
配置ASA Dynamic IPsec IOS and
Dynamicallyaddressed PIX with NAT
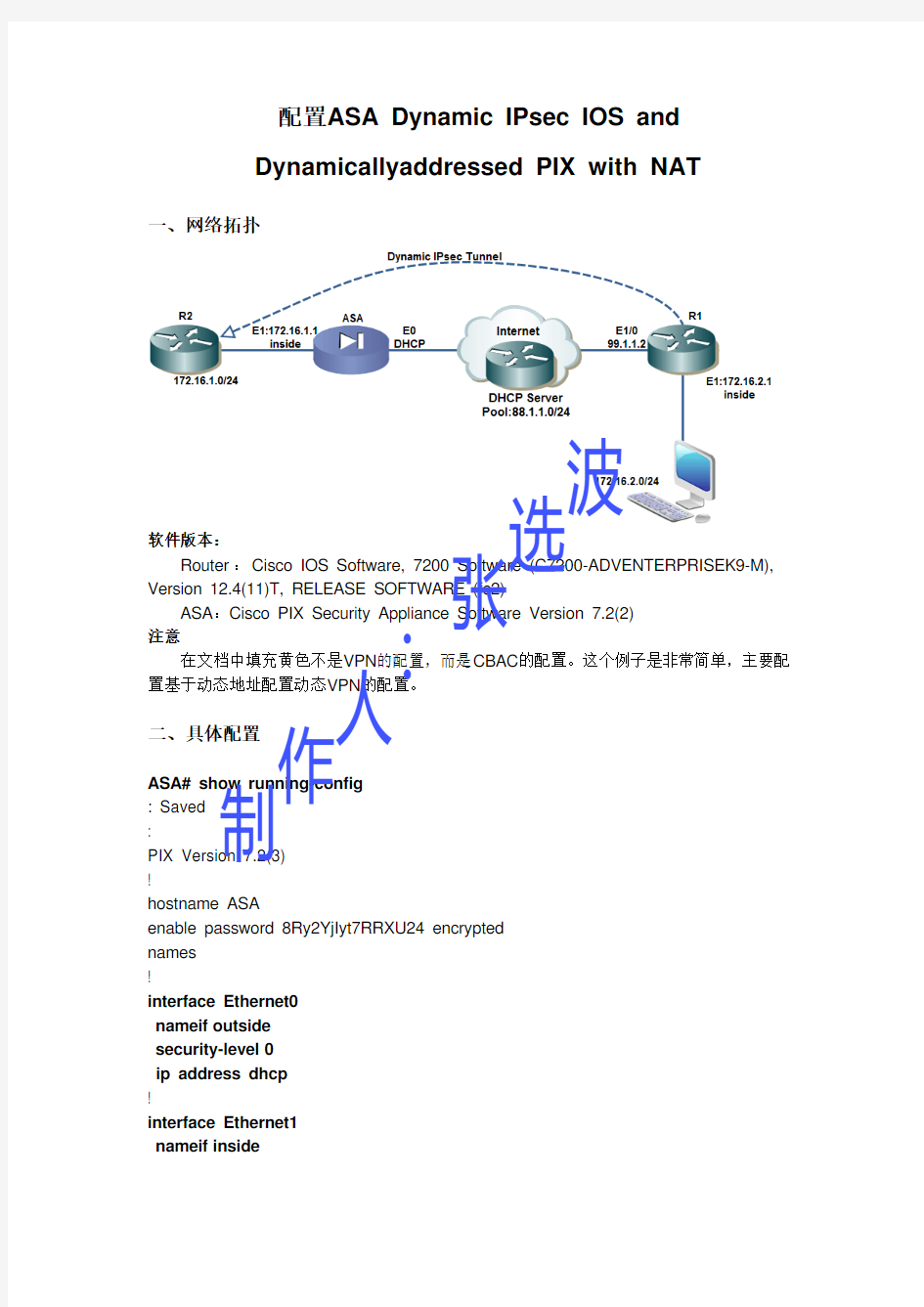
一、网络拓扑
软件版本: Router :Cisco IOS Software, 7200 Software (C7200-ADVENTERPRISEK9-M), Version 12.4(11)T, RELEASE SOFTWARE (fc2) ASA :Cisco PIX Security Appliance Software Version 7.2(2) 注意 在文档中填充黄色不是VPN 的配置,而是CBAC 的配置。这个例子是非常简单,主要配置基于动态地址配置动态VPN 的配置。 二、具体配置
ASA# show running-config
: Saved
:
PIX Version 7.2(3)
!
