medium channels.An Agent Server sits at the top layer of each active node.Based on the agreement of program encod-ing and execution environment,an Agent Server will handle mobile agents which carry specific customizations and pro-vide them with restricted,transient execution environments. In this way,specific services can be deployed into networksFigure2.The Logical Format of a Mobile Agentfrom active nodes to node by terms of the transport of mo-bile agents.In addition,dynamical code loading mechanism is utilized to remotely load referred protocol code objects as need.If a network element does not support the agreement, it processes these network messages(mobile agents)using default protocols.Therefore,active network nodes are com-patible with legacy networks.3.2Mobile Agent Logical FormatIn our design,a mobile agent contains the specific pro-grams together with data payload over active network envi-ronment.The data within mobile agents is in a customizable structure and the computational states of mobile agents can be portable.As depicted in Figure2,a mobile agent must contain an Agent Header to identify themselves from other network messages.Agent Datafiled includes the mobile agent attributes and related arguments or information used for this agent execution at active nodes in active networks. Agent Specific Customizationfield involves the specific code objects to be executed at active nodes.Agent Payloadfield contains delivered data or agent computational results for mi-gratory computing purpose.3.3Agent Communication ProtocolAn agreement of mobile agent communication protocol is a prerequisite for mobile agents to traverse an active net-work.In the beginning,we implemented this protocol based on the Agent Transfer Protocol(ATP)specification[13].The original ATP aims to demonstrate mobile agents endued with ubiquitous computing capacity.At the same time,manage-ment and control mechanisms are either absent or not com-plete in most mobile agent architectures as well as active net-work architectures.With the demand of monitoring mecha-nisms at mobile agents or active messages;as a result,in this paper our architecture has enhanced ATP by adding manage-ment and control actions[8].Figure3shows the life cycle of a mobile agent in our proposed architecture.As a mo-bile agent arrives at an active node,it can be in one of the five states-running,suspended,stopped,aborted,and com-pleted.3.4Agent Server DesignAs shown in Figure4,basically an active node runtime environment is logically divided into two layers,the lower layer is the physical network node and the higher layer is the Agent Server.The Agent Server provides the agent-to-Figure3.The Life Cycle of a Mobile AgentFigure4.Active Node Runtime Environmentnode interface is the real entity which mobile agents con-tact with for network customization.Through the consistent interfaces,mobile agents can indirectly access the local re-sources to facilitate agent computation and communication.3.4.1Components in an Agent ServerAgent Context is a transient agent execution environment.A mobile agent is constrained to achieve local resource only through this interface to use the primitives of Agent Server. Agent Security Manager is to check any operations outside the Agent Context,filter out malicious agent behaviors and unwanted interactions.Currently we practice uniform con-trol of system resource upon all mobile agents.ATP Handler distinguishes active messages from incoming channel and passes it to the evaluation procedure.Similarly, ATP Handler transfers the wrapped mobile agent in an active message in ATP format.Agent Manager records all the mobile agents and instanti-ated service agents,and manages the deployed protocols at this node.Repository Manager stores the protocol-specific“soft-states”and information for agent coordination and collab-oration.3.4.2Primitives in Agent ServerThe initial set of primitives in the Agent Server decides what processing routines mobile agents can do on activenodes,then affects what applications or services mobile agents can deploy in active nodes.For the efficiency aspect in application or protocol development,such a set of primi-tives is applicable for the compactness and effectiveness of mobile agents.In our scheme we suggest that this initial set should include at least the following primitives.Local storage access:the primitives to access the local node resources,e.g.,the localfiles.Local environment access:the primitive to obtain the active node environment information,e.g.,port status.Agent repository access:to store/access shared“soft-states,”arguments or objects of application-defined to per-form cooperative applications.Agent manipulation primitives:the primitives for a mobile agent to access its header,agent date,specific customization and payload and manipulate itself during agent execution. Agent communication channels access:to access the net-work communication channel to achieve agent migration be-tween active nodes.Mobile agent control operations:the agent manage-ment/control operations,e.g.suspend and terminate oper-ations.3.5Applications/Services Deployment Scheme 3.5.1An Abstract Protocol StructureFor the rapid applications/services protocol developments and deployments,an abstract data structure of protocol is necessary.In our design,this abstract protocol structure would enclose the protocol identifier,protocol-defined infor-mation of service agent,protocol-defined arguments,protocol-defined code objects,etc.Any new pro-tocol development has to extend this protocol abstraction so that all protocols have a uniform structure.Therefore,in our active network environment an active node will be enabled to operate,administrate and maintain(OA&M)those deployed protocols.3.5.2Protocol Deployment MechanismsSince neither integrated nor discrete approach suits every need for active networks,we havefirstly devised a mobile agent in combining both of two transfer models.Further-more,we employ a“third party”-a Service Provider,to as-sist the protocol deployment.Active nodes should prohibit arbitrary injection of application-specific code.The customization right is granted only to a few authenticated users for safety and security rea-sons.As a result,it is reasonable and amenable that we em-ploy a“service provider”with trusty authentication to launch trustworthy mobile agents to promote the protocol deploy-ment mechanisms.The third parties are the repository of application-specific codes,by responding to“protocol code requests.”The mechanisms of protocol propagation can be simplified although some degree of the effectiveness and per-formance will be compromised.4Prototype ImplementationSection4.1firstly lists the characteristics of our mobile agents based architecture.Section4.2introduces the exper-imental environment.Section4.3describes the implemen-tation of encapsulating a mobile agent.Section4.4explains how an agent server works.Mobile agent operational model is introduced in Section4.5and mobile agent management mechanism is given in Section4.6.Finally,Section4.7de-scribes the protocol deployment and management mecha-nisms.4.1Characteristics of Our ArchitectureA mobile agent includes an itinerate schedule used foragent mobility.This schedule provides the information about how this agent is transferred within active net-work;hence we can get agent information from it.An Agent Server provides individual incoming mobile agent a transient execution environment.Different mo-bile agents perform different tasks bounded in its in-dividual agent context at an active node.No resource conflict and overlapping will happen.The ATP communication protocol provides agent mo-bility operations and our extensions add the needed management and control operations.A specific service agent in an Agent Server is responsi-ble for mobile agents of a specific applications/services.Multiple service agents can be installed in Agent Server.As a result,multiple services are feasible in active net-work through the service agent facility.The design of the abstraction of protocol structure en-ables the dynamical protocol deployment across active nodes.4.2Experimental Prototype EnvironmentOur prototype is implemented in the Java programming language.The programs of the Agent Server and mobile agents are compiled in JDK1.1.x.The experimental plat-forms include Windows98,Linux Slackware2.0.35and So-laris2.5workstations,which all support Java Virtual Ma-chine.Our prototype uses the enhanced Agent Transfer Pro-tocol(ATP)in application layer and the lower layer is the conventional TCP/IP protocol.4.3The Encapsulation of Mobile AgentFigure5depicts the syntax and structure of agent encap-sulation.Agent Header Field identifies the ATP communi-Figure5.The Mobile Agent Encapsulationcation protocol.The prefix of the header identifies itself as one kind of ATP message according to our ATP specifica-tion.The contents of Agent Data Field1are open for the network designer to define.For instance,User ID identifies the service provider with trusty authentication;Arguments contains all the related information referred or modified by customization process;Agent ID is a unique ID for manage-ment and control purposes.Agent Specific Customization Field stores lead class and all necessary other classes.When Agent Server receives a mobile agent,it will extract thisfield, and execute the customization.Agent Payload Field stores the intermediate/final computational results of String type.4.4Agent Server ImplementationOur prototype provides an Agent Server,which is a software application layer,to run on an active node to support the specified customizations on behalf of mobile agents.Functions of Agent ServerFirst,an Agent Server can parse the incoming active messages,and accordingly generate this agent and then export it a transient execution environment.Second,it can encloses this mobile agent code objects,arguments, dependencies and intermediate results as an active message, and then dispatch it to the next active node.Third,it can pass a mobile agent to its corresponding service agents. Finally,an Agent Server can apply agent control operations accordingly by ATP control messages from the Management Server.Agent Server InstantiationWhen an active network is instantiated,the Agent Server in an active nodefirst initializes the prototype propertiesService agent is a stationary agent in active node,and can provide assistance for mobile agents to customize the active node.Basically,service agents are separate entities from the agent server;therefore,the functions of service agent can beflexibly designed and developed to meet specific application demands.In this case,the agent server is just an intermediator that passes the mo-bile agents to respective service agents.Multiple ser-vice agents can reside in one active node for different services without complicating the agent server’s design.Our prototype utilizes the multiple service agent facili-ties to enable application/protocol deployments and de-velopments.4.6Mobile Agent Management and ControlWe use four tables-Agent Table,Launch Table,Service Table and Management Table to record the management and control information in our prototype.Each Agent Server em-ploys an Agent Table to record the information of the arrived mobile agent as well as service agents.When starting a ser-vice agent,Agent Server assigns a port to this service agent, and then records it.Once a mobile agent requests a service agent to help the assigned customization,it can look up the Service Table by the“service agent name”to get the corre-sponding port.The Management Table located in the Man-agement Server is used to record the information of launched mobile agent in active network.When the Mobile Support-ing Server launches a mobile agent,it also sends this infor-mation to the Management Server.Hence,the Management Server can manage/control a launched mobile agent accord-ing to its record.Note that because the Management Server does not actively trace the launched mobile agent in our im-plementation,the information in the Management Table may be out-of-date.However,the information is still useful for us to locate mobile agents.4.7Protocol Deployment and DevelopmentThe Abstract Data Structure of ProtocolOur prototype implements a data structure to maintain the abstract information and dependencies of the protocol. The Figure6shows the ProtocolInfo constructor.Vec-tor ClassGroup records all of the protocol-specific mobile agent names.Because in our prototype, multiple mobile agents can be grouped in a protocol do-main,they can perform collaboration or coordination in an Agent Server.String Service Name records the ser-vice agent name of this protocol.Vector Arguments serve as a temporary repository which stores all the protocol-related arguments or parameters.Protocol DeploymentPublic class ProtocolInfo {public ProtocolInfo( String uid, String pid, Vector class_group,Vector agent_group, String sa_name, Vector args ) { User_id = uid;Protocol_ID = pid;Protocol_Status = RUNNING;Class_Group = class_group;Service_Agent_Name = sa_name;Arguments = args;}......}Figure6.The ProtocolInfo Constructor Initially,an Agent Server only permits the agent’s cus-tomization if and only if the protocol status is“RUNNING.”In order to meet the ultimate goal of dynamical protocol deployment,our prototype employs the trustworthy Service provider to facilitate the protocol deployment.The location of Service Provider is default specified,and also we can flexibly assign its location in the Arguments Vector of the Agent Data Field.Note that,it is reasonable that we create a new default channel for the utilization of protocol deployment to communicate among a Service Provider and Agent pared that ANTS[20]implemented their protocol propagation mechanisms by referred to the last active node where this mobile agent comes from. Intuitively,our prototype also can perform this mechanism. However,in order to reduce the complexity of implementing the prototype,we employ the central Service Provider.In addition,through the facility we can efficiently handle the protocol propagation.Protocol Management and ControlOur implementation can support multiple protocols si-multaneously in an Agent Server.In addition,mobile agents with different specific customizations can deploy different protocols in an active node.In order to maintain efficiently the deployed protocols,the Agent Server employs a Protocol Table,as shows in Figure7,which records the information of the deployed protocols for protocol management and control in an active node.When an Agent Server is instantiated,itfirst stores the information of deployed protocols into the Protocol Table. When a new protocol is deployed in this active node,its in-formation is recorded in this table.Moreover,trustworthy third parties are granted the authority to delegate a mobile agent to adapt the configurations of their deployed protocols on the active nodes.。

