
Security of Electronic Bonding in Multi-Domain Management Systems
L. Sacks
UCL
England
J. ?lnes
NR
Norway
G. Andrianopoulos
Bull ATC
Greece
D. Maillot
SEMA
France
For the TRUMPET (AC112) Consortium
Abstract
This paper discusses security of management systems which have to integrate and co-operate through use of management services from dif-ferent service providers. The individual man-agement systems involved must be viewed as in-dependent security domains, which must share common inter-domain security measures in or-der to communicate securely. The inter-domain security must then be standardised, preferably through a rather small set of alternatives to ac-commodate security requirements of varying se-verity. Negotiation of alternatives should be pos-sible, although at present only negotiation of se-curity context is possible, not negotiation of the security profile (viewed as a sub-set of the com-munications profile used between management entities). Available alternatives for realising se-curity depend on the underlying management technology, and on the possibility for additions or modifications to especially the communica-tions protocol stack. The work discussed here was developed in the TRUMPET (AC112) [TRUMPET] project, which was partially funded by the European Commission through the ACTS programme.
Keywords
S ECURITY, TMN, GSS-API, S ECURITY PROFILE, N ETWORK MANAGEMENT, S ERVICE MANAGEMENT, M ULTI-DOMAIN MANAGEMENT
1Introduction
This paper concerns the implementation of secu-rity for management services spanning organ-isational and administrative boundaries i.e. spanning multiple domains. These domains concern either; licensed operators of networks, licensed vendors of network connectivity – who may not own network infrastructure; and con-sumers of network services. Automated inter-domain management is crucial to efficient pro-visioning of Integrated Broadband Connection (IBC) services to users. At the same time all providers will regard their management system as a highly critical resource to their operation, which means that access from other domains can only be achieved if security is sufficiently taken care of. The security solutions must:
?ensure authentication and access control to preserve the integrity of the management systems and their operation;
?offer data integrity and confidentiality for management communication;
?ensure accountability of management opera-tions with respect to proofs of origin and destination;
?take into account the privacy requirements that exist even for management.
Note that this does not concern securing the IBC services provided to users, but only their man-agement. To some extent these considerations are applicable. However, there are notable dif-ferences in the environments, such as:
?IBC services use broadband communication
links, while management communication usually has fairly low bandwidth require-ments, and may use PSTN networks.
?IBC communication may be multipoint and multimedia, while management communi-cation with today’s technologies tend to be point-to-point and comprises only a data communication channel.
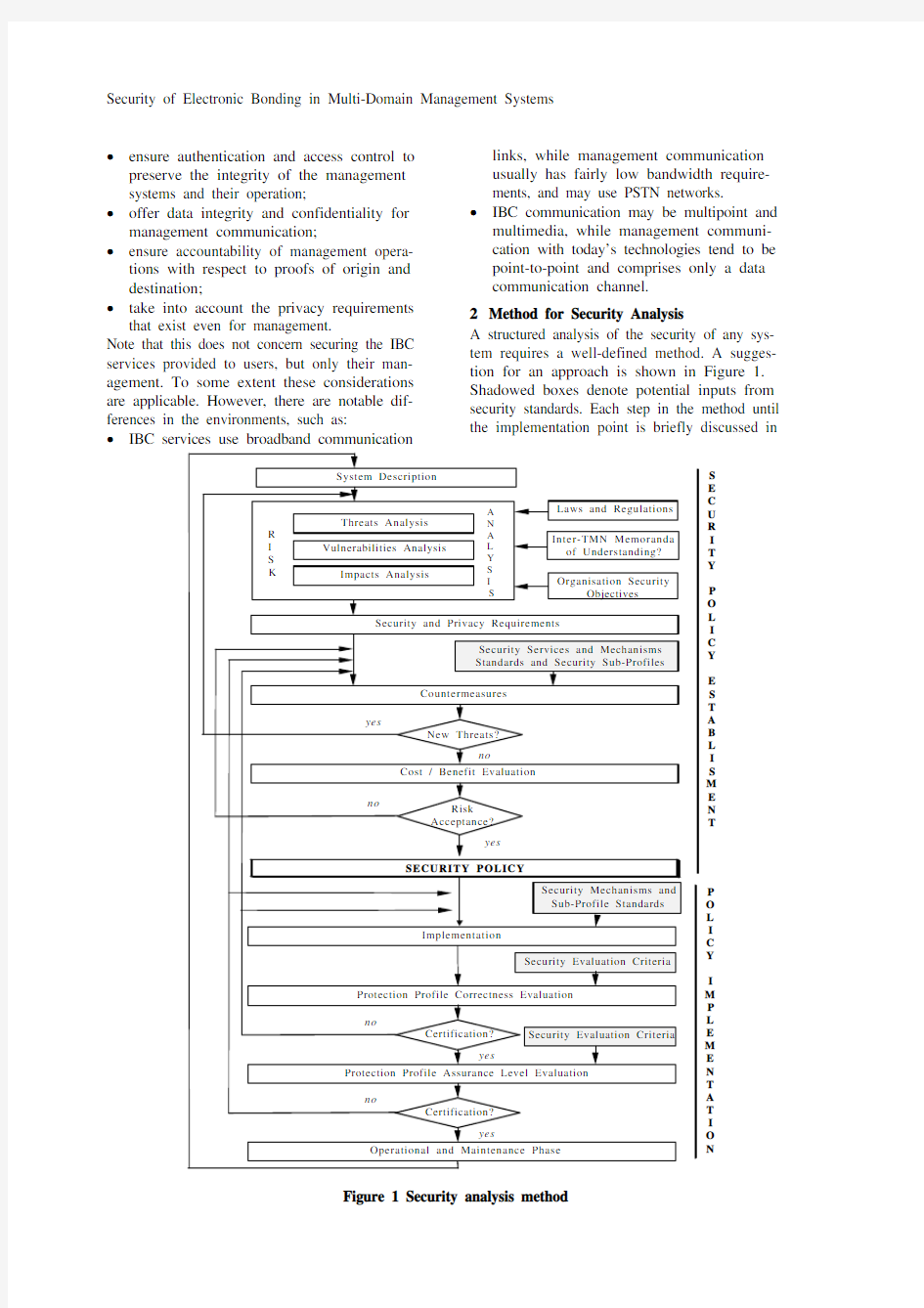
2Method for Security Analysis
A structured analysis of the security of any sys-tem requires a well-defined method. A sugges-tion for an approach is shown in Figure 1. Shadowed boxes denote potential inputs from security standards. Each step in the method until the implementation point is briefly discussed in
Figure 1 Security analysis method
the following. Additional steps are needed for validation and accreditation of the implementa-tion. Daily operation and maintenance of the management systems’ security is not discussed here.
2.1System Description
A system description is needed in order to make useful statements about security. Here, the “sys-tem” is a collection of co-operating management systems, which in concert manage national / in-ternational IBC services. The architecture and functions of the system need to be described and understood, focusing on the following proper-ties:
?functional description of each system com-ponent and its interface(s);?identification of the information’s storage characteristics:the kind of information, where it is stored, whether it is permanent or temporary, and its importance / sensitivity to the correct functioning (integrity) of the system, to the privacy requirements of the system's subscribers and users, and to busi-ness sensitivity (competitive information);?description of sequence and meaning of the information flows between the system com-ponents;
?identification of the borders of responsibili-ties with respect to system management and service provision (the domain boundaries);?identification of all assets / resources inside
a domain in need of protection;?identification of all actors (for example service providers, customers and end-users) and their roles, and their access rights to functions and information in the system (the access policy);
?description (to some degree) of how the sys-tem will be realised physically.
2.2The Legal and Regulatory Environment Laws and regulations, national, European and international, will always effect inter-organisational operation, and in particular the security solutions. These cover, in particular:?liberalisation of the telecommunications en-vironment and fair competition, in particular ONP and related directives;
?privacy and protection of personal data;?national security and public order, including restrictions on use of cryptography. National and international laws may impose ab-solute requirements with respect to security, e.g.require that certain information is kept confi-dential. For Pan-European or global contexts; these considerations can become quite problem-atic as several national legislative frameworks may have to be considered. Such issues cannot always be alleviated by industry specific agree-ments as many concerns are of a general social nature.
