CCNA第二学期第二章考试答案
- 格式:doc
- 大小:867.00 KB
- 文档页数:11

1. Which statements correctly identify the role of intermediary devices in the network? (Choose three.)determine pathways for data 确定数据通路initiate data communicationsretime and retransmit data signals 重分发originate the flow of datamanage data flows 管理数据final termination point for data flow2. Select the statements that are correct concerning network protocols. (Choose three.)define the structure of layer specific PDU'sdictate how to accomplish layer functionsoutline the functions necessary for communications between layers limit the need for hardware compatibilityrequire layer dependent encapsulationseliminate standardization among vendors3. What are two functions of encapsulation? (Choose two.)tracks delay between end devicesenables consistent network paths for communicationallows modification of the original data before transmissionidentifies pieces of data as part of the same communicationensures that data pieces can be directed to the correct receiving end device4. What is a primary function of the trailer information added by the data link layer encapsulation?supports error detection 支持错误检测‘ensures ordered arrival of dataprovides delivery to correct destinationidentifies the devices on the local networkassists intermediary devices with processing and path selection5. Which statements correctly identify the role of intermediary devices in the network? (Choose three.)determine pathways for datainitiate data communicationsretime and retransmit data signalsoriginate the flow of datamanage data flowsfinal termination point for data flow6. What is a PDU?corruption of a frame during transmissiondata reassembled at the destinationretransmitted packets due to lost communicationa layer specific encapsulation 一个具体的封装层7. Which characteristic correctly refers to end devices in a network?manage data flowsoriginate data flow 原数据流retime and retransmit data signalsdetermine pathways for data8.Refer to the exhibit. "Cell A" at IP address 10.0.0.34 has established an IP session with "IP Phone 1" at IP address 172.16.1.103. Based upon the graphic, which device type best describes the function of wireless device "Cell A?"the destination devicean end devicean intermediate devicea media device9.Refer to the exhibit. Which three labels correctly identify the network types for the network segments that are shown?(Choose three.)Network A -- WANNetwork B -- WANNetwork C -- LANNetwork B -- MANNetwork C -- WANNetwork A -- LAN10. Which three statements best describe a Local Area Network (LAN)? (Choose three.)A LAN is usually in a single geographical area.The network is administered by a single organization.The connection between segments in the LAN is usually through a leased connection.The security and access control of the network are controlled by a service provider.A LAN provides network services and access to applications for users within a common organization.Each end of the network is generally connected to a Telecommunication Service Provider (TSP).11.Refer to the exhibit. Which networking term describes the data interleaving process represented in the graphic?pipingPDUstreamingmultiplexingencapsulation12. What is the primary purpose of Layer 4 port assignment?to identify devices on the local mediato identify the hops between source and destinationto identify to the intermediary devices the best path through the network to identify the source and destination end devices that are communicating to identify the processes or services that are communicating within the end devices13. What device is considered an intermediary device?1.file serve2.IP phone ptop 4.printer 5.switch14.Refer to the exhibit. Which term correctly identifies the device type that is included in the area B? sourceendtransferintermediary 中间设备15.Refer to the exhibit. What type of network is shown?WANMANLANWLAN16. Which layer encapsulates the segment into packets?physicaldata linknetwork 网络层封装的是数据包transport17. What can be identified by examining the network layer header?the destination device on the local mediathe destination host address 网络层头部封装目的主机的地址the bits that will be transferred over the mediathe source application or process creating the data18. What is the purpose of the TCP/IP Network Access layer?path determination and packet switchingdata presentationreliability, flow control, and error detectionnetwork media control 接入层控制网络媒体the division of segments into packets19. During the encapsulation process, what occurs at the data link layer? No address is added.The logical address is added.The physical address is added. 数据链路层添加一个物理地址The process port number is added.20.Refer to the exhibit. Which set of devices contains only end devices? A, C, DB, E, G, HC, D, G, H, I, JD, E, F, H, I, JE, F, H, I, J21. What is the proper order of the layers of the OSI model from the highest layer to the lowest layer?4physical, network, application, data link, presentation, session, transportapplication, physical, session, transport, network, data link, presentationapplication, presentation, physical, session, data link, transport, networkapplication, presentation, session, transport, network, data link, physicalpresentation, data link, session, transport, network, physical, application22. Which two layers of the OSI model have the same functions as the TCP/IP model Network Access Layer? (Choose two.)34NetworkTransportPhysicalData Link TCP/IP 工作在第一层和第二层Session。

yy1 ・ Refer to the exhibit・ Identify the devices labeled A, B, C, and D in the network physical documentation. 匚A=bridge, B=switch, C=router, D=hubK A=bridge, B=hub, C=router, D=switchC A=bridge, B=router, C=hub, D=switchc A=hub, B=bridge, C=router, D=switch2 The central hub has malfunctioned in the network. As a result, the entire network is down. Which type of physical network topology is implemented?匚busE starC ring匚mesh3. A switch has failed in the network. As a result, only one segment of the network is down. Which type of physical network topology is implemented?C busC ring匚starE extended star4. Which three features apply to LAN connections? (Choose three.)厂operate using serial in terfacesV make network connection using a hubV limited to operation over small geographic areas厂 provide part-time connectivity to remote servicesV typically operate under local administrative control厂provide lower bandwidth services compared to WANs5. What is one advantage of defining network communication by the seven layers of the OSI model? 【:It in creases the ban dwidth of a n etwork.E It makes networking easier to learn and understand・It eliminates many protocol restrictions.匚It increases the throughput of a network.c It reduces the need for testing network connectivity.6. What makes it easier for different networking vendors to design software and hardware that willin teroperate?E OSI modelc proprietary desig ns匚IP addressing schemec standard logical topologies匚standard physical topologies7. Which term describes the process of adding headers to data as it moves down OSI layers?匚division匚encoding匚separation匚segmentationE encapsulation8. What is the term used to describe the transport layer protocol data unit?匚bits c packetsE segments匚framesc data streams9. Which of the following are layers of the TCP/IP model? (Choose three.)▽ Applicati onr PhysicalV Internet0 Network Access厂Prese ntation10. Which of the following are data link layer encapsulation details? (Choose two.)0 A header and trailer are added・厂Data is con verted into packets ・V Packets are packaged into frames・厂Frames are divided into segments.厂Packets are changed into bits for Internet travel.11. Which layer of the OSI model provides network services to processes in electronic mail and file transfer programs?匚data link匚transport匚n etworkE application12. Which two features apply to WAN connections? (Choose two.)V operate using serial interfacesP make network connection using a hub厂limited to operation over small geographic areasI- typically operate under local administrative control▽provide lower bandwidth services compared to LANs13. Which of the following are ways that bandwidth is commonly measured? (Choose three.)厂GHzps▽kbpsV Mbps厂Nbps厂MHzpsV Gbps14. Refer to the following list. Choose the correct order of data encapsulation when a device sends information. segments bits packetsdata frames匚1 -3-5-4-2C 2- 1-3-5-4C 2-4-3-5-1匚4-3-1-2-5E 4-1 -3-5-2C 3-5-1-2-415. Which of the following are factors that determine throughput? (Choose two.)厂types of passwords used on servers厂type of Layer 3 protocol usedV n etwork topologywidth of the network cable0 number of users on the network16. Refer to the exhibit・ Which column shows the correct sequenee of OSI model layers?E D17. Which layer of the OSI model provides connectivity and path selection between two end systems where routing occurs?c physical layer匚data link layerE network layer匚transport layer18. Which best describes the function of the physical layer?E Defines the electrical and functional specifications for the link between end systems・匚Provides reliable transit of data across a physical link.匚Provides connectivity and path selection between two end systems・匚Concerned with physical addressing, network topology and media access.。
CCNA 2 - Chapter 11What is one advantage of using the cut-through switching method instead of the store-and-forward switching method?has a positive impact on bandwidth by dropping most of the invalid framesmakes a fast forwarding decision based on the source MAC address of the framehas a lower latency appropriate for high-performance computing applications*provides the flexibility to support any mix of Ethernet speeds2A network designer must provide a rationale to a customer for a design which will move an enterprise from a flat network topology to a hierarchical network topology. Which two features of the hierarchical design make it the better choice? (Choose two.)reduced cost for equipment and user trainingless required equipment to provide the same performance levelssimpler deployment for additional switch equipment*easier to provide redundant links to ensure higher availability*lower bandwidth requirements3What are two advantages of modular switches over fixed-configuration switches? (Choose two.)availability of multiple ports for bandwidth aggregationlower forwarding ratesneed for fewer power outlets*lower cost per switchincreased scalability*4Refer to the exhibit. Consider that the main power has just been restored. PC1 asks the DHCP server for IPv4 addressing. The DHCP server sends it an IPv4 address. While PC2 is still booting up, PC3 issues a broadcast IPv4 DHCP request. To which port will SW1 forward this request?to Fa0/1, Fa0/2, and Fa0/4 onlyto Fa0/1, Fa0/2, Fa0/3, and Fa0/4to Fa0/1 and Fa0/2 onlyto Fa0/1, Fa0/2, and Fa0/3 only*to Fa0/1 only5What is one function of a Layer 2 switch?forwards data based on logical addressinglearns the port assigned to a host by examining the destination MAC addressduplicates the electrical signal of each frame to every portdetermines which interface is used to forward a frame based on the destination MAC address*6Refer to the exhibit. Fill in the blank.There are ” 12” collision domains in the topology.7What is a collapsed core in a network design?a combination of the functionality of the access, distribution, and core layersa combination of the functionality of the access and core layersa combination of the functionality of the distribution and core layers*a combination of the functionality of the access and distribution layers 8What are two reasons a network administrator would segment a network with a Layer 2 switch? (Choose two.)to enhance user bandwidth*to eliminate virtual circuitsto create more broadcast domainsto isolate traffic between segments*to isolate ARP request messages from the rest of the networkto create fewer collision domains9Refer to the exhibit.How is a frame sent from PCA forwarded to PCC if the MAC address table on switch SW1 is empty?SW1 forwards the frame directly to SW2. SW2 floods the frame to all ports connected to SW2, excluding the port through which the frame entered the switch.SW1 floods the frame on all ports on the switch, excluding the interconnected port to switch SW2 and the port through which the frame entered the switch.SW1 floods the frame on all ports on SW1, excluding the port through which the frame entered the switch.*SW1 drops the frame because it does not know the destination MAC address.10Place the options in the following order:[+] appropriate for high performance computing applications[+] forwarding process can begin after receiving the destination address [+] may forward invalid frames[#] error checking before forwarding[#] forwarding process only begin after receiving the entire frame [#] only forward valid frames[+] Order does not matter within this group.[#] Order does not matter within this group.11What is a basic function of the Cisco Borderless Architecture distribution layer?aggregating Layer 3 routing boundaries*aggregating all the campus blocksacting as a backboneproviding access to the user12ABC, Inc. has about fifty hosts in one LAN. The administrator would like to increase the throughput of that LAN. Which device will increase the number of collision domains and thereby increase the throughput of the LAN?hubhostNICswitch*13What does the term “port density” represent for an Ethernet switch?the numbers of hosts that are connected to each switch portthe speed of each portthe memory space that is allocated to each switch portthe number of available ports*14Which type of transmission does a switch use when the destination MAC address is not contained in the MAC address table?anycastunicastbroadcast*multicast15What is a basic function of the Cisco Borderless Architecture access layer?aggregates Layer 3 routing boundariesprovides high availabilityaggregates Layer 2 broadcast domainsprovides access to the user*16What information is added to the switch table from incoming frames?source MAC address and incoming port number*destination MAC address and incoming port numberdestination IP address and incoming port numbersource IP address and incoming port number17Fill in the blank.A “converged” network is one that uses the same infrastructure to carry voice, data, and video signals.18An administrator purchases new Cisco switches that have a feature called StackPower. What is the purpose of this feature?It enables many switches to be connected with a special fiber-optic power cable to provide higher bandwidth.It enables the sharing of power among multiple stackable switches.