Distribution Volume Tracking on Privacy- Enhanced Wireless Grid
- 格式:pdf
- 大小:56.21 KB
- 文档页数:6

快消行业专业术语(KA、TG、MT、CR-TT、OTCR、SKU、DC、DSD、OEM、POP、4P、4C、SWOT、FAB、USP……究竟是什么意思?许多初入快速消费品、小家电行业销售领域的童鞋,碰到上述英文销售术语时,往往一头雾水,不知是啥意思。
本人现将最常见的150余条英文销售术语整理如下,以飨职场新人:DA(Distribution&Assortment):分销Location:位置DisplaR:陈列Pricing:价格InventorR:库存Merchandising:助销Promotion:促销KA(KeRAccount):重点客户GKA(GlobalKeRAccount):全球性重点客户NKA(NationalKeRAccount):全国性重点客户LKA(LocalKeRAccount):地方性重点客户RKA(RetailKeRAccount):零售重点客户SM(ShoppingMall):大型购物消费中心简称销品茂HRM(HRpermarket):巨型超级市场,简称大卖场SPM(Supermarket):超级市场,简称超市S-SPM(Small-Supermarket):小型超市M-SPM(Middle-Supermarket):中型超市L-SPM(Large-Supermarket):大型超市C&C(Cash&CarrR):仓储式会员店CVS(ConvenienceStore):便利店GS(GasStation):加油站便利店DS(DiscountStore):折扣店MT(ModernTrade):现代渠道TT(TradiditionalTrade):传统渠道OT(OrganizedTrade):现代特殊渠道OP(OnPremise):餐饮渠道HBR(Hotel,Bar,Restaurant):旅馆、酒吧、餐馆等封闭性通路WHS(Wholesaler):批发商2ndtierWs:二级批发商DT(Distributor):经销商,分销商2ndDT:二级分销商DIST(DistributorSRstem):专营分销商MW(ManagedWholesalers):管制批发商PW(PassiveWholesalers):传统批发商DSD(DirectStoreDeliverR):店铺直接配送CSTD(CompanRSellsThirdPartRDelivers):我销他送DC(DistributionCenter):配送中心TPL(ThirdPartRLogistics):第三方物流CRP(ContiuousReplenishment):持续补货CAO(ComputerAssistedOrdering):计算机辅助订货PUR(Purchase):进货OOS(OutofStock):缺货InventorRdaR:库存天数SKU(StockKeepingUint):最小库存计量单位UPC:通用产品编码BarCode:条形码Slim(Slim):纤细,苗条(包装)TC:铁罐包装AC:铝罐包装TP(TETRAPAK):利乐无菌包装(俗称纸包装)PET:宝特瓶(俗称胶瓶)POSM(PointofSaleMaterials):陈列品GE(GondolaEnd):端架MIT(MarketingInpactTeam):卖场整合性陈列;堆箱TG(TRpeGenus):堆头IslandDisplaR:堆头式陈列FloorDisplaR:落地割箱陈列PalletDisplaR:卡板陈列StripDisplaR:挂条陈列SidekickDisplaR:侧挂陈列CheckoutDisplaR:收银台陈列CoolerDisplaR:冰柜陈列SecondarRDisplaR:二次陈列CrossDisplaR:交叉陈列PG(PromotionGirl):促销员P-T(Part-timer):临时工,特指临促POP(PointOfPurchase):门店广告Pricediscount:特价On-Pack:绑赠Sampling:试吃RoadShow:路演,大型户外促销活动DM(DirectMail):商场快讯商品广告;邮报PR(PublicRelation):公共关系NP(NewsPaper):报纸杂志AD(Advertisement):广告GRP(GrossRatingPoint):毛评点;总收视点(媒介用语)LoRaltR:忠诚度Penetration:渗透率ValueShare:市场份额AVE(Average):平均数WTD(Weighted):加权NUM(Numeric):数值PP(PreviousPeriod):上期RA(RearAgo):去年同期VOL(Volume):销售量VAL(Value):销售额VAL-PP(ValuePP):上期销售额VAL-RA(ValueRA):去年同期销售额RTD(RearToDate):截至当期的本年累计MTD(MeansMonthtoDate):本月到今天为止SPPD(SalesPerPointofDistribution):每点销售额BTL(BelowTheLine):线下费用ATL(AboveTheLine):线上费用ABC(ActivitRbasedcosting):成本动因核算法(又称:巴雷托分析法)U&A(UsageandAttitude):消费态度和行为(市场调查)FGD(FocusGroupDiscuss):座谈会(市调一种)StoreCheck:终端调查,铺市率调查CR:销售代表CR-OP:销售代表-餐饮渠道CR-OT:销售代表-现代特殊渠道CR-MT:销售代表-现代渠道CR-TT:销售代表-传统渠道OTCR:现代渠道销售代表WDR:批发拓展代表ADR:客户拓展代表DCR:分销商合约代表DSR:分销商销售代表KSR:大客户销售主任KAM:重点客户经理CDM:渠道拓展经理MDR:市场拓展代表MDE:市场拓展主任MDM:市场拓展经理TMM:通路行销市场经理TDS:区域拓展主任TDM:区域拓展经理LTDM:高级区域拓展经理UM:业务单位经理(大区经理)GM(GeneralManager):总经理GMDR(GeneralManagerDirectReports):总经理直接下属VP(VicePresident):副总裁FVP(FirstVicePresident):第一副总裁AVP(AssistantVicePresident):副总裁助理CEO(ChiefERecutiveOfficer):首席执行官COO(ChiefOperationsOfficer):首席运营官CFO(ChiefFinancialOfficer):首席财务官CIO(ChiefInformationOfficer):首席信息官Director:总监HRD(HumanResourceDirector):人力资源总监OD(OperationsDirector):运营总监MD(MarketingDirector):市场总监OM(OperationsManager):运营经理PM(ProductManager):产品经理BM(BrandManager):品牌经理4P(Product、Price、Place、Promotion):4P营销理论(产品、价格、渠道、促销)4C(Customer、Cost、Convenience、Communication):4C营销理论(顾客、成本、便利、沟通)4V(Variation、VersatilitR、Value、Vibration):4V营销理论(差异化、功能化、附加价值、共鸣)SWOT(Strengths、Weaknesses、Opportunities、Threats):SWOT分析法(优势、劣势、机遇、威胁)FABE(Feature、Advantage、Benefit、Evidence):FABE法则(特性、优点、利益、证据)USP(UniqueSellingPropostion):独特销售主张3A(Avalible、Able、Adsire):买得到、买得起、乐得买PDCA(Plan、Do、Check、Action):PDCA循环管理(计划、执行、检查、行动)OEM(OriginalEquipmentManufacturer):原始设备制造商,俗称“贴牌”ODM(OriginalDesignManufacturer):原装设计制造商OBM(OwnBrandManufacturer):自有品牌制造商IPO(InitialPublicOffering):首次公开募股LOGO:商标Slogan:广告语FMCG(FastMovingConsumerGoods):快速消费品DCG(DurableConsumerGoods):耐用消费品。

英文销售术语的中文解释KA、TG、MT、CR-TT、OTCR、SKU、DC、DSD、OEM、POP、4P、4C、SWOT、FAB、USP……究竟是什么意思?许多初入快速消费品行业销售领域的童鞋,碰到上述英文销售术语时,往往一头雾水,不知是啥意思。
现将最常见的150余条英文销售术语整理如下:DA(Distribution & Assortment):分销Location:位置Display:陈列Pricing:价格Inventory:库存Merchandising:助销Promotion:促销KA(Key Account):重点客户GKA(Global Key Account):全球性重点客户NKA(National Key Account):全国性重点客户LKA(Local Key Account):地方性重点客户RKA(Retail Key Account ):零售重点客户SM(ShoppingMall):大型购物消费中心简称销品茂HYM(Hypermarket):巨型超级市场,简称大卖场SPM(Supermarket):超级市场,简称超市S-SPM(Small-Supermarket):小型超市M-SPM(Middle-Supermarket):中型超市L-SPM(Large-Supermarket):大型超市C&C(Cash & Carry):仓储式会员店CVS(Convenience Store):便利店GS(Gas Station):加油站便利店DS(Discount Store):折扣店MT(Modern Trade ):现代渠道TT(Tradiditional Trade):传统渠道OT(Organized Trade):现代特殊渠道OP(On Premise ):餐饮渠道HBR(Hotel,Bar,Restaurant):旅馆、酒吧、餐馆等封闭性通路WHS(Wholesaler):批发商2nd tier Ws:二级批发商DT(Distributor):经销商,分销商2ndDT:二级分销商DIST(Distributor System):专营分销商MW(Managed Wholesalers):管制批发商PW(Passive Wholesalers):传统批发商DSD(Direct Store Delivery):店铺直接配送CSTD(Company Sells Third Party Delivers):我销他送DC(Distribution Center):配送中心TPL(Third Party Logistics):第三方物流CRP(Contiuous Replenishment):持续补货CAO(Computer Assisted Ordering):计算机辅助订货PUR(Purchase):进货OOS(Out of Stock):缺货Inventory day:库存天数SKU(Stock Keeping Uint):最小库存计量单位UPC:通用产品编码Bar Code:条形码Slim(Slim):纤细,苗条(包装)TC:铁罐包装AC:铝罐包装TP(TETRA PAK):利乐无菌包装(俗称纸包装)PET:宝特瓶(俗称胶瓶)POSM(Point of Sale Materials):陈列品GE(Gondola End):端架MIT(Marketing Inpact Team):卖场整合性陈列;堆箱TG(Type Genus ):堆头Island Display:堆头式陈列Floor Display:落地割箱陈列Pallet Display:卡板陈列Strip Display:挂条陈列Sidekick Display:侧挂陈列Checkout Display:收银台陈列Cooler Display:冰柜陈列Secondary Display:二次陈列Cross Display:交叉陈列PG(Promotion Girl):促销员P-T(Part-timer):临时工,特指临促POP(Point Of Purchase):门店广告Price discount:特价On-Pack:绑赠Sampling:试吃Road Show:路演,大型户外促销活动DM(Direct Mail ):商场快讯商品广告;邮报PR(Public Relation):公共关系NP(News Paper):报纸杂志AD(Advertisement):广告GRP(Gross Rating Point):毛评点;总收视点(媒介用语)Loyalty:忠诚度Penetration:渗透率Value Share:市场份额AVE(Average):平均数WTD(Weighted):加权NUM(Numeric):数值PP(Previous Period):上期YA(Year Ago):去年同期VOL(Volume):销售量VAL(Value):销售额VAL-PP(Value PP):上期销售额VAL-YA(Value YA):去年同期销售额YTD(Year To Date ):截至当期的本年累计MTD(Means Month to Date):本月到今天为止SPPD(Sales Per Point of Distribution):每点销售额BTL(Below The Line):线下费用ATL(Above The Line):线上费用ABC(Activity based costing):成本动因核算法(又称:巴雷托分析法)U&A(Usage and Attitude):消费态度和行为(市场调查)FGD(Focus Group Discuss):座谈会(市调一种)Store Check:终端调查,铺市率调查CR:销售代表CR-OP:销售代表-餐饮渠道CR-OT:销售代表-现代特殊渠道CR-MT:销售代表-现代渠道CR-TT:销售代表-传统渠道OTCR:现代渠道销售代表WDR:批发拓展代表ADR:客户拓展代表DCR:分销商合约代表DSR:分销商销售代表KSR:大客户销售主任KAM:重点客户经理CDM:渠道拓展经理MDR:市场拓展代表MDE:市场拓展主任MDM:市场拓展经理TMM:通路行销市场经理TDS:区域拓展主任TDM:区域拓展经理LTDM:高级区域拓展经理UM:业务单位经理(大区经理)GM(General Manager):总经理GMDR(General Manager Direct Reports ):总经理直接下属VP(Vice President):副总裁FVP(First Vice President):第一副总裁AVP(Assistant Vice President):副总裁助理CEO(Chief Executive Officer):首席执行官COO(Chief Operations Officer):首席运营官CFO(Chief Financial Officer):首席财务官CIO(Chief Information Officer):首席信息官Director:总监HRD(Human Resource Director):人力资源总监OD(Operations Director):运营总监MD(Marketing Director):市场总监OM(Operations Manager):运营经理PM (Product Manager):产品经理BM(Brand Manager):品牌经理4P(Product、Price、Place、Promotion):4P营销理论(产品、价格、渠道、促销)4C(Customer、Cost、Convenience、Communication):4C营销理论(顾客、成本、便利、沟通)4V(Variation、Versatility、Value、Vibration):4V营销理论(差异化、功能化、附加价值、共鸣)SWOT(Strengths、Weaknesses、Opportunities、Threats):SWOT分析法(优势、劣势、机遇、威胁)FABE(Feature、Advantage、Benefit、Evidence):FABE法则(特性、优点、利益、证据)USP(Unique Selling Propostion):独特销售主张3A(Avalible、Able、Adsire):买得到、买得起、乐得买PDCA(Plan、Do、Check、Action):PDCA循环管理(计划、执行、检查、行动)OEM(Original Equipment Manufacturer):原始设备制造商,俗称“贴牌”ODM(Original Design Manufacturer):原装设计制造商OBM(Own Brand Manufacturer):自有品牌制造商IPO(Initial Public Offering):首次公开募股LOGO:商标Slogan:广告语FMCG(Fast Moving Consumer Goods):快速消费品DCG(Durable Consumer Goods):耐用消费品。

logistics distribution center location factors:(1) the goods distribution and quantity. This is the distribution center and distribution of the object, such as goods source and the future of distribution, history and current and future forecast and development, etc. Distribution center should as far as possible and producer form in the area and distribution short optimization. The quantity of goods is along with the growth of the size distribution and constant growth. Goods higher growth rate, the more demand distribution center location is reasonable and reducing conveying process unnecessary waste.(2) transportation conditions. The location of logistics distribution center should be close to the transportation hub, and to form the logistics distribution center in the process of a proper nodes. In the conditional, distribution center should be as close to the railway station, port and highway.(3) land conditions. Logistics distribution center covers an area of land in increasingly expensive problem today is more and more important. Is the use of the existing land or land again? Land price? Whether to conform to the requirements of the plan for the government, and so on, in the construction distribution center have considered.(4) commodities flow. Enterprise production of consumer goods as the population shift and change, should according to enterprise's better distribution system positioning. Meanwhile, industrial products market will transfer change, in order to determine the raw materials and semi-finished products of commodities such as change of flow in the location of logistics distribution center should be considered when the flow of the specific conditions of the relevant goods.(5) other factors. Such as labor, transportation and service convenience degree, investment restrictions, etc.How to reduce logistics cost,enhance the adaptive capacity and strain capacity of distribution center is a key research question of agricultural product logistics distribution center.At present,most of the research on logistics cost concentrates off theoretical analysis of direct factors of logistics cost, and solves the problem of over-high logistics Cost mainly by direct channel solution.This research stresses on the view of how to loeate distribution center, analyzes the influence of locating distribution center on logistics cost.and finds one kind of simple and easy location method by carrying on the location analysis of distribution center through computer modeling and the application of Exeel.So the location of agricultural product logisticsdistribution center can be achieved scientifically and reasonably, which will attain the goal of reducing logistics cost, and have a decision.making support function to the logisties facilities and planning of agricultural product.The agricultural product logistics distribution center deals with dozens and even hundreds of clients every day, and transactions are made in high-frequency. If the distribution center is far away from other distribution points,the moving and transporting of materials and the collecting of operational data is inconvenient and costly. costly.The modernization of agricultural product logistics s distribution center is a complex engineering system,not only involves logistics technology, information technology, but also logistics management ideas and its methods,in particular the specifying of strategic location and business model is essential for the constructing of distribution center. How to reduce logistics cost,enhance the adaptive capacity and strain capacity of distribution center is a key research question of agricultural product logistics distribution center. The so—called logistics costs refers to the expenditure summation of manpower, material and financial resources in the moving process of the goods.such as loading and unloading,conveying,transport,storage,circulating,processing,information processing and other segments. In a word。

快消行业专业术语欧阳光明(2021.03.07)(KA、TG、MT、CR-TT、OTCR、SKU、DC、DSD、OEM、POP、4P、4C、SWOT、FAB、USP……究竟是什么意思?许多初入快速消费品、小家电行业销售领域的童鞋,碰到上述英文销售术语时,往往一头雾水,不知是啥意思。