hostname ASA
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif outside
security-level 0
ip address dhcp
!
interface Ethernet1
nameif inside 制作人:张
选波
security-level 100
ip address 172.16.1.1 255.255.255.0
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list ipsec extended permit ip 172.16.1.0 255.255.255.0 172.16.2.0
255.255.255.0
access-list nonat extended permit ip 172.16.1.0 255.255.255.0 172.16.2.0
255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 interface
nat (inside) 0 access-list nonat
nat (inside) 1 0.0.0.0 0.0.0.0
route outside 0.0.0.0 0.0.0.0 88.1.1.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set vpn esp-des esp-md5-hmac
crypto map map1 10 match address ipsec
crypto map map1 10 set peer 99.1.1.2
crypto map map1 10 set transform-set vpn
crypto map map1 interface outside
crypto isakmp enable outside
crypto isakmp policy 110
authentication pre-share
encryption des
hash md5
group 1
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des 制作人:张选波
hash sha group 2 lifetime 86400 telnet timeout 5 ssh timeout 5 console timeout 0 ! class-map net match default-inspection-traffic ! ! policy-map type inspect dns dnsmap parameters message-length maximum 512 policy-map map1 class net inspect dns dnsmap inspect ftp inspect h323 h225 inspect h323 ras inspect netbios inspect rsh inspect rtsp inspect skinny inspect esmtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp inspect icmp !
service-policy map1 global
tunnel-group 99.1.1.2 type ipsec-l2l
tunnel-group 99.1.1.2 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:00000000000000000000000000000000
: end
R1#show running-config
Building configuration...
Current configuration : 1522 bytes 制作人:张选波
version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname R1 ! boot-start-marker boot-end-marker ! ! no aaa new-model ip cef ! ! ! ! ! multilink bundle-name authenticated ! ! ! ! ! ! ! ! crypto isakmp policy 110
hash md5
authentication pre-share
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set vpn esp-des esp-md5-hmac
!
crypto dynamic-map dymap 10
set transform-set vpn
match address 110
!
!
crypto map map1 10 ipsec-isakmp dynamic dymap
!
! 制作人:张选波
!
!
interface FastEthernet0/0
ip address 172.16.2.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex half
!
interface Ethernet1/0
ip address 99.1.1.2 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex half
crypto map map1
!
interface Ethernet1/1
no ip address
shutdown
duplex half
!
interface Ethernet1/2
no ip address
shutdown
duplex half
!
interface Ethernet1/3
no ip address
shutdown
duplex half
!
ip route 0.0.0.0 0.0.0.0 99.1.1.1
no ip http server
no ip http secure-server
!
!
ip nat inside source list 100 interface Ethernet1/0 overload
!
logging alarm informational
access-list 100 deny ip 172.16.2.0 0.0.0.255 172.16.1.0 0.0.0.255
access-list 100 permit ip 172.16.2.0 0.0.0.255 any
access-list 110 permit ip 172.16.2.0 0.0.0.255 172.16.1.0 0.0.0.255
!
! 制作人:张选波
! ! ! control-plane ! ! ! ! ! ! gatekeeper shutdown ! ! line con 0 exec-timeout 0 0 stopbits 1 line aux 0 stopbits 1 line vty 0 4 ! ! end internet#sh running-config
Building configuration...
Current configuration : 965 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname internet
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
ip cef
! 制作人:张选波
no ip dhcp use vrf connected
!
i p dhcp pool net
network 88.1.1.0 255.255.255.0
default-router 88.1.1.1
!
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
interface FastEthernet0/0
no ip address
shutdown
duplex half
!
interface Ethernet1/0
ip address 88.1.1.1 255.255.255.0
duplex half
!
interface Ethernet1/1
ip address 99.1.1.1 255.255.255.0
duplex half
!
interface Ethernet1/2
no ip address
shutdown
duplex half
!
interface Ethernet1/3
no ip address
shutdown
duplex half
!
no ip http server
no ip http secure-server
!