习题及答案Chapter 01 Human Resource Management: Gaining a Competitive Advantage Answer KeyTrue / False Questions1. (p. 5) Companies have historically looked at HRM as a means to contribute to profitability, quality, and other business goals through enhancing and supporting business operations.FALSE2. (p. 5) The human resource department is most likely to collaborate with other company functions on outplacement, labor law compliance, testing, and unemployment compensation.FALSE3. (p. 6) The three product lines of HR include a) administrative services and transactions, B) financial services, and c) strategic partners.FALSE4. (p. 9) The amount of time that the HRM function devotes to administrative tasks is decreasing, and its roles as a strategic business partner, change agent, and employee advocate are increasing. TRUE5. (p. 9) Advances in technology have allowed HR services to be offered more on a self-service basis than in the past.TRUE6. (p. 9) HR functions related to areas such as employee development, performance management, and organizational development are outsourced most frequently.FALSE7. (p. 11) Evidence-based HR provides managers with data to make decisions, instead of just relying on intuition.TRUE8. (p. 14) Stakeholders of a company are shareholders, the community, customers, employees, and all of the other parties that have an interest in seeing that the company succeeds.TRUE9. (p. 19) Companies are now more and more interested in using intangible assets and human capital as a way to gain an advantage over competitors.TRUE10. (p. 22) A learning organization places the highest emphasis on completion of formal employment training.FALSE11. (p. 22) The psychological contract describes what an employee expects to contribute and what the company will provide to the employee in return for these contributions.TRUE12. (p. 25) The use of alternative work arrangements, which include independent contractors, on-call workers, temporary workers, and contract company workers, is shrinking.FALSE13. (p. 27) To be effective, balanced scorecards must be customized by companies to fit different market situations, products, and competitive environments.TRUE14. (p. 27) The balanced scorecard should not be used to link the company's human resource management activities to the company's business strategy.FALSE15. (p. 30) Corporate cultures within companies that successfully implement TQM typically emphasize individualism, hierarchy, accountability, and profits.FALSE16. (p. 31) ISO 9000 certification is an integral component of W. Edwards Deming's quality control process.FALSE17. (p. 34) The skills and motivation of a company's internal labor force determine the need for training and development practices and the effectiveness of the company's compensation and reward systems.TRUE18. (p. 37) Because the workforce is predicted to become more uniform in terms of age, ethnicity, and racial background, it is likely that one set of values will characterize all employees.FALSE19. (p. 39) Cultural diversity can provide a company competitive advantage regarding problem-solving. TRUE20. (p. 42) The Sarbanes-Oxley Act of 2002 sets strict rules for corporate behavior and sets heavy fines and prison terms for noncompliance.TRUE21. (p. 43) Every business must be prepared to deal with the global economy.TRUE22. (p. 48) One of the disadvantages of technology is that it does not allow older workers to postpone retirement.FALSE23. (p. 51) E-HRM is more applicable to practices associated with recruiting and training than those associated with analysis and design work, selection, and compensation and benefits.FALSE24. (p. 54) An HR dashboard is a series of indicators that managers and employees have access to on the company intranet or human resource information system.TRUE25. (p. 58) Compensating human resources involves measuring employees' performance.FALSEMultiple Choice Questions26. (p. 4) _____ refers to a company's ability to maintain and gain market share in its industry.A. OutsourcingB. CompetitivenessC. Self-serviceD. Empowerment27. (p. 4) _____ refers to the policies, practices, and systems that influence employees' behavior, attitudes, and performance.A. Total quality managementB. Financial managementC. Human resource managementD. Production and operations management28. (p. 5) Strategic HR management includes all but one of the following. Name the exception.A. Financial planningB. Training and developmentC. Performance managementD. Recruiting talent29. (p. 6) Which of the following is NOT a responsibility of HR departments?A. RecruitingB. BenefitsC. Community relationsD. Production and operations30. (p. 6) Which of the following is NOT a product line of human resources?A. Administrative services and transactionsB. Strategic partnerC. Human capital partnerD. Business partner services31. (p. 8) Which of the following best describes a cultural steward?A. Shapes the organization.B. Delivers results with integrity.C. Facilitates change.D. Recognizes business trends and their impact on the business.32. (p. 8) A strategic architect is one who:A. facilitates change.B. recognizes business trends and their impact on the business.C. implements workplace policies conducive to work environment.D. develops talent and designs reward systems.33. (p. 9) Giving employees online access to information about HR issues such as training, benefits, and compensation is known as:A. outsourcing.B. continuous learning.C. self-service.D. strategic planning.34. (p. 9) The practice of having another company (a vendor, third-party provider, consultant) provide services traditionally associated with the administrative role of HR is known as:A. e-commerce.B. empowering.C. outsourcing.D. benchmarking.35. (p. 10) Traditionally, the HRM department was primarily a(n):A. proactive agency.B. finance expert.C. employer advocate.D. administrative expert.36. (p. 11) Which of the following statements about evidence-based HR is FALSE?A. It helps show that the money invested in HR programs is justified and that HR is contributing to the company's goals and objectives.B. It emphasizes that HR is being transformed from a broad corporate competency to a specialized, stand-alone function in which human resources and line managers build partnerships to gain competitive advantage.C. It requires collecting data on such metrics as productivity, turnover, accidents, employee attitudes and medical costs and showing their relationship with HR practices.D. It refers to demonstrating that human resources practices have a positive influence on the company's bottom line or key stakeholders.37. (p. 12-13) Which one of the following statements about the HR profession is FALSE?A. A college degree is required of HR specialists, but not of generalists.B. Generalists usually perform the full range of HRM activities, including recruiting, training, compensation, and employee relations.C. Professional certification in HRM is less common than membership in professional associations.D. The primary professional organization for HRM is the Society for Human Resource Management.38. (p. 13) All of the following competitive challenges faced by companies will increase the importance of human resource management EXCEPT:A. the global challenge.B. the challenge of sustainability.C. the political challenge.D. the technology challenge.39. (p. 14) _____ refers to the ability of a company to survive and succeed in a dynamic competitive environment.A. OutsourcingB. EmpowermentC. SustainabilityD. Resource management40. (p. 14) Sustainability includes all of the following EXCEPT:A. expanding into foreign markets.B. the ability to deal with economic and social changes.C. engaging in responsible and ethical business practices.D. providing high-quality products and services.41. (p. 19) Which of the following statements about intangible assets is FALSE?A. They include human capital.B. They are less valuable than physical assets.C. They are equally or even more valuable than financial assets.D. They are difficult to duplicate or imitate.42. (p. 20) Tacit knowledge is an example of _____ capital.A. socialB. customerC. humanD. intellectual43. (p. 21) Which of the following is NOT true of knowledge workers?A. They often contribute specialized knowledge that their managers may not have, such as information about customers.B. They have many job opportunities.C. They are in high demand because companies need their skills.D. They contribute to the company through manual labor and intellectual labor.44. (p. 21) Empowering is defined as:A. the movement of women and minorities into managerial positions.B. giving employees responsibility and authority to make decisions regarding all aspects of product development or customer service.C. leading employees by the strength of one's charisma.D. the act of continually learning and improving one's skills and abilities.45. (p. 22) A(n) _____ contract describes what an employee expects to contribute and what the company will provide to the employee for these contributions.A. employerB. employeeC. psychologicalD. job46. (p. 25) All of the following are examples of alternative work arrangements EXCEPT:A. independent contractors.B. current labor force.C. on-call workers.D. temporary workers.47. (p. 27) The balanced scorecard:A. is similar to most measures of company performance.B. uses indicators important to the company's strategy.C. is a standardized instrument of company performance.D. should not be applied to HR practices.48. (p. 27) The balanced scorecard presents a view of company performance from the perspective of:A. its customers only.B. its employees only.C. its employees and customers only.D. its employees, customers, and shareholders.49. (p. 28) According to the financial perspective of the balanced scorecard, which of the following questions should be answered?A. How do customers see us?B. Can we continue to improve and create value?C. What must we excel at?D. How do we look to shareholders?50. (p. 28) Increasingly, companies are trying to meet shareholder and general public demands that they be more socially, ethically, and environmentally responsible. Thus, companies are recognizing the importance of:A. a balanced scorecard approach to business.B. diversity.C. total quality management.D. social responsibility.51. (p. 30) TQM focuses on:A. designing processes to meet the needs of external customers only.B. reducing variability in the product or service.C. preventing errors rather than correcting errors.D. tying pay to employees' total output less rejects52. (p. 31) "How senior executives create and sustain corporate citizenship, customer focus, clear values, and expectations, and promote quality and performance excellence" is the definition for which Malcolm Baldrige National Quality Award criterion?A. Strategic planningB. Workforce focusC. Customer and market focusD. LeadershipMalcolm Baldrige National Quality Award is an award established in 1987 to promote quality awareness, to recognize quality achievements of U.S. companies, and to publicize successful quality strategies.53. (p. 33) Which one of the following is NOT true of the Six Sigma process?A. The objective of the process is to create a total business focus on serving the customer.B. Training is an important component of the process.C. The process is one of seven categories evaluated within the Malcolm Baldrige Quality Award.D. The process involves measuring, analyzing, improving, and controlling processes once they have been brought within six quality standards.54. (p. 33) Which of following holds TRUE for lean thinking?A. It is a way to do more with less effort, time, equipment, and space.B. It is a way to compete for quality awards and certification.C. It includes offering no-frills goods and services to customers.D. It is working for zero inventories.55. (p. 34) The skills and motivation of a company's _____ labor force determine the need for training and development practices and the effectiveness of the company's compensation and reward systems.A. projectedB. secondaryC. externalD. internal56. (p. 34-37) Which of the following statements about the composition of the U.S. labor force in the next decade is TRUE?A. Labor force growth is greater than at any other time in U.S. history.B. The largest proportion of the labor force is expected to be in the 16-to-24-year age group.C. There will be fewer white males than minorities or women in the labor force.D. The number of "baby boom" workers will increase faster than any other age group.57. (p. 35) Which of the following statements about older workers is FALSE?A. Worker performance and learning are adversely affected by aging.B. The aging labor force means companies are likely to employ a growing share of older workers.C. An emerging trend is for qualified older workers to ask to work part-time or for only a few months at a time as a means to transition to retirement.D. Older employees are willing and able to learn new technology.58. (p. 37) Baby boomers:A. like the latest technology, are ambitious and goal-oriented, and seek meaningful work.B. want to be noticed, respected, and involved.C. tend to be uncomfortable challenging the status quo and authority.D. value unexpected rewards for work accomplishments, opportunities to learn new things, praise, recognition, and time with the manager.59. (p. 38) Regardless of their background, most employees' value:A. the ability to challenge the status quo.B. simplistic tasks requiring few skills.C. managerial positions.D. work that leads to self-fulfillment.60. (p. 38-39) To successfully manage a diverse workforce, managers need to develop all of the following skills EXCEPT:A. providing performance feedback that is based on values rather than objective outcomes.B. communicating effectively with employees from a wide variety of cultural backgrounds.C. coaching employees of different ages, educational backgrounds, ethnicity, physical ability, and race.D. recognizing and responding to generational issues.61. (p. 39) Managing cultural diversity involves:A. enforcing EEO rules.B. creating separate career tracks for employees with families.C. establishing a strong affirmative action policy.D. creating a workplace that makes it comfortable for employees of all backgrounds to be creative and innovative.62. (p. 39) How diversity issues are managed in companies has implications for all the following EXCEPT:A. knowing how to learn.B. creativity.C. retaining good employees.D. problem solving.63. (p. 39) Managing cultural diversity can provide a competitive advantage by:A. decreasing the number of available women and minorities in the company's labor pool.B. helping women and minorities understand they must conform to organizational norms and expectations.C. helping companies produce better decisions by including all employees' perspectives and analysis.D. identifying product markets on which the company should focus64. (p. 39) In managing cultural diversity, which of the following would improve the level of creativity thereby providing competitive advantage to an organization?A. Diversity of perspectives and less emphasis on conformity to norms of the past.B. Those with the best reputations for managing diversity will win the competition for the best personnel.C. An implication of the multicultural model for managing diversity is that the system will become less determinate, less standardized, and therefore more fluid.D. Heterogeneity in decisions and problem-solving groups potentially produces better decisions.65. (p. 39) Which of the following cultural diversity arguments states that companies with the best reputations for managing diversity will win the competition for the best personnel?A. System flexibility argumentB. Marketing argumentC. Employee attraction and retention argumentD. Problem-solving argument66. (p. 39) Diversity is important for tapping all of the following skills of employees EXCEPT:A. cultural skills.B. communication skills.C. creativity.D. homogeneous thinking.67. (p. 40) What areas of the legal environment have influenced HRM practices over the past 25 years?A. Equal employment opportunity, safety and health, pay and benefits, privacy, and job security.B. Executive compensation, pay and benefits, workers' compensation, safety and health, and job