*It enables many switches to be connected to increase port density.It enables many switches to be physically stacked in an equipment rack.It enables AC power for a switch to be provided from a powered patch panel.19Which switch form factor should be used when large port density, fault tolerance, and low price are important factors?fixed-configuration switchmodular switchstackable switch*rackable 1U switch20Refer to the exhibit. Fill in the blank.There are ” 5 ”CCNA 2 - Chapter 2Posted by beotron at 8:59 PM1. A static route that points to the next hop IP will have what administrative distance and metric in the routing table?• administrative distance of 0 and metric of 0• administrative distance of 0 and metric of 1• administrative distance of 1 and metric of 0• administrative distance of 1 and metric of 12. What address can be used to summarize networks 172.16.1.0/24, 172.16.2.0/24, 172.16.3.0/24, and 172.16.4.0/24?• 172.16.0.0/21• 172.16.1.0/22• 172.16.0.0 255.255.255.248• 172.16.0.0 255.255.252.03. The routers in the diagram use the subnet assignments shown. What is the most efficient route summary that can be configured on Router3 to advertise the internal networks to the cloud?• 192.1.1.0/26 and 192.1.1.64/27• 192.1.1.128/25• 192.1.1.0/23 and 192.1.1.64/23• 192.1.1.0/24• 192.1.1.0/25• 192.1.1.0/24 and 192.1.1.64/244. Refer to the exhibit. What is the significance of the /8 in the route to the 10.0.0.0 network?• It indicates that there are 8 hops between this router and the 10.0.0.0 network.• It represents the time, in milliseconds, it takes for a ping to reply when sent to the 10.0.0.0 network.• It indicates that there are 8 subnets in the destination network to which the router can forward packets.• It indicates the number of consecutive bits, from the left, in the destination IP address of a packet that must match 10.0.0.0 to use that route.5. Refer to the exhibit. How will packets destined to the 172.16.0.0 network be forwarded?• Router1 will perform recursive lookup and packet will exit S0/0.• Router1 will perform recursive lookup and packet will exit S0/1.• There is no matching interface associated with network 172.16.0.0 so packets will be dropped.• There is no matching interface associated with network 172.16.0.0 so packets will take gateway of last resort and exit out S0/2.6. A network administrator enters the following command into Router1: ip route 192.168.0.0255.255.255.0 S0/1/0. Router1 then receives a packet that is destined for 192.168.0.22/24. After finding the recently configured static route in the routing table, what does Router1 do next to process the packet? • drops the packet because the destination host is not listed in the routing table• looks up the MAC address of the S0/1/0 interface to determine the destination MAC address of the new frame• performs a recursive lookup for the IP address of the S0/1/0 interface before forwarding the packet• encapsulates the packet into a frame for the WAN link and forwards the packet out the S0/1/0 interface7. Refer to the exhibit. Given the output in the exhibit, how would a clock rate be determined for this link? • The rate would be negotiated by both routers.• A rate would not be selected due to the DCE/DTE connection mismatch.• The rate configured on the DTE determines the clock rate.• The rate configured on the DCE determines the clock rate.8. Refer to the exhibit. Which set of commands will configure static routes that will allow the WinterPark and the Altamonte routers to deliver packets from each LAN and direct all other traffic to the Internet? • WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 0.0.0.0 0.0.0.0 s0/1• WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 198.18.222.0 255.255.255.255 s0/1• WinterPark(config)# ip route 172.191.67.0 255.255.255.0 192.168.146.1• WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2• WinterPark(config)# ip route 172.191.67.0 255.255.255.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 0.0.0.0 0.0.0.0 s0/09. Hosts on two separate subnets cannot communicate. The network administrator suspects a missing route in one of the routing tables. Which three commands can be used to help troubleshoot Layer 3 connectivity issues? (Choose three.)• ping• show arp• traceroute• show ip route• show interface• show cdp neighbor d etail10. Refer to the exhibit. A company network engineer is assigned to establish connectivity between the two Ethernet networks so that hosts on the 10.1.1.0/24 subnet can contact hosts on the 10.1.2.0/24 subnet. The engineer has been told to use only static routing for these company routers. Which set of commands will establish connectivity between the two Ethernet networks?• R1(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.1R2(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.2• R1(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.2R2(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.1• R1(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.2R2(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.1• R1(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.1R2(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.2• R1(config)# ip route 0.0.0.0 0.0.0.0 10.1.2.1R2(config)# ip route 0.0.0.0 0.0.0.0 10.1.1.111. Which of the following are displayed by the Router# show cdp neighbors command? (Choose three.) • load• platform• reliability• holdtime• local interface12. Refer to the exhibit. What two commands are required to provide connectivity between the192.168.1.0 and 10.0.0.0 networks without requiring recursive lookup? (Choose two.)• A(config)# ip route 10.0.0.0 255.0.0.0 s 0/1/0• A(config)# ip route 10.0.0.0 255.0.0.0 172.16.40.2• A (config)# ip route 10.0.0.0 255.0.0.0 s 0/0/0• B(config)# ip route 192.168.1.0 255.255.255.0 s 0/0/0• B (config)# ip route 192.168.1.0 255.255.255.0 172.16.40.1• B(config)# ip route 192.168.1.0 255.255.255.0 s 0/1/013. Refer to the exhibit. What two commands will change the next-hop address for the 10.0.0.0/8 network from 172.16.40.2 to 192.168.1.2? (Choose two.)• A(config)# no network 10.0.0.0 255.0.0.0 172.16.40.2• A(config)# no ip address 10.0.0.1 255.0.0.0 172.16.40.2• A(config)# no ip route 10.0.0.0 255.0.0.0 172.16.40.2• A(config)# ip route 10.0.0.0 255.0.0.0 s0/0/0• A(config)# ip route 10.0.0.0 255.0.0.0 192.168.1.214. What happens to a static route entry in a routing table when the outgoing interface is not available? • The route is removed from the table.• The router polls neighbors for a replacement route.• The route remains in the table because it was defined as static.• The router redirects the static route to compensate for the loss of the next hop device.15. A router has one static route to each destination network. Which two scenarios would require an administrator to alter the static routes that are configured on that router? (Choose two.)• The destination network no longer exists.• The destination network is moved to a different interface on the same router.• The path between the source and destination is upgraded with a higher bandwidth link.• A topology change occurs where the exi sting next-hop address or exit interface is not accessible.• The remote destination network interface has to be down for 15 minutes of maintenance.16. Why is it advisable to enter a next-hop IP address when creating a static route whose exit interface is an Ethernet network?• Adding the next-hop address eliminates the need for the router to do any lookups in the routing table before forwarding a packet.• In a multi-access network, the router cannot determine the next-hop MAC address for the Ethernet frame without a next-hop address.• Using a next-hop address in a static route provides a route with a lower metric.• In multi-access networks, using a next-hop address in a static route makes that route a candidate default route.17. The output of the Router# show interfaces serial 0/1 command displays the following:• Serial0/1 is up, line protocol is down.• What is the most likely cause for the line protocol being down?• Serial0/1 is shutdown.• There is no cable connecting the routers.• The remote rout er is using serial 0/0.• No clock rate has been set.18. Refer to the exhibit. Which static route should be configured on Router1 so that host A will be able to reach host B on the 172.16.0.0 network?• ip route 192.168.0.0 172.16.0.0 255.255.0.0• ip rou te 172.16.0.0 255.255.0.0 192.168.0.1• ip route 172.16.0.0 255.255.0.0 S0/0/1• ip route 172.16.0.0 255.255.0.0 S0/0/019. What two devices are responsible for converting the data from the WAN service provider into a form acceptable by the router? (Choose two).• the serial port of the router• a modem• a switch• the ethernet port of the router• a CSU/DSU device• a DTE device20. Which of the following is true regarding CDP and the graphic shown?• CDP running on Router D will gather information about routers A, B, C, and E.• By default, Router A will receive CDP advertisements from routers B and C.• If routers D and E are running different routing protocols, they will not exchange CDP information.• Router E can use CDP to identify the IOS running on Router B.21. Which two statements describe functions or characteristics of CDP? (Choose two.)• It starts up automatically and allows the device to detect directly connected neighbor devices that use CDP.• It operates at the network layer and allows two systems to learn about each other.• It creates a topology map of the entire network.• It allows systems to learn about each other even if different network layer protocols are configured.• It forwards advertisements about routes for faster convergence.22. Which piece of information is available from examining the output of the command show ip interface brief?• Interface speed and duplex• Interface MTU• Errors• Interface MAC address• Interface IP addressCCNA 2 - Chapter 31A network administrator is determining the best placement of VLAN trunklinks. Which two types of point-to-point connections utilize VLAN trunking? (Choose two.)between two switches that share a common VLANbetween a switch and a server that has an 802.1Q NIC*between a switch and a client PCbetween a switch and a network printerbetween two switches that utilize multiple VLANs*2What happens to a port that is associated with VLAN 10 when the administrator deletes VLAN 10 from the switch?The port automatically associates itself with the native VLAN. The port creates the VLAN again.The port goes back to the default VLAN.The port becomes inactive.*3Refer to the exhibit. Interface Fa0/1 is connected to a PC. Fa0/2 is a trunk link to another switch. All other ports are unused. Which security best practice did the administrator forget to configure?Configure all unused ports to a ‘black-hole’ VLAN that is not used f or anything on the network.Disable autonegotiation and set ports to either static access or static trunk.Change the native VLAN to a fixed VLAN that is distinct from all user VLANs and to a VLAN number that is not VLAN 1.All user ports are associated with VLANs distinct from VLAN 1 and distinct from the ‘black-hole’ VLAN.*4Which command is used to remove only VLAN 20 from a switch?no switchport access vlan 20delete flash:vlan.datno vlan 20*delete vlan.dat5A Cisco Catalyst switch has been added to support the use of multiple VLANs as part of an enterprise network. The network technician finds it necessary to clear all VLAN information from the switch in order to incorporate a new network design. What should the technician do to accomplish this task?Erase the startup configuration and reboot the switch.Erase the running configuration and reboot the switch.Delete the startup configuration and the vlan.dat file in the flash memory of the switch and reboot the switch.*Delete the IP address that is assigned to the management VLAN and reboot the switch.6What is the effect of issuing a switchport access vlan 20 command on the Fa0/18 port of a switch that does not have this VLAN in the VLAN database?VLAN 20 will be created automatically.*The command will have no effect on the switch.Port Fa0/18 will be shut down.An error stating that VLAN 20 does not exist will be displayed and VLAN 20 is not created.Which command displays the encapsulation type, the voice VLAN ID, and the access mode VLAN for the Fa0/1 interface?show mac address-table interface Fa0/1show interfaces Fa0/1 switchport*show interfaces trunkshow vlan brief8Place the options in the following order:- not scored -dynamic autononegotiatedynamic desirabletrunk9Port Fa0/11 on a switch is assigned to VLAN 30. If the command no switchport access vlan 30 is entered on the Fa0/11 interface, what will happen?Port Fa0/11 will be returned to VLAN 1.*VLAN 30 will be deleted.An error message would be displayed.Port Fa0/11 will be shutdown.What must the network administrator do to remove Fast Ethernet port fa0/1 from VLAN 2 and assign it to VLAN 3?Enter the no vlan 2 and the vlan 3 commands in global configuration mode. Enter the switchport trunk native vlan 3 command in interface configuration mode.Enter the switchport access vlan 3 command in interface configuration mode.*Enter the no shutdown in interface configuration mode to return it to the default configuration and then configure the port for VLAN 3.11Which two Layer 2 security best practices would help prevent VLAN hopping attacks? (Choose two.)Disable DTP autonegotiation on end-user ports.*Change the management VLAN to a distinct VLAN that is not accessible by regular users.Statically configure all ports that connect to end-user host devices to be in trunk mode.Change the native VLAN number to one that is distinct from all user VLANs and is not VLAN 1.*Use SSH for all remote management access.12In a basic VLAN hopping attack, which switch feature do attackers take advantage of?automatic encapsulation negotiationthe default automatic trunking configuration*an open Telnet connectionforwarding of broadcasts13A Cisco switch currently allows traffic tagged with VLANs 10 and 20 across trunk port Fa0/5. What is the effect of issuing a switchport trunk allowed vlan 30 command on Fa0/5?It allows only VLAN 30 on Fa0/5.*It allows a native VLAN of 30 to be implemented on Fa0/5.It allows VLANs 1 to 30 on Fa0/5.It allows VLANs 10, 20, and 30 on Fa0/5.14Refer to the exhibit. A frame is traveling between PC-A and PC-B through the switch. Which statement is true concerning VLAN tagging of the frame?No VLAN tag is added to the frame.*A VLAN tag is added when the frame is accepted by the switch.A VLAN tag is added when the frame is forwarded out the port to PC-B.A VLAN tag is added when the frame leaves PC-A.15Refer to the exhibit. PC-A and PC-B are both in VLAN 60. PC-A is unable to communicate with PC-B. What is the problem?The native VLAN is being pruned from the link.The VLAN that is used by PC-A is not in the list of allowed VLANs on the trunk.*The trunk has been configured with the switchport nonegotiate command. The native VLAN should be VLAN 60.16What VLANs are allowed across a trunk when the range of allowed VLANs is set to the default value?All VLANs will be allowed across the trunk.