!
! 制作人:张选波
logging alarm informational ! ! ! ! ! ! control-plane ! ! ! ! ! ! gatekeeper shutdown ! ! line con 0 exec-timeout 0 0 stopbits 1 line aux 0 stopbits 1 line vty 0 4 ! ! end 三、验证配置
R2#ping 172.16.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.2.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 120/169/248 ms
R1#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
99.1.1.2 88.1.1.2 QM_IDLE 1001 0 ACTIVE
IPv6 Crypto ISAKMP SA
制作人:张选波
R1#sh crypto ipsec sa
interface: Ethernet1/0
Crypto map tag: map1, local addr 99.1.1.2
protected vrf: (none)
local ident (addr/mask/prot/port): (172.16.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0)
current_peer 88.1.1.2 port 500
PERMIT, flags={}
#pkts encaps: 54, #pkts encrypt: 54, #pkts digest: 54
#pkts decaps: 54, #pkts decrypt: 54, #pkts verify: 54
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 99.1.1.2, remote crypto endpt.: 88.1.1.2
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet1/0
current outbound spi: 0x4E88B97B(1317583227)
inbound esp sas:
spi: 0x3C896639(1015637561)
transform: esp-des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, crypto map: map1
sa timing: remaining key lifetime (k/sec): (4523857/3328)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x4E88B97B(1317583227)
transform: esp-des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, crypto map: map1
sa timing: remaining key lifetime (k/sec): (4523857/3327)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE 制作人:张选波
outbound ah sas:
outbound pcp sas:
ASA# sh crypto isakmp sa
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 99.1.1.2
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
ASA# sh crypto ipsec sa interface: outside Crypto map tag: map1, seq num: 10, local addr: 88.1.1.2 access-list ipsec permit ip 172.16.1.0 255.255.255.0 172.16.2.0 255.255.255.0 local ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (172.16.2.0/255.255.255.0/0/0) current_peer: 99.1.1.2 #pkts encaps: 54, #pkts encrypt: 54, #pkts digest: 54
#pkts decaps: 54, #pkts decrypt: 54, #pkts verify: 54
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 54, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0 #send errors: 0, #recv errors: 0
local crypto endpt.: 88.1.1.2, remote crypto endpt.: 99.1.1.2
path mtu 1500, ipsec overhead 58, media mtu 1500
current outbound spi: 3C896639
inbound esp sas:
spi: 0x4E88B97B (1317583227)
transform: esp-des esp-md5-hmac none
in use settings ={L2L, Tunnel, }
slot: 0, conn_id: 1, crypto-map: map1
sa timing: remaining key lifetime (kB/sec): (4274994/3458)
IV size: 8 bytes 制作人:张选波
replay detection support: Y
outbound esp sas:
spi: 0x3C896639 (1015637561)
transform: esp-des esp-md5-hmac none
in use settings ={L2L, Tunnel, }
slot: 0, conn_id: 1, crypto-map: map1
sa timing: remaining key lifetime (kB/sec): (4274994/3458)
IV size: 8 bytes
replay detection support: Y
ASA# sh crypto ipsec stats
IPsec Global Statistics
-----------------------
Active tunnels: 1
Previous tunnels: 1
Inbound
Bytes: 5400
Decompressed bytes: 5400
Packets: 54
Dropped packets: 0
Replay failures: 0
Authentications: 54
Authentication failures: 0
Decryptions: 54
Decryption failures: 0
Decapsulated fragments needing reassembly: 0
Outbound
Bytes: 5400
Uncompressed bytes: 5400
Packets: 54
Dropped packets: 0
Authentications: 54
Authentication failures: 0
Encryptions: 54
Encryption failures: 0
Fragmentation successes: 0
Pre-fragmentation successses: 0
Post-fragmentation successes: 0
Fragmentation failures: 0
Pre-fragmentation failures: 0
Post-fragmentation failures: 0
Fragments created: 0
PMTUs sent: 0 制作人:张选波
PMTUs rcvd: 0
Protocol failures: 0
Missing SA failures: 0
System capacity failures: 0
ASA# sh crypto isakmp stats
Global IKE Statistics
Active Tunnels: 1
Previous Tunnels: 1
In Octets: 1160
In Packets: 11
In Drop Packets: 0
In Notifys: 7
In P2 Exchanges: 0
In P2 Exchange Invalids: 0
In P2 Exchange Rejects: 0
In P2 Sa Delete Requests: 0
Out Octets: 1320
Out Packets: 12
Out Drop Packets: 0
Out Notifys: 14
Out P2 Exchanges: 1
Out P2 Exchange Invalids: 0
Out P2 Exchange Rejects: 0
Out P2 Sa Delete Requests: 0
Initiator Tunnels: 1
Initiator Fails: 0
Responder Fails: 0
System Capacity Fails: 0
Auth Fails: 0
Decrypt Fails: 0
Hash Valid Fails: 0
No Sa Fails: 0
ASA# show ip address
System IP Addresses:
Interface Name IP address Subnet mask Method Ethernet0 outside 88.1.1.2 255.255.255.0 DHCP Ethernet1 inside 172.16.1.1 255.255.255.0 manual Current IP Addresses:
Interface Name IP address Subnet mask Method Ethernet0 outside 88.1.1.2 255.255.255.0 DHCP Ethernet1 inside 172.16.1.1 255.255.255.0 manual 制作人:张选波
四、Troubleshoot
ASA# debug crypto isakmp 7
ASA# Mar 09 13:58:42 [IKEv1 DEBUG]: Pitcher: received a key acquire message, spi 0x0 Mar 09 13:58:42 [IKEv1]: IP = 99.1.1.2, IKE Initiator: New Phase 1, Intf inside, IKE Peer 99.1.1.2 local Proxy Address 172.16.1.0, remote Proxy Address 172.16.2.0, Crypto map (map1)
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, constructing ISAKMP SA payload Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, constructing Fragmentation VID + extended capabilities payload
Mar 09 13:58:42 [IKEv1]: IP = 99.1.1.2, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + NONE (0) total length : 144
Mar 09 13:58:42 [IKEv1]: IP = 99.1.1.2, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + SA (1) + NONE (0) total length : 84
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, processing SA payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, Oakley proposal is acceptable
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, constructing ke payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, constructing nonce payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, constructing Cisco Unity VID payload Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, constructing xauth V6 VID payload Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, Send IOS VID
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, Constructing ASA spoofing IOS Vendor ID payload (version: 1.0.0, capabilities: 20000001)
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, constructing VID payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, Send Altiga/Cisco VPN3000/Cisco ASA GW VID
Mar 09 13:58:42 [IKEv1]: IP = 99.1.1.2, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 224
Mar 09 13:58:42 [IKEv1]: IP = 99.1.1.2, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 224
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, processing ke payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, processing ISA_KE payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, processing nonce payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, processing VID payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, Received Cisco Unity client VID Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, processing VID payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, Received DPD VID
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, processing VID payload
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, Processing IOS/PIX Vendor ID payload (version: 1.0.0, capabilities: 0000077f)
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, processing VID payload 制作人:张选波
Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, Received xauth V6 VID Mar 09 13:58:42 [IKEv1]: IP = 99.1.1.2, Connection landed on tunnel_group 99.1.1.2 Mar 09 13:58:42 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Generating keys for Initiator... Mar 09 13:58:42 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, constructing ID payload Mar 09 13:58:42 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, constructing hash payload Mar 09 13:58:42 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Computing hash for ISAKMP Mar 09 13:58:42 [IKEv1 DEBUG]: IP = 99.1.1.2, Constructing IOS keep alive payload: proposal=32767/32767 sec. Mar 09 13:58:42 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, constructing dpd vid payload Mar 09 13:58:42 [IKEv1]: IP = 99.1.1.2, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + IOS KEEPALIVE (128) + VENDOR (13) + NONE (0) total length : 92 Mar 09 13:58:43 [IKEv1]: IP = 99.1.1.2, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + NONE (0) total length : 60 Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, processing ID payload Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, processing hash payload Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Computing hash for ISAKMP Mar 09 13:58:43 [IKEv1]: IP = 99.1.1.2, Connection landed on tunnel_group 99.1.1.2 Mar 09 13:58:43 [IKEv1]: Group = 99.1.1.2, IP = 99.1.1.2, Freeing previously allocated memory for authorization-dn-attributes Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Oakley begin quick mode Mar 09 13:58:43 [IKEv1]: Group = 99.1.1.2, IP = 99.1.1.2, PHASE 1 COMPLETED Mar 09 13:58:43 [IKEv1]: IP = 99.1.1.2, Keep-alive type for this connection: DPD
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Starting P1 rekey timer: 82080 seconds.