security.C. Product liability, workers' compensation, equal employment opportunity, safety and health, and labor relations.D. Equal employment opportunity, patent infringement, workers' compensation, safety and health, and job security.68. (p. 40-41) There will likely be continued discussion, debate, and possible legislation in all but one of the following areas in companies. Name the exception.A. Genetic testingB. Glass ceilingC. Employment-at-willD. Design of physical work environment69. (p. 41) Litigation involving job security will have a major influence on human resource management practices because:A. work rules, recruitment practices, and performance evaluation systems might falsely communicate lifetime employment agreements that the company does not intend to honor during layoffs.B. adjustments of test scores to meet affirmative action requirements are now illegal.C. employees now bear the burden of proof in discrimination cases.D. compensation awards for discrimination claims have increased.70. (p. 41) Which of the following is one of the four ethical principles of a successful company?A. Managers assume all responsibility for the actions of the company.B. It has a strong profit orientation.C. Customer, client, and vendor relationships emphasize mutual benefits.D. It does not produce products that can be used for violent purposes.71. (p. 42) Which legislation act sets new strict rules for business especially as regards accounting practices?A. Human Rights Act of 1994B. Reverse Discrimination Act of 1990C. Sarbanes-Oxley Act of 2002D. Corruption and Practices Act of 200072. (p. 43) Which of the following is NOT a standard that human resource managers must satisfy for practices to be ethical?A. Managers must treat employees as family.B. Human resource practices must result in the greatest good for the largest number of people.C. Employment practices must respect basic human rights of privacy, due process, and free speech.D. Managers must treat employees and customers equitably and fairly.73. (p. 45) Exporting jobs from developed to less developed countries is known as:A. insourcing.B. offshoring.C. importing.D. onshoring.74. (p. 47) Exporting jobs to rural parts of the United States is referred to as:A. insourcing.B. offshoring.C. importing.D. onshoring75. (p. 48) Which of the following statements about technology is FALSE?A. The Internet allows employees to locate and gather resources, including software, reports, photos, and videos.B. Technology does not allow older workers to postpone retirement.C. The Internet gives employees instant access to experts whom they can communicate with.D. Technology has made equipment easier to operate, helping companies cope with skill shortages.76. (p. 49) Which of the following is NOT typically true of work teams?A. They are used to increase employee responsibility and control.B. They use cross-training to give employees knowledge on a wide range of skills.C. They frequently select new team members and plan work schedules.D. They assume all of the activities reserved for managers such as controlling, planning, and coordinating activities.77. (p. 49) Which of the following is NOT recommended for supporting work teams?A. Reducing flexibility and interaction between employees to maintain high productivity.B. Giving employees formal performance feedback.C. Linking compensation and rewards with performance.D. Allowing employees to participate in planning changes in equipment, layout, and work methods.78. (p. 49) All of the following statements about cross training are true EXCEPT:A. it provides teams' maximum flexibility.B. it helps in measuring employees' performance.C. it trains employees in a wide range of skills.D. employees can fill any of the roles needed to be performed on the team.79. (p. 50) Company X has offices around the globe. Its teams are separated by time, geographic distance, culture and/or organizational boundaries, and almost rely exclusively on technology for interaction between team members. Its teams are:A. virtual teams.B. geographically-concentrated teams.C. lean teams.D. teleworker teams.80. (p. 50-51) Adaptive organizational structures emphasize:A. efficiency, decision making by managers, and the flow of information from top to bottom of the organization.B. a core set of values, and elimination of boundaries between managers, employees, and organizational functions.C. clear boundaries between managers, employees, customers, vendors, and the functional areas, and a constant state of learning.D. internal linking, external linking, diversification, and a core set of values.81. (p. 51) Which of the following is FALSE about high-involvement, adaptive organizational structures?A. Employees are in a constant state of learning and performance improvement.B. Employees are free to move wherever they are needed in a company.C. Line employees are trained to specialize in one job in order to maximize efficiency.D. Previously established boundaries between managers, employees, customers, and vendors are abandoned.82. (p. 51) Employees in geographically dispersed locations can work together in virtual teams using video, e-mail, and the Internet. This e-HRM implication refers to which aspect of HR?A. RecruitingB. Analysis and design of workC. SelectionD. Compensation and benefits83. (p. 52) From the manager's perspective, an HRIS can be used to perform primarily all but one of the following. Name the exception.A. Support strategic decision makingB. Avoid litigationC. Evaluate programs and policiesD. Motivate employees84. (p. 54) A(n) _____ is a series of indicators or metrics that managers and employees have access to on the company intranet or human resource information system.A. HR dashboardB. balanced scorecardC. web portalD. Intranet85. (p. 54) All of the following HR practices support high-performance work systems EXCEPT:A. employees participate in selection process.B. jobs are designed to use a variety of skills.C. employee rewards are related to company performance.D. individuals tend to work separately.86. (p. 56) Which one of the following is NOT associated with managing the human resource environment?A. Linking HRM practices to the company's business objectives.B. Identifying human resource requirements through human resource planning, recruitment, and selection.C. Ensuring that HRM practices comply with federal, state, and local laws.D. Designing work that motivates and satisfies the employee as well as maximizes customer service, quality, and productivity.87. (p. 56) Economic value is traditionally associated with all of the following EXCEPT:A. equipment.B. technology.C. facilities.D. HRM practices.88. (p. 57) A company's human resource acquisition requirements are influenced by all of the following EXCEPT:A. terminations.B. customer demands for products and services.C. motivation and satisfaction of employees.D. promotions.89. (p. 58) Managing the assessment and development of human resources involves all of the following EXCEPT:A. measuring employees' performance.B. creating an employment relationship and work environment that benefits both the company and the employee.C. recruiting employees and placing them in jobs that best use their skills.D. identifying employees' work interests, goals, and values, and other career issues.90. (p. 58) Besides interesting work, _____ are the most important incentives that companies can offer to its employees.A. training for future work rolesB. beneficial work environmentsC. support for nonwork activitiesD. pay and benefitsEssay Questions91. (p. 8) Name and discuss the competencies that HR professionals need.定义并讨论人力资源专业人员需要的能力1. Credible activist: delivers results with integrity, shares information, builds trusting relationships, and influences others, providing candid observation, taking appropriate risks.2. Cultural steward: facilitates change, develops and values the culture, and helps employees navigate the culture.3. Talent manager/organizational designer: develops talent, designs reward systems, and shapes the organization.4. Strategic architect: recognizes business trends and their impact on the business, evidence-based HR, and develops people strategies that contribute to the business strategy.5. Business ally: understands how the business makes money and the language of the business.6. Operational executor: implements workplace policies, advances HR technology, and administers day-to-day work of managing people.92. (p. 9-10) How has the role of HRM changed in recent years? Discuss three trends that are changing the HRM function. Why have these roles changed?近年来,HRM的角色发生了怎样的变化?讨论三个改变人力资源管理功能的趋势。
M-UML:an extension to UML for the modeling of mobileagent-based software systemsKassem Saleh *,Christo El-MorrDepartment of Computer Science,American University of Sharjah,P.O.Box 26666,Sharjah,United Arab EmiratesReceived 30December 2002;revised 29June 2003;accepted 22July 2003AbstractThe Unified Modeling Language (UML)is a language for the specification,visualization,and documentation of object-oriented software systems [The Unified Modeling Language User Guide,1998].However,UML cannot describe in an explicit manner the mobility requirements needed for modeling mobile agent-based software systems.In this paper,we present M-UML,our proposed extension to UML covering all aspects of mobility at the various views and diagrams of UML.The use of M-UML is illustrated using a simple mobile voting system example.q 2003Elsevier B.V.All rights reserved.Keywords:Language extension;Mobile agents;Mobility requirements;Unified Modeling Language1.IntroductionThe agent mobility paradigm became feasible due to the advances in process migration,remote evaluation,distrib-uted object computing and mobility [2].Mobile agents are mobile objects or programs that carry executable code and data within themselves.They have several features that help them achieving their goals or business functions such as negotiating,and ordering.Intelligent agents deal with new situations for automatic problem solving and learn from past experience.They present several advantages since they are persistent and continuously running.They also reduce traffic on the network significantly since computation,encoded in the mobile agent,is brought to data rather than data to computation.In fact,there are very clear and obvious benefits of mobile agents such as offloading the network communi-cations links,freeing local computing resources,and achieving fault-tolerance by migrating to different network nodes.However,to achieve mobility,there were many important problems to address,such as,among other things,trusting agent software,trusting remote software andenvironment,the degree of autonomy we give them,fault-tolerance vis-a `-vis node failures,agent failures or com-munication failures.In electronic business,the use of modeling tools to describe business processes has a decisive impact on the success of the business implementation.Furthermore,mobile agents are very useful for performing electronic business functionalities [3]making the need for mobile agents modeling tool,like UML,crucial and highly beneficial.Studies on the use of UML in the modeling of mobile agents are rare and limited in extent.Klein et al.[4]proposed an extension to UML for mobile agents.However,their approach is limited to a specific agent platform and to specific class of mobile agent applications.Moreover,they do not provide mobility description for all views and aspects of systems,hence not covering all UML diagrams.Bauer et al.[5]introduce Agent UML for specifying multiagent interactions.In Agent UML,a new diagram type called protocol interaction diagram is developed.However,this agent-based extension did not include aspects of mobility.Also,Baumeister et al.[6]introduce an extension to the Activity Diagram (ACD)to model mobile systems.Their extension includes the introduction of two variants of ACDs for modeling mobility:a responsibility-centered variant that focuses on the actor performing the action,and a location-centered variant that focuses on the topology of locations at0950-5849/$-see front matter q 2003Elsevier B.V.All rights reserved.doi:10.1016/j.infsof.2003.07.004*Corresponding author.Tel.:þ971-6585555;fax:þ971-65858581.E-mail address:ksaleh@aus.ac.ae (K.Saleh).which actions are taking place.In this paper,we present a complete extension of UML1.4standard(M-UML)to deal with all UML diagrams:Use Case,Class,Object,Statechart, Sequence,Collaboration,Activity,Component,and Deployment diagrams.We also use this model to specify a mobile electronic voting system as an example.In this work,we do not describe a methodology for using our proposed extension,however,we only provide a simple example for illustrative purposes.The development of such methodology is the subject of our future research.The rest of the paper is organized as follows.Section2 provides some preliminary background on the Unified Modeling Language(UML),and on mobile software agents and their applications.In Section3,we introduce the Modified UML and we illustrate its use to model a simple mobile agent application.In Section4,we conclude and outline our future work.2.BackgroundIn this section,we provide some background information on the Unified Modeling Language(UML1.4)standardized by the Object Management Group(OMG),and mobile software agents and their applications in various domains.2.1.UML in briefThe UML is a de facto software industry standard modeling language for visualizing,specifying,constructing, and documenting the elements of systems in general,and software systems in particular[1].UML has a well-defined syntax and semantics.It provides a rich set of graphical artifacts to help in the elicitation and top–down refinement of object-oriented software systems from requirements capture to the deployment of software components.In UML,systems can be modeled by considering three aspects,namely,the behavioral,structural and architectural aspects.Each aspect is concerned with both the static and dynamic views of the system.The static view represents a projection onto the static structures of the complete system description.However,the dynamic view represents a projection onto the dynamical behavior of the system. Finally,views are communicated using a number of diagrams containing information emphasizing a particular aspect of the system.In the following,we describe the various aspects,views and diagrams,and their relationships.2.1.1.AspectsThree aspects of systems can be recognized,namely,the behavioral,structural and architectural aspects.The beha-vioral aspects involve the functionalities provided by the system(static behavioral aspects)and their associated interactions,their timings and their orderings(dynamic behavioral aspects).The structural aspects involve the class structures of the object-oriented software and their interrelationships(static structural aspects),and the algo-rithmic details of objects life cycles and their interactions (dynamic structural aspects).Finally,the architectural aspects are related to the deployment and distribution of software and hardware across the various distributed system components.2.1.2.ViewsAspects of systems are covered by various static and/or dynamic views,namely,the use case,design,process, implementation and deployment views.The Use Case view focuses on the behavioral aspects of a system.Primarily,it reflects the user’s concerns and requirements.This view considers the system as a ually,users,testers and requirements analysts are interested in this view.The Design and Process Views are the concern of the development team including the analysts,designers and implementors.They describe both the static and dynamic structural aspects of the system.The Design View is concerned with objects,classes and collaborations,while the Process View is concerned with software architecture issues such as concurrency,multithreading,synchroniza-tion,performance and scalability issues.The Implementation View describes thefiles and components needed to assemble and release the system.Finally,the Deployment View describes the ways to distribute,deliver and install the system components and files across the distributed nodes of the system.2.1.3.DiagramsA diagram contains model elements such as classes, objects,nodes,components,and relationships,described by graphical symbols.Moreover,a diagram can be used to describe certain system aspects at different levels of abstraction.For example,a state diagram can describe system-level input/output interactions,and can also be used to show state changes of a particular system object across multiple use cases.The nine diagrams in the UML are briefly described below.