实验八(一) ASA 配置 NAT 和 ACL
- 格式:docx
- 大小:43.18 KB
- 文档页数:8

acl配置实验报告ACL配置实验报告一、实验目的本实验旨在通过配置ACL(Access Control List)来实现对网络设备的访问控制,保护网络安全,限制非授权用户的访问权限,提高网络设备的安全性。
二、实验环境本次实验使用了一台路由器和多台主机,通过配置ACL来限制主机对路由器的访问权限。
三、实验步骤1. 首先,登录路由器,进入配置模式。
2. 创建ACL,并定义访问控制列表的规则。
可以通过指定源IP地址、目的IP地址、协议类型、端口等条件来限制访问。
3. 将ACL应用到路由器的接口上,实现对该接口的访问控制。
4. 测试ACL的效果,尝试从不同的主机访问路由器,验证ACL是否生效。
四、实验结果经过配置ACL后,我们成功限制了某些主机对路由器的访问权限,只允许特定的主机进行访问。
ACL的规则生效,非授权主机无法访问路由器,有效保护了网络设备的安全。
五、实验总结通过本次实验,我们深入了解了ACL的配置和应用,学会了如何通过ACL来实现对网络设备的访问控制。
ACL是网络安全的重要手段之一,能够有效保护网络设备的安全,限制非授权用户的访问权限,提高网络的安全性。
六、实验感想ACL的配置虽然需要一定的技术和经验,但是通过实验的学习和实践,我们对ACL有了更深入的理解,掌握了ACL的配置方法和应用技巧。
在今后的网络管理和安全工作中,我们将能够更好地应用ACL来保护网络设备的安全,提高网络的安全性。
七、展望ACL作为网络安全的重要手段,将在未来的网络管理和安全工作中发挥越来越重要的作用。
我们将继续深入学习ACL的相关知识,不断提升自己的技术水平,为网络安全做出更大的贡献。
通过本次实验,我们对ACL的配置和应用有了更深入的了解,相信在今后的学习和工作中,我们将能够更好地应用ACL来保护网络设备的安全,提高网络的安全性。
ACL配置实验报告至此完毕。

acl实验报告ACL实验报告一、引言ACL(Access Control List)是一种用于控制系统资源访问权限的机制。
通过ACL,系统管理员可以根据用户的身份、角色或其他标识来限制用户对特定资源的访问。
本实验旨在探索ACL的原理和应用,并通过实际操作来加深对ACL的理解。
二、ACL的基本原理ACL的基本原理是根据用户的身份或角色来控制对资源的访问权限。
ACL可以应用于文件、文件夹、网络设备等各种资源。
在ACL中,通常包含两类主体:访问主体(Subject)和资源主体(Object)。
访问主体可以是用户、用户组或其他身份标识,而资源主体可以是文件、文件夹、网络端口等。
ACL中的权限通常包括读取、写入、执行等操作。
通过为每个主体分配适当的权限,系统管理员可以精确控制用户对资源的操作。
例如,管理员可以设置只有特定用户组的成员才能读取某个文件,或者只有特定用户才能执行某个程序。
三、ACL的应用场景ACL在实际应用中有广泛的应用场景。
以下是几个典型的例子:1. 文件系统权限控制在操作系统中,文件和文件夹是最常见的资源。
通过ACL,管理员可以为每个文件或文件夹设置不同的访问权限。
例如,对于某个重要的文件,管理员可以设置只有自己和特定用户才能读取和写入,其他用户只能读取。
这样可以确保敏感信息不被未授权的用户访问。
2. 网络访问控制对于企业内部的网络,管理员可以使用ACL来控制用户对不同网络资源的访问。
例如,某个部门的员工只能访问本部门的内部网站和文件共享,而不能访问其他部门的资源。
通过ACL,管理员可以轻松实现这种网络访问控制。
3. 路由器和防火墙配置在网络设备中,ACL也扮演着重要的角色。
通过为路由器或防火墙配置ACL,管理员可以控制网络流量的访问权限。
例如,可以设置只有特定IP地址或特定端口的流量才能通过,其他流量则被阻止。
这样可以提高网络的安全性和性能。
四、ACL实验操作步骤以下是一个简单的ACL实验操作步骤,以文件系统权限控制为例:1. 创建测试文件首先,在你的计算机上创建一个测试文件,命名为test.txt。

ASA配置指南,~、文档属性 文档历史; 序号 版本号修订日期 修订人 修订内容 1.郑鑫 文档初定 2. ·3.4.<)(, 属性 内容标题 思科ASA 防火墙配置指南文档传播范围发布日期目录一、文档说明 (5)二、基础配置 (6)(一)查看系统信息 (6)(二)版本区别简介 (6)《(三)接口配置与安全级别简介 (7)(四)NTP 配置 (8)(五)SNMP配置 (9)(六)telnet配置 (9)(七)SSH配置 (9)(八)配置管理 (10)(九)常用设备排错命令 (10)三、NAT静态方向写法 (12)(一)传统静态NAT配置方向写法 (12)(二)新静态NAT配置方向写法 (15)四、NAT配置举例 (16)"(一)Dynamic NAT (16)(二)Static NAT (27)(三)Identity NAT (34)(四)NAT免除 (40)(五)Twice NAT(策略NAT) (40)(六)NAT执行顺序 (52)五、状态化应用监控 (53)(一)状态化监控策略配置 (53)(二)路由、NAT、ACL、策略执行顺序 (57)六、failover (65)(一)配置failover (65)%(二)配置A/A (76)一、文档说明<本文档主要介绍思科ASA防火墙在版本之前与版本之后配置区别和常用的一些管理和运维命令,如:系统管理、防火墙策略、NAT、日志配置等。
思科ASA防火墙目前新出厂的设备都在以后,但有很多老的设备都在以前,所以本文档通过使用ASA 与这两个版本来介绍。
请读者打开文档中的显示批注功能,文档中有部分批注内容。
)二、基础配置(一)查看系统信息hostnat (inside,outside) staticobject networkhostnat (outside,inside) staticaccess-list inbound extended permit ip host host access-group inbound in interface outside@新命令的outbound和inbound流量动作是一样的:(inside,outside)针对outbound流量是源的转换,针对inbound流量是目的的转换(outside,inside)针对outbound流量是转换目的,针对inbound的是转换源。

ciscoASA防火墙如何配置思科cisco是全球高端顶尖的通讯厂商,其出产的路由器功能也是世界级的,那么你知道cisco ASA防火墙如何配置的吗?下面是店铺整理的一些关于cisco ASA防火墙如何配置的相关资料,供你参考。
cisco ASA防火墙配置的方法:常用命令有:nameif、interface、ip address、nat、global、route、static等。
global指定公网地址范围:定义地址池。
Global命令的配置语法:global (if_name) nat_id ip_address-ip_address [netmark global_mask]其中:(if_name):表示外网接口名称,一般为outside。
nat_id:建立的地址池标识(nat要引用)。
ip_address-ip_address:表示一段ip地址范围。
[netmark global_mask]:表示全局ip地址的网络掩码。
nat地址转换命令,将内网的私有ip转换为外网公网ip。