2.3Memorandums of Understanding
For some new telecommunications services, for example GSM mobile telephony, a MoU ap-proach has been taken. Providers signing the MoUs thereby agree to follow their contents with respect to provision of the specified service. Several MoUs are normally developed for each service.
This approach may be useful for formalising agreements for inter-domain management as well, although no work is currently suggested in this area. MoUs may cover overall business agreements like the intention to allow access from other providers to the management sys-tems, as well as more detailed technical specifi-cations about how such access shall be accom-plished, including security.
2.4Security Objectives
Security objectives are high-level goals for the security of an organisation. Focus is on what se-curity shall achieve rather than how it is done. Inter-domain security policies should be derived from agreed requirements, which in turn should be derived from agreed security objectives. The security objectives for inter-domain management may, for example, be reflected in an MoU, as a basis for MoUs treating inter-domain security policies.
The ETSI baseline document [ETSI ETR-336] on standardisation of security for TMN [ITU-T M.3010] states the following objectives for secu-rity of a TMN. This should be equally applicable to non-TMN systems:
?only legitimate actors shall be able to access and operate on assets in a TMN;?legitimate actors shall be able to access and operate on the assets they are authorised to access, but only on these assets;
?all actors shall be held accountable for their own, but only their own, actions in the TMN;
?availability of the TMN shall be protected against unsolicited access or operations;
?it shall be possible to retrieve security related information from the TMN;
?security violations shall be detected, and handled in a controlled way;
?after detection of a breach in security, it shall be possible to restore a normal security state. The first four of the objectives will be met by fulfilling requirements for inter-domain man-agement operations with respect to:?accountability - that legitimate users (hu-man users or entities acting on their behalf or on behalf of external systems) shall be ac-countable for the utilisation of any manage-ment services;
?integrity - that the system behaves in the expected way, and that information stored within or exchanged between the system components is correct;
?confidentiality - that information exchanged between entities shall be kept confidential when needed, and that access to stored in-formation shall be controlled and limited to those with legitimate rights to that informa-tion;
?availability - that functions and information shall be available to authorised users when needed, with the required QoS.
Some objectives must be met by security man-agement systems within each individual domain, notably logging of security and management events and security audit and alarm functional-ity, plus procedures for security recovery. To some extent, these are internal matters for each management system. Nevertheless, some degree of normalisation between players is necessary to ensure accountability and a common level of overall service security.
2.5Risk Analysis
The risk analysis is concerned with the follow-ing:
?identify the threats pertinent to objects within the system;
?estimate the vulnerability related to the threat, i.e. the probability that the threat will manifest;
?estimate the impact (cost) of a manifestation of the threat.
The vulnerability related to a threat can be specified as (cost * vulnerability), which gives the relative cost incurred by not protecting against this threat. This, combined with the technical constraints and costs of security meas-ures, may be used to yield a cost / benefit analy-sis for implementing some (sub)set of security measures in a system.
A risk analysis usually carries a high uncer-tainty, especially in the estimates of the vulner-abilities and impacts, but also in the identifica-tion of possible threats. For inter-domain man-agement, the actual environment of the system plays a role, like the characteristics of the net-work used to transfer management information.
2.6Security Requirements
Security requirements are identified from the se-curity objectives, the risks analysis, and to fulfil relevant laws and regulations. The requirements are more detailed goals that the security imple-mentation must fulfil, in order to offer adequate protection for different kinds of information, and to protect the management systems them-selves.
Requirements relevant to management informa-tion can be expressed as the sensitivity of par-ticular information with respect to availability, confidentiality, integrity, and accountability (tracing of operations performed on the infor-mation). Requirements must be applied to stored information, and to transfer of information be-tween systems.
3Countermeasures
There are three categories of security counter-measures: Physical, logical and administrative. Physical security is an internal task of the indi-vidual management systems, as is administrative security (it may be for further study whether MoUs covering particular administrative proce-dures, for example for security recovery, can be developed as parts of inter-domain management specifications). Thus, only logical security measures need be considered at an inter-working level; and only those measures necessary to protect inter-domain management communica-tion and access from one management domain into another.
Furthermore, there are three types of counter-measures, orthogonal to the three categories:?preventing - to avoid incidents;?detecting - possibly also for limiting effects of an incident;
?correcting - to restore the system to a secure state.
The last two types are typically applied inter-nally to each management domain.
Thus, the countermeasures for inter-domain management that have to be agreed between the
actors involved, are in the class logical, pre-venting countermeasures. For communication, such countermeasures shall implement the secu-rity services defined in the security frameworks [X.810-X.816] by selecting appropriate mecha-nisms, preferably standardised ones.
Services and mechanisms may be pre-grouped into security profiles, which are consistent sets offering protection at a certain level.
An important task, also pertinent to a security profile, is placement of security functionality with respect to the communications stack. With reference to the OSI model, preferred alterna-tives are:
?in the applications - above the application layer;
?in the application and presentation layers (combined);
?in the transport layer;
?in the network layer.
These alternatives are valid even for other com-munication stacks, like the TCP/IP suite with RPC or CORBA distributed application support.
3.1New Threats
Countermeasures will be introduced by adding security services and mechanisms to the system, and in most cases this will add new threats that will have to be accounted for. These threats have to be analysed starting from the threat analysis stage. For example, use of cryptographic mechanisms depends on proper protection of the cryptographic keys.
3.2Countermeasures and Their Cost / Bene-fit Evaluation
Security countermeasures imply costs, which must be justified by the benefits gained from them. Thus, countermeasures should be intro-duced following a cost / benefit analysis. 100% security is impossible, and furthermore costs tend to increase sharply as one approaches this limit. In most cases, implementation of security should follow a trade-off between costs and benefits. Exceptions in the civil world may be found where laws and regulations demand cer-tain protection measures to be in place, regard-less of cost.
A full comparison of costs and benefits can only be done for a real system. However, for logical security mechanisms, some meaningful com-parisons may be done in a general management case. This cost / benefit categorisation is limited to the relative strengths of alternative security mechanisms with respect to certain criteria. Cost analysis has two aspects. On the one hand there is the relationship between the cost of im-plementing some security policy, the value of the data or system thus protected and the cost of the security measures (software, hardware etc.) On the other hand there is the effective cost of the impact from 'turning on' that security tech-nology. This latter factor includes things like performance impacts on the target management systems and increases in the required specifica-tions of the support platforms. Cost also comes in the form of risk to business due, for example, to denial of service in the case of incompatibility with the client systems; clearly a system which intends to restrict access to a system has a finite probability of restricting access to legitimate us-ers.
3.3Risk Acceptance
After introduction of security measures, there will still be a remaining risk, which must be evaluated and deemed to be acceptable. This analysis is done in conjunction with the cost / benefit evaluation. The remaining risk results from threats that are deliberately not totally ac-counted for, and from omissions and mistakes in the security work. For example, threats may have been overlooked, or estimates of probability or impact may be wrong.
If the risk or cost / benefit evaluation yields a negative result, one may either choose other se-curity measures, or even reassess the security re-quirements if, for example, a requirement can-not be met within an acceptable cost.
3.4Security Functional Classes, Profiles, and Contexts
Functional classes (FC) are consistent sets of se-curity services in order to meet requirements of varying severity. The idea is to define a set of security FCs in order to hide the complexity of the security area and to facilitate specification and negotiation of security matters between ac-tors involved in inter-domain management, as well as towards vendors of management prod-ucts.
For example, four FCs for different levels of se-curity for interaction between TMN-based man-agement systems may be considered as shown in Table 1. Each FC is further specified in terms of a security profile, which actually is a sub-profile of a standards profile. A profile specifies at
which layer (above stack, application, transport, network) security is placed, how security infor-mation is passed between entities, and to some extent the nature of the security information.
A security context is the security part of the ap-plication context for an association, and may be said to consist of the security state information, including parameters like cryptographic (ses-sion) keys. The context must be negotiated at as-sociation establishment. Dependent on the pro-file used, re-negotiation of parts of a context may be possible.