(1)Use Case Diagram(UCD):This diagram describes the functions of a system and its users.It shows a number of external actors and their connection to the use cases representing the services provided by the e cases can be inherited by another use case,allowing reusability of use cases.Also,use cases can be associated using‘use’relationship,allowing the modularization of use cases.Similarly,use cases can be associated with the ‘extend’relationship to deal with certain exceptional or abnormal conditions or situations.This diagram is used to model the static behavioral aspects of the use case view of the system to model.(2)Class Diagram(CLD):This diagram shows the static structure of classes and their possible relationships(i.e. association,inheritance,aggregation and dependency)inK.Saleh,C.El-Morr/Information and Software Technology46(2004)219–227 220the system.This diagram is used to model the static structural aspects of the Design and Process Views of the system to model.(3)Object Diagram(OBD):This diagram is a variant of a CLD and uses almost identical notation.An OBD can be an example of a CLD that shows possible instantiations of classes during system execution.This diagram is used to model the static structural aspects of the Design and Process Views of the system to model.(4)Statechart Diagram(STD):This diagram describes the possible behavior of an object using state changes.It can also be used as a system level diagram showing system state changes during the operation of the system.Therefore,this diagram can be used to model both the dynamic behavioral aspects of the use case view,and the dynamic structural aspects of the Design and Process Views of the system tomodel.(5)Sequence Diagram(SQD):This diagram shows the interactions between number of objects and their time ordering.In other words,this diagram describes a scenario involving various interacting objects.This diagram can be used to model the dynamic behavioral aspects of the use case view if the interacting objects are interface objects or actors.However,if the interacting objects are internal ones, this diagram would be then used to model the dynamic structural aspects of the design view of the system to model.(6)Collaboration Diagram(COD):This diagram shows the objects and the messages they exchange.Messages are numbered to provide a time ordering of the message.Similar to SQDs,a COD can be used to model both the dynamic behavioral aspect of the use case view,in addition to the dynamic structural aspect of the process view of the system to model.It is worthwhile to mention here that one can easily produce a SQD from the COD and vice versa.Both sequence and CODs are also referred to as interaction diagrams.(7)Activity Diagram(ACD):This diagram shows a sequential or concurrentflow from activity to another activity.An ACD consists of action states,activity states and transitions between them,and usually spans more than one use case(or functionality).This diagram uses symbols from petri nets,flowcharts andfinite state machines.Similar to interaction diagrams,an ACD can be used to model both the dynamic behavioral aspect of the use case view,in addition to the dynamic structural aspect of the design view of the system to model.(8)Component Diagram(CPD):This diagram shows the physical structure of the code in terms of code component.A component can be a source code,a binary,or executable component.A component contains information about the logical class or classes it implements,thus creating a mapping from the Design View to the Component View.A component diagram is used to model the static architectural aspects of the implementation view of the system to model.(9)Deployment Diagram(DPD):This diagram shows the physical architecture and distribution of the hardware and software components in the system.A DPD is used to model the static architectural aspects of the deployment view of the system to model.Table1summarizes the aspects,views and their supporting diagrams in UML.For a complete tutorial on UML the reader can refer to Refs.[1,7].2.2.Mobile software agentsSoftware agents and their use in various application areas such as electronic commerce have been studied extensively in the literature[8–10].These agents are personalized, continuously running and semi-autonomous programs to which people or other programs may delegate a task automating part of a business process of varying complex-ities and application domains.Mobile agents possess many characteristics,for example they are autonomous since they can chart their working plans and decide when to leave a given computer and where to go next.They are also persistent or temporarily continuous since their lifetime may extend beyond that of their creator.Intelligent agents are adaptive and able to learn from their past experiences,i.e.from the user demands, choices and tastes.In addition they areflexible,as the user can personalize them to meet his/her own criteria and preferences,therefore their working plans(behaviors and actions)are not scripted(i.e.hardcoded).Also,agents are reactive,in fact they respond in a timely fashion to new conditions,incoming requests or changes in their environ-ment.In addition to being reactive,they are active/proac-tive;they have a mission to accomplish and are task-oriented.Finally they are mobile;they are able to move from one node to another on a network until they fulfill their prescribed mission.Such agents are used in electronic commerce where they play different functions;for instance shopping agents do price comparison between shopping portals,while other agents learn examines consumer behavior and deliver personalized services accordingly,some auction sites use intelligent agents,and some other agents were proposed to Table1Aspects,views and supporting diagrams in UMLAspects/views Static view Dynamic viewBehavioral(functional)aspects:Use Case ViewUse CaseDiagramsSequence Diagrams,Collaboration Diagrams,Statechart Diagrams,Activity Diagrams Structural(design)aspects:Designand Process ViewsClass Diagrams,Object DiagramsSequence Diagrams,Collaboration Diagrams,Statechart Diagrams,Activity Diagrams Architectural aspects:ImplementationView,Deployment ViewComponentDiagrams,DeploymentDiagramsK.Saleh,C.El-Morr/Information and Software Technology46(2004)219–227221assist in bartering[11].In fact,intelligent agents help in the different purchasing decisions in electronic commerce[3,9]: need identification,product brokering,merchant brokering, negotiation,purchase and delivery,and product/service evaluation.In addition,mobile agents are used in network management,load balancing,among other distributed systems applications.The growing use of mobile agents necessitated the introduction of tools for modeling and developing mobile agent applications.Mobility is considered one of the important and advanced elements of the object model,such as the one existing in the Java programming language[12,13].3.Mobile UML by exampleIn this section,we describe the extensions made in each of the UML diagrams to allow the explicit representation of the mobility aspect.Wefirst introduce informally our mobile system we want to model.Then we introduce our modifications to the UML.3.1.Example:a mobile voting systemA mobile voting system(MVS)consists of three interacting agents,the Vote Collector(VC),the Vote Manager(VM)and the Voters.The VC is a mobile agent mandated by a stationary VM agent to collect votes from stationary voting agents(VOs).The system can be expanded to have more VMs and more VCs dealing with one VM. First,VOs have to register themselves with their assigned VM and should instantiate their stationary agent with their voting choice after receiving the list of candidates from the VM.On election time,the VCs will contact their respective VMs to get a list of voters.Each VC will then log this list with a stationary logger agent and then visit the VOs on their list to get their votes.Once done,the VCs will return back to their base station reporting to the VM the results of the vote.For simplicity,we are not dealing here with reliability and security issues.For a reference on issues of security in mobile agent systems,the reader can refer to Ref.[10].Parts of the MVS is specified in the following section to illustrate the use of M-UML.3.2.M-UMLIn this section,we describe M-UML by going through each of the UML diagrams and explaining the modifications and extensions needed to describe the mobility aspects of the example voting system to model;Table2summarizes mobility extensions proposed in this section.e Case DiagramA UCD encapsulates actors and use cases.Actors are external entities interacting with the system to model Table2Summary of M-UML Diagrams(a)K.Saleh,C.El-Morr/Information and Software Technology46(2004)219–227 222through use cases.An actor can be a software agent interacting with the system.A mobile actor is a mobile software agent that may interact with the system while at a platform away from the one at which the agent was created (i.e.the base platform).The functionality of a system or subsystem to model is described by a group of use cases.A Use Case represents a functional requirement that may involve one or more interacting actors.A mobile Use Case represents a functional requirement that involves one or more mobile actors.Therefore,at least one mobile actor is involved in a mobile use case.A mobile agent-based software system contains both mobile and non-mobile use cases.Fig.1shows a UCD of the MVS containing one mobile actor and three mobile use cases.In thisfigure,we have a mobile actor Vote Collector and a non-mobile actor Voting Manager both interacting through the mobile use case GetVotersList.Similarly,the VC is interacting with the VO through the mobile use case GetVote.Also,the VC is interacting with the Logger through the mobile use case LogList.3.2.2.Statechart DiagramAn STD is a UML diagram that consists of states and transitions linking pairs of states.Normally,an STD describes the behavior of an actor in terms of state change. An actor or object can be in a particular state at a given time.A mobile state is a state reachable while the actor or object is away from its base platform.A mobile state carries a box (M).A unidirectional link emanating from one state,the source state,and reaching another state,the sink state,is called a transition.A mobile transition is a transition linking two states that are reachable by an agent while at two different platforms.Therefore,we may have a non-mobile transition linking two mobile states,a mobile transition linking a mobile state to a non-mobile state or vice versa, and a mobile transition linking two mobile states.Mobile transitions carry a box(M).However,if an agent can reach a state while it is either at its base or away,that state will carry a dashed box(M).Similarly,if a mobile agent reaches a state while interacting remotely with another agent,the transition will carry box(R).Finally,a transition is labeled with the stereotype p agentreturn q if it corresponds to the return of the agent to its base while changing its state.Fig.2shows a STD containing both types of states and transitions in different combinations.Thefigure shows a part of the state behavior of the VC mobile agent/actor.At its base platform,the agent receives the message StartVo-tingProcess and moves from the state ReadyToMove(RTM) to the state VotingManagerReached(VMR),at which the agent is already at a different platform.At VMR,the agent sends a remote Log message to the Logger and then sends a GetVotersList message to the VM and moves to the WaitForList(WFL)state.Both VMR and WFM states are mobile states,and the transition from RTM to VMR states is a mobile transition.At WFL,the VC receives from VM the message VotersList and moves to the platform of thefirst Fig.2.Statechart Diagram of the VC.K.Saleh,C.El-Morr/Information and Software Technology46(2004)219–227223VO on the voters list while,changing its state to WaitForVote(WFV).3.2.3.Sequence DiagramAn SQD is one kind of interaction diagrams that shows the interactions among agents while time progresses.Time is represented by a vertical timeline for each agent.An interaction is represented by an arrow starting from the initiating agent directed to the receiving agent.If the initiating agent is interacting while not at its base platform, the timeline from the time this interaction occurs to the timethe agent returns to its platform will befilled with‘M’.An interaction emanating from that agent’s timeline is called a mobile interaction.A mobile interaction that implies two agents located on the same platform is labeled with the stereotype p localized q.However,a mobile interaction that implies a mobile agent and the two interacting agents are not located on the same platform will hold a box(R)at the intersection between the timeline of the initiating agent’s platform and the interaction.A dashed line on the SQD is used to trace the source platform of a mobile agent initiating either a localized or remote interaction.This means that mobile interactions need not be co-located(i.e. labeled with p localized q).For example,a mobile agent may move to a remote platform and starts to interact with other remote agents.Finally,the return of the agent to its base is represented by a directed arrow stereotyped with p agentreturn q.Fig.3shows a SQD involving mobile and both p localized q and remote interactions.The VC sends a local message GetVotersList to the VM.Once VC received the voters list,it sends a remote log message to a remote logger agent.Then the VC moves from the VM platform to a Voter(VO)agent platform on its voters list.The mobile VC sends a local message GetVote and moves on to the next voter after receiving the vote.Finally,after getting the vote from the last VO agent,VC returns to its base platform.3.2.4.Collaboration DiagramA COD is one kind of interaction diagrams that shows the behavior of interacting objects using a sequence of exchanged messages.The static relationship among objectsis well defined.Therefore,a COD shows both structural andbehavioral properties of inter-object interactions.A CODcontains objects(or class instances)and lines connectingpairs of interacting objects or agents.Each interaction islabeled by the message sequence number,the messageidentifier,and an arrow indicating the direction of themessage.Functionally,both collaboration and SQDs areequivalent.Consequently,given a SQD,we can derive theequivalent COD and vice versa.If a mobile objectparticipates in the interaction,a