第3章习题及答案..
- 格式:ppt
- 大小:1.79 MB
- 文档页数:51

第3章计算机网络体系结构三、简答题1. 为什么要采用分层的方法解决计算机的通信问题?通过分层的方法,使得计算机网络复杂的通信处理问题转化成为若干相对较小的层次内的局部问题,对其进行的研究和处理变得相对容易。
2. “各层协议之间存在着某种物理连接,因此可以进行直接的通信。
”这句话对吗?不对。
物理连接只存在于最底层的下面。
各层协议之间只存在着称为“对等层通信”的逻辑连接。
3. 请简要叙述服务与协议之间的区别。
通过协议的规定,下一层可以为上一层提供服务,但是对于上一层的服务用户来说下面的协议是透明的。
协议是存在于对等层之间的,是水平的;服务存在于直接相邻的两个层次之间,是垂直的。
4. 请描述一下通信的两台主机之间通过OSI模型进行数据传输的过程。
发送数据的具体过程为:要进行通信的源用户进程首先将要传输的数据送至应用层并由该层的协议根据协议规范进行处理,为用户数据附加上控制信息后形成应用层协议数据单元再送至表示层;表示层根据本层的协议规范对收到的应用层协议数据单元进行处理,给应用层协议数据单元附加上表示层的控制信息后形成表示层的协议数据单元再将它传送至下一层。
数据按这种方式逐层向下传送直至物理层,最后由物理层实现比特流形式的传送。
当比特流沿着传输介质经过各种传输设备后最终到达了目标系统。
此后,接收数据的具体过程为:按照发送数据的逆过程,比特流从物理层开始逐层向上传送,在每一层都按照该层的协议规范以及数据单元的控制信息完成规定的操作,而后再将本层的控制信息剥离,并将数据部分向上一层传送,依此类推直至最终的、通信的目的用户进程。
5. 请简述虚电路服务的特点。
虚电路服务要求发送分组之前必须建立连接,即虚电路。
之后所有的分组都沿着虚电路依次进行传送。
在所有分组传送完毕后要释放连接。
它可以提供顺序、可靠的分组传输,适用于长报文的通信,一般应用于稳定的专用网络。
6. 请简述无连接服务的特点。
无连接服务无需事先建立连接。

第3章 力学基本定律与守恒律 习题及答案1.作用在质量为10 kg 的物体上的力为i t F)210(+=N ,式中t 的单位是s ,(1)求4s 后,这物体的动量和速度的变化.(2)为了使这力的冲量为200 N ·s ,该力应在这物体上作用多久,试就一原来静止的物体和一个具有初速度j 6-m ·s -1的物体,回答这两个问题.解: (1)若物体原来静止,则i t i t t F p t 1401s m kg 56d )210(d -⋅⋅=+==∆⎰⎰,沿x 轴正向,ip I imp v111111s m kg 56s m 6.5--⋅⋅=∆=⋅=∆=∆ 若物体原来具有6-1s m -⋅初速,则⎰⎰+-=+-=-=t tt F v m t m F v m p v m p 000000d )d (,于是⎰∆==-=∆t p t F p p p 0102d,同理, 12v v ∆=∆,12I I=这说明,只要力函数不变,作用时间相同,则不管物体有无初动量,也不管初动量有多大,那么物体获得的动量的增量(亦即冲量)就一定相同,这就是动量定理. (2)同上理,两种情况中的作用时间相同,即⎰+=+=tt t t t I 0210d )210(亦即 0200102=-+t t 解得s 10=t ,(s 20='t 舍去)2.一颗子弹由枪口射出时速率为10s m -⋅v ,当子弹在枪筒内被加速时,它所受的合力为 F =(bt a -)N(b a ,为常数),其中t 以秒为单位:(1)假设子弹运行到枪口处合力刚好为零,试计算子弹走完枪筒全长所需时间;(2)求子弹所受的冲量.(3)求子弹的质量. 解: (1)由题意,子弹到枪口时,有0)(=-=bt a F ,得ba t =(2)子弹所受的冲量⎰-=-=tbt at t bt a I 0221d )(将bat =代入,得 ba I 22=(3)由动量定理可求得子弹的质量202bv a v I m == 3.如图所示,一质量为m 的球,在质量为M 半径为R 的1/4圆弧形滑槽中从静止滑下。

第三章人类社会及其发展规律(课后练习题)一、单项选择题1 .人类社会历史发展的决定力量是( )A .生产方式B .地理条件C .社会意识D .人口因素2 .社会意识相对独立性的最突出表现是它( )A .同社会存在发展的不同步性B .具有历史的继承性C .对社会存在具有能动的反作用D .同社会经济的发展具有不平衡性3 .在生产关系中起决定作用的是( )A .生产资料所有制B .产品的分配和交换C .在生产中人与人的关系D .管理者和生产者的不同地位4 . “手推磨产生的是封建主的社会,蒸汽磨产生的是工业资本家的社会” , 这句话揭示了( )A .生产工具是衡量生产力水平的重要尺度B .科学技术是第一生产力C .社会形态的更替有其一定的顺序性D .物质生产的发展需要建立相应的生产关系5 .十一届三中全会以来,我党制定的一系列正确的路线、方针、政策促进了我国经济的迅猛发展,这说明( )A .经济基础发展的道路是由上层建筑决定的B .上层建筑的发展决定经济基础的发展方向C .上层建筑对经济基础具有积极的能动作用D .社会主义社会的发展不受经济基础决定上层建筑规律的制约6 .一定社会形态的经济基础是( )A .生产力B .该社会的各种生产关系C .政治制度和法律制度D .与一定生产力发展阶段相适应的生产关系的总和7 .上层建筑是指( )A .社会的经济制度B .科学技术C .社会生产关系D .建立在一定社会经济基础之上的意识形态及相应的制度和设施8 .社会形态是( )A .生产力和生产关系的统一B .同生产力发展一定阶段相适应的经济基础和上层建筑的统一体C .社会存在和社会意识的统一D .物质世界和精神世界的统一9 .人类社会发展的一般规律是( )A .生产方式内部的矛盾规律B .生产力和生产关系、经济基础和上层建筑之间的矛盾运动规律C .社会存在和社会意识的矛盾规律D .物质生产和精神生产的矛盾规律10 .阶级斗争对阶级社会发展的推动作用突出表现在( )A .生产力的发展B .生产关系的变革C .社会形态的更替D .科技的进步11 .社会革命根源于( )A .人口太多B .少数英雄人物组织暴动C .先进思想和革命理论的传播D .社会基本矛盾的尖锐化12 .社会主义改革的根本目的在于( )A .改变社会主义制度B .完善社会主义制度C .解放和发展生产力D .实现社会公平13 . “蒸汽、电力和自动纺织机甚至是比巴尔贝斯、拉斯拜尔和布朗基诸位公民更危险万分的革命家。

第三章1. (Q1) Suppose the network layer provides the following service. The network layer in the source host accepts a segment of maximum size 1,200 bytes and a destination host address from the transport layer. The network layer then guarantees to deliver the segment to the transport layer at the destination host. Suppose many network application processes can be running at the destination host.a. Design the simplest possible transport-layer protocol that will get application data to thedesired process at the destination host. Assume the operating system in the destination host has assigned a 4-byte port number to each running application process.b. Modify this protocol so that it provides a “return address” to the destination process.c. In your protocols, does the transport layer “have to do anything” in the core of the computernetwork.Answer:a. Call this protocol Simple Transport Protocol (STP). At the sender side, STP accepts from thesending process a chunk of data not exceeding 1196 bytes, a destination host address, and a destination port number. STP adds a four-byte header to each chunk and puts the port number of the destination process in this header. STP then gives the destination host address and the resulting segment to the network layer. The network layer delivers the segment to STP at the destination host. STP then examines the port number in the segment, extracts the data from the segment, and passes the data to the process identified by the port number.b. The segment now has two header fields: a source port field and destination port field. At thesender side, STP accepts a chunk of data not exceeding 1192 bytes, a destination host address,a source port number, and a destination port number. STP creates a segment which contains theapplication data, source port number, and destination port number. It then gives the segment and the destination host address to the network layer. After receiving the segment, STP at the receiving host gives the application process the application data and the source port number.c. No, the transport layer does not have to do anything in the core; the transport layer “lives” inthe end systems.2. (Q2) Consider a planet where everyone belongs to a family of six, every family lives in its own house, each house has a unique address, and each person in a given house has a unique name. Suppose this planet has a mail service that delivers letters form source house to destination house. The mail service requires that (i) the letter be in an envelope and that (ii) the address of the destination house (and nothing more ) be clearly written on the envelope. Suppose each family has a delegate family member who collects and distributes letters for the other family members. The letters do not necessarily provide any indication of the recipients of the letters.a. Using the solution to Problem Q1 above as inspiration, describe a protocol that thedelegates can use to deliver letters from a sending family member to a receiving family member.b. In your