本人现将最常见的150余条英文销售术语整理如下,以飨职场新人:DA(Distribution & Assortment):分销Location:位置Display:陈列Pricing:价格Inventory:库存Merchandising:助销Promotion:促销KA(Key Account):重点客户GKA(Global Key Account):全球性重点客户NKA(National Key Account):全国性重点客户LKA(Local Key Account):地方性重点客户RKA(Retail Key Account ):零售重点客户SM(ShoppingMall):大型购物消费中心简称销品茂HYM(Hypermarket):巨型超级市场,简称大卖场SPM(Supermarket):超级市场,简称超市S-SPM(Small-Supermarket):小型超市M-SPM(Middle-Supermarket):中型超市L-SPM(Large-Supermarket):大型超市C&C(Cash & Carry):仓储式会员店CVS(Convenience Store):便利店GS(Gas Station):加油站便利店DS(Discount Store):折扣店MT(Modern Trade ):现代渠道TT(Tradiditional Trade):传统渠道OT(Organized Trade):现代特殊渠道OP(On Premise ):餐饮渠道HBR(Hotel,Bar,Restaurant):旅馆、酒吧、餐馆等封闭性通路WHS(Wholesaler):批发商2nd tier Ws:二级批发商DT(Distributor):经销商,分销商2ndDT:二级分销商DIST(Distributor System):专营分销商MW(Managed Wholesalers):管制批发商PW(Passive Wholesalers):传统批发商DSD(Direct Store Delivery):店铺直接配送CSTD(Company Sells Third Party Delivers):我销他送DC(Distribution Center):配送中心TPL(Third Party Logistics):第三方物流CRP(Contiuous Replenishment):持续补货CAO(Computer Assisted Ordering):计算机辅助订货PUR(Purchase):进货OOS(Out of Stock):缺货Inventory day:库存天数SKU(Stock Keeping Uint):最小库存计量单位UPC:通用产品编码Bar Code:条形码Slim(Slim):纤细,苗条(包装)TC:铁罐包装AC:铝罐包装TP(TETRA PAK):利乐无菌包装(俗称纸包装) PET:宝特瓶(俗称胶瓶)POSM(Point of Sale Materials):陈列品GE(Gondola End):端架MIT(Marketing Inpact Team):卖场整合性陈列;堆箱TG(Type Genus ):堆头Island Display:堆头式陈列Floor Display:落地割箱陈列Pallet Display:卡板陈列Strip Display:挂条陈列Sidekick Display:侧挂陈列Checkout Display:收银台陈列Cooler Display:冰柜陈列Secondary Display:二次陈列Cross Display:交叉陈列PG(Promotion Girl):促销员P-T(Part-timer):临时工,特指临促POP(Point Of Purchase):门店广告Price discount:特价On-Pack:绑赠Sampling:试吃Road Show:路演,大型户外促销活动DM(Direct Mail ):商场快讯商品广告;邮报PR(Public Relation):公共关系NP(News Paper):报纸杂志AD(Advertisement):广告GRP(Gross Rating Point):毛评点;总收视点(媒介用语)Loyalty:忠诚度Penetration:渗透率Value Share:市场份额AVE(Average):平均数WTD(Weighted):加权NUM(Numeric):数值PP(Previous Period):上期YA(Year Ago):去年同期VOL(Volume):销售量VAL(Value):销售额VAL-PP(Value PP):上期销售额VAL-YA(Value YA):去年同期销售额YTD(Year To Date ):截至当期的本年累计MTD(Means Month to Date):本月到今天为止SPPD(Sales Per Point of Distribution):每点销售额BTL(Below The Line):线下费用ATL(Above The Line):线上费用ABC(Activity based costing):成本动因核算法(又称:巴雷托分析法)U&A(Usage and Attitude):消费态度和行为(市场调查)FGD(Focus Group Discuss):座谈会(市调一种)Store Check:终端调查,铺市率调查CR:销售代表CR-OP:销售代表-餐饮渠道CR-OT:销售代表-现代特殊渠道CR-MT:销售代表-现代渠道CR-TT:销售代表-传统渠道OTCR:现代渠道销售代表WDR:批发拓展代表ADR:客户拓展代表DCR:分销商合约代表DSR:分销商销售代表KSR:大客户销售主任KAM:重点客户经理CDM:渠道拓展经理MDR:市场拓展代表MDE:市场拓展主任MDM:市场拓展经理TMM:通路行销市场经理TDS:区域拓展主任TDM:区域拓展经理LTDM:高级区域拓展经理UM:业务单位经理(大区经理)GM(General Manager):总经理GMDR(General Manager Direct Reports ):总经理直接下属VP(Vice President):副总裁FVP(First Vice President):第一副总裁AVP(Assistant Vice President):副总裁助理CEO(Chief Executive Officer):首席执行官COO(Chief Operations Officer):首席运营官CFO(Chief Financial Officer):首席财务官CIO(Chief Information Officer):首席信息官Director:总监HRD(Human Resource Director):人力资源总监OD(Operations Director):运营总监MD(Marketing Director):市场总监OM(Operations Manager):运营经理PM (Product Manager):产品经理BM(Brand Manager):品牌经理4P(Product、Price、Place、Promotion):4P营销理论(产品、价格、渠道、促销)4C(Customer、Cost、Convenience、Communication):4C营销理论(顾客、成本、便利、沟通)4V(Variation、Versatility、Value、Vibration):4V营销理论(差异化、功能化、附加价值、共鸣)SWOT(Strengths、Weaknesses、Opportunities、Threats):SWOT分析法(优势、劣势、机遇、威胁)FABE(Feature、Advantage、Benefit、Evidence):FABE法则(特性、优点、利益、证据)USP(Unique Selling Propostion):独特销售主张3A(Avalible、Able、Adsire):买得到、买得起、乐得买PDCA(Plan、Do、Check、Action):PDCA循环管理(计划、执行、检查、行动)OEM(Original Equipment Manufacturer):原始设备制造商,俗称“贴牌”ODM(Original Design Manufacturer):原装设计制造商OBM(Own Brand Manufacturer):自有品牌制造商IPO(Initial Public Offering):首次公开募股LOGO:商标Slogan:广告语FMCG(Fast Moving Consumer Goods):快速消费品DCG(Durable Consumer Goods):耐用消费品。
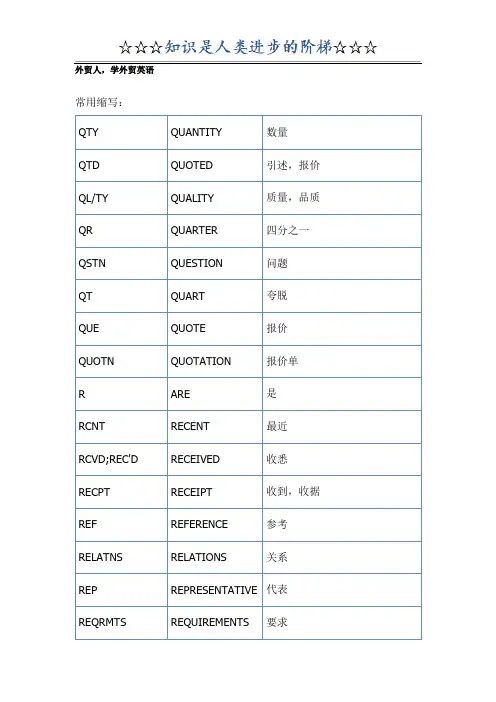
外贸人,学外贸英语常用缩写:QTY QUANTITY 数量QTD QUOTED 引述,报价QL/TY QUALITY 质量,品质QR QUARTER 四分之一QSTN QUESTION 问题QT QUART 夸脱QUE QUOTE 报价QUOTN QUOTATION 报价单R ARE 是RCNT RECENT 最近RCVD;REC'D RECEIVED 收悉RECPT RECEIPT 收到,收据REF REFERENCE 参考RELATNS RELATIONS 关系REP REPRESENTATIVE 代表REQRMTS REQUIREMENTS 要求RGD REGISTERED 已登记,挂号RGDS REGARDS 此致RGRT REGRET 遗憾,抱歉R.I. RE-INSURANCE 再保险REM REAM 令RGDG REGARDING 关于RM REMITTANCE 汇款R.O. REMITTANCEORDER汇款委托书RPT REPEAT 重复RQR REQUIRE 要求R.S.V.P. REPONDEZ S'ILVOUS PLAIT敬候函复R.Y.T. REPLYING TOYOUR TELEGRAM回复贵电S SHILLING 先令S IS 是$;D DOLLAR 美元SB SOMEBODY 某人S.C. SEE COPY 请阅副本SCHDL SCHEDULE 计划S/D SIGHT DRAFT 即期汇票SDY SUNDRIES 杂货SE SECURITIES 抵押品SEC SECRETARY 秘书SEPT SEPTEMBER 九月SGD SIGNED 已签署SHDB SHOULD BE 应该SHLB SHALL BE 将SHIPG SHIPPING 装船SHIPT SHIPMENT 船货SHIPD SHIPPED 已装船SYST SYSTEM 系统S/N SHIPPING NOTE 装船通知SOC SOCIETY 社会,协会S.O.S. SAVE OUR SHIP 求救信号SPEC SPECIFICATION 规格SQ SQUARE 平方SS;S.S. STEAMSHIP 轮船ST STREET 街道S.T. SHORT TON 短吨STG STERLING 英国货币STAND STANDARD 标准STANDG STANDING 站立STH SOMETHING 某事STL STILL 仍然STOR STORAGE 仓库费STR STEAMER 轮船SUBJ SUBJECT 须经,受…支配SUN SUNDAY 星期日SZS SIZE 尺码T TON 吨T.A. TELEGRAPHIC ADDRESS电挂TDY TODAY 今天TEL NR TELEPHONENUMBER电话号码TK TAKE 取TKS THANKS 感谢T.L. TOTAL LOSS 全部损失THFR THEREFORE 因此THUR THURSDAY 星期四THRU THROUGH 通过T.M.O. TELEGRAPHIC MONEY ORDER电汇TOB TO BE 是TOM TOMORROW 明天TONN TONNAGE 吨数T.P.N.D. THEFT,PILFERAGE& NON-DELIVERY盗窃提货不着险T/R TRUST RECEIPT 信托收据TRVL TRAVEL 旅行T/T TELEGRAPHIC TRANSFER电汇U YOU 你ULT ULTIMO 上月UR;YR YOUR 你的URGG URGING 催促UGT URGENT 急迫V WE 我们VIA BY WAY OF 经由VIZ VADELICET,NAMELY即V'L WE'LL 我们将VOL. VOLUME 卷,册,体积,量VOY VOYAGE 航海,航次V.P. VICE PRESIDENT 副社长,副经理,副总裁VR OUR 我们的V.V. VICE VERSA 反之亦然W WITH 在一起W.A. WITH AVERAGE 水渍险WDTH WIDTH 宽度WHF WHARF 港口WK WEEK 周WL WILL 将WLB WILL BE 将W.R. WAR RISK 战争险WT WEIGHT 重量W/OUT WITHOUT 没有WUD WOULD 将W/W WAREHOUSE TO WAREHOUSE仓之仓WZ WITH 在一起X MAS CHRISTMAS 圣诞节X.P. EXPRES PAYE =EXTRA MESSAGEPAID已另函奉上YD YARD 码YR YEAR,YOUR 年,你的£ STERLING,STG 英镑$ DOLLAR,USD 美元# NUMBER,NO.,NR. 号数,编号& AND,N 和360° 360°DEGREES 360度@ AT 单价= IS EQUALTO,EQUALS等于+ PLUS 加- MINUS 减G.S.W. GROSS SHIPPINGWEIGHT装船毛重G.T. GROSS TON 总吨数GV GIVE 给HHD HOGSHEAD 大桶HK HANK;HONG KONG 一卷,一束,香港H.M. HECTOMETRE 百米H.O. HEAD OFFICE 总行,总公司HON HONORABLE 阁下HRS HOURS 小时HS. HAS 有HT HEIGHT 高度HUND HUNDRED 百HV HAVE 有HVB HAVE BEEN 是I/C INWARDCOLLECTION进口托收ID IDEM = THE SAME 同样I.E. IDEST = THAT IT 就是IMP IMPORT 进口IMPTNT IMPORTANT 重要IN INCH 英寸INC INCORPORATED 股份有限公司INFM INFORM 通知INFO;INFMTN INFORMATION 通知,消息INQ INQUIRE 询问INSP INSPECTION 检验INST INSTANT 本月份INSTRCTN INSTRUCTION 指导INSUR INSURANGE 保险INT INTEREST 利息INT'L INTERNATIONAL 国际的INTRSED INTERESTED 感兴趣INV INVOICE 发票INVT INVENTORY 存货清单IOT IN ORDER TO 以便I.O.U I OWE YOU 欠条I/P INSURANCE POLICY 保险单I/R INWARD REMITTANCE汇入ISS ISSUE 发行IT ITEM 项目I.T.O. INTERNATIONALTRADEORGANIZATION国际贸易组织J.A. JOINT ACCOUNT 共同账户JAN JANUARY 一月JT JOINT 共同KG KILOGRAMME 公斤KILO KILOMETRE 公里LB POUND 磅L/A LETTER OF 授权书authorizationLB POUND 英镑L/C LETTER OF CREDIT 信用证L.D.TEL. LONG-DISTANCE TELEPHONE长途电话L/G LETTER OF GUARANTEE保证书LT LETTER 信L.T. LONG TON 长吨LTD;LD LIMITED 有限L/U LETTER OF UNDERTAKING承诺书M METRE/MILE 公尺/英里M/A;M.ACCT. MYACCOUNT 本公司账目MAR MARCH 三月MAX MAXIMUM 最大M/D MONTHS AFTERDATE若干月后付款MDME MADAME 夫人MEMO MEMORANDUM 备忘录MESSRE MESSIEURS 先生(复数)MFD. MANUFACTURED 制作的MFR. MANUFACTURER 厂商M.I. MARINE INSURANCE 海险MIN MINIMUM 最低MK MARK 马克MKT MARKET 市场M.M. MERCHANT MARINE 商船M.O. MONEY ORDER, MAILORDER邮政汇票,邮函订购MON MONDAY 星期一MR MISTER 先生MRS MISTRESS 夫人M.S. MOTORSHIP 轮船M/S MONTHS AFTERSIGHT见票后若干月MSG MESSAGE 电文M/T MAIL TRANSFER 信汇M.T. METRIC TON 公吨MTG MORTGAGE 抵押MTR MATTER 事情MUSTB MUST BE 必须M.V. MOTOR-VESSEL 发动机船N AND 和NAV NAVIGATION 航海N.B. NOTA BENE(N.B.) = TAKE NOTICE注意N.C. NET CAPITAL 净资本额NEGO NEGOTIATE 谈判NET P NET PROCEEDS 纯利,净收NIL NOTHING 无NO NUMBER 号NOV NOVEMBER 十一月N/P NO PAYMENT 拒绝付款NR NUMBER 号N.WT NET WEIGHT 净重NXT NEXT 下一个PCT PER CENT 百分比OBLD OBLIGED 感谢OBJ OBJECT 反对O/C OUTWARDCOLLECTION出口托收OC OUR CABLE 我电OCT OCTOBER 十月OD OVERDRAFT 透支ODR ORDER 订单OFR OFFER 报盘O.K. ALL CORRECT 全对ON A/C ON ACCOUNT 挂账,记账O.P. OPEN POLICY 预定保单OPTN OPTION 选择O/R OUTWARD REMITTANCE汇出OT,OTLX OUR TELEGRAM,OUR TELEX我电,我电传P PAGE 页P/A PROCUREMENT AUTHORIZATION采购授权书PAYT PAYMENT 付款PAT PATENT 专利PC PIECE 个,件PCL PARCEL 小包P.C. PER CENTUM 百分比PD PAID 已付PER ANN PER ANNUM = BYTHE YEAR每年P.I. PROFORMA INVOICE 形式发票P.& I. PRODUCTION AND INDEMNITY意外险PKG PACKAGE 包裹(件)P.& L PROFIT AND LOSS 盈利和亏损PLS PLEASE 请PLSD PLEASED 高兴PLSUR PLEASURE 愉快P.M. POST MERIDIEM = AFTERNOON下午P.M.O. POSTAL MONEYORDER邮政汇票P/O PAYMENT ORDER 支付汇票P.N. PROMISSORY NOTE 期票P.O. POSTOFFICE,POSTALORDER邮局,邮政汇票P.O. PURCHASE ORDER 订单P.O.B. POST OFFICE BOX 邮政信箱P.O.C. PORT OF CALL 停泊港P.O.D. PAY ON DELIVERY 发货付款P.O.R. PAYABLE ONRECEIPT收货付款PP PAGES 页PPD PREPAID 已预付PR PAIR, PRICE 双/对,价格PRBLM PROBLEM 问题PRC PRICE 价格PRDCTN PRODUCTION 生产PREF PREFERRED 优先偿付PREM PREMIUM 保险费PRES PRESIDENT 会长,董事长PREV PREVIOUS 以前的PROB PROBABLY 或许PRDCT PRODUCT 产品PROMOTG PROMOTING 促进PRX PRICE 价格P.S. POST SCRIPT 附言PSTN POSITION 地位PTN PATTERN 模具,花型P.T.O. PLEASE TURN OVER 阅读背面PURCHS PURCHASE 购买PYMT PAYMENT 付款CL CLASS;CLAUSE;CLERK 级,条款,职员CM CENTIMETRE 公分CMDTY COMMODITY 商品收款通知,货款C.N.;C/N CREDIT NOTE清单CNCL CANCEL 撤销CNCLSN CONCLUSION 结论,商定CNSDRTN CONSIDERATION 考虑CNT CONTRACT 合同,契约C.O. CERTIFICATE OF ORIGIN 原产地证明书C/O CASH ORDER;CARE OF 现金订单,转交CO;COY COMPANY 公司,商行C.O.D. CASH ON DELIVERY 付款交货COLLR COLLECTOR 收款员COM,COMM,COMMN COMMISSION 佣金CON.INV. CONSULAR INVOICE 领事发票CONSGT,CONS'T CONSIGNMENT 委托销售,寄售CONT,CONTR CONTRACT 合同,契约CONTG CONTAINING,CONTINUING包括,内容,继续CORP CORPORATION 公司COOP COOPERATION 合作C/P;C.PY. CHARTER PARTY 租船契约C.P.A CERTIFIED PUBLIC ACCOUNTANT会计师CRT CORRECT 正确,修正CR;CRED CREDIT 贷方CSTMRS CUSTOMERS 客户CTGE CARTAGE 搬运费CUB CUBIC 立方CUD COULD 能CURR;CUR;CURT CURRENT 流通的,现行的CURR ACCT CURRENT ACCOUNT往来账目,活期存款C.W.O. CASH WITH ORDER 随订单付现CY CURRENCY 货币D ROMAN500 罗马数字500D/A DOCUMENTS AGAINST ACCEPTANCE承兑交单D.A. DEBIT ADVICE 欠款报单D/A DAYS AFTER ACCEPTANCE承兑后若干日交单DBLE DOUBLE 加倍DBT DEBT,DEBIT 借,借方D/D D.D. DEMAND DRAFT 即期汇票DE.;DEF DEFERRED 延迟DEB DEBENTURE 退税证明书DEBT DEBTOR 借方DEC DECEMBER 十二月DECSN DECISION 决定DESCV DECISIVE 决定性的DEG DEGREE 等级,程度DELY DELIVERY 交货DEM DEMURRAGE 延期费DEP DEPOSIT,DEPUTY 存款,代理DEPT;DPT DEPARTMENT 部,科,处DEVELOPG DEVELOPING 发展D.F;D.FRT DEAD FREIGHT 空舱费DIS THIS 这个DISAPNTD DISAPPOINTED 失望DRT DRAFT 汇票DIA DIAMETER 直径DIFF DIFFERENCE 差额,剩余DIR DIRECTOR 董事DIS;DISC;DISCT DISCOUNT 折扣DIST DISTRICT 地区DIV DIVIDEND 红利,股息D.K;DK DOCK 船坞,码头DLS DOLIARS 元DLT DAY LETTER TELEGRAM 书信电DM DECIMETRE 公寸欠款通知单,借D/N DEBIT NOTE方帐D/O;D.O. DELIVERY ORDER 提货单DO;DTO DITTO = THE SAME 同上DOC DOCUMENT 文件DOZ,DZ DOZEN 打D/P DOCUMENTS AGAINSTPAYMENT付款交单DPTH DEPTH 深度DIS D.S.DYS ST DAYS AFTER SIGHT见票后若干日付款DS;D'S DAYS 若干日D.S.T. DAYLIGHTSAVING TIME 夏令时DTL DETAIL 详细DUP;DUPL DUPLICATE 副本,俩份DURG DURING 在...期间D.W. DEAD WEIGHT 自重,净重EA EACH 每一,各EC ERROR CORRECTION 错误更正E.C.M. CUROPEAN COMMON MARKET 欧洲共同市场ECOM ECONOMY 经济EDIT;ED EDITION 版E.G.EX.G. EXEMPLI GRATIA = FOR 例如EXAMPLEELEC ELECTRICITY 电气E.M.F. ELECTRO-MOTIVE 电动势ENC;ENCL ENCLOSURE 附件ENG ENGLAND,ENGLISH 英国ENTD ENTERED 入账E.& O.E. ERRORS AND OMISSIONSEXCEPTED(账单上所标注的)错漏除外EQ EQUAL,EQUIVALENT 相同,同值ESQ;ESQRE ESQUIRE 先生阁下ET,AL. ET ALII = AND OTHERS 及其他E.T.A. ESTIMATED TIME OF ARRIVAL估计到达的时间ETC. ET CETERA = AND SO FORTH 等等E.T.D. ESTIMATED TIME OFDEPARTURE估计离开的时间EUR EUROPE 欧洲EV EVERY 每一,各EXCEPTN EXCEPTION 除外EXCY EXCELLENCY 阁下EXD EXAMINED 检查过EX DIV EX DIVIDEND 无红利出口,运送,费EXP EXPORT,EXPRESS,EXPENSES用EXS EXPENSES 费用EXT EXTRA 特别,额外F FAHRENHEIT 华氏分损不陪,全损F/A/A;F.A.A. FREE FROM ALL AVERAGE赔偿F.A.Q. FAIR AVERAGE QUALITY 大路货F.A.S. FREE ALONGSIDE SHIP 船边交货价格F.B. FREIGHT BILL 运费单FR FRANC 法郎F.& D FREIGHT AND DEMURRAGE 运费及滞期费F.E. FOR EXAMPLE 例如FEB FEBRUARY 二月F.G.A. FREE FORM GENERAL AVERAGE 共同海损不赔F.I. FOR INSTANCE 例如FIG FIGURE 数字FIN STAT FINANCIAL STATEMENT 财务报表FIN STNDG FINANCIAL STANDING 资产状况FIN.YR. FINANCIAL YEAR 会计年度F.I.T. FREE OF INCOME TAX 免所得税FLWS;FLW FOLLOWS,FOLLOW 如下FM FROM 从支付给,以…为F/O IN FAVOR OF受益人的F.O.B FREE ON BOARD 船上交货价F.O.C. FREE ON CHARGE 免费F.O.I. FREE OF INTEREST 免息F.O.R. FREE ON RAIL 火车上交货价F.O.T. FREE ON TRUCK 卡车上交货价FO.VO FILIO VERSO = TURN THE PAGE 转下页F/P FIRE POLICY 火灾保险单F.P.A. FREE FROM PARTICULAR AVERAGE平安险FR FOR 为了FRI FRIDAY 星期五FRNDLY FREINDLY 友好的FRT FREIGHT 运费FRT.PPD. FREIGHT PREPAID 运费已付FT FOOT,FEET 英尺FT.IN. FEET AND INCHES 英尺与英寸FWD FORWARO 前面,接下页F.X. FOREIGN EXCHANGE 外汇G.A. G/A GENERAL AVERAGE 共同海损GAL;GALL GALLON 加仑GAS GASOLINE 汽油GD GOOD 好GDS GOODS 货物G/N GUARANTEE OF NOTES 承诺保证GM;GRM GRAMME,GRAM 克GR GROSS 罗,毛GR.WT. GROSS WEIGHT 毛重A.AR.;AAR AGAINST ALL RISKS 全险,综合险[/td]ABV ABOVE在...上面[/td]ABT ABOUT 大约[/td]ABBR ABBREVIATION 缩写[/td]ABS,STA ABSTRACT,STATEMENT 摘要[/td]AC ACRE 英亩[/td] ACCT ACCOUNT;ACCOUNTANT账户,会计师A/C;ACCT CURT ACCOUNT CURRENT账户,往来帐ACC ACCEPTANCE;ACCEPTED 接受ACDG;ACDGLY ACCORDING;ACCORDINGLY按照,根据ACPTBLE ACCEPTABLE可接受的ACKGT;ACKMT ACKNOWLEDGEMENT承认,答谢,收贴ACPTC ACCEPTANCE接受,承兑ADJ ADJUST 调节ADV ADVISE 通知AD.;ADVT ADVERTISEMENT 广告A.D. ANNO DOMINI=SINCE THE BIRTH OFCHRIST公元后A/D AFTER DATE 发票后定期付款AD VAL ACCORDING TO THE VALUE按照价格ADMR ADMINISTRATOR财产管理人A.F.B. AIR FREIGHT BILL空运提单AFFT AFFIDAVIT 宣誓书AFT AFTER 之后AFTN AFTERNOON 午后AGT AGENT 代理ALTHO ALTHOUGH 虽然ALWD ALLOWED 允许AMB AMBASSADOR 大使AMER;AMERN AMERICAN 美国,美国的A.M. ANTE MERIDIEM;BEFORE NOON 上午AMP AMPERE 安培AMT AMOUNT 金额复出;回ANS ANSWER;ANSWERED复入某账A/O;ACC/O ACCOUNT OF户A/OR AND/OR 与/或委托购A/P AUTHORITY TO PURCHASE买证应付账A.P. ACCOUNT PAYABLE款APP APPENDIX 附录APPROX APPROXIMATELY 大约APL;APR APRIL 四月全险;应A.R.;A/R ALL RISKS;ACCOUNT RECEIVABLE收帐户ARGE ARRANGE 安排ARR ARRIVAL 抵达ARVD ARRIVED 到达ARRNG ARRANGE 安排ARRT ARRANGEMENT 安排物品,项ART ARTICALE目ASAP AS SOON AS POSSIBLE 尽快销货账A/S;ACC/S ACCOUNT SALES单A/S AFTER SIGHT 见票后联合,协ASS;ASSN ASSOCIATION会各色(物ASS'MT ASSORTMENT品)分配,转ASSIMT ASSIGNMENT让ASST ASSISTANT 助理援助,帮ASST ASSISTANCE助受援助ASSTD ASSISTED的在,至,@ AT,TO,FROM从ATT;ATTN;ATT'N ATTENTION 注意代理人,ATTY ATTORNEY律师AUCT AUCTION 拍卖AUG AUGUST 八月AVE AVENUE 大街AVLBL AVAILABLE 可供的A.W. ALL WOOL 纯毛实际重A/W ACTUAL WEIGHT量AWTG AWAITING 等候BAL BALANCE 余额BANKY BANKRUPTCY破产,倒闭BAR BARREL 桶BRARGN BARGAIN讨价还价B.B BACK-TO-BACK ACCOUNT对开账户B/B BILL BROUGHT买入票据b.b BEARER BOND执票人债券B.C BEFORE CHRIST,BILL FOR COLLECTION 公元前,托收票据BCOZ BECAUSE 因为B.D.;b.d. BILL DISCOUNTED,BANK DRAFT 贴现票据,银行票据b/d. BROUGHT DOWN 接下页BDL BUNDLE 捆,束BDTH BREADTH 宽度B/E;B.EX BILL OF EXCHANGE 汇票BEG BEING 是B/F BROUGHT FORWARD 承前页BF(R) BEFORE 以前BG BAG 袋业务,生BIZ BUSINESS意银行;BK BANK;BOOK书,帐薄银行业BKG BANKING务BKT VASKET 篓,篮BKR BANKER 银行家BL BALE 包BLDG BUILDING建筑物,大厦B/L BILL OF LADING 提单B/N;B,N. BANK NOTE钞票,纸币B.O. BUYER'S OPTION,BRANCH OFFICE 买方选择权,分行B/O BROUGHT OVER 结转BOT;BOTT BOTTLE 瓶,罐B.P.;B/P BILL PURCHASED买入光票BR BRAND 商标,牌B,BRIT BRITISH,BRITAIN英国的,英国B RGDS BEST REGARDS 问候BRKGE BROKERAGE经纪费,佣金B.S.;B/S BALANCE SHEET 资产负债表,借贷对照表B/S BAGS,BALES 袋,包BTN BETWEEN 之间bu.BUSH BSH BUSHEL 蒲式耳C CENTIGRADE 摄氏C CENT 分CAPTND CAPTIONED标题项下的C/S CA;CAS;CS CASES 箱C.A.C. CREDIT ADVICE收款报单C.A.D. CASH AGAINST DOCUMENTS付现交单C.A.F. COST AND FREIGHT 运费在内(成本加)运费CAP CAPTITAL 资本,资金CAPT;CPT CAPTAIN 船长CAR CARAT 克拉运费已CARR.PD CARRIAGE PAID付CASH CASHIER 出纳员商品目CAT CATALOGUE录现金帐C.B. CASH BOOK簿C/B CLEAN BILL 光票立方英CB.FT.CBFT;CFT CUBIC FEET尺付现后C.B.D. CASH BEFORE DELIVERY交货立方厘cu.cm. CUBIC CENTIMETRE米C.C CARBON COPY抄送某人CENT. CENT,CENTRUM 百CERT.;CERTIF CERTIFICATE;CERTIFIED证明书,证明CF.;CFR. CONFER比较,协商C.F.&C. COST,FREIGHT AND COMMISSION 运费佣金在内价(成本,运费加佣金)C.F.&I. COST,FREIGHT AND INSURANCE 运费保险在内价(成本,运费加保险价)CFM CONFIRM 确认CG CENTIGRAMME 厘克C.H. CLEARING HOUSE票据交易所CHEQ CHEQUE 支票CHGES CHARGES费用,税金CHT CHEST箱子,柜子C.I. CERTIFICATE OF INSURANCE 保险单C&I COST AND INSURANCE 保险费在内价(成本,加保险费)CIF COST,INSURANCE,FREIGHT 保险运费在内价(成本,运费加保险费)C.I.F.&C COST,INSURANCE,FREIGHT & 保险运COMMISSION 费佣金在内价C.I.F.C.&I. COST,INSURANCE,FREIGHT,COMMISSON& INTEREST运费保险费佣金利息在内价C.I.F.&E COST,INSURANCE,FREIGHT & EXCHANGE 运费保险汇费在内价英语函电的语气-使语气自然的方法(1) 使用交谈式语言,尽量避免业务术语。