box(M)will be added tothe object.If the interaction is occurring at the sameplatform,the interaction line will carry the stereotypep localized q.However,if the interaction involves two remote agents while one or both are away fromtheir base platform,the interaction line will carry thebox(R).A self-loop interaction line carrying the stereotypep agentreturn q at a mobile object represents the return of the mobile object to its originating platform in the particular order given by the sequence number attached also to the interaction.Fig.4shows a COD involving mobile agents,both inremote and localized interactions.Thefirst and secondinteractions are localized interactions.The third interactionin the diagram shows that at VM’s platform,the VC,amobile object,is remotely interacting with the logger.ThisCOD is equivalent to the SQD in Fig.3.The fourthinteraction shows the VC moving to VO’s platform tointeract locally with a voter VO.Finally,thefifth interactionshows the VC returning to its originating platform.3.2.5.Activity DiagramAn ACD shows the controlflow between actions orcomplex actions called activities.It is basically a blend offinite state machines/statecharts and petri nets syntax andsemantics.However,unlike a statechart,the states repre-senting the activities in an ACD may normally span morethan one object/agent.An ACD is able to model both thesequential and parallelflow among actions and activitiesinvolved in the modeling of a use case.Moreover,an actionis a basic atomic computational step,unlike an activitywhich can be further described by another ACD hencecreating a hierarchy of ACDs.Swimlanes can also be usedto show the agent involved in performing the actionorFig.4.Collaboration Diagram.K.Saleh,C.El-Morr/Information and Software Technology46(2004)219–227224activity.A mobile action or activity involves at least one mobile agent executing at a different platform than its originating platform.A mobile use case involves one or more mobile actions or activities.If the action/activity is executed by an agent outside its originating platform,then this mobile action/activity is represented by an oval with a box (M)attached to its top left corner.Also,if the action is triggered (requested)by a mobile agent,this mobile action will carry a dashed box (M).However,if this mobile action/activity interacts with a remote agent,it will carry the box (R)instead.The return of an agent to its originating platform is represented by a mobile action stereotyped with p agentreturn q .Finally,to explicitly specify the location at which a mobile or remote action performed by a mobile agent is occurring,the action is stereotyped with p location ¼agent q .For example,both the remote action RequestLogList and the mobile action RequestList carry the stereotype p location ¼Manager q .In sum-mary,the diagram will show,in addition to the sequencing of actions/activities,the relative placement of the agents while performing those actions/activities.This extension to the ACD blends both the location-centered and the responsibility-centered extensions proposed in Ref.[6].Fig.5shows the ACD involving mobile actions/activities that are partially or completely performed by mobile agents.For example,The RequestList activity is occurring at VM’s platform and is mobile since it involves one mobile agent (the VC).Similarly,the activity CollectVotes occurring at VO’s platform is also a mobile activity.The LogListRequest activity is a remote activity since it is occurring at the VM’s platform after the VM processes VC’s request.Finally,the activity ProvideVotersList is also a mobile activity since it involves the mobile VC agent who is receiving the voters list and will carry a dashed (M). 3.2.6.Class DiagramA CLD shows the static structure of the system’s software classes and describes all relationships among those classes,including the association,aggregation and generalization relationships.A mobile class is a class from which mobile objects/agents are created.A class inheriting from a mobile class inherits its mobility feature.Classes that are part of another mobile class (in aggregation relationship)are not necessarily mobile classes.Similarly,classes associated with a mobile class are not necessarily mobile classes themselves.Classes from which mobile objects are instantiated are shown with a box (M)at the top left.However,other classes that contain behavior (methods)that is affected (communicating with)by mobile objects are shown with a dashed box (M).Moreover,a class containing behavior affected by a remote mobile agent is shown with a dashed box (R).Therefore,methods invoked by a mobile agent are labeled with either (M)or (R),depending on the location of the calling mobile agent.If a class contains methods of both types,it will carry both dashed boxes (M)and (R).Fig.6shows a CLD involving mobile and non-mobile classes.In this figure,class VM includes the method GetVotersList ðÞwhich is invoked by the mobile agent of class VC,and an object instantiated from VM is not a mobile object.This is also the same for the VO,which instances are not mobile.The class hierarchy shows the association relationships between VO,VC and the VM objects.Finally,the Logger class is associated with the VC class and carries a dashed box (R)since it contains the method logList ðÞinvoked remotely by a mobile object of class VC.This occurs by default when displaying the complete class hierarchy,showing non-mobile classes associated with mobile classes.3.2.7.Object DiagramAn OBD shows objects and links among them.An OBD is derived from a CLD and is based on the static structure of the model,but also shows multiple instances of some objects as illustrations or scenarios of the association relationships Objects made from a mobile class are mobile objects.Those mobile objects a considered themobileFig.5.ActivityDiagram.。
高三英语询问技术创新单选题50题1. Many tech companies are investing heavily in ______ to improve data security.A. artificial intelligenceB. blockchainC. virtual realityD. augmented reality答案:B。
解析:本题考查新兴科技词汇的理解。
A选项人工智能主要用于模拟人类智能,如语音识别、图像识别等,与数据安全关联不大。
B选项区块链是一种分布式账本技术,以其安全性和不可篡改的特性被广泛用于数据安全领域,符合题意。
C选项虚拟现实主要是创建虚拟环境,与数据安全不是直接相关。
D选项增强现实是将虚拟信息叠加到现实世界,和数据安全关系不紧密。
2. The ______ technology has made it possible for self - driving cars to navigate complex roads.A. 5GB. cloud computingC. big dataD. Internet of Things答案:A。
解析:5G技术具有低延迟、高带宽等特性,这些特性使得自动驾驶汽车能够在复杂的道路上进行导航,因为它能快速传输数据。
B选项云计算主要是提供计算资源的网络服务,与自动驾驶汽车导航关系不直接。
C选项大数据侧重于数据的收集、存储和分析,不是直接助力自动驾驶导航的关键。
D选项物联网强调设备之间的连接,并非自动驾驶汽车导航的最主要技术支持。
3. Tech startups are exploring the potential of ______ in the field of medical diagnosis.A. quantum computingB. gene editingC. nanotechnologyD. all of the above答案:D。
Consensus and Cooperation in Networked Multi-Agent SystemsAlgorithms that provide rapid agreement and teamwork between all participants allow effective task performance by self-organizing networked systems.By Reza Olfati-Saber,Member IEEE,J.Alex Fax,and Richard M.Murray,Fellow IEEEABSTRACT|This paper provides a theoretical framework for analysis of consensus algorithms for multi-agent networked systems with an emphasis on the role of directed information flow,robustness to changes in network topology due to link/node failures,time-delays,and performance guarantees. An overview of basic concepts of information consensus in networks and methods of convergence and performance analysis for the algorithms are provided.Our analysis frame-work is based on tools from matrix theory,algebraic graph theory,and control theory.We discuss the connections between consensus problems in networked dynamic systems and diverse applications including synchronization of coupled oscillators,flocking,formation control,fast consensus in small-world networks,Markov processes and gossip-based algo-rithms,load balancing in networks,rendezvous in space, distributed sensor fusion in sensor networks,and belief propagation.We establish direct connections between spectral and structural properties of complex networks and the speed of information diffusion of consensus algorithms.A brief introduction is provided on networked systems with nonlocal information flow that are considerably faster than distributed systems with lattice-type nearest neighbor interactions.Simu-lation results are presented that demonstrate the role of small-world effects on the speed of consensus algorithms and cooperative control of multivehicle formations.KEYWORDS|Consensus algorithms;cooperative control; flocking;graph Laplacians;information fusion;multi-agent systems;networked control systems;synchronization of cou-pled oscillators I.INTRODUCTIONConsensus problems have a long history in computer science and form the foundation of the field of distributed computing[1].Formal study of consensus problems in groups of experts originated in management science and statistics in1960s(see DeGroot[2]and references therein). The ideas of statistical consensus theory by DeGroot re-appeared two decades later in aggregation of information with uncertainty obtained from multiple sensors1[3]and medical experts[4].Distributed computation over networks has a tradition in systems and control theory starting with the pioneering work of Borkar and Varaiya[5]and Tsitsiklis[6]and Tsitsiklis,Bertsekas,and Athans[7]on asynchronous asymptotic agreement problem for distributed decision-making systems and parallel computing[8].In networks of agents(or dynamic systems),B con-sensus[means to reach an agreement regarding a certain quantity of interest that depends on the state of all agents.A B consensus algorithm[(or protocol)is an interaction rule that specifies the information exchange between an agent and all of its neighbors on the network.2 The theoretical framework for posing and solving consensus problems for networked dynamic systems was introduced by Olfati-Saber and Murray in[9]and[10] building on the earlier work of Fax and Murray[11],[12]. The study of the alignment problem involving reaching an agreement V without computing any objective functions V appeared in the work of Jadbabaie et al.[13].Further theoretical extensions of this work were presented in[14] and[15]with a look toward treatment of directed infor-mation flow in networks as shown in Fig.1(a).Manuscript received August8,2005;revised September7,2006.This work was supported in part by the Army Research Office(ARO)under Grant W911NF-04-1-0316. R.Olfati-Saber is with Dartmouth College,Thayer School of Engineering,Hanover,NH03755USA(e-mail:olfati@).J.A.Fax is with Northrop Grumman Corp.,Woodland Hills,CA91367USA(e-mail:alex.fax@).R.M.Murray is with the California Institute of Technology,Control and Dynamical Systems,Pasadena,CA91125USA(e-mail:murray@).Digital Object Identifier:10.1109/JPROC.2006.8872931This is known as sensor fusion and is an important application of modern consensus algorithms that will be discussed later.2The term B nearest neighbors[is more commonly used in physics than B neighbors[when applied to particle/spin interactions over a lattice (e.g.,Ising model).Vol.95,No.1,January2007|Proceedings of the IEEE2150018-9219/$25.00Ó2007IEEEThe common motivation behind the work in [5],[6],and [10]is the rich history of consensus protocols in com-puter science [1],whereas Jadbabaie et al.[13]attempted to provide a formal analysis of emergence of alignment in the simplified model of flocking by Vicsek et al.[16].The setup in [10]was originally created with the vision of de-signing agent-based amorphous computers [17],[18]for collaborative information processing in ter,[10]was used in development of flocking algorithms with guaranteed convergence and the capability to deal with obstacles and adversarial agents [19].Graph Laplacians and their spectral properties [20]–[23]are important graph-related matrices that play a crucial role in convergence analysis of consensus and alignment algo-rithms.Graph Laplacians are an important point of focus of this paper.It is worth mentioning that the second smallest eigenvalue of graph Laplacians called algebraic connectivity quantifies the speed of convergence of consensus algo-rithms.The notion of algebraic connectivity of graphs has appeared in a variety of other areas including low-density parity-check codes (LDPC)in information theory and com-munications [24],Ramanujan graphs [25]in number theory and quantum chaos,and combinatorial optimization prob-lems such as the max-cut problem [21].More recently,there has been a tremendous surge of interest V among researchers from various disciplines of engineering and science V in problems related to multia-gent networked systems with close ties to consensus prob-lems.This includes subjects such as consensus [26]–[32],collective behavior of flocks and swarms [19],[33]–[37],sensor fusion [38]–[40],random networks [41],[42],syn-chronization of coupled oscillators [42]–[46],algebraic connectivity 3of complex networks [47]–[49],asynchro-nous distributed algorithms [30],[50],formation control for multirobot systems [51]–[59],optimization-based co-operative control [60]–[63],dynamic graphs [64]–[67],complexity of coordinated tasks [68]–[71],and consensus-based belief propagation in Bayesian networks [72],[73].A detailed discussion of selected applications will be pre-sented shortly.In this paper,we focus on the work described in five key papers V namely,Jadbabaie,Lin,and Morse [13],Olfati-Saber and Murray [10],Fax and Murray [12],Moreau [14],and Ren and Beard [15]V that have been instrumental in paving the way for more recent advances in study of self-organizing networked systems ,or swarms .These networked systems are comprised of locally interacting mobile/static agents equipped with dedicated sensing,computing,and communication devices.As a result,we now have a better understanding of complex phenomena such as flocking [19],or design of novel information fusion algorithms for sensor networks that are robust to node and link failures [38],[72]–[76].Gossip-based algorithms such as the push-sum protocol [77]are important alternatives in computer science to Laplacian-based consensus algorithms in this paper.Markov processes establish an interesting connection between the information propagation speed in these two categories of algorithms proposed by computer scientists and control theorists [78].The contribution of this paper is to present a cohesive overview of the key results on theory and applications of consensus problems in networked systems in a unified framework.This includes basic notions in information consensus and control theoretic methods for convergence and performance analysis of consensus protocols that heavily rely on matrix theory and spectral graph theory.A byproduct of this framework is to demonstrate that seem-ingly different consensus algorithms in the literature [10],[12]–[15]are closely related.Applications of consensus problems in areas of interest to researchers in computer science,physics,biology,mathematics,robotics,and con-trol theory are discussed in this introduction.A.Consensus in NetworksThe interaction topology of a network of agents is rep-resented using a directed graph G ¼ðV ;E Þwith the set of nodes V ¼f 1;2;...;n g and edges E V ÂV .TheFig.1.Two equivalent forms of consensus algorithms:(a)a networkof integrator agents in which agent i receives the state x j of its neighbor,agent j ,if there is a link ði ;j Þconnecting the two nodes;and (b)the block diagram for a network of interconnecteddynamic systems all with identical transfer functions P ðs Þ¼1=s .The collective networked system has a diagonal transfer function and is a multiple-input multiple-output (MIMO)linear system.3To be defined