protocol, does the mail service ever have to open the envelope and examine theletter in order to provide its service.Answer:a.For sending a letter, the family member is required to give the delegate the letter itself, theaddress of the destination house, and the name of the recipient. The delegate clearly writes the recipient’s name on the top of the letter. The delegate then puts the letter in an e nvelope and writes the address of the destination house on the envelope. The delegate then gives the letter to the planet’s mail service. At the receiving side, the delegate receives the letter from the mail service, takes the letter out of the envelope, and takes note of the recipient name written at the top of the letter. The delegate than gives the letter to the family member with this name.b.No, the mail service does not have to open the envelope; it only examines the address on theenvelope.3. (Q3) Describe why an application developer might choose to run an application over UDP rather than TCP.Answer:An application developer may not want its application to use TCP’s congestion control, which can throttle the application’s sending rate at times of congestion. Often, designers of IP telephony and IP videoconference applications choose to run their applications over UDP because they want to avoid TCP’s congestion control. Also, some applications do not need the reliable data transfer provided by TCP.4. (P1) Suppose Client A initiates a Telnet session with Server S. At about the same time, Client B also initiates a Telnet session with Server S. Provide possible source and destination port numbers fora. The segment sent from A to B.b. The segment sent from B to S.c. The segment sent from S to A.d. The segment sent from S to B.e. If A and B are different hosts, is it possible that the source port number in the segment fromA to S is the same as that fromB to S?f. How about if they are the same host?Yes.f No.5. (P2) Consider Figure 3.5 What are the source and destination port values in the segmentsflowing form the server back to the clients’ processes? What are the IP addresses in the network-layer datagrams carrying the transport-layer segments?Answer:Suppose the IP addresses of the hosts A, B, and C are a, b, c, respectively. (Note that a,b,c aredistinct.)To host A: Source port =80, source IP address = b, dest port = 26145, dest IP address = a To host C, left process: Source port =80, source IP address = b, dest port = 7532, dest IP address = cTo host C, right process: Source port =80, source IP address = b, dest port = 26145, dest IP address = c6. (P3) UDP and TCP use 1s complement for their checksums. Suppose you have the followingthree 8-bit bytes: 01101010, 01001111, 01110011. What is the 1s complement of the sum of these 8-bit bytes? (Note that although UDP and TCP use 16-bit words in computing the checksum, for this problem you are being asked to consider 8-bit sums.) Show all work. Why is it that UDP takes the 1s complement of the sum; that is , why not just sue the sum? With the 1s complement scheme, how does the receiver detect errors? Is it possible that a 1-bit error will go undetected? How about a 2-bit error?Answer:One's complement = 1 1 1 0 1 1 1 0.To detect errors, the receiver adds the four words (the three original words and the checksum). If the sum contains a zero, the receiver knows there has been an error. All one-bit errors will be detected, but two-bit errors can be undetected (e.g., if the last digit of the first word is converted to a 0 and the last digit of the second word is converted to a 1).7. (P4) Suppose that the UDP receiver computes the Internet checksum for the received UDPsegment and finds that it matches the value carried in the checksum field. Can the receiver be absolutely certain that no bit errors have occurred? Explain.Answer:No, the receiver cannot be absolutely certain that no bit errors have occurred. This is because of the manner in which the checksum for the packet is calculated. If the corresponding bits (that would be added together) of two 16-bit words in the packet were 0 and 1 then even if these get flipped to 1 and 0 respectively, the sum still remains the same. Hence, the 1s complement the receiver calculates will also be the same. This means the checksum will verify even if there was transmission error.8. (P5) a. Suppose you have the following 2 bytes: 01001010 and 01111001. What is the 1scomplement of sum of these 2 bytes?b. Suppose you have the following 2 bytes: 11110101 and 01101110. What is the 1s complement of sum of these 2 bytes?c. For the bytes in part (a), give an example where one bit is flipped in each of the 2 bytesand yet the 1s complement doesn’t change.0 1 0 1 0 1 0 1 + 0 1 1 1 0 0 0 0 1 1 0 0 0 1 0 1 1 1 0 0 0 1 0 1 + 0 1 0 0 1 1 0 0 0 0 0 1 0 0 0 1Answer:a. Adding the two bytes gives 10011101. Taking the one’s complement gives 01100010b. Adding the two bytes gives 00011110; the one’s complement gives 11100001.c. first byte = 00110101 ; second byte = 01101000.9. (P6) Consider our motivation for correcting protocol rdt2.1. Show that the receiver, shown inthe figure on the following page, when operating with the sender show in Figure 3.11, can lead the sender and receiver to enter into a deadlock state, where each is waiting for an event that will never occur.Answer:Suppose the sender is in state “Wait for call 1 from above” and the receiver (the receiver shown in the homework problem) is in state “Wait for 1 from below.” The sender sends a packet with sequence number 1, and transitions to “Wait for ACK or NAK 1,” waiting for an ACK or NAK. Suppose now the receiver receives the packet with sequence number 1 correctly, sends an ACK, and transitions to state “Wait for 0 from below,” waiting for a data packet with sequence number 0. However, the ACK is corrupted. When