零售及消费品从业人员必懂的英文销售术语许多初入消费品、小家电行业销售领域的童鞋,碰到上述英文销售术语时,往往一头雾水,不知是啥意思。
本人现将最常见的150余条英文销售术语整理如下,以飨职场新人:DA(Distribution & Assortment)分销Location:位置Display:陈列Pricing:价格Inventory:库存Merchandising:助销Promotion:促销KA(Key Account):重点客户GKA(Global Key Account):全球性重点客户NKA(National Key Account):全国性重点客户LKA(Local Key Account):地方性重点客户RKA(Retail Key Account ):零售重点客户SM(ShoppingMall):大型购物消费中心简称销品茂HYM(Hypermarket):巨型超级市场,简称大卖场SPM(Supermarket):超级市场,简称超市S-SPM(Small-Supermarket):小型超市M-SPM(Middle-Supermarket):中型超市L-SPM(Large-Supermarket):大型超市C&C(Cash & Carry):仓储式会员店CVS(Convenience Store):便利店GS(Gas Station):加油站便利店DS(Discount Store):折扣店MT(Modern Trade ):现代渠道TT(Tradiditional Trade):传统渠道OT(Organized Trade):现代特殊渠道OP(On Premise ):餐饮渠道HBR(Hotel,Bar,Restaurant):旅馆、酒吧、餐馆等封闭性通路WHS(Wholesaler):批发商2nd tier Ws:二级批发商DT(Distributor):经销商,分销商2ndDT:二级分销商DIST(Distributor System):专营分销商MW(Managed Wholesalers):管制批发商PW(Passive Wholesalers):传统批发商DSD(Direct Store Delivery):店铺直接配送CSTD(Company Sells Third Party Delivers):我销他送DC(Distribution Center):配送中心:)Third Party Logistics(TPL.第三方物流CRP(Contiuous Replenishment):持续补货CAO(Computer Assisted Ordering):计算机辅助订货PUR(Purchase):进货OOS(Out of Stock):缺货Inventory day:库存天数SKU(Stock Keeping Uint):最小库存计量单位UPC:通用产品编码Bar Code:条形码Slim(Slim):纤细,苗条(包装)TC:铁罐包装AC:铝罐包装TP(TETRA PAK):利乐无菌包装(俗称纸包装)PET:宝特瓶(俗称胶瓶)POSM(Point of Sale Materials):陈列品GE(Gondola End):端架MIT(Marketing Inpact Team):卖场整合性陈列;堆箱TG(Type Genus ):堆头Island Display:堆头式陈列Floor Display:落地割箱陈列Pallet Display:卡板陈列Strip Display:挂条陈列Sidekick Display:侧挂陈列Checkout Display:收银台陈列Cooler Display:冰柜陈列Secondary Display:二次陈列Cross Display:交叉陈列PG(Promotion Girl):促销员P-T(Part-timer):临时工,特指临促POP(Point Of Purchase):门店广告Price discount:特价On-Pack:绑赠Sampling:试吃Road Show:路演,大型户外促销活动DM(Direct Mail ):商场快讯商品广告;邮报PR(Public Relation):公共关系NP(News Paper):报纸杂志AD(Advertisement):广告GRP(Gross Rating Point):毛评点;总收视点(媒介用语)Loyalty:忠诚度Penetration:渗透率Value Share:市场份额AVE(Average):平均数WTD(Weighted):加权:数值)Numeric(NUM.PP(Previous Period):上期YA(Year Ago):去年同期VOL(Volume):销售量VAL(Value):销售额VAL-PP(Value PP):上期销售额VAL-YA(Value YA):去年同期销售额YTD(Year To Date ):截至当期的本年累计MTD(Means Month to Date):本月到今天为止SPPD(Sales Per Point of Distribution):每点销售额BTL(Below The Line):线下费用ATL(Above The Line):线上费用ABC(Activity based costing):成本动因核算法(又称:巴雷托分析法)U&A(Usage and Attitude):消费态度和行为(市场调查)FGD(Focus Group Discuss):座谈会(市调一种)Store Check:终端调查,铺市率调查CR:销售代表CR-OP:销售代表-餐饮渠道CR-OT:销售代表-现代特殊渠道CR-MT:销售代表-现代渠道CR-TT:销售代表-传统渠道OTCR:现代渠道销售代表WDR:批发拓展代表ADR:客户拓展代表DCR:分销商合约代表DSR:分销商销售代表KSR:大客户销售主任KAM:重点客户经理CDM:渠道拓展经理MDR:市场拓展代表MDE:市场拓展主任MDM:市场拓展经理TMM:通路行销市场经理TDS:区域拓展主任TDM:区域拓展经理LTDM:高级区域拓展经理UM:业务单位经理(大区经理)GM(General Manager):总经理GMDR(General Manager Direct Reports ):总经理直接下属VP(Vice President):副总裁FVP(First Vice President):第一副总裁AVP(Assistant Vice President):副总裁助理CEO(Chief Executive Officer):首席执行官COO(Chief Operations Officer):首席运营官:首席财务官)Chief Financial Officer(CFO.CIO(Chief Information Officer):首席信息官Director:总监HRD(Human Resource Director):人力资源总监OD(Operations Director):运营总监MD(Marketing Director):市场总监OM(Operations Manager):运营经理PM (Product Manager):产品经理BM(Brand Manager):品牌经理4P(Product、Price、Place、Promotion):4P营销理论(产品、价格、渠道、促销)4C(Customer、Cost、Convenience、Communication):4C营销理论(顾客、成本、便利、)4V(Variation、Versatility、Value、Vibration):4V营销理论(差异化、功能化、附加价值、共鸣) SWOT(Strengths、Weaknesses、Opportunities、Threats):SWOT分析法(优势、劣势、机遇威胁) FABE(Feature、Advantage、Benefit、Evidence):FABE法则(特性、优点、利益、证据)USP(Unique Selling Propostion):独特销售主张3A(Avalible、Able、Adsire):买得到、买得起、乐得买PDCA(Plan、Do、Check、Action):PDCA循环管理(计划、执行、检查、行动)OEM(Original Equipment Manufacturer):原始设备制造商,俗称“贴牌”ODM(Original Design Manufacturer):原装设计制造商OBM(Own Brand Manufacturer):自有品牌制造商IPO(Initial Public Offering):首次公开募股LOGO:商标Slogan:广告语FMCG(Fast Moving Consumer Goods):快速消费品DCG(Durable Consumer Goods):耐用消费品诠释零售营运专业术语(中英文). 营运管理(OPERATION MANAGEMENT):是指零售商透过一些硬指标及软指标对其门店的各项作业,起到培训、督导、考核、奖惩的一系列经营管理活动。
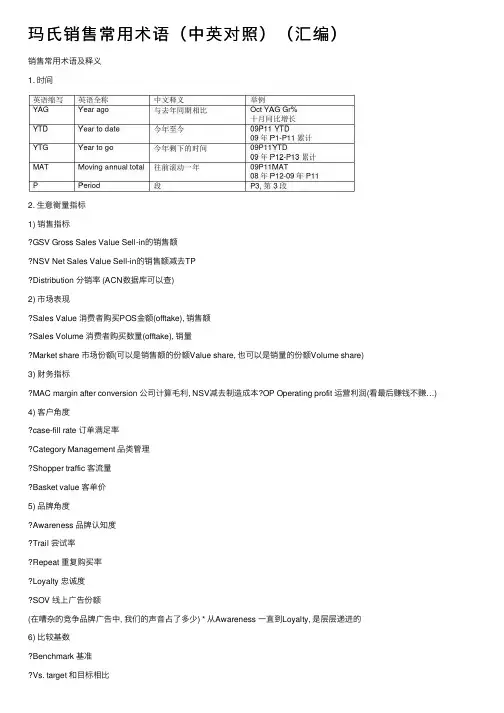
玛⽒销售常⽤术语(中英对照)(汇编)销售常⽤术语及释义1. 时间2. ⽣意衡量指标1) 销售指标GSV Gross Sales Value Sell-in的销售额NSV Net Sales Value Sell-in的销售额减去TPDistribution 分销率 (ACN数据库可以查)2) 市场表现Sales Value 消费者购买POS⾦额(offtake), 销售额Sales Volume 消费者购买数量(offtake), 销量Market share 市场份额(可以是销售额的份额Value share, 也可以是销量的份额Volume share)3) 财务指标MAC margin after conversion 公司计算⽑利, NSV减去制造成本?OP Operating profit 运营利润(看最后赚钱不赚…)4) 客户⾓度case-fill rate 订单满⾜率Category Management 品类管理Shopper traffic 客流量Basket value 客单价5) 品牌⾓度Awareness 品牌认知度Trail 尝试率Repeat 重复购买率Loyalty 忠诚度SOV 线上⼴告份额(在嘈杂的竞争品牌⼴告中, 我们的声⾳占了多少) * 从Awareness ⼀直到Loyalty, 是层层递进的6) ⽐较基数Benchmark 基准Vs. target 和⽬标相⽐Vs LY 和去年同期相⽐Vs competitor 和竞品相⽐3. 渠道1) Mega ⼤型Hyper 超⼤型(收银台Checkout超过20个)Cash & Carry 仓储式(如麦德龙, 收银台Checkout超过20个) ?Large supermarket ⼤超市(收银台Checkout 7-19个) 2) Middle 中型Smaller supermarket (ss) ⼩超(收银台Checkout7-19个)CVS 连锁便利店(⼀个收银台, 20家单店以上) ?Counter store 柜台店OSDO 批发市场Special channel 特渠, 如加油站, ⽕车站…3) IC Impulse channel 冲动渠道NCVS ⾮连锁便利店Small store 夫妻⽼婆店4) B2B 团购4. 销量分类同样是销量, 在公司的衡量指标中有很多不同的名称和定义, 具体如下:Sell-in, Offtake, DTS5. 产品分类1) Brand 分品牌Dove, SNK, Crispy, M&M’s2) Sub-Category 分品类Bulk 散装Sharing 分享装Self-consumption 独享装。

PART IIANSWERS TO END-OF-CHAPTER QUESTIONSCHAPTER 1: AN OVERVIEW OF LOGISTICS1-1. Did it surprise you that logistics has such an important economic impact? Why or why not?The answer to this question likely depends on the student’s prior exposure to logistics. A typical student in an undergraduate, introductory logistics course likely has had limited exposure to and knowledge about logistics and thus might be unaware as to logistics’ economic impact. As such, a student might be pleasantly surprised to learn that logistics is important for a country’s economic growth and development.1-2. Distinguish between possession, form, time, and place utility.Possession utility refers to the value or usefulness that comes from a customer being able to take possession of a product and can be influenced by the relevant payment terms. Form utility refers to a product’s being in a form that (1) can be used by the customer and (2) is of value to the customer. Time utility refers to having products available when they are needed by customers while place utility refers to having products available where they are needed by customers.1-3. How does logistics contribute to time and place utility?Logistics contributes to time utility by recognizing that different products have different sensitivities to time. For example, a three-day-late delivery of bananas likely has more serious consequences than a three-day-late delivery of a box of pencils. As for place utility, logistics facilitates the movement of products from points of lesser value to points of greater value.1-4. How can a particular logistics system be effective but not efficient? Effectiveness can be thought of as “how well a company does what it says it’s going to do;” efficiency focuses on how well (or poorly) company resources are used to achieve what a company promises it can do. There are a multitude of examples that would illustrate an effective, but inefficient, logistics system. For example, some companies routinely use premium and expedited methods of transportation—which increase transportation costs—to meet customer delivery requirements. As such, the logistics system could be considered effective (meeting delivery deadlines) but perhaps not efficient (increased transportation costs).1-5. Explain the significance of the fact that the purpose of logistics is to meet customer requirements.One reason for this significance is that meeting customer requirements means that companies must know—rather than assume—customer needs and wants. This knowledge is facilitated by communication between companies and their customers. Even today, some companies are hesitant to communicate with customers. In addition, meeting customer requirements means that a one-size-fits-all approach to logistics will result in some customers being overserved and others being underserved. As a result, companies should consider a tailored logistics approach, where groups of customers who have similar logistical needs and wants are provided with the appropriate logistical services.1-6. Explain how an understanding of logistics management could be relevant to your favorite charitable organization.There are any number of examples that can be used. The textbook mentions the Food Bank of New York City; from a logistical perspective, the Food Bank of New York City is responsible for collecting, sorting, repacking, and distributing food from its 90,000 square-foot warehouse.1-7. How has a reduction in economic regulation contributed to the increased importance of logistics?Reductions in economic regulation in the United States allowed individual carriers flexibility in pricing and service, and this flexibility was important to logistics for several reasons. First, it provided companies with the capability to implement the tailored logistics approach in the sense that companies could specify different logistics service levels and prices could be adjusted accordingly. Second, the increased pricing flexibility allowed large buyers of transportation services to reduce their transportation costs by leveraging large amounts of freight with a limited number of carriers.1-8. Discuss the logistical implications associated with the increased emphasis on the convenience associated with a family’s shopping experience.This convenience is manifested in various ways to include extended store hours, home delivery of purchased items, and ready-to-eat/ready-to-cook foods. From a logistics perspective, extended store hours force retailers to address issues such as the optimal delivery times for replenishment trucks and when to replenish merchandise. A logistical challenge with home delivery is the coordination of delivery times with the purchaser’s ability to receive the item(s). Finally, ready-to-eat-ready-to-cook foods have different packaging requirements, and food processors continue to experiment with packaging alternatives that will extend the shelf life of ready-to-cook foods.1-9. What are some ways in which technology has impacted logistics management? Technological advances have influenced channel design by allowing companies to offer an alternate distribution channel (or alternate distribution channels) to already existing channels. Technological advances can also improve the productivity of the order picking process, which traditionally involved paper pick tickets. Today, by contrast, order picking can utilize radio frequency devices, voice-directed picking, and robotic picking. Shipment tracking provides another example of how technological advances have impacted logistics management. Global positioning systems can provide real-time location information about a shipment, as well as provide information about a vehic le’s temperature, humidity, and vibrations.1-10. Explain how big-box retailers are logistical trendsetters.The logistics practices of big-box retailers are often viewed as barometers for emerging logistics trends. Big-box retailers have also been trendsetters with respect to environmental and social issues in logistics. As an example, one of Best Buy’s sustainability goals for 2020 is to recycle one billion pounds of consumer goods.1-11. What is the systems approach to problem solving? How is this concept applicable to logistics management?The systems approach to problem solving suggests that a company’s objectives can be realized by recognizing the mutual interdependence of its major functional areas, such as marketing, production, finance, and logistics. As such, decisions made by one functional area can have important implications for the other functional areas. With respect to logistics, the systems approach suggests that one should recognize the mutual interdependence of the various activities that constitute the logistics function. Thus, a transportation decision may impact inventory, warehousing, and packaging, among others.1-12. Distinguish between materials management and physical distribution.Materials management refers to the movement and storage of materials into a firm while physical distribution refers to the storage of finished product and movement to the customer.1-13. Explain what is meant by the total cost approach to logistics.The total cost approach to logistics is built