Negotiation of the FC to use for an association, as one part of negotiation of a security context between communication partners, will be the most flexible solution. Such negotiation may for example be supported by the Generic Upper Layer Security (GULS) framework [ITU-T X.830-X.833].
4Integration of Security with Management Applications
The security architecture, as defined by TRUMPET, consists of a specification of how security is integrated with the applications / platform / communications capabilities of the communicating management systems, and a specification of the security infrastructure - in the form of TTP (Trusted Third Party) services. An important issue is the accessibility to the protocol stack. Typically, security mechanisms need to be integrated on several layers, but this depends on the ability to modify or add func-tionality inside the communications stack. If modifications are not available, all security must be added at the level of the management appli-cations themselves.
Even if all security is integrated at the applica-tion level, there is some minimal support re-quired for the transfer of security data between communicating parties. For an OSI protocol stack, the specific requirements are:
?the authentication field of ACSE must be supported to establish the security context and for authentication;
?the access control field of CMIS manage-ment operations must be supported to trans-fer security related information.
The security architecture also requires that agents have control over accesses to the Man-agement Information Base (MIB), in order to
FC0FC1FC2FC3
No security Emphasis on the integrity and
confidentiality of stored managed
resources FC1 plus integrity of transferred
data
FC2 plus strong accountability of
management operations
?Authentication of peer entity ?Management association access control
?Managed resource access con-trol
?Security alarm, audit and re-covery ?Authentication of peer entity
?Management association access
control
?Management notification access
control
?Managed resource access con-
trol
?Data origin authentication
?Connection integrity
?Security alarm, audit and recov-
ery
?Authentication of peer entity
?Management association access
control
?Management notification access
control
?Managed resource access control
?Data origin authentication
?Selective field integrity
?Connection integrity
?Origin non repudiation
? Receipt non repudiation
?Security alarm, audit and reco-
very
FC1A FC2A FC3A
FC1 plus confidentiality of com-municated data FC2 plus confidentiality of com-
municated data
FC3 plus confidentiality of com-
municated data
?Connection confidentiality?Connection confidentiality?Connection confidentiality
?Selective field confidentiality Table 1. Functional Classes or Security Levels
This architecture cannot fully support data in-tegrity, data confidentiality, non-repudiation and security negotiations. Again with the example of an OSI protocol stack:
?Integrity and non-repudiation of application data can be provided but not integrity of data introduced by ACSE, CMISE and lower lay-ers.
?When encryption for confidentiality is per-formed above CMISE, the encrypted data must be inserted into one of the fields of the particular CMIS operation being requested.
However, most of the fields have specific pre-defined types that cannot accommodate an encrypted data type. In general, the only exception, and the only fields that can be en-crypted, are the fields used to carry the at-tribute values to and from the target MIB.
The encrypted data could be inserted into fields such as the access control field, how-ever, this is not considered as a reasonable approach.
?Security negotiations involving a maximum of two exchanges can be performed during
association establishment using ACSE fields such as the authentication or the user infor-mation field. However, in some cases, it is desirable to perform more than two ex-changes (e.g. 3-way authentication) or to support security exchanges after the associa-tion has been established. For example, it may be desirable to re-negotiate the session key at regular intervals.
?Note also that for integrity and confidential-ity protection, the information must first be encoded in a system independent syntax (also resembling the serialisation done for remote procedure calls), which is normally the task of the presentation layer of the OSI model.
To provide full support for data integrity, data confidentiality, non-repudiation and security ne-gotiations, some security functionality must be introduced below the application layer of the OSI stack. Non-repudiation still introduces some problems, as the granularity is at the level of in-dividual CMIP PDUs, which is probably to de-tailed. The following standards are proposed for lower and upper layers security functionality:?connection integrity and confidentiality: Transport Layer Security Protocol (TLSP) [ITU-T X.274] (layer 4) (for a TCP/IP pro-tocol stack, Secure Sockets Layer (SSL) should be the logical alternative);?security context negotiation: Security Ex-change Service Element (SESE) [ITU-T X.831-X.832] (layer 7).
Figure 2 shows integration of security with an OSI protocol stack. The normal lines/boxes refer to existing interfaces/components expected to be available in a TMN management platform. The dotted lines/boxes refer to new or modified in-terfaces/components. The Security Service Component (SSC) takes care of security proc-essing and holds the security context.
The application service element SESE supports arbitrary security negotiations. Although SESE is introduced in the application layer, SESE cannot be used in the case where the stack in-terfaces are not accessible because it needs to interface directly to the presentation layer and because the presentation layer has to be en-hanced with additional functionality to support security. Connection integrity and confidential-ity security components are introduced in the transport layer of the OSI stack according to TLSP.
An alternative to adding security in each indi-vidual end system is to add parts of the security in front-end computers, like “trusted routers”operating at the network layer. Confidentiality and data integrity, as well as peer-entity authen-tication with respect to other routers, may be provided by use of the Network Layer Security Protocol (NLSP) [ITU-T X.273]. Within the in-ternal (local area) networks, traffic is in clear text, and without integrity protection, based on the assumption that these networks can be trusted.
Although key distribution may be done in differ-ent manners, a centralised key distribution cen-tre is frequently used with such solutions.
The front end separate software/computers need not be constrained to operating on the network layer. It is possible to build “firewalls” operating at the transport layer or the application layer [Berge-96]. In such a case, for example GULS-based security may be implemented in an appli-cation layer gateway, communicating with similar gateways for other TMNs, or even with real end systems implementing the same secu-rity functionality. It is anticipated, however, that an application layer gateway will have a severe impact on the speed of the communication, es-pecially since it may have to decode and re-encode ASN.1 and because of the additional re-quirements to traverse all the layers up to layer 7. Furthermore, a layer 7 gateway cannot en-force access control to management resources.
5Programming Interfaces
In the TRUMPET project, security measures where implemented on HP-OpenView; in which context the stack interfaces were not accessible.The approach taken was to base a security im-plementation on the GSS-API [RFC 2078]. One alternative is to specify all interfaces towards the SSC as (a sub-set of) GSS-API. In practice, this solution is only viable in the case where security can be integrated in the protocol stack. If secu-rity is added only above the protocol stack, a di-rect GSS-API interface from the application would make the application too much “security aware”, while it should be a goal to make secu-rity (at least fairly) transparent to the applica-tion. The most severe problem here lies in the serialisation (system independent syntax) that must be done before the GSS-API calls if integ-rity and/or confidentiality protection is used. The TRUMPET architecture for integration of security at the application level is shown in Figure 3 [Gagnon-97]. A generic security pack-age is developed, that offers an interface defined by the SMAS (Secure Management Association Service) object. Between this interface and the application adapter objects are placed, with the idea that the adapter shall provide an interface very similar to the one normally used by the management application, e.g. XOM/XMP. Solid lines in the figure indicate existing objects and interfaces, while dotted lines indicate additions by TRUMPET.
The security transformations, security context negotiation, and peer-entity authentication are still carried out by a GSS-API compliant object, the SSO (Security Support Object). For inter-domain operation, authentication will have to depend on a certification infrastructure (see be-low). A certificate handling object is thus neces-sary, with the capability of fetching certificates and certificate revocation lists by means of the Lightweight Directory Access Proto-
col (LDAP) [RFC 1777]. Use of a
full-fledged X.500 system for certifi-
cate management is possible; but can
be difficult to manage, and may be
inefficient.
6Security Infrastructure
Inter-domain management may po-
tentially involve a large number of
actors (network and service provid-
ers, and eventually even customers).
To enable establishment of trust, usu-
ally by means of a (mutual) authenti-
cation, a security infrastructure con-
sisting of TTPs is needed. For scaling
purposes, off-line TTPs in the role of
certification authorities (CA) should be used. TRUMPET requires all service providers and network operators to run a CA for their own domain, and issue authentication certificates for their inter-domain management applications through this CA. The CA may also certify cus-tomers, and potentially even end users, of the service / network provider, or alternatively de-termine in its certification policy which CAs that are trusted for customer / user certification (e.g. through cross-certification with these CAs). Note that it is the identities of the applications, not the human users, that are certified. For pri-vacy reasons, user identities should not be dis-closed outside of their home domain, and authentication between domains is at the appli-cation level.