in Section II-A.Olfati-Saber et al.:Consensus and Cooperation in Networked Multi-Agent Systems216Proceedings of the IEEE |Vol.95,No.1,January 2007neighbors of agent i are denoted by N i ¼f j 2V :ði ;j Þ2E g .According to [10],a simple consensus algorithm to reach an agreement regarding the state of n integrator agents with dynamics _x i ¼u i can be expressed as an n th-order linear system on a graph_x i ðt Þ¼X j 2N ix j ðt ÞÀx i ðt ÞÀÁþb i ðt Þ;x i ð0Þ¼z i2R ;b i ðt Þ¼0:(1)The collective dynamics of the group of agents following protocol (1)can be written as_x ¼ÀLx(2)where L ¼½l ij is the graph Laplacian of the network and itselements are defined as follows:l ij ¼À1;j 2N i j N i j ;j ¼i :&(3)Here,j N i j denotes the number of neighbors of node i (or out-degree of node i ).Fig.1shows two equivalent forms of the consensus algorithm in (1)and (2)for agents with a scalar state.The role of the input bias b in Fig.1(b)is defined later.According to the definition of graph Laplacian in (3),all row-sums of L are zero because of P j l ij ¼0.Therefore,L always has a zero eigenvalue 1¼0.This zero eigenvalues corresponds to the eigenvector 1¼ð1;...;1ÞT because 1belongs to the null-space of L ðL 1¼0Þ.In other words,an equilibrium of system (2)is a state in the form x üð ;...; ÞT ¼ 1where all nodes agree.Based on ana-lytical tools from algebraic graph theory [23],we later show that x Ãis a unique equilibrium of (2)(up to a constant multiplicative factor)for connected graphs.One can show that for a connected network,the equilibrium x üð ;...; ÞT is globally exponentially stable.Moreover,the consensus value is ¼1=n P i z i that is equal to the average of the initial values.This im-plies that irrespective of the initial value of the state of each agent,all agents reach an asymptotic consensus regarding the value of the function f ðz Þ¼1=n P i z i .While the calculation of f ðz Þis simple for small net-works,its implications for very large networks is more interesting.For example,if a network has n ¼106nodes and each node can only talk to log 10ðn Þ¼6neighbors,finding the average value of the initial conditions of the nodes is more complicated.The role of protocol (1)is to provide a systematic consensus mechanism in such a largenetwork to compute the average.There are a variety of functions that can be computed in a similar fashion using synchronous or asynchronous distributed algorithms (see [10],[28],[30],[73],and [76]).B.The f -Consensus Problem and Meaning of CooperationTo understand the role of cooperation in performing coordinated tasks,we need to distinguish between un-constrained and constrained consensus problems.An unconstrained consensus problem is simply the alignment problem in which it suffices that the state of all agents asymptotically be the same.In contrast,in distributed computation of a function f ðz Þ,the state of all agents has to asymptotically become equal to f ðz Þ,meaning that the consensus problem is constrained.We refer to this con-strained consensus problem as the f -consensus problem .Solving the f -consensus problem is a cooperative task and requires willing participation of all the agents.To demonstrate this fact,suppose a single agent decides not to cooperate with the rest of the agents and keep its state unchanged.Then,the overall task cannot be performed despite the fact that the rest of the agents reach an agree-ment.Furthermore,there could be scenarios in which multiple agents that form a coalition do not cooperate with the rest and removal of this coalition of agents and their links might render the network disconnected.In a dis-connected network,it is impossible for all nodes to reach an agreement (unless all nodes initially agree which is a trivial case).From the above discussion,cooperation can be infor-mally interpreted as B giving consent to providing one’s state and following a common protocol that serves the group objective.[One might think that solving the alignment problem is not a cooperative task.The justification is that if a single agent (called a leader)leaves its value unchanged,all others will asymptotically agree with the leader according to the consensus protocol and an alignment is reached.However,if there are multiple leaders where two of whom are in disagreement,then no consensus can be asymptot-ically reached.Therefore,alignment is in general a coop-erative task as well.Formal analysis of the behavior of systems that involve more than one type of agent is more complicated,partic-ularly,in presence of adversarial agents in noncooperative games [79],[80].The focus of this paper is on cooperative multi-agent systems.C.Iterative Consensus and Markov ChainsIn Section II,we show how an iterative consensus algorithm that corresponds to the discrete-time version of system (1)is a Markov chainðk þ1Þ¼ ðk ÞP(4)Olfati-Saber et al.:Consensus and Cooperation in Networked Multi-Agent SystemsVol.95,No.1,January 2007|Proceedings of the IEEE217with P ¼I À L and a small 90.Here,the i th element of the row vector ðk Þdenotes the probability of being in state i at iteration k .It turns out that for any arbitrary graph G with Laplacian L and a sufficiently small ,the matrix P satisfies the property Pj p ij ¼1with p ij !0;8i ;j .Hence,P is a valid transition probability matrix for the Markov chain in (4).The reason matrix theory [81]is so widely used in analysis of consensus algorithms [10],[12]–[15],[64]is primarily due to the structure of P in (4)and its connection to graphs.4There are interesting connections between this Markov chain and the speed of information diffusion in gossip-based averaging algorithms [77],[78].One of the early applications of consensus problems was dynamic load balancing [82]for parallel processors with the same structure as system (4).To this date,load balancing in networks proves to be an active area of research in computer science.D.ApplicationsMany seemingly different problems that involve inter-connection of dynamic systems in various areas of science and engineering happen to be closely related to consensus problems for multi-agent systems.In this section,we pro-vide an account of the existing connections.1)Synchronization of Coupled Oscillators:The problem of synchronization of coupled oscillators has attracted numer-ous scientists from diverse fields including physics,biology,neuroscience,and mathematics [83]–[86].This is partly due to the emergence of synchronous oscillations in coupled neural oscillators.Let us consider the generalized Kuramoto model of coupled oscillators on a graph with dynamics_i ¼ Xj 2N isin ð j À i Þþ!i (5)where i and !i are the phase and frequency of the i thoscillator.This model is the natural nonlinear extension of the consensus algorithm in (1)and its linearization around the aligned state 1¼...¼ n is identical to system (2)plus a nonzero input bias b i ¼ð!i À"!Þ= with "!¼1=n P i !i after a change of variables x i ¼ð i À"!t Þ= .In [43],Sepulchre et al.show that if is sufficiently large,then for a network with all-to-all links,synchroni-zation to the aligned state is globally achieved for all ini-tial states.Recently,synchronization of networked oscillators under variable time-delays was studied in [45].We believe that the use of convergence analysis methods that utilize the spectral properties of graph Laplacians willshed light on performance and convergence analysis of self-synchrony in oscillator networks [42].2)Flocking Theory:Flocks of mobile agents equipped with sensing and communication devices can serve as mobile sensor networks for massive distributed sensing in an environment [87].A theoretical framework for design and analysis of flocking algorithms for mobile agents with obstacle-avoidance capabilities is developed by Olfati-Saber [19].The role of consensus algorithms in particle-based flocking is for an agent to achieve velocity matching with respect to its neighbors.In [19],it is demonstrated that flocks are networks of dynamic systems with a dynamic topology.This topology is a proximity graph that depends on the state of all agents and is determined locally for each agent,i.e.,the topology of flocks is a state-dependent graph.The notion of state-dependent graphs was introduced by Mesbahi [64]in a context that is independent of flocking.3)Fast Consensus in Small-Worlds:In recent years,network design problems for achieving faster consensus algorithms has attracted considerable attention from a number of researchers.In Xiao and Boyd [88],design of the weights of a network is considered and solved using semi-definite convex programming.This leads to a slight increase in algebraic connectivity of a network that is a measure of speed of convergence of consensus algorithms.An alternative approach is to keep the weights fixed and design the topology of the network to achieve a relatively high algebraic connectivity.A randomized algorithm for network design is proposed by Olfati-Saber [47]based on random rewiring idea of Watts and Strogatz [89]that led to creation of their celebrated small-world model .The random rewiring of existing links of a network gives rise to considerably faster consensus algorithms.This is due to multiple orders of magnitude increase in algebraic connectivity of the network in comparison to a lattice-type nearest-neighbort graph.4)Rendezvous in Space:Another common form of consensus problems is rendezvous in space [90],[91].This is equivalent to reaching a consensus in position by a num-ber of agents with an interaction topology that is position induced (i.e.,a proximity graph).We refer the reader to [92]and references therein for a detailed discussion.This type of rendezvous is an unconstrained consensus problem that becomes challenging under variations in the network topology.Flocking is somewhat more challenging than rendezvous in space because it requires both interagent and agent-to-obstacle collision avoidance.5)Distributed Sensor Fusion in Sensor Networks:The most recent application of consensus problems is distrib-uted sensor fusion in sensor networks.This is done by posing various distributed averaging problems require to4In honor of the pioneering contributions of Oscar Perron (1907)to the theory of nonnegative matrices,were refer to P as the Perron Matrix of graph G (See Section II-C for details).Olfati-Saber et al.:Consensus and Cooperation in Networked Multi-Agent Systems218Proceedings of the IEEE |Vol.95,No.1,January 2007implement a Kalman filter [38],[39],approximate Kalman filter [74],or linear least-squares estimator [75]as average-consensus problems .Novel low-pass and high-pass consensus filters are also developed that dynamically calculate the average of their inputs in sensor networks [39],[93].6)Distributed Formation Control:Multivehicle systems are an important category of networked systems due to their commercial and military applications.There are two broad approaches to distributed formation control:i)rep-resentation of formations as rigid structures [53],[94]and the use of gradient-based controls obtained from their structural potentials [52]and ii)representation of form-ations using the vectors of relative positions of neighboring vehicles and the use of consensus-based controllers with input bias.We discuss the later approach here.A theoretical framework for design and analysis of distributed controllers for multivehicle formations of type ii)was developed by Fax and Murray [12].Moving in formation is a cooperative task and requires consent and collaboration of every agent in the formation.In [12],graph Laplacians and matrix theory were extensively used which makes one wonder whether relative-position-based formation control is a consensus problem.The answer is yes.To see this,consider a network of self-interested agents whose individual desire is to minimize their local cost U i ðx Þ¼Pj 2N i k x j Àx i Àr ij k 2via a distributed algorithm (x i is the position of vehicle i with dynamics _x i ¼u i and r ij is a desired intervehicle relative-position vector).Instead,if the agents use gradient-descent algorithm on the collective cost P n i ¼1U i ðx Þusing the following protocol:_x i ¼Xj 2N iðx j Àx i Àr ij Þ¼Xj 2N iðx j Àx i Þþb i (6)with input bias b i ¼Pj 2N i r ji [see Fig.1(b)],the objective of every agent will be achieved.This is the same as the consensus algorithm in (1)up to the nonzero bias terms b i .This nonzero bias plays no role in stability analysis of sys-tem (6).Thus,distributed formation control for integrator agents is a consensus problem.The main contribution of the work by Fax and Murray is to extend this scenario to the case where all agents are multiinput multioutput linear systems _x i ¼Ax i þBu i .Stability analysis of relative-position-based formation control for multivehicle systems is extensively covered in Section IV.E.OutlineThe outline of the paper is as follows.Basic concepts and theoretical results in information consensus are presented in Section II.Convergence and performance analysis of consensus on networks with switching topology are given in Section III.A theoretical framework for cooperative control of formations of networked multi-vehicle systems is provided in Section IV.Some simulationresults related to consensus in complex networks including small-worlds are presented in Section V.Finally,some concluding remarks are stated in Section VI.RMATION CONSENSUSConsider a network of decision-making agents with dynamics _x i ¼u i interested in reaching a consensus via local communication with their neighbors on a graph G ¼ðV ;E Þ.By reaching a consensus,we mean asymptot-ically converging to a one-dimensional agreement space characterized by the following equation:x 1¼x 2¼...