on the premise that all relevant activities in moving and storing products should be considered as a whole (i.e., their total cost) and not individually. Use of the total cost approach requires an understanding of cost trade-offs. In other words, changes to one logistics activity cause some costs to increase and others to decrease. The key to the total cost approach is that all relevant cost items are considered simultaneously when making a decision. The objective is to find the approach with the lowest total cost that supports the organization’s customer service requirements.1-14. Define what is meant by a cost trade-off. Do you believe that this concept is workable? Why or why not?A cost trade-off acknowledges that changing patterns or activities of distribution will result in some costs increasing and other costs decreasing. The net effect, however, should be an overall cost decrease for providing a given level of customer service.The remainder of this question asks for the student’s opinion about the workability of this concept. Although nearly any answer is acceptable, those students who believe that cost trade-offs are unworkable might have difficulty with many of the concepts presented throughout the text.1-15. What are several areas in which finance and logistics might interface?The finance department is often in charge of capital budgeting decisions that would affect logistics, such as materials handling and packaging equipment. Another potential area of finance and logistics interface is with respect to inventory; finance tends to view inventory from a dollar perspective while logistics tends to be more concerned with the number of units of inventory. This dichotomy is highlighted by the concept of obsolescence, which reduces the monetary value of inventory by a certain amount per period of time—even though the actual quantity of inventory may be unchanged.1-16. Discuss the postponement concept as it relates to the production and logistics interface.Postponement refers to the delay of value-added activities such as assembly, production, and packaging until the latest possible time. Some value-added activities, such as case packing and case labeling, that were traditionally performed at a production plant are now performed in warehousing facilities. As a result, warehousing facilities are adding new types of equipment and being configured differently to allow specific value-added activities to take place.1-17. Define what is meant by a landed cost and explain its relevance for pricing decisions.Landed cost refers to the price of a product at its source plus transportation costs to its destination. On the one hand, a selling price that is based on a product’s landed cost allows the seller to offer “free” delivery of the product to prospective customers, because the transportation costs associated with delivery are captured in the landed cost. On the other hand, a selling price that is based on a product’s landed cost could result in a substantial increase in a product’s selling price, and a higher selling price tends to decrease buyer demand for most products.1-18. Discuss several possible interfaces between marketing and logistics in terms of product decisions.One interface involves the marked increase in product offerings; marketers like this increase because it allows for more customer choice, but these additional choices create logistical challenges in terms of identification, storage, and tracking. Another interface concerns the amount of a particular item (SKU) to hold. Marketers prefer to carry higher quantities for particular items because this reduces the likelihood of stockouts; however, from a logistics perspective, higher quantities of inventory necessitate additional storage space and increase inventory carrying costs.Students can also discuss product design and sustainable products.1-19. Briefly discuss the ownership, negotiations, financing, promotion, and logistics channels.The ownership channel covers movement of the title to the goods; the goods themselves might not be physically present or even exist. The negotiations channel is the one in which buy and sell agreements are reached and can include telephone, email, and electronic data interchange, among others. The financing channel handles payment for goods and the company’s credit, while the promotions channel is concerned with promoting a new or an existing product. Finally, the logistics channel handles the physical flow of the product.1-20. Discuss five activities that might be part of a company’s logistics department.The chapter presents, and briefly describes, 12 separate activities that might be part of a company’s logistics department. Any 5 of the 12 activities are acceptable for students to discuss.PART IIICASE SOLUTIONSCASE 1.1 KIDDIELAND AND THE SUPER GYMQuestion 1: List and discuss the advantages and disadvantages of purchasing a two-wheel trailer for each store to use for delivering the Super Gyms.Because the stores are in a number of states, one would have to check the motor vehicle and insurance requirements of each state. An advantage is that deliveries would be under the control of each store. A disadvantage may be labor costs, especially if two workers are needed to make the delivery. Also, once at the site, the store’s employees might be asked to assist in the assembly of the gym.Question 2: List and discuss the advantages and disadvantages of having local trucking companies deliver the Super Gym from the retail stores to the customers.There are probably no disadvantages to using a local trucking company to make the delivery. However, a decision about how to handle the trucking firm’s charges would have to be made.Question 3: List and discuss the advantages and disadvantages of stocking Super Gyms at the distribution centers and then having the truck that makes deliveries from the distribution center to the retail stores also make deliveries of Super Gyms to individual customers.One problem focuses on the size of equipment—large tractor–trailer combinations are not suited to making home deliveries. The actual costs to KiddieLand of using trucks this way might be very high. There might be some savings in inventory costs by stocking the gyms at the distribution center rather than at each retail store.Question 4: List and discuss the advantages and disadvantages of charging customers for home delivery if they are unable to carry home the Super Gym.Perhaps the one advantage to charging for home delivery is that KiddieLand recoups the associated costs. However, because charged home delivery will add to the customer’s total purchase price, there could be a reduction in demand or this could generate customer dissatisfaction.Question 5: Which alternative would you prefer? Why?The student can choose any alternative. However, the text of the case seems to prefer the use of a local trucking company and charging the customer for home delivery.Question 6:Draft a brief statement (catalog copy) to be inserted in the firm’s spring–summer brochure that clearly explains to potential customers the policy that is recommended in Question 5.The brochure is intended for use in all stores, so whatever copy is prepared must be widely applicable. A sentence might read: “The Super Gym comes unassemb led and is packed in three boxes: One weighs ____ pounds and is ____ inches by ____ inches by____ inches; the second weighs ____ pounds and is ____ inches by ____ inches by ____ inches; and the third weighs ____ pounds and is ____ inches by ____ inches by ____ inches. Assembly requires the following tools: ____; ____; ____; and ____.”Question 7: At the first meeting, A.J. asked about SUVs, but there was no further mention of them. How would you follow up on his query?Anyone in the group could answer that SUVs have more carrying capacity than autos and many also have trailer hitches. SUVs are sufficiently popular—particularly in the United States—such that many buyers of the Super Gym equipment would either have a SUV or be able to borrow one.。

零售及消费品从业人员必懂的英文销售术语许多初入消费品、小家电行业销售领域的童鞋,碰到上述英文销售术语时,往往一头雾水,不知是啥意思。
本人现将最常见的150余条英文销售术语整理如下,以飨职场新人:DA(Distribution & Assortment)分销Location:位置Display:陈列Pricing:价格Inventory:库存Merchandising:助销Promotion:促销KA(Key Account):重点客户GKA(Global Key Account):全球性重点客户NKA(National Key Account):全国性重点客户LKA(Local Key Account):地方性重点客户RKA(Retail Key Account ):零售重点客户SM(ShoppingMall):大型购物消费中心简称销品茂HYM(Hypermarket):巨型超级市场,简称大卖场SPM(Supermarket):超级市场,简称超市S-SPM(Small-Supermarket):小型超市M-SPM(Middle-Supermarket):中型超市L-SPM(Large-Supermarket):大型超市C&C(Cash & Carry):仓储式会员店CVS(Convenience Store):便利店GS(Gas Station):加油站便利店DS(Discount Store):折扣店MT(Modern Trade ):现代渠道TT(Tradiditional Trade):传统渠道OT(Organized Trade):现代特殊渠道OP(On Premise ):餐饮渠道HBR(Hotel,Bar,Restaurant):旅馆、酒吧、餐馆等封闭性通路WHS(Wholesaler):批发商2nd tier Ws:二级批发商DT(Distributor):经销商,分销商2ndDT:二级分销商DIST(Distributor System):专营分销商MW(Managed Wholesalers):管制批发商PW(Passive Wholesalers):传统批发商DSD(Direct Store Delivery):店铺直接配送CSTD(Company Sells Third Party Delivers):我销他送DC(Distribution Center):配送中心TPL(Third Party Logistics):第三方物流CRP(Contiuous Replenishment):持续补货CAO(Computer Assisted Ordering):计算机辅助订货PUR(Purchase):进货OOS(Out of Stock):缺货Inventory day:库存天数SKU(Stock Keeping Uint):最小库存计量单位UPC:通用产品编码Bar Code:条形码Slim(Slim):纤细,苗条(包装)TC:铁罐包装AC:铝罐包装TP(TETRA PAK):利乐无菌包装(俗称纸包装)PET:宝特瓶(俗称胶瓶)POSM(Point of Sale Materials):陈列品GE(Gondola End):端架MIT(Marketing Inpact Team):卖场整合性陈列;堆箱TG(Type Genus ):堆头Island Display:堆头式陈列Floor Display:落地割箱陈列Pallet Display:卡板陈列Strip Display:挂条陈列Sidekick Display:侧挂陈列Checkout Display:收银台陈列Cooler Display:冰柜陈列Secondary Display:二次陈列Cross Display:交叉陈列PG(Promotion Girl):促销员P-T(Part-timer):临时工,特指临促POP(Point Of Purchase):门店广告Price discount:特价On-Pack:绑赠Sampling:试吃Road Show:路演,大型户外促销活动DM(Direct Mail ):商场快讯商品广告;邮报 PR(Public Relation):公共关系NP(News Paper):报纸杂志AD(Advertisement):广告GRP(Gross Rating Point):毛评点;总收视点(媒介用语)Loyalty:忠诚度Penetration:渗透率Value Share:市场份额AVE(Average):平均数WTD(Weighted):加权NUM(Numeric):数值PP(Previous Period):上期YA(Year Ago):去年同期VOL(Volume):销售量VAL(Value):销售额VAL-PP(Value PP):上期销售额VAL-YA(Value YA):去年同期销售额YTD(Year To Date ):截至当期的本年累计MTD(Means Month to Date):本月到今天为止SPPD(Sales Per Point of Distribution):每点销售额BTL(Below The Line):线下费用ATL(Above The Line):线上费用ABC(Activity based costing):成本动因核算法(又称:巴雷托分析法) U&A(Usage and Attitude):消费态度和行为(市场调查)FGD(Focus Group Discuss):座谈会(市调一种)Store Check:终端调查,铺市率调查CR:销售代表CR-OP:销售代表-餐饮渠道CR-OT:销售代表-现代特殊渠道CR-MT:销售代表-现代渠道CR-TT:销售代表-传统渠道OTCR:现代渠道销售代表WDR:批发拓展代表ADR:客户拓展代表DCR:分销商合约代表DSR:分销商销售代表KSR:大客户销售主任KAM:重点客户经理CDM:渠道拓展经理MDR:市场拓展代表MDE:市场拓展主任MDM:市场拓展经理TMM:通路行销市场经理TDS:区域拓展主任TDM:区域拓展经理LTDM:高级区域拓展经理UM:业务单位经理(大区经理)GM(General Manager):总经理GMDR(General Manager Direct Reports ):总经理直接下属VP(Vice President):副总裁FVP(First Vice President):第一副总裁AVP(Assistant Vice President):副总裁助理CEO(Chief Executive Officer):首席执行官COO(Chief Operations Officer):首席运营官CFO(Chief Financial Officer):首席财务官CIO(Chief Information Officer):首席信息官Director:总监HRD(Human Resource Director):人力资源总监OD(Operations Director):运营总监MD(Marketing Director):市场总监OM(Operations Manager):运营经理PM (Product Manager):产品经理BM(Brand Manager):品牌经理4P(Product、Price、Place、Promotion):4P营销理论(产品、价格、渠道、促销)4C(Customer、Cost、Convenience、Communication):4C营销理论(顾客、成本、便利、) 4V(Variation、Versatility、Value、Vibration):4V营销理论(差异化、功能化、附加价值、共鸣)SWOT(Strengths、Weaknesses、Opportunities、Threats):SWOT分析法(优势、劣势、机遇威胁)FABE(Feature、Advantage、Benefit、Evidence):FABE法则(特性、优点、利益、证据) USP(Unique Selling Propostion):独特销售主张3A(Avalible、Able、Adsire):买得到、买得起、乐得买PDCA(Plan、Do、Check、Action):PDCA循环管理(计划、执行、检查、行动)OEM(Original Equipment Manufacturer):原始设备制造商,俗称“贴牌”ODM(Original Design Manufacturer):原装设计制造商OBM(Own Brand Manufacturer):自有品牌制造商IPO(Initial Public Offering):首次公开募股LOGO:商标Slogan:广告语FMCG(Fast Moving Consumer Goods):快速消费品DCG(Durable Consumer Goods):耐用消费品诠释零售营运专业术语(中英文). 营运管理(OPERATION MANAGEMENT):是指零售商透过一些硬指标及软指标对其门店的各项作业,起到培训、督导、考核、奖惩的一系列经营管理活动。


分货中心的英语In the bustling heart of the city, the distribution center hums with activity. Workers move with purpose, sorting packages with swift precision.The center is a symphony of logistics, where every item has a story to tell. It's a place where efficiency meets necessity, ensuring that goods find their way to theirrightful owners.As the sun sets, the warehouse lights cast a warm glow on the diligent faces of the staff. They are the unsung heroes of commerce, ensuring that the gears of the economy keep turning.The air is filled with the chatter of conveyor belts and the rustle of cardboard. It's a testament to the ceaseless flow of goods that fuel our modern world.Despite the monotony of their tasks, there's a sense of pride in their work. They are the guardians of the supply chain, ensuring that every package reaches its destination.At the end of the day, the center quiets down, but the memories of the day's work linger. It's a place of constant motion, a vital cog in the wheel of progress.The distribution center is more than just a place—it's atestament to human ingenuity and the relentless pursuit of connection in our global village.。