To enable inter-domain authentication, the CAs should be linked to a hierarchy, consisting at a minimum of one top-level CA that issues certifi-cates for all provider CAs. A better option is to place the CAs under an established infrastruc-ture. TRUMPET points at the infrastructure es-tablished by the ICE-TEL project [ICE-TEL] as an alternative.
TRUMPET’s suggestions for certification policy and public key infrastructure are described in [?lnes-98].7Conclusions
Much of the technology and methodology dis-cussed in this paper has been explored and util-ised in the TRUMPET project. This projects was specifically focused on implementation issues, and utilised many of the concepts developed in Sections 4 and 5. With respect to management of security, the project implemented a nagotia-tion system which supports the security levels as described in Table 1 and utilised a public key infrastructure as discussed above.
The broader concepts have been exposed both to the appropriate working groups in EURESCOM and to the network management people of Scot-tish Telecom; a public network operator in the UK. Both these bodies have helped tune the con-siderations of policies and technology. Full ex-ploitation in these places was not within the scope of TRUMPET.
As further work, many of the concepts devel-oped here have been explored in contexts other than CMIS/CMIP based TMNs. The Service Management of TRUMPET [Sacks-98] used CORBA and Java technologies, which also re-quire inter-domain security. Although the issues in this domain are slightly different than for core Network Management, many of the con-cepts can be ported to that context.
8References
[Berge-96]N.H.Berge, J.?lnes: “Firewalls in an OSI Environment”, Computer Communications 19 (1996) 982-989, October 1996.
[ETSI ETR-336] ETSI ETR 336: “TMN: Introduction to Standardising Security of TMN”, 1996. [Gagnon-97] F. Gagnon, D. Maillot, J. ?lnes, L. Hofseth, L. Sacks, “A Security Architecture for TMN Inter-Domain Management”, IS&N ‘97Conference Proceedings.
[ICE-TEL] http://www.darmstadt.gmd.de/ice-tel
[ITU-T M.3010] ITU-T Recommendation M.3010: “Principles for a Telecommunications Management Network.
[ITU-T X.273] ITU-T Recommendation X.273: “Network Layer Security Protocol (NLSP)”, 1994.
[ITU-T X.274] ITU-T Recommendation X.274: “Transport Layer Security Protocol (TLSP)”, 1994. [ITU-T X.810-X816] ITU-T Recommendations X.810-X.816: “Security Frameworks, Parts 1-7”, 1994/1995.
[ITU-T X.830-X833] ITU-T Recommendations X.830-X.833: “Generic Upper Layer Security (GULS), Parts 1-4”, 1995.
[RFC 1777] “Lightweight Directory Access Protocol (LDAP)”, March 1995.
[RFC 2078] “Generic Security Service Application Program Interface (GSS-API), Version 2”, January 1997.
[Sacks-98] L.Sacks, O.Prnjat, M.Wittig, M.M.Kande, B.Bhushan, S.Mazaher, C.Autant: “TRUMPET Service Management Architecture”, Proceedings of the EDOC 98 Workshop.
[?lnes-98] J. ?lnes, M. Verdier, N. Ganivet, D. Maillot, J. Skretting, “Public Key Infrastructure and Cer-tification Policy for Inter-domain Management”, IS&N ’98 Conference Proceedings.
[TRUMPET] https://www.doczj.com/doc/1117773952.html,/ACTS/RUS/PROJECTS/ac112.htm
2020年伦敦大学学院专业排名及历年世界排名 拓展阅读: 一、院校简介 伦敦大学学院成立于1826年,旨在为那些通常被排除在外的人提供高等教育,是英国继牛津大学和剑桥第三所公立性大学。1878年,它成为英格兰第一所接纳女性与男性平等的大学。该校位于伦敦市中心,是伦敦大学的组成学院,也是罗素集团的成员,拥有约850名教授和6,000多名学术和研究人员,由11个学院组成:艺术与人文学院、建筑环境学院、脑科学院、工程学院、教育学院、法学院、生命科学院、数学与物理科学院、医学科学院、人口健康科学院和社会历史科学院。 纵观其历史,伦敦大学学院一直是众多重大科学发现的发源地,向伦敦大学学院的学生或教职员工颁发了29项诺贝尔奖,其中包括威廉·拉姆齐,他因发现惰性气体而于1904年获得诺贝尔化学奖。此外,伦敦大学学院的学术界包括53位皇家学会会员,51位英国学院院士,15位皇家工程院院士和117位医学科学院院士。 学生人数近36,000人,伦敦大学学院拥有该国最大的研究生学习系统之一。近52%的学生从事研究生学习。该校的学生来自全球约150个国家,占该大学整个学生人口的三分之一以上。伦敦大学学院是第一所在卡塔尔多哈开设校园的英国大学,在那里设有文化遗产研究中心。它还在南澳大利亚阿德莱德设有办事处,其中包括空间科学和能源政策研究所。该大学的拉丁格言被翻译为“让所有人得到应得的奖励。” 伦敦大学学院或者伦敦大学学院位于伦敦市中心,但在卡塔尔和澳大利亚也设有分校。此外,伦敦大学学院还与世界各地的大学建立了交流和研究协议以及其他类型的合作伙伴关系,如加拿大蒙特利尔大学和浙江大学在中国。伦敦大学学院的学生来自约150个国
中国FC成员--安利最高级别奖衔,榜样的力量! 安利全球政策咨询委员会(FC)是安利公司最高级别的咨询委员会。每年,安利公司都会从资深营销总监中,邀请杰出的营销领导人,成为安利全球政策咨询委员会成员。他们来自全球各地不同的安利市场,他们将分享创办人家族和管理层带来的公司发展资讯,并对公司未来战略提出自己的看法。 ?安利全球政策咨询委员会成员还应该是安利品牌当之无愧的形象大使:忠诚执着、不懈努力,将安利的优质产品、事业良机和企业文化广为传播,将是他们任重道远的责任;乐观向上,积极热情,用自己的丰富经验和人格魅力,开启事业伙伴对丰盛人生的美好愿望,将是他们赏心乐为的使命;珍惜商誉,富有爱心,让整个社会见证一个负责任的企业对世界永恒不变的承诺,更是他们持之以恒的追求。 ?安利全球政策咨询委员会成员,是一份荣誉,更是一种责任和使命。对他们来说,是多年前的一个明智选择,开启了丰盛人生的第一缕希望;是多年来的一份坚定信念,让他们与公司不离不弃、共创卓越,并赢得了公司的尊重和认可。 ?以下是2011年来自中国的安利全球政策咨询委员会成员: (一) 周帆扬郑新清 (财务主管财务经理) 16年的安利之路让郑新清、周帆扬夫妇体会最深的,是安利的两个不变——第一是承诺不变,“安利承诺的表彰奖励从来没有失言,而且也没有名额的限制,你做到了就能得到,你的成功并不会排斥别人的成功”;第二是伙伴关系不变,“安利公司不是凌驾于你之