the rdt2.1 sender gets the corrupted ACK, it resends the packet with sequence number 1. However, the receiver is waiting for a packet with sequence number 0 and (as shown in the home work problem) always sends a NAK when it doesn't get a packet with sequence number 0. Hence the sender will always be sending a packet with sequence number 1, and the receiver will always be NAKing that packet. Neither will progress forward from that state.10. (P7) Draw the FSM for the receiver side of protocol rdt3.0Answer:The sender side of protocol rdt3.0 differs from the sender side of protocol 2.2 in that timeouts have been added. We have seen that the introduction of timeouts adds the possibility of duplicate packets into the sender-to-receiver data stream. However, the receiver in protocol rdt.2.2 can already handle duplicate packets. (Receiver-side duplicates in rdt 2.2 would arise if the receiver sent an ACK that was lost, and the sender then retransmitted the old data). Hence the receiver in protocol rdt2.2 will also work as the receiver in protocol rdt 3.0.11. (P8) In protocol rdt3.0, the ACK packets flowing from the receiver to the sender do not havesequence numbers (although they do have an ACK field that contains the sequence number of the packet they are acknowledging). Why is it that our ACK packets do not require sequence numbers?Answer:To best Answer this question, consider why we needed sequence numbers in the first place. We saw that the sender needs sequence numbers so that the receiver can tell if a data packet is a duplicate of an already received data packet. In the case of ACKs, the sender does not need this info (i.e., a sequence number on an ACK) to tell detect a duplicate ACK. A duplicate ACK is obvious to the rdt3.0 receiver, since when it has received the original ACK it transitioned to the next state. The duplicate ACK is not the ACK that the sender needs and hence is ignored by the rdt3.0 sender.12. (P9) Give a trace of the operation of protocol rdt3.0 when data packets and acknowledgmentpackets are garbled. Your trace should be similar to that used in Figure 3.16Answer:Suppose the protocol has been in operation for some time. The sender is in state “Wait for call fro m above” (top left hand corner) and the receiver is in state “Wait for 0 from below”. The scenarios for corrupted data and corrupted ACK are shown in Figure 1.13. (P10) Consider a channel that can lose packets but has a maximum delay that is known.Modify protocol rdt2.1 to include sender timeout and retransmit. Informally argue whyyour protocol can communicate correctly over this channel.Answer:Here, we add a timer, whose value is greater than the known round-trip propagation delay. We add a timeout event to the “Wait for ACK or NAK0” and “Wait for ACK or NAK1” states. If the timeout event occurs, the most recently transmitted packet is retransmitted. Let us see why this protocol will still work with the rdt2.1 receiver.• Suppose the timeout is caused by a lost data packet, i.e., a packet on the senderto- receiver channel. In this case, the receiver never received the previous transmission and, from the receiver's viewpoint, if the timeout retransmission is received, it look exactly the same as if the original transmission is being received.• Suppose now that an ACK is lost. The receiver will eventually retransmit the packet on atimeout. But a retransmission is exactly the same action that is take if an ACK is garbled. Thus the sender's reaction is the same with a loss, as with a garbled ACK. The rdt 2.1 receiver can already handle the case of a garbled ACK.14. (P11) Consider the rdt3.0 protocol. Draw a diagram showing that if the network connectionbetween the sender and receiver can reorder messages (that is, that two messagespropagating in the medium between the sender and receiver can be reordered), thenthe alternating-bit protocol will not work correctly (make sure you clearly identify thesense in which it will not work correctly). Your diagram should have the sender on theleft and the receiver on the right, with the time axis running down the page, showingdata (D) and acknowledgement (A) message exchange. Make sure you indicate thesequence number associated with any data or acknowledgement segment.Answer:15. (P12) The sender side of rdt3.0 simply ignores (that is, takes no action on) all received packetsthat are either in error or have the wrong value in the ack-num field of anacknowledgement packet. Suppose that in such circumstances, rdt3.0 were simply toretransmit the current data packet . Would the protocol still work? (hint: Consider whatwould happen if there were only bit errors; there are no packet losses but prematuretimeout can occur. Consider how many times the nth packet is sent, in the limit as napproaches infinity.)Answer:The protocol would still work, since a retransmission would be what would happen if the packet received with errors has actually been lost (and from the receiver standpoint, it never knows which of these events, if either, will occur). To get at the more subtle issue behind this question, one has to allow for premature timeouts to occur. In this case, if each extra copy of the packet is ACKed and each received extra ACK causes another extra copy of the current packet to be sent, the number of times packet n is sent will increase without bound as n approaches infinity.16. (P13) Consider a reliable data transfer protocol that uses only negative acknowledgements.Suppose the sender sends data only infrequently. Would a NAK-only protocol bepreferable to a protocol that uses ACKs? Why? Now suppose the sender has a lot ofdata to send and the end to end connection experiences few losses. In this second case ,would a NAK-only protocol be preferable to a protocol that uses ACKs? Why?Answer:In a NAK only protocol, the