*Only the native VLAN will be allowed across the trunk.The switches will negotiate via VTP which VLANs to allow across the trunk. Only VLAN 1 will be allowed across the trunk.17Under which two occasions should an administrator disable DTP while managing a local area network? (Choose two.)on links that should not be trunking*when connecting a Cisco switch to a non-Cisco switch*on links that should dynamically attempt trunkingwhen a neighbor switch uses a DTP mode of dynamic autowhen a neighbor switch uses a DTP mode of dynamic desirable18Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.Which PCs will receive the broadcast sent by PC-C?PC-D, PC-E*PC-A, PC-B, PC-D, PC-EPC-A, PC-BPC-A, PC-B, PC-D, PC-E, PC-FPC-A, PC-B, PC-E19Which two statements are true about VLAN implementation? (Choose two.)The network load increases significantly because of added trunking information.Devices in one VLAN do not hear the broadcasts from devices in another VLAN.*The size of the collision domain is reduced.VLANs logically group hosts, regardless of physical location.*The number of required switches in a network decreases.20Refer to the exhibit. DLS1 is connected to another switch, DLS2, via a trunk link. A host that is connected to DLS1 is not able to communicate to a host that is connected to DLS2, even though they are both in VLAN 99. Which command should be added to Fa0/1 on DLS1 to correct the problem?switchport trunk allowed vlan add 99switchport trunk native vlan 66*switchport mode dynamic autoswitchport nonegotiate21Which switch feature ensures that no unicast, multicast, or broadcast traffic is passed between ports that are configured with this feature?switch port securityPVLAN protected port*ACLVLAN22Fill in the blank. Use the full command syntax.The ” show vlan brief” command displays the VLAN assignment for all ports as well as the existing VLANs on the switch.23Which three statements accurately describe VLAN types? (Choose three).An 802.1Q trunk port, with a native VLAN assigned, supports both tagged and untagged traffic.*A management VLAN is any VLAN that is configured to access management features of the switch.*A data VLAN is used to carry VLAN management data and user-generated traffic.Voice VLANs are used to support user phone and e-mail traffic on a network. VLAN 1 is always used as the management VLAN.After the initial boot of an unconfigured switch, all ports are members of the default VLAN.*24Which command should the network administrator implement to prevent the transfer of DTP frames between a Cisco switch and a non-Cisco switch?S1(config-if)# switchport mode trunkS1(config-if)# switchport mode accessS1(config-if)# switchport nonegotiate*S1(config-if)# switchport mode dynamic desirableS1(config-if)# switchport trunk allowed vlan noneCCNA 2 - Chapter 41What type of IPv6 address is required as a minimum on IPv6 enabled interfaces?staticglobal unicastlink-local*loopbackunique local2In order for packets to be sent to a remote destination, what three pieces of information must be configured on a host? (Choose three.)default gateway*hostnameDNS server addressDHCP server addressIP address*subnet mask*3What two pieces of information are displayed in the output of the show ip interface brief command? (Choose two.)MAC addressesLayer 1 statuses*IP addresses*next-hop addressesinterface descriptionsspeed and duplex settings4Place the options in the following order:next hopdestination networkmetric- not scored -administrative distanceroute timestamproute source protocol- not scored -5Which two items are used by a host device when performing an ANDing operation to determine if a destination address is on the same local network? (Choose two.)destination MAC addressnetwork numberdestination IP address*source MAC addresssubnet mask*6Refer to the exhibit. A network administrator issues the show ipv6 route command on R1. What two conclusions can be drawn from the routing table? (Choose two.)Packets that are destined for the network 2001:DB8:ACAD:2::/64 will be forwarded through Fa0/1.R1 does not know a route to any remote networks.*The interface Fa0/1 is configured with IPv6 address2001:DB8:ACAD:A::12.*Packets that are destined for the network 2001:DB8:ACAD:2::54/128 will be forwarded through Fa0/0.The network FF00::/8 is installed through a static route command.7Refer to the exhibit. What is the purpose of the highlighted field in the line that is displayed from the show ip route command?It indicates that this is a directly connected route.It indicates that this route has been deleted from the routing table. It indicates that this route was learned via EIGRP.*It indicates that this is a default route.8Which two statements correctly describe the concepts of administrative distance and metric? (Choose two.)The metric varies depending which Layer 3 protocol is being routed, such as IP.A router first installs routes with higher administrative distances. The value of the administrative distance can not be altered by the network administrator.Routes with the smallest metric to a destination indicate the best path.* Administrative distance refers to the trustworthiness of a particular route.*The metric is always determined based on hop count.9What are two functions of a router? (Choose two.)It manages the VLAN database.It increases the size of the broadcast domain.It controls the flow of data via the use of Layer 2 addresses.It determines the best path to send packets.*It connects multiple IP networks.*10A packet moves from a host on one network to a device on a remote network within the same company. If NAT is not performed on the packet, which two items remain unchanged during the transfer of the packet from source to destination? (Choose two.)destination MAC addresssource ARP tablesource IP address*destination IP address*source MAC addressLayer 2 header11。

1、解决路由环问题的方法有____ABD_____A. 水平分割B. 路由保持法C. 路由器重启D. 定义路由权的最大值2、下面哪一项正确描述了路由协议_______C__A. 允许数据包在主机间传送的一种协议B. 定义数据包中域的格式和用法的一种方式C. 通过执行一个算法来完成路由选择的一种协议D. 指定MAC地址和IP地址捆绑的方式和时间的一种协议3、以下哪些内容是路由信息中所不包含的_____A____A. 源地址B. 下一跳C. 目标网络D. 路由权值4、以下说法那些是正确的_____BD____A. 路由优先级与路由权值的计算是一致的B. 路由权的计算可能基于路径某单一特性计算,也可能基于路径多种属性C. 如果几个动态路由协议都找到了到达同一目标网络的最佳路由,这几条路由都会被加入路由表中D. 动态路由协议是按照路由的路由权值来判断路由的好坏,并且每一种路由协议的判断方法都是不一样的5、IGP的作用范围是________C_A. 区域内B. 局域网内C. 自治系统内D. 自然子网范围内6、距离矢量协议包括____AB___A. RIPB. IGRPC. IS-ISD. OSPF7、关于矢量距离算法以下那些说法是错误的___A____A. 矢量距离算法不会产生路由环路问题B. 矢量距离算法是靠传递路由信息来实现的C. 路由信息的矢量表示法是(目标网络,metric)D. 使用矢量距离算法的协议只从自己的邻居获得信息8、如果一个内部网络对外的出口只有一个,那么最好配置_____A____A. 缺省路由B. 主机路由C. 动态路由10、在路由器中,如果去往同一目的地有多条路由,则决定最佳路由的因素有_____A_C_A. 路由的优先级B. 路由的发布者C. 路由的metirc值D. 路由的生存时间9、在RIP协议中,计算metric值的参数是_D________A. MTUB. 时延C. 带宽D. 路由跳数10、路由协议存在路由自环问题______A___A. RIPB. BGPC. OSPFD. IS-IS11、下列关于链路状态算法的说法正确的是: ___D______A. 链路状态是对路由的描述B. 链路状态是对网络拓扑结构的描述C. 链路状态算法本身不会产生自环路由D. OSPF和RIP都使用链路状态算法12、在OSPF同一区域(区域A)内,下列说法正确的是____D_____A. 每台路由器生成的LSA都是相同的B. 每台路由器根据该最短路径树计算出的路由都是相同的C. 每台路由器根据该LSDB计算出的最短路径树都是相同的D. 每台路由器的区域A的LSDB(链路状态数据库)都是相同的13、在一个运行OSPF的自治系统之内: _AD________A. 骨干区域自身也必须是连通的B. 非骨干区域自身也必须是连通的C. 必须存在一个骨干区域 ( 区域号为0 )D. 非骨干区域与骨干区域必须直接相连或逻辑上相连14、下列静态路由配置正确的是__D_______A. ip route 129.1.0.0 16 serial 0B. ip route 10.0.0.2 16 129.1.0.0C. ip route 129.1.0.0 16 10.0.0.2D. ip route 129.1.0.0 255.255.0.0 10.0.0.215、以下不属于动态路由协议的是______B___A. RIPB. ICMPC. IS-ISD. OSPf16、三种路由协议RIP 、OSPF 、BGP和静态路由各自得到了一条到达目标网络,路由器默认情况下,最终选选定____D____作为最优路由A. RIPB. OSPFC. BGPD.静态路由17、IGP 包括如下哪些协议_ABD________A. RIPB. BGPC. IS-ISD. OSPF18、路由环问题会引起_______A_A. 慢收敛B. 广播风暴C. 路由器重起D. 路由不一致19、以下哪些路由表项要由网络管理员手动配置_A_______A. 静态路由B. 直接路由C. 动态路由D. 以上说法都不正确20、关于RIP协议,下列说法正确的有: ________AC_A. RIP协议是一种IGPB. RIP协议是一种EGPC. RIP协议是一种距离矢量路由协议D. RIP协议是一种链路状态路由协议21、RIP协议是基于_____A____A. UDPB. TCPC. ICMPD. Raw IP22、RIP协议的路由项在多少时间内没有更新会变为不可达? __C_______A. 90sB. 120sC. 180sD. 240s23、解决路由环路的方法有______ABCDA. 水平分割B. 抑制时间C. 毒性逆转D. 触发更新24、RIP协议在收到某一邻居网关发布而来的路由信息后,下述对度量值的正确处理有哪些?_AD________A. 对本路由表中没有的路由项,只在度量值少于不可达时增加该路由项B. 对本路由表中已有的路由项,当发送报文的网关相同时,只在度量值减少时更新该路由项的度量值C. 对本路由表中已有的路由项,当发送报文的网关不同时,只在度量值减少时更新该路由项的度量值D. 对本路由表中已有的路由项,当发送报文的网关相同时,只要度量值有改变,一定会更新该路由项的度量值25、关于RIP V1和RIP V2,下列说法哪些正确? _BC_______A. RIP V1报文支持子网掩码B. RIP V2报文支持子网掩码C. RIP V2缺省使用路由聚合功能D. RIP V1只支持报文的简单口令认证,而RIP V2支持MD5认证26、在rip中metric等于_____D____为不可达A. 8B. 10C. 15D. 1627、RIP协议引入路由保持机制的作用是____B_____A. 节省网络带宽B. 防止网络中形成路由环路C. 将路由不可达信息在全网扩散D. 通知邻居路由器哪些路由是从其处得到28、与动态路由协议相比,静态路由有哪些优点? AB_______A. 带宽占用少B. 简单C. 路由器能自动发现网络拓扑变化D. 路由器能自动计算新的路由29、在RIP路由协议中,以下有关减少路由自环的方法正确的是__ABC__D_____A. 触发更新是从减少路由自环发生的概率方面来考虑问题的B. 水平分割的方法只对消除两台路由器之间的自环有作用C. 设置抑制时间的方法可能导致路由的慢收敛D. 为了减轻路由自环产生的后果,RIP协议规定了最大跳数30、路由协议在收到某一邻居发布而来的路由信息后,下述对度量值的正确处理有哪些? __BD_______A. 对本路由表中已有的路由项,当发送该路由信息的邻居相同时,只在度量值减少时更新该路由项的度量值B. 对本路由表中已有的路由项,当发送该路由信息的邻居相同时,只要度量值有改变,一定会更新该路由项的度量值C. 对本路由表中已有的路由项,当发送该路由信息的邻居不同时,只要度量值有改变,一定会更新该路由项的度量值D. 对本路由表中没有的路由项,只在度量值少于不可达时增加该路由项31、下面哪些协议是可路由协议(routed protocol)? ____AB_____A. IPB. IPXC. RIPD. NETBEUI32、以下协议属于路由协议的是_____ABCG____A. RIPB. IS-ISC. OSPFD. PPPE. IPF. IPXG. BGP33、下列哪些技术有助于避免路由环路? ___BCDEF______A. 直通交换B. 采用链路状态路由协议C. 水平分割D. 路由保持(holddown)E. 定义最大跳计数F. 路由中毒(poison reverse)34、静态路由的优点包括: ___AD______A. 管理简单B. 自动更新路由C. 提高网络安全性D. 节省带宽E. 收敛速度快35、以下对于缺省路由描述正确的是: ___BC______A. 缺省路由是优先被使用的路由B. 缺省路由是最后一条被使用的路由C. 缺省路由是一种特殊的静态路由D. 缺省路由是一种特殊的动态路由36、对路由器A配置RIP协议,并在接口S0(IP地址为10.0.0.1/24)所在网段使能RIP路由协议,在全局配置模式下使用的第一条命令是: ______A___A. Router ripB. rip 10.0.0.0C. network 10.0.0.1D. network 10.0.0.037、支持可变长子网掩码的路由协议有: __BCD_______A. RIP v1B. RIP v2C. OSPFD. IS-IS38、以下对路由优先级的说法,正确的是____BC_____A. 仅用于RIP和OSPF之间B. 用于不同路由协议之间C. 是路由选择的重要依据D. 直接路由的优先级缺省为039、您认为下列说法哪些是不正确的? ____CD__A. 每条静态路由的优先级也可以不相同B. 缺省情况下路由优先级的次序是 OSPF > RIPC. 路由算法产生一种权值来表示路由的好坏。

ERouting Chapter 1 - CCNA Exploration: 路由协议和概念(版本4.0)1口令可用于限制对Cisco IOS 所有或部分内容的访问。
请选择可以用口令保护的模式和接口。
(选择三项。
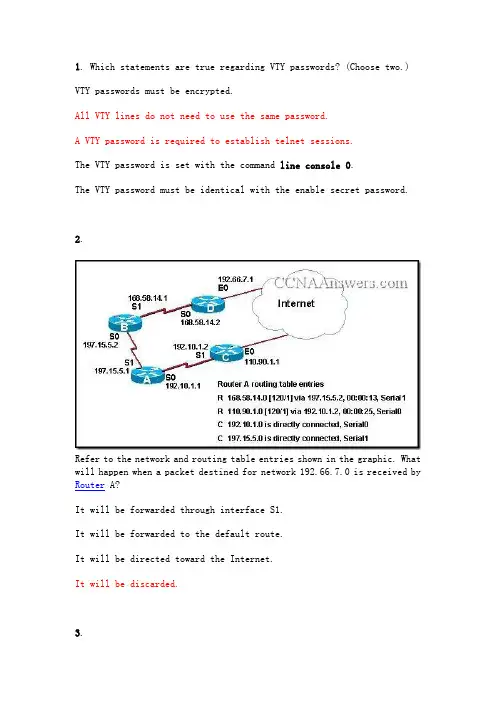
)VTY 接口控制台接口特权执行模式2路由器从相连的以太网接口收到消息后,会更改哪项报头地址,再将消息从另一个接口发送出去?第 2 层源地址和目的地址3请参见图示。
网络管理员已经为路由器连接到直连网络的接口配置了如图所示的IP 地址。
从路由器ping 相连网络上的主机口之间相互ping 都会遭到失败。
此问题最可能的原因是什么?必须使用no shutdown命令启用接口。
4请参见图示。
主机 A ping 主机B。
当R4 收到对以太网接口的ping 时,哪两块报头信息包括在内?(选择两项。
)目的IP 地址:192.168.10.134目的MAC 地址:9999.DADC.12345网络管理员刚把新配置输入Router1。
要将配置更改保存到NVRAM,应该执行哪一条命令?Router1# copy running-config startup-config6您需要配置图中所示的串行连接,必须在Sydney 路由器上发出以下哪条配置命令才能与Melbourne 站点建立连接?(选Sydney(config-if)# ip address 201.100.53.2 255.255.255.0Sydney(config-if)# no shutdownSydney(config-if)# clock rate 560007请参见图示。
从路由器的运行配置输出可得出什么结论?显示的命令决定了路由器的当前运行情况。
8请参见图示。
在主机 2 连接到LAN 上的交换机后,主机2 无法与主机 1 通信。
导致此问题的原因是什么?主机 1 和主机2 位于不同的网络中。
9输入以下命令的作用是什么?R1(config)# line vty 0 4R1(config-line)# password check123R1(config-line)# login设置通过Telnet 连接该路由器时使用的口令10以下哪一项正确描述了路由器启动时的顺序?加载bootstrap、加载IOS、应用配置11加载配置文件时的默认顺序是怎样的?NVRAM、TFTP、CONSOLE12请参见图示。

CCNA Exploration:网络基础知识第二章练习题及答案A.B.C.D.E.F.G.□○1.下列哪些陈述正确指出了中间设备在网络中的作用?(选择三项)□确定数据传输路径□发起数据通信□重新定时和重新传输数据信号□发送数据流□管理数据流□数据流最后的终止点Option 1, Option 3, and Option 5 are correct.2.请选择关于网络协议的正确陈述。
(选择三项。
)□定义特定层 PDU 的结构□规定实现协议层功能的方式□概述层与层之间通信所需的功能□限制了对硬件兼容性的需要□需要取决于协议层的封装过程□杜绝厂商之间的标准化Option 1, Option 3, and Option 5 are correct.3.封装的两个功能是什么?(选择两项)□跟踪终端设备之间的延迟□为通信提供统一的网络路径□在传输前可以修改原始数据□标识属于同一通信的数据片段□确保数据片段可以转发到正确的接收端设备Option 4 and Option 5 are correct.4. 数据链路层封装添加的报尾信息有何主要功能?○支持差错校验○确保数据按照顺序到达○确保送达正确目的○标识本地网络中的设备○帮助中间设备进行处理和路径选择2 points for Option 15. OSI 模型哪两层的功能与 TCP/IP 模型的网络接入层相同?(选择两项)□网络层□传输层□物理层□数据链路层□会话层Option 3 and Option 4 are correct.6. 什么是 PDU?○传输期间的帧损坏○在目的设备上重组的数据○因通信丢失而重新传输的数据包○特定层的封装2 points for Option 47. 以下哪种特征正确代表了网络中的终端设备?□管理数据流□发送数据流□重新定时和重新传输数据信号□确定数据传输路径2 points for Option 28. 请参见图示。
IP 地址为 10.0.0.34 的“手机 A”已经与 IP 地址为 172.16.1.103 的“IP 电话 1”建立了 IP 会话。
1. Which statements are true regarding VTY passwords? (Choose two.)VTY passwords must be encrypted.All VTY lines do not need to use the same password.A VTY password is required to establish telnet sessions.The VTY password is set with the command line console 0.The VTY password must be identical with the enable secret password. 2.Refer to the network and routing table entries shown in the graphic. What will happen when a packet destined for network 192.66.7.0 is received by Router A?It will be forwarded through interface S1.It will be forwarded to the default route.It will be directed toward the Internet.It will be discarded.3.Which command will produce the output shown in the graphic?show cdpshow cdp neighborsshow cdp neighbors detailshow cdp detail4.Router B received an interface configuration change. Suddenly, it transmits a new update. Which of the following could have triggered this update? (Choose two.)Router B received a configuration change.Router A sent a message requesting an update.Router C came online after Router B sent the RIP update.Router B received an error message indicating the last update was not received.5. How many Telnet sessions can take place simultaneously on a router running a standard edition of the IOS?458106. Which of the following WAN connection services typically use synchronous communications? (Choose two.)circuit-switchedleased linepacket-switchedEthernetanalog modem services7. Which of the following will add a TFTP server as a fallback source fora router to load an IOS image?Router# boot system tftp 163.150.9.31 c2500-d-l.120-9Router# copy run startRouter# boot system tftp c2500-d-l.120-9.bin 163.150.9.31Router# copy run startRouter# config tRouter(config)# boot system tftp c2500-d-l.120-9.bin 163.150.9.31 Router(config)# exitRouter# copy run startRouter# config tRouter(config)# boot system tftp 163.150.9.31 c2500-d-l.120-9.binRouter(config)# exitRouter# copy run start8. What types of messages are sent periodically by devices configured for CDP?probesbeaconssignalsadvertisementsrouting updatesunicast9. An administrator has made routing protocol changes to a ro uter’s configuration. To ensure that the changes are implemented, the active configuration is saved and the router is reloaded. After the router has initialized, the output on the screen displays "Would you like to enter the initial configuration dialog?