nat命令配置语法:nat (if_name) nat_id local_ip [netmark]其中:(if_name):表示接口名称,一般为inside.nat_id:表示地址池,由global命令定义。
local_ip:表示内网的ip地址。
对于0.0.0.0表示内网所有主机。
[netmark]:表示内网ip地址的子网掩码。
routeroute命令定义静态路由。
语法:route (if_name) 0 0 gateway_ip [metric]其中:(if_name):表示接口名称。
0 0 :表示所有主机Gateway_ip:表示网关路由器的ip地址或下一跳。
[metric]:路由花费。
缺省值是1。
static配置静态IP地址翻译,使内部地址与外部地址一一对应。
语法:static(internal_if_name,external_if_name) outside_ip_addr inside_ ip_address其中:internal_if_name表示内部网络接口,安全级别较高,如inside。

思科防火墙已经从PIX发展到ASA了,IOS也已经从早期的6.0发展到7.2。
但总体的配置思路并没有多少变化。
只是更加人性化,更加容易配置和管理了。
下面是我工作以来的配置总结,有些东西是6.3版本的,但不影响在7.*版本的配置。
一:6个基本命令: nameif、 interface、 ip address 、nat、 global、 route。
二:基本配置步骤:step1: 命名接口名字nameif ethernet0 outside security0nameif ethernet1 inside security100nameif ethernet2 dmz security50**7版本的配置是先进入接口再命名。
step2:配置接口速率interface ethernet0 10full autointerface ethernet1 10full autointerface ethernet2 10fullstep3:配置接口地址ip address outside 218.106.185.82ip address inside 192.168.100.1 255.255.255.0ip address dmz 192.168.200.1 255.255.255.0step4:地址转换(必须)* 安全高的区域访问安全低的区域(即内部到外部)需NAT和global;nat(inside) 1 192.168.1.1 255.255.255.0global(outside) 1 222.240.254.193 255.255.255.248*** nat (inside) 0 192.168.1.1 255.255.255.255 表示192.168.1.1这个地址不需要转换。
直接转发出去。
* 如果内部有服务器需要映射到公网地址(外网访问内网)则需要static和conduit或者acl.static (inside, outside) 222.240.254.194 192.168.1.240static (inside, outside) 222.240.254.194 192.168.1.240 10000 10后面的10000为限制连接数,10为限制的半开连接数。
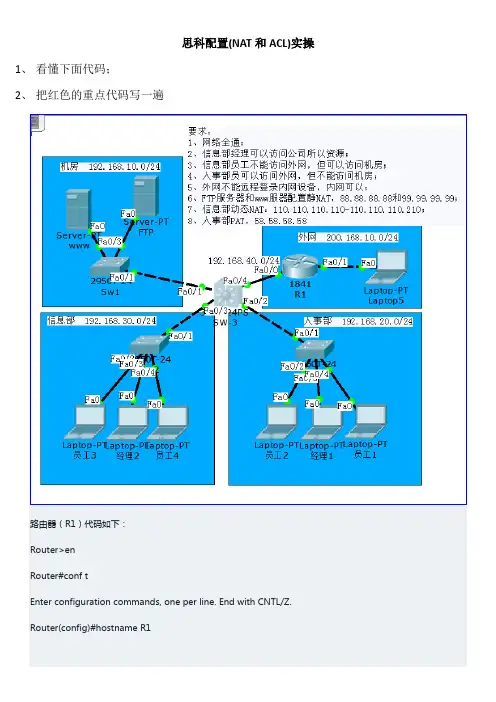
思科配置(NAT和ACL)实操1、看懂下面代码;2、把红色的重点代码写一遍R1(config)#interface f0/0R1(config-if)#no shutdownR1(config-if)#R1(config-if)#ip add 192.168.40.1 255.255.255.0R1(config-if)#exitR1(config)#interface f0/1R1(config-if)#no shutdownR1(config-if)#ip add 200.168.10.1 255.255.255.0R1(config-if)#R1(config-if)#exitR1(config)#router rip 动态路由配置R1(config-router)#network 192.168.40.0R1(config-router)#network 200.168.10.0R1(config-router)#exitR1(config)#line vty 0 4R1(config-line)#password 123R1(config-line)#loginR1(config-line)#exitR1(config)#enable password 123R1(config)#ip access-list extended NOtelnet 禁止外网远程登录R1(config-ext-nacl)#denyR1(config-ext-nacl)#deny tcp any any eq 23R1(config-ext-nacl)#permit ip any anyR1(config-ext-nacl)#exitR1(config)#interface f0/1R1(config-if)#ip access-group NOtelnet inR1(config)#ip nat inside source static 192.168.10.10 88.88.88.88 静态NATR1(config)#ip nat inside source static 192.168.10.20 99.99.99.99R1(config)#R1(config)#access-list 10 permit 192.168.30.0 0.0.0.255 动态NATR1(config)#ip nat pool XXB 110.110.110.110 110.110.110.210 netmask 255.255.255.0 R1(config)#ip nat inside source list 10 pool XXBR1(config)#R1(config)#access-list 20 permit 192.168.20.0 0.0.0.255 PATR1(config)#ip nat pool RSB 58.58.58.58 58.58.58.58 netmask 255.255.255.0R1(config)#ip nat inside source list 20 pool RSB overloadR1(config)#R1(config)#interface f0/0R1(config-if)#ip nat insideR1(config-if)#exitR1(config)#interface f0/1R1(config-if)#ip nat outside三层交换机(SW-3)代码如下:Switch>Switch>enSwitch#conf tSwitch(config)#hostname SW-3SW-3(config)#SW-3(config)#interface range f0/1-4SW-3(config-if-range)#no switchportSW-3(config-if-range)#SW-3(config-if-range)#exitSW-3(config)#SW-3(config)#interface f0/1SW-3(config-if)#ip address 192.168.10.1 255.255.255.0 SW-3(config-if)#exitSW-3(config)#interface f0/2SW-3(config-if)#ip