loss of packet x is only detected by the receiver when packetx+1 is received. That is, the receivers receives x-1 and then x+1, only when x+1 is received does the receiver realize that x was missed. If there is a long delay between the transmission of x and the transmission of x+1, then it will be a long time until x can be recovered, under a NAK only protocol.On the other hand, if data is being sent often, then recovery under a NAK-only scheme could happen quickly. Moreover, if errors are infrequent, then NAKs are only occasionally sent (when needed), and ACK are never sent – a significant reduction in feedback in the NAK-only case over the ACK-only case.17. (P14) Consider the cross-country example shown in Figure 3.17. How big would the windowsize have to be for the channel utilization to be greater than 80 percent?Answer:It takes 8 microseconds (or 0.008 milliseconds) to send a packet. in order for the sender to be busy 90 percent of the time, we must have util = 0.9 = (0.008n) / 30.016 or n approximately 3377 packets.18. (P15) Consider a scenario in which Host A wants to simultaneously send packets to Host Band C. A is connected to B and C via a broadcast channel—a packet sent by A is carriedby the channel to both B and C. Suppose that the broadcast channel connecting A, B,and C can independently lose and corrupt packets (and so, for example, a packet sentfrom A might be correctly received by B, but not by C). Design a stop-and-wait-likeerror-control protocol for reliable transferring packets from A to B and C, such that Awill not get new data from the upper layer until it knows that B and C have correctlyreceived the current packet. Give FSM descriptions of A and C. (Hint: The FSM for Bshould be essentially be same as for C.) Also, give a description of the packet format(s)used.Answer:In our solution, the sender will wait until it receives an ACK for a pair of messages (seqnum and seqnum+1) before moving on to the next pair of messages. Data packets have a data field and carry a two-bit sequence number. That is, the valid sequence numbers are 0, 1, 2, and 3. (Note: you should think about why a 1-bit sequence number space of 0, 1 only would not work in the solution below.) ACK messages carry the sequence number of the data packet they are acknowledging.The FSM for the sender and receiver are shown in Figure 2. Note that the sender state records whether (i) no ACKs have been received for the current pair, (ii) an ACK for seqnum (only) has been received, or an ACK for seqnum+1 (only) has been received. In this figure, we assume that theseqnum is initially 0, and that the sender has sent the first two data messages (to get things going).A timeline trace for the sender and receiver recovering from a lost packet is shown below:Sender Receivermake pair (0,1)send packet 0Packet 0 dropssend packet 1receive packet 1buffer packet 1send ACK 1receive ACK 1(timeout)resend packet 0receive packet 0deliver pair (0,1)send ACK 0receive ACK 019. (P16) Consider a scenario in which Host A and Host B want to send messages to Host C. HostsA and C are connected by a channel that can lose and corrupt (but not reorder)message.Hosts B and C are connected by another channel (independent of the channelconnecting A and C) with the same properties. The transport layer at Host C shouldalternate in delivering messages from A and B to the layer above (that is, it should firstdeliver the data from a packet from A, then the data from a packet from B, and so on).Design a stop-and-wait-like error-control protocol for reliable transferring packets fromA toB and C, with alternating delivery atC as described above. Give FSM descriptionsof A and C. (Hint: The FSM for B should be essentially be same as for A.) Also, give adescription of the packet format(s) used.Answer:This problem is a variation on the simple stop and wait protocol (rdt3.0). Because the channel may lose messages and because the sender may resend a message that one of the receivers has already received (either because of a premature timeout or because the other receiver has yet to receive the data correctly), sequence numbers are needed. As in rdt3.0, a 0-bit sequence number will suffice here.The sender and receiver FSM are shown in Figure 3. In this problem, the sender state indicates whether the sender has received an ACK from B (only), from C (only) or from neither C nor B. The receiver state indicates which sequence number the receiver is waiting for.20. (P17) In the generic SR protocol that we studied in Section 3.4.4, the sender transmits amessage as soon as it is available (if it is in the window) without waiting for anacknowledgment. Suppose now that we want an SR protocol that sends messages twoat a time. That is , the sender will send a pair of messages and will send the next pairof messages only when it knows that both messages in the first pair have been receivercorrectly.Suppose that the channel may lose messages but will not corrupt or reorder messages.Design an error-control protocol for the unidirectional reliable transfer of messages.Give an FSM description of the sender and receiver. Describe the format of the packetssent between sender and receiver, and vice versa. If you use any procedure calls otherthan those in Section 3.4(for example, udt_send(), start_timer(), rdt_rcv(), and soon) ,clearly state their actions. Give an example (a timeline trace of sender and receiver)showing how your protocol recovers from a lost packet.Answer:21. (P18) Consider the GBN protocol with a sender window size of 3 and a sequence numberrange of 1024. Suppose that at time t, the next in-order packet that the receiver isexpecting has a sequence number of k. Assume that the medium does not reordermessages. Answer the following questions:a. What are the possible sets of sequence number