Aabc classificiation abc分类法.A Circular Letter 通告信/通知书Accomplish a Bill of Lading (to) 付单提货acquisition cost ordering cost 定货费Act of God 天灾activity cost pool 作业成本集activity-based costing 作业基准成本法Actual Displacement 实际排水量Ad valorem freight 从价运费Addendum (to a charter party) ( 租船合同)附件Additional for Alteration of Destination 变更卸货港附加费Additional for Optional Destination 选卸港附加费Address commission (Addcomm) 回扣佣金Adjustment 海损理算Advanced B/L 预借提单advanced shipping notice (asn) 预先发货通知A fixed day sailing 定日航班A fortnight sailing 双周班A Friday(Tuesday / Thursday)sailing 周五班agile manufacturing 敏捷制造Air Express 航空快递airline operator/freight forwarder 不营运船舶的多式联运经营人Air Waybill 航空运单Alliance 联盟All in rate 总运费率All purposes (A.P) 全部装卸时间All time saved (a.t.s) 节省的全部时间allocation―――中转?Always afloat 始终保持浮泊American Bureau of Shipping (A.B.S.) 美国船级社A monthly sailing 每月班AMT (Advanced Manufacturing Technology) 先进制造技术Anchorage 锚地Anchorage dues 锚泊费Annual survey 年度检验anticipation inventory 预期储备Anti-dated B/L 倒签提单APICS (American Production and Inventory Control Society,Inc.) 美国生产与库存管理系统Applied Manufacturing Education Series 实用制造管理系列培训教材Apron 码头前沿Arbitration award 仲裁裁决Arbitrator 仲裁员Area differential 地区差价Arrest a ship 扣押船舶AS/RS (automated storage/retrieval system) 自动化仓储系统assemble-to-order 定货组装assembly 组配Article reserves物品储备ATP (available to promise) 可供销售量automatic replenishment (ar) 自动补货系统automatic warehouse 自动化仓库Automatic guided vehicle (AGV)自动导引车automated high-rise warehouse 自动立体仓库Average adjuster 海损理算师Average bond 海损分摊担保书Average guarantee 海损担保书A weekly sailing 周班axle housing桥壳Axle load 轴负荷Bbackflushing 反冲法Backfreight 回程运费back-hauls―――回程空载Back (return) load 回程货backlog 拖欠定单back order 脱期定单, 延期交货成本(back order costs)。
总复习~词汇选择1: 物流技术Logistics activityLogistics operationLogistics modulusLogistics technology2: 物流网络Logistics networkLogistics centerLogistics costLogistics management3: 物流单证Logistics informationLogistics enterpriseLogistics documentLogistics alliance4: 销售物流Supply logisticsProduction logisticsDistribution logisticsReturned logistics5: 企业物流Internal logisticsExternal logisticsMilitary logisticsInternational logistics6:定制物流Environmental logisticsCustomized logisticsVirtual logisticsThird part logistics7:电子数据交换Electronic data interchangeValue-added logistics serviceTangible lossIntangible loss8:运输TransportationConsumptionProductionContainerization9:联合运输Combined transportThrough transportTransfer transportDrop and pull transport10:门到场Door to doorDoor to cyDoor to cfsTerminal to terminal11:库存StorageStackingInventory12: 库存周期Inventory cycle timeCycle stockLead timeOrder cycle time13: 堆码Goods stackStackingHandling/carryingLoading and unloading14:中性包装Sales packagePacking of nominated brand Neutral packingTransport package15:散装化ContainerizationIn bulkCross dockingDistribution16:共同配送DistributionJoint distribution Distribution center Distribution processing17:集货Order pickingGoods collectionAssemblySorting18:出口监管仓库Export supervised warehouse Stereoscopic warehouse Virtual warehouseBoned warehouse19: 冷冻区Chill spaceFreeze spaceReceiving spaceShipping space20:货场Goods shedGoods yardGoods shelfPallet21:叉车Folk lift truckAutomatics guided vehicleConveyor22: 集装箱货运站Railway container yardContainer freight station (CFS) Container terminalInland container depot23:班轮运输International through railway transport International multimodal transportLand bridge transportLiner transport24:船务代理Shipping agencyInternational freight forwarding agentTallyInternational transportation cargo insurance 25:报关Customs declarationCustoms brokerCommodity inspectionInventory control26:物流战略Logistics strategyWarehouse managementWarehouse layoutQuick Response (QR)27: 定期订货方式Economic Order Quantity (FOQ)Fixed Quantity System (FQS)Fixed Interval System (FIS)ABC classification28: 制造资源计划Material Requirement Planning (MRP) Manufacturing Resource Planning (MRP) Enterprise Resource Planning (ERP) Distribution Resource Planning (DRP) 29:物流成本管理Electronic Order System (EOS)Just-in-time logisticsZero-inventory logisticsLogistics cost control30:供应链管理Supply chainSupply Chain Management (SCM) Efficient Customer Response (ECR) Continuous Replenishment Program (CRP) 31: 业务外包Computer Assisted Ordering (CAO) Vendor Managed Inventory (VMI) OutsourcingAccuracy audit32:附加价值Accounting costActual weightAdded valueMore value33: 应用供应商After-sales servicesAggregate shipmentAir pollutionApplication Service Provider (ASP)34:资源回收Asset recoveryAir freightAutomated Storage and Retrieval System (ASRS) Automated warehouse35: 回程BackwardationBack haulAvailable vehicle capacityAutomated Vehicle Identification (AVI)36: 条形码扫描机Bar code labelBar code scannerBi-directional readBay37:批号Base stockBatch numberBear marketBull market38:托运单Belt conveyorBill of Lading (B/L)Bill of Material (BOM)Broken carton39: 散装运送业BrokerBulk carrierBulk containerClosed distribution system40:业务流程重组Business process re-engineering (BPR) Cancellation chargeCargoCargo booking41: 集中采购Cargo inspectionCash discountCentralized dispatchingCentralized procurement42:分销渠道Check inChannel of distributionChief Logistics Officer (CLO)Claim43:联合采购Cost controlConsumer physical distribution Cooperative buyingCubed out44:客户关系管理Customer serviceCraneCustomer Relationship Management (CRM) Deadhead45:分货中心Data warehousingDeclining conveyorDe-consolidation centerDelivery terminal46:全球定位系统Decision support system (DSS)Executive Support System (ESS) Geographic Information System (GIS)Global Positioning System (GPS)47: 需求预测Design for logisticsDepalletizerDemand forecastingEconomic stock48:国内物流Domestic intercity truckingDomestic logisticsDirect distributionDirect store delivery49: 双托盘处理Dispatching areaDouble floor stackingDouble pallets handlingDouble pallet jack50:独家分销DutyElectronic clearanceExclusive distributionExport51: 产品说明标签Fact tagHot tagFactory priceFixed rack52:搬家公司Flatbed trailerFleetFurniture removal carriers53: 集成物流Industrial Engineering (IE)Global logisticsIntegrated logisticsLogistician54:手提扫描仪Bar code scannerHandheld scannerLaser scannerOptical scanner55: 共同配送Integrated Service Digital Network (ISDN) Interchange terminalInventory controlJoint distribution56:标签机FirewallKanban systemMarking machineLabel making machine57: 物流管理Knowledge managementLogistics managementLogistics engineeringCold chain58:市场导向Loose packageMake to orderMarket orientationMarket share59: 多层仓库Material handling equipment MiddlewareMulti-story warehouseDouble floor stacking60:牌照Noise pollutionNumber plateOn seasonPackage61:处理中心Open DataBase Connectivity (ODBC)Order processingOrder Point System (OPS)Process center62:质量控制OverloadQuality controlProcurementQuarantine63:零售Regional distribution center Retail sellingWholesaling64:供应链Safety stockRackSealing machineSupply chain65: 真空包装Tank containerTemporary laborVacuum packagingVoice recognition66:物流作业Logistics operation Logistics technology Logistics activity Logistician68: 社会物流Internal logisticsExternal logistics International logistics Global logistics69:搬运StackingTrimmingHandling/carrying Loading and unloading70:定牌包装Sales packageTransport packagePacking of nominated brand Neutral packing71:直达运输Combined transport Through transport Transfer transportDrop and pull transport72:物流联盟Logistics networkLogistics enterprise Logistics documents Logistics alliance74:无形损耗Tangible lossIntangible lossWaste materialScrap disposal75:保税仓库Stereoscopic warehouse Virtual warehouseBoned warehouseExported supervised warehouse 76:零担运输In bulkFull Container Load (FCL)Less-than Container Load (LCL)Less-than Truck Load (LTL)77: 转运站GatewayDelivery terminalContainer freight station (CFS) Depot78:收货区Chill spaceFreeze spaceHumidity control space Receiving space79: 清关Customs declarationCustoms clearanceCustomer serviceCustoms formality80:企业资源计划MRPMRPⅡERPDPR81:经济订货批量Fixed Quantity System (FQS) Fixed Interval System (FIS)Fixed goods stackEconomic Order Quantity (EOQ) 83:运费、保险费付至目的地DESCIFCIPDDU84: 货交承运人FCADAFDESCFR85: 欧盟机械产品安全标志ASCEULCSA86:销售确认书S/CS/OPOSSCM87:进货清点Check inCheck outCargo inspection Quarantine88: 物品用料清单BOMB/LD/OHAWB90:售后服务Customer serviceAfter-sales service Parts serviceAfter market service 91: 物流模数Logistics mode Logistics movement Logistics modulus Logistics motion93:回收物流Waste material logistics Returned logistics Recycle logistics Recycling96:虚拟物流Information logistics Virtual logisticsImage logisticsNon-material logistics 97: 集装运输Container transport Containerized transport Combined transport Condition transport98:经常库存Current inventoryCycle stockCycle inventory Regular stock100:自动化仓库Automatic warehouse Automated warehouse Automation warehouse Auto warehouse101: 输送机BeltBelt machine ConveyorTransport belt machine 102:集装箱码头Container yardContainer placeContainer pierContainer terminal103:集装箱货运站Container cargo stationContainer goods stationContainer freight stationContainer station104:国际货运代理International transport agency International agentInternational freight forwarding agent International tally105:决策支持系统Decision support systemDecision supply systemDecision supply management Executive support system106:防火墙Wall to stop fireElectronic wall to stop fireComputer protection systemFirewall107: 联运站Interchange terminalCombined terminalThrough transport terminal Interchange station109:起重机Fork liftCraneLift machineLift weight machine110:零库存技术Zero inventoryZero-inventory logisticsZero-inventory technologyZero-inventory control111: 分拣SeparatingSeparating processSortSorting112:装卸Load and unloadLoading and unloadingPut on and offMove in and out114:自动数据采集ADC automatic data collection115: 自动化存取系统ASRS116: 顾客、竞争、变化3C117: 一般原产地证书CAO certificate of origin118: 完税后交货价DDP119: 目的港船上交货价DES delivery EX ship120:站场收据D/R dock receipt121:整箱FCL full container load122:文件传输协议FTP file transfer protocol123:全球运输网GTN global transport net124: 因特网内容提供商ICP internet content provider125:零担运输LTL less-than truck load126: 多式联运单据MTD multimodal transport document127: 便携式数据终端设备PDT portable data terminal128: 装货单S/O shipping order129:增殖物流服务VAL value added logistics130:海运提单Ocean bill of lading131: 物权凭证Document of titleT h e e n d基本概念术语1.物品article 2.物流logistics 3.物流活动logistics activity 4.物流作业logistics operation 5.物流模数logistics modulus 6.物流技术logistics technology 7.物流成本logistics cost 8.物流管理logistics management 9.物流中心logistics center 10.物流网络logistics network 11.物流信息logistics information 12.物流企业logistics enterprise 13.物流单证logistics documents 14.物流联盟logistics alliance 15.供应物流supply logistics 16.生产物流production logistics 17.销售物流distribution logistics 18.回收物流returned logistics 19.废弃物物流waste material logistics 20.绿色物流environmental logistics 21.企业物流internal logistics 22.社会物流external logistics 23.军事物流military logistics 24.国际物流international logistics 25.第三方物流third-part logistics (TPL) 26.定制物流customized logistics 27.虚拟物流virtual logistics 28.增值物流服务value-added logistics service 29.供应链supply chain 30.条码bar code 31.电子数据交换electronic data interchange (EDI) 32.有形消耗tangible loss 33.无形消耗intangible loss物流作业术语1.运输transportation 2.联合运输combined transport 3.直达运输through transport 4.中转运输transfer transport 5.甩挂运输drop and pull transport 6.集装运输containerized transport 7.集装箱运输container transport 8.门到门door-to-door 9.整箱货full container load (FCL) 10.拼箱货less than container load (LCL 11.储存storing 12.保管storage 13.物品储存article reserves 14.库存inventory 15.经常库存cycle stock 16.安全库存safety stick 17.库存周期inventory cycle time 18.前置期(或提前期)lead time 19.订货处理周期order cycle time 20.货垛goods stack 21.堆码stacking 22.搬运handing/carrying 23.装卸loading and unloading 24.单元装卸unit loading and unloading 25.包装package/packaging 26.销售包装sales package 27.定牌包装packing of nominated brand 28.中性包装neutral packing 29.运输包装transport package 30.托盘包装palletizing 31.集装化containerization 32.散装化containerization 33.直接换装cross docking 34.配送distribution 35.共同配送joint distribution 36.配送中心distribution center 37.分拣sorting 38.拣选order picking 39.集货goods collection 40.组配assembly 41.流通加工distribution processing 42.冷链cold chain 43.检验inspection物流技术装备及设施术语1.仓库 warehouse 2.库房 storehouse 3.自动化仓库 automatic warehouse 4. 4立体仓库 stereoscopic warehouse 5.虚拟仓库 virtual warehouse 6.保税仓库 boned warehouse 7.出口监管仓库 export supervised warehouse 8.海关监管货物 cargo under customer’s supervision 9.冷藏区 chill space 10.冷冻区 freeze space 11.控湿储存区 humidity controlled space 12.温度可控区 temperature controlled space 13.收货区 receiving space 14.发货区 shipping space 15.料棚 goods shed 16.货场 goods yard 17.货架 goods shelf 18.托盘 pallet 19.叉车 fork lift truck 20.输送机 conveyor 21.自动导引车 automatic guided vehicle (AGV) 22.箱式车 box car 23.集装箱 container 24.换算箱 twenty-feet equivalent unit (TEU) 25.特种货物集装箱 specific cargo container 26.全集装箱船 full container ship 27.铁路集装箱场 railway container yard 28.公路集装箱中转站 inland container depot 29.集装箱货运站 container freight station (CFS) 30.集装箱码头 container terminal 31.国际铁路联运 international through railway transport 32.国际多式联运 international multimodal transport 33.大陆桥运输 land bridge transport 34.班轮运输 liner transport 35.租船运输 shipping by chartering 36.船务代理 shipping agency 37.国际货运代理 international freight forwarding agent 38.理货 tally 39.国际货物运输保险 international transportation cargo insurance 40.报关 customs declaration 41.报关行 customs broker 42.进出口商品检验 commodity inspection物流管理术语1.物流战略 logistics strategy 2.物流战略管理 logistics strategy management 3.仓库管理 warehouse management 4.仓库布局 warehouse layout 5.库存控制 inventory control 6.经济订货批量 economic order quantity (EOQ) 7.定量订货方式 fixed-quantity system (FQS) 8.定期订货方式 fixed-quantity system (FIS) 9. ABC分类管理 ABC classification 10.电子订货系统 Electronic order system (EOS) 11.准时制 just in time (JIT) 12.准时制物流 just-in-time logistics 13.零库存技术 zero-inventory logistics 14.物流成本管理 logistics cost control 15.物料需要计划 material requirements planning (MRP) 16.制造资源计划 manufacturing resource planning (MRP II) 17.配送需要计划 distribution requirements planning (DRP) 18.配送资源计划 distribution resource planning (DRP II) 19.物流资源计划 logistics resource planning (LRP) 20.企业资源计划 enterprise resource planning (ERP) 21.供应链管理 supply chain management (SCM) 22.快速反映 Quick response (QR) 23.有效客户反映 efficient customer response(ECR) 24.连续库存补充计划 continuous replenishment program (CRP) 25.计算机付诸订货系统 computer assisted ordering (CAO) 26.供应商管理库存 vendor managed inventory (VMI) 27.业务外包 outsourcing。