上来管理你,而是给你提供平台,提供后勤支援,让你来经营。大家是合作关系、伙伴关系。” 怀着对公司、对良师益友、对事业伙伴的感恩之心,郑新清夫妇把这份真挚的回馈之情放大到了全社会。2004年到2005年,他们积极参与“爱心手牵手”活动,资助了30名失学女童重返校园,受到河南省委、省妇联领导的表彰。2008年12月,郑新清不顾腰伤未愈,会同郑州地区的地方业务营运咨询委员会成员们一起前往海拔1700米的贫困山区小学,与孩子们联欢,为孩子们送去温暖。2008年汶川大地震及2010年玉树地震发生后,他们均捐出善款以表达支援灾区的热切心情。 对郑新清夫妇来说,16年的安利之路是一场全新的生命体验,他们收获了比财富更重要的、丰富自己也丰富别人的丰盛人生。 (二) 韩世荣 (贸易公司总经理) 1996年,韩世荣出差到美国洛杉矶,经朋友介绍参加了当地安利营销人员聚会。让她略感意外的是,这个群体的整体素养很高,这也让她意识到了安利产品蕴藏的巨大商机。 回到青岛后,韩世荣立即忙开了。白天工作繁重抽不开身,她便充分利用起晚上的时间。亲朋好友和客户冲着她的面子加入进来,但很快便放弃了,这些变故对于一个新加入者的信心难免会有冲击,但韩世荣并没有轻言放弃,她知道新兴事物的成长必然要经过苦寒和磨砺。
PERSONAL DETAILS (please complete in black ink) 1.Surname/Family Name (Block Capitals) 2.First Names (Block Capitals) 3.Title (Mr/Mrs etc.) Day Month Year Male Female 6. Nationality 7. Country of Ordinary Residence 4.Date of Birth 5. Sex (√ ) 8.Home address 9. Correspondence Address (if different) Postcode Postcode Tel.Fax Tel.Fax E-mail E-mail Dates when Address is Valid FOR OFFICE USE. TO BE COMPLETED BY THE GRADUATE ADVISER/DEPARTMENTAL ADMISSIONS TUTOR ACCEPT REJECT WITHDRAWN Signature Date If “REJECT”, CAO to send a standard letter?YES NO If “ACCEPT”, please complete appropriate boxes below: 1.Qual. (MA, Diploma etc.) 2. Programme Title/Research Field of Study 3. Method of Study (√ ) FT PT Modular PT 4. Start Date 5. Research Acad/Cal Yrs Months (if not Sept.) Duration 6. First Research Supervisor 7. Second or Off-Campus Research Supervisor 8. Minimum Qualifications Required. 9. Other details/condititions for offer letter (eg. studentship or scholarship allocated/nominated for. If qualifying examination is to be set provide details here). 10. In section 15, overleaf, please tick which qualifications should be verified by the Registrar’s Division. WHEN COMPLETED, PLEASE RETURN TO THE COLLEGE ADMISSIONS OFFICE, REGISTRAR’S DIVISION. PROGRAMME OF STUDY FOR WHICH YOU WISH TO APPLY 10.UCLDepartment/Institute 11.Qualification Sought (MPhil/PhD, MSc etc.)12.Research Subject Area/Taught Programme Title 13.Method of Study (√ ) Full-time Part-time (where available) 14. Proposed Starting Date Month Year Taught programmes usually start in September or early October. Research students may begin in September, January,April or July. If there is an alternative programme for which you also wish to be considered, send a photocopy of your application and all supporting papers (except those in sealed envelopes) substituting the alternative details in this section.
英国留学-索学网 https://www.doczj.com/doc/1117773952.html, 英国留学DIY 申请 https://www.doczj.com/doc/1117773952.html,/ 伦敦大学学院面试经验分享 我一直都想去伦敦大学学院读书,所以这次申请了他们的课程。在材料寄出大概两个月后,面试通知就来了,形式是电话面试。于是我开始疯狂在网上搜索UCL 的面经,拟出了我认为可能会问到的问题,主要包括下面三个方面内容: (1)为什么选择我们学校的这个专业? 为了回答这个问题,我们必须对课程本身的背景有充分的了解,基本培养模式、培养目标、是否有实验室工作等等;另外,要说明你的兴趣所在,为什么喜欢这一科目,或是之前的学习、研究经验如何使你适合这个课程的学习。对于为什么选择他们学校这类问题,突出一个鲜明特点的基础上多多吹捧他们就可以了。 (2)学生的个人教育背景和经历 校方对你个人背景经历的了解主要是通过你的CV 和PS ,如果其中有他们感兴趣的经历,他们很可能会就此提问。所以,要对材料进行熟悉,保证每个点都有的讲,并尽量借此机会多展示自己的专业优势。 比如在讲述一个实习工作时,不仅要说都做了什么,更重要的是对自己的工作进行反思,总结学到了什么,最大感受是什么,以及这段经历对你后来的学习有什么促进和影响。没有学校不喜欢会思考的学生。另外在性格方面也可以准备下,说明自己是一个什么样的人,优缺点等等。 (3)学生希望向申请院校提的问题 提问也是体现你水平的一个重要环节。此时你可以表达你希望继续深造的愿望,可以就课程设置提问,或者让他为你这个即将去英国学习的海外学生提一些建议。最好不要问那些在学校网站上就可以轻轻松松找到答案的弱智问题。让面试官觉得你们是在沟通,在交流。另外,面试结束后一定记得说Thank you for your time ,再发一封邮件过去以表示感谢。 结果实际面试过程不出我所料,课程负责人一上来就问了我实习的经历(我强调了我用的英文办公),然后又问了我为何选择医学专业(我说了个人兴趣、课程结构对我的吸引、以及医药工作者的责任感使然),最后让我提问(我问了如果想继续读,这一年能不能接触到未来的教授,以及课程计划的实验设置)。 问完了她立刻就很高兴地告诉我可以给我寄Offer 了。我想,在学校给你打来电话前,他们也是对你做了一番分析的。你只有充分熟悉自己的材料,并且尽量把话题往有利于自己的方面说,才能达到最好的面试效果。 以上是我申请伦敦大学学院的面试经验,同学们可以借鉴,祝大家申请到自己理想的学校。
https://www.doczj.com/doc/1117773952.html, 伦敦大学和伦敦大学学院区别 伦敦大学概况 伦敦大学(University of London)是位于英国首都伦敦的一个由十几所高校和研究机构组成的大学联邦(与美国加州大学一样,亦被称为“公立联邦制大学”),在1836年由伦敦大学学院和伦敦大学国王学院合并而成,并获颁皇家特许状,是世界上最具影响力的公立大学系统之一。伦敦大学是世界最大的大学联邦体之一,其旗下大学在各项学术指标和排名中均名列前茅。这些校区互为独立又互相联系,各自作为独立的大学而存在。目前,英国女王伊丽莎白二世的独生女安妮公主,担任伦敦大学与各级学院的校监。 伦敦大学大学联邦经过177年的扩张,已发展成为包含18个独立自治的学院和10个研究所的巨型联盟,并对世界发展影响深远的巨型大学系统,在各加盟学院的毕业生与教师中,拥有72个诺贝尔奖得主、数十位国家元首。旗下学院都有独立的大学地位和高度的自治权,它们独立招生、独立排名。有9所学院独立颁发文凭,包括:伦敦大学学院、伦敦国王学院、伦敦政治经济学院、伦敦玛丽女王大学、皇家霍洛威学院、皇家音乐专科学院、伦敦大学城市学院、伦敦大学金史密斯学院、圣乔治医学院。 伦敦大学学院概况 伦敦大学学院 (University College London),简称UCL,建校于1826年,位于英国伦敦,是一所世界著名顶尖高等学府,其排名稳居世界前十,为享有顶级声誉的综合研究型大学。