¼x n :This agreement space can be expressed as x ¼ 1where 1¼ð1;...;1ÞT and 2R is the collective decision of the group of agents.Let A ¼½a ij be the adjacency matrix of graph G .The set of neighbors of a agent i is N i and defined byN i ¼f j 2V :a ij ¼0g ;V ¼f 1;...;n g :Agent i communicates with agent j if j is a neighbor of i (or a ij ¼0).The set of all nodes and their neighbors defines the edge set of the graph as E ¼fði ;j Þ2V ÂV :a ij ¼0g .A dynamic graph G ðt Þ¼ðV ;E ðt ÞÞis a graph in which the set of edges E ðt Þand the adjacency matrix A ðt Þare time-varying.Clearly,the set of neighbors N i ðt Þof every agent in a dynamic graph is a time-varying set as well.Dynamic graphs are useful for describing the network topology of mobile sensor networks and flocks [19].It is shown in [10]that the linear system_x i ðt Þ¼Xj 2N ia ij x j ðt ÞÀx i ðt ÞÀÁ(7)is a distributed consensus algorithm ,i.e.,guarantees con-vergence to a collective decision via local interagent interactions.Assuming that the graph is undirected (a ij ¼a ji for all i ;j ),it follows that the sum of the state of all nodes is an invariant quantity,or P i _xi ¼0.In particular,applying this condition twice at times t ¼0and t ¼1gives the following result¼1n Xix i ð0Þ:In other words,if a consensus is asymptotically reached,then necessarily the collective decision is equal to theOlfati-Saber et al.:Consensus and Cooperation in Networked Multi-Agent SystemsVol.95,No.1,January 2007|Proceedings of the IEEE219average of the initial state of all nodes.A consensus algo-rithm with this specific invariance property is called an average-consensus algorithm [9]and has broad applications in distributed computing on networks (e.g.,sensor fusion in sensor networks).The dynamics of system (7)can be expressed in a compact form as_x ¼ÀLx(8)where L is known as the graph Laplacian of G .The graph Laplacian is defined asL ¼D ÀA(9)where D ¼diag ðd 1;...;d n Þis the degree matrix of G with elements d i ¼Pj ¼i a ij and zero off-diagonal elements.By definition,L has a right eigenvector of 1associated with the zero eigenvalue 5because of the identity L 1¼0.For the case of undirected graphs,graph Laplacian satisfies the following sum-of-squares (SOS)property:x T Lx ¼12Xði ;j Þ2Ea ij ðx j Àx i Þ2:(10)By defining a quadratic disagreement function as’ðx Þ¼12x T Lx(11)it becomes apparent that algorithm (7)is the same as_x ¼Àr ’ðx Þor the gradient-descent algorithm.This algorithm globallyasymptotically converges to the agreement space provided that two conditions hold:1)L is a positive semidefinite matrix;2)the only equilibrium of (7)is 1for some .Both of these conditions hold for a connected graph and follow from the SOS property of graph Laplacian in (10).Therefore,an average-consensus is asymptotically reached for all initial states.This fact is summarized in the following lemma.Lemma 1:Let G be a connected undirected graph.Then,the algorithm in (7)asymptotically solves an average-consensus problem for all initial states.A.Algebraic Connectivity and Spectral Propertiesof GraphsSpectral properties of Laplacian matrix are instrumen-tal in analysis of convergence of the class of linear consensus algorithms in (7).According to Gershgorin theorem [81],all eigenvalues of L in the complex plane are located in a closed disk centered at Áþ0j with a radius of Á¼max i d i ,i.e.,the maximum degree of a graph.For undirected graphs,L is a symmetric matrix with real eigenvalues and,therefore,the set of eigenvalues of L can be ordered sequentially in an ascending order as0¼ 1 2 ÁÁÁ n 2Á:(12)The zero eigenvalue is known as the trivial eigenvalue of L .For a connected graph G , 290(i.e.,the zero eigenvalue is isolated).The second smallest eigenvalue of Laplacian 2is called algebraic connectivity of a graph [20].Algebraic connectivity of the network topology is a measure of performance/speed of consensus algorithms [10].Example 1:Fig.2shows two examples of networks of integrator agents with different topologies.Both graphs are undirected and have 0–1weights.Every node of the graph in Fig.2(a)is connected to its 4nearest neighbors on a ring.The other graph is a proximity graph of points that are distributed uniformly at random in a square.Every node is connected to all of its spatial neighbors within a closed ball of radius r 90.Here are the important degree information and Laplacian eigenvalues of these graphsa Þ 1¼0; 2¼0:48; n ¼6:24;Á¼4b Þ 1¼0; 2¼0:25; n ¼9:37;Á¼8:(13)In both cases, i G 2Áfor all i .B.Convergence Analysis for Directed Networks The convergence analysis of the consensus algorithm in (7)is equivalent to proving that the agreement space characterized by x ¼ 1; 2R is an asymptotically stable equilibrium of system (7).The stability properties of system (7)is completely determined by the location of the Laplacian eigenvalues of the network.The eigenvalues of the adjacency matrix are irrelevant to the stability analysis of system (7),unless the network is k -regular (all of its nodes have the same degree k ).The following lemma combines a well-known rank property of graph Laplacians with Gershgorin theorem to provide spectral characterization of Laplacian of a fixed directed network G .Before stating the lemma,we need to define the notion of strong connectivity of graphs.A graph5These properties were discussed earlier in the introduction for graphs with 0–1weights.Olfati-Saber et al.:Consensus and Cooperation in Networked Multi-Agent Systems220Proceedings of the IEEE |Vol.95,No.1,January 2007。
A Mobile Agent-based System for Dynamic TaskAllocation in Clusters of Embedded SmartCamerasMichael Bramberger1,Bernhard Rinner1andHelmut Schwabach21Institute for Technical Informatics,Graz University of Technology,Graz,Austria{bramberger,rinner}@iti.tugraz.at2Video&Safety Technology,ARC seibersdorf research,Seibersdorf,Austriahelmut.schwabach@arcs.ac.atAbstract—This paper presents a dynamic task allocation method for smart cam-eras targeting traffic surveillance.Since our target platforms are distributed em-bedded systems with limited resources,the task allocation has to be light-weight,flexible as well as scalable and has to support real-time requirements.Therefore,surveillance tasks are not allocated to smart cameras directly,but to groups of smartcameras,so called surveillance clusters.We formulate the allocation problem as adistributed constraint satisfaction problem(DCSP)and present a distributed methodforfinding feasible allocations.Finally,a cost function is used to determine theoptimal allocation of tasks.We have realized this dynamic task allocation using het-erogeneous,mobile agents which utilize their agencies and our embedded softwareframework tofind the most appropriate mapping of tasks in a distributed manner.Thedynamic task allocation has been implemented on our smart cameras(SmartCam)which are comprised of a network processor and several digital signal processors(DSPs)and provide a complex software framework.1IntroductionSurveillance systems currently undergo a dramatic shift.Traditional surveillance systems of thefirst and second generation have employed analog CCTV cameras,which trans-ferred the analog video data to digital base stations where the video analysis,storage and retrieval takes place.Current semiconductor technology enables surveillance systems to leap forward to third generation systems which employ digital cameras with on-board video compression and communication capabilities.Smart cameras[1][2]even go one step further;they not only capture and compress the grabbed video stream,but also per-form sophisticated,real-time,on-board video analysis of the captured scene.Smart cam-BRAMBERGER,RINNER,SCHWABACHeras help in(i)reducing the communication bandwidth between camera and base station, (ii)decentralizing the overall surveillance system and hence to improve the fault toler-ance,as well as(iii)realizing more surveillance tasks than with traditional cameras. Typical tasks to be run in a surveillance system targeting traffic surveillance include MPEG-4video compression,various video analysis algorithms such as accident detec-tion,wrong-way drivers detection and stationary vehicle detection.Additionally,traffic parameters such as average speed,lane occupancy and vehicle classification are often required.Since computing power is limited we may not allocate all tasks to the cameras. This paper presents a resource-aware dynamic task allocation system for smart cameras targeting traffic surveillance.Since our target platforms are distributed embedded systems with limited resources,the task allocation has to be light-weight,flexible,scalable,and has to support real-time requirements.Therefore,surveillance tasks are not allocated to smart cameras directly,but to groups of smart cameras,so called surveillance clusters.We formulate the allocation problem as a distributed constraint satisfaction problem(DCSP) and present a distributed method forfinding feasible allocations.Finally,a cost function is used to determine the optimal allocation of tasks.We have realized this dynamic task allocation using heterogeneous,mobile agents which utilize their agencies and our em-bedded software framework tofind the most appropriate mapping of tasks in a distributed mannerThe main contributions of this ongoing research project include(i)the distributed agent-based approach for determining all feasible allocations of a DCSP,(ii)the evaluation of a complex cost function considering the limited resources of the embedded platform in detail,(iii)the integration of a mobile agent system in our embedded software framework. The dynamic task allocation has been implemented on our smart cameras(SmartCam[3]) which are comprised of a network processor and several digital signal processors(DSPs) and provide a complex software framework.The remainder of this paper is organized as follows:Section1.1sketches related work. Section2describes the DCSP approach and focuses onfinding feasible allocations of tasks and the cost function.Section3and4present the implementation and the experi-mental results,respectively.Section5concludes the paper with a summary and an outlook on future work.1.1Related WorkAgents-based load distribution has been an active research in the last decade.An overview of agent standards and available platforms is presented in[4].WY A(While You’re Away)[5]is based on the NOMADS mobile agent system.It provides dynamic load balancing by mobile agents,which utilize a central coordinator to move between work-stations.Qin et al[6]identified the amount I/O-traffic as an important issue for dynamic load balancing beside CPU-load and memory.Chow and Kwok[7]introduced the affinity of an agent to its machine and used a credit-based scheme to determine the agents to be migrated by using a central host station.Agents used in surveillance systems were pro-posed by the MODEST consortium[8],where mobile agents were used to track vehicles using PC based platforms.Distributed constraint satisfaction problems have been analyzed by Yokoo et al.in [9]for variable-split CSPs.The presented asynchronous backtracking algorithm usedDYNAMIC TASK ALLOCATION IN CLUSTERS OF EMBEDDED SMART CAMERAS autonomous agents,however,the high communication effort between the agents is im-practical for real-time systems.2Task AllocationThe goal of the task allocation system is to find a mapping of tasks to smart cameras which satisfies all requirements and is optimal with respect to a specified metric,i.e.some cost function.Since the surveillance tasks have firm real-time requirements,the task allocation system has to take care that no deadlines are missed due to an overload of a camera or a camera’s subsystem,respectively.The re-allocation of tasks may be necessary due to events,raised by hardware or soft-ware:(1)Hardware events usually originate from changed resource availability due to added or removed cameras,hardware breakdown,or re-usability of recovered resources.(2)Software events are caused by changes to resource requirements due to changes in the task set of the surveillance cluster,or because of changes in the quality-of-service level (QoS)of tasks,i.e.due to detected events in the observed scene.The allocation of tasks to smart cameras is done in two steps.(1)In the first step,all fea-sible allocations of tasks to smart cameras (allocations where no real-time requirements are violated)are determined.(2)In the second step,the optimal allocation of tasks is chosen by using a cost function.2.1Find Feasible AllocationsThe determination of feasible allocations of tasks to smart cameras is a distributed con-straint satisfaction problem (CSP)[9].CSPs are defined by a set of n variables T ={T 1,...,T n },which hold values of a finite domain D ,and a set of k constraints C ={C 1,...,C k }.In our case,the surveillance tasks to be allocated to the cameras of the surveillance cluster are the variables,and the values they hold is the identifier of the allo-cated smart camera D ={1,...,m }.Therefore,T i =d indicates,that task i is currently allocated to smart camera d .Equation 1determines all permutations with repetitions A ,denoted by R ,from the m cameras and n tasks.The subsets of A are allocations of tasks to cameras,which have to be checked for feasibility.The constraints (cp.eq.4are formulated using two functions which determine the resource requirements and availability of the tasks and the cameras.req (Res,i )determines the requirements of task i concerning resource Res ,while avail (Res,d )determines the availability of the resource Res on smart camera d .A =R (m,n )={A 1,...,A p };p =m n (1)A j ={a 1,...,a n }|a i ∈D (2)R ={CP U,MEM,DMA }(3)C ={∀A j ∈A :∀d ∈D :∀r ∈R :∀a i ∈A j ∀a i =d :( i req (r,i ))<avail (r,d )}(4)Equations 1to 4define a feasible allocation,i.e.,any allocation A which does not violate any resource constraint C .Note that in our implementation we also considered the DSPsBRAMBERGER,RINNER,SCHWABACHmemory hierarchy and several parameters of the DMA subsystem (cp.resource costs in section 2.2.1).However,this approach requires a central host.A more scalable solution is to distribute the CSP to several cameras in the surveillance cluster.2.1.1The Distributed CSPIn order to distribute the determination of feasible allocations to all smart cameras,we split the domain D into m sub-domains D 1,...,D m ,each comprised of a single value D l =l .The set of tasks T remains the same,while the complexity of the constraints is reduced slightly (cp.equation 5).To achieve all possible allocations of tasks,we choose ∀0<i ≤n tasks out of the set of all tasks ∀0<i ≤n :A i =choose (i,n ).Every set A i is comprised of νallocations A i ={A i 1,...,A i ν},each of which consisting of i tasks A i ν={a 1,...,a i }|∀a η∈T .All allocations A i ν,which meet the constraints (cp.equation 5)for all resources R ,are chosen as feasible,partial allocations.C ={∀A i ∈A :∀A i ν∈A i :∀a j ∈A i ν:∀r ∈R :( j req (r,a j ))<avail (r,d )}(5)Note that the constraints only consider tasks allocated to a single smart camera,so the CSP is split into m sub-CSPs,which can be solved in parallel on the m smart cameras in the surveillance cluster.Normally,CSPs require that all variables are included in the solutions of the problem,however,in our case this rule would imply that only partial allocations are valid,which include all n tasks of the surveillance cluster.In order to accept task allocations which do not include all tasks,the CSP rules have to be weakened.Even the allocation of no task is a valid allocation,which is reasonable,if a surveillance cluster contains less tasks than smart cameras.2.1.2Merging of AllocationsFinally,m sets of partial task allocations are available (cp.eq.6),which have to be merged in order to find all feasible task allocations.P ={P 1,...,P m };P j ={P j 1,...,P j ν}(6)Consequently,valid task allocations (1)do not allocate tasks to more cameras concur-rently,and (2)include all surveillance tasks.The merging of partial allocations can be done in parallel,as long as rule 1is not violated.However,the final merging process has to obey rule 2too.The merging step of the partial allocations finally provides a set of f feasible allocations F ,from which the most appropriate allocation has to be chosen.2.2Find Optimal AllocationFor finding the most appropriate allocation of tasks a cost-scheme is used.This cost-calculation scheme includes five cost classes:(1)Resource costs (C R ),(2)data-transferDYNAMIC TASK ALLOCATION IN CLUSTERS OF EMBEDDED SMART CAMERAS costs(C T),(3)migration costs(C M),(4)affinity costs(C A),and(5)quality-of-service costs(C QoS).These costs are calculated for every task on every smart camera in the surveillance cluster.Finally,the overall costs are accumulated as enlisted in the set of feasible allocations F.The following section presents thefive cost classes,however,a more detailed description of the cost calculation can be found in[10].2.2.1Cost CalculationTo compute the overall cost C T ot of a surveillance task,the cost values of thefive cost classes are weighted and added:C T ot=k R∗C R+k T∗C T+k M∗C M+k A∗C A+k QoS∗C QoS(7) Resource Cost The resource costs are composed of four resources:(1)CPU load,(2) memory usage(including memory hierarchy on DSPs),(3)DMA utilization(including channels,reload-tables,and transfer complete codes),and(4)memory bus utilization.Data-Transfer Cost We have defined two different types of data transfers:(1)Data entering or leaving the system will usually be transmitted using a network interface,while (2)intermediate data transfers operate internally via PCI bus or directly