[yes/no]:" Why did this dialog appear?There was a POST failure.The incorrect IOS loaded.There was an error in the startup configuration file.The configuration register was set to ignore NVRAM.10. Which command is used to redirect debug information to a device that is connected though a Telnet session?Router# monitorRouter# terminal redirect vty 0Router# terminal monitorRouter# monitor output vty 011. After issuing the show interfaces command, a technician notices the line "Serial1 is down, line protocol is down" in the output. Which of the following are possible reasons for this message output? (Choose three.)There is a mismatch in the encapsulation type on both ends of the link.A Layer 1 issue exists.An interface problem exists.The clockrate was not set during configuration.There is no usable media for the protocol.Keepalive messages are not being sent.12.Refer to the above graphic. When using RIP as the routing protocol, how would Chicago use load balancing to route packets to New York? (Choose two.)by forwarding packets over paths of equal costby forwarding packets according to hop count and speed of the linkby determining which interface has the least traffic and sending to it firstby first determining the speed of the links and then cycling packets through the fastest links firstby cycling packets through interfaces and routes following the same pattern (Router 1, 2, 3) each time13. When would the ROM monitor mode be used? (Choose two.) maintaining routing configuration settingsmodifying the IOS image stored in Flashrunning a limited IOS feature setperforming the bootstrap process14. Which two statements are true about route metrics? (Choose two.)The more factors that make up a metric, the greater the flexibility to tailor network operations.The larger the metric number, the better the path.Routing protocols use metrics to send routing updates to directly connected neighbors.Bandwidth and delay are static metrics used by RIP v1.Ticks, delay, and cost are metrics used by routing protocols.15.Which of the following are valid static IP routes? (Choose three.) RouterB(config)# ip route 192.168.5.0 255.255.255.0 S1RouterC(config)# ip route 192.168.1.0 255.255.255.0 S1RouterA(config)# ip route 192.168.3.0 255.255.255.0 192.168.2.2 RouterB(config)# ip route 192.168.1.0 255.255.255.0 192.168.2.2 RouterC(config)# ip route 192.168.2.0 255.255.255.0 192.168.4.1 RouterA(config)# ip route 192.168.4.0 255.255.255.0 192.168.2.116. Of the eight network users on the Human Resources department LAN, one cannot connect to the file serv er. The user’s PC has successfully booted but can not see the network. What should be checked first?the PC power cordthe file serverthe PC network interface card LEDsthe LAN switch in the wiring closetthe configuration of the router interface attached to the LAN17. What can be determined from the partial output of the show ip route command displayed below? (Choose two.)R 200.200.200.0/24 [120/1] via 192.168.10.2, 00:00:14, Serial0/0C 192.168.10.0/24 is directly connected, Serial0/0The next update will be in 76 seconds.The next update will be in 16 seconds.The administrative distance is 120 and the metric is 1.The metric is 120 and the administrative distance is 1.200.200.200.0 is configured on Serial0/0.192.168.10.2 is configured on Serial0/0.18. Why is it useful to have an interface description?A user can telnet to the router using the interface description.The interface description is a shortcut way to edit the running-config. The interface description helps identify distant network connections.The interface will remain inactive until an interface description is applied.19.Assume OSPF is being used on all routers. What happens when the link between Router1 and Router2 goes down? (Choose two.)Updates start broadcasting every 30 seconds.Updates start broadcasting every 90 seconds.Link-state advertisements are flooded.Link-state advertisements are sent only to neighboring routers.All routers note the change and adjust routes.All routers ignore the change until the route becomes active again. 20.The internetwork needs to communicate between the hosts connected to the E0 interface of the Utah router and hosts connected to the E0 interface of the Idaho router. The hosts should also have connectivity to the Internet. Which commands must be configured in order to enable this communication? (Choose three.)Idaho(config)# ip route 172.31.1.0 255.255.255.0 172.31.2.1Idaho(config)# ip route 0.0.0.0 0.0.0.0 s0Idaho(config)# ip route 172.31.2.0 255.255.255.0 172.31.2.2Utah(config)# ip route 172.31.3.0 255.255.255.0 172.31.2.1Utah(config)# ip route 172.31.3.0 255.255.255.0 s1Utah(config)# ip route 0.0.0.0 0.0.0.0 s021. Which statement about datagram life is true?Each router increments the TTL value of the datagram until the maximum hop count of the routing protocol is reached. The packet is then returned to the source.The packet is dropped when the router count and the TTL value match. The source is notified that transmission has failed.Each router decreases the TTL value by one until it reaches zero. The datagram is then discarded and a time exceeded for message is sent to the source.The destination device discards the datagram if the TTL value is zero on arrival. An ICMP destination unreachable message is sent back to the source.22.The following access list has been created to prevent traffic from host 204.204.7.122 from accessing the 201.100.11.0 network.access-list 22 deny host 204.204.7.122access-list 22 permit anyWhich group of commands will properly place this access list so that this host is denied access only to the 201.100.11.0 network?RouterA(config)# interface s0/0RouterA(config-if)# ip access-group 22 inRouterA(config)# interface s0/0RouterA(config-if)# ip access-group 22 outRouterA(config)# interface fa0/0RouterA(config-if)# ip access-group 22 inRouterB(config)# interface fa0/0RouterB(config-if)# ip access-group 22 inRouterB(config)# interface s0/0RouterB(config-if)# ip access-group 22 inRouterB(config)# interface fa0/0RouterB(config-if)# ip access-group 22 out23. A network administrator can establish a remote session to a host using the Router> telnet 192.168.1.1command but is unsuccessful when using the Router> telnet Boston command to connect to the same interface. Which of the following could be the problem? (Choose two.)The ip host table on the router is not configured.The command telnet Boston was issued from the wrong router prompt.The routing table is missing.Domain name services are not available.24. Which of the following are functions of a router? (Choose three.)packet switchingextension of network segmentssegmentation of local area networksselection of best path based on a logical addressingselection of best path based on a physical addressingThe commands shown in the graphic were entered to alter the startup sequence of the router. On the next reload, which IOS will be loaded?The router will load c2500-js-l.112-26d.The router will load c2500-d-l.120-9.The router will load the IOS from ROM.The router will boot into ROM monitor mode.26.A network administrator trying to deny Telnet traffic from the 192.5.5.0 network to the 201.100.11.0 network entered the commands shown in the graphic. When monitoring the network, the administrator noticed that Telnet packets were still passing between those networks. What is the cause?The router ignored this type of traffic because it required a standard access list to be configured instead of an extended one.The wrong port was configured for the ACL so Telnet traffic was still allowed.The access list has not been assigned to an interface.The permit ip any any allowed all traffic to pass regardless of the other statements listed in this ACL.Refer to the network graphic. A packet needs to travel from Router F to Router A. Which path would be selected by the RIP routing protocol if the default metrics are used?F, G, E, D, B, AF, E, D, C, AF, E, D, AF, E, D, B, A28. Which of the following is the correct flow of routines for a router startup?load bootstrap, load IOS, apply configurationload bootstrap, apply configuration, load IOSload IOS, load bootstrap, apply configuration, check hardwarecheck hardware, apply configuration, load bootstrap, load IOS29. In the configuration register value 0×2104, which value represents the boot field setting?x2430. ACL statements operate in sequential, logical order. If a condition match is true, the rest of the ACL statements are not checked. If all of the ACL statements are unmatched, what happens to the packet?The packets will be placed in a buffer and forwarded when the ACL is removed.The packets will be sent to the source with an error notification message.The implicit permit any statement placed at the end of the list will allow the packets to flow through uninhibited.The implicit deny any statement placed at the end of the list will cause the packets to be dropped.31. Which of the following would cause the "Message Of The Day" banner to appear? (Choose three.)telnetting into the routerinitiating a debug sessionconfiguring a router for the first timeusing the Aux port to check the current configurationusing the console port to check the current configuration32.The administrator knows that port E0 on router B connects to a small LAN without any routers. Which command can be executed on router B to conserve bandwidth on port E0?no update timersholdown-timer 96poison reverse E0passive-interface E0no triggered updates33. When must a router serial interface be configured with the clock rate command?when the interface is functioning as a DTE devicewhen the interface timers have been clearedwhen the connected DTE device is shut downwhen the interface is functioning as a DCE device34. What are the major characteristics of a wide area network? (Choose three.)connect devices separated by wide geographical areasincludes technologies of FDDI and Ethernetuses serial connections to access bandwidthcommon carriers are needed for connectionstype of connection between a router and a switch35. If the config-register on a router is set to 0×2102, where is the first place the router will look for boot system commands?RAMROMFlashNVRAM36. Why would an administrator use the Telnet application when troubleshooting a network? (Choose three.)It can be used to verify the operation of application layer software between the source and destination.Telnet can use the ICMP protocol to verify a hardware connection and network layer address.It is the most complete testing mechanism available.Remote networks may be accessed via a Telnet session for troubleshooting.Time to Live values are used by Telnet to identify a failure of device between source and destination.37.The network shown in the graphic is using RIP as the routing protocol. Which of the following are true regarding the network discovery process that will occur for this network? (Choose three.)The Palm Beach router will show networks 192.168.7.0 and 192.168.8.0 as directly connected networks.All of the routers will have direct knowledge of the exact topology of the entire network.The Key West router will forward routing table information to the Miami and Palm Beach routers.The Miami router will learn about network 192.168.1.0 from the Key West router.If network 192.168.4.0 becomes unavailable, the Key West router will notify the other routers of this fact in the next update.38. Which of the following are characteristics of the Open Shortest Path First (OSPF) routing protocol? (Choose two.)functions as a link-state routing protocoldiscards packets when the hop count is greater than 15calculates the shortest path to a destination using the Diffused Update Algorithm (DUAL)created as a proprietary routing protocolfloods updates as topology changes occurbroadcasts routing updates every 90 seconds or as triggered by topology changes39. The following line was displayed in the output of the show ip route command.R 192.168.3.0/24 [120/3] via 192.168.2.2, 00:00:30, Serial0/0What is the value of the routing metric?312203012040.Refer to the output from the show ip route command. What can be concluded from the output of this router command?A preferred route to the destination has not been set.There are two equal cost paths to network 1.0.0.0.Both interfaces are being used equally to route traffic.A variance must be set to load-balance across multiple paths.41. Which of the following are true statements about creating and applying access lists? (Choose three.)Access list entries should filter in the order from general to specific.One access list per port per protocol per direction is permitted.Standard ACLs should be applied closest to the source while extended ACLs should be applied closest to the destination.There is an implicit deny at the end of all access lists.Statements are processed sequentially from top to bottom until a match is found.The inbound keyword refers to traffic entering the network from the router interface where the ACL is applied.42. Which of the following are true regarding the setup configuration mode? (Choose three.)To abort the setup mode, use the CTRL+SHIFT+6 keys.To abort the setup mode, use the CTRL+C keys.Setup mode allows a complete configuration of the router.To enter setup mode, use the privileged mode setup command.A router that does not find a valid IOS during the boot process will start the system configuration dialog.A router that does not find a valid configuration file during the boot process will start the system configuration dialog.43. Which of the following are necessary for basic network communication to occur between hosts that will run such applications as Telnet, web browsers, and e-mail? (Choose three.)TCP/IP must be installed and properly configured on each device.Multiple subnets must be configured on the router to ensure accurate delivery.A default gateway must be configured for datagrams to travel outside of the LAN.The hosts must be directly connected to a switch to travel outside of the LAN.To ensure accurate delivery, a router must be configured and accessible by hosts on the network.44.Given the above topology, which of the following statements are true? (Choose two.)If RouterC receives a packet destined for 10.5.183.46, it will be forwarded out interface Serial 1.If RouterA receives a packet destined for 192.168.3.146, it will be forwarded out interface Ethernet 0.If RouterA receives a packet destined for 10.5.27.15, it will be forwarded out interface Serial 1.If RouterB receives a packet destined for 10.5.27.83, it will be forwarded out interface Serial 0.If RouterA receives a packet destined for 172.16.55.101, it will be forwarded out interface Serial 1.45. Host name resolution allows for the use of an alphanumeric name to identify network devices. Select the answer that displays the correct configuration syntax for creating a host name.Router# ip host Fontana 200.100.50.5Router(config)# ip host Fontana 200.100.50.5Router(config-if)# ip host Fontana 200.100.50.5Router(config)# ip host Fontana 200.100.50.5/24。

以下是针对您未获得满分的试题给出的反馈。
某些交互式试题可能不显示您的答案。
分项分数:1与固定配置的交换机相比,模块化交换机具有哪两个优点?(请选择两项。
)正确响应您的响应每台交换机的成本更低可扩展性更高转发率更低需要的电源插座数目更少带宽聚合可以使用多个端口固定配置交换机价格较低,但是它具有指定数量的端口且不能添加端口。
它们提供的高速端口通常比较少。
为了在包含固定配置交换机的网络上扩展交换,需要购买更多的交换机。
这增加了需要使用的电源插座数量。
模块化交换机只需要购买额外的线卡便可以扩展。
带宽聚合也更容易,因为机箱的背板可以为交换机端口线卡提供所需的带宽。
此试题参考以下领域的内容:Routing and Switching Essentials• 1.1.2 交换网络2思科无边界架构接入层的基本功能是什么?正确响应您的响应聚合第 2 层广播域聚合第 3 层路由边界为用户提供访问权提供高可用性思科无边界架构接入层的功能是为用户提供网络访问。
第 2 层广播域聚合、第 3 层路由边界聚合和高可用性是分布层的功能。
也有说答案是聚合第 3 层路由边界此试题参考以下领域的内容:Routing and Switching Essentials• 1.1.1 融合网络3思科无边界架构分布层的基本功能是什么?正确响应您的响应充当主干聚合所有园区块聚合第 3 层路由边界为用户提供访问权思科无边界架构的分布层的一项基本功能是在不同的VLAN 之间路由。
充当主干和聚合园区块是核心层的功能。
为用户提供访问是接入层的功能。