address 192.168.20.1 255.255.255.0 SW-3(config-if)#exitSW-3(config)#interface f0/3SW-3(config-if)#ip address 192.168.30.1 255.255.255.0 SW-3(config-if)#exitSW-3(config)#interface f0/4SW-3(config-if)#ip address 192.168.40.2 255.255.255.0 SW-3(config-if)#exitSW-3(config)#ip routingSW-3(config)#router ripSW-3(config-router)#network 192.168.10.0SW-3(config-router)#network 192.168.20.0SW-3(config-router)#network 192.168.30.0SW-3(config-router)#network 192.168.40.0SW-3(config-router)#exitSW-3(config)#SW-3(config)#ip access-list extended JFACL 信息部员工可以访问机房,人事部员不能访问机房SW-3(config-ext-nacl)#permit ip 192.168.30.0 0.0.0.255 192.168.10.0 0.0.0.255SW-3(config-ext-nacl)#deny ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255SW-3(config-ext-nacl)#permit ip any anySW-3(config-ext-nacl)#exit、信息部员工不能访问外网,但可以访问机房;4、人事部员可以访问外网,但不能访问机房;SW-3(config)#interface f0/1SW-3(config-if)#ip access-group JFACL outSW-3(config-if)#exitSW-3(config)#SW-3(config)#ip access-list extended WWACL 人事部和信息部经理可以访问外网,信息部不能访问外网SW-3(config-ext-nacl)#permit ip 192.168.20.0 0.0.0.255 200.168.10.0 0.0.0.255SW-3(config-ext-nacl)#permit ip host 192.168.30.20 200.168.10.0 0.0.0.255SW-3(config-ext-nacl)#deny ip 192.168.30.0 0.0.0.255 200.168.10.0 0.0.0.255 SW-3(config-ext-nacl)#permit ip any anySW-3(config-ext-nacl)#exitSW-3(config)#SW-3(config)#interface f0/4SW-3(config-if)#ip access-group WWACL out。

acl在nat中的作用(一)ACL在NAT中的作用什么是ACL(Access Control List)ACL是一种用于控制网络流量的机制,它定义了网络上设备处理数据包的规则。
ACL可用于过滤某些特定类型的流量,同时也可以用于限制特定流量的源和目标。
在网络设备中,ACL通常由一条条规则组成,每条规则都包含一些条件来匹配数据包和一些操作来控制该数据包的处理方式。
ACL在NAT中的作用ACL在NAT(Network Address Translation)中起着重要的作用,它能够帮助我们更好地管理和保护我们的网络。
以下是ACL在NAT中的一些作用:1.限制访问:ACL可以配置为只允许特定的IP地址或IP地址范围访问特定的网络资源。
通过ACL,我们可以限制访问某些敏感信息或重要的网络设备。
2.保护内部网络:ACL可以配置为只允许特定的IP地址或IP地址范围从外部网络访问内部网络。
这样一来,我们可以防止外部网络中的未经授权的用户访问我们的内部网络,提高安全性。
3.过滤流量:ACL可以过滤特定类型的流量,例如某些危险的协议或恶意的流量。
通过ACL,我们可以限制某些危险流量的进入,从而保护我们的网络免受攻击。
4.调整流量优先级:ACL可以配置为根据特定的条件调整流量的处理方式。
例如,我们可以使用ACL设置某些流量的优先级,确保重要的流量具有更高的带宽和更低的延迟。
5.实现端口转发:ACL可以帮助我们实现端口转发,将外部网络上的请求转发到内部网络的特定设备或服务器。
通过ACL的配置,我们可以将特定的端口映射到内部网络的地址上,提供服务或应用程序的访问。
总结ACL在NAT中扮演着重要的角色,通过ACL的配置,我们可以更好地管理和保护我们的网络。
通过限制访问、保护内部网络、过滤流量、调整流量优先级以及实现端口转发,ACL可以帮助我们提高网络的安全性和性能。
总之,ACL是网络管理中不可或缺的一部分,在NAT中的应用尤为重要。
基本思路如图所示1、配置DNS外网那个服务器注意网关是为了实验方便,实际不会设置防火墙outside口的IP地址的2、DMZ区的web服务器IP地址192.168.202.2 网关为192.168.202.13、inside 区则放了一台PC机,pc机的IP:192.168.201.2网关为192.168.201.1DNS就用拓扑图中的DNS地址4、首先要将防火墙的主机名域名路由配置好这样才可以PC机ping通192.168.201.1通过三个配置你会发现DNS PC DMZ去ping自己所在的网关都是通的但是如果想pc 想pingDmz会发现无法ping通的这个是时候要做一个ACL 让他们两两ping通其中111是一个扩展访问ACL 但因为后面接了一个permit 所以不写extend也可以这个时候你用netstat -an 你会发现在outside的DNS 可以看到内网的IP 这个就不符合要求了。
也就是防火墙现在单单是一个路由器的功能所以这个时候要做的是1、将DNS服务器的网关去掉因为实际就这样不可能配置好网关的。
2、为内网的出站做一个网络地址转换----NAT 做一个PAT 其中命令中的1表示一个标记这个时候你会发现PC机又可以重新ping通外网了。
用netstat –an 可以看到地址已转换3、新问题:这时你会发现内网访问DMZ区不行也就是说如果要访问DMZ区要做一个针对DMZ区的地址转换这个时候你去DMZ区用netstat –an 可以看到地址已转换。
3、以上就是NAT的DMZ与outside的做好了要求:外网的DNS 可以访问到内网的DMZ区:这个时候做一个静态NAT 将DMZ区的服务器发布出去这个时候要考虑与前面的111extended想对应这个时候最好show run 看看。
做一个远程管理接入:开启telnet ssh 等SSH这里弄了一个钥匙对。

ACL配置步骤范文ACL(Access Control List)是一种网络安全机制,用于控制网络设备上的流量。
在网络设备上配置ACL可以限制特定IP地址、网络流量类型或端口来控制网络访问权限,提高网络安全性。
下面是配置ACL的一般步骤:1.确定ACL策略的目的:在配置ACL之前,需要确定ACL的目的和需求。
例如,你可能想要限制访问一些特定的网络服务或者仅允许特定的IP地址访问网络设备。
2.创建ACL规则:根据设定的目的,创建适当的ACL规则。