inside the sender’s window at timet? Justify your Answer.b .What are all possible values of the ACK field in all possible messages currentlypropagating back to the sender at time t? Justify your Answer.Answer:a.Here we have a window size of N=3. Suppose the receiver has received packet k-1, and hasACKed that and all other preceeding packets. If all of these ACK's have been received by sender, then sender's window is [k, k+N-1]. Suppose next that none of the ACKs have been received at the sender. In this second case, the sender's window contains k-1 and the N packets up to and including k-1. The sender's window is thus [k- N,k-1]. By these arguments, the senders window is of size 3 and begins somewhere in the range [k-N,k].b.If the receiver is waiting for packet k, then it has received (and ACKed) packet k-1 and the N-1packets before that. If none of those N ACKs have been yet received by the sender, then ACKmessages with values of [k-N,k-1] may still be propagating back. Because the sender has sent packets [k-N, k-1], it must be the case that the sender has already received an ACK for k-N-1.Once the receiver has sent an ACK for k-N-1 it will never send an ACK that is less that k-N-1.Thus the range of in-flight ACK values can range from k-N-1 to k-1.22. (P19) Answer true or false to the following questions and briefly justify your Answer.a. With the SR protocol, it is possible for the sender to receive an ACK for a packet thatfalls outside of its current window.b. With CBN, it is possible for the sender to receiver an ACK for a packet that fallsoutside of its current window.c. The alternating-bit protocol is the same as the SR protocol with a sender and receiverwindow size of 1.d. The alternating-bit protocol is the same as the GBN protocol with a sender andreceiver window size of 1.Answer:a.True. Suppose the sender has a window size of 3 and sends packets 1, 2, 3 at t0 . At t1 (t1 > t0)the receiver ACKS 1, 2, 3. At t2 (t2 > t1) the sender times out and resends 1, 2, 3. At t3 the receiver receives the duplicates and re-acknowledges 1, 2, 3. At t4 the sender receives the ACKs that the receiver sent at t1 and advances its window to 4, 5, 6. At t5 the sender receives the ACKs 1, 2, 3 the receiver sent at t2 . These ACKs are outside its window.b.True. By essentially the same scenario as in (a).c.True.d.True. Note that with a window size of 1, SR, GBN, and the alternating bit protocol arefunctionally equivalent. The window size of 1 precludes the possibility of out-of-order packets (within the window). A cumulative ACK is just an ordinary ACK in this situation, since it can only refer to the single packet within the window.23. (Q4) Why is it that voice and video traffic is often sent over TCP rather than UDP in today’sInternet. (Hint: The Answer we are looking for has nothing to do with TCP’s congestion-control mechanism. )Answer:Since most firewalls are configured to block UDP traffic, using TCP for video and voice traffic lets the traffic though the firewalls24. (Q5) Is it possible for an application to enjoy reliable data transfer even when the applicationruns over UDP? If so, how?Answer:Yes. The application developer can put reliable data transfer into the application layer protocol. This would require a significant amount of work and debugging, however.25. (Q6) Consider a TCP connection between Host A and Host B. Suppose that the TCP segmentstraveling form Host A to Host B have source port number x and destination portnumber y. What are the source and destination port number for the segments travelingform Host B to Host A?Answer:Source port number y and destination port number x.26. (P20) Suppose we have two network entities, A and B. B has a supply of data messages thatwill be sent to A according to the following conventions. When A gets a request fromthe layer above to get the next data (D) message from B, A must send a request (R)message to B on the A-to-B channel. Only when B receives an R message can it send adata (D) message back to A on the B-to-A channel. A should deliver exactly one copy ofeach D message to the layer above. R message can be lost (but not corrupted) in the A-to-B channel; D messages, once sent, are always delivered correctly. The delay alongboth channels is unknown and variable.Design(give an FSM description of) a protocol that incorporates the appropriatemechanisms to compensate for the loss-prone A-to-B channel and implementsmessage passing to the layer above at entity A, as discussed above. Use only thosemechanisms that are absolutely necessary.Answer:Because the A-to-B channel can lose request messages, A will need to timeout and retransmit its request messages (to be able to recover from loss). Because the channel delays are variable and unknown, it is possible that A will send duplicate requests (i.e., resend a request message that has already been received by B). To be able to detect duplicate request messages, the protocol will use sequence numbers. A 1-bit sequence number will suffice for a stop-and-wait type of request/response protocol.A (the requestor) has 4 states:• “Wait for Request 0 from above.” Here the requestor is waiting for a call from above to request a unit of data. When it receives a request from above, it sends a request message, R0, to B, starts a timer and make s a transition to the “Wait for D0” state. When in the “Wait for Request 0 from above” state, A ign ores anything it receives from B.• “Wait for D0”. Here the requestor is waiting for a D0 data message from B. A timer is always running in this state. If the timer expires, A sends another R0 message, restarts the timer and remains in this state. If a D0 message is received from B, A stops the time and transits to the “Wait for Request 1 from above” state. If A receives a D1 data message while in this state, it is ignored.• “Wait for Request 1 from above.” Here the requestor is again waiting for a call from above to request a unit of data. When it receives a request from above, it sends a request message, R1, to B, starts a timer and makes a transition to the “Wait for D1” state. When in the “Wait for Request 1 from above” state, A ignores anything it receives from B.• “Wait for D1”. Here the requestor is waiting for a D1 data message from B. A timer is always running in this state. If the timer expires, A sends another R1 message, restarts the timer and remains in this state. If a D1 message is received from B, A stops the timer and transits to the “Wait for Request 0 from above” state. If A receives a D0 data message while in this state, it is ignored.The data supplier (B) has only two states:。