此试题参考以下领域的内容:Routing and Switching Essentials• 1.1.1 融合网络4若将大端口密度、容错和低价作为重要指标,应使用哪个交换机外形因素?正确响应您的响应固定配置交换机模块化交换机可配备机架的1U 交换机可堆叠式交换机堆叠式交换机可以使用特殊电缆实现互联,从而在交换机之间提供高带宽的吞吐量,并像单个大型交换机一样运行。

CCNA 2 - Module 1If a router cannot find a valid configuration file during the startup sequence, what will occur?The router will prompt the user for a response to enter setup mode.Refer to the exhibit. The network administrator has configured the router with the interface IP addresses shown for the directly connected networks. Pings from the router to hosts on the connected networks or pings between router interfaces are not working. What is the most likely problem?The interfaces must be enabled with the no shutdown command.Refer to the exhibit. What can be concluded from the routing table output in the exhibit? (Choose two.) The FastEthernet0/0 and Serial0/0/0 interfaces of this router were configured with an IP address and the no shutdown command.An IP packet received by this router with a destination address of 198.18.9.1 will be forwarded out of the Serial0/0/0 interface.Refer to the exhibit. The frame shown in the exhibit was received by the router. The router interfaces are operational. How will the router process this frame? (Choose two.)The router will change the frame type to one supported by the WAN link before forwarding the frame.The frame was received on the Fa0/0 interface of the router and will be s witched to the S0/0/0 interface.Passwords can be used to restrict access to all or parts of the Cisco IOS. Select the modes and interfaces that can be protected with passwords. (Choose three.)VTY interfaceconsole interfaceprivileged EX EC modeWhich two statements correctly describe the components of a router? (Choose two.)ROM contains diagnostics executed on hardware modules.Flash memory does not lose its contents during a reboot.Refer to the exhibit. After host 2 is connected to the switch on the LAN, host 2 is unable to communicate with host 1. What is the cause of this problem?The subnet mask of host 2 is incorrect.Host 1 and host 2 are on different networks.The switch needs an IP address that is not configured.The router LA N interface and host 1 are on different networks.The IP address of host 1 is on a different network than is the LAN interface of the router.Which are functions of a router? (Choose three.)packet s witchingsegmentation of broadcast domainsselection of best path based on logical addressingRefer to the exhibit. A ll routers have a route in its routing table to each network that is shown in the exhibit. Default routes have not been issued on these routers. What can be concluded about how packets are forwarded in this network? (Choose two.)If RouterA receives a packet that is destined for 192.168.3.146, it will be forwarded out interface S0/0/1.If RouterB receives a packet that is destined for 10.5.27.15, it will be forwarded out interface S0/0/1.The serial connection shown in the graphic needs to be configured. Which configuration commands must be made on the Sydney router to establish connectivity with the Melbourne site? (Choose three.) Sydney(config-if)# ip address 201.100.53.2 255.255.255.0Sydney(config-if)# no shutdownSydney(config-if)# clock rate 56000Refer to the exhibit. What can be concluded from the output of the running-configuration of a router? The commands that are dis played determine the current operation of the router.Refer to the exhibit. Host A pings host B. When R4 accepts the ping into the Ethernet interface, what two pieces of header information are included? (Choose two.)destination IP address: 192.168.10.134destination MAC address: 9999.DADC.1234What is the outcome of entering these commands?R1(config)# line vty 0 4R1(config-line)# password check123R1(config-line)# loginsets the password to be used for connecting to this router via T elnetWhich of the following is the correct flow of routines for a router startup?load bootstrap, load IOS, apply configurationWhat three processes does a router execute when it receives a packet from one network that is destinedfor another network? (Choose three.)decapsulates the Layer 3 packet by stripping off the Layer 2 frame headeruses the destination IP Address in the IP header to look up the next-hop address in the routing tableencapsulates the Layer 3 packet into the new Layer 2 frame and forwards it out the exit interfaceThe network administrator needs to connect two routers directly via their FastEthernet ports. What cable should the network administrator use?cross-overWhich two statements describe characteristics of load balancing? (Choose two.)Load balancing allows a router to forward packets over multiple paths to the same destination network.Unequal cost load balancing is supported by EIGRP.What information about the router and its startup process can be gathered from the output of the show version command? (Choose three.)the last restart methodthe configuration register settingsthe location from where the IOS loadedWhich interfaces in the exhibit could be used for a leased line WAN connection? (Choose two.)14From what location can a router load the Cisco IOS during the boot process? (Choose two.)TFTP serverFlash memoryA network administrator has just entered new configurations into Router1. Which command should be executed to save configuration changes to NVRAM?Router1# copy running-config startup-configWhat is the default sequence for loading the configuration file?NVRAM, TFTP, CONSOLEWhat header address information does a router change in the information it receives from an attached Ethernet interface before information is transmitted out another interface?the Layer 2 source and destination addressCCNA 2 - Module 2Which of the following are displayed by the Router# show cdp neighbors command? (Choose three.)platformholdtimelocal interfaceWhy is it advisable to enter a next-hop IP address when creating a static route whose exit interface is an Ethernet network?In a multi-access network, the router cannot determine the next-hop MAC address for the Ethernet frame without a next-hop address.The output of the Router# show interfaces serial 0/1 command displays the following: Serial0/1 is up, line protocol is down.What is the most likely cause for the line protocol being down?No clock rate has been set.A static route that points to the next hop IP will have what administrative distance and metric in the routing table?administrative distance of 1 and metric of 0Refer to the exhibit. What two commands will change the next-hop address for the 10.0.0.0/8 network from 172.16.40.2 to 192.168.1.2? (Choose two.)A(config)# no ip route 10.0.0.0 255.0.0.0 172.16.40.2A(config)# ip route 10.0.0.0 255.0.0.0 192.168.1.2Refer to the exhibit. A company network engineer is assigned to establish connectivity between the two Ethernet networks so that hosts on the 10.1.1.0/24 subnet can contact hosts on the 10.1.2.0/24 subnet. The engineer has been told to use only static routing for these company routers. Which set of commands will establish connectivity between the two Ethernet networks?R1(config)# ip route 10.1.1.0 255.255.255.0 192.168.0.2R2(config)# ip route 10.1.2.0 255.255.255.0 192.168.0.1Refer to the exhibit. Which static route should be configured on Router1 so that hostA will be able to reach hostB on the 172.16.0.0 network?ip route 172.16.0.0 255.255.0.0 S0/0/0Which address can be used to summarize networks 172.16.0.0/24 thru 172.16.7.0/24?172.16.0.0/21Refer to the exhibit. What is the significance of the /8 in the route to the 10.0.0.0 network?It indicates the number of consecutive bits, from the left, in the destination IP address of a packet that must match 10.0.0.0 to use that route.What two devices are responsible for converting the data from the WAN service provider into a form acceptable by the router? (Choose two).a modema CSU/DSU deviceA network administrator enters the following command into Router1: ip route 192.168.0.0 255.255.255.0 S0/1/0. Router1 then receives a packet that is destined for192.168.0.22/24. After finding the recently configured static route in the routing table, what does Router1 do next to process the packet?encapsulates the packet into a frame for the WAN link and forwards the packet out the S0/1/0 interfaceWhich piece of information is available from examining the output of the command show ip interface brief?Interface IP addressWhich of the following is true regarding CDP and the graphic shown?By default, Router A will receive CDP advertisements from routers B and C.Which two statements describe functions or characteristics of CDP? (Choose two.)It starts up automatically and allows the device to detect directly connected neighbor devices that use CDP.It allows systems to learn about each other even if different network layer protocols are configured.Hosts on two separate subnets cannot communicate. The network administrator suspectsa missing route in one of the routing tables. Which three commands can be used to help troubleshoot Layer 3 connectivity issues? (Choose three.)pingtracerouteshow ip routeWhat happens to a static route entry in a routing table when the outgoing interface is not available?The route is removed from the table.The routers in the diagram use the subnet assignments shown. What is the most efficient route summary that can be configured on Router3 to advertise the internal networks to the cloud?192.1.1.0/25Refer to the exhibit. How will packets destined to the 172.16.0.0 network be forwarded? Router1 will perform recursive lookup and packet will exit S0/0.A router has one static route configured to each destination network. Which two scenarios would require an administrator to alter the static routes that are configured on that router? (Choose two.)The destination network no longer exists.A topology change occurs where the existing next-hop address or exit interface is not accessible.Refer to the exhibit. Given the output in the exhibit, how would a clock rate be determined for this link?The rate configured on the DCE determines the clock rate.Refer to the exhibit. Which set of commands will configure static routes that will allow the WinterPark and the Altamonte routers to deliver packets from each LAN and direct all other traffic to the Internet?WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 0.0.0.0 0.0.0.0 s0/1Refer to the exhibit. What two commands are required to provide connectivity betw een the 192.168.1.0 and 10.0.0.0 networks without requiring recursive lookup? (Choose two.)A(config)# ip route 10.0.0.0 255.0.0.0 s 0/1/0B(config)# ip route 192.168.1.0 255.255.255.0 s 0/0/0CCNA 2 - Module 3Which two statements correctly describe the concepts of administrative distance and metric? (Choose two.)Administrative distance refers to the trustworthiness of a particular route.Routes with the smallest metric to a destination indicate the best path.Refer to the exhibit. Which statement correctly describes how R1 will determine the best path to R2?R1 will install an EIGRP route using network B in its routing table because the administrative distance of EIGRP is lower than RIP.Which two statements are true regarding classless routing protoc ols? (Choose two.) sends subnet mask information in routing updatesallows for use of both 192.168.1.0/30 and 192.168.1.16/28 subnets in the same topologyWhich command would the network administrator issue to determine if load balancing is in effect on a router?show ip routeWhich statement is true regarding routing protocols?EIGRP uses DUAL to calculate the shortest path and can be configured to do unequal cost load balancing.Which two conditions would create a setting where the use of a distance-vector routing protocol would be efficient? (Choose two.)the network is using a hub and spoke topologythe network is using a flat designWhat is the purpose of a routing protocol?It allows a router to share information about known networks with other rou ters.Which of the following best describes the operation of distance vector routing protocols? They send their routing tables to directly connected neighbors.Which of the following is associated with link-state routing protocols?shortest-path first calculationsWhy is fast convergence desirable in networks that use dynamic routing protocols? Routers may make incorrect forwarding decisions until the network has converged.Which of the following conditions must be met in order for a network to have con verged The routers in the network are operating with consistent routing knowledge.Which two statements are true regarding metrics? (Choose two.)EIGRP uses bandwidth as a metric.OSPF uses cost based on bandwidth as a metric.Which two statements are true regarding the advantages of the use of static routes? (Choose two).increased securitythe administrator maintains control over routingThe following line of code is displayed in a routing table:R 209.165.201.0/24 [120/2] via 192.168.252.2, 00:00:16, S0/0/0What can be concluded from this output?The value, 120, is used to determine the best path when a router has more than one routing protocol configured for the same destination network.What will be the result of the following commands?ORL(config)# interface fastethernet 0/0ORL(config-if)# ip address 172.16.3.1 255.255.255.0ORL(config-if)# no shutdownA routing table entry is made to the 172.16.3.0 network with a code of "C".An engineer creates a static route by entering the Router(config)# ip route 10.0.0.0 255.255.255.0 192.168.1.2 command. What can be concluded about this route?The administrative distance of this route is 1.Refer to the exhibit. Router1 and Router2 are running EIGRP. All interfaces are operational and packets can be forwarded between all networks. What information will be found in the routing table for Router1?The administrative distance of the route to network 172.16.0.0 will be 90.The following line of code is present in the routing table:O 10.16.1.0/27 [110/129] via 192.168.1.5, 00:00:05, Serial0/0/1What does the number 129 indicate in this output?The cost for this link has a value of 129.A growing medium-sized manufacturing company recently began to have routing instability issues. The company uses static routes and has a mixture of over 30 Cisco and non-Cisco routers. The network administrator has decided to convert the network to dynamic routing. What characteristics of protocols should be considered in this selection process?OSPF can be used between the routers.Refer to the exhibit. If RIP is the routing protocol, what is the value of the metric from router A to network 192.168.5.0/24?3A router learns two paths with equal metrics to a destination network via the RIP routing protocol. How will the router handle packets to the destination network?The router will install both routes in the routing table and load balance between the two.CCNA 2 - Module 4Which event will cause a triggered update?a route is installed