ACL规则是根据源IP地址、目标IP地址、协议类型、端口号等条件来匹配和处理流量。
2.1 确定源地址和目标地址:确定需要限制的源IP地址和目标IP地址。
可以是单个IP地址、子网地址、IP地址范围,也可以是任意(any)或未知(unknown)。
2.2确定协议类型:确定需要限制的协议类型,例如TCP、UDP、ICMP 等。
2.3 确定端口号:如果要限制特定的服务或端口号,需要指定源端口和目标端口。
例如,如果希望限制对Web服务(80端口)的访问,则需要指定TCP协议和源端口80。
2.4确定动作:对于匹配到的ACL规则,需要确定应该执行的动作。
动作可以是允许通过、拒绝、转发、丢弃等。
2.5配置ACL规则:在设备上的配置界面或CLI(命令行界面)上,依次输入每个ACL规则,确保正确设置源地址、目标地址、协议类型、端口号和动作。
3.配置ACL应用范围:在设备上配置ACL的应用范围,以将ACL规则应用到特定的接口或者设备。
可以选择将ACL配置到输入接口、输出接口或者特定路由上。
3.1选择接口:选择需要应用ACL的接口,例如以太网接口、无线接口等。
3.2配置接口:在设备上的配置界面或CLI上为所选接口配置ACL。
根据设备类型和操作系统,配置方式可能会有所不同。
4.验证ACL配置:在完成ACL配置后,需要验证其是否起作用并达到预期的目的。
可以使用一些网络分析工具来验证ACL的配置效果。

双实验平台的路由实验设计双实验平台的路由实验设计实验一路由器基本配置实验实验二路由器的密码恢复实验实验三路由器的IOS恢复实验实验四路由器通信基础实验实验五静态路由的配置实验实验六RIP路由协议实验实验七OSPF路由协议实验实验八PPP协议实验实验九ACL配置实验实验十NAT配置实验实验十一DHCP配置实验实验十二Packet Tracer综合实验实验一路由器基本配置实验1.1实验目标:通过本实验,我们应该掌握:●通过Console口配置路由器●通过telnet配置设备●基本配置命令1.2 设备要求●路由器一台●PC机一台●网线一根●Console线一根1.3实验环境搭建图1-1实验基本拓扑1.4命令参考1.5 检测PC与路由器的连通性使用ping命令检测,能否ping通路由器;并在PC上运行telnet应用程序登录路由器。
如果没有成功,请检查配置文档实验二路由器的密码恢复实验2.1实验目标:通过本实验,我们应该掌握:●路由器的密码恢复●路由器重置2.2 设备要求●路由器一台●PC机一台●Console线一根2.3实验环境搭建图2-1 实验基本拓扑2.4命令参考真机平台第一步:当我们用console线连接MSR路由器控制时同样需要密码,而这个密码也被遗忘了。
第二步:这时我们可以将MSR路由器的电源关闭,然后在CONSOLE线连接正常的情况下重新启动MSR路由器。
第三步:注意观察终端连接中显示的信息,当出现“press CTRL+B to enter extended boot menu”时我们迅速按下CTRL和B键,这样将进入扩展启动选项。
第四步:在扩展启动选项中有九个选项提供给我们选择,依次是启动CF卡中的系统,进入串口子菜单,进入以太口子菜单,文件控制,修改bootrom的密码,忽略加载系统config文件启动,清空super超级密码,设备操作以及重新启动。
要注意的是清空super超级密码并不是我们要选择的,他只适用于基于密码的验证而不是基于用户名和密码两者验证的方式。

acl基本配置实验总结ACL(Access Control List)是网络设备中常用的一种安全控制机制,用于限制网络流量的访问权限。
在网络配置实验中,基本的ACL配置是必不可少的一环,它能够帮助管理员实现对网络流量的精细化控制。
本文将对ACL基本配置实验进行总结,并介绍实验过程中需要注意的关键点。
一、实验目的本次实验的主要目的是学习和掌握ACL的基本配置方法,并了解其在网络安全中的重要作用。
通过实践操作,加深对ACL的理解,为今后在网络管理和安全中的应用打下基础。
二、实验环境本次实验使用的环境是一个模拟的网络拓扑结构,包括多个主机和网络设备。
通过连接这些设备,并进行相应的配置,实现ACL的功能。
三、实验步骤1. 配置网络设备:首先需要对网络设备进行基本的配置,包括设置IP地址、子网掩码、网关等。
这些配置将为后续的ACL配置提供基础支持。
2. 创建ACL规则:在网络设备中创建ACL规则,用于限制网络流量的访问权限。
ACL规则可以基于源IP地址、目标IP地址、协议类型等进行过滤。
管理员可以根据实际需求,设置不同的ACL规则。
3. 应用ACL规则:将ACL规则应用到网络设备的特定接口上。
通过应用ACL规则,可以限制特定接口的流量访问权限,提高网络的安全性。
4. 测试ACL配置:在ACL配置完成后,需要进行测试验证。
可以通过发送不同类型的网络流量,观察ACL规则是否生效,以及网络流量是否按照规则进行过滤。
四、实验总结ACL基本配置实验是学习网络安全中重要的一环。
通过实验,我深入了解了ACL的配置方法和原理,掌握了基本的ACL规则设置和应用。
ACL能够在网络中起到精细化的流量控制作用,提高网络的安全性和可管理性。
在实验过程中,我遇到了一些问题,例如配置错误导致ACL规则无法生效,或者配置过于复杂导致网络流量无法正常传输。
通过仔细分析问题原因,并进行相应的调整和修正,最终解决了这些问题。
通过本次实验,我还发现ACL配置需要考虑以下几个关键点:1. 精确的ACL规则:ACL规则应该尽可能精确,以避免对合法流量的误过滤。
acl配置实验报告ACL配置实验报告一、实验目的本实验旨在通过配置ACL(Access Control List)来实现对网络数据包的访问控制,实现对网络流量的过滤和控制,保障网络安全。
二、实验环境本次实验使用了一台运行Linux操作系统的服务器作为实验环境,通过配置iptables来实现ACL的配置。
三、实验步骤1. 首先,我们需要在服务器上安装iptables,可以通过以下命令进行安装:sudo apt-get install iptables2. 接下来,我们需要创建ACL规则,可以通过以下命令进行配置:sudo iptables -A INPUT -s 192.168.1.0/24 -j DROP以上命令表示拒绝所有来自192.168.1.0/24网段的数据包。
3. 配置完成后,我们可以通过以下命令查看已配置的ACL规则:sudo iptables -L4. 最后,我们可以测试ACL规则是否生效,可以通过向服务器发送数据包来进行测试,如果ACL规则配置正确,服务器应该能够正确过滤和控制数据包。
四、实验结果经过测试,ACL配置成功生效,服务器能够正确过滤和控制数据包,实现了对网络流量的有效管理。
五、实验总结通过本次实验,我们了解了ACL的配置和使用方法,掌握了对网络流量进行过滤和控制的技能,这对于提升网络安全性和保障网络畅通具有重要意义。
六、实验展望未来,我们可以进一步研究ACL的高级用法,如通过ACL实现对特定协议或端口的访问控制,以及结合其他安全设备和技术,进一步提升网络安全水平。
综上所述,本次实验取得了良好的效果,对ACL的配置和使用有了更深入的了解,为今后的网络安全工作奠定了基础。
《数据通信与计算机网络实验》实验报告实验八网络配置综合设计班级:xxxxxxxx学号:xxxxxx姓名:xxxxx案例3一公司总部与分部公网互联一、目标1、熟悉VLAN规和VLAN间路由2、熟悉路由的配置(rip或其他的路由都可以)。
3、熟悉acl配置4、熟悉NAT配置5、ip地址划分与拓扑结构设计二、场景1、某公司总部为一栋三层大楼,如图1所示,每层节点数量如图所示。