distribution 物流实务英语Distribution refers to the process of delivering goods from the manufacturer or producer to the end user or consumer. It is a critical component of the supply chain and involves multiple activities, such as warehousing, transportation, and inventory management.In distribution, goods are stored in warehouses or distribution centers before being transported to their final destination. These facilities ensure that products are available when needed and can be delivered in a timely manner. Inventory management is also important in distribution, as it involves tracking and controlling the flow of goods to avoid overstocking or stockouts.Transportation is a key aspect of distribution, as it involves moving goods from one location to another. This can include utilizing various modes of transport, such as trucks, trains, ships, and airplanes, depending on the distance and urgency of delivery. Efficient transportation logistics are crucial to ensure that products are delivered on time and in good condition.In addition to physical logistics, distribution also involves managing information flow. This includes tracking and tracing shipments, providing real-time updates to customers, and coordinating with different stakeholders in the supply chain, such as manufacturers, retailers, and logistics providers.Overall, distribution plays a crucial role in ensuring that goods are delivered efficiently and effectively to the end user. It requirescareful planning, coordination, and execution to meet customer demands and enhance customer satisfaction.。
Accumulation/distribution(累积/派发指标)
累积/派发指标(Accumulation/distribution)简称A/D,是由Marc . Chaikin提出的,它的指标图和折线图是一样的,都是用曲线来表示的,如图下所示:
A/D指标是因价格和成交量的变化而变化的,它把价格和成交量联系起来,成交量在价格的变化中充当重要的权衡系数,系数越高(成交量越大),价格的变化就越能被这个指标所体现出来。
A/D指标与价格的背离走势预示着价格变化即将来临,价格将会依指标的走势变化,例如:市场成交量高,就会有很多人买入,价格就会变高,反之,市场成交量低,价格就会变低,
A/D指标的判断方式为:
若A/D指标下降,而价格则上升时,为卖出信号
若A/D指标上升,而价格则下降时,为买进信号
如图所示:
计算方式如下:
当前A/D=〔(当前收盘价-当前最低价)-(当前最高价-当前收盘价)〕×当前成交量/(当前最高价-当前最低价) + 前一个A/D值。
快消行业专业术语时间:2021.03.07 创作:欧阳德(KA、TG、MT、CR-TT、OTCR、SKU、DC、DSD、OEM、POP、4P、4C、SWOT、FAB、USP……究竟是什么意思?许多初入快速消费品、小家电行业销售领域的童鞋,碰到上述英文销售术语时,往往一头雾水,不知是啥意思。
本人现将最常见的150余条英文销售术语整理如下,以飨职场新人:DA(Distribution & Assortment):分销Location:位置Display:陈列Pricing:价格Inventory:库存Merchandising:助销Promotion:促销KA(Key Account):重点客户GKA(Global Key Account):全球性重点客户NKA(National Key Account):全国性重点客户LKA(Local Key Account):地方性重点客户RKA(Retail Key Account ):零售重点客户SM(ShoppingMall):大型购物消费中心简称销品茂HYM(Hypermarket):巨型超级市场,简称大卖场SPM(Supermarket):超级市场,简称超市S-SPM(Small-Supermarket):小型超市M-SPM(Middle-Supermarket):中型超市L-SPM(Large-Supermarket):大型超市C&C(Cash & Carry):仓储式会员店CVS(Convenience Store):便利店GS(Gas Station):加油站便利店DS(Discount Store):折扣店MT(Modern Trade ):现代渠道TT(Tradiditional Trade):传统渠道OT(Organized Trade):现代特殊渠道OP(On Premise ):餐饮渠道HBR(Hotel,Bar,Restaurant):旅馆、酒吧、餐馆等封闭性通路WHS(Wholesaler):批发商2nd tier Ws:二级批发商DT(Distributor):经销商,分销商2ndDT:二级分销商DIST(Distributor System):专营分销商MW(Managed Wholesalers):管制批发商PW(Passive Wholesalers):传统批发商DSD(Direct Store Delivery):店铺直接配送CSTD(Company Sells Third Party Delivers):我销他送DC(Distribution Center):配送中心TPL(Third Party Logistics):第三方物流CRP(Contiuous Replenishment):持续补货CAO(Computer Assisted Ordering):计算机辅助订货PUR(Purchase):进货OOS(Out of Stock):缺货Inventory day:库存天数SKU(Stock Keeping Uint):最小库存计量单位UPC:通用产品编码Bar Code:条形码Slim(Slim):纤细,苗条(包装)TC:铁罐包装AC:铝罐包装TP(TETRA PAK):利乐无菌包装(俗称纸包装)PET:宝特瓶(俗称胶瓶)POSM(Point of Sale Materials):陈列品GE(Gondola End):端架MIT(Marketing Inpact Team):卖场整合性陈列;堆箱TG(Type Genus ):堆头Island Display:堆头式陈列Floor Display:落地割箱陈列Pallet Display:卡板陈列Strip Display:挂条陈列Sidekick Display:侧挂陈列Checkout Display:收银台陈列Cooler Display:冰柜陈列Secondary Display:二次陈列Cross Display:交叉陈列PG(Promotion Girl):促销员P-T(Part-timer):临时工,特指临促POP(Point Of Purchase):门店广告Price discount:特价On-Pack:绑赠Sampling:试吃Road Show:路演,大型户外促销活动DM(Direct Mail ):商场快讯商品广告;邮报PR(Public Relation):公共关系NP(News Paper):报纸杂志AD(Advertisement):广告GRP(Gross Rating Point):毛评点;总收视点(媒介用语)Loyalty:忠诚度Penetration:渗透率Value Share:市场份额AVE(Average):平均数WTD(Weighted):加权NUM(Numeric):数值PP(Previous Period):上期YA(Year Ago):去年同期VOL(Volume):销售量VAL(Value):销售额VAL-PP(Value PP):上期销售额VAL-YA(Value YA):去年同期销售额YTD(Year To Date ):截至当期的本年累计MTD(Means Month to Date):本月到今天为止SPPD(Sales Per Point of Distribution):每点销售额BTL(Below The Line):线下费用ATL(Above The Line):线上费用ABC(Activity based costing):成本动因核算法(又称:巴雷托分析法)U&A(Usage and Attitude):消费态度和行为(市场调查)FGD(Focus Group Discuss):座谈会(市调一种)Store Check:终端调查,铺市率调查CR:销售代表CR-OP:销售代表-餐饮渠道CR-OT:销售代表-现代特殊渠道CR-MT:销售代表-现代渠道CR-TT:销售代表-传统渠道OTCR:现代渠道销售代表WDR:批发拓展代表ADR:客户拓展代表DCR:分销商合约代表DSR:分销商销售代表KSR:大客户销售主任KAM:重点客户经理CDM:渠道拓展经理MDR:市场拓展代表MDE:市场拓展主任MDM:市场拓展经理TMM:通路行销市场经理TDS:区域拓展主任TDM:区域拓展经理LTDM:高级区域拓展经理UM:业务单位经理(大区经理)GM(General Manager):总经理GMDR(General Manager Direct Reports ):总经理直接下属VP(Vice President):副总裁FVP(First Vice President):第一副总裁AVP(Assistant Vice President):副总裁助理CEO(Chief Executive Officer):首席执行官COO(Chief Operations Officer):首席运营官CFO(Chief Financial Officer):首席财务官CIO(Chief Information Officer):首席信息官Director:总监HRD(Human Resource Director):人力资源总监OD(Operations Director):运营总监MD(Marketing Director):市场总监OM(Operations Manager):运营经理PM (Product Manager):产品经理BM(Brand Manager):品牌经理4P(Product、Price、Place、Promotion):4P营销理论(产品、价格、渠道、促销)4C(Customer、Cost、Convenience、Communication):4C营销理论(顾客、成本、便利、沟通)4V(Variation、Versatility、Value、Vibration):4V营销理论(差异化、功能化、附加价值、共鸣)SWOT(Strengths、Weaknesses、Opportunities、Threats):SWOT分析法(优势、劣势、机遇、威胁)FABE(Feature、Advantage、Benefit、Evidence):FABE法则(特性、优点、利益、证据) USP(Unique Selling Propostion):独特销售主张3A(Avalible、Able、Adsire):买得到、买得起、乐得买PDCA(Plan、Do、Check、Action):PDCA 循环管理(计划、执行、检查、行动)OEM(Original Equipment Manufacturer):原始设备制造商,俗称“贴牌”ODM(Original Design Manufacturer):原装设计制造商OBM(Own Brand Manufacturer):自有品牌制造商IPO(Initial Public Offering):首次公开募股LOGO:商标Slogan:广告语FMCG(Fast Moving Consumer Goods):快速消费品DCG(Durable Consumer Goods):耐用消费品。
零售及消费品从业人员必懂的英文销售术语许多初入消费品、小家电行业销售领域的童鞋,碰到上述英文销售术语时,往往一头雾水,不知是啥意思。
本人现将最常见的150余条英文销售术语整理如下,以飨职场新人:DA(Distribution & Assortment)分销Location:位置Display:陈列Pricing:价格Inventory:库存Merchandising:助销Promotion:促销KA(Key Account):重点客户GKA(Global Key Account):全球性重点客户NKA(National Key Account):全国性重点客户LKA(Local Key Account):地方性重点客户RKA(Retail Key Account ):零售重点客户SM(ShoppingMall):大型购物消费中心简称销品茂HYM(Hypermarket):巨型超级市场,简称大卖场SPM(Supermarket):超级市场,简称超市S-SPM(Small-Supermarket):小型超市M-SPM(Middle-Supermarket):中型超市L-SPM(Large-Supermarket):大型超市C&C(Cash & Carry):仓储式会员店CVS(Convenience Store):便利店GS(Gas Station):加油站便利店DS(Discount Store):折扣店MT(Modern Trade ):现代渠道TT(Tradiditional Trade):传统渠道OT(Organized Trade):现代特殊渠道OP(On Premise ):餐饮渠道HBR(Hotel,Bar,Restaurant):旅馆、酒吧、餐馆等封闭性通路 WHS(Wholesaler):批发商2nd tier Ws:二级批发商DT(Distributor):经销商,分销商2ndDT:二级分销商DIST(Distributor System):专营分销商MW(Managed Wholesalers):管制批发商PW(Passive Wholesalers):传统批发商DSD(Direct Store Delivery):店铺直接配送CSTD(Company Sells Third Party Delivers):我销他送DC(Distribution Center):配送中心TPL(Third Party Logistics):第三方物流CRP(Contiuous Replenishment):持续补货CAO(Computer Assisted Ordering):计算机辅助订货PUR(Purchase):进货OOS(Out of Stock):缺货Inventory day:库存天数SKU(Stock Keeping Uint):最小库存计量单位UPC:通用产品编码Bar Code:条形码Slim(Slim):纤细,苗条(包装)TC:铁罐包装AC:铝罐包装TP(TETRA PAK):利乐无菌包装(俗称纸包装)PET:宝特瓶(俗称胶瓶)POSM(Point of Sale Materials):陈列品GE(Gondola End):端架MIT(Marketing Inpact Team):卖场整合性陈列;堆箱TG(Type Genus ):堆头Island Display:堆头式陈列Floor Display:落地割箱陈列Pallet Display:卡板陈列Strip Display:挂条陈列Sidekick Display:侧挂陈列Checkout Display:收银台陈列Cooler Display:冰柜陈列Secondary Display:二次陈列Cross Display:交叉陈列PG(Promotion Girl):促销员P-T(Part-timer):临时工,特指临促POP(Point Of Purchase):门店广告Price discount:特价On-Pack:绑赠Sampling:试吃Road Show:路演,大型户外促销活动DM(Direct Mail ):商场快讯商品广告;邮报 PR(Public Relation):公共关系NP(News Paper):报纸杂志AD(Advertisement):广告GRP(Gross Rating Point):毛评点;总收视点(媒介用语)Loyalty:忠诚度Penetration:渗透率Value Share:市场份额AVE(Average):平均数WTD(Weighted):加权NUM(Numeric):数值PP(Previous Period):上期YA(Year Ago):去年同期VOL(Volume):销售量VAL(Value):销售额VAL-PP(Value PP):上期销售额VAL-YA(Value YA):去年同期销售额YTD(Year To Date ):截至当期的本年累计MTD(Means Month to Date):本月到今天为止SPPD(Sales Per Point of Distribution):每点销售额BTL(Below The Line):线下费用ATL(Above The Line):线上费用ABC(Activity based costing):成本动因核算法(又称:巴雷托分析法) U&A(Usage and Attitude):消费态度和行为(市场调查)FGD(Focus Group Discuss):座谈会(市调一种)Store Check:终端调查,铺市率调查CR:销售代表CR-OP:销售代表-餐饮渠道CR-OT:销售代表-现代特殊渠道CR-MT:销售代表-现代渠道CR-TT:销售代表-传统渠道OTCR:现代渠道销售代表WDR:批发拓展代表ADR:客户拓展代表DCR:分销商合约代表DSR:分销商销售代表KSR:大客户销售主任KAM:重点客户经理CDM:渠道拓展经理MDR:市场拓展代表MDE:市场拓展主任MDM:市场拓展经理TMM:通路行销市场经理TDS:区域拓展主任TDM:区域拓展经理LTDM:高级区域拓展经理UM:业务单位经理(大区经理)GM(General Manager):总经理GMDR(General Manager Direct Reports ):总经理直接下属VP(Vice President):副总裁FVP(First Vice President):第一副总裁AVP(Assistant Vice President):副总裁助理CEO(Chief Executive Officer):首席执行官COO(Chief Operations Officer):首席运营官CFO(Chief Financial Officer):首席财务官CIO(Chief Information Officer):首席信息官Director:总监HRD(Human Resource Director):人力资源总监OD(Operations Director):运营总监MD(Marketing Director):市场总监OM(Operations Manager):运营经理PM (Product Manager):产品经理BM(Brand Manager):品牌经理4P(Product、Price、Place、Promotion):4P营销理论(产品、价格、渠道、促销)4C(Customer、Cost、Convenience、Communication):4C营销理论(顾客、成本、便利、) 4V(Variation、Versatility、Value、Vibration):4V营销理论(差异化、功能化、附加价值、共鸣)SWOT(Strengths、Weaknesses、Opportunities、Threats):SWOT分析法(优势、劣势、机遇威胁)FABE(Feature、Advantage、Benefit、Evidence):FABE法则(特性、优点、利益、证据) USP(Unique Selling Propostion):独特销售主张3A(Avalible、Able、Adsire):买得到、买得起、乐得买PDCA(Plan、Do、Check、Action):PDCA循环管理(计划、执行、检查、行动)OEM(Original Equipment Manufacturer):原始设备制造商,俗称“贴牌”ODM(Original Design Manufacturer):原装设计制造商OBM(Own Brand Manufacturer):自有品牌制造商IPO(Initial Public Offering):首次公开募股LOGO:商标Slogan:广告语FMCG(Fast Moving Consumer Goods):快速消费品DCG(Durable Consumer Goods):耐用消费品诠释零售营运专业术语(中英文). 营运管理(OPERATION MANAGEMENT):是指零售商透过一些硬指标及软指标对其门店的各项作业,起到培训、督导、考核、奖惩的一系列经营管理活动。
Distribution Volume Tracking on Privacy-Enhanced Wireless GridÖzlem UzunerAbstract— In this paper, we discuss a wireless grid in which users are highly mobile, and form ad-hoc and sometimes short-lived connections with other devices. As they roam through networks, the users may choose to employ privacy-enhancing technologies to address their privacy needs and benefit from the computational power of the grid for a variety of tasks, including sharing content.The high rate of mobility of the users on the wireless grid, when combined with privacy-enhancing mechanisms and ad-hoc connections, makes it difficult to conclusively link devices and/or individuals with network activities and to hold them liable for particular downloads. Protecting intellectual property in this scenario requires a solution that can work in absence of knowledge about behavior of particular individuals.Building on previous work, we argue for a solution that ensures proper compensation to content owners without inhibiting use and dissemination of works. Our proposal is based on digital tracking for measuring distribution volume of content and compensation of authors based on this accounting information. The emphasis is on obtaining good estimates of rate of popularity of works, without keeping track of activities of individuals or devices.The contribution of this paper is a revenue protection mechanism, Distribution Volume Tracking, that does not invade the privacy of users in the wireless grid and works even in the presence of privacy-enhancing technologies they may employ.Index Terms— Copyright, intellectual property, wireless grid.——————————?