in the routing tableThree routers running a distance-vector routing protocol lost all power, including the battery backups. When the routers reload, what will happen?They will send updates that include only directly connected routes to their directly connected neighbors.What does the RIP holddown timer do?instructs routers to ignore updates, for a specified time or event, about possible inaccessible routesWhich two statements are true regarding the function of the RIPv1 routing updates? (Choose two).updates are broadcast at regular intervalsbroadcasts are sent to 255.255.255.255Which of the following statements are correct about RIP?will send out an update if there is a failure of a linkWhich two statements describe EIGRP? (Choose two.)EIGRP sends triggered updates whenever there is a change in topology that influences the routing information.EIGRP sends a partial routing table update, which includes just routes that have been changed.Which statement is true regarding cisco’s RIP_JITTER variable?It prevents the synchronization of routing updates by subtracting a random length of time ranging from 0% to 15% of the specified interval time from the next routing update interval.What actions will occur after RouterA loses connectivity to network 114.125.16.0? (Choose two.)RouterB will include network 123.92.76.0 and 136.125.85.0 in its update to RouterA.Router C will learn of the loss of connectivity to network 114.125.16.0 from RouterB.Which of the following methods does split horizon use to reduce incorrect routing information?Information learned from one source is not distributed back to that source.The graphic shows a network that is configured to use RIP routing protocol. Router2 detects that the link to Router1 has gone down. It then advertises the network for this link with a hop count metric of 16. Which routing loop prevention mechanism is in effect?route poisoningWhat is the purpose of the TTL field in the IP header?limits the time or hops that a packet can traverse through the network before it should be discardedWhich of the following can exist in a distance vector network that has not converged? (Choose three.)routing loopsinconsistent traffic forwardinginconsistent routing table entriesRefer to the exhibit. The routers in this network are running RIP. Router A has not received an update from Router B in over three minutes. How will Router A respond?The Invalid timer will mark the route as unusable if an update has not been received in 180 seconds.A network administrator is evaluating RIP versus EIGRP for a new network. The network will be sensitive to congestion and must respond quickly to topology changes. What are two good reasons to choose EIGRP instead of RIP in this case? (Choose two.)EIGRP only updates affected neighbors.EIGRP updates are partial.Refer to the exhibit. What path will packets from the 192.168.1.0/24 network travel to reach the 10.0.0.0/8 network if RIP is the active routing protocol?The path will be router A -> router D -> router E.Which three routing protocols are distance vector routing proto cols? (Choose three).RIPv1EIGRPRIPv2What is a routing loop?a condition where a packet is constantly transmitted within a series of routers without ever reaching its intended destinationWhich two conditions are most likely to cause a routing loop? (Choose two.)inconsistent routing tablesincorrectly configured static routesWhat metric does the RIP routing protocol consider to be infinity?16What does a router running RIP do first with a new route that is received from an advertisement?adjusts the metric for the new route to show the added distance for the routeRefer to the exhibit. If all routers are using RIP, how many rounds of updates will occur before all routers know all networks?3CCNA 2 - Module 5Refer to the exhibit. The network that is shown is running RIPv1. The 192.168.10.0/24 network was recently added and will only contain end users. What command or set of commands should be entered on Router1 to prevent RIPv1 updates from being sent to the end user devices on the new network while still allowing this new network to be advertised to other routers?Router1(config-router)# passive-interface fastethernet 0/0The following line was displayed in the output of the show ip route command.R 192.168.3.0/24 [120/3] via 192.168.2.2, 00:00:30, Serial0/0What is the value of the routing metric?3Which of the following is considered a limitation of RIP v1?RIP v1 does not send subnet mask information in its updates.Refer to the exhibit. The Ethernet interface on Router2 goes down and the administrator notices that the route is still in the Router1 routing table. How much longer will Router1 keep the down network in its routing table before marking it as possibly down?155 secondsRefer to the exhibit. Router1 is running RIPv1. What command was entered into Router1 to configure the gateway of last resort?ip route 0.0.0.0 0.0.0.0 S0/0/1What are three characteristics of the RIPv1 routing protocol? (Choose three.)uses hop count as a metricconsiders a metric of 16 as infinitycalculates metrics using the Bellman Ford algorithmWhich of the following would be the correct command sequence to enable RIP on Router B for all connected networks?RouterB(config)# router ripRouterB(config-router)# network 198.16.4.0RouterB(config-router)# network 210.36.7.0RouterB(config-router)# network 220.17.29.0What is the default update period in seconds for the RIP routing protocol?30Refer to the exhibit. What can be concluded from the routing table output of router B? The default-information originate command has been entered on A.Refer to the exhibit. A network consists of multiple routers. What can be verified when the show ip protocols command is issued on one of the routers in the network? routing protocol configuration in use for IP on this routerRefer to the exhibit. All routers are configured with valid interface addresses in the indicated networks and are running RIPv1. The network is converged. Which routes are present in the routing tables?All routers have all /30 routes. Routers A and E also have some of the /24 routes in their routing table.Which two statements are true regarding the characteristics of RIPv1? (Choose two). It is a distance vector routing protocol.The data portion of a RIP message is encapsulated into a UDP segment.Which command or set of commands will stop the RIP routing process?RouterB(config)# no router ripRefer to the exhibit. All routers in the exhibit are running RIP v1. The network administrator issues the show ip route command on router A. What routes would ap pear in the routing table output if the network is converged? (Choose two).R 192.168.2.0/24 [120/1]R 10.10.1.0/24 [120/2]Which command will display RIP activity as it occurs on a router?debug ip ripRefer to the output from the show ip route command. What can be concluded from the output of this router command?There are two equal cost paths to network 1.0.0.0.Refer to the exhibit. Router1 and Router2 are running the RIPv1 protocol. The network administrator configures the command network 10.1.0.0 on Router1. What network will Router1 advertise to Router2?10.0.0.0/8Refer to the exhibit. Pings between the serial interfaces of the routers are successful. Hosts on each LAN can ping the Fa0/0 interface of the router to which they are directlyconnected through the switch. However, pings between hosts on the 10.1.1.0/24 and 10.1.2.0/24 networks are unsuccessful. What is a likely cause of this problem?RIP is configured incorrectly on R1.What will happen if an interface IP address is entered for the address portion of the network command in a RIPv1 configuration instead of a network address?All interfaces in the same classful network as the configured address will be included in the RIPv1 routing process.Refer to the exhibit. All routers that are shown are running the RIP routing protocol. All unknown IP traffic must be forwarded to the ISP. What router or set of routers are recommended to have both a default route and the default-information originate command issued to implement this forwarding policy?only the gateway routerCCNA 2 - Module 6What two advantages does CIDR provide to a network? (Choose two.)reduced routing table sizereduced routing update trafficRefer to the exhibit. The network administrator wants to create a subnet for the po int-to-point connection between the two routers. Which subnetwork mask would provide enough addresses for the point-to-point link with the least number of wasted addresses?255.255.255.252Refer to the exhibit. A network engineer is summarizing the two groups of routes on router R1 shown in the exhibit. Which summarization will work for all the subnets?192.168.0.0/21Which of the following are contained in the routing updates of classless routing protocols? (Choose two.)32-bit addresssubnet maskWhich of the following problems does VLSM help to alleviate?the shortage of IP addressesWhat does VLSM allow a network administrator to do?utilize multiple subnet masks in the same IP address spaceRefer to the exhibit. What subnet mask will be applied if Router A sends a RIPv1 update for the network 172.16.1.0 to Router B?24Refer to the exhibit. The network administrator wants to minimize the number of entries in Router1’s routing table. What should the administrator implement on the network?CIDRA router has a summary route to network 192.168.32.0/20 installed in its routing table. What range of networks are summarized by this route?192.168.32.0 – 192.168.47.0/24A network administrator is tasked with dividing up a class C network among the QA, Sales, and Administration departments. The QA department is made up of 10 people, the Sales is made up of 28 people, and the Administration has 6. Which two subnets masks adequately address the QA and Sales departments? (Choose two.)255.255.255.224 for Sales255.255.255.240 for QAIn the network shown in the graphic, three bits were borrowed from the host portion of a Class C address. How many valid host addresses will be unused on the three point-to-point links combined if VLSM is not used?84A Class C address has been assigned for use in the network shown in the graphic. Using VLSM, which bit mask should be used to provide for the number of host addresses required on Router A, while wasting the fewest addresses?/27An additional subnet is required for a new Ethernet link between Router1 and Router2 as shown in the diagram. Which of the following subnet addresses can be configured in this network to provide a maximum of 14 useable addresses for this link while wasting the fewest addresses?192.1.1.224/28Which three interior routing protocols support VLSM? (Choose three.)OSPFRIP v2EIGRPRefer to the exhibit. The number of required host addresses for each subnet in a network is listed in the exhibit. This number includes the host address requirements for all router ports and hosts on that subnet. After all device and router port address assignments are determined, what will be the total number of unused host addresses available?29Refer to the exhibit. In the network that is shown, the router interfaces are assigned the first address ineach subnet. Which IP address would be usable for a host on one of the LANs in this network?192.168.2.130/25Refer to the exhibit. Which address is a broadcast address for one of the subnets that are shown in the exhibit?192.168.4.15/29Refer to the exhibit. A network administrator needs to create two subnetworks from 10.0.0.0/8 for a router running RIPv2. The Admin subnet requires 120 hosts and the Sales subnet requires 58 hosts. The network administrator assigned 10.0.1.128/25 to the Admin subnet. The Sales subnet i s given 10.0.1.192/26. What will be the result of this addressing scheme?Because RIPv2 does not support VLSM, the subnet masks will not be allowed.The subnets overlap and will be rejected by the router.Refer to the exhibit. A network technician enters the static route in R1 needed to reach network 10.1.1.0/24. A ping from the S0/0/0 interface on R1 to host B fails. The technician begins testing the network and has the following results:1. pings from R1 to the S0/0/0 interface on R2....successful2. pings from R1 to the Fa0/0 interface on R2....successful3. pings from host B to hosts on the 10.1.1.0/24 network....successful4. pings from host B to the Fa0/0 interface on R2....successful5. pings from R2 to host B....successful.The default gateway on host B is not correctly set.What is a supernet?a summarization of classful addressesCCNA 2 - Module 7Refer to the exhibit. If all routers are running RIP version 2, why is there no route for the 192.168.1.32/27 network?Rip version 2 will auto summarize routes by default.Refer to the exhibit. Which two statements are true? (Choose two.)Router1 will install a route to 192.168.0.0/20Router2 will not install a route to 192.168.16.0/20Refer to the exhibit. Which command on which router will allow Router1 to learn about the 192.168.0.0/20 network?Router2(config-router)# version 2What are two reasons to implement RIP version 2 rather than RIP version 1? (Choose two.)RIP version 2 supports VLS M.。
1请参见图示。
对于发往192.168.2.0 的数据包,R2 会采取什么操作?它会丢弃数据包。
它会通过S0/0/0 接口转发数据包。
它会通过Fa0/0 接口转发数据包。
它会将数据包转发给R1。
2请参见图示。
R1 会使用哪一总结地址来向R2 通告其网络?3请参见图示。
尽管R2 已配置正确,但主机A 还是无法访问Internet。
可以在R1 上配置哪两条可让主机A 访问Internet 的静态路由?(选择两项。
)ip route .0 0.0.0.0 Fa0/0ip route .0 0.0.0.0 Fa0/1ip routeip routeip route 209.165.202.0 255.255.255.0 .14请参见图示。
网络管理员已按图示配置了R1,并且所有接口都运作正常。
但从R1 ping 172.16.1.1 时失败。
造成此问题的原因可能是什么?R1 上的串行接口配置有误。
默认路由配置有误。
必须在R1 上发出default-information originate命令。
必须在R1 上禁用自动总结。
5请参见图示。
所有接口都已编址,并且运行正常。
网络管理员在主机A 上运行了tracert命令。
得到这种输出的原因可能是什么?(选择两项。
)主机A 缺少网关或配置不正确。
主机B 缺少网关或配置不正确。
R1 的路由表中缺少192.168.1.0/24 的条目。
R2 的路由表中缺少192.168.1.0/24 的条目。
R1 的路由表中缺少192.168.2.0/24 的条目。
R2 的路由表中缺少192.168.2.0/24 的条目。
6请参见图示。
从主机A 到主机B 的ping 成功,但从主机A ping 在Internet 上正常运行的主机却失败了。
此问题的原因是什么?R1 的快速以太网接口被禁用。
其中一条默认路由配置有误。
未在这两台路由器上配置路由协议。
主机A 上尚未配置默认网关。
7 网络管理员使用RIP 路由协议在一个自治系统内实施路由。

CCNA路由和交换网络简介第章探索网络练习和答案(二)CCNA路由和交换网络简介第章探索网络练习和答案本文将为大家介绍CCNA路由和交换网络简介第章探索网络练习和答案,帮助大家更好地了解网络知识。
一、练习题1. 什么是计算机网络?2. 什么是协议?3. OSI模型中,每一层的作用是什么?4. 什么是TCP/IP协议?5. 什么是IP地址?6. 什么是子网掩码?7. 什么是路由器?8. 什么是交换机?二、答案解析1. 计算机网络是指两台或两台以上计算机通过通信设备和通信线路连接起来,以实现信息交换和资源共享的系统。
2. 协议是计算机网络中用于规定通信双方之间的通信规则和格式的一种约定。
3. OSI模型中每一层的作用如下:- 应用层:提供应用程序之间的通信和数据交换服务。
- 表示层:负责处理数据格式的转换、数据加密和解密等。
- 会话层:负责建立、管理和终止会话。
- 传输层:负责数据的传输和流量控制。
- 网络层:负责数据的路由和寻址。
- 数据链路层:负责数据的传输和错误检测。
- 物理层:负责数据的传输和物理连接。
4. TCP/IP协议是一种网络协议,它是互联网的基础协议,包括TCP和IP两个部分。
TCP负责数据的分段和重组,IP负责数据的路由和寻址。
5. IP地址是指互联网协议地址,它是用于标识网络上设备的一种地址,由32位二进制数表示。
6. 子网掩码是一种用于划分网络的地址掩码,它与IP地址一起使用,用于确定网络地址和主机地址的范围。
7. 路由器是一种网络设备,它负责将数据包从一个网络传输到另一个网络,是网络中的重要组成部分。
8. 交换机是一种网络设备,它负责在局域网中转发数据包,是局域网中的重要组成部分。
以上就是本文为大家介绍的CCNA路由和交换网络简介第章探索网络练习和答案,希望对大家有所帮助。
第一章:正确答案:2.4.5•解析:由于不需要使用网络设备和专用服务器,对等网络易于创建,复杂性更低,且成本更少。
而且对等网络也没有集中管理。