1 楼由人力资源部门占用,2 楼由 IT 部门占用,3 楼由销售部门占用。
所有部门必须能相互通信,但是同时又拥有自己独立的工作网络。
给定的IP地址范围是:192.168.X.0/24,根据实际情况划分子网(其中X为个人的学号序号)。
图1 公司总部2、该公司有一个分支机构离公司总部不远,该分支机构为一个二层小楼如图2所示,1 楼由研发部门占用,2 楼由行政部门占用,所有部门必须能相互通信,但是同时又拥有自己独立的工作网络。
给定的IP地址范围是:192.168.X+1.0/24,根据实际情况划分子网(其中X为个人的学号序号)。
图2 分支机构3、公司内部无网络设备,全部设备需新采购,总部与分支机构之间通过专网相连,但都能访问公网,你是网络管理员,必须设计公司总部、分支机构与公网三者之间的联网方案,以便为所有公司员工提供高速的内部网络和INTERNET服务。
三、步骤第 1 步: 设计拓扑。
图3 网络拓扑图设计第 2 步: 制定 VLAN 方案。
a. 为所有部门设计 VLAN 的名称和编号。
b. 包括一个管理 VLAN,可以命名为“管理”或“本征”,根据您的选择编号。
c. 使用 IPv4作为你的 LAN 编址方案,也必须使用 VLSM。
d. IP地址与VLAN分配,以下为示例表格。
地址表VLAN与端口分配(交换机1)VLAN与端口分配(交换机2)VLAN与端口分配(交换机3)VLAN与端口分配(交换机4)第 3 步: 设计一个图来展示你的 VLAN 设计和地址方案。
实验10 思科ASA防火墙的NAT配置一、实验目标1、掌握思科ASA防火墙的NAT规则的基本原理;2、掌握常见的思科ASA防火墙的NAT规则的配置方法。
二、实验拓扑根据下图搭建拓扑通过配置ASA防火墙上的NAT规则,使得inside区能单向访问DMZ区和outside区,DMZ区和outside区能够互访。
三、实验配置1、路由器基本网络配置,配置IP地址和默认网关R1#conf tR1(config)#int f0/0R1(config-if)#ip address 192.168.2.1 255.255.255.0R1(config-if)#no shutdownR1(config-if)#exitR1(config)#ip default-gateway 192.168.2.254 //配置默认网关R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.2.254 //添加默认路由R1(config)#exitR1#writeR2#conf tR2(config)#int f0/0R2(config-if)#ip address 202.1.1.1 255.255.255.0R2(config-if)#no shutdownR2(config-if)#exitR2(config)#ip default-gateway 202.1.1.254R2(config)#exitR2#writeServer#conf tServer(config)#no ip routing //用路由器模拟服务器,关闭路由功能Server(config)#int f0/0Server(config-if)#ip address 192.168.1.1 255.255.255.0Server(config-if)#no shutdownServer(config-if)#exitServer(config)#ip default-gateway 192.168.1.254Server(config)#exitServer#write*说明:实际配置中最好在三台路由器上都添加一条通往防火墙的默认路由,但在本实验中Server和R2不配置不影响实验效果。
NAT和ACL综合实验,让内⽹部...NAT和ACL课后实验作业现在将图整理成以下拓扑图:上图中的R4更换成下⾯图中的R1,上图中的R3更换成下⾯图中的R2,上图中的R1更换成下⾯图中的PC1,上图中的R2更换成下⾯图中的PC2本实验禁⽌动态路由协议,静态路由最多不会超过2条实验要求:1.R1和R2模拟成某公司的PC1和PC2,并且R1的IP地址为192.168.1.1,R2的地址为192.168.1.100。
2.R3模拟成改公司的⽹关,R4模拟成Internet⽹。
并且要求在R3上配置NAT和ACL。
3.在R4存在起环回⼝地址分是10.1.1.1 ,22.1.1.1,33.1.1.1 ,44.1.1.1 ,4.在R3上配置NAT要求能够实现192.168.1.0/24⽹段类的主机能够访问R4上的所有⽹段。
5.在R3上配置ACL要求实现允许公司IP地址范围在192.168.1.1–192.168.1.10的地址任意访问Internet⽹,但是其他的地址只能上QQ和去访问⼀个地址为33.1.1.1的WWW服务器。
R1的地址范围在192.168.1.1-10之间,R2的地址范围在192.168.1.11-2546.并且当受限制的⽤户将地址改成192.168.1.1—192.168.1.10也是⼀样不能正常访问Internet的,例如R2将地址改成192.168.1.1的地址还是⼀样不能访问Internet⽹的。
7.并且禁⽌外⽹的⽤户去PING R3以及内⽹所有的地址,禁⽌去telnet R38.作业做玩以后现象截图,配置⽂档全部以word⽂档上交。
试验步骤:1、按照配置路由器以及交换机交换机只需要打好预配就可以了,这⾥就不再截图了,所有预配的步骤我都没有截图,讲的是重点2、因为PC1和PC2是路由器模拟的,所以需要关闭路由功能然后配置地址以及⽹关3、配置默认路由4、做连通性测试5、在R2上配置NAT和ACL实现192.168.1.0/24⽹段类的主机能够访问R1上的所有⽹段。
nat配置实验报告一、实验目的本次实验的主要目的是深入了解和掌握网络地址转换(NAT)的配置方法和工作原理,通过实际操作,实现不同网络之间的地址转换,提高网络的安全性和可扩展性。
二、实验环境1、操作系统:Windows Server 20192、网络设备:Cisco 路由器3、模拟软件:Packet Tracer三、实验原理NAT(Network Address Translation)即网络地址转换,是一种将私有 IP 地址转换为公有 IP 地址的技术。
其主要作用包括:1、解决 IPv4 地址短缺问题:通过多个私有地址共用一个公有地址进行网络通信,节省了公有地址资源。
2、增强网络安全性:隐藏内部网络的拓扑结构和私有 IP 地址,降低了来自外部网络的攻击风险。
NAT 主要有三种类型:1、静态 NAT:将一个私有 IP 地址永久映射到一个公有 IP 地址。
2、动态 NAT:将一组私有 IP 地址动态映射到一组公有 IP 地址。
3、端口地址转换(PAT):也称为 NAT 重载,通过端口号区分不同的私有 IP 地址与公有 IP 地址的映射关系。
四、实验步骤1、打开 Packet Tracer 软件,创建网络拓扑结构。
包括一个内部网络、一个外部网络和一台执行 NAT 功能的路由器。
2、配置内部网络的 IP 地址和子网掩码。
为内部网络中的主机分配私有 IP 地址,例如 19216811 192168110 ,子网掩码为 2552552550 。
3、配置外部网络的 IP 地址和子网掩码。
为外部网络中的主机分配公有 IP 地址,例如 20210011 ,子网掩码为 2552552550 。
4、配置路由器的接口 IP 地址。
为连接内部网络的接口配置私有 IP 地址,为连接外部网络的接口配置公有 IP 地址。
5、配置静态 NAT 。