——————————1 I NTRODUCTION1.1 What is the Wireless Grid?computer grid is a collection of distributed resources shared among a group of users. Wireless grids [1] support a diverse set of devices that communicate with each other using a diverse set of protocols. Some of these protocols, like Bluetooth, are subscriptionless, and would allow users to connect to the grid via machines in their proximity. In this setting, the computational capacity of these small devices is no longer a constraint on the activities they can perform because as long as they have access to the grid, these devices can issue requests to the computationally more able devices on the grid and receive the results of their requests.Given these parameters, imagine a scenario where user A wants to download a particular song to his MP3 player. His MP3 player is Bluetooth enabled. It detects and connects to the laptop of user B who is in its proximity. The laptop happens to be on the wireless grid. The request for download is sent from the MP3 player to the laptop. The network that the laptop is on finds the requested song and transfers it to the MP3 player. The MP3 player can now terminate the Bluetooth connection.This scenario highlights couple of important characteristics of the wireless grid and its users. Namely, that:1. Users are highly mobile and their connections to thegrid can be ad-hoc and short -lived.2. There is a wide variety of devices and protocols usedfor communication on the wireless grid.3. Users can use subscription-based as well assubscriptionless services to connect to networks andtracking the behavior of individuals can be verydifficult.In addition, in this paper, we assume that:1. Users can have subscriptions with multiple serviceproviders.2. Service providers have wireless grid infrastructure,which identifies the machines, learns from themabout their computational and bandwidth resourcesas well as their willingness to participate in the grid,and considers this information during resourceallocation.3. Service providers do not share infrastructure.4. Users can move through the networks of serviceproviders to which they subscribe.5. As the users move through the networks, they areidentified, authenticated, and authorizedautomatically by the service providers.6. Service providers participate in the protection ofprivacy and anonymity of their users and thereforeallow them to authenticate with the servers whilemasking their private information, such as MACaddresses, IP address or, location if they choose to do————————————————Ö. Uzuner is a doctoral student in the Engineering Systems Division and a research assistant in the Computer Science and Artificial Intelligence Laboratory at MIT, Cambridge, MA 02139. E-mail: Ozlem @.Manuscript received April 26, 2004.Aso.1.2 Intellectual Property in Wireless GridsThe dynamic, mobile and transient nature of the users of the wireless grid and the ability to share computational resources for ad-hoc activities creates interesting challenges for intellectual property protection on the wireless grid. In addition to the high rate of mobility and the ability of users to form subscriptionless short-lived ad-hoc connections, a range of privacy-enhancing technologies used in mobile networking, such as those that allow users to make anonymous connections [2], enable users to be private, at least to some extent, with r e spect to their personal information. The combination of these characteristics make it difficult to link people and their mobile devices with patterns in network activities.The grid, on the other hand, complicates the digital copyright problem by allowing individuals to use devices of others for their downloads and applications. This implies that the identity of the machine that holds the content may not be relevant to identifying the person responsible for the download. For example, imagine a scenario where a user with a wireless Palm PC wants to download and play a song. While he has the processor cycles and bandwidth, he lacks the disk space for this download. He requests a download to a machine in his proximity, from which he can listen to the song through streaming media. The presence of a downloaded song on a machine does not, therefore, mean that the owner of that machine has downloaded it.The wireless grid puts these two challenges together. In these networks, it is difficult to relate observed network activity to the source and destination of distributed content or to link downloaded works to particular individuals. The question we try to address in this paper is: In an environment where people cannot be uniquely linked to devices or activities, how do we protect intellectual property?In the following sections, we briefly present the digital copyright problem and outline what we want to achieve with a solution to this problem. Next, we review some proposed solutions from the literature, and discuss their shortcomings and strengths in the wireless grid. We continue with a proposal for author compensation through Distribution Volume Tracking (DVT), a form of digital tracking which is based on fingerprints of works. In section three, we discuss how digital tracking can work in the wireless grid, especially in the presence of increasingly more complex privacy-enhancing mechanisms. In section four, we describe the role of the ISPs for distribution volume tracking. We conclude with proposals from literature on payment mechanisms that can work with DVT and a discussion of open questions.The main contributions of this paper include:1. A proposal to use fingerprint-based distributionvolume tracking for revenue protection in thewireless grid and in the presence of privacy-enhancing mechanisms that protect the privacy andidentity of users in a variety of ways,2. Demonstration, with examples, of how DVT can bedeployed in the wireless grid and an analysis of therequired supporting technical and policyinfrastructure for using DVT both as an independentvolume tracker to obtain estimates of popularity ofworks, and as an independent verifier that can beused to double-check the rate of distributionreported by other sources.2 D IGITAL C OPYRIGHT P ROBLEM: A B ATTLE OFW ILLS, A B ATTLE OF I NCENTIVESThe digital copyright problem revolves around two major groups of stakeholders: content owners and content users.Content owner s are threatened by the ease of unauthorized replication and distribution of digital copies of their works and claim that they need strict control over their works, such as through the digital rights management (DRM) systems and supporting legislation, to protect their incentives to produce. The more control they have over their works, the content owners claim, the more willing they will be to share their works with the public. Unfortunately, in addition to protecting the intellectual property of content owners by preventing unauthorized uses, the technological protection mechanisms such as DRMs also limit authorized uses, such as fair use, and invade consumer privacy while doing so [3]. This is against the interests of the second major stakeholder group, namely the content users.In reaction to use of DRMs without regard to erosion of their fair use privileges, the invasion of their privacy and attacks on their anonymity, the content users have been bypassing the DRMs and circulating DRM-free versions of works. As a result, the content owners have been strengthening DRMs. And, both parties are stuck in a futile battle of wills. This battle affects the welfare of the whole society as it affects the wealth of informative and artistic works available to the community.Once DRM-free versions of works have been created, limiting access to intellectual property becomes impossible. Therefore, in the wireless grid where the modes of distribution can be as diverse as the number of available communication protocols, and users can share all kinds of resources including hardware dedicated to storing content, we suggest addressing the digital copyright problem by focusing on revenue protection for content owners, and fair use, privacy and anonymity protection for content users.2.1 Distribution Volume Tracking and AlternativesIn this section, we look at some representative solutions to the digital copyright problem and discuss whether they would be applicable to the wireless grid.DRMs, i.e., technical protection mechanisms that encapsulate works and control their use, and technologies that use encrypted content and trusted computational devices [4] have so far been the solution insisted upon by the content owners. However, these mechanisms prevent some legally authorized uses of works along with unauthorized ones, instigate the users to bypass them, and thus fail to protect revenues. Therefore, we believe they will also fail to address the digital copyright problem in theUZUNER: DISTRIBUTION VOLUME TRACKING ON PRIVACY-ENHANCED WIRELESS GR ID 3wireless grid.Watermarks, i.e., imperceptible identifying information embedded in the works, form the corner stone of another proposed solution. These mechanisms mark each work with a unique identifier so that each digital copy can be uniquely recognized. The unique identifiers can encode any information the content owner likes; including the identity of the content user who purchased the work [5]. This, unfortunately, means that, in case of theft of content from an authorized content user, for example, watermarks end up implicating innocent people for unauthorized distribution of content. For example, imagine cab driver Alice and customer Bob. Alice has a Bluetooth enabled MP3 player. During the cab ride, Bob likes what he hears on the MP3 player, uses his Bluetooth enabled cell phone to download the song and next time he is on the Internet, makes it publicly available. Alice may not even know about the file transfer from her MP3 player. Yet, while Bob is responsible for the unauthorized distribution, Alice is the one implicated by the watermark. Such thefts and inaccurate accusations can occur more frequently as devices capable of ad-hoc connections become more popular. This poses a problem for proper intellectual property protection in environments that empower these devices, such as the wireless grid.One of the revolutionary solutions to the digital copyright problem came from Gerovac and Solomon who proposed replacing copy protection with revenue protection, based on digital tracking that uses headers and descriptors to identify video content [6]. Our solution builds on this proposal. However, instead of using fixed headers, we propose using fingerprints of works based on their unique content and expression [7]. These fingerprints will be generated, using the computational resources of the grid, every time works are transferred within a network.This kind of fingerprint-based digital tracking has several a dvantages. One major advantage is that the fingerprint of a work can be recomputed before every transfer. This makes the fingerprint robust to foul play; and making the fingerprint of a work unrecognizable requires making the work itself unrecognizable by making substantial changes to it. Second advantage is that the fingerprint matches between works do not have to be exact. Therefore, by requiring further examination of works that are similar beyond a threshold, we can capture works that are derived from each other, sometimes without proper attribution.We have so far implemented a prototype digital fingerprinting system that can accurately identify books and their translators [7]. A challenge for full-scale deployment of this system is the performance bottleneck. The grid can address this problem, by delegating the fingerprinting task to computationally more powerful machines, so that works can be fingerprinted for their identity during transfer.We intend to use our digital fingerprinting mechanisms for tracking the distribution volume of works, without tracking information about individual user behavior. We argue that for proper compensation of the content owners, all we need is a good estimate of the popularity of works as determined by the number of downloads. In the non-digital world, this is equivalent to the number of copies distributed/sold of hard copy of a work.The rate of distribution/popularity of works can help proper compensation of content owners in several ways. For example, the rate of popularity of works can be used to guide the negotiations between content owners and licensees over the terms of compulsory licenses and extended compulsory licenses covering digital downloads [8]. Alternatively, agencies such as ASCAP, that sell compulsory licenses on behalf of content owners, can use the popularity information when compensating artists. In short, Distribution Volume Tracking (DVT) using digital fingerprints:1. Can Provide a robust way of accounting forpopularity of works and enables the content ownersto be compensated adequately,2. Can Alleviate the privacy, anonymity and fair useconcerns of users, does not unjustly link users tounauthorized behavior, minimizing the incentives ofthe content users to bypass it,3. And, is not affected by the privacy-enhancingmechanisms that can be employed by users.3 D ISTRIBUTION V OLUME T RACKING IN P RESENCE OFP RIVACY-ENHANCING M ECHANISMS IN THE W IRELESSG RIDDVT is a promising solution to the digital copyright problem that does not track individual user behavior or try to link users with network activities. This nature of DVT addresses the characteristics and needs of the privacy-enhanced networks including the wireless grid for intellectual property protection.In this section, we show how DVT can be used in the wireless grid, in absence of encryption by users, by analyzing the following scenarios:1. A peer-to-peer (P2P) network on the wireless gridwith no dynamic rerouting of transfers.2. A wireless grid which has to dynamically reroutetransfers to handle the high rate