https://www.doczj.com/doc/1117773952.html, 它是伦敦大学联盟(University of London,简称UOL)的创校学院,与剑桥大学、牛津大学、帝国理工学院、伦敦政治经济学院并称“G5超级精英大学”。英国金三角名校,罗素集团成员,中英大学工程教育与研究联盟成员,SES-5成员。 伦敦大学学院诞生了34位诺贝尔奖获得者和3位菲尔兹奖获得者,此外还不乏科学、政治以及文化等领域的名人。其中包括“光纤之父”高锟,“电话通讯之父”亚历山大·贝尔,DNA发现者“生物分子学之父”弗朗西斯·克里克,“建筑电讯派”核心彼得·库克,人工智能AlphaGo 算法的创建者戴密斯·哈萨比斯与大卫·席尔瓦,文学大师泰戈尔, 印度国父圣雄甘地,日本近代政治家伊藤博文等。 伦敦大学学院拥有国家医学研究中心(NIMR),欧洲顶尖的太空探索实验室(MSSL),以及世界著名的盖茨比计算神经科学中心(GCNU)等领先科研机构。其主校区邻近大英博物馆、大英图书馆、国王十字车站和摄政公园,坐落于伦敦市中心。 该校在2018 QS世界大学排名中位列世界第7名,英国第3名;2017年上海交大世界大学学术排名(ARWU)中位列世界第16名,英国第3名;2017年泰晤士高等教育世界大学排名位列世界第15名,英国第4名;在由英国官方2014年大学科研水平排名(REF)中,伦敦大学学院位列全英第2名,仅次于牛津大学。 伦敦大学国际课程 伦敦大学国际课程 (University of London International Programmes),前称伦敦大学校外课程(University of London External Programmes),成立于1858年,经维多利亚女皇授权取得皇家特许资格,是全世界第一个开办跨境教育和境外合作办学的学府。2010年,更名为伦敦大学国际课程。2018年2月起,
我想目前中国人上广泛认为适合移民国家主要有四个:北美的美国和加拿大;大洋洲的澳大利亚和新西兰。其中美国和新西兰因为各自都有很严重的劣势(前者要求太高,后者经济不够发达)目前中国移民大多集中在澳大利亚和加拿大。本人拿了国内大学学士去了加拿大ubc读硕士,毕业后申请美国的学校未果,经过多方考虑移民去了悉尼,我想我还是有资格比较一下这两个国家的。 首先介绍一下两个国家的概况吧,还是能说明一些问题的。澳洲人口2000万,国土面积770万平方公里,2004年人均收入21,650,世界排名19;加拿大人口2700万,国土面积997.61万平方公里,2004年人均收入23,930,排名世界18。数字上看加拿大都要略胜一筹,不过差距都很小,基本是一个档次。(2007年CIA数据,澳洲排世界16,43,798美元;加拿大排18,43,478美元,还是不分上下,但是澳洲已经超过加拿大。数据连接自美国中央情报局年鉴,The World Factbook, provided by theCentralIntelligence Agency, as of October 2, 2008.) 从经济上看,两个国家制造业都不是很发达,重工业基本都没有,强项都是农业和类似矿石这样的出口加工业,两国都是世界上排名前列的农业出口国,澳洲更是世界最大的羊肉出口国(但澳洲人很少吃羊肉)。(补充,上次没有介绍失业率方面的数据。加拿大2008年12月失业率是6.6%,澳大利亚2008年12月失业率是4.4%。不要小看这2%的差距,这在经济领域是非常大的差距,这也是为什么目前很多加拿大人来澳洲找工作的原因。关于失业率的数字,可以去google搜索。) 评价:加拿大略胜(现在可以改成澳大利亚大胜) 国际政治上看两国都是英联邦成员国,加拿大是七国集团的成员,虽然排最后,不过也很值得骄傲。但是在各自区域上来看,加拿大只能唯美国马首是瞻,澳洲在自己的区域则是无可争议的老大, 评价:打成平手。 气候上澳洲在南半球,加拿大在北半球,差异很大,至于哪里更好,自然是各有所好,就我个人感觉,澳洲比加拿大最好的一点就是气候了。我在温哥华呆了一年半,那里的气候基本上和中国东北差不多(我本科是在哈尔滨念的),夏天要比哈尔滨凉快,冬天户外要冷一点,但是只要待在室内,你是不会感到冷的,但还是不适合大多数中国人生存。澳洲就不用多说了,冬天有几天会冷,夏天有几天会热,剩下的330的多天简直就像是度假。 评价:澳洲大胜 教育上不太好比较,我本来以为加拿大毕竟是在北美,应该要好一些(当初就是冲着北美去的),不过有两个资料可以参考,一个是泰晤士报的世界大学排名,澳洲有7个大学排名前五十,加拿大只有3个。另外一个是香港人心中留学的选择地,第一就是澳洲,超过10%的香港人都选择去澳洲留学,英国排名第二,加拿大落后美国排第四。造成这种局面的原因很难说,不过个人感觉可能是因为澳洲学校的海外学生数量要强于加拿大,所以造成在
华威大学本科预科 大家都知道,高中出国读英国大学读预科,英国有个著名大学:华威大学,综合排名一直在前10名,商学院也是英国10大商学院之一。预科也是口碑不错。 一、华威大学本科预科:HEFP (Higher Education Foundation Programme) 华威大学预科课程是华威大学设计和授权,由Warwickshire College和Strafford College(沃里克大学和斯特学院)两个学院负责。其中商科和社会科学专业在Strafford College授课,其余的法律、生化和工程科学在Warwickshire College授课。华威大学HEFP预科课程是英国最早开设的预科之一,有着非常高的知名度。 25年的国际学生教学经验 100%升入英国大学的记录 50%的2010年的学生进入英国前10名大学 二、华威大学的预科历史。 英国大学开展预科教育时间并不长,只有20多年的历史。华威大学开始预科有25年的历史,确实是比较早的,通过官方网站介绍,英国的索尔福德大学自称是英国第一个开设本科预科的学校,但做的最成功的应该是:华威大学、伦敦亚非学院,巴斯大学。 在2000年之前,著名大学开办预科的学校并不多,因为招生无法保障,学校没有额外的教育经费,预科的开展都小心翼翼的。伦敦大学亚非学院是唯一开展最成功的大学,因为是亚非学院,学校的专业都是侧重亚非类研究,本国学生选择少,倒是和亚非拉学生接触的多,正好专业对口,由于输送高质量的学生,而被伦敦大学系统广泛接受,曾经有1年7个进入伦敦政治经济学院(LSE)一下子火起来。曾被称为英国第一预科,就是今天这个成就也无人能超过。 伦敦亚非学院在中国 一直是不定期的招生和考试,很多高中学生并不能直接获得学校的信息和介绍。巴斯大学预科自己也非常清高,一直要求通过UCAS申请,门槛雅思6分,标准很高,虽然预科不错,可是在中国的推广力度不大。完全是靠学生自己选择。2010 年巴斯大学扩大了预科规模,针对中国学生也可以直接申请,不需要UCAS。 华威学校教育质量很好,学生质量也不错,基本没有负面新闻,都能去比较理想的大学。多年的推广,让华威在世界各地知名度一直很高。 三、华威的优势 华威知名度还在,吸引优秀学生去的质量很高,6.5分以上的学生比比皆是。 华威大学控制自己的国际学生比例,本校招生数量不大,录取难度很高。 如果华威不能进去,只能选择其他认可的学校 如果认可的学校录取标准很高,可能会去不理想的学校。 华威预科学习如地狱磨练,压力非常大。不适合普通学生。 那么我们的建议是: 如果你是雅思6.5分以上,本人十分优秀,非常渴望进入华威大学,那么你可以考虑读这个预科,毕竟每年有25%的机会进入华威大学,商学院有10%的机会。华威商学院是不招收外面预科学生的。 如果你想进入曼大,这个可以考虑,因为曼大比较喜欢华威预科的学生,有着传统的招生照顾。当然你的成绩也必须达到曼大的标准。(曼大的对华威的标准算是低的)。 如果预科不能毕业是非常糟糕的,如果你个人能力一般,就不要去挑战那些高排名的预科,每个成绩都是需要你付出艰辛努力的。或许在一个排名普通的大学你活的更健康。
立思辰留学360介绍说,伦敦大学学院 (University College London),简称UCL,建校于1826年,位于英国伦敦,是一所世界著名的顶尖高等学府,为享有顶级学术声誉的综合研究型大学。它是伦敦大学联盟(University of London,简称UOL)的创校学院,与剑桥大学、牛津大学、帝国理工学院、伦敦政治经济学院并称“G5超级精英大学”。“G5超级精英大学”代表了英国最顶尖的科研实力、师生质量以及经济实力。 时至今日,曾就读、曾任职或现任职于UCL的校友中,共有32位诺贝尔奖获得者和3位菲尔兹奖(世界数学最高奖)获得者,此外还不乏政治、科学、文化以及娱乐等多个领域的名人。其中包括人工智能“AlphaGo之父”戴密斯·哈萨比斯,“光纤之父”高锟,“电话通信之父”及发明家亚历山大·贝尔,前中国科学院院长卢嘉锡,泰戈尔, 圣雄甘地以及日本前首相伊藤博文和小泉纯一郎等。 UCL主校区邻近大英博物馆、大英图书馆、国王十字车站、牛津街、摄政街和摄政公园,坐落于伦敦市中心,因此使其成为了世界最昂贵的大学之一。该校在2015-16年QS世界大学排名中位列第7名,英国第3名、2015-16年泰晤士高等教育(Times)世界大学排名位列第14名,英国第4名、2015-16年ARWU 世界大学学术排名中位列世界第18名,英国第3名。2014年12月18日,英国唯一由官方每7年发布一次的REF英国大学科研实力排名中,UCL高居全英第2位,仅次于牛津大学。 创建背景 伦敦大学学院是伦敦大学联盟(University of London)的创校学院,与剑桥、牛津、帝国理工、伦敦政经并称“G5超级精英大学”,代表了英国最顶尖的科研实力、师生质量、经济实力,在经济危机时期政府财政预算不减反增, 是英国金三角的名校之一,同时也是英国顶尖研究型大学联盟——罗素大学集团(有24所成员大学,类似于美国的“常春藤”)的成员,享有英国政府最多的财政预算。此外,UCL与剑桥大学,牛津大学,帝国理工学院,伦敦国王学院以及南安普顿大学共同组成英国“南部科学与技术研究六校集团(SES-6)”,该学术科研机构为英国在理工科研领域的中坚力量。UCL是第一个在招生上不论种族、宗教和政治信仰的英国大学,被称为是英国教育平权的先锋。创校之初名为伦敦大学(University of London),1836年加盟伦敦大学联盟,故更名为伦敦大学学院(University College London)。 世界名校 伦敦大学学院是英国顶尖研究型大学联盟---罗素大学集团的一员。“罗素大学集团”(The Russel Group)成立于1994年,由二十四所英国研究型大学组成,包含了牛津大学、剑桥大学与伦敦大学学院等,被称为英国的常春藤联盟,代表着英国最优秀的大学。 有32位来自UCL的学者或毕业生获得诺贝尔奖,3位菲尔兹奖得主。 2009年-2010年度伦敦大学学院的年净收入约 12.6亿美元。 伦敦大学学院(UCL)的主校区邻近大英博物馆和大英图书馆,坐落于伦敦市中心,也因此使其成为了世界最昂贵的大学。UCL在卡塔尔--多哈的校区主要从事考古学及博物馆文物保存研究。UCL在澳大利亚--阿德莱德的校区主要从事能源与环境科学的研究。UCL有欧洲最大的医学研究中心,及生命科学研究所。2009年起, UCL与耶鲁大学在医学方向展开深度合作,建立“UCL-Yale Collaborative”(UCL-耶鲁联合研究部)。后由医学拓展至诸如物理,法律,哲学等多方向的科研合作及博士联合培养。 G5超级精英大学