选择一个内部主机(例如 19216811 ),将其私有 IP 地址静态映射到一个公有 IP 地址(例如 20210012 )。
实验八ASA 配置NAT 和ACL实验拓扑实验要求1 配置PAT,实现inside 区域内主机访问internet2 配置静态地址转换,实现DMZ 区域主机172.16.2.1 转换为202.100.0.1023 配置Identity NAT,实现172.16.100.2 访问inside 时,使用本ip地址4 配置ACL,实现DMZ 区域内主机只允许icmp,telnet 流量访问去往inside 区域5 配置ACL,实验inside 区域内主机192.168.1.1 不允许去往任何地址,只能在本区域访问实验步骤步骤2根据设备表,配置ASA 和路由器的接口IP 地址R1(config)#interface fastEthernet 0/0R1(config-if)#ip address 192.168.100.1 255.255.255.0R1(config-if)#no shutdownR1(config-if)#exitR1(config)#interface loopback 0R1(config-if)#ip address 192.168.1.1 255.255.255.0R1(config-if)#exitR2(config)#interface fastEthernet 0/0R2(config-if)#ip address 172.16.100.2 255.255.255.0R2(config-if)#no shutdownR2(config-if)#exitR2(config)#interface loopback 0R2(config-if)#ip address 172.16.2.1 255.255.255.0R2(config-if)#exitR3(config)#interface fastEthernet 0/0R3(config-if)#ip address 202.100.0.3 255.255.255.0R3(config-if)#no shutdownR3(config-if)#exitR3(config)#interface loopback 0R3(config-if)#ip address 123.123.123.123 255.255.255.0R3(config-if)#exitciscoasa(config)# interface ethernet 0/0ciscoasa(config-if)# nameif insideINFO: Security level for "inside" set to 100 by default.ciscoasa(config-if)# ip address 192.168.100.100 255.255.255.0 ciscoasa(config-if)# no shutdownciscoasa(config-if)# exitciscoasa(config)# interface ethernet 0/1ciscoasa(config-if)# nameif DMZINFO: Security level for "DMZ" set to 0 by default.ciscoasa(config-if)# security-level 50ciscoasa(config-if)# ip address 172.16.100.100 255.255.255.0 ciscoasa(config-if)# no shutdownciscoasa(config-if)# exitciscoasa(config)# interface ethernet 0/2ciscoasa(config-if)# nameif outsideINFO: Security level for "outside" set to 0 by default.ciscoasa(config-if)# ip address 202.100.0.100 255.255.255.0ciscoasa(config-if)# no shutdownciscoasa(config-if)# exit测试连通性:ciscoasa(config)# ping 192.168.100.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.100.1, timeout is 2 seconds: !!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/10 ms ciscoasa(config)# ping 172.16.100.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 172.16.100.2, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/10 msciscoasa(config)# ping 202.100.0.3Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 202.100.0.3, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms步骤3配置路由协议,保证每台设备可以转发相应的数据包R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.100.100 //将所有不认识的数据包发送给ASA R2(config)#ip route 0.0.0.0 0.0.0.0 172.16.100.100 //将所有不认识的数据包发送给ASA ciscoasa(config)# route outside 0 0 202.100.0.3 //ASA 为企业网关,默认路由指向internet配置OSPF,保证内网通信R1(config)#router ospf 1R1(config-router)#router-id 1.1.1.1R1(config-router)#network 192.168.100.1 0.0.0.0 area 100R1(config-router)#network 192.168.1.1 0.0.0.0 area 100R1(config-router)#exitR2(config)#router ospf 1R2(config-router)#router-id 2.2.2.2R2(config-router)#network 172.16.100.2 0.0.0.0 area 100R2(config-router)#network 172.16.2.1 0.0.0.0 area 100R2(config-router)#exitciscoasa(config)# router ospf 1ciscoasa(config-router)# router-id 100.100.100.100ciscoasa(config-router)# network 192.168.100.100 255.255.255.255 area 100ciscoasa(config-router)# network 172.16.100.100 255.255.255.255 area 100ciscoasa(config-router)# exit步骤4配置PAT,实现inside 