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, IKE got SPI from key engine: SPI = 0x35e2d6b3
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, oakley constucting quick mode
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, constructing blank hash payload
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, constructing IPSec SA payload
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, constructing IPSec nonce payload
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, constructing proxy ID 制作人:张选波
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Transmitting Proxy Id: Local subnet: 172.16.1.0 mask 255.255.255.0 Protocol 0 Port 0
Remote subnet: 172.16.2.0 Mask 255.255.255.0 Protocol 0 Port 0
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, constructing qm hash payload
Mar 09 13:58:43 [IKEv1]: IP = 99.1.1.2, IKE_DECODE SENDING Message
(msgid=3c988995) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + ID (5) + ID
(5) + NOTIFY (11) + NONE (0) total length : 192
Mar 09 13:58:43 [IKEv1]: IP = 99.1.1.2, IKE_DECODE RECEIVED Message
(msgid=3c988995) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + ID (5) + ID
(5) + NOTIFY (11) + NONE (0) total length : 192
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, processing hash payload
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, processing SA payload Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, processing nonce payload
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, processing ID payload Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, processing ID payload Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, processing notify payload
Mar 09 13:58:43 [IKEv1]: Group = 99.1.1.2, IP = 99.1.1.2, Responder forcing change of IPSec rekeying duration from 28800 to 3600 seconds
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, loading all IPSEC SAs Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Generating Quick Mode Key!
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Generating Quick Mode Key!
Mar 09 13:58:43 [IKEv1]: Group = 99.1.1.2, IP = 99.1.1.2, Security negotiation complete for LAN-to-LAN Group (99.1.1.2) Initiator, Inbound SPI = 0x35e2d6b3, Outbound SPI = 0x6530aa90
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, oakley constructing final quick mode
Mar 09 13:58:43 [IKEv1]: IP = 99.1.1.2, IKE_DECODE SENDING Message
(msgid=3c988995) with payloads : HDR + HASH (8) + NONE (0) total length : 72
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, IKE got a KEY_ADD msg for SA: SPI = 0x6530aa90
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Pitcher: received KEY_UPDATE, spi 0x35e2d6b3
Mar 09 13:58:43 [IKEv1 DEBUG]: Group = 99.1.1.2, IP = 99.1.1.2, Starting P2 rekey timer: 3060 seconds.
Mar 09 13:58:43 [IKEv1]: Group = 99.1.1.2, IP = 99.1.1.2, PHASE 2 COMPLETED (msgid=3c988995)
ASA#
制作人:张选波
R1#debug crypto isakmp
Crypto ISAKMP debugging is on
R1#
*Mar 9 21:59:43.011: ISAKMP (0:0): received packet from 88.1.1.2 dport 500 sport 500 Global (N) NEW SA
*Mar 9 21:59:43.015: ISAKMP: Created a peer struct for 88.1.1.2, peer port 500
*Mar 9 21:59:43.015: ISAKMP: New peer created peer = 0x67DAF79C peer_handle = 0x80000003
*Mar 9 21:59:43.015: ISAKMP: Locking peer struct 0x67DAF79C, refcount 1 for crypto_isakmp_process_block
*Mar 9 21:59:43.015: ISAKMP: local port 500, remote port 500
*Mar 9 21:59:43.019: insert sa successfully sa = 67DA4F8C
*Mar 9 21:59:43.019: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH *Mar 9 21:59:43.023: ISAKMP:(0):Old State = IKE_READY New State = IKE_R_MM1
*Mar 9 21:59:43.027: ISAKMP:(0): processing SA payload. message ID = 0
*Mar 9 21:59:43.027: ISAKMP:(0): processing vendor id payload
*Mar 9 21:59:43.031: ISAKMP:(0): vendor ID seems Unity/DPD but major 194 mismatch *Mar 9 21:59:43.031: ISAKMP:(0):found peer pre-shared key matching 88.1.1.2 *Mar 9 21:59:43.031: ISAKMP:(0): local preshared key found
*Mar 9 21:59:43.031: ISAKMP : Scanning profiles for xauth ...