这种网络安全性更低,不可扩展,而且那些同时充当客户端和服务器的设备可能性能更差正确答案:1解析:正确答案: 3.5解析:选择网络介质的条件包括:所选介质可以成功传送信号的距离、要安装所选介质的环境、必须传输的数据量和速度以及介质和安装的成本。
正确答案:3和4解析:终端设备上的应用程序可以生成数据,更改数据内容并且负责启动封装过程。
正确答案:1和4解析:终端设备会发出通过网络传输的数据。
中间设备会在链路发生故障时通过备用路径传输数据,并且会过滤数据传输以增强安全性。
网络介质提供网络消息的传输通道。
正确答案:4解析:外联网是公司外部的人或企业合作伙伴访问数据的网络区域。
内部网只描述通常仅供内部人员访问的网络区域。
当设备连接到有线网络时,有线LAN 会受BYOD(自带设备)影响。
使用大学无线LAN 的设备多为平板电脑和智能手机。
大学生主要使用无线WAN 来访问他们的手机运营商网络。
.正确答案:2解析:由于通过Internet 可以联系在线供应商,所以家庭用户通过Internet 进行网上购物。
内联网基本上是仅供内部使用的局域网。
外联网是外部合作伙伴访问组织内部特定资源的网络。
家庭用户并不一定使用LAN 来访问Internet。
例如,PC 可以通过调制解调器直接连接到ISP。
正确答案:1解析:内部网这个术语用于表示一个组织的私有局域网和广域网连接。
内部网的设计旨在仅允许该组织的成员、员工或其他获得授权的人员进行访问。
正确答案:2和4解析:电缆和DSL 均能实现高带宽、始终联网,并提供到主机计算机或LAN 的以太网连接。
10正确答案:2和3解析:移动电话连接需要使用移动电话网络。
卫星连接通常用于家庭或企业外部不便使用物理布线的位置。
11正确答案:2解析:当对网络资源的请求超出了可用容量时,网络就会变得拥堵。
第1章路由和数据包转发介绍1.下面哪些路由器的组成和它的功能是匹配的?DA.Flash:永久的储存bootstrap程序B.ROM:永久地存储启动配置文件C.NVRAM:永久地存储操作系统镜像D.RAM:存储路由表和ARP缓存2.哪两个命令可以用来检查给路由器串行接口分配的IP地址?A、EA.show interfacesB.show interfaces ip briefC.show controllers allD.show ip configE.show ip interface brief3.下面哪些命令可以设置特权模式口令为“quiz”?AA.R1(config)# enable secret quizB.R1(config)# password secret quizC.R1(config)# enable password secret quizD.R1(config)# enable secret password quiz4.哪个路由原理是正确的?CA.如果一个路由器在它的路由表中具有确定的信息,那么所有邻接的路由也拥有同样的信息B.从一个网络到另外一个网络路径的路由信息意味着存在着反向(或返回)路径的路由信息C.每个路由器根据它自己路由表中的信息,独立作出路由判断D.每个路由器根据它自己和邻居路由表中的信息,独立作出路由判断5.动态路由协议执行哪两个任务?B、DA.发现主机B.更新和维护路由表C.传播主机默认网关D.网络发现E.分配IP地址6.网络工程师正在配置一个新的路由器。
接口已经配置好了IP地址,并且已经激活。
但是还没有配置路由协议或静态路由。
这时路由表中出现的是什么路由?CA.默认路由B.广播路由C.直接路由D.没有路由,路由表也是空的7.下面哪两个对于路由器转发数据包的描述是正确的?B、DA.如果数据包是去往远程网络的,那么路由器会向所有到这个网络的下一跳接口发送该数据包B.如果数据包是去往直连网络的,那么路由器会向路由表中所指示的外出接口发送C.如果数据包是去往远程网络的,那么路由器会根据路由主机表来发送该数据包D.如果数据包是去往远程网络的,那么路由器会向路由表中所指示下一跳IP发送E.如果数据包是去往直连网络的,那么路由器会根据目的MAC地址发送该数据包F.如果数据包是去往直连网络的,那么路由器会转发数据包到下一跳VLAN的交换机8.关于路由协议使用的度量的哪个描述是正确的?AA.度量是路由协议用来检测给定路由的一个测量值B.度量是思科专有的用来转换距离到标准单元的方法C.度量表示了对于所有路由协议中发生的数据包丢失的数量的一个统计值D.路由器使用度量lai 决定哪些包是错误的和要被丢失的9.网络管理员在路由器上配置了ip rout 0.0.0.0 0.0.0.0 serial 0/0/0命令。
第2章 配置网络操作系统1 下列哪两项是闪存的特征?(请选择两项。
)闪存提供非易失性存储。
当设备启动时,闪存接收来自 RAM 的 IOS 副本。
重新启动时闪存中的内容可能会丢失。
闪存是思科交换机的组件,但不是思科路由器的组件。
闪存的内容可以被覆盖。
当设备启动时,闪存会保存 IOS ,并将 IOS 副本传输到 RAM 中。
尽管闪存可以升级和覆盖,但它是非易失性存储器。
设备重新启动或断开电源时,闪存内容仍会保留。
答案 说明 最高分值correctness of response Option 1 and Option 5 are correct.1 point for each correct option. 0 points if more options are selected than required.22 网络管理员计划在总部的几个路由器和交换机上升级 IOS 。
继续选择和升级 IOS 之前必须回答哪三个问题?(请选择三项。
)设备是否位于同一 LAN ?设备是否有足够的 NVRAM 来存储 IOS 映像?什么型号的路由器和交换机需要升级?路由器和交换机上安装了哪些端口?路由器和交换机是否有足够的 RAM 和闪存来用于提议的 IOS 版本?设备需要哪些功能?启动配置文件存储在 NVRAM 中,而不是 IOS 中。
升级到新 IOS 版本时应考虑的重要因素包括可用 RAM 和闪存数量、设备类型和型号以及所需功能。
答案 说明 最高分值correctness of response Option 3, Option 5, and Option 6 are correct.1 point for each correct option. 0 points if more options are selected than required.33 当在安全环境下执行初始配置时,下列哪个程序可用来访问 Cisco 2960 交换机?使用 Telnet 通过网络远程访问交换机。
1. What are two possible reasons a router would not load a valid IOS from flash? (Choose two.)The configuration register is set to 0×2142.The first boot system command executed in the startup configuration file is boot system rom.The configuration register is set to 0×2100.The boot field is set to the hexadecimal number 2.The startup configuration file is missing or corrupt.2. What are two recommended uses of login banners? (Choose two.)to display security warning messagesto welcome any user to the routerto warn people about misusing privileged EXEC modeto identify circuits and other devices connected to the routerto announce a scheduled system shutdown3.Router A and Router B have been correctly configured to use RIP as a dynamic routing protocol and all intefaces on Router A and Router B are reporting "interface is up, line protocol is up" status. RIP is then configured onRouter C using the following commands:RouterC(config)# router ripRouterC(config-router)# network 192.168.4.0RouterC(config-router)# network 172.16.0.0If no additional routing is configured on Router A, Router B, and Router C, what will be the result?Networks 192.168.12.0/24, 192.168.4.0/24, and 172.16.0.0/16 will be unreachable from Router A.Router A will have no knowledge of network 192.168.12.0/24, but will have routes to networks 192.168.4.0/24 and 172.16.0.0/16.All networks shown in the graphic will be reachable by Router A, Router B, and Router C.Networks 192.168.4.0/24 and 172.16.0.0/16 will be unreachable from Router A and Router B.4. What are the primary functions of a router? (Choose two.) determine the best path for packetsprevent collisions on the network LANregulate flow control between sender and receiverprovide domain name resolutionforward packets to the appropriate interface5. What are some reasons to change the configuration register setting? (Choose two.)to force the system to ignore the configuration file stored in NVRAM to monitor password changesto change the POST sequenceto force the router to boot the IOS from NVRAMto force the system into ROM monitor mode6. A network administrator issues the erase startup-config command on a configured router with the configuration register set to 0×2102 and observes the following output:Erasing the nvram filesystem will remove all files! Continue? [Confirm] [OK]Erase of nvram: completeIf the router unexpectedly loses power after this sequence, what will occur when power is restored?The router will enter ROM monitor mode upon completion of the power-on self test (POST).The router will load the last known valid configuration file.The router will enter Rx-boot mode.The router will prompt the user to enter setup mode or to continue without entering setup mode.7. Why are routed protocols important to networking? (Choose two.) Routed protocols detect collisions and fragments.Routers use routed protocols to calculate the best path to a destination. Routed protocols transport data across the network.The fields and formats used within a packet are defined by routed protocols.Routed protocols are used to configure the metrics used by routing protocols.8. The main router of XYZ company has enough flash and RAM to store multiple IOS images. An administrator wants to upload a second IOS image from a TFTP server to the flash of the router. Which method will accomplish this task?Paste the IOS filename to the command line of the router while in global configuration mode. Press enter. Then issue the copy tftp flash command.Use the setup utility to load the new image to flash.Copy the IOS image file from a TFTP server using the command copy filenameip address flash .Copy the IOS image file from a TFTP server using the command copy tftp flash. When prompted, provide the IP address or name of the TFTP server and the IOS image filename.9.A network administrator has a console connection to the Fremantle router. Pings to Melville are successful, but pings to Cottesloe and Nedlands fail. What could be a first step in troubleshooting the problem?Use an extended ping from Fremantle to each router in the network.Use the show interfaces command from a Telnet session on Melville to check the connection to Cottesloe.Use the traceroute command to discover exactly which link in the network is down.Use the show cdp neighbors detail command from Fremantle to gather information about all Cisco routers in the network.10.Refer to the exhibit. The new security policy for the company allows all IP traffic from the Engineering LAN to the Internet while only web traffic from the Marketing LAN is allowed to the Internet. Which ACL can be applied in the outbound direction of Serial 0/1 on the Marketing router to implement the new security policy?access-list 197 permit ip 192.0.2.0 0.0.0.255 anyaccess-list 197 permit ip 198.18.112.0 0.0.0.255 any eq wwwaccess-list 165 permit ip 192.0.2.0 0.0.0.255 anyaccess-list 165 permit tcp 198.18.112.0 0.0.0.255 any eq wwwaccess-list 165 permit ip any anyaccess-list 137 permit ip 192.0.2.0 0.0.0.255 anyaccess-list 137 permit tcp 198.18.112.0 0.0.0.255 any eq wwwaccess-list 89 permit 192.0.2.0 0.0.0.255 anyaccess-list 89 permit tcp 198.18.112.0 0.0.0.255 any eq www11.Hosts from the Limerick LAN are not allowed access to the Shannon LAN but should be able to access the Internet. Which set of commands will create a standard ACL that will apply to traffic on the Shannon router interface Fa0/0 implementing this security?access-list 42 deny 172.19.123.0 0.0.0.255 192.0.2.0 0.0.0.255 access-list 42 permit anyaccess-list 56 deny 172.19.123.0 0.0.0.255access-list 56 permit anyaccess-list 61 deny 172.19.123.0 0.0.0.0access-list 61 permit anyaccess-list 87 deny ip any 192.0.2.0 0.0.0.255access-list 87 permit ip any12. Which of the following commands will correctly configure an extended ACL? (Choose two).Router(config)# access-list 18 permit tcp host 192.168.73.3 eq 25Router(config)# access-list 102 permit tcp 10.43.0.0 0.0.255.255 any eq 80Router(config)# access-list 187 permit tcp host 192.168.42.34 172.29.0.0 0.0.255.255 eq 23Router(config)# access-list 99 permit host 10.217.32.3Router(config)# access-list 128 permit tcp host 192.168.100.31 eq 2313. What are the results of setting the boot field bits in the configuration register to "0000"? (Choose two.)The startup-config file will be ignored at bootup.The router will load the IOS from Flash.The router will enter ROM monitor mode upon reload.The router will enter boot ROM mode and have limited capabilities. The administrator can enter the b command to manually boot the IOS.14.Refer to the exhibit. Router D interface S0 on has gone down. What is the maximum time that will elapse before Router A learns that network 168.58.14.0 is down?5 seconds13 seconds17 seconds25 seconds30 seconds77 seconds15. During initial router bootup the following line appears: "NVRAM invalid, possibly due to write erase."What are two possible reasons for this result? (Choose two.)The startup-config file was not saved to RAM before reboot.The IOS has been erased.The router has not been configured.The startup-config file cannot be located.The router will not enter initial configuration dialog.16.The Suffolk router is directly connected to the networks shown in the graphic and has a default route that points to the Richmond router. All interfaces are active and properly addressed. However, when the workstation on network 172.29.5.0/24 sends a packet to destination address 172.29.198.5, it is discarded by the Suffolk router. What can be a reason for this result?The ip classless command is not enabled on the Richmond router.The route was ignored if the Richmond router did not include the 172.29.198.0/24 network in its routing updates.The Richmond router is in a different autonomous system than the Suffolk router.The ip subnet-zero command was not configured on the Suffolk router.The ip classless command is not enabled on the Suffolk router.17. access-list 199 deny tcp 178.15.0.0 0.0.255.255 any eq 23 access-list 199 permit ip any anyAssuming this ACL is correctly applied to a router interface, which statements describe traffic on the network? (Choose two.)All FTP traffic from network 178.15.0.0 will be permitted.All Telnet traffic destined for network 178.15.0.0 will be denied.Telnet and FTP will be permitted from all hosts on network 178.15.0.0 to any destination.Telnet will not be permitted from any hosts on network 178.15.0.0 to any destination.Telnet will not be permitted to any host on network 178.15.0.0 from any destination.18.What facts can be determined from the highlighted text shown in the exhibit? (Choose two.)A weak encryption was applied to all unencrypted passwords.The enable password is now more secure than the enable secret password.An MD5 hashing algorithm was used on all encrypted passwords.Any configured user EXEC mode or Telnet passwords will be encrypted in this configuration.The service password-encryption command was used to encrypt all passwords on the router including enable secret.19. What are three features of CDP? (Choose three.)provides information on directly connected devices that have CDP enabled tests Layer 2 connectivityenabled by default on each interfaceprovides a layer of securityused for debugging Layer 4 connectivity issues20. What information can be learned during the initial router bootup? (Choose two.)the configuration register valuethe number and types of interfaces installedthe router model and the amount of memory that is availablethe amount of memory required to load the IOS and configurationthe number of interfaces with connected cables21.What can be concluded from the output shown in the exhibit? (Choose three.)This is a standard IP access list.This is an extended IP access list.The keyword host is implied in the command line access-list 99 deny 10.213.177.76.The wildcard mask must be configured for this access list to function properly.Host 10.213.177.100 will be allowed access to the Serial0/1 interface.22. Which statements are true regarding setup mode? (Choose three.)Press Ctrl-z to terminate setup mode.Enter a question mark (?) for help at any point.Press Spacebar to accept the default settings.Use setup mode to enter complex protocol features.Press Enter to accept the default settings.Press Ctrl-c to abort configuration dialog.23.Refer to the graphic. Which series of commands will create static routes that will allow Router A and Router B to deliver packets destined for LAN A and LAN B, and direct all other traffic to the Internet?RouterA(config)# ip route 10.90.3.0 255.255.255.0 192.168.3.2RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1 RouterB(config)# ip route 0.0.0.0 0.0.0.0 s0/0RouterA(config)# ip route 10.90.3.0 255.255.255.0 192.168.3.2RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1 RouterB(config)# ip route 172.20.20.4 255.255.255.252 s0/0RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1 RouterB(config)# ip route 0.0.0.0 0.0.0.0 s0/024.Which devices can be used to convert the data from a WAN router at the customer site into a form acceptable for use by the WAN service provider? (Choose three.)Ethernet switchDTEmodemhubDCE deviceCSU/DSU25.What will occur when the following ACL is applied inbound to both FastEthernet interfaces of Router A in the graphic?access-list 125 permit tcp 192.168.2.0 0.0.0.255 10.90.3.0 0.0.0.255 eq 23access-list 125 permit tcp 10.90.3.0 0.0.0.255 192.168.2.0 0.0.0.255 eq 23access-list 125 permit tcp 192.168.2.0 0.0.0.255 any eq wwwWorkstations A and B will be able to Telnet to each other. WorkstationA will be allowed to access Web servers on the Internet, while WorkstationB will be denied Internet Web access.Workstations A and B will be able to Telnet to each other. All other traffic will be denied.The ACL will have no effect because it should be applied in the outbound direction on the FastEthernet interfaces.The ACL will deny all traffic because of the implied deny ip any any statement at the end of the ACL.26. Based on this partial output of the show ip