英国大学学士学位的四大等级大揭秘 英国大学学士学位有严格的等级之分,英格兰大学本科学制为3年(苏格兰4年),大二、大三的考试成绩各占学位课程的50%,大一作为学士学位适应阶段,考试成绩不计算在学位等级里。 英国大学考试满分是100分,40分及格。成绩与对应的学分相联系,采用加权平均的方法计算分数。 英国大学士学位等级划分为四个级别(一等、二等、三等、普通成绩): 一等成绩(First Class) 70分以上 一等成绩通常是大学颁发学位的最高成绩,英国大约有11%的毕业生拿到一等成绩毕业。 不同大学和不同课程之间,拿到一等成绩的学生比例也有很大的差别,法律、物理、工程等专业的学生能拿到一等成绩的人数就比较少。一等成绩一般需要达到70%分以上,英国大学很少见到80%分以上的成绩。 二等成绩(Second Class) 50-69分 二等一级(Upper Second Class) 60-69% 二等一级成绩仅次于一等成绩是第二高成绩,大部分的毕业生都以二等一级成绩取得毕业证书。二等一级成绩是60-69%分。就职雇主都要求毕业生至少要达到这个成绩才会聘用。 二等二级(Lower Second Class) 50-59% 二等二级成绩是仅次于二等一级成绩,得分人数仅次于二等一级的成绩,每年大约有29%的毕业生能拿到这个成绩。二等二级成绩相当于50-59%分。虽然也是二等成绩,但在就业雇主来看和二等一级成绩有很大的差距。 三等成绩(Third Class) 40-49分 三等成绩40-49%,申请硕士学位课程受到限制,一般职业就业不会受到限制。普通成绩(Ordinary degree)普通成绩相当于及格,勉强能拿到学位证书,成绩在40%左右。 在英国人的眼里,A-Level和大学教育是为高级别就业准备的学习课程。研究生教育是为读博士或职业进修提升学习课程。 英国人上完大学就开始工作。想找工作的人,大学毕业成绩也十分重要。一般来说,英国当地的世界顶级企业在招聘的时候,基本上都会明确要求大学应聘者的学位至少达到二等甲等(2.1),不然是没有资格申请的,或者也容易在简历筛选那关被刷掉。 英国名校的研究生入学标准,主要看你的学士学位等级,大学排名在英国硕士申请中并不在乎也不重要。 牛津、剑桥毕业的学生,学位等级达不到一等或二等以上的学位,照样不能申请硕士学位课程。英国大学排名低的学校,毕业成绩好学位等级达到一等或二等以上的学位,一样可以申请牛津、剑桥硕士学位课程。 英国大学毕业证书上,会标明学生所拿的学位等级。在英国留学想要取得一个好的学位等级,需要学生认真对待每一篇论文,每一门考试的。英国老师给分数都很手紧,能上60分的论文都算不错了。考试突击背书,投机取巧的学习方法,在英国严谨的教育风气下,非常不适用了。 来源:扬格剑桥国际高中学校
Personal Statement By XXX Iam writing to apply into theprogram of Comparative Literature at your prestigious university, believing that the study at University College London(UCL)would not only furnish me with world class know-how and practical ability, but broad my vision by experiencing a wealth ofdifferent culture and history.Moreover, I am fully convinced that the profound literary deposits and resourceful cultural heritage in UK would well prepare me to be anexcellent college professor or professional in culturalresearch and dissemination, which is also the career objective of my whole life. Since I was young, I was obsessed with diverse vivid characters in Chinese masterpieces like Journey to the West, Romance of Three Kingdoms, and All Men are Brothers, etc. I spared most of my time in reading varied genres of fictions, novels, lyrics and history documentaries. The more books I read, the more fascinated I was by Chinese culture and literature. Sharing such cultural treasure with the outside world burgeoned in my mind since then. As time passed by, to be a cultural disseminator was haunting me again and again, which turned out to be more and more clear and tempting. In the last year of my high school, I chose teaching Chinese as foreign language (TCFL) as my college major and I succeeded in entering XX University, one of the top 10 universities in China. By virtue of my abundant previous extracurricular reading and diligent work, I achieved a GPA of 3.95 out of 4, ranking top in my class. Being cultivated by such a group of erudite professionals for four years, I was fostered to be proficient in both Chinese and foreign languages and literatures, learningfundamental cultural differences and the features of intercultural exchanges. However, the more I learnt, the more pressing I felt to continue my study, for I realized that understandingonly the literature and culture of my nation cannot necessarily make Chinese literature and culture well understood, and there are occasions when I read foreign works I could not grab the essence of some phrases and idioms. I realized that language and literature might only be the carrier of a culture. The exchange of two different languages is in fact the exchange of two different literatures and cultures. In order to broaden my thinkings, I took the course of comparative literature and got the score of 87. During the whole semester, I have completed two projects: the comparison of girl’s image in Border Town by ShenTs'ung-wen and The Izu Dancer by Kawabata Yasunari, and comparison of tragedy in Tess of the d’Urbervilles by Harker and Rickshaw Boy by Shu Ch'ing-ch'un. I started each project with quantity reading of the author’s works, background, and even his cultural intendancy and religious beliefs. For instance, in the first project, the author Kawabata Yasunariwas deeply influenced by Japan Buddhism, while Japan Buddhism was introduced from China and developed differently. By participating in these two projects, I realized that in comparative literature studies, the valuable part lies in exploring the underlying culture, regime, value, religion, etc from the works. At the same time, a strong inductive and analytical ability to perceive the essence is equally necessary for comparative literature. Fortunately, the learning of this course gave me useful inspirations for my further study. I