*Mar 9 21:59:43.035: ISAKMP:(0):Checking ISAKMP transform 1 against priority 110 policy
*Mar 9 21:59:43.035: ISAKMP: default group 1
*Mar 9 21:59:43.035: ISAKMP: encryption DES-CBC
*Mar 9 21:59:43.035: ISAKMP: hash MD5
*Mar 9 21:59:43.035: ISAKMP: auth pre-share
*Mar 9 21:59:43.035: ISAKMP: life type in seconds
*Mar 9 21:59:43.039: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80 *Mar 9 21:59:43.039: ISAKMP:(0):atts are acceptable. Next payload is 3
*Mar 9 21:59:43.043: ISAKMP:(0): processing vendor id payload
*Mar 9 21:59:43.043: ISAKMP:(0): vendor ID seems Unity/DPD but major 194 mismatch *Mar 9 21:59:43.043: ISAKMP:(0):Input = IKE_MESG_INTERNAL,
IKE_PROCESS_MAIN_MODE
*Mar 9 21:59:43.047: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM1
*Mar 9 21:59:43.051: ISAKMP:(0): sending packet to 88.1.1.2 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Mar 9 21:59:43.055: ISAKMP:(0):Input = IKE_MESG_INTERNAL,
IKE_PROCESS_COMPLETE
*Mar 9 21:59:43.059: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM2
*Mar 9 21:59:43.375: ISAKMP (0:0): received packet from 88.1.1.2 dport 500 sport 500 制作人:张选波
Global (R) MM_SA_SETUP
*Mar 9 21:59:43.379: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH *Mar 9 21:59:43.383: ISAKMP:(0):Old State = IKE_R_MM2 New State = IKE_R_MM3
*Mar 9 21:59:43.387: ISAKMP:(0): processing KE payload. message ID = 0
*Mar 9 21:59:43.483: ISAKMP:(0): processing NONCE payload. message ID = 0 *Mar 9 21:59:43.499: ISAKMP:(0):found peer pre-shared key matching 88.1.1.2 *Mar 9 21:59:43.503: ISAKMP:(1002): processing vendor id payload
*Mar 9 21:59:43.503: ISAKMP:(1002): vendor ID is Unity
*Mar 9 21:59:43.507: ISAKMP:(1002): processing vendor id payload
*Mar 9 21:59:43.507: ISAKMP:(1002): vendor ID seems Unity/DPD but major 67 mismatch
*Mar 9 21:59:43.507: ISAKMP:(1002): vendor ID is XAUTH
*Mar 9 21:59:43.507: ISAKMP:(1002): processing vendor id payload
*Mar 9 21:59:43.511: ISAKMP:(1002): speaking to another IOS box!