区域内主机访问internet配置PAT 前,现将MPF 中ICMP 流量放行ciscoasa(config)# policy-map global_policyciscoasa(config-pmap)# class-mapinspection_default(class-mapinspection_defaultmatch default-inspection-traffic)ciscoasa(config-pmap-c)# inspect icmpciscoasa(config-pmap-c)# exitciscoasa(config-pmap)# exit配置PATciscoasa(config)# nat (inside) 1 192.168.0.0 255.255.0.0ciscoasa(config)# global (outside) 1 interfaceINFO: outside interface address added to PAT poolciscoasa(config)#测试:R1#ping 123.123.123.123Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 123.123.123.123, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 m查看NAT 地址转换表ciscoasa(config)# show xlate1 in use,2 most usedPAT Global 202.100.0.100(8) Local 192.168.100.1 ICMP id 11步骤5配置静态地址转换,实现DMZ 区域主机172.16.2.1 转换为202.100.0.102 ciscoasa(config)# static (DMZ,outside) 202.100.0.102 172.16.2.1测试:R2#ping 123.123.123.123 source 172.16.2.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 123.123.123.123, timeout is 2 seconds:Packet sent with a source address of 172.16.2.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 msR3#debugipicmpICMP packet debugging is onR3#*Mar 1 01:09:38.391: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.102 *Mar 1 01:09:40.387: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.102 *Mar 1 01:09:40.391: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.102 *Mar 1 01:09:40.395: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.102 *Mar 1 01:09:40.399: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.102 *Mar 1 01:10:52.263: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.102步骤6配置Identity NAT,实现192.168.1.1 访问outside 时,使用本ip地址R1#ping 123.123.123.123 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 123.123.123.123, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/4 msR3#*Mar 1 02:33:28.955: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.100*Mar 1 02:33:28.959: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.100*Mar 1 02:33:28.963: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.100*Mar 1 02:33:28.967: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.100*Mar 1 02:33:28.971: ICMP: echo reply sent, src 123.123.123.123, dst 202.100.0.100//此时用192.168.1.1 去ping 123.123.123.123 时,对于R3 来说看到是被地址转换后得IP配置Identity NATciscoasa(config)# nat (inside) 0 192.168.1.1 255.255.255.255nat 0 192.168.1.1 will be identity translated for outboundciscoasa(config)#测试R1#ping 123.123.123.123 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 123.123.123.123, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1.....Success rate is 0 percent (0/5)//发现现在不能ping 通123.123.123.123 了R3# //在R3 开启debug,发现192.168.1.1 没有被地址转换*Mar 1 02:35:50.639: ICMP: echo reply sent, src 123.123.123.123, dst 192.168.1.1*Mar 1 02:35:52.635: ICMP: echo reply sent, src 123.123.123.123, dst 192.168.1.1*Mar 1 02:35:54.635: ICMP: echo reply sent, src 123.123.123.123, dst 192.168.1.1*Mar 1 02:35:56.635: ICMP: echo reply sent, src 123.123.123.123, dst 192.168.1.1*Mar 1 02:35:58.635: ICMP: echo reply sent, src 123.123.123.123, dst 192.168.1.1现在大家想想不通的原因?