to memory.To consider the bandwidth of the used interface,the data-transfer cost C T is calculated as the amount of megabytes(MB)transferred,multiplied by a slowness factor depending on the bandwidth of the connection.Migration Cost The migration of tasks between smart cameras is accounted for by the migration costs depending on(1)required data transfer,and(2)the algorithms downtime due to migration.Affinity Cost Affinity costs express the priority of tasks inside a surveillance cluster (cluster affine tasks),and additionally provide the possibility to bind a surveillance task to a specific camera(scene affine task),as it is required for tracking tasks,for example. Quality-of-Service Cost In oder to allow a morefine-grained control over the system, surveillance tasks may feature several quality-of-service(QoS)levels with different qual-ity levels and,therefore,different resource ually it is desired to run all tasks with highest possible quality,therefore,this cost adds penalty costs if the task should be run with lower QoS-levels(e.g.due to insufficient resource availability for running at best quality).These penalty costs and the number of QoS-levels are defined by the task designer.2.3Reallocation ScenariosAs mentioned before,two scenarios are possible,where a reallocation of tasks is neces-sary.However,we handle the scenarios differently to improve the performance of the system.BRAMBERGER,RINNER,SCHWABACHIncreased Requirements/Decreased Resource Availability Increased requirements or decreased resource availability indicates a higher system load.Therefore,the number of feasible allocations will decrease,since less combinations of tasks will satisfy the con-straints of the CSP.Therefore,the value of the changed resource or availability is updated in the set of feasible allocations F.Finally,the feasible allocations are re-checked and infeasible allocations are removed from F.This re-checking process does not require to recalculate all possible allocations,therefore,the time required for determination of the new allocation is reduced dramatically.Decreased Requirements/Increased Resource Availability In contrast to the upper scenario,the decrease of requirements or increase of resource availability can be seen as a reduced load of the system.Consequently,the number of both,partial and complete, allocations will increase.Therefore,all feasible allocations have to be re-computed.This approach leads to longer execution times,however,as the service quality will rise by this reallocation,the real-time deadlines are not asfirm as in the upper scenario.3ImplementationFor the implementation of our surveillance system we have chosen to use mobile agent technology.Mobile agents are most suitable for our system,since they support mobility, autonomy,and platform independence.3.1Agent SystemWe have chosen to use the diet-agents1system since it includes all required features like mobility,autonomy,and platform independence and is reasonable small,which is in-evitable for embedded systems.However,extensions to the agent system were necessary to add the support for the DSPs,and the decentralized management of the surveillance clusters.DSP Agencies Agencies provide the environment for agents to live in.An extension to standard agencies is required to support multiple surveillance clusters.Therefore,a logical grouping of agents within the agency is desirable.We have implemented a cluster-information agent(CIA),which hosts local knowledge of other cameras belonging to the surveillance cluster,and provides lookup services for agents within the surveillance cluster.The integration of the DSPs into the agent system is done by one DSP integration agent(DIA)per DSP in the system.This DIA is a stationary agent,which manages message registrations,message dispatching,and binary downloads to the DSP.Two basic agent types are deployed within the agent system:(1)Management-oriented SmartCam-agents,which are not included in the task allocation system,and(2)DSP agents,which implement algorithmic functionality to be executed on a DSP.Conse-quently,DSP-agents represent the tasks allocated by the presented allocation system. Therfore the next paragraph focuses on these agents.1see DYNAMIC TASK ALLOCATION IN CLUSTERS OF EMBEDDED SMART CAMERAS DSP Agents DSP agents are an enhancement of standard agents,as they are the base of the task allocation system.Therefore,DSP agents include their requirements to the system and their cost parameters.Additionally,the cost calculation functionality is added to these agents.As the computational intensive parts of these agents are executed on the DSPs,the agents contain a binary,which is downloaded to the DSP and dynamically integrated into the system.Therefore,the agents maintains communication channels to the DSP by using the DSP integration-agent(DIA).In case of migration the agent notifies the DSPs task to stop computation and to trans-mit the persistent intermediate results to the agent.After migration the agent loads the binary to the DSP and transmits the stored intermediate results to the DSP.This enables the algorithm to continue computation or to use the intermediate results as new starting values,respectively.3.2Task Allocation SystemThis section outlines the actions taken during a reconfiguration of a surveillance cluster. Since our goal is aflexible,scalable and distributed implementation we have chosen to realize the task allocation system using mobile agents.A new allocation is always initiated by a smart camera,either due to a hardware event (changes of availability)or a software event(changes of requirements).This camera initiates the reallocation by broadcasting the request-for-requirements to all agents,that encapsulate the surveillance tasks,within the surveillance cluster.After the agents receive this request,they broadcast their requirements to all smart cameras in their surveillance cluster.Additionally,all agents calculate their costs for every smart camera and transmit the cost values to the initiating camera.The smart cameras determine in parallel the partial allocations,which have to be merged in the next step.As the smart cameras are comprised of more DSPs,the partial allocations for the DSPs are merged.To further merge the partial allocations,the half of the smart cameras(determined during the creation of the surveillance cluster)create allocation-merging agents(AMA),which pick up the merged partial allocation and migrate to predetermined smart cameras(which comprise the other half of the surveillance cluster),where they grab the partial allocation,and merge both,the local and the included partial allocations.After the merging process, the agents migrate to the next smart camera,as defined by thefixed itinerary,and merge their partial allocation with the partial allocation provided by another AMA.This way the partial allocations are merged to afinal allocation,whereas the last allocation merge is done on the initiating smart camera.The merging process corresponds to a binary tree, therefore ld(m)(where m is the number of smart cameras)sequential steps have to be done.The initiating smart camera has to determine the most appropriate task allocation,there-fore,the costs,as submitted by the agents,are accumulated for every task allocation. Consequently,the task allocation with the lowest cost is selected as the new task alloca-tion.Since the selection of the most appropriate task allocation is based on the costs of the agents,the desired optimization goal like the number of migrations,degradation of quality-of-service,or balanced use of resources can be achieved by adapting the scaling factors of the cost classes.Finally,the new task allocation is broadcast to all smart cam-eras and agents,which may update their QoS level,or migrate to another smart cameraBRAMBERGER,RINNER,SCHWABACHFigure1:The prototype of the smart camerathen.To enable the fast reconfiguration by removing feasible task allocations,also the set of feasible task allocations is broadcast to all smart cameras in the surveillance cluster after the system has settled.3.3Hardware SetupTo verify,test and evaluate the presented agent system,we have used two hardware plat-forms.A prototype of our smart camera and PCs equipped with DSP boards.The prototype of our smart camera consists of an Intel IXDP425Development Board, which is equipped with an Intel IXP425network processor running at533MHz,as well as two Network Video Development Kits(NVDK)from ATEME.Each board is comprised of a TMS320C6416DSP from Texas Instruments,running at600MHz,with a total of 264MB of on-board memory.Image acquisition is done using the National Semiconduc-tor LM9618monochrome CMOS image sensor,which is connected to one of the DSP boards.Due to the lack of additional smart camera prototypes,we are using two Pentium-III personal computers(PCs)running at1GHz,which are equipped with one Network Video Development Kit(NVDK)from ATEME.4ExperimentsIn order to verify and evaluate the presented task allocation system,we used the smart camera prototype and two PCs.Consequently,we have setup a surveillance cluster con-taining these three“cameras”.We have used four different agent types for our experi-ments:(1)A MPEG-4video compression agent,(2)a stationary-vehicle detection(StVD) agent,(3)a vehicle count agent,and(4)a vehicle classifier agent.The MPEG-4agent and the stationary-vehicle detection agent[2]are well tested and evaluated agents,how-ever,the vehicle count and vehicle classify agents only simulated real behavior.A total of six agents have been instantiated from these four classes,where we used three MPEG-agents(as every camera has to transmit a live video stream),and one agent of every other agent-type.Table1enlists the execution times of the two stages of the task allocation.On the PCsDYNAMIC TASK ALLOCATION IN CLUSTERS OF EMBEDDED SMART CAMERAS Case PC PC SmartCam SmartCamExecuted by JDK1.4.2JamVM JamVM Native/C++ 1a Partial Allocations(6ag.)20ms14ms79ms13ms1b Partial Allocations(3ag.)14ms7ms55ms9ms2a Merge Solutions(6ag.)766ms4852ms21363ms2360ms2b Merge Solutions(3ag.)9ms5ms31ms4ms3a Overall running time(6ag.)786ms4866ms21442ms2373ms3b Overall running time(3ag.)23ms12ms86ms13ms4Pruning of allocations(6ag.)14ms32ms172ms26msTable1:Running times of task allocationwe have used two Java virtual-machines:(a)Sun’s JDK1.4.2,which uses a just-in-time (JIT)compiler,and therefore reaches better performance values,while(b)the JamVM virtual machine2is designed as an interpreter.JamVM was also used on the prototype of the smart camera(c),andfinally we have implemented the core calculation functions (determine partial allocations,allocation merging)in C++to estimate the maximum per-formance(d).Lines1a,2a,and3a represent the execution times if all six tasks were considered.In a second scenario we have removed the MPEG-4encoding agents from the surveillance cluster,and allocated them statically to the cameras.The results of the dynamic allocation of the resulting three agents is enlisted in lines1b,2b,and3b in table1.Lines1a and1b show that the determination of partial allocations only requires a low amount of time.However,lines2a and2b enlist that the merging process requires most of the computation time.It can be seen,that merging using the JamVM requires up to 21seconds,which is unacceptable.The C++implementation,however,performs better, but also requires about2seconds for computation.The running time of the merging stage rises exponentially with the number of agents and cameras,since the number of feasible allocations rises exponentially,too(e.g.there are2880feasible allocations in case2a). Therefore,a reduction of feasible allocations would yield in better performance.Lines3a and3b enlist the overall execution time,as the sum offinding the partial allocations and the merging process.Finally,we have also evaluated the performance of the task allocation system at in-creasing system load,in which case the previously determined allocations a rechecked for feasibility.Line4enlists the times required to recheck all2880allocations.Note that even running JamVM on our prototype delivers a new allocation within172ms,which is sufficient.5ConclusionIn this paper we have presented a resource-aware dynamic task-allocation system target-ing embedded smart cameras.Surveillance tasks are not allocated to the smart cameras directly,but to groups of smart cameras,surveillance clusters,within the tasks are allo-cated by the smart cameras in a distributed manner.We show that the task allocation can 2BRAMBERGER,RINNER,SCHWABACHbe formulated as a distributed constraint satisfaction problem(DCSP)and present a solu-tion for this DCSP.Therefore we combine the results of the DCSP with a cost function to retrieve the optimal allocation of tasks.Finally,we discuss the mobile-agent based im-plementation of the system and present results achieved by evaluation of the implemented system.Future work includes(1)the further evaluation of the system,using more complex scenarios,(2)the tighter combination offinding feasible allocations and calculating the costs for an allocation in order to delete expensive allocations at an early stage,(3)the test and evaluation of the system in real-world scenarios,and(4)the integration of learning agents into surveillance clusters,which influence the behavior of the system by adapting the cost function based on previous behavior,events,and actions.References[1]W.Wolf,B.Ozer,and T.Lv.Smart Cameras as Embedded Systems.IEEE Computer,35(9):48–53,Sep2002.[2]M.Bramberger,J.Brunner,B.Rinner,and H.Schwabach.Real-Time Video Analysis on an Em-bedded Smart Camera for Traffic Surveillance.In Proceedings of the10th IEEE Real-Time and Embedded Technology and Applications Symposium,pages174–181,2004.[3]M.Bramberger,B.Rinner,and H.Schwabach.An Embedded Smart Camera on a Scalable Heteroge-neous Multi-DSP System.In Proceedings of the European DSP Education and Research Symposium (EDERS2004),Nov2004.[4]M.K.Perdikeas,F.G.Chatzipapadopoulos,I.S.Venieris,and G.Marino.Mobile agent standardsand available platforms.Elsevier Computer Networks,(31),1999.[5]N.Suri,P.T.Groth,and J.M.Bradshaw.While You’re Away:A System for Load-Balancing andResource Sharing based on Mobile Agents.In Proceedings of the First IEEE/ACM International Symposium on Cluster Computing and the Grid,pages470–473,2001.[6]X.Qin,Q.Zhu,and D.Swanson.A Dynamic Load Balancing Scheme for I/O-Intensive Applicationsin Distributed Systems.In Proceedinges of the2003International Conference on Parallel Processing Workshops.IEEE,2003.[7]K.-P.Chow and Y.-K.Kwok.On Load Balancing for Distributed Multiagent Computing.IEEETransactions on Parallel and Distributed Systems,13(8):787–801,Aug2002.[8] B.Abreu,L.Botelho,A.Cavallaro,D.Douxchamps,T.Ebrahimi,P.Figueiredo,B.Macq,B.Mory,L.Nunes,J.Orri,M.J.Trigueiros,and A.Violante.Video-Based Multi-Agent Surveillance System.In Proceedings of the2000Intelligent Vehicles Conference,Oct2000.[9]M.Yokoo,E.H.Durfee,T.Ishida,and K.Kuwabara.The distributed constraint satisfaction prob-lem:formalization and algorithms.IEEE Transactions on Knowledge and Data Engineering, 10(5):Sep/Oct,1998.[10]M.Bramberger,B.Rinner,and H.Schwabach.Resource-aware dynamic task-allocation in clustersof embedded smart cameras by mobile agents.In Proceedings of the IEE Intenational Workshop on Intelligent Environments.IEE,June2005.to appear.[11]G.L.Foresti,P.M¨a h¨o nen,and C.S.Regazzoni,editors.Multimedia video-based surveillance systems.Kluwer Academic Publishers,Boston,2000.[12] C.S.Regazzoni,V.Ramesh,and G.L.Foresti.Introduction of the special issue.Proceedings of theIEEE,89(10),Oct2001.。