route command, which routing protocol is configured on the router?R 172.16.3.0/24 [120/3] via 172.16.2.2, 00:00:27, Serial0/0RIPEIGRPOSPFIGPBGP27.Which of the following are correct statements verified by the router output shown in the graphic? (Choose two.)Layer 3 connectivity exists between BigCity and the devices in the Device ID column.Layer 2 connectivity exists between BigCity and the devices in the Device ID column.All devices shown in the Device ID column use the TCP/IP protocol suite.All devices shown in the Device ID column can be pinged from BigCity.All devices listed in the Device ID column are directly connected to BigCity.28. A network administrator must configure a FastEthernet interface with an IP address. The configuration must also identify the remote site to which the interface is connected. Which set of commands will meet these requirements?StPetersburg(config)# banner San Jose T1StPetersburg(config)# interface fa0/0StPetersburg(config-if)# ip address 172.26.155.5 255.255.255.252StPetersburg(config)# interface fa0/0StPetersburg(config-if)# ip address 172.26.155.5 netmask255.255.255.252StPetersburg(config-if)# description San Jose T1StPetersburg(config)# interface fa0/0StPetersburg(config-if)# ip address 172.26.155.5 255.255.255.252 StPetersburg(config-if)# banner remote site San Jose T1StPetersburg(config)# interface fa0/0StPetersburg(config-if)# ip address 172.26.155.5 255.255.255.252 StPetersburg(config-if)# description San Jose T129. What are the features of a serial interface on a router? (Choose two.) enabled by defaultassigned a unique MAC addressmust be configured as a DCE in lab and production environmentsmust be configured with the default clock rate of 56000may be administratively enabled by using the no shutdown commandmust be configured with a valid IP address and subnet mask in order to forward packets30. Assuming the following ACL is correctly applied to a router interface, what can be concluded about this set of commands? (Choose two.) Router(config)# access-list 165 deny tcp 192.28.115.0 0.0.0.255 172.20.0.0 0.0.255.255 eq 23Router(config)# access-list 165 permit ip any anyThis is a standard IP access list that denies network 192.28.115.0 Telnet access to the 172.20.0.0 network.All Telnet traffic destined for 172.20.0.0 from any network will be denied access.Network 192.28.115.0 is denied Telnet access to the 172.20.0.0 network. Network 172.20.0.0 is denied Telnet access to the 192.28.115.0 network.All FTP and HTTP traffic destined for 172.20.0.0 will be permitted access.31. Which two steps describe how to create a functional physical connection between a router console and a terminal? (Choose two.)Use a crossover cable to connect the terminal serial port to the router console port.Use a rollover cable to connect the terminal NIC to the router console port.Use an RJ-45 to DB-9 adapter on the terminal serial port to connect to the cable going to the router console.Use a transceiver to connect a straight-through cable to the router console port.Use a straight-through cable to connect the router console port to the terminal NIC.Use a rollover cable to connect from a terminal serial port to the router console port.32. What critical information about the status of the router can be found in the outputs of both the show interfaces and show protocols commands? (Choose two.)the Layer 3 address of each configured interfacethe routing protocol configured to forward updates out of each interface the operational status of each interfacetraffic statistics for each interfacewhether the interface is configured as a DTE or DCE33.The following access list has been created to prevent traffic from the 192.0.2.63 host on the Sales LAN from accessing servers and hosts on the Payroll LAN.access-list 26 deny host 192.0.2.63access-list 26 permit anyRefer to the exhibit. Which group of commands will properly place the access list so that only the host on the Sales LAN is denied access to the 172.29.7.0 network but all other traffic is permitted?Payroll(config)# interface fa0/0Payroll(config-if)# ip access-group 26 outPayroll(config)# interface fa0/1Payroll(config-if)# ip access-group 26 outSales(config)# interface fa0/1Sales(config-if)# ip access-group 26 inSales(config)# interface fa0/0Sales(config-if)# ip access-group 26 out34.Refer to the exhibit. Assuming default metrics are used and the networkis fully converged, which path will RIP use to send a packet from Router A to Router F?A, D, E, FA, B, D, E, FA, C, D, E, G, FA, B, D, E, G, F35.Refer to the graphic. Communication is needed between the LAN connected to the fa0/0 interface of the Kansas router and the fa0/0 interface of the Maine router. All hosts on those LANs also need connectivity to the Internet. Which commands will allow this communication? (Choose three).Kansas(config)# ip route 192.168.6.0 255.255.255.0 172.18.64.2Kansas(config)# ip route 192.168.6.0 255.255.255.0 s0/1Kansas(config)# ip route 0.0.0.0 0.0.0.0 s0/1Maine(config)# ip route 192.168.6.0 255.255.255.0 172.18.64.1Maine(config)# ip route 0.0.0.0 0.0.0.0 s0/1Maine(config)# ip route 172.16.32.0 255.255.255.0 172.18.64.236. Why are interface descriptions used in router configurations? (Choose three).to enable support personnel to easily identify networks and customers that may be affected by a possible interface issueto provide comments on the interface without affecting the router functionalityto display access warning messages before users enter the interface configuration modeto eliminate the need to use IP addresses when using the ping and telnet commandsto identify the purpose and location of the interface37.A network administrator has enabled RIP on routersB andC in the network diagram. Which of the following commands will prevent RIP updates from being sent to Router A?A(config)# router ripA(config-router)# passive-interface S0/0B(config)# router ripB(config-router)# network 192.168.25.48B(config-router)# network 192.168.25.64A(config)# router ripA(config-router)# no network 192.168.25.32B(config)# router ripB(config-router)# passive-interface S0/0A(config)# no router rip38. What could a Cisco support technician learn from the IOS filename c2600-d-mz.121-3? (Choose three.)the format of the filethe RAM memory requirements of the filethe version number of the filethe size of the filethe device platform of the file39.While planning an IOS upgrade, the administrator issues the show version command. Based on the output in the graphic, what is the current IOS boot location?RAMNVRAMFlashROM40. A new technician must add boot system commands to one of the department routers. Which available commands will the router return as output when the command shown below is entered? (Choose two.)Router(config)# boot system ?RAMNVRAMIOSIP AddressTFTPFLASH41. From the running-config, the following configuration entries are displayed:Router(config)# line vty 0 2Router(config-line)# password g8k33prRouter(config-line)# loginWhat can be interpreted from the exhibited configuration? (Choose two.)Three Telnet lines are available for remote access.Two Telnet lines are available for remote access.Future configuration of the remaining Telnet lines will require the password to be set to g8k33pr.To login to the remote device, g8k33pr will be used as the Telnet and secret password.Remote access to this local router will require a Telnet password of g8k33pr.42. Which router component stores the information that is displayed by the show running-config command?flashNVRAMRAMROM43. What are two characteristics of the support for Telnet within Cisco IOS software? (Choose two.)Up to five separate Telnet lines are supported by default in standard edition IOS files.For security purposes, Telnet sessions are required to be established from the privileged mode.A router can host simultaneous Telnet sessions.Once established, a Telnet session can remain operational regardless of network status.Telnet tests wireless connectivity and does not require a physical connection between devices to gain remote access.44. Which router components and operations are correctly described? (Choose two.)RAM – stores the ARP cacheNVRAM – store the operating systemROM – stores the backup IOSPOST – verifies the validity of the running-configFlash – executes diagnostics at bootupDRAM – loads the bootstrap45.Given the output shown in the exhibit, in what order and location will the router search for the IOS if no boot system commands are found in the startup-config file?ROM, Flash, TFTP serverFlash, NVRAM, RAMROM, TFTP server, FlashRAM, Flash, NVRAMFlash, TFTP server, ROM46. What can a network administrator do to recover from a lost router password?perform a reload or resettelnet from another router and issue the show running-config command to view the passwordboot the router to ROM monitor mode and configure the router to ignore NVRAM when it initializesboot the router to bootROM mode and enter the b command to load the IOS manually47.Neither router in the exhibit has a host table or DNS available. The interfaces and passwords have been correctly configured. Which of the following commands will initiate a Telnet session? (Choose two.)Tottenham# telnet OxfordTottenham> telnet 198.18.139.1Oxford# connect 198.18.139.0Oxford> connect TottenhamOxford# telnet TottenhamOxford# 198.18.139.248. If a PC does not have network connectivity to a router, which router port can be used to establish communication?consoleEthernetserialVTY。
ERouting Chapter 2 - CCNA Exploration: 路由协议和概念 (版本 4.0)1当外发接口不可用时,路由表中的静态路由条目有何变化?该路由将从路由表中删除。
路由器将轮询邻居以查找替用路由。
该路由将保持在路由表中,因为它是静态路由。
路由器将重定向该静态路由,以补偿下一跳设备的缺失。
2 哪两种设备负责将来自 WAN服务提供商的数据转换为路由器可以接受的形式?(选择两项。
)路由器的串行端口调制解调器交换机路由器的以太网端口CSU/DSU 设备DTE 设备3请参见图示。
要使WinterPark 和Altamonte 路由器能够传送来自每个LAN 的数据包并将所有其它流量转到Internet,应命令来配置静态路由?WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 0.0.0.0 0.0.0.0 s0/1WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 198.18.222.0 255.255.255.255 s0/1WinterPark(config)# ip route 172.191.67.0 255.255.255.0 192.168.146.1WinterPark(config)# ip route 0.0.0.0 0.0.0.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2WinterPark(config)# ip route 172.191.67.0 255.255.255.0 192.168.146.1Altamonte(config)# ip route 10.0.234.0 255.255.255.0 192.168.146.2Altamonte(config)# ip route 0.0.0.0 0.0.0.0 s0/04路由器配置有到达每个目的网络的静态路由。
以下是针对您未获得满分的试题给出的反馈。
某些交互式试题可能不显示您的答案。
分项分数:1哪个接口是包含用于管理24 个端口以太网交换机的IP 地址的默认位置?正确响应您的响应VLAN 1Fa0/0Fa0/1连接到默认网关的接口VLAN 99此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.1 使用初始设置配置交换机2下列关于使用全双工快速以太网的陈述中,哪三项是正确的?(请选择三项。
)正确响应您的响应通过双向数据流改善了性能。
由于禁用了设备上的冲突检测功能,因此性能得到了改善。
节点以全双工单向数据流运行。
由于网卡可以检测到冲突,因此性能得到了改善。
全双工快速以太网在两个方向上提供100% 的效率。
由于网卡能更快速地处理帧,因此延迟减少了。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.2 配置交换机端口3使用mdix auto 配置命令会对交换机上的以太网接口产生什么影响?正确响应您的响应自动检测双工设置自动检测接口速度自动检测铜电缆类型自动将第一个检测到的MAC 地址分配给接口此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.2 配置交换机端口4在Cisco IOS 软件无法加载的情况下,网络管理员需要哪种类型的电缆将PC 与交换机连接才能恢复它?正确响应您的响应同轴电缆控制台电缆交叉电缆直通电缆因为交换机上没有运行Cisco IOS 软件,所以管理员需要使用控制台电缆将PC 连接到交换机控制台端口,比便将来自PC 的软件转移到交换机。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.1 使用初始设置配置交换机5在对连接问题进行故障排除时,网络管理员发现交换机端口状态LED 在绿色和琥珀色之间跳转。
此LED 表示什么?正确响应您的响应该端口没有链路。
该端口遇到了错误。
该端口管理性关闭。
有一台计算机正在使用错误的电缆连接到该端口。
该端口拥有一个具有正常流量活动的活动链路。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.1 使用初始设置配置交换机6生产交换机重新加载并以显示Switch> 提示符结束。
可确定以下哪两项事实?(请选择两项。
)正确您的响应响应POST 正常执行。
启动过程被打断。
此路由器上RAM 或闪存不足。
找到并重新加载了完整版本的Cisco IOS。
路由器未位于闪存中的Cisco IOS,因此默认在ROM 中。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.1 使用初始设置配置交换机7下列哪条命令可以显示某个特定接口的auto-MDIX 设置信息?正确响应您的响应show interfacesshow controllersshow processesshow running-config要检查某个特定接口的Auto-MDIX 设置,应当使用show controllers ethernet-controller 命令和关键字 phy 。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.2 配置交换机端口8 请参见图示。
基于show interface 命令输出,在连接到Fa0/1 的链路上可能存在什么介质问题?正确响应您的响应接口上的带宽参数可能过高。
可能存在网卡故障的问题。
链路上可能存在过多电子干扰和噪音。
连接主机到端口Fa0/1 的电缆可能过长。
接口可配置为半双工。
不断升级的CRC 错误通常说明在将数据从主机传输到交换机的过程中已对数据作了修改。
这通常是由链路上高强度的电磁干扰造成的。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.1.2 配置交换机端口9 请参见图示。
网络管理员要将Switch1 配置为允许SSH 连接并禁止Telnet 连接。
网络管理员应如何更改图中所示配置才能满足此要求?正确响应您的响应使用SSH 版本1。
重新配置RSA 密钥。
在其它线路上配置SSH。
修改transport input命令。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.2.1 安全远程访问10哪种协议或服务可以发送包含Cisco IOS 软件版本的发送设备的广播,并且其数据包可能被网络上的恶意主机所捕获?正确响应您的响应CDPDHCPDNSSSHCDP 可以发送包含诸如设备IP 地址和Cisco IOS 软件版本等信息的定期广播。
运行数据包捕获应用程序的节点可以收到这些数据包并恶意使用它们。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.2.2 LAN 中的安全问题11在哪种类型的攻击中,一个恶意节点可以请求DHCP 服务器地址池中的所有可用IP 地址,从而阻止合法主机获取网络访问权限?正确响应您的响应CAM 表溢出MAC 地址泛洪DHCP 耗竭DHCP 监听在DHCP 耗竭攻击中,恶意节点会发送足够多的DHCP 请求,以耗尽DHCP 服务器上的可用地址池。
由于服务器没有可用IP 地址可以分配给尝试加入网络的节点,攻击者因此实现了拒绝服务攻击。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.2.2 LAN 中的安全问题12下列哪种方法能够缓解MAC 地址泛洪攻击?正确响应您的响应增加CAM 表的大小配置端口安全使用ACL 过滤交换机上的广播流量提高交换机端口的速度可以在交换机上配置端口安全,以帮助防止无效的MAC 地址占据MAC 地址表。
ACL 不会协助交换机过滤广播流量,而且增加CAM 表的规模或交换机端口的速度并不能解决这个问题。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.2.2 LAN 中的安全问题13网络安全工具执行哪两项基本功能?(请选择两项。
)正确响应您的响应揭示攻击者可以通过监控网络流量所获取信息的类型向员工就社会工程攻击进行培训模拟对生产网络的攻击以确定任何现有的漏洞编写安全政策文件以保护网络控制对用户设备的物理访问应当使用网络安全工具来衡量当前网络安全的薄弱程度。
它们执行两项基本功能:安全审核和渗透测试。
安全审核可揭示攻击者只需监视网络流量就能收集到哪类信息。
渗透测试是一种网络模拟攻击,用于确定网络在真实攻击中易受攻击的程度。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.2.3 最佳安全实践14下列哪项操作可以将错误禁用交换机端口返回至运行状态?正确响应您的响应在接口上删除并重新配置端口安全。
在接口上发出switchport mode access 命令。
清除交换机上的MAC 地址表。
发出 shutdown 和 no shutdown 接口命令。
当配置了端口安全的交换机端口出现违规时会将违规操作关闭,端口将置为err-disabled 状态。
可以通过关闭接口然后发出no shutdown 命令重新启用接口。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.2.4 交换机端口安全15 请参见图示。
在已实施最佳实践的情况下,应当使用 ip dhcp snooping trust 命令配置哪个S1 交换机端口接口或接口?正确响应您的响应只配置G0/1 端口只配置未使用的端口只配置G0/1 和G0/24 端口只配置G0/2、G0/3 和G0/4 端口只配置G0/1、G0/2、G0/3 和G0/4 端口DHCP 消息应当信任的交换机端口是那些将接收来自DHCP 服务器的DHCP 传入消息的端口。
这包括与DHCP 服务器直接连接的所有端口以及与DHCP 服务器连接的其他交换机的上行链路。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.2.4 交换机端口安全16 请参见图示。
端口Fa0/2 已正确配置。
IP 电话和PC 正常工作。
如果网络管理员想要实现以下目标,哪种交换机配置最适于端口Fa0/2?•不允许任何人断开IP 电话或PC 连接或连接其他一些有线设备。
•如果已连接其他设备,应关闭端口Fa0/2。
•交换机应自动检测IP 电话和PC 的MAC 地址并将这些地址添加至运行配置中。
正确响应您的响应SWA(config-if)# switchport port-securitySWA(config-if)# switchport port-security mac-address sticky SWA(config-if)# switchport port-security mac-address stickySWA(config-if)# switchport port-security maximum 2SWA(config-if)# switchport port-securitySWA(config-if)# switchport port-security maximum 2SWA(config-if)# switchport port-security mac-address sticky SWA(config-if)# switchport port-securitySWA(config-if)# switchport port-security maximum 2SWA(config-if)# switchport port-security mac-address sticky SWA(config-if)# switchport port-security violation restrict端口安全违规的默认模式为关闭端口,因此无需使用switchport port-security violation 命令。
switchport port-security 命令输入时必须没有其他为端口启用端口安全的选项。
然后可以添加其他端口安全选项。
此试题参考以下领域的内容:Routing and Switching Essentials• 2.2.4 交换机端口安全17请参见图示。
可以从显示信息中得出端口安全的什么信息?正确响应您的响应端口已关闭。
端口有两个连接设备。