查看R3 的路由表R3#show ip routeGateway of last resort is not setC 202.100.0.0/24 is directly connected, FastEthernet0/0123.0.0.0/24 is subnetted, 1 subnetsC 123.123.123.0 is directly connected, Loopback0//没有去往192.168.1.1 的路由,因为192.168.1.1 为私有地址,在公网中是不能路由的,在本实验环境中,我们可以手工写一个静态路由去往192.168.1.1R3(config)#ip route 192.168.1.1 255.255.255.255 202.100.0.100R1#ping 123.123.123.123 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 123.123.123.123, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms步骤7配置ACL,实现DMZ 区域内主机只允许icmp,telnet 流量访问去往inside 区域删除之前配置的NA T,防止干扰配置前,先测试下R2#ping 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:.....Success rate is 0 percent (0/5)在ASA 查看日志ciscoasa(config)# show loggingSyslog logging: enabledFacility: 20Timestamp logging: enabledStandby logging: disabledDeny Conn when Queue Full: disabledConsole logging: disabledMonitor logging: disabledBuffer logging: level informational, 561 messages loggedTrap logging: disabledHistory logging: disabledDevice ID: disabledMail logging: disabledASDM logging: disabledMar 29 2011 19:34:15: %ASA-3-106014: Deny inbound icmpsrc DMZ:172.16.100.2dst inside:192.168.1.1 (type 8, code 0)Mar 29 2011 19:34:17: %ASA-3-106014: Deny inbound icmpsrc DMZ:172.16.100.2dst inside:192.168.1.1 (type 8, code 0)Mar 29 2011 19:34:19: %ASA-3-106014: Deny inbound icmpsrc DMZ:172.16.100.2dst inside:192.168.1.1 (type 8, code 0)Mar 29 2011 19:34:21: %ASA-3-106014: Deny inbound icmpsrc DMZ:172.16.100.2dst inside:192.168.1.1 (type 8, code 0)Mar 29 2011 19:34:23: %ASA-3-106014: Deny inbound icmpsrc DMZ:172.16.100.2dst inside:192.168.1.1 (type 8, code 0)ciscoasa(config)#//可以看到DMZ 区域去往inside 区域的ICMP 流量被拒绝掉了因为防火墙默认为,安全级别低的区域访问安全级别高的区域时,拒绝所有数据通过ciscoasa(config)#access-list DMZ extended permit icmp 172.16.0.0 255.255.0.0192.168.0.0 255.255.0.0ciscoasa(config)#access-list DMZ extended permit tcp 172.16.0.0 255.255.0.0192.168.0.0 255.255.0.0 eq telnetciscoasa(config)# access-group DMZ in interface DMZ测试:R2#ping 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 msR2#telnet 192.168.1.1Trying 192.168.1.1 ... OpenR1>R1>exit[Connection to 192.168.1.1 closed by foreign host]R2#步骤8配置ACL,实验inside 区域内主机192.168.1.1 不允许去往任何地址,只能在本区域访问R1#ping 172.16.2.1 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 172.16.2.1, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 44/64/84 msR1#ping 123.123.123.123 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 123.123.123.123, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms配置ACL,192.168.1.1 不允许去往任何地址,只能在本区域访问ciscoasa(config)# access-list deny-inside standard deny 192.168.1.1 255.255.255.255 ciscoasa(config)# access-list deny-inside standard permit anyciscoasa(config)# access-group deny-inside in interface insideERROR: access- - list <deny- - inside> is standard. Only "extended" or "ethertype" acls can be attached to an interfaceciscoasa(config)#//本步骤使用标准ACL 是可以实现的,但是在ASA 上标准ACL 不能在接口应用ciscoasa(config)# access-list deny-inside-any extended deny ip host 192.168.1.1 any ciscoasa(config)# access-list deny-inside-any extended permit ip any anyciscoasa(config)# access-group deny-inside-any in interface inside测试:R1#ping 172.16.2.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 172.16.2.1, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 48/58/84 msR1#ping 172.16.2.1 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 172.16.2.1, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1.....Success rate is 0 percent (0/5)。