*Mar 9 21:59:43.511: ISAKMP:(1002): processing vendor id payload
*Mar 9 21:59:43.511: ISAKMP:(1002):vendor ID seems Unity/DPD but hash mismatch *Mar 9 21:59:43.515: ISAKMP:(1002):Input = IKE_MESG_INTERNAL,
IKE_PROCESS_MAIN_MODE
*Mar 9 21:59:43.515: ISAKMP:(1002):Old State = IKE_R_MM3 New State = IKE_R_MM3
*Mar 9 21:59:43.523: ISAKMP:(1002): sending packet to 88.1.1.2 my_port 500 peer_port 500 (R) MM_KEY_EXCH
*Mar 9 21:59:43.527: ISAKMP:(1002):Input = IKE_MESG_INTERNAL,
IKE_PROCESS_COMPLETE
*Mar 9 21:59:43.527: ISAKMP:(1002):Old State = IKE_R_MM3 New State = IKE_R_MM4
*Mar 9 21:59:43.775: ISAKMP (0:1002): received packet from 88.1.1.2 dport 500 sport 500 Global (R) MM_KEY_EXCH
*Mar 9 21:59:43.779: ISAKMP:(1002):Input = IKE_MESG_FROM_PEER,
IKE_MM_EXCH
*Mar 9 21:59:43.783: ISAKMP:(1002):Old State = IKE_R_MM4 New State = IKE_R_MM5
*Mar 9 21:59:43.787: ISAKMP:(1002): processing ID payload. message ID = 0 *Mar 9 21:59:43.787: ISAKMP (0:1002): ID payload
next-payload : 8
type : 1
address : 88.1.1.2
protocol : 17
port : 500
length : 12 制作人:张选波
*Mar 9 21:59:43.791: ISAKMP:(0):: peer matches *none* of the profiles *Mar 9 21:59:43.791: ISAKMP:(1002): processing HASH payload. message ID = 0 *Mar 9 21:59:43.791: ISAKMP:received payload type 17 *Mar 9 21:59:43.795: ISAKMP:(1002): processing vendor id payload *Mar 9 21:59:43.795: ISAKMP:(1002): vendor ID is DPD *Mar 9 21:59:43.795: ISAKMP:(1002):SA authentication status: authenticated *Mar 9 21:59:43.795: ISAKMP:(1002):SA has been authenticated with 88.1.1.2 *Mar 9 21:59:43.799: ISAKMP: Trying to insert a peer 99.1.1.2/88.1.1.2/500/, and inserted successfully 67DAF79C. *Mar 9 21:59:43.799: ISAKMP:(1002):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE *Mar 9 21:59:43.803: ISAKMP:(1002):Old State = IKE_R_MM5 New State = IKE_R_MM5 *Mar 9 21:59:43.807: ISAKMP:(1002):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR *Mar 9 21:59:43.811: ISAKMP (0:1002): ID payload next-payload : 8 type : 1
address : 99.1.1.2
protocol : 17
port : 500
length : 12
*Mar 9 21:59:43.811: ISAKMP:(1002):Total payload length: 12
*Mar 9 21:59:43.815: ISAKMP:(1002): sending packet to 88.1.1.2 my_port 500 peer_port 500 (R) MM_KEY_EXCH
*Mar 9 21:59:43.819: ISAKMP:(1002):Input = IKE_MESG_INTERNAL,
IKE_PROCESS_COMPLETE
*Mar 9 21:59:43.819: ISAKMP:(1002):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
*Mar 9 21:59:43.823: ISAKMP:(1002):Input = IKE_MESG_INTERNAL,
IKE_PHASE1_COMPLETE
*Mar 9 21:59:43.827: ISAKMP:(1002):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Mar 9 21:59:43.979: ISAKMP (0:1002): received packet from 88.1.1.2 dport 500 sport 500 Global (R) QM_IDLE
*Mar 9 21:59:43.979: ISAKMP: set new node 1016629653 to QM_IDLE *Mar 9 21:59:43.983: ISAKMP:(1002): processing HASH payload. message ID = 1016629653
*Mar 9 21:59:43.983: ISAKMP:(1002): processing SA payload. message ID = 1016629653 制作人:张选波
*Mar 9 21:59:43.987: ISAKMP:(1002):Checking IPSec proposal 1
*Mar 9 21:59:43.987: ISAKMP: transform 1, ESP_DES
*Mar 9 21:59:43.987: ISAKMP: attributes in transform:
*Mar 9 21:59:43.987: ISAKMP: SA life type in seconds
*Mar 9 21:59:43.987: ISAKMP: SA life duration (basic) of 28800
*Mar 9 21:59:43.987: ISAKMP: SA life type in kilobytes
*Mar 9 21:59:43.991: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0 *Mar 9 21:59:43.991: ISAKMP: encaps is 1 (Tunnel)
*Mar 9 21:59:43.991: ISAKMP: authenticator is HMAC-MD5
*Mar 9 21:59:43.995: ISAKMP:(1002):atts are acceptable.