第3章本量利分析一、单项选择题:1、生产单一品种产品企业,保本销售额=( B )A. 保本销售量×单位利润B. 固定成本总额÷贡献边际率C. 固定成本总额÷(单价一单位变动成本)D. 固定成本总额÷综合贡献边际率E. 固定成本总额÷贡献边际2、生产多品种产品企业测算综合保本销售额=固定成本总额÷( D )A.单位贡献边际B.贡献边际率C.单价一单位变动成本D.加权平均贡献毛益率3、某企业只生产一种产品,单价6元,单位变动生产成本4元,单位销售和管理变动成本0.5元,销量为500件,则其产品贡献边际为( B )元A.650B.750C.850D.9504、下属因素中导致保本销售量下降的是( D )A.销售量上升B.产品单价下降C.固定成本上升D.产品单位变动成本下降5、在变动成本法下,其利润表所提供的中间指标是( A )A.贡献边际B.营业利润C.营业毛利D.期间成本6、在下列指标中,可据以判断企业经营安全程度的指标是( C )A.保本量B.贡献边际C.保本作业率D.保本额7、保本作业率与安全边际率之间的关系是( D )A.两者相等B.前者一般大于后者C.后者一般大于前者D.两者之和等于18、销售量不变,保本点越高,则能实现的利润( A )A.越小B.不变C.越大D.不一定9、销售量不变,单价单独变动时,会使安全边际( C )A.不变B.不一定变动C.同方向变动D.反方向变动10、下列因素单独变动时,不对实现目标利润的销售量产生影响的是( D )A.单价B.目标利润C.成本水平D.销售量二、多项选择题:1、安全边际率=( AC )A.安全边际量÷实际销售量B.保本销售量÷实际销售量C.安全边际额÷实际销售额D.保本销售额÷实际销售额E.安全边际量÷安全边际额2、从传统式保本图得知( CE )A.保本点右边,成本大于收入,是亏损区B.销售量一定的情况下,保本点越高,盈利区越大C.实际销售量超过保本点销售量部分即是安全边际D.在其他因素不变的情况,保本点越低,盈利面积越小E.安全边际越大,盈利面积越大3、贡献边际率的计算公式可表示为(ABDE )A.1-变动成本率B.贡献边际/销售收入C.固定成本/保本销售量D.固定成本/保本销售额E.单位贡献边际/单价4、在盈亏临界图中,盈亏临界点的位置取决于( ABD )等因素。


习题3 参考答案一、选择题3.1 C 分析:本题考查程序和数组的基本概念。
3.2 A 分析:字符串比较大小是以第1个不相同字符的大小为标准的,跟长度没有关系,B选项不正确;字符串比较大小除了使用库函数strcn3()以外,就只能靠自己写代码来实现了,而不能通过关系运算符来比较大小。
因为字符串在表达式中相当于const char*,即常字符指针,代表的是字符串的首地址,关系运算符会将两个字符串的首地址值比较大小,这是毫无意义的。
C选项不正确。
C语言中只有字符串常量而没有字符串变量,D选项描述不正确;空串的长度为0,而以空格打头的字符串的长度至少为1,因此A选项是正确。
3.3 A 分析:如果第一维的长度没有指定,则定义的同时需要完成初始化,否则不知道分配多大的内存空间给它,所以选项B、C错误;二维数组a[2][3]中只有两个元素,都是一维数组,一维下标最大只能是a[1],所以选项D错误;若完成初始化的二维数组,第一维的长度没有指定,则第一维的大小按如下规则确定:若初值个数能被第二维大小整除,所得的商就是第一维的大小,若不能整除,则所得的商加1作为第一维的大小,所以选项A相当于:double a[1][3] = {6};其中a[0][0]=6,其他元素赋值0,选项A正确,答案为A。
3.4 D 分析:本题考察的知识点是:字符串常量。
在C语言中,字符串常量是以双引号括起来的字符序列。
因此B选项和C选项不正确。
字符序列中可包含一些转义字符,转义字符都是以"\"开头的。
A选项中包含了三个"\",前两个(\\)代表了一个"\"字符,后面一个和"""一起(\")被看作一个""",所以该字符串缺少一个结束的""",因此不正确。
D选项的两个"""之间没有任何字符,代表的是一个空串,是合法的字符串常量,因此D选项正确。

第三章弹性理论思考与练习一、选择题1.计算需求弹性的弹性系数的一般公式是( )。
A.需求量与价格之比B.需求量变动的百分比除以价格变动的百分比C.需求量变动的绝对值除以价格变动的绝对值D.价格变动的百分比除以需求量变动的百分比2.某种商品的价格变动10%,需求量变动20%。
则它的弹性系数为( )。
A.10%B.30%C.1/2D.23.如果一种商品的需求的价格弹性为2,价格由1元上升到1.02元会导致需求量( )。
A.增加4%B.增加2%C.减少4%D.减少2%4.如果一种商品的需求的价格弹性为0.5,价格由l元上升到1.04元会导致需求量( )。
A.增加4%B.增加2%C.减少4%D.减少2%5.如果需求的价格弹性为1/3,价格上升30%时,需求量将( )。
A.增加10%B.减少10%C.增加90%D.减少90%6.如果一种商品的价格上升时,需求量完全没有下降,那么该商品的需求( )。
A.完全有弹性B.完全无弹性C.富有弹性D.缺乏弹性7.如果一种商品的价格变动5%,需求量因此变动5%.那么该商品的需求( )。
A.富有弹性B.缺乏弹性C.无弹性D.单位弹性8.如果( ),我们就说一种商品的需求缺乏弹性。
A.需求量变化百分比大于价格变化百分比B.需求量变化百分比小于价格变化百分比C.需求变化大于价格变化D.价格变化大于需求变化9.如果一种商品的需求缺乏弹性,其弹性系数( )。
A.大于1B.大于0小于1C.等于1D.为010.如果一种商品的需求缺乏弹性,商品价格上升5%将使( )。
A.需求量的增加超过5%B.需求量的增加小于5%C.需求量的减少超过5%D.需求量的减少小于5%参考答案1.B;2.D;3.C;4.D;5.B;6.B;7.D;8.B;9.B;10.D二、判断题1.同一条线性需求曲线上不同点的弹性系数是不同的。
( )2.需求的价格弹性为零意味着需求曲线是一条水平线。
( )3.当某种产品的价格上升8%,而需求量减少7%时。

第3章 习题及答案1.将下列烃类化合物按沸点降低的次序排列。
(1)2,3-二甲基戊烷 (2)正庚烷 (3)2-甲基庚烷 (4)正戊烷 (5)2-甲基己烷解:2-甲基庚烷>正庚烷>2-甲基己烷>2,3-二甲基戊烷>正戊烷(注:随着烷烃相对分子量的增加,分子间的作用力亦增加,其沸点也相应增加;同数碳原子的构造异构体中,分子的支链愈多,则沸点愈低。
)2.比较下列化合物在水中的溶解度的大小,并说明理由。
(1)(2)(3)(4)(5)CH 3CH 2CH 2OH CH 2OHCH 2 CH 2OHCH 3OCH 2CH 3CH 2OHCHOHCH 2OHCH 3CH 2CH 3 解:溶解度顺序是:(4)>(2)>(1)>(3)>(5)。
理由:羟基与水形成分子间氢键,羟基越多在水中溶解度越大,醚可与水形成氢键,而丙烷不能。
3.比较下列化合物沸点的高低。
(1)乙醚 (2)正丁醇 (3)仲丁醇 (4)叔丁醇解:(2)>(3)>(4)>(1)4.比较下列化合物沸点的高低。
(1)丙醛 (2)1-丙醇 (3)乙酸解:(3)>(2)>(1)5.将下列烷烃的沸点按从高到低的顺序排列。
(1)2甲基戊烷 (2)正己烷 (3)正庚烷 (4)十二烷解:(4)>(3)>(2)(1)6.将下列化合物按碱性由强到弱排列:(1)(2)(CH 3)3N (3)(C 6H 5)3N(4)CH 3NH 2(5)(6)(7)(8)(9)NH 3NH 2NH 2NO 2CH 3NH 2NO 2NH 2NO 2NH C 2H 5 解:胺的碱性由强到弱的顺序是脂肪胺>氨>芳香胺。
对于脂肪胺,电子效应、溶剂化效应和空间位阻效应共同影响的结果,二甲胺的碱性大于三甲胺;而对于芳香胺,电子效应起主导作用,连有斥电子基碱性增强,连有吸电子基碱性减弱;三苯胺的碱性最弱,主要是空间位阻效应所致。

第三章练习题一、填空题1、从国际经济地理的分布上看,发达国家大都分布在北方,发展中国家大都分布在南方,因此,国际经济学界有时将这种发达国家与发展中国家的产业间贸易称作。
2、规模经济指企业的平均成本随着整个行业生产规模的不断扩大而下降。
3、不以要素禀赋差异为基础,而以规模经济和差异产品为基础的国际贸易是贸易。
4、外部规模经济下的国际分工与贸易模式是不可预测的,在很大程度上由因素决定。
5、从技术转移的角度探讨比较优势动态演变的贸易理论是技术差距理论和理论。
6、重叠需求理论认为,是影响一国需求结构的最主要因素。
7、1961年瑞典经济学家提出了重叠需求理论,从需求的角度探讨了国际贸易发生的原因。
8、国际贸易理论最新的发展方向之一是将技术作为贸易的内生变量来分析,既研究技术变化的原因,也研究作为生产和贸易结果的技术进步对与社会福利的影响。
9、在国内投资乘数理论的基础上,凯恩斯的追随们引申出理论。
10、战略性贸易理论的基本内容是利用关税分享外国企业的垄断利润和。
11、贸易政策有两大基本类型,即和保护贸易政策。
12、美国1988年在中修订过301条款。
13、就是以国内生产的工业品代替进口产品的政策。
14、指用工业制成品和半制成品的出口代替初级产品出口的政策。
15、除比较优势外,成为国际贸易的一个独立的基础和源泉。
16、某种商品的进口大国设置一定程度的关税会使贸易条件向有利于本国不利于外国的方向转化,使国内实际收入最大化,这种程度关税叫。
二、判断题1、如果厂商的生产具有规模报酬递增的特征,那么该厂商一定存在规模经济,但规模经济不一定要求规模报酬递增。
2、一个只存在外部规模经济的行业一般由大量较小的厂商构成。
3、外部规模经济下的国际分工与贸易格局在很大程度上由历史或偶然因素决定。
4、市场规模大的国家生产的差异化产品种类一般较多。
5、新制度经济学认为,所有交易集中在一个地方可以改进交易效率,只要交易效率改进带来的收益大于该地区地价上升产生的成本,行业还会进一步向该地区及其周边集中。
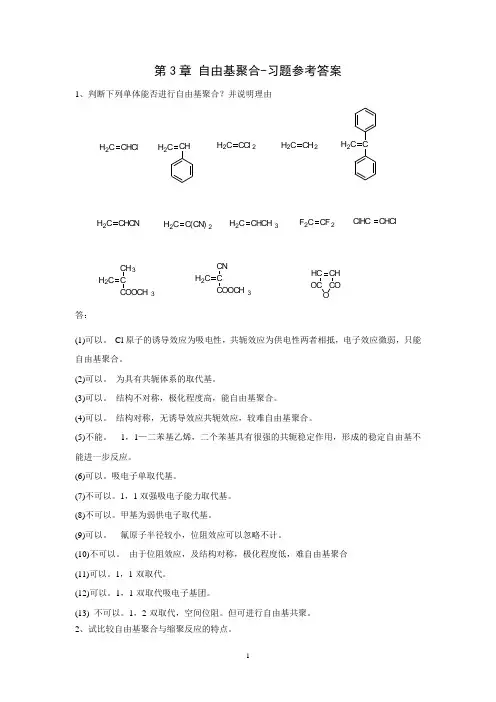
第3章自由基聚合-习题参考答案1、判断下列单体能否进行自由基聚合?并说明理由H2C CHCl H2C CH H2C CCl2H2C CH2H2C CH2C CHCN H2C C(CN)2H2C CHCH3F2C CF2ClHC CHClH2C CCH3COOCH3H2C CCNCOOCH3HC CHOC COO答:(1)可以。
Cl原子的诱导效应为吸电性,共轭效应为供电性两者相抵,电子效应微弱,只能自由基聚合。
(2)可以。
为具有共轭体系的取代基。
(3)可以。
结构不对称,极化程度高,能自由基聚合。
(4)可以。
结构对称,无诱导效应共轭效应,较难自由基聚合。
(5)不能。
1,1—二苯基乙烯,二个苯基具有很强的共轭稳定作用,形成的稳定自由基不能进一步反应。
(6)可以。
吸电子单取代基。
(7)不可以。
1,1双强吸电子能力取代基。
(8)不可以。
甲基为弱供电子取代基。
(9)可以。
氟原子半径较小,位阻效应可以忽略不计。
(10)不可以。
由于位阻效应,及结构对称,极化程度低,难自由基聚合(11)可以。
1,1-双取代。
(12)可以。
1,1-双取代吸电子基团。
(13) 不可以。
1,2-双取代,空间位阻。
但可进行自由基共聚。
2、试比较自由基聚合与缩聚反应的特点。
答:自由基聚合:(1)由链引发,链增长,链终止等基元反应组成,其速率常数和活化能均不等,链引发最慢是控制步骤。
(2)单体加到少量活性种上,使链迅速增长。
单体-单体,单体-聚合物,聚合物-聚合物之间均不能反应。
(3)只有链增长才是聚合度增加,从一聚体增加到高聚物,时间极短,中间不能暂停。
聚合一开始就有高聚物产生。
(4)在聚合过程中,单体逐渐减少,转化率相应增加(5)延长聚合时间,转化率提高,分子量变化较小。