伦敦大学学院 空间数据科学与可视化(研究)授课型研究生申请要求
伦敦大学学院简介 学校名称伦敦大学学院 学校英文名称University College London 学校位置英国 | 英格兰 | 伦敦 2020 QS 世界排名8 伦敦大学学院概述 伦敦大学学院(University College London),英文简称UCL,建校于1826年,位于英国伦敦,世界著名的顶尖高等学府,为享有顶级声誉的综合研究型大学,其排名稳居世界各类权威榜单英国前五。 伦敦大学学院位居2020QS世界大学排名世界第8 ,2020泰晤士高等教育世界大学排名世界第15,2020USNews世界大学排名世界第21 , 2019软科世界大学学术排名(ARWU)世界第15 ,在REF 2014 英国大学官方排名中科研实力以及影响力均位列全英第1 。同时位列2018ARWU学科排名医疗技术世界第2,心理学、人体生命科学世界第3;2019QS学科排名中教育学、建筑学世界第1,人类学、考古学、解剖生理学世界前5 , 空间数据科学与可视化(研究)专业简介 空间数据科学与可视化(研究) 空间数据科学与可视化(研究)专业相关信息 专业名称空间数据科学与可视化(研究) 专业英文名称Spatial Data Science and Visualisation MRes 隶属学院建筑环境学院 学制1年 语言要求雅思6.5(6)托福92(读写24听说20) GMAT/GRE 要求不需要
2020 Fall 申请时间11月 学费(当地货币)24,980 空间数据科学与可视化(研究)课程内容 序号课程中文名称课程英文名称 1 * 伦敦大学学院空间数据科学与可视化(研究)研究生申请要求由 M astermate 收集并整理,如果发现疏漏,请以学校官网为准
https://www.doczj.com/doc/1117773952.html, 英国华威大学地址 华威大学坐落在英格兰中部城市考文垂市郊,距离市中心约5公里。学校有巴士直通考文垂及莱明顿温泉镇(Leamington Spa);乘坐维珍火车(Virgin Train)1个小时到达伦敦,London Midland火车约为1小时40分;20分钟可到达伯明翰(Birmingham New Street)。 英国华威大学校区介绍 华威大学的校园占地约300公顷,整个校园分为三个部分:主校区、吉比山校区(Gibbet Hill)和西木校区(Westwood)。学校既有现代化的教学大楼与基础设施,更有景色怡人的湖区和森林。《泰晤士报》的一项调查表示:华威大学的校园被受访者公认为全英最佳大学校园。学校周围的乡村地区不仅风光明媚,更保留着许多名胜古迹,如华威古堡、莎士比亚故居、科尼尔伍兹、考文垂大教堂等。 主校区占地面积约为2.9平方千米,跨越考文垂和华威郡边界。大学最初的建筑均采用20世纪60年代建筑风格,有别于传统英国大学的“红砖”风格。校园既有现代化的教学楼与基础设施,还有景色宜人湖区与森林。由《泰晤士报》组织的一项调查表明:华威大学的校园被公认为全英最佳校园。学校周围的乡村地区不仅风光明媚,更保留着许多名胜古迹,如沃里克古堡、莎士比亚故居、科尼尔伍兹、考文垂大教堂等。 据立思辰留学360介绍,除了位于大学内的主校园,华威大学商学院在全欧洲最高的建筑——碎片大厦(The Shard)开设华威商学院伦敦校区,现在开设人力资源、金融的非全日制硕士课程,以及MBA的全日制和非全日制硕士课程。
https://www.doczj.com/doc/1117773952.html, 英国华威大学排名 英国综合排名 华威大学在英国大学国内排名中稳居前十。 2016《泰晤士报》排名位居全英第六,2015泰晤士排名第八并荣获“英国年度大学”称号, 有五个单科高居全英第一,分别是:会计与金融,经济学,创意写作,戏剧,以及传媒。 2016《卫报》排名全英第六 2016《完全大学指南》排名全英第七 2014 REF*排名:全英GPA第七名, 其中英语语言文学等专业排名全英第一。 英国Highfliers最受顶尖雇主青睐的大学毕业生排名:全英第一。 *REF(Research Excellence Framework)排名是英国大学研究水平的重要衡量标准 世界综合排名 2015-2016QS世界大学排名中第48名
https://www.doczj.com/doc/1117773952.html, 伦敦大学学院2019排名信息如下 2019年《泰晤士高等教育》英国大学排名第 4 位 2019年《卫报》英国大学综合排名第 11 位 2019年《完全大学指南》英国大学综合排名第 10 位 2019年《泰晤士报》英国大学综合排名第 8 位 2019年U.S.News欧洲大学排名第 4 位 2019年U.S.News世界大学500强排名第 21 位 2019年QS世界大学排名第 10 位 2019年《泰晤士高等教育》世界大学排名第 14 位 伦敦大学学院2019硕士预科申请 标准水平 授课式研究生课程包括:
https://www.doczj.com/doc/1117773952.html, 建筑学建筑学硕士(英国皇家建筑学第二部分免试) 土木工程理学硕士 临床药学、国际实践与政策理学硕士 申请要求 总分:65% 各单项最低:60% (建筑学硕士预科课程适用于研究生阶段学习建筑学课程的学生)雅思 总分:6.5 各单项最低:6.0 良好水平 授课式研究生课程包括: 生物科学研究硕士 比较商业经济文学硕士 管理学力学硕士 申请要求 总分:70% 各单项最低:65% 雅思 总分:7.0 各单项最低:6.5 高级水平
https://www.doczj.com/doc/1117773952.html, 授课式研究生课程包括: 比较文学文学硕士 国际公共政策理学硕士 法律学法学硕士 申请要求 总分:75% 各单项最低:65% 雅思 总分:7.5 各单项最低:6.5 伦敦大学学院硕士预科课程优势 ·寖入式教育:您将在英国教育系统中获得宝贵经验,并迅速了解英国所需要的学习方式。立思辰留学360介绍说,授课方式与硕士学位课程一致,包括讲座、课堂教学及导师辅导。伦敦大学学院平均每周20个课时;通过此课程,学生能够更加自信地参与研究生水平的各项活动。
雏鹰文化培训中心https://www.doczj.com/doc/1117773952.html, 顺德碧桂园业主论坛https://www.doczj.com/doc/1117773952.html, 雅思(IELTS)分数档次详细说明 9分 Expert User. Has fully operational command of thelanguage:appropriate, accurate and fluent with completeunderstanding. 成绩极佳,能将英语运用自如,精确、流利并能完全理解. 8分 Very Good User. Has fully operational command of the languagewithonly occasional unsystematic inaccuracies andinappropriacies.Misunderstandings may occur in unfamiliarsituations. Handlescomplex detailed argumentation well. 非常良好,能将英语运用自如,只是偶尔有不连接的错误和不恰当,在不熟悉的状况下可能出现误解,可将复杂细节的争论掌握的相当好. 7分 Good User. Has operational command of the language, thoughwithoccasional inaccuracies, inappropriacies and misunderstandingsinsome situations. Generally handles complex language wellandunderstands detailed reasoning. 良好,有能力运用英语,虽然在某些情况有时会发生不准确、不适当和误解,大致可将复杂的英语掌握的不错,也理解其全部内容. 6分(澳大利亚移民&英国留学分数线) Competent User. Has generally effective command of thelanguagedespite some inaccuracies, inappropriacies andmisunderstandings.Can use and understand fairly complex language,particularly infamiliar situations. 及格,大致能有效的运用英语,虽然有不准确、不适当和误解发生,能使用并理解相当复杂的英语,特别是在熟悉的情况时. 5分(加拿大移民&新西兰移民分数线)