*Mar 9 21:59:43.995: ISAKMP:(1002): processing NONCE payload. message ID = 1016629653
*Mar 9 21:59:43.999: ISAKMP:(1002): processing ID payload. message ID =
1016629653
*Mar 9 21:59:43.999: ISAKMP:(1002): processing ID payload. message ID =
1016629653
*Mar 9 21:59:43.999: ISAKMP:(1002): processing NOTIFY INITIAL_CONTACT protocol 1
spi 0, message ID = 1016629653, sa = 67DA4F8C
*Mar 9 21:59:43.999: ISAKMP:(1002):SA authentication status:
authenticated
*Mar 9 21:59:44.003: ISAKMP:(1002): Process initial contact,
bring down existing phase 1 and 2 SA's with local 99.1.1.2 remote 88.1.1.2 remote port 500
*Mar 9 21:59:44.007: ISAKMP:(1002):QM Responder gets spi
*Mar 9 21:59:44.007: ISAKMP:(1002):Node 1016629653, Input =
IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Mar 9 21:59:44.007: ISAKMP:(1002):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
*Mar 9 21:59:44.031: ISAKMP:(1002): Creating IPSec SAs
*Mar 9 21:59:44.031: inbound SA from 88.1.1.2 to 99.1.1.2 (f/i) 0/ 0 (proxy 172.16.1.0 to 172.16.2.0)
*Mar 9 21:59:44.031: has spi 0x6530AA90 and conn_id 0
*Mar 9 21:59:44.031: lifetime of 28800 seconds
*Mar 9 21:59:44.031: lifetime of 4608000 kilobytes
*Mar 9 21:59:44.035: outbound SA from 99.1.1.2 to 88.1.1.2 (f/i) 0/0 (proxy 172.16.2.0 to 172.16.1.0)
*Mar 9 21:59:44.035: has spi 0x35E2D6B3 and conn_id 0
*Mar 9 21:59:44.035: lifetime of 28800 seconds
*Mar 9 21:59:44.035: lifetime of 4608000 kilobytes
*Mar 9 21:59:44.039: ISAKMP:(1002): sending packet to 88.1.1.2 my_port 500 peer_port 500 (R) QM_IDLE
*Mar 9 21:59:44.043: ISAKMP:(1002):Node 1016629653, Input =
IKE_MESG_INTERNAL, IKE_GOT_SPI 制作人:张选波
*Mar 9 21:59:44.043: ISAKMP:(1002):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_R_QM2
*Mar 9 21:59:44.099: ISAKMP (0:1002): received packet from 88.1.1.2 dport 500 sport 500 Global (R) QM_IDLE
*Mar 9 21:59:44.103: ISAKMP:(1002):deleting node 1016629653 error FALSE reason "QM done (await)"
*Mar 9 21:59:44.107: ISAKMP:(1002):Node 1016629653, Input =
IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Mar 9 21:59:44.107: ISAKMP:(1002):Old State = IKE_QM_R_QM2 New State = IKE_QM_PHASE2_COMPLETE
ASA# debug crypto ipsec 7
ASA# IPSEC: New embryonic SA created @ 0x027BE338,
SCB: 0x027C0C10,
Direction: inbound
SPI : 0x5ED30013
Session ID: 0x00000003
VPIF num : 0x00000001
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
IPSEC: New embryonic SA created @ 0x027C0EC0,
SCB: 0x027BFA50,
Direction: outbound
SPI : 0xD362B315
Session ID: 0x00000003
VPIF num : 0x00000001
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
IPSEC: Completed host OBSA update, SPI 0xD362B315
IPSEC: Creating outbound VPN context, SPI 0xD362B315
Flags: 0x00000005
SA : 0x027C0EC0
SPI : 0xD362B315
MTU : 1500 bytes
VCID : 0x00000000
Peer : 0x00000000
SCB : 0x027BFA50
Channel: 0x01766418
IPSEC: Completed outbound VPN context, SPI 0xD362B315
VPN handle: 0x00015954
IPSEC: New outbound encrypt rule, SPI 0xD362B315
Src addr: 172.16.1.0 制作人:张选波