(6)反应产物由单体,聚合物,微量活性种组成。
(7)微量苯酚等阻聚剂可消灭活性种,使聚合终止。
缩聚反应:(1)不能区分出链引发,链增长,链终止,各部分反应速率和活化能基本相同。
(一) 填空题1.在高温热源T 1和低温热源T 2之间的卡诺循环, 其热温熵之和()1212Q Q T T +=。
循环过程的热机效率()η=。
2.任一不可逆循环过程的热温熵之和可以表示为()0Q T δ⎛⎫⎪⎝⎭⎰不可逆。
3.在绝热密闭的刚性容器中发生某一化学反应,此过程的()sys 0S ∆;()amb0S ∆。
4.系统经可逆循环后,S ∆( )0, 经不可逆循环后S ∆( )。
(填>,=,<)。
5.某一系统在与环境300K 大热源接触下经历一不可逆循环过程,系统从环境得到10kJ 的功,则系统与环境交换的热()Q =;()sysS∆=;()ambS∆=。
6.下列过程的△U 、△H 、△S 、△G 何者为零? ⑴ 理想气体自由膨胀( );⑵ H 2(g )和Cl 2(g )在绝热的刚性容器中反应生成HCl (g )的过程( ); ⑶ 在0 ℃、101.325 kPa 下水结成冰的相变过程( )。
⑷ 一定量真实气体绝热可逆膨胀过程( )。
⑸ 实际气体节流膨胀过程( )。
7.一定量理想气体与300K 大热源接触做等温膨胀,吸热Q =600kJ,对外所做功为可逆功的40%,则系统的熵变()S ∆=。
8. 1 mol O 2(p 1,V 1,T 1)和1 mol N 2(p 1,V 1,T 1)混合后,总压为2 p 1,总体积为V 1,温度为T 1,此过程的△S ( )0(填>,<或=,O 2和N 2均可看作理想气体)。
9.热力学第三定律用公式表示为:()()*m S =。
10. 根据 d G =-S d T+V d p 可知任一化学反应的 (1)r m ΔTG p ⎛⎫∂= ⎪∂⎝⎭( ); (2)r m ΔP G T ∂⎛⎫= ⎪∂⎝⎭( ); (3)r m ΔPV T ∂⎛⎫= ⎪∂⎝⎭( )。
11.某理想气体在500 K 、100 kPa 时,其m TS p ⎛⎫∂= ⎪∂⎝⎭ ( )(要求填入具体数值和单位)。
第三章练习题及参考答案复习思考题一、单项选择题1、材料采购途中的合理损耗应()。
A、由供应单位赔偿B、计入材料采购成本C、由保险公司赔偿D、计入管理费用2、在物价上升的情况下,采用( )计价可使期末库存材料的价值最接近现行市场价格。
A、先进先出法B、实际成本法C、加权平均法D、个别计价法3、原材料按计划成本核算时,在途材料在()账户余额中反映。
A、原材料B、材料采购C、在途物资D、生产成本4、某企业为增值税一般纳税人。
购入甲材料5 000吨,收到的增值税专用发票上标明:售价每吨1 200元,增值税额1 020 000元。
另发生运输费用60 000元,抵扣率7%,装卸费20 000元,途中保险费18 000元。
原材料运抵企业后,验收入库材料4996吨,运输途中发生的合理损耗4吨。
该原材料的入账价值为( )元。
A、6 078 000B、6 098 000C、6 093 800D、6 089 0005、某企业为一般纳税人,原材料采用计划成本核算,乙材料计划成本每吨为20元。
本期购进乙材料6 000吨,收到的增值税发票上标明,价款总额102 000元,增值税17 340元,另发生运杂费1 400元,途中保险费359元。
原材料运抵企业后验收入库5995吨,运输途中合理损耗5吨。
购进乙材料发生的成本差异为( )元。
A、-1099B、-16141C、-1199D、-162416、存货期末计价采用成本与可变现净值孰低法,体现的会计核算信息质量要求是( )。
A、谨慎性B、重要性C、可比性D、客观性7、某企业采用毛利率法计算发出存货的成本,2005年1月份实际毛利率30%,2月初的存货成本为160 000元,2月份购入存货成本为620 000元,销售收入为950 000元。
该企业2月份的存货成本为( )。
A、665 000B、495 000C、285 000D、115 0008、某商品流通企业期初库存商品成本为30万元,售价总额为43万元;当期购入商品的实际成本为67.5万元,售价总额为107万元;当期销售收入为110万元,在采用零售价法的情况下,该企业期末库存商品成本为( )万元。
习题3.1计算下列行列式:①5312--+a a ②212313121+----a a a解 ①5312--+a a =(a+2)(a-5)+3=a 2-3a-7②212313121+----a a a =(a-1)(a-1)(a+2)-3-12+2(a-1)-3(a-1)+6(a+2)= a 3+2a习题3.2求从大到小的n 阶排列(n n-1 … 2 1)的逆序数. 解 τ(n n-1 … 2 1)=(n-1)+(n-2)+…+1+0=2)1(-n n 习题3.31.在6阶行列式中,项a 23a 31a 42a 56a 14a 65和项a 32a 43a 14a 51a 66a 25应各带有什么符号?解 因为a 23a 31a 42a 56a 14a 65=a 14a 23a 31a 42a 56a 65,而τ(4 3 1 2 6 5)=3+2+0+0+1+0=6,所以项a 23a 31a 42a 56a 14a 65带有正号.又因为项a 32a 43a 14a 51a 66a 25=a 14a 25a 32a 43a 51a 66,而τ(4 5 2 3 1 6)=3+3+1+1+0+0=8,所以项a 32a 43a 14a 51a 66a 25带有正号. 2.计算:000400010002000300050000 解 因为a 15a 24a 33a 42a 51的逆序数为τ(5 4 3 2 1)=5×4/2=10,带有正号,所以000400010002000300050000=5×3×2×1×4=120 习题3.4计算:6217213424435431014327427246-解 6217213424435431014327427246-=6211003424431001014327100246-=100×621134244*********1246-=-294×105习题3.51.计算下列行列式:①1723621431524021----- ②6234352724135342------解 ①1723621431524021-----=1374310294111120001------=137410291111-----=-726②6234352724135342------=1035732130010313410------=0105731331310---- =05723133710----=-5×72337--=-1002. 计算下列n 阶行列式(n ≥2):①ab ba b a b a 000000000000 ②1210010010011110-n a a a③n n n n x x x x x x a a a a x a 1322113211000000000-----+④111)()1()()1()()1(111n a a a n a a a n a a a n n n n n n --------- 解 ① n n a b b a b a b a ⨯000000000000=)1()1(00000000000-⨯-⨯n n a b a b a b a a+)1()1(1000000000000)1(-⨯-+⨯-n n n b a b b ab b=a n+(-1)n+1b n② D n =1210010*********-n a a a=a n-1×D n-1+(-1)n+1×)1)(1(2100000000001111---n n n a a= a n-1D n-1+(-1)n+1×(-1)1+(n-1)×)2)(2(232100000000----n n n n a a a a=a n-1D n-1-a 1a 2…a n-2=a n-1(a n-2D n-2-a 1a 2…a n-3)-a 1a 2…a n-2 =a n-1a n-2D n-2-a n-1a 1a 2…a n-3-a 1a 2…a n-2 …= a n-1a n-2…a 2D 2-a n-1a n-2…a 3a 1-…-a n-1a n-2a 1a 2…a n-4-a n-1a 1a 2…a n-3-a 1a 2…a n-2= a n-1a n-2…a 21110a -a n-1a n-2…a 3a 1-…-a n-1a n-2a 1a 2…a n-4-a n-1a 1a 2…a n-3-a 1a 2…a n-2=-a n-1a n-2…a 2-a n-1a n-2…a 3a 1-…-a n-1a n-2a 1a 2…a n-4-a n-1a 1a 2…a n-3-a 1a 2…a n-2 =-∑---11211)...(n i in a a a a ③ D n =nn n n x x x x x x a a a a x a 1322113211000000000-----+=112111...)1()1(---++-⨯-n n n n n n D x x x x a =a n x 1x 2…x n-1+x n D n-1=a n x 1x 2…x n-1+x n (a n-1x 1x 2…x n-2+x n-1D n-2) =a n x 1x 2…x n-1+x n a n-1x 1x 2…x n-2+x n x n-1D n-2 …=a n x 1x 2…x n-1+x n a n-1x 1x 2…x n-2+…+x n x n-1…x 4a 3x 1x 2+x n x n-1…x 4x 3D 2=a n x 1x 2...x n-1+x n a n-1x 1x 2...x n-2+...+x n x n-1...x 4a 3x 1x 2+x n x n-1...x 4x 3[(a 1+x 1)x 2+a 2x 1] =)( (1)1121121∑=+--+ni n i i i n n x x a xx x x x x x④D n+1=111)()1()()1()()1(111n a a a n a a a n a a a n n n nn n ---------=nn n n n n n n a a a n a a a n a a a )1()1()()1()()1(111)1(1112)1(----------+=)1()]}1([)2)(1)]{(()2)(1[()1(2)1(---------+ n n n n=2!3!...n!3.计算下列n 阶行列式(n ≥1):①n a a a a ++++1111111111111111321②ax x x x x a x x x x a x a x x x x x a x n n nn ----- 321321321321解 ① D n =na a a a ++++1111111111111111321=na a a a +++++++11110111*********11321=1111111111111111321a a a ++++na a a a111011101110111321+++ =110010010321a a a +1-n n D a =a n D n-1-a 1a 2…a n-1=a n (a n-1D n-2-a 1a 2…a n-2)-a 1a 2…a n-1 =a n a n-1D n-2-a n a 1a 2…a n-2-a 1a 2…a n-1 =n ni n i i a a a a a aa 211111)(+∑=+-=⎪⎪⎭⎫ ⎝⎛+∑=ni i n a a a a 12111 (a i ≠0) ②D n =a x x x x x a x x x x a x a x x x x x a x n n n n -----321321321321=ax x x x x a x x x x a x a x x x x x a x n n n n -+-+--+- 321321321321000=n n n n x x x x x a x x x x a x a x x x x x a x 321321321321----+ax x x a x x x a x a x x x x a x -----321321321321000 =x n (-a)n-1(x 1+x 2+…+x n )+(-a)n4.证明:n 阶行列式yz z x y y x z xzz zz y y x z z yy y x z yy y y x nn ----=)()( 其中z ≠y .解 D n =xzz zzy y x z z yy y x z x y zx00--=(x-z)D n-1-(y-x))1()1(-⨯-n n x zz zy y x zy y y z=(x-z)D n-1-(y-x)z)1()1(111-⨯-n n x z z y y x y yy=(x-z)D n-1-(y-x)z)1()1(10010001-⨯-----n n y x yz y z y x=(x-z)D n-1-(y-x)z(x-y)n-2=(x-z)D n-1+z(x-y)n-1即有D n =(x-z)D n-1+z(x-y)n-1(1)又D n =xzz zy y x z yy y x x z yy y y y x--=(x-y)D n-1-(z-x))1()1(-⨯-n n x zz zy y x zy y y y=(x-y)D n-1-(z-x)y)1()1(1111-⨯-n n x z z z yy x z=(x-y)D n-1-(z-x)y)1()1(001111-⨯-----n n z x z y z y z x=(x-y)D n-1-(z-x)y(x-z)n-2即有D n =(x-y)D n-1+y(x-z)n-1(2) 联立式(1)和式(2)得yz z x y y x z xzz zzy y x z z yy y x z yy y y x nn ----=)()( 习题3.61.