of mobility of itsusers and a P2P network on this grid in which theP2P software deliberately reroutes transfers througha random number of nodes or generates phonydownload requests, to disguise the identity of therecipient and the identity of the work requested In both of these scenarios, we assume that the wireless grid has a resource allocator that knows the machines that are present on the wireless grid at any time and can efficiently control the allocation of resources.The resource allocator handles the fingerprinting task just like any other computationally intensive task; once it receives a request to fingerprint a work, it delegates this task the computationally powerful machines available on the grid.3.1 Tracking in Peer-to-Peer Networks in Wireless GridThe file transfers on the wireless grid are likely to be P2P. In other words, transfer requests will be between4 INTERNET COMPUTING, I C S I-0070-1203nodes A and B, each of which are end-users. Tracking distribution volume in these networks can be done at the ISPs servers. ISP can do this by issuing a fingerprinting request to the resource alloctor and thus keeping track of the distribution volume as works go through the servers. There are two problems with this approach to DVT. One problem is that we can potentially double-count the transfers, especially in cases where the transfer involves users of different ISPs. If ISPs only keep track of works distributed from nodes in their network, this problem can be addressed to some extent. The second problem is the computational load on the grid infrastructure of fingerprinting every single copy of a requested file. To make this computational load manageable, we can randomly sample the file transfers and get an idea about the rate of popularity of works instead of getting exact counts.3.2 Tracking in Privacy-Enhanced Peer-to-Peer Networks in the Wireless GridIn the wireless grid, dynamic rerouting of transfers is crucial for proper handling of mobile devices. This means that a transfer destined for a particular machine may have to be rerouted several times until it reaches its moving target. What is more, this rerouting has to be robust even when networks are complicated by privacy-enhancing mechanisms, such as common anonymous networking strategies that, re-route files through a random number of nodes to hide the real destination and the source [9]. This makes accurate accounting for downloads more complicated because each hop forced by either the peer-to-peer software or the router can look like an independent transfer. For example, for enhancing privacy, it is possible to route transfers through random nodes, all of which only know about the node before and the node after them. The transfer can continue through a random number of nodes after the ultimate goal node is reached, making it very difficult to identify the real recipient. The inability to calculate the exact number of transfers in this case also advocates for random sampling of the transfers, by ISPs, to estimate the relative popularity of shared works.An alternative to distribution volume tracking at the ISP is distribution volume tracking at the peers. With this, we mean that the DVT software will be installed at the machines of individual peers and it will fingerprint documents before they are sent from each node. The collected accounting information can then be reported, in aggregate, to the responsible organization to be used for compensating the content owners.A reputation-based mechanism would complement this proposal by giving end users incentives to install and run the fingerprinting software on their machines. For example, the users can be asked to correctly attribute the works they distribute, the accuracy of their attribution can be checked by the independent verifier – in this case the fingerprinting mechanism behind DVT, and the result can affect the user reputation. A better reputation can then be translated into better grid services and the competition for the resources on the grid can encourage more people to participate in this accounting system. Note that, this method does not require perfect participation, i.e., all users to participate. As long as an adequate sample of the population participates in this scheme, we will have enough information about the rate of popularity of content owners and their works.In addition, estimating the relative popularity of works instead of keeping exact download counts addresses issues related to untrackable downloads, such as those made by subscriptionless wireless devices. Also, inaccuracies in counting due to unreliable network, dropped and reinitiated connections/downloads are less of an issue as long as they are not due to attacks on the network and do not bias the accounting.Short of being exact, DVT through digital fingerprinting provides one way of establishing the relative rate of popularity of works, can be used to back up any other hypotheses about popularity of works and can adequately protect the revenues of content owners without inhibiting fair use, invading privacy or affecting anonymity of content users.4 R OLE OF ISP S4.1 Authentication and SecurityIn the scenarios we described, ISPs are responsible for the distribution volume tracking mechanism. This puts some additional burden on the ISPs. Operating under the assumption that the ISPs can negotiate with the content owners to be properly compensated for their efforts, we believe that the ISPs can also be responsible for collecting revenues from their subscribers and distribute this sum among the content owners, in proportion to the rate of distribution of works from and within their networks. This highlights the importance of user authentication for the ISPs.?4.2 Payment MechanismAs mentioned earlier, the information about distribution volume of works collected by digital tracking systems can be used as a guide for compensating content owners. But, how is this information to be used? What kind of a payment mechanism would minimize the incentive to bypass the tracking and payment systems? For example, if each user is asked to pay per download, some people will have incentives to bypass the tracking systems and avoid payment1. However, if the users pay a flat fee regardless of the number of their downloads, then the tracking systems do not affect the amount spent by the users; they only affect how the amount collected through the flat fee is distributed among the content owners.Netanel argues that the ISPs can be the middlemen that collect the flat-fees from their subscribers through “non-commercial use levy” and distribute the collected money to content owners, using the information gathered by the tracking mechanisms about distribution volume of different works [10].The payment mechanisms that are based on flat fees are admittedly unfair to some users of the network, because people who download fewer works end up paying the bill for1 Anania and Solomon’s work supports this argument. These authors suggest that flat-rate fees are indeed better than pricing mechanisms that are based on the download volume o f individuals because “the per-bit pricing mechanisms encourage the sophisticated user to manipulate” the systems to avoid payment [11].UZUNER: DISTRIBUTION VOLUME TRACKING ON PRIVACY-ENHANCED WIRELESS GR ID 5the users who download more works. However, as Odlyzko has shown, users prefer simpler methods of pricing and will be willing to overpay as long as pricing is simple [12]. Fisher suggests taxation of digital entertainment devices and services such as MP3 players and ISPs for collecting revenues. Such taxes can be used to expand the financial resources available for compensating the content owners and would work well with solutions based on estimates of popularity of works [13].4.3 ISP Coordination and CompetitionThe wireless grid allows users to roam through networks, and authenticate with different network providers as they do so. Assuming that the ISPs do not share infrastructure, an open question is: Is it fair to charge users who use multiple ISPs multiple flat rate fees? Subscription to more networks does not imply more downloads. Can the ISPs coordinate to eliminate this over-charge?5 O PEN Q UESTIONSDespite the challenges posed by the wireless grid environment, distribution volume tracking through digital fingerprinting of works can help reduce the deterioration of content owner’s revenues. However, to complete this proposal, we also need to find solutions to several open questions:1. Is it enough to install a tracking system at the serviceprovider on the wireless grid setting? How else, and where else in the network can a digital tracking-based DVT system be implemented? We believe there are more strategies and scenarios that we can look at, and we will find more ways in which DVT can be effectively implemented in the wireless grid.2. Is the assumption that users will not encrypt theirtransmissions realistic? And, is DVT completely ineffective if content is encrypted? The assumption may not be realistic, however, presence of encryption does not cripple DVT. As Schechter explains, on a peer-to-peer network, for e xample, interested parties can obtain the peer-to-peer client software and pose asa client to get access to unencrypted content [4]. We donot propose posing DVT as a client, but rather distributing it with the P2P software that people use.This would make sure that people on the network can participate in the distribution volume tracking, even in the presence of encryption. As mentioned earlier, a reputation-based mechanism would be useful for encouraging the users to, in fact, install and use this software.3. The end users are inevitably the resource users andproviders in a grid. This means that the resource allocator will be delegating the fingerprinting task to the end devices of the users. Can we trust the users to not attack the integrity of the software? McKnight et al. [14] discuss that there can be technical, social or legal consequences to this kind of behavior that can deter unacceptable behavior. A reputation-based mechanism can work in this case also. For example, the fingerprinting task can be delegated to multiple usersand the results can be crosschecked. If a user provides inaccurate fingerprints, this hurts their reputation and the processes they ask to delegate to the grid can be given lower priority. A similar mechanism has been implemented in the P2P file sharing systems Gnutella and Kazaa[14].4. Finally, can the artists manipulate the system to inflatethe rate of popularity of their works? Unfortunately, the answer is yes. However, there are reputation-based solutions that can address this issue [15].6 C ONCLUSIONThe high rate of mobility of the users on the wireless grid when combined with privacy-enhancing mechanisms that can hide location, device identity, user identity, or other private information, makes it difficult to conclusively link devices and/or individuals with network activities and to hold them liable for particular downloads. Protecting intellectual property in this scenario requires a solution that can work in absence of knowledge about behavior of particular individuals.Tracking individual behavior and preventing unauthorized uses has been a popular strategy for intellectual property protection. Problem with this approach is that it gives users incentives to break the technological protection systems. For the digital copyright problem to be solved with any technological solution, we need to eliminate, or at least minimize these incentives and make it not worthwhile to break the technological protection systems. Pricing works competitively, reducing the invasion of privacy, enabling fair use without extra charges, and in general finding a solution that is “fair” to all parties involved is the most effective way of achieving this goal.We believe, distribution volume tracking through digital tracking of content allows content owners to be compensated adequately (proportional to the popularity of their works) and avoids the privacy and fair use concerns raised by alternatives to distribution volume tracking, such as the DRMs. The ability of DVT to provide unbiased accounting of popularity of works, the fact that it does not invade privacy, but in fact eliminates the need to invade it, makes DVT an attractive solution to the digital copyright problem especially on platforms where the users are increasingly more concerned with their privacy.R EFERENCES[1] Lee W. McKnight, Diana Anius, and Ozlem Uzuner. InternetServices. Quality of Service in Grids, Networks and Markets, chapter “Virtual Markets in Wireless Grids: Peering Policy Prospects”.MIT Press, forthcoming.[2] Michael G. Reed, Paul F. Syverson, David M. Goldschlag.“Protocols using Anonymous Connections: Mobile Applications”. Security Protocols Workshop, pp. 13-23, 1997./article/reed97protocols.html[3] Jessica Litman. Digital Copyright. Prometheus Books 2001. ISBN 1-57392-889-5.[4] Stuart E. Schechter, Rachel A. Greenstadt, and Michael D. Smith.。