设A,B,P ∈Mat n ×n (F),并且P 是可逆的,证明:如果B=P -1AP ,则|B|=|A|.证 因为|P -1||P|=1,所以|B|=|P -1AP|=|P -1||A||P|=|A|. 2*.仿照例3.6.1,试用分块初等变换,证明定理3.6.1. 证 设A ,B 都是n ×n 矩阵,则nE BA -0=B A B A A E B n n n n=-=--+)1(0)1(另一方面,对nE BA -0的第2行小块矩阵乘以A 加到第一行上去,有nE BA -0=AB E BAB n=0所以B A AB =.习题3.71.求下列矩阵的伴随矩阵和逆矩阵①⎪⎪⎭⎫⎝⎛--1112 ②⎪⎪⎪⎭⎫ ⎝⎛--325436752解 ①设原矩阵为A ,则A 11=-1,A 21=-1,A 12=1,A 22=2,伴随矩阵A *=⎪⎪⎭⎫⎝⎛--2111,|A|=-2+1=-1,所以,A -1=⎪⎪⎭⎫ ⎝⎛---211111=⎪⎪⎭⎫ ⎝⎛--2111②设原矩阵为A ,则A 11=3243--=-9+8=-1,A 21=3275---=-(-15+14)=1,A 31=4375=20-21=-1,A 12=3546--=38,A 22=3572-=-41,A 32=4672-=34, A 13=2536-=-27,A 23=2552--=29,A 33=3652=-24伴随矩阵A *=⎪⎪⎪⎭⎫ ⎝⎛-----242927344138111,|A|=-18-84+100-105+16+90=-1,所以,A -1=⎪⎪⎪⎭⎫ ⎝⎛------24292734413811111=⎪⎪⎪⎭⎫ ⎝⎛----2429273441381112.证明:上三角形矩阵是可逆矩阵的充分必要条件是:它的主对角线元全不为零.证 因为矩阵可逆的充分必要条件是它的行列式不为零,而上三角形矩阵的行列式等于它的主对角线上所有元的乘积,所以上三角形矩阵的行列式不为零的充分必要条件是:它的主对角线元全不为零,故上三角形矩阵可逆矩阵的充分必要条件是:它的主对角线元全不为零.3.设A 是n ×n 矩阵.证明:A 是可逆的,当且仅当A *也是可逆的.证 因为 AA *=|A|E ,两边取行列式得|A||A *|=|A|n.若A 可逆,则A 的行列式|A|≠0,从而有|A *|=|A|n-1≠0,所以A *可逆.反之,若A *可逆,设A *的逆阵为(A *)-1.用反证法,假设A 不可逆,则A 的行列式|A|=0,所以AA *=|A|E=0,对AA *=0两边同时右乘(A *)-1,得A=0,从而A 的任一n-1阶子式必为零,故A *=0,这与A *可逆相矛盾,因此A 可逆. 4.证明定理3.7.2的推论1.推论1的描述:设A 是分块对角矩阵,A=diag(A 1,A 2,…,A s ),证明:A 可逆当且仅当A 1,A 2,…,A s 均可逆,并且A -1=diag(A 1-1,A 2-1,…,A s -1).证 A 可逆,当且仅当A 的行列式|A|≠0,而|A|=|A 1||A 2|…|A s |,所以|A|≠0当且仅当|A 1|,|A 2|,…,|A s |都不为零,即A 1,A 2,…,A s 均可逆.令B=diag(A 1-1,A 2-1,…,A s -1),则有AB=⎪⎪⎪⎪⎪⎭⎫ ⎝⎛S A A A21⎪⎪⎪⎪⎪⎭⎫ ⎝⎛---11211s A A A =⎪⎪⎪⎪⎪⎭⎫⎝⎛S E E E21=E 故A -1=diag(A 1-1,A 2-1,…,A s -1).4.设A=⎪⎪⎪⎭⎫⎝⎛333231232221131211a a aa a a a a a 是实矩阵(实数域上的矩阵),且a 33=-1.证明:如果A 的每一个元都等于它的代数余子式,则|A|=1.证 如果A 的每一个元都等于它的代数余子式,则A 的伴随矩阵A *=⎪⎪⎪⎭⎫ ⎝⎛332313322212312111a a a a a a a a a =A T .所以|A *|=|A|,又AA *=|A|E ,两边取行列式得|A|2=|A|3. 由a 33=-1,得AA *=⎪⎪⎪⎭⎫ ⎝⎛333231232221131211a a aa a a a a a ⎪⎪⎪⎭⎫ ⎝⎛332313322212312111a a a a a a a a a =⎪⎪⎪⎭⎫ ⎝⎛-12313322212312111a a a a a a a a ⎪⎪⎪⎭⎫⎝⎛-12313322212312111a a a a a a a a =⎪⎪⎪⎭⎫ ⎝⎛++1232231a a =⎪⎪⎪⎭⎫ ⎝⎛||000||000||A A A比较最后一个等式两端第3行3列的元素知|A|=a 312+a 322+1≠0,对|A|2=|A|3两边同时除以|A|2得|A|=1.6.设A=(a ij )是n ×n 可逆矩阵,有两个线性方程组(Ⅰ)⎪⎪⎪⎩⎪⎪⎪⎨⎧=+++=+++=+++=+++u x c x c x c bx a x a x a b x a x a x a b x a x a x a n n nn nn n n n n n n (221122112222212111212111)(Ⅱ)⎪⎪⎪⎩⎪⎪⎪⎨⎧=+++=+++=+++=+++vx b x b x b cx a x a x a c x a x a x a c x a x a x a n n nn nn n n n n n n (221122112222211211221111)如果(Ⅰ)有解.证明:当且仅当u =v 时,(Ⅱ)有解.证 设方程组(Ⅰ)的解为x 1*, x 2*,…, x n *,代入方程组(Ⅰ)得(Ⅲ)⎪⎪⎪⎩⎪⎪⎪⎨⎧=+++=+++=+++=+++ux c x c x c bx a x a x a b x a x a x a b x a x a x a n n n n n nnn n n n n **2*1**2*12*2*22*211*1*12*11................................................ (212)12121 当u =v 时,因为 A=(a ij )是n ×n 可逆矩阵,A 的行列式不等于零,根据克莱姆法则,方程组(Ⅱ)的前n 个方程作为一个线性方程组,它有唯一解,记该解为x 1**, x 2**,…, x n **,代入方程组(Ⅱ)的前n 个方程中得(Ⅳ)⎪⎪⎪⎩⎪⎪⎪⎨⎧=+++=+++=+++=+++----nnn n n n nn n n n n c x a x a x a cx a x a x a c x a x a x a c x a x a x a n n nn ****2**11**1**12**112**2**22**121**1**21**11......................................................21212121 对等式组(Ⅳ)中第1个等式的两端同时乘以x 1*,第2个等式的两端同时乘以 x 2*,…, 第n个等式的两端同时乘以 x n *,然后将n 各等式的左边全部相加,也将右边全部相加,并利用(Ⅲ)式,可得b 1x 1**+b 2x 2**+…+b n x n **=c 1x 1*+ c 2x 2*+…+ c n x n *=u由u =v ,得b 1x 1**+b 2x 2**+…+b n x n **=u即x 1**, x 2**,…, x n **也满足(Ⅱ)中最后一个方程.所以方程组(Ⅱ)有解.反之,若方程组(Ⅱ)有解,设其解为x 1**, x 2**,…, x n **,代入(Ⅱ)得到(Ⅴ)⎪⎪⎪⎩⎪⎪⎪⎨⎧=+++=+++=+++=+++-vx b x b x b cx a x a x a c x a x a x a c x a x a x a n n n n n n nn n n n n ****2**11****2**12**2**22**121**1**21**11......................................................21212121 对等式组(Ⅲ)中第1个等式的两端同时乘以x 1**,第2个等式的两端同时乘以 x 2**,…,第n 个等式的两端同时乘以 x n **,然后将n 各等式的左边全部相加,也将右边全部相加,并利用(Ⅴ)式,可得c 1x 1*+c 2x 2*+…+c n x n *=b 1x 1**+ b 2x 2**+…+ b n x n **将上式左端与(Ⅴ)式中最后一个等式比较,将上式右端与(Ⅲ)式中最后一个等式比较,得 u =v .7.设A 是n ×n 矩阵.证明:|A *|=|A|n-1证 因为AA *=|A|E ,两边取行列式得 |A||A *|=|A|n .如果|A|≠0,两边除以|A|,得|A *|=|A|n-1如果|A|=0,也可写成|A *|=|A|n-1,总之,有|A *|=|A|n-1成立.。
1.链式栈与顺序栈相比,一个比较明显的优点是 ( )。
A. 插入操作更加方便B. 通常不会出现栈满的情况C. 不会出现栈空的情况D. 删除操作更加方便2.在一个顺序存储的循环队列中,队头指针指向队头元素的 ( )。
A. 前一个位置B. 后一个位置C. 队头元素位置D. 队尾元素的前一位置3.设S表示进栈,X表示出栈,则将CABDB执行操作序列SSXXSSXXSX后得到ACDBB 。
4.设循环队列中数组的下标范围是0至m-1,其头尾指针分别为f和r,则其元素个数为。
A. r-fB. r-f+1C. (r-f)%m+1D. (r-f+m)%m5.判定一个循环队列Q(数组元素为m个)队满的条件为。
A.Q.front==Q.rear B. Q.front!=Q.rearC. Q.front==(Q.rear+1)%m0 D. Q.front!=(Q.rear+1)%m6.长度为m的循环队列q的队满条件为q.front==(q.rear+1)%m,队空条件为q.front==q.rear。
7.队列是一种特殊的线性表,它的特点是后进先出。
(错)8.栈和队列的存储方式,既可以是顺序方式,又可以是链式方式。
(对)9. 循环队列采用的存储结构为顺序存储结构,其引入的目的是为了克服__假溢出的现象 _____。
10.有六个元素6,5,4,3,2,1 的顺序进栈,问下列哪一个不是合法的出栈序列?()A. 543612B. 453126C. 346521D. 23415611. 栈和队列都是线性表,只是在插入和删除时受到了一些限制。
(对)12. 链栈通常不会出现满的情况。
(对)13.往顺序栈中插入一个元素时,栈顶指针是( )。
A) 加1 B) 减1 C) 不变 D) 清014.栈和队列的共同点是( )。
A)都是先进后出 B)都是先进先出C)只允许在端点处插入和删除元素 D)没有共同点15.为解决计算机主机与打印机之间速度不匹配问题,通常设置一个打印缓冲区,主机将要打印的数据依次写入该缓冲区,而打印机则依次从该缓冲区中取出数据,该缓冲区的逻辑结构应该是:A.栈B. 图C.树D. 队列16.线性表、栈和队列都是( 线性 )结构,可以在线性表的( 任意 )位置插入和删除元素;对于栈只能在( 栈顶 )插入和删除元素;对于队列只能在( 队尾 )插入和( 队头 )删除元素。
第三章习题参考答案一、填空题1、指令格式是由操作码和操作数所组成,也可能仅由操作码组成。
2、若用传送指令访问MCS-51的程序存储器,它的操作码助记符应为MOVC 。
3、若用传送指令访问MCS-51的片内数据存储器,它的操作码助记符应为MOV 。
4、若访问MCS-51的片外数据存储器,它的操作码助记符应为MOVX 。
5、累加器(A)=80H,执行完指令ADD A,#83H后,进位位C= 1 。
6、执行ANL A,#0FH指令后,累加器A的高4位= 0000 。
7、JZ rel的操作码地址为1000H,rel=20H,它的转移目的地址为1022H 。
8、JBC 00H,rel 操作码的地址为2000H,rel=70H,它的转移目的地址为2073H 。
9、累加器(A)=7EH,(20H)= #04H,MCS-51执行完ADD A,20H指令后= 0 。
10、MOV PSW,#10H是将MCS-51的工作寄存器置为第 2 组。
11、指令LCALL 37B0H,首地址在2000H,所完成的操作是2003H 入栈,37B0H →PC。
12、MOVX A,@DPTR源操作数寻址方式为寄存器间接寻址。
13、ORL A,#0F0H是将A的高4位置1,而低4位保持不变。
14、SJMP rel的指令操作码地址为0050H,rel=65H,那么它的转移目标地址为 00B7H 。
15、设DPTR=2000H,(A)=80H,则MOVC A,@A+DPTR的操作数的实际地址为2080H 。
16、MOV C,20H源寻址方式为位寻址。
17、在直接寻址方式中,只能使用8 位二进制数作为直接地址,因此其寻址对象只限于片内RAM 。
18、在寄存器间接寻址方式中,其“间接”体现在指令中寄存器的内容不是操作数,而是操作数的地址。
19、在变址寻址方式中,以 A 作变址寄存器,以PC 或DPTR 作基址寄存器。
20、假定累加器A中的内容为30H,执行指令1000H:MOVC A,@A+PC后,把程序存储器1031H 单元的内容送入累加器A中。